1 Preventing Devices from Connecting to Unsecure Wireless Networks
|
|
|
- Emery Heath
- 8 years ago
- Views:
Transcription
1 ZENworks 11 Endpoint Security Management - Wireless Access Control January 2015 This document provides test scenarios that show you how to use ZENworks Endpoint Security Management to ensure that users, regardless of their location, connect only to secure wireless networks. 1 Preventing Devices from Connecting to Unsecure Wireless Networks As a ZENworks administrator, you want to ensure that your mobile users don t connect to wireless networks that are not secure. The best way to do this is to create a Wi-Fi policy that establishes the minimum level of security (WEP, WPA, or WPA2) that wireless network must provide, and then assign that policy to your Unknown security location. The following steps use predefined policies to create a scenario that shows you how Wi-Fi policies can be used to filter out unsecure wireless networks. The final step helps you assign the appropriate Wi-Fi policy to your Unknown location if you so choose. 1 Import the Location Assignment policy and Wi-Fi policies: 1a Copy the following files to a directory on the ZENworks Primary Server: Location-Assignment.xml Wireless-Minimum-WiFi-Security-WPA.xml Wireless-Minimum-WiFi-Security-WPA2.xml policykey.txt When you click a filename, the file will either be opened, saved, or you will be prompted to open or save it. You need to save the file. If it opens, click File > Save. If you downloaded the Endpoint Security Resource Kit, you can copy the files from the PolicyExamples directory. 1b On the Primary Server, open a command prompt, change to the directory where you copied the files, then run the following commands one at a time, entering your ZENworks administrator username and password when prompted: zman epi "Location Assignment" policykey.txt Location-Assignment.xml zman epi "Wireless - Minimum Wi-Fi Security WPA" policykey.txt Wireless- Minimum-WiFi-Security-WPA.xml zman epi "Wireless - Minimum Wi-Fi Security WPA2" policykey.txt Wireless- Minimum-WiFi-Security-WPA2.xml A message similar to the following is displayed when a policy is successfully imported: Successfully created the object "Location Assignment" in "/Policies". 2 Validate the policy import: 2a In ZENworks Control Center, click Policies to display the Policies list with the three imported policies. ZENworks 11 Endpoint Security Management - Wireless Access Control 1
2 2b Click the Location Assignment policy, then click its Details tab. There are six locations included in the policy: the standard Unknown location and five locations that start with BB_ZESM_ZONE. The BB_ZESM_ZONE locations were imported with the policy and added as locations in your zone. If you go to the Locations page (Configuration > Locations), you will see them listed. For this test scenario, only the Wi-Fi locations are used. The other locations are used with the test scenarios for other policies (VPN and Scripting). The locations do not include any network environments, which means that the only way a device can switch to one of the locations is for the device s user to manually change to the location. For this reason, each location is configured to appear in the Security Locations list (available when right-clicking the ZENworks icon on the device) and to allow the user to manually change to the location. 2c Return to the Policies list. 3 Assign the Location Assignment and Wi-Fi policies to a device that has a wireless network card: 3a In the Policies list, select the check boxes next to the following policies: Location Assignment Wireless - Minimum Wi-Fi Security WPA Wireless - Minimum Wi-Fi Security WPA2 3b Click Action > Assign to Device, then follow the prompts to assign the policies to the appropriate device. When prompted for the policy conflict method, you can leave it set to User Last. 2 ZENworks 11 Endpoint Security Management - Wireless Access Control
3 4 Test the policies on the assigned device: 4a On the device, right-click the ZENworks icon, then click Refresh to retrieve the new policies. 4b When the device finishes refreshing, double-click the ZENworks icon to display the ZENworks Adaptive Agent properties, then click Policies and make sure the Location Assignment, Wireless - Minimum Wi-Fi Security WPA, and Wireless - Minimum Wi-Fi Security WPA2 policies have been successfully applied. 4c Right-click the ZENworks icon > click Security Location > click ~unknown~ to change the device s location to the Unknown location. 4d View your detected wireless networks. The list of wireless networks hopefully includes unsecure, WPA, and WPA2 networks, similar to the following screenshot. ZENworks 11 Endpoint Security Management - Wireless Access Control 3
4 4e Change the security location to the BB_ZESM_ZONE_Wi-Fi Minimum Security WPA location, wait a minute, then view the list of detected wireless networks again. The BB_ZESM_ZONE_Wi-Fi Minimum Security WPA location applies the Wireless - Wi-Fi Minimum Security WPA policy. The policy requires a wireless network to provide a minimum security level of WPA encryption, which results in all unsecured wireless networks being filtered from the list, similar to the following screenshot. 4 ZENworks 11 Endpoint Security Management - Wireless Access Control
5 4f Change the security location to the BB_ZESM_ZONE_Wi-Fi Minimum Security WPA2 location, wait a minute, then view the list of detected wireless networks again. The BB_ZESM_ZONE_Wi-Fi Minimum Security WPA2 location applies the Wireless - Wi-Fi Minimum Security WPA2 policy. The policy requires a wireless network to provide a minimum security level of WPA2 encryption, which results in all unsecured wireless networks being filtered from the list. The WPA wireless networks are not filtered from the list because differentiation between WPA and WPA2 isn t made until the device attempts to ZENworks 11 Endpoint Security Management - Wireless Access Control 5
