Physical Security: Status and Outlook
|
|
|
- Neal Berry
- 10 years ago
- Views:
Transcription
1 Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich
2 Ideal World P C 2
3 Real World P C, C,errC 3
4 Implementation Attacks First publication ~ 16 years ago Exploitation of various physical effects Developing/improving attacks: passive/active, (non/semi-)invasive Countermeasures on various levels: cell, architecture, protocol/construction Evaluation of attack & countermeasure effectiveness 4
5 Countermeasures Hiding E.g. Noise increase, signal reduction, shuffling / dummy ops, some secure logic styles Masking E.g. First-order/higher-order masking, blinding, some secure logic styles Protocol/Construction E.g. Re-keying, Leakage-resilient crypto 5
6 Some State-of-the-Art (I) Practical attack capabilities Non-profiled SCA Profiled SCA Algebraic attacks Fault attacks 6
7 Some State-of-the-Art (II) Evaluation framework Secure logic styles Leakage-resilient crypto Protecting software Protecting processors 7
8 Practical Capabilities Collection and processing of > 1 billion samples Josh Jaffe, CHES 2010 Reverse engineering of security chips with low/medium cost E.g. Chris Tarnovsky (Flylogic) 8
9 Non-Profiled SCA DoM, correlation common distinguishers Require reasonable good leakage models Mutual Information Analysis as toolbox 1) Estimate pdf of key-dependent models 2) Test correspondence to actual traces MIA generalized easily for higher-order attacks 9
10 Statistical View SCA as detecting dependence between two random variables Leakage models (X) E.g. HW(Sbox(x i k)) Actual measurements (Y) 10
11 Basic Question Does the leakage model allow a meaningful partitioning of the practical leakages? Correct key hypothesis Wrong key hypothesis 11
12 Distinguishers DoM: Correlation: MIA: 12
13 Distinguishers Methods for comparing pdfs without explicit pdf estimation E.g. Kolmogorov-Smirnov test, Cramér-von- Mises test For all attacks: The leakage model may not be totally wrong Different resilience handling non-perfect models 13
14 Profiled SCA Templates as most powerful SCA attacks Suitable for estimating worst-case attack scenario Various techniques Multi-variate Gaussian templates PCA as pre-processing tool Use of stochastic models T-test templates 14
15 Algebraic Attacks Express input-output relation as Boolean equations with many unknown variables (incl. key) SAT solvers: Use side-channel leakage to assign values to some of the variables Problems to cope with wrong guesses 15
16 Algebraic Attacks Optimization problem solver: Can use template probabilities directly Avoids problem of wrong guesses Requires more time 16
17 Fault Attacks Countermeasures normally based on some form of redundancy Redundant data or computation Recent proposals for combined countermeasures (i.e. also vs. SCA) Protecting generic exponentiation 17
18 Fault-Sensitivity Analysis Targeting not the fault per se but the exact conditions producing the fault In some implementations, these conditions are key dependent 18
19 Infective Computation Most fault attacks depend on learning faulty ciphertexts Faults in infective computation will garble the ciphertext Can be safely returned without final checks Attacker doesn t learn useful information 19
20 Evaluation Framework Proposed by Standaert et al. in 2009 Combination of (1) information theoretic (IT) and (2) security metrics (1) How much information about the key leaks (independent of any adversary)? (2) How effective can different adversaries exploit the leakage? 20
21 Evaluation Framework Applied to evaluate different classes of countermeasures Masking Shuffling (in software implementations) 21
22 Some lessons learned IT metric allows to capture security against worst-case attacker Standard attacks in practice not enough to assess SCA resistance of a device Higher-order masking requires a certain amount of noise to be effective Simplified shuffling (random start index) can be more vulnerable 22
23 Secure Logic Styles Goal: Prevent the leakage at the cell level Research started about a decade ago Many different logic styles proposed Some revisions trying to fix shortcomings of proposed logic styles 23
24 (Some) Secure Logic Styles SABL, CRSABL WDDL, (DWDDL), Separated DDL, Double WDDL, Double WDDL(ASIC) (MCML), DyCML, LSCML, IFLSCML, DDSLL, TPDyCML GF RSL, DRSL (MCMOS), MDPL, imdpl SecLib TDPL DSDRL SAL Asynchronous logic 24
25 Secure Logic Evaluation Leakage depends on both cell structure and interconnect Evaluation with simulation often insufficient Need to capture low-level effects, e.g. glitches, early evaluation, memory effect Practical evaluation in ASICs costly 25
26 Secure Logic Implementation EDA tools often do not directly support some of the required functions/constraints e.g. balancing of wire capacitances Usually, extra steps are added to the standard EDA flow e.g. cell substitution, netlist duplication Tools often need to be tricked into doing the necessary steps e.g. fat wire routing 26
