Registering in the Encrypted System at Lancaster General Health
|
|
|
- Joleen Nelson
- 8 years ago
- Views:
Transcription
1 Registering in the Encrypted System at Lancaster General Health Requirements Requirements for using the Lancaster General Health (LGHealth) encrypted system are: 1. You must have internet access so you can communicate with the LG encrypted web server ( Ports 80 ( and port 443 ( must be enabled to pass. 2. You must have HTML content enabled in your mail reader. 3. You must have JAVA installed on your workstation (the latest SUN/JAVA works fine ( 4. You can only use this system for encrypted traffic with LG employees and representatives (that is, users who have LG electronic addresses). 5. You should be on a Windows workstation (XP/SP3 or Windows 7). 6. You should be using IE7 or better as the web browser. Firefox and a number of additional browsers work, as well. 7. You may have trouble reading encrypted s through some web based readers (like Microsoft OWA), or through accelerator services (AOL, Verizon, etc.) since they will re-write the URL s of embedded links in HTML s. Sign-up for the LGH encrypted system is by invitation only. That means that you must receive an encrypted from someone from LGHealth to start the registration process. You cannot share your encrypted with other users. If you do need to share the , you must either 1. Print out a paper copy, or 2. Cut and past the important contents into another , or 3. Request that your contact at LGHealth include them in the original encrypted , so they will be able to use their own account to read it directly. Lancaster General Hospital RELEASED 1 of 6
2 Registration and Reading the Local Copy 1. An encrypted will look like the following: 2. When you open the , you will see something like this: You will have the option of viewing your on the LGHealth Encrypted server, or viewing your locally. We will proceed with what it looks like to read the local copy. NOTE: The local copy of the encrypted will always be available to you. The copy that exists on the LGHealth encrypted server will only be Lancaster General Hospital RELEASED 2 of 6
3 available for one week. After that, the server copy will be purged. 3. Some browsers will alert you that some of the content is coming from another page. This is expected, and it s all right to click [OK]: 4. There are three things to be aware of in the encrypted notice: a. The first link will be back to the a secure server run by LGHealth. This will be available for one week before it is purged. b. There is a support number available. c. The will have an enclosure. This is your copy of the encrypted . As long as you have the enclosure, you will always be able to decrypt this We will click on the View link (see above) to see what decrypting the local enclosure looks like. You will see a re-direct message. Go ahead and press [Decrypt Message] Lancaster General Hospital RELEASED 3 of 6
4 6. You will see the registration page for the LGHealth encrypted service. This page will appear : The password must be 8 characters long, and the password history is 3 deep. The password will never expire. 7. Enter the answers to the five questions. You will only be required to answer three of the correctly to reset your password: Lancaster General Hospital RELEASED 4 of 6
5 8. Your encrypted will look like this. There are buttons on the menu bar (look up near the Lancaster General Health logo) to allow you to reply and to print. 9. When you hit the [Reply] button, you will see this page. Notice that you have the chance at this point to make secure attachments to your reply: You will see a message box to let you know that your reply has been queued for delivery. Click on the [OK] button to proceed. At this point, click on the [Logout] link in the upper right to leave the interface. 10. You are registered in the LGHealth encrypted system. You will only need to enter your password from now on to read messages. Reading Encrypted from the Lancaster General Health Encrypted Server The main differences between reading the local copy, and reading the copy on the mail server are: Lancaster General Hospital RELEASED 5 of 6
6 on the web server will only be available for one week. That copy will be purged after that time. You will always be able to read your local copy of the encrypted . That will appear as an HTML attachment to the notification that you have received encrypted (see the first section). If you have been sent several encrypted s that are not older than one week, you will be able to review all those s in this interface. All the features that are available to you when reading your local copy will also be available to you on the interface. The same requirements apply for the web based encrypted reader that apply to reading the local copy. Lancaster General Hospital RELEASED 6 of 6
P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems
 Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
Procedure P309 - Proofpoint Encryption - Decrypting Secure Messages Business systems P309 - Page: Page 1 of 12 Date of Release: 23 February 2011 Status: Final Document Reference: Title: P309 Release Number:
Instructions For Opening UHA Encrypted Email
 Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
Receiving Encrypted Email You have received a secure, encrypted message from UHA. The message will contain the following notice and an attachment named SecureMessageAtt.hml. The attachment is shown circled
User Guide. The AMF's File Transfer Service (FTS)
 User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
TriCore Secure Web Email Gateway User Guide 1
 TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
Manual. Netumo NETUMO HELP MANUAL WWW.NETUMO.COM. Copyright Netumo 2014 All Rights Reserved
 Manual Netumo NETUMO HELP MANUAL WWW.NETUMO.COM Copyright Netumo 2014 All Rights Reserved Table of Contents 1 Introduction... 0 2 Creating an Account... 0 2.1 Additional services Login... 1 3 Adding a
Manual Netumo NETUMO HELP MANUAL WWW.NETUMO.COM Copyright Netumo 2014 All Rights Reserved Table of Contents 1 Introduction... 0 2 Creating an Account... 0 2.1 Additional services Login... 1 3 Adding a
Overview of Registered Envelopes. Registered Envelope Notification Message
 Overview of Registered Envelopes A Registered Envelope is a type of encrypted email message. Some Registered Envelopes are password-protected, while others are encrypted but do not require a password.
