SECURITY APPLIANCES
|
|
|
- Dinah Wilkinson
- 10 years ago
- Views:
Transcription
1 CHECK POINT SECURITY APPLIANCES
2 Table of Contents Introduction 1 Power-1 Appliances 2 IP Appliances 3 UTM-1 Appliances 4 Series 80 Appliance 5 VSX-1 Appliances 6 DLP-1 Appliances 7 Smart-1 Appliances 8 Smart-1 SmartEvent Appliances 9 Integrated Appliance Solutions 10 Appliance Specifications 14
3 Introduction Check Point appliances deliver a powerful turnkey solution for deploying Check Point award-winning software solutions to address virtually any security need. Based on the new Check Point Software Blade Architecture, Check Point appliances provide the highest level of flexibility, scalability, and extensibility in the industry. All Check Point appliances are built around a unified security architecture, enabling organizations to perform all aspects of security management via a single, unified console. With Check Point appliances, organizations of all sizes can tailor their network security infrastructure to meet their functional and performance needs with centralized management, simple deployment, and full extensibility. CHECK POINT APPLIANCE OPTIONS Check Point offers the following appliance options to effectively deliver comprehensive security applications: n Dedicated Appliances Check Point dedicated hardware platforms devoted to a single security application such as intrusion prevention (IPS) and data loss prevention (DLP). Dedicated appliances provide hardware resources for a single application, delivering higher performance. n Integrated Appliances Check Point integrated appliances take an all-in-one approach, combining multiple security applications on a single enterprise-class platform. Because applications are consolidated within a unified security architecture, organizations can reduce TCO and simplify security configuration. n IAS Bladed Hardware Check Point bladed hardware platforms include a chassis with multiple hardware blades that run independent security applications. Each blade is equivalent to an independent server or appliance, and contains dedicated resources for the Software Blades. Bladed hardware platforms deliver built-in failover and load-balancing utilities, as well as an increase in system performance. 1
4 Power-1 Appliances Security for high-performance environments OVERVIEW Check Point Power-1 appliances enable organizations to maximize security in high-performance environments such as large campuses or data centers. They combine integrated firewall, IPsec VPN, and intrusion prevention with advanced acceleration and networking technologies, delivering a high-performance security platform for multi-gbps environments. The Check Point Software Blade Architecture enables flexible and fast deployment of additional security capabilities, such as VoIP protections and UTM functionality, on Power-1 appliances. BENEFITS n Streamlines deployment of enterprise security for large offices and data centers n Ensures availability of business-critical applications with up to 30 Gbps firewall throughput and up to 15 Gbps intrusion prevention throughput n Provides comprehensive security including Firewall, IPS, IPsec VPN, Advanced Networking, and Acceleration & Clustering Software Blades n Protects against emerging threats with optional Software Blades such as VoIP, Web Security, Antivirus, and more n Simplifies administration with a single management console for all sites n Power series adds performance extensibility via field upgradeability and enables customers to boost performance by 100% from lowest to highest model Power-1 appliances, which include Power , Power , and the Power series, let organizations choose the proper levels of performance and port density for their environments. Power Power Power series For more information: 2
5 IP Appliances Flexible networking and performance options OVERVIEW Proven for years in complex networking and performance-demanding environments, Check Point IP Appliances offer customers integrated turnkey security functionality such as firewall, VPN, and intrusion prevention across a wide range of models. Optimized for Check Point Security Gateway software, the IP Appliances offer unsurpassed scalability, high performance, manageability, and high port densities that reduces operational costs in complex, mission-critical security environments. IP Appliances enable customers to extend a unified security architecture from the network core out to branch and remote offices. IP297 BENEFITS n Integrated security appliances based on Check Point Software Blade Architecture for fast, flexible deployment of security functionality n Scalable, modular, and configurable security architecture with multiple acceleration (ADP service modules), security, and interface options insures investment protection n Achieve high performance across a broad spectrum of traffic types n Enterprise-class high availability, scalability, and fault tolerance to insure network resiliency and business continuity n Carrier-grade serviceability and redundancy n Streamlined IT efficiency with advanced management tools for installation, configuration, and maintenance IP697 IP2457 IP Appliances come in six models that deliver security solutions ideal for large enterprises, carrier-grade networks and remote and branch offices. Accelerated Data Path (ADP) for IP Appliances For more information: 3
6 UTM-1 Appliances All inclusive. All secured. OVERVIEW UTM-1 appliances offer the ideal combination of proven security technologies and easy-to-use deployment and management features. With a full line of hardware-based solutions, Check Point UTM-1 appliances consolidate key security applications such as firewall, VPN, intrusion prevention, and antivirus and more into a single, easy-to-manage solution. UTM-1 Appliances are based on the Check Point Software Blade Architecture that enables flexible and fast deployment of additional security capabilities, such as VoIP protections, without the addition of new hardware. UTM-1 appliances deliver a comprehensive set of security features including firewall, intrusion prevention, antivirus, anti-spyware, anti-spam, Web filtering, Web application security as well as secure site-to-site and remote access connectivity. UTM-1 Edge family of appliances deliver integrated firewall, intrusion prevention, VPN, and antivirus for branch offices of up to 100 users, ensuring small offices stay as secure as the corporate office. BENEFITS n Industry-leading application- and network-layer firewall n Site-to-site and remote-access VPNs n Gateway antivirus and anti-spyware n Intrusion prevention with type-based protections and security updates n Web security with URL filtering and integrated security for Web applications n security and anti-spam, including the Check Point six dimensions of comprehensive messaging security n Software Blade Architecture for fast and flexible deployment of new security services UTM-1 appliances come in six models and UTM-1 Edge family of appliances consists of X-Series and N-Series models. UTM-1 Edge X-Series appliances come in four models and UTM-1 Edge N-Series appliances come in two models that let organizations choose the right solution to meet price and performance requirements. UTM-1 Edge N-Series UTM UTM For more information: 4
7 Series 80 Appliance Enterprise-grade branch office security OVERVIEW The Check Point Series 80 Appliance raises the bar on remote and branch office security by extending Software Blades to the edge of the network delivering enterprise-grade security in a high-performance desktop form factor. The Series 80 appliance delivers IPsec/SSL VPN and the same industry-proven firewall technology that secures the Global 100 all right out-of-the box. Based on the Check Point Software Blade Architecture, the Series 80 appliance enables flexible, single-click upgrades of additional security capabilities, including IPS, antivirus and anti-malware, anti-spam and security, and URL filtering. And, the Series 80 can be easily configured, deployed and managed without the need for corporate IT staff. BENEFITS n Delivers flexible and manageable enterprise-grade security for branch offices n Includes Best-in-Class Integrated Firewall and IPsec/ SSL VPN n Provides the best price/performance in its class with proven throughput of 1.5 Gbps for firewall, 220 Mbps for VPN and 720 Mbps for IPS n Protects against emerging threats with optional Software Blades such as IPS, antivirus, security, and more n High port density provides enhanced performance and minimizes the overhead of switches and routers in remote environments n New intuitive and fast start-up wizard allows hassle-free configuration, deployment and management n Centrally managed by SmartCenter and Provider-1 Series 80 Series 80 For more information: 5
