Employer s Reference Manual Chapter 19. Public School Employees Retirement System. Employers Reference Manual Chapter 19 Revised: 2/26/2015 i
|
|
|
- Alexander Chase
- 8 years ago
- Views:
Transcription
1 Employer s Reference Manual Chapter 19 Public School Employees Retirement System 5 N. 5th Street Harrisburg PA Phone Fax ContactESC@state.pa.us Employers Reference Manual Chapter 19 Revised: 2/26/2015 i
2
3 TABLE OF CONTENTS CHAPTER 19 CONTACTING PSERS... 1 CONTACTING PSERS THROUGH THE ONLINE SYSTEM... 1 EMPLOYER SERVICE CENTER CONTACT INFORMATION... 1 CONTACTING PSERS BY TELEPHONE OR FAX... 2 CONTACTING PSERS BY MAIL... 2 CONTACTING PSERS BY OPENING SECURE S FROM A NON COMMONWEALTH ADDRESS... 3 Triggers... 3 Steps... 3 REPLYING TO SECURE S FROM A NON COMMONWEALTH ADDRESS... 6 Triggers... 6 Steps... 6 OBTAINING PSERS FORMS Forms Within the Online System or From the Forms Page COMMUNICATING ANONYMOUSLY RETIREMENT ERRORS (CARE) LINE Employers Reference Manual Chapter 19 Revised: 2/26/2015 i
4
5 Chapter 19 Contacting PSERS Contacting PSERS through the Online System If you would like to determine your ESC Regional Representative s contact information, use the following steps to access the information: Access the Employer Services window in the online system. From the Employer Services window, click Contact PSERS in the left hand menu. Once the window opens, you will see a map of Pennsylvania. Scroll down to see the names of the Employer Service Center contact for your area, click on your representative s address and send them your question. Employer Service Center Contact Information Employers Reference Manual Chapter 19 Revised: 2/26/2015 1
6 Contacting PSERS by Telephone or Fax The Employer Service Center can be reached at: Toll Free enter your Employer Code at the prompt. If you need to fax a form to PSERS, use this fax number: Contacting PSERS by Mail You may mail forms and letters to PSERS at this address: Employer Service Center Public School Employees Retirement System 5 N 5th Street Harrisburg, PA Do NOT use this address for purchase of service payments by check. Instead, see Chapter 12: Payments Remitting to PSERS. Contacting PSERS by You may your contact person at Employer Service Center via the addresses listed on the Web. Please be sure to include your name, school district, and phone number in your message. If it is necessary to confidential information to PSERS, it is important to ensure that communications are exchanged in the most secure manner possible. The Commonwealth provides a Send Secure feature to help ensure the security of confidential s. Confidential information includes all correspondence, including attachments, which contains personal information for a member or members, or which contains any other information that may not be considered public knowledge. Personal information has been defined by the Commonwealth as an individual s first name or first initial and last name in combination with and linked to one or more of the following data elements when the data is not encrypted or redacted: 1. Social Security Number 2. Driver s license number or state identification card number 3. Financial account number, credit or debit card number, in combination with any required security code, access code or password. In order to utilize the Commonwealth s Send Secure feature, the exchange must be initiated by a Commonwealth employee from a Commonwealth address. Recipients can reply from within the Send Secure system but cannot generate Send Secure s without utilizing the respond feature unless they have another security process in place for use on their system. If the Send Secure does not 2 Employers Reference Manual Chapter 19 Revised: 2/26/2015
7 work with your operating system (see your Information Technology staff for assistance), you will need to continue to mail, fax, or mask personal information in the exchange with PSERS. The following procedures will assist you in the process of receiving a Commonwealth Send Secure and in responding to the Send Secure . Opening Secure s from a Non Commonwealth Address Triggers Once recipients using non Commonwealth addresses have followed the instructions for registering to receive secure Commonwealth s per the document Encryption Desk Reference for Non Commonwealth Users included with the initial Send Secure , the following instructions may be used for opening the resulting secure s and any applicable attachments. Note: As part of the Send Secure feature, you must register to receive and send s with the Commonwealth. The software prompts you through the registration process. If you are having problems registering, receiving, or sending documents through the Send Secure feature, please contact your Information Technology office. The problems can usually be corrected by changing the settings on your computer. Steps 1) You will receive an notification indicating that a secure has been sent to you 2) Click on the securedoc icon in the lower left hand corner of the notification Employers Reference Manual Chapter 19 Revised: 2/26/2015 3
8 3) Type your Password in the designated space and click on Open 4) A view of the secure will appear in a new window 5) If an attachment was included with the , the attachment will be listed below the Subject line. If no attachments were included, you may process and close the . If an attachment was included, double click on the attachment name to open the file and move to step 6. 6) If you opened an attachment, you will receive a pop up window asking if you would like to Open or Save the file or cancel processing of the file. You may choose either of these options. Selecting Open or Save will give you access to the file, and you may then process the attachment just like any attachment from a normal . 4 Employers Reference Manual Chapter 19 Revised: 2/26/2015
9 7) Be sure to close all folders and internet browser windows as soon as you have finished processing the confidential information so that unauthorized parties cannot gain access to confidential information. This can be accomplished by Clicking on the red Xs in the upper right hand corner of each applicable screen Employers Reference Manual Chapter 19 Revised: 2/26/2015 5
10 Replying to Secure s from a Non Commonwealth Address Triggers Once recipients using non Commonwealth addresses have followed the instructions for registering to receive secure Commonwealth s per the document Encryption Desk Reference for Non Commonwealth Users included with the initial Send Secure , the following instructions may be used for replying to secure s. In order for the reply to be sent securely, these instructions must be followed. Failure to comply with these instructions will result in s being sent devoid of required security features. Steps 1) Follow steps 1 4 In Appendix A: Opening Secure s from a Non Commonwealth Address to log in to the Send Secure that you originally received. 2) Select Reply in the Send Secure view of the ; you can click on either occurrence of Reply or Reply All that appears on your screen. 3) Type your message in the body of the 6 Employers Reference Manual Chapter 19 Revised: 2/26/2015
