Understanding Integrated Circuit Security Threats. Asif Iqbal Senior Program Manager, Apple Inc. SDM 11
|
|
|
- Calvin Henderson
- 10 years ago
- Views:
Transcription
1 Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11
2 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated Circuit (IC) Design Flow Trust in IC development lifecycle Stages of entry Pre Silicon Attacks In Silicon Attacks Post Silicon Attacks Deep Dive on Hardware Trojans Trojan Anatomy Trojan Classification Design Examples Challenges in detection Current Security Initiatives
3 Layers of information processing
4 Attacks at different layers Social Engineering Malwares / Macros Viruses/ Trojans??
5 Relative Impact , ,000 ~100 Million ~100 Million Key Takeaway #1 : Hardware is the root of trust; Even a small malicious modification can be devastating to system security
6 Internet of things 10 billion Devices and counting Everything right from your computer to your phone to your microwave can be compromised without you ever knowing about it.
7 Syrian Radar Case September 2007, Israeli jets bombed a suspected nuclear installation in northeastern Syria. Among the many mysteries still surrounding that strike was the failure of Syrian radar, supposedly state of the art, to warn the Syrian military of the incoming assault. It wasn t long before military and technology bloggers concluded that this was an incident of electronic warfare and not just any kind. Post after post speculated that the commercial offthe-shelf microprocessors in the Syrian radar might have been purposely fabricated with a hidden backdoor inside. By sending a preprogrammed code to those chips, an unknown antagonist had disrupted the chips function and temporarily blocked the radar Source : IEEE spectrum, 2007
8 Counterfeit Chips in Military
9 Computer Chip in a Commercial Jet Compromised A hidden 'back door' in a computer chip could allow cyber-criminals a way to override and control computer systems on Boeing 787s -- dailymail.co.uk, 30 th May
10 Laptop Batteries Can Be Bricked The method involves accessing and sending instructions to the chip housed on smart batteries completely disables the batteries on laptops, making them permanently unusable, perform a number of other unintended actions like false reporting of battery levels, temperature etc. could also be used for more malicious purposes down the road.
11 More Cases
12 Intel Ivy Bridge Can t Keep Your Secret Sabotage on the cryptographic capability of Intel processors including the latest Ivy Bridge which is the heart of most 2012 PCs. Reduces the entropy of the random number generator from 128 bits to 32 bits. Accomplished by changing the doping polarity of a few transistors. Undetectable by built in self tests and physical inspection. [Stealthy Dopant-Level Hardware Trojans, Georg T. Becker, Francesco Regazzoni, Christof Paar, and Wayne P. Burleson]
13 Compromise virtually every System and National Security Key Takeaway #2 : Virtually any and every electronic system around us can be potentially be compromised.
14 Semiconductor Economics Moore s Law Capital Costs for setting up a foundry Typical Useful lifetime of a foundry Selling Price of a Chip Gross Margins
15 Semiconductor Economics Moore s Law and the market requirements for higher performance chips are driving the production of smaller transistors Smaller devices and larger wafers Technology Changes every ~1.5 years Cost of Setting up a foundry ~$5-$10 Billion Low yields for first few months 6-9 months Learning curve in for process improvement. Cyclic demand for consumer electronic products Gross Margins less than 45% is not competitive if you do not have scale.
16 Impact on Semiconductor Product Design Time to Market Pressure Lots of Reuse Third Party IPs Sometimes cheaper than developing on their own Third party tools and scripts Outsourced Manufacturing (Fab-Less Model) Outsourced Testing Key Takeaway #3 : Most semiconductor companies outsource their manufacturing due to the high capital and operational costs.
17 Security Implications of Outsourced Manufacturing Compromising the IC supply chain for sensitive commercial and defense applications becomes easy. Attacker could substitute Trojan ICs for genuine ICs during the process. Attacker could subvert the fabrication process itself by implanting additional Trojan circuitry into the IC mask. Fragmentation makes it easy for the counterfeit / recycled ICs to enter the supply chain.
18 IC Design Flow Lots of Third party IP and Code Reuse! Complicated Scripts, Third Party tools! Physical Placement of Gates, Heavy use of tcl scripts
19 Different Views of a Design RTL GDSII NETLIST
20 Semiconductor Manufacturing Process
21 Trust in IC development Life Cycle
22 Trusted and Untrusted Components of the design process Design Untrusted Third Party IP Cores Trusted CAD Tools Untrusted automation scripts Untrusted Libraries, Standard Cells Fabrication Untrusted foundries Test and Validation Untrusted if not done in house Trusted if done in house Key Takeaway #4 : The trust in the chip design process is broken
23 Pre Silicon Attacks ( Design Stage) Modification of Functional Logic Third party corrupt IPs Tampering with clocks Tampering the voltage control logic Modification of Test and Debug Logic Testability Debug Logic Vendor Controls Modification of the Layout Thinning of the conducting wires Weakening the transistors Using Spare gates
24 In Silicon Attacks ( Manufacturing Stage)
25 Different types of In Silicon Attacks DARPA initiated the Trust in ICs program. Source : Thehuntforthekillswitch. design/the-hunt-for-the-kill-switch.
