Enabling Security in ProASIC 3 FPGAs with Hardware and Software Features
|
|
|
- Abigayle Singleton
- 8 years ago
- Views:
Transcription
1 Enabling Security in ProASIC 3 FPGAs with Hardware and Software Features Hans Schmitz Area Technical Manager / Field Applications Engineer September 2, 2009
2 Abstract Two types of security features available in Actel s ProASIC3 family for applications requiring security Hardware security features Software security features Hardware security features exist in the ProASIC3 FPGA fabric Hardware security features are selectable in Actel s Libero Integrated Design Environment (IDE) software Software security features exist in Libero IDE Design examples will illustrate how these features work Actel Corporation May be published with permission by MAPLD
3 What is Security? Security is defined in various ways, and Actel supports various methods of security Hardware Single-chip component, with no bitstream susceptible to interception during power-up Inability to read the data out of the device (this is good) Encrypted programming file (AES128) FlashLock security key (128-bit key) Software Placement and routing constraints Block methodology Actel Corporation May be published with permission by MAPLD
4 Hardware Security Description FlashLock Key None No security key selected FlashLock A key locks the array from being erased, programmed or verified Individual security settings for logic array and FlashROM Permanent lock Permanently lock the array from being erased, programmed or verified Permanently lock the FROM from being erased/written or read (verify always allowed) STAPL File FlashLock Key AES Key AES Decryption Core MAC Security Header AES encryption AES128 encryption protects programming data for file transfer into device FPGA Array FROM ProASIC3/E Device Actel Corporation May be published with permission by MAPLD
5 Hardware Security: Value to User A3P/E FlashLock FlashLock Key 128 bits Years to Uncover Key 1 5.4x10 23 Permanent FlashLock AES Encryption on Programming File AES Key 128 bits Years to Uncover Key 149 trillion 2 Permanent Lock Individual Security Settings 1 - Based on maximum JTAG clock frequency 20MHz 2 - Using a computing system that could recover a DES key in one second (DES standard has a 56- bit key size) [National Institute of Standards and Technology, ADVANCED ENCRYPTION STANDARD (AES) Questions and Answers, 28 January 2002, Actel Corporation May be published with permission by MAPLD
6 Software Security Physical design constraints Preserve block routing, prevent routing conflicts Floorplanning design with multiple blocks Moving routed block or cross family/die block instantiation Multiple block instantiation Isolation and security applications Secure boundaries/fences Secure inter-block connections Applications examples Redundant type 1 encryptions Red and black data resident Multiple independent levels of security on a single chip Control routing Timing or congestion issues Actel Corporation May be published with permission by MAPLD
7 Software Security: Region Definitions Region constraint: a rectilinear area with assigned macros 3 types: inclusive, exclusive or empty Such region divides all nets into Internal net all pins belong to the region External net no pin belongs to the region Interface net has pins inside and outside of the region Such region divides all routing resources into Internal resource all switches belong to the region External resource no switch belongs to the region Interface resource has switches inside and outside of the region Actel Corporation May be published with permission by MAPLD
8 Software Security: Routing Definitions An inclusive routing region is an inclusive placement region along with the following additional constraints All internal nets must use only internal routing resources All other nets can be routed anywhere An exclusive routing region is an exclusive placement region along with the following additional constraints All internal nets must use only internal routing resources All external nets must use only external resources Interface nets can be routed anywhere They will cross region boundaries Globals, quadrant clocks and local clocks are excluded An empty routing region is an empty placement region along with the following additional constraints All nets must use only external resources Globals, quadrant clocks and local clocks are excluded Actel Corporation May be published with permission by MAPLD
9 Example 1: An Empty Routing Region Actel Corporation May be published with permission by MAPLD
10 Example 2: Secure Fence and Connections Actel Corporation May be published with permission by MAPLD
11 Example 3: Isolation of Red and Black Datapaths Actel Corporation May be published with permission by MAPLD
12 Example 4: Isolation of Red and Black Datapaths Actel Corporation May be published with permission by MAPLD
Horst Görtz Institute for IT-Security
 Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Rapid System Prototyping with FPGAs
 Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Using Global Resources in Actel ProASIC3/E Devices
 Application Note Using Global Resources in Actel ProASIC3/E Devices Introduction Actel ProASIC3/E FPGA devices offer a powerful, low-delay VersaNet global network scheme and have extensive support for
Application Note Using Global Resources in Actel ProASIC3/E Devices Introduction Actel ProASIC3/E FPGA devices offer a powerful, low-delay VersaNet global network scheme and have extensive support for
Designing a SuperClock with an Axcelerator Device
 Application Note AC212 Designing a SuperClock with an Axcelerator Device Introduction Many board designs today require complex clocking schemes involving multiple frequencies and phases. Semiconductor
Application Note AC212 Designing a SuperClock with an Axcelerator Device Introduction Many board designs today require complex clocking schemes involving multiple frequencies and phases. Semiconductor
LatticeECP2/M S-Series Configuration Encryption Usage Guide
 Configuration Encryption Usage Guide June 2013 Introduction Technical Note TN1109 All Lattice FPGAs provide configuration data read security, meaning that a fuse can be set so that when the device is read
Configuration Encryption Usage Guide June 2013 Introduction Technical Note TN1109 All Lattice FPGAs provide configuration data read security, meaning that a fuse can be set so that when the device is read
AES1. Ultra-Compact Advanced Encryption Standard Core. General Description. Base Core Features. Symbol. Applications
 General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (start at 800 Actel tiles). Enhanced versions
General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (start at 800 Actel tiles). Enhanced versions
Design of a High Speed Communications Link Using Field Programmable Gate Arrays
 Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
FPGAs for Trusted Cloud Computing
 FPGAs for Trusted Cloud Computing Traditional Servers Datacenter Cloud Servers Datacenter Cloud Manager Client Client Control Client Client Control 2 Existing cloud systems cannot offer strong security
FPGAs for Trusted Cloud Computing Traditional Servers Datacenter Cloud Servers Datacenter Cloud Manager Client Client Control Client Client Control 2 Existing cloud systems cannot offer strong security
LatticeXP2 Configuration Encryption and Security Usage Guide
 April 2013 Introduction Technical Note TN1142 Unlike a volatile FPGA, which requires an external boot-prom to store configuration data, the LatticeXP2 devices are non-volatile and have on-chip configuration
April 2013 Introduction Technical Note TN1142 Unlike a volatile FPGA, which requires an external boot-prom to store configuration data, the LatticeXP2 devices are non-volatile and have on-chip configuration
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
SmartDesign MSS. Clock Configuration
 SmartDesign MSS Clock Configuration Table of Contents Configuration Options.............................................................. 3 CLK (x= A/B/C) Reference Clocks...........................................................