27 Secure Logic Cost Security improvements often bought at a relatively high price Increased development cost / area / power consumption Decreased speed 27
28 Leakage-Resilient Crypto Idea: Account for physical leakage in cryptographic construction Goal: Provable physical security against broad classes of adversaries 28
29 Leakage-Resilient Crypto Impossible to prove security against unrestricted physical adversary -> Determine meaningful physical limits for adversary Constructions with various assumptions E.g. λ-bit leakage/iteration, onlycomputation leaks 29
30 Leakage-Resilient Crypto Not all assumptions correspond with engineering experience Relatively high implementation cost -> Still a gap between theoretic proofs and practice 30
31 Protected Software Combination of countermeasures First-order masking & shuffling can be attacked Higher-order masking & strong shuffling (random permutation) seems more secure Execution overhead at least several times the original running time Self-modifying code for offloading overhead to precomputation 31
32 Construction/leakage resilience Fresh re-keying 32
33 Protecting Processors Non-deterministic execution E.g. NONDET processor (hiding in time) Protected execution unit E.g. Power-Trust processor (masking, leveraging secure logic) 33
34 μp with Prot. Execution Unit Secure zone Similar to FU Secure logic Rest of μp Largely unchanged Ordinary CMOS Protected by mask 34
35 Outlook Integrated countermeasures for SCA and fault attacks (More) practical leakage-resilient crypto Leveraging new architectures to implement countermeasures Move to more system-wide view of physical protection 35
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Three-Phase Dual-Rail Pre-Charge Logic
 Infineon Page 1 CHES 2006 - Yokohama Three-Phase Dual-Rail Pre-Charge Logic L. Giancane, R. Luzzi, A. Trifiletti {marco.bucci, raimondo.luzzi}@infineon.com {giancane, trifiletti}@die.mail.uniroma1.it Summary
Infineon Page 1 CHES 2006 - Yokohama Three-Phase Dual-Rail Pre-Charge Logic L. Giancane, R. Luzzi, A. Trifiletti {marco.bucci, raimondo.luzzi}@infineon.com {giancane, trifiletti}@die.mail.uniroma1.it Summary
On Security Evaluation Testing
 On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
Fault Modeling. Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults. Transistor faults Summary
 Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
Unknown Plaintext Template Attacks
 Unknown Plaintext Template Attacks Neil Hanley, Michael Tunstall 2, and William P. Marnane Department of Electrical and Electronic Engineering, University College Cork, Ireland. [email protected], [email protected]
Unknown Plaintext Template Attacks Neil Hanley, Michael Tunstall 2, and William P. Marnane Department of Electrical and Electronic Engineering, University College Cork, Ireland. [email protected], [email protected]
Horst Görtz Institute for IT-Security
 Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Identity-based Encryption with Post-Challenge Auxiliary Inputs for Secure Cloud Applications and Sensor Networks
 Identity-based Encryption with Post-Challenge Auxiliary Inputs for Secure Cloud Applications and Sensor Networks Tsz Hon Yuen - Huawei, Singapore Ye Zhang - Pennsylvania State University, USA Siu Ming
Identity-based Encryption with Post-Challenge Auxiliary Inputs for Secure Cloud Applications and Sensor Networks Tsz Hon Yuen - Huawei, Singapore Ye Zhang - Pennsylvania State University, USA Siu Ming
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
Ensuring Data Storage Security in Cloud Computing
 Ensuring Data Storage Security in Cloud Computing Cong Wang 1, Qian Wang 1, Kui Ren 1, and Wenjing Lou 2 1 ECE Department, Illinois Institute of Technology 2 ECE Department, Worcester Polytechnic Institute
Ensuring Data Storage Security in Cloud Computing Cong Wang 1, Qian Wang 1, Kui Ren 1, and Wenjing Lou 2 1 ECE Department, Illinois Institute of Technology 2 ECE Department, Worcester Polytechnic Institute
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Power Reduction Techniques in the SoC Clock Network. Clock Power
 Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Lecture 9 - Message Authentication Codes
 Lecture 9 - Message Authentication Codes Boaz Barak March 1, 2010 Reading: Boneh-Shoup chapter 6, Sections 9.1 9.3. Data integrity Until now we ve only been interested in protecting secrecy of data. However,
Lecture 9 - Message Authentication Codes Boaz Barak March 1, 2010 Reading: Boneh-Shoup chapter 6, Sections 9.1 9.3. Data integrity Until now we ve only been interested in protecting secrecy of data. However,
Digital Circuit Design
