Hardware Trojans Detection Methods Julien FRANCQ
|
|
|
- Duane Antony Higgins
- 8 years ago
- Views:
Transcription
1 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th
2 Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 / 40
3 Section Presentation Presentation c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 3 / 40
4 HINT Project Profile Presentation HINT = Holistic Approaches for Integrity of ICT-Systems Project Number: Project website: Project start: October 1, 2012 Project duration: 3 years Total Costs: e EC-Contribution: e Project is co-financed by the European Commission under Seventh Framework Programme c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 4 / 40
5 Missions Presentation Development of a common framework for system integrity checking Use developed technologies on real-time applications Prepare adoption by future security evaluation schemes c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 5 / 40
6 Motivation Presentation Authenticity and integrity of hardware components in modern ICT systems Security challenged by improving attacks Recent trends: Counterfeiting of hardware components Hardware Trojans : Hidden functions in Integrated Circuits HINT proposal: Novel technologies to support assurance of genuineness and integrity c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 6 / 40
7 Technical Approach Presentation Holistic Integrity Checking for Components in ICT-Systems c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 7 / 40
8 Objectives Presentation Main objective: Improve security of architectures and platforms based on tamper-resistant integrated circuits Development of methods to: Perform at-time-of-use integrated checking of the global integrity of a system for hardware and embedded software Check the genuineness of the secure integrated circuits by detecting functional clones or counterfeited circuits Detect the presence of Hardware Trojans Main technologies used: Physically Unclonable Functions, enabling to authenticate a hardware component using a physical, intrinsic and unique property of the device Side Channel based analysis to monitor the behaviour of hardware components and to detect changes from their original specifications and implementations c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 8 / 40
9 Section Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 9 / 40
10 Hardware Trojan (HT) Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects Malicious modifications of an Integrated Circuit (IC) during its design flow c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 10 / 40
11 Context Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects Outsourcing of the fabrication of the ICs Difficult to ensure the trust in all the steps of the design flow Trusted Intentional mistakes Idea Specification Malicious IP-Cores Malicous Design Tampering Files Design (HDL) Synthesis IP Cores Manipulated Tools Mapping FPGA Place & Route ASIC Tampering Files Manipulation While Loading Config File Loader Tampering Files Hardware Layout Production Manipulate Design Process Backdoors FPGA ASIC Attack IC Malicious External Components Board IC c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 11 / 40
12 HTs in Practice Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects 2005: US Department of Defense 2007: DARPA Trust in IC Program 2009: Hot Topic of CHES conference After 2009: other conferences (DATE, HOST, CARDIS, ReConFig, etc.) [Skorobogatov et al.: Breaktrough Silicon Scanning Discovers Backdoor in Military Chip, CHES 2012] [Becker et al.: Stealthy Dopant-Level Hardware Trojans, CHES 2013] 2 research projects: HINT (European funded) and HOMERE (French funded) HTs: real and emerging threat c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 12 / 40
13 Possible Payloads Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects Kill switch Fighters Dysfonctional circuit Satellite which works only 6 months Secret information leakage Ciphered communications Help a malware by providing a backdoor Privilege escalation, automatic login, password theft Prevent from going to sleep mode Autonomy etc. c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 13 / 40
14 Section c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 14 / 40
15 Taxonomy: tree where each branch defines a different property In the ideal case, a specific HT must be on only one leaf of the tree Benefits of the taxonomy Systematic study of their characteristics Specific detection methods for each HT class Benchmark circuits for each class Best existing taxonomy: Trust-Hub c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 15 / 40
16 Trust-Hub Taxonomy c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 16 / 40
17 Factoring the Taxonomy 4 (effects) 5 (locations) 5 (insertion phases) 6 (abstraction levels) 5 (activation mechanisms) = 3000 different HTs! Very rich taxonomy! Impossible to implement them all, and then detect them Factoring this taxonomy Total: 100 HTs c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 17 / 40
18 Section c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 18 / 40
19 Presentation Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 19 / 40
20 HT Protection Post Production Detection Prevention Destructive Non-Destructive Supportive Design Secure Design Trusted Production Optical Run-Time Test-Time Side Channel Analysis Logic Testing No method is 100% successfull! c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 20 / 40
21 Detect HTs? Not so easy... 1 Systems on Chip are more and more complex, and detecting a small malicious modification is difficult 2 Reverse-engineering inspection is costly and difficult No guarantee that the remaining ICs are HT-free 3 By nature, HTs are designed to be stealthy Not easily detectable with conventional logic testing 4 By nature, HTs are small to be not easily detected by optical analysis Difficult to detect them with side-channel (power consumption, electromagnetic radiations, etc.) analysis c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 21 / 40
22 Presentation Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 22 / 40
23 Test Generation (1/2) Conventional logic testing cannot be used to reliably detect HT Manufacturing defects (stuck-at-faults) HT effects Difficult to trigger a HT Time-bombs Some HTs have no impact on functional outputs (Trojan Side-Channels) Vast spectrum of possible HTs c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 23 / 40