SmartDesign MSS Clock Configuration Table of Contents Configuration Options.............................................................. 3 CLK (x= A/B/C) Reference Clocks...........................................................
MAX 10 FPGA Configuration User Guide
 MAX 10 FPGA Configuration User Guide Subscribe UG-M10CONFIG 101 Innovation Drive San Jose, CA 95134 www.altera.com TOC-2 Contents MAX 10 FPGA Configuration Overview... 1-1 MAX 10 FPGA Configuration Schemes
MAX 10 FPGA Configuration User Guide Subscribe UG-M10CONFIG 101 Innovation Drive San Jose, CA 95134 www.altera.com TOC-2 Contents MAX 10 FPGA Configuration Overview... 1-1 MAX 10 FPGA Configuration Schemes
Extending Networking to Fit the Cloud
 VXLAN Extending Networking to Fit the Cloud Kamau WangŨ H Ũ Kamau Wangũhgũ is a Consulting Architect at VMware and a member of the Global Technical Service, Center of Excellence group. Kamau s focus at
VXLAN Extending Networking to Fit the Cloud Kamau WangŨ H Ũ Kamau Wangũhgũ is a Consulting Architect at VMware and a member of the Global Technical Service, Center of Excellence group. Kamau s focus at
SmartDesign MSS. How to Create a MSS and Fabric AMBA AHBLite/APB3 Design (MSS Master Mode)
 SmartDesign MSS How to Create a MSS and Fabric AMBA AHBLite/APB3 Design (MSS Master Mode) Libero IDE Software Table of Contents 1 Configuration and Connectivity.......................................................
SmartDesign MSS How to Create a MSS and Fabric AMBA AHBLite/APB3 Design (MSS Master Mode) Libero IDE Software Table of Contents 1 Configuration and Connectivity.......................................................
Fusion Embedded Development Kit. Webserver Demo User s Guide
 Fusion Embedded Development Kit Webserver Demo User s Guide Actel Corporation, Mountain View, CA 94043 2009 Actel Corporation. All rights reserved. Printed in the United States of America Part Number:
Fusion Embedded Development Kit Webserver Demo User s Guide Actel Corporation, Mountain View, CA 94043 2009 Actel Corporation. All rights reserved. Printed in the United States of America Part Number:
Security Policy: Key Management Facility Crypto Card (KMF CC)
 Security Policy: Key Management Facility Crypto Card (KMF CC) Version 2.12.2 2/7/11 1.0 Introduction 3 1.1 Scope 3 1.2 Overview 3 1.3 KMF CC Implementation 4 1.4 KMF CC HW/SW version numbers 4 1.5 KMF
Security Policy: Key Management Facility Crypto Card (KMF CC) Version 2.12.2 2/7/11 1.0 Introduction 3 1.1 Scope 3 1.2 Overview 3 1.3 KMF CC Implementation 4 1.4 KMF CC HW/SW version numbers 4 1.5 KMF
Distributed Elastic Switch Architecture for efficient Networks-on-FPGAs
 Distributed Elastic Switch Architecture for efficient Networks-on-FPGAs Antoni Roca, Jose Flich Parallel Architectures Group Universitat Politechnica de Valencia (UPV) Valencia, Spain Giorgos Dimitrakopoulos
Distributed Elastic Switch Architecture for efficient Networks-on-FPGAs Antoni Roca, Jose Flich Parallel Architectures Group Universitat Politechnica de Valencia (UPV) Valencia, Spain Giorgos Dimitrakopoulos
SPI Configuration and Flash Programming in UltraScale FPGAs
 XAPP1233 (v1.0) May 29, 2015 Application Note: UltraScale FPGAs SPI Configuration and Flash Programming in UltraScale FPGAs Authors: Matt Nielson and Ryan Rumsey Summary This application note describes
XAPP1233 (v1.0) May 29, 2015 Application Note: UltraScale FPGAs SPI Configuration and Flash Programming in UltraScale FPGAs Authors: Matt Nielson and Ryan Rumsey Summary This application note describes
Reconfigurable Computing. Reconfigurable Architectures. Chapter 3.2
 Reconfigurable Architectures Chapter 3.2 Prof. Dr.-Ing. Jürgen Teich Lehrstuhl für Hardware-Software-Co-Design Coarse-Grained Reconfigurable Devices Recall: 1. Brief Historically development (Estrin Fix-Plus
Reconfigurable Architectures Chapter 3.2 Prof. Dr.-Ing. Jürgen Teich Lehrstuhl für Hardware-Software-Co-Design Coarse-Grained Reconfigurable Devices Recall: 1. Brief Historically development (Estrin Fix-Plus
SecureDoc Disk Encryption Cryptographic Engine
 SecureDoc Disk Encryption Cryptographic Engine FIPS 140-2 Non-Proprietary Security Policy Abstract: This document specifies Security Policy enforced by SecureDoc Cryptographic Engine compliant with the
SecureDoc Disk Encryption Cryptographic Engine FIPS 140-2 Non-Proprietary Security Policy Abstract: This document specifies Security Policy enforced by SecureDoc Cryptographic Engine compliant with the
FPGA-based Multithreading for In-Memory Hash Joins
 FPGA-based Multithreading for In-Memory Hash Joins Robert J. Halstead, Ildar Absalyamov, Walid A. Najjar, Vassilis J. Tsotras University of California, Riverside Outline Background What are FPGAs Multithreaded
FPGA-based Multithreading for In-Memory Hash Joins Robert J. Halstead, Ildar Absalyamov, Walid A. Najjar, Vassilis J. Tsotras University of California, Riverside Outline Background What are FPGAs Multithreaded
How To Set Up A Hard Drive With A Harddrive With A 2Gb Hard Drive (I386) And 2Gb Drive (Amd64) On A Hardrive (I219) (Iee) (Amd66) (Ai219