Overview of Registered Envelopes A Registered Envelope is a type of encrypted email message. Some Registered Envelopes are password-protected, while others are encrypted but do not require a password.
Secure Email Recipient Guide
 Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
Secure Email Recipient Guide Contents How to open your first Encrypted Message.... 3 Step-by-Step Guide to Opening Your First Envelope... 3 Step One:... 3 Step Two:... 4 Step Three:... 4 Step Four:...
MICROSOFT OUTLOOK 2003
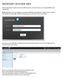 MICROSOFT OUTLOOK 2003 Follow these steps to update an Outlook 2003 account to send and receive e-mail using GCMUNI's new mail settings. Before you start, you must change your temporary GCMUNI e-mail password.
MICROSOFT OUTLOOK 2003 Follow these steps to update an Outlook 2003 account to send and receive e-mail using GCMUNI's new mail settings. Before you start, you must change your temporary GCMUNI e-mail password.
U.S. Bank Secure Mail
 U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
U.S. Bank Secure Mail @ Table of Contents Getting Started 3 Logging into Secure Mail 5 Opening Your Messages 7 Replying to a Message 8 Composing a New Message 8 1750-All Introduction: The use of email
How To Send An Encrypted Email To The State From The Outside (Public)
 Section 1. How to Send an Encrypted E-mail from the Private Network/State Employee The following conditions must be true to send an encrypted e-mail using Proofpoint e-mail encryption: Your State Agency
Section 1. How to Send an Encrypted E-mail from the Private Network/State Employee The following conditions must be true to send an encrypted e-mail using Proofpoint e-mail encryption: Your State Agency
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
Honeywell Secure Email External User Guide August 2013
 Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
Honeywell Secure Email External User Guide August 2013 PAGE: 1 of 14 Chapter No Table of Content Page No 1 Introduction 3 2 Using the Honeywell Secure Email Interface 3 3 Sending an Encrypted Email to
SECURE Email User Guide
 SECURE Email User Guide Receiving SECURE Email from Starion Financial Starion Financial is now offering an enhanced email encryption tool, IronPort PXE, which enables the email communication of sensitive
SECURE Email User Guide Receiving SECURE Email from Starion Financial Starion Financial is now offering an enhanced email encryption tool, IronPort PXE, which enables the email communication of sensitive
Instructions for Microsoft Outlook 2003
 ElkhartNet, Inc. is dedicated to providing our email customers with excellent service and support. In a targeted effort to reduce SPAM and to provide more secure and faster email, we are changing our outgoing
ElkhartNet, Inc. is dedicated to providing our email customers with excellent service and support. In a targeted effort to reduce SPAM and to provide more secure and faster email, we are changing our outgoing
Using Remote Web Workplace Version 1.01
 Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Steps to Opening Your First Password-Protected Envelope
 This section provides step-by-step instructions for opening a password-protected Registered Envelope for the first time. The steps demonstrate a typical scenario for a first-time recipient. Some of the
This section provides step-by-step instructions for opening a password-protected Registered Envelope for the first time. The steps demonstrate a typical scenario for a first-time recipient. Some of the
DEPLOYMENT GUIDE DEPLOYING THE BIG-IP SYSTEM WITH MICROSOFT INTERNET INFORMATION SERVICES (IIS) 7.0
 DEPLOYMENT GUIDE DEPLOYING THE BIG-IP SYSTEM WITH MICROSOFT INTERNET INFORMATION SERVICES (IIS) 7.0 Deploying F5 with Microsoft IIS 7.0 F5's BIG-IP system can increase the existing benefits of deploying
DEPLOYMENT GUIDE DEPLOYING THE BIG-IP SYSTEM WITH MICROSOFT INTERNET INFORMATION SERVICES (IIS) 7.0 Deploying F5 with Microsoft IIS 7.0 F5's BIG-IP system can increase the existing benefits of deploying
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
Table of Contents. Welcome... 2. Login... 3. Password Assistance... 4. Self Registration... 5. Secure Mail... 7. Compose... 8. Drafts...
 Table of Contents Welcome... 2 Login... 3 Password Assistance... 4 Self Registration... 5 Secure Mail... 7 Compose... 8 Drafts... 10 Outbox... 11 Sent Items... 12 View Package Details... 12 File Manager...
Table of Contents Welcome... 2 Login... 3 Password Assistance... 4 Self Registration... 5 Secure Mail... 7 Compose... 8 Drafts... 10 Outbox... 11 Sent Items... 12 View Package Details... 12 File Manager...
