Housekeeping Your PC
|
|
|
- Jemimah Elinor Hodges
- 10 years ago
- Views:
Transcription
1 for WINDOW 7 Course documentation Material at:sussex.ac.uk/its/training/material/housekeeping University of Sussex Updated: June 2011 IT Services Created: December 2002 University of Sussex IT Services
2 Summary of Good Housekeeping Table of Contents INTRODUCTION... 1 SUMMARY OF GOOD HOUSEKEEPING... 1 FIRST THINGS FIRST - BACKING UP YOUR DATA... 2 WHERE TO BACK UP YOUR FILES... 2 HOW TO BACK UP YOUR FILES... 2 SECURITY... 3 SETTING UP SAFE PASSWORDS... 3 TO SET OR CHANGE YOUR PASSWORD... 3 ADD A NEW USER TO YOUR COMPUTER... 3 VERSIONS OF WINDOWS AND OFFICE... 4 DEALING WITH VIRUSES AND OTHER NASTIES... 5 INSTALLING MSE ANTI-VIRUS SOFTWARE (FREE)... 5 DEALING WITH SPYWARE... 6 CONFIGURE WINDOWS FILE NAMES... 6 INSTALLING WINDOWS AND OFFICE UPDATES... 7 SETTING UP TO AUTOMATICALLY DOWNLOAD FUTURE UPDATES... 7 MORE ABOUT OFFICE AND WINDOWS READING AT HOME... 8 STUDENT STAFF AND RESEARCH POSTGRADUATE PERFORMANCE... 9 DISK CLEANUP... 9 DELETING TEMPORARY INTERNET FILES... 9 FINDING AND DELETING TEMPORARY (TMP) FILES EMPTYING THE RECYCLE BIN DISK DEFRAGMENTER CHECKING THE HARD DISK FOR ERRORS REMOVING UNUSED SOFTWARE MANUALLY DELETING A FILE OR FOLDER FINDING OUT MORE... 13
3 Introduction Introduction A computer, like a car, needs regular maintenance. It is possible to do nothing and let your computer slowly come to a grinding halt, either by virus attack or neglect. This document is intended to provide a few suggestions on how to improve security and performance of your PC at home. It assumes that you are using Microsoft Windows 7 and have an Internet connection supplied by an ISP (Internet Service Provider). Summary of Good Housekeeping This following table summarises the tasks to be completed and gives a guide to the frequency of each task. Task How Often How to do it! 1. Keep virus checking software up to date Daily/ Weekly 2. Use Disk Cleanup Weekly/ Monthly 3. Backup Weekly/ Monthly 4. Defrag 3 to 6 Monthly 5. Delete unwanted Files 6. Empty the Recycle Bin Monthly Monthly Update your virus definitions. Done automatically or by manual updates See Disk Cleanup section in this guide Back up to CD/Zip or other Use disk defragmenter 7. Scandisk/ Chkdsk Monthly Use Scandisk 8. Windows and Microsoft Office Update Automatic Manually search through your hard disk to ensure that files no longer used are deleted. Be sure to empty the Recycle Bin Go to: windowsupdate.microsoft.com 9. Use Anti-Spy ware Monthly Update spyware definitions and run a deep scan (thorough) check. 10. Check MSE (Microsoft Security Essentials) Annually Check for new versions of software as released by IT Services 11. Check Anti-Spy ware Annually Check for new versions of software as released by vendor University of Sussex - IT Services Page 1
4 Where to back up your files First Things First - Backing up your Data Before starting any updates of your OS system (Windows) you should backup any important files (CVs, reports, essays, and dissertations). Where to back up your files The following are some storage devices and locations to consider. External hard drive CD DVD USB flash drive Online backup and storage service How to back up your files A good step-by-step guide for backing up files in Windows 7 is: microsoft.com/windows/windows-7/features/backup-and-restore.aspx For more information also see: sussex.ac.uk/its/help/guide?id=50 sussex.ac.uk/its/help/guide?id=51 And to back up your Internet Explorer bookmarks see: sussex.ac.uk/its/helpdesk/faq.php?faqid=972 Page 2 University of Sussex IT Services
5 Security Security Setting up Safe Passwords Passwords add a level of security to your computer. When sharing a computer with others, your customized settings, computer programs and system resources are more secure when you assign a password to your user account. Some passwords are better than others. A password that is easy to guess or break into is described as WEAK. You can help to protect your information by choosing a STRONG password. Strong passwords are described in: microsoft.com/security/online-privacy/passwords-create.aspx To Set or change your password When you are logged in: Click > then select Control Panel Select User Accounts Click Create a password, or Change the password Type the new password Type the new password in again to confirm Type some descriptive or meaningful text to use as a password hint to help you remember your password Click Create or Change Password Add a new user to your computer If more than one person is using your computer, then you should create separate user accounts for each person. When you are logged in: Click > then select Control Panel Select User Accounts Select Manage another account Select Create a new account Type a name for the new user account Click either Standard user or Administrator, depending on the type of account you want to assign to the new user Click Create Account Then you can select the user account to change the picture or add a password University of Sussex - IT Services Page 3
6 Versions of Windows and Office Versions of Windows and Office To find out which version of windows your have: Click > All programs > Accessories > and choose Run (or you can Click and type run into the Start Search box) Type winver in the box, and click OK A box will pop up showing you the version of Windows and which service packs you have installed The box below was taken from a machine running Windows 7 Enterprise with no Service Packs: To find out which version of Office you have: It is useful to know which version of Office (Word, Excel etc) you have installed when discussing problems or looking for relevant information. In Word 2007: Start Word Click the Microsoft Office Button then click Word Options at the bottom of the window Click Resources, and then click about Microsoft Office Word 2007 A window will appear that tell you what version and service pack level of Office 2007 you have In Word 2003: Start Word From the Help menu choose About Microsoft Word A window will appear that tells you what version and service pack level of Office 2003 you have on your PC Page 4 University of Sussex IT Services
7 Security Dealing with Viruses and Other Nasties This section briefly describes computer viruses and how to protect your computer by using Anti-Virus software. What is a computer virus? A computer virus is a program that has been written with malicious or mischievous intent. This is called a virus because it will usually include some mechanism to copy itself to other computers and therefore spreads in a similar way to a biological infection. A combination of anti-virus software and regular updating of Windows and Office will help to protect your computer. Anti-Virus software has to contend with new types of virus appearing daily. So, it is important to regularly update your anti-virus software definition list (not the software itself but the list of all viruses). Anti-Virus software on IT Services computers has been configured to update its definitions list daily. Installing MSE Anti-Virus Software (FREE) Microsoft Security Essentials (MSE) is the free antivirus software that we recommend for home users. Before installing any Anti-Virus software please ensure that you do not have any Anti-Virus software already installed. Running two Anti-Virus packages could cause your PC to become unstable but there are special removal tools that you can use to delete Anti-Virus software that you no longer need. To remove Anti-Virus software, see the section on Removing Unused Software. We recommend that you disconnect your computer from the Internet before uninstalling one antivirus software product and installing another. This is because your computer will not be protected while this is being done. You can get a copy of MSE Anti-Virus software, and step-by-step installation instructions, from the Microsoft Website at: microsoft.com/security_essentials University of Sussex - IT Services Page 5
