Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems
|
|
|
- Angelica Austin
- 10 years ago
- Views:
Transcription
1 Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC [email protected] 2. NASA/GSFC [email protected] 1
2 Acknowledgements Some of this work has been sponsored by the NASA Electronic Parts and Packaging (NEPP) Program and the Defense Threat Reduction Agency (DTRA). Thanks is given to the NASA Goddard Radiation Effects and Analysis Group (REAG) for their technical assistance and support. REAG is led by Kenneth LaBel and Jonathan Pellish. Contact Information: Melanie Berg: NASA Goddard REAG FPGA Principal Investigator: 2
3 Acronyms Binary decision diagram (BDD) Block Triple Modular Redundancy (BTMR) Combinatorial logic (CL) Computer Aided Design (CAD) Device under test (DUT) Distributed triple modular redundancy (DTMR) Dual interlocked storage cell (DICE) Edge-triggered flip-flops (DFFs) Equivalence checking (EC) Error detection and correction (EDAC) Error rate (de/dt) Fault tolerance (FT) Field programmable gate array (FPGA) Formal verification (FV) Global triple modular redundancy (GTMR) Hardware description language (HDL) Input output (I/O) Linear energy transfer (LET) Local triple modular redundancy (LTMR) Mitigation Window (MW) Mean time to failure (MTTF) Operational frequency (fs) Power on reset (POR) Radiation Effects and Analysis Group (REAG) Single Error Correct Double Error Detect (SECDED) Single event functional interrupt (SEFI) Single event effects (SEEs) Single event latch-up (SEL) Single event transient (SET) Single event upset (SEU) Single event upset cross-section (σ SEU ) Static random access memory (SRAM) Static timing analysis (STA) Triple modular redundancy (TMR) 3
4 Abstract We propose a method for triple modular redundancy (TMR) insertion verification that satisfies the process for reliable and trusted systems. If a system is expected to be protected using TMR, improper insertion can jeopardize the reliability and security of the system. Due to the complexity of the verification process and the complexity of digital designs, there are currently no available techniques that can provide complete and reliable confirmation of TMR insertion. 4
5 Overview This presentation addresses the challenge of confirming that TMR has been inserted without corruption of functionality and with correct application of the expected TMR topology. The proposed verification method combines the usage of existing formal analysis tools with a novel search-detect-and-verify tool. This presentation does not address the strength/performance of the selected TMR. The susceptibility of a circuit post-tmr insertion should be evaluated using accelerated testing. Selection of the appropriate TMR scheme is based on the device type, requirements, and design- flush frequency. 5
6 HDL: Hardware description language STA: Static timing analysis EC: Equivalence checking Functional Specification FPGA User Design Flow HDL Behavioral Simulation Output of synthesis is a gate net list that represents the given HDL function. Synthesis Place and Route STA, EC, and Gate Level Simulation Performed by user with manufacturer FPGA specific design tools Create Configuration STA, and back annotated Gate Level Simulation User creates a design that is mapped into a manufacturer provided FPGA 6
7 Triple Modular Redundancy (TMR) 7
8 TMR Schemes Use Majority Voting MajorityVoter = I1 I 2 + I0 I 2 + I0 I1 I0 I1 I2 Majority Voter Triplicate and Vote 8
9 Triplicate and Vote: But Implementation Schemes Are Not All the Same TMR Schemes are differentiated by how the triplication is performed and where the voters are placed S a ed ata put ca ot be oted out a d ca cause upset a t ee s D SET Q D CLR SET CLR Q Q Q V O T E R D SET Q CLR Singular Data Path: Localized Triple Modular redundancy (LTMR) Q Redundant Data Path: Distributed TMR (DTMR) or Global TMR (GTMR = XTMR) But it s not this easy!!!!!!!!!!!!!!!!!!!! 9
10 Various TMR Schemes Block diagram of block TMR (BTMR): a complex function containing combinatorial logic (CL) and flip-flops (DFFs) is triplicated as three black boxes; majority voters are placed at the outputs of the triplet. Block diagram of local TMR (LTMR): only flipflops (DFFs) are triplicated and datapaths stay singular; voters are brought into the design and placed in front of the DFFs. Block Diagram of distributed TMR (DTMR): the entire design is triplicated except for the global routes (e.g., clocks); voters are brought into the design and placed after the flip-flops (DFFs). DTMR masks and corrects most 10 single event upsets (SEUs).