26 Post Silicon Attacks Modify Operating Conditions Temperature Power Frequency FIBbing to cut or create connections Exploiting inbuilt security holes due to poor design Invalid instructions Protocol errors Denial of service Creative Use of Test and Debug Modes and Designer s Backdoors
27 The designers Backdoor! Commonly built into chips by designers to allow quick and easy access to some test and debugging features. Can Allow cyber-criminals a way to override and control computer systems on Boeing 787s Security researchers have previously suggested that Chinese companies build vulnerabilities into chips that are exported to the West for use in military systems.
28 Hardware Trojans A malicious circuit put inside a chip which is harmless in normal operation until it gets triggered by a preset internal or an external condition.
29 Anatomy of a Hardware Trojan Trigger Events which Enable the Trojan Stealth depends on triggers Image Source : Payload The Ammo / firepower Size is not proportional to destruction
30 A very Simple Trojan Towards a comprehensive and systematic classification of hardware Trojans J. Rajendran, et al
31 Why is Trojan Detection Difficult Stealthy nature Low probability Triggers are finite state machines that can change states when time or input data changes Nano-scale devices and high system complexity make detection through physical inspection almost impossible. Test time is expensive. Consider testing a million chips per production batch Even a small chip today has a billion nodes and 2 billion States. Test are for known use cases Very difficult to test for Unknown Unknowns! Large number of gates in modern chips Gate Level Simulations are extremely computation and memory intensive. Inspection through destructive reverse engineering does not guarantee absence of Trojans in ICs not destructively inspected. Audits not very effective at catching bugs Key Takeaway #5 : A Hardware Trojan is near impossible to detect in tests because its designed to trigger in mission mode.
32 Trojan Classification LEVEL 1 LEVEL 2 LEVEL 3 Source : A Survey of Hardware Trojan Taxonomy and Detection, Tehranipoor et.al
33 Types of Triggers Analog On chip sensors, antennas used to trigger a malfunction Digital Combinatorial triggers generated by logical combination a particular circuit state. Sequential Triggers are counters/ state machine based and re sometimes impossible to detect until the failure mode Image Source : Hardware Trojan: Threats and Emerging Solutions, Chakraborty et al
34 Types of Triggers TIME BOMB Analog On chip sensors, antennas used to trigger a malfunction Digital Combinatorial triggers generated by logical combination a particular circuit state. Sequential Triggers are counters/ state machine based and re sometimes impossible to detect until the failure mode Image Source : Hardware Trojan: Threats and Emerging Solutions, Chakraborty et al
35 A simple Time Bomb Trigger : Internal Payload : Functionality Change Detection Probability : Low Codename : Time Bomb Image Source : Hardware Trojan: Threats and Emerging Solutions, Chakraborty et al
36 A very Simple information stealing Trojan Trigger : Internal Payload : Information Leak Detection Probability : Low Codename : Agent X Experiences in Hardware Trojan Design and Implementation Yier Jin, Nathan Kupp, and Yiorgos Makris
37 A very Simple information stealing Trojan Image Source : Experiences in Hardware Trojan Design and Implementation Yier Jin, Nathan Kupp, and Yiorgos Makris
38 Trojan Detection Approaches Destructive Scanning optical microscopy (SOM) Scanning electron microscopy (SEM) Non Destructive and Non Invasive Bulk Current Measurement Bulk Power Measurement Data path delay measurement Reliability Tests like burn in at elevated voltage and temperatures. ATPG scan chains Logic tests Functional Tests ( Run time monitoring) Built in self tests Invasive techniques wherein special circuitry is embedded in the chip to aid Trojan detection. Connectivity signatures Triple modular redundancy Transparent modes for state machines. Improving observability and controllability of internal nodes.
39 Mitigating the Threat Ensuring Authenticity of ICs make the entire Development process trusted Silicon Design Authentication Trust In IC Program (DARPA) Design Trustable Hardware Redundancy Obfuscation 3D IC technology Tamper proof designs EDA Tool Support Key Takeaway #6 : Long term research can bring built in security and tamper resistance in IC designs. However, for short term, the threat can be mitigated by making the supply chain trusted.
40 Questions Speaker Contact Asif Iqbal
41 Video Resources 40% fake chips in millitary Chip recycling Blackhat Videos
42 References Cyber security in federal government, Booz Allen Hamilton The hunt for the kill switch, IEEE Spectrum, May 2008 The hunt for the kill switch, IEEE Spectrum, May 2008 Report of the Defense Science Board Task Force on High Performance Microchip Supply, Defense Science Board, US DoD, Feb. 2005; reports/ hpms_report_final.pdf. Innovation at Risk Intellectual Property Challenges and Opportunities, white paper, Semiconductor Equipment and Materials International, June The hunt for the kill switch, IEEE Spectrum, May 2008 Towards a comprehensive and systematic classification of hardware Trojans, J Rajendran et.al. X. Wang, M. Tehranipoor, and J. Plusquellic, Detecting Malicious Inclusions in Secure Hardware: Challenges and Solutions, Proc. IEEE Int l Workshop Hardware- Oriented Security and Trust (HOST 08), IEEE CS Press, 2008, pp Hardware Trojan: Threats and Emerging Solutions, Rajat Subhra Chakraborty et al.