11 4) If you do not need to attach a file to the Send Secure , move to step 9. If you have a file to attach to the Send Secure reply, click on Attachments. If you included an attachment, the Attachment will now appear under the subject line. 5) Click on Add Files in the pop up box Employers Reference Manual Chapter 19 Revised: 2/26/2015 7
12 6) Highlight the file that you need to attach and click on Open 7) Highlight the file and click on Upload File 8 Employers Reference Manual Chapter 19 Revised: 2/26/2015
13 8) Click on Done 9) If you included an attachment, the Attachment will now appear under the subject line. Select Send; you can select either occurrence of Send that appears on your screen. Employers Reference Manual Chapter 19 Revised: 2/26/2015 9
14 10) You will receive a message indicating that your was sent successfully 11) Be sure to close all folders and internet browser windows as soon as you have finished processing the confidential information so that unauthorized parties cannot gain access to confidential information. This can be accomplished by Clicking on the Xs in the upper right hand corner of each applicable screen Note: If you are having problems registering, receiving, or sending documents through the Send Secure feature, please contact your Information Technology office. The problems can usually be corrected by changing the settings on your computer. 10 Employers Reference Manual Chapter 19 Revised: 2/26/2015
15 Obtaining PSERS Forms Forms Within the Online System or From the Forms Page The most commonly used forms are available directly in the online system. 1. Access the Employer Services window in the online system. 2. From the Employer Services window, click Forms in the left hand menu. You will see the following window open. From the list of Employer forms, you may: View the form on your screen Print a blank form or Complete the form, then print If you don t see the form you need or you have questions on a form, contact your ESC Regional Representative for assistance. Employers Reference Manual Chapter 19 Revised: 2/26/
16 Communicating Anonymously Retirement Errors (CARE) Line CARE Line Toll free number: CARE Line Local number: The CARE Line is a toll free number that can be used to call PSERS regarding pension related issues of which PSERS should be made aware. Anyone can call this line to inform PSERS about retirees who have incorrectly returned to work for a Pennsylvania public school employer, money that has been inadvertently reported as retirement covered compensation, etc. When you call the CARE Line, you will reach a voic box where you can anonymously leave a message at any time of day or night without fear of retribution. Messages from the CARE Line voic box are written down and deleted. PSERS does not trace the numbers from received phone calls. Callers are not required to identify themselves. The caller can use the toll free number from a cell phone, home phone, or pay phone; PSERS will not know where the call was placed. PSERS understands that we all play a vital role in ensuring that the rules established by the Pennsylvania State Legislature are followed. With your help, we can ensure the pension laws are administered fairly and equally to all PSERS members. 12 Employers Reference Manual Chapter 19 Revised: 2/26/2015
Business Procedures: Send Secure Emails Created: 02-25-2014 Updated: 04-15-2014
 Business Procedures: Send Secure Emails Created: 02-25-2014 Updated: 04-15-2014 Page 1 of 10 Overview From time to time it is necessary to be able to share confidential information with school districts
Business Procedures: Send Secure Emails Created: 02-25-2014 Updated: 04-15-2014 Page 1 of 10 Overview From time to time it is necessary to be able to share confidential information with school districts
Secure Email Client User Guide Receiving Secure Email from Mercantile Bank
 Receiving Secure Email from Contents This document provides a brief, end-user overview of the Secure Email system which has been implemented by. Why Secure Email? When someone sends you an email, the email
Receiving Secure Email from Contents This document provides a brief, end-user overview of the Secure Email system which has been implemented by. Why Secure Email? When someone sends you an email, the email
10/28/2013. Partners Zixmail Web Portal. Provider Training. Let s Get Started!
 Partners Zixmail Web Portal Provider Training Let s Get Started! 1 Setting Up Your Partners Zixmail Web Portal There are two methods to begin this process. Option #1 Use the link on the Partners Provider
Partners Zixmail Web Portal Provider Training Let s Get Started! 1 Setting Up Your Partners Zixmail Web Portal There are two methods to begin this process. Option #1 Use the link on the Partners Provider
How to Use Boston Private Bank s Secure Mail Service
 1. ONE-TIME REGISTRATION PROCESS Prior to using the Secure Mail service for the first time, a user must initially register with the service by completing steps A thru E below: A. When a Secure Mail encrypted
1. ONE-TIME REGISTRATION PROCESS Prior to using the Secure Mail service for the first time, a user must initially register with the service by completing steps A thru E below: A. When a Secure Mail encrypted
Baylor Secure Messaging. For Non-Baylor Users
 Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
7. In the boxed unlabeled field, enter the last 4 digits of your Social Security number.
 CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
Cloud Web Portal User Guide Version 2.0
 Cloud Web Portal User Guide Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
Cloud Web Portal User Guide Version 2.0 Welcome to ncrypted Cloud! ncrypted Cloud is a Privacy, Security, and Collaboration application that uses Industry Standard Encryption Technology (AES-256 bit encryption)
USC Marshall School of Business ShareFile_With_Outlook_Client_v2.docx 6/12/13 1 of 9
 About ShareFile When you wish to send someone a file or need a file from someone else, your best option is to use ShareFile. It not only provides increased security by automatically encrypting files but
About ShareFile When you wish to send someone a file or need a file from someone else, your best option is to use ShareFile. It not only provides increased security by automatically encrypting files but
U.S. Bank Secure Mail
 U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
Secure Mail Registration and Viewing Procedures
 Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Email - Customer User Guide How to receive an encrypted email
 How to receive an encrypted email This guide has been developed for customers/suppliers of Glasgow City Council who are due to receive sensitive information from us. It will explain how to use our secure
How to receive an encrypted email This guide has been developed for customers/suppliers of Glasgow City Council who are due to receive sensitive information from us. It will explain how to use our secure
Hosted PBX. TelePacific Communicator User Guide. Desktop Edition
 Hosted PBX TelePacific Communicator User Guide Desktop Edition 11/19/2014 CONTENTS Login... 2 Home Window... 3 Status Flag... 4 My Room... 6 Contacts Screen... 6 History... 8 Directory... 9 Dialpad...
