GETTING STARTED SECURE FILE TRANSFER PROCEDURES A. Secure File Transfer Protocol (SFTP) Procedures
|
|
|
- Juliana Jennings
- 10 years ago
- Views:
Transcription
1 A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using the SFTP are: 1. SFTP is a standard protocol for file transfer. SFTP is a universally used tool for securely exchanging files between entities. 2. SFTP provides additional security. A username and password must be used to establish a connection and data is encrypted during transmission. Each provider has their own credentials to ensure file transmissions are secure and can be tracked. 3. SFTP is more flexible. Files placed on the SFTP server are available until they are picked up. The SFTP server can be accessed 24 hours a day, 7 days a week. Files remain on the SFTP server until they are deleted. They can be re-accessed multiple times and do not have to be retransmitted. 4. SFTP complies with HIPAA requirements. Every file that is transmitted to IEHP is encrypted and password protected. File Transfer Procedures All files for Eligibility, Encounter data, Capitation, and Claims submission must be exchanged via the SFTP using the formats described in: Section III - Eligibility Processing Procedures Section IV - Encounter Processing Procedures Section V - Capitation Processing Procedures Section VI - Claims Processing Procedures The SFTP server can be accessed via a web browser, but there are several graphical user Interface (GUI) based SFTP client programs available as well. Examples of these include WS_FTP, FileZilla, and CoreFTP. SFTP functionality may also come bundled into other software products such as Microsoft SSIS and WRQ Reflection. Since the use of an SFTP client varies from vendor to vendor, we are providing instructions for using the internet browser web interface only. SFTP Internet Browser Web Interface 1. Open your web browser (e.g. Internet Explorer, Chrome, and Firefox). 2. Navigate to the web address 3. In the login prompt, enter the SFTP credentials given to you by IEHP, typically based on your provider ID. 4. Click the Sign On button to view your home screen. IEHP Provider EDI Manual 07/15 II-1
2 A. SFTP Procedures 1. Downloading Click on the Folders link on the left to see your home directory from where you can navigate to the different subfolders that are used for posting and receiving different kinds of data files. For some of the file formats, an OpenPGP standards compatible encryption program like GPG (GNU Privacy Guard) or PGP (Pretty Good Privacy) may be necessary. Note: IEHP may occasionally place messages on the SFTP server that will appear when you log in, please pay attention to these messages as they may direct you to download a new file or processing schedule. DOWNLOAD FILES FROM IEHP ELIGIBILITY 1. From your home directory click the ELIG subfolder link. 2. In the ELIG subfolder you will find the eligibility file(s) that are ready for download. 4. Remember that eligibility files will be encrypted using your public key. An encryption program will be needed to decrypt the files locally using your private key. DOWNLOAD FILES FROM IEHP CLAIMS STATUS RESPONSE 1. From your home directory click the Claims subfolder link, then from the Claims folder list, click the outbound subfolder link. 2. In the outbound subfolder you will find the claims response file(s) that are ready for download. This will include both 997/999 acknowledgements, 277 status files, and potentially 835 remittance files. To receive 835 files, you must specifically request enrollment. DOWNLOAD FILES FROM IEHP CAPITATION 1. From your home directory click the CAP subfolder link. 2. In the CAP subfolder you will find the Capitation file(s) that are ready for download. 4. Remember that capitation files will be encrypted using your public key. An encryption program will be needed to decrypt the files locally using your private key. IEHP Provider EDI Manual 07/15 II-2
3 A. SFTP Procedures 2. Uploading UPLOAD FILES TO IEHP ENCOUNTER DATA 1. From your home directory click the encounter subfolder link. 2. At the bottom of the screen, use the Upload a File Now function to select which local files to upload. 3. If uploading multiple encounter files, make sure the Upload files individually option is selected. This will ensure that files are not grouped into one archive file for upload. Remember, the encounter folder is for the submission of encrypted encounter files only. UPLOAD FILES TO IEHP CLAIMS SUBMISSION 1. From your home directory click the Claims subfolder link, then from the Claims folder list, click the inbound subfolder link. 2. At the bottom of the screen, use the Upload a File Now function to select which local files to upload. 3. If uploading multiple files, make sure the Upload files individually option is selected. This will ensure that files are not grouped into one archive file for upload. Remember, the claims/inbound folder is for the submission of claims files, only. IEHP Provider EDI Manual 07/15 II-3
4 Introduction B. Encryption Questions and Answers With some of our transactions, file encryption is utilized to ensure security. IEHP has chosen GNU Privacy Guard (GPG) as our encryption program, but there others also available that take advantage of the OpenPGP standards, like PGP. These are very powerful and fairly easy to use packages that are transportable across several popular platforms. There are many levels of security that can be employed. Both commercial and open source software packages based on the OpenPGP Standard can be found. Examples include PGP at or GPG at Installation and Configuration See documentation provided with your software. Generating Private and Public Keys OpenPGP standard encryption is dual key encryption containing a Private key and a Public key. The Private key is kept secure and will be used to decrypt files received. The Public key is given to the data file sender. The sender uses the Public key to encrypt the data files for transmission. Once the data is encrypted with the Public key, not even the sender can view it. The Private key is now required to decrypt it ensuring that only the intended file recipient will be able to access the data. IEHP will need to receive a Public key from each trading partner. If you do not already have a key pair set up, you will need to generate them. Typically you will need to enter a name, an address, and a pass phrase (longer then a password) to generate your key pair. Share your Public key with IEHP by ing it to [email protected] or post it to your home directory on our SFTP. Decrypting A File Once you have downloaded an encrypted file posted by IEHP, the process of decrypting can vary depending on your encryption software. 