43 multiplexer may be triggered by an external component. B. At what abstraction level is a trojan inserted? Levels of Abstractions Trojan circuits can be inserted at various hardware abstraction levels as shown in 4. HIGHEST LEVEL Fig. 4. Abstractions in a top LOWEST down VLSI LEVEL design flow. The forward arrow represents Increasing the synthesis. sophistication The red Decreasing boxes on Trust either side Increasing showease theof example detectability Trojans in that level (darkly shaded in case viewed in black and white). Image Source :Towards a comprehensive and systematic classification of hardware Trojans, J Rajendran et al 1) At the system level different hardware modules, interconnections and communication protocols used are Increasing Sophistication Of agent and detectability C. Ho d m Som remain event - activat dorma 1) A t e w p T s d v 2) A t
44 DARPA TRUST in IC Program Trusted Foundry Program provide interim measure for trusted high performance IC s. Certain Circuit topologies and building blocks to be used. Design guidelines with respected to debug options, testability, backdoors, TMR etc. Techniques that can quickly and accurately determine whether an IC provided is the same as one available in a gold standard design
45 Agents of Attack Remote Hackers : no physical access to the device, rely on sophisticated hacking tools. Security specialist : technically capable attackers are criminal gangs, security experts, and users attacking devices for fun, capable of executing a lab attack Trusted developer : Engineers, scientists working for trusted organizations, may be bribed to insert backdoors in design and specifications. Device Distributor/ Fab Owner : In general the device owner is motivated to perform the attack, but is not technically competent. A technical expert will have developed an attack and embed in onsite.
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
PFP Technology White Paper
 PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
Implementing Program Protection and Cybersecurity
 Implementing Program Protection and Cybersecurity Melinda Reed Office of the Deputy Assistant Secretary of Defense for Systems Engineering Mark Godino Office of the Deputy Assistant Secretary of Defense
Implementing Program Protection and Cybersecurity Melinda Reed Office of the Deputy Assistant Secretary of Defense for Systems Engineering Mark Godino Office of the Deputy Assistant Secretary of Defense
What is Really Needed to Secure the Internet of Things?
 What is Really Needed to Secure the Internet of Things? By Alan Grau, Icon Labs [email protected] The Internet of Things (IoT) has become a ubiquitous term to describe the tens of billions of devices
What is Really Needed to Secure the Internet of Things? By Alan Grau, Icon Labs [email protected] The Internet of Things (IoT) has become a ubiquitous term to describe the tens of billions of devices
Cyber Threats in Physical Security Understanding and Mitigating the Risk
 Cyber Threats in Physical Security Understanding and Mitigating the Risk Synopsis Over the last few years, many industrial control systems, including security solutions, have adopted digital technology.
Cyber Threats in Physical Security Understanding and Mitigating the Risk Synopsis Over the last few years, many industrial control systems, including security solutions, have adopted digital technology.
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
BlackRidge Technology Transport Access Control: Overview
 2011 BlackRidge Technology Transport Access Control: Overview 1 Introduction Enterprises and government agencies are under repeated cyber attack. Attacks range in scope from distributed denial of service
2011 BlackRidge Technology Transport Access Control: Overview 1 Introduction Enterprises and government agencies are under repeated cyber attack. Attacks range in scope from distributed denial of service
Capabilities for Cybersecurity Resilience
 Capabilities for Cybersecurity Resilience In the Homeland Security Enterprise May 2012 DHS Cybersecurity Strategy A cyberspace that: Is Secure and Resilient Enables Innovation Protects Public Advances
Capabilities for Cybersecurity Resilience In the Homeland Security Enterprise May 2012 DHS Cybersecurity Strategy A cyberspace that: Is Secure and Resilient Enables Innovation Protects Public Advances
Smart Card Security How Can We Be So Sure?
 Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Plain English Guide To Common Criteria Requirements In The. Field Device Protection Profile Version 0.75
 Plain English Guide To Common Criteria Requirements In The Field Device Protection Profile Version 0.75 Prepared For: Process Control Security Requirements Forum (PCSRF) Prepared By: Digital Bond, Inc.
Plain English Guide To Common Criteria Requirements In The Field Device Protection Profile Version 0.75 Prepared For: Process Control Security Requirements Forum (PCSRF) Prepared By: Digital Bond, Inc.