11 HDL: Hardware description language Functional Specification FPGA User Design Flow HDL Output of synthesis is a gate net list that represents the given HDL function. Synthesis Place and Route Create Configuration TMR can be inserted during synthesis or post synthesis. If inserted post synthesis, the gate level netlist is replicated, ripped apart, and voters + feedback are inserted. 11
12 Concerns during the TMR Insertion Process Synthesis TMR insertion: Did the tool insert the correct type of TMR? Did the user correctly select the expected type of TMR? Does the tool implement the correct the topology of the expected TMR? Is the functionality implemented as expected? Post-synthesis TMR insertion: Is the functionality broken during the netlist replication and voter+feedback insertion process? Is the functionality implemented as expected? Only DTMR (or XTMR) is offered in available tools. Who is involved in the tool development process? How is the tool development environment controlled and verified? 12
13 Current Verification Process of TMR When using a tool the designer usually assumes the insertion to be reliable. Not good enough: I received a call from an organization that used synopsis to insert TMR. They stated that the results were compatible to the design that had no mitigation. This is because the version of the tool only had LTMR available. LTMR should never be used with SRAM-based FPGAs. This has been reported. Group didn t take into account nor verify the topology of the inserted TMR. Other suggestions to TMR verification: Simulation, Fault injection, and Formal Verification. None of these suggestions will suffice! 13
14 Verification of TMR Insertion Verification is two fold: Verification that the functionality was not broken during the TMR insertion process. Verification that the topology of the TMR scheme matches the expected methodology. Simulation and fault injection: Although any type verification helps, simulation and fault injection is ineffective as a total proof because of its limited exploration of state-space. Limited state-space traversal cannot ensure that all nodes have been mitigated as expected. Reliable verification is compromised. 14
15 Formal Verification (FV): Created to address the state-space traversal challenge. 15
16 Formal Verification: Binary Decision Diagram (BDD) Synchronous circuits are modeled using BDDs. Verification of logic is performed by searching BDDs: Find a given logic group, and search through to terminal nodes while evaluating logic function. Types of searches are mostly event based: A is always triggered if B occurs. A is never triggered if B occurs. A is triggered exactly n- cycles after B occurs. 16
17 Challenges of BDD Implementation BDD nodes do not represent circuit elements (e.g., DFFs or combinatorial logic blocks). BDDs are logic representations of the circuit under evaluation. Logic representation of a design requires exponentially more nodes than circuit graphs. In most cases, full designs cannot be represented in one BDD. In order to model a design using BDDs: Designs are intelligently partitioned, and Groups of redundant logic nodes are collapsed into one group. 17
18 Collapse of Redundant Logic 18
19 Challenges of Formal Verification and TMR Verification The intention of TMR implementation is to insert redundancy. However, FV BDD modeling removes redundant nodes. Hence, FV, as currently implemented, cannot prove that: redundancy exists for all nodes and that it is inserted correctly. 19
20 FV and Equivalence Checking (EC) Equivalence checking is a watered-down version of FV. It is used to prove that the synthesized logic output matches the designer generated HDL. Hence, EC can be used to prove that the insertion of TMR has not broken functionality. However, once again, it cannot be used to verify that the expected TMR has been inserted correctly. EC tools are readily available. 20
21 Proposed TMR Verification Methodology Functional Verification: Use EC. Topology Verification: Use a circuit graph (model) to verify TMR topology with cone-of-logic theory. A cone-of-logic is defined by selecting an element under analysis (vertex) and performing a backward trace towards its base components. The trace starts at the cone-of-logic vertex (in this case a voter or another DFF) and ends at the vertex s previous stage of flip-flops (DFFs) or a system input (cone-of-logic base elements). The goal is to verify whether the three copies (TMR domains) of logic that feed each voter under analysis are equivalent and the voters are inserted as expected 21
22 BTMR Topological Verification First Stage of Algorithm: Voter and Connected DFF Evaluation Search for the voter under analysis; i.e., first stage vertex. This voter is directly connected to a device output. It will be referred to as output-voter. Establish the direct cone-of-logic that feeds the output-voter. For proper synchronous design, it is expected that the first cone-of-logic stage consist solely of the triplicated DFFs and the output-voter. Verify that the cones-of-logic per TMR domain are equivalent copies of each other. This step is simply checking that three of the same copies of DFFs are directly connected to the voter output. 22
23 BTMR Topological Verification Second Stage of Algorithm: Internal Circuitry Evaluation For the following iterations, the vertex for each cone-of-logic is no longer a voter. Alternatively, the vertices are DFFs. The Start Points for each cone s backward trace remain DFFs or system inputs. Recursive iterations within the algorithm are based on cones-of-logic and are exhausted when all system inputs that are associated with the first stage cone-of-logic (i.e., the voter) are reached and verified. Perform a backwards trace to the previous stage of DFFs (cone-of-logic base components); and establish the cone-of-logic vertex (DFF) under analysis. Search for the two other TMR domain vertex-dff copies and establish their cones-of-logic. Verify that the three cones-of-logic are equivalent. 23
24 DTMR Topological Verification First Iteration of Algorithm: Identify all system output DFFvoter pairs. As a clarification, these components are physically connected to the DTMR design s output. Establish a cone-of-logic for each of the system output DFFvoter pairs. Search and identify the TMR replicas of the cones-of-logic. Compare cone-of-logic replicas across TMR domains. Verify that each cone-of-logic is equivalent to its copies. 24
25 DTMR Topological Verification Second Iteration of Algorithm: After performing the first iteration, each of the DFF-voter pairs that were labeled as coneof-logic base elements now become cone-of-logic vertices. The recursive procedure terminates when all paths have been traced back to system inputs. 25
26 Conclusion The decision to mitigate a design with TMR is associated with a system with significantly high expectations of reliability and trust. Improper TMR insertion can comprise a mission along with security. This presentation describes a novel TMR insertion verification process with two primary concerns: proof that TMR insertion leaves functionality intact; and proof that TMR insertion is topologically implemented as expected. Computer aided design (CAD) tools exist that can verify original (unmitigated) functionality is intact. It is important to take into account that simply proving original functionality is intact does not definitively prove that mitigation is inserted correctly. We suggest performing an additional stage of TMR insertion verification. This stage evaluates design topology. We refer to the proposed topological evaluation tool as searchdetect-and-verify. 26
How To Fix A 3 Bit Error In Data From A Data Point To A Bit Code (Data Point) With A Power Source (Data Source) And A Power Cell (Power Source)
 FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
Implementation Details
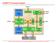 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Use of Reprogrammable FPGA on EUCLID mission
 19/05/2016 Workshop su Applicazioni FPGA in ambito Astrofisico Raoul Grimoldi Use of Reprogrammable FPGA on EUCLID mission Euclid mission overview EUCLID is a cosmology mission part of Cosmic Vision 2015-2025
19/05/2016 Workshop su Applicazioni FPGA in ambito Astrofisico Raoul Grimoldi Use of Reprogrammable FPGA on EUCLID mission Euclid mission overview EUCLID is a cosmology mission part of Cosmic Vision 2015-2025
Combinational Controllability Controllability Formulas (Cont.)
