LTE Tutorial GSM Tutorial i
|
|
|
- Holly Moore
- 9 years ago
- Views:
Transcription
1 GSM Tutorial i
2 GLOBAL SYSTEM FOR MOBILE COMMUNICATIONS (GSM) TUTORIAL Simply Easy Learning by tutorialspoint.com tutorialspoint.co ii
3 ABOUT THE TUTORIAL GSM Tutorial GSM is a globally accepted standard for digital cellular communications. GSM uses narrowband Time Division Multiple Access (TDMA) for providing voice and text based services over mobile phone networks. Audience This tutorial has been designed for readers who want to understand the basics of GSM in very simple terms. This tutorial provides just about enough material to have a solid foundation on GSM from where you can move on to higher levels of expertise. Prerequisites A general awareness of some basics of telecommunications is sufficient to understand the concepts explained in this tutorial. 1
4 Copyright & Disclaimer Notice Copyright 2014 by Tutorials Point Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutotorials Point Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. This tutorial may contain inaccuracies or errors. Tutorials Point Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. If you discover any errors on our website or in this tutorial, please notify us at [email protected] 2
5 Table of Contents Overview... 5 What is GSM?... 5 Why GSM?... 6 GSM History:... 6 GSM Architecture... 8 GSM network areas:... 9 GSM Specification Modulation: Access Methods: Transmission Rate: Frequency Band: Channel Spacing: Speech Coding: Duplex Distance: Misc: GSM Addressing and Identifiers International Mobile Station Equipment Identity (IMEI): International Mobile Subscriber Identity ( IMSI): Mobile Subscriber ISDN Number ( MSISDN): Mobile Station Roaming Number ( MSRN): Location Area Identity (LAI): Temporary Mobile Subscriber Identity (TMSI): Local Mobile Subscriber Identity (LMSI):... Error! Bookmark not defined. Cell Identifier (CI):... Error! Bookmark not defined. GSM Operations... Error! Bookmark not defined. Call from Mobile Phone to Public Switched Telephone Network (PSTN):... Error! Bookmark not defined. Call from PSTN to Mobile Phone:... Error! Bookmark not defined. GSM Protocol Stack MS Protocols: The Mobile Station (MS) to Base Tranceiver Station (BTS) Protocols:... Error! Bookmark not defined. 3
6 BSC Protocols: MSC Protocols:... Error! Bookmark not defined. GSM User Services... Error! Bookmark not defined. 1. Teleservices or Telephony Services:... Error! Bookmark not defined. VOICE CALLS:... Error! Bookmark not defined. VIDEOTEXT AND FACSMILE:... Error! Bookmark not defined. SHORT TEXT MESSAGES:... Error! Bookmark not defined. 2. Bearer Services or Data Services... Error! Bookmark not defined. 3. Supplementary Services... Error! Bookmark not defined. GSM Security and Encryption... Error! Bookmark not defined. Mobile Station Authentication:... Error! Bookmark not defined. Signaling and Data Confidentiality:... Error! Bookmark not defined. Subscriber Identity Confidentiality:... Error! Bookmark not defined. GSM Billing... Error! Bookmark not defined. Telephony Service:... Error! Bookmark not defined. SMS Service:... Error! Bookmark not defined. GPRS Services... Error! Bookmark not defined. Supplementary Services... Error! Bookmark not defined. GSM Mobile Phones... Error! Bookmark not defined. GSM Enabled Phones... Error! Bookmark not defined. 4
7 CHAPTER 1 Overview What is GSM? If you are in Europe or Asia and using a mobile phone, then most probably you are using GSM technology in your mobile phone. GSM stands for Global System for Mobile Communication. It is a digital cellular technology used for transmitting mobile voice and data services. The concept of GSM emerged from a cell-based mobile radio system at Bell Laboratories in the early 1970s. GSM is the name of a standardization group established in 1982 to create a common European mobile telephone standard. GSM is the most widely accepted standard in telecommunications and it is implemented globally. GSM is a circuit-switched system that divides each 200 khz channel into eight 25 khz timeslots. GSM operates on the mobile communication bands 900 MHz and 1800 MHz in most parts of the world. In the US, GSM operates in the bands 850 MHz and 1900 MHz. GSM owns a market share of more than 70 percent of the world's digital cellular subscribers. GSM makes use of narrowband Time Division Multiple Access (TDMA) technique for transmitting signals. GSM was developed using digital technology. It has an ability to carry 64 kbps to 120 Mbps of data rates. Presently GSM supports more than one billion mobile subscribers in more than 210 countries throughout the world. GSM provides basic to advanced voice and data services including roaming service. Roaming is the ability to use your GSM phone number in another GSM network. GSM digitizes and compresses data, then sends it down through a channel with two other streams of user data, each in its own timeslot. 5
8 Why GSM? Listed below are the features of GSM that account for its popularity and wide accepatance. Improved spectrum efficiency International roaming Low-cost mobile sets and base stations (BSs) High-quality speech Compatibility with Integrated Services Digital Network (ISDN) and other telephone company services Support for new services GSM History The following table shows some of the important events in the rollout of the GSM system. Years Events 1982 Conference of European Posts and Telegraph (CEPT) establishes a GSM group to widen the standards for a pan-european cellular mobile system A list of recommendations to be generated by the group is accepted Executed field tests to check the different radio techniques recommended for the air interface. Time Division Multiple Access (TDMA) is chosen as the access method (with Frequency Division Multiple Access [FDMA]). The initial Memorandum of Understanding (MoU) is signed by telecommunication operators representing 12 countries GSM system is validated The European Telecommunications Standards Institute (ETSI) was given the responsibility of the GSM specifications Phase 1 of the GSM specifications is delivered Commercial launch of the GSM service occurs. The DCS1800 specifications are finalized. The addition of the countries that signed the GSM MoU takes place. Coverage spreads to larger cities and airports Coverage of main roads' GSM services starts outside Europe. 6
9 1994 Data transmission capabilities launched. The number of networks rises to 69 in 43 countries by the end of Phase 2 of the GSM specifications occurs. Coverage is extended to rural areas June: 133 networks in 81 countries operational July: 200 networks in 109 countries operational, around 44 million subscribers worldwide. Wireless Application Protocol (WAP) came into existence and became operational in 130 countries with 260 million subscribers General Packet Radio Service (GPRS) came into existence As of May 2001, over 550 million people were subscribers to mobile telecommunications. 7
10 CHAPTER 2 GSM Architecture A GSM network comprises of many functional units. These functions and interfaces are explained in this chapter. The GSM network can be broadly divided into: The Mobile Station (MS) The Base Station Subsystem (BSS) The Network Switching Subsystem (NSS) The Operation Support Subsystem (OSS) Given below is a simple pictorial view of the GSM architecture. 8
11 The additional components of the GSM architecture comprise of databases and messaging systems functions: Home Location Register (HLR) Visitor Location Register (VLR) Equipment Identity Register (EIR) Authentication Center (AuC) SMS Serving Center (SMS SC) Gateway MSC (GMSC) Chargeback Center (CBC) Transcoder and Adaptation Unit (TRAU) The following diagram shows the GSM netwrok along with the added elements: The MS and the BSS communicate across the Um interface. It is also known as the air interface or the radio link. The BSS communicates with the Network Service Switching (NSS) center across the A interface. GSM Network Areas In a GSM network, the following areas are defined: Cell: Cell is the basic service area; one BTS covers one cell. Each cell is given a Cell Global Identity (CGI), a number that uniquely identifies the cell. Location Area: A group of cells form a Location Area (LA). This is the area that is paged when a subscriber gets an incoming call. Each LA is assigned a Location Area Identity (LAI). Each LA is served by one or more BSCs. MSC/VLR Service Area: The area covered by one MSC is called the MSC/VLR service area. PLMN: The area covered by one network operator is called the Public Land Mobile Network (PLMN). A PLMN can contain one or more MSCs. 9
12 CHAPTER 3 GSM Specification The requirements for different Personal Communication Services (PCS) systems differ for each PCS network. Vital characteristics of the GSM specification are listed below: Modulation Modulation is the process of transforming the input data into a suitable format for the transmission medium. The transmitted data is demodulated back to its original form at the receiving end. The GSM uses Gaussian Minimum Shift Keying (GMSK) modulation method. Access Methods Radio spectrum being a limited resource that is consumed and divided among all the users, GSM devised a combination of TDMA/FDMA as the method to divide the bandwith among the users. In this process, the FDMA part divides the frequency of the total 25 MHz bandwidth into 124 carrier frequencies of 200 khz bandwidth. Each BS is assigned with one or multiple frequencies, and each of this frequency is divided into eight timeslots using a TDMA scheme. Each of these slots are used for both transmission as well as reception of data. These slots are separated by time so that a mobile unit doesn t transmit and receive data at the same time. Transmission Rate The total symbol rate for GSM at 1 bit per symbol in GMSK produces K symbols/second. The gross transmission rate of a timeslot is 22.8 Kbps. GSM is a digital system with an over-the-air bit rate of 270 kbps. 10