Hosted PBX TelePacific Communicator User Guide Desktop Edition 11/19/2014 CONTENTS Login... 2 Home Window... 3 Status Flag... 4 My Room... 6 Contacts Screen... 6 History... 8 Directory... 9 Dialpad...
Directory and Messaging Services Enterprise Secure Mail Services
 Title: Directory and Messaging Services Enterprise Secure Mail Services Enterprise Secure Mail Services for End Users Attention: Receivers of Secure Mail Retrieval of Secure Mail by the Recipient Once
Title: Directory and Messaging Services Enterprise Secure Mail Services Enterprise Secure Mail Services for End Users Attention: Receivers of Secure Mail Retrieval of Secure Mail by the Recipient Once
2. Registration You need to register an account before you can start using sft.pearson.com. You can do this either by
 1. SFT.PEARSON.COM is a web based secure file transfer utility that enables secure delivery of data of any type and size to and from anyone with a valid email address. It works very much like email but
1. SFT.PEARSON.COM is a web based secure file transfer utility that enables secure delivery of data of any type and size to and from anyone with a valid email address. It works very much like email but
MS Outlook Address Book and Phone Directory Features
 MS Outlook Address Book and Phone Directory Features Information Technology has implemented a process to automatically update employee information in Microsoft Outlook; specifically in the Outlook Address
MS Outlook Address Book and Phone Directory Features Information Technology has implemented a process to automatically update employee information in Microsoft Outlook; specifically in the Outlook Address
Department of Alcohol & Drug Programs. Information Management Services Division (IMSD) EMAIL ENCRYPTION INSTRUCTIONS
 Department of Alcohol & Drug Programs (IMSD) EMAIL ENCRYPTION INSTRUCTIONS July 1, 2010 Why Do We Need Email Encryption? Code of Regulations, Title 45, Subtitle A, Part 164 The Health Insurance Portability
Department of Alcohol & Drug Programs (IMSD) EMAIL ENCRYPTION INSTRUCTIONS July 1, 2010 Why Do We Need Email Encryption? Code of Regulations, Title 45, Subtitle A, Part 164 The Health Insurance Portability
Secure Message Center User Guide
 Secure Message Center User Guide Using the Department of Banking Secure Email Message Center 2 Receiving and Replying to Messages 3 Initiating New Messages 7 Using the Address Book 9 Managing Your Account
Secure Message Center User Guide Using the Department of Banking Secure Email Message Center 2 Receiving and Replying to Messages 3 Initiating New Messages 7 Using the Address Book 9 Managing Your Account
Access and Login. Single Sign On Reference. Signoff
 Access and Login To access single sign on, here are the steps: Step 1: type in the URL: postone.onelogin.com Step 2: Enter your Post student email in the username field Step 3: Enter your Post student
Access and Login To access single sign on, here are the steps: Step 1: type in the URL: postone.onelogin.com Step 2: Enter your Post student email in the username field Step 3: Enter your Post student
Secure Email A Guide for Users
 Secure Email A Guide for Users October 14, 2013 10/13 TABLE OF CONTENTS USING THE SYSTEM FOR THE FIRST TIME... 3 EMAIL NOTIFICATION OF SECURE INFORMATION... 3 GETTING REGISTERED ON THE SYSTEM... 4 ACCOUNT
Secure Email A Guide for Users October 14, 2013 10/13 TABLE OF CONTENTS USING THE SYSTEM FOR THE FIRST TIME... 3 EMAIL NOTIFICATION OF SECURE INFORMATION... 3 GETTING REGISTERED ON THE SYSTEM... 4 ACCOUNT
Moving your GroupWise archive to Outlook 2010 Key step to take the day after your e-mail upgrade
 Moving your GroupWise archive to Outlook 2010 Key step to take the day after your e-mail upgrade About this guide /transformation Who should use it This guide is intended for those DBHDD (Department of
Moving your GroupWise archive to Outlook 2010 Key step to take the day after your e-mail upgrade About this guide /transformation Who should use it This guide is intended for those DBHDD (Department of
Can I manually trigger secure e-mail to encrypt a message that does not contain PI or other sensitive information? Yes, by use of the word TID.
 How does Secure E-mail work? When an e-mail is initiated or responded to the secure e-mail algorithm will determine if the e-mail needs to be encrypted based on predefined criteria. If it meets the predefined
How does Secure E-mail work? When an e-mail is initiated or responded to the secure e-mail algorithm will determine if the e-mail needs to be encrypted based on predefined criteria. If it meets the predefined
CLIENT PORTAL USER GUIDE
 CLIENT PORTAL USER GUIDE JULY 28, 2011 At Gelman, Rosenberg & Freedman, CPAs we take the privacy and security of your information seriously. That's why we've introduced the Client Portal for sharing your
CLIENT PORTAL USER GUIDE JULY 28, 2011 At Gelman, Rosenberg & Freedman, CPAs we take the privacy and security of your information seriously. That's why we've introduced the Client Portal for sharing your
Word Secure Messaging User Guide. Version 3.0
 Word Secure Messaging User Guide Version 3.0 Copyright 2007-2013 WordSecure, LLC. All Rights Reserved. Page 1 of 7 1. Introduction Word Secure Messaging is a program that allows you to exchange encrypted
Word Secure Messaging User Guide Version 3.0 Copyright 2007-2013 WordSecure, LLC. All Rights Reserved. Page 1 of 7 1. Introduction Word Secure Messaging is a program that allows you to exchange encrypted
To successfully initialize Microsoft Outlook (Outlook) the first time, email settings need to be verified.