6 connect to the wireless network. At that point, if the security level is WPA, the connection fails and the wireless network disappears from the list, leaving only the WPA2 secured networks. 5 To assign a Wi-Fi policy to your Unknown location in order to enforce a minimum security level in that location: 5a In ZENworks Control Center, click Policies to display the Policies list. 5b If you want to use WPA as the minimum security level, click the Wireless - Minimum Wi-Fi Security WPA policy, then click Details. or If you want to use WPA2 as the minimum security level, click the Wireless - Minimum Wi-Fi Security WPA2 policy, then click the Details tab. 5c On the Details page, do the following: 5c1 In the Location Assignments panel, remove the locations used for the scenario and add the Unknown location. 5c2 In the Minimum Security Level section, modify the message if desired. 5c3 Click Apply to save your changes. 5d Click the Relationships tab and assign the policy to the devices and users you want it to apply to. 6 ZENworks 11 Endpoint Security Management - Wireless Access Control
7 5e Close the Wi-Fi policy. 5f Make sure that the users and devices you assigned the Wi-Fi policy to also have a Location Assignment policy assigned to them that includes the Unknown location. 2 Allowing Access to Approved Wireless Network Access Points (SSIDs) Only As a ZENworks administrator, you want to ensure that users at work only connect to your corporate wireless network and that all other wireless networks are disallowed. The following steps help you import a predefined W-Fi policy and Location Assignment policy that limits wireless network access to two approved Access Points (SSIDs) when the device in a Work location. 1 Import the Wi-Fi policy and Location Assignment policy: 1a Copy the following files to a directory on the ZENworks Primary Server: Location-Assignment.xml Wireless-Work-WiFi-SSID-Filtering.xml policykey.txt When you click a filename, the file will either be opened, saved, or you will be prompted to open or save it. You need to save the file. If it opens, click File > Save. If you downloaded the Endpoint Security Resource Kit, you can copy the files from the PolicyExamples directory. 1b On the Primary Server, open a command prompt, change to the directory where you copied the files, then run the following command, entering your ZENworks administrator username and password when prompted: zman epi "Wireless - Work Wi-Fi SSID Filtering" policykey.txt Wireless- Work-WiFi-SSID-Filtering.xml The following message is displayed if the policy is successfully imported: Successfully created the object "Wireless - Work Wi-Fi SSID Filtering" in "/Policies". 1c If you completed the Preventing Devices from Connecting to Unsecure Wireless Networks scenario, you can skip this step. Otherwise, run the following command to import the Location Assignment policy, entering your ZENworks administrator username and password when prompted: zman epi "Location Assignment" policykey.txt Location-Assignment.xml The following message is displayed if the policy is successfully imported: Successfully created the object "Location Assignment" in "/Policies". 2 Validate the policy import: 2a In ZENworks Control Center, click Policies to display the Policies list with the two imported policies. ZENworks 11 Endpoint Security Management - Wireless Access Control 7
8 2b Click the Location Assignment policy, then click its Details tab. There are six locations included in the policy: the standard Unknown location and five locations that start with BB_ZESM_ZONE. The BB_ZESM_ZONE locations were imported with the policy and added as locations in your zone. If you go to the Locations page (Configuration > Locations), you will see them listed. For this test scenario, only the Work location is used. The other locations are used with the test scenarios for other policies (VPN and Scripting). The Work location does not include any network environments, which means that the only way a device can switch to the location is for the device s user to manually change to the location. For this reason, the location is configured to appear in the Security Locations list (available when right-clicking the ZENworks icon on the device) and to allow the user to manually change to the location. 2c Return to the Policies list. 3 Modify the Wireless - Work Wi-Fi SSID Filtering policy to add the SSIDs for your Work location: 3a Click the Wireless - Work Wi-Fi SSID Filtering policy, then click its Details tab. The Access Points list is used to explicitly approve (whitelist) or prohibit (blacklist) Access Point SSIDs. If the list doesn t include any Access Points, all Access Points are approved. As soon as one Access Point is added, the list becomes an explicit list and only explicitly approved Access Points are allowed. In the Wireless - Work Wi-Fi SSID Filtering policy you imported, there are two explicitly approved (whitelisted) Access Points, which means that all other Access Points are prohibited. 8 ZENworks 11 Endpoint Security Management - Wireless Access Control
