Assertion Synthesis Enabling Assertion-Based Verification For Simulation, Formal and Emulation Flows
|
|
|
- Damian Erik Golden
- 10 years ago
- Views:
Transcription
1 Assertion Synthesis Enabling Assertion-Based Verification For Simulation, Formal and Emulation Flows
2 Manual Assertion Creation is ABV Bottleneck Assertion-Based Verification adopted by leading design companies o Most effective approach to reduce chip failure Corner case bugs Identify testing coverage holes o Reduce overall verification effort Not enough assertions and coverage goals written Not getting the benefit of ABV methodology o Functional errors still #1 chip failure cause and cost o Need an effective approach to create assertions <2>
3 Blackbox Assertions Capture End to End behaviors using interface signals o Off the shelf VIP for standard bus protocols o An alternative to blackbox checkers Issues o Difficult to create and maintain due to complexity Duplicates RTL logic in assertion language More temporal because of limited use of signals o Slow down simulation (due to multi-cycle temporal properties) o Large area overhead in Emulation/FPGA prototype o Difficult to debug failed assertions DV write them based on functional spec <3>
4 White-box Assertions Capture RTL behaviors using internal signals o Low overhead in simulation runtime and emulation area o Reduce debug turn-around by pinpoint error source o Easier for formal tools to converge o Identify implementation specific assertions and coverage Issues o Require designer time and expertise o Need orthogonal perspective Which combination of signals to use? o Beyond functional specification assertions and coverage not conceived/missed by human Not enough whitebox assertions from designers <4>
5 Example Properties Master req rdy Memory Useless property: req -> ##1 busy (!req & rdy) -> ##1!busy Memory Controller Orthogonal White-box property: rdy -> busy If(req) busy <= 1 b1; else if(rdy) busy < = 1 b0; When rdy is asserted, in the same cycle, bus is always busy. That is, rdy must follows a req. Another orthogonal white-box property: req ->!busy When req is asserted, in the same cycle, bus is always non-busy. That is, new req is only asserted when rdy for previous req is asserted before. Blackbox property: $rose(req) ->!req throughout ##[1:$] rdy; <5>
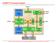
6 BugScope Assertion Synthesis Flow No Changes in Methodology Required <6>
7 BugScope Assertion Synthesis Use Model 1. Simulate using NextOp PLI o Input: Testbench + Test Vectors + RTL o Output: a Nextop database.ndb file for each simulation run 2. NextOp post processing o Input: Nextop databases + RTL o Output: Nextop properties Properties guaranteed to hold for the given tests A property is an assertion OR its negation is a coverage hole 3. Review/classify properties into assertions and coverages o SVA, PSL, Verilog and/or Synthesizable Verilog <7>
8 Key Features to Make Assertion Synthesis Useful Automated o discover properties not recognized by engineers High Quality of Results o 1%-10% of RTL lines o Don t duplicate RTL or other properties Efficient Assertions o Low runtime overhead for simulation o Low area overhead for emulation Capacity o Full chip assertion synthesis solution Seamless integration within existing flows <8>
9 Primary Use Models Coverage-driven simulation flow o Mainstream methodology Simulation + formal property checking flow o Advance corner-case bug-hunting methodology Emulation/Acceleration Flow o Enable trigger point to reduce debug turn-around Functional Review o Property classification using debugger drives functional review <9>
10 Coverage-Driven Simulation Flow Find design errors Prevent usage errors Coverage hole/bug Bug Simulate NextOp PLI Database NextOp Analysis Review Assertions Simulate/ FPGA/ Emulate IP Design/Verification Coverage holes detect TB issues Assertions catch RTL errors IP Users/Firmware/Software Ship RTL + Assertions as IPs to catch usage errors. <10>
11 Number of Properties Assertions & Coverage Over Verification Cycle [NVIDIA, DAC 10] Early Middle Late Verification Cycle #coverage #assertion Number of Simulation Runs <11>
12 Packet Processing Engine [DVCon 11] The packet processor includes ~30K lines of Verilog o The key filtering block includes 3K lines Total 2000 direct+random tests reaches 100% statement coverage and >95% conditional coverage packets pre_proc filtering lookup_table match_rule <12>
13 Properties on Filtering Block [DVCon 11] Using all 2000 tests, BugScope generates o 145 properties, average 5% of RTL lines o 43 cover properties and 102 assertions!(buffer_empty && filter_fifo_rd) No FIFO underflow {valid, sop}!=0 ->@pkt_length!= pkt_length Cell length cannot be 0 onehot0( {key_pkt, bypass_pkt, invalid_tag} ) mutual exclusive type!(eop && state == DATA1) A special size runt pkt is not tested!(multicast_pkt && cur_multicast_pkt) Need to test back-to-back multicast pkts <13>
14 Properties on Filtering Block [DVCon 11] Using all 2000 tests, BugScope generates o 145 properties, average 5% of RTL lines o 43 cover properties and 102 assertions assert!(buffer_empty && filter_fifo_rd) No FIFO underflow assert {valid, sop}!=0 ->@pkt_length!= pkt_length Cell length cannot be 0 assert onehot0( {key_pkt, bypass_pkt, invalid_tag} ) mutual exclusive type cover (eop && state == DATA1) cover (multicast_pkt && cur_multicast_pkt) A special size runt pkt is not tested Need to test back-toback multicast pkts <14>
15 Simulation + Formal Property Checking Create Properties Find corner case issues Proof Simulate NextOp PLI Database NextOp Analysis Properties Formal Property Checking Bug Cover patch Simulation Regression Formal/Semi-Formal Assertions and coverage goals created based on simulation Whitebox properties are more tractable for formal algorithms <15>
16 Example Customer Scenario A complex SOC with >10K tests o A semi-formal tool is used to drive stimulus o Designer wrote ~5 assertions, no bug found by formal engine o SOC is taped-out and used in field for a few years Properties based on direct and random simulation o RTL ~1.8K lines o BugScope reports 117 properties, including 2 manual assertions <2hrs and ~300MB memory Properties used as targets for semi-formal tool o 1 BugScope assertion is violated == ACCEPT o Bug happens when timer wraps around from 32 hffffffff to 32 h0 <16>