8 Dealing with Spyware Dealing with Spyware Several other types of malicious programs are not detected by anti-virus software; these are known as malware or spyware. These have become common on the Internet and many computers have become infected with them. These programs can compromise your privacy and cause your computer to run slowly. Malwarebytes and SpyBot are two tools that can help you to get rid of spyware. Free versions are available for personal use, see: sussex.ac.uk/its/services/programsandsoftware/software/owncomputer Notes: To install Malwarebytes click on the link to download the free software, select Save, then when the download is complete run the software to install Malwarebytes on your PC. You are recommended to run this program regularly to check your PC for spyware. When installing Spybot, you don t need to donate, just click the download button for the free version. There are several download sites that you can select. Select the site, select Save, then when the download is complete run the software to install Spybot on your PC. You are recommended to run this program regularly to check your PC for spyware. Configure Windows file names Windows often hides the full names of files. This can make it more difficult to spot files that might be unusual or harmful. You can make a simple change to see the full file names in Windows 7: Click Click Folder Options Click the View tab > then select Control Panel Scroll down to the line Hide extensions for known file types and make sure the box next to it is unchecked Click OK Page 6 University of Sussex IT Services
9 Security Installing Windows and Office Updates When Microsoft becomes aware of problems, especially security concerns, they release updates (also called patches) to fix them. If you install Windows updates regularly, you will avoid many potential problems. If you haven t installed updates before, they will take several hours to download. You can decrease the amount of time necessary by installing the latest service pack first. We strongly recommend that you install Service Packs which has many security enhancements. A service pack for windows 7 will be available in 2011, see: windows.microsoft.com/en-us/windows/downloads/service-packs Once you have installed the latest service pack, you must visit the Microsoft Update Site at: update.microsoft.com And get the updates that have been released since the service pack was issued. Details of how to find out which version of Windows and which service pack you have currently installed can be found in this booklet in the section called Versions of Windows and Office. Setting up to automatically download future updates Once you have caught up with current critical Windows updates, you'll need to install any new ones that come out. You can do this manually, or you can set up your computer so that it happens automatically. Your computer will check for updates, download them, install them at a time specified by you, and reboot all on its own. If your computer is turned off at your selected installation time, it will perform the installation the next time it is powered on. To set up the automatic updates, follow the instructions at: windows.microsoft.com/en-us/windows7/install-windows-updates More about Office and Windows 7 You can find more information about Office and Windows 7 at the following URLs: windows.microsoft.com/en-us/windows7/help microsoft.com/office University of Sussex - IT Services Page 7
10 Reading at home Reading at home For general information about your Sussex account, see: Student All Sussex students are allocated 1GB of storage space. The Sussex student system allows s of up to 50MB in size to be sent or received. You can use webmail (roundcube) to read your from home, by going to: webmail.sussex.ac.uk/ For information about using webmail, go to: Staff and research Postgraduate The Outlook Web App (OWA) is a very good way of using your . There s nothing to install or configure and you can simply login with almost any web browser including Internet Explorer, Firefox and Chrome. All staff and research postgraduates are entitled to a calendar stored centrally on the University's system which can be accessed from anywhere using OWA. To use OWA: Go to exchange.sussex.ac.uk/owa Enter your normal username (e.g. ano23) in the Domain\user name box Enter your password and click Log On Page 8 University of Sussex IT Services
11 Performance Performance You should periodically store (archive or backup) or throw out documents and files just as you would with a paper based filing system. Your computer will then run more smoothly. Disk Cleanup The disk cleanup program attempts to consolidate the removal of all unused and temporary files. This is useful but you should also make regular checks yourself, even if only to familiarise yourself with the structure of the file system on your hard disk (the C drive). To delete the files manually see the information on the next page. Click > then in the search box type Disk Cleanup lick on Disk Cleanup in the programs window, the following window will appear: Select the C: drive, click OK, then Disk Cleanup will calculate how much space you can save and display the following window: Each tick box can be selected to indicate the areas of the disk you wish to delete unused files from, tick the boxes next to: Temporary Internet Files Temporary files Recycle bin Click OK to delete the selected files Deleting Temporary Internet Files When you browse web pages, Internet Explorer automatically saves a lot of the information into a temporary folder. This helps to speed up web browsing but the temporary files take up space on your computer. You should regularly remove temporary internet files from Internet Explorer: University of Sussex - IT Services Page 9
12 Finding and Deleting Temporary (TMP) files Start Internet Explorer From the Tools menu, choose Internet Options Under the General tab, click the Delete button Now you can delete you temporary internet files, cookies, history, form data and passwords that have been saved by Internet explorer Click Delete Finding and Deleting Temporary (TMP) files Temporary files have the suffix.tmp. They are created temporarily by Windows programs and Utilities, such as Word and are normally deleted when the program is closed down. Temporary files should be automatically stored in a TEMP directory. However, it s possible with Windows that a number of TEMPorary locations have been set-up for each user. To find and manually delete these files: Click In the search box type %temp% An explorer window will appear with the names of all folders and files on your PC, which contain temporary files. You can then select any file or folder you want to delete and press the <<delete>> key on the keyboard to send the file or folder to the Recycle Bin. Emptying the Recycle Bin When you delete files, they end up in your Recycle Bin, to remove them completely: Double click the Recycle Bin icon on your desktop Check that all files in the Recycle bin are either backed-up or no longer required Select Empty Recycle Bin Page 10 University of Sussex IT Services
