Pretty Good Privacy with GnuPG
|
|
|
- Daniela Bell
- 10 years ago
- Views:
Transcription
1 Pretty Good Privacy with GnuPG Steve Revilak Cabot House Sep. 24, / 16
2 Encryption and Signing Encryption The purpose is to ensure that a message is readable only by someone possessing a specific key. Signing Guarantees that a message was sent by someone with a specific key (and wasn t altered after sending). (Here I m using the term message in a very generic sense it could be , a file, or any arbitrary piece of data). Leap of faith: You need some level of trust that a particular key belongs to a particular person. 2 / 16
3 Public vs Private Keys Keys exist as a pair: There s a public key. You share this with everyone. There s a private key (also called a secret key). This is a closely guarded secret. During encryption, the sender encrypts the message with the recipient s public key. The recipient uses their private key to decrypt the message. During signing, the sender signs the message with their private key. The signature can be verified by anyone with the corresponding public key. 3 / 16
4 Goals for this workshop Generate a keypair Upload your public key to a keyserver Download my public key. Set up your mail program to send and receive signed and encrypted . (Mail program = Mail User Agent, or MUA) Send me a signed and encrypted message. (I should be able to decrypt your message, and verify your signature.) Let me sent you a signed and encrypted message. (You should be able to decrypt my message and verify my signature.) 4 / 16
5 Generating a Keypair We can do these things with GUI tools. I m including command-line equivalents for reference. Generate Key. gpg --gen-key Choose RSA, RSA. Use the longest key possible. Upload Key. gpg --send-key KEYID Download my key. gpg --search [email protected] OR gpg --recv-key 28C2A300 5 / 16
6 Mail Client Basics Sending: You ll use a protocol called SMTP, or Simple Mail Transfer Protocol. Receiving: Two options: IMAP (Internet Mail Access Protocol), or POP (Post Office Protocol) IMAP stores all messages on your ESP s mail server. You can move them to local folders, but you have to do this explicitly. POP downloads mail from your ESP s mail server. By default, the server copy is deleted; you can also configure your mail client to leave it on the server. If you have a lot of mail on the server, the initial synchronization might take a while, especial with POP. 6 / 16
7 Configuring your MUA (GMail) GMail: Enable IMAP or POP in Gmail s web interface. Sending: smtp.gmail.com, port 587, use SSL Receiving: imap.gmail.com, port 993, use SSL; OR pop.gmail.com, port 995, use SSL ?hl=en&ref_topic= / 16
8 Configuring your MUA (Hotmail) Hotmail: Enable POP/IMAP in outlook.com s web interface Sending: smtp-mail.outlook.com, port 587, use TLS Receiving: imap-mail.outlook.com, Port 993, use SSL; OR pop-mail.outlook.com, port 995, SSL outlook/send-receive-from-app 8 / 16
9 Configuring your MUA (Yahoo) Yahoo: POP is only available for Yahoo Plus Accounts Sending: smtp.mail.yahoo.com, port 587, use SSL Receving: pop.mail.yahoo.com, port 995, use SSL; OR imap.mail.yahoo.com, port 993, use SSL PROD_MAIL_ML&locale=en_US&id=SLN / 16
10 Sending and receiving mail We ll take this one step at a time. Send me a signed and encrypted message. Open your Sent Mail folder. Make sure that you can read the encrypted message you sent! I ll respond. Work on downloading, decrypting, and reading my message. Be sure to verify the signature. 10 / 16
11 Trusting and Signing Keys (1) How do you verify that a given key belongs to a given person? You check the fingerprint. Here s mine: gpg --fingerprint 28C2A Key fingerprint = 6F09 15FF 59CE E093 56F4 BEEC E772 7C56 28C2 A300 If the fingerprint matches, you ve got the right key. 11 / 16
12 Trusting and Signing Keys (2) Once you trust a key, sign it. gpg --sign-key 28C2A300 OR gpg --lsign-key 28C2A300 lsign is a local signature; it s only visible to you. To distribute a non-local (aka exportable ) signature: Send it to a key server: gpg --send-key 28C2A300 Export the key (containing your signature), and send it to the key holder. gpg -a --export 28C2A300 > signed-key.asc The key holder will gpg --import signed-key.asc to import your signature. 12 / 16
13 Revocation Certificates What if (say) your laptop is stolen, and you lose your private key? You revoke it. Generate a revocation certificate gpg -a --gen-revoke KEYID > pgp-revoke.asc Uploading the revocation certificate cancels your key. Note: you cannot generate a revocation certificate without a private key! Keep the revocation certificate in a safe place. 13 / 16
14 Backing up your keys If you lose your private key, you won t be able to decrypt messages. Lost private keys cannot be recovered! Backup your private key gpg -a --export-secret-keys KEYID > private-key.asc Store a copy of private-key.asc in a safe place. For example, keep electronic and printed copies in a safe deposit box. 14 / 16
15 Wrap Up PGP can protect your privacy through encryption. PGP can provide non-repudiation through signatures. PGP is something that you can (and IMHO, should) use every day. My favorite reason for using PGP: because I can! GnuPG is a free software implementation of a public standard. Remember: it s hard to backdoor software when the source code is public. 15 / 16
16 Resources GnuPG: GPG4win: GPG Tools: Riseup.net s Best practices for OpenPGP: openpgp-best-practices Cryptoparty handbook: Surveillance Self-Defense: 16 / 16
Signing and Encryption with GnuPG
 Signing and Encryption with GnuPG Steve Revilak Cryptoparty @ Northeastern Law School Feb. 9, 2014 1 / 22 What is GnuPG? GnuPG is a free software implementation of the OpenPGP standard. PGP stands for