Ciphermail Gateway PDF Encryption Setup Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway PDF Encryption Setup Guide March 6, 2014, Rev: 5454 Copyright c 2008-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Portal 4 3 PDF encryption
CIPHERMAIL EMAIL ENCRYPTION Ciphermail Gateway PDF Encryption Setup Guide March 6, 2014, Rev: 5454 Copyright c 2008-2014, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 4 2 Portal 4 3 PDF encryption
Reading an email sent with Voltage SecureMail. Using the Voltage SecureMail Zero Download Messenger (ZDM)
 Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Reading an email sent with Voltage SecureMail Using the Voltage SecureMail Zero Download Messenger (ZDM) SecureMail is an email protection service developed by Voltage Security, Inc. that provides email
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Quick Start Guide to Logging in to Online Banking
 Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Page 1 Rev Date: February 2010. User Manual for Encrypted Email Services
 Page 1 User Manual for Encrypted Email Services Instructions for Using Encrypted Email Services This document is being provided to assist you in opening encrypted emails sent from Century Bank. The following
Page 1 User Manual for Encrypted Email Services Instructions for Using Encrypted Email Services This document is being provided to assist you in opening encrypted emails sent from Century Bank. The following
Creating a User Profile for Outlook 2013
 Creating a User Profile for Outlook 2013 This document tells you how to create a user profile for Outlook 2013 on your computer (also known as the Outlook client). This is necessary, for example, when
Creating a User Profile for Outlook 2013 This document tells you how to create a user profile for Outlook 2013 on your computer (also known as the Outlook client). This is necessary, for example, when
How to set up Outlook Anywhere on your home system
 How to set up Outlook Anywhere on your home system The Outlook Anywhere feature for Microsoft Exchange Server 2007 allows Microsoft Office Outlook 2007 and Outlook 2003 users to connect to their Outlook
How to set up Outlook Anywhere on your home system The Outlook Anywhere feature for Microsoft Exchange Server 2007 allows Microsoft Office Outlook 2007 and Outlook 2003 users to connect to their Outlook
Setup Corporate (Microsoft Exchange) Email. This tutorial will walk you through the steps of setting up your corporate email account.
 Setup Corporate (Microsoft Exchange) Email This tutorial will walk you through the steps of setting up your corporate email account. Microsoft Exchange Email Support Exchange Server Information You will
Setup Corporate (Microsoft Exchange) Email This tutorial will walk you through the steps of setting up your corporate email account. Microsoft Exchange Email Support Exchange Server Information You will
MICROSOFT WORD 2011 SECURE AND SHARE DOCUMENT
 MICROSOFT WORD 2011 SECURE AND SHARE DOCUMENT Last edited: 2012-07-10 1 Inspect documents before Sharing... 3 Edit or Remove Personal Information... 3 Edit author information for a document... 3 Remove
MICROSOFT WORD 2011 SECURE AND SHARE DOCUMENT Last edited: 2012-07-10 1 Inspect documents before Sharing... 3 Edit or Remove Personal Information... 3 Edit author information for a document... 3 Remove
For all other applications, including new applications, please visit www.apvma.gov.au
 This content only applies to transition applications that were received before 1 July 2014. The content will be relevant for these applications until 30 June 2015. For all other applications, including
This content only applies to transition applications that were received before 1 July 2014. The content will be relevant for these applications until 30 June 2015. For all other applications, including
MY HELPDESK - END-USER CONSOLE...
 Helpdesk User Guide Page 1 Helpdesk User Guide Table of Contents 1 INTRODUCTION... 3 1.1. OBJECTIVES... 3 1.2. END-USER CONSOLE... 3 1.3. SUMMARY OF RESPONSIBILITY... 3 1.4. HELPDESK INCIDENT LIFE CYCLE...
Helpdesk User Guide Page 1 Helpdesk User Guide Table of Contents 1 INTRODUCTION... 3 1.1. OBJECTIVES... 3 1.2. END-USER CONSOLE... 3 1.3. SUMMARY OF RESPONSIBILITY... 3 1.4. HELPDESK INCIDENT LIFE CYCLE...
Vanguard Secure E-Mail Service (VSES) User Guide
 Vanguard Secure E-Mail Service (VSES) User Guide Information Security Department January 8, 2013 Contents Guide for Users of Secure E-Mail From Vanguard 1 View Secure E-Mail 1 New Registration 3 Compose
Vanguard Secure E-Mail Service (VSES) User Guide Information Security Department January 8, 2013 Contents Guide for Users of Secure E-Mail From Vanguard 1 View Secure E-Mail 1 New Registration 3 Compose
Using Voltage SecureMail
 Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Using Voltage SecureMail Using Voltage SecureMail Desktop Based on the breakthrough Identity-Based Encryption technology, Voltage SecureMail makes sending a secure email as easy as sending it without encryption.
Background Information
 User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
Orbital ATK Secure Email: Receiving Encrypted Messages. Why Orbital ATK Secure Email? Initial Email: Orbital ATK Secure Email Notification
 Orbital ATK Secure Email: Receiving Encrypted Messages This document is intended for Orbital ATK Employees, Partners & Clients as an introduction & instructional user guide for Orbital ATK Secure Email.
Orbital ATK Secure Email: Receiving Encrypted Messages This document is intended for Orbital ATK Employees, Partners & Clients as an introduction & instructional user guide for Orbital ATK Secure Email.