 1 Package Contents Device User manual Power adapter Power cord USB 2.0 Cable FireWire 800 Cable (IEEE1394.B) esata cable 2 Front View of the Device A Drive eject button B LED indicator C Front door panel
1 Package Contents Device User manual Power adapter Power cord USB 2.0 Cable FireWire 800 Cable (IEEE1394.B) esata cable 2 Front View of the Device A Drive eject button B LED indicator C Front door panel
Building an Embedded Processor System on a Xilinx Zync FPGA (Profiling): A Tutorial
 Building an Embedded Processor System on a Xilinx Zync FPGA (Profiling): A Tutorial Embedded Processor Hardware Design January 29 th 2015. VIVADO TUTORIAL 1 Table of Contents Requirements... 3 Part 1:
Building an Embedded Processor System on a Xilinx Zync FPGA (Profiling): A Tutorial Embedded Processor Hardware Design January 29 th 2015. VIVADO TUTORIAL 1 Table of Contents Requirements... 3 Part 1:
ELPBack Online Backup Whitepaper Data Security Version 5.5.x Jun 2008 Protecting Tomorrow with yesterday ELPBack Offsite Backup Whitepaper Data
 ELPBack Online Backup Version 5.5.x Jun 2008 Protecting Tomorrow with yesterday ELPBack Offsite Backup Table of Content 1 Introduction...3 2 ELPBack Offsite Backup Server Secure, Robust and Reliable...4
ELPBack Online Backup Version 5.5.x Jun 2008 Protecting Tomorrow with yesterday ELPBack Offsite Backup Table of Content 1 Introduction...3 2 ELPBack Offsite Backup Server Secure, Robust and Reliable...4
AMC13 T1 Rev 2 Preliminary Design Review. E. Hazen Boston University. 2012-10-30 E. Hazen - AMC13 T1 V2 1
 13 T1 Rev 2 Preliminary Design Review E. Hazen Boston University 2012-10-30 E. Hazen - 13 T1 V2 1 Scope of this Review Background: 13 T1 board is being revised to support 10 GbE per request from CDAQ group
13 T1 Rev 2 Preliminary Design Review E. Hazen Boston University 2012-10-30 E. Hazen - 13 T1 V2 1 Scope of this Review Background: 13 T1 board is being revised to support 10 GbE per request from CDAQ group
Ahsay Online Backup. Whitepaper Data Security
 Ahsay Online Backup Version 5.x Jun 2006 Table of Content 1 Introduction...3 2 Server Secure, Robust and Reliable...4 2.1 Secure 128-bit SSL communication...4 2.2 Backup data are securely encrypted...4
Ahsay Online Backup Version 5.x Jun 2006 Table of Content 1 Introduction...3 2 Server Secure, Robust and Reliable...4 2.1 Secure 128-bit SSL communication...4 2.2 Backup data are securely encrypted...4
MAX II ISP Update with I/O Control & Register Data Retention
 MAX II ISP Update with I/O Control & Register Data Retention March 2006, ver 1.0 Application Note 410 Introduction MAX II devices support the real-time in-system mability (ISP) feature that allows you
MAX II ISP Update with I/O Control & Register Data Retention March 2006, ver 1.0 Application Note 410 Introduction MAX II devices support the real-time in-system mability (ISP) feature that allows you
Preventing Piracy and Reverse Engineering of SRAM FPGAs Bitstream
 Approche de conception d interface de communication pour les systèmes sur puce Preventing Piracy and Reverse Engineering of SRAM FPGAs Bitstream Lilian Bossuet 1, Guy Gogniat 1, Wayne Burleson 2 1 LESTER
Approche de conception d interface de communication pour les systèmes sur puce Preventing Piracy and Reverse Engineering of SRAM FPGAs Bitstream Lilian Bossuet 1, Guy Gogniat 1, Wayne Burleson 2 1 LESTER
Implementation Details
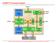 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Arquitectura Virtex. Delay-Locked Loop (DLL)
 Arquitectura Virtex Compuesta de dos elementos principales configurables : CLBs y IOBs. Los CLBs se interconectan a través de una matriz general de routeado (GRM). Posse una intefaz VersaRing que proporciona
Arquitectura Virtex Compuesta de dos elementos principales configurables : CLBs y IOBs. Los CLBs se interconectan a través de una matriz general de routeado (GRM). Posse una intefaz VersaRing que proporciona
Implementation of Web-Server Using Altera DE2-70 FPGA Development Kit
 1 Implementation of Web-Server Using Altera DE2-70 FPGA Development Kit A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENT OF FOR THE DEGREE IN Bachelor of Technology In Electronics and Communication
1 Implementation of Web-Server Using Altera DE2-70 FPGA Development Kit A THESIS SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENT OF FOR THE DEGREE IN Bachelor of Technology In Electronics and Communication
FLASH USB 2. 0. Introduction ENGLISH
 ENGLISH FLASH RED LED (LOCKED) GREEN LED (UNLOCKED) KEY BUTTON PIN KEYS BLUE LED (ACTIVITY) Introduction Thank you for purchasing the Corsair Your new Flash Padlock 2 is a 256-bit hardware encrypted USB
ENGLISH FLASH RED LED (LOCKED) GREEN LED (UNLOCKED) KEY BUTTON PIN KEYS BLUE LED (ACTIVITY) Introduction Thank you for purchasing the Corsair Your new Flash Padlock 2 is a 256-bit hardware encrypted USB
Data Superhero Online Backup Whitepaper Data Security
 Data Superhero Online Backup Whitepaper Data Security Cottage Computers Ltd. Page 1 of 5 (April 15, 2008) Table of Contents Contents 1. Data Superhero Offsite Backup Server Secure, Robust and Reliable...
