Free and Legal Software You Can Download By Tom Krauser
|
|
|
- Bethanie Goodwin
- 9 years ago
- Views:
Transcription
1 Free and Legal Software You Can Download By Tom Krauser Here is a list of free programs that you can download for your personal use. They are legal and free for you to install. Some may have restrictions for non-personal use. NOTE: When installing software be careful to read the screens that have software offers on them. Many free software offers want to install other products as part of the installation process. It is not that these additional software products are bad but you just may not want them on your computer. During the installation process, look for windows with check boxes or Accept/Decline buttons to ensure you are not installing software products you may not want. Sometimes you have to read the offers very carefully to see how to decline the offer to install the additional software. Some examples of this are free software that wants to install the Ask search engine and make it your default search engine or it may want you to install a weather program or Google Chrome. If you do accidentally install these products you can always uninstall them using the control panel to remove them. Also, look for check boxes that want you to install the trial version of the software because after the trial period is over it will start asking you to upgrade and pay for the real version. CAUTION: Also, due to the way some viruses are installed you may want to go directly to a trusted site to install updates instead of installing through the pop-up that says an update is available. For example, one virus is a fake Adobe Flash software update. It tells you that Adobe Flash (used for videos) needs to be updated and to click on the window to update it. It could actually be a virus that will download and install when you click on the Install button. You should go directly to the Adobe site ( to install the latest version. The same thing applies for updating Java ( See discussion on Adobe Flash and Java later. CAUTION: If you get a pop-up telling you that you have a virus or something wrong with your computer and to click a button to remove the threats and you do not recognize the program giving you the message, you should not click ANYWHERE on the pop-up window including the X in the upper right hand corner and instead use Task Manager to end that process. To start the Task Manager in Windows press Ctrl-Alt-Delete keys at the same time. This will bring up a menu then choose Start Task Manager from this menu. When Task Manager is up look under Applications tab and find the application with the same heading as the pop-up windows. Select this application and then click on End Task at the bottom. This will close the application without having to click anywhere in the pop-up windows telling you that you have a virus or problem. If this window keeps coming up it is a sign that you have malware installed and you should run a Full virus scan of your computer plus install and run the malware programs discussed later.
2 Browsers A browser is the software that you use to connect to the internet with. It provides the Graphical User Interface (GUI) that lays out the web page for your viewing. Windows operating systems automatically come with Internet Explorer (IE). You should have more than one internet browser installed. If Internet Explorer (IE) is your only browser and it gets a virus or corrupted you should have a way to get to the internet to find a repair for IE or update virus scan info. You may find you like one of the following browsers better than IE and you can make it your default browser. There are more browsers you can install besides those below. Mozilla Firefox Google Chrome Apple Safari The following link does a review of some popular browsers by PC Magazine: Anti-Virus Programs NOTE: You should only be using one anti-virus program at a time. Using more than one antivirus program at a time can cause conflicts with each other. You should uninstall any anti-virus programs you are not using. Windows Defender from Microsoft comes built into Windows 8. Probably due to anti-trust reasons it usually may not be active if a trial version of another anti-virus is installed on the new computer. You can uninstall the trial software and make Windows Defender active. This is the same program as Microsoft Security Essentials used on earlier versions of Windows. Microsoft Security Essentials can be downloaded free from Microsoft This is a free anti-virus program from Microsoft. It is used on Windows 7 and Vista. It no longer works with XP but you can use AVG on XP. AVG Free AVG works with Windows XP still. AVAST Free Compodo Anti-Virus
3 Malware Software Malware are programs that are not considered viruses but can have very detrimental effects on your computer. They can hijack your browser or start downloading programs you do not want. They can redirect your browser to unwanted websites or give pop-up ads you do not want to see. Many anti-virus programs do catch malware but the following programs seem to find malware that the anti-virus programs miss. Malwarebytes The free version of this program has to be run manually and is not real time unless you purchase the paid version. This program finds malware that others don t seem to find. Under Settings/Detection and Protection check the box for Scan for rootkits. Under Settings/Update Settings change the notify if out of date setting to 1 day. You may also want to download Spybot - Search and Destroy below for additional protection. Malwarebytes Anit-Exploit Select Malwarebytes Anti-Exploit Free Download. This runs real time with your anti-virus. Malwarebytes Anit-Rootkit Select the Malwarebyets Anti-Rootkit (Beta) installation. Install and run the program. This may take awhile to run. Malwarebytes Chameleon If your computer is infected and will not let you install malware software try to install Malwarebytes Chamelon. This program is designed to be installed on infected computers to run a malware scan. Spybot Search and Destroy Spybot - Search and Destroy is very useful to get rid of malware that other programs may not detect. It has found malware that Malwarebytes did not detect. You can download both Malwarebytes and Spybot since both are manually run and do not interfere with each other. They can even be run at the same time as each other and while your anti-virus program is performing a scan. Make sure you click the free version and not the paid or trial version.
4 Firewalls Note: You can only run one firewall at a time. A firewall is necessary to keep unauthorized sites from accessing your computer or to block outgoing traffic that may be malicious. Windows comes with its own firewall which is what most people use but many people like to use a 3 rd party firewall instead of the Windows firewall. If you install a different firewall you must make sure that the other firewalls are uninstalled or disabled. The firewall installation software will usually disable the Windows firewall automatically as part of the install process. ZoneAlarm ZoneAlarm is one of the most popular 3 rd party firewalls. The link below from PC Magazine discusses some free firewall programs: Utility downloads and useful information websites Kim Komando website This website gives a lot of useful info and safe downloads. Sign up for her newsletter to get useful tips in your . You can search the site for downloads you desire. Some downloads can only be downloaded if you belong to her club but many downloads can be accessed by everyone. CNET website This site gives a lot of information and safe downloads for all kinds of programs. It also gives a lot of reviews of different software that you may find useful. Belarc Advisor This program gives a lot of useful info about the software and hardware on your computer. You should run the program and print the output to save. It gives hardware/software info including license numbers. Speccy by Piriform This program gives information about the software and hardware on the PC. Internet speed test This tests the upload and download speeds for your internet provider. Compare the numbers against the speed you are supposed to be getting. Remember that if using wireless connections the wireless router may also limit/reduce the speeds.
