Check Point License Guide (April-2012) General Pricelist
|
|
|
- Jeffery Lambert
- 9 years ago
- Views:
Transcription
1 CPAP-SG61* License Guide (April-2012) General Pricelist SKU Prefix Name Description Blades included CPAP-SG21412 CPAP-SG12610 CPAP-SG12608 CPAP-SG12607 CPAP-SG12410 CPAP-SG12408 CPAP-SG12407 CPAP-SG12210 CPAP-SG12208 CPAP-SG12207 CPAP-SG4810 CPAP-SG4808 CPAP-SG4807 CPAP-SG4610 CPAP-SG4608 CPAP-SG4607 CPAP-SG4210 CPAP-SG4208 CPAP-SG4207 CPAP-SG System Gateway - The System is the industry s fastest security appliance, offering scalable performance for data centers and telecommunication companies. It s based on a multi-d hardware platform that is capable of an unprecedented performance of more than 1 Tbps of firewall throughput, and achieves over 200 Gbps today. Even more, the ability to support 70 million concurrent connections and 600,000 sessions per second brings unparalleled performance to multi-transaction environments is a Data Center security platform that uses acceleration technologies to deliver comprehensive security. The offers high performance with up to 100 Gbps of throughput and low latency The s, featuring multi-core security technology and high port density, are ideally suited for perimeter security of large network environments as well as business-critical internal network segments. High business continuity and serviceability are delivered through features such as hot-swappable redundant power supplies/disk drives, a Lights-Out- card, and High- Availability features such as ClusterXL and Load- Sharing s offer complete and integrated security solutions in a compact 1U form factor. Delivering firewall throughput up to 11 Gbps and IPS throughput up to 6 Gbps, these enterprisegrade appliances deliver superior performance for their class. FW, VPN, IA, ADN, ACCL FW, VPN, IA, ADN, ACCL, MOB-5, IPS, URLF, AV, APCL, ASPM, DLP, NPM, LOGS FW, VPN, IA, ADNC, MOB-5, IPS, APCL, NPM, LOGS (8 Blades package includes also the DLP. 10 Blades package includes also AV, URLF, ASPM) FW, VPN, IA, ADNC, MOB-5, NPM, LOGS (7 s package includes also IPS and APCL, 8 Blades package includes also the IPS, APCL and DLP s. 10 Blades package includes also IPS, APCL AV, URLF, ASPM) One on the device ent and Managem One on the device ent and Managem One on the device ent and Managem License is per model. License supports unlimited users. License also includes container managing up to 2 gateways. Prices do not include shipping costs. License is per model. License supports unlimited users. License also includes container managing up to 2 gateways. Prices do not include shipping costs. License is per model. License supports unlimited users. License also includes container managing up to 2 gateways. Prices do not include shipping costs Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 1
2 CPAP-SG2210 CPAP-SG2208 CPAP-SG2207 CPAP-SG2205 SKU Prefix Name Description Blades included CPAP-SG5077 CPAP-SG9077 CPAP-SG11067 CPAP-SG11077 CPAP-SG11087 CPAP-IP2457 CPAP-IP1287 CPAP-IP697 CPAP-IP567 CPAP-IP397 CPAP-IP297 CPAP-IP282 CPAP-SG3078 CPAP-SG2078 CPAP-SG1078 CPAP-SG5778 CPAP-SG278 CPAP-SG138 CPAP-SG3075 CPAP-SG2075 CPAP-SG1075 CPAP-SG574 CPAP-SG272 CPAP-SG274 CPAP-SG134 CPAP-SG132 CPAP-SG86 CPAP-SG Power-1 IP s UTM-1 Total s UTM-1 appliance Series 80 appliance The 2200 offers enterprise-grade security with leading performance in a compact desktop form factor. With its multi-core technology and six 1-gigabit Ethernet ports, the 2200 is easily capable of securing any branch office or small office. Power-1 appliances with extensive 5 package for high performance and unrivaled security: Firewall, IPSec VPN, Advanced Networking, Acceleration & Clustering and IPS. IP s are the combination of the former Nokia appliances fully integrated with software into a single solution. IP s with extensive 5 package for high performance and unrivaled security: Firewall, IPSec VPN, Advanced Networking, Acceleration & Clustering and IPS. UTM-1 appliances offer a complete unified security solution for organizations of all sizes. They combine firewall, IPSec VPN, IPS, URL filtering, anti-spam, security, antivirus and more in a convenience, easy to deploy and easy to manage solution.. UTM-1 appliances offer a complete unified security solution for organizations of all sizes. They combine firewall, IPSec VPN, IPS and more in a convenience, easy to deploy and easy to manage solution.. UTM-1 appliances offer a complete unified security solution for remote office and branch office (ROBO). They combine firewall, IPSec VPN, IPS, URL filtering, anti-spam, security, antivirus and more in a convenience, easy to deploy and easy to manage solution. FW, VPN, IA, ADNC, MOB-5, NPM, LOGS (7 s package includes also IPS and APCL, 8 Blades package includes also the IPS, APCL and DLP s. 10 Blades package includes also IPS, APCL AV, URLF, ASPM) FW, VPN, IPS, ACCL, ADN, APCL, IA FW, VPN, IPS, ACCL, ADN, APCL, IA (IP282 includes FW & VPN only) FW, VPN, IPS, AV, URLF, ASPM, APCL, IA, NPM, EPM, LOGS FW, VPN, NPM, EPM, LOGS (the 4 s included also APCL, IA. The 5 s includes also IPS) FW, VPN (the 6 s model includes IPS, AV, ASPM, URLF 2 2 One on the device ent and Managem One on the and device License is per model. License supports unlimited users. License also includes container managing up to 2 gateways. Prices do not include shipping costs. Lincese is per model. License is for Unlimited users. Includes 5,000 VPN-1 SecuRemote users, as well as MultiCore. Prices do not include shipping costs. License is per model. License is for unlimited users. Includes 1,000 VPN-1 SecuRemote users. License also includes container and 5 Secure Access. The 130 model can manage 1 gateway only. Models 270, 570, 1070, 2070 and 3070 can manage 2 gateways including themselves. Prices do not include shipping costs. License is per model. Includes 1,000 VPN-1 SecuRemote users.. License also includes container and 5 Check Point Secure Access. The 130 model can manage 1 gateway only. Models 270, 570, 1070, 2070 and 3070 can manage 2 gateways including themselves. Prices do not include shipping costs. License is per model. License is for unlimited users. Prices do not include shipping costs. CPUTM-EDGE VPN-1 UTM Edge A unified threat management hardware appliance that provides allin-one security including firewall, VPN, SmartDefense Service, IPS and Antivirus for enterprise branch offices and remote offices. The appliances are available with built-in secure wireless access point and/or ADSL modem. All wireless and/or ADSL models include a USB port used as a print server. N/A N/A Not licensable through UC. The product comes with a key preinstalled Licensed per number of concurrent connections. The SKU is a product key tied up to the MAC address of the appliance. Prices do not include shipping costs 2010 Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 2
3 CPSG-P1207 CPSG-P807 CPSG-P407i CPSG-P409 CPSG-P203U CPSG-P205U CPSG-P203 CPSG-P205i CPSG-P207i CPSG-P209 CPSG-P103 CPSG-P108 CPSG-C801 CPSG-C401 CPSG-C201 CPSG-C101 CPSB-FW CPSB-IA CPSB-VPN CPSB-MOB CPSB-WS SKU Prefix Name Description Blades included Gateway predefined system Gateway Container Firewall Identity Awareness IPSEC VPN Mobile Access Web Gateway - Software Gateways provide the most comprehensive, flexible and extensible security while keeping security operations simple and affordable. Software Blade containers are the common platform that contains all the necessary services to run the software environment. Every security gateway container comes prepopulated with a Firewall, based on awardwinning and patented FireWall-1 technology. 3 s includes FW, VPN, IPS. 5 s also includes APCL and IA. 7 s also includes ADN and ACCL. 9 s includes FW, VPN, ACCL, IPS, IA, APCL, AV, ASPM, URLF 1 or 2 Gateway - Blades Firewall Software Blade provides the highest level of security, with access control, application security, authentication and Network Address Translation (NAT) available to block unauthorized network FW 0 -- users and protect enterprise users and data. Provides granular security policy at a per user, per group and per machine level. It centralizes the management, monitoring and reporting of user actions across the internal network, its perimeter IA 0 -- and beyond. 