Computer Security DD2395
 Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger [email protected] Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger [email protected] Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
KASPERSKY SECURITY INTELLIGENCE SERVICES. EXPERT SERVICES. www.kaspersky.com
 KASPERSKY SECURITY INTELLIGENCE SERVICES. EXPERT SERVICES www.kaspersky.com EXPERT SERVICES Expert Services from Kaspersky Lab are exactly that the services of our in-house experts, many of them global
KASPERSKY SECURITY INTELLIGENCE SERVICES. EXPERT SERVICES www.kaspersky.com EXPERT SERVICES Expert Services from Kaspersky Lab are exactly that the services of our in-house experts, many of them global
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
NVM memory: A Critical Design Consideration for IoT Applications
 NVM memory: A Critical Design Consideration for IoT Applications Jim Lipman Sidense Corp. Introduction The Internet of Things (IoT), sometimes called the Internet of Everything (IoE), refers to an evolving
NVM memory: A Critical Design Consideration for IoT Applications Jim Lipman Sidense Corp. Introduction The Internet of Things (IoT), sometimes called the Internet of Everything (IoE), refers to an evolving
Cyber Security In High-Performance Computing Environment Prakashan Korambath Institute for Digital Research and Education, UCLA July 17, 2014
 Cyber Security In High-Performance Computing Environment Prakashan Korambath Institute for Digital Research and Education, UCLA July 17, 2014 Introduction: Cyber attack is an unauthorized access to a computer
Cyber Security In High-Performance Computing Environment Prakashan Korambath Institute for Digital Research and Education, UCLA July 17, 2014 Introduction: Cyber attack is an unauthorized access to a computer
SanDisk Enterprise Secure USB Flash Drive Security Vulnerability
 SanDisk Enterprise Secure USB Flash Drive Security Vulnerability Device CD-ROM partition can be a host for malware and crimeware February 2009 Introduction After my recent experiences with the Read Only
SanDisk Enterprise Secure USB Flash Drive Security Vulnerability Device CD-ROM partition can be a host for malware and crimeware February 2009 Introduction After my recent experiences with the Read Only
2. From a control perspective, the PRIMARY objective of classifying information assets is to:
 MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
MIS5206 Week 13 Your Name Date 1. When conducting a penetration test of an organization's internal network, which of the following approaches would BEST enable the conductor of the test to remain undetected
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
CS 356 Lecture 17 and 18 Intrusion Detection. Spring 2013
 CS 356 Lecture 17 and 18 Intrusion Detection Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
CS 356 Lecture 17 and 18 Intrusion Detection Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
Developing Secure Software in the Age of Advanced Persistent Threats
 Developing Secure Software in the Age of Advanced Persistent Threats ERIC BAIZE EMC Corporation DAVE MARTIN EMC Corporation Session ID: ASEC-201 Session Classification: Intermediate Our Job: Keep our Employer
Developing Secure Software in the Age of Advanced Persistent Threats ERIC BAIZE EMC Corporation DAVE MARTIN EMC Corporation Session ID: ASEC-201 Session Classification: Intermediate Our Job: Keep our Employer
On Security Evaluation Testing
 On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
WEB APPLICATION FIREWALLS: DO WE NEED THEM?
 DISTRIBUTING EMERGING TECHNOLOGIES, REGION-WIDE WEB APPLICATION FIREWALLS: DO WE NEED THEM? SHAIKH SURMED Sr. Solutions Engineer [email protected] www.fvc.com HAVE YOU BEEN HACKED????? WHAT IS THE PROBLEM?
DISTRIBUTING EMERGING TECHNOLOGIES, REGION-WIDE WEB APPLICATION FIREWALLS: DO WE NEED THEM? SHAIKH SURMED Sr. Solutions Engineer [email protected] www.fvc.com HAVE YOU BEEN HACKED????? WHAT IS THE PROBLEM?
Practical Threat Intelligence. with Bromium LAVA
 Practical Threat Intelligence with Bromium LAVA Practical Threat Intelligence Executive Summary Threat intelligence today is costly and time consuming and does not always result in a reduction of successful
Practical Threat Intelligence with Bromium LAVA Practical Threat Intelligence Executive Summary Threat intelligence today is costly and time consuming and does not always result in a reduction of successful
Triangle InfoSeCon. Alternative Approaches for Secure Operations in Cyberspace
 Triangle InfoSeCon Alternative Approaches for Secure Operations in Cyberspace Lt General Bob Elder, USAF (Retired) Research Professor, George Mason University Strategic Advisor, Georgia Tech Research Institute
Triangle InfoSeCon Alternative Approaches for Secure Operations in Cyberspace Lt General Bob Elder, USAF (Retired) Research Professor, George Mason University Strategic Advisor, Georgia Tech Research Institute
1. Computer Security: An Introduction. Definitions Security threats and analysis Types of security controls Security services
 1. Computer Security: An Introduction Definitions Security threats and analysis Types of security controls Security services Mar 2012 ICS413 network security 1 1.1 Definitions A computer security system
1. Computer Security: An Introduction Definitions Security threats and analysis Types of security controls Security services Mar 2012 ICS413 network security 1 1.1 Definitions A computer security system
What will I learn as an Electrical Engineering student?
