Check Point Corporate Logo Usage Guidelines
|
|
|
- Cameron Marsh
- 8 years ago
- Views:
Transcription
1 Check Point Corporate Logo Usage Guidelines
2 1. The Check Point Logo The Check Point logo is the most visible and recognizable symbol of our brand. It should appear on every piece of communication from Check Point from the basic internal memo to the website and everything in between. Use the logo with black text when it is placed on white or light color background The corporate logo should always be placed in an unobstructed area on a clean, clear, solid background that provides maximum clarity and visibility. Use the logo with white text when it is placed on black or medium-to-dark color background 2
3 2. Corporate Tagline The corporate tagline for Check Point Software Technologies is: We Secure the Internet. Corporate tagline is an important part of the Check Point logo lockup. It should always be used with the logo. Tagline is justified and placed beneath the logo as shown. The tagline should always be used in the exact proportion to the company logo as shown on the right. The typeface is Helvetica 65. It is set in initial caps, and a period should always be used at the end. If Check Point logo is placed multiple times on a multiple page document, use the version with tagline for the document cover; use the version without tagline for the inside pages and back cover. The lockup format of the logo can only be used one time on a single document. When multiple application of the logo needed for a single document, use the version with tagline for the document cover; use the version without tagline for the inside pages and back cover. 3
4 UTM-1 Edge X, UTM-1 Edge W, UTM-1 Edge X ADSL, UTM-1 Edge W ADSL 1 Test based on real-world traffic blend using the default profile 2 Maximum of 256 VLANs per interface 3 UTM-1 Edge operating environment: Temperature: 0º to 40º C, Humidity: 10% 90% non-condensing, Altitude: 4500m (15,000ft ) 6,873,988, 6,850,943, and 7,165,076 and may be protected by other U.S. Patents, foreign patents, or pending applications. November 10, 2009 Worldwide Headquarters 5 Ha Solelim Street, Tel Aviv 67897, Israel Tel: Fax: info@checkpoint.com U.S. Headquarters 800 Bridge Parkway, Redwood City, CA Tel: ; Fax: Corporate Logo Usage Guidelines February Logo application samples CHECK POINT TOTAL SECURITY APPLIANCES : Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point award-winning software solutions to address virtually any security need. Based on the new Check Point Software Blade architecture, Check Point appliances provide a level of flexibility, scalability, and extensibility unique in the industry. All Check Point appliances are built around a unified security architecture, enabling organizations to perform all aspects of security management via a single, unified console. With Check Point appliances, organizations of all sizes can tailor their network security infrastructure to meet their functional and performance needs with centralized management, simple deployment, and full extensibility. Use logo with tagline for document cover UTM-1 Appliances All inclusive. All secured. UTM-1 appliances offer the ideal combination of proven security technologies and easy-to-use deployment and management features. With a full line of hardware-based solutions, Check Point UTM-1 appliances consolidate key security applications such as firewall, VPN, intrusion prevention, and antivirus and more into a single, easy-to-manage solution. UTM-1 Appliances are based on the Check Point Software Blade architecture that enables flexible and fast deployment of additional security capabilities, such as VoIP protections, without the addition of new hardware. UTM-1 appliances deliver a comprehensive set of security features including firewall, intrusion prevention, antivirus, anti-spyware, anti-spam, Web filtering, Web application security as well as secure site-to-site and remote access connectivity. UTM-1 Edge appliances deliver integrated firewall, intrusion prevention, VPN, and antivirus for branch offices of up to 100 users, ensuring small offices stay as secure as the corporate office. BENEFITS n Industry-leading application- and network-layer firewall n Site-to-site and remote-access VPNs n Gateway antivirus and anti-spyware UTM-1 Edge n Intrusion prevention with type-based protections and security updates n Web security with URL filtering and integrated security for Web applications n security and anti-spam, including the Check Point six dimensions of comprehensive messaging security n Software Blade architecture for fast and flexible deployment of new security services UTM UTM-1 appliances come in six models and UTM-1 Edge appliances come in four models that let organizations choose the right solution to meet price and performance requirements. UTM For more information: Use the logo without tagline for inside pages and back cover. Check Point Integrated Appliance Solutions Appliance Specifications Integrated software and hardware from Check Point and IBM Check Point Integrated Appliance Solutions (IAS) provide organizations with the ultimate choice in appliances integrated software and hardware bundles customized to their exact specifications. These customized platforms enable them to provision security services based on exact corporate needs. Organizations can choose from Check Point Software Blades such as firewall, IPSec VPN, and intrusion prevention, and additional blades including UTM functionality. They can also chose to deploy Check Point s virtualized security gateway, VPN-1 Power VSX, as well as Provider-1 for management of large deployments with separate security domains. Check Point integrates the selected software onto an IBM System x server or IBM BladeCenter to provide a comprehensive solution that includes direct technical support from Check Point. BENEFITS n Provides a software/hardware combination trusted by the largest organizations in the world n Reduces complexity by ensuring compatibility of the latest certified components and servers n Increases flexibility for security services provisioning by allowing customers to choose from multiple Check Point solutions n Delivers scalable performance and port density based on customer needs : n Protects against emerging threats with service-based Check Point Software Blades including IPS, Antivirus, Anti-Malware, and URL Filtering M series Integrated Appliance Solutions are predefined models that can be customized to meet specific needs. The M2 model delivers UTM