 TO: UAN CLIENTS FROM: UAN STAFF DATE: OCTOBER 8, 2008 SUBJECT: Steps for Initial Setup of Microsoft Outlook To successfully initialize Microsoft Outlook (Outlook) the first time, email settings need to
TO: UAN CLIENTS FROM: UAN STAFF DATE: OCTOBER 8, 2008 SUBJECT: Steps for Initial Setup of Microsoft Outlook To successfully initialize Microsoft Outlook (Outlook) the first time, email settings need to
TriCore Secure Web Email Gateway User Guide 1
 TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
Version 4 Revised 5/2015
 Email Encryption Manual Version 4 Revised 5/2015 This document provides information on sending, receiving, and saving encrypted emails using the WRC Group Message Center. Contents What is Email Encryption...
Email Encryption Manual Version 4 Revised 5/2015 This document provides information on sending, receiving, and saving encrypted emails using the WRC Group Message Center. Contents What is Email Encryption...
Reference Guide to the Attorney Registration System
 Reference Guide to the Attorney Registration System What is the Attorney Registration System? The Attorney Registration System allows attorneys to register for a secure user account. Upon registration
Reference Guide to the Attorney Registration System What is the Attorney Registration System? The Attorney Registration System allows attorneys to register for a secure user account. Upon registration
GMass Getting Started Guide
 Powerful Mass Email System for Gmail Created by: Ajay Goel September 2015 GMass Getting Started Guide Table of Contents Section 1: Set Up Google Chrome & GMass... 1 Who Should Use This Guide... 1 Benefits
Powerful Mass Email System for Gmail Created by: Ajay Goel September 2015 GMass Getting Started Guide Table of Contents Section 1: Set Up Google Chrome & GMass... 1 Who Should Use This Guide... 1 Benefits
EJGH Email Encryption User Tip Sheet 10-11-2013 1 of 8
 EJGH Email Encryption User Tip Sheet 10-11-2013 1 of 8 External Users Decrypting Secure Messages The following sections describe how users external to EJGH receive and decrypt secure messages. Reading
EJGH Email Encryption User Tip Sheet 10-11-2013 1 of 8 External Users Decrypting Secure Messages The following sections describe how users external to EJGH receive and decrypt secure messages. Reading
How To Open An Encrypted Email
 Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
HOW TO USE OIT EMAIL VIA THE WEB
 HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
How to Use JCWHosting Reseller Cloud Storage Solution
 How to Use JCWHosting Reseller Cloud Storage Solution Go to https://www.internetspace.co.za and log in with your Cloud Reseller account username and password. How to Use create a cloud account for your
How to Use JCWHosting Reseller Cloud Storage Solution Go to https://www.internetspace.co.za and log in with your Cloud Reseller account username and password. How to Use create a cloud account for your
Hallpass Instructions for Connecting to Mac with a Mac
 Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
REINVENTING COMMUNICATIONS. User s Guide !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! User s Guide
 " $%&'()*+),$(,$- %&).$,./0)11111111111111111111111111111111111111223 %++(--0,4$5(,./0)6(&7)8$%'222111111111111111111111111229,%/04%$0,4$5(7)8$%'111111111111111111111111111111122: 5);(7%4(1111111111111111111111111111111111111111
" $%&'()*+),$(,$- %&).$,./0)11111111111111111111111111111111111111223 %++(--0,4$5(,./0)6(&7)8$%'222111111111111111111111111229,%/04%$0,4$5(7)8$%'111111111111111111111111111111122: 5);(7%4(1111111111111111111111111111111111111111
Phone.com. Communicate Better
 1 Communicate Better - 1 / 16 - 2 Faxes Setting a Number to Receive Faxes Fax Notification Email Notification Text Message (SMS) notification Managing Faxes Viewing a Fax Downloading a Fax Viewing a Fax
1 Communicate Better - 1 / 16 - 2 Faxes Setting a Number to Receive Faxes Fax Notification Email Notification Text Message (SMS) notification Managing Faxes Viewing a Fax Downloading a Fax Viewing a Fax
Installing SmartGate Remote Backup (Ahsay) Software
 Installing Remote Backup (Ahsay) Software Installing Remote Backup (Ahsay) Software Thank you for using the remote backup solution. We re confident that this will greatly improve the performance and reliability
Installing Remote Backup (Ahsay) Software Installing Remote Backup (Ahsay) Software Thank you for using the remote backup solution. We re confident that this will greatly improve the performance and reliability
How To Encrypt An Email From A Cell Phone To A Pc Or Ipad (For A Partner) With A Cisco Email Encryption Solution (For Partners)
 New PHI & PII E-mail Encryption Solution (Partner Notification) In a continuing effort to utilize the advantages of email security while at the same time protecting clients private information, the Department
New PHI & PII E-mail Encryption Solution (Partner Notification) In a continuing effort to utilize the advantages of email security while at the same time protecting clients private information, the Department
Outlook Operating Instructions. Internal Desktop Access
 Outlook Operating Instructions Internal Desktop Access OUTLOOK OPERATING INSTRUCTIONS (INTERNAL DESKTOP ACCESS) FREQUENTLY ASKED QUESTIONS & ANSWERS Q: How do I check my email while on campus? A: Click
Outlook Operating Instructions Internal Desktop Access OUTLOOK OPERATING INSTRUCTIONS (INTERNAL DESKTOP ACCESS) FREQUENTLY ASKED QUESTIONS & ANSWERS Q: How do I check my email while on campus? A: Click
Welcome to your new ShoreTel 230 voice over IP telephone.
 ShoreTel 230 Table of Contents Preparing for your new phone:... 3 Set up:... 3 Record Multiple Greetings... 4 Retrieving Voice Mail... 5 ShoreTel Call Manager... 6 Call Manager Voice Mail... 8 Call Manager
ShoreTel 230 Table of Contents Preparing for your new phone:... 3 Set up:... 3 Record Multiple Greetings... 4 Retrieving Voice Mail... 5 ShoreTel Call Manager... 6 Call Manager Voice Mail... 8 Call Manager
Stewart Secure Email User Guide. March 13, 2015
 Stewart Secure Email User Guide March 13, 2015 Table of Contents Introduction... 1 What is secure email?... 1 Why secure email?... 1 What is personal, non-public information?... 1 How is my data protected?...
Stewart Secure Email User Guide March 13, 2015 Table of Contents Introduction... 1 What is secure email?... 1 Why secure email?... 1 What is personal, non-public information?... 1 How is my data protected?...