 Test and Diagnosis of of ICs Fault coverage (%) 95 9 85 8 75 7 65 97.92 SSL 4,246 Shawn Blanton Professor Department of ECE Center for Silicon System Implementation CMU Laboratory for Integrated Systems
Test and Diagnosis of of ICs Fault coverage (%) 95 9 85 8 75 7 65 97.92 SSL 4,246 Shawn Blanton Professor Department of ECE Center for Silicon System Implementation CMU Laboratory for Integrated Systems
Hey, You, Get Off of My Cloud! Exploring Information Leakage in Third-Party Clouds. Thomas Ristenpart, Eran Tromer, Hovav Shacham, Stefan Savage
 Hey, You, Get Off of My Cloud! Exploring Information Leakage in Third-Party Clouds Thomas Ristenpart, Eran Tromer, Hovav Shacham, Stefan Savage UCSD MIT UCSD UCSD Today s talk in one slide Third-party
Hey, You, Get Off of My Cloud! Exploring Information Leakage in Third-Party Clouds Thomas Ristenpart, Eran Tromer, Hovav Shacham, Stefan Savage UCSD MIT UCSD UCSD Today s talk in one slide Third-party
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Information Leakage in Encrypted Network Traffic
 Information Leakage in Encrypted Network Traffic Attacks and Countermeasures Scott Coull RedJack Joint work with: Charles Wright (MIT LL) Lucas Ballard (Google) Fabian Monrose (UNC) Gerald Masson (JHU)
Information Leakage in Encrypted Network Traffic Attacks and Countermeasures Scott Coull RedJack Joint work with: Charles Wright (MIT LL) Lucas Ballard (Google) Fabian Monrose (UNC) Gerald Masson (JHU)
Adversary Modelling 1
 Adversary Modelling 1 Evaluating the Feasibility of a Symbolic Adversary Model on Smart Transport Ticketing Systems Authors Arthur Sheung Chi Chan, MSc (Royal Holloway, 2014) Keith Mayes, ISG, Royal Holloway
Adversary Modelling 1 Evaluating the Feasibility of a Symbolic Adversary Model on Smart Transport Ticketing Systems Authors Arthur Sheung Chi Chan, MSc (Royal Holloway, 2014) Keith Mayes, ISG, Royal Holloway
Local Heating Attacks on Flash Memory Devices. Dr Sergei Skorobogatov
 Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
McPAT: An Integrated Power, Area, and Timing Modeling Framework for Multicore and Manycore Architectures
 McPAT: An Integrated Power, Area, and Timing Modeling Framework for Multicore and Manycore Architectures Sheng Li, Junh Ho Ahn, Richard Strong, Jay B. Brockman, Dean M Tullsen, Norman Jouppi MICRO 2009
McPAT: An Integrated Power, Area, and Timing Modeling Framework for Multicore and Manycore Architectures Sheng Li, Junh Ho Ahn, Richard Strong, Jay B. Brockman, Dean M Tullsen, Norman Jouppi MICRO 2009
Applying Remote Side-Channel Analysis Attacks on a Security-enabled NFC Tag
 Applying Remote Side-Channel Analysis Attacks on a Security-enabled NFC Tag Thomas Korak Thomas Plos Institute for Applied Information Processing and Communications (IAIK), Graz University of Technology,
Applying Remote Side-Channel Analysis Attacks on a Security-enabled NFC Tag Thomas Korak Thomas Plos Institute for Applied Information Processing and Communications (IAIK), Graz University of Technology,
Wireless Sensor Network Security. Seth A. Hellbusch CMPE 257
 Wireless Sensor Network Security Seth A. Hellbusch CMPE 257 Wireless Sensor Networks (WSN) 2 The main characteristics of a WSN include: Power consumption constrains for nodes using batteries or energy
Wireless Sensor Network Security Seth A. Hellbusch CMPE 257 Wireless Sensor Networks (WSN) 2 The main characteristics of a WSN include: Power consumption constrains for nodes using batteries or energy
Are Cache Attacks on Public Clouds Practical?
 Are Cache Attacks on Public Clouds Practical? Thomas Eisenbarth Joint work with Gorka Irazoqui, Mehmet Sinan Inci, Berk Gulmezoglu and Berk Sunar WPI - 10/19/2015 Outline Cloud Computing and Isolation
Are Cache Attacks on Public Clouds Practical? Thomas Eisenbarth Joint work with Gorka Irazoqui, Mehmet Sinan Inci, Berk Gulmezoglu and Berk Sunar WPI - 10/19/2015 Outline Cloud Computing and Isolation
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion
 Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Mixed-Criticality Systems Based on Time- Triggered Ethernet with Multiple Ring Topologies. University of Siegen Mohammed Abuteir, Roman Obermaisser
 Mixed-Criticality s Based on Time- Triggered Ethernet with Multiple Ring Topologies University of Siegen Mohammed Abuteir, Roman Obermaisser Mixed-Criticality s Need for mixed-criticality systems due to
Mixed-Criticality s Based on Time- Triggered Ethernet with Multiple Ring Topologies University of Siegen Mohammed Abuteir, Roman Obermaisser Mixed-Criticality s Need for mixed-criticality systems due to
Computer Network. Interconnected collection of autonomous computers that are able to exchange information
 Introduction Computer Network. Interconnected collection of autonomous computers that are able to exchange information No master/slave relationship between the computers in the network Data Communications.