 Outline Digital Testing: Testability Measures The case for DFT Testability Measures Controllability and observability SCOA measures Combinational circuits Sequential circuits Adhoc techniques Easily testable
Outline Digital Testing: Testability Measures The case for DFT Testability Measures Controllability and observability SCOA measures Combinational circuits Sequential circuits Adhoc techniques Easily testable
ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT
 216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
Chapter 13: Verification
 Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
CLASS: Combined Logic Architecture Soft Error Sensitivity Analysis
 CLASS: Combined Logic Architecture Soft Error Sensitivity Analysis Mojtaba Ebrahimi, Liang Chen, Hossein Asadi, and Mehdi B. Tahoori INSTITUTE OF COMPUTER ENGINEERING (ITEC) CHAIR FOR DEPENDABLE NANO COMPUTING
CLASS: Combined Logic Architecture Soft Error Sensitivity Analysis Mojtaba Ebrahimi, Liang Chen, Hossein Asadi, and Mehdi B. Tahoori INSTITUTE OF COMPUTER ENGINEERING (ITEC) CHAIR FOR DEPENDABLE NANO COMPUTING
How To Write An Fpa Programmable Gate Array
 Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications Niccolò Battezzati Luca Sterpone Massimo Violante Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications
Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications Niccolò Battezzati Luca Sterpone Massimo Violante Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
CHAPTER 5 FINITE STATE MACHINE FOR LOOKUP ENGINE
 CHAPTER 5 71 FINITE STATE MACHINE FOR LOOKUP ENGINE 5.1 INTRODUCTION Finite State Machines (FSMs) are important components of digital systems. Therefore, techniques for area efficiency and fast implementation
CHAPTER 5 71 FINITE STATE MACHINE FOR LOOKUP ENGINE 5.1 INTRODUCTION Finite State Machines (FSMs) are important components of digital systems. Therefore, techniques for area efficiency and fast implementation
Fault Modeling. Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults. Transistor faults Summary
 Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Modeling Sequential Elements with Verilog. Prof. Chien-Nan Liu TEL: 03-4227151 ext:34534 Email: [email protected]. Sequential Circuit
 Modeling Sequential Elements with Verilog Prof. Chien-Nan Liu TEL: 03-4227151 ext:34534 Email: [email protected] 4-1 Sequential Circuit Outputs are functions of inputs and present states of storage elements
Modeling Sequential Elements with Verilog Prof. Chien-Nan Liu TEL: 03-4227151 ext:34534 Email: [email protected] 4-1 Sequential Circuit Outputs are functions of inputs and present states of storage elements
Sequential Logic. (Materials taken from: Principles of Computer Hardware by Alan Clements )
 Sequential Logic (Materials taken from: Principles of Computer Hardware by Alan Clements ) Sequential vs. Combinational Circuits Combinatorial circuits: their outputs are computed entirely from their present
Sequential Logic (Materials taken from: Principles of Computer Hardware by Alan Clements ) Sequential vs. Combinational Circuits Combinatorial circuits: their outputs are computed entirely from their present
Design Verification & Testing Design for Testability and Scan
 Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Digital Design Verification
 Digital Design Verification Course Instructor: Debdeep Mukhopadhyay Dept of Computer Sc. and Engg. Indian Institute of Technology Madras, Even Semester Course No: CS 676 1 Verification??? What is meant
Digital Design Verification Course Instructor: Debdeep Mukhopadhyay Dept of Computer Sc. and Engg. Indian Institute of Technology Madras, Even Semester Course No: CS 676 1 Verification??? What is meant
Dr Markus Hagenbuchner [email protected] CSCI319. Distributed Systems
 Dr Markus Hagenbuchner [email protected] CSCI319 Distributed Systems CSCI319 Chapter 8 Page: 1 of 61 Fault Tolerance Study objectives: Understand the role of fault tolerance in Distributed Systems. Know
Dr Markus Hagenbuchner [email protected] CSCI319 Distributed Systems CSCI319 Chapter 8 Page: 1 of 61 Fault Tolerance Study objectives: Understand the role of fault tolerance in Distributed Systems. Know
Network (Tree) Topology Inference Based on Prüfer Sequence
 Network (Tree) Topology Inference Based on Prüfer Sequence C. Vanniarajan and Kamala Krithivasan Department of Computer Science and Engineering Indian Institute of Technology Madras Chennai 600036 [email protected],
Network (Tree) Topology Inference Based on Prüfer Sequence C. Vanniarajan and Kamala Krithivasan Department of Computer Science and Engineering Indian Institute of Technology Madras Chennai 600036 [email protected],
MultiPARTES. Virtualization on Heterogeneous Multicore Platforms. 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM
 MultiPARTES Virtualization on Heterogeneous Multicore Platforms 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM Contents Analysis of scheduling approaches Virtualization of devices Dealing with heterogeneous
MultiPARTES Virtualization on Heterogeneous Multicore Platforms 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM Contents Analysis of scheduling approaches Virtualization of devices Dealing with heterogeneous
White Paper FPGA Performance Benchmarking Methodology