USING OUTLOOK WEB ACCESS
 USING OUTLOOK WEB ACCESS 17 March 2009, Version 1.0 WHAT IS OUTLOOK WEB ACCESS? Outlook Web Access (OWA) is a webmail service of Microsoft Exchange Server. The web interface of Outlook Web Access resembles
USING OUTLOOK WEB ACCESS 17 March 2009, Version 1.0 WHAT IS OUTLOOK WEB ACCESS? Outlook Web Access (OWA) is a webmail service of Microsoft Exchange Server. The web interface of Outlook Web Access resembles
Sale Grammar School Remote Desktop Services User Instructions
 Sale Grammar School Remote Desktop Services User Instructions Sale Grammar School Remote Desktop Services allows Staff and Students access to a virtual school computer while connected to the internet at
Sale Grammar School Remote Desktop Services User Instructions Sale Grammar School Remote Desktop Services allows Staff and Students access to a virtual school computer while connected to the internet at
Secure Email User Guide Receiving Secure Email from Merchants Bank
 Secure Email User Guide Receiving Secure Email from Merchants Bank Contents This document provides a brief, end-user overview of the Cisco Registered Envelope Service Email system which has been implemented
Secure Email User Guide Receiving Secure Email from Merchants Bank Contents This document provides a brief, end-user overview of the Cisco Registered Envelope Service Email system which has been implemented
Secure Email Actions for Email Recipients
 Secure Email Actions for Email Recipients Actions for Email Recipients The recipient cannot forward encrypted email outside the secure system. Each email will only be available to the recipient for 30
Secure Email Actions for Email Recipients Actions for Email Recipients The recipient cannot forward encrypted email outside the secure system. Each email will only be available to the recipient for 30
Secure E-Mail Management Guide. June 2008
 Secure E-Mail Management Guide June 2008 What are Paychex Secure Messages? To enhance the security of client and vendor data, Paychex created the Paychex Secure E-mail Message Center, a Web site hosted
Secure E-Mail Management Guide June 2008 What are Paychex Secure Messages? To enhance the security of client and vendor data, Paychex created the Paychex Secure E-mail Message Center, a Web site hosted
Instructions for Secure Email Cisco Registered Envelope Service (CRES)
 Instructions for Secure Email Cisco Registered Envelope Service (CRES) Please read the official Cisco Guidance on the Cisco Registered Envelope Service And Frequently Asked Questions A courtesy attempt
Instructions for Secure Email Cisco Registered Envelope Service (CRES) Please read the official Cisco Guidance on the Cisco Registered Envelope Service And Frequently Asked Questions A courtesy attempt
Email Encryption User Guide
 Email Encryption User Guide August, 2013 Adapted from: Cisco Registered Envelope Recipient Guide Cisco Systems, Inc. TABLE of CONTENTS Section 1: Overview of Email Encryption... 3 Page Section 2: Overview
Email Encryption User Guide August, 2013 Adapted from: Cisco Registered Envelope Recipient Guide Cisco Systems, Inc. TABLE of CONTENTS Section 1: Overview of Email Encryption... 3 Page Section 2: Overview
DEPLOYMENT GUIDE Version 1.2. Deploying the BIG-IP System v9.x with Microsoft IIS 7.0 and 7.5
 DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v9.x with Microsoft IIS 7.0 and 7.5 Deploying F5 with Microsoft IIS 7.0 and 7.5 F5's BIG-IP system can increase the existing benefits of deploying
DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v9.x with Microsoft IIS 7.0 and 7.5 Deploying F5 with Microsoft IIS 7.0 and 7.5 F5's BIG-IP system can increase the existing benefits of deploying
Accessing your Exchange Mailbox using an Internet Browser
 Accessing your Exchange Mailbox using an Internet Browser The best way to access your Exchange mailbox on a PC or Mac is by using Outlook. This isn t always possible, or convenient, but Exchange also allows
Accessing your Exchange Mailbox using an Internet Browser The best way to access your Exchange mailbox on a PC or Mac is by using Outlook. This isn t always possible, or convenient, but Exchange also allows
Proofpoint Email Encryption Manual. 18 July 2014
 Proofpoint Email Encryption Manual 18 July 2014 Table of Contents Table of Contents... 2 Why did I Receive an Encrypted Email?... 3 Registering to Open an Encrypted Email for the First Time... 3 Opening
Proofpoint Email Encryption Manual 18 July 2014 Table of Contents Table of Contents... 2 Why did I Receive an Encrypted Email?... 3 Registering to Open an Encrypted Email for the First Time... 3 Opening
Add Title. Single Sign-On Registration
 Add Title Single Sign-On Registration Registration Instructions for Single Sign-On (SSO) Create SSO User ID Create SSO Password Subscribing to CHAMPS Accessing CHAMPS Step 1: Open your web browser (e.g.
Add Title Single Sign-On Registration Registration Instructions for Single Sign-On (SSO) Create SSO User ID Create SSO Password Subscribing to CHAMPS Accessing CHAMPS Step 1: Open your web browser (e.g.
PaperClip. em4 Cloud Client. Setup Guide
 PaperClip em4 Cloud Client Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand and product
PaperClip em4 Cloud Client Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand and product
Using the Findlay City Schools Help Desk Program. This document describes how to submit a helpdesk request into the new system for the first time.
 Using the Findlay City Schools Help Desk Program This document describes how to submit a helpdesk request into the new system for the first time. In order to submit a helpdesk request you will need to
Using the Findlay City Schools Help Desk Program This document describes how to submit a helpdesk request into the new system for the first time. In order to submit a helpdesk request you will need to
Secure Mail Registration and Viewing Procedures
 Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Contents. Before You Install... 3. Server Installation... 5. Configuring Print Audit Secure... 10
 Installation Guide Contents Before You Install... 3 Server Installation... 5 Configuring Print Audit Secure... 10 Configuring Print Audit Secure to use with Print Audit 6... 15 Licensing Print Audit Secure...