8 VSX-1 Appliances Virtualized security OVERVIEW The VSX-1 appliances are virtualized security gateways that enable the creation of hundreds of security systems on a single hardware platform, delivering deep cost savings and infrastructure consolidation. Based on the proven security of VPN-1 Power, VSX-1 provides best-in-class firewall, VPN, URL filtering, and intrusion-prevention technology to multiple networks, securely connecting them to each other and shared resources such as the Internet and DMZs. All security systems, virtual and real, are centrally managed through Check Point SmartCenter or or Multi-Domain Security Management consoles. Powerful turnkey VSX-1 appliances further reduce deployment cost while delivering carrier-class reliability and scalability. VSX-1 enables any organization to optimize space and costs by operating a virtual network of hundreds of routers, switches, and VPN-1 gateways. For MSPs, VSX-1 becomes the ideal platform for new subscription revenue opportunities by delivering new security services easily and efficiently. These include value-add virtualized content filtering, VPN, network segmentation and firewall services, instantly provisioned using the VSX Virtual Systems Wizard at the lowest possible cost. BENEFITS n Unique and comprehensive virtualized security solution with firewall, VPN, IPS, and URL filtering n Consolidate from five to hundreds of security gateways on a single device, increasing device hardware utilization and reducing power, space, and cooling n Linear scalability, load sharing and multi-gigabit performance n Flexible deployment options including open platforms and a full line of turnkey appliances n Centralized security management unifies both physical and virtual management in a single solution VSX VSX-1 appliances come in nine models that allow organizations to choose the right solution for their performance and scalability needs. VSX VSX /70/80 For more information: 6
9 DLP-1 Appliances Check Point makes DLP work OVERVIEW Check Point DLP-1 solves the longstanding problem with data loss prevention technology enabling organizations to effectively protect sensitive company and customer data, without placing an additional burden on your scarce IT resources. Check Point DLP combines state-of-the-art prevention and enforcement with end user remediation capabilities, for the ideal blend of security and usability. UserCheck, Check Point s unique user remediation function, educates users on self-incident handling and corporate data policies, while empowering them to remediate events in real-time. Files that are sent or uploaded to the web are processed by Check Point MultiSpect, a multi-data classification engine that inspects traffic flow for all data-in-motion, and provides high accuracy in correlating users, data types, and processes. BENEFITS n Easily defines data policies while assuring consistent enforcement across the entire network n Prevents data loss by inspecting traffic in real-time, and proactively blocking the transmission of sensitive information n Includes more than 250 pre-defined best-practices policies and rules for easy administration n High performance from 700Mbps to over 2.5Gbps n Centralized Check Point management for unprecedented visibility and control n Open scripting language to create customized data types for easily extensible and granular prevention DLP DLP For more information: 7
10 Smart-1 Appliances Extensible security management OVERVIEW Smart-1 appliances deliver Check Point s market leading security management software blades on a dedicated hardware platform specifically designed for mid-size and large enterprise security networks. Based on Check Point s Software Blade Architecture, the line of four Smart-1 appliances are first to deliver a unified management solution for network, IPS and endpoint security with unsurpassed extensibility. BENEFITS n Provides a comprehensive set of security management Software Blades in four turnkey security management appliances n Maximize efficiency with a single unified management console for network and endpoint security n Reduce costs and conserve resources with up to 12 TB of integrated storage capabilities n Ensure operational continuity for the most demanding environments n Simplify large scale security policy provisioning with multi-domain management (Provider-1) Smart-1 5 Smart-1 25b Smart-1 150: Security management for large service providers with more than 150 gateways and including up to 12 TB of integrated log storage Smart-1 50: Security management for enterprises and service providers with 50 to 150 gateways, including up to 4 TB of integrated log storage Smart-1 25b: Security management for enterprises with 25 to 50 gateways, including up to 2 TB of integrated log storage Smart-1 50 Smart-1 5: Security management for businesses with 5 to 25 gateways including up to 500 GB of integrated log storage Smart For more information: 8
11 Smart-1 SmartEvent Appliances Unified security event management OVERVIEW Smart-1 SmartEvent appliances deliver Check Point s SmartEvent Software Blade event management Software Blades on a dedicated hardware platform. Smart-1 SmartEvent appliances are specifically designed for mid-size and large enterprise security networks, providing comprehensive security event analysis in a turnkey, plug-and-play appliance. Based on Check Point s Software Blade Architecture, Smart-1 SmartEvent appliances are first to deliver a unified event management solution for network, IPS and endpoint security with unsurpassed extensibility. BENEFITS n Provides a comprehensive set of security management Software Blades in three turnkey security management appliances n Maximize efficiency with a single unified management console for network and endpoint security event management n Reduce costs and conserve resources with up to 4 TB of built-in storage capabilities n Ensure operational continuity for the most demanding environments Smart-1 SmartEvent 5 Smart-1 SmartEvent 50: Security Management for enterprises that need maximum flexibility, high performance and up to 2 years of log storage Smart-1 SmartEvent 25b: Security Management for enterprises that want maximum flexibility and up to 1 year of log storage Smart-1 SmartEvent 25b Smart-1 SmartEvent 5: Security Management for businesses that want an affordable solution that can scale as their business grows Smart-1 SmartEvent 50 For more information: 9
12 Check Point Integrated Appliance Solutions Integrated hardware and software from Check Point and IBM OVERVIEW Check Point Integrated Appliance Solutions (IAS) M-Series Appliances offer flexibility and choice in security appliances enabling integrated software and hardware bundles customized to their exact specifications. These customized platforms enable them to provision security services based on exact corporate needs. Organizations can choose from Check Point Software Blades such as firewall, IPSec VPN, and intrusion prevention, and additional blades including UTM functionality. They can also chose to deploy Check Point s virtualized security gateway, VPN-1 Power VSX, as well as Provider-1 for management of large deployments with separate security domains. Check Point integrates the selected software onto an IBM System x server or IBM BladeCenter to provide a comprehensive solution that includes direct technical support from Check Point. BENEFITS n Provides a software/hardware combination trusted by the largest organizations in the world n Reduces complexity by ensuring compatibility of the latest certified components and servers n Increases flexibility for security services provisioning by allowing customers to choose from multiple Check Point solutions n Delivers scalable performance and port density based on customer needs n Protects against emerging threats with service-based Check Point Software Blades including IPS, Antivirus, Anti-Malware, and URL Filtering M series Integrated Appliance Solutions are predefined models that can be customized to meet specific needs. The M2 model delivers UTM functionality. The M6 and M8 models both provide maximum security for high-performance environments with integrated firewall, VPN, and intrusion prevention. IAS M8 For more information: 10