5 CCleaner by Piriform This free program analyzes and cleans up your computer of unused/unnecessary files. It will also analyze your registry and remove unused or unnecessary entries in your registry. When cleaning the registry it gives the option of backing up the registry before it removes the suggested entries. I recommend that you backup the registry before cleaning it. NOTE: CC Cleaner can also look at the add-ons for the different browsers and allow you to disable or remove add-ons that may be causing problems with your browsers such as unwanted pop-ups or redirects without the browser being open. I have used this program to get rid of browser pop-ups and redirects. I would recommend using this feature while the browsers are closed to make it easier to remove them. StickyPad Notes You may want to leave notes on your desktop to remind you of upcoming things you want to take care of. StickyPad Notes are Post It notes for your desktop that remind you of things your want to take care of. Microsoft Office Free Replacement LibreOffice Suite Download both program and Help files. Under Tools/Options select Load/Save then General Set the different document types to the Microsoft Office 2003/2007/2103 XML version. This program reads and creates Microsoft Office files. Photo/Graphics Programs Picasa by Google This is a nice program for keeping track of your photos. On the setup select to locate photos in the normal document areas and not the whole computer. It allows you to easily see all the photos on your computer and gives nice editing features for the photos. Photoshop replacement Gimp Gimp is a replacement for Photoshop photo editor. It allows you to edit photos and put special effects on photos.
6 PDF Printer It is nice to be able to print documents as a Portable Document Format (PDF) file that can be stored as a file or ed to someone. After you install the PDF printer it becomes a printer choice when you choose the Print button. You select the PDF printer as the desired printer and instead of printing the document out to a physical printer it asks you where you want to save it. You can select any location such as Documents or Desktop and give the document any name that you desire. After it is saved you can attach the file to an if you want to mail it to someone. The saved document looks exactly like the original document did. CutePDFWriter This program prints documents as PDF files so they can be stored or ed. Also have to install the PDF converter program (part of install process). You can select it as the printer to print out PDF files which can be read by anyone and sent as s. dopdf Printer Tools If you do not have Microsoft Office and have an older version of Windows, you may only have Outlook Express for your program. Newer versions of Windows may come with Windows Live Mail. If you want to download your from the server to your computer, you can replace Outlook Express with the following program which is equivalent to the version of Outlook that comes with Microsoft Office. Thunderbird by Mozilla Free program to replace Microsoft Outlook. This program can automatically download your from several programs. Some programs (such as Yahoo) do not allow to be downloaded. Thunderbird Calendar add on. Thisadd on gives a calendar function to Thunderbird. Zimbra Free program to replace Microsoft Outlook. Get , contacts, and calendar all in one application. Easily set up Zimbra, Yahoo. Mail Plus, AOL and Gmail accounts with the Account Wizard. Any POP or IMAP account can be added to Zimbra Desktop, there's no limit to the size of your storage, and Zimbra Desktop works online and offline. The following link shows 11 programs that are free that you can use to handle .
7 Adobe Reader Adobe Flash Java Adobe Reader used to read PDF files. Install the latest version of Adobe Reader for reading PDF files. Adobe Flash is used by many programs to support graphics and video. It may already be installed on your computer. If you get a message saying Flash needs to be updated verify the actual update link it to adobe.com, you can always go directly to the adobe site to ensure you have the latest version. Go to the following site: I create a shortcut link on my desktop to go directly to this site for updates: Right click on desktop and choose New then Shortcut. Copy the link above into the location field then click Next. Type Adobe Flash Update for name of shortcut then click Finish. You can also change the Icon by right clicking on the Icon and select Properties. Click Change Icon to see available icons. If you do not see any icons you like you can browse to the following file: C:\Windows\System32\Shell32.dll or C:\W\indows\System32\moricons.dll These files contains a lot of different icons you can choose from. Select the icon you like for the shortcut and then click OK. Then click Apply and OK. There is a lot of controversy on whether Java should be installed or not. A lot of malware uses weaknesses in Java to install their programs. There are some programs that require Java to be installed in order to work. The following site should be used to ensure that your Java is the latest version. It can also remove older versions of Java if they are installed. Be sure to uncheck the additional software suggestions or decline them during the installation process. I create a shortcut link on my desktop to go directly to this site for updates: Right click on desktop and choose New then Shortcut. Copy the link above into the location field then click Next. Type Java Update for name of shortcut then click Finish. You can also change the Icon by right clicking on the Icon and select Properties. Click Change Icon to see available icons. If you do not see any icons you like you can click on Browse then browse to the following file: C:\Windows\System32\Shell32.dll or C:\W\indows\System32\moricons.dll These files contains a lot of different icons you can choose from. Select the icon you like for the shortcut and then click OK. Then click Apply and OK.
How To Use Moodle Online Class On A Pc Or Mac Or Ipad (For Acedo) On A Computer Or Mac) On Your Computer Or Ipod Or Ipo (For An Ipo) For Acedor Or Mac (
 Welcome to Stanly Online, This document has been sent to you to supply the information you need to: access our online learning system AND find help, should the need arise Accessing : Your online class
Welcome to Stanly Online, This document has been sent to you to supply the information you need to: access our online learning system AND find help, should the need arise Accessing : Your online class
Get Started Guide - PC Tools Internet Security
 Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
How to easily clean an infected computer (Malware Removal Guide)
 How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
In order to get the most out of your Bert Rodgers courses, it is important to ensure that your computer meets some minimum system requirements.