FILING REPRESENTATIVES TRAINING ONLINE COURSE SCHEDULING USER GUIDE
 FILING REPRESENTATIVES TRAINING ONLINE COURSE SCHEDULING USER GUIDE October 18, 2013 Online Course Scheduling User Guide Page 1 of 28 TABLE OF CONTENT 1 ABOUT THIS DOCUMENT... 3 2 REGISTRATION... 4 2.1
FILING REPRESENTATIVES TRAINING ONLINE COURSE SCHEDULING USER GUIDE October 18, 2013 Online Course Scheduling User Guide Page 1 of 28 TABLE OF CONTENT 1 ABOUT THIS DOCUMENT... 3 2 REGISTRATION... 4 2.1
ACS Email Encryption Recipient Guide
 ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
ACS Email Encryption Recipient Guide ACS ENCRYPTION SERVICES / TRAINING AND AWARENESS ACS Email Encryption Recipient Guide Email Encryption Recipient Guide ACS A Xerox Company 2828 North Haskell Dallas,
ADVANCED UNIFIED MESSAGING FEATURES
 ADVANCED UNIFIED MESSAGING FEATURES Information Technology Systems Division Unified Messaging (UM) at UNCW, 2 Installing and Using the Outlook plug-in, 2 Optional Customization of Unified Messaging within
ADVANCED UNIFIED MESSAGING FEATURES Information Technology Systems Division Unified Messaging (UM) at UNCW, 2 Installing and Using the Outlook plug-in, 2 Optional Customization of Unified Messaging within
Secure E-Mail Management Guide. June 2008
 Secure E-Mail Management Guide June 2008 What are Paychex Secure Messages? To enhance the security of client and vendor data, Paychex created the Paychex Secure E-mail Message Center, a Web site hosted
Secure E-Mail Management Guide June 2008 What are Paychex Secure Messages? To enhance the security of client and vendor data, Paychex created the Paychex Secure E-mail Message Center, a Web site hosted
Database Program Instructions
 Database Program Instructions 1) Start your Comparative Rating software by double-clicking the icon on your desktop. 2) Click on the button on the Comparative Rating Software Main Menu. 3) A message Loading
Database Program Instructions 1) Start your Comparative Rating software by double-clicking the icon on your desktop. 2) Click on the button on the Comparative Rating Software Main Menu. 3) A message Loading
Secure Messaging Service
 Human Resources Secure Messaging Service Receiving Secure Emails from West Berkshire Council Table of Contents What are Secure Messaging notifications?... 3 How do I set up my Secure Messaging account?...
Human Resources Secure Messaging Service Receiving Secure Emails from West Berkshire Council Table of Contents What are Secure Messaging notifications?... 3 How do I set up my Secure Messaging account?...
ClicktoFax Service Usage Manual
 ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
Online Employment Application Guide. 1. Find Jobs
 Online Employment Application Guide This guide describes how to apply for jobs using the Ramsey County Job Opportunities web site. When applying for a job, please make note of the application filing deadline
Online Employment Application Guide This guide describes how to apply for jobs using the Ramsey County Job Opportunities web site. When applying for a job, please make note of the application filing deadline
Registering at the Securemail site
 Registering at the Securemail site Before using the Secure Mail service for the first time, you must perform a one-time service registration by completing the following steps. 1. When a Secure Mail is
Registering at the Securemail site Before using the Secure Mail service for the first time, you must perform a one-time service registration by completing the following steps. 1. When a Secure Mail is
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Outlook Web Access. PRECEDED by v\
 Outlook Web Access Logging in to OWA (Outlook Web Access) from Home 1. Login page http://mail.vernonct.org/exchange 2. To avoid these steps each time you login, you can add the login page to your favorites.
Outlook Web Access Logging in to OWA (Outlook Web Access) from Home 1. Login page http://mail.vernonct.org/exchange 2. To avoid these steps each time you login, you can add the login page to your favorites.
Edinburg CISD Technology Department Internet Part 3 Using Microsoft Exchange E-mail
 Edinburg CISD Technology Department Internet Part 3 Using Microsoft Exchange E-mail I. Introductions and Objectives II. III. IV. Acceptable Use Policy & Exhibit C forms Logging in Procedures Exploring
Edinburg CISD Technology Department Internet Part 3 Using Microsoft Exchange E-mail I. Introductions and Objectives II. III. IV. Acceptable Use Policy & Exhibit C forms Logging in Procedures Exploring
Install MSU Google Drive on your Computer
 416 Agriculture Hall Michigan State University 517-355-3776 http://support.anr.msu.edu support@anr.msu.edu Install MSU Google Drive on your Computer Document # - 168 Creation/Revision Date 4/2013 Revision
416 Agriculture Hall Michigan State University 517-355-3776 http://support.anr.msu.edu support@anr.msu.edu Install MSU Google Drive on your Computer Document # - 168 Creation/Revision Date 4/2013 Revision
Direct Mail Training Manual
 Direct Mail Training Manual 9D Revised 4.29.15 HealtheConnections Secure Messaging (Direct Mail) HealtheConnections Secure Messaging is a solution based on the Nationwide Health Information Network (NwHIN)
Direct Mail Training Manual 9D Revised 4.29.15 HealtheConnections Secure Messaging (Direct Mail) HealtheConnections Secure Messaging is a solution based on the Nationwide Health Information Network (NwHIN)
How To Send An Encrypted Email To The State From The Outside (Public)
 Section 1. How to Send an Encrypted E-mail from the Private Network/State Employee The following conditions must be true to send an encrypted e-mail using Proofpoint e-mail encryption: Your State Agency
Section 1. How to Send an Encrypted E-mail from the Private Network/State Employee The following conditions must be true to send an encrypted e-mail using Proofpoint e-mail encryption: Your State Agency
Quick Reference Guide Jabber Calls (Mac)
 Quick Reference Guide Jabber Calls (Mac) Calls You can use Jabber to make and receive phone calls instead of using your desk phone (ie: video phone). When you use Jabber on your computer for calls, your