13 Check Point Integrated Appliance Solutions Integrated hardware and software from Check Point and HP ES OVERVIEW Check Point Integrated Appliance Solutions (IAS) D-Series Appliances allow organizations to create a customized security solution integrated software and hardware built on a baseline set of standardized platforms for delivery of security services. This choice allows organizations to combine the proven security of Check Point on high performance-oriented platforms with a single point of contact for fulfillment and support of all issues. Organizations can customize their security solution using Check Point Software Blades such as firewall, IPSec VPN, and intrusion prevention, advanced networking and more. Organizations can also chose to deploy Check Point s virtualized security gateway, VPN-1 Power VSX, Provider-1 for management of large deployment with separate security domains, End Point Suite POINTSEC. BENEFITS n Provides a customized security software and hardware bundle on high performance-oriented platforms n Allows customers to extend security by simple Software Blades upgrade n Delivers high firewall performance of up to 20 Gbps based on customer needs n Increases flexibility for security services provisioning by allowing customers to choose from multiple Check Point solutions n Provides a single point of contact for hardware, software and support D-Series Integrated Appliance Solutions are predefined models that can be customized to meet specific needs. There are eleven (11) models to choose from to meet your security needs. The VSX and VSLS provides virtualized security solution and the UTM models deliver UTM functionality. D8 For more information: 11
14 Check Point Integrated Appliance Solutions Integrated hardware and software from Check Point and Fujitsu OVERVIEW Check Point Integrated Appliance Solutions (IAS) R-Series Appliances enable IT departments to design a total security solution for their specific needs. They combine proven Check Point security software solution with high performance hardware integrated and delivered by Check Point with its award-winning global support services. Organizations can benefit from the extensible Check Point Software Blades architecture by choosing the appropriate security solutions such as firewall, IPSec VPN, and intrusion prevention, and additional blades including UTM functionality. They can also chose to deploy Check Point s virtualized security gateway, VPN-1 Power VSX, as well as Multi-Domain Security Management for management of large deployments with separate security domains. A single point of contact for support is achieved by Check Point providing total support for the Integrated Appliance Solutions. Check Point s award-winning support service is available 24x7. BENEFITS n Comprehensive protection with best-in-class security software combined with high-performance hardware n Scalable performance with up to 26 ports and 20 Gbps of firewall throughput n Reduces complexity by ensuring compatibility of the latest certified components and servers n Protects against emerging threats with the extensible Check Point Software Blades including IPS, Antivirus, Anti-Malware, and URL Filtering n High availability and redundancy with virtualized security R series Integrated Appliance Solutions are predefined models that can be customized to meet specific needs. The R2 model delivers UTM functionality. The R6 and R8 models both provide maximum security for high-performance environments with integrated firewall, VPN, and intrusion prevention. IAS-R Appliances For more information: 12
15 Integrated Appliance Solution Bladed Hardware Integrated hardware and software from Check Point and Crossbeam OVERVIEW Check Point Integrated Appliance Solution (IAS) X-Series Bladed Hardware provides a customized, integrated security solution on a single, high-performance chassis. By integrating essential Check Point Security Gateway Software Blades with Crossbeam s X-Series carrier-grade chassis, IAS Bladed Hardware can effectively serve the needs of the most demanding, highest performance environments. Alternatively, the VPN-1 Power VSX provides a dedicated gateway for multi-layer, multi-domain virtualized security. Leveraging the Check Point Software Blade Architecture, IAS Bladed Hardware provides customized security solutions to meet specific customer needs including unified management of physical and virtual environments. BENEFITS n Provides a customized, integrated security solution on a single, high-performance chassis n Integrates extensible award-winning security software blades for a comprehensive security solution n Centralized management with Security Management and Multi-Domain Security Management options n Increases flexibility for security services with multiple security solutions consolidated on a single platform n Provides a single point of contact for hardware, software, and support With Check Point IAS Bladed Hardware, customers can choose among two hardware chassis and two security software bundles for a customized solution that best fits their individual needs. The Crossbeam X80-S hardware chassis provides scalability and performance, while the X60 chassis provides performance in a space-saving design. The Check Point Security Gateway SG1207 software bundle is designed for physical environments, while the VPN-1 Power VSX provides a virtualized security solution. Crossbeam X60 and X80-S For more information: 13
16 Appliance Specifications Power-1 Series Power Power Power Series Software Edition R65, R70, R71, R75 R65, R70, R71, R75 R70, R71, R75 R70, R71, R75 R70, R71, R75 10/100/1000 Ports 10/14 14/18 14/18 14/18 14/18 SecurityPower Up to 1222 Firewall Throughput 1 9 Gbps 16 Gbps 15 Gbps 20 Gbps 30 Gbps VPN Throughput Gbps 3.7 Gbps 3.7 Gbps 4 Gbps 4.5 Gbps Concurrent Sessions 1.2 million 1.2 million 1.2 million 1.2 million 1.2 million IPS Throughput Gbps 2 10 Gbps 2 10 Gbps 2 12 Gbps 2 15 Gbps 2 Licensed Users Unlimited Unlimited Unlimited Unlimited Unlimited VLANs UTM Out of the Box Optional Optional Optional Optional Optional Storage 160 GB 2 x 160 GB 2 x 250 GB 2 x 250 GB 2 x 250 GB Enclosure 2U 2U 2U 2U 2U Dimensions W x D x H (Standard) Dimensions W x D x H (Metric) 17 x 20 x 3.46 in. 17 x 20 x 3.46 in. 17 x 22.8 x 3.46 in. 17 x 22.8 x 3.46 in. 17 x 22.8 x 3.46 in. 431 x x 88mm 431 x x 88mm 431 x 580 x 88mm 431 x 580 x 88mm 431 x 580 x 88mm Weight 14.5kg (31.9 lbs) 16.5kg (36.3 lbs) 23.4kg (51.6 lbs) 23.4kg (51.6 lbs) 23.4kg (51.6 lbs) Operating Environment Temperature: 5 to 40 C, Humidity: 10% 85% non-condensing, Altitude: 2,500m Non-Operating Environment Power Input Dual, Hot-Swappable Power Supplies Temperature: -20 C to 70 C; Relative Humidity: 5% 95% non-condensing 100~240V, 50~60Hz Included Included Included Included Included Power Supply Spec (Max) 250W 400W 500W 500W 500W Power Consumption (Max) 164.1W 200.7W 253.2W 253.2W 253.2W Compliance UL 60950; FCC Part 15, Subpart B, Class A; EN 55024; EN 55022; VCCI V-3AS/NZS 3548:1995; CNS Class A (test passed; country approval pending); KN22KN Series, TTA; IC-950; ROHS 1 Performance data represents the maximum capabilities of the systems as measured under optimal testing conditions. Deployment and policy considerations may impact performance results. 2 Test based on real-world traffic blend using the default profile 3 Maximum of 256 VLANs per interface 14