17 Bug Found by Property Bug was harder to find by other means o Difficult for simulation because it takes 4 billion cycles to wrap around o End-to-end properties written by engineers cannot be proven o Extremely difficult to write constraints for formal at module level o The bug degrades system performance Performance bug is hard to detect with black-box checkers Solution with BugScope Assertion Synthesis o Apply formal with large number of white-box properties o Apply formal at a higher level that includes > 20 modules White-box assertions allow formal to converge Easier to develop constraints at a higher level <17>
18 Emulation/Acceleration Flow Create Assertions and Coverage Detect Corner Case Bug Bug Simulate NextOp PLI Database NextOp Analysis Review Assertions FPGA/ Emulate Simulation based Verification WhiteBox Assertion as trigger condition or assertions to reduce debug turn-around time <18>
19 Example Customer Scenario Assertions synthesis debug Post-Silicon problem o A Complex Networking SoC hangs o Traffic pattern too complex to be reproduced in simulation o Emulation reproduces the hang but cannot be debugged Create properties based on random simulation o RTL ~2K lines with simulation tests o BugScope reports 300 properties Add assertions as trigger points in emulation o A NextOp assertion triggered o clear_cnt <= 19 Assertion pinpoints the RTL bug <19>
20 Functional Review Using Properties & Debugger Waveform Viewer Directly find bugs Review becomes more objective between design, architect and verification teams <20>
21 Functional Review Finding Implementation Bug clk..) begin if(load_cnt) cnt_incr <= 1 b1; else if(cnt == 71) cnt_incr <= 1 b0; if(cnt_incr) cnt <= cnt+1; else cnt <= 0; end BugScope property: cnt == d72 == d0; Whenever cnt is 72, in the next cycle, cnt is never 73. Two bugs founds: 1. The priority to load_cnt was incorrect. 2. The code to latch load_cnt when cnt == 71 was missing to handle the scenario correctly. <21>
22 Functional Review Finding Micro-architecture Bug The packet processing state machine included 4 states: IDLE-> RUN-> WAIT-> PAYLOAD. The signal start comes from another block, initiates the transaction, and could only be asserted at IDLE state according to the design assumption. BugScope property: start -> cur_state!= RUN Whenever start is asserted, cur state is never run. Designer was expecting a property, start -> cur_state == IDLE When waveform and code was traced using debugger, the team find out that in certain scenario, the next packet is initiated to transmit before previous packet is completely sent. This is indicated by start signal getting asserted in states other than IDLE. Bug : This may result into dropping the transactions and un-necessarily retried. <22>
23 Summary Assertion Synthesis Reduce verification resources o productivity gain : Hours vs minutes in creating assertions o Reduce verification schedule o Synthesized assertions to find bugs early, reduce debug time Find critical bugs o including post-silicon, post RTL freeze, IP integration Verification signoff o o <23>
Introduction to Functional Verification. Niels Burkhardt
 Introduction to Functional Verification Overview Verification issues Verification technologies Verification approaches Universal Verification Methodology Conclusion Functional Verification issues Hardware
Introduction to Functional Verification Overview Verification issues Verification technologies Verification approaches Universal Verification Methodology Conclusion Functional Verification issues Hardware
Digital Design Verification
 Digital Design Verification Course Instructor: Debdeep Mukhopadhyay Dept of Computer Sc. and Engg. Indian Institute of Technology Madras, Even Semester Course No: CS 676 1 Verification??? What is meant
Digital Design Verification Course Instructor: Debdeep Mukhopadhyay Dept of Computer Sc. and Engg. Indian Institute of Technology Madras, Even Semester Course No: CS 676 1 Verification??? What is meant
Chapter 13: Verification
 Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
Codesign: The World Of Practice
 Codesign: The World Of Practice D. Sreenivasa Rao Senior Manager, System Level Integration Group Analog Devices Inc. May 2007 Analog Devices Inc. ADI is focused on high-end signal processing chips and
Codesign: The World Of Practice D. Sreenivasa Rao Senior Manager, System Level Integration Group Analog Devices Inc. May 2007 Analog Devices Inc. ADI is focused on high-end signal processing chips and
BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH
 WHITE PAPER METRIC-DRIVEN VERIFICATION ENSURES SOFTWARE DEVELOPMENT QUALITY BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH INTRODUCTION The complexity of electronic systems is rapidly
WHITE PAPER METRIC-DRIVEN VERIFICATION ENSURES SOFTWARE DEVELOPMENT QUALITY BY STEVE BROWN, CADENCE DESIGN SYSTEMS AND MICHEL GENARD, VIRTUTECH INTRODUCTION The complexity of electronic systems is rapidly
Using SystemVerilog Assertions for Creating Property-Based Checkers
 Using SystemVerilog Assertions for Creating Property-Based Checkers Eduard Cerny Synopsys, Inc. Marlborough, USA [email protected] Dmitry Korchemny Intel Corp. Haifa, Israel [email protected]
Using SystemVerilog Assertions for Creating Property-Based Checkers Eduard Cerny Synopsys, Inc. Marlborough, USA [email protected] Dmitry Korchemny Intel Corp. Haifa, Israel [email protected]
Automating Root-Cause Analysis to Reduce Time to Find Bugs by Up to 50%
 Automating Root-Cause Analysis to Reduce Time to Find Bugs by Up to 50% By Kishore Karnane and Corey Goss, Cadence Design Systems If you re spending more than 50% of your verification effort in debug,
Automating Root-Cause Analysis to Reduce Time to Find Bugs by Up to 50% By Kishore Karnane and Corey Goss, Cadence Design Systems If you re spending more than 50% of your verification effort in debug,
What is LOG Storm and what is it useful for?