Signing and Encryption with GnuPG Steve Revilak Cryptoparty @ Northeastern Law School Feb. 9, 2014 1 / 22 What is GnuPG? GnuPG is a free software implementation of the OpenPGP standard. PGP stands for
Signing and Encryption with GnuPG
 Signing and Encryption with GnuPG Steve Revilak http://www.srevilak.net/wiki/talks Cryptoparty @ Somerville Public Library January 10, 2015 1 / 20 What is GnuPG? GnuPG is a free software implementation
Signing and Encryption with GnuPG Steve Revilak http://www.srevilak.net/wiki/talks Cryptoparty @ Somerville Public Library January 10, 2015 1 / 20 What is GnuPG? GnuPG is a free software implementation
Encrypting Email with KMail, Mozilla Thunderbird, and Evolution LOCK AND KEY BY FRAUKE OSTER
 COVER STORY Encrypting Email Encrypting Email with KMail, Mozilla Thunderbird, and Evolution LOCK AND KEY The leading email applications include new features for helping users secure and authenticate their
COVER STORY Encrypting Email Encrypting Email with KMail, Mozilla Thunderbird, and Evolution LOCK AND KEY The leading email applications include new features for helping users secure and authenticate their
Tutorial: Encrypted Email with Thunderbird and Enigmail. Author: Shashank Areguli. Published: Ed (August 9, 2014)
 Tutorial: Encrypted Email with Thunderbird and Enigmail Author: Shashank Areguli Published: Ed (August 9, 2014) There are three issues of security that needs to dealt with on the internet, concerning information.
Tutorial: Encrypted Email with Thunderbird and Enigmail Author: Shashank Areguli Published: Ed (August 9, 2014) There are three issues of security that needs to dealt with on the internet, concerning information.
Networks & Security Course. Web of Trust and Network Forensics
 Networks & Security Course Web of Trust and Network Forensics Virtual Machine Virtual Machine Internet connection You need to connect the VM to the Internet for some of the Web of Trust exercises. Make
Networks & Security Course Web of Trust and Network Forensics Virtual Machine Virtual Machine Internet connection You need to connect the VM to the Internet for some of the Web of Trust exercises. Make
Getting started with IMAP for Aggiemail What is IMAP?
 Getting started with IMAP for Aggiemail What is IMAP? IMAP, or Internet Message Access Protocol, lets you download messages from Aggiemail s servers onto your computer so you can access your mail with
Getting started with IMAP for Aggiemail What is IMAP? IMAP, or Internet Message Access Protocol, lets you download messages from Aggiemail s servers onto your computer so you can access your mail with
Create Mail Profiles for Gmail, Yahoo or Hotmail Accounts for Outlook Windows
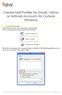 Create Mail Profiles for Gmail, Yahoo or Hotmail Accounts for Outlook Windows 1 Create Mail Profiles Firstly select the start menu and open control Panel. In the control panel window select Mail (32-bit)
Create Mail Profiles for Gmail, Yahoo or Hotmail Accounts for Outlook Windows 1 Create Mail Profiles Firstly select the start menu and open control Panel. In the control panel window select Mail (32-bit)
Published : 2013-12-02 License : None
 K9 1 2 Published : 2013-12-02 License : None INTRODUCTION K-9 Mail is an email application (app) for Android phones or tablets. K-9 supports multiple mailboxes, each independently configurable. T his ability
K9 1 2 Published : 2013-12-02 License : None INTRODUCTION K-9 Mail is an email application (app) for Android phones or tablets. K-9 supports multiple mailboxes, each independently configurable. T his ability
HW/Lab 1: Email Security with PGP, and Crypto CS 336/536: Computer Network Security DUE 09/28/2015 (11am)
 HW/Lab 1: Email Security with PGP, and Crypto CS 336/536: Computer Network Security DUE 09/28/2015 (11am) This HW/Lab assignment covers Lectures 2 to 4. Please review these thoroughly before starting to
HW/Lab 1: Email Security with PGP, and Crypto CS 336/536: Computer Network Security DUE 09/28/2015 (11am) This HW/Lab assignment covers Lectures 2 to 4. Please review these thoroughly before starting to
GPG installation and configuration
 Contents Introduction... 3 Windows... 5 Install GPG4WIN... 5 Configure the certificate manager... 7 Configure GPG... 7 Create your own set of keys... 9 Upload your public key to the keyserver... 11 Importing
Contents Introduction... 3 Windows... 5 Install GPG4WIN... 5 Configure the certificate manager... 7 Configure GPG... 7 Create your own set of keys... 9 Upload your public key to the keyserver... 11 Importing
GPG Tutorial. 1 Introduction. 2 Creating a signing and encryption keys. 3 Generating a revocation certicate. Andreas Hirt July 12, 2009
 GPG Tutorial Andreas Hirt July 12, 2009 1 Introduction The purpose of this document is to give a brief introduction on how to set up and use GPG, the GNU implementation of PGP. The reader must rst generate
GPG Tutorial Andreas Hirt July 12, 2009 1 Introduction The purpose of this document is to give a brief introduction on how to set up and use GPG, the GNU implementation of PGP. The reader must rst generate
THUNDERBIRD SETUP (STEP-BY-STEP)
 Jim McKnight www.jimopi.net Thunderbird_Setup.lwp revised 12-11-2013 (Note1: Not all sections have been updated for the latest version of Thunderbird available at the time I verified that Section. Each
Jim McKnight www.jimopi.net Thunderbird_Setup.lwp revised 12-11-2013 (Note1: Not all sections have been updated for the latest version of Thunderbird available at the time I verified that Section. Each
The KGpg Handbook. Jean-Baptiste Mardelle Rolf Eike Beer
 Jean-Baptiste Mardelle Rolf Eike Beer 2 Contents 1 Introduction 5 2 Getting Started 6 3 Using KGpg 8 3.1 Generating a key...................................... 8 3.2 Revoking a key.......................................