17 Appliance Specifications IP Appliance Series IP282 IP297 IP397 IP567 IP697 IP1287 IP2457 Software Edition R65, R70, R71, R75 R65, R70, R71, R75 R65, R70, R71, R75 R65, R70, R71, R75 R65, R70, R71, R75 R65, R70, R71, R75 R65, R70, R71, R75 10/100/1000 Ports 6 6/8 4/8 4/16 4/16 4/28 4/32 10 GbE Ports SecurityPower Firewall Throughput 1.5Gbps 1.5 Gbps 3.0 Gbps 7 Gbps 7.2/11.7 Gbps /17.5 Gbps 2 11/30 Gbps 2 VPN Throughput 1.0 Gbps 1.0 Gbps 677 Mbps 1.7 Gbps 1.9/ 3.3 Gbps 2 1.9/8.3 Gbps 2 1.9/8.3 Gbps 2 Concurrent Sessions 900, ,000 1 million 1 million 1 million 1 million 1 million IPS Throughput 1.4 Gbps 1.4 Gbps Gbps Gbps 3 4 Gbps 3 7 Gbps 3 9 Gbps 3 VLANs ADP Module Optional Optional Optional VPN Acceleration Optional Optional Included Included Included Included Included Storage 80GB 80 GB 80 GB 80 GB 80 GB 80 GB 80 GB Disk-Based or Flash Disk Disk or Flash Disk or Flash Disk or Flash Disk or Flash Disk or Flash Disk or Flash Enclosure 1U/half rack 1U/half rack 1U 1U 1U 2U 2U Dimensions W x D x H (Standard) 8.52 x 18 x 1.71 in 8.52 x 18 x 1.71 in. 17 x 16 x 1.71 in x 22 x 1.71 in x 24 x 1.71 in x x 3.46 in x x 3.46 in. Dimensions W x D x H (Metric) Weight 216 x 457 x 44 mm 5.1kg (11.25 lbs) 216 x 457 x 44mm 5.1kg (11.25 lbs) 432 x 406 x 44mm 7.71kg (17.0 lbs) 438 x 559 x 44mm 11.84kg (26.1 lbs) 438 x 610 x 44mm 12.38kg (27.3 lbs) 438 x 613 x 88mm 19.6kg (43.2 lbs) 438 x 613 x 88mm 20.57kg (45.35 lbs) Operating Environment Temperature: 5 to 40 C 5 ; Humidity: 10% to 85% non-condensing; Altitude: 2,500m Non-Operating Environment Power Input Power Supply Spec (Max) Power Consumption (Max) Non-Operating Temperature: -20C to 70C; Relative Humidity: 5% to 95% 100/240V, 50/60Hz 133W 133W 150W 225W 250W 700W 700W W 165W DC Power Supply Optional Optional Compliance Safety: UL , First Edition: 2003, CAN/CSAC22.2, No 60950:2000, IEC : 2001, EN :2001+A11 with Japanese National Deviations; Emission Compliance: FCC Part 15, Subpart B, Class A, EN50024,EN55022A: 1998, CISPR 22 Class A: 1985, EN , EN ; Immunity: EN55024: Optional 2 Performance without ADP/with ADP 3 Preliminary results 4 Maximum of 256 VLANs per interface 5 IP395 can go to 50 C 15
18 Appliance Specifications UTM-1 Series Models Software Edition UTM-1 Edge UTM-1 Edge W, UTM-1 Edge W ADSL Embedded NGX UTM-1 Edge N-Series UTM-1 Edge N UTM-1 Edge NW UTM-1 Edge N/ NW ADSL Embedded NGX UTM UTM UTM UTM UTM UTM R65, R70, R71, R75 UTM UTM UTM R65, R70, R71, R75 UTM UTM R65, R70, R71, R75 UTM UTM UTM R65, R70, R71, R75 UTM UTM UTM R65, R70, R71, R75 UTM UTM UTM /100 Ports /100/1000 Ports R65, R70, R71, R SecurityPower Firewall Throughput VPN Throughput Concurrent Sessions 190 Mbps 1.0 Gbps 1.5 Gbps 1.5 Gbps 2.5 Gbps 3 Gbps 3.5 Gbps 4.5 Gbps 35 Mbps 200 Mbps 120 Mbps 120 Mbps 300 Mbps 350 Mbps 450 Mbps 1100 Mbps 8,000 60, , , , ,000 1,100,000 1,100,000 IPS Throughput 35 Mbps 180 Mbps 1 Gbps 1 Gbps 1.7 Gbps 2.2 Gbps 2.7 Gbps 4 Gbps Licensed Users 8/16 32/U Unlimited Unlimited Unlimited Unlimited Unlimited Unlimited VLANs UTM Out of the Box Multisite Management Yes Yes Yes Yes Yes Yes Yes Yes No No Standalone Yes Yes Yes Yes Yes Storage GB 160 GB 160 GB 160 GB 160 GB 160 GB Enclosure Desktop Desktop Desktop 1U 1U 1U 1U 1U Dimensions W x D x H (Standard) Dimensions W x D x H (Metric) 1.2 x 8 x 4.8 in. 30 x 203 x 122mm 1.2 x 8 x 4.8 in. 30 x 203 x 122mm Weight 0.7kg (1.6lbs) 0.7kg (1.6lbs) Operating Environment Non-Operating Environment Power Input Power Supply Spec (Max) Power Consumption (Max) Compliance 10.6 x 5.7 x 1.6 in. 270 x 145 x 40mm 1.6kg (3.52lbs) 16.8 x 10 x 1.73 in. 429 x 255 x 44mm 16.8 x 10 x 1.73 in. 429 x 255 x 44mm 16.8 x 10 x 1.73 in. 429 x 255 x 44mm 3.7kg (8.1lbs) 3.7kg (8.1lbs) 3.7kg (8.1lbs) 17.4 x 15 x 1.73 in. 443 x 381 x 44mm 6.5kg (14.3lbs) 17.4 x 15 x 1.73 in. 443 x 381 x 44mm 6.5kg (14.3lbs) Temperature: 5 C to 40 C, Humidity: 10% 85% non-condensing, Altitude: 2,500m 2 Temperature: 5 C to 40 C, Humidity: 10% 85% non-condensing, Altitude: 2,500m2 Temperature: -20 C to 70 C Temperature: -20 C to 70 C, Relative Humidity: 5% 95% non-condensing 100/240V, 50/60Hz 18W 18W 60W 65W 65W 65W 250W 250W W 26.2W 41.1W 40.1W 63.1W 77.5W UL 60950; FCC Part 15, Subpart B, Class A; EN 55024; EN 55022; VCCI V-3; AS/NZS 3548:1995; CNS Class A (test passed; country approval pending); KN22, KN Series, TTA; IC-950; ROHS 1 Maximum of 256 VLANs per interface 2 UTM-1 Edge operating environment: Temperature: 0º to 40º C, Humidity: 10% 90% non-condensing, Altitude: 4500m (15,000ft ) 16
19 Appliance Specifications Series 80 Series 80 Software Edition R71 10/100/1000 Ports 10 Firewall Throughput VPN Throughput 1.5 Gbps 220 Mbps Concurrent Sessions 150,000 IPS Throughput 720 Mbps Licensed Users Unlimited VLANs 1024 UTM Out of the Box Multisite Management Enclosure Dimensions W x D x H (Standard) Dimensions W x D x H (Metric) Weight Operating Environment Power Input Power Supply Spec (Max) Yes No Desktop 8.75 x 1.75 x 6 in. 22 x 4.4 x cm 2.4 lb (1.085kg) Temperature: 0 C to 40 C, Humidity: 5% 95% non-condensing 100/240V, 50/60Hz 12V/2A DC 24W Power Consumption (Max) 16.68W Compliance EMC: EN _2007-ITE; FCC: FCCP15B+ICES-003-ITE; Safety: UL/c-UL _2nd_2007(US+CA); IEC 60950_1_2nd_2005-CB 17
20 Appliance Specifications VSX-1 Series VSX Single Unit VSX Single Unit VSX VSLS VSX /070/080 Single Unit VSX /270/280 VSLS Software Edition VSX R67 VSX R67 VSX R67 VSX R67 VSX R67 10/100/1000 Ports Optional Interfaces - LOM, 2x4 1 GbE Fiber, 2x4 1GbE Copper, 2x2 10 GbE LOM, 2x2x4 1 GbE Fiber, 2x2x4 1GbE Copper, 2x2x2 10 GbE LOM, 2x4 1 GbE Fiber, 2x4 1GbE Copper, 2x2 10 GbE LOM, 2x2x4 1 GbE Fiber, 2x2x4 1GbE Copper, 2x2x2 10 GbE Firewall Throughput 4.5 Gbps 14 Gpbs 28 Gbps 15/20/25 Gbps 30/40/50 Gbps VPN Throughput 1.0 Gbps 3.6 Gbps 7.2 Gbps 3.7/4.0/4.5 Gbps 7.4/8.0/9.0 Gbps Security Acceleration Yes Yes Yes Yes Yes Concurrent Sessions 1 million 1.1 million 1.6 million 1.2 million 1.6 million Licensed Users Unlimited Unlimited Unlimited Unlimited Unlimited VLANs Virtual Systems (Included/Capacity) 5/10 10/150 10/150 10/250 10/250 UTM Out of the Box Optional Optional Optional Optional Optional Multisite Management Optional 2 Optional 2 Optional 2 Optional 2 Optional 2 Storage 160 GB 2 x 160 GB 4 x 160 GB 2 x 250 GB 4 x 250 GB Enclosure 1U 2U 4U 2U 4U Dimensions W x D x H (Standard) 17.4 x 15 x 1.73 in. 17 x 20 x 3.46 in. 17 x 20 x 7 in. 17 x 20 x 3.46 in. 17 x 20 x 7 in. Dimensions W x D x H (Metric) 443 x 381 x 44mm 431 x x 88mm 431 x x 176mm 431 x x 88mm 431 x x 176mm Weight 6.5kg (14.3 lbs) 16.5kg (36.3 lbs) 33kg (72.6 lbs) 23.4kg (51.6 lbs) 46.8kg (103.2 lbs) Dual, Hot-Swappable Power Supplies Power Input No Yes Yes Yes Yes 100/240V, 50/60Hz Power Supply Spec (Max) 250W 400W 800W 500W 1000W Power Consumption (Max) 78W 201W 400W 253W 506W Operating Environment Temperature: 5 to 40 C, Humidity: 10% 85% non-condensing, Altitude: 2,500m Non-Operating Environment Temperature: -20 C to 70 C, Relative Humidity: 5% 95% non-condensing Compliance UL 60950; FCC Part 15, Subpart B, Class A; EN 55024; EN 55022; VCCI V-3AS/NZS 3548:1995; CNS Class A (test passed; country approval pending); KN22KN Series, TTA; IC-950; ROHS UL , First Edition: 2003, CAN/ CSAC22.2, No 60950:2000, IEC : 2001, EN :2001+A11 with Japanese National Deviations; FCC Part 15, Subpart B, Class A, EN50024,EN55022A:1998, CISPR 22 Class A, 1985, EN , EN ; EN55024: With Acceleration Card, available in Management Server resides on separate server 18
21 Appliance Specifications DLP-1 Series DLP DLP Software Edition R71, R75 R71, R75 Number of Users Messages/Hour 70, ,000 Throughput 700 Mbps 2.5 Gbps Built-in Interfaces 6 Copper 1 GbE 10 Copper 1 GbE Optional Interfaces Built-in 4-Port Copper Bypass Card LOM, 2x4 1 GbE Fiber, 2x4 1GbE Copper, 2x2 10 GbE, Modular 4-Port Copper Bypass Card Storage Size 500GB 2x2TB (Mirrored RAID 1) Enclosure 1U 2U Dimensions W x D x H (Standard) 17.4 x 15 x 1.73 in. 17 x 20 x 3.46 in. Dimensions W x D x H (Metric) 443 x 381 x 44mm 431 x x 88mm Weight 6.5kg (14.3 lbs.) 16.5kg (36.3 lbs.) Dual, Hot-Swappable Power Supplies No Yes Power Input 100/240V, 50/60Hz Power Supply Spec (Max) 250W 400W Power Consumption (Max) 77.5W 200.7W Operating Environment Temperature: 5 to 40 C; Humidity: 10% to 85% non-condensing; Altitude: 2,500m Compliance UL 60950; FCC Part 15, Subpart B, Class A; EN 55024; EN 55022; VCCI V-3AS/NZS 3548:1995; CNS Class A (test passed; country approval pending); KN22KN Series, TTA; IC-950; ROHS 1 With Acceleration Card, available in Management Server resides on separate server 19
22 Appliance Specifications Smart-1 Series Smart-1 5 Smart-1 25b Smart-1 50 Smart Software Edition R70, R71, R75 R70, R71, R75 R70, R71, R75 R70, R71, R75 Managed Gateways 5 up to up to up to up to unlimited Managed Domains up to 3/5/10 3 up to 5/10/50 Management HA Included Included Included Included Logs/sec 7,500 14,000 30,000 30,000 Built-in Interfaces 4 Copper GbE 4 Copper GbE 4 Copper GbE 4 Copper GbE LCD Display Yes Yes Yes Yes Storage 1 x 0.5 TB 2 x 1 TB 4 x 1 TB 4 x 1 TB, up to 12 TB Storage Type - RAID 1 RAID 10 RAID 10 Fiber Channel SAN Card - - Optional Optional Out-of-Band Management - Integrated Integrated Integrated Enclosure 1U 1U 2U 3U Dimensions W x D x H (Standard) Dimensions W x D x H (Metric) 17 x 10.9 x 1.75 in. 17 x x 1.75 in x 17.4 x 3.5 in x 17.4 x 5.2 in. 431 x 277 x 44mm 431 x 550 x 44.4mm 580 x 442 x 88mm 632 x 442 x 131mm Weight 6kg (13.2 lbs.) 13kg (28.7 lbs.) 23.5kg (51.8 lbs.) 29.5kg (65 lbs.) Power Supply Power Input 100/240V, 50/60Hz 100/240V, 50/60Hz 90/264V, 47/63Hz 90/264V, 47/63Hz DC Option - - Yes - Power Supply Spec (Max) 150W 2 x 275W 2 x 600W 3 x 930W Power Consumption (Max) 70.5W 171W 505.3W 399.6W Operating Environment Compliance Temperature: Ambient operating 0 to 40 C; Humidity: 5% to 95% non-condensing (RH) CE, FCC Class A, RoHS 20