functionality. The M6 and M8 models both provide maximum security for high-performance environments with integrated firewall, VPN, and intrusion prevention. UTM-1 Edge UTM UTM UTM UTM UTM UTM UTM UTM UTM UTM UTM UTM Models UTM UTM UTM UTM UTM UTM Embedded Software Edition R65, R70 R65, R70 R65, R70 R65, R70 R65, R70 R65, R70 NGX 10/100 Ports /100/1000 Ports Firewall Throughput 190 Mbps 400 Mbps 600 Mbps 1.1 Gbps 2 Gbps 3 Gbps 4.5 Gbps VPN Throughput 35 Mbps 100 Mbps 100 Mbps 250 Mbps 250 Mbps 280 Mbps 1.1 Gbps Concurrent Sessions 8, , , , million 1.1 million 1.1 million 1 IPS Throughput Mbps 380 Mbps1 700 Mbps1 900 Mbps1 1 Gbps1 4 Gbps1 Licensed Users 8/16/32/U Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited 2 VLANs UTM Out of the Box Yes Yes Yes Yes Yes Yes Yes Security Acceleration No No No No No No Yes Multisite Management No Standalone Yes Yes Yes Yes Yes Storage - 80 GB 160 GB 160 GB 160 GB 160 GB 160 GB Enclosure Desktop Desktop 1U 1U 1U 1U 1U Dimensions 1.2 x x x x x x x 15 (standard) x 4.8 in. x 1.6 in. x 1.73 in. x 1.73 in. x 1.73 in. x 1.73 in. x 1.73 in. 30 x x x x x x x 381 Dimensions (metric) x 122mm x 40mm x 44mm x 44mm x 44mm x 44mm x 44mm Weight 0.7kg (1.6lbs) 1.6kg (3.52lbs) 3.7kg (8.1lbs) 3.7kg (8.1lbs) 3.7kg (8.1lbs) 6.5kg (14.3lbs) 6.5kg (14.3lbs) Operating Environment Temperature: 5 to 40 C, Humidity: 10%-85% non-condensing, Altitude: 2,500m 3 IAS M8 Power Input 100/240V, 50/60Hz Power Supply Spec 18W 60W 65W 65W 65W 250W 250W (Max) Power 46.9W 26.2W 41.1W 40.1W 63.1W 77.5W Contact Consumption (Max) Check Point now to discuss your Total Security appliances: For more information: By phone in the US: option 5 or CONTACT CHECK POINT 2009 Check Point Software Technologies Ltd. All rights reserved. Check Point, AlertAdvisor, Application Intelligence, Check Point Endpoint Security, Check Point Endpoint Security On Demand, Check Point Express, Check Point Express CI, the Check Point logo, ClusterXL, Confidence Indexing, ConnectControl, Connectra, Connectra Accelerator Card, Cooperative Enforcement, Cooperative Security Alliance, CoreXL, CoSa, DefenseNet, Dynamic Shielding Architecture, Eventia, Eventia Analyzer, Eventia Reporter, Eventia Suite, FireWall-1, FireWall-1 GX, FireWall-1 SecureServer, FloodGate-1, Full Disk Encryption, Hacker ID, Hybrid Detection Engine, IMsecure, INSPECT, INSPECT XL, Integrity, Integrity Clientless Security, Integrity SecureClient, InterSpect, IPS-1, IQ Engine, MailSafe, NG, NGX, Open Security Extension, OPSEC, OSFirewall, Pointsec, Pointsec Mobile, Pointsec PC, Pointsec Protector, Policy Lifecycle Management,Power-1, Provider-1, PureAdvantage, PURE Security, the puresecurity logo, Safe@Home, Safe@Office, SecureClient, SecureClient Mobile, SecureKnowledge, SecurePlatform, SecurePlatform Pro, SecuRemote, SecureServer, SecureUpdate, SecureXL, SecureXL Turbocard, Security Management Portal, Sentivist, SiteManager-1, Smart-1, SmartCenter, SmartCenter Express, SmartCenter Power, SmartCenter Pro, SmartCenter UTM, SmartConsole, SmartDashboard, SmartDefense, SmartDefense Advisor, Smarter Security, SmartLSM, SmartMap, SmartPortal, SmartProvisioning, SmartUpdate, SmartView, SmartView Monitor, SmartView Reporter, SmartView Status, SmartView Tracker, SMP, SMP On-Demand, SofaWare, SSL Network Extender, Stateful Clustering, Total Security, the totalsecurity logo, TrueVector, Turbocard, UAM, UserAuthority, User-to-Address Mapping, UTM-1, UTM-1 Edge, UTM-1 Edge Industrial, UTM-1 Total Security, VPN-1, VPN-1 Accelerator Card, VPN-1 Edge, VPN-1 Express, VPN-1 Express CI, VPN-1 Power, VPN-1 Power Multi-core, VPN-1 Power VSX, VPN-1 Pro, VPN-1 SecureClient, VPN-1 SecuRemote, VPN-1 SecureServer, VPN-1 UTM, VPN-1 UTM Edge, VPN-1 VSX, VSX-1, Web Intelligence, ZoneAlarm, ZoneAlarm Anti-Spyware, ZoneAlarm Antivirus, ZoneAlarm ForceField, ZoneAlarm Internet Security Suite, ZoneAlarm Pro, ZoneAlarm Secure Wireless Router, Zone Labs, and the Zone Labs logo are trademarks or registered trademarks of Check Point Software Technologies Ltd. or its affiliates. ZoneAlarm is a Check Point Software Technologies, Inc. Company. All other product names mentioned herein are trademarks or registered trademarks of their respective owners. The products described in this document are protected by U.S. Patent No. 5,606,668, 5,835,726, 5,987,611, 6,496,935, 4
5 4. Corporate Logo Colors Our audiences recognize Check Point by our colors as well as the design of our logo. This is why all of our communications must use a consistent color palette. Never change the color of the corporate logo. White Pink Pantone 701 Blue Pantone 072 Red Pantone 200 Yellow Process Yellow C Black The color of the logotype should only be black or white. Always use the approved Pantone ( PMS ) color or the equivalent Pantone CMYK or RGB mix to reproduce colors in the logo icon. (Please see chart on the following page for exact color formula percentages.) Full-color version: Pantone Color Specifications 5
6 4. Corporate Logo Colors (continued) The Check Point Software logo color palette consists of six colors, including black and white. When printing on a nonwhite background, white must be used as an extra color for the computer screen. The chart on the right lists the formulas for the RGB colors for onscreen usage and the Pantone and process (CMYK) colors for print usage. Check Point Software Logo Color Palette PANTONE CMYK RGB Pantone 072 cyan 100 red 28 magenta 88 green 63 yellow 0 blue 148 black 5 Pantone 200 cyan 0 red 211 magenta 100 green 18 yellow 63 blue 69 black 12 Pantone 701 cyan 0 red 246 magenta 45 green 162 yellow 20 blue 168 black 0 Process Yellow C cyan 0 red 255 magenta 0 green 242 yellow 100 blue 0 black 0 Process Black cyan 0 red 0 magenta 0 green 0 yellow 0 blue 0 black 100 Opaque white for logo monitor when red 255 reproducing on solid green 255 dark background blue 255 6
7 4. Corporate Logo Colors (continued) When use of Pantone colors or four-color process is not an option, the alternatives is Black and white line art Black and White line art version 7
8 5. Corporate Logo Sizing The size of the Check Point Software logo, when used in communications and signage, depends on many variables such as environment, emphasis, audience, etc. Always consider the logo as an integral part of the design, rather than as an element to be added after the design is complete. If there is a question, make the logo larger rather than smaller. With visibility and clarity as objectives in the use of the corporate logo, a minimum acceptable size has been established to ensure readability. The minimum size for the horizontal format logo is 1.33 inches wide Logo with tagline 1.33 Logo without tagline When appearing in conjunction with other company logos in an equal relationship, the Check Point corporate logo should be at least the same size and in an equally prominent position in the layout. Example of logo size proportion for co-branding 8