's VPN Software Blade is an integrated software solution that provides secure connectivity to corporate networks, remote and mobile users, branch offices and business partners. The integrates access control, authentication and encryption VPN 0 -- to guarantee the security of network connections over the public Internet. Mobile Access Software Blade is the safe and easy solution to connect to corporate applications over the internet with Smartphone or PC. The solution provides enterprise-grade remote access via SSL VPN, allowing simple, safe and secure connectivity to , calendar, contacts and corporate applications. The Web Software Blade provides a set of advanced capabilities that detect and prevent attacks launched against the Web infrastructure. The Web Software Blade delivers comprehensive protection when using the Web for business and communication. MOB 0 -- WS Centrally on the server or localy on the Gateway server SG100, SG200, SG400 and SG800 series are designed utilize 1, 2, 4 and 8 cores respectively. SG100 series is limited to 50 users. SG200 series is limited to 500 users. SG200U, SG400 and SG800 are unlimited. FW is included. Blade should be attached to a Gateway Container. Blade should be attached to a Gateway Container. Blade should be attached to a Gateway Container. Licensed per number of cuncurrent connection (devices) handled by the Gateway. Blade should be attached to a Gateway Container. Mobile Access allows connectivity from the following clients: Mobile for Smartphones, SSL VPN Portal, SNX for Windows, Mac and Linux. Mobile client for PC is coming soon. Available in R71 and above. Blade should be attached to a Gateway Container Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 3
4 CPSB-ADNC CPSB-VOIP SKU Prefix Name Description Blades included CPSB-ESEC-6B CPSB-DLPP-3B CPSB-ETPR-2B CPSB-ABAV-2B CPSB-WBCL-2B CPSB-UTMP-5B CPSB-TS-XL CPSB-TS-L CPSB-TS-M CPSB-TS-S CPSB-DLP-U CPSB-DLP-1500 CPSB-DLP-500 CPSB-ABOT-XL CPSB-ABOT-L CPSB-ABOT-M CPSB-ABOT-S Advanced Networking and Cluster Voice over IP Extended package DLP Plus Package Extended Threat Protection package Anti-Malware package Web Conctrol package UTM Plus/ Total package Data Loss Prevention Anti-Bot annual The Advanced Networking and Clustering Software Blade simplifies network security deployment and management within complex and highly utilized networks, while maximizing network performance and security in multi-gbps environments. Built on top of the Software s architecture, the Advanced Networking & Clustering provides advanced routing, multicast support, QOS, ISP redundancy, Load Balancing, and Acceleration technologies. Please note that the Advanced Networking (ADN) and the Accesleration & Clustering (ACCL) should not appear in the PL unless specifically searched for (like the IAS systems). The security family enables you to deploy VoIP applications such as telephony or video. Software Blades packages Extended Software Blades Package for 1, 2 or 3 years (including IPS, URL Filtering, Application Control, Anti- Malware, , and DLP s) ADNC 0 -- VOIP 0 -- IPS, AV, URLF, ASPM, APCL, DLP DLP+ Software Blades Package for 1, 2 or 3 Years (including IPS, Application Control, and DLP) IPS, APCL, DLP 0 Extended Threat Protection Software Blades Package for 12, or 3 years (including IPS s and Application Control). IPS< APCL 0 Anti-Bot and Antivirus Software Blades provide a complete pre/post infection bot and malware protection, to detect and stop incoming attacks and existing infections. Uses unified Bot and virus defense, event investigation and reports, with real-time updates from ThreatCloud collaborative cybercrime-fighting network. The Web Software Blade provides a set of advanced capabilities that detect and prevent attacks launched against the Web infrastructure. The Web Software Blade delivers comprehensive Web related protections, including malicious code protector and advanced streaming inspection, to secure Web business and communications. UTM+ and Total Software Blades Package for 1, 2 or 3 years (including IPS, URL Filtering, Application Control, Anti-Malware, and s.) ABOT, AV 0 URLF, APCL 0 IPS, AV, URLF, ASPM, APCL Annual Software Blades Data Loss Prevention (DLP) solution helps businesses move data loss from detection to prevention by pre-emptively protecting sensitive information regulatory, confidential and proprietary from unintentional loss. Unlike other solutions that are DLP 0 -- unable to address user activity context, UserCheck technology brings a human factor to DLP by empowering users to remediate incidents in real-time while educating on DLP policies. Revolutionize bot protection: detect bot infected machines and APT attacks, prevent data theft and stop bot damages, and provide tools to investigate infections. Uses unique multi-layer discovery ABOT 0 -- technology with real-time updates from ThreatCloud collaborative cybercrime-fighting network Blade should be attached to a Gateway Container. Generate 2 license strings one for the Gateway container and another for the container. Voice over IP software is currently available on security gateway release R and is currently managed by security management R65.4 and higher. Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Avaialble in R75.40 and above Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Avaialble in R75.40 and above 2010 Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 4
5 CPSB-APCL-XL CPSB-APCL-L CPSB-APCL-M CPSB-APCL-S SKU Prefix Name Description Blades included Application Control annual Application Control Software Blade enables organizations to identify, allow, block or limit usage of thousands of Web 2.0 applications. The new software integrates s unique UserCheck technology to engage employees in the decision-making process, while educating them on risks and usage policies. APCL 0 -- Blades should be attached to a Gateway Container. Service s are yearly renewable s. License is per gateway. Available in R75 and above. CPSB-IPS-XL CPSB-IPS-L CPSB-IPS-M CPSB-IPS-S CPSB-URLF-XL CPSB-URLF-L CPSB-URLF-M CPSB-URLF-S CPSB-AV-XL CPSB-AV-L CPSB-AV-M CPSB-AV-S CPSB-ASPM CPAP-SM504 CPAP-SM2507 CPAP-SM5007 CPAP-SM503-EVNT CPAP-SM2503-EVNT CPAP-SM5003-EVNT CPAP-SM150-MD308 CPAP-SM150-MD508 CPAP-SM150-MD1008 CPAP-SM50-MD308 CPAP-SM50-MD508 CPAP-SM50-MD1008 CPSM-PU003 CPSM-PU007 CPSM-P2506 CPSM-P1003 CPSM-P1007 IPS annual URL Filtering annual Antivirus annual Anti-Spam & annual Smart-1 Smart-1 Smart-1 SmartEvent Smart-1 Multi- Domain pre-defined system The IPS Software Blade provides complete, integrated, next generation firewall intrusion prevention capabilities at multigigabit speeds, resulting in industry-leading total system security and performance. The IPS Blade provides complete threat coverage for clients, servers, OS and other vulnerabilities, malware/worm infections, and more. IPS 0 -- The URL Filtering Software Blade protects users and enterprises by restricting access to an array of potentially dangerous sites and content, blocking inappropriate Web surfing to over 20-million URLs. Pre-configured policy templates enable quick URLF 0 -- and simple deployment of policies using content categories. All content profiles are updated continually through a software update service. Extended Antivirus protection to stop viruses, worms and other malware at the gateway. Supporting millions of signatures using real-time updates from ThreatCloud collaborative cybercrimefighting AV 0 -- network. The Anti-Spam and Software Blade provide comprehensive protection for an organization's messaging infrastructure. A multidimensional approach protects the infrastructure, provides highly accurate spam protection, and ASPM 0 -- defends organizations from a wide variety of virus and malware threats delivered within . Continual updates assure that all threats are intercepted before they spread. - Smart-1 appliances deliver s market leading security management software s on a dedicated hardware platform specifically designed for mid-size and large enterprise security networks. Based on s software architecture, the line of four Smart-1 appliances are first to deliver a unified management solution for network, IPS and endpoint security with unsurpassed extensibility. NPM, EPM, LOGS & PRVS NPM, EPM, LOGS, PRVS, MNTR, UDIR & EVIN LOGS, RPRT & EVNT NPM, EPM, LOGS, PRVS, MNTR, MPTL, UDIR & EVIN - Software solutions integrate policy configuration, monitoring, logging, reporting and security event management in a single interface - helping minimize total cost of ownership. NPM, EPM LOGS. 6 s includes also MNTR, EVIN, PRVS. 7 s 1 server Blade should be attached to a Gateway Container. Service is yearly renewable. License is per gateway. Blade should be attached to a Gateway Container. Service is yearly renewable. License is per gateway. Blade should be attached to a Gateway Container. Service is yearly renewable. License is per gateway. Blade should be attached to a Gateway Container. Service is yearly renewable. License is per gateway. License is per model. License is for managing 5 gateways. License also includes MGMT HA. Prices do not include shipping costs. License is per model. License is for managing 25 or 50 gateways. License also includes MGMT HA. Prices do not include shipping costs. License is per model. License is for managing 5, 25 or 50 gateways (based on the model number). License also includes MGMT HA. Prices do not include shipping costs. License is per model. License is for managing 3, 5 or 10 Domains (based on the model number). License also includes MGMT HA. Additional Domain software can be added using the standard Software domain SKUs. License is per number of managed gateways and s (and not per cluster or per site.) High Availability configuration of the requires both primary and secondary servers to have the same container 2010 Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 5
