Hardware Testing and Security Requirements in the Nano Era
|
|
|
- Victoria Melton
- 3 years ago
- Views:
Transcription
1 Secure Hardware in the Nano Era: Some New Directions Swarup Bhunia T. and A. Schroeder Associate Professor Electrical Engineering and Computer Science March ISQED SoC Security Issues & Protection D-f-S Solutions Spans all stage es in IC life cyc cle Trojan-resistant design; improved detectability * Hardware Obfuscation # ; Protect IP Eval. Copy^, PUF $ SCA resistant Design ** ; Prevent scan-based attack *** * Wang et al., DFT, 2012, * Narasimhan et al., Tcomp 2012, * Chakraborty et al., CHES 2009, ^Narasimhan et al., D&T, 2012 $ Krishna et al., CHES 2011; $ Zheng et al. ASP-DAC 2013, $ Zheng et al, DAC 2013, *** Paul et al, VTS 2007 ** Wang et al., DAC 2013, # Chakraborty et al. ICCAD 2008 March ISQED
2 Protection o against IP Piracy: Hardware Obfuscation Primarily protects the IP owner! March ISQED What are the challenges? Taxonomy of hardware IP security issues Hardware Trojan Attacks! March ISQED
3 Basic Idea: Security Through Obfuscation Obfuscate the design functionally and structurally Achieved by modifying the state transition function Normal behavior is enabled only upon application of a key! Prevents illegal l usage of IPs! Chakraborty & Bhunia, ICCAD 2008 Chakraborty & Bhunia, TCAD 2009 March ISQED Results: Trojan Detectability 4 Trigger Signals = 2 Tri igger Sig gnals = 21% average improvement in Trojan coverage Overhead: ~11% area, 11% power overhead at iso-delay Average run-time: ~1200 seconds (90% of total run-time taken by Tetramax) Chakraborty & Bhunia, ICCAD 2009 March ISQED
4 From the SoC designer s s perspective, integrity of 3 rd Party IPs need to be checked! IP Vendor Hardware IPs CPU Memory Bus DSP Trojan Backdoor IP Trus st Va alidat tion SoC Design House IP Trust Validation SoC Integration SoC Design Convergence Foundry SoC DSP CPU Bus Memory March ISQED Anti-Counterfeiting Design Solutions March ISQED
5 Threats & Vulnerabilities Globally ll distributed ib t d semiconductor business model - Ample sneak paths to insert counterfeit chips Semiconductor Business Model Ways for Counterfeiting ICs Two Broad Categories: - Recycled/Remarked: selling of used/aged chips as new - Cloned New Chips: IP piracy, reverse-eng, overproduction March ISQED Examples of Physical Unclonable Functions (PUFs) RO PUF -Gassend et al, 2002, Suh et al, 2007 Arbiter PUF -Lee et al, 2004 PUF using on-chip structure! Butterfly PUF -Kumar et al, 2008 SRAM PUF -Guajardo et al, Holcomb et al, 2007 Can we generate robust strong PUF using on-chip structure? March ISQED
6 PUFs Using On-Chip Structure Good for legacy chips MECCA PUF -Krishna et al, CHES 2011 RESP PUF -Zheng et al, DAC 2013 Scan PUF -Zheng et al, ASP-DAC 2013 March ISQED Active Defense against IC Cloning A chip locking approach with antifuses (AF) on I/O port - AF is an OTP, normally open switch 1 (R off ~ 100M 1Gῼ) - AF program on correct key input (stored in on-chip NVM) - Active defense against recycling/cloning g Basak et al., VTS S, 2014 Tamper- -evident S eal Test path provided for each locked pin through e-fuse 2 IC/Device family specific key 1. W. T. Li et al., EDL, N. Robson et al., CICC, 2007 March ISQED
7 Hardware Trojan Attacks: A Problem from Hell * Bhunia et al. PIEEE, 2014 * Michael Hayden March ISQED HW Trojan Attacks: in the News March ISQED
8 HW Trojan Threats Most vulnerable stages! Modern SoC Design and Manufacturing Flow* * March ISQED HW Trojan Examples/Models Comb Trojan Example Seq Trojan Example MOLES * : Info Leakage Trojan Comb Trojan model Seq. Trojan Model *Lin et al, ICCAD 2009 System level view March ISQED
9 Introduction to Trojan Detection Taxonomy of Existing Trojan Detection Approaches Side-channel approaches do not require triggering g the Trojan to observe its impact at primary input nodes. March ISQED Methodology Multiple-parameter Approach for Trojan Detection Due to process variations, it is extremely challenging to detect the Trojan by considering F max or I DDT individually. March ISQED
10 Methodology Multiple-parameter Approach for Trojan Detection Due to process variations, it is extremely challenging to detect the Trojan by considering F max or I DDT alone. c880 from ISCAS-85 benchmark suite with 8-bit ALU circuit Trojan March ISQED Methodology Multiple-parameter Approach for Trojan Detection Consider the intrinsic relationship between I DDT and F t th I F F max together, I DDT vs. F max c880 (8-bit ALU) from ISCAS-85 benchmark suite with 8-bit comparator Trojan March ISQED
