Hardware Trojans: A Threat for CyberSecurity
|
|
|
- Eileen Hardy
- 10 years ago
- Views:
Transcription
1 Hardware Trojans: A Threat for CyberSecurity Julien Francq [email protected] Cassidian CyberSecurity 2013, July the 8th
2 Outline 1 Introduction to Hardware Trojans
3 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 4 5 3
4 Hardware Trojan (HT) Malicious modifications of an Integrated Circuit (IC) during its design flow 4
5 Context Outsourcing of the fabrication of the ICs Difficult to ensure the trust in all the steps of the design flow Trusted Intentional mistakes Idea Specification Malicious IP-Cores Malicous Design Tampering Files Design (HDL) Synthesis IP Cores Manipulated Tools Mapping FPGA Place & Route ASIC Tampering Files Manipulation While Loading Config File Loader Tampering Files Hardware Layout Production Manipulate Design Process Backdoors FPGA ASIC Attack IC Malicious External Components Board IC 5
6 Hardware Trojans in Practice 2005 : US Department of Defense 2007 : DARPA Trust in IC Program 2007 : Israël vs. Syria 2009 : Hot Topic of CHES conference After 2009 : other conferences (DATE, HOST, CARDIS, ReConFig, etc.) [Skorobogatov et al. : Breaktrough Silicon Scanning Discovers Backdoor in Military Chip, CHES 2012] HTs : real and emerging threat 6
7 Quantification of Risks Overproduction Software HTs cloning Attackers Fab Competitors Terrorists Goal Feed the Grey IP Theft Denial of Service, Market Data Theft, Sabotage Impact Economical Economical Risks on Security, Economy, Infrastructures (Society) Risks Impact Risks too important to be neglicted 7
8 Possible Payloads Kill switch Fighters Dysfonctional circuit Satellite which works only 6 months Secret information leakage Ciphered communications Help a malware by providing a backdoor Privilege escalation, automatic login, password theft Prevent from going to sleep mode Autonomy etc. 8
9 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 4 5 9
10 Taxonomy : tree where each branch defines a different property In the ideal case, a specific HT must be on only one leaf of the tree Benefits of the taxonomy Systematic study of their characteristics Specific detection methods for each HT class Benchmark circuits for each class Best existing taxonomy : Trust-Hub 10
11 11 Introduction to Hardware Trojans Trust-Hub Taxonomy
12 Factoring the Taxonomy 4 (effects) 5 (locations) 5 (insertion phases) 6 (abstraction levels) 5 (activation mechanisms) = 3000 different HTs! Very rich taxonomy! Impossible to implement them all, and then detect them Factoring this taxonomy Total : 100 HTs 12
13 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
14 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
15 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Overview HT Protection Post Production Detection Prevention Destructive Non-Destructive Supportive Design Secure Design Trusted Production Optical Run-Time Test-Time Side Channel Analysis Logic Testing No method is 100% successfull! 15
16 Detect HTs? Not so easy... Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 1 Systems on Chip are more and more complex, and detecting a small malicious modification is difficult 2 Reverse-engineering inspection is costly and difficult No guarantee that the remaining ICs are HT-free 3 By nature, HTs are designed to be stealthy Not easily detectable with conventional logic testing 4 By nature, HTs are small to be not easily detected by optical analysis Difficult to detect them with side-channel (power consumption, electromagnetic radiations, etc.) analysis 16
17 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
18 Test Generation (1/2) Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Conventional logic testing cannot be used to reliably detect HT Manufacturing defects (stuck-at-faults) HT effects Difficult to trigger a HT Time-bombs Some HTs have no impact on functional outputs (Trojan Side-Channels) Vast spectrum of possible HTs 18
19 Test Generation (2/2) Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary HTs are on low controllability and observability nodes for a rare triggering Extremely challenging to exhaustively generate test vectors for triggering a HT 19
20 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Deterministic vs. Probabilistic Approach Deterministic approach difficult Many possible HTs Function of some IC nodes Exhaustive enumeration impossible Statistic approach : 1 Find rare events in the circuit 2 Get a list of HTs which can be inserted 3 Generate test vectors and estimate their coverage 4 Set of high quality test vectors 85% reduction in testset length compared to a random approach, but less efficient with big triggers and takes a long time 20
21 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
22 Side-Channel Analysis Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Any HT in the IC should modify its leakage current (IDDQ), dynamic power trace (IDDT), path-delay characteristic, ElectroMagnetic (EM) radiation. Don t need to trigger a HT for measuring its effects Test vectors generation easier than for logic testing Needs HT-free circuits Get side-channel measurements and then reverse-engineering to check if the IC is HT-free If so, the measurements become a reference, and we can then compare the side-channels of the other circuits 22
23 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Global Side-Channel Analysis Green : RSA signal Red : Process noise (offset) Black : HT signal (offset) 23
24 Local Side-Channel Analysis Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Local Side-Channel Analysis more efficient than global ones Needs again HT-free circuits Maximize/Minimize the activity of some IC areas 24