13 Performance Disk Defragmenter Files on a disk can become fragmented. This means that files may be stored in two or more chunks on different parts of your disk. This can slow down your system, as it takes longer to read and write files that aren t stored neatly in one place. The disk defragmenter takes fragmented files and puts them back together so that the hard drive doesn t have to work as hard to get them. By default Windows 7 Disk Defragmenter automatically defragments your hard drive(s) on a schedule for you. A normal computer user should never have to deal with the disk defragmenter in Windows 7. The Disk Defragmenter runs as a low priority task in the background without affecting the performance of the computer. To see, or modify the schedule: Click > then in the search box type Disk Defragmenter Click on Disk Defragmenter in the programs window The following window will appear: Checking the Hard Disk for Errors Errors can appear on your hard disk and may affect performance. You can use the check disk tool to identify and possibly remove disk errors. Click Click Computer Select the local disk you want to check (C) Right click, click Properties, click the Tools tab Under Error-checking, click Check Now Click Continue To perform a complete check of your hard drive for errors check both options in the check disk window that pops up. Click Start University of Sussex - IT Services Page 11
14 Removing Unused Software Removing Unused Software If you share your computer with other people or often install software to try-out, then you will find that your hard disk (however large) may become full. Computer games are particularly large, often requiring in excess of a Gigabyte of space. Consider regularly looking at the software you have installed and deciding if it is still required. Click > then select the Control Panel Select Programs and Features Wait until your list of installed programs appears Select the program you want to remove and click the Uninstall button at the top of the window Wait for the program to be removed and follow any on-screen instructions You may receive a message that parts of the software (file or folders) could not be removed. This may be files that you have created yourself that were not installed by the software (installer). In the case of computer Games this will be game saves i.e. information relating to your current status within a game. You may wish to back-up these files or remove them manually. Manually Deleting a File or Folder It is useful to be able to find files or folders on your computer to delete them manually. This is how to delete your program files using Windows Explorer: Click Click Computer Double click on the C: drive, a window will open showing your folders Double click the Program Files folder Select the file or folder you want to delete and press the <<Delete>> key on your keyboard The file is moved to the recycle bin Page 12 University of Sussex IT Services
15 Finding out more Finding out more There is lots of information on the ITS web pages: sussex.ac.uk/its/help There are plenty of web pages offering information about using and maintaining your computer ; here is a sample: Security Advice microsoft.com/security/default.aspx Performance Advice microsoft.com/atwork/getstarted/speed.mspx Help and How to windows.microsoft.com/en-us/windows7/help University of Sussex - IT Services Page 13
Housekeeping Your PC. for XP
 for XP Course documentation Material at:sussex.ac.uk/its/training/material/housekeeping University of Sussex Updated: June 2011 IT Services Created: December 2002 University of Sussex IT Services Summary
for XP Course documentation Material at:sussex.ac.uk/its/training/material/housekeeping University of Sussex Updated: June 2011 IT Services Created: December 2002 University of Sussex IT Services Summary
Basic Computer Maintenance
 Basic Computer Maintenance Presented by East Central Regional Library The Institute of, a Federal Agency that fosters innovation, leadership and a lifetime of learning, in conjunction with State Library
Basic Computer Maintenance Presented by East Central Regional Library The Institute of, a Federal Agency that fosters innovation, leadership and a lifetime of learning, in conjunction with State Library
OUTLOOK WEB ACCESS. User Guide
 OUTLOOK WEB ACCESS User Guide V3 2 August 2013 Not protectively marked GETTING STARTED Outlook Web Access (OWA) provides a useful means to remotely access Council email from outside of the council access.
OUTLOOK WEB ACCESS User Guide V3 2 August 2013 Not protectively marked GETTING STARTED Outlook Web Access (OWA) provides a useful means to remotely access Council email from outside of the council access.
Configuring your email client to connect to your Exchange mailbox
 Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
Michelle Vonderhaar June 23, 2010
 Michelle Vonderhaar June 23, 2010 PC Maintenance Checklist Back up any data BEFORE you perform any PC maintenance Check Hard Drive for free space (for comparison after clean up) Perform Disk Clean-up (use
Michelle Vonderhaar June 23, 2010 PC Maintenance Checklist Back up any data BEFORE you perform any PC maintenance Check Hard Drive for free space (for comparison after clean up) Perform Disk Clean-up (use
PC Security and Maintenance
 PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
PC Security and Maintenance by IMRAN GHANI PC Maintenance and Security-Forecast. Major sources of danger. Important steps to protect your PC. PC Security Tools. PC Maintenance Tools. Tips. PC Security-
Microsoft Security Essentials Installation and Configuration Guide
 Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
Overview. What Counts Against Your Mailbox Size
 Overview The staff of Firelands Local Schools access email primarily through two methods: An Outlook client on their desktop/laptop or webmail. The procedures outlined in this document will show the Firelands
Overview The staff of Firelands Local Schools access email primarily through two methods: An Outlook client on their desktop/laptop or webmail. The procedures outlined in this document will show the Firelands
How to Install Windows 7 software
 Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
DISK DRIVE MAINTENANCE. 1. Disk Cleanup
 DISK DRIVE MAINTENANCE To keep a PC running smoothly, regular maintenance is critical. Many users shy away from maintenance tasks, thinking it is a long, drawn out manual affair, but the Disk Cleanup Utility
DISK DRIVE MAINTENANCE To keep a PC running smoothly, regular maintenance is critical. Many users shy away from maintenance tasks, thinking it is a long, drawn out manual affair, but the Disk Cleanup Utility
McAfee Enterprise Edition v 7.1.0 Installation & Configuration For Windows NT, 2000, and XP
 McAfee Enterprise Edition v 7.1.0 Installation & Configuration For Windows NT, 2000, and XP McAfee Enterprise Edition v 7.1.0: Installation & Configuration 1 McAfee Enterprise Edition v 7.1.0: Installation
McAfee Enterprise Edition v 7.1.0 Installation & Configuration For Windows NT, 2000, and XP McAfee Enterprise Edition v 7.1.0: Installation & Configuration 1 McAfee Enterprise Edition v 7.1.0: Installation
Cleaning your Windows 7, Windows XP and Macintosh OSX Computers
 Cleaning your Windows 7, Windows XP and Macintosh OSX Computers A cleaning of your computer can help your computer run faster and make you more efficient. We have listed some tools and how to use these
Cleaning your Windows 7, Windows XP and Macintosh OSX Computers A cleaning of your computer can help your computer run faster and make you more efficient. We have listed some tools and how to use these
16.4.3 Lab: Data Backup and Recovery in Windows XP
 16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
What is PC Matic?...4. System Requirements...4. Launching PC Matic.5. How to Purchase a PC Matic Subscription..6. Additional Installations.