23 Appliance Specifications Smart-1 SmartEvent Series Smart-1 SmartEvent 5 Smart-1 SmartEvent 25b Smart-1 SmartEvent 50 Software Edition R70.2, R71, R75 R70.2, R71, R75 R70.2, R71, R75 Managed Gateways 5 up to up to up to 150 Logging Capacity (Recommended) 2GB per day 10GB per day 25GB per day Storage 1 x 0.5 TB 2 x 1 TB 4 x 1 TB Storage Type - RAID 1 RAID 10 Built-in Interfaces 4 Copper GbE 4 Copper GbE 4 Copper GbE Fibre Channel SAN card - - optional Out-of-band management - Integrated Integrated LCD Display Yes Yes Yes Enclosure 1U 1U 2U Dimensions W x D x H (Standard) 17 x 10.9 x 1.75 in. 17 x x 1.75 in x 17.4 x 3.5 in. Dimensions W x D x H (Metric) 431 x 277 x 44mm 431 x 550 x 44.4mm 580 x 442 x 88mm Weight 6kg (13.2 lbs.) 13kg (28.7 lbs.) 23.5kg (51.8 lbs.) Power Supply Power Input 100/240V, 50/60Hz 100/240V, 50/60Hz 90/264V, 47/63Hz DC Option - - Yes Power Supply Spec (Max) 150W 2 x 275W 2 x 600W Power Consumption (Avg) 61.7W 171W 350.8W Operating Environment Compliance Temperature: Ambient operating 0 to 40 C; Humidity: 5% to 95% non-condensing (RH) CE, FCC, Class A, RoHS 21
24 Appliance Specifications Integrated Hardware and Software from Check Point and IBM IAS 1 M2* IAS 1 M6* IAS 1 M8* Software Edition R71, R75 R71, R75 R71, R75 10/100/1000 Ports 4/10 10/10 14/18 Firewall Throughput 2 7 Gbps 16 Gbps 20 Gbps VPN Throughput Gbps 3 Gbps 4 Gbps Concurrent Sessions 1.2 million 1.2 million 1.2 million IPS Throughput 2 4 Gbps Gbps Gbps 3 Licensed Users Unlimited Unlimited Unlimited VLANs UTM Out of the Box Optional Optional Optional Security Acceleration Yes Yes Yes Integrated Multigateway Management Optional Optional Optional Storage 2 x 146 GB 2 x 146 GB 2 x 146 GB Enclosure 1U 1U 2U Dimensions W x D x H (Standard) 17.3 x 27.5 x 1.75 in x 27.5 x 1.75 in x 27.5 x 3.36 in. Dimensions W x D x H (Metric) 440 x 698 x 44mm 443 x 698 x 44mm 444 x 698 x 84.8mm Weight 16.1kg (35.5 lbs.) 16.1kg (35.5 lbs.) 26.1kg (57.5 lbs.) Operating Environment Temperature: 5 to 40 C; Humidity: 10% to 85% non-condensing; Altitude: 2,500m Power Input 100/240V, 50/60Hz 4 Power Supply Spec (Max) 650W 650W 1300W Power Consumption (Max) 180W 212W 342W * Virtualized Solutions with NGX R67 VSX are also available on this appliance 1 IAS = Integrated Appliance Solutions 2 Performance data represents the maximum capabilities of the systems as measured under optimal testing conditions. Deployment and policy considerations may impact performance results. 3 Test based on real-world traffic blend using the default profile 4 Redundant power supply 5 Maximum of 256 VLANs per interface 22
25 Appliance Specifications Integrated Hardware and Software from Check Point and HP D1 Gateway* D1 Gateway Pair* D2 Gateway* D6 Gateway* D8 Gateway* Software Edition R71, R75 R71, R75 R71, R75 R71, R75 R71, R75 Virtual Firewalls - 10/100/1000 Ports 6/6 6/6 6/10 6/10 8/18 10 Gb Ports - Firewall Throughput 2 Gbps 2 Gbps 7 Gbps 16 Gbps 20 Gbps VPN Throughput 1.2 Gbps 1.2 Gbps 2.4 Gbps 3 Gbps 4 Gbps Concurrent Sessions 1.2 million 1.2 million 1.2 million 1.2 million 1.2 million IPS Throughput - VLANs Lights Out Management Included Included Included Included Included Storage 2 x 160 GB 2 x 160 GB 2 x 146 GB (8 Max) 2 x 146 GB (8 Max) 2 x 146 GB (12 Max) Memory 1 GB 1 GB 2 GB 4 GB 8 GB Dimensions W x D x H (Standard) Dimensions W x D x H (Metric) 1.69 x x in x x in x x in x x in x x in. 432 x x 700mm 432 x x 700mm 432 x x 692.2mm 432 x x 692.2mm 859 x x 743mm Weight 14.3 kg (31.49 lbs.) 14.3 kg (31.49 lbs.) kg (39.5 lbs.) kg (39.5 lbs.) - Power Input 90/132V, 180/264V, 47/63Hz 90/132V, 180/264V, 47/63Hz 100/240V, 50-60Hz 100/240V, 50/60Hz 100/240V, 50/60Hz Power Supply Spec (Max) Power Consumption (Max) Operating Environment 430W 430W 460W 460W 460W 75W 75W 170W 181W 290W Temperature: 10 to 35 C (50 to 95 F); Humidity: 10% to 90% non-condensing; Attitude: 3,050m (10,000 ft.) Compliance CISPR 22; EN55022; EN55024; FCC CFR 47, Pt 15; ICES-003; CNS13438; GB9254; EN ; EN ; EN ; IEC CISPR 22; EN55022; EN55024; FCC CFR 47, Pt 15; ICES-003; CNS13438; GB9254; K22; K24; EN ; EN ; EN ; IEC * Virtualized Solutions with NGX R67 VSX are also available on this appliance 1 Maximum of 256 VLANs per interface continues on next page 23
26 Appliance Specifications Integrated hardware and software from Check Point and Fujitsu IAS 1 R2* IAS 1 R6* IAS 1 R8* Software Edition R71, R75 R71, R75 R71, R75 10/100/1000 Ports 4/10 10/10 14/26 Firewall Throughput 2 7 Gbps 16 Gbps 20 Gbps VPN Throughput Gbps 3 Gbps 4 Gbps Concurrent Sessions 1.2 million 1.2 million 1.2 million IPS Throughput 2 4 Gbps Gbps Gbps 3 Licensed Users Unlimited Unlimited Unlimited VLANs UTM Out of the Box Optional Optional Optional Security Acceleration Yes Yes Yes Integrated Multisite Management Optional Optional Optional Storage 2 x 146 GB 2 x 146 GB 2 x 146 GB Enclosure 1U 1U 2U Dimensions W x D x H (Standard) 17 x 30 x 1.70 in. 17 x 30 x 1.70 in x 30.3 x 3.38 in. Dimensions W x D x H (Metric) 431 x 762 x 43 mm 431 x 762 x 43 mm 445 x 770 x 86 mm Weight (Max) 17 kg (37.5 lbs) kg (39.5 lbs) 25 kg (55.1 lbs) Operating Environment Temperature: 5 to 40 C; Humidity: 10% to 85% non-condensing; Altitude: 2,500m Power Input 100/240V, 50/60Hz 5 Dual, Hot-Swappable Power Supplies Optional Optional Included Power Supply Spec (Max) 450W 450W 800W Power Consumption (Max) 178W (Min) 178W (Min) 504W Compliance GS; CE Class A; CSAc/us; ULc/us; ICES-003 Class A; FCC Class A; CB; RoHS; WEE; VCCI Class A + JIS ; CNS class A GS; CE Class A; CSAc/us; FCC Class A; CB; RoHS; WEEE; VCCI; CCC; C-Tick * Virtualized Solutions with NGX R67 VSX are also available on this appliance 1 IAS = Integrated Appliance Solutions 2 Performance data represents the maximum capabilities of the systems as measured under optimal testing conditions. Deployment and policy considerations may impact performance results. 3 Test based on real-world traffic blend using the default profile 4 Maximum of 256 VLANs per interface 24
27 Appliance Specifications Integrated hardware and software from Check Point and Crossbeam IAS X60* IAS X80-S* Throughput Up to 16Gbps per APM Up to 75Gbps per chassis Up to 16 Gbps per APM Up to 140 Gbps per chassis Form Factor/Size W x D x H 13.5 x 17.5 x 19 in. 29 x 17.5 x 17.5 in. Interfaces/Connectivity Up to 32 x 1Gb SFP/10Gb SFP+ (16 per NPM) Per Network UP to 64 x 1Gb SFP/10Gb SFP+ (16 per NPM) Processor System Memory Disk Size 4 Core, 8Core or 12 Core Application Processor Module (APM) Up to 24GB per Application Processor Module (APM) Up to 2 x 450GB HDD with RAID 1 per Application Processor Module (APM) Power Module Support VAC, 2,700W Rated Maximum Up to 2 NPM-x, up to 5 APM-x, up to 2 CPM-x; Supports 7 modules total X80-S AC: VAC, 5,100 Rated Maximum X80-S DC: 48V DC 100A Up to 4 NPM-x, up to 10-x APM, up to 2 CPM-x; Supports 14 modules total Management Certification Status Indicators Regulatory Compliance for Chassis Green IT Compliancy Other Check Point Software X-Series Management System (XMS), Greenlight Element Manager (GEM), Command Line Interface (CLI) with Automated Workflow System (AWS), SNMP V1,2,3 and NetFlow v5, v9, v10 support Network Equipment Building System (NEBS) compliant, under evaluation for Common Criteria EAL4+ Power Supply and Module Active/Failed Status LED, Port link (NPM, CPM), Minor/Major/Critical Alarm LEDs RoHS; UL 60950, IEC 950, FCC 47 CFR Part 15 Class A, EN : EN 55024, VCCI V-3 : AS/NZS 3548 : 1995 : CNS Class A High efficiency power system up to 91 percent, WEEE Directive, ISO 14001, RoHS Single or Dual System High-Availability Security Gateway R70, R70 HCC Release, R70 IPv6, R71 and R75.20, VPN-1 Power VSX R65, R67 & R68, Firewall-1 GX 4.0, 5.0 Operating System XOS 7.2.1, , 8.0.1, 8.1.0, 8.5.0, 9.0, 9.5 & 9.6 Operating Environment Temperature: 0 to 40 C (32 to 104 F); Humidity: 10% to 90% non-condensing; Altitude: 3,048m (10,000 ft.) * Virtualized Solutions with NGX R67 VSX are also available on this appliance 25