24 Test Generation (2/2) HTs are on low controllability and observability nodes for a rare triggering Extremely challenging to exhaustively generate test vectors for triggering a HT c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 24 / 40
25 Deterministic vs. Probabilistic Approach Deterministic approach difficult Many possible HTs Function of some IC nodes Exhaustive enumeration impossible Statistic approach : 1 Find rare events in the circuit 2 Get a list of HTs which can be inserted 3 Generate test vectors and estimate their coverage 4 Set of high quality test vectors 85% reduction in testset length compared to a random approach, but less efficient with big triggers and takes a long time c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 25 / 40
26 Presentation Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 26 / 40
27 Side-Channel Analysis Any HT in the IC should modify its leakage current (IDDQ), dynamic power trace (IDDT), path-delay characteristic, ElectroMagnetic (EM) radiation. Don t need to trigger a HT for measuring its effects Test vectors generation easier than for logic testing Needs HT-free circuits Get side-channel measurements and then reverse-engineering to check if the IC is HT-free If so, the measurements become a reference, and we can then compare the side-channels of the other circuits c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 27 / 40
28 Global Side-Channel Analysis Green: RSA signal Red: Process noise (offset) Black: HT signal (offset) c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 28 / 40
29 Local Side-Channel Analysis Local Side-Channel Analysis more efficient than global ones Needs again HT-free circuits Maximize/Minimize the activity of some IC areas c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 29 / 40
30 Noise and Sensitivity c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 30 / 40
31 Presentation Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 31 / 40
32 Added circuitry for the HT detection must not be infected itself At best, the added circuitry is disabled (e.g., fault countermeasure) At worst, it can be turned into a backdoor (e.g., scan chain) A HT triggering logic can exploit the Test/Scan Enable control line to disable itself Parametric HTs very difficult to detect c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 32 / 40
33 Presentation Definition Where introducing HTs? Initiatives (Possibly) Desastrous Effects c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 33 / 40
34 Complementary methods Combine test-time and run-time methods Modify the IC for assistive and preventive methods c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 34 / 40
35 Section c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 35 / 40
36 Introduction To improve HT detection rate, modify the IC Prevent from the insertion of HT Ease side-channel analysis and logic testing 4 main methods: Delay-Based Methods Rare Event Removal Design for Trojan Test Proof-Carrying Hardware Run-Time Detection Methods c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 36 / 40
37 Run-Time Methods Last line of defense On-line monitoring of the IC in real-time, for checks: Critical operations, Idle mode, Security policies, Performance or availability of some units, etc. Costly c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 37 / 40
38 Run-Time Methods Disable one suspect block or force one operation SPN : Signal Probe Network SM : Security Monitor ( FSM) SECOPRO : Security and Control Processor Configurations ciphered and stored in secured Flash memory Overhead? c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 38 / 40
39 Hardware Trojans are real threats for integrated circuits HT taxonomy is very rich No HT detection method of the state-of-the-art is 100% successful 3 lines of defense: Test-Time Methods Run-Time Methods A European initiative: HINT project Let s talk in front of HINT Poster! A French initiative: HOMERE project Let s attend to the Franck Courbon presentation! Very encouraging first results: Infected benchmark circuits will be available soon A common platform for side-channel analysis A low-cost way to extract internal delays of ICs by clock glitching c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 39 / 40
40 Thanks! Questions? c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 40 / 40
Hardware Trojans: A Threat for CyberSecurity
 Hardware Trojans: A Threat for CyberSecurity Julien Francq julien.francq@cassidian.com Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
Hardware Trojans: A Threat for CyberSecurity Julien Francq julien.francq@cassidian.com Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
Microsemi Security Center of Excellence
 Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
PFP Technology White Paper
 PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
Horst Görtz Institute for IT-Security
 Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
KEEP IT SYNPLE STUPID
 Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Understanding Integrated Circuit Security Threats. Asif Iqbal Senior Program Manager, Apple Inc. SDM 11
 Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Implementing Program Protection and Cybersecurity
 Implementing Program Protection and Cybersecurity Melinda Reed Office of the Deputy Assistant Secretary of Defense for Systems Engineering Mark Godino Office of the Deputy Assistant Secretary of Defense
Implementing Program Protection and Cybersecurity Melinda Reed Office of the Deputy Assistant Secretary of Defense for Systems Engineering Mark Godino Office of the Deputy Assistant Secretary of Defense
Hardware Testing and Security Requirements in the Nano Era
 Secure Hardware in the Nano Era: Some New Directions Swarup Bhunia T. and A. Schroeder Associate Professor Electrical Engineering and Computer Science March ISQED 2015 1 SoC Security Issues & Protection
Secure Hardware in the Nano Era: Some New Directions Swarup Bhunia T. and A. Schroeder Associate Professor Electrical Engineering and Computer Science March ISQED 2015 1 SoC Security Issues & Protection
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
Computer Security DD2395
 Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger buc@kth.se Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger buc@kth.se Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
What is a Smart Card?