9 6. Corporate Logo Clear Space Requirements Always give the Check Point logo enough clear space to garner presence on the page. A proper amount of clear space ensures that the logo will not be crowded by other elements and can be identified immediately. Mandatory clear space around corporate logo Full logo icon height Full logo icon height Illustrations, photography or type should not enter the clear space area around the logo. Full logo icon height Logo with tagline Full logo height Full logo height Full logo height Full logo height Logo without tagline 9
10 7. Unacceptable Uses of the Corporate Logo These graphic standards have been created to protect our brand and our trademarks. They help define both authorized and unauthorized uses of the corporate logo. Graphic treatments such as blurs and speed lines dilute the Check Point brand and lessen the value of our logo as a recognizable visual identity. Do not enclose the logo in a box or any other shape. Do not alter or substitute any colors of the corporate logo. Using digital artwork downloaded from CP Image Library is the best way to ensure proper use of the Check Point logo. When you use the logo in a layout, do not alter the proportions, colors or angles; such deviations weaken our brand and negatively impact our identity. Do not replace the graphical elements within the screen with other graphics. Do not use typefaces other than the approved standard for the logotype. Do not alter the proportions of the logotype or the graphic symbol in any way. Do not transpose the logotype and the graphic symbol in any way. Do not place the logo on a busy background or any solid background that does not provide strong contrast with the logo colors. 10
11 w w w. c h e c k p o i n t. c o m Worldwide Headquarters Check Point Software Technologies, Ltd. 5 Ha Solelim Street Tel Aviv 67897, Israel Tel: Fax: info@checkpoint.com U.S. Headquarters Check Point Software Technologies, Inc. 800 Bridge Parkway Redwood City, CA Tel: ; Fax:
CHECK POINT. Software Blade Architecture. Secure. Flexible. Simple.
 CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
CHECK POINT TOTAL SECURITY APPLIANCES. Flexible Deployment. Centralized Management.
 CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
The Evolution of IPS. Intrusion Prevention (Protection) Systems aren't what they used to be
 The Evolution of IPS Intrusion Prevention (Protection) Systems aren't what they used to be The Evolution of IPS Contents Background 3 Past Case for Standalone IPS 3 Organizational Control 3 Best-of-Breed
The Evolution of IPS Intrusion Prevention (Protection) Systems aren't what they used to be The Evolution of IPS Contents Background 3 Past Case for Standalone IPS 3 Organizational Control 3 Best-of-Breed
CHECK POINT. Software Blade Architecture
 CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
Endpoint Security Considerations for Achieving PCI Compliance
 Endpoint Security Considerations for Achieving PCI Compliance Contents PCI Requirements and Endpoint Security 3 Overview of the PCI Data Security Standard 3 Developing a PCI Compliance Plan 4 Endpoint
Endpoint Security Considerations for Achieving PCI Compliance Contents PCI Requirements and Endpoint Security 3 Overview of the PCI Data Security Standard 3 Developing a PCI Compliance Plan 4 Endpoint
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
Secure Remote Access for the Distributed Business. Challenges, trends, and considerations
 Secure Remote Access for the Distributed Business Challenges, trends, and considerations Secure Remote Access for the Distributed Business Contents Overview 3 Remote access trends 3 Increasing security
Secure Remote Access for the Distributed Business Challenges, trends, and considerations Secure Remote Access for the Distributed Business Contents Overview 3 Remote access trends 3 Increasing security
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Leverage IPS to Make Patch Tuesday Just Another Day
 Leverage IPS to Make Patch Tuesday Just Another Day Contents Introduction 3 Evolution of a Practice 3 Weaknesses of the Model 4 Lack of timeliness 4 Inherent predictability 4 Painful disruptions 5 A Better
Leverage IPS to Make Patch Tuesday Just Another Day Contents Introduction 3 Evolution of a Practice 3 Weaknesses of the Model 4 Lack of timeliness 4 Inherent predictability 4 Painful disruptions 5 A Better
Portal On-Demand Cost-effective and hosted managed security
 Security Management Check Point security management solutions provide unified policy management, monitoring, and analysis Security Management Portal On-Demand Cost-effective and hosted managed security
Security Management Check Point security management solutions provide unified policy management, monitoring, and analysis Security Management Portal On-Demand Cost-effective and hosted managed security
Guide to the TCO of Encryption. Deployment of Check Point data security can reduce the total cost of ownership by half
 Guide to the TCO of Encryption Deployment of Check Point data security can reduce the total cost of ownership by half Deployment of Check Point data security can reduce the total cost of ownership by half
Guide to the TCO of Encryption Deployment of Check Point data security can reduce the total cost of ownership by half Deployment of Check Point data security can reduce the total cost of ownership by half
Check Point Whitepaper. Check Point Abra: A Virtual Secure Workspace Technical Whitepaper
 Check Point Whitepaper Check Point Abra: A Virtual Secure Workspace Technical Whitepaper Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile Workforce 3 Abra Provides the Solution 4
Check Point Whitepaper Check Point Abra: A Virtual Secure Workspace Technical Whitepaper Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile Workforce 3 Abra Provides the Solution 4
How to Get NAC Up-and-Running in One Hour. For Check Point Firewall or Endpoint Security Administrators
 How to Get NAC Up-and-Running in One Hour For Check Point Firewall or Endpoint Security Administrators Contents Introduction 3 Defining an Organization s Requirements for NAC 3 Two Paths to NAC Port vs.