 USER Manual Table of Contents Getting Started What is PC Matic?...4 System Requirements....4 Launching PC Matic.5 How to Purchase a PC Matic Subscription..6 Additional Installations. 6 Registration...6
USER Manual Table of Contents Getting Started What is PC Matic?...4 System Requirements....4 Launching PC Matic.5 How to Purchase a PC Matic Subscription..6 Additional Installations. 6 Registration...6
Computer Maintenance Guide
 Computer Maintenance Guide Do you get days where you feel like tearing your hair out, because your Pc will not operate in the manner which it did when you first bought it. Believe me you are not alone,
Computer Maintenance Guide Do you get days where you feel like tearing your hair out, because your Pc will not operate in the manner which it did when you first bought it. Believe me you are not alone,
Contents. McAfee Internet Security 3
 User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
How To Use Your Computer Safely And Effectively
 2010 Everyone wants to build but nobody wants to do any maintenance. - Kurt Vonnegut COMPUTER HOUSEKEEPING This document is intended to support the Silver Surfers course of the same name. It addresses
2010 Everyone wants to build but nobody wants to do any maintenance. - Kurt Vonnegut COMPUTER HOUSEKEEPING This document is intended to support the Silver Surfers course of the same name. It addresses
Some simple computer maintenance to keep your computer running well.
 PC Tune-up for Windows XP Some simple computer maintenance to keep your computer running well. When you use your computer often, preventive maintenance is necessary. This is the same concept as for your
PC Tune-up for Windows XP Some simple computer maintenance to keep your computer running well. When you use your computer often, preventive maintenance is necessary. This is the same concept as for your
Xythos on Demand Quick Start Guide For Xythos Drive
 Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
Xythos on Demand Quick Start Guide For Xythos Drive What is Xythos on Demand? Xythos on Demand is not your ordinary online storage or file sharing web site. Instead, it is an enterprise-class document
The Care and Feeding of Your Computer Troubleshooting and Maintenance
 Keeping It Clean The Care and Feeding of Your Computer Troubleshooting and Maintenance The computer itself: Regularly dust the exterior. You can use a cloth dampened slightly with water, but do not use
Keeping It Clean The Care and Feeding of Your Computer Troubleshooting and Maintenance The computer itself: Regularly dust the exterior. You can use a cloth dampened slightly with water, but do not use
Accessing your Staff (N and O drive) files from off campus
 Accessing your Staff (N and O drive) files from off campus It is possible to access your N and O drive files while you are off campus, for example whilst working from home or travelling. This document
Accessing your Staff (N and O drive) files from off campus It is possible to access your N and O drive files while you are off campus, for example whilst working from home or travelling. This document
Microsoft Outlook. Transition from the ECS Exchange Server to the University Exchange Server. ECS Computing Services August 21, 2012 Version 3.
 Microsoft Outlook Transition from the ECS Exchange Server to the University Exchange Server ECS Computing Services August 21, 2012 Version 3.3 1 Table of Contents Transition Process... 4 What is going
Microsoft Outlook Transition from the ECS Exchange Server to the University Exchange Server ECS Computing Services August 21, 2012 Version 3.3 1 Table of Contents Transition Process... 4 What is going
10.3.1.6 Lab - Data Backup and Recovery in Windows XP
 5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
5.0 10.3.1.6 Lab - Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment
Remote Desktop Web Access. Using Remote Desktop Web Access
 Remote Desktop Web Access What is RD Web Access? RD Web Access is a Computer Science service that allows you to access department software and machines from your Windows or OS X computer, both on and off
Remote Desktop Web Access What is RD Web Access? RD Web Access is a Computer Science service that allows you to access department software and machines from your Windows or OS X computer, both on and off
SystemTech AntiSpyware Manual
 Summitsoft Corporation SystemTech AntiSpyware Manual This guide is distributed with software that includes an end user agreement, this guide, as well as the software described in it, is furnished under
Summitsoft Corporation SystemTech AntiSpyware Manual This guide is distributed with software that includes an end user agreement, this guide, as well as the software described in it, is furnished under
F-Secure Anti-Virus for Mac 2015
 F-Secure Anti-Virus for Mac 2015 TOC F-Secure Anti-Virus for Mac 2015 Contents Chapter 1: Getting started...3 1.1 Manage subscription...4 1.2 How to make sure that my computer is protected...4 1.2.1 Protection
F-Secure Anti-Virus for Mac 2015 TOC F-Secure Anti-Virus for Mac 2015 Contents Chapter 1: Getting started...3 1.1 Manage subscription...4 1.2 How to make sure that my computer is protected...4 1.2.1 Protection
Easy Do-It-Yourself Computer Maintenance Tips
 Easy Do-It-Yourself Computer Maintenance Tips Presented by: Scott A. Hartley, M.A.T. President/CEO, Calibre Computer Solutions, LLC 318 W. Glendale St. Princeton, IN 47670 (812) 386-8919 www.calibre-cs.com
Easy Do-It-Yourself Computer Maintenance Tips Presented by: Scott A. Hartley, M.A.T. President/CEO, Calibre Computer Solutions, LLC 318 W. Glendale St. Princeton, IN 47670 (812) 386-8919 www.calibre-cs.com
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Cox Business Premium Security Service FAQs
 FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
PC Security & Housekeeping March 2015