Introduction Computer Network. Interconnected collection of autonomous computers that are able to exchange information No master/slave relationship between the computers in the network Data Communications.
Pervasive Computing und. Informationssicherheit
 Pervasive Computing und 11. Symposium on Privacy and Security Rüschlikon, 13. September 2006 Prof. Christof Paar European Competence Center for IT Security www.crypto.rub.de Contents 1. Pervasive Computing
Pervasive Computing und 11. Symposium on Privacy and Security Rüschlikon, 13. September 2006 Prof. Christof Paar European Competence Center for IT Security www.crypto.rub.de Contents 1. Pervasive Computing
System Aware Cyber Security
 System Aware Cyber Security Application of Dynamic System Models and State Estimation Technology to the Cyber Security of Physical Systems Barry M. Horowitz, Kate Pierce University of Virginia April, 2012
System Aware Cyber Security Application of Dynamic System Models and State Estimation Technology to the Cyber Security of Physical Systems Barry M. Horowitz, Kate Pierce University of Virginia April, 2012
A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks
 A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks HoonJae Lee 1, ManKi Ahn 2, SeonGan Lim 3, and SangJae Moon 4 1 Dongseo University, Busan, 617-716, Korea [email protected]
A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks HoonJae Lee 1, ManKi Ahn 2, SeonGan Lim 3, and SangJae Moon 4 1 Dongseo University, Busan, 617-716, Korea [email protected]
DPA : Attaques et Contre-mesures
 SECURE DPA : Attaques et Contre-mesures Shivam BHASIN, Taoufik CHOUTA, Guillaume DUC, Jean-Luc DANGER, Aziz EL AABID, Florent FLAMENT, Philippe HOOGVORST, Tarik GRABA, Sylvain GUILLEY, Houssem MAGHR EBI,
SECURE DPA : Attaques et Contre-mesures Shivam BHASIN, Taoufik CHOUTA, Guillaume DUC, Jean-Luc DANGER, Aziz EL AABID, Florent FLAMENT, Philippe HOOGVORST, Tarik GRABA, Sylvain GUILLEY, Houssem MAGHR EBI,
Hardware Implementation of AES Encryption and Decryption System Based on FPGA
 Send Orders for Reprints to [email protected] The Open Cybernetics & Systemics Journal, 2015, 9, 1373-1377 1373 Open Access Hardware Implementation of AES Encryption and Decryption System Based
Send Orders for Reprints to [email protected] The Open Cybernetics & Systemics Journal, 2015, 9, 1373-1377 1373 Open Access Hardware Implementation of AES Encryption and Decryption System Based
Leakage-Resilient Authentication and Encryption from Symmetric Cryptographic Primitives
 Leakage-Resilient Authentication and Encryption from Symmetric Cryptographic Primitives Olivier Pereira Université catholique de Louvain ICTEAM Crypto Group B-1348, Belgium [email protected]
Leakage-Resilient Authentication and Encryption from Symmetric Cryptographic Primitives Olivier Pereira Université catholique de Louvain ICTEAM Crypto Group B-1348, Belgium [email protected]
An Overview of Common Adversary Models
 An Overview of Common Adversary Karl Palmskog [email protected] 2012-03-29 Introduction Requirements of Software Systems 1 Functional Correctness: partial, termination, liveness, safety,... 2 Nonfunctional
An Overview of Common Adversary Karl Palmskog [email protected] 2012-03-29 Introduction Requirements of Software Systems 1 Functional Correctness: partial, termination, liveness, safety,... 2 Nonfunctional
List of courses MEngg (Computer Systems)
 List of courses MEngg (Computer Systems) Course No. Course Title Non-Credit Courses CS-401 CS-402 CS-403 CS-404 CS-405 CS-406 Introduction to Programming Systems Design System Design using Microprocessors
List of courses MEngg (Computer Systems) Course No. Course Title Non-Credit Courses CS-401 CS-402 CS-403 CS-404 CS-405 CS-406 Introduction to Programming Systems Design System Design using Microprocessors
AES implementation on Smart Card
 1 AES implementation on Smart Card Pongnukit Juthamas, Tingthanathikul Witit Abstract This paper focus on the cryptographic algorithm on smart card. Many algorithms are used to implement on smart card.
1 AES implementation on Smart Card Pongnukit Juthamas, Tingthanathikul Witit Abstract This paper focus on the cryptographic algorithm on smart card. Many algorithms are used to implement on smart card.