 What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
What is LOG Storm and what is it useful for? LOG Storm is a high-speed digital data logger used for recording and analyzing the activity from embedded electronic systems digital bus and data lines. It
Use, Analysis, and Debug of SystemVerilog Assertions
 Use, Analysis, and Debug of SystemVerilog Assertions Agenda Introduction Source Code Tracing Assertion Checking Analyzing and Debugging Waveform Active Annotation Property Result Table Standards: The Life
Use, Analysis, and Debug of SystemVerilog Assertions Agenda Introduction Source Code Tracing Assertion Checking Analyzing and Debugging Waveform Active Annotation Property Result Table Standards: The Life
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip
 Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
ESP-CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation
 Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Datasheet -CV Custom Design Formal Equivalence Checking Based on Symbolic Simulation Overview -CV is an equivalence checker for full custom designs. It enables efficient comparison of a reference design
Understanding DO-254 Compliance for the Verification of Airborne Digital Hardware
 White Paper Understanding DO-254 Compliance for the of Airborne Digital Hardware October 2009 Authors Dr. Paul Marriott XtremeEDA Corporation Anthony D. Stone Synopsys, Inc Abstract This whitepaper is
White Paper Understanding DO-254 Compliance for the of Airborne Digital Hardware October 2009 Authors Dr. Paul Marriott XtremeEDA Corporation Anthony D. Stone Synopsys, Inc Abstract This whitepaper is
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic
 Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
System-on. on-chip Design Flow. Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems. jouni.tomberg@tut.
 System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems [email protected] 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
ARM Webinar series. ARM Based SoC. Abey Thomas
 ARM Webinar series ARM Based SoC Verification Abey Thomas Agenda About ARM and ARM IP ARM based SoC Verification challenges Verification planning and strategy IP Connectivity verification Performance verification
ARM Webinar series ARM Based SoC Verification Abey Thomas Agenda About ARM and ARM IP ARM based SoC Verification challenges Verification planning and strategy IP Connectivity verification Performance verification
Hunting Asynchronous CDC Violations in the Wild
 Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
find model parameters, to validate models, and to develop inputs for models. c 1994 Raj Jain 7.1
 Monitors Monitor: A tool used to observe the activities on a system. Usage: A system programmer may use a monitor to improve software performance. Find frequently used segments of the software. A systems
Monitors Monitor: A tool used to observe the activities on a system. Usage: A system programmer may use a monitor to improve software performance. Find frequently used segments of the software. A systems
Architectures and Platforms
 Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Model Checking based Software Verification
 Model Checking based Software Verification 18.5-2006 Keijo Heljanko [email protected] Department of Computer Science and Engineering Helsinki University of Technology http://www.tcs.tkk.fi/~kepa/ 1/24
Model Checking based Software Verification 18.5-2006 Keijo Heljanko [email protected] Department of Computer Science and Engineering Helsinki University of Technology http://www.tcs.tkk.fi/~kepa/ 1/24
VHDL GUIDELINES FOR SYNTHESIS
 VHDL GUIDELINES FOR SYNTHESIS Claudio Talarico For internal use only 1/19 BASICS VHDL VHDL (Very high speed integrated circuit Hardware Description Language) is a hardware description language that allows
VHDL GUIDELINES FOR SYNTHESIS Claudio Talarico For internal use only 1/19 BASICS VHDL VHDL (Very high speed integrated circuit Hardware Description Language) is a hardware description language that allows
Chapter 7 outline. 7.5 providing multiple classes of service 7.6 providing QoS guarantees RTP, RTCP, SIP. 7: Multimedia Networking 7-71
 Chapter 7 outline 7.1 multimedia networking applications 7.2 streaming stored audio and video 7.3 making the best out of best effort service 7.4 protocols for real-time interactive applications RTP, RTCP,
Chapter 7 outline 7.1 multimedia networking applications 7.2 streaming stored audio and video 7.3 making the best out of best effort service 7.4 protocols for real-time interactive applications RTP, RTCP,
A Verilog HDL Test Bench Primer Application Note
 A Verilog HDL Test Bench Primer Application Note Table of Contents Introduction...1 Overview...1 The Device Under Test (D.U.T.)...1 The Test Bench...1 Instantiations...2 Figure 1- DUT Instantiation...2
A Verilog HDL Test Bench Primer Application Note Table of Contents Introduction...1 Overview...1 The Device Under Test (D.U.T.)...1 The Test Bench...1 Instantiations...2 Figure 1- DUT Instantiation...2
SVA4T: SystemVerilog Assertions - Techniques, Tips, Tricks, and Traps
 SVA4T: SystemVerilog Assertions - Wolfgang Ecker, Volkan Esen, Thomas Kruse, Thomas Steininger Infineon Technologies Peter Jensen Syosil Consulting Abstract ABV (Assertion Based Verification) is a very
SVA4T: SystemVerilog Assertions - Wolfgang Ecker, Volkan Esen, Thomas Kruse, Thomas Steininger Infineon Technologies Peter Jensen Syosil Consulting Abstract ABV (Assertion Based Verification) is a very
Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor
 Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor A Starter Guide Joseph Yiu November 2014 version 1.02 27 Nov 2014 1 - Background Since the ARM Cortex -M0 Processor was released a few years
Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor A Starter Guide Joseph Yiu November 2014 version 1.02 27 Nov 2014 1 - Background Since the ARM Cortex -M0 Processor was released a few years
Lab #5: Design Example: Keypad Scanner and Encoder - Part 1 (120 pts)
 Dr. Greg Tumbush, [email protected] Lab #5: Design Example: Keypad Scanner and Encoder - Part 1 (120 pts) Objective The objective of lab assignments 5 through 9 are to systematically design and implement
Dr. Greg Tumbush, [email protected] Lab #5: Design Example: Keypad Scanner and Encoder - Part 1 (120 pts) Objective The objective of lab assignments 5 through 9 are to systematically design and implement
FPGA-Centric Functional Verification
 FPGA-Centric Functional Verification Mark Litterick Senior Consultant, Verilab Ltd. Scotland & Ireland Designers Forum 2002 Presentation Outline Complex FPGA verification problem Propose a practical solution
FPGA-Centric Functional Verification Mark Litterick Senior Consultant, Verilab Ltd. Scotland & Ireland Designers Forum 2002 Presentation Outline Complex FPGA verification problem Propose a practical solution