13 Frequency Band The uplink frequency range specified for GSM is MHz (basic 900 MHz band only). The downlink frequency band is MHz (basic 900 MHz band only). Channel Spacing Channel spacing indicates the spacing between adjacent carrier frequencies. For GSM, it is 200 khz. Speech Coding For speech coding or processing, GSM uses Linear Predictive Coding (LPC). This tool compresses the bit rate and gives an estimate of the speech parameters. When the audio signal passes through a filter, it mimics the vocal tract. Here, the speech is encoded at 13 kbps. Duplex Distance Duplex distance is the space between the uplink and downlink frequencies. The duplex distance for GSM is 80 MHz, where each channel has two frequencies that are 80 MHz apart. Miscellaneous Frame duration: ms Duplex Technique: Frequency Division Duplexing (FDD) access mode previously known as WCDMA. Speech channels per RF channel: 8. 11
14 CHAPTER 4 GSM Addressing and Identifiers GSM treats the users and the equipment in different ways. Phone numbers, subscribers, and equipment identifiers are some of the known ones. There are many other identifiers that have been well-defined, which are required for the subscriber s mobility management and for addressing the remaining network elements. Vital addresses and identifiers that are used in GSM are addressed below. International Mobile Station Equipment Identity The International Mobile Station Equipment Identity (IMEI) looks more like a serial number which distinctively identifies a mobile station internationally. This is allocated by the equipment manufacturer and registered by the network operator, who stores it in the Entrepreneurs-in- Residence (EIR). By means of IMEI, one recognizes obsolete, stolen, or non-functional equipment. Following are the parts of IMEI: Type Approval Code (TAC): 6 decimal places, centrally assigned. Final Assembly Code (FAC): 6 decimal places, assigned by the manufacturer. Serial Number (SNR): 6 decimal places, assigned by the manufacturer. Spare (SP): 1 decimal place. Thus, IMEI = TAC + FAC + SNR + SP. It uniquely characterizes a mobile station and gives clues about the manufacturer and the date of manufacturing. International Mobile Subscriber Identity Every registered user has an original International Mobile Subscribter Identity (IMSI) with a valid IMEI stored in their Subscriber Identity Module (SIM). 12
15 IMSI comprises of the following parts: Mobile Country Code (MCC): 3 decimal places, internationally standardized. Mobile Network Code (MNC): 2 decimal places, for unique identification of a mobile network within the country. Mobile Subscriber Identification Number (MSIN): Maximum 10 decimal places, identification number of the subscriber in the home mobile network. Mobile Subscriber ISDN Number The authentic telephone number of a mobile station is the Mobile Subscriber ISDN Number (MSISDN). Based on the SIM, a mobile station can have many MSISDNs, as each subscriber is assigned with a separate MSISDN to their SIM respectively. Listed below is the structure followed by MSISDN categories, as they are defined based on international ISDN number plan: Country Code (CC) : Up to 3 decimal places. National Destination Code (NDC): Typically 2 3 decimal places. Subscriber Number (SN): Maximum 10 decimal places. Mobile Station Roaming Number Mobile Station Roaming Number (MSRN) is an interim location dependent ISDN number, assigned to a mobile station by a regionally responsible Visitor Location Register (VLA). Using MSRN, the incoming calls are channeled to the MS. The MSRN has the same structure as the MSISDN. Country Code (CC) : of the visited network. National Destination Code (NDC): of the visited network. Subscriber Number (SN): in the current mobile network. Location Area Identity Within a PLMN, a Location Area identifies its own authentic Location Area Identity (LAI). The LAI hierarchy is based on international standard and structured in a unique format as mentioned below: Country Code (CC): 3 decimal places. Mobile Network Code (MNC): 2 decimal places. Location Area Code (LAC): maximum 5 decimal places or maximum twice 8 bits coded in hexadecimal (LAC < FFFF). 13
16 Temporary Mobile Subscriber Identity Temporary Mobile Subscriber Identity (TMSI) can be assigned by the VLR, which is responsible for the current location of a subscriber. The TMSI needs to have only local significance in the area handled by the VLR. This is stored on the network side only in the VLR and is not passed to the Home Location Register (HLR). Together with the current location area, the TMSI identifies a subscriber uniquely. It can contain up to 4 8 bits. Local Mobile Subscriber Identity Each mobile station can be assigned with a Local Mobile Subscriber Identity (LMSI), which is an original key, by the VLR. This key can be used as the auxiliary searching key for each mobile station within its region. It can also help accelerate the database access. An LMSI is assigned if the mobile station is registered with the VLR and sent to the HLR. LMSI comprises of four octets (4x8 bits). Cell Identifier Using a Cell Identifier (CI) (maximum 2 8) bits, the individual cells that are within an LA can be recognized. When the Global Cell Identity (LAI + CI) calls are combined, then it is uniquely defined. 14
17 CHAPTER 5 GSM Operations Once a Mobile Station initiates a call, a series of events takes place. Analyzing these events can give an insight into the operation of the GSM system. Mobile Phone to Public Switched Telephone Network (PSTN) When a mobile subscriber makes a call to a PSTN telephone subscriber, the following sequence of events takes place: 1. The MSC/VLR receives the message of a call request. 2. The MSC/VLR checks if the mobile station is authorized to access the network. If so, the mobile station is activated. If the mobile station is not authorized, then the service will be denied. 3. MSC/VLR analyzes the number and initiates a call setup with the PSTN. 4. MSC/VLR asks the corresponding BSC to allocate a traffic channel (a radio channel and a timeslot). 5. The BSC allocates the traffic channel and passes the information to the mobile station. 6. The called party answers the call and the conversation takes place. 7. The mobile station keeps on taking measurements of the radio channels in the present cell and the neighboring cells and passes the information to the BSC. The BSC decides if a handover is required. If so, a new traffic channel is allocated to the mobile station and the handover takes place. If handover is not required, the mobile station continues to transmit in the same frequency. PSTN to Mobile Phone When a PSTN subscriber calls a mobile station, the following sequence of events takes place: 1. The Gateway MSC receives the call and queries the HLR for the information needed to route the call to the serving MSC/VLR. 2. The GMSC routes the call to the MSC/VLR. 3. The MSC checks the VLR for the location area of the MS. 4. The MSC contacts the MS via the BSC through a broadcast message, that is, through a paging request. 5. The MS responds to the page request. 15
18 6. The BSC allocates a traffic channel and sends a message to the MS to tune to the channel. The MS generates a ringing signal and, after the subscriber answers, the speech connection is established. 7. Handover, if required, takes place, as discussed in the earlier case. To transmit the speech over the radio channel in the stipulated time, the MS codes it at the rate of 13 Kbps. The BSC transcodes the speech to 64 Kbps and sends it over a land link or a radio link to the MSC. The MSC then forwards the speech data to the PSTN. In the reverse direction, the speech is received at 64 Kbps at the BSC and the BSC transcodes it to 13 Kbps for radio transmission. GSM supports 9.6 Kbps data that can be channeled in one TDMA timeslot. To supply higher data rates, many enhancements were done to the GSM standards (GSM Phase 2 and GSM Phase 2+). 16
19 CHAPTER 6 GSM Protocol Stack GSM architecture is a layered model that is designed to allow communications between two different systems. The lower layers assure the services of the upper-layer protocols. Each layer passes suitable notifications to ensure the transmitted data has been formatted, transmitted, and received accurately. The GSM protocol stacks diagram is shown below: MS Protocols Based on the interface, the GSM signaling protocol is assembled into three general layers: 1. Layer 1: The physical layer. It uses the channel structures over the air interface. 2. Layer 2: The data-link layer. Across the Um interface, the data-link layer is a modified version of the Link Access Protocol for the D channel (LAP-D) protocol used in ISDN, called Link Access Protocol on the Dm channel (LAP-Dm). Across the A interface, the Message Transfer Part (MTP), Layer 2 of SS7 is used. 17
20 3. Layer 3: GSM signaling protocol s third layer is divided into three sublayers: Radio Resource Management (RR), Mobility Management (MM), and Connection Management (CM). MS to BTS Protocols The RR layer is the lower layer that manages a link, both radio and fixed, between the MS and the MSC. For this formation, the main components involved are the MS, BSS, and MSC. The responsibility of the RR layer is to manage the RR-session, the time when a mobile is in a dedicated mode, and the radio channels including the allocation of dedicated channels. The MM layer is stacked above the RR layer. It handles the functions that arise from the mobility of the subscriber, as well as the authentication and security aspects. Location management is concerned with the procedures that enable the system to know the current location of a poweredon MS so that incoming call routing can be completed. The CM layer is the topmost layer of the GSM protocol stack. This layer is responsible for Call Control, Supplementary Service Management, and Short Message Service Management. Each of these services are treated as individual layer within the CM layer. Other functions of the CC sublayer include call establishment, selection of the type of service (including alternating between services during a call), and call release. BSC Protocols The BSC uses a different set of protocols after receiving the data from the BTS. The Abis interface is used between the BTS and BSC. At this level, the radio resources at the lower portion of Layer 3 are changed from the RR to the Base Transceiver Station Management (BTSM). The BTS management layer is a relay function at the BTS to the BSC. The RR protocols are responsible for the allocation and reallocation of traffic channels between the MS and the BTS. These services include controlling the initial access to the system, paging for MT calls, the handover of calls between cell sites, power control, and call termination. The BSC still has some radio resource management in place for the frequency coordination, frequency allocation, and the management of the overall network layer for the Layer 2 interfaces. To transit from the BSC to the MSC, the BSS mobile application part or the direct application part is used, and SS7 protocols is applied by the relay, so that the MTP 1-3 can be used as the prime architecture. 18