28 Contact Check Point now By phone in the US: option 5 or CONTACT CHECK POINT Worldwide Headquarters 5 Ha Solelim Street, Tel Aviv 67897, Israel Tel: Fax: [email protected] U.S. Headquarters 800 Bridge Parkway, Redwood City, CA Tel: ; Fax: Check Point Software Technologies Ltd. All rights reserved. Check Point, Abra, AlertAdvisor, Application Intelligence, Check Point DLP, Check Point Endpoint Security, Check Point Endpoint Security On Demand, the Check Point logo, Check Point Full Disk Encryption, Check Point Horizon Manager, Check Point Media Encryption, Check Point NAC, Check Point Network Voyager, Check Point OneCheck, Check Point R70, Check Point Security Gateway, Check Point Update Service, Check Point WebCheck, ClusterXL, Confidence Indexing, ConnectControl, Connectra, Connectra Accelerator Card, Cooperative Enforcement, Cooperative Security Alliance, CoreXL, DefenseNet, DLP-1, DynamicID, Endpoint Connect VPN Client, Eventia, Eventia Analyzer, Eventia Reporter, Eventia Suite, FireWall-1, FireWall-1 GX, FireWall-1 SecureServer, FloodGate-1, Hacker ID, Hybrid Detection Engine, IMsecure, INSPECT, INSPECT XL, Integrity, Integrity Clientless Security, Integrity SecureClient, InterSpect, IP Appliances, IPS-1, IPS Software Blade, IPSO, Software Blade, IQ Engine, MailSafe, the More, Better, Simpler Security logo, MultiSpect, NG, NGX, Open Security Extension, OPSEC, OSFirewall, Pointsec, Pointsec Mobile, Pointsec PC, Pointsec Protector, Policy Lifecycle Management,Power-1, Provider-1, PureAdvantage, PURE Security, the puresecurity logo, Safe@Home, Safe@Office, Secure Virtual Workspace, SecureClient, SecureClient Mobile, SecureKnowledge, SecurePlatform, SecurePlatform Pro, SecuRemote, SecureServer, SecureUpdate, SecureXL, SecureXL Turbocard, Security Management Portal, SiteManager-1, Smart-1, SmartCenter, SmartCenter Power, SmartCenter Pro, SmartCenter UTM, SmartConsole, SmartDashboard, SmartDefense, SmartDefense Advisor, SmartEvent, Smarter Security, SmartLSM, SmartMap, SmartPortal, SmartProvisioning, SmartReporter, SmartUpdate, SmartView, SmartView Monitor, SmartView Reporter, SmartView Status, SmartViewTracker, SmartWorkflow, SMP, SMP On-Demand, SofaWare, Software Blade Architecture, the softwareblades logo, SSL Network Extender, Stateful Clustering, Total Security, the totalsecurity logo, TrueVector, UserCheck, UTM-1, UTM-1 Edge, UTM-1 Edge Industrial, UTM-1 Total Security, VPN-1, VPN-1 Edge, VPN-1 MASS, VPN-1 Power, VPN-1 Power Multi-core, VPN-1 Power VSX, VPN-1 Pro, VPN-1 SecureClient, VPN-1 SecuRemote, VPN-1 SecureServer, VPN-1 UTM, VPN-1 UTM Edge, VPN-1 VE, VPN-1 VSX, VSX-1, Web Intelligence, ZoneAlarm, ZoneAlarm Antivirus, ZoneAlarm DataLock, ZoneAlarm Extreme Security, ZoneAlarm ForceField, ZoneAlarm Free Firewall, ZoneAlarm Pro, ZoneAlarm Internet Security Suite, ZoneAlarm Security Toolbar, ZoneAlarm Secure Wireless Router, Zone Labs, and the Zone Labs logo are trademarks or registered trademarks of Check Point Software Technologies Ltd. or its affiliates. ZoneAlarm is a Check Point Software Technologies, Inc. Company. All other product names mentioned herein are trademarks or registered trademarks of their respective owners. The products described in this document are protected by U.S. Patent No. 5,606,668, 5,835,726, 5,987,611, 6,496,935, 6,873,988, 6,850,943, 7,165,076, 7,540,013 and 7,725,737 and may be protected by other U.S. Patents, foreign patents, or pending applications. December 12, Check Point Software Technologies Ltd. All rights reserved. Classification: [Protected] - All rights reserved.
CHECK POINT TOTAL SECURITY APPLIANCES. Flexible Deployment. Centralized Management.
 CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
CHECK POINT. Software Blade Architecture
 CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
CHECK POINT. Software Blade Architecture. Secure. Flexible. Simple.
 CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
The Evolution of IPS. Intrusion Prevention (Protection) Systems aren't what they used to be
 The Evolution of IPS Intrusion Prevention (Protection) Systems aren't what they used to be The Evolution of IPS Contents Background 3 Past Case for Standalone IPS 3 Organizational Control 3 Best-of-Breed
The Evolution of IPS Intrusion Prevention (Protection) Systems aren't what they used to be The Evolution of IPS Contents Background 3 Past Case for Standalone IPS 3 Organizational Control 3 Best-of-Breed
How to Implement an Integrated GRC Architecture
 How to Implement an Integrated GRC Architecture Companies that select individual solutions for each regulatory challenge they face will spend 10 times more on IT portion of compliance projects than companies
How to Implement an Integrated GRC Architecture Companies that select individual solutions for each regulatory challenge they face will spend 10 times more on IT portion of compliance projects than companies
Appliance Comparison Chart
 202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
Appliance Comparison Chart
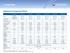 Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Check Point Corporate Logo Usage Guidelines
 Check Point Corporate Logo Usage Guidelines 1. The Check Point Logo The Check Point logo is the most visible and recognizable symbol of our brand. It should appear on every piece of communication from
Check Point Corporate Logo Usage Guidelines 1. The Check Point Logo The Check Point logo is the most visible and recognizable symbol of our brand. It should appear on every piece of communication from
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
Check Point. Software Blade Architecture
 Check Point Software Blade Architecture TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity
Check Point Software Blade Architecture TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity
Check Point Whitepaper. Enterprise IPv6 Transition Technical Whitepaper
 Check Point Whitepaper Enterprise IPv6 Transition Technical Whitepaper Contents Introduction 3 Transition Mechanisms 3 Dual Stack 4 Tunneling 4 Translation 7 Recommendations 8 Transition Security Considerations
Check Point Whitepaper Enterprise IPv6 Transition Technical Whitepaper Contents Introduction 3 Transition Mechanisms 3 Dual Stack 4 Tunneling 4 Translation 7 Recommendations 8 Transition Security Considerations
Endpoint Security Considerations for Achieving PCI Compliance
 Endpoint Security Considerations for Achieving PCI Compliance Contents PCI Requirements and Endpoint Security 3 Overview of the PCI Data Security Standard 3 Developing a PCI Compliance Plan 4 Endpoint
Endpoint Security Considerations for Achieving PCI Compliance Contents PCI Requirements and Endpoint Security 3 Overview of the PCI Data Security Standard 3 Developing a PCI Compliance Plan 4 Endpoint
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Appliance Comparison Chart
 Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Security Gateway Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark - version R77 and later) Security 2 2 230 405 673 Firewall (Gbps).4.4 2.2 3.4
Leverage IPS to Make Patch Tuesday Just Another Day
 Leverage IPS to Make Patch Tuesday Just Another Day Contents Introduction 3 Evolution of a Practice 3 Weaknesses of the Model 4 Lack of timeliness 4 Inherent predictability 4 Painful disruptions 5 A Better
Leverage IPS to Make Patch Tuesday Just Another Day Contents Introduction 3 Evolution of a Practice 3 Weaknesses of the Model 4 Lack of timeliness 4 Inherent predictability 4 Painful disruptions 5 A Better
The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels
 The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels The Power-1 Performance Architecture Contents Introduction 3 A delicate balance: Performance
The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels The Power-1 Performance Architecture Contents Introduction 3 A delicate balance: Performance
How to Get NAC Up-and-Running in One Hour. For Check Point Firewall or Endpoint Security Administrators
 How to Get NAC Up-and-Running in One Hour For Check Point Firewall or Endpoint Security Administrators Contents Introduction 3 Defining an Organization s Requirements for NAC 3 Two Paths to NAC Port vs.
How to Get NAC Up-and-Running in One Hour For Check Point Firewall or Endpoint Security Administrators Contents Introduction 3 Defining an Organization s Requirements for NAC 3 Two Paths to NAC Port vs.