 PC Security & Housekeeping March 2015 Anti-malware programs Always keep your firewall, anti-virus, and anti-spyware products up to date! There are many good commercial products available, such as: o Norton
PC Security & Housekeeping March 2015 Anti-malware programs Always keep your firewall, anti-virus, and anti-spyware products up to date! There are many good commercial products available, such as: o Norton
OUTLOOK ANYWHERE CONNECTION GUIDE FOR USERS OF OUTLOOK 2010
 OUTLOOK ANYWHERE CONNECTION GUIDE FOR USERS OF OUTLOOK 2010 CONTENTS What is Outlook Anywhere? Before you begin How do I configure Outlook Anywhere with Outlook 2010? How do I use Outlook Anywhere? I already
OUTLOOK ANYWHERE CONNECTION GUIDE FOR USERS OF OUTLOOK 2010 CONTENTS What is Outlook Anywhere? Before you begin How do I configure Outlook Anywhere with Outlook 2010? How do I use Outlook Anywhere? I already
How to easily clean an infected computer (Malware Removal Guide)
 How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
CITRIX TROUBLESHOOTING TIPS
 CITRIX TROUBLESHOOTING TIPS The purpose of this document is to outline the Most Common Frequently Asked Questions regarding access to the County of York Computer Systems via Citrix. SYSTEM REQUIREMENTS:
CITRIX TROUBLESHOOTING TIPS The purpose of this document is to outline the Most Common Frequently Asked Questions regarding access to the County of York Computer Systems via Citrix. SYSTEM REQUIREMENTS:
How To Use Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Web24 Supported Software
 Web24 Supported Software Browser & OS Requirements Connectivity, hardware and browser support are critical to providing the best user experience within Web24. We work hard to make sure that Web24 renders
Web24 Supported Software Browser & OS Requirements Connectivity, hardware and browser support are critical to providing the best user experience within Web24. We work hard to make sure that Web24 renders
BASIC PC MAINTENANCE AND BACKUP Lesson 1
 BASIC PC MAINTENANCE AND BACKUP Lesson 1 Table of Contents Lesson 1: Computer Maintenance, Printing, and Finding Help Disk Clean-up, Error-Checking, Defragmentation...2, 3 Learn the Details of Your Computer...4
BASIC PC MAINTENANCE AND BACKUP Lesson 1 Table of Contents Lesson 1: Computer Maintenance, Printing, and Finding Help Disk Clean-up, Error-Checking, Defragmentation...2, 3 Learn the Details of Your Computer...4
Professional Mailbox Email Software Setup Guide
 Professional Mailbox Email Software Setup Guide Table of contents Download and Install Microsoft Outlook 2010 or 2011... 2 Enabling access from email software... 4 Setting up Outlook 2010... 6 Before you
Professional Mailbox Email Software Setup Guide Table of contents Download and Install Microsoft Outlook 2010 or 2011... 2 Enabling access from email software... 4 Setting up Outlook 2010... 6 Before you
Basic PC Maintenance. Instructors. Action Center
 Basic PC Maintenance The St. Edward's University workshop "Basic PC Maintenance" addresses best practices for maintaining your (Windows 7) PC at home. This document includes notes and recommendations for
Basic PC Maintenance The St. Edward's University workshop "Basic PC Maintenance" addresses best practices for maintaining your (Windows 7) PC at home. This document includes notes and recommendations for
Table of Contents. Rebit 5 Help
 Rebit 5 Help i Rebit 5 Help Table of Contents Getting Started... 1 Making the First Recovery Point... 1 Don't Forget to Create a Recovery Media... 1 Changing Backup Settings... 1 What Does Rebit 5 Do?...
Rebit 5 Help i Rebit 5 Help Table of Contents Getting Started... 1 Making the First Recovery Point... 1 Don't Forget to Create a Recovery Media... 1 Changing Backup Settings... 1 What Does Rebit 5 Do?...
Information Services. Accessing the University Network using a Virtual Private Network Connection (VPN), with Windows XP Professional
 Information Services Accessing the University Network using a Virtual Private Network Connection (VPN), with Windows XP Professional Amendment & Authorisation History Ver Date Changes Name Author A 29/3/05
Information Services Accessing the University Network using a Virtual Private Network Connection (VPN), with Windows XP Professional Amendment & Authorisation History Ver Date Changes Name Author A 29/3/05
Using TS-ACCESS for Remote Desktop Access
 Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Dartmouth College Technical Support Document for Kronos PC version
 Dartmouth College Technical Support Document for Kronos PC version Contents How to Save the Kronos URL as a Favorite or Bookmark... 2 Internet Explorer... 2 Firefox... 4 Possible Problems When Logging
Dartmouth College Technical Support Document for Kronos PC version Contents How to Save the Kronos URL as a Favorite or Bookmark... 2 Internet Explorer... 2 Firefox... 4 Possible Problems When Logging
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client
 Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Disabling Microsoft SharePoint in order to install the OneDrive for Business Client If you try to setup and sync your OneDrive online documents with the client software and Microsoft SharePoint opens,
Using Spy Sweeper for Windows Author: Jocelyn Kasamoto
 WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
Microsoft OneDrive. How to login to OneDrive:
 Microsoft OneDrive The beauty of OneDrive is that it is accessible from anywhere you have an Internet connection. You can access it from a Mac or Windows computer. You can even access it on your Smartphone
Microsoft OneDrive The beauty of OneDrive is that it is accessible from anywhere you have an Internet connection. You can access it from a Mac or Windows computer. You can even access it on your Smartphone
Auslogics BoostSpeed 5 Manual
 Page 1 Auslogics BoostSpeed 5 Manual [ Installing and using Auslogics BoostSpeed 5 ] Page 2 Table of Contents What Is Auslogics BoostSpeed?... 3 Features... 3 Compare Editions... 4 Installing the Program...