21 MSC Protocols At the MSC, starting from the BSC, the information is mapped across the A interface to the MTP Layers 1 through 3. Here, Base Station System Management Application Part (BSS MAP) is said to be the equivalent set of radio resources. The relay process is finished by the layers that are stacked on top of Layer 3 protocols, they are BSS MAP/DTAP, MM, and CM. This completes the relay process. To find and connect to the users across the network, MSCs interact using the controlsignaling network. Location registers are included in the MSC databases to assist in the role of determining how and whether connections are to be made to roaming users. Each GSM MS user is given a HLR that in turn comprises of the user s location and subscribed services. VLR is a separate register that is used to track the location of a user. When the users move out of the HLR covered area, the VLR is notified by the MS to find the location of the user. The VLR in turn, with the help of the control network, signals the HLR of the MS s new location. With the help of location information contained in the user s HLR, the MT calls can be routed to the user. 19
22 CHAPTER 7 GSM User Services GSM offers much more than just voice telephony. Contact your local GSM network operator to the specific services that you can avail. GSM offers three basic types of services: Telephony services or teleservices Data services or bearer services Supplementary services Teleservices The abilities of a Bearer Service are used by a Teleservice to transport data. These services are further transited in the following ways: Voice Calls The most basic Teleservice supported by GSM is telephony. This includes full-rate speech at 13 kbps and emergency calls, where the nearest emergency-service provider is notified by dialing three digits. Videotext and Facsimile Another group of teleservices includes Videotext access, Teletex transmission, Facsimile alternate speech and Facsimile Group 3, Automatic facsimile Group 3, etc. 20
23 Shot Text Messages Short Messaging Service (SMS) service is a text messaging service that allows sending and receiving text messages on your GSM mobile phone. In addition to simple text messages, other text data including news, sports, financial, language, and location-based data can also be transmitted. Bearer Services Data services or Bearer Services are used through a GSM phone. to receive and send data is the essential building block leading to widespread mobile Internet access and mobile data transfer. GSM currently has a data transfer rate of 9.6k. New developments that will push up data transfer rates for GSM users are HSCSD (high speed circuit switched data) and GPRS (general packet radio service) are now available. Supplementary Services Supplementary services are additional services that are provided in addition to teleservices and bearer services. These services include caller identification, call forwarding, call waiting, multiparty conversations, and barring of outgoing (international) calls, among others. A brief description of supplementary services is given here: Conferencing: It allows a mobile subscriber to establish a multiparty conversation, i.e., a simultaneous conversation between three or more subscribers to setup a conference call. This service is only applicable to normal telephony. Call Waiting: This service notifies a mobile subscriber of an incoming call during a conversation. The subscriber can answer, reject, or ignore the incoming call. Call Hold: This service allows a subscriber to put an incoming call on hold and resume after awhile. The call hold service is applicable to normal telephony. Call Forwarding: Call Forwarding is used to divert calls from the original recipient to another number. It is normally set up by the subscriber himself. It can be used by the subscriber to divert calls from the Mobile Station when the subscriber is not available, and so to ensure that calls are not lost. Call Barring: Call Barring is useful to restrict certain types of outgoing calls such as ISD or stop incoming calls from undesired numbers. Call barring is a flexible service that enables the subscriber to conditionally bar calls. Number Identification: There are following supplementary services related to number identification: o Calling Line Identification Presentation: This service displays the telephone number of the calling party on your screen. 21
24 o o o o Calling Line Identification Restriction: A person not wishing their number to be presented to others subscribes to this service. Connected Line Identification Presentation: This service is provided to give the calling party the telephone number of the person to whom they are connected. This service is useful in situations such as forwardings where the number connected is not the number dialled. Connected Line Identification Restriction: There are times when the person called does not wish to have their numbers presented and so they would subscribe to this person. Normally, this overrides the presentation service. Malicious Call Identification: The malicious call identification service was provided to combat the spread of obscene or annoying calls. The victim should subscribe to this service, and then they could cause known malicious calls to be identified in the GSM network, using a simple command. Advice of Charge (AoC): This service was designed to give the subscriber an indication of the cost of the services as they are used. Furthermore, those service providers who wish to offer rental services to subscribers without their own SIM can also utilize this service in a slightly different form. AoC for data calls is provided on the basis of time measurements. Closed User Groups (CUGs): This service is meant for groups of subscribers who wish to call only each other and no one else. Unstructured Supplementary Services Data (USSD): This service allows operator-defined individual services. 22
25 CHAPTER 8 GSM Security and Encryption GSM is the most secured cellular telecommunications system available today. GSM has its security methods standardized. GSM maintains end-to-end security by retaining the confidentiality of calls and anonymity of the GSM subscriber. Temporary identification numbers are assigned to the subscriber s number to maintain the privacy of the user. The privacy of the communication is maintained by applying encryption algorithms and frequency hopping that can be enabled using digital systems and signaling. This chapter gives an outline of the security measures implemented for GSM subscribers. Mobile Station Authentication The GSM network authenticates the identity of the subscriber through the use of a challengeresponse mechanism. A 128-bit Random Number (RAND) is sent to the MS. The MS computes the 32-bit Signed Response (SRES) based on the encryption of the RAND with the authentication algorithm (A3) using the individual subscriber authentication key (Ki). Upon receiving the SRES from the subscriber, the GSM network repeats the calculation to verify the identity of the subscriber. The individual subscriber authentication key (Ki) is never transmitted over the radio channel, as it is present in the subscriber's SIM, as well as the AUC, HLR, and VLR databases. If the received SRES agrees with the calculated value, the MS has been successfully authenticated and may continue. If the values do not match, the connection is terminated and an authentication failure is indicated to the MS. The calculation of the signed response is processed within the SIM. It provides enhanced security, as confidential subscriber information such as the IMSI or the individual subscriber authentication key (Ki) is never released from the SIM during the authentication process. Signaling and Data Confidentiality The SIM contains the ciphering key generating algorithm (A8) that is used to produce the 64-bit ciphering key (Kc). This key is computed by applying the same random number (RAND) used in the authentication process to ciphering key generating algorithm (A8) with the individual subscriber authentication key (Ki). 23
26 GSM provides an additional level of security by having a way to change the ciphering key, making the system more resistant to eavesdropping. The ciphering key may be changed at regular intervals as required. As in case of the authentication process, the computation of the ciphering key (Kc) takes place internally within the SIM. Therefore, sensitive information such as the individual subscriber authentication key (Ki) is never revealed by the SIM. Encrypted voice and data communications between the MS and the network is accomplished by using the ciphering algorithm A5. Encrypted communication is initiated by a ciphering mode request command from the GSM network. Upon receipt of this command, the mobile station begins encryption and decryption of data using the ciphering algorithm (A5) and the ciphering key (Kc). Subscriber Identity Confidentiality To ensure subscriber identity confidentiality, the Temporary Mobile Subscriber Identity (TMSI) is used. Once the authentication and encryption procedures are done, the TMSI is sent to the mobile station. After the receipt, the mobile station responds. The TMSI is valid in the location area in which it was issued. For communications outside the location area, the Location Area Identification (LAI) is necessary in addition to the TMSI. 24