9 3b Edit the list to define real Access Points for your Work location, referring to the sample entries as needed. Add only the Access Points you want to allow users to connect to in that location. 3c Click Apply to save your changes. 3d Click Publish to publish the changed policy. 4 Assign the two policies to a device that has a wireless network card: 4a In the Policies list, select the check boxes next to the following policies: Location Assignment Wireless - Work Wi-Fi SSID Filtering 4b Click Action > Assign to Device, then follow the prompts to assign the policies to the appropriate device. When prompted for the policy conflict method, you can leave it set to User Last. 5 Test the policies on the assigned device: 5a On the device, right-click the ZENworks icon, then click Refresh to retrieve the new policies. 5b When the device finishes refreshing, double-click the ZENworks icon to display the ZENworks Adaptive Agent properties, then click Policies and make sure the Location Assignment and Wireless - Work Wi-Fi SSID Filtering policies have been successfully applied. 5c Right-click the ZENworks icon > click Security Location > click ~unknown~ to change the device s location to the Unknown location. ZENworks 11 Endpoint Security Management - Wireless Access Control 9
10 5d View your detected wireless networks. The list of wireless networks hopefully includes multiple networks, similar to the following screenshot. 5e Change the security location to the BB_ZESM_ZONE_Work Location, wait a minute, then view the list of detected wireless networks again. 10 ZENworks 11 Endpoint Security Management - Wireless Access Control
11 The BB_ZESM_ZONE_Work Location applies the Wireless - Work Wi-Fi SSID Filtering policy. The policy allows only those wireless networks you explicitly whitelisted through their Access Point SSIDs. This results in all non-approved wireless networks being filtered from the list, similar to the following screenshot. ZENworks 11 Endpoint Security Management - Wireless Access Control 11
1 Disabling Access to USB Mass Storage Devices
 ZENworks 11 Endpoint Security Management - USB Device Control January 20154 This document provides test scenarios that show you how to use ZENworks Endpoint Security Management to control users access
ZENworks 11 Endpoint Security Management - USB Device Control January 20154 This document provides test scenarios that show you how to use ZENworks Endpoint Security Management to control users access
MANUAL FOR CONNECTING TO VIVACOM NET WI-FI NETWORK HIDDEN ENCRYPTED WI-FI NETWORK
 VIVACOM NET WI-FI NETWORK HIDDEN ENCRYPTED WI-FI NETWORK Instructions for users of ASUS EeePC с Linux Before you go through the steps in this manual, make sure to press the «submit» button in http://my.contact.bg
VIVACOM NET WI-FI NETWORK HIDDEN ENCRYPTED WI-FI NETWORK Instructions for users of ASUS EeePC с Linux Before you go through the steps in this manual, make sure to press the «submit» button in http://my.contact.bg
1. Open your Internet Browser and enter http://192.168.1.254. 2. You will be prompted to enter a username and password.
 Connect to your Thomson modem. It is recommended that you connect your computer to your Thomson modem via an Ethernet cable. This guarantees maintainability of connection to modem and prevents loss of
Connect to your Thomson modem. It is recommended that you connect your computer to your Thomson modem via an Ethernet cable. This guarantees maintainability of connection to modem and prevents loss of
Using Microsoft Vista and Windows XP to Manage Wireless Network Connections
 Application Note Using Microsoft Vista and Windows XP to Manage Wireless Network Connections Summary This document explains how to use Microsoft Vista and Windows XP (SP2 and SP 1) to join a wireless network
Application Note Using Microsoft Vista and Windows XP to Manage Wireless Network Connections Summary This document explains how to use Microsoft Vista and Windows XP (SP2 and SP 1) to join a wireless network
How to connect to VUWiFi
 Wireless Registration Instructions Windows XP How to connect to VUWiFi 1. The first step in setting up your wireless card for VUWiFi is to open your Network Connections window. You can find this by going
Wireless Registration Instructions Windows XP How to connect to VUWiFi 1. The first step in setting up your wireless card for VUWiFi is to open your Network Connections window. You can find this by going
Installation Guides - Information required for connection to the Goldfields Institute s (GIT) Wireless Network
 Installation Guides - Information required for connection to the Goldfields Institute s (GIT) Wireless Network Wireless Network Names and Credentials There are two wireless networks operating at the Goldfields
Installation Guides - Information required for connection to the Goldfields Institute s (GIT) Wireless Network Wireless Network Names and Credentials There are two wireless networks operating at the Goldfields
Connecting to Wireless in Windows Vista
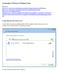 Connecting to Wireless in Windows Vista Reference: http://www.microsoft.com/technet/community/columns/cableguy/cg0406.mspx http://www.microsoft.com/technet/network/evaluate/hiddennet.mspx http://www.csd.toshiba.com/cgibin/tais/su/su_sc_dtlview.jsp?soid=1524510&moid=null&bv_sessionid=@@@@0175
Connecting to Wireless in Windows Vista Reference: http://www.microsoft.com/technet/community/columns/cableguy/cg0406.mspx http://www.microsoft.com/technet/network/evaluate/hiddennet.mspx http://www.csd.toshiba.com/cgibin/tais/su/su_sc_dtlview.jsp?soid=1524510&moid=null&bv_sessionid=@@@@0175
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail
 Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18
 Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
SATO Network Interface Card Configuration Instructions
 SATO Network Interface Card Configuration Instructions Table of Contents 1. Reset of wired/wireless interface card... 3 2. Installing the All-In-One Utility (recommended)... 4 3. Configuring wired/wireless
SATO Network Interface Card Configuration Instructions Table of Contents 1. Reset of wired/wireless interface card... 3 2. Installing the All-In-One Utility (recommended)... 4 3. Configuring wired/wireless
eduroam wireless setup guide for Windows 7, XP and Vista
 Information Technology Services eduroam wireless setup guide for Windows 7, XP and Vista Configuring Windows to connect to the eduroam wireless network June 2011 Introduction This document describes how