Data Superhero Online Backup Whitepaper Data Security Cottage Computers Ltd. Page 1 of 5 (April 15, 2008) Table of Contents Contents 1. Data Superhero Offsite Backup Server Secure, Robust and Reliable...
ELECTENG702 Advanced Embedded Systems. Improving AES128 software for Altera Nios II processor using custom instructions
 Assignment ELECTENG702 Advanced Embedded Systems Improving AES128 software for Altera Nios II processor using custom instructions October 1. 2005 Professor Zoran Salcic by Kilian Foerster 10-8 Claybrook
Assignment ELECTENG702 Advanced Embedded Systems Improving AES128 software for Altera Nios II processor using custom instructions October 1. 2005 Professor Zoran Salcic by Kilian Foerster 10-8 Claybrook
Aims and Objectives. E 3.05 Digital System Design. Course Syllabus. Course Syllabus (1) Programmable Logic
 Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: p.cheung@ic.ac.uk How to go
Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: p.cheung@ic.ac.uk How to go
Advanced Encryption Standard (AES) User's Guide
 Advanced Encryption Standard (AES) User's Guide Version 1.00 BETA For use with AES versions 1.6 and above Date: 11-Feb-2015 11:23 All rights reserved. This document and the associated software are the
Advanced Encryption Standard (AES) User's Guide Version 1.00 BETA For use with AES versions 1.6 and above Date: 11-Feb-2015 11:23 All rights reserved. This document and the associated software are the
Aegis Padlock for business
 Aegis Padlock for business Problem: Securing private information is critical for individuals and mandatory for business. Mobile users need to protect their personal information from identity theft. Businesses
Aegis Padlock for business Problem: Securing private information is critical for individuals and mandatory for business. Mobile users need to protect their personal information from identity theft. Businesses
Enova X-Wall XO Frequently Asked Questions--FAQs
 Enova X-Wall XO Frequently Asked Questions--FAQs Q: What is X-Wall XO? A: X-Wall XO is the fourth generation product that encrypts and decrypts the entire volume of the hard drive. The entire volume includes
Enova X-Wall XO Frequently Asked Questions--FAQs Q: What is X-Wall XO? A: X-Wall XO is the fourth generation product that encrypts and decrypts the entire volume of the hard drive. The entire volume includes
Hardware Implementation of Improved Adaptive NoC Router with Flit Flow History based Load Balancing Selection Strategy
 Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
Securely Yours LLC We secure your information world. www. SecurelyYoursllc.com
 We secure your information world www. Mobile Security Features What are the new security features in Android KitKat 4.4 and IOS 7?. IOS Feature 1 Single Sign-on Previously available for multiple apps developed
We secure your information world www. Mobile Security Features What are the new security features in Android KitKat 4.4 and IOS 7?. IOS Feature 1 Single Sign-on Previously available for multiple apps developed
GoldKey Software. User s Manual. Revision 7.12. WideBand Corporation www.goldkey.com. Copyright 2007-2014 WideBand Corporation. All Rights Reserved.
 GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
How To Design A Chip Layout
 Spezielle Anwendungen des VLSI Entwurfs Applied VLSI design (IEF170) Course and contest Intermediate meeting 3 Prof. Dirk Timmermann, Claas Cornelius, Hagen Sämrow, Andreas Tockhorn, Philipp Gorski, Martin
Spezielle Anwendungen des VLSI Entwurfs Applied VLSI design (IEF170) Course and contest Intermediate meeting 3 Prof. Dirk Timmermann, Claas Cornelius, Hagen Sämrow, Andreas Tockhorn, Philipp Gorski, Martin
Networking Virtualization Using FPGAs
 Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
All Programmable Logic. Hans-Joachim Gelke Institute of Embedded Systems. Zürcher Fachhochschule
 All Programmable Logic Hans-Joachim Gelke Institute of Embedded Systems Institute of Embedded Systems 31 Assistants 10 Professors 7 Technical Employees 2 Secretaries www.ines.zhaw.ch Research: Education:
All Programmable Logic Hans-Joachim Gelke Institute of Embedded Systems Institute of Embedded Systems 31 Assistants 10 Professors 7 Technical Employees 2 Secretaries www.ines.zhaw.ch Research: Education:
DRV8312-C2-KIT How to Run Guide
 DRV8312-C2-KIT How to Run Guide Version 1.1 October 2011 C2000 Systems and Applications Team This Guide explains the steps needed to run the DRV8312-C2-KIT with the software supplied through controlsuite.