27 CHAPTER 9 GSM Billing GSM service providers are doing billing based on the services they are providing to their customers. All the parameters are simple enough to charge a customer for the provided services. This chapter provides an overview of the frequently used billing techniques and parameters applied to charge a GSM subscriber. Telephony Service These services can be charged on per call basis. The call initiator has to pay the charges, and the incoming calls are nowadays free. A customer can be charged based on different parameters such as: International call or long distance call. Local call Call made during peak hours. Call made during night time Discounted call during weekends. Call per minute or per second. Many more other criteria can be designed by a service provider to charge their customers. SMS Service Most of the service providers charge their customers SMS services based on the number of text messages sent. There are other prime SMS services available where service providers charge more than normal SMS charge. These services are being availed in collaboration of Television Networks or Radio Networks to demand SMS from the audiences. Most of the time, the charges are paid by the SMS sender but for some services like stocks and share prices, mobile banking facilities, and leisure booking services, etc. the recipient of the SMS has to pay for the service. 25
28 GPRS Services Using GPRS service, you can browse, play games on the Internet, and download movies. So a service provider will charge you based on the data uploaded as well as data downloaded on your mobile phone. These charges will be based on per Kilo Byte data downloaded/uploaded. Additional parameter could be a QoS provided to you. If you want to watch a movie, then a low QoS may work because some data loss may be acceptable, but if you are downloading a zip file, then a single byte loss will corrupt your complete downloaded file. Another parameter could be peak and off peak time to download a data file or to browse the Internet. Supplementary Services Most of the supplementary services are being provided based on monthly rental or absolutely free. For example, call waiting, call forwarding, calling number identification, and call on hold are available at zero cost. Call barring is a service, which service providers use just to recover their dues, etc., otherwise this service is not being used by any subscriber. Call conferencing service is a form of simple telephone call where the customers are charged for multiple calls made at a time. No service provider charges extra charge for this service. Closed User Group (CUG) is very popular and is mainly being used to give special discounts to the users if they are making calls to a particular defined group of subscribers. Advice of Charge (AoC) can be charged based on the number of queries made by a subscriber. 26
29 CHAPTER 10 GSM Mobile Phones GSM Arena is the biggest source of information about the latest GSM mobile phones. This page is being displayed here as a courtesy of GSM Arena. If you are planning to buy a GSM mobile phone, then we suggest you go through all the review comments and then decide which phone is suitable for you. Alcatel phones Apple phones Benefon phones BenQ-Siemens phones BlackBerry phones Chea phones Eten phones Gigabyte phones HP phones i-mate phones Kyocera phones Maxon phones Mitsubishi phones NEC phones Nokia phones Palm phones Pantech phones Qtek phones Samsung phones Sewon phones Siemens phones Amoi phones Asus phones BenQ phones Bird phones Bosch phones Ericsson phones Fujitsu Siemens phones Haier phones HTC phones Innostream phones LG phones Mitac phones Motorola phones Neonode phones O2 phones Panasonic phones Philips phones Sagem phones Sendo phones Sharp phones Sony phones 27
30 Sony Ericsson phones Telit phones Toshiba phones VK Mobile phones XCute phones Tel.Me. phones Thuraya phones Vertu phones WND phones GSM Enabled Phones 28
Global System for Mobile Communication (GSM)
 Global System for Mobile Communication (GSM) Definition Global system for mobile communication (GSM) is a globally accepted standard for digital cellular communication. GSM is the name of a standardization
Global System for Mobile Communication (GSM) Definition Global system for mobile communication (GSM) is a globally accepted standard for digital cellular communication. GSM is the name of a standardization
The GSM and GPRS network T-110.300/301
 The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
The GSM and GPRS network T-110.300/301 History The successful analog 1:st generation mobile telephone systems proved that there is a market for mobile telephones ARP (AutoRadioPuhelin) in Finland NMT (Nordic
2G/3G Mobile Communication Systems
 2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
2G/3G Mobile Communication Systems Winter 2012/13 Integrated Communication Systems Group Ilmenau University of Technology Outline 2G Review: GSM Services Architecture Protocols Call setup Mobility management
Global System for Mobile Communications (GSM)
 Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE [email protected] UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Global System for Mobile Communications (GSM) Nguyen Thi Mai Trang LIP6/PHARE [email protected] UPMC/PUF - M2 Networks - PTEL 1 Outline Principles of cellular networks GSM architecture Security
Lecture overview. History of cellular systems (1G) GSM introduction. Basic architecture of GSM system. Basic radio transmission parameters of GSM
 Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
Lecture overview History of cellular systems (1G) GSM introduction Basic architecture of GSM system Basic radio transmission parameters of GSM Analogue cellular systems 70 s In the early 70 s radio frequencies
1. Introduction: The Evolution of Mobile Telephone Systems
 IEC: The Global System for Mobile Communication Tutorial: Index Page 1 of 14 Global System for Mobile Communication (GSM) Tutorial Definition Global System for Mobile Communication (GSM) is a globally
IEC: The Global System for Mobile Communication Tutorial: Index Page 1 of 14 Global System for Mobile Communication (GSM) Tutorial Definition Global System for Mobile Communication (GSM) is a globally
How To Understand The Gsm And Mts Mobile Network Evolution
 Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Mobile Network Evolution Part 1 GSM and UMTS GSM Cell layout Architecture Call setup Mobility management Security GPRS Architecture Protocols QoS EDGE UMTS Architecture Integrated Communication Systems
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu
 Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
Mobile Communications Chapter 4: Wireless Telecommunication Systems slides by Jochen Schiller with modifications by Emmanuel Agu Market GSM Overview Services Sub-systems Components Prof. Dr.-Ing. Jochen
Mobile Communications
 October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
October 21, 2009 Agenda Topic 2: Case Study: The GSM Network 1 GSM System General Architecture 2 GSM Access network. 3 Traffic Models for the Air interface 4 Models for the BSS design. 5 UMTS and the path
Global System for Mobile Communication (GSM)
 Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
Global System for Mobile Communication (GSM) Li-Hsing Yen National University of Kaohsiung GSM System Architecture Um (ME/SIM) C E C PSTN, ISDN, PSPDN, CSPDN A-bis A F A-bis C B BTS BSS BSC HLR VLR EIR
GSM BASICS GSM HISTORY:
 GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
GSM BASICS GSM HISTORY: In 1982 the Nordic PTTs sent a proposal to CEPT (Conference of European Postal & telegraph Administration) to study and to improve digital cellular technology by forming a team
!!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' Giuseppe Bianchi
 !!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' "#$!!% "&'! #&'!%! () *+,, 3 & 5 &,! #-!*! ' & '.! #%!* //!! & (0)/!&/, 6 5 /, "! First system: NMT-450 (Nordic Mobile Telephone)
!!! "# $ % & & # ' (! ) * +, -!!. / " 0! 1 (!!! ' &! & & & ' ( 2 3 0-4 ' 3 ' "#$!!% "&'! #&'!%! () *+,, 3 & 5 &,! #-!*! ' & '.! #%!* //!! & (0)/!&/, 6 5 /, "! First system: NMT-450 (Nordic Mobile Telephone)
Global System for Mobile Communication Technology
 Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
Global System for Mobile Communication Technology Mobile Device Investigations Program Technical Operations Division DHS - FLETC GSM Technology Global System for Mobile Communication or Groupe Special
GSM GPRS. Course requirements: Understanding Telecommunications book by Ericsson (Part D PLMN) + supporting material (= these slides)
 GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
GSM Example of a PLMN (Public Land Mobile Network) At present most successful cellular mobile system (over 200 million subscribers worldwide) Digital (2 nd Generation) cellular mobile system operating
Ch 2.3.3 GSM PENN. Magda El Zarki - Tcom 510 - Spring 98
 Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
Ch 2.3.3 GSM In the early 80 s the European community decided to work together to define a cellular system that would permit full roaming in all countries and give the network providers freedom to provide
Mobile Wireless Overview
 Mobile Wireless Overview A fast-paced technological transition is occurring today in the world of internetworking. This transition is marked by the convergence of the telecommunications infrastructure
Mobile Wireless Overview A fast-paced technological transition is occurring today in the world of internetworking. This transition is marked by the convergence of the telecommunications infrastructure
GSM Architecture and Interfaces
 GSM.05 Page 71 Monday, November 30, 1998 2:07 PM C H A P T E R 5 GSM Architecture and Interfaces 5.1 INTRODUCTION In this chapter we present an overview of the GSM as described in ETSI s recommendations.