Page 1 Auslogics BoostSpeed 5 Manual [ Installing and using Auslogics BoostSpeed 5 ] Page 2 Table of Contents What Is Auslogics BoostSpeed?... 3 Features... 3 Compare Editions... 4 Installing the Program...
Computer Security. Uses Zip disks that hold up to 750 MB of data. Must buy and hook up the drive.
 Basic Computer Security Practices Make backups of important files. Apply patches to the operating system. Use anti-virus software, update definitions very frequently, and run a full virus scan at least
Basic Computer Security Practices Make backups of important files. Apply patches to the operating system. Use anti-virus software, update definitions very frequently, and run a full virus scan at least
Quick Start. Installing the software. for Webroot Internet Security Complete, Version 7.0
 Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
MyNetFone Virtual Fax. Virtual Fax Installation
 Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Optimal Browser Settings for Internet Explorer Running on Microsoft Windows
 Optimal Browser Settings for Internet Explorer Running on Microsoft Windows If you have Internet Explorer 7 or 8: Each time you log in to our web site, it evaluates whether you are using the same computer
Optimal Browser Settings for Internet Explorer Running on Microsoft Windows If you have Internet Explorer 7 or 8: Each time you log in to our web site, it evaluates whether you are using the same computer
Outlook Web App (Online)... 3 Outlook 2013 (Desktop)... 16 Apple Mail Mobile Devices... 33 Android... 33 iphone... 40
 Webmail Tutorials Page 2 Table of Contents Outlook Web App (Online)... 3 How do I send an email?... 3 How do I create rules to manage my email?... 3 How do I forward email to my personal account?... 4
Webmail Tutorials Page 2 Table of Contents Outlook Web App (Online)... 3 How do I send an email?... 3 How do I create rules to manage my email?... 3 How do I forward email to my personal account?... 4
SecuraLive ULTIMATE SECURITY
 SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
SecuraLive ULTIMATE SECURITY Home Edition for Windows USER GUIDE SecuraLive ULTIMATE SECURITY USER MANUAL Introduction: Welcome to SecuraLive Ultimate Security Home Edition. SecuraLive Ultimate Security
MSD IT High Compliance system Fact sheet
 MSD IT High Compliance system Fact sheet The MSD IT High Compliance system is a service for Clinical Trials Units (CTUs) and Medical Division Departments or Units who need to securely access critical applications,
MSD IT High Compliance system Fact sheet The MSD IT High Compliance system is a service for Clinical Trials Units (CTUs) and Medical Division Departments or Units who need to securely access critical applications,
Exchange 2003 Mailboxes
 Exchange 2003 Mailboxes Microsoft will stop supporting Exchange 2003 mailboxes in 2014 as it comes to the end of it s life. To maintain our levels of support and performance of all our customers, we will
Exchange 2003 Mailboxes Microsoft will stop supporting Exchange 2003 mailboxes in 2014 as it comes to the end of it s life. To maintain our levels of support and performance of all our customers, we will
Driver Updater Manual
 Driver Updater Manual Keep your drivers up-to-date! Improve your system performance and stability by keeping your drivers updated. Automatically find, update and fix the drivers on your computer and turn
Driver Updater Manual Keep your drivers up-to-date! Improve your system performance and stability by keeping your drivers updated. Automatically find, update and fix the drivers on your computer and turn
Computer s History Quick Start Guide & Safety Tips
 How to: Check Your Computer s History Quick Start Guide & Safety Tips Copyright Web Wise Kids. 2009. All Rights Reserved WHAT IS COMPUTER HISTORY? Your computer contains records that can tell you a lot
How to: Check Your Computer s History Quick Start Guide & Safety Tips Copyright Web Wise Kids. 2009. All Rights Reserved WHAT IS COMPUTER HISTORY? Your computer contains records that can tell you a lot
Understand Backup and Recovery Methods
 Understand Backup and Recovery Methods Lesson Overview Understand backup and recovery methods. In this lesson, you will explore: Backup management Backup options Recovery methods Backup Management Windows
Understand Backup and Recovery Methods Lesson Overview Understand backup and recovery methods. In this lesson, you will explore: Backup management Backup options Recovery methods Backup Management Windows
Student Mail Access. Introduction. Option One: Using an E-mail Client
 Student Mail Access Introduction There are two ways that you will be able to access your e-mail from any location. You can use an e-mail client or a Web browser (p. 11). These options will be accessible
Student Mail Access Introduction There are two ways that you will be able to access your e-mail from any location. You can use an e-mail client or a Web browser (p. 11). These options will be accessible
How To Use Outlook On A Virtual Desktop On A Pc Or Macbook
 Virtual Desktop Frequently Asked Questions 1. How do I download the VMWare agent? 2. I downloaded the client from another computer. Why don t I see the shortcut on the desktop of this computer? 3. How
Virtual Desktop Frequently Asked Questions 1. How do I download the VMWare agent? 2. I downloaded the client from another computer. Why don t I see the shortcut on the desktop of this computer? 3. How
Microsoft Entourage 2008 / Microsoft Exchange Server 2010. Installation and Configuration Instructions
 Microsoft Entourage 2008 / Microsoft Exchange Server 2010 Installation and Configuration Instructions Table of Contents How to connect Microsoft Entourage 2008 EWS to the Exchange Server... 3 Important
Microsoft Entourage 2008 / Microsoft Exchange Server 2010 Installation and Configuration Instructions Table of Contents How to connect Microsoft Entourage 2008 EWS to the Exchange Server... 3 Important
Vess A2000 Series. NVR Storage Appliance. Windows Recovery Instructions. Version 1.0. 2014 PROMISE Technology, Inc. All Rights Reserved.