DRV8312-C2-KIT How to Run Guide Version 1.1 October 2011 C2000 Systems and Applications Team This Guide explains the steps needed to run the DRV8312-C2-KIT with the software supplied through controlsuite.
Offline HW/SW Authentication for Reconfigurable Platforms
 Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech esimpson@vt.edu Patrick Schaumont Virginia Tech schaum@vt.edu Abstract Many Field-Programmable Gate Array (FPGA) based
Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech esimpson@vt.edu Patrick Schaumont Virginia Tech schaum@vt.edu Abstract Many Field-Programmable Gate Array (FPGA) based
A Gigabit Transceiver for Data Transmission in Future HEP Experiments and An overview of optoelectronics in HEP
 A Gigabit Transceiver for Data Transmission in Future HEP Experiments and An overview of optoelectronics in HEP Ken Wyllie, CERN 1 Outline Optoelectronics What? Why? How? Experience in HEP (LHC) & future
A Gigabit Transceiver for Data Transmission in Future HEP Experiments and An overview of optoelectronics in HEP Ken Wyllie, CERN 1 Outline Optoelectronics What? Why? How? Experience in HEP (LHC) & future
Isolation Design Flow for Xilinx 7 Series FPGAs or Zynq-7000 AP SoCs (ISE Tools)
 XAPP1086 (v1.3.1) February 5, 2015 Application Note: 7 Series FPGAs and Zynq-7000 AP SoC Isolation Design Flow for Xilinx 7 Series FPGAs or Zynq-7000 AP SoCs (ISE Tools) Author: Ed Hallett Summary This
XAPP1086 (v1.3.1) February 5, 2015 Application Note: 7 Series FPGAs and Zynq-7000 AP SoC Isolation Design Flow for Xilinx 7 Series FPGAs or Zynq-7000 AP SoCs (ISE Tools) Author: Ed Hallett Summary This
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
From Bus and Crossbar to Network-On-Chip. Arteris S.A.
 From Bus and Crossbar to Network-On-Chip Arteris S.A. Copyright 2009 Arteris S.A. All rights reserved. Contact information Corporate Headquarters Arteris, Inc. 1741 Technology Drive, Suite 250 San Jose,
From Bus and Crossbar to Network-On-Chip Arteris S.A. Copyright 2009 Arteris S.A. All rights reserved. Contact information Corporate Headquarters Arteris, Inc. 1741 Technology Drive, Suite 250 San Jose,
Seeking Opportunities for Hardware Acceleration in Big Data Analytics
 Seeking Opportunities for Hardware Acceleration in Big Data Analytics Paul Chow High-Performance Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Toronto Who
Seeking Opportunities for Hardware Acceleration in Big Data Analytics Paul Chow High-Performance Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Toronto Who
2. Scope of the DE0 Board and Supporting Material
 1 Getting Started with Altera s DE0 Board This document describes the scope of Altera s DE0 Development and Education Board and the supporting materials provided by the Altera Corporation. It also explains
1 Getting Started with Altera s DE0 Board This document describes the scope of Altera s DE0 Development and Education Board and the supporting materials provided by the Altera Corporation. It also explains
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler
 ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
Open Flow Controller and Switch Datasheet
 Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
Security Architecture Whitepaper
 Security Architecture Whitepaper 2015 by Network2Share Pty Ltd. All rights reserved. 1 Table of Contents CloudFileSync Security 1 Introduction 1 Data Security 2 Local Encryption - Data on the local computer
Security Architecture Whitepaper 2015 by Network2Share Pty Ltd. All rights reserved. 1 Table of Contents CloudFileSync Security 1 Introduction 1 Data Security 2 Local Encryption - Data on the local computer
Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012)
 Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012) Sergei Skorobogatov University of Cambridge Cambridge, UK sps32@cam.ac.uk Christopher Woods Quo Vadis Labs London,
Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012) Sergei Skorobogatov University of Cambridge Cambridge, UK sps32@cam.ac.uk Christopher Woods Quo Vadis Labs London,
Using FPGAs to Design Gigabit Serial Backplanes. April 17, 2002
 Using FPGAs to Design Gigabit Serial Backplanes April 17, 2002 Outline System Design Trends Serial Backplanes Architectures Building Serial Backplanes with FPGAs A1-2 Key System Design Trends Need for.
Using FPGAs to Design Gigabit Serial Backplanes April 17, 2002 Outline System Design Trends Serial Backplanes Architectures Building Serial Backplanes with FPGAs A1-2 Key System Design Trends Need for.
FPGA Implementation of IP Packet Segmentation and Reassembly in Internet Router*
 SERBIAN JOURNAL OF ELECTRICAL ENGINEERING Vol. 6, No. 3, December 2009, 399-407 UDK: 004.738.5.057.4 FPGA Implementation of IP Packet Segmentation and Reassembly in Internet Router* Marko Carević 1,a,
SERBIAN JOURNAL OF ELECTRICAL ENGINEERING Vol. 6, No. 3, December 2009, 399-407 UDK: 004.738.5.057.4 FPGA Implementation of IP Packet Segmentation and Reassembly in Internet Router* Marko Carević 1,a,
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems
 Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
How To Write An Fpa Programmable Gate Array
 Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications Niccolò Battezzati Luca Sterpone Massimo Violante Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications
Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications Niccolò Battezzati Luca Sterpone Massimo Violante Reconfigurable Field Programmable Gate Arrays for Mission-Critical Applications
CAUTION! THE 7I29 USES VOLTAGE AND POWER LEVELS THAT REPRESENT A HAZARD TO LIFE AND LIMB.