 What will I learn as an Electrical Engineering student? Department of Electrical and Computer Engineering Tu5s School of Engineering Trying to decide on a major? Most college course descrip>ons are full
What will I learn as an Electrical Engineering student? Department of Electrical and Computer Engineering Tu5s School of Engineering Trying to decide on a major? Most college course descrip>ons are full
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
State-of-Art (SoA) System-on-Chip (SoC) Design HPC SoC Workshop
 Photos placed in horizontal position with even amount of white space between photos and header State-of-Art (SoA) System-on-Chip (SoC) Design HPC SoC Workshop Michael Holmes Manager, Mixed Signal ASIC/SoC
Photos placed in horizontal position with even amount of white space between photos and header State-of-Art (SoA) System-on-Chip (SoC) Design HPC SoC Workshop Michael Holmes Manager, Mixed Signal ASIC/SoC
TUSKEGEE CYBER SECURITY PATH FORWARD
 TUSKEGEE CYBER SECURITY PATH FORWARD Preface Tuskegee University is very aware of the ever-escalating cybersecurity threat, which consumes continually more of our societies resources to counter these threats,
TUSKEGEE CYBER SECURITY PATH FORWARD Preface Tuskegee University is very aware of the ever-escalating cybersecurity threat, which consumes continually more of our societies resources to counter these threats,
Executable Integrity Verification
 Executable Integrity Verification Abstract Background Determining if a given executable has been trojaned is a tedious task. It is beyond the capabilities of the average end user and even many network
Executable Integrity Verification Abstract Background Determining if a given executable has been trojaned is a tedious task. It is beyond the capabilities of the average end user and even many network
Security Threats on National Defense ICT based on IoT
 , pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
, pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
IoT Security Platform
 IoT Security Platform 2 Introduction Wars begin when the costs of attack are low, the benefits for a victor are high, and there is an inability to enforce law. The same is true in cyberwars. Today there
IoT Security Platform 2 Introduction Wars begin when the costs of attack are low, the benefits for a victor are high, and there is an inability to enforce law. The same is true in cyberwars. Today there
Advanced Threat Protection with Dell SecureWorks Security Services
 Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Advanced Threat Protection with Dell SecureWorks Security Services Table of Contents Summary... 2 What are Advanced Threats?... 3 How do advanced threat actors operate?... 3 Addressing the Threat... 5
Fundamentals of Information Systems Security Unit 1 Information Systems Security Fundamentals
 Fundamentals of Information Systems Security Unit 1 Information Systems Security Fundamentals Learning Objective Explain the concepts of information systems security (ISS) as applied to an IT infrastructure.
Fundamentals of Information Systems Security Unit 1 Information Systems Security Fundamentals Learning Objective Explain the concepts of information systems security (ISS) as applied to an IT infrastructure.
Malicious Software. Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ [email protected] +46 470 70 86 49. Viruses and Related Threats
 Malicious Software Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ [email protected] +46 470 70 86 49 1 Outline Viruses and Related Threats Malicious Programs The Nature of Viruses Antivirus
Malicious Software Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ [email protected] +46 470 70 86 49 1 Outline Viruses and Related Threats Malicious Programs The Nature of Viruses Antivirus
Problems of Security in Ad Hoc Sensor Network
 Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Chapter 1: Introduction
 Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Defense in Cyber Space Beating Cyber Threats that Target Mesh Networks
 Beating Cyber Threats that Target Mesh Networks Trent Nelson, Cyber Security Assessment Lead, Idaho National Laboratory Jeff Becker, Global Wireless Business Director, Honeywell Process Solutions Table
Beating Cyber Threats that Target Mesh Networks Trent Nelson, Cyber Security Assessment Lead, Idaho National Laboratory Jeff Becker, Global Wireless Business Director, Honeywell Process Solutions Table
Architecture of distributed network processors: specifics of application in information security systems
 Architecture of distributed network processors: specifics of application in information security systems V.Zaborovsky, Politechnical University, Sait-Petersburg, Russia [email protected] 1. Introduction Modern
Architecture of distributed network processors: specifics of application in information security systems V.Zaborovsky, Politechnical University, Sait-Petersburg, Russia [email protected] 1. Introduction Modern
UNCLASSIFIED Version 1.0 May 2012
 Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
System Security Engineering
 A Critical Discipline of SE Ms. Kristen Baldwin Director, Systems Analysis DDR&E/Systems Engineering 12th Annual NDIA Systems Engineering Conference 28 October 2009 10/28/09 Page-1 Defense Research & Engineering
A Critical Discipline of SE Ms. Kristen Baldwin Director, Systems Analysis DDR&E/Systems Engineering 12th Annual NDIA Systems Engineering Conference 28 October 2009 10/28/09 Page-1 Defense Research & Engineering
Penetration Testing Service. By Comsec Information Security Consulting
 Penetration Testing Service By Consulting February, 2007 Background The number of hacking and intrusion incidents is increasing year by year as technology rolls out. Equally, there is no hiding place your
Penetration Testing Service By Consulting February, 2007 Background The number of hacking and intrusion incidents is increasing year by year as technology rolls out. Equally, there is no hiding place your
COB 302 Management Information System (Lesson 8)
 COB 302 Management Information System (Lesson 8) Dr. Stanley Wong Macau University of Science and Technology Chapter 13 Security and Ethical Challenges 安 全 與 倫 理 挑 戰 Remarks: Some of the contents in this
COB 302 Management Information System (Lesson 8) Dr. Stanley Wong Macau University of Science and Technology Chapter 13 Security and Ethical Challenges 安 全 與 倫 理 挑 戰 Remarks: Some of the contents in this
Implementation Details
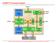 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Challenges in Industrial IT-Security Dr. Rolf Reinema, Head of Technology Field IT-Security, Siemens AG Siemens AG 2015. All rights reserved
 Siemens AG - Corporate Technology - IT Security Challenges in Industrial IT-Security Dr. Rolf Reinema, Head of Technology Field IT-Security, Siemens AG Siemens AG 2015. All rights reserved Not a single
Siemens AG - Corporate Technology - IT Security Challenges in Industrial IT-Security Dr. Rolf Reinema, Head of Technology Field IT-Security, Siemens AG Siemens AG 2015. All rights reserved Not a single
Smart Grid Security: A Look to the Future
 Smart Grid Security: A Look to the Future SESSION ID: TECH-W03A Gib Sorebo Chief Cybersecurity Technologist Leidos @gibsorebo Overview Distributed Energy Plug-in Vehicles Evolving Threats: Market Manipulation,
Smart Grid Security: A Look to the Future SESSION ID: TECH-W03A Gib Sorebo Chief Cybersecurity Technologist Leidos @gibsorebo Overview Distributed Energy Plug-in Vehicles Evolving Threats: Market Manipulation,