6 CPSM-CU000 CPSM-C2500 CPSM-C1000 SKU Prefix Name Description Blades included CPSM-P1003-E CPSM-P2503-E CPSM-PU003-E CPSM-MD1004 CPSM-MLOGS-10 CPSM-P1001 CPSM-C500 CPSB-NPM CPSB-EPM CPSB-LOGS CPSB-MNTR CPSB-PRVS CPSB-MPTL CPSB-UDIR container pre-defined system Multi-Domain pre-defined system pre-defined system including Customer Log Module Add-on Container Expansion for additional 5 managed gateways Network Policy Policy Logging & Status Monitoring Smart Provisioning Portal User Directory Customer Log Module Enables real-time log accumulation, tracking and management on a dedicated log server for Gateways. It includes a container and a license for collecting logs from up to 10 gateways Container Expansion increases the number of managed gateways in a given container. There is no change to the installed s. includes also UDIR NPM, EPM, LOGS, GBLP LOGS - Blades Comprehensive network security policy management for Check Point gateways and s via SmartDashboard, a single, unified console. Centrally deploy, manage, monitor and enforce security policy for endpoint devices across any sized organization. Comprehensive information in the form of logs and a complete visual picture of changes to gateways, tunnels, remote users and security activities. A complete view of network and security performance, enabling fast response to changes in traffic patterns or security events. Centralized administration and SmartProvisioning of security gateways via a single management console. Extends a browser-based view of security policies to outside groups such as support staff while maintaining central policy control. Leverage LDAP-based user information stores, eliminating the risks associated with manually maintaining and synchronizing redundant data stores. LOGS NPM 0 -- EPM 0 -- LOGS 0 -- MNTR 0 -- PRVS 0 -- MPTL 0 -- UDIR 0 -- Log Server Device and topology. No additional (or license) is required beyond this requirement. contianer can manage 10, 25 or Unlimited gateways and 1000, 2500 or Unlimited devices. Blade should be attached to a Container. Blade should be attached to a Container. Blade should be attached to a Container. Blade should be attached to a Container. Blade should be attached to a Container. Blade should be attached to a Container. Blade should be attached to a Container. Blade should be attached to a Container Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 6
7 SKU Prefix Name Description Blades included CPSB-EVNT-INT CPSB-WKFL CPSB-EVS SmartEvent Intro SmartWorkflow SmartReporter & SmartEvent package Centralized, real-time, security event correlation and management for a single. policy change management with visual traceability and full auditability Eventia Suite package provides the benefits of Event Correlation and Reporting s EVNT-INT 0 -- WKFL 0 -- RPRT, EVNT 0 -- Blade should be attached to a Container. EVNT-INT provides centralized SmartEvent and management for the IPS, DLP or Application Control s. Blade should be attached to a Container. License of SmartWorkflow s is per number of managed gateways. EVS-C1000 and EVS-C2500 come with one correlation unit. EVS-CU000 comes with four correlation units. SmartEvent bundle size needs to match the Container size. CPSB-RPRT CPSB-EVNT SmartReporter SmartEvent Turn the vast amount of data collected from security and network devices into graphical, easy-to-understand reports. Centralized, real-time, security event correlation and management for and 3rd party devices. RPRT 0 Reporter Server EVNT 0 SmartEvent server Blade should be attached to a Container. SmartReporter and SmartEvent s can only be purchased in a package of two. License is per number of managed gateways and should match the container s size. CPSB-GBPL Check point Global Policy Enhance your security management with Global Policy software and enhanced administrator hierarchy GBPL 0 -- Blade should be attached to a Container. The required to add additional security domains.can be installed only on "standalone" Servers (and not on servers running and GWs). Should be installed only on a Container for Unlimited GWs only. CPSB-DMN200 CPSB-DMN1000 CPSB-DMNU000 CPSB-DMNVSX CPSB-DMNLOGS Domain software Additional Virtual Domains DMN 0 -- Blade should be attached to a Container. The Global Policy software is required to add additional security domains. Up to 250 security domains are support per single multi-domain server. CPSB-DMNVSX can only manage a singel VSX Virtual System. CPSG-P805-CPSM-PU007 CPSG-P405-CPSM-PU003 CPSG-P405-CPSM-P2506 CPSG-P405-CPSM-P1003 CPSG-P203-CPSM-P1003 CPSG-P203-CPSM-P303 CPSG-P103-CPSM-P303 CPSG-P103-CPSM-P203 CPAP-VSX bundle VSX & Gateway - bundle and Gateway bundles make it easy for customers to purchase the right combination of gateway and management products in a single and affordable SKU. It includes managing a specified number of gateways and one. Both the and Gateway containers comes pre-populated with s Virtual Secuirty Gateways Can run up to 250 VSs. License is additive for increasing numbers of Virtual Systems.These products are based on NGX architecture. The appliance includes 1 year hardware warranty. 2 server or & Gateway servers SG100, SG200, SG400 and SG800 series are designed to utilize 1, 2, 4 and 8 cores respectively. SG100 series is limited to 50 users. SG200 series is limited to 500 users. SG400 and SG800 are unlimited. SM200, SM300, SM1000, SM2500, SMU000 are licensed to manage 2, 3, 10, 25 and Unlimited gateways respectively. Can run up to 250 VSs. License is additive for increasing numbers of Virtual Systems.These products are based on NGX architecture. The appliance includes 1 year hardware warranty Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 7
8 SKU Prefix Name Description Blades included CPAP-VSX CPAP-VSX CPAP-VSX VSX VSX is a dedicated solution for multilayer, multi-domain virtualized security for multi-layer, multi-domain virtualized security VSX provides organizations with maximum security in high-performance environments such as large campuses or data centers. Allows enterprises, data centers and service providers to consolidate up to 150 security gateways with firewall, IPsec and SSL virtual private network (VPN), intrusion prevention and URL filtering on a single device. The VSX bundle offering provides linear performance scalability with system high availability and VSX appliances can run up to 150 VSs VSX appliance can run up to 10 VSs. License is additive for increasing numbers of Virtual Systems.These products are based on NGX architecture. The appliance includes 1 year hardware warranty. CPPWR-VSX-APP CPPWR-VSX-ADD VSX-1 Add-on for XX VSs for VSX-1 The VSX Gateway enforces up to 250 discrete VPN-1 Power security policies on a single machine. Each VS (Virtual System) is associated with a VLAN, which is attached to an internal interface of the VSX Gateway. The additional Virtual Gateway enables automatic high availability by providing an additional Virtual Gateway. SecureXL is provided with every VSX Gateway for enhanced VPN and firewall performance. SecurePlatform Pro is included. N/A Licensed based on virtual number of systems running on a VSX gateway. The VSX-1 appliance Models 11060, 11070, 11080, 11260, and can run up to 250 VSs. The VSX-1 appliance Models 9070, 9090 can run up to 150 VSs. The VSX-1 appliance Model 3070 can run up to 10 VSs. VSX-1 appliance includes 1 year hardware warranty. CPPWR-VSX CPPWR-VSX-HA CPSG-VE4801 CPSG-VE1601 CPSG-VE801 CPAP-DLP CPIS-IPS-M CPAP-IPS CPIS-IPS-SW Power Virtual Gateway - VSX Secondary VPN- 1 Power VSX gateway for Load Sharing and High Availability Gateway Virtual Edition on Virtual System DLP-1 IPS-1 sensor IPS-1 OpenSensor The VSX Gateway enforces up to 250 discrete VPN-1 Power security policies on a single machine. Each VS (Virtual System) is associated with a VLAN, which is attached to an internal