Jean-Baptiste Mardelle Rolf Eike Beer 2 Contents 1 Introduction 5 2 Getting Started 6 3 Using KGpg 8 3.1 Generating a key...................................... 8 3.2 Revoking a key.......................................
Gold Lock Desktop. User Manual. Follow these simple steps to install, configure, and use Gold Lock Desktop.
 User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
GPG - GNU Privacy Guard
 GPG - GNU Privacy Guard How to use Károly Erdei October 15, 2014 Károly Erdei GPG - GNU Privacy Guard 1/60 1 Why 2 Cryptography 3 PGP 4 KGPG-Assistant 5 -Key-Manager 6 -Editor 7 GPG4Win 8 Enigmail Károly
GPG - GNU Privacy Guard How to use Károly Erdei October 15, 2014 Károly Erdei GPG - GNU Privacy Guard 1/60 1 Why 2 Cryptography 3 PGP 4 KGPG-Assistant 5 -Key-Manager 6 -Editor 7 GPG4Win 8 Enigmail Károly
How To Send Mail From A Macbook Access To A Pc Or Ipad With A Password Protected Email Address (Monroe Access) On A Pc (For Macbook) Or Ipa (For Ipa) On Pc Or Macbook (For
 Email client settings: Incoming Mail (IMAP) Server requires SSL: Outgoing Mail (SMTP) Server requires TLS or SSL: Account Name: Email Address: Password: imap.gmail.com Use SSL: Yes Port: 993 smtp.gmail.com
Email client settings: Incoming Mail (IMAP) Server requires SSL: Outgoing Mail (SMTP) Server requires TLS or SSL: Account Name: Email Address: Password: imap.gmail.com Use SSL: Yes Port: 993 smtp.gmail.com
Configuring Outlook 2010 for Windows
 Configuring Outlook 2010 for Windows This document assumes that you already have Outlook 2010 installed on your computer and you are ready to configure Outlook. Table of Contents Configuring Outlook 2010
Configuring Outlook 2010 for Windows This document assumes that you already have Outlook 2010 installed on your computer and you are ready to configure Outlook. Table of Contents Configuring Outlook 2010
User Guide Supplement. S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series
 User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
Encrypting your Email Communications using PGP
 Encrypting your Email Communications using PGP If you are watching this tutorial as part of the conference materials, the software is on a separate CD. Alternately, you can obtain the software at the following
Encrypting your Email Communications using PGP If you are watching this tutorial as part of the conference materials, the software is on a separate CD. Alternately, you can obtain the software at the following
GETTING STARTED SECURE FILE TRANSFER PROCEDURES A. Secure File Transfer Protocol (SFTP) Procedures
 A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
e- storage Mail Archive
 e- storage Mail Archive 1 TABLE OF CONTENTS 1.0 OVERVIEW 3 1.1 INTRODUCTION... 3 1.2 REQUIREMENT. 4 2.0 SETUP AND CONFIGURATION. 6 2.1 CREATE NEW ARCHIVE PROFILE. 6 2.1.1 Gmail Account.. 8 2.1.2 Hotmail
e- storage Mail Archive 1 TABLE OF CONTENTS 1.0 OVERVIEW 3 1.1 INTRODUCTION... 3 1.2 REQUIREMENT. 4 2.0 SETUP AND CONFIGURATION. 6 2.1 CREATE NEW ARCHIVE PROFILE. 6 2.1.1 Gmail Account.. 8 2.1.2 Hotmail
C R E A T E D O N 8 / 2 2 / 2 0 1 3 MCALLISTER SOFTWARE SYSTEMS. AVImark Software Support. E-Mail S e t u p
 C R E A T E D O N 8 / 2 2 / 2 0 1 3 MCALLISTER SOFTWARE SYSTEMS AVImark Software Support AV I m a r k E-Mail S e t u p If you do not see your E-Mail provider listed below you will need to contact your
C R E A T E D O N 8 / 2 2 / 2 0 1 3 MCALLISTER SOFTWARE SYSTEMS AVImark Software Support AV I m a r k E-Mail S e t u p If you do not see your E-Mail provider listed below you will need to contact your
Set up Outlook for your new student e mail with IMAP/POP3 settings
 Set up Outlook for your new student e mail with IMAP/POP3 settings 1. Open Outlook. The Account Settings dialog box will open the first time you open Outlook. If the Account Settings dialog box doesn't
Set up Outlook for your new student e mail with IMAP/POP3 settings 1. Open Outlook. The Account Settings dialog box will open the first time you open Outlook. If the Account Settings dialog box doesn't
isecuremail User Guide for iphone
 isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
isecuremail User Guide for iphone Page 1 CONTENTS Chapter 1: Welcome... 4 Chapter 2: Getting Started... 5 Compatability... 5 Preliminary Steps... 5 Setting up a POP3 / IMAP4/ Exchange Email Account...