25 Noise and Sensitivity Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 25
26 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
27 Some Subtleties Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Added circuitry for the HT detection must not be infected itself At best, the added circuitry is disabled (e.g., fault countermeasure) At worst, it can be turned into a backdoor (e.g., scan chain) A HT triggering logic can exploit the Test/Scan Enable control line to disable itself Parametric HTs very difficult to detect 27
28 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
29 Summary Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary Complementary methods Combine test-time and run-time methods Modify the IC for assistive and preventive methods 29
30 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
31 Introduction To improve HT detection rate, modify the IC Prevent from the insertion of HT Ease side-channel analysis and logic testing 4 main methods : Delay-Based Methods Rare Event Removal Design for Trojan Test Proof-Carrying Hardware Run-Time Detection Methods 31
32 Run-Time Methods Last line of defense On-line monitoring of the IC in real-time, for checks : Critical operations, Idle mode, Security policies, Performance or availability of some units, etc. Costly 32
33 Run-Time Methods Disable one suspect block or force one operation SPN : Signal Probe Network SM : Security Monitor ( FSM) SECOPRO : Security and Control Processor Configurations ciphered and stored in secured Flash memory Overhead? 33
34 1 Introduction to Hardware Trojans 2 3 Overview Logic Testing : Challenges & Solutions Side-Channels : Challenges & Solutions Some Subtleties Summary
35 A French Project : HOMERE FUI14 ( ) : HOMERE project Large companies Cassidian CyberSecurity, Gemalto Small company Secure-IC Academic partners ARMINES, CEA-LETI, LIRMM, Télécom ParisTech Governmental help and support ANSSI, (DGA) 35
36 HOMERE : First Results Infection of Benchmark Circuits General Side-Channel Test-Bench HT Detection via Visual Inspection Internal Delays Extraction by Fault Analysis 36
37 HOMERE : First Results Infection of Benchmark Circuits General Side-Channel Test-Bench HT Detection via Visual Inspection Internal Delays Extraction by Fault Analysis 37
38 Infection of Benchmark Circuits Can be done at RTL level (VHDL) But it will greatly change the final layout Trust-Hub website suggest to implement the HT in VHDL level, place and route the circuit, and then delete the HT Quicker than adding HT manually, but we will get a pair of (HT-free/Infected circuit) for each HT Will be done at netlist level We have a common reference for each HT Manipulation of.ngc files for Xilinx We can then modify : LUT content Routing Configurations (FFs or LATCH, IBUF delays in IOB, etc.) 38
39 HT Inserted in RTL Mode key k lock state lock state unlock lock key lock state unlock lock k lock state I0 I1 39
40 Slice of a Virtex-5 50T A6 A5 A4 A3 A2 A1 LUT D Q6 Q6 = A1... D DQ A6 A5 A4 A3 A2 A1 LUT C Q6 Q6 = A1... C CQ A6 A5 A4 A3 A2 A1 LUT B Q6 = A1... B BQ A6 A5 A4 A3 A2 A1 LUT A Q6 = A1... A AQ 40
41 41 Introduction to Hardware Trojans The same on FPGA Editor
42 Non-Infected Circuit key(1) key(3) key(2) key(6) key(0) key(4) A6 A5 A4 A3 A2 A1 LUT D Q6 D DQ Q6 = ( A5*( A2*( A3*( A4*( A1* A6))))) N2 N2 A6 unlock A5 lock state A4 key(7) A3 lock A2 key(0) A1 A6 A5 A4 A3 A2 A1 LUT C LUT B Q6 C lock state CQ lock state Q6 = (( A2*((A5*(A3*(A1*A6)))+A4))+ (A2*(A5*(A3*(A1*( A4*A6)))))) B BQ Q6 = A1... A6 A5 A4 A3 A2 A1 LUT A Q6 = A1... A AQ 42
43 43 Introduction to Hardware Trojans Non-Infected Circuit
44 Infected Circuit key(1) key(3) key(2) key(6) key(0) key(4) A6 A5 A4 A3 A2 A1 Q6 D N2 LUT D DQ Q6 = ( A5*( A2*( A3*( A4*( A1* A6))))) N2 A6 unlock A5 lock state A4 key(7) A3 lock A2 key(0) A1 NET 0 I0 I1 A6 A5 A4 A3 A2 A1 LUT C LUT B Q6 C CQ NET 0 Q6 = (( A2*((A5*(A3*(A1*A6)))+A4))+ (A2*(A5*(A3*(A1*( A4*A6)))))) B lock state BQ lock state Q6 = (A6+(A5*A4)) A6 A5 A4 A3 A2 A1 LUT A Q6 = A1... A AQ 44
45 45 Introduction to Hardware Trojans Infected Circuit
46 46 Introduction to Hardware Trojans Original Circuit
47 47 Introduction to Hardware Trojans Infected Circuit at Netlist Level
48 Infected Circuit at RTL Level Trojan Trigger : 32-bit counter in the I/O of an AES. Incremented at each clock cycle. HT activated when counter = FFFFFFFF. After activation, no more ciphertext will be sent to the output. 48
49 HOMERE : First Results Infection of Benchmark Circuits General Side-Channel Test-Bench HT Detection via Visual Inspection Internal Delays Extraction by Fault Analysis 49
50 Our Goals We want : to understand the development process of an HT, a list of candidates HTs, to implement these HTs, to check that inserted HTs can be triggered. We want a side-channel test-bench which : is generic, allows to test different circuits......infected by different HTs. Side-chAnnel Standard Evaluation BOard (SASEBO) 50
51 Overview of SASEBO Ethernet USB SASEBO Board CTRL FPGA CUT FPGA Trigger Signal 2 FPGAs : 1 for the Circuit Under Test (CUT), 1 for the control (can be used for different CUTs). USB connection between PC and SASEBO 51
52 Side Channel Analysis Side Channel Attack Introduction to Hardware Trojans Side-Channel Analysis Attack (for retrieving keys) Analysis (for detecting HTs) Set Input Phase key key1 Run Phase Read Output Phase data data1 result res start running clock Input 1 t Input 2 Input 3 Output start running Input Vector 52
53 Lessons for our Test-Bench In general : we must generate complex sequences of input vectors, we have to get intermediate outputs, we want real-time I/O processing. To trigger an HT, and for detect it, we need : to wait for a long time, to react according to the behavior of the tested circuit. For side-channel analysis : Dynamic triggering of the measurements. 53