Information Technology Services eduroam wireless setup guide for Windows 7, XP and Vista Configuring Windows to connect to the eduroam wireless network June 2011 Introduction This document describes how
Connecting to UNOSECURE using Windows 7
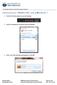 Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall:
 How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
Deploying BitDefender Client Security and BitDefender Windows Server Solutions
 Deploying BitDefender Client Security and BitDefender Windows Server Solutions Quick Install Guide Copyright 2010 BitDefender; 1. Installation Overview Thank you for selecting BitDefender Business Solutions
Deploying BitDefender Client Security and BitDefender Windows Server Solutions Quick Install Guide Copyright 2010 BitDefender; 1. Installation Overview Thank you for selecting BitDefender Business Solutions
Instructions for accessing the new TU wireless Network
 Instructions for accessing the new TU wireless Network These instructions are meant for University owned systems directly supported by ENS Computer Services. Users of other systems may find this document
Instructions for accessing the new TU wireless Network These instructions are meant for University owned systems directly supported by ENS Computer Services. Users of other systems may find this document
1. Installation Overview
 Quick Install Guide 1. Installation Overview Thank you for selecting Bitdefender Business Solutions to protect your business. This document enables you to quickly get started with the installation of Bitdefender
Quick Install Guide 1. Installation Overview Thank you for selecting Bitdefender Business Solutions to protect your business. This document enables you to quickly get started with the installation of Bitdefender
Connecting to Secure Wireless (iitk-sec) on Fedora
 Connecting to Secure Wireless (iitk-sec) on Fedora Go to System Preferences Network Connections. Click on Wireless tab and then Add button. Check Connect automatically and Available to all users. Set SSID
Connecting to Secure Wireless (iitk-sec) on Fedora Go to System Preferences Network Connections. Click on Wireless tab and then Add button. Check Connect automatically and Available to all users. Set SSID
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops
 Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops A wireless network for Students to use with their personal laptops, is available throughout campus with the SSID NCC-STUDENT. This network
Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops A wireless network for Students to use with their personal laptops, is available throughout campus with the SSID NCC-STUDENT. This network
Montefiore Portal Quick Reference Guide
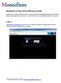 Montefiore Portal Quick Reference Guide Montefiore s remote portal allows users to securely access Windows applications, file shares, internal web applications, and more. To use the Portal, you must already
Montefiore Portal Quick Reference Guide Montefiore s remote portal allows users to securely access Windows applications, file shares, internal web applications, and more. To use the Portal, you must already
What is a Home Network? A home network is a collection of two or more home computers connected together through a wired or wireless connection.
 Building A Home Network What is a Home Network? A home network is a collection of two or more home computers connected together through a wired or wireless connection. Why should I network my computers
Building A Home Network What is a Home Network? A home network is a collection of two or more home computers connected together through a wired or wireless connection. Why should I network my computers
Instructions for connecting to winthropsecure. Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530
 SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
Installation Overview
 Contents Installation Overview... 2 How to Install Ad-Aware Management Server... 3 How to Deploy the Ad-Aware Security Solutions... 5 General Deployment Conditions... 5 Deploying Ad-Aware Management Agent...
Contents Installation Overview... 2 How to Install Ad-Aware Management Server... 3 How to Deploy the Ad-Aware Security Solutions... 5 General Deployment Conditions... 5 Deploying Ad-Aware Management Agent...
Deploying BitDefender Client Security and BitDefender Windows Server Solutions
 Deploying BitDefender Client Security and BitDefender Windows Server Solutions Quick Install Guide Copyright 2011 BitDefender 1. Installation Overview Thank you for selecting BitDefender Business Solutions
Deploying BitDefender Client Security and BitDefender Windows Server Solutions Quick Install Guide Copyright 2011 BitDefender 1. Installation Overview Thank you for selecting BitDefender Business Solutions
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows 7 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows 7 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
educ Office 365 email: Remove & create new Outlook profile
 Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
MyNetFone Virtual Fax. Virtual Fax Installation
 Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Configuring Windows 2000/XP IPsec for Site-to-Site VPN
 IPsec for Site-to-Site VPN November 2002 Copyright 2002 SofaWare Technologies Inc, All Rights Reserved. Reproduction, adaptation, or translation with prior written permission is prohibited except as allowed
IPsec for Site-to-Site VPN November 2002 Copyright 2002 SofaWare Technologies Inc, All Rights Reserved. Reproduction, adaptation, or translation with prior written permission is prohibited except as allowed
How to connect to the diamonds wireless network with Vista.