Secure application programming in the presence of side channel attacks. Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203
 Secure application programming in the presence of side channel attacks Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203 Attacks in the field Survey 2007*, Hong Kong: Asia-Pacific Pay-TV
Secure application programming in the presence of side channel attacks Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203 Attacks in the field Survey 2007*, Hong Kong: Asia-Pacific Pay-TV
Karsten Nohl University of Virginia. Henryk Plötz HU Berlin
 Karsten Nohl University of Virginia Henryk Plötz HU Berlin Radio Frequency IDentification Tiny computer chips Passively Powered Karsten Nohl, Henryk Plötz - RFID Security 2 Constant monitoring is already
Karsten Nohl University of Virginia Henryk Plötz HU Berlin Radio Frequency IDentification Tiny computer chips Passively Powered Karsten Nohl, Henryk Plötz - RFID Security 2 Constant monitoring is already
2 Protocol Analysis, Composability and Computation
 2 Protocol Analysis, Composability and Computation Ross Anderson, Michael Bond Security protocols early days The study of security protocols has been associated with Roger Needham since 1978, when he published
2 Protocol Analysis, Composability and Computation Ross Anderson, Michael Bond Security protocols early days The study of security protocols has been associated with Roger Needham since 1978, when he published
VLSI Design Verification and Testing
 VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: [email protected]). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: [email protected]). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
SECURE AND TRUSTY STORAGE SERVICES IN CLOUD COMPUTING
 SECURE AND TRUSTY STORAGE SERVICES IN CLOUD COMPUTING Saranya.V 1, Suganthi.J 2, R.G. Suresh Kumar 3 1,2 Master of Technology, Department of Computer Science and Engineering, Rajiv Gandhi College of Engineering
SECURE AND TRUSTY STORAGE SERVICES IN CLOUD COMPUTING Saranya.V 1, Suganthi.J 2, R.G. Suresh Kumar 3 1,2 Master of Technology, Department of Computer Science and Engineering, Rajiv Gandhi College of Engineering
Systematization of Knowledge Lessons Learned From SSL/TLS Attacks 20.08.2013
 Systematization of Knowledge Lessons Learned From SSL/TLS Attacks 20.08.2013 [email protected] Source: http://www.digicert.com Source: http://www.digicert.com Source: http://www.digicert.com What
Systematization of Knowledge Lessons Learned From SSL/TLS Attacks 20.08.2013 [email protected] Source: http://www.digicert.com Source: http://www.digicert.com Source: http://www.digicert.com What
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
These help quantify the quality of a design from different perspectives: Cost Functionality Robustness Performance Energy consumption
 Basic Properties of a Digital Design These help quantify the quality of a design from different perspectives: Cost Functionality Robustness Performance Energy consumption Which of these criteria is important
Basic Properties of a Digital Design These help quantify the quality of a design from different perspectives: Cost Functionality Robustness Performance Energy consumption Which of these criteria is important
Overview of Cryptographic Tools for Data Security. Murat Kantarcioglu
 UT DALLAS Erik Jonsson School of Engineering & Computer Science Overview of Cryptographic Tools for Data Security Murat Kantarcioglu Pag. 1 Purdue University Cryptographic Primitives We will discuss the
UT DALLAS Erik Jonsson School of Engineering & Computer Science Overview of Cryptographic Tools for Data Security Murat Kantarcioglu Pag. 1 Purdue University Cryptographic Primitives We will discuss the
Removing The Linux Routing Cache
 Removing The Red Hat Inc. Columbia University, New York, 2012 Removing The 1 Linux Maintainership 2 3 4 5 Removing The My Background Started working on the kernel 18+ years ago. First project: helping
Removing The Red Hat Inc. Columbia University, New York, 2012 Removing The 1 Linux Maintainership 2 3 4 5 Removing The My Background Started working on the kernel 18+ years ago. First project: helping
Machine Data Analytics with Sumo Logic
 Machine Data Analytics with Sumo Logic A Sumo Logic White Paper Introduction Today, organizations generate more data in ten minutes than they did during the entire year in 2003. This exponential growth
Machine Data Analytics with Sumo Logic A Sumo Logic White Paper Introduction Today, organizations generate more data in ten minutes than they did during the entire year in 2003. This exponential growth
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur
 Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. #01 Lecture No. #10 Symmetric Key Ciphers (Refer
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Module No. #01 Lecture No. #10 Symmetric Key Ciphers (Refer
Update On Smart Grid Cyber Security
 Update On Smart Grid Cyber Security Kshamit Dixit Manager IT Security, Toronto Hydro, Ontario, Canada 1 Agenda Cyber Security Overview Security Framework Securing Smart Grid 2 Smart Grid Attack Threats
Update On Smart Grid Cyber Security Kshamit Dixit Manager IT Security, Toronto Hydro, Ontario, Canada 1 Agenda Cyber Security Overview Security Framework Securing Smart Grid 2 Smart Grid Attack Threats
Counter Expertise Review on the TNO Security Analysis of the Dutch OV-Chipkaart. OV-Chipkaart Security Issues Tutorial for Non-Expert Readers