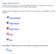 System Requirements In order to get the most out of your Bert Rodgers courses, it is important to ensure that your computer meets some minimum system requirements. Please select your preferred or current
System Requirements In order to get the most out of your Bert Rodgers courses, it is important to ensure that your computer meets some minimum system requirements. Please select your preferred or current
Antivirus. Quick Start Guide. Antivirus
 Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Microsoft Security Essentials Installation and Configuration Guide
 Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
Dartmouth College Technical Support Document for Kronos PC version
 Dartmouth College Technical Support Document for Kronos PC version Contents How to Save the Kronos URL as a Favorite or Bookmark... 2 Internet Explorer... 2 Firefox... 4 Possible Problems When Logging
Dartmouth College Technical Support Document for Kronos PC version Contents How to Save the Kronos URL as a Favorite or Bookmark... 2 Internet Explorer... 2 Firefox... 4 Possible Problems When Logging
Quick Start. Installing the software. for Webroot Internet Security Complete, Version 7.0
 Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
Preparing Your Personal Computer to Connect to the VPN
 Preparing Your Personal Computer to Connect to the VPN (Protecting Your Personal Computer Running Windows) Using the VPN to connect your computer to the campus network is the same as bringing your computer
Preparing Your Personal Computer to Connect to the VPN (Protecting Your Personal Computer Running Windows) Using the VPN to connect your computer to the campus network is the same as bringing your computer
OPS Data Quick Start Guide
 OPS Data Quick Start Guide OPS Data Features Guide Revision: October, 2014 Technical Support (24/7) - (334) 705-1605 http://www.opelikapower.com Quick Start Guide OPS Data: Beginning today, you have access
OPS Data Quick Start Guide OPS Data Features Guide Revision: October, 2014 Technical Support (24/7) - (334) 705-1605 http://www.opelikapower.com Quick Start Guide OPS Data: Beginning today, you have access
PC Security & Housekeeping March 2015
 PC Security & Housekeeping March 2015 Anti-malware programs Always keep your firewall, anti-virus, and anti-spyware products up to date! There are many good commercial products available, such as: o Norton
PC Security & Housekeeping March 2015 Anti-malware programs Always keep your firewall, anti-virus, and anti-spyware products up to date! There are many good commercial products available, such as: o Norton
How To Use Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
BULLGUARD BAckUp GUIDE
 BULLGUARD backup GUIDE CONTENTS BullGuard Backup introduction page 3 Installing BullGuard Backup page 6 Uninstalling BullGuard Backup page 11 Registering BullGuard Backup: creating an account page 12 Running
BULLGUARD backup GUIDE CONTENTS BullGuard Backup introduction page 3 Installing BullGuard Backup page 6 Uninstalling BullGuard Backup page 11 Registering BullGuard Backup: creating an account page 12 Running
Troubleshooting steps for Oracle Financials and Markview. Jan 2015
 Troubleshooting steps for Oracle Financials and Markview Jan 2015 RU-VPN... 3 RECOMMENDED BROWSERS AND BROWSER SETTINGS... 4 Mozilla Firefox... 4 Internet Explorer... 5 CHROME... 7 Verify JAVA Version...
Troubleshooting steps for Oracle Financials and Markview Jan 2015 RU-VPN... 3 RECOMMENDED BROWSERS AND BROWSER SETTINGS... 4 Mozilla Firefox... 4 Internet Explorer... 5 CHROME... 7 Verify JAVA Version...
SURPASS HOSTING SERVICE GETTING STARTED AND OPERATIONS GUIDE
 SURPASS HOSTING SERVICE GETTING STARTED AND OPERATIONS GUIDE Welcome To Surpass Hosting Service. This document contains instructions to help you get up and running with your new service. The instructions
SURPASS HOSTING SERVICE GETTING STARTED AND OPERATIONS GUIDE Welcome To Surpass Hosting Service. This document contains instructions to help you get up and running with your new service. The instructions
Adobe Reader Settings
 Adobe Reader Settings Table of Contents Adobe 9 and X (10) Reader Settings...2 For Adobe Reader X (10)... 5 Adobe Reader XI (11)...7 Internet Explorer 8 and 9... 8 Google Chrome... 9 Mozilla Firefox...
Adobe Reader Settings Table of Contents Adobe 9 and X (10) Reader Settings...2 For Adobe Reader X (10)... 5 Adobe Reader XI (11)...7 Internet Explorer 8 and 9... 8 Google Chrome... 9 Mozilla Firefox...
Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer?
 Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer? 1 2 This is the second part of a two-part course on spyware and adware. In this portion of the course we will: Review
Welcome to Part 2 of the online course, Spyware and Adware What s in Your Computer? 1 2 This is the second part of a two-part course on spyware and adware. In this portion of the course we will: Review
Remote Access to Niagara Wheatfield s Computer Network
 Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9
 Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9 If you are not working from a Windows 7 or 8 computer, you will need to update: Windows XP to Service Pack 3 Windows Vista
Before You Begin Your Computer Must Meet the System Requirements to Access Cloud9 If you are not working from a Windows 7 or 8 computer, you will need to update: Windows XP to Service Pack 3 Windows Vista
Technical Specifications. Technical requirements for Eversheds E-Learning and Learning Management System (LMS)
 Technical Specifications Technical requirements for Eversheds E-Learning and Learning Management System (LMS) 1 Learning Management System (LMS) Client Requirements... 3 Web browsers... 3 ActiveX security
Technical Specifications Technical requirements for Eversheds E-Learning and Learning Management System (LMS) 1 Learning Management System (LMS) Client Requirements... 3 Web browsers... 3 ActiveX security
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM
 REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
How to Disable Common Pop-Up Blockers
 How to Disable Common Pop-Up Blockers Listed below are some of the more popular Pop-up Blocking software packages and the workarounds that should be followed in order to disable the Pop-Up blocking feature
How to Disable Common Pop-Up Blockers Listed below are some of the more popular Pop-up Blocking software packages and the workarounds that should be followed in order to disable the Pop-Up blocking feature
avast! Small Office Administration Console Small Office Administration Console User Guide
 Small Office Administration Console User Guide 1 2 Introduction to the Small Off ice Administrat ion Console The Small Office Administration Console provides central management capability for your installation
Small Office Administration Console User Guide 1 2 Introduction to the Small Off ice Administrat ion Console The Small Office Administration Console provides central management capability for your installation
Housekeeping Your PC
 for WINDOW 7 Course documentation Material at:sussex.ac.uk/its/training/material/housekeeping University of Sussex Updated: June 2011 IT Services Created: December 2002 University of Sussex IT Services
for WINDOW 7 Course documentation Material at:sussex.ac.uk/its/training/material/housekeeping University of Sussex Updated: June 2011 IT Services Created: December 2002 University of Sussex IT Services
Set Up E-mail Setup with Microsoft Outlook 2007 using POP3
 Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
INTERNET & COMPUTER SECURITY March 20, 2010. Scoville Library. [email protected]
 INTERNET & COMPUTER SECURITY March 20, 2010 Scoville Library [email protected] Internet: Computer Password strength Phishing Malware Email scams Identity Theft Viruses Windows updates Browser updates Backup
INTERNET & COMPUTER SECURITY March 20, 2010 Scoville Library [email protected] Internet: Computer Password strength Phishing Malware Email scams Identity Theft Viruses Windows updates Browser updates Backup
Quick Start Guide to Logging in to Online Banking
 Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Follow these steps to configure Outlook Express to access your Staffmail email account:
 Windows Instructions (This documentation is based on Outlook Express version 6). Outlook Express is no longer a recommended email client as it can cause unnecessary network traffic and server overload.
Windows Instructions (This documentation is based on Outlook Express version 6). Outlook Express is no longer a recommended email client as it can cause unnecessary network traffic and server overload.
HOSTED DESKTOP MANUAL
 HOSTED DESKTOP MANUAL TABLE OF CONTENTS REMOTE DESKTOP MANUAL Last revision August 18, 2005 WHAT IS A REMOTE DESKTOP... 1 Security... 1 Terminals...2 SETTING UP YOUR REMOTE DESKTOP... 2 Installing Remote
HOSTED DESKTOP MANUAL TABLE OF CONTENTS REMOTE DESKTOP MANUAL Last revision August 18, 2005 WHAT IS A REMOTE DESKTOP... 1 Security... 1 Terminals...2 SETTING UP YOUR REMOTE DESKTOP... 2 Installing Remote
Auto Archiving Folders in Outlook XP
 Auto Archiving Folders in Outlook XP Your Outlook email account on the Exchange server is allotted 50 megabytes of storage space on the server. Items in the Inbox, Calendar, Sent Items, Deleted Items,
Auto Archiving Folders in Outlook XP Your Outlook email account on the Exchange server is allotted 50 megabytes of storage space on the server. Items in the Inbox, Calendar, Sent Items, Deleted Items,
TASKSTREAM FAQs. 2. I have downloaded a lesson attachment, but I cannot open it. What is wrong?
 TASKSTREAM FAQs Why do I not receive emails from TaskStream? It could be that your email program is interpreting incoming TaskStream mail as spam, which is a term for junk mail Spam is not typically stored
TASKSTREAM FAQs Why do I not receive emails from TaskStream? It could be that your email program is interpreting incoming TaskStream mail as spam, which is a term for junk mail Spam is not typically stored
Frequently Asked Questions: Xplornet Internet Security Suite
 Frequently Asked Questions: Xplornet Internet Security Suite Before Installation: Does the Xplornet Internet Security Suite (XISS), product work with other antivirus or firewall products installed on my
Frequently Asked Questions: Xplornet Internet Security Suite Before Installation: Does the Xplornet Internet Security Suite (XISS), product work with other antivirus or firewall products installed on my
QQConnect Overview Guide
 QQConnect Overview Guide Last Updated: 3/20/2015 About QQConnect QQConnect is an add-on utility for QQCatalyst that makes it easy to transfer documents and e- mails from your Windows desktop or desktop
QQConnect Overview Guide Last Updated: 3/20/2015 About QQConnect QQConnect is an add-on utility for QQCatalyst that makes it easy to transfer documents and e- mails from your Windows desktop or desktop
Contents. Hardware Configuration... 27 Uninstalling Shortcuts Black...29
 Contents Getting Started...1 Check your Computer meets the Minimum Requirements... 1 Ensure your Computer is Running in Normal Sized Fonts... 7 Ensure your Regional Settings are Correct... 9 Reboot your
Contents Getting Started...1 Check your Computer meets the Minimum Requirements... 1 Ensure your Computer is Running in Normal Sized Fonts... 7 Ensure your Regional Settings are Correct... 9 Reboot your
Safe internet for business use: Getting Started Guide
 Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
Safe internet for business use: Getting Started Guide Table of Contents 1. Preface 1 2. Before You Install 2 2.1 Disabling Firewalls 2 2.2 About Accelerators 3 3. About Profiles 4 4. Installation and Initial
Before You Begin, Your Computer Must Meet the System Requirements
 Before You Begin, Your Computer Must Meet the System Requirements Windows: Minimum: Windows Vista SP2 or Windows 7 & 8 Remote Desktop Protocol (connection) 7.1 or higher 150 MB hard drive space 2 GB RAM
Before You Begin, Your Computer Must Meet the System Requirements Windows: Minimum: Windows Vista SP2 or Windows 7 & 8 Remote Desktop Protocol (connection) 7.1 or higher 150 MB hard drive space 2 GB RAM
GrandView. Web Client Software Requirements and Recommendations. Revision 2012.9.26
 GrandView Web Client Software Requirements and Recommendations Revision 2012.9.26 RoviSys 1455 Danner Drive Aurora, OH 44202 330-562-8600 grandviewbusinesssolutions.com TABLE OF CONTENTS Introduction...