 How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
User Manual. Onsight Management Suite Version 5.1. Another Innovation by Librestream
 User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
User Manual Onsight Management Suite Version 5.1 Another Innovation by Librestream Doc #: 400075-06 May 2012 Information in this document is subject to change without notice. Reproduction in any manner
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure & Ad Hoc Networks Mac OS X 10.5-10.6 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure & Ad Hoc Networks Mac OS X 10.5-10.6 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without
Setting up a WiFi Network (WLAN)
 Setting up a WiFi Network (WLAN) How to set up Wi-Fi on your Huawei E960 InZone Step 1: In the address field on your internet browser, type http://192.168.1.1/ Step 2: Type admin into the Password box
Setting up a WiFi Network (WLAN) How to set up Wi-Fi on your Huawei E960 InZone Step 1: In the address field on your internet browser, type http://192.168.1.1/ Step 2: Type admin into the Password box
Android App User Guide
 www.novell.com/documentation Android App User Guide ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
www.novell.com/documentation Android App User Guide ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
CruzNet Secure Set-Up Instructions for Windows Vista
 CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
HUAWEI HG256s. Home Gateway Quick Start
 HUAWEI HG256s Home Gateway Quick Start 1 Introduction The Front Panel of the HG256s The front panel of the HG256s provides the following indicators: One power indicator: POWER One Internet indicator: INTERNET
HUAWEI HG256s Home Gateway Quick Start 1 Introduction The Front Panel of the HG256s The front panel of the HG256s provides the following indicators: One power indicator: POWER One Internet indicator: INTERNET
WIRELESS SETUP FOR WINDOWS 7
 Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
Novell ZENworks 10 Configuration Management SP3
 AUTHORIZED DOCUMENTATION Software Distribution Reference Novell ZENworks 10 Configuration Management SP3 10.3 November 17, 2011 www.novell.com Legal Notices Novell, Inc., makes no representations or warranties
AUTHORIZED DOCUMENTATION Software Distribution Reference Novell ZENworks 10 Configuration Management SP3 10.3 November 17, 2011 www.novell.com Legal Notices Novell, Inc., makes no representations or warranties
VPN: Virtual Private Network Setup Instructions
 VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
Managing Identities and Admin Access
 CHAPTER 4 This chapter describes how Cisco Identity Services Engine (ISE) manages its network identities and access to its resources using role-based access control policies, permissions, and settings.
CHAPTER 4 This chapter describes how Cisco Identity Services Engine (ISE) manages its network identities and access to its resources using role-based access control policies, permissions, and settings.
Configuring Your Network s Security
 Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
Configuring Your Network s Security Security is an important issue when using a wireless home network. Because radio waves are used to transfer information between your networked computers, it's possible
How to Turn a Laptop into a Wireless Hot Spot (Microsoft Windows XP)
 How to Turn a Laptop into a Wireless Hot Spot (Microsoft Windows XP) Internet This tutorial will explain how to convert a laptop's wireless network adapter into a wireless hot spot. The first time the
How to Turn a Laptop into a Wireless Hot Spot (Microsoft Windows XP) Internet This tutorial will explain how to convert a laptop's wireless network adapter into a wireless hot spot. The first time the
Create, Link, or Edit a GPO with Active Directory Users and Computers
 How to Edit Local Computer Policy Settings To edit the local computer policy settings, you must be a local computer administrator or a member of the Domain Admins or Enterprise Admins groups. 1. Add the
How to Edit Local Computer Policy Settings To edit the local computer policy settings, you must be a local computer administrator or a member of the Domain Admins or Enterprise Admins groups. 1. Add the
How to Configure Outlook 2010 E-mail Client for Exchange
 LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students.
 Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services a...
 1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
Remote Access Services Apple Macintosh - Installation Guide
 Remote Access Services Apple Macintosh - Installation Guide Version. February, 05 P age Contents GETTING STARTED... JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... Checking Mac OS version... Java
Remote Access Services Apple Macintosh - Installation Guide Version. February, 05 P age Contents GETTING STARTED... JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... Checking Mac OS version... Java
Unity Application Suite SQL Server Database Integration
 Unity Application Suite SQL Server Database Integration 1.0 Introduction This document outlines the steps required to integrate the Unity Client with a Microsoft SQL Server database. Unity Integrates with
Unity Application Suite SQL Server Database Integration 1.0 Introduction This document outlines the steps required to integrate the Unity Client with a Microsoft SQL Server database. Unity Integrates with
The back story of our Wireless (reading will help you understand what is going on in the building):
 Wireless Network The back story of our Wireless (reading will help you understand what is going on in the building): At Robeson we have a non-broadcasting wireless network. This means that if you are using
Wireless Network The back story of our Wireless (reading will help you understand what is going on in the building): At Robeson we have a non-broadcasting wireless network. This means that if you are using
HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA. Installation
 HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
HI-SPEED INTERNET USER GUIDE
 HI-SPEED INTERNET USER GUIDE Connecting to a Wireless Network (Wi-Fi) 2012-10 VERSION 1-800-360-8555 TABLE OF CONTENTS 4. Connecting to a Wireless Network (Wi-Fi)...3 Before you connect to a wireless network...3
HI-SPEED INTERNET USER GUIDE Connecting to a Wireless Network (Wi-Fi) 2012-10 VERSION 1-800-360-8555 TABLE OF CONTENTS 4. Connecting to a Wireless Network (Wi-Fi)...3 Before you connect to a wireless network...3
WiFi Internet Access. Windows XP Setup Instructions. Please Return After Use. Produced Oct 2010
 WiFi Internet Access Windows XP Setup Instructions Produced Oct 2010 Please Return After Use About the Janet Roaming Service The University of Plymouth provides an infrastructure for guest users to use
WiFi Internet Access Windows XP Setup Instructions Produced Oct 2010 Please Return After Use About the Janet Roaming Service The University of Plymouth provides an infrastructure for guest users to use
Windows Clients and GoPrint Print Queues
 Windows Clients and GoPrint Print Queues Overview The following tasks demonstrate how to configure shared network printers on Windows client machines in a Windows Active Directory Domain and Workgroup
Windows Clients and GoPrint Print Queues Overview The following tasks demonstrate how to configure shared network printers on Windows client machines in a Windows Active Directory Domain and Workgroup
ACTIVE DIRECTORY DEPLOYMENT
 ACTIVE DIRECTORY DEPLOYMENT CASAS Technical Support 800.255.1036 2009 Comprehensive Adult Student Assessment Systems. All rights reserved. Version 031809 CONTENTS 1. INTRODUCTION... 1 1.1 LAN PREREQUISITES...