 An Introduction to Smart Cards and RFIDs Prof. Keith E. Mayes Keith.Mayes@rhul.ac.uk Director of the ISG - Smart Card Centre www.scc.rhul.ac.uk Learning Objectives (MSc MSc) Identify the various types
An Introduction to Smart Cards and RFIDs Prof. Keith E. Mayes Keith.Mayes@rhul.ac.uk Director of the ISG - Smart Card Centre www.scc.rhul.ac.uk Learning Objectives (MSc MSc) Identify the various types
Problems of Security in Ad Hoc Sensor Network
 Problems of Security in Ad Hoc Sensor Network Petr Hanáček * hanacek@fit.vutbr.cz Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Problems of Security in Ad Hoc Sensor Network Petr Hanáček * hanacek@fit.vutbr.cz Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Detecting Zero-Day Attacks in Real Time on Day Zero
 Detecting Zero-Day Attacks in Real Time on Day Zero Standards Certification Education & Training Publishing Conferences & Exhibits Industrial Device Integrity Assessment Hardware, OS & Software Malware
Detecting Zero-Day Attacks in Real Time on Day Zero Standards Certification Education & Training Publishing Conferences & Exhibits Industrial Device Integrity Assessment Hardware, OS & Software Malware
Hardware Security Modules for Protecting Embedded Systems
 Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006
 Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
Threats and Attacks. Modifications by Prof. Dong Xuan and Adam C. Champion. Principles of Information Security, 5th Edition 1
 Threats and Attacks Modifications by Prof. Dong Xuan and Adam C. Champion Principles of Information Security, 5th Edition 1 Learning Objectives Upon completion of this material, you should be able to:
Threats and Attacks Modifications by Prof. Dong Xuan and Adam C. Champion Principles of Information Security, 5th Edition 1 Learning Objectives Upon completion of this material, you should be able to:
Raccoon: Closing Side-Channels through Obfuscated Execution
 Raccoon: Closing Side-Channels through Obfuscated Execution by Ashay Rane, Calvin Lin, Mohit Tiwari Presentation by Arjun Khurana and Timothy Wong Outline Background Raccoon Design Evaluation Conclusion
Raccoon: Closing Side-Channels through Obfuscated Execution by Ashay Rane, Calvin Lin, Mohit Tiwari Presentation by Arjun Khurana and Timothy Wong Outline Background Raccoon Design Evaluation Conclusion
Section 12 MUST BE COMPLETED BY: 4/22
 Test Out Online Lesson 12 Schedule Section 12 MUST BE COMPLETED BY: 4/22 Section 12.1: Best Practices This section discusses the following security best practices: Implement the Principle of Least Privilege
Test Out Online Lesson 12 Schedule Section 12 MUST BE COMPLETED BY: 4/22 Section 12.1: Best Practices This section discusses the following security best practices: Implement the Principle of Least Privilege
Security IC Platform Protection Profile
 Security IC Platform Protection Profile Version 1.0 15.06.2007 developed by Atmel Infineon Technologies AG NXP Semiconductors Renesas Technology Europe Ltd. STMicroelectronics Registered and Certified
Security IC Platform Protection Profile Version 1.0 15.06.2007 developed by Atmel Infineon Technologies AG NXP Semiconductors Renesas Technology Europe Ltd. STMicroelectronics Registered and Certified
Attachment A. Identification of Risks/Cybersecurity Governance
 Attachment A Identification of Risks/Cybersecurity Governance 1. For each of the following practices employed by the Firm for management of information security assets, please provide the month and year
Attachment A Identification of Risks/Cybersecurity Governance 1. For each of the following practices employed by the Firm for management of information security assets, please provide the month and year
Secure application programming in the presence of side channel attacks. Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203
 Secure application programming in the presence of side channel attacks Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203 Attacks in the field Survey 2007*, Hong Kong: Asia-Pacific Pay-TV
Secure application programming in the presence of side channel attacks Marc Witteman & Harko Robroch Riscure 04/09/08 Session Code: RR-203 Attacks in the field Survey 2007*, Hong Kong: Asia-Pacific Pay-TV
Value Paper Author: Edgar C. Ramirez. Diverse redundancy used in SIS technology to achieve higher safety integrity
 Value Paper Author: Edgar C. Ramirez Diverse redundancy used in SIS technology to achieve higher safety integrity Diverse redundancy used in SIS technology to achieve higher safety integrity Abstract SIS
Value Paper Author: Edgar C. Ramirez Diverse redundancy used in SIS technology to achieve higher safety integrity Diverse redundancy used in SIS technology to achieve higher safety integrity Abstract SIS
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Software Hardware Binding with Quiddikey