GrandView Web Client Software Requirements and Recommendations Revision 2012.9.26 RoviSys 1455 Danner Drive Aurora, OH 44202 330-562-8600 grandviewbusinesssolutions.com TABLE OF CONTENTS Introduction...
Firewall Rules (Outbound)
 Secure File Sharing FAQ & Troubleshooting Tips Q: I am accessing Secure File Sharing through a firewall. What should I do? A: Provide the following firewall rules to your IT Professional. Firewall Rules
Secure File Sharing FAQ & Troubleshooting Tips Q: I am accessing Secure File Sharing through a firewall. What should I do? A: Provide the following firewall rules to your IT Professional. Firewall Rules
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome
 Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software
Remove ANY TOOLBAR from Internet Explorer, Firefox and Chrome Browser toolbars have been around for years, however, in the last couple of months they became a huge mess. Unfortunately, lots of free software
Malware, Spyware, Adware, Viruses. Gracie White, Scott Black Information Technology Services
 Malware, Spyware, Adware, Viruses Gracie White, Scott Black Information Technology Services The average computer user should be aware of potential threats to their computer every time they connect to the
Malware, Spyware, Adware, Viruses Gracie White, Scott Black Information Technology Services The average computer user should be aware of potential threats to their computer every time they connect to the
Law School Computing Services User Memo
 Law School Computing Services User Memo Accessing and Using Shared No. 37 7/28/2015 Email Accounts in Outlook Overview: Many Law School departments and organizations use shared email accounts. Shared email
Law School Computing Services User Memo Accessing and Using Shared No. 37 7/28/2015 Email Accounts in Outlook Overview: Many Law School departments and organizations use shared email accounts. Shared email
CHARTER BUSINESS custom hosting faqs 2010 INTERNET. Q. How do I access my email? Q. How do I change or reset a password for an email account?
 Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Student ANGEL FAQs. General Issues: System Requirements:
 Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
How to Disable Common Pop-Up Blockers
 How to Disable Common Pop-Up Blockers Listed below are some of the most popular pop-up blocking software packages, and instructions to enable pop-up windows with them. Pop-up windows must be enabled to
How to Disable Common Pop-Up Blockers Listed below are some of the most popular pop-up blocking software packages, and instructions to enable pop-up windows with them. Pop-up windows must be enabled to
Using the ScoMIS Remote Access Service (VPN Gateway) to access the ScoMIS SIMS.net Terminal Server Service.
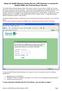 Using the ScoMIS Remote Access Service (VPN Gateway) to access the ScoMIS SIMS.net Terminal Server Service. The ScoMIS Remote Access Gateway offers a convenient method to connect direct to SIMS.net Terminal
Using the ScoMIS Remote Access Service (VPN Gateway) to access the ScoMIS SIMS.net Terminal Server Service. The ScoMIS Remote Access Gateway offers a convenient method to connect direct to SIMS.net Terminal
Amazon WorkMail. User Guide Version 1.0
 Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2016 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
USER MANUAL SlimComputer
 USER MANUAL SlimComputer 1 Contents Contents...2 What is SlimComputer?...2 Introduction...3 The Rating System...3 Buttons on the Main Interface...5 Running the Main Scan...8 Restore...11 Optimizer...14
USER MANUAL SlimComputer 1 Contents Contents...2 What is SlimComputer?...2 Introduction...3 The Rating System...3 Buttons on the Main Interface...5 Running the Main Scan...8 Restore...11 Optimizer...14
Vodafone Text Centre User Guide for Microsoft Outlook
 Vodafone Text Centre User Guide for Microsoft Outlook 1 Contents Introduction 1 System requirements 2 Installation 3 The installation guide 3 First use 5 Send a message 8 Select recipient 8 Enter the message
Vodafone Text Centre User Guide for Microsoft Outlook 1 Contents Introduction 1 System requirements 2 Installation 3 The installation guide 3 First use 5 Send a message 8 Select recipient 8 Enter the message
The UC Learning Center: Disabling Pop-Up Blockers
 The UC Learning Center: Disabling Pop-Up Blockers In order to launch online courses within the UC Learning Center all pop-up blockers must be turned off. This guide will walk you through disabling pop-up
The UC Learning Center: Disabling Pop-Up Blockers In order to launch online courses within the UC Learning Center all pop-up blockers must be turned off. This guide will walk you through disabling pop-up
FAQ. F-Secure Online Backup
 F-Secure Online Backup Before installation... 3 Does the F Secure Online Backup program work if there are other online backup programs installed on my computer?... 4 Are two online backup programs better
F-Secure Online Backup Before installation... 3 Does the F Secure Online Backup program work if there are other online backup programs installed on my computer?... 4 Are two online backup programs better
Malwarebytes Anti-Malware 1.42
 Downloading Installing And First-Time Use Updating and Scanning Malwarebytes Anti-Malware 1.42 DOWNLOADING Download the latest version of Malwarebytes Anti-Malware (currently 1.42) from http://www.download.com.
