Introduction to WSU
|
|
|
- Arron Armstrong
- 10 years ago
- Views:
Transcription
1 Introduction to WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember Malware... 2 Information to Remember Firewalls... 3 Information to Remember Anti-spam Utility Network Drives Logging into the Campus Network VPN (Virtual Private Network) Software Accessing Your Network Files from Home WINGS Wright Information, News, and Group Services Campus Password... 7 Information to Remember WINGS Express (WE) University ID (UID) and PIN Software Discounts File Encryption... 9 Information to Remember WINGS Resource Center (WRC) CaTS Resources Contact CaTS... 11
2 1 - Information Technology (IT) Security IT security has become an integral part of the worldwide computing environment, and keeping computers, networks, and data safe is of utmost importance. In keeping with this trend, CaTS has created a security website that houses a wealth of information regarding IT security. Please visit to review this information. You can also view a short security video at the following website: Information to Remember Downloading and installing security updates are crucial when defending against viruses and other computer oriented attacks Never allow another person to use your computer account Close and lock your door whenever you leave your office Use a password protected screensaver Lock your workstation whenever you leave for any amount of time 2 - Malware Malware is a term that encompasses both viruses and spyware. A computer virus is a program that is infectious and can by highly complex. Viruses implant instructions in other programs or storage devices that can attack, scramble, or erase computer data. To check WSU s current computing status go to the CaTS homepage ( and look for the CaTS Bulletin button on the right sidebar. Check this location for important computing news or alerts such as the latest worm/virus outbreak information. The following activities are among the most common ways of getting computer viruses. Minimizing the frequency of these activities will reduce your risk of getting a computer virus: Freely sharing computer programs and system disks Downloading executable software from public-access bulletin boards Opening attachments from people you don't know 2
3 Spyware is software that watches your activities and collects personal data without your permission. Adware displays pop-ups and other forms of unauthorized advertising. Because these programs run in the background while you use your computer, they consume system resources and can slow down your PC significantly. WSU Policy: Wright State University is concerned with the health of your computer and with maintaining effective network resources. In the interest of your computer and the health of the University network, you are REQUIRED to have up-to-date operating system patches as well as virus and spyware scanning software on your system. In order to ensure uninterrupted network access, you must keep your operating system and all virus/spyware tools updated. Virus and Spyware scanning software for home use is available on the ConnectWright website, located at Information to Remember Characteristics of spyware: monitoring computer activity, collect personal information, sends personal information back to the spyware creator Macintosh computers are susceptible to this type of computer oriented attack; CaTS recommends users download and install our free antivirus program for the Mac OS Characteristics of a virus: erase data, scramble data, replicate itself 3 - Firewalls A firewall is a system that is designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software formats. Here at Wright State University, CaTS maintains both hardware and software perimeter firewalls for the entire campus community that control Internet traffic in and out of our network. For individual computers, personal desktop firewalls, such as Windows Firewall, should be installed to help prevent unauthorized access. CaTS manages the security software on all university computers. For home use, the easiest and most convenient firewall to use is the Windows Firewall, but other popular programs include Zone Alarm and Tiny Firewall, which can be downloaded from the website 3
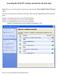
4 Information to Remember Personal firewalls protect your computer from unauthorized access 4 Anti-spam Utility Unsolicited commercial , also known as spam, has become an increasing problem at WSU. To reduce the amount of time involved with managing spam, CaTS offers a spam filtering service for faculty, staff, and students. The service is currently available to all users with CaTS based accounts (addresses ending Instructions for using the utility can be found at: The screenshot below shows the new End User Digest, a way to see all the spam that the filter has blocked for your account. 5 - Network Drives Active Directory Description H:/ Drive 5 GB Personal network storage K:/ Drive Dependent on department Shared departmental drive 4
5 6 - Logging into the Campus Network Recently, Wright State University made a transition from Novell to Microsoft Active Directory for our file storage and printing network infrastructure. The screenshot below shows what the login screen should look like when you turn on your computer. To log in, type in your campus w username and password and click the blue arrow. 7 VPN (Virtual Private Network) Software The AnyConnect VPN from Cisco allows authorized users to securely connect to the WSU data network from the campus wireless network or from off campus using various commercial Internet Service Providers (ISPs). Using AnyConnect, wireless and remote users are connected to the university's internal network as if they were directly connected to the campus network. This allows WSU wireless and remote users to access servers and other devices restricted to WSU network users. In addition, a VPN connection allows the user to access all network files (Home H:\ and shared drives K:\). To learn more about VPN software or to download it for your computer, please visit the CaTS VPN site, located at 5