11 Statistical Approach Feasible Trojan search space is inordinately large! Exhaustive enumeration impossible Deterministic test generation computationally infeasible A Statistical Approach for Trojan Detection Finds the rare events in the circuit Generates test vectors to trigger each trigger node multiple times (N times) Provides high confidence about detecting arbitrary Trojans! Chakraborty et al, CHES 2009 March ISQED Circuit Example (i) Combinational Trojan (ii) Sequential Trojan Trojan Trigger Condition: (i) a=0, b=1, c=1 (ii) a=1, b=0 Generate vectors to satisfy each of these conditions multiple utpe( (N)times Probability of Trojan activation increases with N The concept is similar to N-Detect Tests* * I. Pomeranz and S.M. Reddy, 2004 March ISQED
12 Self-Referencing: Golden-Free Trojan & Counterfeit Detection courtesy: Intel Image c DAC Zhe eng et al, Du et al, CHES Supported by DARPA March ISQED Temporal Self-Referencing Seq. ckts have diff. switching currents based on both input & state conditions Uncorrelated switching in time is attributed to a seq. Trojan! Seq. Trojans impose greater threats! ALU circuit with Trojan DLX circuit w/o & w/ Trojan FSM Noise th. is obtained from experiments w/ any chip! No golden chip is required!!! Narasimhan et al. HOST 2011 March ISQED
13 Integrative Measures Design for Security Trust Validation Security Monitoring SM Processor Secure by design, test and run-time monitoring! Chakraborty, Narasimhan and Bhunia, Hardware IP protection, US Patent, 2013 March ISQED Infrastructure IP for Security: A Scalable Solution to SoC Security & Debug Wang et al., IEEE Tcomp, To Appear New SRC grant March ISQED
14 Infrastructure IP for SoC Security (IIPS) IIPS is a centralized IP block for various security protections Major Features of IIPS 1. Ease of integration; plug-n-play play using IEEE 1500 Standard 2. Reusable IP 3. Configurable 4. Functionally scalable & flexible 5. Minimal performance/power/area overhead 6. Does not affect IP level design & IP integration in SoC 7. Can be merged with other (e.g. test / debug) infrastructure IPs X. Wang et al., IEEE TComp, 2014 March ISQED Custom Design of IIPS Target threat models: scan-based attack, IP piracy, HT attacks Mitigation strategies: scan chain authentication, ScanPUF, path delay based Trojan detection IIPS contains a Master Finite State Machine (M-FSM), a scan chain enabling FSM (SE-FSM), and a clock control logic IIPS interface Inputs: standard SoC test inputs, an active low reset IIPS_RSTN Outputs: a scan enable for each IP, test clock (WRCK) & test control signals (i.e. ShiftWR, CaptureWR) Locking states SC_LOCK and TD_LOCK designed to support scan chain based SoC testing and delay fault testing March ISQED
15 ScanPUF Primitive Desired features of PUF in IIPS: low-overhead, IEEE 1500 compliant signature generation and extraction, test reusable via Core Test Language (CTL) As a case study, we choose the ultralow-overhead ScanPUF * which exploits the existing scan chain DFT structures in an SoC Y. Zheng and S. Bhuina, ASPDAC, 2013 March ISQED IIPS Test Protocol under IEEE Std The control of M-FSM and SE-FSM is at SoC level l ScanPUF and HT detection test sets are developed at core level and expanded to SoC level Test procedure: (1) core test mode configuration; (2) test initialization; (3) signature gen.; (4) signature propagation Trojans in a core: LOC & LOS; Trojans on interconnects: LOS Xiao et al. D&T 2013 March ISQED
16 Integrity Validation in Printed Circuit Boards (PCBs) Courtesy: Andover Consulting Group Ghosh et al., IEEE D&T, To Appear Provisional Patent March ISQED Security Attacks in PCB Security Attacks on PCB Hardware Trojan a Piracy/ Counterfeiting In-field Alteration Malicious modific on Hidden components Cloning / Overproduc on Recycling Peripheral Exploita on Test/debug int. Exploita on PCBs are increasingly vulnerable to Counterfeiting/Tampering attacks: - Long distributed supply chain - Global design/manufacturing team - Rapid rise of PCB design cost & complexity - Easier to hack/tamper JTAG Unused test ports Thick tracks for HF Sigs Diff. signals - Makes Trojan attacks viable * * Ghosh et al., IEEE D&T, To Appear March ISQED
17 Protecting PCBs against Counterfeiting PCBs go thru. long distributed supply chain PCBs can be authenticated by unique signature from each board Key ideas to generate unique signature for each PCB - Exploit variations in Cu Trace impedances - Generate unique signature from each PCB - Use existing test equipment's for integrity validation Zhang et al., VTS 2015 The propose ed schem me March ISQED Summary & Future Directions Protect all levels of hardware (IC, PCB, System) Integrative ti Solution maximize i confidence! Cost-Effectiveness low design/test cost Easy to interface with existing design tools & infrastructure! Explore new attacks/countermeasures for emerging devices discover vulnerabilities & effective security solutions based on unique properties of post-cmos devices! March ISQED
18 Acknowledgements: Students in Nanoscape Research Lab., Case Collaborators at Intel, IBM, UFL, GaTech, Purdue U., USF Sponsors: March ISQED
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge
 Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
How Secure Are Printed Circuit Boards Against Trojan Attacks?