Installation Guide Contents Before You Install... 3 Server Installation... 5 Configuring Print Audit Secure... 10 Configuring Print Audit Secure to use with Print Audit 6... 15 Licensing Print Audit Secure...
Organization Name National Institutional Facilitation Technologies (Pvt.) Ltd. Business Division Name Information Security Solutions (NIFTeTRUST)
 Organization Name National Institutional Facilitation Technologies (Pvt.) Ltd. Business Division Name Information Security Solutions (NIFTeTRUST) Document Name Digital ID Installation Guide (Microsoft
Organization Name National Institutional Facilitation Technologies (Pvt.) Ltd. Business Division Name Information Security Solutions (NIFTeTRUST) Document Name Digital ID Installation Guide (Microsoft
MSGCU SECURE MESSAGE CENTER
 MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
MSGCU SECURE MESSAGE CENTER Welcome to the MSGCU Secure Message Center. Email is convenient, but is it secure? Before reaching the intended recipient, email travels across a variety of public servers and
How to Use Boston Private Bank s Secure Mail Service
 1. ONE-TIME REGISTRATION PROCESS Prior to using the Secure Mail service for the first time, a user must initially register with the service by completing steps A thru E below: A. When a Secure Mail encrypted
1. ONE-TIME REGISTRATION PROCESS Prior to using the Secure Mail service for the first time, a user must initially register with the service by completing steps A thru E below: A. When a Secure Mail encrypted
Active Directory Self-Service FAQ
 Active Directory Self-Service FAQ General Information: info@cionsystems.com Online Support: support@cionsystems.com CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
Active Directory Self-Service FAQ General Information: info@cionsystems.com Online Support: support@cionsystems.com CionSystems Inc. Mailing Address: 16625 Redmond Way, Ste M106 Redmond, WA. 98052 http://www.cionsystems.com
E Mail Encryption End User Guide
 E Mail Encryption End User Guide TABLE OF CONTENTS Why Use Email Encryption... 2 What is a Registered Envelope... 2 Features & Benefits... 2 Security Policies... 2 How to Compose and Send an Encrypted
E Mail Encryption End User Guide TABLE OF CONTENTS Why Use Email Encryption... 2 What is a Registered Envelope... 2 Features & Benefits... 2 Security Policies... 2 How to Compose and Send an Encrypted
Web24 Web Hosting Guide
 Web24 Web Hosting Guide Welcome Dear Web24 customer, We would like to thank you for choosing Web24 as your preferred web hosting provider. To make your experience as enjoyable as possible, we have prepared
Web24 Web Hosting Guide Welcome Dear Web24 customer, We would like to thank you for choosing Web24 as your preferred web hosting provider. To make your experience as enjoyable as possible, we have prepared
How To Encrypt An Email From A Cell Phone To A Pc Or Ipad (For A Partner) With A Cisco Email Encryption Solution (For Partners)
 New PHI & PII E-mail Encryption Solution (Partner Notification) In a continuing effort to utilize the advantages of email security while at the same time protecting clients private information, the Department
New PHI & PII E-mail Encryption Solution (Partner Notification) In a continuing effort to utilize the advantages of email security while at the same time protecting clients private information, the Department
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE
 CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
CITY OF BURLINGTON PUBLIC SCHOOLS MICROSOFT EXCHANGE 2010 OUTLOOK WEB APP USERS GUIDE INTRODUCTION You can access your email account from any workstation at your school using Outlook Web Access (OWA),
External End User Training Guide: Secure Email Extract
 External End User Training Guide: Secure Email Extract Version 6 August 12, 2013 Prepared by 7/29/2013: Kris Chromey, Training Coordinator Michelle Tuscher, Vault Implementation Coordinator Edited for
External End User Training Guide: Secure Email Extract Version 6 August 12, 2013 Prepared by 7/29/2013: Kris Chromey, Training Coordinator Michelle Tuscher, Vault Implementation Coordinator Edited for
TIBCO Slingshot User Guide
 TIBCO Slingshot User Guide v1.8.1 Copyright 2008-2010 TIBCO Software Inc. ALL RIGHTS RESERVED. Page 1 September 2, 2011 Documentation Information Slingshot Outlook Plug-in Important Information SOME TIBCO
TIBCO Slingshot User Guide v1.8.1 Copyright 2008-2010 TIBCO Software Inc. ALL RIGHTS RESERVED. Page 1 September 2, 2011 Documentation Information Slingshot Outlook Plug-in Important Information SOME TIBCO
PaperClip. em4 Cloud Client. Manual Setup Guide
 PaperClip em4 Cloud Client Manual Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand
PaperClip em4 Cloud Client Manual Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand
Surplus Lines Online User Guide
 Surplus Lines Online User Guide Missouri Department of Insurance, Financial Institutions and Professional Registration Contents Summary... 1 Site Address... 1 Account Management... 2 Account Registration...
Surplus Lines Online User Guide Missouri Department of Insurance, Financial Institutions and Professional Registration Contents Summary... 1 Site Address... 1 Account Management... 2 Account Registration...