6 8 Accessing Your Network Files from Home If you want to access your personal and departmental files from off-campus you must use the university s VPN connection. This connection allows you to securely connect to the WSU data network to access your files stored on your network drives. In order to use the connection you will be required to install the university s VPN software on your computer and use it to connect to your files. For instructions on how to download, install, and use the VPN client, please visit the following website: You will need to click on the link for AnyConnect VPN Registration to start the process. After downloading and installing the software, re-visit the above listed website and click on the Accessing Your Files from Home link under the Existing AnyConnect VPN Users section. 9 - WINGS Wright Information, News, and Group Services WINGS (an acronym for Wright Information, News, and Group Services), is an electronic portal used by the WSU community to access various systems, services, and information from one location. This secure site provides you with a customizable layout enabling you to add channelized content that matters to you. Log in using your campus account to access your , personal calendar, announcements, course software, and WINGS Express. Visit WINGS at the following location: 6
7 10 - Campus Password Account management should be done through the WINGS portal ( Once you are on the WINGS login page, click the Forgot your Campus Password? link located on the left side of the screen and you will have the ability to change your password. Your campus password must be changed every 180 days. When changing your campus password there are a few things to keep in mind: The password length must be 8 to 14 characters The password must contain a letter The password must contain at least one of these special characters: ^()-_!$ Do not use names or common words in the dictionary Do not use the following symbols: % The password cannot be one that you have used before Resetting your password There are two ways to change your password. Here s the preferred way for you to do it. 1) Login to WINGS ( 2) Click the My Account link in the top left corner. 3) Enter your current password. 4) Enter your new password and confirm it. 5) Click the Save Changes button. If you have trouble changing the password using this route, or you can t log in to WINGS, there s a second way to change your password. Here s how. 1) Go to the WINGS website ( 2) Click the Forgot Your Campus Password? link under the WINGS login box. 3) Enter your UID and PIN then click Submit. 4) Answer your security question(s). 5) Enter and re-enter your new password. 6) Click Submit. 7
8 Information to Remember Characteristics of a secure password: a random collection of numbers and letters Secure password are not easily guessed or found in the dictionary Example of secure password: summer2009=5umm3r2oo9 Simply exchanging numbers for letters can make a password more secure Never write down your password, even if you plan to store it in a secure place 11 - WINGS Express (WE) WINGS Express is a service that allows faculty and staff to access personal information at Wright State University, including pay information and grade entering. You can access WINGS Express by logging in to WINGS, then clicking the WINGS Express icon in the top right corner University ID (UID) and PIN Your 9-digit University Identification Number (UID) is assigned to you when you apply as a student or become affiliated with Wright State University. Your UID never changes and is never re-used. It replaces the use of your Social Security Number as a permanent, unique ID number identifying you as a member of the university community. The UID, along with your PIN, is used to access the WINGS Express system. If you have forgotten your PIN, go to enter your UID then click the Forgot PIN? button. Answer your security questions correctly and you ll be able to create a new PIN. 8
9 13 - There are numerous methods to check your WINGS ( Thunderbird, Outlook, etc. The most convenient method is through WINGS. Login to WINGS and click the icon in the top right. Quota: Faculty/Staff = 250 MB Official WSU Policy: There is an increasing reliance on electronic communication among students, faculty, staff and administration at Wright State University. Because of this reliance and the acceptance of electronic communication, is considered the official means for communication. The University will send official communications via and expects that those communications will be received and read in a timely fashion. Students are expected to check their official address frequently to stay current with university communications. 14 Software Discounts Wright State University has a special licensing agreement with Microsoft and Apple that allows the distribution of a broad range of Microsoft and Apple software to employees. The software can be purchased by logging into the WINGS portal ( clicking on the Resources tab, and then on Order Software under the CaTS Support channel. Available software includes: Office 2010 for the PC, Office 2008 for the Macintosh, Windows and Macintosh system upgrades, and various other software titles. To see the list of all available titles and to read more about software licensing at the university, visit 15 File Encryption Encryption is the process of transforming information from clear or plain text into a non-readable format so that only the intended reader can understand or change the message content. Encryption ensures privacy. It is a way to keep prying eyes from reading confidential information that is sent across the public internet. Certain software applications have encryption methods embedded in them for sending and receiving secure information and for the storage of information. There is also third party software available that can be used to encrypt information. 9
10 For directions on encrypting files, check out the following links: Encrypting files using Microsoft Office Word, Excel, and PowerPoint Encrypting files using Microsoft Office Access Encrypting files using Microsoft Office Encryption with the Macintosh Operating System Information to Remember A Microsoft document can be encrypted so that a password is required to view the contents Documents should be encrypted if they contain any personal information The following are examples of personal information: username, password, educational records such as grades, social security numbers, etc Never include the encryption password in your If you have any questions about what should be encrypted, please contact the CaTS Help Desk 16 - WINGS Resource Center (WRC) Looking for help accessing your information in WINGS and WINGS Express? Turn to the WINGS Resource Center, designed to help you more easily navigate WINGS, WINGS Express, and more. In this central location you will find training videos, documentation, training dates, FAQs, and more. You can find the WINGS Resource Center at 10