ACTIVE DIRECTORY DEPLOYMENT CASAS Technical Support 800.255.1036 2009 Comprehensive Adult Student Assessment Systems. All rights reserved. Version 031809 CONTENTS 1. INTRODUCTION... 1 1.1 LAN PREREQUISITES...
Instructions for Accessing the Advanced Computing Facility Supercomputing Cluster at the University of Kansas
 ACF Supercomputer Access Instructions 1 Instructions for Accessing the Advanced Computing Facility Supercomputing Cluster at the University of Kansas ACF Supercomputer Access Instructions 2 Contents Instructions
ACF Supercomputer Access Instructions 1 Instructions for Accessing the Advanced Computing Facility Supercomputing Cluster at the University of Kansas ACF Supercomputer Access Instructions 2 Contents Instructions
1. Download VPN client software for Macintosh (Note: You must be connected to the campus network to perform this step.)
 North Carolina Agricultural and Technical State University Division of Information Technology (DoIT) VPN Client Installation & Configuration Guide for Macintosh Note: A VPN is a secure method for employees
North Carolina Agricultural and Technical State University Division of Information Technology (DoIT) VPN Client Installation & Configuration Guide for Macintosh Note: A VPN is a secure method for employees
Configuring the wireless security of your Linksys Wireless-N router through the web-based setup page
 Contents Configuring the wireless security of your Linksys Wireless-N router through the web-based setup page.. 2 Checking the Linksys router s wireless settings through the web-based setup page and adding
Contents Configuring the wireless security of your Linksys Wireless-N router through the web-based setup page.. 2 Checking the Linksys router s wireless settings through the web-based setup page and adding
AeroLab Wireless Network Code of Conduct. Connecting to the AeroLab Wireless Network
 AeroLab Wireless Network Code of Conduct The AeroLab wireless network is intended for academic use only. Any use of the wireless network for BitTorrent or other Peer-to-Peer file sharing is strictly prohibited.
AeroLab Wireless Network Code of Conduct The AeroLab wireless network is intended for academic use only. Any use of the wireless network for BitTorrent or other Peer-to-Peer file sharing is strictly prohibited.
Global VPN Client Getting Started Guide
 Global VPN Client Getting Started Guide PROTECTION AT THE SPEED OF BUSINESS Introduction The SonicWALL Global VPN Client creates a Virtual Private Network (VPN) connection between your computer and the
Global VPN Client Getting Started Guide PROTECTION AT THE SPEED OF BUSINESS Introduction The SonicWALL Global VPN Client creates a Virtual Private Network (VPN) connection between your computer and the
STEP III: Enable the Wireless Network Card. STEP IV: Print out the Printer Settings pages to determine the IP Address
 Title: How do I configure the wireless printer without a network cable and install the printer driver in Windows? NOTE: For successful wireless setup, you MUST know your network security settings. STEP
Title: How do I configure the wireless printer without a network cable and install the printer driver in Windows? NOTE: For successful wireless setup, you MUST know your network security settings. STEP
Setting up a SQ20xx WIFI and Laptop for a Peer-to-peer (Ad-hoc) connection
 Setting up a SQ20xx WIFI and Laptop for a Peer-to-peer (Ad-hoc) connection Setting up the logger for a Peer-to-peer (Ad-hoc) connection The SQ20xx WIFI needs to be powered by an external supply. Connect
Setting up a SQ20xx WIFI and Laptop for a Peer-to-peer (Ad-hoc) connection Setting up the logger for a Peer-to-peer (Ad-hoc) connection The SQ20xx WIFI needs to be powered by an external supply. Connect
Towson University s VPN Virtual Private Network
 Towson University s VPN Virtual Private Network OTS PUBLICATION: VPN01 REVISED 11-25-2008 TRAINING@TOWSON.EDU OFFICE OF TECHNOLOGY SERVICES =Shortcut =Advice =Caution Introduction When connecting through
Towson University s VPN Virtual Private Network OTS PUBLICATION: VPN01 REVISED 11-25-2008 TRAINING@TOWSON.EDU OFFICE OF TECHNOLOGY SERVICES =Shortcut =Advice =Caution Introduction When connecting through
How to setup a VPN on Windows XP in Safari.