 How Secure Are Printed Circuit Boards Against Trojan Attacks? Swaroop Ghosh Dept. of CSE University of S. Florida Tampa, FL 33620, USA sghosh@cse.usf.edu Abhishek Basak Dept. of EECS Case Western Reserve
How Secure Are Printed Circuit Boards Against Trojan Attacks? Swaroop Ghosh Dept. of CSE University of S. Florida Tampa, FL 33620, USA sghosh@cse.usf.edu Abhishek Basak Dept. of EECS Case Western Reserve
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Hardware Trojans: A Threat for CyberSecurity
 Hardware Trojans: A Threat for CyberSecurity Julien Francq julien.francq@cassidian.com Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
Hardware Trojans: A Threat for CyberSecurity Julien Francq julien.francq@cassidian.com Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
The Reduced Address Space (RAS) for Application Memory Authentication
 The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES
 SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
Implementation Details
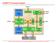 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Power Reduction Techniques in the SoC Clock Network. Clock Power
 Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
The Boundary Scan Test (BST) technology
 The Boundary Scan Test () technology J. M. Martins Ferreira FEUP / DEEC - Rua Dr. Roberto Frias 42-537 Porto - PORTUGAL Tel. 35 225 8 748 / Fax: 35 225 8 443 (jmf@fe.up.pt / http://www.fe.up.pt/~jmf) Objectives
The Boundary Scan Test () technology J. M. Martins Ferreira FEUP / DEEC - Rua Dr. Roberto Frias 42-537 Porto - PORTUGAL Tel. 35 225 8 748 / Fax: 35 225 8 443 (jmf@fe.up.pt / http://www.fe.up.pt/~jmf) Objectives
Software Hardware Binding with Quiddikey
 Software Hardware Binding with Quiddikey Mass scale solution against software piracy Secure your digital life Software-Hardware Binding solutions are typically required for Flash-based systems in which
Software Hardware Binding with Quiddikey Mass scale solution against software piracy Secure your digital life Software-Hardware Binding solutions are typically required for Flash-based systems in which
UNCLASSIFIED Version 1.0 May 2012
 Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
Secure By Default: Platforms Computing platforms contain vulnerabilities that can be exploited for malicious purposes. Often exploitation does not require a high degree of expertise, as tools and advice
PFP Technology White Paper
 PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
Horst Görtz Institute for IT-Security
 Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Security in the Age of Nanocomputing. Hacking Devices
 Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
Anti-Counterfeiting with Hardware Intrinsic Security
 Anti-Counterfeiting with Hardware Intrinsic Security Vincent van der Leest and Pim Tuyls Intrinsic-ID, Eindhoven, The Netherlands http://www.intrinsic-id.com Abstract Counterfeiting of goods and electronic
Anti-Counterfeiting with Hardware Intrinsic Security Vincent van der Leest and Pim Tuyls Intrinsic-ID, Eindhoven, The Netherlands http://www.intrinsic-id.com Abstract Counterfeiting of goods and electronic
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
Von der Hardware zur Software in FPGAs mit Embedded Prozessoren. Alexander Hahn Senior Field Application Engineer Lattice Semiconductor
 Von der Hardware zur Software in FPGAs mit Embedded Prozessoren Alexander Hahn Senior Field Application Engineer Lattice Semiconductor AGENDA Overview Mico32 Embedded Processor Development Tool Chain HW/SW
Von der Hardware zur Software in FPGAs mit Embedded Prozessoren Alexander Hahn Senior Field Application Engineer Lattice Semiconductor AGENDA Overview Mico32 Embedded Processor Development Tool Chain HW/SW
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
ARM Ltd 110 Fulbourn Road, Cambridge, CB1 9NJ, UK. *peter.harrod@arm.com
 Serial Wire Debug and the CoreSight TM Debug and Trace Architecture Eddie Ashfield, Ian Field, Peter Harrod *, Sean Houlihane, William Orme and Sheldon Woodhouse ARM Ltd 110 Fulbourn Road, Cambridge, CB1
Serial Wire Debug and the CoreSight TM Debug and Trace Architecture Eddie Ashfield, Ian Field, Peter Harrod *, Sean Houlihane, William Orme and Sheldon Woodhouse ARM Ltd 110 Fulbourn Road, Cambridge, CB1
Understanding Integrated Circuit Security Threats. Asif Iqbal Senior Program Manager, Apple Inc. SDM 11
 Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Raccoon: Closing Side-Channels through Obfuscated Execution
 Raccoon: Closing Side-Channels through Obfuscated Execution by Ashay Rane, Calvin Lin, Mohit Tiwari Presentation by Arjun Khurana and Timothy Wong Outline Background Raccoon Design Evaluation Conclusion
Raccoon: Closing Side-Channels through Obfuscated Execution by Ashay Rane, Calvin Lin, Mohit Tiwari Presentation by Arjun Khurana and Timothy Wong Outline Background Raccoon Design Evaluation Conclusion
Confidentio. Integrated security processing unit. Including key management module, encryption engine and random number generator
 Confidentio Integrated security processing unit Including key management module, encryption engine and random number generator Secure your digital life Confidentio : An integrated security processing unit
Confidentio Integrated security processing unit Including key management module, encryption engine and random number generator Secure your digital life Confidentio : An integrated security processing unit
Improving Hardware Security by Using Hidden Information of Computer
 Improving Hardware Security by Using Hidden Information of Computer System Ilya Levin, 2 Osnat Keren, 2 Vladimir Sinelnikov * Tel Aviv University, ilia@post.tau.ac.il 2 Bar Ilan University, kereno@eng.biu.ac.il
Improving Hardware Security by Using Hidden Information of Computer System Ilya Levin, 2 Osnat Keren, 2 Vladimir Sinelnikov * Tel Aviv University, ilia@post.tau.ac.il 2 Bar Ilan University, kereno@eng.biu.ac.il
Series Six Plus Programmable Controller
 Series Six Plus Programmable Controller Gl?K-0147B June 1989 Central Processor Unit 8-Slot Rack 1l-Slot Rack General Description The Central Processor Unit (CPU) for the Series Six Plus Programmable Logic