 White Paper Introduction This paper presents a rigorous methodology for benchmarking the capabilities of an FPGA family. The goal of benchmarking is to compare the results for one FPGA family versus another
White Paper Introduction This paper presents a rigorous methodology for benchmarking the capabilities of an FPGA family. The goal of benchmarking is to compare the results for one FPGA family versus another
Aims and Objectives. E 3.05 Digital System Design. Course Syllabus. Course Syllabus (1) Programmable Logic
 Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: [email protected] How to go
Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: [email protected] How to go
SAN Conceptual and Design Basics
 TECHNICAL NOTE VMware Infrastructure 3 SAN Conceptual and Design Basics VMware ESX Server can be used in conjunction with a SAN (storage area network), a specialized high speed network that connects computer
TECHNICAL NOTE VMware Infrastructure 3 SAN Conceptual and Design Basics VMware ESX Server can be used in conjunction with a SAN (storage area network), a specialized high speed network that connects computer
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems
 Harris Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems David Harris Harvey Mudd College [email protected] Based on EE271 developed by Mark Horowitz, Stanford University MAH
Harris Introduction to CMOS VLSI Design (E158) Lecture 8: Clocking of VLSI Systems David Harris Harvey Mudd College [email protected] Based on EE271 developed by Mark Horowitz, Stanford University MAH
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic
 Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
Rapid System Prototyping with FPGAs
 Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Embedded Systems Lecture 9: Reliability & Fault Tolerance. Björn Franke University of Edinburgh
 Embedded Systems Lecture 9: Reliability & Fault Tolerance Björn Franke University of Edinburgh Overview Definitions System Reliability Fault Tolerance Sources and Detection of Errors Stage Error Sources
Embedded Systems Lecture 9: Reliability & Fault Tolerance Björn Franke University of Edinburgh Overview Definitions System Reliability Fault Tolerance Sources and Detection of Errors Stage Error Sources
Digital Systems Design! Lecture 1 - Introduction!!
 ECE 3401! Digital Systems Design! Lecture 1 - Introduction!! Course Basics Classes: Tu/Th 11-12:15, ITE 127 Instructor Mohammad Tehranipoor Office hours: T 1-2pm, or upon appointments @ ITE 441 Email:
ECE 3401! Digital Systems Design! Lecture 1 - Introduction!! Course Basics Classes: Tu/Th 11-12:15, ITE 127 Instructor Mohammad Tehranipoor Office hours: T 1-2pm, or upon appointments @ ITE 441 Email:
Lecture 7: Clocking of VLSI Systems
 Lecture 7: Clocking of VLSI Systems MAH, AEN EE271 Lecture 7 1 Overview Reading Wolf 5.3 Two-Phase Clocking (good description) W&E 5.5.1, 5.5.2, 5.5.3, 5.5.4, 5.5.9, 5.5.10 - Clocking Note: The analysis
Lecture 7: Clocking of VLSI Systems MAH, AEN EE271 Lecture 7 1 Overview Reading Wolf 5.3 Two-Phase Clocking (good description) W&E 5.5.1, 5.5.2, 5.5.3, 5.5.4, 5.5.9, 5.5.10 - Clocking Note: The analysis
Contents. System Development Models and Methods. Design Abstraction and Views. Synthesis. Control/Data-Flow Models. System Synthesis Models
 System Development Models and Methods Dipl.-Inf. Mirko Caspar Version: 10.02.L.r-1.0-100929 Contents HW/SW Codesign Process Design Abstraction and Views Synthesis Control/Data-Flow Models System Synthesis
System Development Models and Methods Dipl.-Inf. Mirko Caspar Version: 10.02.L.r-1.0-100929 Contents HW/SW Codesign Process Design Abstraction and Views Synthesis Control/Data-Flow Models System Synthesis
Best Practises for LabVIEW FPGA Design Flow. uk.ni.com ireland.ni.com
 Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Latches, the D Flip-Flop & Counter Design. ECE 152A Winter 2012
 Latches, the D Flip-Flop & Counter Design ECE 52A Winter 22 Reading Assignment Brown and Vranesic 7 Flip-Flops, Registers, Counters and a Simple Processor 7. Basic Latch 7.2 Gated SR Latch 7.2. Gated SR
Latches, the D Flip-Flop & Counter Design ECE 52A Winter 22 Reading Assignment Brown and Vranesic 7 Flip-Flops, Registers, Counters and a Simple Processor 7. Basic Latch 7.2 Gated SR Latch 7.2. Gated SR
Programming NAND devices
 Technical Guide Programming NAND devices Kelly Hirsch, Director of Advanced Technology, Data I/O Corporation Recent Design Trends In the past, embedded system designs have used NAND devices for storing
Technical Guide Programming NAND devices Kelly Hirsch, Director of Advanced Technology, Data I/O Corporation Recent Design Trends In the past, embedded system designs have used NAND devices for storing
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Index Terms Domain name, Firewall, Packet, Phishing, URL.
 BDD for Implementation of Packet Filter Firewall and Detecting Phishing Websites Naresh Shende Vidyalankar Institute of Technology Prof. S. K. Shinde Lokmanya Tilak College of Engineering Abstract Packet
BDD for Implementation of Packet Filter Firewall and Detecting Phishing Websites Naresh Shende Vidyalankar Institute of Technology Prof. S. K. Shinde Lokmanya Tilak College of Engineering Abstract Packet
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
System-on. on-chip Design Flow. Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems. jouni.tomberg@tut.