54 Workflow Test Scenario Definition Simulation SASEBO Board Parameter Setup Scenario Download Commands Outputvectors Read Back Parameter Setup Wait on Trigger Data Acquisition Data Read Back Measurement Equipment Compare Outputs (Simulation vs Actual) Different Outputs Perform SCA Potential Anomalies Obvious Anomalies Refine Scenario Nothing Suspicious Design OK HT found 54
55 Test Scenario Description USB communication of the test scenario file Stored in the memory (BRAM) of control FPGA CTRL FPGA Commands and Parameters USB Controller Memory CUT Controller Inter 38 FPGA Bus Scenario and Output Vectors Ext. Trigger 3 options for sending the next input vector Immediate Time condition Output condition External triggering flag Data format? 55
56 Data Format 37 IV 0 TC ET 15 D 0 37 OC 0 37 OM 0 reserved IV : Input Vector, TC : Transition Condition, time or output conditions to send the next IV, ET : External Trigger, sent to the oscilloscope for starting measurements, D : Delay : number of clock cycles to delay the next IV, OM : Output Mask : which bits we are looking at? OC : Output Condition : values of these bits to send the next IV. 56
57 Test Scenario Format Scenario Description Parameters Parameter 1 Parameter 2 Input Profile n Commands Command 1 Command 2 Value 1 Value IV TC ET D OC OM reserved IV TC ET D OC OM reserved IV TC ET D OC OM reserved IV TC ET D OC OM reserved Attributes Name Version Scenario Name Definition Version Parameters : tristate mask Controller supporting this format validated 57
58 HOMERE : First Results Infection of Benchmark Circuits General Side-Channel Test-Bench HT Detection via Visual Inspection Internal Delays Extraction by Fault Analysis 58
59 Principle [Bhasin et al., FDTC 2013] Study the effect of HT insertion at the layout level (GDSII) Is it possible to detect HTs via visual inspection? CUT : AES-128 HT : key leakage with fault injection (Piret/Quisquater attack) triggered on a specific plaintext Placement density of the circuit : 50% 99% HT trigger size : AND gates Cadence SOC Encounter 59
60 AES Layout (Metal6) AES Layouts for the 6th Metal Layer (1200 µm 1200 µm) with placement density = 50% : (left) HT-Free AES, (middle) AES with 1 AND gate HT, (right) AES with 128 AND gates HT (Credits : Télécom ParisTech) 60
61 Results Preventive method : it is impossible to insert a HT in ECO mode if placement density > 90% (Post-mortem) detection : visual correlation decreases when HT size and placement density of the circuit increase Low Cost way to detect HTs by the correlation between GDSII and circuit images More difficult to detect the very small HTs 61
62 HOMERE : First Results Infection of Benchmark Circuits General Side-Channel Test-Bench HT Detection via Visual Inspection Internal Delays Extraction by Fault Analysis 62
63 Principle [Exurville et al., ReCoSoC 2013] An inserted HT will modify internal delays Idea : compare the fault sensitivity analysis of a genuine circuit and an infected one Glitches on external clock The clock glitch is a local change of a period The choice of the injection cycle is possible Setup time violations Metastability (non-deterministic behavior) 63
64 Fault Sensitivity Analysis in HT-Free IC (Credits : CEA-LETI) 64
65 Fault Sensitivity Analysis in Infected IC (Credits : CEA-LETI) 65
66 First Results AES characterization thanks to the fault sensitivity analysis of each AES bit An inserted HT can influence the critical paths Challenges : Process variations HTs inserted in non-critical paths Fault countermeasures 66
67 Hardware Trojans are real threats for integrated circuits HT taxonomy is very rich No HT detection method of the state-of-the-art is 100% successful 3 lines of defense : Test-Time Methods Run-Time Methods A French initiative : HOMERE project Very encouraging first results : Infected benchmark circuits will be available soon A common platform for side-channel analysis A low-cost way to detect some HTs by visual inspection A low-cost way to extract internal delays of ICs by clock glitching Other on-going works : Logic test Run-time HT detection 67
68 Thanks! Questions? 68
69 Shadow Registers Measurement of delays between registers Shadow Clock has a negative skew with respect to System Clock for characterizing the path delay Millions of paths Big overhead 69
70 Ring Oscillators (1/2) Alternative to shadow registers Build new paths and measure the delays of these paths Small area Easy insertion Under normal operation, all the inserted ring oscillators will be muted to avoid power consumption 70
71 Ring Oscillators (2/2) Any malicious modifications to the original design woud also change parameters of pre-inserted ROs Frequency change for the ROs How many ROs are needed where they should be located inside the chip? Construct ROs from gates of the original design by inserting multiplexors, NAND gates and inverters On-chip frequency measurement modules Drawbacks Difficult automation of RO insertion Easy to evade 71
72 72 Introduction to Hardware Trojans Rare Event Removal (1/2)
73 Rare Event Removal (2/2) Not adapted 73
74 Introduction to Hardware Trojans Partenaires HOMERE 74
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
PFP Technology White Paper
 PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
Horst Görtz Institute for IT-Security
 Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices
 An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany [email protected]
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany [email protected]