 How to setup a VPN on Windows XP in Safari. If you want to configure a VPN connection from a Windows XP client computer you only need what comes with the Operating System itself, it's all built right in.
How to setup a VPN on Windows XP in Safari. If you want to configure a VPN connection from a Windows XP client computer you only need what comes with the Operating System itself, it's all built right in.
Android App Release Notes
 www.novell.com/documentation Android App Release Notes ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
www.novell.com/documentation Android App Release Notes ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
Configuration for Microsoft Windows 7 Enterprise Edition
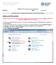 NMMU VPN Configuration Guidelines Revision: 1 Date: 4 May 2010 Setting up the VPN connection Configuration for Microsoft Windows 7 Enterprise Edition Before starting with the VPN connection setup, please
NMMU VPN Configuration Guidelines Revision: 1 Date: 4 May 2010 Setting up the VPN connection Configuration for Microsoft Windows 7 Enterprise Edition Before starting with the VPN connection setup, please
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website
 Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Networking. General networking. Networking overview. Common home network configurations. Wired network example. Wireless network examples
 Networking General networking Networking overview A network is a collection of devices such as computers, printers, Ethernet hubs, wireless access points, and routers connected together for communication
Networking General networking Networking overview A network is a collection of devices such as computers, printers, Ethernet hubs, wireless access points, and routers connected together for communication
Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops
 Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops A wireless network for Faculty and Staff to use with their personal laptops, is available throughout campus with
Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops A wireless network for Faculty and Staff to use with their personal laptops, is available throughout campus with
Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet)
 Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet) What is WPA (Wi-Fi Protected Access)? WPA is a powerful, standards-based, interoperable security technology
Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet) What is WPA (Wi-Fi Protected Access)? WPA is a powerful, standards-based, interoperable security technology
Remote Access - Mac OS X
 Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Ad Hoc Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited. 1
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Ad Hoc Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited. 1
Step-by-Step Setup Guide Wireless File Transmitter FTP Mode
 EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
EOS Step-by-Step Setup Guide Wireless File Transmitter FTP Mode Infrastructure Setup Windows XP 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in whole or in part without permission is prohibited.
Mac OS X Secure Wireless Setup Guide
 Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
TECH BULLETIN NETGEN1 DOOR CONTROLLER WI-FI NETWORK CONFIG
 TECH BULLETIN NETGEN1 DOOR CONTROLLER WI-FI NETWORK CONFIG February 12, 2008 The factory default network configuration for BlueWave Security s Wi-Fi NetGen1 door controllers is a dynamic DHCP IP address,
TECH BULLETIN NETGEN1 DOOR CONTROLLER WI-FI NETWORK CONFIG February 12, 2008 The factory default network configuration for BlueWave Security s Wi-Fi NetGen1 door controllers is a dynamic DHCP IP address,
ECA IIS Instructions. January 2005
 ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
ECA IIS Instructions January 2005 THIS PAGE INTENTIONALLY BLANK ECA IIS Instructions ii July 22, 2005 Table of Contents 1. Install Certificate in IIS 5.0... 1 2. Obtain and Install the ECA Root Certificate
Step-by-Step Setup Guide Wireless File Transmitter
 EOS Step-by-Step Setup Guide Wireless File Transmitter EOS UTility Mode Infrastructure or Ad Hoc Networks Windows XP / Windows 7 Professional 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in
EOS Step-by-Step Setup Guide Wireless File Transmitter EOS UTility Mode Infrastructure or Ad Hoc Networks Windows XP / Windows 7 Professional 2012 Canon U.S.A., Inc. All Rights Reserved. Reproduction in
Eduroam wireless network Windows Vista
 Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Canterbury College Eduroam Wi-Fi Guide
 Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Connecting to the University Wireless Network
 Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
RSC-Secure-Wireless provides...
 RSC-Secure-Wireless provides... Security: RSC-Secure-Wireless provides a layer of encryption for added security. Convenience: You don't have to type in your username and password each time you connect.
RSC-Secure-Wireless provides... Security: RSC-Secure-Wireless provides a layer of encryption for added security. Convenience: You don't have to type in your username and password each time you connect.
How to Connect to UAB s Wireless Networks
 How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
Administration Quick Start
 www.novell.com/documentation Administration Quick Start ZENworks 11 Support Pack 3 February 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
www.novell.com/documentation Administration Quick Start ZENworks 11 Support Pack 3 February 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of
Installing the VPN Client for Microsoft Windows OS
 Installing the VPN Client for Microsoft Windows OS 1. Go to the VPN Information Center web site and click on the Cisco VPN Client for Microsoft Windows OS link. 2. A File Download window will appear. Click
Installing the VPN Client for Microsoft Windows OS 1. Go to the VPN Information Center web site and click on the Cisco VPN Client for Microsoft Windows OS link. 2. A File Download window will appear. Click
Palomar College Dial-up Remote Access
 Palomar College Dial-up Remote Access Instructions for Windows 95/98 and Windows 2000 Following are instructions to implement dialup access to the Palomar College network, email and Internet. The minimum
Palomar College Dial-up Remote Access Instructions for Windows 95/98 and Windows 2000 Following are instructions to implement dialup access to the Palomar College network, email and Internet. The minimum
GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios Devices
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios Devices GO!Enterprise MDM for ios Devices, Version 3.x GO!Enterprise MDM for ios Devices 1 Table of Contents GO!Enterprise
GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios Devices GO!Enterprise MDM for ios Devices, Version 3.x GO!Enterprise MDM for ios Devices 1 Table of Contents GO!Enterprise
WatchGuard Mobile User VPN Guide
 WatchGuard Mobile User VPN Guide Mobile User VPN establishes a secure connection between an unsecured remote host and a protected network over an unsecured network using Internet Protocol Security (IPSec).