1. Typically, you can right click on the file and select the context menu option associated with decryption. 2. Enter the Pass Phrase associated with your Private/Public key set and allow the decrypted file to be saved where you can easily find it. Remember that encrypted file extensions may vary. The most common are.pgp,.gpg, and.asc. The extension may have to be configured in your encryption software or changed to suit your software s requirements. IEHP Provider EDI Manual 07/15 II-4
5 B. Encryption Questions and Answers Q: What is OpenPGP based encryption software? A: OpenPGP software allows data trading partners to securely exchange data, relying on Key or Certificate files to encrypt and decrypt the files only by those authorized to do so. Q: Who needs to have OpenPGP based encryption software? A: All data providers: IPAs, Hospitals, clearinghouses, which exchange data electronically with IEHP may at some point be required to decrypt files posted by IEHP. Q: Why do we need to have OpenPGP based encryption software? A: OpenPGP based software allows the users to scramble and encrypt a file. If anyone other than the intended recipient intercepts the encrypted file, it is not readable. PGP also complies with HIPAA and State requirements that a secure means of transmission be implemented. Q: How do we obtain a copy of an OpenPGP based encryption software? A: Both commercial and open source software packages based on the OpenPGP Standard can be found online. Examples include PGP at or GPG at Q: Can I share my keys and if so, how? A: Yes. Encryption Software based on the OpenPGP standard use keyrings or certificate servers to share keys. See your software s guide to find out how. Q: If different people/entities process Eligibility, Encounter, Capitation, and Claims data for my organization, do I need separate keys/software/etc? A: While you will not need additional software, it would be best to have different keys for each of these functions to prevent accidental decryption of the various file types by unauthorized personnel. IEHP Provider EDI Manual 07/15 II-5
Molina Medicaid Solutions EDI Unit sftp Companion Guide 9/5/2012
 Molina Medicaid Solutions EDI Unit sftp Companion Guide 9/5/2012 Contents Introduction... 2 Enrollment... 2 System Regions... 3 Files Sent to Molina... 3 Files Sent From Molina... 4 First Time Logging
Molina Medicaid Solutions EDI Unit sftp Companion Guide 9/5/2012 Contents Introduction... 2 Enrollment... 2 System Regions... 3 Files Sent to Molina... 3 Files Sent From Molina... 4 First Time Logging
Please note that a username and password will be made available upon request. These are necessary to transfer files.
 Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
CBH Provider EDI Browser Manual
 CBH Provider EDI Browser Manual Table of Contents PGP Software Installation Windows XP 2 PGP Software Installation Windows 7 9 Main Screen 16 Log In Screen 19 Report: Authorizations 21 Decryption Instructions
CBH Provider EDI Browser Manual Table of Contents PGP Software Installation Windows XP 2 PGP Software Installation Windows 7 9 Main Screen 16 Log In Screen 19 Report: Authorizations 21 Decryption Instructions
Moveit DMZ User Manual
 ARKANSAS BLUE CROSS BLUE SHIELD Moveit DMZ User Manual EDI Services 2/1/2013 Index Moveit DMZ Introduction...1 Initial Login and Password Change...2 Navigation...8 Getting Started Folders...11 Upload a
ARKANSAS BLUE CROSS BLUE SHIELD Moveit DMZ User Manual EDI Services 2/1/2013 Index Moveit DMZ Introduction...1 Initial Login and Password Change...2 Navigation...8 Getting Started Folders...11 Upload a
Instructions For Opening UHA Encrypted Email
 Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Using LCC s media web server to store files
 Using LCC s media web server to store files Information Technology What is it? Lane s media server is a web repository for instructors to make electronic materials available via the web. Although it s
Using LCC s media web server to store files Information Technology What is it? Lane s media server is a web repository for instructors to make electronic materials available via the web. Although it s
ClicktoFax Service Usage Manual
 ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
Accessing the FTP Server - User Manual
 CENTRAL BANK OF CYPRUS Accessing the FTP Server - User Manual IT Department, CENTRAL BANK OF CYPRUS TABLE OF CONTENTS 1 EXECUTIVE SUMMARY... 1 1.1 AUDIENCE... 1 1.2 SCOPE... 1 2 CHANGES FROM THE OLD FTP
CENTRAL BANK OF CYPRUS Accessing the FTP Server - User Manual IT Department, CENTRAL BANK OF CYPRUS TABLE OF CONTENTS 1 EXECUTIVE SUMMARY... 1 1.1 AUDIENCE... 1 1.2 SCOPE... 1 2 CHANGES FROM THE OLD FTP
HMRC Secure Electronic Transfer (SET)
 HMRC Secure Electronic Transfer (SET) How to use HMRC SET using PGP Desktop Version 2.0 Contents Welcome to HMRC SET 1 HMRC SET overview 2 Encrypt a file to send to HMRC 3 Upload files to the Government
HMRC Secure Electronic Transfer (SET) How to use HMRC SET using PGP Desktop Version 2.0 Contents Welcome to HMRC SET 1 HMRC SET overview 2 Encrypt a file to send to HMRC 3 Upload files to the Government
E-mail Encryption. How do I send my e-mail encryption key?