Implementation Details
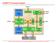 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
Microsemi Security Center of Excellence
 Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Secure application programming in the presence of side channel attacks. Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203
 Secure application programming in the presence of side channel attacks Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203 Attacks in the field Survey 2007*, Hong Kong: Asia-Pacific Pay-TV
Secure application programming in the presence of side channel attacks Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203 Attacks in the field Survey 2007*, Hong Kong: Asia-Pacific Pay-TV
How To Design A Chip Layout
 Spezielle Anwendungen des VLSI Entwurfs Applied VLSI design (IEF170) Course and contest Intermediate meeting 3 Prof. Dirk Timmermann, Claas Cornelius, Hagen Sämrow, Andreas Tockhorn, Philipp Gorski, Martin
Spezielle Anwendungen des VLSI Entwurfs Applied VLSI design (IEF170) Course and contest Intermediate meeting 3 Prof. Dirk Timmermann, Claas Cornelius, Hagen Sämrow, Andreas Tockhorn, Philipp Gorski, Martin
Local Heating Attacks on Flash Memory Devices. Dr Sergei Skorobogatov
 Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Modeling a GPS Receiver Using SystemC
 Modeling a GPS Receiver using SystemC Modeling a GPS Receiver Using SystemC Bernhard Niemann Reiner Büttner Martin Speitel http://www.iis.fhg.de http://www.iis.fhg.de/kursbuch/kurse/systemc.html The e
Modeling a GPS Receiver using SystemC Modeling a GPS Receiver Using SystemC Bernhard Niemann Reiner Büttner Martin Speitel http://www.iis.fhg.de http://www.iis.fhg.de/kursbuch/kurse/systemc.html The e
KEEP IT SYNPLE STUPID
 Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Understanding Integrated Circuit Security Threats. Asif Iqbal Senior Program Manager, Apple Inc. SDM 11
 Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Clocking. Figure by MIT OCW. 6.884 - Spring 2005 2/18/05 L06 Clocks 1
 ing Figure by MIT OCW. 6.884 - Spring 2005 2/18/05 L06 s 1 Why s and Storage Elements? Inputs Combinational Logic Outputs Want to reuse combinational logic from cycle to cycle 6.884 - Spring 2005 2/18/05
ing Figure by MIT OCW. 6.884 - Spring 2005 2/18/05 L06 s 1 Why s and Storage Elements? Inputs Combinational Logic Outputs Want to reuse combinational logic from cycle to cycle 6.884 - Spring 2005 2/18/05
Best Practises for LabVIEW FPGA Design Flow. uk.ni.com ireland.ni.com
 Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
MXMedia CipherStream. Preliminary Assessment. Copyright 2012 Farncombe 1.0. Author: T +44 1256 844161 F +44 1256 844162 www.farncombe.
 MXMedia CipherStream Preliminary Assessment 1.0 Author: T +44 1256 844161 F +44 1256 844162 www.farncombe.com Copyright 2012 Farncombe Belvedere Basing View Basingstoke RG21 4HG This document and the information
MXMedia CipherStream Preliminary Assessment 1.0 Author: T +44 1256 844161 F +44 1256 844162 www.farncombe.com Copyright 2012 Farncombe Belvedere Basing View Basingstoke RG21 4HG This document and the information
Delay Characterization in FPGA-based Reconfigurable Systems
 Institute of Computer Architecture and Computer Engineering University of Stuttgart Pfaffenwaldring 47 D 70569 Stuttgart Master s Thesis Nr. 3505 Delay Characterization in FPGA-based Reconfigurable Systems
Institute of Computer Architecture and Computer Engineering University of Stuttgart Pfaffenwaldring 47 D 70569 Stuttgart Master s Thesis Nr. 3505 Delay Characterization in FPGA-based Reconfigurable Systems
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Design of a High Speed Communications Link Using Field Programmable Gate Arrays
 Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
IL2225 Physical Design
 IL2225 Physical Design Nasim Farahini [email protected] Outline Physical Implementation Styles ASIC physical design Flow Floor and Power planning Placement Clock Tree Synthesis Routing Timing Analysis Verification
IL2225 Physical Design Nasim Farahini [email protected] Outline Physical Implementation Styles ASIC physical design Flow Floor and Power planning Placement Clock Tree Synthesis Routing Timing Analysis Verification
Design Verification & Testing Design for Testability and Scan
 Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
TIMING-DRIVEN PHYSICAL DESIGN FOR DIGITAL SYNCHRONOUS VLSI CIRCUITS USING RESONANT CLOCKING
 TIMING-DRIVEN PHYSICAL DESIGN FOR DIGITAL SYNCHRONOUS VLSI CIRCUITS USING RESONANT CLOCKING BARIS TASKIN, JOHN WOOD, IVAN S. KOURTEV February 28, 2005 Research Objective Objective: Electronic design automation
TIMING-DRIVEN PHYSICAL DESIGN FOR DIGITAL SYNCHRONOUS VLSI CIRCUITS USING RESONANT CLOCKING BARIS TASKIN, JOHN WOOD, IVAN S. KOURTEV February 28, 2005 Research Objective Objective: Electronic design automation
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic
 Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
Digital Systems. Role of the Digital Engineer
 Digital Systems Role of the Digital Engineer Digital Design Engineers attempt to clearly define the problem(s) Possibly, break the problem into many smaller problems Engineers then develop a strategy for
Digital Systems Role of the Digital Engineer Digital Design Engineers attempt to clearly define the problem(s) Possibly, break the problem into many smaller problems Engineers then develop a strategy for
Power Reduction Techniques in the SoC Clock Network. Clock Power
 Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
BECKHOFF. Application Notes. www.beckhoffautomation.com. BC9000: Getting Started Guide. For additional documentation, please visit.