interface of the VSX Gateway. The additional Virtual Gateway enables automatic high availability by providing an additional Virtual Gateway. SecureXL is provided with every VSX Gateway for enhanced VPN and firewall performance. SecurePlatform Pro is included. Gateway - Virtualization Edition provides security within VMware virtualized environment securing virtual machines. VE provides consistent security for the virtual and physical environments, and is certified by VMware for use on ESX and ESXi servers. Dedicated Gateways The DLP appliance family offers easy deployment and activation, for immediate data loss prevention, by automatically preventing violations day-1 with over 250 pre-defined DLP policies that associate user, document and process. Users can also define their own DLP policies and rules and get better control and audit capabilities with intuitive, standalone or centralized security management. IPS-1 is a network intrusion detection and prevention system (IDS/IPS) that helps organizations secure their enterprise network and protect servers and critical data against known and unknown worms, automated malware and blended threats. N/A 1 Gateway FW 1 Gateway DLP, NPM, LOGS, EVIN, UDIR N/A 1 IPS-1 Server Licensed based on virtual number of systems running on a VSX gateway License must be of the same size as the primary VSX in the cluster. License must be used in a VSX cluster. Additional VE license is required per each instance of virtual machine running the Gateway VE. The Gateway Virtual Edition may utilize up to 2 virtual cores per virtual machine. FW is included. VE license does not count the number of 3rd party VM instances running on the host. s include a first year license for the annual DLP software. From second year onwards, it is required to re-purchase the annual. The license also includes container. IPS-1 appliance includes 1 year hardware warranty. Subscription to IPS Update Services (SmartDefense for NGX versions) is required to receive new protections. Subscription to IPS Update Services (SmartDefense for NGX versions) is required to receive new protections 2010 Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 8
9 SKU Prefix Name Description Blades included is the first single agent for Total CPEP-C1-1TO100. It protects endpoints and eliminates the need to CPEP-C1-101TO1000 deploy and manage multiple agents, reducing total cost of CPEP-C1-1001TO2500 ownership. Based on endpoint container and software s you container CPEP-C1-2501TOU can build your endpoint solution as required, and add additional EP-FW 1 Server s as needed in the future. CPSB-EP-FW CPSB-EP-FDE CPSB-EP-ME CPSB-EP-VPN CPSB-EP-AM CPSB-EP-WEBC CPSB-EP-TS CPSB-EP-FDE-P CPSB-EP-ME-P Firewall for 1 year Full Disk Encryption for 1 year Media Encryption for 1 year Remote Access (VPN) for 1 year Anti Malware and Program Control for 1 year WebCheck for 1 year Total package for 1 year Full Disk Encryption Media Encryption World's most proven firewall solution secures more than 200 applications, protocols and services featuring the most adaptive and intelligent inspection technology Delivers strong encryption with access control protecting data on hard drives Provides strong encryption for removable media and keeps data safe by controlling activity on ports and devices. Securely connect to corporate resources from an integrated Remote Access and client High Performance Anti malware (Anti Virus / Anti Spyware) engine. Control and protect endpoints from unwanted access of programs using Program Control and Program Advisory Patent Pending technology for Web Browsing Virtualization, protecting your from malicious drive-by-downloads Includes all s: Full Disk Encryption, Media Encryption, VPN, and WebCheck. Antimalware is also included in the annual Total. Delivers strong encryption with access control protecting data on hard drives Provides strong encryption for removable media and keeps data safe by controlling activity on ports and devices. EP-FW 0 -- EP-FDE 1 Server EP-ME 1 Server EP-VPN 1 Server EP-AM 1 Server EP-WEBC 1 Server EP-FDE, EP- VPN, EP-ME, EP- WEBC, EP-AM 5 (or 2 in R80) EP-FDE 1 Server EP-ME 1 Server Each server (or in R80 on EP management server and ) licensed per protected endpoint. An is defined as a Computer Instance in the End User License Agreement. EP FW in included contract. Comes pre-bundled with the EP container. contract. Annual software s include support, (as applied on the container). Includes the utilization in Enterprise Workplace management mode. contract. Annual software s include support, (as applied on the container). contract. Annual software s include support, (as applied on the container). contract. Annual software s include support, (as applied on the container). contract. Annual software s include support, (as applied on the container). contract. Annual software s include support, (as applied on the container). Includes all endpoint s, including Anti Malware. contract. Includes the utilization in Enterprise Workplace management mode. contract Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 9
10 SKU Prefix Name Description Blades included CPSB-EP-VPN-P CPSB-EP-WEBC-P CPSB-EP-TS-P CPEP-VW CPEP-VW Remote Access (VPN) WebCheck Total package Abra Go Securely connect to corporate resources from an integrated Remote Access and client Patent Pending technology for Web Browsing Virtualization, protecting your from malicious drive-by-downloads Includes all s: Full Disk Encryption, Media Encryption, VPN, and WebCheck. Abra puts your office in your pocket, with a secure virtual workspace that instantly turns any PC into your own corporate desktop, allowing users to access files and applications anywhere, anytime - without the weight of bulky laptops or work files. GO puts your office in your pocket, with a secure virtual workspace that instantly turns any PC into your own corporate desktop, allowing users to access files and applications anywhere, anytime - without the weight of bulky laptops or work files. EP-VPN 1 Server EP-WEBC 1 Server EP-FDE, EP- VPN, EP-ME, EP- WEBC 4 (or 2 in R80) N/A N/A N/A Each server (or in R80 on EP management server and ) contract. contract. contract. Abra is licensed per Abra USB unit. Abra is centrally managed from Smart Dashboard when used with VPN solutions. Minimum Order Quantity of 10 units. GO ships with pre-packaged license, no licensing operations are required 2010 Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 10
11 High End Solutions SKU Prefix Name Description Additive CPPR-MDS-MC Provider-1 MDS Manager and Container Provider-1 Multi Domain Servers (MDS) enable one-click centralized policy distribution with centralized resilient security SmartCenter for a specified number of Customer SmartCenter Add-ons (CMAs) on a single hardware platform. Each MDS system consists from 2 basic parts: MDS Manager & MDS Container. The Provider-1 system can manage ALL types of Customer SmartCenter Add-ons (CMAs). CPPR-MDS-C Provider-1 MDS Container Enables the addition of multiple Customer SmartCenter Add-ons (CMAs) to the MDS Server, thus allowing centralized security SmartCenter and policy distribution of VPN-1 Power Gateways for multiple Customers. Multiple MDS Container hosts can be cascaded to manage thousands of Customers in a single Provider-1 system. The Provider-1 MDS Container can contain all types of CMAs. CPPR-PRO Pro Add-on for MDS Pro Add-ons extend the ArchiTecture (SMART) by providing high end SmartCenter tools for the Provider-1 environment on the CMA level. The additional abilities includes: SmartDirectory - Powerful Integration with LDAP-based directories, SmartMap Allows visualizing the network structure in a graph view, SmartUpdate Allows remote deployment of software updates and upgrades, SmartLSM Allows large-scale management and provisioning, SmartView Monitor Advanced real-time monitoring functionality, SmartPortal Allow the web access to the CMA configuration data. The above features are licensed per CMA. CPPR-CMA CPPR-CMA-XX- HA Provider-1 CMA (Primary CMA) Provider-1 CMA HA (Secondary CMA) The Provider-1 Customer SmartCenter Add-on (CMA) utilizes Check Point s SmartCenter ArchiTecture (SMART) to enable oneclick centralized security SmartCenter and policy distribution of a specified number of VPN-1 Power Gateways, for a single Customer. Includes SmartDashboard - user interface for defining and managing the security policy and SmartView Tracker - for displaying detailed log information on all enforcement points. A CMA must be hosted within an MDS Container. CMAs of different Customers are completely isolated from each other. Provider-1 CMAs can only be used within a Provider-1 