 System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
Verification and Validation of Software Components and Component Based Software Systems
 Chapter 5 29 Verification and Validation of Software Components and Component Based Christina Wallin Industrial Information Technology Software Engineering Processes ABB Corporate Research [email protected]
Chapter 5 29 Verification and Validation of Software Components and Component Based Christina Wallin Industrial Information Technology Software Engineering Processes ABB Corporate Research [email protected]
KEEP IT SYNPLE STUPID
 Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Engineering Change Order (ECO) Support in Programmable Logic Design
 White Paper Engineering Change Order (ECO) Support in Programmable Logic Design A major benefit of programmable logic is that it accommodates changes to the system specification late in the design cycle.
White Paper Engineering Change Order (ECO) Support in Programmable Logic Design A major benefit of programmable logic is that it accommodates changes to the system specification late in the design cycle.
ESP-CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation
 Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Upon completion of unit 1.1, students will be able to
 Upon completion of unit 1.1, students will be able to 1. Demonstrate safety of the individual, class, and overall environment of the classroom/laboratory, and understand that electricity, even at the nominal
Upon completion of unit 1.1, students will be able to 1. Demonstrate safety of the individual, class, and overall environment of the classroom/laboratory, and understand that electricity, even at the nominal
Structural Cloud Audits that Protect Private Information
 Structural Cloud Audits that Protect Private Information Hongda Xiao, Bryan Ford, Joan Feigenbaum Department of Computer Science Yale University Cloud Computing Security Workshop November 8, 2013 Motivation
Structural Cloud Audits that Protect Private Information Hongda Xiao, Bryan Ford, Joan Feigenbaum Department of Computer Science Yale University Cloud Computing Security Workshop November 8, 2013 Motivation
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING
 FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
Digital Systems. Role of the Digital Engineer
 Digital Systems Role of the Digital Engineer Digital Design Engineers attempt to clearly define the problem(s) Possibly, break the problem into many smaller problems Engineers then develop a strategy for
Digital Systems Role of the Digital Engineer Digital Design Engineers attempt to clearly define the problem(s) Possibly, break the problem into many smaller problems Engineers then develop a strategy for
Testing & Verification of Digital Circuits ECE/CS 5745/6745. Hardware Verification using Symbolic Computation
 Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla ([email protected]) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla ([email protected]) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
Boolean Network Models
 Boolean Network Models 2/5/03 History Kaufmann, 1970s Studied organization and dynamics properties of (N,k) Boolean Networks Found out that highly connected networks behave differently than lowly connected
Boolean Network Models 2/5/03 History Kaufmann, 1970s Studied organization and dynamics properties of (N,k) Boolean Networks Found out that highly connected networks behave differently than lowly connected
Scheduling Home Health Care with Separating Benders Cuts in Decision Diagrams
 Scheduling Home Health Care with Separating Benders Cuts in Decision Diagrams André Ciré University of Toronto John Hooker Carnegie Mellon University INFORMS 2014 Home Health Care Home health care delivery
Scheduling Home Health Care with Separating Benders Cuts in Decision Diagrams André Ciré University of Toronto John Hooker Carnegie Mellon University INFORMS 2014 Home Health Care Home health care delivery
Seeking Opportunities for Hardware Acceleration in Big Data Analytics
 Seeking Opportunities for Hardware Acceleration in Big Data Analytics Paul Chow High-Performance Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Toronto Who
Seeking Opportunities for Hardware Acceleration in Big Data Analytics Paul Chow High-Performance Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Toronto Who
HyperAccess Access Control System
 Control System We manufacture, an advanced PC based access control solution that will give you control over who has access to your building. With you can control access on hundreds of doors for up to 10,000
Control System We manufacture, an advanced PC based access control solution that will give you control over who has access to your building. With you can control access on hundreds of doors for up to 10,000
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Life Cycle of a Memory Request. Ring Example: 2 requests for lock 17
 Life Cycle of a Memory Request (1) Use AQR or AQW to place address in AQ (2) If A[31]==0, check for hit in DCache Ring (3) Read Hit: place cache word in RQ; Write Hit: replace cache word with WQ RDDest/RDreturn
Life Cycle of a Memory Request (1) Use AQR or AQW to place address in AQ (2) If A[31]==0, check for hit in DCache Ring (3) Read Hit: place cache word in RQ; Write Hit: replace cache word with WQ RDDest/RDreturn
Theory of Logic Circuits. Laboratory manual. Exercise 3
 Zakład Mikroinformatyki i Teorii Automatów yfrowych Theory of Logic ircuits Laboratory manual Exercise 3 Bistable devices 2008 Krzysztof yran, Piotr zekalski (edt.) 1. lassification of bistable devices
Zakład Mikroinformatyki i Teorii Automatów yfrowych Theory of Logic ircuits Laboratory manual Exercise 3 Bistable devices 2008 Krzysztof yran, Piotr zekalski (edt.) 1. lassification of bistable devices
Introduction to Programmable Logic Devices. John Coughlan RAL Technology Department Detector & Electronics Division
 Introduction to Programmable Logic Devices John Coughlan RAL Technology Department Detector & Electronics Division PPD Lectures Programmable Logic is Key Underlying Technology. First-Level and High-Level
Introduction to Programmable Logic Devices John Coughlan RAL Technology Department Detector & Electronics Division PPD Lectures Programmable Logic is Key Underlying Technology. First-Level and High-Level
So far we have investigated combinational logic for which the output of the logic devices/circuits depends only on the present state of the inputs.
 equential Logic o far we have investigated combinational logic for which the output of the logic devices/circuits depends only on the present state of the inputs. In sequential logic the output of the
equential Logic o far we have investigated combinational logic for which the output of the logic devices/circuits depends only on the present state of the inputs. In sequential logic the output of the
Having read this workbook you should be able to: recognise the arrangement of NAND gates used to form an S-R flip-flop.