 BECKHOFF Application Notes www.beckhoffautomation.com BC9000: Getting Started Guide BC-AppNote-002 1.0 27 August 2007 This application note is intended for the first time user of the BC9000 and TwinCAT
BECKHOFF Application Notes www.beckhoffautomation.com BC9000: Getting Started Guide BC-AppNote-002 1.0 27 August 2007 This application note is intended for the first time user of the BC9000 and TwinCAT
VLSI Design Verification and Testing
 VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: [email protected]). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: [email protected]). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
Physical Security: Status and Outlook
 Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
Computer Security DD2395
 Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger [email protected] Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger [email protected] Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
DDS. 16-bit Direct Digital Synthesizer / Periodic waveform generator Rev. 1.4. Key Design Features. Block Diagram. Generic Parameters.
 Key Design Features Block Diagram Synthesizable, technology independent VHDL IP Core 16-bit signed output samples 32-bit phase accumulator (tuning word) 32-bit phase shift feature Phase resolution of 2π/2
Key Design Features Block Diagram Synthesizable, technology independent VHDL IP Core 16-bit signed output samples 32-bit phase accumulator (tuning word) 32-bit phase shift feature Phase resolution of 2π/2
Architectures and Platforms
 Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
System-on. on-chip Design Flow. Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems. jouni.tomberg@tut.
 System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
CHAPTER 11: Flip Flops
 CHAPTER 11: Flip Flops In this chapter, you will be building the part of the circuit that controls the command sequencing. The required circuit must operate the counter and the memory chip. When the teach
CHAPTER 11: Flip Flops In this chapter, you will be building the part of the circuit that controls the command sequencing. The required circuit must operate the counter and the memory chip. When the teach
IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits
 IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits SUMMARY CONTENTS 1. CONTEXT 2. TECHNOLOGY TRENDS 3. MOTIVATION 4. WHAT IS IC-EMC 5. SUPPORTED STANDARD 6. EXAMPLES CONTEXT - WHY
IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits SUMMARY CONTENTS 1. CONTEXT 2. TECHNOLOGY TRENDS 3. MOTIVATION 4. WHAT IS IC-EMC 5. SUPPORTED STANDARD 6. EXAMPLES CONTEXT - WHY
Design Compiler Graphical Create a Better Starting Point for Faster Physical Implementation
 Datasheet Create a Better Starting Point for Faster Physical Implementation Overview Continuing the trend of delivering innovative synthesis technology, Design Compiler Graphical delivers superior quality
Datasheet Create a Better Starting Point for Faster Physical Implementation Overview Continuing the trend of delivering innovative synthesis technology, Design Compiler Graphical delivers superior quality
White Paper FPGA Performance Benchmarking Methodology
 White Paper Introduction This paper presents a rigorous methodology for benchmarking the capabilities of an FPGA family. The goal of benchmarking is to compare the results for one FPGA family versus another
White Paper Introduction This paper presents a rigorous methodology for benchmarking the capabilities of an FPGA family. The goal of benchmarking is to compare the results for one FPGA family versus another
Cryptographic Rights Management of FPGA Intellectual Property Cores
 Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom [email protected] ABSTRACT As the capacity of FPGA s increases
Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom [email protected] ABSTRACT As the capacity of FPGA s increases
BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH
 WHITE PAPER METRIC-DRIVEN VERIFICATION ENSURES SOFTWARE DEVELOPMENT QUALITY BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH INTRODUCTION The complexity of electronic systems is rapidly
WHITE PAPER METRIC-DRIVEN VERIFICATION ENSURES SOFTWARE DEVELOPMENT QUALITY BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH INTRODUCTION The complexity of electronic systems is rapidly
40G MACsec Encryption in an FPGA
 40G MACsec Encryption in an FPGA Dr Tom Kean, Managing Director, Algotronix Ltd, 130-10 Calton Road, Edinburgh EH8 8JQ United Kingdom Tel: +44 131 556 9242 Email: [email protected] February 2012 1 MACsec
40G MACsec Encryption in an FPGA Dr Tom Kean, Managing Director, Algotronix Ltd, 130-10 Calton Road, Edinburgh EH8 8JQ United Kingdom Tel: +44 131 556 9242 Email: [email protected] February 2012 1 MACsec
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems
 Harris Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems David Harris Harvey Mudd College [email protected] Based on EE271 developed by Mark Horowitz, Stanford University MAH
Harris Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems David Harris Harvey Mudd College [email protected] Based on EE271 developed by Mark Horowitz, Stanford University MAH