Check Point Whitepaper. Check Point Abra: A Virtual Secure Workspace Technical Whitepaper
 Check Point Whitepaper Check Point Abra: A Virtual Secure Workspace Technical Whitepaper Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile Workforce 3 Abra Provides the Solution 4
Check Point Whitepaper Check Point Abra: A Virtual Secure Workspace Technical Whitepaper Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile Workforce 3 Abra Provides the Solution 4
Check Point Appliances. 2012 Models
 Check Point Appliances 2012 Models Table of Contents Introduction 3 Check Point GAiA the Next-Gen Security OS 4 About SecurityPower 5 2200 Appliance 6 4000 Appliances 7 12000 Appliances 8 21400 Appliance
Check Point Appliances 2012 Models Table of Contents Introduction 3 Check Point GAiA the Next-Gen Security OS 4 About SecurityPower 5 2200 Appliance 6 4000 Appliances 7 12000 Appliances 8 21400 Appliance
Solving the Performance Hurdle for Integrated IPS
 Solving the Performance Hurdle for Integrated IPS New Check Point Technologies Enable a Full-Function, Integrated Intrusion Prevention System without Compromise to Performance or Security Solving the Performance
Solving the Performance Hurdle for Integrated IPS New Check Point Technologies Enable a Full-Function, Integrated Intrusion Prevention System without Compromise to Performance or Security Solving the Performance
Check Point taps the power of virtualization to simplify security for private clouds
 Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
Unified Threat Management from Check Point. The security you need. The simplicity you want
 Unified Threat Management from Check Point The security you need. The simplicity you want Unified Threat Management from Check Point Contents Introduction 3 Complexity of the security problem 3 Comprehensive
Unified Threat Management from Check Point The security you need. The simplicity you want Unified Threat Management from Check Point Contents Introduction 3 Complexity of the security problem 3 Comprehensive
USB Drives: Friend or Foe? New User Trends and Exploits in USB Requires Security Controls to Protect Endpoints and the Networked Enterprise
 New User Trends and Exploits in USB Requires Security Controls to Protect Endpoints and the Networked Enterprise Contents Executive Summary 3 Exploiting Risks of USB Drives and Portable Applications 3
New User Trends and Exploits in USB Requires Security Controls to Protect Endpoints and the Networked Enterprise Contents Executive Summary 3 Exploiting Risks of USB Drives and Portable Applications 3
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
LICENSE GUIDE. Software Blades products. Number of Strings. SKU Prefix Name Description Additive
 LICENSE GUIDE Software Blades products SKU Prefix Name Description Additive CPAP-SG5075 CPAP-SG9075 CPAP-SG11065 CPAP-SG11075 CPAP-SG11085 CPAP-IP2455 CPAP-IP1285 CPAP-IP695 CPAP-IP565 CPAP-IP395 CPAP-IP295
LICENSE GUIDE Software Blades products SKU Prefix Name Description Additive CPAP-SG5075 CPAP-SG9075 CPAP-SG11065 CPAP-SG11075 CPAP-SG11085 CPAP-IP2455 CPAP-IP1285 CPAP-IP695 CPAP-IP565 CPAP-IP395 CPAP-IP295
Benefits. Product Overview. There is nothing more important than our customers. DATASHEET
 DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
VIRTUALIZED SECURITY: THE NEXT GENERATION OF CONSOLIDATION
 WHITEPAPER A consolidated security infrastructure is more than just an idea; in today s world of increasingly diversified threats and associated rising costs, it s imperative that organizations adopt a
WHITEPAPER A consolidated security infrastructure is more than just an idea; in today s world of increasingly diversified threats and associated rising costs, it s imperative that organizations adopt a
Scalable. Reliable. Flexible. High Performance Architecture. Fault Tolerant System Design. Expansion Options for Unique Business Needs
 Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Check Point Endpoint Security. Single agent for endpoint security delivering total protection and simplified management
 Single agent for endpoint security delivering total protection and simplified management Contents Executive summary 3 Meeting the challenge of securing endpoints 4 A new strategy: Unifying endpoint security
Single agent for endpoint security delivering total protection and simplified management Contents Executive summary 3 Meeting the challenge of securing endpoints 4 A new strategy: Unifying endpoint security
Delivers fast, accurate data about security threats:
 DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
Benefits. Product Overview. There is nothing more important than our customers. DATASHEET
 DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
Scalable. Reliable. Flexible. High Performance Architecture. Fault Tolerant System Design. Expansion Options for Unique Business Needs
 Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Protecting the Data That Drives Business SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding network environments.
Check Point 2200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
Datasheet: Check Point 2200 Appliance 2200 Branch & Small Office Solution Enterprise security in a desktop package Check Point 2200 Appliance Today the Internet gateway is more than a firewall. It is a
Ixia Director TM. Powerful, All-in-One Smart Filtering with Ultra-High Port Density. Efficient Monitoring Access DATA SHEET
 Ixia Director TM Powerful, All-in-One Smart Filtering with Ultra-High Port Density The Ixia Director TM is a smart filtering appliance that directs traffic of interest to your monitoring tools. Now you
Ixia Director TM Powerful, All-in-One Smart Filtering with Ultra-High Port Density The Ixia Director TM is a smart filtering appliance that directs traffic of interest to your monitoring tools. Now you
Security Information & Event Manager (SIEM)
 DATA SHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Benefits Enables NOC and SOC staff to
DATA SHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Benefits Enables NOC and SOC staff to
Security Information & Event Manager (SIEM)
 DATA SHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Benefits Enables NOC and SOC staff to
DATA SHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Benefits Enables NOC and SOC staff to
Best Practices for Deploying Intrusion Prevention Systems. A better approach to securing networks
 Best Practices for Deploying Intrusion Prevention Systems A better approach to securing networks A better approach to securing networks Contents Introduction 3 Understanding deployment needs 3 Selecting
Best Practices for Deploying Intrusion Prevention Systems A better approach to securing networks A better approach to securing networks Contents Introduction 3 Understanding deployment needs 3 Selecting
Cisco ASA 5500 Series IPS Solution
 Cisco ASA 5500 Series IPS Solution Product Overview Network threats and security compliance mandates continue to increase in number. The Cisco ASA 5500 Series Intrusion Prevention System (IPS) solution
Cisco ASA 5500 Series IPS Solution Product Overview Network threats and security compliance mandates continue to increase in number. The Cisco ASA 5500 Series Intrusion Prevention System (IPS) solution
Check Point Appliances
 Check Point Appliances Table of Contents Introduction 3 Check Point GAiA - a Unified Secure Operating System 4 About SecurityPower 5 Next Generation Security Solutions 6 600 Appliances 7 1100 Appliances
Check Point Appliances Table of Contents Introduction 3 Check Point GAiA - a Unified Secure Operating System 4 About SecurityPower 5 Next Generation Security Solutions 6 600 Appliances 7 1100 Appliances
The Cisco ASA 5500 Series Adaptive Security Appliances
 Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Benefits. Product Overview. There is nothing more important than our customers. DATASHEET
 DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
DATASHEET Security Information & Event Manager (SIEM) Compliance through Security Information and Event Management, Log Management, and Network Behavioral Analysis Product Overview Delivers fast, accurate
Cisco SR 520-T1 Secure Router
 Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Virtualized Security: The Next Generation of Consolidation
 Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Deliver More Applications for More Users
 HARDWARE DATASHEET Deliver More Applications for More Users F5 BIG-IP Application Delivery Controller (ADC) platforms can manage even the heaviest traffic loads at both layer 4 and layer 7. By merging
HARDWARE DATASHEET Deliver More Applications for More Users F5 BIG-IP Application Delivery Controller (ADC) platforms can manage even the heaviest traffic loads at both layer 4 and layer 7. By merging
The Cisco ASA 5500 Series Adaptive Security Appliances
 Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Cisco ASA 5500 Series Adaptive Security Appliances Cisco ASA 5500 Series Adaptive Security Appliances deliver a robust suite of highly integrated, marketleading security services for small and medium-sized
Cisco ASA 5500 Series Adaptive Security Appliances for the Internet Edge
 Data Sheet 5500 Series Adaptive Security Appliances for the Internet Edge A key component of the Cisco SecureX framework, the 5500 Series integrates the world's most proven firewall with a robust suite
Data Sheet 5500 Series Adaptive Security Appliances for the Internet Edge A key component of the Cisco SecureX framework, the 5500 Series integrates the world's most proven firewall with a robust suite
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Cisco WAE Deployed with Cisco ACNS: Product Function Matrix. Two 10/100/1000BASE-T. Two 10/100/1000BASE- T
 :: Seite 1 von 6 :: Datenblatt zum Produkt Cisco 4 GB RAM UPGRADE FOR WAE-674 mit DC# 478819 :: Cisco Wide Area Application Engine The Cisco Wide Area Application Engine (WAE) platforms are a portfolio
:: Seite 1 von 6 :: Datenblatt zum Produkt Cisco 4 GB RAM UPGRADE FOR WAE-674 mit DC# 478819 :: Cisco Wide Area Application Engine The Cisco Wide Area Application Engine (WAE) platforms are a portfolio
A Getting Started Guide: What Every Small Business Needs To Know About Internet Security
 A Getting Started Guide: What Every Small Business Needs To Know About Internet Security In This Document 1 Overview: Internet Security In Small Businesses 2 Internet Access New Business Opportunities
A Getting Started Guide: What Every Small Business Needs To Know About Internet Security In This Document 1 Overview: Internet Security In Small Businesses 2 Internet Access New Business Opportunities
Cisco Intrusion Detection System Services Module (IDSM-2)
 Data Sheet Cisco Intrusion Detection System Services Module (IDSM-2) Cisco integrated network security solutions enable organizations to minimize risk and maximize business continuity. The Cisco IDSM-2
Data Sheet Cisco Intrusion Detection System Services Module (IDSM-2) Cisco integrated network security solutions enable organizations to minimize risk and maximize business continuity. The Cisco IDSM-2
Check Point 13500 Appliance
 Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Check Point 12200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Datacenter-grade security appliance Check Point 2200 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 2200 Appliance 2200 Datacenter-grade security appliance Check Point 2200 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Securing Virtualization with Check Point and Consolidation with Virtualized Security
 Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Check Point 21400 Appliance
 Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance Check Point 2400 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance Check Point 2400 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Data Sheet FUJITSU Storage ETERNUS DX200F All Flash Array
 Data Sheet FUJITSU Storage ETERNUS DX200F All Flash Array Superior performance at reasonable cost ETERNUS DX - Business-centric Storage Combining leading performance architecture with automated quality
Data Sheet FUJITSU Storage ETERNUS DX200F All Flash Array Superior performance at reasonable cost ETERNUS DX - Business-centric Storage Combining leading performance architecture with automated quality
The Seven Key Factors for Internet Security TCO
 The Seven Key Factors for Internet Security TCO Executive Summary Total Cost of Ownership, or TCO, of any information technology deployment consists of more than simply the direct costs of acquisition
The Seven Key Factors for Internet Security TCO Executive Summary Total Cost of Ownership, or TCO, of any information technology deployment consists of more than simply the direct costs of acquisition
SecureSphere Appliances
 DATASHEET SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding datacenter environments. With fail open interfaces,
DATASHEET SecureSphere Appliances Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior performance and resiliency for demanding datacenter environments. With fail open interfaces,
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance Check Point 4800 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance Check Point 4800 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Cisco Wide Area Application Services (WAAS) Appliances
 Data Sheet Cisco Wide Area Application Services (WAAS) Appliances Cisco Wide Area Virtualization Engine Product Overview The Cisco Wide Area Application Virtualization Engine (WAVE) product line comprises
Data Sheet Cisco Wide Area Application Services (WAAS) Appliances Cisco Wide Area Virtualization Engine Product Overview The Cisco Wide Area Application Virtualization Engine (WAVE) product line comprises
Preventing Data Leaks on USB Ports. Check Point Endpoint Security Media Encryption simply regulates access and data for any plug-and-play peripherals
 Preventing Data Leaks on USB Ports Check Point Endpoint Security Media Encryption simply regulates access and data for any plug-and-play peripherals Preventing Data Leaks on USB Ports Contents Executive
Preventing Data Leaks on USB Ports Check Point Endpoint Security Media Encryption simply regulates access and data for any plug-and-play peripherals Preventing Data Leaks on USB Ports Contents Executive
Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System
 Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System The all-in-one storage system for SMBs or subsidiaries ETERNUS DX - Business-centric Storage ETERNUS DX200 S3 Combining leading performance architecture
Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System The all-in-one storage system for SMBs or subsidiaries ETERNUS DX - Business-centric Storage ETERNUS DX200 S3 Combining leading performance architecture
Check Point 12600 Appliance
 Datasheet: Check Point 2600 Appliance 2600 Datacenter-grade security appliance Check Point 2600 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 2600 Appliance 2600 Datacenter-grade security appliance Check Point 2600 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Check Point 12400 Appliance
 Datasheet: Check Point 400 Appliance 400 Datacenter-grade security appliance Check Point 400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an ever-increasing
Datasheet: Check Point 400 Appliance 400 Datacenter-grade security appliance Check Point 400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an ever-increasing
Check Point UserAuthority Guide. Version NGX R61
 Check Point UserAuthority Guide Version NGX R61 700358 January 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point UserAuthority Guide Version NGX R61 700358 January 2006 2003-2006 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Extreme Security Threat Protection G2 - Intrusion Prevention Integrated security, visibility, and control for next- generation network protection
 DATA SHEET Extreme Security Threat Protection G2 - Intrusion Prevention Integrated security, visibility, and control for next- generation network protection HIGHLIGHTS Delivers superior zero-day threat
DATA SHEET Extreme Security Threat Protection G2 - Intrusion Prevention Integrated security, visibility, and control for next- generation network protection HIGHLIGHTS Delivers superior zero-day threat
Infoblox DDI Appliances. Hardware and Performance Specifications
 Hardware and Performance Specifications Trinzic Appliances are Optimized for Remote Management and Energy Efficiency Purpose-built network appliances deliver high-performance reliable and secure DNS, DHCP
Hardware and Performance Specifications Trinzic Appliances are Optimized for Remote Management and Energy Efficiency Purpose-built network appliances deliver high-performance reliable and secure DNS, DHCP
Check Point QoS. Administration Guide Version NGX R65
 Check Point QoS Administration Guide Version NGX R65 700726 January 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point QoS Administration Guide Version NGX R65 700726 January 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Data Sheet FUJITSU Storage ETERNUS CS800 S5
 Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Protection Appliance: Backup to Disk with Deduplication ETERNUS CS Backup Appliance The ETERNUS CS portfolio
Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Protection Appliance: Backup to Disk with Deduplication ETERNUS CS Backup Appliance The ETERNUS CS portfolio
How To Build A Cisco Uniden Computing System
 Data Sheet Cisco UCS 5100 Series Blade Server Chassis Cisco Unified Computing System Overview The Cisco Unified Computing System (Cisco UCS ) is a next-generation data center platform that unites computing,
Data Sheet Cisco UCS 5100 Series Blade Server Chassis Cisco Unified Computing System Overview The Cisco Unified Computing System (Cisco UCS ) is a next-generation data center platform that unites computing,
Sophos SG Series Appliances
 Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Unleash the full potential of your network With bandwidth requirements constantly increasing, network security appliances need to do more than ever before. The Sophos SG Series appliances are built to
Imperva SecureSphere Appliances
 Imperva SecureSphere Appliances DA T A SH E E T Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior and resiliency for demanding data center environments. With fail open interfaces,
Imperva SecureSphere Appliances DA T A SH E E T Scalable. Reliable. Flexible. Imperva SecureSphere appliances provide superior and resiliency for demanding data center environments. With fail open interfaces,
Configuring Check Point Firewall-1 to support Avaya Contact Center Solutions - Issue 1.1
 Avaya Solution & Interoperability Test Lab Configuring Check Point Firewall-1 to support Avaya Contact Center Solutions - Issue 1.1 Abstract These Application Notes explain how to configure Check Point
Avaya Solution & Interoperability Test Lab Configuring Check Point Firewall-1 to support Avaya Contact Center Solutions - Issue 1.1 Abstract These Application Notes explain how to configure Check Point
IREBOX X. Firebox X Family of Security Products. Comprehensive Unified Threat Management Solutions That Scale With Your Business
 IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
STORAGETEK SL150 MODULAR TAPE LIBRARY
 STORAGETEK SL150 MODULAR TAPE LIBRARY Oracle s StorageTek SL150 modular tape library is the first scalable tape library designed for growing small to midsized companies. Built from Oracle software and
STORAGETEK SL150 MODULAR TAPE LIBRARY Oracle s StorageTek SL150 modular tape library is the first scalable tape library designed for growing small to midsized companies. Built from Oracle software and
Cisco UCS B-Series M2 Blade Servers
 Cisco UCS B-Series M2 Blade Servers Cisco Unified Computing System Overview The Cisco Unified Computing System is a next-generation data center platform that unites compute, network, storage access, and
Cisco UCS B-Series M2 Blade Servers Cisco Unified Computing System Overview The Cisco Unified Computing System is a next-generation data center platform that unites compute, network, storage access, and
How To Backup To Disk With Deduplication On An Fujitsu Ecson Cser800 S4 Data Protection Appliance
 Data Sheet Fujitsu ETERNUS CS800 S4 Data Protection Appliance: Backup to Disk with Deduplication ETERNUS CS Backup Appliance Many IT departments are looking for solutions that provide faster backup and
Data Sheet Fujitsu ETERNUS CS800 S4 Data Protection Appliance: Backup to Disk with Deduplication ETERNUS CS Backup Appliance Many IT departments are looking for solutions that provide faster backup and
How To Use An Fujitsu Ces800 S5 Backup Appliance
 Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Protection Appliance: Backup to Disk with Deduplication ETERNUS CS Backup Appliance The FUJITSU Storage ETERNUS
Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Sheet FUJITSU Storage ETERNUS CS800 S5 Data Protection Appliance: Backup to Disk with Deduplication ETERNUS CS Backup Appliance The FUJITSU Storage ETERNUS
Cisco ASA 5585-X Next-Generation Firewall
 Data Sheet Next-Generation Firewall Today s enterprise networks must deal with an increasingly mobile workforce requiring anywhere, anytime access from a variety of company and personal devices. These
Data Sheet Next-Generation Firewall Today s enterprise networks must deal with an increasingly mobile workforce requiring anywhere, anytime access from a variety of company and personal devices. These
The On-Demand Application Delivery Controller
 What s Inside: 2 Increase Intelligence, Not Operating Costs 2 Simplify Your Network 2 Maximize Large-Scale Application Performance 2 Achieve Ultimate Reliability 2 The Advantages of Technology 6 Platforms
What s Inside: 2 Increase Intelligence, Not Operating Costs 2 Simplify Your Network 2 Maximize Large-Scale Application Performance 2 Achieve Ultimate Reliability 2 The Advantages of Technology 6 Platforms
Check Point License Guide (April-2012) General Pricelist
 CPAP-SG61* License Guide (April-2012) General Pricelist SKU Prefix Name Description Blades included CPAP-SG21412 CPAP-SG12610 CPAP-SG12608 CPAP-SG12607 CPAP-SG12410 CPAP-SG12408 CPAP-SG12407 CPAP-SG12210
CPAP-SG61* License Guide (April-2012) General Pricelist SKU Prefix Name Description Blades included CPAP-SG21412 CPAP-SG12610 CPAP-SG12608 CPAP-SG12607 CPAP-SG12410 CPAP-SG12408 CPAP-SG12407 CPAP-SG12210