 Counter Expertise Review on the TNO Security Analysis of the Dutch OV-Chipkaart OV-Chipkaart Security Issues Tutorial for Non-Expert Readers The current debate concerning the OV-Chipkaart security was
Counter Expertise Review on the TNO Security Analysis of the Dutch OV-Chipkaart OV-Chipkaart Security Issues Tutorial for Non-Expert Readers The current debate concerning the OV-Chipkaart security was
Computing on Encrypted Data
 Computing on Encrypted Data Secure Internet of Things Seminar David Wu January, 2015 Smart Homes New Applications in the Internet of Things aggregation + analytics usage statistics and reports report energy
Computing on Encrypted Data Secure Internet of Things Seminar David Wu January, 2015 Smart Homes New Applications in the Internet of Things aggregation + analytics usage statistics and reports report energy
Whitewash: Securely Outsourcing Garbled Circuit Generation
 Whitewash: Securely Outsourcing Garbled Circuit Generation MSR Workshop on Applied Multi-Party Computation February 2014 Henry Hank Carter, Charles Lever, Patrick Traynor SMC on mobile devices Mobile devices
Whitewash: Securely Outsourcing Garbled Circuit Generation MSR Workshop on Applied Multi-Party Computation February 2014 Henry Hank Carter, Charles Lever, Patrick Traynor SMC on mobile devices Mobile devices
How To Perform Differential Frequency Analysis (Dfa) On A Powerline (Aes) On An Iphone Or Ipad (Ase) On Microsoft Powerline 2 (Aces) On Pc Or Ipa (Aas)
 A New Frequency-Based Side Channel Attack for Embedded Systems by Chin Chi Tiu A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree of Master of Applied
A New Frequency-Based Side Channel Attack for Embedded Systems by Chin Chi Tiu A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree of Master of Applied
Cryptography & Network Security. Introduction. Chester Rebeiro IIT Madras
 Cryptography & Network Security Introduction Chester Rebeiro IIT Madras The Connected World 2 Information Storage 3 Increased Security Breaches 81% more in 2015 http://www.pwc.co.uk/assets/pdf/2015-isbs-executive-summary-02.pdf
Cryptography & Network Security Introduction Chester Rebeiro IIT Madras The Connected World 2 Information Storage 3 Increased Security Breaches 81% more in 2015 http://www.pwc.co.uk/assets/pdf/2015-isbs-executive-summary-02.pdf
Sleuth: Automated Verification of Software Power Analysis Countermeasures
 Sleuth: Automated Verification of Software Power Analysis Countermeasures Ali Galip Bayrak*, Francesco Regazzoni, David Novo*, and Paolo Ienne* * Ecole Polytechnique Fédérale de Lausanne (EPFL) TU Delft
Sleuth: Automated Verification of Software Power Analysis Countermeasures Ali Galip Bayrak*, Francesco Regazzoni, David Novo*, and Paolo Ienne* * Ecole Polytechnique Fédérale de Lausanne (EPFL) TU Delft
More effective protection for your access control system with end-to-end security
 More effective protection for your access control system with end-to-end security By Jeroen Harmsen The first article on end-to-end security appeared as long ago as 1981. The principle originated in ICT
More effective protection for your access control system with end-to-end security By Jeroen Harmsen The first article on end-to-end security appeared as long ago as 1981. The principle originated in ICT
PLCs and SCADA Systems
 Hands-On Programmable Logic Controllers and Supervisory Control / Data Acquisition Course Description This extensive course covers the essentials of SCADA and PLC systems, which are often used in close
Hands-On Programmable Logic Controllers and Supervisory Control / Data Acquisition Course Description This extensive course covers the essentials of SCADA and PLC systems, which are often used in close
Lecture 10: CPA Encryption, MACs, Hash Functions. 2 Recap of last lecture - PRGs for one time pads
 CS 7880 Graduate Cryptography October 15, 2015 Lecture 10: CPA Encryption, MACs, Hash Functions Lecturer: Daniel Wichs Scribe: Matthew Dippel 1 Topic Covered Chosen plaintext attack model of security MACs
CS 7880 Graduate Cryptography October 15, 2015 Lecture 10: CPA Encryption, MACs, Hash Functions Lecturer: Daniel Wichs Scribe: Matthew Dippel 1 Topic Covered Chosen plaintext attack model of security MACs
Advanced Threat Protection with Dell SecureWorks Security Services
 Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
System-on. on-chip Design Flow. Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems. jouni.tomberg@tut.
 System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
A Predictive Model for Cache-Based Side Channels in Multicore and Multithreaded Microprocessors
 A Predictive Model for Cache-Based Side Channels in Multicore and Multithreaded Microprocessors Leonid Domnitser, Nael Abu-Ghazaleh and Dmitry Ponomarev Department of Computer Science SUNY-Binghamton {lenny,
A Predictive Model for Cache-Based Side Channels in Multicore and Multithreaded Microprocessors Leonid Domnitser, Nael Abu-Ghazaleh and Dmitry Ponomarev Department of Computer Science SUNY-Binghamton {lenny,
High-speed cryptography and DNSCurve. D. J. Bernstein University of Illinois at Chicago
 High-speed cryptography and DNSCurve D. J. Bernstein University of Illinois at Chicago Stealing Internet mail: easy! Given a mail message: Your mail software sends a DNS request, receives a server address,
High-speed cryptography and DNSCurve D. J. Bernstein University of Illinois at Chicago Stealing Internet mail: easy! Given a mail message: Your mail software sends a DNS request, receives a server address,
SecureCom Mobile s mission is to help people keep their private communication private.