GSM.05 Page 71 Monday, November 30, 1998 2:07 PM C H A P T E R 5 GSM Architecture and Interfaces 5.1 INTRODUCTION In this chapter we present an overview of the GSM as described in ETSI s recommendations.
Wireless Mobile Telephony
 Wireless Mobile Telephony The Ohio State University Columbus, OH 43210 [email protected] http://www.cis.ohio-state.edu/~durresi/ 1 Overview Why wireless mobile telephony? First Generation, Analog
Wireless Mobile Telephony The Ohio State University Columbus, OH 43210 [email protected] http://www.cis.ohio-state.edu/~durresi/ 1 Overview Why wireless mobile telephony? First Generation, Analog
Wireless Telecommunication Systems GSM, GPRS, UMTS. GSM as basis of current systems Satellites and
 Chapter 2 Technical Basics: Layer 1 Methods for Medium Access: Layer 2 Chapter 3 Wireless Networks: Bluetooth, WLAN, WirelessMAN, WirelessWAN Mobile Networks: Wireless Telecommunication Systems GSM, GPRS,
Chapter 2 Technical Basics: Layer 1 Methods for Medium Access: Layer 2 Chapter 3 Wireless Networks: Bluetooth, WLAN, WirelessMAN, WirelessWAN Mobile Networks: Wireless Telecommunication Systems GSM, GPRS,
Theory and Practice. IT-Security: GSM Location System Syslog XP 3.7. Mobile Communication. December 18, 2001. GSM Location System Syslog XP 3.
 Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke [email protected] Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
Participant: Hack contacting... IT-Security: Theory and Practice Mobile Communication December 18, 2001 Uwe Jendricke [email protected] Lecture Homepage: http://www.informatik.uni-freiburg.de/~softech/teaching/ws01/itsec/
Mobile Computing. Basic Call Calling terminal Network Called terminal 10/25/14. Public Switched Telephone Network - PSTN. CSE 40814/60814 Fall 2014
 Mobile Computing CSE 40814/60814 Fall 2014 Public Switched Telephone Network - PSTN Transit switch Transit switch Long distance network Transit switch Local switch Outgoing call Incoming call Local switch
Mobile Computing CSE 40814/60814 Fall 2014 Public Switched Telephone Network - PSTN Transit switch Transit switch Long distance network Transit switch Local switch Outgoing call Incoming call Local switch
Wireless Cellular Networks: 1G and 2G
 Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
Wireless Cellular Networks: 1G and 2G Raj Jain Professor of Computer Science and Engineering Washington University in Saint Louis Saint Louis, MO 63130 Audio/Video recordings of this lecture are available
2G Mobile Communication Systems
 2G Mobile Communication Systems 2G Review: GSM Services Architecture Protocols Call setup Mobility management Security HSCSD GPRS EDGE References Jochen Schiller: Mobile Communications (German and English),
2G Mobile Communication Systems 2G Review: GSM Services Architecture Protocols Call setup Mobility management Security HSCSD GPRS EDGE References Jochen Schiller: Mobile Communications (German and English),
The Global System for Mobile communications (GSM) Overview
 The Global System for Mobile communications (GSM) Overview GSM D-AMPS Japan Digital PCS 1900 DCS 1800 CDMA Digital Cellular Systems World-wide Multiple Access Techniques In the GSM/DCS mobile system each
The Global System for Mobile communications (GSM) Overview GSM D-AMPS Japan Digital PCS 1900 DCS 1800 CDMA Digital Cellular Systems World-wide Multiple Access Techniques In the GSM/DCS mobile system each
GSM Architecture Training Document
 Training Document TC Finland Nokia Networks Oy 1 (20) The information in this document is subject to change without notice and describes only the product defined in the introduction of this documentation.
Training Document TC Finland Nokia Networks Oy 1 (20) The information in this document is subject to change without notice and describes only the product defined in the introduction of this documentation.
GSM Databases. Virginia Location Area HLR Vienna Cell Virginia BSC. Virginia MSC VLR
 Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
Update ( Update Procedure) Network Mobiles Maryland Maryland Other Rockville Bethesda Maryland Mobile Mobile Cell Cell HLR Vienna Cell 12-Jun-14 22:48 (Page 1) This sequence diagram was generated with
MAP/C SEND ROUTING INFO FOR SM. Destination Mobile Number. Obtain the SS7 address of the MSC VLR currently serving the specified Mobile Number
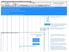 In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
In this call flow we will look at how a terminating SMS is handled in GSM. Setting up a terminating SMS session is a multi-step process. (1) Interrogate the MSC to locate the subscriber (2)Setting SMS
GSM - Global System for Mobile Communications
 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN MS HLR 1) Overview of GSM architecture 2) GSM channel structure 05-1 GSM - Global System for Mobile Communications VLR BTS BSC GMSC PSTN
GSM System. Global System for Mobile Communications
 GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
GSM System Global System for Mobile Communications Introduced in 1991. Settings of standards under ETSI (European Telecommunication Standards Institute) Services - Telephone services - Data services -
In this Lecture" Access method CDMA" Mobile and Sensor Systems Lecture 2: Mobile Medium Access Control Layer and Telecommunications
 Mobile and Sensor Systems Lecture 2: Mobile Medium Access Control Layer and Telecommunications Dr. Cecilia Mascolo In this Lecture In this lecture we will discuss aspects related to the MAC Layer of wireless
Mobile and Sensor Systems Lecture 2: Mobile Medium Access Control Layer and Telecommunications Dr. Cecilia Mascolo In this Lecture In this lecture we will discuss aspects related to the MAC Layer of wireless
Wireless Access of GSM
 Wireless Access of GSM Project Report FALL, 1999 Wireless Access of GSM Abstract: Global System for Mobile communications (GSM) started to be developed by Europeans when the removal of many European trade
Wireless Access of GSM Project Report FALL, 1999 Wireless Access of GSM Abstract: Global System for Mobile communications (GSM) started to be developed by Europeans when the removal of many European trade
Mobile Communications Chapter 4: Wireless Telecommunication Systems
 Mobile Communications Chapter 4: Wireless Telecommunication Systems Market GSM Overview Services Sub-systems Components GPRS DECT Not a part if this course! TETRA Not a part if this course! w-cdma (rel
Mobile Communications Chapter 4: Wireless Telecommunication Systems Market GSM Overview Services Sub-systems Components GPRS DECT Not a part if this course! TETRA Not a part if this course! w-cdma (rel
Wireless and Mobile Network Architecture
 Wireless and Mobile Network Architecture Chapter 7: GSM Network Signaling Prof. Yuh-Shyan Chen Department of Computer Science and Information Engineering National Taipei University Nov. 2006 1 Outline
Wireless and Mobile Network Architecture Chapter 7: GSM Network Signaling Prof. Yuh-Shyan Chen Department of Computer Science and Information Engineering National Taipei University Nov. 2006 1 Outline
Mobile Services (ST 2010)
 Mobile Services (ST 2010) Chapter 3: Mobility Management Axel Küpper Service-centric Networking Deutsche Telekom Laboratories, TU Berlin 1 Mobile Services Summer Term 2010 3 Mobility Management 3.1 Handover
Mobile Services (ST 2010) Chapter 3: Mobility Management Axel Küpper Service-centric Networking Deutsche Telekom Laboratories, TU Berlin 1 Mobile Services Summer Term 2010 3 Mobility Management 3.1 Handover
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail
 CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
CS 8803 - Cellular and Mobile Network Security: GSM - In Detail Professor Patrick Traynor 9/27/12 Cellular Telecommunications Architecture Background Air Interfaces Network Protocols Application: Messaging