 Objectives Having read this workbook you should be able to: recognise the arrangement of NAND gates used to form an S-R flip-flop. describe how such a flip-flop can be SET and RESET. describe the disadvantage
Objectives Having read this workbook you should be able to: recognise the arrangement of NAND gates used to form an S-R flip-flop. describe how such a flip-flop can be SET and RESET. describe the disadvantage
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain [email protected] Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain [email protected] Department of Computer
International Journal of Advancements in Research & Technology, Volume 3, Issue 2, February-2014 10 ISSN 2278-7763
 International Journal of Advancements in Research & Technology, Volume 3, Issue 2, February-2014 10 A Discussion on Testing Hadoop Applications Sevuga Perumal Chidambaram ABSTRACT The purpose of analysing
International Journal of Advancements in Research & Technology, Volume 3, Issue 2, February-2014 10 A Discussion on Testing Hadoop Applications Sevuga Perumal Chidambaram ABSTRACT The purpose of analysing
1. Relational database accesses data in a sequential form. (Figures 7.1, 7.2)
 Chapter 7 Data Structures for Computer Graphics (This chapter was written for programmers - option in lecture course) Any computer model of an Object must comprise three different types of entities: 1.
Chapter 7 Data Structures for Computer Graphics (This chapter was written for programmers - option in lecture course) Any computer model of an Object must comprise three different types of entities: 1.
High-Level Synthesis for FPGA Designs
 High-Level Synthesis for FPGA Designs BRINGING BRINGING YOU YOU THE THE NEXT NEXT LEVEL LEVEL IN IN EMBEDDED EMBEDDED DEVELOPMENT DEVELOPMENT Frank de Bont Trainer consultant Cereslaan 10b 5384 VT Heesch
High-Level Synthesis for FPGA Designs BRINGING BRINGING YOU YOU THE THE NEXT NEXT LEVEL LEVEL IN IN EMBEDDED EMBEDDED DEVELOPMENT DEVELOPMENT Frank de Bont Trainer consultant Cereslaan 10b 5384 VT Heesch
Emulated Digital Control System Validation in Nuclear Power Plant Training Simulators
 Digital Control System Validation in Nuclear Power Training s Gregory W. Silvaggio Westinghouse Electric Company LLC [email protected] Keywords: Validation, nuclear, digital control systems Abstract
Digital Control System Validation in Nuclear Power Training s Gregory W. Silvaggio Westinghouse Electric Company LLC [email protected] Keywords: Validation, nuclear, digital control systems Abstract
Chapter 2 Clocks and Resets
 Chapter 2 Clocks and Resets 2.1 Introduction The cost of designing ASICs is increasing every year. In addition to the non-recurring engineering (NRE) and mask costs, development costs are increasing due
Chapter 2 Clocks and Resets 2.1 Introduction The cost of designing ASICs is increasing every year. In addition to the non-recurring engineering (NRE) and mask costs, development costs are increasing due
Certification Authorities Software Team (CAST) Position Paper CAST-13
 Certification Authorities Software Team (CAST) Position Paper CAST-13 Automatic Code Generation Tools Development Assurance Completed June 2002 NOTE: This position paper has been coordinated among the
Certification Authorities Software Team (CAST) Position Paper CAST-13 Automatic Code Generation Tools Development Assurance Completed June 2002 NOTE: This position paper has been coordinated among the
Switch Fabric Implementation Using Shared Memory
 Order this document by /D Switch Fabric Implementation Using Shared Memory Prepared by: Lakshmi Mandyam and B. Kinney INTRODUCTION Whether it be for the World Wide Web or for an intra office network, today
Order this document by /D Switch Fabric Implementation Using Shared Memory Prepared by: Lakshmi Mandyam and B. Kinney INTRODUCTION Whether it be for the World Wide Web or for an intra office network, today
Modeling Latches and Flip-flops
 Lab Workbook Introduction Sequential circuits are digital circuits in which the output depends not only on the present input (like combinatorial circuits), but also on the past sequence of inputs. In effect,
Lab Workbook Introduction Sequential circuits are digital circuits in which the output depends not only on the present input (like combinatorial circuits), but also on the past sequence of inputs. In effect,
SOCWIRE: A SPACEWIRE INSPIRED FAULT TOLERANT NETWORK-ON-CHIP FOR RECONFIGURABLE SYSTEM-ON-CHIP DESIGNS
 SOCWIRE: A SPACEWIRE INSPIRED FAULT TOLERANT NETWORK-ON-CHIP FOR RECONFIGURABLE SYSTEM-ON-CHIP DESIGNS IN SPACE APPLICATIONS Session: Networks and Protocols Long Paper B. Osterloh, H. Michalik, B. Fiethe
SOCWIRE: A SPACEWIRE INSPIRED FAULT TOLERANT NETWORK-ON-CHIP FOR RECONFIGURABLE SYSTEM-ON-CHIP DESIGNS IN SPACE APPLICATIONS Session: Networks and Protocols Long Paper B. Osterloh, H. Michalik, B. Fiethe
EXPERIMENT 8. Flip-Flops and Sequential Circuits
 EXPERIMENT 8. Flip-Flops and Sequential Circuits I. Introduction I.a. Objectives The objective of this experiment is to become familiar with the basic operational principles of flip-flops and counters.