Ubuntu Open PGP IMPLEMENTATION. Dr. ENİS KARAARSLAN 2014
 Ubuntu Open PGP IMPLEMENTATION Dr. ENİS KARAARSLAN 2014 Enter your personal information, select your key encryption type, key strength, and when you want your key to expire. Your name and email address
Ubuntu Open PGP IMPLEMENTATION Dr. ENİS KARAARSLAN 2014 Enter your personal information, select your key encryption type, key strength, and when you want your key to expire. Your name and email address
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on. User Information
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.btconline.net mail (default) Click on Properties button Click on the General tab User Information
The basic groups of components are described below. Fig X- 1 shows the relationship between components on a network.
 Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
Elements of Email Email Components There are a number of software components used to produce, send and transfer email. These components can be broken down as clients or servers, although some components
How To Encrypt A Traveltrax Report On Gpg On A Pc Or Mac Or Mac (For A Free Download) On A Thumbdrive Or Ipad Or Ipa (For Free) On Pc Or Ipo (For An Ipo)
 EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on Mail Tab.
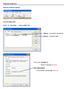 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
After you've enabled POP/IMAP access in i.mail, you need to configure your email client to download i.mail messages.
 User Guide- i.mail enhancement Configure POP/IMAP access using Outlook and Windows Mail Firstly, you need to enable POP/IMAP on your i.mail account: 1. Log into your i.mail account via web 2. Click Mail
User Guide- i.mail enhancement Configure POP/IMAP access using Outlook and Windows Mail Firstly, you need to enable POP/IMAP on your i.mail account: 1. Log into your i.mail account via web 2. Click Mail
ENCRYPTION EMAIL ENCRYPTION A BLACK PAPER HOW TO SECURE YOUR EMAILS FOR FREE WITH THE STRONGEST ENCRYPTION IN THE WORLD EMAIL A BLACK PAPER
 EMIL REPORT FROM SOVEREIGNMN.COM PPER EMIL HOW TO SECURE YOUR EMILS FOR FREE WITH THE STRONGEST IN THE WORLD PPER 1 EMIL PPER Why You Should Encrypt Your Emails... 3 Encrypting Your Emails With PGP:...
EMIL REPORT FROM SOVEREIGNMN.COM PPER EMIL HOW TO SECURE YOUR EMILS FOR FREE WITH THE STRONGEST IN THE WORLD PPER 1 EMIL PPER Why You Should Encrypt Your Emails... 3 Encrypting Your Emails With PGP:...
How to Setup Privacy Guard Encryption.
 How to Setup Privacy Guard Encryption. Contents Setting up for the first time.... 1 Installing the Software (free)... 1 Generating your own key... 2 Share your key with your friends so they can send you
How to Setup Privacy Guard Encryption. Contents Setting up for the first time.... 1 Installing the Software (free)... 1 Generating your own key... 2 Share your key with your friends so they can send you
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Biography of Trainer. Education. Experience. Summary. TLS/SSL : Securing your website PGP : Secure your email communication. Topic
 Topic Name of the Trainer/Speaker Professional Position and Name of Organization Email TLS/SSL : Securing your website PGP : Secure your email communication Mohammad Fakrul Alam CTO bdhub Limited [email protected]
Topic Name of the Trainer/Speaker Professional Position and Name of Organization Email TLS/SSL : Securing your website PGP : Secure your email communication Mohammad Fakrul Alam CTO bdhub Limited [email protected]
How to use PGP Encryption with iscribe
 How to use PGP Encryption with iscribe iscribe e-mail seamlessly supports e-mail encryption and digital signatures. This bulletin describes how to setup iscribe so that you can send and receive encrypted
How to use PGP Encryption with iscribe iscribe e-mail seamlessly supports e-mail encryption and digital signatures. This bulletin describes how to setup iscribe so that you can send and receive encrypted
LiteCommerce Advanced Security Module. Version 2.8
 LiteCommerce Advanced Security Module Version 2.8 Reference Manual Revision date: Jul/03/2007 LiteCommerce Advanced Security Module Reference Manual I Table of Contents Introduction...1 Administrator...2
LiteCommerce Advanced Security Module Version 2.8 Reference Manual Revision date: Jul/03/2007 LiteCommerce Advanced Security Module Reference Manual I Table of Contents Introduction...1 Administrator...2
Android: Configure IMAP/POP/SMTP
 Android: Configure IMAP/POP/SMTP April 10, 2015 Table of Contents Android 5.0: Configure IMAP/POP/SMTP Introduction... 3 Email Settings... 3 IMAP... 3 POP... 3 SMTP... 3 Process Overview... 3 Anatomy of
Android: Configure IMAP/POP/SMTP April 10, 2015 Table of Contents Android 5.0: Configure IMAP/POP/SMTP Introduction... 3 Email Settings... 3 IMAP... 3 POP... 3 SMTP... 3 Process Overview... 3 Anatomy of
Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points
 Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points Objective 1. To explore a practical application of cryptography secure e-mail 2. To use public key encryption 3. To gain experience with the various
Secure E-Mail Part II Due Date: Sept 27 Points: 25 Points Objective 1. To explore a practical application of cryptography secure e-mail 2. To use public key encryption 3. To gain experience with the various
Sending an Encrypted/Unencrypted Message. Let's Begin: Log In and Set Up Security Questions. Create Additional ProMailSource Accounts:
 Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
Let's Begin: Log In and Set Up Security Questions To start, you can log in from the ProMailSource home page. Sending an Encrypted/Unencrypted Message Every message you send through ProMailSource is automatically
CLIENT DATABASE SECURITY
 CLIENT DATABASE SECURITY 1502 RXR Plaza 15th Floor, West Tower Uniondale, NY 11556 Telephone: (516) 227-6600 Facsimile: (516) 227-1799 Website: http://www.openlink.com Revision History Document Name Date
CLIENT DATABASE SECURITY 1502 RXR Plaza 15th Floor, West Tower Uniondale, NY 11556 Telephone: (516) 227-6600 Facsimile: (516) 227-1799 Website: http://www.openlink.com Revision History Document Name Date
An Introduction to Secure Email. Presented by: Addam Schroll IT Security & Privacy Analyst
 An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
Setting up and controlling E-mail
 Setting up and controlling E-mail Two methods Web based PC based Setting up and controlling E-mail Web based the messages are on the Internet accessed by dial-up or broadband at your Internet Service Provider
Setting up and controlling E-mail Two methods Web based PC based Setting up and controlling E-mail Web based the messages are on the Internet accessed by dial-up or broadband at your Internet Service Provider
Configuring Outlook 2016 for Windows
 Configuring Outlook 2016 for Windows This document assumes that you already have Outlook 2016 installed on your computer and you are ready to configure Outlook. Table of Contents Configuring Outlook 2016
Configuring Outlook 2016 for Windows This document assumes that you already have Outlook 2016 installed on your computer and you are ready to configure Outlook. Table of Contents Configuring Outlook 2016
UNI EMAIL - WINDOWS. How to... Access your University email on your Windows Computer. Introduction. Step 1/1 - Setting Up Your Windows Computer
 UNIVERSITY EMAIL - WINDOWS How to... Access your University email on your Windows Computer Introduction The University of South Wales offers all enrolled students the use of a free personal e-mail account
UNIVERSITY EMAIL - WINDOWS How to... Access your University email on your Windows Computer Introduction The University of South Wales offers all enrolled students the use of a free personal e-mail account
1 Login to your CSUF student email account and click on the Settings icon ( ) at the far right.
 Connect to Your Student Email: Microsoft Outlook for PC Before you can access your student email account on your e-mail client, you must first enable POP/IMAP features on your student email account and
Connect to Your Student Email: Microsoft Outlook for PC Before you can access your student email account on your e-mail client, you must first enable POP/IMAP features on your student email account and
Initial Setup of Microsoft Outlook 2011 with IMAP for OS X Lion
 Initial Setup of Microsoft Outlook Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access Protocol
Initial Setup of Microsoft Outlook Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access Protocol
Move Your Email to AT&T Website Solutions
 September 2012 Move Your Email to AT&T Website Solutions Moving Email from one Provider to AT&T Website Solutions With AT&T Website Solutions, you can check your email using your favorite email program
September 2012 Move Your Email to AT&T Website Solutions Moving Email from one Provider to AT&T Website Solutions With AT&T Website Solutions, you can check your email using your favorite email program
Entrust Managed Services PKI. Getting started with digital certificates and Entrust Managed Services PKI. Document issue: 1.0
 Entrust Managed Services PKI Getting started with digital certificates and Entrust Managed Services PKI Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust
Entrust Managed Services PKI Getting started with digital certificates and Entrust Managed Services PKI Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust
Transitioning Your School Email Account
 Transitioning Your School Email Account This tutorial will walk you through transferring the email and other data from your School account to a personal email account. Establish a New Email Address (or
Transitioning Your School Email Account This tutorial will walk you through transferring the email and other data from your School account to a personal email account. Establish a New Email Address (or
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Configure Outlook 2007 for Brandeis Gmail
 Configure Outlook 2007 for Brandeis Gmail These instructions detail how to configure Microsoft Outlook 2007 to access Brandeis Gmail. Note: You may need to change your UNet password before configuring
Configure Outlook 2007 for Brandeis Gmail These instructions detail how to configure Microsoft Outlook 2007 to access Brandeis Gmail. Note: You may need to change your UNet password before configuring
Initial Setup of Mozilla Thunderbird with IMAP for Windows 7
 Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Exam Papers Encryption Project PGP Universal Server Trial Progress Report
 Exam Papers Encryption Project PGP Universal Server Trial Progress Report Introduction Using encryption for secure file storage and transfer presents a number of challenges. While the use of strong, well
Exam Papers Encryption Project PGP Universal Server Trial Progress Report Introduction Using encryption for secure file storage and transfer presents a number of challenges. While the use of strong, well