 Software Hardware Binding with Quiddikey Mass scale solution against software piracy Secure your digital life Software-Hardware Binding solutions are typically required for Flash-based systems in which
Software Hardware Binding with Quiddikey Mass scale solution against software piracy Secure your digital life Software-Hardware Binding solutions are typically required for Flash-based systems in which
PUBLIC REPORT. Red Team Testing of the ES&S Unity 3.0.1.1 Voting System. Freeman Craft McGregor Group (FCMG) Red Team
 PUBLIC REPORT Red Team Testing of the Voting System Freeman Craft McGregor Group (FCMG) Red Team Prepared for the California Secretary of State by: Jacob D. Stauffer, FCMG Red Team Project Manager Page
PUBLIC REPORT Red Team Testing of the Voting System Freeman Craft McGregor Group (FCMG) Red Team Prepared for the California Secretary of State by: Jacob D. Stauffer, FCMG Red Team Project Manager Page
Cisco Trust Anchor Technologies
 Data Sheet Cisco Trust Anchor Technologies Overview Cisco Trust Anchor Technologies provide the foundation for trustworthy systems across Cisco. The Cisco Trust Anchor and a Secure Boot check of signed
Data Sheet Cisco Trust Anchor Technologies Overview Cisco Trust Anchor Technologies provide the foundation for trustworthy systems across Cisco. The Cisco Trust Anchor and a Secure Boot check of signed
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
Developing Secure Software in the Age of Advanced Persistent Threats
 Developing Secure Software in the Age of Advanced Persistent Threats ERIC BAIZE EMC Corporation DAVE MARTIN EMC Corporation Session ID: ASEC-201 Session Classification: Intermediate Our Job: Keep our Employer
Developing Secure Software in the Age of Advanced Persistent Threats ERIC BAIZE EMC Corporation DAVE MARTIN EMC Corporation Session ID: ASEC-201 Session Classification: Intermediate Our Job: Keep our Employer
Cybersecurity Kill Chain. William F. Crowe, CISA, CISM, CRISC, CRMA September 2015 ISACA Jacksonville Chapter Meeting August 13, 2015
 Cybersecurity Kill Chain William F. Crowe, CISA, CISM, CRISC, CRMA September 2015 ISACA Jacksonville Chapter Meeting August 13, 2015 Who Am I? Over 20 years experience with 17 years in the financial industry
Cybersecurity Kill Chain William F. Crowe, CISA, CISM, CRISC, CRMA September 2015 ISACA Jacksonville Chapter Meeting August 13, 2015 Who Am I? Over 20 years experience with 17 years in the financial industry
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Local Heating Attacks on Flash Memory Devices. Dr Sergei Skorobogatov
 Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: sps32@cam.ac.uk Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: sps32@cam.ac.uk Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 2 Systems Threats and Risks
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits)
 Page 1 of 6 Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits) TNCC Cybersecurity Program web page: http://tncc.edu/programs/cyber-security Course Description: Encompasses
Page 1 of 6 Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits) TNCC Cybersecurity Program web page: http://tncc.edu/programs/cyber-security Course Description: Encompasses
Security Architecture: From Start to Sustainment. Tim Owen, Chief Engineer SMS DGI Cyber Security Conference June 2013
 Security Architecture: From Start to Sustainment Tim Owen, Chief Engineer SMS DGI Cyber Security Conference June 2013 Security Architecture Topics Introduction Reverse Engineering the Threat Operational
Security Architecture: From Start to Sustainment Tim Owen, Chief Engineer SMS DGI Cyber Security Conference June 2013 Security Architecture Topics Introduction Reverse Engineering the Threat Operational
White Paper THE FOUR ATTACK VECTORS TO PREVENT OR DETECT RETAILER BREACHES. By James Christiansen, VP, Information Risk Management
 White Paper THE FOUR ATTACK VECTORS TO PREVENT OR DETECT RETAILER BREACHES By James Christiansen, VP, Information Risk Management Executive Summary Security breaches in the retail sector are becoming more
White Paper THE FOUR ATTACK VECTORS TO PREVENT OR DETECT RETAILER BREACHES By James Christiansen, VP, Information Risk Management Executive Summary Security breaches in the retail sector are becoming more
Advancing Cyber Security Using System Dynamics Simulation Modeling for System Resilience, Patching, and Software Development
 Interdisciplinary Consortium for Improving Critical Infrastructure Cybersecurity (IC) 3 12 February 2015 Advancing Cyber Security Using System Dynamics Simulation Modeling for System Resilience, Patching,
Interdisciplinary Consortium for Improving Critical Infrastructure Cybersecurity (IC) 3 12 February 2015 Advancing Cyber Security Using System Dynamics Simulation Modeling for System Resilience, Patching,
Smart Card Security How Can We Be So Sure?
 Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands bovenlander@tpd.tno.nl 1. Introduction
Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands bovenlander@tpd.tno.nl 1. Introduction
OCIE CYBERSECURITY INITIATIVE
 Topic: Cybersecurity Examinations Key Takeaways: OCIE will be conducting examinations of more than 50 registered brokerdealers and registered investment advisers, focusing on areas related to cybersecurity.
Topic: Cybersecurity Examinations Key Takeaways: OCIE will be conducting examinations of more than 50 registered brokerdealers and registered investment advisers, focusing on areas related to cybersecurity.
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge
 Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
The Reduced Address Space (RAS) for Application Memory Authentication
 The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
Implementation Details
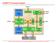 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
WORMS : attacks, defense and models. Presented by: Abhishek Sharma Vijay Erramilli
 WORMS : attacks, defense and models Presented by: Abhishek Sharma Vijay Erramilli What is a computer worm? Is it not the same as a computer virus? A computer worm is a program that selfpropagates across
WORMS : attacks, defense and models Presented by: Abhishek Sharma Vijay Erramilli What is a computer worm? Is it not the same as a computer virus? A computer worm is a program that selfpropagates across
Covert Operations: Kill Chain Actions using Security Analytics
 Covert Operations: Kill Chain Actions using Security Analytics Written by Aman Diwakar Twitter: https://twitter.com/ddos LinkedIn: http://www.linkedin.com/pub/aman-diwakar-ccie-cissp/5/217/4b7 In Special
Covert Operations: Kill Chain Actions using Security Analytics Written by Aman Diwakar Twitter: https://twitter.com/ddos LinkedIn: http://www.linkedin.com/pub/aman-diwakar-ccie-cissp/5/217/4b7 In Special
A8.1 Asset Management Responsibility for assets: To identify organisational assets and define appropriate protection responsibilities.
 A8.1 Asset Management Responsibility for assets: To identify organisational assets and define appropriate protection responsibilities. 8.1.1 Inventory of assets. Tripwire IP360 provides comprehensive host
A8.1 Asset Management Responsibility for assets: To identify organisational assets and define appropriate protection responsibilities. 8.1.1 Inventory of assets. Tripwire IP360 provides comprehensive host
Certified Ethical Hacker Exam 312-50 Version Comparison. Version Comparison
 CEHv8 vs CEHv7 CEHv7 CEHv8 19 Modules 20 Modules 90 Labs 110 Labs 1700 Slides 1770 Slides Updated information as per the latest developments with a proper flow Classroom friendly with diagrammatic representation
CEHv8 vs CEHv7 CEHv7 CEHv8 19 Modules 20 Modules 90 Labs 110 Labs 1700 Slides 1770 Slides Updated information as per the latest developments with a proper flow Classroom friendly with diagrammatic representation
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices
 An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany vater@ihpmicroelectronics.com
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany vater@ihpmicroelectronics.com
Joint Interpretation Library
 for smart cards and similar devices Document purpose: provide requirements to developers and guidance to evaluators to fulfill the Security Architecture requirements of CC V3 ADV_ARC family. Version 2.0
for smart cards and similar devices Document purpose: provide requirements to developers and guidance to evaluators to fulfill the Security Architecture requirements of CC V3 ADV_ARC family. Version 2.0
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl chris@flylogic.net nohl@srlabs.de Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl chris@flylogic.net nohl@srlabs.de Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Securing the Supply Chain for Electronic Equipment: A Strategy and Framework by Scott Borg
 The Internet Security Alliance Securing the Supply Chain for Electronic Equipment: A Strategy and Framework by Scott Borg Background on This Project This short paper is based on sixteen months of meetings,
The Internet Security Alliance Securing the Supply Chain for Electronic Equipment: A Strategy and Framework by Scott Borg Background on This Project This short paper is based on sixteen months of meetings,
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion
 Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Wireless Sensor Network Security. Seth A. Hellbusch CMPE 257
 Wireless Sensor Network Security Seth A. Hellbusch CMPE 257 Wireless Sensor Networks (WSN) 2 The main characteristics of a WSN include: Power consumption constrains for nodes using batteries or energy
Wireless Sensor Network Security Seth A. Hellbusch CMPE 257 Wireless Sensor Networks (WSN) 2 The main characteristics of a WSN include: Power consumption constrains for nodes using batteries or energy
Persistence Mechanisms as Indicators of Compromise