Testing & Verification of Digital Circuits ECE/CS 5745/6745. Hardware Verification using Symbolic Computation
 Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla ([email protected]) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla ([email protected]) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
ISTQB Certified Tester. Foundation Level. Sample Exam 1
 ISTQB Certified Tester Foundation Level Version 2015 American Copyright Notice This document may be copied in its entirety, or extracts made, if the source is acknowledged. #1 When test cases are designed
ISTQB Certified Tester Foundation Level Version 2015 American Copyright Notice This document may be copied in its entirety, or extracts made, if the source is acknowledged. #1 When test cases are designed
JOURNAL OF OBJECT TECHNOLOGY
 JOURNAL OF OBJECT TECHNOLOGY Online at http://www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2006 Vol. 5, No. 6, July - August 2006 On Assuring Software Quality and Curbing Software
JOURNAL OF OBJECT TECHNOLOGY Online at http://www.jot.fm. Published by ETH Zurich, Chair of Software Engineering JOT, 2006 Vol. 5, No. 6, July - August 2006 On Assuring Software Quality and Curbing Software
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
AMS Verification at SoC Level: A practical approach for using VAMS vs SPICE views
 AMS Verification at SoC Level: A practical approach for using VAMS vs SPICE views Nitin Pant, Gautham Harinarayan, Manmohan Rana Accellera Systems Initiative 1 Agenda Need for SoC AMS Verification Mixed
AMS Verification at SoC Level: A practical approach for using VAMS vs SPICE views Nitin Pant, Gautham Harinarayan, Manmohan Rana Accellera Systems Initiative 1 Agenda Need for SoC AMS Verification Mixed
CSE467: Project Phase 1 - Building the Framebuffer, Z-buffer, and Display Interfaces
 CSE467: Project Phase 1 - Building the Framebuffer, Z-buffer, and Display Interfaces Vincent Lee, Mark Wyse, Mark Oskin Winter 2015 Design Doc Due Saturday Jan. 24 @ 11:59pm Design Review Due Tuesday Jan.
CSE467: Project Phase 1 - Building the Framebuffer, Z-buffer, and Display Interfaces Vincent Lee, Mark Wyse, Mark Oskin Winter 2015 Design Doc Due Saturday Jan. 24 @ 11:59pm Design Review Due Tuesday Jan.
AXI Performance Monitor v5.0
 AXI Performance Monitor v5.0 LogiCORE IP Product Guide Vivado Design Suite Table of Contents IP Facts Chapter 1: Overview Advanced Mode...................................................................
AXI Performance Monitor v5.0 LogiCORE IP Product Guide Vivado Design Suite Table of Contents IP Facts Chapter 1: Overview Advanced Mode...................................................................
A low-cost, connection aware, load-balancing solution for distributing Gigabit Ethernet traffic between two intrusion detection systems
 Iowa State University Digital Repository @ Iowa State University Graduate Theses and Dissertations Graduate College 2010 A low-cost, connection aware, load-balancing solution for distributing Gigabit Ethernet
Iowa State University Digital Repository @ Iowa State University Graduate Theses and Dissertations Graduate College 2010 A low-cost, connection aware, load-balancing solution for distributing Gigabit Ethernet
Life Cycle of a Memory Request. Ring Example: 2 requests for lock 17
 Life Cycle of a Memory Request (1) Use AQR or AQW to place address in AQ (2) If A[31]==0, check for hit in DCache Ring (3) Read Hit: place cache word in RQ; Write Hit: replace cache word with WQ RDDest/RDreturn
Life Cycle of a Memory Request (1) Use AQR or AQW to place address in AQ (2) If A[31]==0, check for hit in DCache Ring (3) Read Hit: place cache word in RQ; Write Hit: replace cache word with WQ RDDest/RDreturn
Software Tracing of Embedded Linux Systems using LTTng and Tracealyzer. Dr. Johan Kraft, Percepio AB
 Software Tracing of Embedded Linux Systems using LTTng and Tracealyzer Dr. Johan Kraft, Percepio AB Debugging embedded software can be a challenging, time-consuming and unpredictable factor in development
Software Tracing of Embedded Linux Systems using LTTng and Tracealyzer Dr. Johan Kraft, Percepio AB Debugging embedded software can be a challenging, time-consuming and unpredictable factor in development
Implementation Details
 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
SDLC Controller. Documentation. Design File Formats. Verification
 January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: [email protected] URL: www.cast-inc.com Features AllianceCORE
January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: [email protected] URL: www.cast-inc.com Features AllianceCORE
10 Gigabit Ethernet MAC Core for Altera CPLDs. 1 Introduction. Product Brief Version 1.4 - February 2002
 1 Introduction Initially, network managers use 10 Gigabit Ethernet to provide high-speed, local backbone interconnection between large-capacity switches. 10 Gigabit Ethernet enables Internet Service Providers
1 Introduction Initially, network managers use 10 Gigabit Ethernet to provide high-speed, local backbone interconnection between large-capacity switches. 10 Gigabit Ethernet enables Internet Service Providers
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Requirements-driven Verification Methodology for Standards Compliance
 Requirements-driven Verification Methodology for Standards Compliance Serrie-justine Chapman (TVS) [email protected] Mike Bartley (TVS) [email protected] Darren Galpin (Infineon)
Requirements-driven Verification Methodology for Standards Compliance Serrie-justine Chapman (TVS) [email protected] Mike Bartley (TVS) [email protected] Darren Galpin (Infineon)
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler
 ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
Using a Generic Plug and Play Performance Monitor for SoC Verification
 Using a Generic Plug and Play Performance Monitor for SoC Verification Dr. Ambar Sarkar Kaushal Modi Janak Patel Bhavin Patel Ajay Tiwari Accellera Systems Initiative 1 Agenda Introduction Challenges Why
Using a Generic Plug and Play Performance Monitor for SoC Verification Dr. Ambar Sarkar Kaushal Modi Janak Patel Bhavin Patel Ajay Tiwari Accellera Systems Initiative 1 Agenda Introduction Challenges Why
Verification. Formal. OneSpin 360 LaunchPad Adaptive Formal Platform. www.onespin-solutions.com May 2015
 Formal Verification OneSpin 360 LaunchPad Adaptive Formal Platform www.onespin-solutions.com May 2015 Copyright OneSpin Solutions 2015 Slide 2 Automated Apps: Enabling Mainstream Formal Verification Apps
Formal Verification OneSpin 360 LaunchPad Adaptive Formal Platform www.onespin-solutions.com May 2015 Copyright OneSpin Solutions 2015 Slide 2 Automated Apps: Enabling Mainstream Formal Verification Apps
SystemVerilog Is Getting Even Better!