USING YOUR GMAIL ACCOUNT FOR SCRUBBING YOUR REGULAR EMAIL OF SPAM Beginners Kaffee Klatch Presented by Bill Wilkinson
 USING YOUR GMAIL ACCOUNT FOR SCRUBBING YOUR REGULAR EMAIL OF SPAM Beginners Kaffee Klatch Presented by Bill Wilkinson The Gmail spam filter is highly acclaimed by many experts in the security and privacy
USING YOUR GMAIL ACCOUNT FOR SCRUBBING YOUR REGULAR EMAIL OF SPAM Beginners Kaffee Klatch Presented by Bill Wilkinson The Gmail spam filter is highly acclaimed by many experts in the security and privacy
Using Your PGP Tool to Update Your Email Address Settings for Encrypted Messaging
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Using Your PGP Tool to Update Your Email Address Settings for Encrypted Messaging Overview The University of Pittsburgh is removing the
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Using Your PGP Tool to Update Your Email Address Settings for Encrypted Messaging Overview The University of Pittsburgh is removing the
Initial Setup of Mozilla Thunderbird with IMAP for OS X Lion
 Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
Initial Setup of Mozilla Thunderbird Concept This document describes the procedures for setting up the Mozilla Thunderbird email client to download messages from Google Mail using Internet Message Access
New Mexico State University
 E-mail Set Up for Microsoft Office Outlook 2003 Click on the option that describes you: I am setting up my NMSU e-mail with Outlook for the first time I currently use Outlook to view my NMSU e-mail and
E-mail Set Up for Microsoft Office Outlook 2003 Click on the option that describes you: I am setting up my NMSU e-mail with Outlook for the first time I currently use Outlook to view my NMSU e-mail and
Set Up E-mail Setup with Microsoft Outlook 2007 using POP3
 Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Setting up CatMail on Outlook 2010
 Setting up CatMail on Outlook 2010 Before beginning this process, make sure that IMAP is enabled in your account and that you have your CatMail Secondary password. For more information on CatMail Secondary
Setting up CatMail on Outlook 2010 Before beginning this process, make sure that IMAP is enabled in your account and that you have your CatMail Secondary password. For more information on CatMail Secondary
File and email encryption with GPG4win & Enigmail
 Protektor Services Windows Manual 11.5 File and email encryption with GPG4win & Enigmail Introduction, Contact, Legals, License Introduction Protektor Services Manual version 11.5 A new edition of the
Protektor Services Windows Manual 11.5 File and email encryption with GPG4win & Enigmail Introduction, Contact, Legals, License Introduction Protektor Services Manual version 11.5 A new edition of the
3. On the E-mail Accounts wizard window, select Add a new e-mail account, and then click Next.
 To Set Up Your E-mail Account in Microsoft Outlook 2003 1. Open Microsoft Outlook 03 3. On the E-mail Accounts wizard window, select Add a new e-mail account, and then click Next. 4. For your server type,
To Set Up Your E-mail Account in Microsoft Outlook 2003 1. Open Microsoft Outlook 03 3. On the E-mail Accounts wizard window, select Add a new e-mail account, and then click Next. 4. For your server type,
to hide away details from prying eyes. Pretty Good Privacy (PGP) utilizes many
 In the world of secure email, there are many options from which to choose from to hide away details from prying eyes. Pretty Good Privacy (PGP) utilizes many cryptographical concepts to achieve a supposedly
In the world of secure email, there are many options from which to choose from to hide away details from prying eyes. Pretty Good Privacy (PGP) utilizes many cryptographical concepts to achieve a supposedly
Setting Up Email. on Your Touch by HTC
 Setting Up Email on Your Touch by HTC Intellectual Property Notices 2007 Sprint Nextel. All rights reserved. No reproduction in whole or in part without prior written approval. SPRINT and other trademarks
Setting Up Email on Your Touch by HTC Intellectual Property Notices 2007 Sprint Nextel. All rights reserved. No reproduction in whole or in part without prior written approval. SPRINT and other trademarks
The Case For Secure Email
 The Case For Secure Email By Erik Kangas, PhD, President, Lux Scientiae, Incorporated http://luxsci.com Contents Section 1: Introduction Section 2: How Email Works Section 3: Security Threats to Your Email
The Case For Secure Email By Erik Kangas, PhD, President, Lux Scientiae, Incorporated http://luxsci.com Contents Section 1: Introduction Section 2: How Email Works Section 3: Security Threats to Your Email
Exchange 2010. Outlook Profile/POP/IMAP/SMTP Setup Guide
 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide September, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Exchange 2010 Outlook Profile Configuration... 1 Outlook Profile
Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide September, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Exchange 2010 Outlook Profile Configuration... 1 Outlook Profile
Clearswift Information Governance
 Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Introduction to Cryptography
 Introduction to Cryptography Part 3: real world applications Jean-Sébastien Coron January 2007 Public-key encryption BOB ALICE Insecure M E C C D channel M Alice s public-key Alice s private-key Authentication