11 17 - CaTS Resources Resource CaTS Website WINGS WINGS Resource Center IT Security Online Training Online Documentation Online Forms Computer Lab Schedules Anti-Spam Software CaTS Bulletin Free Software Web Location Contact CaTS Contact CaTS for all of your campus computing needs. Here s our information: Phone: (937) or [email protected] Location: 025 Library Annex (basement of Dunbar Library) 11
GETTING STARTED ON THE WINDOWS SERVICE A GUIDE FOR NEW STAFF MEMBERS
 Your Login ID: GETTING STARTED ON THE WINDOWS SERVICE A GUIDE FOR NEW STAFF MEMBERS CONTENTS 1.0 Introduction... 3 1.1 Welcome to Edinburgh Napier University from Information Services!... 3 1.2 About Information
Your Login ID: GETTING STARTED ON THE WINDOWS SERVICE A GUIDE FOR NEW STAFF MEMBERS CONTENTS 1.0 Introduction... 3 1.1 Welcome to Edinburgh Napier University from Information Services!... 3 1.2 About Information
IT@DUSON. IT Service Desk
 IT@DUSON Technology plays a key role in the learning process for nursing students at Duke. This is your guide to the technology used at the Duke School of Nursing and how to request assistance for all
IT@DUSON Technology plays a key role in the learning process for nursing students at Duke. This is your guide to the technology used at the Duke School of Nursing and how to request assistance for all
Quick Start Guide to Logging in to Online Banking
 Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Charter Business Desktop Security Administrator's Guide
 Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
VPN AND CITRIX INSTALLATION GUIDE
 Information Technology VPN AND CITRIX INSTALLATION GUIDE Overview of the CISCO SSL VPN Portal TMCC's Cisco SSL Virtual Private Network (VPN) portal was designed to give TMCC employees secure access to
Information Technology VPN AND CITRIX INSTALLATION GUIDE Overview of the CISCO SSL VPN Portal TMCC's Cisco SSL Virtual Private Network (VPN) portal was designed to give TMCC employees secure access to
THE EDINBURGH NAPIER UNIVERSITY WINDOWS VIRTUAL PRIVATE NETWORK (VPN) GUIDE FOR MAC USERS
 THE EDINBURGH NAPIER UNIVERSITY WINDOWS VIRTUAL PRIVATE NETWORK (VPN) GUIDE FOR MAC USERS INTRODUCTION... 2 WHAT SERVICES CAN I ACCESS USING THE VPN?... 2 WHAT ARE THE REQUIREMENTS OF THE VPN SERVICE?...
THE EDINBURGH NAPIER UNIVERSITY WINDOWS VIRTUAL PRIVATE NETWORK (VPN) GUIDE FOR MAC USERS INTRODUCTION... 2 WHAT SERVICES CAN I ACCESS USING THE VPN?... 2 WHAT ARE THE REQUIREMENTS OF THE VPN SERVICE?...
CBI s Corporate Internet Banking Inquiry Services gives you the ability to view account details and transactions anytime, anywhere.
 Benefits & Features CBI s Corporate Internet Banking Inquiry Services gives you the ability to view account details and transactions anytime, anywhere. What can I do with Internet Banking? You can inquire
Benefits & Features CBI s Corporate Internet Banking Inquiry Services gives you the ability to view account details and transactions anytime, anywhere. What can I do with Internet Banking? You can inquire
Vancouver Community College Web Orientation
 Access the myvcc Web Portal The myvcc portal provides a secure environment for VCC students to: Access VCC s Moodle online learning environment Access your student email (Microsoft Office365) Check your
Access the myvcc Web Portal The myvcc portal provides a secure environment for VCC students to: Access VCC s Moodle online learning environment Access your student email (Microsoft Office365) Check your
Using UWyo Wireless vs. WyoLync
 Winter 2013 In this issue: Lync - Making Conference Calls Simple IT - Helping You Stretch Your Dollar Windows OS Update Avoiding Phishing Top 4 Reasons to Use UWyo Wireless vs UW Guest Microsoft Updates
Winter 2013 In this issue: Lync - Making Conference Calls Simple IT - Helping You Stretch Your Dollar Windows OS Update Avoiding Phishing Top 4 Reasons to Use UWyo Wireless vs UW Guest Microsoft Updates
Frequently Asked Questions
 What is ecentral? Who can use ecentral? What can ecentral do? Frequently Asked Questions How do I start using ecentral? What if I forget my User ID? Step-by-step: How to find your User ID Can I change
What is ecentral? Who can use ecentral? What can ecentral do? Frequently Asked Questions How do I start using ecentral? What if I forget my User ID? Step-by-step: How to find your User ID Can I change
Millikin University Student Tech Training http://www.millikin.edu/it [email protected] 217.362.6488
 Millikin University Student Tech Training http://www.millikin.edu/it [email protected] 217.362.6488 mymillikin (my.millikin.edu) A means to access Millikin applications, discussion boards and announcements
Millikin University Student Tech Training http://www.millikin.edu/it [email protected] 217.362.6488 mymillikin (my.millikin.edu) A means to access Millikin applications, discussion boards and announcements
Student ANGEL FAQs. General Issues: System Requirements:
 Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
Remote Access - Mac OS X
 Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Frequently Asked Questions
 Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
Business ebanking Fraud Prevention Best Practices
 Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
Business ebanking Fraud Prevention Best Practices User ID and Password Guidelines Create a strong password with at least 8 characters that includes a combination of mixed case letters, numbers, and special
ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS
 $ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
$ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
TUT IT services www.tut.fi/pop > STUDY INFO > IT Services
 TUT IT services www.tut.fi/pop > STUDY INFO > IT Services TUT IT Helpdesk The single point of contact for all your IT-related questions When you contact the IT Helpdesk by email, please include the following
TUT IT services www.tut.fi/pop > STUDY INFO > IT Services TUT IT Helpdesk The single point of contact for all your IT-related questions When you contact the IT Helpdesk by email, please include the following
New Employee Technology Orientation
 New Employee Technology Orientation Policies Division of Information Technology Services Policies IT@Sam has several policies with which you should familiarize yourself. Those policies can be found online
New Employee Technology Orientation Policies Division of Information Technology Services Policies IT@Sam has several policies with which you should familiarize yourself. Those policies can be found online
VPN: Virtual Private Network Setup Instructions
 VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
VPN: Virtual Private Network Setup Instructions Virtual Private Network (VPN): For e-journals and web-based databases, plus applications like EndNote's Online Search (formerly "Connect") and business systems.