 Persistence Persistence Mechanisms as Indicators of Compromise An automated technology for identifying cyber attacks designed to survive indefinitely the reboot process on PCs White Paper Date: October
Persistence Persistence Mechanisms as Indicators of Compromise An automated technology for identifying cyber attacks designed to survive indefinitely the reboot process on PCs White Paper Date: October
On Security Evaluation Testing
 On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
Poisoning Network Visibility in Software-Defined Networks: New Attacks and Countermeasures Sungmin Hong, Lei Xu, Haopei Wang, Guofei Gu
 Poisoning Network Visibility in Software-Defined Networks: New Attacks and Countermeasures Sungmin Hong, Lei Xu, Haopei Wang, Guofei Gu Presented by Alaa Shublaq SDN Overview Software-Defined Networking
Poisoning Network Visibility in Software-Defined Networks: New Attacks and Countermeasures Sungmin Hong, Lei Xu, Haopei Wang, Guofei Gu Presented by Alaa Shublaq SDN Overview Software-Defined Networking
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems
 Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
Security in the Age of Nanocomputing. Hacking Devices
 Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
CycurHSM An Automotive-qualified Software Stack for Hardware Security Modules
 CycurHSM An Automotive-qualified Software Stack for Hardware Security Modules Dr. Frederic Stumpf, ESCRYPT GmbH Embedded Security, Stuttgart, Germany 1 Introduction Electronic Control Units (ECU) are embedded
CycurHSM An Automotive-qualified Software Stack for Hardware Security Modules Dr. Frederic Stumpf, ESCRYPT GmbH Embedded Security, Stuttgart, Germany 1 Introduction Electronic Control Units (ECU) are embedded
Cryptographic Rights Management of FPGA Intellectual Property Cores
 Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom tom@algotronix.com ABSTRACT As the capacity of FPGA s increases
Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom tom@algotronix.com ABSTRACT As the capacity of FPGA s increases
Seven Strategies to Defend ICSs
 INTRODUCTION Cyber intrusions into US Critical Infrastructure systems are happening with increased frequency. For many industrial control systems (ICSs), it s not a matter of if an intrusion will take
INTRODUCTION Cyber intrusions into US Critical Infrastructure systems are happening with increased frequency. For many industrial control systems (ICSs), it s not a matter of if an intrusion will take
Enterprise Cybersecurity: Building an Effective Defense
 Enterprise Cybersecurity: Building an Effective Defense Chris Williams Oct 29, 2015 14 Leidos 0224 1135 About the Presenter Chris Williams is an Enterprise Cybersecurity Architect at Leidos, Inc. He has
Enterprise Cybersecurity: Building an Effective Defense Chris Williams Oct 29, 2015 14 Leidos 0224 1135 About the Presenter Chris Williams is an Enterprise Cybersecurity Architect at Leidos, Inc. He has
Transaction Anomaly Protection Stopping Malware At The Door. White Paper
 Transaction Anomaly Protection Stopping Malware At The Door White Paper Table of Contents Overview 3 Programmable Crime Logic Alter Web Application Flow & Content 3 Programmable Crime Logic Defeats Server-Side
Transaction Anomaly Protection Stopping Malware At The Door White Paper Table of Contents Overview 3 Programmable Crime Logic Alter Web Application Flow & Content 3 Programmable Crime Logic Defeats Server-Side
Power Reduction Techniques in the SoC Clock Network. Clock Power
 Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
How To Protect A Web Application From Attack From A Trusted Environment
 Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
Database and Data Mining Security
 Database and Data Mining Security 1 Threats/Protections to the System 1. External procedures security clearance of personnel password protection controlling application programs Audit 2. Physical environment
Database and Data Mining Security 1 Threats/Protections to the System 1. External procedures security clearance of personnel password protection controlling application programs Audit 2. Physical environment
SENSE Security overview 2014
 SENSE Security overview 2014 Abstract... 3 Overview... 4 Installation... 6 Device Control... 7 Enrolment Process... 8 Authentication... 9 Network Protection... 12 Local Storage... 13 Conclusion... 15 2
SENSE Security overview 2014 Abstract... 3 Overview... 4 Installation... 6 Device Control... 7 Enrolment Process... 8 Authentication... 9 Network Protection... 12 Local Storage... 13 Conclusion... 15 2
Security testing of hardware product
 Alain MERLE CESTI LETI CEA Grenoble Alain.merle@cea.fr Security testing of hardware product DCIS/SASTI/CESTI 1 Abstract «What are you doing in ITSEFs?» Testing, Security testing, Attacks, Evaluations,
Alain MERLE CESTI LETI CEA Grenoble Alain.merle@cea.fr Security testing of hardware product DCIS/SASTI/CESTI 1 Abstract «What are you doing in ITSEFs?» Testing, Security testing, Attacks, Evaluations,
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things.