Introduction to Cryptography Part 3: real world applications Jean-Sébastien Coron January 2007 Public-key encryption BOB ALICE Insecure M E C C D channel M Alice s public-key Alice s private-key Authentication
How To Access Your Cpa.Com Email From Your Computer Or A Mobile Phone Or Ipad (For A Free Download) Without Having To Use A Webmail Account
 CPA.com Full Email Account Getting Started Guide Note: You do not need to read this guide if you signed up for the CPA.com Forward-Only Service. Congratulations on the purchase of your new CPA.com Full
CPA.com Full Email Account Getting Started Guide Note: You do not need to read this guide if you signed up for the CPA.com Forward-Only Service. Congratulations on the purchase of your new CPA.com Full
Configuring Your Email Client: Eudora 5.x
 Configuring Your Email Client: Eudora 5.x Configuring Eudora for POP 1-1 Table of Contents Chapter 1. Introduction...1-1 What is an Email Client?...1-1 Who Should Read This Manual?...1-1 How Does Email
Configuring Your Email Client: Eudora 5.x Configuring Eudora for POP 1-1 Table of Contents Chapter 1. Introduction...1-1 What is an Email Client?...1-1 Who Should Read This Manual?...1-1 How Does Email
Internet Programming. Security
 Internet Programming Security Introduction Security Issues in Internet Applications A distributed application can run inside a LAN Only a few users have access to the application Network infrastructures
Internet Programming Security Introduction Security Issues in Internet Applications A distributed application can run inside a LAN Only a few users have access to the application Network infrastructures
Configuring, Customizing, and Troubleshooting Outlook Express
 3 Configuring, Customizing, and Troubleshooting Outlook Express............................................... Terms you ll need to understand: Outlook Express Newsgroups Address book Email Preview pane
3 Configuring, Customizing, and Troubleshooting Outlook Express............................................... Terms you ll need to understand: Outlook Express Newsgroups Address book Email Preview pane
Using Outlook with SaderApps
 William Carey University Information Technology Using Outlook with SaderApps January 12, 2011 2011 William Carey University 498 Tuscan Avenue, Box 147 Hattiesburg, MS 39401 Phone 601.318.6203 Fax 601.318.6546
William Carey University Information Technology Using Outlook with SaderApps January 12, 2011 2011 William Carey University 498 Tuscan Avenue, Box 147 Hattiesburg, MS 39401 Phone 601.318.6203 Fax 601.318.6546
BlackBerry Internet Service. Version: 4.5.1. User Guide
 BlackBerry Internet Service Version: 4.5.1 User Guide Published: 2014-05-22 SWD-20140522173857703 Contents 1 Getting started...7 About the messaging service plans for the BlackBerry Internet Service...7
BlackBerry Internet Service Version: 4.5.1 User Guide Published: 2014-05-22 SWD-20140522173857703 Contents 1 Getting started...7 About the messaging service plans for the BlackBerry Internet Service...7
Public Key Infrastructure (PKI)
 Public Key Infrastructure (PKI) In this video you will learn the quite a bit about Public Key Infrastructure and how it is used to authenticate clients and servers. The purpose of Public Key Infrastructure
Public Key Infrastructure (PKI) In this video you will learn the quite a bit about Public Key Infrastructure and how it is used to authenticate clients and servers. The purpose of Public Key Infrastructure
How To Encrypt Data With Encryption
 USING ENCRYPTION TO PROTECT SENSITIVE INFORMATION Commonwealth Office of Technology Security Month Seminars Alternate Title? Boy, am I surprised. The Entrust guy who has mentioned PKI during every Security
USING ENCRYPTION TO PROTECT SENSITIVE INFORMATION Commonwealth Office of Technology Security Month Seminars Alternate Title? Boy, am I surprised. The Entrust guy who has mentioned PKI during every Security
THUNDERBIRD WORKBOOK
 THUNDERBIRD WORKBOOK 1 2 Published : 2012-05-25 License : None INTRODUCTION 1. ABOUT THIS WORKBOOK 2. INTRODUCTION TO THUNDERBIRD 3 1. ABOUT THIS WORKBOOK T his workbook is designed to complete specific
THUNDERBIRD WORKBOOK 1 2 Published : 2012-05-25 License : None INTRODUCTION 1. ABOUT THIS WORKBOOK 2. INTRODUCTION TO THUNDERBIRD 3 1. ABOUT THIS WORKBOOK T his workbook is designed to complete specific
Set Up Your Email. HTC Touch Pro. www.sprint.com
 Set Up Your Email HTC Touch Pro www.sprint.com 2008 Sprint. Sprint and the logo are trademarks of Sprint. Other marks are the property of their respective owners. Intellectual Property Notices Copyright
Set Up Your Email HTC Touch Pro www.sprint.com 2008 Sprint. Sprint and the logo are trademarks of Sprint. Other marks are the property of their respective owners. Intellectual Property Notices Copyright
Overview Keys. Overview
 Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
ireadsmime User Guide For iphone, ipad, and ipod Touch
 ireadsmime User Guide For iphone, ipad, and ipod Touch Page 1 CONTENTS Chapter 1: Welcome... 3 Chapter 2: Getting Started... 3 Compatability... 3 Preliminary Steps... 3 Setting up a POP3 / IMAP4 Email
ireadsmime User Guide For iphone, ipad, and ipod Touch Page 1 CONTENTS Chapter 1: Welcome... 3 Chapter 2: Getting Started... 3 Compatability... 3 Preliminary Steps... 3 Setting up a POP3 / IMAP4 Email
Ciphire Mail. Abstract
 Ciphire Mail Technical Introduction Abstract Ciphire Mail is cryptographic software providing email encryption and digital signatures. The Ciphire Mail client resides on the user's computer between the