EXPERIMENT 8. Flip-Flops and Sequential Circuits I. Introduction I.a. Objectives The objective of this experiment is to become familiar with the basic operational principles of flip-flops and counters.
System Interconnect Architectures. Goals and Analysis. Network Properties and Routing. Terminology - 2. Terminology - 1
 System Interconnect Architectures CSCI 8150 Advanced Computer Architecture Hwang, Chapter 2 Program and Network Properties 2.4 System Interconnect Architectures Direct networks for static connections Indirect
System Interconnect Architectures CSCI 8150 Advanced Computer Architecture Hwang, Chapter 2 Program and Network Properties 2.4 System Interconnect Architectures Direct networks for static connections Indirect
PROGETTO DI SISTEMI ELETTRONICI DIGITALI. Digital Systems Design. Digital Circuits Advanced Topics
 PROGETTO DI SISTEMI ELETTRONICI DIGITALI Digital Systems Design Digital Circuits Advanced Topics 1 Sequential circuit and metastability 2 Sequential circuit - FSM A Sequential circuit contains: Storage
PROGETTO DI SISTEMI ELETTRONICI DIGITALI Digital Systems Design Digital Circuits Advanced Topics 1 Sequential circuit and metastability 2 Sequential circuit - FSM A Sequential circuit contains: Storage
Krishna Institute of Engineering & Technology, Ghaziabad Department of Computer Application MCA-213 : DATA STRUCTURES USING C
 Tutorial#1 Q 1:- Explain the terms data, elementary item, entity, primary key, domain, attribute and information? Also give examples in support of your answer? Q 2:- What is a Data Type? Differentiate
Tutorial#1 Q 1:- Explain the terms data, elementary item, entity, primary key, domain, attribute and information? Also give examples in support of your answer? Q 2:- What is a Data Type? Differentiate
SOFTWARE-IMPLEMENTED SAFETY LOGIC Angela E. Summers, Ph.D., P.E., President, SIS-TECH Solutions, LP
 SOFTWARE-IMPLEMENTED SAFETY LOGIC Angela E. Summers, Ph.D., P.E., President, SIS-TECH Solutions, LP Software-Implemented Safety Logic, Loss Prevention Symposium, American Institute of Chemical Engineers,
SOFTWARE-IMPLEMENTED SAFETY LOGIC Angela E. Summers, Ph.D., P.E., President, SIS-TECH Solutions, LP Software-Implemented Safety Logic, Loss Prevention Symposium, American Institute of Chemical Engineers,
(Refer Slide Time: 2:03)
 Control Engineering Prof. Madan Gopal Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 11 Models of Industrial Control Devices and Systems (Contd.) Last time we were
Control Engineering Prof. Madan Gopal Department of Electrical Engineering Indian Institute of Technology, Delhi Lecture - 11 Models of Industrial Control Devices and Systems (Contd.) Last time we were
Engr354: Digital Logic Circuits
 Engr354: igital Circuits Chapter 7 Sequential Elements r. Curtis Nelson Sequential Elements In this chapter you will learn about: circuits that can store information; Basic cells, latches, and flip-flops;
Engr354: igital Circuits Chapter 7 Sequential Elements r. Curtis Nelson Sequential Elements In this chapter you will learn about: circuits that can store information; Basic cells, latches, and flip-flops;
CNES fault tolerant architectures intended for electronic COTS components in space applications
 4ème Atelier Thématique du RIS Nlles architectures & techno des processeurs et SdF Aix-en-Provence 20 novembre 2002 CNES fault tolerant architectures intended for electronic COTS components in space applications
4ème Atelier Thématique du RIS Nlles architectures & techno des processeurs et SdF Aix-en-Provence 20 novembre 2002 CNES fault tolerant architectures intended for electronic COTS components in space applications
PIONEER RESEARCH & DEVELOPMENT GROUP
 SURVEY ON RAID Aishwarya Airen 1, Aarsh Pandit 2, Anshul Sogani 3 1,2,3 A.I.T.R, Indore. Abstract RAID stands for Redundant Array of Independent Disk that is a concept which provides an efficient way for
SURVEY ON RAID Aishwarya Airen 1, Aarsh Pandit 2, Anshul Sogani 3 1,2,3 A.I.T.R, Indore. Abstract RAID stands for Redundant Array of Independent Disk that is a concept which provides an efficient way for
SDLC Controller. Documentation. Design File Formats. Verification
 January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: [email protected] URL: www.cast-inc.com Features AllianceCORE
January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: [email protected] URL: www.cast-inc.com Features AllianceCORE
81110A Pulse Pattern Generator Simulating Distorted Signals for Tolerance Testing
 81110A Pulse Pattern Generator Simulating Distorted Signals for Tolerance Testing Application Note Introduction Industry sectors including computer and components, aerospace defense and education all require
81110A Pulse Pattern Generator Simulating Distorted Signals for Tolerance Testing Application Note Introduction Industry sectors including computer and components, aerospace defense and education all require
Module 2. Embedded Processors and Memory. Version 2 EE IIT, Kharagpur 1
 Module 2 Embedded Processors and Memory Version 2 EE IIT, Kharagpur 1 Lesson 5 Memory-I Version 2 EE IIT, Kharagpur 2 Instructional Objectives After going through this lesson the student would Pre-Requisite
Module 2 Embedded Processors and Memory Version 2 EE IIT, Kharagpur 1 Lesson 5 Memory-I Version 2 EE IIT, Kharagpur 2 Instructional Objectives After going through this lesson the student would Pre-Requisite