Downloading Installing And First-Time Use Updating and Scanning Malwarebytes Anti-Malware 1.42 DOWNLOADING Download the latest version of Malwarebytes Anti-Malware (currently 1.42) from http://www.download.com.
Dexcom Portrait on the Web User Guide For Use with the Dexcom G4 PLATINUM Continuous Glucose Monitoring System
 Dexcom Portrait on the Web User Guide For Use with the Dexcom G4 PLATINUM Continuous Glucose Monitoring System LBL 0123491 Rev 10 Table of Contents 1 Introduction to Dexcom Portrait on the Web... 3 1.1
Dexcom Portrait on the Web User Guide For Use with the Dexcom G4 PLATINUM Continuous Glucose Monitoring System LBL 0123491 Rev 10 Table of Contents 1 Introduction to Dexcom Portrait on the Web... 3 1.1
Security Practices Essentials. Viruses McAfee Virus Software Critical Windows Updates Network Settings. Spyware Adaware Spybot Windows Defender
 Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
The Care and Feeding of Your Computer Troubleshooting and Maintenance
 Keeping It Clean The Care and Feeding of Your Computer Troubleshooting and Maintenance The computer itself: Regularly dust the exterior. You can use a cloth dampened slightly with water, but do not use
Keeping It Clean The Care and Feeding of Your Computer Troubleshooting and Maintenance The computer itself: Regularly dust the exterior. You can use a cloth dampened slightly with water, but do not use
Using TS-ACCESS for Remote Desktop Access
 Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Learning Management System (LMS) Quick Tips. Contents LMS REFERENCE GUIDE
 Learning Management System (LMS) Quick Tips Contents Process Overview... 2 Sign into the LMS... 3 Troubleshooting... 5 Required Software... 5 Mobile devices are not supported... 5 Using the Check System
Learning Management System (LMS) Quick Tips Contents Process Overview... 2 Sign into the LMS... 3 Troubleshooting... 5 Required Software... 5 Mobile devices are not supported... 5 Using the Check System
Google Docs A Tutorial
 Google Docs A Tutorial What is it? Google Docs is a free online program that allows users to create documents, spreadsheets and presentations online and share them with others for collaboration. This allows
Google Docs A Tutorial What is it? Google Docs is a free online program that allows users to create documents, spreadsheets and presentations online and share them with others for collaboration. This allows
Basic Computer Maintenance
 Basic Computer Maintenance Presented by East Central Regional Library The Institute of, a Federal Agency that fosters innovation, leadership and a lifetime of learning, in conjunction with State Library
Basic Computer Maintenance Presented by East Central Regional Library The Institute of, a Federal Agency that fosters innovation, leadership and a lifetime of learning, in conjunction with State Library
FAQ. Safe Anywhere PC. Disclaimer:
 FAQ Safe Anywhere PC Version: 1.0 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch
FAQ Safe Anywhere PC Version: 1.0 Disclaimer: You can freely use (copy and edit) the information in this document for your own purposes. You may want to replace all references to F-Secure, F-Secure launch
Google Apps Migration
 Academic Technology Services Google Apps Migration Getting Started 1 Table of Contents How to Use This Guide... 4 How to Get Help... 4 Login to Google Apps:... 5 Import Data from Microsoft Outlook:...
Academic Technology Services Google Apps Migration Getting Started 1 Table of Contents How to Use This Guide... 4 How to Get Help... 4 Login to Google Apps:... 5 Import Data from Microsoft Outlook:...
2. PMP New Computer Installation. & Networking Instructions
 ONTARIO CHIROPRACTIC ASSOCIATION PATIENT MANAGEMENT PROGRAM PUTTING EXPERIENCE INTO PRACTICE PMP New Computer Installation & Networking Instructions This document provides installation instructions for
ONTARIO CHIROPRACTIC ASSOCIATION PATIENT MANAGEMENT PROGRAM PUTTING EXPERIENCE INTO PRACTICE PMP New Computer Installation & Networking Instructions This document provides installation instructions for
Parallels Panel. Parallels Small Business Panel 10.2: User's Guide. Revision 1.0
 Parallels Panel Parallels Small Business Panel 10.2: User's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax:
Parallels Panel Parallels Small Business Panel 10.2: User's Guide Revision 1.0 Copyright Notice ISBN: N/A Parallels 660 SW 39 th Street Suite 205 Renton, Washington 98057 USA Phone: +1 (425) 282 6400 Fax:
Switching to Gmail from Microsoft Outlook
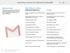 Welcome to Gmail What's different, at a glance... Now that you've switched from Microsoft Outlook to Google Apps, here are some tips on beginning to use Gmail as your new mail program. In Microsoft Outlook,
Welcome to Gmail What's different, at a glance... Now that you've switched from Microsoft Outlook to Google Apps, here are some tips on beginning to use Gmail as your new mail program. In Microsoft Outlook,
Magaya Software Installation Guide
 Magaya Software Installation Guide MAGAYA SOFTWARE INSTALLATION GUIDE INTRODUCTION Introduction This installation guide explains the system requirements for installing any Magaya software, the steps to
Magaya Software Installation Guide MAGAYA SOFTWARE INSTALLATION GUIDE INTRODUCTION Introduction This installation guide explains the system requirements for installing any Magaya software, the steps to
Student Getting Started Guide
 with with Student Getting Started Guide TABLE OF CONTENTS Table of Contents FIRST STEPS TO ENSURE SUCCESS... 3 Ensure System Requirements are met on Your Computer... 3 Find Out Which Operating System Is
with with Student Getting Started Guide TABLE OF CONTENTS Table of Contents FIRST STEPS TO ENSURE SUCCESS... 3 Ensure System Requirements are met on Your Computer... 3 Find Out Which Operating System Is
System Administration Training Guide. S100 Installation and Site Management
 System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
Microsoft Internet explorer 7.0 or higher (Except 10), Mozilla Firefox.