MDS Container. CPPR-CLM Customer Log Module Enables real-time accumulation, tracking and SmartCenter of logs from VPN-1 Power Gateways of one Customer. Log servers are managed at the CMA level, and are not considered part of the Provider-1 System. CPPR-MLM-C CPPR-VSX-CMA Multi-Domain Log Module MLM Virtual Systems Extension - CMA Bundles (Primary VSX-CMA) The MLM is a Container of Customer Log Modules (CLMs). It enables centralized log processing for multiple Customers on a dedicated MDS host. An MLM is recommended for larger deployments to improve performance of MDS Container hosts, by offloading their log processing functions. An MLM license cannot be added to a Provider-1 (or a SiteManager-1) MDS Container host. Enables the management of a specified number of Virtual Systems, for multiple Customers, on a Provider-1. With this product, users can define all the Primary CMAs that are needed to manage the bundled Virtual Systems and the MVSs of the VSX gateways hosting them. These CMAs are hosted on a Virtual Container, and do not require a regular MDS Container. of Strings Yes 1 MDS Server Yes 1 MDS Server Yes 1 MDS Server No 1 CMA Level No 1 Yes 1 Yes 1 MDS A stand-alone host, or cohosted on a VPN-1 Power gateway. MLM Server level, and covers all of the CLM licensing. CMA licenses are mandatory for the proper functionality of Provider-1 MDS systems. There is no need to purchase a High Availability software for the secondary MDS. Multiple MDS Container licenses can be added to the same MDS host, up to a maximum of 500 CMAs. CMA licenses are required for each CMA on the Container Needs to be installed at the CMA level Licensed per number of sites managed The Secondary CMA must be of the same size as the Primary CMA. Licensed per SmartCenter console. If hosted on non-mlm server must have own CLM license The MLM license enables all the contained CLMs. No additional CLM licenses are required. Multiple MLM licenses can be added to the same host, up to a maximum of 250 CLMs. This description is valid for VSX 2.0 and higher. Users with previous were credited with separate CKs for the: MDS Container, CMAs for managing the VSs, CMA for managing the VSX Gateway. The CMAs created within the VSX- CMA license can manage only Virtual Systems. If management of VPN-1 gateways/clusters is required, MDS Container and CMA licenses need to be purchased Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 11
12 SKU Prefix Name Description Additive CPPR-VSX-CMA- HA Virtual Systems Extension - CMA Bundles (Secondary VSX-CMA) CPGX-VFF FireWall-1 GX Module FireWall-1 GX combines 's patented Stateful Inspection technology with full GPRS Tunneling Protocol (GTP) awareness. FireWall-1 GX inspects all GTP tunnel fields in the context of both the packet and the tunnel. FireWall-1 GX secures the GPRS backbone CPGX-HVFF CPGX-GMC FireWall-1 GX Secondary Module FireWall-1 GX SmartCenter when connecting to roaming partner and roaming exchanges (GRX). FireWall-1 GX also protects distributed GPRS backbone environments where operators have connections to Gateway GPRS Support Nodes (GGSNs) outside of their own network or to GGSNs that are geographically dispersed FireWall-1 GX SmartCenter provides a rich set of GTP-specific log information, including granular logging details on tunnel creation, updates and deletions. Beyond logging, a wide range of security alerting options exists as well CPPR-GX-CMA FireWall-1 GX CMA A Provider-1 Customer SmartCenter Add-on for managing an unlimited number of FireWall-1 GX Modules. Includes the Pro Add-on features for this CMA. SMP SMP-OD Portal Portal On Demand The Portal (SMP) is a SmartCenter solution for service providers that deliver Internet security to consumers and small businesses. The SMP enables service providers to create flexible service categories and to centrally manage tens of thousands of subscribers. Based on SMP, SMP On-Demand is a fully- hosted solution offering managed firewall and intrusion prevention services, always-on antivirus protection, VPN connectivity, and other value-added services SMP Web Filtering An OPSEC plug-in that allows Service Providers utilizing SMP to provide centrally managed URL filtering services to Safe@ appliances. Service based on SurfControl's Web Filter UFP product. of Strings This description is valid for VSX 2.0 and higher. Users with previous versions were credited with separate CKs for the: MDS Container, CMAs for managing the VSs, CMA for managing the VSX Gateway. No 1 Gateway Licensed for an unlimited number of gateways Licensed for an unlimited number of gateways No 1 SmartCenter No 1 CMA Level No 1 No 1 Yes 1 Licensed for an unlimited number of gateways Licensed for an unlimited number of gateways Licensed per number of appliances. Not licensable through UserCenter. Licensed per number of appliances. Not licensable through UserCenter. Licensed per user. Not licensable through UserCenter Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 12
13 Home Office/Small Business Solutions of Strings A fully-integrated wireless firewall, intrusion prevention, VPN and antivirus gateway. Incorporating an b/g access point. Employing s Firewall-1 and VPN-1 technology. No N/A SKU Prefix Name Description Additive CPSB-1000NW CPSB-1000N ST-CPSB ST-SDTS-CPSB Safe@Office 1000N wireless appliance Safe@Office 1000N appliance Annual Safe@Office Support and Subscription Safe@Office Annual Support and Advanced Services A fully-integrated intrusion prevention, VPN and antivirus gateway. Incorporating an b/g access point. Employing s Firewall-1 and VPN-1 technology. No N/A Support and Subscription For Safe@Office appliances only. Includes the following: a) and firmware updates, b) , web and chat support, c) Telephone support in English from 8:00 AM to 5 PM US time and d) Advanced Replacment. Includes the following: Gateway antivirus updates Advanced replacement URL filtering based on category classification of web-sites Messaging and Anti Spam Updates and firmware updates , web and chat support Extended Hardware Warranty Dynamic DNS Monthly security reports No N/A Not licensable through UC. The product comes with a key preinstalled Not licensable through UC. The product comes with a key preinstalled Licensed per number of concurrent users Licensed per number of concurrent users The appliance MAC address is required to purchase the Support Plan. Prices are Annual fees. No N/A The appliance MAC address is required to purchase the Support and Services Plan. Prices are Annual fees Software Technologies Ltd. All rights reserved. Classification: [Unrestricted] For everyone P. 13
LICENSE GUIDE. Software Blades products. Number of Strings. SKU Prefix Name Description Additive
 LICENSE GUIDE Software Blades products SKU Prefix Name Description Additive CPAP-SG5075 CPAP-SG9075 CPAP-SG11065 CPAP-SG11075 CPAP-SG11085 CPAP-IP2455 CPAP-IP1285 CPAP-IP695 CPAP-IP565 CPAP-IP395 CPAP-IP295
LICENSE GUIDE Software Blades products SKU Prefix Name Description Additive CPAP-SG5075 CPAP-SG9075 CPAP-SG11065 CPAP-SG11075 CPAP-SG11085 CPAP-IP2455 CPAP-IP1285 CPAP-IP695 CPAP-IP565 CPAP-IP395 CPAP-IP295
CHECK POINT. Software Blade Architecture
 CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
CHECK POINT Software Blade Architecture 2 softwareblades from Check Point Today s Security Challenge Protecting enterprises against today s constantly evolving threat environment has never been more challenging.
CHECK POINT. Software Blade Architecture. Secure. Flexible. Simple.
 CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
CHECK POINT Software Blade Architecture Secure. Flexible. Simple. softwareblades from Check Point Today s Security Challenge Protecting networks against today s constantly evolving threat environment has
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Contents Introduction 3 Check Point Software Blade architecture overview 3 What is a Software
Check Point. Software Blade Architecture
 Check Point Software Blade Architecture TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity
Check Point Software Blade Architecture TODAY S SECURITY CHALLENGE Protecting enterprises against today s constantly evolving threat environment has never been more challenging. Infrastructure, connectivity
Securing Virtualization with Check Point and Consolidation with Virtualized Security
 Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
Securing Virtualization with Check Point and Consolidation with Virtualized Security consolidate security gateways with full power of Software Blades with Check Point Virtual Systems (VSX) secure virtualized
CHECK POINT TOTAL SECURITY APPLIANCES. Flexible Deployment. Centralized Management.
 CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
CHECK POINT TOTAL SECURITY APPLIANCES Flexible Deployment. Centralized Management. Check Point appliances deliver a powerful turnkey solution for deploying Check Point awardwinning software solutions to
Check Point Software Blade Architecture. Achieving the right balance between security protection and investment
 Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
Check Point Software Blade Architecture Achieving the right balance between security protection and investment Check Point Software Blade Architecture Contents Introduction 3 Check Point Software Blade
Infrastruktur Sicherheit mit Checkpoint
 Infrastruktur Sicherheit mit Checkpoint Neue Module Markus Kohlmeier Teamleiter Internet und Security Services Übersicht Checkpoint Releases Firewall 1 4.1, release 2000 Firewall 1 NG, FP1, FP2 und FP3,
Infrastruktur Sicherheit mit Checkpoint Neue Module Markus Kohlmeier Teamleiter Internet und Security Services Übersicht Checkpoint Releases Firewall 1 4.1, release 2000 Firewall 1 NG, FP1, FP2 und FP3,
The Evolution of IPS. Intrusion Prevention (Protection) Systems aren't what they used to be
 The Evolution of IPS Intrusion Prevention (Protection) Systems aren't what they used to be The Evolution of IPS Contents Background 3 Past Case for Standalone IPS 3 Organizational Control 3 Best-of-Breed
The Evolution of IPS Intrusion Prevention (Protection) Systems aren't what they used to be The Evolution of IPS Contents Background 3 Past Case for Standalone IPS 3 Organizational Control 3 Best-of-Breed
How to Implement an Integrated GRC Architecture
 How to Implement an Integrated GRC Architecture Companies that select individual solutions for each regulatory challenge they face will spend 10 times more on IT portion of compliance projects than companies
How to Implement an Integrated GRC Architecture Companies that select individual solutions for each regulatory challenge they face will spend 10 times more on IT portion of compliance projects than companies
IREBOX X. Firebox X Family of Security Products. Comprehensive Unified Threat Management Solutions That Scale With Your Business
 IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
IREBOX X IREBOX X Firebox X Family of Security Products Comprehensive Unified Threat Management Solutions That Scale With Your Business Family of Security Products Comprehensive unified threat management
Cisco Small Business ISA500 Series Integrated Security Appliances
 Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Q & A Cisco Small Business ISA500 Series Integrated Security Appliances Q. What is the Cisco Small Business ISA500 Series Integrated Security Appliance? A. The Cisco Small Business ISA500 Series Integrated
Check Point taps the power of virtualization to simplify security for private clouds
 Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Datasheet: Check Point Virtual Systems Check Point taps the power of virtualization to simplify security for private clouds Looking for ways to reduce complexity and simplify network security in your private
Security Administration R77
 Security Administration R77 Validate your skills on the GAiA operating system Check Point Security Administration R77 provides an understanding of the basic concepts and skills necessary to configure Check
Security Administration R77 Validate your skills on the GAiA operating system Check Point Security Administration R77 provides an understanding of the basic concepts and skills necessary to configure Check
Check Point Whitepaper. Enterprise IPv6 Transition Technical Whitepaper
 Check Point Whitepaper Enterprise IPv6 Transition Technical Whitepaper Contents Introduction 3 Transition Mechanisms 3 Dual Stack 4 Tunneling 4 Translation 7 Recommendations 8 Transition Security Considerations
Check Point Whitepaper Enterprise IPv6 Transition Technical Whitepaper Contents Introduction 3 Transition Mechanisms 3 Dual Stack 4 Tunneling 4 Translation 7 Recommendations 8 Transition Security Considerations
The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels
 The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels The Power-1 Performance Architecture Contents Introduction 3 A delicate balance: Performance
The Power-1 Performance Architecture: Delivering Application-layer Security at Data Center Performance Levels The Power-1 Performance Architecture Contents Introduction 3 A delicate balance: Performance
Endpoint Security Considerations for Achieving PCI Compliance
 Endpoint Security Considerations for Achieving PCI Compliance Contents PCI Requirements and Endpoint Security 3 Overview of the PCI Data Security Standard 3 Developing a PCI Compliance Plan 4 Endpoint
Endpoint Security Considerations for Achieving PCI Compliance Contents PCI Requirements and Endpoint Security 3 Overview of the PCI Data Security Standard 3 Developing a PCI Compliance Plan 4 Endpoint
Check Point Safe@Office 500 UTM Frequently Asked Questions
 For internal use only Check Point Safe@Office 500 UTM Frequently Asked Questions Business Related Questions What are Safe@Office appliances? Designed specifically to meet the needs of small businesses,
For internal use only Check Point Safe@Office 500 UTM Frequently Asked Questions Business Related Questions What are Safe@Office appliances? Designed specifically to meet the needs of small businesses,
Appliance Comparison Chart
 202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
202 Appliances 2200 4200 4400 4600 4800 Small-Office Enterprise Grade Production Performance (Security Benchmark) Security 4 4 223 374 623 Firewall (Gbps).4.4 2.2 3.4 5.8 Firewall and IPS (Mbps) 50 50
Check Point Whitepaper. Check Point Abra: A Virtual Secure Workspace Technical Whitepaper
 Check Point Whitepaper Check Point Abra: A Virtual Secure Workspace Technical Whitepaper Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile Workforce 3 Abra Provides the Solution 4
Check Point Whitepaper Check Point Abra: A Virtual Secure Workspace Technical Whitepaper Contents An Increasingly Mobile World 3 Threats and Dangers of a Mobile Workforce 3 Abra Provides the Solution 4
Secure Cloud-Ready Data Centers Juniper Networks
 Secure Cloud-Ready Data Centers Juniper Networks JUNIPER SECURITY LEADERSHIP A $1B BUSINESS Market Leadership Data Center with High- End Firewall #1 at 42% Secure Mobility with SSL VPN #1 at 25% Security
Secure Cloud-Ready Data Centers Juniper Networks JUNIPER SECURITY LEADERSHIP A $1B BUSINESS Market Leadership Data Center with High- End Firewall #1 at 42% Secure Mobility with SSL VPN #1 at 25% Security
Checkpoint 156-815. 156-815 Check Point Provider-1 NGX (v4) Practice Test. Version 2.1
 Checkpoint 156-815 156-815 Check Point Provider-1 NGX (v4) Practice Test Version 2.1 QUESTION NO: 1 Two CMAs can be created for a single Customer, for High availability (HA). Which of these statements
Checkpoint 156-815 156-815 Check Point Provider-1 NGX (v4) Practice Test Version 2.1 QUESTION NO: 1 Two CMAs can be created for a single Customer, for High availability (HA). Which of these statements
Cisco ASA 5500 Series Content Security Edition for the Enterprise
 Cisco ASA 5500 Series Content Security Edition for the Enterprise Viruses and other malicious code can overwhelm your IT resources, disrupting business operations and impacting business transactions. The
Cisco ASA 5500 Series Content Security Edition for the Enterprise Viruses and other malicious code can overwhelm your IT resources, disrupting business operations and impacting business transactions. The
Unified Threat Management, Managed Security, and the Cloud Services Model
 Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Unified Threat Management, Managed Security, and the Cloud Services Model Kurtis E. Minder CISSP Global Account Manager - Service Provider Group Fortinet, Inc. Introduction Kurtis E. Minder, Technical
Cisco ASA 5500 Series Business Edition
 Cisco ASA 5500 Series Business Edition Cisco ASA 5500 Series Business Edition Provides an All-in-One Security Solution The Cisco ASA 5500 Series Business Edition is an enterprise-strength comprehensive
Cisco ASA 5500 Series Business Edition Cisco ASA 5500 Series Business Edition Provides an All-in-One Security Solution The Cisco ASA 5500 Series Business Edition is an enterprise-strength comprehensive
Multi-Domain Security Management
 Multi-Domain Security Management R77 Versions Administration Guide 20 May 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Multi-Domain Security Management R77 Versions Administration Guide 20 May 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Advantages of Managed Security Services
 Advantages of Managed Security Services Cloud services via MPLS networks for high security at low cost Get Started Now: 877.611.6342 to learn more. www.megapath.com Executive Summary Protecting Your Network
Advantages of Managed Security Services Cloud services via MPLS networks for high security at low cost Get Started Now: 877.611.6342 to learn more. www.megapath.com Executive Summary Protecting Your Network
A Getting Started Guide: What Every Small Business Needs To Know About Internet Security
 A Getting Started Guide: What Every Small Business Needs To Know About Internet Security In This Document 1 Overview: Internet Security In Small Businesses 2 Internet Access New Business Opportunities
A Getting Started Guide: What Every Small Business Needs To Know About Internet Security In This Document 1 Overview: Internet Security In Small Businesses 2 Internet Access New Business Opportunities
Check Point 12200 Appliance
 Datasheet: Check Point 2200 Appliance 2200 Datacenter-grade security appliance Check Point 2200 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 2200 Appliance 2200 Datacenter-grade security appliance Check Point 2200 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Check Point Positions
 Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
Check Point Positions - Gartner Magic Quadrants - IDC Market Share Research 2012 Dean J. Whitehair Analyst Relations October 2012 Version 9.0 Updated 10/17/2012 2012 Check Point Software Technologies Ltd.
How to Get NAC Up-and-Running in One Hour. For Check Point Firewall or Endpoint Security Administrators
 How to Get NAC Up-and-Running in One Hour For Check Point Firewall or Endpoint Security Administrators Contents Introduction 3 Defining an Organization s Requirements for NAC 3 Two Paths to NAC Port vs.
How to Get NAC Up-and-Running in One Hour For Check Point Firewall or Endpoint Security Administrators Contents Introduction 3 Defining an Organization s Requirements for NAC 3 Two Paths to NAC Port vs.
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance Check Point 4800 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance Check Point 4800 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Cisco ASA 5500 Series Anti-X Edition for the Enterprise
 Solution Overview Cisco ASA 5500 Series Anti-X Edition for the Enterprise Viruses and other malicious code can overwhelm your IT resources disrupting business operations and impacting business transactions.
Solution Overview Cisco ASA 5500 Series Anti-X Edition for the Enterprise Viruses and other malicious code can overwhelm your IT resources disrupting business operations and impacting business transactions.