2014 Entry Form (Complete one for each entry.) Fill out the entry name exactly as you want it listed in the program.
 2014 Entry Form (Complete one for each entry.) Fill out the entry name exactly as you want it listed in the program. Entry Name HFA Submission Contact Phone Email Qualified Entries must be received by
2014 Entry Form (Complete one for each entry.) Fill out the entry name exactly as you want it listed in the program. Entry Name HFA Submission Contact Phone Email Qualified Entries must be received by
Critical Controls for Cyber Security. www.infogistic.com
 Critical Controls for Cyber Security www.infogistic.com Understanding Risk Asset Threat Vulnerability Managing Risks Systematic Approach for Managing Risks Identify, characterize threats Assess the vulnerability
Critical Controls for Cyber Security www.infogistic.com Understanding Risk Asset Threat Vulnerability Managing Risks Systematic Approach for Managing Risks Identify, characterize threats Assess the vulnerability
The Internet of Things: Opportunities & Challenges
 The Internet of Things: Opportunities & Challenges What is the IoT? Things, people and cloud services getting connected via the Internet to enable new use cases and business models Cloud Services How is
The Internet of Things: Opportunities & Challenges What is the IoT? Things, people and cloud services getting connected via the Internet to enable new use cases and business models Cloud Services How is
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
a) Encryption is enabled on the access point. b) The conference room network is on a separate virtual local area network (VLAN)
 MIS5206 Week 12 Your Name Date 1. Which significant risk is introduced by running the file transfer protocol (FTP) service on a server in a demilitarized zone (DMZ)? a) User from within could send a file
MIS5206 Week 12 Your Name Date 1. Which significant risk is introduced by running the file transfer protocol (FTP) service on a server in a demilitarized zone (DMZ)? a) User from within could send a file
Cyber/IT Risk: Threat Intelligence Countering Advanced Adversaries Jeff Lunglhofer, Principal, Booz Allen. 14th Annual Risk Management Convention
 Cyber/IT Risk: Threat Intelligence Countering Advanced Adversaries Jeff Lunglhofer, Principal, Booz Allen 14th Annual Risk Management Convention New York, New York March 13, 2013 Today s Presentation 1)
Cyber/IT Risk: Threat Intelligence Countering Advanced Adversaries Jeff Lunglhofer, Principal, Booz Allen 14th Annual Risk Management Convention New York, New York March 13, 2013 Today s Presentation 1)
Reducing Application Vulnerabilities by Security Engineering
 Reducing Application Vulnerabilities by Security Engineering - Subash Newton Manager Projects (Non Functional Testing, PT CoE Group) 2008, Cognizant Technology Solutions. All Rights Reserved. The information
Reducing Application Vulnerabilities by Security Engineering - Subash Newton Manager Projects (Non Functional Testing, PT CoE Group) 2008, Cognizant Technology Solutions. All Rights Reserved. The information
EEI Business Continuity. Threat Scenario Project (TSP) April 4, 2012. EEI Threat Scenario Project
 EEI Business Continuity Conference Threat Scenario (TSP) April 4, 2012 EEI Threat Scenario 1 Background EEI, working with a group of CIOs and Subject Matter Experts, conducted a survey with member companies
EEI Business Continuity Conference Threat Scenario (TSP) April 4, 2012 EEI Threat Scenario 1 Background EEI, working with a group of CIOs and Subject Matter Experts, conducted a survey with member companies
PCI PA - DSS. Point ipos Implementation Guide. Version 1.01. VeriFone Vx820 using the Point ipos Payment Core
 PCI PA - DSS Point ipos Implementation Guide VeriFone Vx820 using the Point ipos Payment Core Version 1.01 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566 287 00 www.point.se Page
PCI PA - DSS Point ipos Implementation Guide VeriFone Vx820 using the Point ipos Payment Core Version 1.01 POINT TRANSACTION SYSTEMS AB Box 92031, 120 06 Stockholm, Tel. +46 8 566 287 00 www.point.se Page
CS 356 Lecture 25 and 26 Operating System Security. Spring 2013
 CS 356 Lecture 25 and 26 Operating System Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control
CS 356 Lecture 25 and 26 Operating System Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control
Yaffs NAND Flash Failure Mitigation
 Yaffs NAND Flash Failure Mitigation Charles Manning 2012-03-07 NAND flash is one of very few types of electronic device which are knowingly shipped with errors and are expected to generate further errors
Yaffs NAND Flash Failure Mitigation Charles Manning 2012-03-07 NAND flash is one of very few types of electronic device which are knowingly shipped with errors and are expected to generate further errors
WHITE PAPER Security in M2M Communication What is secure enough?