Quick Reference Guide Jabber Calls (Mac) Calls You can use Jabber to make and receive phone calls instead of using your desk phone (ie: video phone). When you use Jabber on your computer for calls, your
Websense Secure Messaging User Help
 Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
Websense Secure Messaging User Help Welcome to Websense Secure Messaging, a tool that provides a secure portal for the transmission and viewing of sensitive, personal data in email. Use the portal to view
Using Your ShoreTel Phone
 Using Your ShoreTel Phone Placing Calls A. Using the Handset a. To place an internal call, pick up the handset and dial the extension. b. To place an external call, dial 9, then the phone number. c. To
Using Your ShoreTel Phone Placing Calls A. Using the Handset a. To place an internal call, pick up the handset and dial the extension. b. To place an external call, dial 9, then the phone number. c. To
Secure Messaging (Direct) Training Manual
 Secure Messaging (Direct) Training Manual 9D Revised 4.1.14 HealtheConnections Secure Messaging (Direct Mail) HealtheConnections Secure Messaging is a solution based on the Nationwide Health Information
Secure Messaging (Direct) Training Manual 9D Revised 4.1.14 HealtheConnections Secure Messaging (Direct Mail) HealtheConnections Secure Messaging is a solution based on the Nationwide Health Information
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Receiving Secure Email Customer Support frequently asked questions
 Registering a Secure Password Q. Where do I find the current Secure email guidance documentation? A. Published on Glasgow City Council website. Q. My organisation has its own email encryption tool, do
Registering a Secure Password Q. Where do I find the current Secure email guidance documentation? A. Published on Glasgow City Council website. Q. My organisation has its own email encryption tool, do
Outlook Web App McKinney ISD 5/27/2011
 Outlook Web App McKinney ISD 5/27/2011 Outlook Web App Tutorial Outlook Web Access allows you to gain access to your messages, calendars, contacts, tasks and public folders from any computer with internet
Outlook Web App McKinney ISD 5/27/2011 Outlook Web App Tutorial Outlook Web Access allows you to gain access to your messages, calendars, contacts, tasks and public folders from any computer with internet
Receiving Secure Emails
 Receiving Secure Emails This document explains how you can access emails that have been sent to you through CyberArk s Secure Email system in several simple steps. When you receive a secure email, you
Receiving Secure Emails This document explains how you can access emails that have been sent to you through CyberArk s Secure Email system in several simple steps. When you receive a secure email, you
GroupWise Web Access 8.0
 GroupWise Web Access 8.0 How to check your email via the Internet For More Information, please contact: Administrative Office of the Courts Technology Help Desk (615) 532 9503 or (800) 448-7980 Table of
GroupWise Web Access 8.0 How to check your email via the Internet For More Information, please contact: Administrative Office of the Courts Technology Help Desk (615) 532 9503 or (800) 448-7980 Table of
Voice Mail Online User Guide
 Voice Mail Online User Guide Overview Welcome to the online version of SaskTel Voice Mail that is now accessible from any computer with Internet access You can listen to, sort, forward and/or delete your
Voice Mail Online User Guide Overview Welcome to the online version of SaskTel Voice Mail that is now accessible from any computer with Internet access You can listen to, sort, forward and/or delete your
SECURE E-MAIL COMMUNICATIONS PLAN Updated August 25, 2011
 SECURE E-MAIL COMMUNICATIONS PLAN Updated August 25, 2011 Introduction In October, 2008, the Division of Welfare and Supportive Services (DWSS) announced the introduction of secure e-mail through ASM 17-08.
SECURE E-MAIL COMMUNICATIONS PLAN Updated August 25, 2011 Introduction In October, 2008, the Division of Welfare and Supportive Services (DWSS) announced the introduction of secure e-mail through ASM 17-08.
FICOM S SECURE FILE TRANSFER PROTOCOL (SFTP) SITE
 FICOM S SECURE FILE TRANSFER PROTOCOL (SFTP) SITE Frequently Asked Questions FINANCIAL INSTITUTIONS COMMISSION 2800-555 West Hastings Street Vancouver, BC V6B 4N6 P: 604.660.3555 F: 604.660.3365 W: www.fic.gov.bc.ca
FICOM S SECURE FILE TRANSFER PROTOCOL (SFTP) SITE Frequently Asked Questions FINANCIAL INSTITUTIONS COMMISSION 2800-555 West Hastings Street Vancouver, BC V6B 4N6 P: 604.660.3555 F: 604.660.3365 W: www.fic.gov.bc.ca
Trusted Relationships. Sending Invitations. Sending Invitations from Outlook
 Trusted Relationships Establishing Trusted Relationships through the invitation process are core to the Securencrypt security process. This insures that you can only share secure documents with someone
Trusted Relationships Establishing Trusted Relationships through the invitation process are core to the Securencrypt security process. This insures that you can only share secure documents with someone
Microsoft OneDrive. How to login to OneDrive:
 Microsoft OneDrive The beauty of OneDrive is that it is accessible from anywhere you have an Internet connection. You can access it from a Mac or Windows computer. You can even access it on your Smartphone
Microsoft OneDrive The beauty of OneDrive is that it is accessible from anywhere you have an Internet connection. You can access it from a Mac or Windows computer. You can even access it on your Smartphone
Citrus Valley Health Partners. Web Outlook User Guide. Table of Contents
 Citrus Valley Health Partners Web Outlook User Guide Table of Contents Getting Started Page Access to Web Outlook... 1 Log in Instructions... 1 Basic Navigation... 1 The Menu Bar... 1 The Reading Pane...
Citrus Valley Health Partners Web Outlook User Guide Table of Contents Getting Started Page Access to Web Outlook... 1 Log in Instructions... 1 Basic Navigation... 1 The Menu Bar... 1 The Reading Pane...
Surplus Lines Online User Guide
 Surplus Lines Online User Guide Missouri Department of Insurance, Financial Institutions and Professional Registration Contents Summary... 1 Site Address... 1 Account Management... 2 Account Registration...