ClicktoFax Service Usage Manual
 ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
Can I manually trigger secure e-mail to encrypt a message that does not contain PI or other sensitive information? Yes, by use of the word TID.
 How does Secure E-mail work? When an e-mail is initiated or responded to the secure e-mail algorithm will determine if the e-mail needs to be encrypted based on predefined criteria. If it meets the predefined
How does Secure E-mail work? When an e-mail is initiated or responded to the secure e-mail algorithm will determine if the e-mail needs to be encrypted based on predefined criteria. If it meets the predefined
Deploying the BIG-IP System with Oracle E-Business Suite 11i
 Deploying the BIG-IP System with Oracle E-Business Suite 11i Introducing the BIG-IP and Oracle 11i configuration Configuring the BIG-IP system for deployment with Oracle 11i Configuring the BIG-IP system
Deploying the BIG-IP System with Oracle E-Business Suite 11i Introducing the BIG-IP and Oracle 11i configuration Configuring the BIG-IP system for deployment with Oracle 11i Configuring the BIG-IP system
Send and receive encrypted e-mails
 Manual Send and receive encrypted e-mails Bank J. Safra Sarasin Ltd Document Owner Security Classification Document Type Bank J. Safra Sarasin Ltd internal and external use Manual Document change history
Manual Send and receive encrypted e-mails Bank J. Safra Sarasin Ltd Document Owner Security Classification Document Type Bank J. Safra Sarasin Ltd internal and external use Manual Document change history
bank zweiplus email Gateway user manual
 bank zweiplus email Gateway user manual T +41 (0)58 059 22 22, F +41 (0)58 059 22 44, www.bankzweiplus.ch 1/29 Table of contents 1 Foreword... 3 2 Important Notes... 3 2.1 General... 3 2.2 Password...
bank zweiplus email Gateway user manual T +41 (0)58 059 22 22, F +41 (0)58 059 22 44, www.bankzweiplus.ch 1/29 Table of contents 1 Foreword... 3 2 Important Notes... 3 2.1 General... 3 2.2 Password...
How To Restore Your Data On A Backup By Mozy (Windows) On A Pc Or Macbook Or Macintosh (Windows 2) On Your Computer Or Mac) On An Pc Or Ipad (Windows 3) On Pc Or Pc Or Micro
 Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
Online Backup by Mozy Restore Common Questions Document Revision Date: June 29, 2012 Online Backup by Mozy Common Questions 1 How do I restore my data? There are five ways of restoring your data: 1) Performing
USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4
 USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4 March 2014 TABLE OF CONTENTS Chapter 1 Welcome... 4 Introducing WWPass Security for Email (Outlook)... 5 Supported Outlook Products...
USER GUIDE WWPass Security for Email (Outlook) For WWPass Security Pack 2.4 March 2014 TABLE OF CONTENTS Chapter 1 Welcome... 4 Introducing WWPass Security for Email (Outlook)... 5 Supported Outlook Products...
How To Set Up A Sartorius Mailbox In Outlook On A Non-Standard Pc On A Windows Xp Oracle 365 On A Pc Oracle365 On A Sertorius Mailbox On A Microsoft Office365 On Pc Orca 2 On A
 CA-IS Documentation Installing and Using Sartorius Office365 on non-standard Installing and Using Sartorius Office365 on non-standard Install and user guide 002 9/19/2012 3:10:00 PM Heiko Moeller 12/18/2012
CA-IS Documentation Installing and Using Sartorius Office365 on non-standard Installing and Using Sartorius Office365 on non-standard Install and user guide 002 9/19/2012 3:10:00 PM Heiko Moeller 12/18/2012
MIDAS Authorization User Guide. Provider Portal
 MIDAS Authorization User Guide Provider Portal Table of Contents Logging On... 2 Change Your Password... 4 Homepage/Welcome Screen... 5 Provider Management.. 5 Provider Demographics... 6 Provider Additional
MIDAS Authorization User Guide Provider Portal Table of Contents Logging On... 2 Change Your Password... 4 Homepage/Welcome Screen... 5 Provider Management.. 5 Provider Demographics... 6 Provider Additional
Secure Email A Guide for Users
 Secure Email A Guide for Users October 14, 2013 10/13 TABLE OF CONTENTS USING THE SYSTEM FOR THE FIRST TIME... 3 EMAIL NOTIFICATION OF SECURE INFORMATION... 3 GETTING REGISTERED ON THE SYSTEM... 4 ACCOUNT
Secure Email A Guide for Users October 14, 2013 10/13 TABLE OF CONTENTS USING THE SYSTEM FOR THE FIRST TIME... 3 EMAIL NOTIFICATION OF SECURE INFORMATION... 3 GETTING REGISTERED ON THE SYSTEM... 4 ACCOUNT
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
How-to: Single Sign-On
 How-to: Single Sign-On Document version: 1.02 nirva systems info@nirva-systems.com nirva-systems.com How-to: Single Sign-On - page 2 This document describes how to use the Single Sign-On (SSO) features
How-to: Single Sign-On Document version: 1.02 nirva systems info@nirva-systems.com nirva-systems.com How-to: Single Sign-On - page 2 This document describes how to use the Single Sign-On (SSO) features
7. In the boxed unlabeled field, enter the last 4 digits of your Social Security number.
 CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
Proofpoint provides the capability for external users to send secure/encrypted emails to EBS-RMSCO employees.