 by, SystemVerilog Is Getting Even Better! An Update on the Proposed 2009 SystemVerilog Standard Part 2 presented by Clifford E. Cummings Sunburst Design, Inc. [email protected] www.sunburst-design.com
by, SystemVerilog Is Getting Even Better! An Update on the Proposed 2009 SystemVerilog Standard Part 2 presented by Clifford E. Cummings Sunburst Design, Inc. [email protected] www.sunburst-design.com
White Paper. S2C Inc. 1735 Technology Drive, Suite 620 San Jose, CA 95110, USA Tel: +1 408 213 8818 Fax: +1 408 213 8821 www.s2cinc.com.
 White Paper FPGA Prototyping of System-on-Chip Designs The Need for a Complete Prototyping Platform for Any Design Size, Any Design Stage with Enterprise-Wide Access, Anytime, Anywhere S2C Inc. 1735 Technology
White Paper FPGA Prototyping of System-on-Chip Designs The Need for a Complete Prototyping Platform for Any Design Size, Any Design Stage with Enterprise-Wide Access, Anytime, Anywhere S2C Inc. 1735 Technology
Low Cost System on Chip Design for Audio Processing
 Low Cost System on Chip Design for udio Processing 1 yas Kanta Swain, 2 Kamala Kanta Mahapatra bstract System-on-Chip (SoC) design is an integration of multi million transistors in a single chip for alleviating
Low Cost System on Chip Design for udio Processing 1 yas Kanta Swain, 2 Kamala Kanta Mahapatra bstract System-on-Chip (SoC) design is an integration of multi million transistors in a single chip for alleviating
RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition
 RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition A Tutorial Approach James O. Hamblen Georgia Institute of Technology Michael D. Furman Georgia Institute of Technology KLUWER ACADEMIC PUBLISHERS Boston
RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition A Tutorial Approach James O. Hamblen Georgia Institute of Technology Michael D. Furman Georgia Institute of Technology KLUWER ACADEMIC PUBLISHERS Boston
Best Practises for LabVIEW FPGA Design Flow. uk.ni.com ireland.ni.com
 Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
10/100/1000Mbps Ethernet MAC with Protocol Acceleration MAC-NET Core with Avalon Interface
 1 Introduction Ethernet is available in different speeds (10/100/1000 and 10000Mbps) and provides connectivity to meet a wide range of needs from desktop to switches. MorethanIP IP solutions provide a
1 Introduction Ethernet is available in different speeds (10/100/1000 and 10000Mbps) and provides connectivity to meet a wide range of needs from desktop to switches. MorethanIP IP solutions provide a
10/100/1000 Ethernet MAC with Protocol Acceleration MAC-NET Core
 1 Introduction The implements, in conjunction with a triple speed 10/100/1000 MAC, Layer 3 network acceleration functions, which are designed to accelerate the processing of various common networking protocols
1 Introduction The implements, in conjunction with a triple speed 10/100/1000 MAC, Layer 3 network acceleration functions, which are designed to accelerate the processing of various common networking protocols
USB Test Environment ATUSBTEST- SS7400. Summary
 Features Simple Command-driven Host Model Comprehensive Reports by Monitor Protocol Validation by Monitor Comprehensive Test Suite Fully Compliant with USB Forum Checklist Generates and Monitors Packets
Features Simple Command-driven Host Model Comprehensive Reports by Monitor Protocol Validation by Monitor Comprehensive Test Suite Fully Compliant with USB Forum Checklist Generates and Monitors Packets
Specification and Analysis of Contracts Lecture 1 Introduction
 Specification and Analysis of Contracts Lecture 1 Introduction Gerardo Schneider [email protected] http://folk.uio.no/gerardo/ Department of Informatics, University of Oslo SEFM School, Oct. 27 - Nov.
Specification and Analysis of Contracts Lecture 1 Introduction Gerardo Schneider [email protected] http://folk.uio.no/gerardo/ Department of Informatics, University of Oslo SEFM School, Oct. 27 - Nov.