 7I29 MANUAL Rev 1.5 CAUTION! THE 7I29 USES VOLTAGE AND POWER LEVELS THAT REPRESENT A HAZARD TO LIFE AND LIMB. THE 7I29 IS INTENDED FOR USE BY OEMS THAT WILL INTEGRATE IT INTO A SYSTEM WITH INTERLOCKS AND
7I29 MANUAL Rev 1.5 CAUTION! THE 7I29 USES VOLTAGE AND POWER LEVELS THAT REPRESENT A HAZARD TO LIFE AND LIMB. THE 7I29 IS INTENDED FOR USE BY OEMS THAT WILL INTEGRATE IT INTO A SYSTEM WITH INTERLOCKS AND
FIPS 140 2 Non Proprietary Security Policy: Kingston Technology DataTraveler DT4000 Series USB Flash Drive
 FIPS 140 2 Non Proprietary Security Policy Kingston Technology Company, Inc. DataTraveler DT4000 G2 Series USB Flash Drive Document Version 1.8 December 3, 2014 Document Version 1.8 Kingston Technology
FIPS 140 2 Non Proprietary Security Policy Kingston Technology Company, Inc. DataTraveler DT4000 G2 Series USB Flash Drive Document Version 1.8 December 3, 2014 Document Version 1.8 Kingston Technology
User's Manual. Intego Remote Management Console User's Manual Page 1
 User's Manual Intego Remote Management Console User's Manual Page 1 Intego Remote Management Console for Macintosh 2007 Intego, Inc. All Rights Reserved Intego, Inc. www.intego.com This manual was written
User's Manual Intego Remote Management Console User's Manual Page 1 Intego Remote Management Console for Macintosh 2007 Intego, Inc. All Rights Reserved Intego, Inc. www.intego.com This manual was written
Cautions When Using BitLocker Drive Encryption on PRIMERGY
 Cautions When Using BitLocker Drive Encryption on PRIMERGY July 2008 Fujitsu Limited Table of Contents Preface...3 1 Recovery mode...4 2 Changes in hardware configurations...5 3 Prior to hardware maintenance
Cautions When Using BitLocker Drive Encryption on PRIMERGY July 2008 Fujitsu Limited Table of Contents Preface...3 1 Recovery mode...4 2 Changes in hardware configurations...5 3 Prior to hardware maintenance
Cryptographic Rights Management of FPGA Intellectual Property Cores
 Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom tom@algotronix.com ABSTRACT As the capacity of FPGA s increases
Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom tom@algotronix.com ABSTRACT As the capacity of FPGA s increases
Hunting Asynchronous CDC Violations in the Wild
 Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
Hunting Asynchronous Violations in the Wild Chris Kwok Principal Engineer May 4, 2015 is the #2 Verification Problem Why is a Big Problem: 10 or More Clock Domains are Common Even FPGA Users Are Suffering
Header Parsing Logic in Network Switches Using Fine and Coarse-Grained Dynamic Reconfiguration Strategies
 Header Parsing Logic in Network Switches Using Fine and Coarse-Grained Dynamic Reconfiguration Strategies by Alexander Sonek A thesis presented to the University of Waterloo in fulfillment of the thesis
Header Parsing Logic in Network Switches Using Fine and Coarse-Grained Dynamic Reconfiguration Strategies by Alexander Sonek A thesis presented to the University of Waterloo in fulfillment of the thesis
Using the Agilent 3070 Tester for In-System Programming in Altera CPLDs
 Using the Agilent 3070 Tester for In-System Programming in Altera CPLDs AN-628-1.0 Application Note This application note describes how to use the Agilent 3070 test system to achieve faster programming
Using the Agilent 3070 Tester for In-System Programming in Altera CPLDs AN-628-1.0 Application Note This application note describes how to use the Agilent 3070 test system to achieve faster programming
Blaze Vault Online Backup. Whitepaper Data Security
 Blaze Vault Online Backup Version 5.x Jun 2006 Table of Content 1 Introduction... 3 2 Blaze Vault Offsite Backup Server Secure, Robust and Reliable... 4 2.1 Secure 256-bit SSL communication... 4 2.2 Backup
Blaze Vault Online Backup Version 5.x Jun 2006 Table of Content 1 Introduction... 3 2 Blaze Vault Offsite Backup Server Secure, Robust and Reliable... 4 2.1 Secure 256-bit SSL communication... 4 2.2 Backup
SPI Flash Programming and Hardware Interfacing Using ispvm System
 March 2005 Introduction Technical Note TN1081 SRAM-based FPGA devices are volatile and require reconfiguration after power cycles. This requires external configuration data to be held in a non-volatile
March 2005 Introduction Technical Note TN1081 SRAM-based FPGA devices are volatile and require reconfiguration after power cycles. This requires external configuration data to be held in a non-volatile
Lab 1: Introduction to Xilinx ISE Tutorial
 Lab 1: Introduction to Xilinx ISE Tutorial This tutorial will introduce the reader to the Xilinx ISE software. Stepby-step instructions will be given to guide the reader through generating a project, creating
Lab 1: Introduction to Xilinx ISE Tutorial This tutorial will introduce the reader to the Xilinx ISE software. Stepby-step instructions will be given to guide the reader through generating a project, creating
Lesson 7: SYSTEM-ON. SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY. Chapter-1L07: "Embedded Systems - ", Raj Kamal, Publs.: McGraw-Hill Education
 Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
RCC2 Test Proceedures
 RCC2 Test Proceedures 1. Power-up Test 1. install board in VME crate (6U style or 6U section of 9U) and turn on power 2. check that cfg LED (D4) on front panel and D3 LED on board near U47 are lit (red)
RCC2 Test Proceedures 1. Power-up Test 1. install board in VME crate (6U style or 6U section of 9U) and turn on power 2. check that cfg LED (D4) on front panel and D3 LED on board near U47 are lit (red)
Pmod peripheral modules are powered by the host via the interface s power and ground pins.