 Dear Client, Welcome to www.canmoney.in, our portal for online trading. We thank you for choosing us as your trading partner. Our website provides host of services and we have taken adequate care to make
Dear Client, Welcome to www.canmoney.in, our portal for online trading. We thank you for choosing us as your trading partner. Our website provides host of services and we have taken adequate care to make
Minimum Computer System Requirements
 Minimum Computer System Requirements http://ualr.edu/blackboard/welcome/system- requirements/ The following minimum hardware and software requirements are necessary in order to access an online class through
Minimum Computer System Requirements http://ualr.edu/blackboard/welcome/system- requirements/ The following minimum hardware and software requirements are necessary in order to access an online class through
Section 1.0 Getting Started with the Vālant EMR. Contents
 Section 1.0 Getting Started with the Vālant EMR Contents Getting Started with the Valant EMR application:... 2 Hardware Requirements for the Vālant EMR:... 3 Software Requirements for the Vālant EMR:...
Section 1.0 Getting Started with the Vālant EMR Contents Getting Started with the Valant EMR application:... 2 Hardware Requirements for the Vālant EMR:... 3 Software Requirements for the Vālant EMR:...
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network.
 This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
Remote Access Services Microsoft Windows - Installation Guide
 Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
Remote Access Services Microsoft Windows - Installation Guide Version 3.1 February 23, 2015 1 P age Contents GETTING STARTED... 3 JAVA VERIFICATION, INSTALLATION, AND CONFIGURATION... 3 Windows XP... 3
MyReports Recommended Browser Settings MYR-200a
 MyReports Recommended Browser Settings MYR-200a Note: If you have installed an additional Tool Bar on your browser, such as Yahoo Tool Bar or Google Tool Bar, be sure that it is also configured to allow
MyReports Recommended Browser Settings MYR-200a Note: If you have installed an additional Tool Bar on your browser, such as Yahoo Tool Bar or Google Tool Bar, be sure that it is also configured to allow
1) Important browser information New 2) Why is my browser so slow? 3) How can I view more than one screen without the other disappearing?
 Known/Unresolved issues: Browser Scan to e-mail Creating Help Desk tickets for the scan-to-email issue is no longer necessary. A member of MIS will follow up with each office to determine scan-to-email
Known/Unresolved issues: Browser Scan to e-mail Creating Help Desk tickets for the scan-to-email issue is no longer necessary. A member of MIS will follow up with each office to determine scan-to-email
FAQ. F-Secure Online Backup 2.1
 FAQ F-Secure Online Backup 2.1 Before installation... 4 Does the F-Secure Online Backup program work if there are other online backup programs installed on my computer?... 4 Are two online backup programs
FAQ F-Secure Online Backup 2.1 Before installation... 4 Does the F-Secure Online Backup program work if there are other online backup programs installed on my computer?... 4 Are two online backup programs
Frequently Asked Questions Cabinet WEB 9.0
 Frequently Asked Questions Cabinet WEB 9.0 Quick Start Guide December 2013 Page 1 Frequently Asked Questions None of my documents will download. When I try to view document a popup is displayed briefly
Frequently Asked Questions Cabinet WEB 9.0 Quick Start Guide December 2013 Page 1 Frequently Asked Questions None of my documents will download. When I try to view document a popup is displayed briefly
Table of Contents. Oracle/Sun JRE Upgrade Instructions. Verify Hard Disk Space JRE 1.6.0.35
 Table of Contents Oracle/Sun JRE Upgrade Instructions... 1 Verify Hard Disk Space... 1 JRE Install Directions for Windows Vista or Windows 7... 2 EWB Sign-on with the New JRE... 7 Problem and Resolution
Table of Contents Oracle/Sun JRE Upgrade Instructions... 1 Verify Hard Disk Space... 1 JRE Install Directions for Windows Vista or Windows 7... 2 EWB Sign-on with the New JRE... 7 Problem and Resolution
Introduction to Computer Security Table of Contents
 Introduction to Computer Security Table of Contents Introduction... 2 1 - Viruses... 3 Virus Scanners... 3 2 - Spyware... 7 Spyware Scanners... 8 3 - Firewalls... 10 Windows Firewall... 10 4 - References...
Introduction to Computer Security Table of Contents Introduction... 2 1 - Viruses... 3 Virus Scanners... 3 2 - Spyware... 7 Spyware Scanners... 8 3 - Firewalls... 10 Windows Firewall... 10 4 - References...