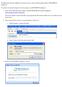 Proofpoint provides the capability for external users to send secure/encrypted emails to EBS-RMSCO employees. To create a new email message to be sent securely to an EBS-RMSCO employee: 1. Click on the
Proofpoint provides the capability for external users to send secure/encrypted emails to EBS-RMSCO employees. To create a new email message to be sent securely to an EBS-RMSCO employee: 1. Click on the
Using ipass Secure Anywhere. Secure Remote Access for Hallmark Independent Retailers
 Secure Remote Access for Hallmark Independent Retailers ipass Inc. Managed Network Services 125 Technology Drive, Suite 100 Irvine, CA 92618 USA www.ipass.com +1 949-681-5076 +1 949-681-5114 fx TABLE OF
Secure Remote Access for Hallmark Independent Retailers ipass Inc. Managed Network Services 125 Technology Drive, Suite 100 Irvine, CA 92618 USA www.ipass.com +1 949-681-5076 +1 949-681-5114 fx TABLE OF
HOW TO USE OIT EMAIL VIA THE WEB
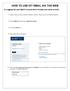 HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
Lync for Mac Get Help Guide
 How do I download the Lync Client Tool for Mac? The Lync Client allows you to use your computer as a telephone as well as enabling the unified communication features. Part 1: Installing the Lync Client
How do I download the Lync Client Tool for Mac? The Lync Client allows you to use your computer as a telephone as well as enabling the unified communication features. Part 1: Installing the Lync Client
Secure Email Client User Guide Receiving Secure Email from Mercantile Bank
 Receiving Secure Email from Contents This document provides a brief, end-user overview of the Secure Email system which has been implemented by. Why Secure Email? When someone sends you an email, the email
Receiving Secure Email from Contents This document provides a brief, end-user overview of the Secure Email system which has been implemented by. Why Secure Email? When someone sends you an email, the email
New Online Banking Guide for FIRST time Login
 New Online Banking Guide for FIRST time Login Step 1: Login Enter your existing Online Banking User ID and Password. Click Log-In. Step 2: Accepting terms and Conditions to Proceed Click on See the terms
New Online Banking Guide for FIRST time Login Step 1: Login Enter your existing Online Banking User ID and Password. Click Log-In. Step 2: Accepting terms and Conditions to Proceed Click on See the terms
1. Chat4Support Introduction
 1. Chat4Support Introduction Chat4Support is a CodingBest product that helps businesses to improve their sales and customer service on the Internet. Website visitors just only need to click on the chat
1. Chat4Support Introduction Chat4Support is a CodingBest product that helps businesses to improve their sales and customer service on the Internet. Website visitors just only need to click on the chat
Outlook Web Access is accessible to all users where Internet access is available. This document contains instructions on how to use OWA.
 Welcome to the City of Sarasota s Outlook Web Access (OWA). As a member of the Board you are required to use your City-issued email address for correspondence that is related to the business of the Advisory
Welcome to the City of Sarasota s Outlook Web Access (OWA). As a member of the Board you are required to use your City-issued email address for correspondence that is related to the business of the Advisory
Recommended Browser Setting for MySBU Portal
 The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
The MySBU portal is built using Microsoft s SharePoint technology framework, therefore, for the best viewing experience, Southwest Baptist University recommends the use of Microsoft s Internet Explorer,
NeoMail Guide. Neotel (Pty) Ltd
 NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
USER GUIDE WWPass Security for Windows Logon
 USER GUIDE WWPass Security for Windows Logon December 2015 TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Windows Logon... 4 Related Documentation... 4 Presenting Your PassKey
USER GUIDE WWPass Security for Windows Logon December 2015 TABLE OF CONTENTS Chapter 1 Welcome... 3 Introducing WWPass Security for Windows Logon... 4 Related Documentation... 4 Presenting Your PassKey
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E. Administrator Guide
 Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
Policy Based Encryption E Administrator Guide Policy Based Encryption E Administrator Guide Documentation version: 1.2 Legal Notice Legal Notice Copyright 2012 Symantec Corporation. All rights reserved.
DEPLOYMENT GUIDE DEPLOYING F5 WITH MICROSOFT WINDOWS SERVER 2008
 DEPLOYMENT GUIDE DEPLOYING F5 WITH MICROSOFT WINDOWS SERVER 2008 Table of Contents Table of Contents Deploying F5 with Microsoft Windows Server 2008 Prerequisites and configuration notes...1-1 Deploying
DEPLOYMENT GUIDE DEPLOYING F5 WITH MICROSOFT WINDOWS SERVER 2008 Table of Contents Table of Contents Deploying F5 with Microsoft Windows Server 2008 Prerequisites and configuration notes...1-1 Deploying
GRS Advantage Website User Reference Guide
 GRS Advantage Website User Reference Guide This document describes how to use the GRS Advantage Website. Table of Contents GRS Advantage Website... 2 Accessing the Website... 2 Requesting Access to the
GRS Advantage Website User Reference Guide This document describes how to use the GRS Advantage Website. Table of Contents GRS Advantage Website... 2 Accessing the Website... 2 Requesting Access to the
DEPLOYMENT GUIDE Version 1.2. Deploying the BIG-IP System v10 with Microsoft IIS 7.0 and 7.5
 DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v10 with Microsoft IIS 7.0 and 7.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft IIS Prerequisites and configuration
DEPLOYMENT GUIDE Version 1.2 Deploying the BIG-IP System v10 with Microsoft IIS 7.0 and 7.5 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Microsoft IIS Prerequisites and configuration
Apache JMeter HTTP(S) Test Script Recorder
 Apache JMeter HTTP(S) Test Script Recorder This tutorial attempts to explain the exact steps for recording HTTP/HTTPS. For those new to JMeter, one easy way to create a test plan is to use the Recorder.