WatchGuard Mobile User VPN Guide Mobile User VPN establishes a secure connection between an unsecured remote host and a protected network over an unsecured network using Internet Protocol Security (IPSec).
ZENworks Adaptive Agent Reference
 www.novell.com/documentation ZENworks Adaptive Agent Reference ZENworks 11 Support Pack 2 March 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
www.novell.com/documentation ZENworks Adaptive Agent Reference ZENworks 11 Support Pack 2 March 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use
How do I find the Wireless Security Information in Windows XP, Vista, 7, 8 or 8.1?
 Description of Problem 100000025093 How do I find the Wireless Security Information in Windows XP, Vista, 7, 8 or 8.1? Description of Solution 200000032138 These steps may help you locate your wireless
Description of Problem 100000025093 How do I find the Wireless Security Information in Windows XP, Vista, 7, 8 or 8.1? Description of Solution 200000032138 These steps may help you locate your wireless
Email Migration Manual (For Outlook 2010)
 Email Migration Manual (For Outlook 2010) By SYSCOM (USA) May 13, 2013 Version 2.2 1 Contents 1. How to Change POP3/SMTP Setting for Outlook 2010... 3 2. How to Login to Webmail... 10 3. How to Change
Email Migration Manual (For Outlook 2010) By SYSCOM (USA) May 13, 2013 Version 2.2 1 Contents 1. How to Change POP3/SMTP Setting for Outlook 2010... 3 2. How to Login to Webmail... 10 3. How to Change
How to Access Coast Wi-Fi
 How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
SSL VPN Setup for Windows
 SSL VPN Setup for Windows SSL VPN allows you to connect from off campus to access campus resources such as Outlook email client, file sharing and remote desktop. These instructions will guide you through
SSL VPN Setup for Windows SSL VPN allows you to connect from off campus to access campus resources such as Outlook email client, file sharing and remote desktop. These instructions will guide you through
Installing the ASP.NET VETtrak APIs onto IIS 5 or 6
 Installing the ASP.NET VETtrak APIs onto IIS 5 or 6 2 Installing the ASP.NET VETtrak APIs onto IIS 5 or 6 3... 3 IIS 5 or 6 1 Step 1- Install/Check 6 Set Up and Configure VETtrak ASP.NET API 2 Step 2 -...
Installing the ASP.NET VETtrak APIs onto IIS 5 or 6 2 Installing the ASP.NET VETtrak APIs onto IIS 5 or 6 3... 3 IIS 5 or 6 1 Step 1- Install/Check 6 Set Up and Configure VETtrak ASP.NET API 2 Step 2 -...
Basic Exchange Setup Guide
 Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
Basic Exchange Setup Guide The following document and screenshots are provided for a single Microsoft Exchange Small Business Server 2003 or Exchange Server 2007 setup. These instructions are not provided
D-Link DAP-1360 Repeater Mode Configuration
 D-Link DAP-1360 Repeater Mode Configuration Outline 1. Package Contents 2. System Requirements 3. Hardware Overview Connections LED s WPS LED/Button 4. Default Settings 5. Configuring your LAN Adapter
D-Link DAP-1360 Repeater Mode Configuration Outline 1. Package Contents 2. System Requirements 3. Hardware Overview Connections LED s WPS LED/Button 4. Default Settings 5. Configuring your LAN Adapter
If you have questions or find errors in the guide, please, contact us under the following e-mail address:
 1. Introduction... 2 2. Remote Access via PPTP... 2 2.1. Configuration of the Astaro Security Gateway... 3 2.2. Configuration of the Remote Client...10 2.2.1. Astaro User Portal: Getting Configuration
1. Introduction... 2 2. Remote Access via PPTP... 2 2.1. Configuration of the Astaro Security Gateway... 3 2.2. Configuration of the Remote Client...10 2.2.1. Astaro User Portal: Getting Configuration
Frequently Asked Questions
 Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
WiFi troubleshooting. How s your WiFi signal? Android WiFi settings. ios WiFi settings
 1 WiFi troubleshooting How s your WiFi signal? If your connection appears to keep dropping off: check in your WiFi settings that you added @kent.ac.uk to your username, and entered your password correctly.
1 WiFi troubleshooting How s your WiFi signal? If your connection appears to keep dropping off: check in your WiFi settings that you added @kent.ac.uk to your username, and entered your password correctly.
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP with Service Pack 2 Your wireless card must support 802.1x, AES, and WPA2. Windows XP with service pack 2, it is recommended
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP with Service Pack 2 Your wireless card must support 802.1x, AES, and WPA2. Windows XP with service pack 2, it is recommended
Wireless Network Configuration Guide
 CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