Solving the Performance Hurdle for Integrated IPS
 Solving the Performance Hurdle for Integrated IPS New Check Point Technologies Enable a Full-Function, Integrated Intrusion Prevention System without Compromise to Performance or Security Solving the Performance
Solving the Performance Hurdle for Integrated IPS New Check Point Technologies Enable a Full-Function, Integrated Intrusion Prevention System without Compromise to Performance or Security Solving the Performance
Astaro Gateway Software Applications
 Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
Astaro Overview Astaro Products - Astaro Security Gateway - Astaro Web Gateway - Astaro Mail Gateway - Astaro Command Center - Astaro Report Manager Astaro Gateway Software Applications - Network Security
The Seven Key Factors for Internet Security TCO
 The Seven Key Factors for Internet Security TCO Executive Summary Total Cost of Ownership, or TCO, of any information technology deployment consists of more than simply the direct costs of acquisition
The Seven Key Factors for Internet Security TCO Executive Summary Total Cost of Ownership, or TCO, of any information technology deployment consists of more than simply the direct costs of acquisition
Check Point 3D Security
 Check Point 3D Security Combining Policies, People and Enforcement for Unbeatable Protection John Vecchi Head of WW Product Marketing 2011 Check Point Software Technologies Ltd. [Unrestricted] For everyone
Check Point 3D Security Combining Policies, People and Enforcement for Unbeatable Protection John Vecchi Head of WW Product Marketing 2011 Check Point Software Technologies Ltd. [Unrestricted] For everyone
R75. Installation and Upgrade Guide
 R75 Installation and Upgrade Guide 24 March 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under
R75 Installation and Upgrade Guide 24 March 2011 2011 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright and distributed under
Next Gen Firewall and UTM Buyers Guide
 Next Gen Firewall and UTM Buyers Guide Implementing and managing a network protected by point solutions is far from simple. But complete protection doesn t have to be complicated. This buyers guide explains
Next Gen Firewall and UTM Buyers Guide Implementing and managing a network protected by point solutions is far from simple. But complete protection doesn t have to be complicated. This buyers guide explains
WatchGuard Technologies. 2011 WatchGuard Technologies
 WatchGuard Technologies 2011 WatchGuard Technologies About WatchGuard Founded in 1996 - privately held Firewall appliance pioneers Headquartered in Seattle, WA with 400+ employees globally More than 600,000
WatchGuard Technologies 2011 WatchGuard Technologies About WatchGuard Founded in 1996 - privately held Firewall appliance pioneers Headquartered in Seattle, WA with 400+ employees globally More than 600,000
SA Series SSL VPN Virtual Appliances
 SA Series SSL VPN Virtual Appliances Data Sheet Published Date July 2015 Product Overview The world s mobile worker population passed the 1 billion mark in 2010 and will grow to more than 1.3 billion by
SA Series SSL VPN Virtual Appliances Data Sheet Published Date July 2015 Product Overview The world s mobile worker population passed the 1 billion mark in 2010 and will grow to more than 1.3 billion by
V1.4. Spambrella Email Continuity SaaS. August 2
 V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
Endpoint Security VPN for Mac
 Security VPN for Mac E75 Release Notes 8 April 2012 Classification: [Protected] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Security VPN for Mac E75 Release Notes 8 April 2012 Classification: [Protected] 2012 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by
Appliance Comparison Chart
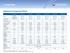 Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Appliance Comparison Chart Models Edge 10 270 570 1070 2070 070 Edge X, Edge W, Edge X ADSL, Edge W ADSL 12 16 272 276 572 576 107 1076 207 2076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65,
Simple security is better security Or: How complexity became the biggest security threat
 Simple security is better security Or: How complexity became the biggest security threat Christoph Litzbach, Pre-Sales Engineer NSG 1 What do they have in common? DATA BREACH 2 Security is HARD! Components
Simple security is better security Or: How complexity became the biggest security threat Christoph Litzbach, Pre-Sales Engineer NSG 1 What do they have in common? DATA BREACH 2 Security is HARD! Components
Check Point Security Administrator R70
 Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
Page 1 of 6 Check Point Security Administrator R70 Check Point Security Administration R70 Length Prerequisites 5 days* (recommended) Basic networking knowledge, knowledge of Windows Server and/or UNIX,
SonicWALL Clean VPN. Protect applications with granular access control based on user identity and device identity/integrity
 SSL-VPN Combined With Network Security Introducing A popular feature of the SonicWALL Aventail SSL VPN appliances is called End Point Control (EPC). This allows the administrator to define specific criteria
SSL-VPN Combined With Network Security Introducing A popular feature of the SonicWALL Aventail SSL VPN appliances is called End Point Control (EPC). This allows the administrator to define specific criteria
Move over, TMG! Replacing TMG with Sophos UTM
 Move over, TMG! Replacing TMG with Sophos UTM Christoph Litzbach, Pre-Sales Engineer NSG 39 Key Features of TMG HTTP Antivirus/spyware URL Filtering HTTPS forward inspection Web Caching Role based access
Move over, TMG! Replacing TMG with Sophos UTM Christoph Litzbach, Pre-Sales Engineer NSG 39 Key Features of TMG HTTP Antivirus/spyware URL Filtering HTTPS forward inspection Web Caching Role based access
How To Protect Your Network From Attack From A Virus And Attack From Your Network (D-Link)
 NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering
NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering
Symantec Brightmail Gateway Real-time protection backed by the largest investment in security infrastructure
 Real-time protection backed by the largest investment in security infrastructure Overview delivers inbound and outbound messaging security, with effective and accurate real-time antispam and antivirus
Real-time protection backed by the largest investment in security infrastructure Overview delivers inbound and outbound messaging security, with effective and accurate real-time antispam and antivirus
Cisco ASA 5500 Series Content Security Edition for the Enterprise
 Cisco ASA 5500 Series Content Security Edition for the Enterprise Viruses and other malicious code can overwhelm your IT resources disrupting business operations and impacting business transactions. The
Cisco ASA 5500 Series Content Security Edition for the Enterprise Viruses and other malicious code can overwhelm your IT resources disrupting business operations and impacting business transactions. The
Secure Remote Access Solutions Balancing security and remote access Bob Hicks, Rockwell Automation
 Secure Remote Access Solutions Balancing security and remote access Bob Hicks, Rockwell Automation Rev 5058-CO900C Agenda Control System Network Security Defence in Depth Secure Remote Access Examples
Secure Remote Access Solutions Balancing security and remote access Bob Hicks, Rockwell Automation Rev 5058-CO900C Agenda Control System Network Security Defence in Depth Secure Remote Access Examples
Leverage IPS to Make Patch Tuesday Just Another Day
 Leverage IPS to Make Patch Tuesday Just Another Day Contents Introduction 3 Evolution of a Practice 3 Weaknesses of the Model 4 Lack of timeliness 4 Inherent predictability 4 Painful disruptions 5 A Better
Leverage IPS to Make Patch Tuesday Just Another Day Contents Introduction 3 Evolution of a Practice 3 Weaknesses of the Model 4 Lack of timeliness 4 Inherent predictability 4 Painful disruptions 5 A Better
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Virtualized Security: The Next Generation of Consolidation
 Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Virtualization. Consolidation. Simplification. Choice. WHITE PAPER Virtualized Security: The Next Generation of Consolidation Virtualized Security: The Next Generation of Consolidation As we approach the
Clavister InSight TM. Protecting Values
 Clavister InSight TM Clavister SSP Security Services Platform firewall VPN termination intrusion prevention anti-virus anti-spam content filtering traffic shaping authentication Protecting Values & Enterprise-wide
Clavister InSight TM Clavister SSP Security Services Platform firewall VPN termination intrusion prevention anti-virus anti-spam content filtering traffic shaping authentication Protecting Values & Enterprise-wide
Providing Secure IT Management & Partnering Solution for Bendigo South East College
 Providing Secure IT Management & Partnering Solution for Bendigo South East College Why did Bendigo South East College engage alltasksit & DELL? BSEC is in the midst of school population growth in 2015,
Providing Secure IT Management & Partnering Solution for Bendigo South East College Why did Bendigo South East College engage alltasksit & DELL? BSEC is in the midst of school population growth in 2015,
How UTM-1, DLP and Application Control Protect your IT environment
 How UTM-1, DLP and Application Control Protect your IT environment Louis Cheung Security Consultant CISSP, CISA Dec 2010 2010 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups
How UTM-1, DLP and Application Control Protect your IT environment Louis Cheung Security Consultant CISSP, CISA Dec 2010 2010 Check Point Software Technologies Ltd. [Restricted] ONLY for designated groups
Check Point 13500 Appliance
 Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Datasheet: Check Point 3500 Appliance 3500 Blazing fast data center cyber-security Check Point 3500 Appliance YOUR CHALLENGE Large data centers have uncompromising needs for performance, uptime and scalability.