Security considerations are denoted by a lock icon.
 About This Guide This guide introduces you to some of the technology resources available at the University of Iowa, with the aim of making those resources easily accessible to you. It is an overview of
About This Guide This guide introduces you to some of the technology resources available at the University of Iowa, with the aim of making those resources easily accessible to you. It is an overview of
ViRobot Desktop 5.5. User s Guide
 ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
Macs are not directly compatible with Noetix.
 Those that use Macintosh computers to access Noetix cannot directly access Noetix through http://www.sandiego.edu/noetix. If one is on a Mac and goes to Noetix directly in a web browser, the page is likely
Those that use Macintosh computers to access Noetix cannot directly access Noetix through http://www.sandiego.edu/noetix. If one is on a Mac and goes to Noetix directly in a web browser, the page is likely
Information Technology Department. Miller School of Medicine New User Guide
 Information Technology Department Miller School of Medicine New User Guide EDUCATION & COMMUNICATIONS Miller School of Medicine New User Guide 1051 NW 14 th Street #165, Miami, FL 33136 (305) 243-5999
Information Technology Department Miller School of Medicine New User Guide EDUCATION & COMMUNICATIONS Miller School of Medicine New User Guide 1051 NW 14 th Street #165, Miami, FL 33136 (305) 243-5999
Cox Business Premium Security Service FAQs
 FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac?
 Enterprise Computing & Service Management How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend
Enterprise Computing & Service Management How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend
High Speed Internet - User Guide. Welcome to. your world.
 High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
High Speed Internet - User Guide Welcome to your world. 1 Welcome to your world :) Thank you for choosing Cogeco High Speed Internet. Welcome to your new High Speed Internet service. When it comes to a
Why you need. McAfee. Multi Acess PARTNER SERVICES
 Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
ITSC Training Courses Student IT Competence Programme SIIS1 Information Security
 ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
ITSC Training Courses Student IT Competence Programme SI1 2012 2013 Prof. Chan Yuen Yan, Rosanna Department of Engineering The Chinese University of Hong Kong SI1-1 Course Outline What you should know
ONE Mail Direct for Mobile Devices
 ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning
 Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning Lee Zelyck Network Administrator Regina Public Library Malware, Spyware, Trojans
Spam, Spyware, Malware and You! Don't give up just yet! Presented by: Mervin Istace Provincial Library Saskatchewan Learning Lee Zelyck Network Administrator Regina Public Library Malware, Spyware, Trojans
U.S. Cellular Mobile Data Security. User Guide Version 00.01
 U.S. Cellular Mobile Data Security User Guide Version 00.01 Table of Contents Install U.S. Cellular Mobile Data Security...3 Activate U.S. Cellular Mobile Data Security...3 Main Interface...3 Checkup...4
U.S. Cellular Mobile Data Security User Guide Version 00.01 Table of Contents Install U.S. Cellular Mobile Data Security...3 Activate U.S. Cellular Mobile Data Security...3 Main Interface...3 Checkup...4
Student Access Reference Guide
 Student Access Reference Guide Table of Contents Student Access Overview... 2 Logging on to the Student Portal... 3 Password Security Question Setup... 4 Need Help Signing In... 6 Navigating the Student
Student Access Reference Guide Table of Contents Student Access Overview... 2 Logging on to the Student Portal... 3 Password Security Question Setup... 4 Need Help Signing In... 6 Navigating the Student
How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus?
 Haas How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus? The Cisco virtual private network (VPN) client allows a computer to make secure network connections via specific
Haas How do I Install and Use the Cisco VPN Any Connect Client for the Berkeley Campus? The Cisco virtual private network (VPN) client allows a computer to make secure network connections via specific
Activating Wake on LAN/Remote Access for Your Office Computer
 EXSEED Client Integration Testing Version 1.0 Activating Wake on LAN/Remote Access for Your Office Computer This guide is intended to show you how to activate your office computer for the Wake on LAN service,
EXSEED Client Integration Testing Version 1.0 Activating Wake on LAN/Remote Access for Your Office Computer This guide is intended to show you how to activate your office computer for the Wake on LAN service,
Frequently Asked Questions The next section includes FAQs to help you to access and use your student email account.
 Factsheet 22 Student Email September 2011 This factsheet can be made available in alternative formats. Please make your request at the Library Help Desk, telephone 01642 342100 or email [email protected]
Factsheet 22 Student Email September 2011 This factsheet can be made available in alternative formats. Please make your request at the Library Help Desk, telephone 01642 342100 or email [email protected]
Windows and MAC User Handbook Remote and Secure Connection Version 1.01 09/19/2013. User Handbook
 Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
Windows and MAC User Handbook How to Connect Your PC or MAC Remotely and Securely to Your U.S. Department of Commerce Account Developed for You by the Office of IT Services (OITS)/IT Service Desk *** For
Setting up VPN and Remote Desktop for Home Use
 Setting up VPN and Remote Desktop for Home Use Contents I. Prepare Your Work Computer... 1 II. Prepare Your Home Computer... 2 III. Run the VPN Client... 3-4 IV. Remote Connect to Your Work Computer...