Ciphire Mail Technical Introduction Abstract Ciphire Mail is cryptographic software providing email encryption and digital signatures. The Ciphire Mail client resides on the user's computer between the
GPG4win / Kleopatra Documentation. Secure file and e-mail encryption by using GnuPG for Windows
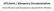 GPG4win / Kleopatra Documentation Secure file and e-mail encryption by using GnuPG for Windows GPG4win Detailed How To: Installing Gpg4win: 1. Go to the following website http://www.gpg4win.org/download.html,
GPG4win / Kleopatra Documentation Secure file and e-mail encryption by using GnuPG for Windows GPG4win Detailed How To: Installing Gpg4win: 1. Go to the following website http://www.gpg4win.org/download.html,
PrivaSphere Gateway Certificate Authority (GW CA)
 PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
PrivaSphere Gateway Certificate Authority (GW CA) Send and receive secure emails with your email program through restricting firewalls using SMIME gateway functionalities. PrivaSphere Secure Messaging
How To Protect Your Email From Being Hacked On A Pc Or Mac Or Ipa From Being Stolen On A Network (For A Free Download) On A Computer Or Ipo (For Free) On Your Pc Or Ipom (For An Ipo
 The Case for Email Security secure, premium by Erik Kangas, President, Lux Scientiae Section 1: Introduction to Email Security You may already know that email is insecure; however, it may surprise you
The Case for Email Security secure, premium by Erik Kangas, President, Lux Scientiae Section 1: Introduction to Email Security You may already know that email is insecure; however, it may surprise you
Getting the most from Apple Mail
 Getting the most from Apple Mail Larry Kerschberg, Roy Wagner, Jonathan Bernstein and Friends February 28, 2015 1 Topics Mail on Macs and ios devices Configuring your accounts IMAP Folders VIP Contacts,
Getting the most from Apple Mail Larry Kerschberg, Roy Wagner, Jonathan Bernstein and Friends February 28, 2015 1 Topics Mail on Macs and ios devices Configuring your accounts IMAP Folders VIP Contacts,
Frequently Asked Questions. Frequently Asked Questions. 2013 SSLPost Page 1 of 31 [email protected]
 Frequently Asked Questions 2013 SSLPost Page 1 of 31 [email protected] Table of Contents 1 What is SSLPost Cloud? 3 2 Why do I need SSLPost Cloud? 4 3 What do I need to use SSLPost Cloud? 5 4 Which Internet
Frequently Asked Questions 2013 SSLPost Page 1 of 31 [email protected] Table of Contents 1 What is SSLPost Cloud? 3 2 Why do I need SSLPost Cloud? 4 3 What do I need to use SSLPost Cloud? 5 4 Which Internet
How to setup your iphone email client
 How to setup your iphone email client First things first! Make sure you can access mail directly through webmail using your username and password. Webmail can be accessed using the following format http://webmail.stmkr.net
How to setup your iphone email client First things first! Make sure you can access mail directly through webmail using your username and password. Webmail can be accessed using the following format http://webmail.stmkr.net
Cornerstones of Security
 Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Internet Security Cornerstones of Security Authenticity the sender (either client or server) of a message is who he, she or it claims to be Privacy the contents of a message are secret and only known to
Patriots Email Outlook Configuration
 Patriots Email Outlook Configuration Contents Configuration in Outlook... 2 Exchange/Active Sync Configuration... 2 IMAP and POP Configuration... 5 Retrieve Unique POP/IMAP Server... 5 IMAP or POP Setup
Patriots Email Outlook Configuration Contents Configuration in Outlook... 2 Exchange/Active Sync Configuration... 2 IMAP and POP Configuration... 5 Retrieve Unique POP/IMAP Server... 5 IMAP or POP Setup
How to Set Up Your. Email Account
 How to Set Up Your Email Account Contents Outlook 2002 (Office XP)... 3 Outlook 2003 (Office 2003)... 6 Outlook 2007 (Office 2007)... 10 Outlook 2010 (Office 2010)... 14 Outlook Account Setup Page 2 HOW
How to Set Up Your Email Account Contents Outlook 2002 (Office XP)... 3 Outlook 2003 (Office 2003)... 6 Outlook 2007 (Office 2007)... 10 Outlook 2010 (Office 2010)... 14 Outlook Account Setup Page 2 HOW
Sync Security and Privacy Brief
 Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Introduction Security and privacy are two of the leading issues for users when transferring important files. Keeping data on-premises makes business and IT leaders feel more secure, but comes with technical
Security. Friends and Enemies. Overview Plaintext Cryptography functions. Secret Key (DES) Symmetric Key
 Friends and Enemies Security Outline Encryption lgorithms Protocols Message Integrity Protocols Key Distribution Firewalls Figure 7.1 goes here ob, lice want to communicate securely Trudy, the intruder
Friends and Enemies Security Outline Encryption lgorithms Protocols Message Integrity Protocols Key Distribution Firewalls Figure 7.1 goes here ob, lice want to communicate securely Trudy, the intruder
gpg4o Manual Version 3.0
 gpg4o Manual Version 3.0 Table of Contents 1 GENERAL... 3 2 SYSTEM REQUIREMENTS... 4 3 INSTALLATION... 5 3.1 Required Software... 5 3.2 Installing GnuPG... 5 3.3 Installing gpg4o... 10 3.4 Setting gpg4o...
gpg4o Manual Version 3.0 Table of Contents 1 GENERAL... 3 2 SYSTEM REQUIREMENTS... 4 3 INSTALLATION... 5 3.1 Required Software... 5 3.2 Installing GnuPG... 5 3.3 Installing gpg4o... 10 3.4 Setting gpg4o...