 Digilent Pmod Interface Specification Revision: November 20, 2011 1300 NE Henley Court, Suite 3 Pullman, WA 99163 (509) 334 6306 Voice (509) 334 6300 Fax Introduction The Digilent Pmod interface is used
Digilent Pmod Interface Specification Revision: November 20, 2011 1300 NE Henley Court, Suite 3 Pullman, WA 99163 (509) 334 6306 Voice (509) 334 6300 Fax Introduction The Digilent Pmod interface is used
Chapter 13: Verification
 Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
Chapter 13: Verification Prof. Ming-Bo Lin Department of Electronic Engineering National Taiwan University of Science and Technology Digital System Designs and Practices Using Verilog HDL and FPGAs @ 2008-2010,
Enova X-Wall LX Frequently Asked Questions
 Enova X-Wall LX Frequently Asked Questions Q: What is X-Wall LX? A: X-Wall LX is the third generation of Enova real-time hard drive cryptographic gateway ASIC (Application Specific Integrated Circuit)
Enova X-Wall LX Frequently Asked Questions Q: What is X-Wall LX? A: X-Wall LX is the third generation of Enova real-time hard drive cryptographic gateway ASIC (Application Specific Integrated Circuit)
Job Management System Extension To Support SLAAC-1V Reconfigurable Hardware
 Job Management System Extension To Support SLAAC-1V Reconfigurable Hardware Mohamed Taher 1, Kris Gaj 2, Tarek El-Ghazawi 1, and Nikitas Alexandridis 1 1 The George Washington University 2 George Mason
Job Management System Extension To Support SLAAC-1V Reconfigurable Hardware Mohamed Taher 1, Kris Gaj 2, Tarek El-Ghazawi 1, and Nikitas Alexandridis 1 1 The George Washington University 2 George Mason
Understanding the Impact of Encryption on Certified Wireless USB Testing. Introduction. Association vs. Security
 on Certified Wireless USB Testing Mike Micheletti Wireless USB Product Manager LeCroy Protocol Solutions Group Introduction Certified Wireless USB (WUSB) is a new shortrange, high-bandwidth wireless extension
on Certified Wireless USB Testing Mike Micheletti Wireless USB Product Manager LeCroy Protocol Solutions Group Introduction Certified Wireless USB (WUSB) is a new shortrange, high-bandwidth wireless extension
Route Processor. Route Processor Overview CHAPTER
 CHAPTER 6 This chapter describes the route processor (RP) card. The following sections are included: Overview, page 6-1 Primary and Standby Arbitration, page 6-4 RP Card to Fabric Module Queuing, page
CHAPTER 6 This chapter describes the route processor (RP) card. The following sections are included: Overview, page 6-1 Primary and Standby Arbitration, page 6-4 RP Card to Fabric Module Queuing, page
Note monitors controlled by analog signals CRT monitors are controlled by analog voltage. i. e. the level of analog signal delivered through the
 DVI Interface The outline: The reasons for digital interface of a monitor the transfer from VGA to DVI. DVI v. analog interface. The principles of LCD control through DVI interface. The link between DVI
DVI Interface The outline: The reasons for digital interface of a monitor the transfer from VGA to DVI. DVI v. analog interface. The principles of LCD control through DVI interface. The link between DVI
S E A h a w k C r y p t o M i l l CryptoMill Technologies Ltd. www.cryptomill.com
 SEAhawk CryptoMill CryptoMill Technologies Ltd. www.cryptomill.com OVERVIEW S EAhawk is an endpoint and removable storage security solution for desktop PCs and laptops running the Microsoft Windows operating
SEAhawk CryptoMill CryptoMill Technologies Ltd. www.cryptomill.com OVERVIEW S EAhawk is an endpoint and removable storage security solution for desktop PCs and laptops running the Microsoft Windows operating
First Semester Examinations 2011/12 INTERNET PRINCIPLES
 PAPER CODE NO. EXAMINER : Martin Gairing COMP211 DEPARTMENT : Computer Science Tel. No. 0151 795 4264 First Semester Examinations 2011/12 INTERNET PRINCIPLES TIME ALLOWED : Two Hours INSTRUCTIONS TO CANDIDATES
PAPER CODE NO. EXAMINER : Martin Gairing COMP211 DEPARTMENT : Computer Science Tel. No. 0151 795 4264 First Semester Examinations 2011/12 INTERNET PRINCIPLES TIME ALLOWED : Two Hours INSTRUCTIONS TO CANDIDATES
- Nishad Nerurkar. - Aniket Mhatre
 - Nishad Nerurkar - Aniket Mhatre Single Chip Cloud Computer is a project developed by Intel. It was developed by Intel Lab Bangalore, Intel Lab America and Intel Lab Germany. It is part of a larger project,
- Nishad Nerurkar - Aniket Mhatre Single Chip Cloud Computer is a project developed by Intel. It was developed by Intel Lab Bangalore, Intel Lab America and Intel Lab Germany. It is part of a larger project,
RAID Utility User s Guide Instructions for setting up RAID volumes on a computer with a MacPro RAID Card or Xserve RAID Card.