How to Get NAC Up-and-Running in One Hour For Check Point Firewall or Endpoint Security Administrators Contents Introduction 3 Defining an Organization s Requirements for NAC 3 Two Paths to NAC Port vs.
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 6-K Report of Foreign Private Issuer
 UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 6-K Report of Foreign Private Issuer Pursuant to Rule 13a-16 or 15d-16 of the Securities Exchange Act of 1934 For the month
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 6-K Report of Foreign Private Issuer Pursuant to Rule 13a-16 or 15d-16 of the Securities Exchange Act of 1934 For the month
How to Implement an Integrated GRC Architecture
 How to Implement an Integrated GRC Architecture Companies that select individual solutions for each regulatory challenge they face will spend 10 times more on IT portion of compliance projects than companies
How to Implement an Integrated GRC Architecture Companies that select individual solutions for each regulatory challenge they face will spend 10 times more on IT portion of compliance projects than companies
The New Face of Intrusion Prevention. Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price
 Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price Contents Better than the Best of Both Worlds 3 Best Protection 3 Best Total Threat Control 3 Reduced
Check Point IPS Software Blade gives breakthrough performance and protection at a breakthrough price Contents Better than the Best of Both Worlds 3 Best Protection 3 Best Total Threat Control 3 Reduced
The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels
 The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels The Power-1 Performance Architecture Contents Introduction 3 A delicate balance: Performance
The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels The Power-1 Performance Architecture Contents Introduction 3 A delicate balance: Performance
FORM 6-K SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549. Report of Foreign Private Issuer
 For the month of July, 2006 Commission File Number 0-28584 FORM 6-K SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Report of Foreign Private Issuer Pursuant to Rule 13a-16 or 15d-16 of the Securities
For the month of July, 2006 Commission File Number 0-28584 FORM 6-K SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 Report of Foreign Private Issuer Pursuant to Rule 13a-16 or 15d-16 of the Securities
Check Point Whitepaper. Securing Web 2.0. More Security, Lower TCO
 Check Point Whitepaper Securing Web 2.0 More Security, Lower TCO The Problem The rules of the game have changed. Internet applications were once considered to be a pass time activity; a means to see pictures
Check Point Whitepaper Securing Web 2.0 More Security, Lower TCO The Problem The rules of the game have changed. Internet applications were once considered to be a pass time activity; a means to see pictures
Solving the Performance Hurdle for Integrated IPS
 Solving the Performance Hurdle for Integrated IPS New Check Point Technologies Enable a Full-Function, Integrated Intrusion Prevention System without Compromise to Performance or Security Solving the Performance
Solving the Performance Hurdle for Integrated IPS New Check Point Technologies Enable a Full-Function, Integrated Intrusion Prevention System without Compromise to Performance or Security Solving the Performance
Appliance Comparison Chart
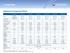 Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Check Point Whitepaper. Enterprise IPv6 Transition Technical Whitepaper
 Check Point Whitepaper Enterprise IPv6 Transition Technical Whitepaper Contents Introduction 3 Transition Mechanisms 3 Dual Stack 4 Tunneling 4 Translation 7 Recommendations 8 Transition Security Considerations
Check Point Whitepaper Enterprise IPv6 Transition Technical Whitepaper Contents Introduction 3 Transition Mechanisms 3 Dual Stack 4 Tunneling 4 Translation 7 Recommendations 8 Transition Security Considerations
Neutralizing Spyware in the Enterprise Environment
 White Paper Neutralizing Spyware in the Enterprise Environment Check Point protects every part of your network perimeter, internal, Web to keep your information resources safe, accessible, and easy to
White Paper Neutralizing Spyware in the Enterprise Environment Check Point protects every part of your network perimeter, internal, Web to keep your information resources safe, accessible, and easy to
Check Point GO: A Virtual Secure Workspace Technical Whitepaper
 Check Point Whitepaper Check Point GO: A Virtual Secure Workspace Technical Whitepaper Check Point GO Put your office in your pocket Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile
Check Point Whitepaper Check Point GO: A Virtual Secure Workspace Technical Whitepaper Check Point GO Put your office in your pocket Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile
Software Blade Architecture
 Software Blade Architecture Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity and performance
Software Blade Architecture Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity and performance
Check Point. Software Blade Architecture
 Check Point Software Blade Architecture TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity
Check Point Software Blade Architecture TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity
USB Drives: Friend or Foe? New User Trends and Exploits in USB Requires Security Controls to Protect Endpoints and the Networked Enterprise
 New User Trends and Exploits in USB Requires Security Controls to Protect Endpoints and the Networked Enterprise Contents Executive Summary 3 Exploiting Risks of USB Drives and Portable Applications 3
New User Trends and Exploits in USB Requires Security Controls to Protect Endpoints and the Networked Enterprise Contents Executive Summary 3 Exploiting Risks of USB Drives and Portable Applications 3
SOFTWARE BLADE ARCHITECTURE
 SOFTWARE BLADE ARCHITECTURE 2015 CHECK POINT APPLIANCES 03 TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure,
SOFTWARE BLADE ARCHITECTURE 2015 CHECK POINT APPLIANCES 03 TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure,
SOFTWARE BLADE ARCHITECTURE
 SOFTWARE BLADE ARCHITECTURE 2015 CHECK POINT APPLIANCES 03 TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure,
SOFTWARE BLADE ARCHITECTURE 2015 CHECK POINT APPLIANCES 03 TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure,
Defending Small and Medium Sized Businesses with Cloud-Managed Security
 Defending Small and Medium Sized Businesses with Cloud-Managed Security Contents Introduction 3 Social Networking Could Mean Compromised Networks 4 Blended Threats More Blended than Ever 5 The Cloud Revolution
Defending Small and Medium Sized Businesses with Cloud-Managed Security Contents Introduction 3 Social Networking Could Mean Compromised Networks 4 Blended Threats More Blended than Ever 5 The Cloud Revolution
Unified Threat Management from Check Point. The security you need. The simplicity you want