Surplus Lines Online User Guide Missouri Department of Insurance, Financial Institutions and Professional Registration Contents Summary... 1 Site Address... 1 Account Management... 2 Account Registration...
How to Configure UCO Exchange Email on an Android Device
 Please be aware that every Android device is different, and so your screenshots may not look exactly as shown in this guide. If you have any questions, please contact the IT Service Desk at 405.974.2255.
Please be aware that every Android device is different, and so your screenshots may not look exactly as shown in this guide. If you have any questions, please contact the IT Service Desk at 405.974.2255.
Facilities and Safety How-To Guide: Accessing and Using Your UCF Webmail Account
 Launch Internet Explorer Click on the Internet Explorer icon at the bottom left of the computer screen. Go to the UCF Webmail Website 1. In the address bar at the top of the screen, type webmail.ucf.edu.
Launch Internet Explorer Click on the Internet Explorer icon at the bottom left of the computer screen. Go to the UCF Webmail Website 1. In the address bar at the top of the screen, type webmail.ucf.edu.
FDIC Secure Email Procedures for External Users April 23, 2010
 FDIC Secure Email Procedures for External Users April 23, 2010 This document contains information proprietary to the Federal Deposit Insurance Corporation. Table of Contents 1. Introduction...2 2. Receiving
FDIC Secure Email Procedures for External Users April 23, 2010 This document contains information proprietary to the Federal Deposit Insurance Corporation. Table of Contents 1. Introduction...2 2. Receiving
Why should you participate in the Connect-ED notification system?
 What is Connect-ED? The Connect-ED system is a communication service that enables East Georgia State College (EGSC) administrators and campus safety personnel to quickly contact EGSC students, faculty
What is Connect-ED? The Connect-ED system is a communication service that enables East Georgia State College (EGSC) administrators and campus safety personnel to quickly contact EGSC students, faculty
P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems
 Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
SECURE Email User Guide
 SECURE Email User Guide Receiving SECURE Email from Starion Financial Starion Financial is now offering an enhanced email encryption tool, IronPort PXE, which enables the email communication of sensitive
SECURE Email User Guide Receiving SECURE Email from Starion Financial Starion Financial is now offering an enhanced email encryption tool, IronPort PXE, which enables the email communication of sensitive
How to access your email via Outlook Web Access
 How to access your email via Outlook Web Access 1) Open your internet browser and type in the following address: www.law.miami.edu * Aol users must minimize their browser and use Internet Explorer 6.0+
How to access your email via Outlook Web Access 1) Open your internet browser and type in the following address: www.law.miami.edu * Aol users must minimize their browser and use Internet Explorer 6.0+
Getting Started: Test Administrator. June 2014 6/13/14 1
 Getting Started: Test Administrator June 2014 6/13/14 1 Intentionally Blank 6/13/14 2 Test Administrator Guidance Keystone Exams are state-developed end-of-course assessments. Based upon Chapter 4 regulations,
Getting Started: Test Administrator June 2014 6/13/14 1 Intentionally Blank 6/13/14 2 Test Administrator Guidance Keystone Exams are state-developed end-of-course assessments. Based upon Chapter 4 regulations,
Guidelines For Completing Your Purchase of Intervening or Activated Military Service
 Commonwealth of Pennsylvania - Public School Employees' Retirement System Guidelines For Completing Your Purchase of Intervening or Activated Military Service If you receive or will be eligible to receive
Commonwealth of Pennsylvania - Public School Employees' Retirement System Guidelines For Completing Your Purchase of Intervening or Activated Military Service If you receive or will be eligible to receive
UnitedHealthcare Agent Toolkit QUICK START GUIDE
 UnitedHealthcare Agent Toolkit QUICK START GUIDE NOTE: The Quick Start Guide was created using a UnitedHealth Producers account; however this guide applies to both UnitedHealth Producers and Advisors.
UnitedHealthcare Agent Toolkit QUICK START GUIDE NOTE: The Quick Start Guide was created using a UnitedHealth Producers account; however this guide applies to both UnitedHealth Producers and Advisors.
Algoma District School Board. Microsoft Office 365 Guide
 Algoma District School Board Microsoft Office 365 Guide Table of Contents Accessing Your Office 365 Account... 3 Outlook - Your Office 365 Email Account... 4 Calendar - Your Office 365 Events Calendar...
Algoma District School Board Microsoft Office 365 Guide Table of Contents Accessing Your Office 365 Account... 3 Outlook - Your Office 365 Email Account... 4 Calendar - Your Office 365 Events Calendar...