 About SecureCom Mobile SecureCom Mobile s mission is to help people keep their private communication private. We believe people have a right to share ideas with each other, confident that only the intended
About SecureCom Mobile SecureCom Mobile s mission is to help people keep their private communication private. We believe people have a right to share ideas with each other, confident that only the intended
Hardware Trojans: A Threat for CyberSecurity
 Hardware Trojans: A Threat for CyberSecurity Julien Francq [email protected] Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
Hardware Trojans: A Threat for CyberSecurity Julien Francq [email protected] Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
Secure Way of Storing Data in Cloud Using Third Party Auditor
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 12, Issue 4 (Jul. - Aug. 2013), PP 69-74 Secure Way of Storing Data in Cloud Using Third Party Auditor 1 Miss.
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 12, Issue 4 (Jul. - Aug. 2013), PP 69-74 Secure Way of Storing Data in Cloud Using Third Party Auditor 1 Miss.
Lightweight and Secure PUF Key Storage Using Limits of Machine Learning
 Lightweight and Secure PUF Key Storage Using Limits of Machine Learning Meng-Day (Mandel) Yu 1, David M Raïhi 1, Richard Sowell 1, Srinivas Devadas 2 1 Verayo, Inc., San Jose, CA, USA 2 MIT, Cambridge,
Lightweight and Secure PUF Key Storage Using Limits of Machine Learning Meng-Day (Mandel) Yu 1, David M Raïhi 1, Richard Sowell 1, Srinivas Devadas 2 1 Verayo, Inc., San Jose, CA, USA 2 MIT, Cambridge,
BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH
 WHITE PAPER METRIC-DRIVEN VERIFICATION ENSURES SOFTWARE DEVELOPMENT QUALITY BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH INTRODUCTION The complexity of electronic systems is rapidly
WHITE PAPER METRIC-DRIVEN VERIFICATION ENSURES SOFTWARE DEVELOPMENT QUALITY BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH INTRODUCTION The complexity of electronic systems is rapidly
A Tutorial on Physical Security and Side-Channel Attacks
 A Tutorial on Physical Security and Side-Channel Attacks François Koeune 12 and François-Xavier Standaert 1 1 UCL Crypto Group Place du Levant, 3. 1348 Louvain-la-Neuve, Belgium [email protected]
A Tutorial on Physical Security and Side-Channel Attacks François Koeune 12 and François-Xavier Standaert 1 1 UCL Crypto Group Place du Levant, 3. 1348 Louvain-la-Neuve, Belgium [email protected]
Attestation and Authentication Protocols Using the TPM
 Attestation and Authentication Protocols Using the TPM Ariel Segall June 21, 2011 Approved for Public Release: 11-2876. Distribution Unlimited. c 2011. All Rights Reserved. (1/28) Motivation Almost all
Attestation and Authentication Protocols Using the TPM Ariel Segall June 21, 2011 Approved for Public Release: 11-2876. Distribution Unlimited. c 2011. All Rights Reserved. (1/28) Motivation Almost all
Making Multicore Work and Measuring its Benefits. Markus Levy, president EEMBC and Multicore Association
 Making Multicore Work and Measuring its Benefits Markus Levy, president EEMBC and Multicore Association Agenda Why Multicore? Standards and issues in the multicore community What is Multicore Association?
Making Multicore Work and Measuring its Benefits Markus Levy, president EEMBC and Multicore Association Agenda Why Multicore? Standards and issues in the multicore community What is Multicore Association?