Series Six Plus Programmable Controller Gl?K-0147B June 1989 Central Processor Unit 8-Slot Rack 1l-Slot Rack General Description The Central Processor Unit (CPU) for the Series Six Plus Programmable Logic
All Programmable Logic. Hans-Joachim Gelke Institute of Embedded Systems. Zürcher Fachhochschule
 All Programmable Logic Hans-Joachim Gelke Institute of Embedded Systems Institute of Embedded Systems 31 Assistants 10 Professors 7 Technical Employees 2 Secretaries www.ines.zhaw.ch Research: Education:
All Programmable Logic Hans-Joachim Gelke Institute of Embedded Systems Institute of Embedded Systems 31 Assistants 10 Professors 7 Technical Employees 2 Secretaries www.ines.zhaw.ch Research: Education:
Extended Boundary Scan Test breaching the analog ban. Marcel Swinnen, teamleader test engineering
 Extended Boundary Scan Test breaching the analog ban Marcel Swinnen, teamleader test engineering 11-11-2014 2 zero-defect quality impossible to produce zero-defect boards early involvement services (Design
Extended Boundary Scan Test breaching the analog ban Marcel Swinnen, teamleader test engineering 11-11-2014 2 zero-defect quality impossible to produce zero-defect boards early involvement services (Design
Logically Reconfigurable PUFs: Memory-Based Secure Key Storage
 Logically Reconfigurable PUFs: Memory-Based Secure Key Storage Ilze Eichhorn Intrinsic-ID High Tech Campus 9 Eindhoven, The Netherlands ilze.eichhorn@ intrinsic-id.com Patrick Koeberl Intel Ireland Collinstown
Logically Reconfigurable PUFs: Memory-Based Secure Key Storage Ilze Eichhorn Intrinsic-ID High Tech Campus 9 Eindhoven, The Netherlands ilze.eichhorn@ intrinsic-id.com Patrick Koeberl Intel Ireland Collinstown
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
Pre-tested System-on-Chip Design. Accelerates PLD Development
 Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip
 Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
Design and Implementation of an On-Chip timing based Permutation Network for Multiprocessor system on Chip Ms Lavanya Thunuguntla 1, Saritha Sapa 2 1 Associate Professor, Department of ECE, HITAM, Telangana
SPI I2C LIN Ethernet. u Today: Wired embedded networks. u Next lecture: CAN bus u Then: 802.15.4 wireless embedded network
 u Today: Wired embedded networks Ø Characteristics and requirements Ø Some embedded LANs SPI I2C LIN Ethernet u Next lecture: CAN bus u Then: 802.15.4 wireless embedded network Network from a High End
u Today: Wired embedded networks Ø Characteristics and requirements Ø Some embedded LANs SPI I2C LIN Ethernet u Next lecture: CAN bus u Then: 802.15.4 wireless embedded network Network from a High End
KEEP IT SYNPLE STUPID
 Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
How to build a security assessment program. Dan Boucaut
 How to build a security assessment program Dan Boucaut Agenda 1 Problem statement 2 Business case 3 How to avoid creating more problems Problem statement Security assessments are hard, costly and may take
How to build a security assessment program Dan Boucaut Agenda 1 Problem statement 2 Business case 3 How to avoid creating more problems Problem statement Security assessments are hard, costly and may take
Architectures and Platforms
 Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
How To Design A Single Chip System Bus (Amba) For A Single Threaded Microprocessor (Mma) (I386) (Mmb) (Microprocessor) (Ai) (Bower) (Dmi) (Dual
 Architetture di bus per System-On On-Chip Massimo Bocchi Corso di Architettura dei Sistemi Integrati A.A. 2002/2003 System-on on-chip motivations 400 300 200 100 0 19971999 2001 2003 2005 2007 2009 Transistors
Architetture di bus per System-On On-Chip Massimo Bocchi Corso di Architettura dei Sistemi Integrati A.A. 2002/2003 System-on on-chip motivations 400 300 200 100 0 19971999 2001 2003 2005 2007 2009 Transistors
TABLE OF CONTENTS. xiii List of Tables. xviii List of Design-for-Test Rules. xix Preface to the First Edition. xxi Preface to the Second Edition
 TABLE OF CONTENTS List of Figures xiii List of Tables xviii List of Design-for-Test Rules xix Preface to the First Edition xxi Preface to the Second Edition xxiii Acknowledgement xxv 1 Boundary-Scan Basics
TABLE OF CONTENTS List of Figures xiii List of Tables xviii List of Design-for-Test Rules xix Preface to the First Edition xxi Preface to the Second Edition xxiii Acknowledgement xxv 1 Boundary-Scan Basics
Embedded Java & Secure Element for high security in IoT systems
 Embedded Java & Secure Element for high security in IoT systems JavaOne - September 2014 Anne-Laure SIXOU - ST Thierry BOUSQUET - ST Frédéric VAUTE - Oracle Speakers 2 Anne-Laure SIXOU Smartgrid Product
Embedded Java & Secure Element for high security in IoT systems JavaOne - September 2014 Anne-Laure SIXOU - ST Thierry BOUSQUET - ST Frédéric VAUTE - Oracle Speakers 2 Anne-Laure SIXOU Smartgrid Product
Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012)
 Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012) Sergei Skorobogatov University of Cambridge Cambridge, UK sps32@cam.ac.uk Christopher Woods Quo Vadis Labs London,
Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012) Sergei Skorobogatov University of Cambridge Cambridge, UK sps32@cam.ac.uk Christopher Woods Quo Vadis Labs London,
JTAG Applications. Product Life-Cycle Support. Software Debug. Integration & Test. Figure 1. Product Life Cycle Support
 JTAG Applications While it is obvious that JTAG based testing can be used in the production phase of a product, new developments and applications of the IEEE-1149.1 standard have enabled the use of JTAG
JTAG Applications While it is obvious that JTAG based testing can be used in the production phase of a product, new developments and applications of the IEEE-1149.1 standard have enabled the use of JTAG
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Notes and terms of conditions. Vendor shall note the following terms and conditions/ information before they submit their quote.