Setting up VPN and Remote Desktop for Home Use Contents I. Prepare Your Work Computer... 1 II. Prepare Your Home Computer... 2 III. Run the VPN Client... 3-4 IV. Remote Connect to Your Work Computer...
Business Internet Banking / Cash Management Fraud Prevention Best Practices
 Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
Business Internet Banking / Cash Management Fraud Prevention Best Practices This document provides fraud prevention best practices that can be used as a training tool to educate new Users within your organization
MyAACC Anne Arundel Comm om uni ty C y ollege
 What is MyAACC? MyAACC It is your online connection to AACC. It gives you access to many on-campus services online instead of requiring visits to the campus. What are you able to do with MyAACC? Search,
What is MyAACC? MyAACC It is your online connection to AACC. It gives you access to many on-campus services online instead of requiring visits to the campus. What are you able to do with MyAACC? Search,
Thank you for choosing Zoom Internet!
 Thank you for choosing Zoom Internet! We know you are going to love the speed, convenience and reliability of Zoom s super fast, always on connectivity to the Web! This guide provides helpful information
Thank you for choosing Zoom Internet! We know you are going to love the speed, convenience and reliability of Zoom s super fast, always on connectivity to the Web! This guide provides helpful information
User's Manual. Intego Remote Management Console User's Manual Page 1
 User's Manual Intego Remote Management Console User's Manual Page 1 Intego Remote Management Console for Macintosh 2007 Intego, Inc. All Rights Reserved Intego, Inc. www.intego.com This manual was written
User's Manual Intego Remote Management Console User's Manual Page 1 Intego Remote Management Console for Macintosh 2007 Intego, Inc. All Rights Reserved Intego, Inc. www.intego.com This manual was written
New Student Orientation Information Technology Packet
 New Student Orientation Information Technology Packet Welcome Welcome to the College of Nursing (CoN)! The Information Technology (IT) Department provides technical support to students, faculty, and staff.
New Student Orientation Information Technology Packet Welcome Welcome to the College of Nursing (CoN)! The Information Technology (IT) Department provides technical support to students, faculty, and staff.
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM
 REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
REMOTELY ACCESS YOUR FILES WITH THE FLAGLER FILECONNECT SYSTEM This document explains the various ways to connect to your network files and group share data. In addition, staff and full-time faculty are
Off-Campus Piratedrive Connection Using VPN
 Off-Campus Piratedrive Connection Using VPN Mac OS X Off-campus students, staff and faculty are required to open a Virtual Private Network (VPN) connection through which to access on-campus resources like
Off-Campus Piratedrive Connection Using VPN Mac OS X Off-campus students, staff and faculty are required to open a Virtual Private Network (VPN) connection through which to access on-campus resources like
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Yale School of Art Digital Technology Office Information
 Yale School of Art Digital Technology Office Information Online: http://art.yale.edu/diglab/ Email: [email protected] Phone: 203-432- 9120 Edgewood Email: [email protected] The Digital Technology
Yale School of Art Digital Technology Office Information Online: http://art.yale.edu/diglab/ Email: [email protected] Phone: 203-432- 9120 Edgewood Email: [email protected] The Digital Technology
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Mac OS X: INSTALLING TUNNELBLICK
 Mac OS X: INSTALLING TUNNELBLICK 1. Download "Tunnelblick" for Mac OS X from the UWG VPN website. Go to http://vpn.westga.edu. You will find a link to the installation file on the right hand side of the
Mac OS X: INSTALLING TUNNELBLICK 1. Download "Tunnelblick" for Mac OS X from the UWG VPN website. Go to http://vpn.westga.edu. You will find a link to the installation file on the right hand side of the
Working Together - Your Apple Mac and Microsoft Windows
 Contains information about complex concepts and /or requires technical knowledge to get the most out of the article. Aimed at the more experienced / ambitious ICT manager or accidental techie. Working
Contains information about complex concepts and /or requires technical knowledge to get the most out of the article. Aimed at the more experienced / ambitious ICT manager or accidental techie. Working
PowerSchool Parent Portal User Guide. PowerSchool 7.x Student Information System
 PowerSchool 7.x Student Information System Released December 2011 Document Owner: Documentation Services This edition applies to Release 7.1 of the [product name] software and to all subsequent releases
PowerSchool 7.x Student Information System Released December 2011 Document Owner: Documentation Services This edition applies to Release 7.1 of the [product name] software and to all subsequent releases
Recommended Settings for PACS HRS-d/eJacket via Remote Access
 The Main Line Health (MLH) system can be accessed through the Internet using the MLH Extranet Portal. The Extranet Portal gives users access to the MLH Intranet, PACS Horizon RadStation Distributed (HRS-d),
The Main Line Health (MLH) system can be accessed through the Internet using the MLH Extranet Portal. The Extranet Portal gives users access to the MLH Intranet, PACS Horizon RadStation Distributed (HRS-d),
https://it.cmich.edu HELP DESK Park Library 101 989.774.3662
 https://it.cmich.edu HELP DESK Park Library 101 989.774.3662 Top Two Questions Does our Student get this information? What kind of computer should we get? New Computer Purchases https://www.cmubookstore.com
https://it.cmich.edu HELP DESK Park Library 101 989.774.3662 Top Two Questions Does our Student get this information? What kind of computer should we get? New Computer Purchases https://www.cmubookstore.com
BEST / Act 230 Funding
 BEST / Act 230 Funding GRANTIUM APPLICATION INSTRUCTIONS FOR FY 16 (2015 2016 Academic Year) Table of Contents Logging into Grantium and Changing Your Password... 3 Forgot Your Password?... 4 How to Get
BEST / Act 230 Funding GRANTIUM APPLICATION INSTRUCTIONS FOR FY 16 (2015 2016 Academic Year) Table of Contents Logging into Grantium and Changing Your Password... 3 Forgot Your Password?... 4 How to Get
About This Guide. Security considerations are denoted by a lock icon.