 What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
What s Wrong with Information Security Today? You are looking in the wrong places for the wrong things. AGENDA Current State of Information Security Data Breach Statics Data Breach Case Studies Why current
10 Gbps Line Speed Programmable Hardware for Open Source Network Applications*
 10 Gbps Line Speed Programmable Hardware for Open Source Network Applications* Livio Ricciulli livio@metanetworks.org (408) 399-2284 http://www.metanetworks.org *Supported by the Division of Design Manufacturing
10 Gbps Line Speed Programmable Hardware for Open Source Network Applications* Livio Ricciulli livio@metanetworks.org (408) 399-2284 http://www.metanetworks.org *Supported by the Division of Design Manufacturing
High Performance Network Security
 White PAPER High Performance Network Security Following the inexorable rise in the demand for bandwidth, the adoption of 10 Gigabit Ethernet is accelerating. An estimated 60,000 Ten GbE ports were sold
White PAPER High Performance Network Security Following the inexorable rise in the demand for bandwidth, the adoption of 10 Gigabit Ethernet is accelerating. An estimated 60,000 Ten GbE ports were sold
Extended Boundary Scan Test breaching the analog ban. Marcel Swinnen, teamleader test engineering
 Extended Boundary Scan Test breaching the analog ban Marcel Swinnen, teamleader test engineering 11-11-2014 2 zero-defect quality impossible to produce zero-defect boards early involvement services (Design
Extended Boundary Scan Test breaching the analog ban Marcel Swinnen, teamleader test engineering 11-11-2014 2 zero-defect quality impossible to produce zero-defect boards early involvement services (Design
MXMedia CipherStream. Preliminary Assessment. Copyright 2012 Farncombe 1.0. Author: T +44 1256 844161 F +44 1256 844162 www.farncombe.
 MXMedia CipherStream Preliminary Assessment 1.0 Author: T +44 1256 844161 F +44 1256 844162 www.farncombe.com Copyright 2012 Farncombe Belvedere Basing View Basingstoke RG21 4HG This document and the information
MXMedia CipherStream Preliminary Assessment 1.0 Author: T +44 1256 844161 F +44 1256 844162 www.farncombe.com Copyright 2012 Farncombe Belvedere Basing View Basingstoke RG21 4HG This document and the information
EVITA-Project.org: E-Safety Vehicle Intrusion Protected Applications
 EVITA-Project.org: E-Safety Vehicle Intrusion Protected Applications 7 th escar Embedded Security in Cars Conference November 24 25, 2009, Düsseldorf Dr.-Ing. Olaf Henniger, Fraunhofer SIT Darmstadt Hervé
EVITA-Project.org: E-Safety Vehicle Intrusion Protected Applications 7 th escar Embedded Security in Cars Conference November 24 25, 2009, Düsseldorf Dr.-Ing. Olaf Henniger, Fraunhofer SIT Darmstadt Hervé
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip
 Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
CHANCES AND RISKS FOR SECURITY IN MULTICORE PROCESSORS
 CHANCES AND RISKS FOR SECURITY IN MULTICORE PROCESSORS Prof. Dr.-Ing. Georg Sigl Institute for Security in Information Technology Technical University Munich sigl@tum.de Fraunhofer Research Institution
CHANCES AND RISKS FOR SECURITY IN MULTICORE PROCESSORS Prof. Dr.-Ing. Georg Sigl Institute for Security in Information Technology Technical University Munich sigl@tum.de Fraunhofer Research Institution
Physical Security: Status and Outlook
 Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
1. Computer Security: An Introduction. Definitions Security threats and analysis Types of security controls Security services
 1. Computer Security: An Introduction Definitions Security threats and analysis Types of security controls Security services Mar 2012 ICS413 network security 1 1.1 Definitions A computer security system
1. Computer Security: An Introduction Definitions Security threats and analysis Types of security controls Security services Mar 2012 ICS413 network security 1 1.1 Definitions A computer security system
Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified
 Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
UNCLASSIFIED Version 1.0 May 2012
 Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
Security in ST : From Company to Products
 Security in ST : From Company to Products July 2015 Thierry FENSCH Innovation, Collaboration and Efficiency Director Grenoble Site A global semiconductor leader 2014 revenues of $7.40B Who we are 2 Approximately
Security in ST : From Company to Products July 2015 Thierry FENSCH Innovation, Collaboration and Efficiency Director Grenoble Site A global semiconductor leader 2014 revenues of $7.40B Who we are 2 Approximately
Defending Against Data Beaches: Internal Controls for Cybersecurity
 Defending Against Data Beaches: Internal Controls for Cybersecurity Presented by: Michael Walter, Managing Director and Chris Manning, Associate Director Protiviti Atlanta Office Agenda Defining Cybersecurity
Defending Against Data Beaches: Internal Controls for Cybersecurity Presented by: Michael Walter, Managing Director and Chris Manning, Associate Director Protiviti Atlanta Office Agenda Defining Cybersecurity
Rapid System Prototyping with FPGAs
 Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
WEB ATTACKS AND COUNTERMEASURES
 WEB ATTACKS AND COUNTERMEASURES February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