 Specifications for ARINC 653 compliant RTOS & Development Environment Notes and terms of conditions Vendor shall note the following terms and conditions/ information before they submit their quote. 1.
Specifications for ARINC 653 compliant RTOS & Development Environment Notes and terms of conditions Vendor shall note the following terms and conditions/ information before they submit their quote. 1.
EEM870 Embedded System and Experiment Lecture 1: SoC Design Overview
 EEM870 Embedded System and Experiment Lecture 1: SoC Design Overview Wen-Yen Lin, Ph.D. Department of Electrical Engineering Chang Gung University Email: wylin@mail.cgu.edu.tw Feb. 2013 Course Overview
EEM870 Embedded System and Experiment Lecture 1: SoC Design Overview Wen-Yen Lin, Ph.D. Department of Electrical Engineering Chang Gung University Email: wylin@mail.cgu.edu.tw Feb. 2013 Course Overview
ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows
 ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows Products Details ESET Endpoint Security 6 protects company devices against most current threats. It proactively looks for suspicious activity
ESET Endpoint Security 6 ESET Endpoint Antivirus 6 for Windows Products Details ESET Endpoint Security 6 protects company devices against most current threats. It proactively looks for suspicious activity
Wireless Microcontrollers for Environment Management, Asset Tracking and Consumer. October 2009
 Wireless Microcontrollers for Environment Management, Asset Tracking and Consumer October 2009 Jennic highlights Jennic is a fabless semiconductor company providing Wireless Microcontrollers to high-growth
Wireless Microcontrollers for Environment Management, Asset Tracking and Consumer October 2009 Jennic highlights Jennic is a fabless semiconductor company providing Wireless Microcontrollers to high-growth
Microsemi Security Center of Excellence
 Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET)
 INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET) International Journal of Electronics and Communication Engineering & Technology (IJECET), ISSN 0976 ISSN 0976 6464(Print)
INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET) International Journal of Electronics and Communication Engineering & Technology (IJECET), ISSN 0976 ISSN 0976 6464(Print)
Patch and Vulnerability Management Program
 Patch and Vulnerability Management Program What is it? A security practice designed to proactively prevent the exploitation of IT vulnerabilities within an organization To reduce the time and money spent
Patch and Vulnerability Management Program What is it? A security practice designed to proactively prevent the exploitation of IT vulnerabilities within an organization To reduce the time and money spent
The Advanced JTAG Bridge. Nathan Yawn nathan.yawn@opencores.org 05/12/09
 The Advanced JTAG Bridge Nathan Yawn nathan.yawn@opencores.org 05/12/09 Copyright (C) 2008-2009 Nathan Yawn Permission is granted to copy, distribute and/or modify this document under the terms of the
The Advanced JTAG Bridge Nathan Yawn nathan.yawn@opencores.org 05/12/09 Copyright (C) 2008-2009 Nathan Yawn Permission is granted to copy, distribute and/or modify this document under the terms of the
Virtual Platforms Addressing challenges in telecom product development
 white paper Virtual Platforms Addressing challenges in telecom product development This page is intentionally left blank. EXECUTIVE SUMMARY Telecom Equipment Manufacturers (TEMs) are currently facing numerous
white paper Virtual Platforms Addressing challenges in telecom product development This page is intentionally left blank. EXECUTIVE SUMMARY Telecom Equipment Manufacturers (TEMs) are currently facing numerous
G. Squillero, M. Rebaudengo. Test Techniques for Systems-on-a-Chip
 G. Squillero, M. Rebaudengo Test Techniques for Systems-on-a-Chip December 2005 Preface Fast innovation in VLSI technologies makes possible the integration a complete system into a single chip (System-on-Chip,
G. Squillero, M. Rebaudengo Test Techniques for Systems-on-a-Chip December 2005 Preface Fast innovation in VLSI technologies makes possible the integration a complete system into a single chip (System-on-Chip,
Freescale Semiconductor, Inc. Product Brief Integrated Portable System Processor DragonBall ΤΜ
 nc. Order this document by MC68328/D Microprocessor and Memory Technologies Group MC68328 MC68328V Product Brief Integrated Portable System Processor DragonBall ΤΜ As the portable consumer market grows
nc. Order this document by MC68328/D Microprocessor and Memory Technologies Group MC68328 MC68328V Product Brief Integrated Portable System Processor DragonBall ΤΜ As the portable consumer market grows
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
Detecting Zero-Day Attacks in Real Time on Day Zero
 Detecting Zero-Day Attacks in Real Time on Day Zero Standards Certification Education & Training Publishing Conferences & Exhibits Industrial Device Integrity Assessment Hardware, OS & Software Malware
Detecting Zero-Day Attacks in Real Time on Day Zero Standards Certification Education & Training Publishing Conferences & Exhibits Industrial Device Integrity Assessment Hardware, OS & Software Malware
AN10850. LPC1700 timer triggered memory to GPIO data transfer. Document information. LPC1700, GPIO, DMA, Timer0, Sleep Mode
 LPC1700 timer triggered memory to GPIO data transfer Rev. 01 16 July 2009 Application note Document information Info Keywords Abstract Content LPC1700, GPIO, DMA, Timer0, Sleep Mode This application note
LPC1700 timer triggered memory to GPIO data transfer Rev. 01 16 July 2009 Application note Document information Info Keywords Abstract Content LPC1700, GPIO, DMA, Timer0, Sleep Mode This application note
Confinement Problem. The confinement problem Isolating entities. Example Problem. Server balances bank accounts for clients Server security issues:
 Confinement Problem The confinement problem Isolating entities Virtual machines Sandboxes Covert channels Mitigation 1 Example Problem Server balances bank accounts for clients Server security issues:
Confinement Problem The confinement problem Isolating entities Virtual machines Sandboxes Covert channels Mitigation 1 Example Problem Server balances bank accounts for clients Server security issues:
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines
 Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada ken@unb.ca Micaela Serra
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada ken@unb.ca Micaela Serra
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006
 Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
Enterprise Cybersecurity Best Practices Part Number MAN-00363 Revision 006 April 2013 Hologic and the Hologic Logo are trademarks or registered trademarks of Hologic, Inc. Microsoft, Active Directory,
An Observability Branch Coverage Metric Based on Dynamic Factored Use-Define Chains
 An Observability Branch Coverage Metric Based on Dynamic Factored Use-Define Chains Tao Lv Ling-yi Liu Yang Zhao Hua-wei Li Xiao-wei Li Institute of Computing Technology, Chinese Academy of Sciences, Beijing,
An Observability Branch Coverage Metric Based on Dynamic Factored Use-Define Chains Tao Lv Ling-yi Liu Yang Zhao Hua-wei Li Xiao-wei Li Institute of Computing Technology, Chinese Academy of Sciences, Beijing,
Outline. Introduction. Multiprocessor Systems on Chip. A MPSoC Example: Nexperia DVP. A New Paradigm: Network on Chip
 Outline Modeling, simulation and optimization of Multi-Processor SoCs (MPSoCs) Università of Verona Dipartimento di Informatica MPSoCs: Multi-Processor Systems on Chip A simulation platform for a MPSoC
Outline Modeling, simulation and optimization of Multi-Processor SoCs (MPSoCs) Università of Verona Dipartimento di Informatica MPSoCs: Multi-Processor Systems on Chip A simulation platform for a MPSoC
Design Verification & Testing Design for Testability and Scan
 Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Cable Discharge Event
 Cable Discharge Event 1.0 Introduction The widespread use of electronic equipment in various environments exposes semiconductor devices to potentially destructive Electro Static Discharge (ESD). Semiconductor
Cable Discharge Event 1.0 Introduction The widespread use of electronic equipment in various environments exposes semiconductor devices to potentially destructive Electro Static Discharge (ESD). Semiconductor
M-Shield mobile security technology
 Technology for Innovators TM M-Shield mobile security technology making wireless secure Overview As 3G networks are successfully deployed worldwide, opportunities are arising to deliver to end-users a
Technology for Innovators TM M-Shield mobile security technology making wireless secure Overview As 3G networks are successfully deployed worldwide, opportunities are arising to deliver to end-users a
2B1459 System-on-Chip Applications (5CU/7.5ECTS) Course Number for Graduate Students (2B5476, 4CU)
 2B1459 System-on-Chip Applications (5CU/7.5ECTS) Course Number for Graduate Students (2B5476, 4CU) Course Coordinator: Dr. Li-Rong Zheng Laboratory of Electronics and Computer Systems Royal Institute of
2B1459 System-on-Chip Applications (5CU/7.5ECTS) Course Number for Graduate Students (2B5476, 4CU) Course Coordinator: Dr. Li-Rong Zheng Laboratory of Electronics and Computer Systems Royal Institute of
A Generic Network Interface Architecture for a Networked Processor Array (NePA)
 A Generic Network Interface Architecture for a Networked Processor Array (NePA) Seung Eun Lee, Jun Ho Bahn, Yoon Seok Yang, and Nader Bagherzadeh EECS @ University of California, Irvine Outline Introduction
A Generic Network Interface Architecture for a Networked Processor Array (NePA) Seung Eun Lee, Jun Ho Bahn, Yoon Seok Yang, and Nader Bagherzadeh EECS @ University of California, Irvine Outline Introduction
National CR16C Family On-Chip Emulation. Contents. Technical Notes V9.11.75
 _ V9.11.75 Technical Notes National CR16C Family On-Chip Emulation Contents Contents... 1 1 Introduction... 2 2 Emulation options... 3 2.1 Hardware Options... 3 2.2 Initialization Sequence... 4 2.3 JTAG
_ V9.11.75 Technical Notes National CR16C Family On-Chip Emulation Contents Contents... 1 1 Introduction... 2 2 Emulation options... 3 2.1 Hardware Options... 3 2.2 Initialization Sequence... 4 2.3 JTAG
NAND Flash FAQ. Eureka Technology. apn5_87. NAND Flash FAQ
 What is NAND Flash? What is the major difference between NAND Flash and other Memory? Structural differences between NAND Flash and NOR Flash What does NAND Flash controller do? How to send command to
What is NAND Flash? What is the major difference between NAND Flash and other Memory? Structural differences between NAND Flash and NOR Flash What does NAND Flash controller do? How to send command to
Offline HW/SW Authentication for Reconfigurable Platforms
 Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech esimpson@vt.edu Patrick Schaumont Virginia Tech schaum@vt.edu Abstract Many Field-Programmable Gate Array (FPGA) based
Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech esimpson@vt.edu Patrick Schaumont Virginia Tech schaum@vt.edu Abstract Many Field-Programmable Gate Array (FPGA) based
find model parameters, to validate models, and to develop inputs for models. c 1994 Raj Jain 7.1
 Monitors Monitor: A tool used to observe the activities on a system. Usage: A system programmer may use a monitor to improve software performance. Find frequently used segments of the software. A systems
Monitors Monitor: A tool used to observe the activities on a system. Usage: A system programmer may use a monitor to improve software performance. Find frequently used segments of the software. A systems
GFI White Paper PCI-DSS compliance and GFI Software products
 White Paper PCI-DSS compliance and Software products The Payment Card Industry Data Standard () compliance is a set of specific security standards developed by the payment brands* to help promote the adoption
White Paper PCI-DSS compliance and Software products The Payment Card Industry Data Standard () compliance is a set of specific security standards developed by the payment brands* to help promote the adoption
System-on. on-chip Design Flow. Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems. jouni.tomberg@tut.