 About This Guide This guide introduces students to some of the technology resources available at the University of Iowa, with the aim of making those resources easily accessible. It is an overview of the
About This Guide This guide introduces students to some of the technology resources available at the University of Iowa, with the aim of making those resources easily accessible. It is an overview of the
Contents. McAfee Internet Security 3
 User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
The initial set up takes a few steps, but then each time you want to connect it is just a two set process.
 Remote Access to your Desktop using VPN Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from
Remote Access to your Desktop using VPN Overview VPN is a tool that enables you to access one computer from another. Typical uses for Pop Center members would be 1) access their pop center computer from
MAPPING THE WEBDRIVE REFERENCE GUIDE
 MAPPING THE WEBDRIVE REFERENCE GUIDE INTRODUCTION The university WebDrive is a dedicated drive to host all university web content. For help with mapping the WebDrive, please read the instructions below
MAPPING THE WEBDRIVE REFERENCE GUIDE INTRODUCTION The university WebDrive is a dedicated drive to host all university web content. For help with mapping the WebDrive, please read the instructions below
UCL Remote Access VPN Service Mac OS X User Guide
 INFORMATION SERVICES DIVISION (ISD) NETWORK SERVICES GROUP UCL Remote Access VPN Service Mac OS X User Guide Version 3.0 Date 14 th November 2012 Author MC Document Details N/A Last Updated 05 November
INFORMATION SERVICES DIVISION (ISD) NETWORK SERVICES GROUP UCL Remote Access VPN Service Mac OS X User Guide Version 3.0 Date 14 th November 2012 Author MC Document Details N/A Last Updated 05 November
Cyber Security Awareness
 Cyber Security Awareness User IDs and Passwords Home Computer Protection Protecting your Information Firewalls Malicious Code Protection Mobile Computing Security Wireless Security Patching Possible Symptoms
Cyber Security Awareness User IDs and Passwords Home Computer Protection Protecting your Information Firewalls Malicious Code Protection Mobile Computing Security Wireless Security Patching Possible Symptoms
Using TS-ACCESS for Remote Desktop Access
 Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
General Questions... 1. Requesting Access... 2. Client Support... 3. Downloading Issues... 4. Installation Issues... 4. Connectivity Issues...
 Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
Contents General Questions... 1 Requesting Access... 2 Client Support... 3 Downloading Issues... 4 Installation Issues... 4 Connectivity Issues... 5 Performance Issues... 7 Application Issues... 8 General
Sophos Enterprise Console Help. Product version: 5.1 Document date: June 2012
 Sophos Enterprise Console Help Product version: 5.1 Document date: June 2012 Contents 1 About Enterprise Console...3 2 Guide to the Enterprise Console interface...4 3 Getting started with Sophos Enterprise
Sophos Enterprise Console Help Product version: 5.1 Document date: June 2012 Contents 1 About Enterprise Console...3 2 Guide to the Enterprise Console interface...4 3 Getting started with Sophos Enterprise
Yale Software Library
 Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Remote Desktop for Macintosh connection to Windows MS Remote Desktop Client
Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Remote Desktop for Macintosh connection to Windows MS Remote Desktop Client
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac?
 How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend the MS Remote Desktop for Mac client.
How do I Install and Configure MS Remote Desktop for the Haas Terminal Server on my Mac? In order to connect remotely to a PC computer from your Mac, we recommend the MS Remote Desktop for Mac client.