WEB ATTACKS AND COUNTERMEASURES February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in
The Web AppSec How-to: The Defenders Toolbox
 The Web AppSec How-to: The Defenders Toolbox Web application security has made headline news in the past few years. Incidents such as the targeting of specific sites as a channel to distribute malware
The Web AppSec How-to: The Defenders Toolbox Web application security has made headline news in the past few years. Incidents such as the targeting of specific sites as a channel to distribute malware
Enterprise Application Security Workshop Series
 Enterprise Application Security Workshop Series Phone 877-697-2434 fax 877-697-2434 www.thesagegrp.com Defending JAVA Applications (3 Days) In The Sage Group s Defending JAVA Applications workshop, participants
Enterprise Application Security Workshop Series Phone 877-697-2434 fax 877-697-2434 www.thesagegrp.com Defending JAVA Applications (3 Days) In The Sage Group s Defending JAVA Applications workshop, participants
Secure Hardware PV018 Masaryk University Faculty of Informatics
 Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
Database security issues PETRA BILIĆ ALEXANDER SPARBER
 Database security issues PETRA BILIĆ ALEXANDER SPARBER Introduction Database security is one aspect of computer security It uses different information security controls to protect databases Information
Database security issues PETRA BILIĆ ALEXANDER SPARBER Introduction Database security is one aspect of computer security It uses different information security controls to protect databases Information
IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits
 IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits SUMMARY CONTENTS 1. CONTEXT 2. TECHNOLOGY TRENDS 3. MOTIVATION 4. WHAT IS IC-EMC 5. SUPPORTED STANDARD 6. EXAMPLES CONTEXT - WHY
IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits SUMMARY CONTENTS 1. CONTEXT 2. TECHNOLOGY TRENDS 3. MOTIVATION 4. WHAT IS IC-EMC 5. SUPPORTED STANDARD 6. EXAMPLES CONTEXT - WHY
MRG Effitas 360 Assessment & Certification Programme Q4 2014
 MRG Effitas 360 Assessment & Certification Programme Q4 2014 1 Contents Introduction... 3 Executive summary... 3 Certification... 4 The purpose of this report... 5 Tests employed... 6 Security Applications
MRG Effitas 360 Assessment & Certification Programme Q4 2014 1 Contents Introduction... 3 Executive summary... 3 Certification... 4 The purpose of this report... 5 Tests employed... 6 Security Applications
Announcement of a new IAEA Co-ordinated Research Programme (CRP)
 Announcement of a new IAEA Co-ordinated Research Programme (CRP) 1. Title of Co-ordinated Research Programme Design and engineering aspects of the robustness of digital instrumentation and control (I&C)
Announcement of a new IAEA Co-ordinated Research Programme (CRP) 1. Title of Co-ordinated Research Programme Design and engineering aspects of the robustness of digital instrumentation and control (I&C)
Malicious Software. Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ Ola.Flygt@vxu.se +46 470 70 86 49. Viruses and Related Threats
 Malicious Software Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ Ola.Flygt@vxu.se +46 470 70 86 49 1 Outline Viruses and Related Threats Malicious Programs The Nature of Viruses Antivirus
Malicious Software Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ Ola.Flygt@vxu.se +46 470 70 86 49 1 Outline Viruses and Related Threats Malicious Programs The Nature of Viruses Antivirus
An Innovative Two Factor Authentication Method: The QRLogin System
 An Innovative Two Factor Authentication Method: The QRLogin System Soonduck Yoo*, Seung-jung Shin and Dae-hyun Ryu Dept. of IT, University of Hansei, 604-5 Dangjung-dong Gunpo city, Gyeonggi do, Korea,
An Innovative Two Factor Authentication Method: The QRLogin System Soonduck Yoo*, Seung-jung Shin and Dae-hyun Ryu Dept. of IT, University of Hansei, 604-5 Dangjung-dong Gunpo city, Gyeonggi do, Korea,
Cyber/IT Risk: Threat Intelligence Countering Advanced Adversaries Jeff Lunglhofer, Principal, Booz Allen. 14th Annual Risk Management Convention
 Cyber/IT Risk: Threat Intelligence Countering Advanced Adversaries Jeff Lunglhofer, Principal, Booz Allen 14th Annual Risk Management Convention New York, New York March 13, 2013 Today s Presentation 1)
Cyber/IT Risk: Threat Intelligence Countering Advanced Adversaries Jeff Lunglhofer, Principal, Booz Allen 14th Annual Risk Management Convention New York, New York March 13, 2013 Today s Presentation 1)
Security Threats on National Defense ICT based on IoT
 , pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
, pp.94-98 http://dx.doi.org/10.14257/astl.205.97.16 Security Threats on National Defense ICT based on IoT Jin-Seok Yang 1, Ho-Jae Lee 1, Min-Woo Park 1 and Jung-ho Eom 2 1 Department of Computer Engineering,
Fighting Off an Advanced Persistent Threat & Defending Infrastructure and Data. Dave Shackleford February, 2012
 Fighting Off an Advanced Persistent Threat & Defending Infrastructure and Data Dave Shackleford February, 2012 Agenda Attacks We ve Seen Advanced Threats what s that mean? A Simple Example What can we
Fighting Off an Advanced Persistent Threat & Defending Infrastructure and Data Dave Shackleford February, 2012 Agenda Attacks We ve Seen Advanced Threats what s that mean? A Simple Example What can we