 System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems jouni.tomberg@tut.fi 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems jouni.tomberg@tut.fi 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl chris@flylogic.net nohl@srlabs.de Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl chris@flylogic.net nohl@srlabs.de Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Building Blocks for PRU Development
 Building Blocks for PRU Development Module 1 PRU Hardware Overview This session covers a hardware overview of the PRU-ICSS Subsystem. Author: Texas Instruments, Sitara ARM Processors Oct 2014 2 ARM SoC
Building Blocks for PRU Development Module 1 PRU Hardware Overview This session covers a hardware overview of the PRU-ICSS Subsystem. Author: Texas Instruments, Sitara ARM Processors Oct 2014 2 ARM SoC
Current and Future Trends in Medical Electronics
 Current and Future Trends in Medical Electronics By Steven Dean, Medical Marketing Director, Texas Instruments www.arrownac.com 800.833.3557 Current and Future Trends in Medical Electronics By Steven Dean,
Current and Future Trends in Medical Electronics By Steven Dean, Medical Marketing Director, Texas Instruments www.arrownac.com 800.833.3557 Current and Future Trends in Medical Electronics By Steven Dean,
M.Sc. IT Semester III VIRTUALIZATION QUESTION BANK 2014 2015 Unit 1 1. What is virtualization? Explain the five stage virtualization process. 2.
 M.Sc. IT Semester III VIRTUALIZATION QUESTION BANK 2014 2015 Unit 1 1. What is virtualization? Explain the five stage virtualization process. 2. What are the different types of virtualization? Explain
M.Sc. IT Semester III VIRTUALIZATION QUESTION BANK 2014 2015 Unit 1 1. What is virtualization? Explain the five stage virtualization process. 2. What are the different types of virtualization? Explain
數 位 積 體 電 路 Digital Integrated Circuits
 IEE5049 - Spring 2012 數 位 積 體 電 路 Digital Integrated Circuits Course Overview Professor Wei Hwang 黃 威 教 授 Department of Electronics Engineering National Chiao Tung University hwang@mail.nctu.edu.tw Wei
IEE5049 - Spring 2012 數 位 積 體 電 路 Digital Integrated Circuits Course Overview Professor Wei Hwang 黃 威 教 授 Department of Electronics Engineering National Chiao Tung University hwang@mail.nctu.edu.tw Wei
MICROPROCESSOR. Exclusive for IACE Students www.iace.co.in iacehyd.blogspot.in Ph: 9700077455/422 Page 1
 MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
AN460 Using the P82B96 for bus interface
 INTEGRATED CIRCUITS 2001 Feb 14 IC12a and IC28 Data Handbook The P82B96 offers many different ways in which it can be used as a bus interface. In its simplest application it can be used as an interface
INTEGRATED CIRCUITS 2001 Feb 14 IC12a and IC28 Data Handbook The P82B96 offers many different ways in which it can be used as a bus interface. In its simplest application it can be used as an interface
NVM memory: A Critical Design Consideration for IoT Applications
 NVM memory: A Critical Design Consideration for IoT Applications Jim Lipman Sidense Corp. Introduction The Internet of Things (IoT), sometimes called the Internet of Everything (IoE), refers to an evolving
NVM memory: A Critical Design Consideration for IoT Applications Jim Lipman Sidense Corp. Introduction The Internet of Things (IoT), sometimes called the Internet of Everything (IoE), refers to an evolving
Serial port interface for microcontroller embedded into integrated power meter
 Serial port interface for microcontroller embedded into integrated power meter Mr. Borisav Jovanović, Prof. dr. Predrag Petković, Prof. dr. Milunka Damnjanović, Faculty of Electronic Engineering Nis, Serbia
Serial port interface for microcontroller embedded into integrated power meter Mr. Borisav Jovanović, Prof. dr. Predrag Petković, Prof. dr. Milunka Damnjanović, Faculty of Electronic Engineering Nis, Serbia
Lesson 7: SYSTEM-ON. SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY. Chapter-1L07: "Embedded Systems - ", Raj Kamal, Publs.: McGraw-Hill Education
 Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler
 ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor
 Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor A Starter Guide Joseph Yiu November 2014 version 1.02 27 Nov 2014 1 - Background Since the ARM Cortex -M0 Processor was released a few years
Designing a System-on-Chip (SoC) with an ARM Cortex -M Processor A Starter Guide Joseph Yiu November 2014 version 1.02 27 Nov 2014 1 - Background Since the ARM Cortex -M0 Processor was released a few years
GEDAE TM - A Graphical Programming and Autocode Generation Tool for Signal Processor Applications
 GEDAE TM - A Graphical Programming and Autocode Generation Tool for Signal Processor Applications Harris Z. Zebrowitz Lockheed Martin Advanced Technology Laboratories 1 Federal Street Camden, NJ 08102
GEDAE TM - A Graphical Programming and Autocode Generation Tool for Signal Processor Applications Harris Z. Zebrowitz Lockheed Martin Advanced Technology Laboratories 1 Federal Street Camden, NJ 08102
Network Access Control in Virtual Environments. Technical Note
 Contents Security Considerations in.... 3 Addressing Virtualization Security Challenges using NAC and Endpoint Compliance... 3 Visibility and Profiling of VMs.... 4 Identification of Rogue or Unapproved
Contents Security Considerations in.... 3 Addressing Virtualization Security Challenges using NAC and Endpoint Compliance... 3 Visibility and Profiling of VMs.... 4 Identification of Rogue or Unapproved
From Bus and Crossbar to Network-On-Chip. Arteris S.A.