Security Analysis for Order Preserving Encryption Schemes
 Security Analysis for Order Preserving Encryption Schemes Liangliang Xiao University of Texas at Dallas Email: [email protected] Osbert Bastani Harvard University Email: [email protected] I-Ling
Security Analysis for Order Preserving Encryption Schemes Liangliang Xiao University of Texas at Dallas Email: [email protected] Osbert Bastani Harvard University Email: [email protected] I-Ling
How To Design A Chip Layout
 Spezielle Anwendungen des VLSI Entwurfs Applied VLSI design (IEF170) Course and contest Intermediate meeting 3 Prof. Dirk Timmermann, Claas Cornelius, Hagen Sämrow, Andreas Tockhorn, Philipp Gorski, Martin
Spezielle Anwendungen des VLSI Entwurfs Applied VLSI design (IEF170) Course and contest Intermediate meeting 3 Prof. Dirk Timmermann, Claas Cornelius, Hagen Sämrow, Andreas Tockhorn, Philipp Gorski, Martin
Enova X-Wall LX Frequently Asked Questions
 Enova X-Wall LX Frequently Asked Questions Q: What is X-Wall LX? A: X-Wall LX is the third generation of Enova real-time hard drive cryptographic gateway ASIC (Application Specific Integrated Circuit)
Enova X-Wall LX Frequently Asked Questions Q: What is X-Wall LX? A: X-Wall LX is the third generation of Enova real-time hard drive cryptographic gateway ASIC (Application Specific Integrated Circuit)
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Karagpur
 Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Karagpur Lecture No. #06 Cryptanalysis of Classical Ciphers (Refer
Cryptography and Network Security Prof. D. Mukhopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Karagpur Lecture No. #06 Cryptanalysis of Classical Ciphers (Refer
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 1 January 9, 2012 CPSC 467b, Lecture 1 1/22 Course Overview Symmetric Cryptography CPSC 467b, Lecture 1 2/22 Course Overview CPSC
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 1 January 9, 2012 CPSC 467b, Lecture 1 1/22 Course Overview Symmetric Cryptography CPSC 467b, Lecture 1 2/22 Course Overview CPSC
Computer Security (EDA263 / DIT 641)
 Computer Security (EDA263 / DIT 641) Lecture 12: Database Security Erland Jonsson Department of Computer Science and Engineering Chalmers University of Technology Sweden Outline Introduction to databases
Computer Security (EDA263 / DIT 641) Lecture 12: Database Security Erland Jonsson Department of Computer Science and Engineering Chalmers University of Technology Sweden Outline Introduction to databases
Six Strategies for Building High Performance SOA Applications
 Six Strategies for Building High Performance SOA Applications Uwe Breitenbücher, Oliver Kopp, Frank Leymann, Michael Reiter, Dieter Roller, and Tobias Unger University of Stuttgart, Institute of Architecture
Six Strategies for Building High Performance SOA Applications Uwe Breitenbücher, Oliver Kopp, Frank Leymann, Michael Reiter, Dieter Roller, and Tobias Unger University of Stuttgart, Institute of Architecture
Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010
 CS 494/594 Computer and Network Security Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010 1 Introduction to Cryptography What is cryptography?
CS 494/594 Computer and Network Security Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010 1 Introduction to Cryptography What is cryptography?
Mobile network security report: Poland
 Mobile network security report: Poland GSM Map Project [email protected] Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
Mobile network security report: Poland GSM Map Project [email protected] Security Research Labs, Berlin February 2015 Abstract. Mobile networks differ widely in their protection capabilities against common
Module 1: Introduction to Computer System and Network Validation
 Module 1: Introduction to Computer System and Network Validation Module 1, Slide 1 What is Validation? Definition: Valid (Webster s Third New International Dictionary) Able to effect or accomplish what
Module 1: Introduction to Computer System and Network Validation Module 1, Slide 1 What is Validation? Definition: Valid (Webster s Third New International Dictionary) Able to effect or accomplish what
Secure Deduplication of Encrypted Data without Additional Independent Servers
 Secure Deduplication of Encrypted Data without Additional Independent Servers Jian Liu Aalto University [email protected] N. Asokan Aalto University and University of Helsinki [email protected] Benny Pinkas
Secure Deduplication of Encrypted Data without Additional Independent Servers Jian Liu Aalto University [email protected] N. Asokan Aalto University and University of Helsinki [email protected] Benny Pinkas
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
The Classical Architecture. Storage 1 / 36
 1 / 36 The Problem Application Data? Filesystem Logical Drive Physical Drive 2 / 36 Requirements There are different classes of requirements: Data Independence application is shielded from physical storage
1 / 36 The Problem Application Data? Filesystem Logical Drive Physical Drive 2 / 36 Requirements There are different classes of requirements: Data Independence application is shielded from physical storage
Implementation Details
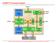 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
White Paper. Cisco MPLS based VPNs: Equivalent to the security of Frame Relay and ATM. March 30, 2001
 The leading edge in networking information White Paper Cisco MPLS based VPNs: Equivalent to the security of Frame Relay and ATM March 30, 2001 Abstract: The purpose of this white paper is to present discussion
The leading edge in networking information White Paper Cisco MPLS based VPNs: Equivalent to the security of Frame Relay and ATM March 30, 2001 Abstract: The purpose of this white paper is to present discussion
Module 1. Introduction to Software Engineering. Version 2 CSE IIT, Kharagpur
 Module 1 Introduction to Software Engineering Lesson 2 Structured Programming Specific Instructional Objectives At the end of this lesson the student will be able to: Identify the important features of
Module 1 Introduction to Software Engineering Lesson 2 Structured Programming Specific Instructional Objectives At the end of this lesson the student will be able to: Identify the important features of
Microsemi Security Center of Excellence
 Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