 Unified Threat Management from Check Point The security you need. The simplicity you want Unified Threat Management from Check Point Contents Introduction 3 Complexity of the security problem 3 Comprehensive
Unified Threat Management from Check Point The security you need. The simplicity you want Unified Threat Management from Check Point Contents Introduction 3 Complexity of the security problem 3 Comprehensive
Check Point Endpoint Security. Single agent for endpoint security delivering total protection and simplified management
 Single agent for endpoint security delivering total protection and simplified management Contents Executive summary 3 Meeting the challenge of securing endpoints 4 A new strategy: Unifying endpoint security
Single agent for endpoint security delivering total protection and simplified management Contents Executive summary 3 Meeting the challenge of securing endpoints 4 A new strategy: Unifying endpoint security
Best Practices for Deploying Intrusion Prevention Systems. A better approach to securing networks
 Best Practices for Deploying Intrusion Prevention Systems A better approach to securing networks A better approach to securing networks Contents Introduction 3 Understanding deployment needs 3 Selecting
Best Practices for Deploying Intrusion Prevention Systems A better approach to securing networks A better approach to securing networks Contents Introduction 3 Understanding deployment needs 3 Selecting
Stateful Inspection Technology
 White Paper Stateful Inspection Technology The industry standard for enterprise-class network security solutions Check Point protects every part of your network perimeter, internal, Web to keep your information
White Paper Stateful Inspection Technology The industry standard for enterprise-class network security solutions Check Point protects every part of your network perimeter, internal, Web to keep your information
SECURITY APPLIANCES www.checkpoint.com
 CHECK POINT SECURITY APPLIANCES www.checkpoint.com Table of Contents Introduction 1 Power-1 Appliances 2 IP Appliances 3 UTM-1 Appliances 4 Series 80 Appliance 5 VSX-1 Appliances 6 DLP-1 Appliances 7 Smart-1
CHECK POINT SECURITY APPLIANCES www.checkpoint.com Table of Contents Introduction 1 Power-1 Appliances 2 IP Appliances 3 UTM-1 Appliances 4 Series 80 Appliance 5 VSX-1 Appliances 6 DLP-1 Appliances 7 Smart-1
Achieving a Clean Bill of Health in HIPAA Compliance with Check Point Solutions
 Achieving a Clean Bill of Health in HIPAA Compliance with Check Point Solutions Contents Executive summary 3 Overview of HIPAA and the healthcare environment 4 The HIPAA security challenge 7 A healthy
Achieving a Clean Bill of Health in HIPAA Compliance with Check Point Solutions Contents Executive summary 3 Overview of HIPAA and the healthcare environment 4 The HIPAA security challenge 7 A healthy
Virtualized Network Security with. A VPN-1 better approach Power to securing VSX networks
 Virtualized Network Security with A VPN-1 better approach Power to securing VSX networks Contents Executive summary 3 Introduction to virtualization 4 Check Point VPN-1 Power VSX 4 Components virtualized
Virtualized Network Security with A VPN-1 better approach Power to securing VSX networks Contents Executive summary 3 Introduction to virtualization 4 Check Point VPN-1 Power VSX 4 Components virtualized
Preventing Data Leaks on USB Ports. Check Point Endpoint Security Media Encryption simply regulates access and data for any plug-and-play peripherals
 Preventing Data Leaks on USB Ports Check Point Endpoint Security Media Encryption simply regulates access and data for any plug-and-play peripherals Preventing Data Leaks on USB Ports Contents Executive
Preventing Data Leaks on USB Ports Check Point Endpoint Security Media Encryption simply regulates access and data for any plug-and-play peripherals Preventing Data Leaks on USB Ports Contents Executive
Pointsec PC. Quick Start Guide
 Pointsec PC Quick Start Guide Version 6.3.1 HFA1, A April 2008 2003-2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and
Pointsec PC Quick Start Guide Version 6.3.1 HFA1, A April 2008 2003-2008 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and
Configuring Check Point Firewall-1 to support Avaya Contact Center Solutions - Issue 1.1
 Avaya Solution & Interoperability Test Lab Configuring Check Point Firewall-1 to support Avaya Contact Center Solutions - Issue 1.1 Abstract These Application Notes explain how to configure Check Point
Avaya Solution & Interoperability Test Lab Configuring Check Point Firewall-1 to support Avaya Contact Center Solutions - Issue 1.1 Abstract These Application Notes explain how to configure Check Point
Check Point Endpoint Security Full Disk Encryption. Detailed product overview for Windows and Linux
 Check Point Endpoint Security Full Disk Encryption Detailed product overview for Windows and Linux Check Point Endpoint Security Full Disk Encryption Contents How secure is my data? 3 How effective is
Check Point Endpoint Security Full Disk Encryption Detailed product overview for Windows and Linux Check Point Endpoint Security Full Disk Encryption Contents How secure is my data? 3 How effective is
User Guide for ZoneAlarm security software
 User Guide for ZoneAlarm security software version 7.1 Smarter Security TM 2003-2007 Check Point Software Technologies Ltd. All rights reserved. Check Point, AlertAdvisor, Application Intelligence, Check
User Guide for ZoneAlarm security software version 7.1 Smarter Security TM 2003-2007 Check Point Software Technologies Ltd. All rights reserved. Check Point, AlertAdvisor, Application Intelligence, Check
Check Point UserAuthority Guide. Version NGX R61
 Check Point UserAuthority Guide Version NGX R61 700358 January 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point UserAuthority Guide Version NGX R61 700358 January 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point QoS. Administration Guide Version NGX R65
 Check Point QoS Administration Guide Version NGX R65 700726 January 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point QoS Administration Guide Version NGX R65 700726 January 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
A Getting Started Guide: What Every Small Business Needs To Know About Internet Security
 A Getting Started Guide: What Every Small Business Needs To Know About Internet Security In This Document 1 Overview: Internet Security In Small Businesses 2 Internet Access New Business Opportunities
A Getting Started Guide: What Every Small Business Needs To Know About Internet Security In This Document 1 Overview: Internet Security In Small Businesses 2 Internet Access New Business Opportunities
LICENSE GUIDE. Software Blades products. Number of Strings. SKU Prefix Name Description Additive
 LICENSE GUIDE Software Blades products SKU Prefix Name Description Additive CPAP-SG5075 CPAP-SG9075 CPAP-SG11065 CPAP-SG11075 CPAP-SG11085 CPAP-IP2455 CPAP-IP1285 CPAP-IP695 CPAP-IP565 CPAP-IP395 CPAP-IP295