How To Install A Cisco Vpn Client V4.9.9 On A Mac Or Ipad (For A University)
 Cisco VPN Client v4.9.x for Mac OS X 10.4-10.5.x: Installation and Usage Guide Revised July 2009 by UTHSCSA IMS Departments of Client Support Services and Systems & Network Operations INTRODUCTION If you
Cisco VPN Client v4.9.x for Mac OS X 10.4-10.5.x: Installation and Usage Guide Revised July 2009 by UTHSCSA IMS Departments of Client Support Services and Systems & Network Operations INTRODUCTION If you
Accessing Restricted University Online Resources Using Network Connect. on the Secure Remote Access Service
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Accessing Restricted University Online Resources Using Network Connect Table of Contents Overview... 1 Connecting to the Secure Remote
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Accessing Restricted University Online Resources Using Network Connect Table of Contents Overview... 1 Connecting to the Secure Remote
Computing Orientation
 Computing Orientation Welcome to Carnegie Mellon! Computing Orientation Online Orientation Computing Resources Websites Security Online Orientation http://www.heinz.cmu.edu Current Students -> Computing
Computing Orientation Welcome to Carnegie Mellon! Computing Orientation Online Orientation Computing Resources Websites Security Online Orientation http://www.heinz.cmu.edu Current Students -> Computing
Research Information Security Guideline
 Research Information Security Guideline Introduction This document provides general information security guidelines when working with research data. The items in this guideline are divided into two different
Research Information Security Guideline Introduction This document provides general information security guidelines when working with research data. The items in this guideline are divided into two different
Welcome to the UVU IT Help Desk
 Welcome to the UVU IT Help Desk Agenda 1. Getting Procedures Help 2. Network & EMail 3. UVLink Portal 4. Professional Web Pages 5. Security 6. Outages & Emergencies 7. Software Getting Help Phone 863-8888
Welcome to the UVU IT Help Desk Agenda 1. Getting Procedures Help 2. Network & EMail 3. UVLink Portal 4. Professional Web Pages 5. Security 6. Outages & Emergencies 7. Software Getting Help Phone 863-8888
TUSCULUM COLLEGE. Ellucian Go: Installing and using the mobile application
 TUSCULUM COLLEGE Ellucian Go: Installing and using the mobile application ABOUT THE ELLUCIAN GO MOBILE APPLICATION The Ellucian Go Mobile application allows students with iphones and Android smartphones
TUSCULUM COLLEGE Ellucian Go: Installing and using the mobile application ABOUT THE ELLUCIAN GO MOBILE APPLICATION The Ellucian Go Mobile application allows students with iphones and Android smartphones
Information Technology Services technology immersion for new employees
 Information Technology Services technology immersion for new employees Technology Immersion At CWRU The ITS Mission: To provide for the information technology needs of the campus community We re always
Information Technology Services technology immersion for new employees Technology Immersion At CWRU The ITS Mission: To provide for the information technology needs of the campus community We re always
Steps for: POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) setup on MAC Platforms
 Steps for: POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) setup on MAC Platforms The following instructions offer options for POP and IMAP e-mail retrieval locally on your MAC.
Steps for: POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) setup on MAC Platforms The following instructions offer options for POP and IMAP e-mail retrieval locally on your MAC.
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
New ehealth Computer Account User Information. July 2014
 New ehealth Computer Account User Information July 2014 Security and Identification Manitoba ehealth takes very seriously the need to protect your computer account along with the confidential data and
New ehealth Computer Account User Information July 2014 Security and Identification Manitoba ehealth takes very seriously the need to protect your computer account along with the confidential data and
COLORADO DEPARTMENT OF LABOR AND EMPLOYMENT STANDARD POLICY AND PROCEDURE. Remote Access and Security I. PURPOSE.2 II. BACKGROUND.
 COLORADO DEPARTMENT OF LABOR AND EMPLOYMENT STANDARD POLICY AND PROCEDURE S T A N D A R D P O L I C Y A N D P R O C E D U R E COLORADO DEPARTMENT OF LABOR AND EMPLOYMENT 1515 Arapahoe Street Denver Colorado
COLORADO DEPARTMENT OF LABOR AND EMPLOYMENT STANDARD POLICY AND PROCEDURE S T A N D A R D P O L I C Y A N D P R O C E D U R E COLORADO DEPARTMENT OF LABOR AND EMPLOYMENT 1515 Arapahoe Street Denver Colorado
ecstudent-ts Terminal Server How to Use
 ecstudent-ts Terminal Server How to Use Connect to Cisco Any Connect Connect to Terminal Server, Set Options to Use Home Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network
ecstudent-ts Terminal Server How to Use Connect to Cisco Any Connect Connect to Terminal Server, Set Options to Use Home Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network
MSD IT High Compliance system Fact sheet
 MSD IT High Compliance system Fact sheet The MSD IT High Compliance system is a service for Clinical Trials Units (CTUs) and Medical Division Departments or Units who need to securely access critical applications,
MSD IT High Compliance system Fact sheet The MSD IT High Compliance system is a service for Clinical Trials Units (CTUs) and Medical Division Departments or Units who need to securely access critical applications,
This guide provides all of the information necessary to connect to MoFo resources from outside of the office
 REMOTE ACCESS GUIDE INTRODUCTION This guide provides all of the information necessary to connect to MoFo resources from outside of the office Links to topics in this document Connect remotely from your
REMOTE ACCESS GUIDE INTRODUCTION This guide provides all of the information necessary to connect to MoFo resources from outside of the office Links to topics in this document Connect remotely from your