Mobile Performance Testing Approaches and Challenges
 NOUS INFOSYSTEMS LEVERAGING INTELLECT Mobile Performance Testing Approaches and Challenges ABSTRACT Mobile devices are playing a key role in daily business functions as mobile devices are adopted by most
NOUS INFOSYSTEMS LEVERAGING INTELLECT Mobile Performance Testing Approaches and Challenges ABSTRACT Mobile devices are playing a key role in daily business functions as mobile devices are adopted by most
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Introduction to Automated Testing
 Introduction to Automated Testing What is Software testing? Examination of a software unit, several integrated software units or an entire software package by running it. execution based on test cases
Introduction to Automated Testing What is Software testing? Examination of a software unit, several integrated software units or an entire software package by running it. execution based on test cases
Registers & Counters
 Objectives This section deals with some simple and useful sequential circuits. Its objectives are to: Introduce registers as multi-bit storage devices. Introduce counters by adding logic to registers implementing
Objectives This section deals with some simple and useful sequential circuits. Its objectives are to: Introduce registers as multi-bit storage devices. Introduce counters by adding logic to registers implementing
Lecture Outline Overview of real-time scheduling algorithms Outline relative strengths, weaknesses
 Overview of Real-Time Scheduling Embedded Real-Time Software Lecture 3 Lecture Outline Overview of real-time scheduling algorithms Clock-driven Weighted round-robin Priority-driven Dynamic vs. static Deadline
Overview of Real-Time Scheduling Embedded Real-Time Software Lecture 3 Lecture Outline Overview of real-time scheduling algorithms Clock-driven Weighted round-robin Priority-driven Dynamic vs. static Deadline
VERIFICATION TECHNOLOGIES
 CHAPTER 2 VERIFICATION TECHNOLOGIES As mentioned in the previous chapter, one of the mechanisms that can be used to improve the efficiency and reliability of a process is automation. This chapter covers
CHAPTER 2 VERIFICATION TECHNOLOGIES As mentioned in the previous chapter, one of the mechanisms that can be used to improve the efficiency and reliability of a process is automation. This chapter covers
Below is a diagram explaining the data packet and the timing related to the mouse clock while receiving a byte from the PS-2 mouse:
 PS-2 Mouse: The Protocol: For out mini project we designed a serial port transmitter receiver, which uses the Baud rate protocol. The PS-2 port is similar to the serial port (performs the function of transmitting
PS-2 Mouse: The Protocol: For out mini project we designed a serial port transmitter receiver, which uses the Baud rate protocol. The PS-2 port is similar to the serial port (performs the function of transmitting
More Verilog. 8-bit Register with Synchronous Reset. Shift Register Example. N-bit Register with Asynchronous Reset.
 More Verilog 8-bit Register with Synchronous Reset module reg8 (reset, CLK, D, Q); input reset; input [7:0] D; output [7:0] Q; reg [7:0] Q; if (reset) Q = 0; else Q = D; module // reg8 Verilog - 1 Verilog
More Verilog 8-bit Register with Synchronous Reset module reg8 (reset, CLK, D, Q); input reset; input [7:0] D; output [7:0] Q; reg [7:0] Q; if (reset) Q = 0; else Q = D; module // reg8 Verilog - 1 Verilog
8-ch RAID0 Design by using SATA Host IP Manual Rev1.0 9-Jun-15
 8-ch RAID0 Design by using SATA Host IP Manual Rev1.0 9-Jun-15 1 Overview RAID0 system uses multiple storages to extend total storage capacity and increase write/read performance to be N times. Assumed
8-ch RAID0 Design by using SATA Host IP Manual Rev1.0 9-Jun-15 1 Overview RAID0 system uses multiple storages to extend total storage capacity and increase write/read performance to be N times. Assumed
Secure Software Programming and Vulnerability Analysis
 Secure Software Programming and Vulnerability Analysis Christopher Kruegel [email protected] http://www.auto.tuwien.ac.at/~chris Testing and Source Code Auditing Secure Software Programming 2 Overview
Secure Software Programming and Vulnerability Analysis Christopher Kruegel [email protected] http://www.auto.tuwien.ac.at/~chris Testing and Source Code Auditing Secure Software Programming 2 Overview
Efficient Project Management and Verification Sign-off Using Questa Verification Management
 Efficient Project Management and Verification Sign-off Using Questa Verification Management by Suresh Babu P., Chakravarthi M.G., Test and Verification Solutions India Pvt. Ltd. ABSTRACT Test and Verification
Efficient Project Management and Verification Sign-off Using Questa Verification Management by Suresh Babu P., Chakravarthi M.G., Test and Verification Solutions India Pvt. Ltd. ABSTRACT Test and Verification
A Methodology and the Tool for Testing SpaceWire Routing Switches Session: SpaceWire test and verification
 A Methodology and the Tool for Testing SpaceWire Routing Switches Session: SpaceWire test and verification Elena Suvorova Saint-Petersburg University of Aerospace Instrumentation. 67, B. Morskaya, Saint-
A Methodology and the Tool for Testing SpaceWire Routing Switches Session: SpaceWire test and verification Elena Suvorova Saint-Petersburg University of Aerospace Instrumentation. 67, B. Morskaya, Saint-
Hybrid Platform Application in Software Debug
 Hybrid Platform Application in Software Debug Jiao Feng July 15 2015.7.15 Software costs in SoC development 2 Early software adoption Previous Development Process IC Development RTL Design Physical Design
Hybrid Platform Application in Software Debug Jiao Feng July 15 2015.7.15 Software costs in SoC development 2 Early software adoption Previous Development Process IC Development RTL Design Physical Design
FPGA Prototyping Primer
 FPGA Prototyping Primer S2C Inc. 1735 Technology Drive, Suite 620 San Jose, CA 95110, USA Tel: +1 408 213 8818 Fax: +1 408 213 8821 www.s2cinc.com What is FPGA prototyping? FPGA prototyping is the methodology
FPGA Prototyping Primer S2C Inc. 1735 Technology Drive, Suite 620 San Jose, CA 95110, USA Tel: +1 408 213 8818 Fax: +1 408 213 8821 www.s2cinc.com What is FPGA prototyping? FPGA prototyping is the methodology
Finite State Machine Design and VHDL Coding Techniques
 Finite State Machine Design and VHDL Coding Techniques Iuliana CHIUCHISAN, Alin Dan POTORAC, Adrian GRAUR "Stefan cel Mare" University of Suceava str.universitatii nr.13, RO-720229 Suceava [email protected],
Finite State Machine Design and VHDL Coding Techniques Iuliana CHIUCHISAN, Alin Dan POTORAC, Adrian GRAUR "Stefan cel Mare" University of Suceava str.universitatii nr.13, RO-720229 Suceava [email protected],
Modeling Registers and Counters
 Lab Workbook Introduction When several flip-flops are grouped together, with a common clock, to hold related information the resulting circuit is called a register. Just like flip-flops, registers may
Lab Workbook Introduction When several flip-flops are grouped together, with a common clock, to hold related information the resulting circuit is called a register. Just like flip-flops, registers may
Whitepaper Performance Testing and Monitoring of Mobile Applications
 M eux Test Whitepaper Performance Testing and Monitoring of Mobile Applications Abstract The testing of a mobile application does not stop when the application passes all functional tests. Testing the
M eux Test Whitepaper Performance Testing and Monitoring of Mobile Applications Abstract The testing of a mobile application does not stop when the application passes all functional tests. Testing the
Intrusion Detection System
 Intrusion Detection System Time Machine Dynamic Application Detection 1 NIDS: two generic problems Attack identified But what happened in the past??? Application identification Only by port number! Yet
Intrusion Detection System Time Machine Dynamic Application Detection 1 NIDS: two generic problems Attack identified But what happened in the past??? Application identification Only by port number! Yet
10-/100-Mbps Ethernet Media Access Controller (MAC) Core
 10-/100-Mbps Ethernet Media Access Controller (MAC) Core Preliminary Product Brief December 1998 Description The Ethernet Media Access Controller (MAC) core is a high-performance core with a low gate count,
10-/100-Mbps Ethernet Media Access Controller (MAC) Core Preliminary Product Brief December 1998 Description The Ethernet Media Access Controller (MAC) core is a high-performance core with a low gate count,
LogiCORE IP AXI Performance Monitor v2.00.a
 LogiCORE IP AXI Performance Monitor v2.00.a Product Guide Table of Contents IP Facts Chapter 1: Overview Target Technology................................................................. 9 Applications......................................................................