LICENSE GUIDE Software Blades products SKU Prefix Name Description Additive CPAP-SG5075 CPAP-SG9075 CPAP-SG11065 CPAP-SG11075 CPAP-SG11085 CPAP-IP2455 CPAP-IP1285 CPAP-IP695 CPAP-IP565 CPAP-IP395 CPAP-IP295
Firewall and SmartDefense. Administration Guide Version NGX R65
 Firewall and SmartDefense Administration Guide Version NGX R65 701682 April 27, 2008 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Firewall and SmartDefense Administration Guide Version NGX R65 701682 April 27, 2008 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Integrity Advanced Server Gateway Integration Guide
 Integrity Advanced Server Gateway Integration Guide 1-0273-0650-2006-03-09 Editor's Notes: 2006 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application Intelligence, Check
Integrity Advanced Server Gateway Integration Guide 1-0273-0650-2006-03-09 Editor's Notes: 2006 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application Intelligence, Check
Check Point 2200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
The Seven Key Factors for Internet Security TCO
 The Seven Key Factors for Internet Security TCO Executive Summary Total Cost of Ownership, or TCO, of any information technology deployment consists of more than simply the direct costs of acquisition
The Seven Key Factors for Internet Security TCO Executive Summary Total Cost of Ownership, or TCO, of any information technology deployment consists of more than simply the direct costs of acquisition
Check Point Appliances. 2012 Models
 Check Point Appliances 2012 Models Table of Contents Introduction 3 Check Point GAiA the Next-Gen Security OS 4 About SecurityPower 5 2200 Appliance 6 4000 Appliances 7 12000 Appliances 8 21400 Appliance
Check Point Appliances 2012 Models Table of Contents Introduction 3 Check Point GAiA the Next-Gen Security OS 4 About SecurityPower 5 2200 Appliance 6 4000 Appliances 7 12000 Appliances 8 21400 Appliance
Malicious Code Protector
 Malicious Code Protector A New Approach for Detecting and Blocking Buffer Overflow Attacks In This Document Introduction 2 Buffer Overflow Attacks 3 Current Defenses Against Buffer Overflow Attacks 3 A
Malicious Code Protector A New Approach for Detecting and Blocking Buffer Overflow Attacks In This Document Introduction 2 Buffer Overflow Attacks 3 Current Defenses Against Buffer Overflow Attacks 3 A
User Guide for Zone Labs security software
 User Guide for Zone Labs security software version 6.5 Smarter Security TM 2006 Zone Labs, LLC. All rights reserved. 2006 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
User Guide for Zone Labs security software version 6.5 Smarter Security TM 2006 Zone Labs, LLC. All rights reserved. 2006 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
A Practical Guide to Web Application Security
 Mitigating the OWASP Ten Most Critical Web Application Security Problems with s In This Document Introduction 2 The Top 10 Web Application Vulnerabilities and Their Remedies 1: Unvalidated Input 3 2: Broken
Mitigating the OWASP Ten Most Critical Web Application Security Problems with s In This Document Introduction 2 The Top 10 Web Application Vulnerabilities and Their Remedies 1: Unvalidated Input 3 2: Broken
User Guide for Zone Labs security software
 User Guide for Zone Labs security software Version 6.0 Smarter Security TM 2005 Zone Labs, LLC. All rights reserved. 2005 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
User Guide for Zone Labs security software Version 6.0 Smarter Security TM 2005 Zone Labs, LLC. All rights reserved. 2005 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
How To Set Up Checkpoint Vpn For A Home Office Worker
 SofaWare VPN Configuration Guide Part No.: 700411 Oct 2002 For Safe@ gateway version 3 COPYRIGHT & TRADEMARKS Copyright 2002 SofaWare, All Rights Reserved. SofaWare, SofaWare S-box, Safe@Home and Safe@Office
SofaWare VPN Configuration Guide Part No.: 700411 Oct 2002 For Safe@ gateway version 3 COPYRIGHT & TRADEMARKS Copyright 2002 SofaWare, All Rights Reserved. SofaWare, SofaWare S-box, Safe@Home and Safe@Office
SonicWALL Corporate Design System. The SonicWALL Brand Identity
 SonicWALL Corporate Design System The SonicWALL Brand Identity 1 SonicWALL Corporate Vision Vision Dynamic Security for the Global Network Our vision is simple: we believe security solutions should be
SonicWALL Corporate Design System The SonicWALL Brand Identity 1 SonicWALL Corporate Vision Vision Dynamic Security for the Global Network Our vision is simple: we believe security solutions should be
Check Point Security Administrator R70
 Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
User Guide for Zone Labs Security Software
 User Guide for Zone Labs Security Software Version 5.5 Smarter Security TM 2004 Zone Labs, Inc. All rights reserved. 2004 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
User Guide for Zone Labs Security Software Version 5.5 Smarter Security TM 2004 Zone Labs, Inc. All rights reserved. 2004 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
Check Point taps the power of virtualization to simplify security for private clouds
 Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Check Point ZoneAlarm
 Check Point ZoneAlarm Secure Wireless Router Z100G User Guide Version 7.5 August 2007 COPYRIGHT & TRADEMARKS Copyright 2007 SofaWare, All Rights Reserved. No part of this document may be reproduced in
Check Point ZoneAlarm Secure Wireless Router Z100G User Guide Version 7.5 August 2007 COPYRIGHT & TRADEMARKS Copyright 2007 SofaWare, All Rights Reserved. No part of this document may be reproduced in
Pointsec PC Linux Edition. Installation Guide
 Pointsec PC Linux Edition Installation Guide Version 2.2.2 A October 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Pointsec PC Linux Edition Installation Guide Version 2.2.2 A October 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Eventia Suite. Getting Started Guide. Version: NGX R63. 702215 January 10, 2007
 TM Eventia Suite Getting Started Guide Version: NGX R63 702215 January 10, 2007 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
TM Eventia Suite Getting Started Guide Version: NGX R63 702215 January 10, 2007 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
PURE Security. Revolutionising the way you think about IT Security. Protected infrastructure and data. Unified security architecture
 PURE Security Revolutionising the way you think about IT Security Since founding in 1993 has become the de facto standard in network security. Today we are more than just a firewall vendor. Our PURE security
PURE Security Revolutionising the way you think about IT Security Since founding in 1993 has become the de facto standard in network security. Today we are more than just a firewall vendor. Our PURE security
VPN-1 VE Evaluation Guide
 VPN-1 VE Evaluation Guide This document is intended for users who are new to Check Point VPN-1 products and would like to evaluate and review VPN-1 VE. We recommend reading the VPN-1 VE Administration