GSM System Architecture
 Intersystem Operation and Mobility Management David Tipper Associate Professor Graduate Program in Telecommunications and Networking University it of Pittsburgh Telcom 2700 Slides 6 http://www.tele.pitt.edu/tipper.html
Intersystem Operation and Mobility Management David Tipper Associate Professor Graduate Program in Telecommunications and Networking University it of Pittsburgh Telcom 2700 Slides 6 http://www.tele.pitt.edu/tipper.html
Module 5. Broadcast Communication Networks. Version 2 CSE IIT, Kharagpur
 Module 5 Broadcast Communication Networks Lesson 9 Cellular Telephone Networks Specific Instructional Objectives At the end of this lesson, the student will be able to: Explain the operation of Cellular
Module 5 Broadcast Communication Networks Lesson 9 Cellular Telephone Networks Specific Instructional Objectives At the end of this lesson, the student will be able to: Explain the operation of Cellular
Cellular Network Organization. Cellular Wireless Networks. Approaches to Cope with Increasing Capacity. Frequency Reuse
 Cellular Network Organization Cellular Wireless Networks Use multiple low-power transmitters (100 W or less) Areas divided into cells Each served by its own antenna Served by base station consisting of
Cellular Network Organization Cellular Wireless Networks Use multiple low-power transmitters (100 W or less) Areas divided into cells Each served by its own antenna Served by base station consisting of
ETSI ETR 363 TECHNICAL January 1997 REPORT
 ETSI ETR 363 TECHNICAL January 1997 REPORT Source: ETSI TC-SMG Reference: DTR/SMG-101020Q ICS: 33.020 Key words: Digital cellular telecommunications system, Global System for Mobile communications (GSM)
ETSI ETR 363 TECHNICAL January 1997 REPORT Source: ETSI TC-SMG Reference: DTR/SMG-101020Q ICS: 33.020 Key words: Digital cellular telecommunications system, Global System for Mobile communications (GSM)
Hello viewers, welcome to today s lecture on cellular telephone systems.
 Data Communications Prof. A. Pal Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture minus 31 Cellular Telephone Systems Hello viewers, welcome to today s lecture
Data Communications Prof. A. Pal Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture minus 31 Cellular Telephone Systems Hello viewers, welcome to today s lecture
MRN 6 GSM part 1. Politecnico di Milano Facoltà di Ingegneria dell Informazione. Mobile Radio Networks Prof. Antonio Capone
 Politecnico di Milano Facoltà di Ingegneria dell Informazione MRN 6 GSM part 1 Mobile Radio Networks Prof. Antonio Capone A. Capone: Mobile Radio Networks 1 General characteristics of the system A. Capone:
Politecnico di Milano Facoltà di Ingegneria dell Informazione MRN 6 GSM part 1 Mobile Radio Networks Prof. Antonio Capone A. Capone: Mobile Radio Networks 1 General characteristics of the system A. Capone:
Cellular Network Organization
 Cellular Networks Cellular Network Organization Use multiple low-power transmitters (100 W or less) Areas divided into cells o Each served by its own antenna o Served by base station consisting of transmitter,
Cellular Networks Cellular Network Organization Use multiple low-power transmitters (100 W or less) Areas divided into cells o Each served by its own antenna o Served by base station consisting of transmitter,
The Network Layer Layer 3
 CHAPTER 7 The Network Layer Layer 3 Now it is time to hijack the GSM freight train, to see what is inside, to break into the time-slotted boxcars and spill the drums of unknown acids and solvents on the
CHAPTER 7 The Network Layer Layer 3 Now it is time to hijack the GSM freight train, to see what is inside, to break into the time-slotted boxcars and spill the drums of unknown acids and solvents on the
SPYTEC 3000 The system for GSM communication monitoring
 SPYTEC 3000 The system for GSM communication monitoring The SPYTEC 3000 system is intended for passive (if system encryption is absent of if A5.2 encryption is used) or semi-active (if A5.1 encryption
SPYTEC 3000 The system for GSM communication monitoring The SPYTEC 3000 system is intended for passive (if system encryption is absent of if A5.2 encryption is used) or semi-active (if A5.1 encryption
2 System introduction
 2 System introduction Objectives After this chapter the student will: be able to describe the different nodes in a GSM network. be able to describe geographical subdivision of a GSM network. be able to
2 System introduction Objectives After this chapter the student will: be able to describe the different nodes in a GSM network. be able to describe geographical subdivision of a GSM network. be able to
GSM Network and Services
 GSM Network and Services GPRS - sharing of resources 1 What is the problem? Many data applications are very bursty in its traffic pattern: http, smtp, pop, telnet,... Why reserve physical resources at
GSM Network and Services GPRS - sharing of resources 1 What is the problem? Many data applications are very bursty in its traffic pattern: http, smtp, pop, telnet,... Why reserve physical resources at
Cellular Phone Systems
 Cellular Phone Systems Li-Hsing Yen National University of Kaohsiung Cellular System HLR PSTN MSC MSC VLR BSC BSC BSC 1 Why Cellular Mobile Telephone Systems? Operational limitations of conventional mobile
Cellular Phone Systems Li-Hsing Yen National University of Kaohsiung Cellular System HLR PSTN MSC MSC VLR BSC BSC BSC 1 Why Cellular Mobile Telephone Systems? Operational limitations of conventional mobile
Chapters 1-21 Introduction to Wireless Communication Systems
 Chapters 1-21 Introduction to Wireless Communication Systems Yimin Zhang, Ph.D. Department of Electrical & Computer Engineering Villanova University http://yiminzhang.com/ece8708 Yimin Zhang, Villanova
Chapters 1-21 Introduction to Wireless Communication Systems Yimin Zhang, Ph.D. Department of Electrical & Computer Engineering Villanova University http://yiminzhang.com/ece8708 Yimin Zhang, Villanova
Provides a communication link between MS and MSC; Manages DB for MS location. Controls user connection. Transmission.
 Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
Provides a communication link between MS and MSC; Manages DB for MS location Controls user connection CM MM RR Transmission Several RR functions considered in previous part!"# Surprise! handover is part
GSM Channels. Physical & Logical Channels. Traffic and Control Mutltiframing. Frame Structure
 GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
GSM Channels Physical & Logical Channels Traffic and Control Mutltiframing Frame Structure Engr. Mian Shahzad Iqbal Lecturer Department of Telecommunication Engineering Radio Interface The radio interface
Global System for Mobile (GSM) Global System for Mobile (GSM)
 Global System for Mobile (GSM) David Tipper Associate Professor Graduate Program of Telecommunications and Networking University of Pittsburgh Telcom 2720 Slides 8 Based largely on material from Jochen
Global System for Mobile (GSM) David Tipper Associate Professor Graduate Program of Telecommunications and Networking University of Pittsburgh Telcom 2720 Slides 8 Based largely on material from Jochen
Indian Journal of Advances in Computer & Information Engineering Volume.1 Number.1 January-June 2013, pp.1-5 @ Academic Research Journals.
 Cellular System Rajat Chugh, Parag Jasoria, Tushar Arora, Nitin Ginotra and Vivek Anand V Semester, Department of Computer Science and Engineering, Dronacharya College of Engineering, Khentawas, Farukhnagar,
Cellular System Rajat Chugh, Parag Jasoria, Tushar Arora, Nitin Ginotra and Vivek Anand V Semester, Department of Computer Science and Engineering, Dronacharya College of Engineering, Khentawas, Farukhnagar,
Bölüm 8. GSM. 6 Milyar mobil telefon kullanıcısı (2011 sonu)* Dünya nüfusu 7 Milyar!