 WHITE PAPER Security in M2M Communication What is secure enough? Motivation Wireless Machine-To-Machine (M2M) communication has grown dramatically over the past decade and is still growing rapidly. In
WHITE PAPER Security in M2M Communication What is secure enough? Motivation Wireless Machine-To-Machine (M2M) communication has grown dramatically over the past decade and is still growing rapidly. In
Application Security in the Software Development Lifecycle
 Application Security in the Software Development Lifecycle Issues, Challenges and Solutions www.quotium.com 1/15 Table of Contents EXECUTIVE SUMMARY... 3 INTRODUCTION... 4 IMPACT OF SECURITY BREACHES TO
Application Security in the Software Development Lifecycle Issues, Challenges and Solutions www.quotium.com 1/15 Table of Contents EXECUTIVE SUMMARY... 3 INTRODUCTION... 4 IMPACT OF SECURITY BREACHES TO
Getting Ahead of Malware
 IT@Intel White Paper Intel Information Technology Security December 2009 Getting Ahead of Malware Executive Overview Since implementing our security event monitor and detection processes two years ago,
IT@Intel White Paper Intel Information Technology Security December 2009 Getting Ahead of Malware Executive Overview Since implementing our security event monitor and detection processes two years ago,
The FBI Cyber Program. Bauer Advising Symposium //UNCLASSIFIED
 The FBI Cyber Program Bauer Advising Symposium October 11, 2012 Today s Agenda What is the threat? Who are the adversaries? How are they attacking you? What can the FBI do to help? What can you do to stop
The FBI Cyber Program Bauer Advising Symposium October 11, 2012 Today s Agenda What is the threat? Who are the adversaries? How are they attacking you? What can the FBI do to help? What can you do to stop
Yier Jin RESEARCH INTERESTS
 Yier Jin Department of Electrical Engineering and Computer Science University of Central Florida, Orlando, FL 32816 Phone: (407) 823-5321 (Office), (203) 859-1202 (Mobile) Fax: (407) 823-5483 Email: [email protected]
Yier Jin Department of Electrical Engineering and Computer Science University of Central Florida, Orlando, FL 32816 Phone: (407) 823-5321 (Office), (203) 859-1202 (Mobile) Fax: (407) 823-5483 Email: [email protected]
COSC 472 Network Security
 COSC 472 Network Security Instructor: Dr. Enyue (Annie) Lu Office hours: http://faculty.salisbury.edu/~ealu/schedule.htm Office room: HS114 Email: [email protected] Course information: http://faculty.salisbury.edu/~ealu/cosc472/cosc472.html
COSC 472 Network Security Instructor: Dr. Enyue (Annie) Lu Office hours: http://faculty.salisbury.edu/~ealu/schedule.htm Office room: HS114 Email: [email protected] Course information: http://faculty.salisbury.edu/~ealu/cosc472/cosc472.html
Lifecycle Solutions & Services. Managed Industrial Cyber Security Services
 Lifecycle Solutions & Services Managed Industrial Cyber Security Services Around the world, industrial firms and critical infrastructure operators partner with Honeywell to address the unique requirements
Lifecycle Solutions & Services Managed Industrial Cyber Security Services Around the world, industrial firms and critical infrastructure operators partner with Honeywell to address the unique requirements
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
How To Learn To Understand And Understand The Physics Of Chemistry
 What will I learn as an Electrical Engineering student? Department of Electrical and Computer Engineering Tufts School of Engineering Trying to decide on a major? Most college course descriptions are full
What will I learn as an Electrical Engineering student? Department of Electrical and Computer Engineering Tufts School of Engineering Trying to decide on a major? Most college course descriptions are full
INTRUSION DETECTION SYSTEM (IDS) D souza Adam Jerry Joseph 0925910 I MCA
 INTRUSION DETECTION SYSTEM (IDS) D souza Adam Jerry Joseph 0925910 I MCA OVERVIEW Introduction Overview The IDS Puzzle Current State of IDS Threats I have a good firewall, why do I need an IDS? Expectations
INTRUSION DETECTION SYSTEM (IDS) D souza Adam Jerry Joseph 0925910 I MCA OVERVIEW Introduction Overview The IDS Puzzle Current State of IDS Threats I have a good firewall, why do I need an IDS? Expectations
Cryptography and Network Security Chapter 21. Malicious Software. Backdoor or Trapdoor. Logic Bomb 4/19/2010. Chapter 21 Malicious Software
 Cryptography and Network Security Chapter 21 Fifth Edition by William Stallings Chapter 21 Malicious Software What is the concept of defense: The parrying of a blow. What is its characteristic feature:
Cryptography and Network Security Chapter 21 Fifth Edition by William Stallings Chapter 21 Malicious Software What is the concept of defense: The parrying of a blow. What is its characteristic feature:
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things.
 What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
WHITE PAPER. FortiWeb and the OWASP Top 10 Mitigating the most dangerous application security threats
 WHITE PAPER FortiWeb and the OWASP Top 10 PAGE 2 Introduction The Open Web Application Security project (OWASP) Top Ten provides a powerful awareness document for web application security. The OWASP Top
WHITE PAPER FortiWeb and the OWASP Top 10 PAGE 2 Introduction The Open Web Application Security project (OWASP) Top Ten provides a powerful awareness document for web application security. The OWASP Top
Enterprise Cybersecurity: Building an Effective Defense
 Enterprise Cybersecurity: Building an Effective Defense Chris Williams Oct 29, 2015 14 Leidos 0224 1135 About the Presenter Chris Williams is an Enterprise Cybersecurity Architect at Leidos, Inc. He has
Enterprise Cybersecurity: Building an Effective Defense Chris Williams Oct 29, 2015 14 Leidos 0224 1135 About the Presenter Chris Williams is an Enterprise Cybersecurity Architect at Leidos, Inc. He has
Network Security 網 路 安 全. Lecture 1 February 20, 2012 洪 國 寶
 Network Security 網 路 安 全 Lecture 1 February 20, 2012 洪 國 寶 1 Outline Course information Motivation Introduction to security Basic network concepts Network security models Outline of the course 2 Course
Network Security 網 路 安 全 Lecture 1 February 20, 2012 洪 國 寶 1 Outline Course information Motivation Introduction to security Basic network concepts Network security models Outline of the course 2 Course
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course. Module-VII Lecture-I Introduction to Digital VLSI Testing
 Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
Why should I care about PDF application security?