VPN-1 VE Evaluation Guide This document is intended for users who are new to Check Point VPN-1 products and would like to evaluate and review VPN-1 VE. We recommend reading the VPN-1 VE Administration
User Guide for ZoneAlarm security software
 User Guide for ZoneAlarm security software version 7.0 Smarter Security TM 2007 Zone Labs, LLC. All rights reserved. 2007 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
User Guide for ZoneAlarm security software version 7.0 Smarter Security TM 2007 Zone Labs, LLC. All rights reserved. 2007 Check Point Software Technologies Ltd. All rights reserved. Check Point, Application
Introduction to Endpoint Security
 Chapter Introduction to Endpoint Security 1 This chapter provides an overview of Endpoint Security features and concepts. Planning security policies is covered based on enterprise requirements and user
Chapter Introduction to Endpoint Security 1 This chapter provides an overview of Endpoint Security features and concepts. Planning security policies is covered based on enterprise requirements and user
Check Point Safe@Office 500 UTM Frequently Asked Questions
 For internal use only Check Point Safe@Office 500 UTM Frequently Asked Questions Business Related Questions What are Safe@Office appliances? Designed specifically to meet the needs of small businesses,
For internal use only Check Point Safe@Office 500 UTM Frequently Asked Questions Business Related Questions What are Safe@Office appliances? Designed specifically to meet the needs of small businesses,
NG with Application Intelligence (R55) http://support.checkpoint.com/kb/ See the latest version of this document in the User Center at:
 VPN-1 NG with Application Intelligence (R55) For additional technical information about Check Point products, consult Check Point s SecureKnowledge at: http://support.checkpoint.com/kb/ See the latest
VPN-1 NG with Application Intelligence (R55) For additional technical information about Check Point products, consult Check Point s SecureKnowledge at: http://support.checkpoint.com/kb/ See the latest
The Attacker s Target: The Small Business
 Check Point Whitepaper The Attacker s Target: The Small Business Even Small Businesses Need Enterprise-class Security to protect their Network July 2013 Contents Introduction 3 Enterprise-grade Protection
Check Point Whitepaper The Attacker s Target: The Small Business Even Small Businesses Need Enterprise-class Security to protect their Network July 2013 Contents Introduction 3 Enterprise-grade Protection
AirWatch by VMware. Partner Brand Guide
 AirWatch by VMware Partner Brand Guide AirWatch by VMware Partner Brand Guide Introduction 3 Corporate Logo 4 Logo Specifications 4 Colors and File Formats 4 Print 4 Digital 4 Logo Options 4 Sizing 5 Backgrounds
AirWatch by VMware Partner Brand Guide AirWatch by VMware Partner Brand Guide Introduction 3 Corporate Logo 4 Logo Specifications 4 Colors and File Formats 4 Print 4 Digital 4 Logo Options 4 Sizing 5 Backgrounds
Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs
 Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs P/N 500205 July 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 1 Integrated VPN/firewall Page 2 placed
Why Choose Integrated VPN/Firewall Solutions over Stand-alone VPNs P/N 500205 July 2000 Check Point Software Technologies Ltd. In this Document: Introduction Page 1 Integrated VPN/firewall Page 2 placed
Remote Access Clients for Windows
 Remote Access Clients for Windows E80.60 Release Notes 3 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Remote Access Clients for Windows E80.60 Release Notes 3 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Check Point License Guide (April-2012) General Pricelist
 CPAP-SG61* License Guide (April-2012) General Pricelist SKU Prefix Name Description Blades included CPAP-SG21412 CPAP-SG12610 CPAP-SG12608 CPAP-SG12607 CPAP-SG12410 CPAP-SG12408 CPAP-SG12407 CPAP-SG12210
CPAP-SG61* License Guide (April-2012) General Pricelist SKU Prefix Name Description Blades included CPAP-SG21412 CPAP-SG12610 CPAP-SG12608 CPAP-SG12607 CPAP-SG12410 CPAP-SG12408 CPAP-SG12407 CPAP-SG12210
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Antivirus. Quick Start Guide. Antivirus
 Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Antivirus 2007 Antivirus plus I Firewall Quick Start Guide Helpful Information on Installation and Set-Up STOPS and Removes Viruses DELIVERS Proactive Firewall Protection EASY to Set Up and Use FREE Upgrades
Endpoint Security VPN for Mac
 Security VPN for Mac E80.41 Release Notes 16 January 2013 Classification: [Protected] 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
Security VPN for Mac E80.41 Release Notes 16 January 2013 Classification: [Protected] 2013 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
IREBOX X. Firebox X Family of Security Products. Comprehensive Unified Threat Management Solutions That Scale With Your Business
 IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
Endpoint Security VPN for Mac
 Security VPN for Mac E75 Release Notes 8 April 2012 Classification: [Protected] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Security VPN for Mac E75 Release Notes 8 April 2012 Classification: [Protected] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions
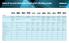 Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions Positioning Enterprise ROBO 8, 16, 32 and Unlimited Work extender, telecommuter, small office FW or VPN Medium businesses
Nokia IP Security Platforms Technical Specifications Guide Nokia Enterprise Solutions Positioning Enterprise ROBO 8, 16, 32 and Unlimited Work extender, telecommuter, small office FW or VPN Medium businesses
CONTENTS. 3 Introduction. 7 Nuance Corporate Signature. 5 Nuance Corporate Signature Color. Minimum Size and Clearspace Requirements
 NUANCE Interim corporate identity styleguide O C T O B E R 2 0 0 5 CONTENTS 3 Introduction 4 Nuance Corporate Signature 5 Nuance Corporate Signature Color 6 Nuance Corporate Signature Minimum Size and
NUANCE Interim corporate identity styleguide O C T O B E R 2 0 0 5 CONTENTS 3 Introduction 4 Nuance Corporate Signature 5 Nuance Corporate Signature Color 6 Nuance Corporate Signature Minimum Size and
Security. Quick Sales Guide
 Security Quick Sales Guide Security Quick Finder 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 Unified Security Gateway (Hybrid VPN & UTM) 50 ~ 75 PC Users USG 300 USG 200 10 ~ 50 PC Users USG
Security Quick Sales Guide Security Quick Finder 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 Unified Security Gateway (Hybrid VPN & UTM) 50 ~ 75 PC Users USG 300 USG 200 10 ~ 50 PC Users USG
Appliance Comparison Chart
 202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
SOMERS POINT BRAND IDENTITY STYLE GUIDE
 SOMERS POINT BRAND IDENTITY STYLE GUIDE WHAT IT IS The new Somers Point logo will be the single most recognizable icon used to represent our City. WHY IT MATTERS Our logo immediately identifies our brand.