 Bölüm 8. GSM http://ceng.gazi.edu.tr/~ozdemir Durum 6 Milyar mobil telefon kullanıcısı (2011 sonu)* Dünya nüfusu 7 Milyar! * http://www.itu.int/dms_pub/itu-d/opb/ind/d-ind-ictoi-2012-sum-pdf-e.pdf 1 Global
Bölüm 8. GSM http://ceng.gazi.edu.tr/~ozdemir Durum 6 Milyar mobil telefon kullanıcısı (2011 sonu)* Dünya nüfusu 7 Milyar! * http://www.itu.int/dms_pub/itu-d/opb/ind/d-ind-ictoi-2012-sum-pdf-e.pdf 1 Global
Cellular Networks: Background and Classical Vulnerabilities
 Cellular Networks: Background and Classical Vulnerabilities Patrick Traynor CSE 545 1 Cellular Networks Provide communications infrastructure for an estimated 2.6 billion users daily. The Internet connects
Cellular Networks: Background and Classical Vulnerabilities Patrick Traynor CSE 545 1 Cellular Networks Provide communications infrastructure for an estimated 2.6 billion users daily. The Internet connects
GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving
 GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving 1 Space Division Multiple Access of the signals from the MSs A BTS with n directed antennae covers mobile stations
GSM and Similar Architectures Lesson 07 GSM Radio Interface, Data bursts and Interleaving 1 Space Division Multiple Access of the signals from the MSs A BTS with n directed antennae covers mobile stations
Appendix C GSM System and Modulation Description
 C1 Appendix C GSM System and Modulation Description C1. Parameters included in the modelling In the modelling the number of mobiles and their positioning with respect to the wired device needs to be taken
C1 Appendix C GSM System and Modulation Description C1. Parameters included in the modelling In the modelling the number of mobiles and their positioning with respect to the wired device needs to be taken
Vehicle Theft Intimation Using GSM
 ISSN (e): 2250 3005 Vol, 04 Issue, 8 August 2014 International Journal of Computational Engineering Research (IJCER) Vehicle Theft Intimation Using GSM 1, Minakshi Kumari, 2, Prof. Manoj Singh 1, 2, Computer
ISSN (e): 2250 3005 Vol, 04 Issue, 8 August 2014 International Journal of Computational Engineering Research (IJCER) Vehicle Theft Intimation Using GSM 1, Minakshi Kumari, 2, Prof. Manoj Singh 1, 2, Computer
Development of Wireless Networks
 Development of Wireless Networks Cellular Revolution In 1990 mobile phone users populate 11 million. By 2004 the figure will become 1 billion Phones are most obvious sign of the success of wireless technology.
Development of Wireless Networks Cellular Revolution In 1990 mobile phone users populate 11 million. By 2004 the figure will become 1 billion Phones are most obvious sign of the success of wireless technology.
3GPP Wireless Standard
 3GPP Wireless Standard Shishir Pandey School of Technology and Computer Science TIFR, Mumbai April 10, 2009 Shishir Pandey (TIFR) 3GPP Wireless Standard April 10, 2009 1 / 23 3GPP Overview 3GPP : 3rd Generation
3GPP Wireless Standard Shishir Pandey School of Technology and Computer Science TIFR, Mumbai April 10, 2009 Shishir Pandey (TIFR) 3GPP Wireless Standard April 10, 2009 1 / 23 3GPP Overview 3GPP : 3rd Generation
1 Introduction. 2 Assumptions. Implementing roaming for OpenBTS
 Implementing roaming for OpenBTS 1 Introduction One of the main advantages of OpenBTS TM system architecture is absence of a legacy GSM core network. SIP is used for registering, call control and messaging.
Implementing roaming for OpenBTS 1 Introduction One of the main advantages of OpenBTS TM system architecture is absence of a legacy GSM core network. SIP is used for registering, call control and messaging.
GSM v. CDMA: Technical Comparison of M2M Technologies
 GSM v. CDMA: Technical Comparison of M2M Technologies Introduction Aeris provides network and data analytics services for Machine-to- Machine ( M2M ) and Internet of Things ( IoT ) applications using multiple
GSM v. CDMA: Technical Comparison of M2M Technologies Introduction Aeris provides network and data analytics services for Machine-to- Machine ( M2M ) and Internet of Things ( IoT ) applications using multiple
Worldwide attacks on SS7 network
 Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin ([email protected]) Alexandre De Oliveira ([email protected]) Agenda Overall telecom architecture Architecture
Worldwide attacks on SS7 network P1 Security Hackito Ergo Sum 26 th April 2014 Pierre-Olivier Vauboin ([email protected]) Alexandre De Oliveira ([email protected]) Agenda Overall telecom architecture Architecture
CS 8803 - Cellular and Mobile Network Security: Cellular Networking
 CS 8803 - Cellular and Mobile Network Security: Cellular Networking Professor Patrick Traynor 9/13/2012 The Big Picture Details create the big picture. -Sanford I. Weill 2 Overview Evolution Architecture
CS 8803 - Cellular and Mobile Network Security: Cellular Networking Professor Patrick Traynor 9/13/2012 The Big Picture Details create the big picture. -Sanford I. Weill 2 Overview Evolution Architecture
What is telecommunication? electronic communications? What is telephony?
 What is telecommunication? Telecommunication: Any transmission, emission or reception of signs, signals, writing, images and sounds or intelligence of any nature by wire, radio, optical or other electromagnetic
What is telecommunication? Telecommunication: Any transmission, emission or reception of signs, signals, writing, images and sounds or intelligence of any nature by wire, radio, optical or other electromagnetic
Analysis of GSM Network for Different Transmission Powers
 Analysis of GSM Network for Different Transmission Powers Mandeep Singh 1, Supreet Kaur 2 1,2 (Department of Electronics and Communication Engineering, Punjabi University, Patiala, India) Abstract: To
Analysis of GSM Network for Different Transmission Powers Mandeep Singh 1, Supreet Kaur 2 1,2 (Department of Electronics and Communication Engineering, Punjabi University, Patiala, India) Abstract: To
GSM Network Architecture, Channelisation, Signalling and Call Processing
 GSM Network Architecture, Channelisation, Signalling and Call Processing Dr Bhaskar Ramamurthi Professor Department of Electrical Engineering IIT Madras Dr Bhaskar Ramamurthi GSM 1 Call Routing in Wireline
GSM Network Architecture, Channelisation, Signalling and Call Processing Dr Bhaskar Ramamurthi Professor Department of Electrical Engineering IIT Madras Dr Bhaskar Ramamurthi GSM 1 Call Routing in Wireline
MOBILE CREDIT USING GSM NETWORK TOPUP FOR MOBILE PHONES
 Master Thesis Electrical Engineering September 2015 MOBILE CREDIT USING GSM NETWORK TOPUP FOR MOBILE PHONES MEKALA.SAKETHA RAM Faculty of Computing Blekinge Institute of Technology SE-371 79 Karlskrona
Master Thesis Electrical Engineering September 2015 MOBILE CREDIT USING GSM NETWORK TOPUP FOR MOBILE PHONES MEKALA.SAKETHA RAM Faculty of Computing Blekinge Institute of Technology SE-371 79 Karlskrona
How To Understand Cellular Communications
 Definition Cellular Communications A cellular mobile communications system uses a large number of low-power wireless transmitters to create cells the basic geographic service area of a wireless communications
Definition Cellular Communications A cellular mobile communications system uses a large number of low-power wireless transmitters to create cells the basic geographic service area of a wireless communications
What is telecommunication? electronic communications. service?