What is My Teamwork? What s new in this release? MY TEAMWORK 5.0 QUICK START GUIDE
 MY TEAMWORK 5.0 QUICK START GUIDE What is My Teamwork? My Teamwork is a converged communications solution that combines presence-aware instant messaging with the ability to make phone calls, conference
MY TEAMWORK 5.0 QUICK START GUIDE What is My Teamwork? My Teamwork is a converged communications solution that combines presence-aware instant messaging with the ability to make phone calls, conference
Instructions for Configuring Your Browser Settings and Online Security FAQ s. ios8 Settings for iphone and ipad app
 Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Driver Updater Manual
 Driver Updater Manual Keep your drivers up-to-date! Improve your system performance and stability by keeping your drivers updated. Automatically find, update and fix the drivers on your computer and turn
Driver Updater Manual Keep your drivers up-to-date! Improve your system performance and stability by keeping your drivers updated. Automatically find, update and fix the drivers on your computer and turn
Accessing your Exchange Mailbox using an Internet Browser
 Accessing your Exchange Mailbox using an Internet Browser The best way to access your Exchange mailbox on a PC or Mac is by using Outlook. This isn t always possible, or convenient, but Exchange also allows
Accessing your Exchange Mailbox using an Internet Browser The best way to access your Exchange mailbox on a PC or Mac is by using Outlook. This isn t always possible, or convenient, but Exchange also allows
Standard Client Configuration Requirements
 Test Developer s Studio (TDS) Standard Client Configuration Requirements Information Technologies (IT) Content Applications Development Group (CADG) Version 1.0 February 20, 2008 Copyright 2008 by NCS
Test Developer s Studio (TDS) Standard Client Configuration Requirements Information Technologies (IT) Content Applications Development Group (CADG) Version 1.0 February 20, 2008 Copyright 2008 by NCS
System Planning, Deployment, and Best Practices Guide
 www.novell.com/documentation System Planning, Deployment, and Best Practices Guide ZENworks Application Virtualization 9.0 February 22, 2012 Legal Notices Novell, Inc., makes no representations or warranties
www.novell.com/documentation System Planning, Deployment, and Best Practices Guide ZENworks Application Virtualization 9.0 February 22, 2012 Legal Notices Novell, Inc., makes no representations or warranties
Qlik Sense Desktop. Qlik Sense 2.0.6 Copyright 1993-2015 QlikTech International AB. All rights reserved.
 Qlik Sense Desktop Qlik Sense 2.0.6 Copyright 1993-2015 QlikTech International AB. All rights reserved. Copyright 1993-2015 QlikTech International AB. All rights reserved. Qlik, QlikTech, Qlik Sense, QlikView,
Qlik Sense Desktop Qlik Sense 2.0.6 Copyright 1993-2015 QlikTech International AB. All rights reserved. Copyright 1993-2015 QlikTech International AB. All rights reserved. Qlik, QlikTech, Qlik Sense, QlikView,
SecuraLive ULTIMATE SECURITY
 SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
Technology Services Group Procedures. IH Anywhere guide. 0 P a g e
 VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)... 2 1. Installation... 2 Disable Apple
How to configure your Windows PC post migrating to Microsoft Office 365
 How to configure your Windows PC post migrating to Microsoft Office 365 1 Contents Purpose... 3 Document Support Boundaries... 3 Examples used in this document... 4 Several different Microsoft Office 365
How to configure your Windows PC post migrating to Microsoft Office 365 1 Contents Purpose... 3 Document Support Boundaries... 3 Examples used in this document... 4 Several different Microsoft Office 365
How to use Google Cloud Print
 How to use Google Cloud Print 1 You can use your Canon printer for Google Cloud Print, following the procedures explained below. In Google Cloud Print, you will be able to print from anywhere you like
How to use Google Cloud Print 1 You can use your Canon printer for Google Cloud Print, following the procedures explained below. In Google Cloud Print, you will be able to print from anywhere you like
Frequent Smart Updates: Used to detect and guard against new infections as well as adding enhancements to Spyware Doctor.
 Faqs > Spyware Doctor Q1. What is Spyware Doctor? Ans.: Spyware Doctor is an easy-to-use, award winning, comprehensive software suite designed to protect your computer against stealthy spyware, aggressive
Faqs > Spyware Doctor Q1. What is Spyware Doctor? Ans.: Spyware Doctor is an easy-to-use, award winning, comprehensive software suite designed to protect your computer against stealthy spyware, aggressive
Gold Lock Desktop. User Manual. Follow these simple steps to install, configure, and use Gold Lock Desktop.
 User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
How to Use Windows Firewall With User Account Control (UAC)
 Keeping Windows 8.1 safe and secure 14 IN THIS CHAPTER, YOU WILL LEARN HOW TO Work with the User Account Control. Use Windows Firewall. Use Windows Defender. Enhance the security of your passwords. Security
Keeping Windows 8.1 safe and secure 14 IN THIS CHAPTER, YOU WILL LEARN HOW TO Work with the User Account Control. Use Windows Firewall. Use Windows Defender. Enhance the security of your passwords. Security
Basic Setup Guide. Remote Administrator 4 NOD32 Antivirus 4 Business Edition Smart Security 4 Business Edition
 Basic Setup Guide Remote Administrator 4 NOD32 Antivirus 4 Business Edition Smart Security 4 Business Edition Contents Getting started...1 Software components...1 Section 1: Purchasing and downloading
Basic Setup Guide Remote Administrator 4 NOD32 Antivirus 4 Business Edition Smart Security 4 Business Edition Contents Getting started...1 Software components...1 Section 1: Purchasing and downloading
Thirtyseven4 Endpoint Security (EPS) Upgrading Instructions
 Thirtyseven4 Endpoint Security (EPS) Upgrading Instructions Disclaimer: As with any software upgrade or new release, it is strongly encouraged to fully test the new build within your environment prior
Thirtyseven4 Endpoint Security (EPS) Upgrading Instructions Disclaimer: As with any software upgrade or new release, it is strongly encouraged to fully test the new build within your environment prior
F-Secure Internet Security 2012
 F-Secure Internet Security 2012 F-Secure Internet Security 2012 TOC 3 Contents Chapter 1: Getting started...7 How to use automatic updates...8 Check the update status...8 Change the Internet connection
F-Secure Internet Security 2012 F-Secure Internet Security 2012 TOC 3 Contents Chapter 1: Getting started...7 How to use automatic updates...8 Check the update status...8 Change the Internet connection