SOMERS POINT BRAND IDENTITY STYLE GUIDE WHAT IT IS The new Somers Point logo will be the single most recognizable icon used to represent our City. WHY IT MATTERS Our logo immediately identifies our brand.
Check Point Positions
 Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
Cisco SR 520-T1 Secure Router
 Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
2015 Marketing Guidelines. 2015 Parallels IP Holdings GmbH. All rights reserved. Terms of Use Privacy Policy
 2015 Marketing Guidelines 2015 Parallels IP Holdings GmbH. All rights reserved. Terms of Use Privacy Policy Master Brand Components The Parallels logo is the cornerstone of the Parallels brand. Please
2015 Marketing Guidelines 2015 Parallels IP Holdings GmbH. All rights reserved. Terms of Use Privacy Policy Master Brand Components The Parallels logo is the cornerstone of the Parallels brand. Please
The FIAT Brand. Key Visual Elements and Usage Guidelines
 The FIAT Brand Key Visual Elements and Usage Guidelines Contents Brand Mark Guidelines 3 FIAT Brand Mark / trademark statement 4 exclusion zone 5 Primary FIAT Brand Mark 6 secondary fiat brand mark 7 tertiary
The FIAT Brand Key Visual Elements and Usage Guidelines Contents Brand Mark Guidelines 3 FIAT Brand Mark / trademark statement 4 exclusion zone 5 Primary FIAT Brand Mark 6 secondary fiat brand mark 7 tertiary
NG with Application Intelligence (R55)
 SmartView Monitor NG with Application Intelligence (R55) IMPORTANT Check Point recommends that customers stay up-to-date with the latest service packs and versions of security products, as they contain
SmartView Monitor NG with Application Intelligence (R55) IMPORTANT Check Point recommends that customers stay up-to-date with the latest service packs and versions of security products, as they contain
Logo Standards Guideline
 Logo Standards Guideline TABLE OF CONTENTS Nurturing The Brand 1 Logo Guidelines 2 Correct Usage 2 Color Guidelines 6 How to Use the Provided Logo Files 9 Glossary 10 NURTURING THE BRAND THE FOLLOWING
Logo Standards Guideline TABLE OF CONTENTS Nurturing The Brand 1 Logo Guidelines 2 Correct Usage 2 Color Guidelines 6 How to Use the Provided Logo Files 9 Glossary 10 NURTURING THE BRAND THE FOLLOWING
THIRD-PARTY BRAND. Version 1.1
 COMCAST Business Class THIRD-PARTY BRAND Guidelines Version 1.1 July 2, 2012 Contents 1 Using the third-party brand guidelines 2 Third-party logos 3 Clearspace and minimum size 4 Third-party logo color
COMCAST Business Class THIRD-PARTY BRAND Guidelines Version 1.1 July 2, 2012 Contents 1 Using the third-party brand guidelines 2 Third-party logos 3 Clearspace and minimum size 4 Third-party logo color
Microsoft Partner Program Certified Partner Logo Usage Guidelines
 This document provides guidelines on the use of logos and visual brand elements on all Microsoft partner marketing and collateral materials. Regardless of whether they originate from Microsoft or the partner,
This document provides guidelines on the use of logos and visual brand elements on all Microsoft partner marketing and collateral materials. Regardless of whether they originate from Microsoft or the partner,
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
SmartView Monitor. R77 Versions. Administration Guide. 21 May 2014. Classification: [Protected]
![SmartView Monitor. R77 Versions. Administration Guide. 21 May 2014. Classification: [Protected] SmartView Monitor. R77 Versions. Administration Guide. 21 May 2014. Classification: [Protected]](/thumbs/39/19291733.jpg) SmartView Monitor R77 Versions Administration Guide 21 May 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
SmartView Monitor R77 Versions Administration Guide 21 May 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected
PROFESSIONAL SECURITY SYSTEMS
 PROFESSIONAL SECURITY SYSTEMS Check Point SecurePlatform Firewall security platform for use in the systems with increased security requirements IT technologies are essential for proper operation of majority
PROFESSIONAL SECURITY SYSTEMS Check Point SecurePlatform Firewall security platform for use in the systems with increased security requirements IT technologies are essential for proper operation of majority
Astaro Gateway Software Applications
 Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Checkpoint 156-815. 156-815 Check Point Provider-1 NGX (v4) Practice Test. Version 2.1
 Checkpoint 156-815 156-815 Check Point Provider-1 NGX (v4) Practice Test Version 2.1 QUESTION NO: 1 Two CMAs can be created for a single Customer, for High availability (HA). Which of these statements
Checkpoint 156-815 156-815 Check Point Provider-1 NGX (v4) Practice Test Version 2.1 QUESTION NO: 1 Two CMAs can be created for a single Customer, for High availability (HA). Which of these statements
BRAND GUIDELINES NOVEMBER 2015
 BRAND GUIDELINES NOVEMBER 2015 2 TABLE OF CONTENTS The WatchGuard Brand 3 Logo Color Use 4 Logo Clearances 5 Logo Correct & incorrect Uses 6 Tagline ADVANCED NETWORK SECURITY 7 WatchGuardONE Logo Usage
BRAND GUIDELINES NOVEMBER 2015 2 TABLE OF CONTENTS The WatchGuard Brand 3 Logo Color Use 4 Logo Clearances 5 Logo Correct & incorrect Uses 6 Tagline ADVANCED NETWORK SECURITY 7 WatchGuardONE Logo Usage