 E-mail Encryption SecurenCrypt e-mail encryption was designed to work as a plug-in with Microsoft Outlook. The following instructions are geared toward users encrypting e-mail with Outlook. However, throughout
E-mail Encryption SecurenCrypt e-mail encryption was designed to work as a plug-in with Microsoft Outlook. The following instructions are geared toward users encrypting e-mail with Outlook. However, throughout
Overview of edx Analytics
 Overview of edx Analytics I. Data Available from edx EdX provides researchers with data about your institution's classes running on edx.org and edge.edx.org. This includes: Course data Student information
Overview of edx Analytics I. Data Available from edx EdX provides researchers with data about your institution's classes running on edx.org and edge.edx.org. This includes: Course data Student information
How To Encrypt A Traveltrax Report On Gpg On A Pc Or Mac Or Mac (For A Free Download) On A Thumbdrive Or Ipad Or Ipa (For Free) On Pc Or Ipo (For An Ipo)
 EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
Erie 1 BOCES/WNYRIC. Secure File Transfer. Upload/Download Wizard
 Erie 1 BOCES/WNYRIC Secure File Transfer Upload/Download Wizard Revised June 3, 2014 These instructions were created using Internet Explorer Version 11. If you are a using a Firefox or Chrome browser you
Erie 1 BOCES/WNYRIC Secure File Transfer Upload/Download Wizard Revised June 3, 2014 These instructions were created using Internet Explorer Version 11. If you are a using a Firefox or Chrome browser you
GENERAL FILE TRANSFER GUIDELINES
 GENERAL FILE TRANSFER GUIDELINES EMSTARS extracts (the XML files containing patient care records) will be transferred to the FDOH Secure Server at intervals defined in the EMSTARS Business Rules (available
GENERAL FILE TRANSFER GUIDELINES EMSTARS extracts (the XML files containing patient care records) will be transferred to the FDOH Secure Server at intervals defined in the EMSTARS Business Rules (available
MSGCU SECURE MESSAGE CENTER
 MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
Business Internet Email service from Bell User Guide
 Business Internet Email service from Bell User Guide Table Of Contents (click a page number to access that page) Getting Started 3 Access your email remotely using Webmail 3 Basic Features 4 Out Of Office
Business Internet Email service from Bell User Guide Table Of Contents (click a page number to access that page) Getting Started 3 Access your email remotely using Webmail 3 Basic Features 4 Out Of Office
Reading an email sent with Voltage SecureMail. Using the Voltage SecureMail Zero Download Messenger (ZDM)
 Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Google Trusted Stores Setup in Magento
 Google Trusted Stores Setup in Magento Google Trusted Stores is a free badging program that can improve your conversion rate and average order size by reassuring potential customers you offer a great shopping
Google Trusted Stores Setup in Magento Google Trusted Stores is a free badging program that can improve your conversion rate and average order size by reassuring potential customers you offer a great shopping
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Tutorial: Encrypted Email with Thunderbird and Enigmail. Author: Shashank Areguli. Published: Ed (August 9, 2014)
 Tutorial: Encrypted Email with Thunderbird and Enigmail Author: Shashank Areguli Published: Ed (August 9, 2014) There are three issues of security that needs to dealt with on the internet, concerning information.
Tutorial: Encrypted Email with Thunderbird and Enigmail Author: Shashank Areguli Published: Ed (August 9, 2014) There are three issues of security that needs to dealt with on the internet, concerning information.