Apache JMeter HTTP(S) Test Script Recorder This tutorial attempts to explain the exact steps for recording HTTP/HTTPS. For those new to JMeter, one easy way to create a test plan is to use the Recorder.
DROOMS DATA ROOM USER GUIDE. www.drooms.com
 USER GUIDE www.drooms.com USER GUIDE Dear User, Whether simply reviewing documentation, sending queries during the due diligence process or administering a data room yourself, Drooms is the software solution
USER GUIDE www.drooms.com USER GUIDE Dear User, Whether simply reviewing documentation, sending queries during the due diligence process or administering a data room yourself, Drooms is the software solution
Department of Alcohol & Drug Programs. Information Management Services Division (IMSD) EMAIL ENCRYPTION INSTRUCTIONS
 Department of Alcohol & Drug Programs (IMSD) EMAIL ENCRYPTION INSTRUCTIONS July 1, 2010 Why Do We Need Email Encryption? Code of Regulations, Title 45, Subtitle A, Part 164 The Health Insurance Portability
Department of Alcohol & Drug Programs (IMSD) EMAIL ENCRYPTION INSTRUCTIONS July 1, 2010 Why Do We Need Email Encryption? Code of Regulations, Title 45, Subtitle A, Part 164 The Health Insurance Portability
What is Aconex Local Copy? Controlling Access to a Datastore Hardware Requirements Software Requirements Installing Aconex Local Copy Troubleshooting
 Version 1.6 1 1 1 2 2 8 8 9 9 9 What is Aconex Local Copy? Controlling Access to a Datastore Hardware Requirements Software Requirements Installing Aconex Local Copy Troubleshooting your Installation Managing
Version 1.6 1 1 1 2 2 8 8 9 9 9 What is Aconex Local Copy? Controlling Access to a Datastore Hardware Requirements Software Requirements Installing Aconex Local Copy Troubleshooting your Installation Managing
Table of Contents. Oracle/Sun JRE Upgrade Instructions. Verify Hard Disk Space JRE 1.6.0.35
 Table of Contents Oracle/Sun JRE Upgrade Instructions... 1 Verify Hard Disk Space... 1 JRE Install Directions for Windows Vista or Windows 7... 2 EWB Sign-on with the New JRE... 7 Problem and Resolution
Table of Contents Oracle/Sun JRE Upgrade Instructions... 1 Verify Hard Disk Space... 1 JRE Install Directions for Windows Vista or Windows 7... 2 EWB Sign-on with the New JRE... 7 Problem and Resolution
Here are the steps to configure Outlook Express for use with Salmar's Zimbra server. Select "Tools" and then "Accounts from the pull down menu.
 Salmar Consulting Inc. Setting up Outlook Express to use Zimbra Marcel Gagné, February 2010 Here are the steps to configure Outlook Express for use with Salmar's Zimbra server. Open Outlook Express. Select
Salmar Consulting Inc. Setting up Outlook Express to use Zimbra Marcel Gagné, February 2010 Here are the steps to configure Outlook Express for use with Salmar's Zimbra server. Open Outlook Express. Select
isupplier PORTAL ACCESS SYSTEM REQUIREMENTS
 TABLE OF CONTENTS Recommended Browsers for isupplier Portal Recommended Microsoft Internet Explorer Browser Settings (MSIE) Recommended Firefox Browser Settings Recommended Safari Browser Settings SYSTEM
TABLE OF CONTENTS Recommended Browsers for isupplier Portal Recommended Microsoft Internet Explorer Browser Settings (MSIE) Recommended Firefox Browser Settings Recommended Safari Browser Settings SYSTEM
CISCO SECURE MAIL. External User Guide. 1/15/15 Samson V.
 1/15/15 Samson V. 1. These instructions are for users who reside outside the University of Colorado Denver that receive encrypted emails from faculty or staff of UC Denver. As a part of our HIPAA compliance
1/15/15 Samson V. 1. These instructions are for users who reside outside the University of Colorado Denver that receive encrypted emails from faculty or staff of UC Denver. As a part of our HIPAA compliance
Training Manual. Version 6
 Training Manual TABLE OF CONTENTS A. E-MAIL... 4 A.1 INBOX... 8 A.1.1 Create New Message... 8 A.1.1.1 Add Attachments to an E-mail Message... 11 A.1.1.2 Insert Picture into an E-mail Message... 12 A.1.1.3
Training Manual TABLE OF CONTENTS A. E-MAIL... 4 A.1 INBOX... 8 A.1.1 Create New Message... 8 A.1.1.1 Add Attachments to an E-mail Message... 11 A.1.1.2 Insert Picture into an E-mail Message... 12 A.1.1.3