 Why should I care about PDF application security? What you need to know to minimize your risk Table of contents 1: Program crashes present an opportunity for attack 2: Look for software that fully uses
Why should I care about PDF application security? What you need to know to minimize your risk Table of contents 1: Program crashes present an opportunity for attack 2: Look for software that fully uses
Chap. 1: Introduction
 Chap. 1: Introduction Introduction Services, Mechanisms, and Attacks The OSI Security Architecture Cryptography 1 1 Introduction Computer Security the generic name for the collection of tools designed
Chap. 1: Introduction Introduction Services, Mechanisms, and Attacks The OSI Security Architecture Cryptography 1 1 Introduction Computer Security the generic name for the collection of tools designed
Index Terms Cloud Storage Services, data integrity, dependable distributed storage, data dynamics, Cloud Computing.
 Volume 3, Issue 5, May 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Privacy - Preserving
Volume 3, Issue 5, May 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Privacy - Preserving
PREVENTING ZERO-DAY ATTACKS IN MOBILE DEVICES
 PREVENTING ZERO-DAY ATTACKS IN MOBILE DEVICES Ira Winkler Codenomicon Session ID: MBS-W05 Session Classification: Intermediate Zero Day Attacks Zero day attacks are rising in prominence They tend to be
PREVENTING ZERO-DAY ATTACKS IN MOBILE DEVICES Ira Winkler Codenomicon Session ID: MBS-W05 Session Classification: Intermediate Zero Day Attacks Zero day attacks are rising in prominence They tend to be
Towards a Hardware Trojan Detection Cycle
 Towards a Hardware Trojan Detection Cycle Adrian Dabrowski, Heidelinde Hobel, Johanna Ullrich, Katharina Krombholz, Edgar Weippl SBA Research, Vienna, Austria E-Mail: (firstletterfirstname)(lastname)@sba-research.org
Towards a Hardware Trojan Detection Cycle Adrian Dabrowski, Heidelinde Hobel, Johanna Ullrich, Katharina Krombholz, Edgar Weippl SBA Research, Vienna, Austria E-Mail: (firstletterfirstname)(lastname)@sba-research.org
Introduction to Runtime Application Self Protection (RASP) Making Applications Self Protecting, Self Diagnosing and Self Testing
 Introduction to Runtime Application Self Protection (RASP) Making Applications Self Protecting, Self Diagnosing and Self Testing The cyber security landscape has become increasingly complex in recent years.
Introduction to Runtime Application Self Protection (RASP) Making Applications Self Protecting, Self Diagnosing and Self Testing The cyber security landscape has become increasingly complex in recent years.
VON BRAUN LABS. Issue #1 WE PROVIDE COMPLETE SOLUTIONS ULTRA LOW POWER STATE MACHINE SOLUTIONS VON BRAUN LABS. State Machine Technology
 VON BRAUN LABS WE PROVIDE COMPLETE SOLUTIONS WWW.VONBRAUNLABS.COM Issue #1 VON BRAUN LABS WE PROVIDE COMPLETE SOLUTIONS ULTRA LOW POWER STATE MACHINE SOLUTIONS State Machine Technology IoT Solutions Learn
VON BRAUN LABS WE PROVIDE COMPLETE SOLUTIONS WWW.VONBRAUNLABS.COM Issue #1 VON BRAUN LABS WE PROVIDE COMPLETE SOLUTIONS ULTRA LOW POWER STATE MACHINE SOLUTIONS State Machine Technology IoT Solutions Learn
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Are you prepared to be next? Invensys Cyber Security
 Defense In Depth Are you prepared to be next? Invensys Cyber Security Sven Grone Critical Controls Solutions Consultant Presenting on behalf of Glen Bounds Global Modernization Consultant Agenda Cyber
Defense In Depth Are you prepared to be next? Invensys Cyber Security Sven Grone Critical Controls Solutions Consultant Presenting on behalf of Glen Bounds Global Modernization Consultant Agenda Cyber
CMSC 421, Operating Systems. Fall 2008. Security. URL: http://www.csee.umbc.edu/~kalpakis/courses/421. Dr. Kalpakis
 CMSC 421, Operating Systems. Fall 2008 Security Dr. Kalpakis URL: http://www.csee.umbc.edu/~kalpakis/courses/421 Outline The Security Problem Authentication Program Threats System Threats Securing Systems
CMSC 421, Operating Systems. Fall 2008 Security Dr. Kalpakis URL: http://www.csee.umbc.edu/~kalpakis/courses/421 Outline The Security Problem Authentication Program Threats System Threats Securing Systems