 From Bus and Crossbar to Network-On-Chip Arteris S.A. Copyright 2009 Arteris S.A. All rights reserved. Contact information Corporate Headquarters Arteris, Inc. 1741 Technology Drive, Suite 250 San Jose,
From Bus and Crossbar to Network-On-Chip Arteris S.A. Copyright 2009 Arteris S.A. All rights reserved. Contact information Corporate Headquarters Arteris, Inc. 1741 Technology Drive, Suite 250 San Jose,
Production Flash Programming Best Practices for Kinetis K- and L-series MCUs
 Freescale Semiconductor Document Number:AN4835 Application Note Rev 1, 05/2014 Production Flash Programming Best Practices for Kinetis K- and L-series MCUs by: Melissa Hunter 1 Introduction This application
Freescale Semiconductor Document Number:AN4835 Application Note Rev 1, 05/2014 Production Flash Programming Best Practices for Kinetis K- and L-series MCUs by: Melissa Hunter 1 Introduction This application
PUBLIC REPORT. Red Team Testing of the ES&S Unity 3.0.1.1 Voting System. Freeman Craft McGregor Group (FCMG) Red Team
 PUBLIC REPORT Red Team Testing of the Voting System Freeman Craft McGregor Group (FCMG) Red Team Prepared for the California Secretary of State by: Jacob D. Stauffer, FCMG Red Team Project Manager Page
PUBLIC REPORT Red Team Testing of the Voting System Freeman Craft McGregor Group (FCMG) Red Team Prepared for the California Secretary of State by: Jacob D. Stauffer, FCMG Red Team Project Manager Page
Vehicular On-board Security: EVITA Project
 C2C-CC Security Workshop 5 November 2009 VW, MobileLifeCampus Wolfsburg Hervé Seudié Corporate Sector Research and Advance Engineering Robert Bosch GmbH Outline 1. Project Scope and Objectives 2. Security
C2C-CC Security Workshop 5 November 2009 VW, MobileLifeCampus Wolfsburg Hervé Seudié Corporate Sector Research and Advance Engineering Robert Bosch GmbH Outline 1. Project Scope and Objectives 2. Security
Steelcape Product Overview and Functional Description
 Steelcape Product Overview and Functional Description TABLE OF CONTENTS 1. General Overview 2. Applications/Uses 3. Key Features 4. Steelcape Components 5. Operations Overview: Typical Communications Session
Steelcape Product Overview and Functional Description TABLE OF CONTENTS 1. General Overview 2. Applications/Uses 3. Key Features 4. Steelcape Components 5. Operations Overview: Typical Communications Session
Interconnection Networks
 Advanced Computer Architecture (0630561) Lecture 15 Interconnection Networks Prof. Kasim M. Al-Aubidy Computer Eng. Dept. Interconnection Networks: Multiprocessors INs can be classified based on: 1. Mode
Advanced Computer Architecture (0630561) Lecture 15 Interconnection Networks Prof. Kasim M. Al-Aubidy Computer Eng. Dept. Interconnection Networks: Multiprocessors INs can be classified based on: 1. Mode
Cyber Security Considerations in the Development of I&C Systems for Nuclear Power Plants
 Cyber Security Considerations in the Development of I&C Systems for Nuclear Power Plants Jung-Woon Lee, Cheol-Kwon Lee, Jae-Gu Song, and Dong-Young Lee I&C and HF Research Division, Korea Atomic Energy
Cyber Security Considerations in the Development of I&C Systems for Nuclear Power Plants Jung-Woon Lee, Cheol-Kwon Lee, Jae-Gu Song, and Dong-Young Lee I&C and HF Research Division, Korea Atomic Energy
A Proxy-Based Data Security Solution in Mobile Cloud
 , pp. 77-84 http://dx.doi.org/10.14257/ijsia.2015.9.5.08 A Proxy-Based Data Security Solution in Mobile Cloud Xiaojun Yu 1,2 and Qiaoyan Wen 1 1 State Key Laboratory of Networking and Switching Technology,
, pp. 77-84 http://dx.doi.org/10.14257/ijsia.2015.9.5.08 A Proxy-Based Data Security Solution in Mobile Cloud Xiaojun Yu 1,2 and Qiaoyan Wen 1 1 State Key Laboratory of Networking and Switching Technology,
Non-Contact Test Access for Surface Mount Technology IEEE 1149.1-1990
 Non-Contact Test Access for Surface Mount Technology IEEE 1149.1-1990 ABSTRACT Mechanical and chemical process challenges initially limited acceptance of surface mount technology (SMT). As those challenges
Non-Contact Test Access for Surface Mount Technology IEEE 1149.1-1990 ABSTRACT Mechanical and chemical process challenges initially limited acceptance of surface mount technology (SMT). As those challenges
Cisco Trust Anchor Technologies
 Data Sheet Cisco Trust Anchor Technologies Overview Cisco Trust Anchor Technologies provide the foundation for trustworthy systems across Cisco. The Cisco Trust Anchor and a Secure Boot check of signed
Data Sheet Cisco Trust Anchor Technologies Overview Cisco Trust Anchor Technologies provide the foundation for trustworthy systems across Cisco. The Cisco Trust Anchor and a Secure Boot check of signed