 Vess A2000 Series NVR Storage Appliance Windows Recovery Instructions Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Different ways to backup the system disk 2 Before
Vess A2000 Series NVR Storage Appliance Windows Recovery Instructions Version 1.0 2014 PROMISE Technology, Inc. All Rights Reserved. Contents Introduction 1 Different ways to backup the system disk 2 Before
Security Practices Essentials. Viruses McAfee Virus Software Critical Windows Updates Network Settings. Spyware Adaware Spybot Windows Defender
 Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
Security Practices Essentials Viruses McAfee Virus Software Critical Windows Updates Network Settings Spyware Adaware Spybot Windows Defender Security Practices Essentials: All computer passwords should
ACCESSING CERNER ON A MAC (October 1, 2012)
 ACCESSING CERNER ON A MAC (October 1, 2012) For any questions regarding these instructions, or for assistance with accessing Cerner from a Mac, iphone or ipad please contact Dr. Behra at [email protected].
ACCESSING CERNER ON A MAC (October 1, 2012) For any questions regarding these instructions, or for assistance with accessing Cerner from a Mac, iphone or ipad please contact Dr. Behra at [email protected].
First Time On-Campus VLab Setup Windows XP Edition
 First Time On-Campus VLab Setup Windows XP Edition General: This guide is a step-by-step walkthrough of downloading, installing and configuring VMware View Client for the University of Cincinnati s VLab
First Time On-Campus VLab Setup Windows XP Edition General: This guide is a step-by-step walkthrough of downloading, installing and configuring VMware View Client for the University of Cincinnati s VLab
Microsoft Office 365 with MailDefender
 (PC) for Microsoft Office 365 with MailDefender V1.0 Contents 1 Logging in to the Office 365 Portal... 3 1.1 Outlook Web Access Exchange & Lync... 3 1.2 Team Site SharePoint Online... 3 2 Configuring your
(PC) for Microsoft Office 365 with MailDefender V1.0 Contents 1 Logging in to the Office 365 Portal... 3 1.1 Outlook Web Access Exchange & Lync... 3 1.2 Team Site SharePoint Online... 3 2 Configuring your
Outlook Express POP Instructions - Bloomsburg University Students
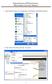 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
Passport Installation. Windows 8 + Internet Explorer 10
 Passport Installation Windows 8 + Internet Explorer 10 OS Version Windows 8 System Type 32bit and 64bit Browser Name & version Internet Explorer 10 Before you begin Make sure you have Anti Virus software
Passport Installation Windows 8 + Internet Explorer 10 OS Version Windows 8 System Type 32bit and 64bit Browser Name & version Internet Explorer 10 Before you begin Make sure you have Anti Virus software
Outlook Web App Logging in
 Outlook Web App Logging in 8 Outlook Web App or OWA is a web-based version of Outlook which you can use to read your Sussex email from any computer with a web browser and internet access. Some web browsers
Outlook Web App Logging in 8 Outlook Web App or OWA is a web-based version of Outlook which you can use to read your Sussex email from any computer with a web browser and internet access. Some web browsers
Free and Legal Software You Can Download By Tom Krauser
 Free and Legal Software You Can Download By Tom Krauser Here is a list of free programs that you can download for your personal use. They are legal and free for you to install. Some may have restrictions
Free and Legal Software You Can Download By Tom Krauser Here is a list of free programs that you can download for your personal use. They are legal and free for you to install. Some may have restrictions
VPN User Guide. For Mac
 VPN User Guide For Mac System Requirements Operating System: Mac OSX. Internet Browser: Safari (Firefox and Google Chrome are NOT currently supported). Disclaimer Your computer must have the system requirements
VPN User Guide For Mac System Requirements Operating System: Mac OSX. Internet Browser: Safari (Firefox and Google Chrome are NOT currently supported). Disclaimer Your computer must have the system requirements
Passport Installation. Windows XP + Internet Explorer 8
 Passport Installation Windows XP + Internet Explorer 8 OS Version Windows XP System Type 32bit or 64bit Browser & version Internet Explorer 8 Before you begin.. Make sure you have Anti Virus software installed
Passport Installation Windows XP + Internet Explorer 8 OS Version Windows XP System Type 32bit or 64bit Browser & version Internet Explorer 8 Before you begin.. Make sure you have Anti Virus software installed
Email Archiving. Follow these steps to archive your email:
 Email Archiving Archiving is a process by which your email messages and attached files are moved from the database on our email server to a location on your computer. This document contains step-by-step
Email Archiving Archiving is a process by which your email messages and attached files are moved from the database on our email server to a location on your computer. This document contains step-by-step
How To Run Eve 5 On A Pc Or Mac Or Ipad (For Pc Or Ipa) On A Network (For Mac) On Your Computer Or Ipro (For Ipro) On An Ipro Or Ipo (For Windows)
 EVE5 Hardware and Software Requirements EVE5 is a Client/Server program. i.e. there are 2 components to the program: 1/ The Server: this controls your database and will be installed on one computer only.
EVE5 Hardware and Software Requirements EVE5 is a Client/Server program. i.e. there are 2 components to the program: 1/ The Server: this controls your database and will be installed on one computer only.