SanDisk Enterprise Secure USB Flash Drive Security Vulnerability
 SanDisk Enterprise Secure USB Flash Drive Security Vulnerability Device CD-ROM partition can be a host for malware and crimeware February 2009 Introduction After my recent experiences with the Read Only
SanDisk Enterprise Secure USB Flash Drive Security Vulnerability Device CD-ROM partition can be a host for malware and crimeware February 2009 Introduction After my recent experiences with the Read Only
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
PROGETTO DI SISTEMI ELETTRONICI DIGITALI. Digital Systems Design. Digital Circuits Advanced Topics
 PROGETTO DI SISTEMI ELETTRONICI DIGITALI Digital Systems Design Digital Circuits Advanced Topics 1 Sequential circuit and metastability 2 Sequential circuit - FSM A Sequential circuit contains: Storage
PROGETTO DI SISTEMI ELETTRONICI DIGITALI Digital Systems Design Digital Circuits Advanced Topics 1 Sequential circuit and metastability 2 Sequential circuit - FSM A Sequential circuit contains: Storage
SECURE USB FLASH DRIVE. Non-Proprietary Security Policy
 SECURE USB FLASH DRIVE Non-Proprietary Security Policy FIPS 140-2 SECURITY POLICY VERSION 9 Page 1 of 10 Definitions and Acronyms AES Advanced Encryption Standard CBC Cipher Block Chaining CRC Cyclic Redundancy
SECURE USB FLASH DRIVE Non-Proprietary Security Policy FIPS 140-2 SECURITY POLICY VERSION 9 Page 1 of 10 Definitions and Acronyms AES Advanced Encryption Standard CBC Cipher Block Chaining CRC Cyclic Redundancy
Case Study: Improving FPGA Design Speed with Floorplanning
 Case Study: Improving FPGA Design Speed with Floorplanning - An introduction to Xilinx PlanAhead 10.1 by Consultant Kent Salomonsen ([email protected]) Picture this: the RTL is simulating
Case Study: Improving FPGA Design Speed with Floorplanning - An introduction to Xilinx PlanAhead 10.1 by Consultant Kent Salomonsen ([email protected]) Picture this: the RTL is simulating
Latch Timing Parameters. Flip-flop Timing Parameters. Typical Clock System. Clocking Overhead
 Clock - key to synchronous systems Topic 7 Clocking Strategies in VLSI Systems Peter Cheung Department of Electrical & Electronic Engineering Imperial College London Clocks help the design of FSM where
Clock - key to synchronous systems Topic 7 Clocking Strategies in VLSI Systems Peter Cheung Department of Electrical & Electronic Engineering Imperial College London Clocks help the design of FSM where
A8.1 Asset Management Responsibility for assets: To identify organisational assets and define appropriate protection responsibilities.
 A8.1 Asset Management Responsibility for assets: To identify organisational assets and define appropriate protection responsibilities. 8.1.1 Inventory of assets. Tripwire IP360 provides comprehensive host
A8.1 Asset Management Responsibility for assets: To identify organisational assets and define appropriate protection responsibilities. 8.1.1 Inventory of assets. Tripwire IP360 provides comprehensive host
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip
 Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
Network- vs. Host-based Intrusion Detection
 Network- vs. Host-based Intrusion Detection A Guide to Intrusion Detection Technology 6600 Peachtree-Dunwoody Road 300 Embassy Row Atlanta, GA 30348 Tel: 678.443.6000 Toll-free: 800.776.2362 Fax: 678.443.6477
Network- vs. Host-based Intrusion Detection A Guide to Intrusion Detection Technology 6600 Peachtree-Dunwoody Road 300 Embassy Row Atlanta, GA 30348 Tel: 678.443.6000 Toll-free: 800.776.2362 Fax: 678.443.6477
Fondamenti su strumenti di sviluppo per microcontrollori PIC
 Fondamenti su strumenti di sviluppo per microcontrollori PIC MPSIM ICE 2000 ICD 2 REAL ICE PICSTART Ad uso interno del corso Elettronica e Telecomunicazioni 1 2 MPLAB SIM /1 MPLAB SIM is a discrete-event
Fondamenti su strumenti di sviluppo per microcontrollori PIC MPSIM ICE 2000 ICD 2 REAL ICE PICSTART Ad uso interno del corso Elettronica e Telecomunicazioni 1 2 MPLAB SIM /1 MPLAB SIM is a discrete-event
Von der Hardware zur Software in FPGAs mit Embedded Prozessoren. Alexander Hahn Senior Field Application Engineer Lattice Semiconductor
 Von der Hardware zur Software in FPGAs mit Embedded Prozessoren Alexander Hahn Senior Field Application Engineer Lattice Semiconductor AGENDA Overview Mico32 Embedded Processor Development Tool Chain HW/SW
Von der Hardware zur Software in FPGAs mit Embedded Prozessoren Alexander Hahn Senior Field Application Engineer Lattice Semiconductor AGENDA Overview Mico32 Embedded Processor Development Tool Chain HW/SW
White Paper 40-nm FPGAs and the Defense Electronic Design Organization
 White Paper 40-nm FPGAs and the Defense Electronic Design Organization Introduction With Altera s introduction of 40-nm FPGAs, the design domains of military electronics that can be addressed with programmable
White Paper 40-nm FPGAs and the Defense Electronic Design Organization Introduction With Altera s introduction of 40-nm FPGAs, the design domains of military electronics that can be addressed with programmable
Security IC Platform Protection Profile