How To Open An Encrypted Email
 Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
AVTranz The Court Record Online (TCRO) Operating Instructions Vermont Court System
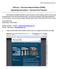 TCRO Operating Instructions 1 AVTranz The Court Record Online (TCRO) Operating Instructions Vermont Court System This document is intended to provide very clear instructions on how to upload content to
TCRO Operating Instructions 1 AVTranz The Court Record Online (TCRO) Operating Instructions Vermont Court System This document is intended to provide very clear instructions on how to upload content to
Quick Start Guide. Hosting Your Domain
 Quick Start Guide Hosting Your Domain http://www.names.co.uk/support/ Table of Contents Web Hosting... 3 FTP (File Transfer Protocol)... 3 File Manager... 6 SiteMaker... 7 2 Please keep these documents
Quick Start Guide Hosting Your Domain http://www.names.co.uk/support/ Table of Contents Web Hosting... 3 FTP (File Transfer Protocol)... 3 File Manager... 6 SiteMaker... 7 2 Please keep these documents
SECURE E-MAIL COMMUNICATIONS PLAN Updated August 25, 2011
 SECURE E-MAIL COMMUNICATIONS PLAN Updated August 25, 2011 Introduction In October, 2008, the Division of Welfare and Supportive Services (DWSS) announced the introduction of secure e-mail through ASM 17-08.
SECURE E-MAIL COMMUNICATIONS PLAN Updated August 25, 2011 Introduction In October, 2008, the Division of Welfare and Supportive Services (DWSS) announced the introduction of secure e-mail through ASM 17-08.
How to setup Electronic Claims
 How to setup Electronic Claims Copyright DSOFT SYSTEMS Inc. Page 1 Introduction Electronic Claims is the automation of medical claim submission. Instead of printing the HCFA form, simply generate a batch
How to setup Electronic Claims Copyright DSOFT SYSTEMS Inc. Page 1 Introduction Electronic Claims is the automation of medical claim submission. Instead of printing the HCFA form, simply generate a batch
FTP Use. Internal NPS FTP site instructions using Internet Explorer:
 FTP Use File Transfer Protocol (FTP), a standard Internet protocol, is the simplest way to exchange files between computers on the Internet. Like the Hypertext Transfer Protocol (HTTP), which transfers
FTP Use File Transfer Protocol (FTP), a standard Internet protocol, is the simplest way to exchange files between computers on the Internet. Like the Hypertext Transfer Protocol (HTTP), which transfers
Montefiore Portal Quick Reference Guide
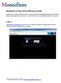 Montefiore Portal Quick Reference Guide Montefiore s remote portal allows users to securely access Windows applications, file shares, internal web applications, and more. To use the Portal, you must already
Montefiore Portal Quick Reference Guide Montefiore s remote portal allows users to securely access Windows applications, file shares, internal web applications, and more. To use the Portal, you must already
Can I manually trigger secure e-mail to encrypt a message that does not contain PI or other sensitive information? Yes, by use of the word TID.
 How does Secure E-mail work? When an e-mail is initiated or responded to the secure e-mail algorithm will determine if the e-mail needs to be encrypted based on predefined criteria. If it meets the predefined
How does Secure E-mail work? When an e-mail is initiated or responded to the secure e-mail algorithm will determine if the e-mail needs to be encrypted based on predefined criteria. If it meets the predefined
Secure File Transfer Protocol Updated Procedures. June 20, 2011
 Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
Mimecast Services for Outlook (MSO4)
 Mimecast Services for Outlook (MSO4) End User Quick Start Guide for Outlook 2010/2013 Mimecast Services for Outlook (MSO 4) is a software application that integrates with your Microsoft Outlook. Once installed,
Mimecast Services for Outlook (MSO4) End User Quick Start Guide for Outlook 2010/2013 Mimecast Services for Outlook (MSO 4) is a software application that integrates with your Microsoft Outlook. Once installed,
Secure Mail Registration and Viewing Procedures
 Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Email Encryption User Guide
 Email Encryption User Guide August, 2013 Adapted from: Cisco Registered Envelope Recipient Guide Cisco Systems, Inc. TABLE of CONTENTS Section 1: Overview of Email Encryption... 3 Page Section 2: Overview
Email Encryption User Guide August, 2013 Adapted from: Cisco Registered Envelope Recipient Guide Cisco Systems, Inc. TABLE of CONTENTS Section 1: Overview of Email Encryption... 3 Page Section 2: Overview
OCAN - Ontario Common Assessment of Need
 Community Mental Health Common Assessment Project OCAN - Ontario Common Assessment of Need Data File Submission and Report Retrieval Via Secure File Transfer Protocol (SFTP) Table of Contents 1. Document
Community Mental Health Common Assessment Project OCAN - Ontario Common Assessment of Need Data File Submission and Report Retrieval Via Secure File Transfer Protocol (SFTP) Table of Contents 1. Document
Air Resources Board File Transfer Protocol (FTP)
 Air Resources Board File Transfer Protocol (FTP) A Handbook for External Users (those not connected to the ARB network) July 2006 How do I use ARB FTP? What is the FTP server and who can use it? What software
Air Resources Board File Transfer Protocol (FTP) A Handbook for External Users (those not connected to the ARB network) July 2006 How do I use ARB FTP? What is the FTP server and who can use it? What software
6. Is it mandatory to have the digital certificate issued from NICCA?...3. 7. Is it mandatory for the sender and receiver to have a NIC email id?...
 FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
FTP Accounts Contents
 FTP Accounts Contents Goal... 2 1. Add an FTP Account... 2 2. The FTP Account Management Table... 3 3. Remove an FTP Account... 4 4. Edit an FTP Account's Quota... 4 5. Change an FTP Account's Password...
FTP Accounts Contents Goal... 2 1. Add an FTP Account... 2 2. The FTP Account Management Table... 3 3. Remove an FTP Account... 4 4. Edit an FTP Account's Quota... 4 5. Change an FTP Account's Password...
File Transfer with Secure FTP
 File Transfer with Secure FTP The Princeton Review values the security of all client s information and would like to encourage all FTP file transfers to and from our clients be conducted utilizing a Secure
File Transfer with Secure FTP The Princeton Review values the security of all client s information and would like to encourage all FTP file transfers to and from our clients be conducted utilizing a Secure
DSI File Server Client Documentation
 Updated 11/23/2009 Page 1 of 10 Table Of Contents 1.0 OVERVIEW... 3 1.0.1 CONNECTING USING AN FTP CLIENT... 3 1.0.2 CONNECTING USING THE WEB INTERFACE... 3 1.0.3 GETTING AN ACCOUNT... 3 2.0 TRANSFERRING
Updated 11/23/2009 Page 1 of 10 Table Of Contents 1.0 OVERVIEW... 3 1.0.1 CONNECTING USING AN FTP CLIENT... 3 1.0.2 CONNECTING USING THE WEB INTERFACE... 3 1.0.3 GETTING AN ACCOUNT... 3 2.0 TRANSFERRING
Use your UNNCNetID and password to log in. The first time you login to the system, you may receive the following screen:
 (Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. Personnel at UNMC occasionally need
(Secure FTP to/from Outside (non-unmc Parties) Information Technology Services July 2012 Contact the ITS Helpdesk at 402-559-7700 or [email protected] with questions. Personnel at UNMC occasionally need
User Guide. The AMF's File Transfer Service (FTS)
 User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
Green Climate Fund Online Accreditation System: User s Guide
 Green Climate Fund Online Accreditation System: User s Guide Page b Table of Contents I. Introduction 1 II. Contacting the Fund s administrator 1 III. Setting your account 1 IV. Accessing and logging into
Green Climate Fund Online Accreditation System: User s Guide Page b Table of Contents I. Introduction 1 II. Contacting the Fund s administrator 1 III. Setting your account 1 IV. Accessing and logging into
Welcome to the TransPerfect Translations Secure File Transfer Website What is Secure FTP?
 Welcome to the TransPerfect Translations Secure File Transfer Website What is Secure FTP? SFTP (Secure File Transfer Protocol) is an added layer of security provided to our clients. SFTP requires an encrypted
Welcome to the TransPerfect Translations Secure File Transfer Website What is Secure FTP? SFTP (Secure File Transfer Protocol) is an added layer of security provided to our clients. SFTP requires an encrypted
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
PDG Software. Encryption Guide
 Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2006 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2006 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
eadvantage Certificate Enrollment Procedures
 eadvantage Certificate Enrollment Procedures Purpose: Instructions for members to obtain a digital certificate which is a requirement to conduct financial transactions with the Federal Home Loan Bank of
eadvantage Certificate Enrollment Procedures Purpose: Instructions for members to obtain a digital certificate which is a requirement to conduct financial transactions with the Federal Home Loan Bank of
Using Internet or Windows Explorer to Upload Your Site
 Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
This document provides a brief, end-user overview of the Cisco Registered Envelop Service which has been implemented by Sterne Agee.
 Email Encryption User Guide Sterne Agee is committed to the security of your information. We have implemented Cisco Email Encryption to secure email communication so that only you can open it.* Questions?
Email Encryption User Guide Sterne Agee is committed to the security of your information. We have implemented Cisco Email Encryption to secure email communication so that only you can open it.* Questions?