Dual-boot Windows 10 alongside Windows 8
 Most of the people are very much interested to install the newly launched Operating System Windows 10 on their devices. But, it is not recommended to directly use Windows 10 as the primary OS because it
Most of the people are very much interested to install the newly launched Operating System Windows 10 on their devices. But, it is not recommended to directly use Windows 10 as the primary OS because it
Instructions for Configuring Your Browser Settings and Online Security FAQ s. ios8 Settings for iphone and ipad app
 Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Instructions for Configuring Your Browser Settings and Online Security FAQ s ios8 Settings for iphone and ipad app General Settings The following browser settings and plug-ins are required to properly
Intelligent Office: Web Optimisation Guide. Published Date: 06/11/2015. Version: 3.3
 Intelligent Office: Web Optimisation Guide Published Date: 06/11/2015 Version: 3.3 Table of Contents System Requirements:... 3 Introduction... 3 Difficulties Logging on to Intelligent Office (io)... 3
Intelligent Office: Web Optimisation Guide Published Date: 06/11/2015 Version: 3.3 Table of Contents System Requirements:... 3 Introduction... 3 Difficulties Logging on to Intelligent Office (io)... 3
How to remotely access your Virtual Desktop from outside the college using VMware View Client. How to guide
 How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
STEP 1: INSTALLING WINDOWS DEFENDER
 Office of Information Technology Secure your Windows XP Computer for Use on AU s Network Every member of the AU community has a shared responsibility for the safekeeping of our computer network. Since
Office of Information Technology Secure your Windows XP Computer for Use on AU s Network Every member of the AU community has a shared responsibility for the safekeeping of our computer network. Since
Protecting Your Computer from Viruses and Spyware
 Protecting Your Computer from Viruses and Spyware PROTECTING YOUR COMPUTER FROM VIRUSES AND SPYWARE A virus is a program that runs on your computer without asking permission and makes copies of itself.
Protecting Your Computer from Viruses and Spyware PROTECTING YOUR COMPUTER FROM VIRUSES AND SPYWARE A virus is a program that runs on your computer without asking permission and makes copies of itself.
Downloading and installing SMART Notebook Software
 Connected Classrooms Program: Interactive Classrooms Project 03 June 2009 Downloading and installing SMART Notebook Software Step-by-step instructions for Windows and Apple Macs DET has licensed the SMART
Connected Classrooms Program: Interactive Classrooms Project 03 June 2009 Downloading and installing SMART Notebook Software Step-by-step instructions for Windows and Apple Macs DET has licensed the SMART
SMS for Outlook. Installation, Configuration and Usage Guide
 SMS for Outlook Installation, Configuration and Usage Guide INTRODUCTION Installing TxTStream s SMS for Outlook is easy and will only take a minute or two. We will be using screen shots from a Windows
SMS for Outlook Installation, Configuration and Usage Guide INTRODUCTION Installing TxTStream s SMS for Outlook is easy and will only take a minute or two. We will be using screen shots from a Windows
ViRobot Desktop 5.5. User s Guide
 ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
Selected Windows XP Troubleshooting Guide
 1 Selected Windows XP Troubleshooting Guide To locate lost files: Compiled by: Jason M. Cohen Check these locations to locate lost files: The My Documents folder Click Start, and then click My Documents.
1 Selected Windows XP Troubleshooting Guide To locate lost files: Compiled by: Jason M. Cohen Check these locations to locate lost files: The My Documents folder Click Start, and then click My Documents.
educ Office 365 email: Remove & create new Outlook profile
 Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Remote Access to Niagara Wheatfield s Computer Network
 Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
Remote Access to Niagara Wheatfield s Computer Network Niagara Wheatfield Central School District Office of Instructional Technology Revised: June 24, 2010 Page 1 of 15 To gain access to Niagara Wheatfield
Using desktop ANYWHERE
 Using desktop ANYWHERE A facility for students and staff which provides access to University IT facilities from most computers which have a connection to the Internet. Using a web browser you can access:
Using desktop ANYWHERE A facility for students and staff which provides access to University IT facilities from most computers which have a connection to the Internet. Using a web browser you can access:
Windows XP with Symantec AntiVirus 10 Corporate Edition
 NC State University 1 of 7 Windows XP with Symantec AntiVirus 10 Corporate Edition home download free antivirus now windows xp with symantec antivirus 10 corporate edition Install SAV10 on Windows XP only
NC State University 1 of 7 Windows XP with Symantec AntiVirus 10 Corporate Edition home download free antivirus now windows xp with symantec antivirus 10 corporate edition Install SAV10 on Windows XP only
PREMIUM MAIL USER GUIDE
 PREMIUM MAIL USER GUIDE WHO THIS USER GUIDE IS FOR This document is for users of BigPond Premium Mail. It describes the features of BigPond Premium Mail from a user s perspective. It contains: A general
PREMIUM MAIL USER GUIDE WHO THIS USER GUIDE IS FOR This document is for users of BigPond Premium Mail. It describes the features of BigPond Premium Mail from a user s perspective. It contains: A general
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Charter Business Desktop Security Administrator's Guide
 Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
How To Use Secureanything On A Mac Or Ipad (For A Mac)
 User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
BSDI Advanced Fitness & Wellness Software
 BSDI Advanced Fitness & Wellness Software 6 Kellie Ct. Califon, NJ 07830 http://www.bsdi.cc SOFTWARE BACKUP/RESTORE INSTRUCTION SHEET This document will outline the steps necessary to take configure the
BSDI Advanced Fitness & Wellness Software 6 Kellie Ct. Califon, NJ 07830 http://www.bsdi.cc SOFTWARE BACKUP/RESTORE INSTRUCTION SHEET This document will outline the steps necessary to take configure the
NS Financials. Client Platform Guide for Mac Using Safari Incl Citrix Setup As A Local Client
 NS Financials Client Platform Guide for Mac Using Safari Incl Citrix Setup As A Local Client This document describes how to access the NS Financials system through Safari on an Apple Mac and outlines the
NS Financials Client Platform Guide for Mac Using Safari Incl Citrix Setup As A Local Client This document describes how to access the NS Financials system through Safari on an Apple Mac and outlines the
HDDtoGO. User Guide. User Manual Version 3.4 2004-2010 CoSoSys SRL 2010 A-DATA Technology Co., Ltd. HDDtoGO User Manual
 HDDtoGO User Guide User Manual Version 3.4 2004-2010 CoSoSys SRL 2010 A-DATA Technology Co., Ltd. HDDtoGO User Manual Table of Contents Table of Contents...1 1. Introduction...2 2. System Requirements...3
HDDtoGO User Guide User Manual Version 3.4 2004-2010 CoSoSys SRL 2010 A-DATA Technology Co., Ltd. HDDtoGO User Manual Table of Contents Table of Contents...1 1. Introduction...2 2. System Requirements...3