 Security IC Platform Protection Profile Version 1.0 15.06.2007 developed by Atmel Infineon Technologies AG NXP Semiconductors Renesas Technology Europe Ltd. STMicroelectronics Registered and Certified
Security IC Platform Protection Profile Version 1.0 15.06.2007 developed by Atmel Infineon Technologies AG NXP Semiconductors Renesas Technology Europe Ltd. STMicroelectronics Registered and Certified
Information Security Group (ISG) Core Research Areas. The ISG Smart Card Centre. From Smart Cards to NFC Smart Phone Security
 Information Security Group (ISG) From Smart Cards to NFC Smart Phone Security Information Security Group Activities Prof. Keith and Mayes Research From the Information Security Group ACE-CSR at Royal Holloway
Information Security Group (ISG) From Smart Cards to NFC Smart Phone Security Information Security Group Activities Prof. Keith and Mayes Research From the Information Security Group ACE-CSR at Royal Holloway
Hardware Implementation of Improved Adaptive NoC Router with Flit Flow History based Load Balancing Selection Strategy
 Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion
 Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
ARM Ltd 110 Fulbourn Road, Cambridge, CB1 9NJ, UK. *[email protected]
 Serial Wire Debug and the CoreSight TM Debug and Trace Architecture Eddie Ashfield, Ian Field, Peter Harrod *, Sean Houlihane, William Orme and Sheldon Woodhouse ARM Ltd 110 Fulbourn Road, Cambridge, CB1
Serial Wire Debug and the CoreSight TM Debug and Trace Architecture Eddie Ashfield, Ian Field, Peter Harrod *, Sean Houlihane, William Orme and Sheldon Woodhouse ARM Ltd 110 Fulbourn Road, Cambridge, CB1
Digital IC Design Flow
 Collège Militaire Royal du Canada (Cadence University Alliance Program Member) Department of Electrical and Computer Engineering Départment de Génie Electrique et Informatique RMC Microelectronics Lab
Collège Militaire Royal du Canada (Cadence University Alliance Program Member) Department of Electrical and Computer Engineering Départment de Génie Electrique et Informatique RMC Microelectronics Lab
Testing & Verification of Digital Circuits ECE/CS 5745/6745. Hardware Verification using Symbolic Computation
 Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla ([email protected]) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla ([email protected]) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
SDLC Controller. Documentation. Design File Formats. Verification
 January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: [email protected] URL: www.cast-inc.com Features AllianceCORE
January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: [email protected] URL: www.cast-inc.com Features AllianceCORE
Serial port interface for microcontroller embedded into integrated power meter
 Serial port interface for microcontroller embedded into integrated power meter Mr. Borisav Jovanović, Prof. dr. Predrag Petković, Prof. dr. Milunka Damnjanović, Faculty of Electronic Engineering Nis, Serbia
Serial port interface for microcontroller embedded into integrated power meter Mr. Borisav Jovanović, Prof. dr. Predrag Petković, Prof. dr. Milunka Damnjanović, Faculty of Electronic Engineering Nis, Serbia
Physical Attacks on Tamper Resistance: Progress and Lessons
 Physical Attacks on Tamper Resistance: Progress and Lessons Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Why do we need tamper resistance? Theft of service: unauthorised
Physical Attacks on Tamper Resistance: Progress and Lessons Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Why do we need tamper resistance? Theft of service: unauthorised
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain [email protected] Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain [email protected] Department of Computer
Offline HW/SW Authentication for Reconfigurable Platforms
 Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech [email protected] Patrick Schaumont Virginia Tech [email protected] Abstract Many Field-Programmable Gate Array (FPGA) based
Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech [email protected] Patrick Schaumont Virginia Tech [email protected] Abstract Many Field-Programmable Gate Array (FPGA) based
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems
 Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC [email protected] 2. NASA/GSFC [email protected]
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC [email protected] 2. NASA/GSFC [email protected]
Pre-tested System-on-Chip Design. Accelerates PLD Development
 Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
LogiCORE IP AXI Performance Monitor v2.00.a
 LogiCORE IP AXI Performance Monitor v2.00.a Product Guide Table of Contents IP Facts Chapter 1: Overview Target Technology................................................................. 9 Applications......................................................................
LogiCORE IP AXI Performance Monitor v2.00.a Product Guide Table of Contents IP Facts Chapter 1: Overview Target Technology................................................................. 9 Applications......................................................................