How to Create a New User Account for MyGovernmentOnline
 How to Create a New User Account for MyGovernmentOnline *Prior to getting started, we encourage you to download and install the web browser Mozilla Firefox. While the MyGovernmentOnline software is designed
How to Create a New User Account for MyGovernmentOnline *Prior to getting started, we encourage you to download and install the web browser Mozilla Firefox. While the MyGovernmentOnline software is designed
Using Internet or Windows Explorer to Upload Your Site
 Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
1. How to Register... 2. 2. Forgot Password... 4. 3. Login to MailTrack Webmail... 5. 4. Accessing MailTrack message Centre... 6
 MailTrack How To Document 27 March 2014 Table of Contents 1. How to Register... 2 2. Forgot Password... 4 3. Login to MailTrack Webmail... 5 4. Accessing MailTrack message Centre... 6 5. Creating a MailTrack
MailTrack How To Document 27 March 2014 Table of Contents 1. How to Register... 2 2. Forgot Password... 4 3. Login to MailTrack Webmail... 5 4. Accessing MailTrack message Centre... 6 5. Creating a MailTrack
THE CHILDREN S HEALTH NETWORK CONTRACTING TOOL TRAINING MANUAL
 THE CHILDREN S HEALTH NETWORK CONTRACTING TOOL TRAINING MANUAL 1 TCHN CONTRACTING TOOL TABLE OF CONTENTS 2 Overview 3 Step by Step Instructions 3 Logging In 4 The Main Menu Options 5 Creating Custom Lists
THE CHILDREN S HEALTH NETWORK CONTRACTING TOOL TRAINING MANUAL 1 TCHN CONTRACTING TOOL TABLE OF CONTENTS 2 Overview 3 Step by Step Instructions 3 Logging In 4 The Main Menu Options 5 Creating Custom Lists
GCSx Email Guide for Internal Users. How to send sensitive business and personal information securely
 GCSx Email Guide for Internal Users How to send sensitive business and personal information securely Document control Description Version V.2 Created May 2013 GCSx Email Guide for Internal Users Status
GCSx Email Guide for Internal Users How to send sensitive business and personal information securely Document control Description Version V.2 Created May 2013 GCSx Email Guide for Internal Users Status
Upon Installation, Soda
 Upon Installation, Soda Prompts you to create your user profile to register for a new profile Note: Asks your for your particulars Prompts you to select a password. You would need to provide this password
Upon Installation, Soda Prompts you to create your user profile to register for a new profile Note: Asks your for your particulars Prompts you to select a password. You would need to provide this password
SchoolMessenger for iphone
 The SchoolMessenger app lets you quickly and easily send messages from anywhere using your iphone. Setting up and using the application is simple. This guide will show you how! [Important: Before you can
The SchoolMessenger app lets you quickly and easily send messages from anywhere using your iphone. Setting up and using the application is simple. This guide will show you how! [Important: Before you can
Voice Mail - Web PhoneManager (WPM) Rev. 8/4/15
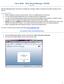 Voice Mail - Web PhoneManager (WPM) Rev. 8/4/15 Web PhoneManager allows subscribers to manage their messages, mailbox recordings, and mailbox settings over the Internet. Important Notes: WPM is available
Voice Mail - Web PhoneManager (WPM) Rev. 8/4/15 Web PhoneManager allows subscribers to manage their messages, mailbox recordings, and mailbox settings over the Internet. Important Notes: WPM is available
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies
 Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
Wakefield Council Secure email and file transfer User guide for customers, partners and agencies The nature of the work the council carries out means that we often deal with information that is sensitive
What to do with: Computer, Files, Phone? When Retire or Resign from Employment
 What to do with: Computer, Files, Phone? When Retire or Resign from Employment 1. Setting Up Out of Office Assistant- Web OUTLOOK CLIENT 2. Assistance with Setting Up Personal Email Address 3. Moving Lockers
What to do with: Computer, Files, Phone? When Retire or Resign from Employment 1. Setting Up Out of Office Assistant- Web OUTLOOK CLIENT 2. Assistance with Setting Up Personal Email Address 3. Moving Lockers
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE
 CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
Olathe District Schools 1 of 11 GroupWise 7
 Olathe District Schools 1 of 11 GroupWise 7 Creating an email group To create and save a personal group: 1. Click on the toolbar. 2. Click the personal address book you want to add this group to. 3. Click
Olathe District Schools 1 of 11 GroupWise 7 Creating an email group To create and save a personal group: 1. Click on the toolbar. 2. Click the personal address book you want to add this group to. 3. Click
External End User Training Guide: Secure Email Extract
 External End User Training Guide: Secure Email Extract Version 6 August 12, 2013 Prepared by 7/29/2013: Kris Chromey, Training Coordinator Michelle Tuscher, Vault Implementation Coordinator Edited for
External End User Training Guide: Secure Email Extract Version 6 August 12, 2013 Prepared by 7/29/2013: Kris Chromey, Training Coordinator Michelle Tuscher, Vault Implementation Coordinator Edited for
MICROSOFT OUTLOOK 2003
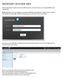 MICROSOFT OUTLOOK 2003 Follow these steps to update an Outlook 2003 account to send and receive e-mail using GCMUNI's new mail settings. Before you start, you must change your temporary GCMUNI e-mail password.
MICROSOFT OUTLOOK 2003 Follow these steps to update an Outlook 2003 account to send and receive e-mail using GCMUNI's new mail settings. Before you start, you must change your temporary GCMUNI e-mail password.
This document provides a brief, end-user overview of the Cisco Registered Envelop Service which has been implemented by Sterne Agee.
 Email Encryption User Guide Sterne Agee is committed to the security of your information. We have implemented Cisco Email Encryption to secure email communication so that only you can open it.* Questions?
Email Encryption User Guide Sterne Agee is committed to the security of your information. We have implemented Cisco Email Encryption to secure email communication so that only you can open it.* Questions?
BankNet Instructions for Large File Transfer. May 20, 2013 Version 1.1
 May 20, 2013 Version 1.1 Table of Contents 1 Introduction... 1 2 Accessing the Secure Large File Transfer Tool... 2 3 Setting Your Email Address for Confirmation Notifications.. 7 4 Uploading a File...
May 20, 2013 Version 1.1 Table of Contents 1 Introduction... 1 2 Accessing the Secure Large File Transfer Tool... 2 3 Setting Your Email Address for Confirmation Notifications.. 7 4 Uploading a File...
Contents. Dianne Harrison Ferro Mesarch
 Georgetown Box Basics Contents What is Georgetown Box?... 2 Claiming Your Georgetown Box Account... 2 Logging into Georgetown Box... 2 Uploading Files... 2 File Version History... 3 Downloading Files...
Georgetown Box Basics Contents What is Georgetown Box?... 2 Claiming Your Georgetown Box Account... 2 Logging into Georgetown Box... 2 Uploading Files... 2 File Version History... 3 Downloading Files...
PPM User Guide Telephone: 0800 988 2020. IP Solutions, Aldermans House, 34-37 Liverpool Street, London, EC2M 3UJ
 Telephone: 0800 988 2020 IP Solutions, Aldermans House, 34-37 Liverpool Street, London, EC2M 3UJ Address: voip.ipsolutions.co.uk This will then take you to the personal phone manager login screen where
Telephone: 0800 988 2020 IP Solutions, Aldermans House, 34-37 Liverpool Street, London, EC2M 3UJ Address: voip.ipsolutions.co.uk This will then take you to the personal phone manager login screen where