Check Point 4800 Appliance
 Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
Datasheet: Check Point 4800 Appliance 4800 Enterprise-grade security appliance (623 SPU/Gbps) great multi-blade performance and 0Gb Fiber connectivity options Check Point 4800 Appliance Today the enterprise
ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239
 ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239 Check Point Firewall Software and Management Software I. Description of the Item Up gradation, installation and commissioning of Checkpoint security gateway
ANNEXURE TO TENDER NO. MRPU/IGCAR/COMP/5239 Check Point Firewall Software and Management Software I. Description of the Item Up gradation, installation and commissioning of Checkpoint security gateway
Remote Access Clients for Windows
 Remote Access Clients for Windows E80.60 Release Notes 3 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
Remote Access Clients for Windows E80.60 Release Notes 3 December 2014 Classification: [Protected] 2014 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation
IBM Internet Security Systems
 IBM Global Services IBM Internet Security Systems Norberto Gazzoni Italy Channel Manager [email protected] +39 347 3499617 IBM Internet Security Systems Ahead of the threat. 2006 IBM Corporation
IBM Global Services IBM Internet Security Systems Norberto Gazzoni Italy Channel Manager [email protected] +39 347 3499617 IBM Internet Security Systems Ahead of the threat. 2006 IBM Corporation
Check Point QoS. Administration Guide Version NGX R65
 Check Point QoS Administration Guide Version NGX R65 700726 January 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point QoS Administration Guide Version NGX R65 700726 January 2007 2003-2007 Check Point Software Technologies Ltd. All rights reserved. This product and related documentation are protected by copyright
Check Point 21400 Appliance
 Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance Check Point 2400 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Datasheet: Check Point 2400 Appliance 2400 Datacenter-grade security appliance Check Point 2400 Appliance Today s firewall is a security device presented with an ever-increasing number of sophisticated
Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security
 Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security White Paper September 2003 Abstract The network security landscape has changed dramatically over the past several years. Until
Total Cost of Ownership: Benefits of Comprehensive, Real-Time Gateway Security White Paper September 2003 Abstract The network security landscape has changed dramatically over the past several years. Until
Check Point 12400 Appliance
 Datasheet: Check Point 400 Appliance 400 Datacenter-grade security appliance Check Point 400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an ever-increasing
Datasheet: Check Point 400 Appliance 400 Datacenter-grade security appliance Check Point 400 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an ever-increasing
Network protection and UTM Buyers Guide
 Network protection and UTM Buyers Guide Using a UTM solution for your network protection used to be a compromise while you gained in resource savings and ease of use, there was a payoff in terms of protection
Network protection and UTM Buyers Guide Using a UTM solution for your network protection used to be a compromise while you gained in resource savings and ease of use, there was a payoff in terms of protection
Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET
 Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET ELITE S NEXT GENERATION MANAGED SECURITY SERVICES Security risks to business information systems are expanding at a rapid rate; often,
Product Factsheet MANAGED SECURITY SERVICES - FIREWALLS - FACT SHEET ELITE S NEXT GENERATION MANAGED SECURITY SERVICES Security risks to business information systems are expanding at a rapid rate; often,
Introduction to Endpoint Security
 Chapter Introduction to Endpoint Security 1 This chapter provides an overview of Endpoint Security features and concepts. Planning security policies is covered based on enterprise requirements and user
Chapter Introduction to Endpoint Security 1 This chapter provides an overview of Endpoint Security features and concepts. Planning security policies is covered based on enterprise requirements and user
The Cisco ASA 5500 as a Superior Firewall Solution
 The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
The Cisco ASA 5500 as a Superior Firewall Solution The Cisco ASA 5500 Series Adaptive Security Appliance provides leading-edge firewall capabilities and expands to support other security services. Firewalls
Cisco ASA 5500 Series Firewall Edition for the Enterprise
 Solution Overview Cisco ASA 5500 Series Firewall Edition for the Enterprise Threats to today s networks continue to grow, with attacks coming from both outside and within corporate networks. These threats
Solution Overview Cisco ASA 5500 Series Firewall Edition for the Enterprise Threats to today s networks continue to grow, with attacks coming from both outside and within corporate networks. These threats
Cisco ASA 5500 Series Firewall Edition for the Enterprise
 Взято с сайта www.wit.ru Solution Overview Cisco ASA 5500 Series Firewall Edition for the Enterprise Threats to today s networks continue to grow, with attacks coming from both outside and within corporate
Взято с сайта www.wit.ru Solution Overview Cisco ASA 5500 Series Firewall Edition for the Enterprise Threats to today s networks continue to grow, with attacks coming from both outside and within corporate
Check Point Appliances
 Check Point Appliances Table of Contents Introduction 3 Check Point GAiA - a Unified Secure Operating System 4 About SecurityPower 5 Next Generation Security Solutions 6 600 Appliances 7 1100 Appliances
Check Point Appliances Table of Contents Introduction 3 Check Point GAiA - a Unified Secure Operating System 4 About SecurityPower 5 Next Generation Security Solutions 6 600 Appliances 7 1100 Appliances
How NETGEAR ProSecure UTM Helps Small Businesses Meet PCI Requirements
 How NETGEAR ProSecure UTM Helps Small Businesses Meet PCI Requirements I n t r o d u c t i o n The Payment Card Industry Data Security Standard (PCI DSS) was developed in 2004 by the PCI Security Standards
How NETGEAR ProSecure UTM Helps Small Businesses Meet PCI Requirements I n t r o d u c t i o n The Payment Card Industry Data Security Standard (PCI DSS) was developed in 2004 by the PCI Security Standards
Check Point 12600 Appliance
 Datasheet: Check Point 2600 Appliance 2600 Datacenter-grade security appliance Check Point 2600 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Datasheet: Check Point 2600 Appliance 2600 Datacenter-grade security appliance Check Point 2600 Appliance Today the enterprise gateway is more than a firewall. It is a security device presented with an
Achieving PCI-Compliance through Cyberoam
 White paper Achieving PCI-Compliance through Cyberoam The Payment Card Industry (PCI) Data Security Standard (DSS) aims to assure cardholders that their card details are safe and secure when their debit
White paper Achieving PCI-Compliance through Cyberoam The Payment Card Industry (PCI) Data Security Standard (DSS) aims to assure cardholders that their card details are safe and secure when their debit
NetDefend Firewall UTM Services
 NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering (WCF) for superior
NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content Filtering (WCF) for superior
Simplify Your Network Security with All-In-One Unified Threat Management
 Singtel Business Product Factsheet Brochure Managed Defense Unified Services Management Simplify Your Network Security with All-In-One Unified Management Singtel Managed Unified Management (UTM) Services,
Singtel Business Product Factsheet Brochure Managed Defense Unified Services Management Simplify Your Network Security with All-In-One Unified Management Singtel Managed Unified Management (UTM) Services,
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8
 WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
WHAT S NEW IN WEBSENSE TRITON RELEASE 7.8 Overview Global organizations are constantly battling with advanced persistent threats (APTs) and targeted attacks focused on extracting intellectual property
Network Security. Protective and Dependable. 52 Network Security. UTM Content Security Gateway CS-2000
 Network Security Protective and Dependable With the growth of the Internet threats, network security becomes the fundamental concerns of family network and enterprise network. To enhance your business
Network Security Protective and Dependable With the growth of the Internet threats, network security becomes the fundamental concerns of family network and enterprise network. To enhance your business
Check Point Corporate Logo Usage Guidelines
 Check Point Corporate Logo Usage Guidelines 1. The Check Point Logo The Check Point logo is the most visible and recognizable symbol of our brand. It should appear on every piece of communication from
Check Point Corporate Logo Usage Guidelines 1. The Check Point Logo The Check Point logo is the most visible and recognizable symbol of our brand. It should appear on every piece of communication from
Websense Web Security Solutions. Websense Web Security Gateway Websense Web Security Websense Web Filter Websense Express Websense Hosted Web Security
 Web Security Gateway Web Security Web Filter Express Hosted Web Security Web Security Solutions The Approach In the past, most Web content was static and predictable. But today s reality is that Web content
Web Security Gateway Web Security Web Filter Express Hosted Web Security Web Security Solutions The Approach In the past, most Web content was static and predictable. But today s reality is that Web content