LiteCommerce Advanced Security Module. Version 2.8
 LiteCommerce Advanced Security Module Version 2.8 Reference Manual Revision date: Jul/03/2007 LiteCommerce Advanced Security Module Reference Manual I Table of Contents Introduction...1 Administrator...2
LiteCommerce Advanced Security Module Version 2.8 Reference Manual Revision date: Jul/03/2007 LiteCommerce Advanced Security Module Reference Manual I Table of Contents Introduction...1 Administrator...2
Secure Email User Guide Receiving Secure Email from Merchants Bank
 Secure Email User Guide Receiving Secure Email from Merchants Bank Contents This document provides a brief, end-user overview of the Cisco Registered Envelope Service Email system which has been implemented
Secure Email User Guide Receiving Secure Email from Merchants Bank Contents This document provides a brief, end-user overview of the Cisco Registered Envelope Service Email system which has been implemented
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Your Archiving Service
 It s as simple as 1, 2, 3 This email archiving setup guide provides you with easy to follow instructions on how to setup your new archiving service as well as how to create archiving users and assign archiving
It s as simple as 1, 2, 3 This email archiving setup guide provides you with easy to follow instructions on how to setup your new archiving service as well as how to create archiving users and assign archiving
https://weboffice.edu.pe.ca/
 NETSTORAGE MANUAL INTRODUCTION Virtual Office will provide you with access to NetStorage, a simple and convenient way to access your network drives through a Web browser. You can access the files on your
NETSTORAGE MANUAL INTRODUCTION Virtual Office will provide you with access to NetStorage, a simple and convenient way to access your network drives through a Web browser. You can access the files on your
Law School Computing Services User Memo
 Law School Computing Services User Memo Accessing and Using Shared No. 37 7/28/2015 Email Accounts in Outlook Overview: Many Law School departments and organizations use shared email accounts. Shared email
Law School Computing Services User Memo Accessing and Using Shared No. 37 7/28/2015 Email Accounts in Outlook Overview: Many Law School departments and organizations use shared email accounts. Shared email
Global TAC Secure FTP Site Customer User Guide
 Global TAC Secure FTP Site Customer User Guide Introduction This guide is provided to assist you in using the GTAC Secure FTP site. This site resides in the Houston Remote Services Center (RSC), and is
Global TAC Secure FTP Site Customer User Guide Introduction This guide is provided to assist you in using the GTAC Secure FTP site. This site resides in the Houston Remote Services Center (RSC), and is
Methods available to GHP for out of band PUBLIC key distribution and verification.
 GHP PGP and FTP Client Setup Document 1 of 7 10/14/2004 3:37 PM This document defines the components of PGP and FTP for encryption, authentication and FTP password changes. It covers the generation and
GHP PGP and FTP Client Setup Document 1 of 7 10/14/2004 3:37 PM This document defines the components of PGP and FTP for encryption, authentication and FTP password changes. It covers the generation and
Encryption Key Best Practices Nasuni Corporation Natick, MA
 Nasuni Corporation Natick, MA Summary of Best Practices Recommendations The best practices for managing encryption keys for the Nasuni Filer include the following: If your enterprise has existing OpenPGP-compatible
Nasuni Corporation Natick, MA Summary of Best Practices Recommendations The best practices for managing encryption keys for the Nasuni Filer include the following: If your enterprise has existing OpenPGP-compatible
Secure Data Transfer
 Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
Experian Secure Transport Service
 Experian Secure Transport Service Secure Transport Overview In an effort to provide higher levels of data protection and standardize our file transfer processes, Experian will be utilizing the Secure Transport
Experian Secure Transport Service Secure Transport Overview In an effort to provide higher levels of data protection and standardize our file transfer processes, Experian will be utilizing the Secure Transport
IIS, FTP Server and Windows
 IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
SFTP Server User Login Instructions. Open Internet explorer and enter the following url: https://sftp.sae.org
 SFTP Server User Login Instructions Open Internet explorer and enter the following url: https://sftp.sae.org You will be prompted for a user id and password as such. Please enter your account id and password.
SFTP Server User Login Instructions Open Internet explorer and enter the following url: https://sftp.sae.org You will be prompted for a user id and password as such. Please enter your account id and password.
Overview Keys. Overview
 Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
Overview Keys Overview The PGPmail program performs fast, high-security, public-key encrypting (with optional compression), decrypting, and authenticating of electronic messages and files. The program
Unifying Information Security. Implementing TLS on the CLEARSWIFT SECURE Email Gateway
 Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Unifying Information Security Implementing TLS on the CLEARSWIFT SECURE Email Gateway Contents 1 Introduction... 3 2 Understanding TLS... 4 3 Clearswift s Application of TLS... 5 3.1 Opportunistic TLS...
Setting Up Microsoft Outlook 2007 with GroupWise
 Setting Up Microsoft Outlook 2007 with GroupWise This page is one of several you might come across on our website discussing how to setup Outlook with GroupWise. We provide several sets of instructions
Setting Up Microsoft Outlook 2007 with GroupWise This page is one of several you might come across on our website discussing how to setup Outlook with GroupWise. We provide several sets of instructions
DSHS Secure FTP Instructions
 DSHS Secure FTP Instructions NOTE: Screenshots are for illustration purposes only! Please follow written directions! Important directions will be in RED. Getting logged into the DSHS secure ftp server:
DSHS Secure FTP Instructions NOTE: Screenshots are for illustration purposes only! Please follow written directions! Important directions will be in RED. Getting logged into the DSHS secure ftp server:
Using Voltage SecureMail
 Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
WinSCP: Secure File Transfer Using WinSCP for Secure File Transfer on Windows
 WinSCP: Secure File Transfer Using WinSCP for Secure File Transfer on Windows Overview WinSCP is an SFTP (Secure File Transfer Protocol), FTP (File Transfer Protocol), and SCP (Secure Copy Protocol) application
WinSCP: Secure File Transfer Using WinSCP for Secure File Transfer on Windows Overview WinSCP is an SFTP (Secure File Transfer Protocol), FTP (File Transfer Protocol), and SCP (Secure Copy Protocol) application
Guide to the Configuration and Use of SFTP Clients for Uploading Digital Treatment Planning Data to IROC RI
 Guide to the Configuration and Use of SFTP Clients for Uploading Digital Treatment Planning Data to IROC RI The Quality Assurance Review Center has tested several SFTP client programs for submitting digital
Guide to the Configuration and Use of SFTP Clients for Uploading Digital Treatment Planning Data to IROC RI The Quality Assurance Review Center has tested several SFTP client programs for submitting digital
Managed Devices - Web Browser/HiView
 Managed Devices - Web Browser/HiView All Hirschmann managed devices have a web based GUI interface available for configuration purposes. This is typically the primary means of configuration used for most
Managed Devices - Web Browser/HiView All Hirschmann managed devices have a web based GUI interface available for configuration purposes. This is typically the primary means of configuration used for most
File Share Service User guide
 File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE
 WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both.