Sentinel-SSO: Full DDR-Bank Power and Signal Integrity. Design Automation Conference 2014
 Sentinel-SSO: Full DDR-Bank Power and Signal Integrity Design Automation Conference 2014 1 Requirements for I/O DDR SSO Analysis Modeling Package and board I/O circuit and layout PI + SI feedback Tool
Sentinel-SSO: Full DDR-Bank Power and Signal Integrity Design Automation Conference 2014 1 Requirements for I/O DDR SSO Analysis Modeling Package and board I/O circuit and layout PI + SI feedback Tool
Extended Boundary Scan Test breaching the analog ban. Marcel Swinnen, teamleader test engineering
 Extended Boundary Scan Test breaching the analog ban Marcel Swinnen, teamleader test engineering 11-11-2014 2 zero-defect quality impossible to produce zero-defect boards early involvement services (Design
Extended Boundary Scan Test breaching the analog ban Marcel Swinnen, teamleader test engineering 11-11-2014 2 zero-defect quality impossible to produce zero-defect boards early involvement services (Design
IronKey Data Encryption Methods
 IronKey Data Encryption Methods An IronKey Technical Brief November 2007 Information Depth:Technical Introduction IronKey is dedicated to building the world s most secure fl ash drives. Our dedication
IronKey Data Encryption Methods An IronKey Technical Brief November 2007 Information Depth:Technical Introduction IronKey is dedicated to building the world s most secure fl ash drives. Our dedication
Seeking Opportunities for Hardware Acceleration in Big Data Analytics
 Seeking Opportunities for Hardware Acceleration in Big Data Analytics Paul Chow High-Performance Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Toronto Who
Seeking Opportunities for Hardware Acceleration in Big Data Analytics Paul Chow High-Performance Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Toronto Who
Hunting Asynchronous CDC Violations in the Wild
 Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
CS 356 Lecture 17 and 18 Intrusion Detection. Spring 2013
 CS 356 Lecture 17 and 18 Intrusion Detection Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
CS 356 Lecture 17 and 18 Intrusion Detection Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits)
 Page 1 of 6 Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits) TNCC Cybersecurity Program web page: http://tncc.edu/programs/cyber-security Course Description: Encompasses
Page 1 of 6 Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits) TNCC Cybersecurity Program web page: http://tncc.edu/programs/cyber-security Course Description: Encompasses
Problems of Security in Ad Hoc Sensor Network
 Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
What is LOG Storm and what is it useful for?
 What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
Introduction to Programmable Logic Devices. John Coughlan RAL Technology Department Detector & Electronics Division
 Introduction to Programmable Logic Devices John Coughlan RAL Technology Department Detector & Electronics Division PPD Lectures Programmable Logic is Key Underlying Technology. First-Level and High-Level
Introduction to Programmable Logic Devices John Coughlan RAL Technology Department Detector & Electronics Division PPD Lectures Programmable Logic is Key Underlying Technology. First-Level and High-Level
Networking Virtualization Using FPGAs
 Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
CONNECT PROTECT SECURE. Communication, Networking and Security Solutions for Defense
 CONNECT PROTECT Communication, Networking and Security Solutions for Defense Engage Communication provides Defense, Homeland Security and Intelligence Communities with innovative and cost effective solutions
CONNECT PROTECT Communication, Networking and Security Solutions for Defense Engage Communication provides Defense, Homeland Security and Intelligence Communities with innovative and cost effective solutions
Lecture 7: Clocking of VLSI Systems
 Lecture 7: Clocking of VLSI Systems MAH, AEN EE271 Lecture 7 1 Overview Reading Wolf 5.3 Two-Phase Clocking (good description) W&E 5.5.1, 5.5.2, 5.5.3, 5.5.4, 5.5.9, 5.5.10 - Clocking Note: The analysis
Lecture 7: Clocking of VLSI Systems MAH, AEN EE271 Lecture 7 1 Overview Reading Wolf 5.3 Two-Phase Clocking (good description) W&E 5.5.1, 5.5.2, 5.5.3, 5.5.4, 5.5.9, 5.5.10 - Clocking Note: The analysis
Barracuda Intrusion Detection and Prevention System
 Providing complete and comprehensive real-time network protection Today s networks are constantly under attack by an ever growing number of emerging exploits and attackers using advanced evasion techniques
Providing complete and comprehensive real-time network protection Today s networks are constantly under attack by an ever growing number of emerging exploits and attackers using advanced evasion techniques
LatticeECP3 High-Speed I/O Interface
 April 2013 Introduction Technical Note TN1180 LatticeECP3 devices support high-speed I/O interfaces, including Double Data Rate (DDR) and Single Data Rate (SDR) interfaces, using the logic built into the
April 2013 Introduction Technical Note TN1180 LatticeECP3 devices support high-speed I/O interfaces, including Double Data Rate (DDR) and Single Data Rate (SDR) interfaces, using the logic built into the
ATMEL FPGA 3rd User Group Workshop. 2010, 3rd June Christophe POURRIER
 ATMEL FPGA 3rd User Group Workshop 2010, 3rd June Christophe POURRIER Summary Sodern first experience with AT40K Megha-Tropiques Project PHARAO Project ATF280 Evaluation Tests performed on the first development
ATMEL FPGA 3rd User Group Workshop 2010, 3rd June Christophe POURRIER Summary Sodern first experience with AT40K Megha-Tropiques Project PHARAO Project ATF280 Evaluation Tests performed on the first development
Introduction to Functional Verification. Niels Burkhardt
 Introduction to Functional Verification Overview Verification issues Verification technologies Verification approaches Universal Verification Methodology Conclusion Functional Verification issues Hardware
Introduction to Functional Verification Overview Verification issues Verification technologies Verification approaches Universal Verification Methodology Conclusion Functional Verification issues Hardware
Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor
 Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor A Starter Guide Joseph Yiu November 2014 version 1.02 27 Nov 2014 1 - Background Since the ARM Cortex -M0 Processor was released a few years
Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor A Starter Guide Joseph Yiu November 2014 version 1.02 27 Nov 2014 1 - Background Since the ARM Cortex -M0 Processor was released a few years
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course. Module-VII Lecture-I Introduction to Digital VLSI Testing
 Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