 RAID Utility User s Guide Instructions for setting up RAID volumes on a computer with a MacPro RAID Card or Xserve RAID Card. 1 Contents 3 RAID Utility User s Guide 3 Installing the RAID Software 4 Running
RAID Utility User s Guide Instructions for setting up RAID volumes on a computer with a MacPro RAID Card or Xserve RAID Card. 1 Contents 3 RAID Utility User s Guide 3 Installing the RAID Software 4 Running
4D v11 SQL Release 6 (11.6) ADDENDUM
 ADDENDUM Welcome to release 6 of 4D v11 SQL. This document presents the new features and modifications of this new version of the program. Increased ciphering capacities Release 6 of 4D v11 SQL extends
ADDENDUM Welcome to release 6 of 4D v11 SQL. This document presents the new features and modifications of this new version of the program. Increased ciphering capacities Release 6 of 4D v11 SQL extends
USB-Blaster II Download Cable User Guide
 USB-Blaster II Download Cable User Guide Subscribe UG-01150 101 Innovation Drive San Jose, CA 95134 www.altera.com TOC-2 Contents Setting Up the USB-Blaster II Download Cable...1-1 Supported Devices and
USB-Blaster II Download Cable User Guide Subscribe UG-01150 101 Innovation Drive San Jose, CA 95134 www.altera.com TOC-2 Contents Setting Up the USB-Blaster II Download Cable...1-1 Supported Devices and
Sectra Communications ensuring security with flexibility
 Panthon Sectra Communications ensuring security with flexibility Sectra has more than 30 years of experience in developing secure communications. We know what is required to meet the toughest demands.
Panthon Sectra Communications ensuring security with flexibility Sectra has more than 30 years of experience in developing secure communications. We know what is required to meet the toughest demands.
White Paper Using the Intel Flash Memory-Based EPC4, EPC8 & EPC16 Devices
 White Paper Introduction Altera enhanced configuration devices provide single-device, advanced configuration solutions for high-density Altera FPGAs. The core of an enhanced configuration device is divided
White Paper Introduction Altera enhanced configuration devices provide single-device, advanced configuration solutions for high-density Altera FPGAs. The core of an enhanced configuration device is divided
Contents. Getting Started...1. Managing Your Drives...14. Backing Up & Restoring Folders...28. Synchronizing Folders...48. Managing Security...
 Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Storage and File Structure
 Storage and File Structure Chapter 10: Storage and File Structure Overview of Physical Storage Media Magnetic Disks RAID Tertiary Storage Storage Access File Organization Organization of Records in Files
Storage and File Structure Chapter 10: Storage and File Structure Overview of Physical Storage Media Magnetic Disks RAID Tertiary Storage Storage Access File Organization Organization of Records in Files
Advanced Security Encryption Key Programming Guide for ECP5, LatticeECP3, and LatticeECP2/MS Devices
 March 2014 Introduction Technical Note TN1215 All Lattice FPGAs provide configuration data read security, meaning that a fuse can be set so that when the device is read all zeros will be output instead
March 2014 Introduction Technical Note TN1215 All Lattice FPGAs provide configuration data read security, meaning that a fuse can be set so that when the device is read all zeros will be output instead
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Pre-tested System-on-Chip Design. Accelerates PLD Development
 Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
SOOKASA WHITEPAPER SECURITY SOOKASA.COM
 SOOKASA WHITEPAPER SECURITY SOOKASA.COM Sookasa Overview Sookasa was founded in 2012 by a team of leading security experts. The company s patented file-level encryption enables enterprises to protect data
SOOKASA WHITEPAPER SECURITY SOOKASA.COM Sookasa Overview Sookasa was founded in 2012 by a team of leading security experts. The company s patented file-level encryption enables enterprises to protect data
SmartGen, FlashROM, Analog System Builder, and Flash Memory System Builder. v8.4 User s Guide
 SmartGen, FlashROM, Analog System Builder, and Flash Memory System Builder v8.4 User s Guide Actel Corporation, Mountain View, CA 94043 2008 Actel Corporation. All rights reserved. Printed in the United
SmartGen, FlashROM, Analog System Builder, and Flash Memory System Builder v8.4 User s Guide Actel Corporation, Mountain View, CA 94043 2008 Actel Corporation. All rights reserved. Printed in the United
Certes Networks Layer 4 Encryption. Network Services Impact Test Results
 Certes Networks Layer 4 Encryption Network Services Impact Test Results Executive Summary One of the largest service providers in the United States tested Certes Networks Layer 4 payload encryption over
Certes Networks Layer 4 Encryption Network Services Impact Test Results Executive Summary One of the largest service providers in the United States tested Certes Networks Layer 4 payload encryption over
PCI Express Overview. And, by the way, they need to do it in less time.
 PCI Express Overview Introduction This paper is intended to introduce design engineers, system architects and business managers to the PCI Express protocol and how this interconnect technology fits into
PCI Express Overview Introduction This paper is intended to introduce design engineers, system architects and business managers to the PCI Express protocol and how this interconnect technology fits into
Architekturen und Einsatz von FPGAs mit integrierten Prozessor Kernen. Hans-Joachim Gelke Institute of Embedded Systems Professur für Mikroelektronik
 Architekturen und Einsatz von FPGAs mit integrierten Prozessor Kernen Hans-Joachim Gelke Institute of Embedded Systems Professur für Mikroelektronik Contents Überblick: Aufbau moderner FPGA Einblick: Eigenschaften
Architekturen und Einsatz von FPGAs mit integrierten Prozessor Kernen Hans-Joachim Gelke Institute of Embedded Systems Professur für Mikroelektronik Contents Überblick: Aufbau moderner FPGA Einblick: Eigenschaften
Relay attacks on card payment: vulnerabilities and defences
 Relay attacks on card payment: vulnerabilities and defences Saar Drimer, Steven J. Murdoch http://www.cl.cam.ac.uk/users/{sd410, sjm217} Computer Laboratory www.torproject.org 24C3, 29 December 2007, Berlin,
Relay attacks on card payment: vulnerabilities and defences Saar Drimer, Steven J. Murdoch http://www.cl.cam.ac.uk/users/{sd410, sjm217} Computer Laboratory www.torproject.org 24C3, 29 December 2007, Berlin,