GREEN HOUSE DATA. E-Mail Services Guide. Built right. Just for you. greenhousedata.com. Green House Data 340 Progress Circle Cheyenne, WY 82007
 GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
Accessing TP SSL VPN
 Accessing TP SSL VPN This guide describes the steps to install, connect and disconnect the SSL VPN for remote access to TP intranet systems using personal notebooks. A. Installing the SSL VPN client Junos
Accessing TP SSL VPN This guide describes the steps to install, connect and disconnect the SSL VPN for remote access to TP intranet systems using personal notebooks. A. Installing the SSL VPN client Junos
Secured Remote Access Using Cisco AnyConnect with your Grid Card or Token Information Technology Services January 2015
 Secured Remote Access Using Cisco AnyConnect with your Grid Card or Token Information Technology Services January 2015 The following instructions are for connecting to the UNMC/Nebraska Medicine campus
Secured Remote Access Using Cisco AnyConnect with your Grid Card or Token Information Technology Services January 2015 The following instructions are for connecting to the UNMC/Nebraska Medicine campus
Secure Share (Novell Filr) Remote Teacher Video Sharing Process School Year 2014-2015
 Secure Share (Novell Filr) Remote Teacher Video Sharing Process School Year 2014-2015 UTHealth Secure Share (Novell Filr) is a Family Educational Rights and Privacy Act (FERPA) compliant online system
Secure Share (Novell Filr) Remote Teacher Video Sharing Process School Year 2014-2015 UTHealth Secure Share (Novell Filr) is a Family Educational Rights and Privacy Act (FERPA) compliant online system
Manchester Community College Student Technology Handbook. How to log into campus PCs
 Manchester Community College Student Technology Handbook How to log into campus PCs... 1 mycommnet... 4 The mycommnet Homepage... 5 Blackboard Vista... 6 Remember to LOG OUT... 7 Technical Support... 8
Manchester Community College Student Technology Handbook How to log into campus PCs... 1 mycommnet... 4 The mycommnet Homepage... 5 Blackboard Vista... 6 Remember to LOG OUT... 7 Technical Support... 8
INFORMATION SECURITY BASICS. A computer security tutorial for Holyoke Community College
 INFORMATION SECURITY BASICS A computer security tutorial for Holyoke Community College I NTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
INFORMATION SECURITY BASICS A computer security tutorial for Holyoke Community College I NTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
Accessing the SUNYIT wireless network for the first time
 Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Connecting to securevirtual Workspace
 Connecting to securevirtual Workspace The following document provides information on connecting to securevirtual Workspace. This Document includes: Connecting Using Remote Desktop Connection (RDC) Connecting
Connecting to securevirtual Workspace The following document provides information on connecting to securevirtual Workspace. This Document includes: Connecting Using Remote Desktop Connection (RDC) Connecting
ecfshome-ts Terminal Server How to Use
 ecfshome-ts Terminal Server How to Use Connect to VPN Connect to Terminal Server, Set Options to Use Personal Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network Folders to
ecfshome-ts Terminal Server How to Use Connect to VPN Connect to Terminal Server, Set Options to Use Personal Computer Files, Printers, Clipboard Use Network Folders Copy Files from Network Folders to
FAQ. How does the new Big Bend Backup (powered by Keepit) work?
 FAQ How does the new Big Bend Backup (powered by Keepit) work? Once you establish which of the folders on your hard drive you ll be backing up, you ll log into myaccount.bigbend.net and from your control
FAQ How does the new Big Bend Backup (powered by Keepit) work? Once you establish which of the folders on your hard drive you ll be backing up, you ll log into myaccount.bigbend.net and from your control
How to find your VCCS username, password, and emplid to access NOVAConnect and Blackboard
 Faculty and staff at NOVA have access to many technology tools. The IT Help Desk, the Extended Learning Institute (ELI), and the Technology Applications Center (TAC) provide college-wide support in addition
Faculty and staff at NOVA have access to many technology tools. The IT Help Desk, the Extended Learning Institute (ELI), and the Technology Applications Center (TAC) provide college-wide support in addition
Mortgage Quest WebDesk Setup and Login Instructions
 Initial WebDesk Setup Mortgage Quest WebDesk Setup and Login Instructions 1. The following steps need to be performed one time only. 2. Start Microsoft Internet Explorer. 3. Enter the address: http://webdesk.emarketfocus.com/
Initial WebDesk Setup Mortgage Quest WebDesk Setup and Login Instructions 1. The following steps need to be performed one time only. 2. Start Microsoft Internet Explorer. 3. Enter the address: http://webdesk.emarketfocus.com/
Getting credit for completing this lab
 Lab Exercise: Introduction to Microsoft SharePoint The purpose of this lab is to give you an introduction to Microsoft SharePoint, a team collaboration software technology. As the use of SharePoint grows
Lab Exercise: Introduction to Microsoft SharePoint The purpose of this lab is to give you an introduction to Microsoft SharePoint, a team collaboration software technology. As the use of SharePoint grows
Password Management Help
 Release: v1.7 Date: 24.12.08 DET SINGLE SIGN-ON ACCOUNT... 2 USER VALIDATION QUESTION... 3 FORGOT MY PASSWORD... 4 CHANGING PASSWORDS... 5 CHANGING PASSWORDS (CONTINUED)... 6 v1.7.doc Page 1 of 6 DET Single
Release: v1.7 Date: 24.12.08 DET SINGLE SIGN-ON ACCOUNT... 2 USER VALIDATION QUESTION... 3 FORGOT MY PASSWORD... 4 CHANGING PASSWORDS... 5 CHANGING PASSWORDS (CONTINUED)... 6 v1.7.doc Page 1 of 6 DET Single
Student Getting Started Guide
 with with Student Getting Started Guide TABLE OF CONTENTS Table of Contents FIRST STEPS TO ENSURE SUCCESS... 3 Ensure System Requirements are met on Your Computer... 3 Find Out Which Operating System Is
with with Student Getting Started Guide TABLE OF CONTENTS Table of Contents FIRST STEPS TO ENSURE SUCCESS... 3 Ensure System Requirements are met on Your Computer... 3 Find Out Which Operating System Is