LogiCORE IP AXI Performance Monitor v2.00.a Product Guide Table of Contents IP Facts Chapter 1: Overview Target Technology................................................................. 9 Applications......................................................................
Rapid System Prototyping with FPGAs
 Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Random Testing: The Best Coverage Technique - An Empirical Proof
 , pp. 115-122 http://dx.doi.org/10.14257/ijseia.2015.9.12.10 Random Testing: The Best Coverage Technique - An Empirical Proof K Koteswara Rao 1 and Prof GSVP Raju 2 1 Asst prof, (PhD) @JNTUK, CSE Department,
, pp. 115-122 http://dx.doi.org/10.14257/ijseia.2015.9.12.10 Random Testing: The Best Coverage Technique - An Empirical Proof K Koteswara Rao 1 and Prof GSVP Raju 2 1 Asst prof, (PhD) @JNTUK, CSE Department,
Extending the Power of FPGAs. Salil Raje, Xilinx
 Extending the Power of FPGAs Salil Raje, Xilinx Extending the Power of FPGAs The Journey has Begun Salil Raje Xilinx Corporate Vice President Software and IP Products Development Agenda The Evolution of
Extending the Power of FPGAs Salil Raje, Xilinx Extending the Power of FPGAs The Journey has Begun Salil Raje Xilinx Corporate Vice President Software and IP Products Development Agenda The Evolution of
Asynchronous Bypass Channels
 Asynchronous Bypass Channels Improving Performance for Multi-Synchronous NoCs T. Jain, P. Gratz, A. Sprintson, G. Choi, Department of Electrical and Computer Engineering, Texas A&M University, USA Table
Asynchronous Bypass Channels Improving Performance for Multi-Synchronous NoCs T. Jain, P. Gratz, A. Sprintson, G. Choi, Department of Electrical and Computer Engineering, Texas A&M University, USA Table
System on Chip Platform Based on OpenCores for Telecommunication Applications
 System on Chip Platform Based on OpenCores for Telecommunication Applications N. Izeboudjen, K. Kaci, S. Titri, L. Sahli, D. Lazib, F. Louiz, M. Bengherabi, *N. Idirene Centre de Développement des Technologies
System on Chip Platform Based on OpenCores for Telecommunication Applications N. Izeboudjen, K. Kaci, S. Titri, L. Sahli, D. Lazib, F. Louiz, M. Bengherabi, *N. Idirene Centre de Développement des Technologies
Eingebettete Systeme. 4: Entwurfsmethodik, HW/SW Co-Design. Technische Informatik T T T
 Eingebettete Systeme 4: Entwurfsmethodik, HW/SW Co-Design echnische Informatik System Level Design: ools and Flow Refinement of HW/SW Systems ools for HW/SW Co-Design C-based design of HW/SW Systems echnische
Eingebettete Systeme 4: Entwurfsmethodik, HW/SW Co-Design echnische Informatik System Level Design: ools and Flow Refinement of HW/SW Systems ools for HW/SW Co-Design C-based design of HW/SW Systems echnische
The V-model. Validation and Verification. Inspections [24.3] Testing overview [8, 15.2] - system testing. How much V&V is enough?