Hunting Asynchronous CDC Violations in the Wild
 Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
Software Defined Radio Architecture for NASA s Space Communications
 From July 2007 High Frequency Electronics Copyright 2007 Summit Technical Media Software Defined Radio Architecture for NASA s Space Communications By Maximilian C. Scardelletti, Richard C. Reinhart, Monty
From July 2007 High Frequency Electronics Copyright 2007 Summit Technical Media Software Defined Radio Architecture for NASA s Space Communications By Maximilian C. Scardelletti, Richard C. Reinhart, Monty
FSM Decomposition and Functional Verification of FSM Networks
 VLSI DESIGN 1995, Vol. 3, Nos. 3-4, pp. 249-265 Reprints available directly from the publisher Photocopying permitted by license only (C) 1995 OPA (Overseas Publishers Association) Amsterdam B.V. Published
VLSI DESIGN 1995, Vol. 3, Nos. 3-4, pp. 249-265 Reprints available directly from the publisher Photocopying permitted by license only (C) 1995 OPA (Overseas Publishers Association) Amsterdam B.V. Published
Design Compiler Graphical Create a Better Starting Point for Faster Physical Implementation
 Datasheet Create a Better Starting Point for Faster Physical Implementation Overview Continuing the trend of delivering innovative synthesis technology, Design Compiler Graphical delivers superior quality
Datasheet Create a Better Starting Point for Faster Physical Implementation Overview Continuing the trend of delivering innovative synthesis technology, Design Compiler Graphical delivers superior quality
MapReduce and Distributed Data Analysis. Sergei Vassilvitskii Google Research
 MapReduce and Distributed Data Analysis Google Research 1 Dealing With Massive Data 2 2 Dealing With Massive Data Polynomial Memory Sublinear RAM Sketches External Memory Property Testing 3 3 Dealing With
MapReduce and Distributed Data Analysis Google Research 1 Dealing With Massive Data 2 2 Dealing With Massive Data Polynomial Memory Sublinear RAM Sketches External Memory Property Testing 3 3 Dealing With
Chapter 4 Software Lifecycle and Performance Analysis
 Chapter 4 Software Lifecycle and Performance Analysis This chapter is aimed at illustrating performance modeling and analysis issues within the software lifecycle. After having introduced software and
Chapter 4 Software Lifecycle and Performance Analysis This chapter is aimed at illustrating performance modeling and analysis issues within the software lifecycle. After having introduced software and
TECHNOLOGY BRIEF. Compaq RAID on a Chip Technology EXECUTIVE SUMMARY CONTENTS
 TECHNOLOGY BRIEF August 1999 Compaq Computer Corporation Prepared by ISSD Technology Communications CONTENTS Executive Summary 1 Introduction 3 Subsystem Technology 3 Processor 3 SCSI Chip4 PCI Bridge
TECHNOLOGY BRIEF August 1999 Compaq Computer Corporation Prepared by ISSD Technology Communications CONTENTS Executive Summary 1 Introduction 3 Subsystem Technology 3 Processor 3 SCSI Chip4 PCI Bridge
ECE380 Digital Logic
 ECE38 igital Logic Flip-Flops, Registers and Counters: Flip-Flops r.. J. Jackson Lecture 25- Flip-flops The gated latch circuits presented are level sensitive and can change states more than once during
ECE38 igital Logic Flip-Flops, Registers and Counters: Flip-Flops r.. J. Jackson Lecture 25- Flip-flops The gated latch circuits presented are level sensitive and can change states more than once during
Memory Elements. Combinational logic cannot remember
 Memory Elements Combinational logic cannot remember Output logic values are function of inputs only Feedback is needed to be able to remember a logic value Memory elements are needed in most digital logic
Memory Elements Combinational logic cannot remember Output logic values are function of inputs only Feedback is needed to be able to remember a logic value Memory elements are needed in most digital logic
Attaining EDF Task Scheduling with O(1) Time Complexity
 Attaining EDF Task Scheduling with O(1) Time Complexity Verber Domen University of Maribor, Faculty of Electrical Engineering and Computer Sciences, Maribor, Slovenia (e-mail: [email protected]) Abstract:
Attaining EDF Task Scheduling with O(1) Time Complexity Verber Domen University of Maribor, Faculty of Electrical Engineering and Computer Sciences, Maribor, Slovenia (e-mail: [email protected]) Abstract:
No Room for Error: Creating Highly Reliable, High-Availability FPGA Designs
 White Paper No Room for Error: Creating Highly Reliable, High-Availability FPGA Designs April 2012 Author Angela Sutton, Staff Product Marketing Manager, Synopsys, Inc. It comes as no surprise that the
White Paper No Room for Error: Creating Highly Reliable, High-Availability FPGA Designs April 2012 Author Angela Sutton, Staff Product Marketing Manager, Synopsys, Inc. It comes as no surprise that the
路 論 Chapter 15 System-Level Physical Design
 Introduction to VLSI Circuits and Systems 路 論 Chapter 15 System-Level Physical Design Dept. of Electronic Engineering National Chin-Yi University of Technology Fall 2007 Outline Clocked Flip-flops CMOS
Introduction to VLSI Circuits and Systems 路 論 Chapter 15 System-Level Physical Design Dept. of Electronic Engineering National Chin-Yi University of Technology Fall 2007 Outline Clocked Flip-flops CMOS
Design of a High Speed Communications Link Using Field Programmable Gate Arrays
 Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