WHITE PAPER MANAGED FILE TRANSFER: 10 STEPS TO HIPAA/HITECH COMPLIANCE 1. OVERVIEW Do you want to design a file transfer process that is secure? Or one that is compliant? Of course, the answer is both.
IBM Aspera Add-in for Microsoft Outlook 1.3.2
 IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
Marcum LLP MFT Guide
 MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
MFT Guide Contents 1. Logging In...3 2. Installing the Upload Wizard...4 3. Uploading Files Using the Upload Wizard...5 4. Downloading Files Using the Upload Wizard...8 5. Frequently Asked Questions...9
SchoolBooking SSO Integration Guide
 SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
E-LEARNING STUDENT S MANUAL
 E-LEARNING STUDENT S MANUAL By Williams College E-Learning is the College s Online Learning Environment, designed to enhance your learning experience by providing access to online course materials, activities,
E-LEARNING STUDENT S MANUAL By Williams College E-Learning is the College s Online Learning Environment, designed to enhance your learning experience by providing access to online course materials, activities,
educ Office 365 email: Remove & create new Outlook profile
 Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
An Introduction to Secure Email. Presented by: Addam Schroll IT Security & Privacy Analyst
 An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
How to Add or Change a Billing Agent and Other Claim Submission Options in NCTracks
 How to Add or Change a Billing Agent and Other Claim Submission Options in NCTracks Overview This user guide provides step-by-step instructions for adding or changing a billing agent or making other claim
How to Add or Change a Billing Agent and Other Claim Submission Options in NCTracks Overview This user guide provides step-by-step instructions for adding or changing a billing agent or making other claim
Microsoft OneDrive. How to login to OneDrive:
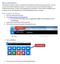 Microsoft OneDrive The beauty of OneDrive is that it is accessible from anywhere you have an Internet connection. You can access it from a Mac or Windows computer. You can even access it on your Smartphone
Microsoft OneDrive The beauty of OneDrive is that it is accessible from anywhere you have an Internet connection. You can access it from a Mac or Windows computer. You can even access it on your Smartphone
8x8 Click2Pop User Guide
 USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
USER GUIDE 8x8 User Guide Getting Started with April 2014 Contents Introduction... 3 What s new.... 3 8x8.... 3 Here is how works...4 8x8 Click2Connect.... 4 Requirements.... 4 Installation on Microsoft
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
Clearswift Information Governance
 Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Clearswift Information Governance Implementing the CLEARSWIFT SECURE Encryption Portal on the CLEARSWIFT SECURE Email Gateway Version 1.10 02/09/13 Contents 1 Introduction... 3 2 How it Works... 4 3 Configuration
Ad Hoc (Temporary) Accounts Instructions
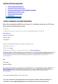 DLG/PDV SFTP Server Instructions 1. Ad Hoc (Temporary) Accounts. 2. LeadsGen (Permanent) Accounts. 3. Manually configuring SFTP Clients (WinSCP & FileZilla). 4. Uploading files into SFTP server. 5. Frequently
DLG/PDV SFTP Server Instructions 1. Ad Hoc (Temporary) Accounts. 2. LeadsGen (Permanent) Accounts. 3. Manually configuring SFTP Clients (WinSCP & FileZilla). 4. Uploading files into SFTP server. 5. Frequently
FAQs. OneDrive for Business?
 Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
Contents FAQs... 1 From a Web Browser (for PCs and mobile devices)... 1 From the OneDrive for Business Sync Application (for PCs only)... 2 From Office 2013 (for PCs only)... 3 From the OneDrive for Business
HIPAA Transaction ANSI X12 835 Companion Guide
 HIPAA Transaction ANSI X12 835 Companion Guide HIPAA ASC x12 V5010X279A1 Version: 1.0 11/1/2013 Document History DOCUMENT VERSION HISTORY TABLE Version Sections Revised Description Revised By Date 2 Table
HIPAA Transaction ANSI X12 835 Companion Guide HIPAA ASC x12 V5010X279A1 Version: 1.0 11/1/2013 Document History DOCUMENT VERSION HISTORY TABLE Version Sections Revised Description Revised By Date 2 Table
EDGETECH FTP SITE CUSTOMER & VENDOR ACCESS
 EDGETECH FTP SITE CUSTOMER & VENDOR ACCESS 1. The EdgeTech FTP site is a web hosted site, not a true FTP site, remember to use http:// not ftp:// in the web address. IMPORTANT: Do Not use FileZilla or
EDGETECH FTP SITE CUSTOMER & VENDOR ACCESS 1. The EdgeTech FTP site is a web hosted site, not a true FTP site, remember to use http:// not ftp:// in the web address. IMPORTANT: Do Not use FileZilla or
Secure Email User Guide
 Secure Email User Guide Contents Secure email at HSBC. 2 About SecureMail... 2 Receiving a secure email sent via SecureMail 3 Opening a secure email sent via SecureMail... 4 Resetting your SecureMail password..
Secure Email User Guide Contents Secure email at HSBC. 2 About SecureMail... 2 Receiving a secure email sent via SecureMail 3 Opening a secure email sent via SecureMail... 4 Resetting your SecureMail password..
Schools Remote Access Server
 Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
Schools Remote Access Server This system is for school use only. Not for personal or private file use. Please observe all of the school district IT rules. 6076 State Farm Rd., Guilderland, NY 12084 Phone:
EDI Insight Manual. Training Manual. Presented By
 EDI Insight Manual Training Manual Presented By EDI Insight Manual 2 Step 1 Upload File: Select the file to transmit on the eceno claims transmission screen and click connect. Login to EDI Insight, when
EDI Insight Manual Training Manual Presented By EDI Insight Manual 2 Step 1 Upload File: Select the file to transmit on the eceno claims transmission screen and click connect. Login to EDI Insight, when
Installation Guide. Before We Begin: Please verify your practice management system is compatible with Dental Collect Enterprise.
 Installation Guide Before We Begin: Please verify your practice management system is compatible with Dental Collect Enterprise. Compatibility List: https://www.sikkasoft.com/pms-fs-supported-by-spu/ NOTE:
Installation Guide Before We Begin: Please verify your practice management system is compatible with Dental Collect Enterprise. Compatibility List: https://www.sikkasoft.com/pms-fs-supported-by-spu/ NOTE:
PayFlex FTP - Wired Commute
 PayFlex FTP - Wired Commute What is FTP? FTP stands for File Transfer Protocol. PayFlex uses FTP to send and receive files from our clients. We do so through a secure website that uses PGP encryption to
PayFlex FTP - Wired Commute What is FTP? FTP stands for File Transfer Protocol. PayFlex uses FTP to send and receive files from our clients. We do so through a secure website that uses PGP encryption to
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Outlook Data File navigate to the PST file that you want to open, select it and choose OK. The file will now appear as a folder in Outlook.
 Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Commport FTP Client Set-up
 Commport FTP Client Set-up Instructions for downloading and installing the Commport FTP Client. Version 1.2 Commport Communications International, inc. May 2013 Download from Commport Website: http://www.commport.com/documents/commportftpclientsetup.zip
Commport FTP Client Set-up Instructions for downloading and installing the Commport FTP Client. Version 1.2 Commport Communications International, inc. May 2013 Download from Commport Website: http://www.commport.com/documents/commportftpclientsetup.zip
Configure Backup Server for Cisco Unified Communications Manager
 Configure Backup Server for Cisco Unified Communications Manager Document ID: 110309 Contents Introduction Prerequisites Requirements Components Used Conventions Configure a Backup Server for Cisco Unified
Configure Backup Server for Cisco Unified Communications Manager Document ID: 110309 Contents Introduction Prerequisites Requirements Components Used Conventions Configure a Backup Server for Cisco Unified
Secure Email Client User Guide Receiving Secure Email from Mercantile Bank
 Receiving Secure Email from Contents This document provides a brief, end-user overview of the Secure Email system which has been implemented by. Why Secure Email? When someone sends you an email, the email
Receiving Secure Email from Contents This document provides a brief, end-user overview of the Secure Email system which has been implemented by. Why Secure Email? When someone sends you an email, the email
Redtail CRM Integration. Users Guide. 2011 Cities Digital, Inc. All rights reserved. Contents i
 Redtail CRM Integration Users Guide 2011 Cities Digital, Inc. All rights reserved. Contents i Contents Redtail Integration with Laserfiche by Cities Digital 1 Overview... 1 Requirements 3 Minimum Server
Redtail CRM Integration Users Guide 2011 Cities Digital, Inc. All rights reserved. Contents i Contents Redtail Integration with Laserfiche by Cities Digital 1 Overview... 1 Requirements 3 Minimum Server