![The V-model. Validation and Verification. Inspections [24.3] Testing overview [8, 15.2] - system testing. How much V&V is enough? The V-model. Validation and Verification. Inspections [24.3] Testing overview [8, 15.2] - system testing. How much V&V is enough?](/thumbs/26/9053796.jpg) Validation and Verification Inspections [24.3] Testing overview [8, 15.2] - system testing Requirements Design The V-model V & V Plans Implementation Unit tests System tests Integration tests Operation,
Validation and Verification Inspections [24.3] Testing overview [8, 15.2] - system testing Requirements Design The V-model V & V Plans Implementation Unit tests System tests Integration tests Operation,
Applications of Machine Learning in Software Testing. Lionel C. Briand Simula Research Laboratory and University of Oslo
 Applications of Machine Learning in Software Testing Lionel C. Briand Simula Research Laboratory and University of Oslo Acknowledgments Yvan labiche Xutao Liu Zaheer Bawar Kambiz Frounchi March 2008 2
Applications of Machine Learning in Software Testing Lionel C. Briand Simula Research Laboratory and University of Oslo Acknowledgments Yvan labiche Xutao Liu Zaheer Bawar Kambiz Frounchi March 2008 2
Putting it on the NIC: A Case Study on application offloading to a Network Interface Card (NIC)
 This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE CCNC 2006 proceedings. Putting it on the NIC: A Case Study on application
This full text paper was peer reviewed at the direction of IEEE Communications Society subject matter experts for publication in the IEEE CCNC 2006 proceedings. Putting it on the NIC: A Case Study on application
Design by Contract beyond class modelling
 Design by Contract beyond class modelling Introduction Design by Contract (DbC) or Programming by Contract is an approach to designing software. It says that designers should define precise and verifiable
Design by Contract beyond class modelling Introduction Design by Contract (DbC) or Programming by Contract is an approach to designing software. It says that designers should define precise and verifiable
CoreSight SoC enabling efficient design of custom debug and trace subsystems for complex SoCs
 CoreSight SoC enabling efficient design of custom debug and trace subsystems for complex SoCs Key steps to create a debug and trace solution for an ARM SoC Mayank Sharma, Technical Marketing Engineer,
CoreSight SoC enabling efficient design of custom debug and trace subsystems for complex SoCs Key steps to create a debug and trace solution for an ARM SoC Mayank Sharma, Technical Marketing Engineer,
Introducing Performance Engineering by means of Tools and Practical Exercises
 Introducing Performance Engineering by means of Tools and Practical Exercises Alexander Ufimtsev, Trevor Parsons, Lucian M. Patcas, John Murphy and Liam Murphy Performance Engineering Laboratory, School
Introducing Performance Engineering by means of Tools and Practical Exercises Alexander Ufimtsev, Trevor Parsons, Lucian M. Patcas, John Murphy and Liam Murphy Performance Engineering Laboratory, School
SYSTEMVERILOG ASSERTIONS FOR FORMAL VERIFICATION
 SYSTEMVERILOG ASSERTIONS FOR FORMAL VERIFICATION Dmitry Korchemny, Intel Corp. HVC2013, November 4, 2013, Haifa November 4, 2013 HVC2013 2 Most of the examples used in this tutorial are borrowed from our
SYSTEMVERILOG ASSERTIONS FOR FORMAL VERIFICATION Dmitry Korchemny, Intel Corp. HVC2013, November 4, 2013, Haifa November 4, 2013 HVC2013 2 Most of the examples used in this tutorial are borrowed from our
Integrated Error-Detection Techniques: Find More Bugs in Java Applications
 Integrated Error-Detection Techniques: Find More Bugs in Java Applications Software verification techniques such as pattern-based static code analysis, runtime error detection, unit testing, and flow analysis
Integrated Error-Detection Techniques: Find More Bugs in Java Applications Software verification techniques such as pattern-based static code analysis, runtime error detection, unit testing, and flow analysis
Getting the Most Out of Synthesis
 Outline Getting the Most Out of Synthesis Dr. Paul D. Franzon 1. Timing Optimization Approaches 2. Area Optimization Approaches 3. Design Partitioning References 1. Smith and Franzon, Chapter 11 2. D.Smith,
Outline Getting the Most Out of Synthesis Dr. Paul D. Franzon 1. Timing Optimization Approaches 2. Area Optimization Approaches 3. Design Partitioning References 1. Smith and Franzon, Chapter 11 2. D.Smith,
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Network Traffic Monitoring an architecture using associative processing.
 Network Traffic Monitoring an architecture using associative processing. Gerald Tripp Technical Report: 7-99 Computing Laboratory, University of Kent 1 st September 1999 Abstract This paper investigates
Network Traffic Monitoring an architecture using associative processing. Gerald Tripp Technical Report: 7-99 Computing Laboratory, University of Kent 1 st September 1999 Abstract This paper investigates
Fault-Tolerant Framework for Load Balancing System
 Fault-Tolerant Framework for Load Balancing System Y. K. LIU, L.M. CHENG, L.L.CHENG Department of Electronic Engineering City University of Hong Kong Tat Chee Avenue, Kowloon, Hong Kong SAR HONG KONG Abstract:
Fault-Tolerant Framework for Load Balancing System Y. K. LIU, L.M. CHENG, L.L.CHENG Department of Electronic Engineering City University of Hong Kong Tat Chee Avenue, Kowloon, Hong Kong SAR HONG KONG Abstract:
CONSTRAINT RANDOM VERIFICATION OF NETWORK ROUTER FOR SYSTEM ON CHIP APPLICATION
 CONSTRAINT RANDOM VERIFICATION OF NETWORK ROUTER FOR SYSTEM ON CHIP APPLICATION T.S Ghouse Basha 1, P. Santhamma 2, S. Santhi 3 1 Associate Professor & Head, Department Electronic & Communication Engineering,
CONSTRAINT RANDOM VERIFICATION OF NETWORK ROUTER FOR SYSTEM ON CHIP APPLICATION T.S Ghouse Basha 1, P. Santhamma 2, S. Santhi 3 1 Associate Professor & Head, Department Electronic & Communication Engineering,
Best Practices for Verification, Validation, and Test in Model- Based Design
 2008-01-1469 Best Practices for Verification, Validation, and in Model- Based Design Copyright 2008 The MathWorks, Inc. Brett Murphy, Amory Wakefield, and Jon Friedman The MathWorks, Inc. ABSTRACT Model-Based
2008-01-1469 Best Practices for Verification, Validation, and in Model- Based Design Copyright 2008 The MathWorks, Inc. Brett Murphy, Amory Wakefield, and Jon Friedman The MathWorks, Inc. ABSTRACT Model-Based
Electronic system-level development: Finding the right mix of solutions for the right mix of engineers.
 Electronic system-level development: Finding the right mix of solutions for the right mix of engineers. Nowadays, System Engineers are placed in the centre of two antagonist flows: microelectronic systems
Electronic system-level development: Finding the right mix of solutions for the right mix of engineers. Nowadays, System Engineers are placed in the centre of two antagonist flows: microelectronic systems