 What is telecommunication? Telecommunication: Any transmission, emission or reception of signs, signals, writing, images and sounds or intelligence of any nature by wire, radio, optical or other electromagnetic
What is telecommunication? Telecommunication: Any transmission, emission or reception of signs, signals, writing, images and sounds or intelligence of any nature by wire, radio, optical or other electromagnetic
An Example of Mobile Forensics
 An Example of Mobile Forensics Kelvin Hilton K319 kchilton@staffsacuk [email protected] www.soc.staffs.ac.uk/kch1 Objectives The sources of evidence The subscriber The mobile station The network
An Example of Mobile Forensics Kelvin Hilton K319 kchilton@staffsacuk [email protected] www.soc.staffs.ac.uk/kch1 Objectives The sources of evidence The subscriber The mobile station The network
ETSI TR 101 643 V8.0.0 (2000-06)
 TR 101 643 V8.0.0 (2000-06) Technical Report Digital cellular telecommunications system (Phase 2+); General network interworking scenarios (GSM 09.01 version 8.0.0 Release 1999) GLOBAL SYSTEM FOR MOBILE
TR 101 643 V8.0.0 (2000-06) Technical Report Digital cellular telecommunications system (Phase 2+); General network interworking scenarios (GSM 09.01 version 8.0.0 Release 1999) GLOBAL SYSTEM FOR MOBILE
UMTS security. Helsinki University of Technology S-38.153 Security of Communication Protocols [email protected] 15.4.2003
 UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols [email protected] 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
UMTS security Helsinki University of Technology S-38.153 Security of Communication Protocols [email protected] 15.4.2003 Contents UMTS Security objectives Problems with GSM security UMTS security mechanisms
Backgrounds regarding data transmission in GSM and UMTS mobile networks for Sunny WebBox / Sunny Boy Control
 GSM Backgrounds regarding data transmission in GSM and UMTS mobile networks for Sunny WebBox / Sunny Boy Control Contents In addition to telephony, services for digital fax and data transmission were already
GSM Backgrounds regarding data transmission in GSM and UMTS mobile networks for Sunny WebBox / Sunny Boy Control Contents In addition to telephony, services for digital fax and data transmission were already
192620010 Mobile & Wireless Networking. Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4]
![192620010 Mobile & Wireless Networking. Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4] 192620010 Mobile & Wireless Networking. Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4]](/thumbs/18/698539.jpg) 192620010 Mobile & Wireless Networking Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4] Geert Heijenk Outline of Lecture 5 Cellular Systems (UMTS / LTE) (1/2) q Evolution of cellular
192620010 Mobile & Wireless Networking Lecture 5: Cellular Systems (UMTS / LTE) (1/2) [Schiller, Section 4.4] Geert Heijenk Outline of Lecture 5 Cellular Systems (UMTS / LTE) (1/2) q Evolution of cellular
9.1 Introduction. 9.2 Roaming
 9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
9 Location Updating Objectives After this chapter the student will: be able to define the concepts of roaming and location updating. be able to name the different types of location updating and why they
Telecommunication Systems (GSM) Mobile Communications (Ch 4) John Schiller, Addison-Wesley
 Telecommunication Systems (GSM) Mobile Communications (Ch 4) John Schiller, Addison-Wesley 1 Telecommunication System Wireless extension of traditional PSTN Telephony architecture (NOT computer net) Many
Telecommunication Systems (GSM) Mobile Communications (Ch 4) John Schiller, Addison-Wesley 1 Telecommunication System Wireless extension of traditional PSTN Telephony architecture (NOT computer net) Many
GSM Network Structure and Network Planning. Contents: Dipl.- Ing. Reiner Stuhlfauth, ROHDE & SCHWARZ; Training Centre
 GSM Network Structure and Network Planning Dipl.- Ing. Reiner Stuhlfauth, ROHDE & SCHWARZ; Training Centre Contents: 1. Geographical structures in a GSM network 2. Methods of network planning 2.1. Principles
GSM Network Structure and Network Planning Dipl.- Ing. Reiner Stuhlfauth, ROHDE & SCHWARZ; Training Centre Contents: 1. Geographical structures in a GSM network 2. Methods of network planning 2.1. Principles
General Packet Radio Service (GPRS)
 General Packet Radio Service (GPRS) What is GPRS? GPRS (General Packet Radio Service) a packet oriented data service for IP and X.25 over GSM networks enables packet-switched services on the resources
General Packet Radio Service (GPRS) What is GPRS? GPRS (General Packet Radio Service) a packet oriented data service for IP and X.25 over GSM networks enables packet-switched services on the resources
Mobile Communication Systems: DECT Digital Enhanced Cordless Telecommunication
 Mobile ommunication Systems: DET Digital Enhanced ordless Telecommunication Mobile ommunication: Telecommunication Systems - Jochen Schiller http://www.jochenschiller.de 1 Overview DET (Digital European
Mobile ommunication Systems: DET Digital Enhanced ordless Telecommunication Mobile ommunication: Telecommunication Systems - Jochen Schiller http://www.jochenschiller.de 1 Overview DET (Digital European
Mobile Application Part protocol implementation in OPNET
 Mobile Application Part protocol implementation in OPNET Vladimir Vukadinovic and Ljiljana Trajkovic School of Engineering Science Simon Fraser University Vancouver, BC, Canada E-mail: {vladimir, ljilja}@cs.sfu.ca
Mobile Application Part protocol implementation in OPNET Vladimir Vukadinovic and Ljiljana Trajkovic School of Engineering Science Simon Fraser University Vancouver, BC, Canada E-mail: {vladimir, ljilja}@cs.sfu.ca
Handoff in GSM/GPRS Cellular Systems. Avi Freedman Hexagon System Engineering
 Handoff in GSM/GPRS Cellular Systems Avi Freedman Hexagon System Engineering Outline GSM and GSM referemce model GPRS basics Handoffs GSM GPRS Location and Mobility Management Re-selection and routing
Handoff in GSM/GPRS Cellular Systems Avi Freedman Hexagon System Engineering Outline GSM and GSM referemce model GPRS basics Handoffs GSM GPRS Location and Mobility Management Re-selection and routing
Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography
 ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 10 Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography Wilayat Khan 1 and Habib Ullah 2 1 Department of Electrical
ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 10 Authentication and Secure Communication in GSM, GPRS, and UMTS Using Asymmetric Cryptography Wilayat Khan 1 and Habib Ullah 2 1 Department of Electrical
Mobile Office Security Requirements for the Mobile Office
 Mobile Office Security Requirements for the Mobile Office [email protected] Alcatel SEL AG 20./21.06.2001 Overview Security Concepts in Mobile Networks Applications in Mobile Networks Mobile Terminal used
Mobile Office Security Requirements for the Mobile Office [email protected] Alcatel SEL AG 20./21.06.2001 Overview Security Concepts in Mobile Networks Applications in Mobile Networks Mobile Terminal used
Wireless LANs vs. Wireless WANs
 White Paper Wireless LANs vs. Wireless WANs White Paper 2130273 Revision 1.0 Date 2002 November 18 Subject Supported Products Comparing Wireless LANs and Wireless WANs Wireless data cards and modules,
White Paper Wireless LANs vs. Wireless WANs White Paper 2130273 Revision 1.0 Date 2002 November 18 Subject Supported Products Comparing Wireless LANs and Wireless WANs Wireless data cards and modules,
GPRS Overview. GPRS = General Packet Radio Service. GPRS Network
 GPRS - Overview GPRS Overview GPRS = General Packet Radio Service INTERNET/ INTRANET GPRS Network abcde X.25 Disclaimer: These overview slides are intended for informational purposes only. They have not
GPRS - Overview GPRS Overview GPRS = General Packet Radio Service INTERNET/ INTRANET GPRS Network abcde X.25 Disclaimer: These overview slides are intended for informational purposes only. They have not
GSM: PHYSICAL & LOGICAL CHANNELS
 GSM: PHYSICAL & LOGICAL CHANNELS AN OVERVIEW Prepared by Learntelecom.com 1. GSM: PHYSICAL AND LOGICAL CHANNELS GSM uses a mix of Frequency Division Multiple Access (FDMA) and Time Division Multiple Access
GSM: PHYSICAL & LOGICAL CHANNELS AN OVERVIEW Prepared by Learntelecom.com 1. GSM: PHYSICAL AND LOGICAL CHANNELS GSM uses a mix of Frequency Division Multiple Access (FDMA) and Time Division Multiple Access
Mobility and cellular networks
 Mobility and cellular s Wireless WANs Cellular radio and PCS s Wireless data s Satellite links and s Mobility, etc.- 2 Cellular s First generation: initially debuted in Japan in 1979, analog transmission
Mobility and cellular s Wireless WANs Cellular radio and PCS s Wireless data s Satellite links and s Mobility, etc.- 2 Cellular s First generation: initially debuted in Japan in 1979, analog transmission
CS263: Wireless Communications and Sensor Networks
 CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 4: Medium Access Control October 5, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Medium Access Control Schemes: FDMA TDMA
CS263: Wireless Communications and Sensor Networks Matt Welsh Lecture 4: Medium Access Control October 5, 2004 2004 Matt Welsh Harvard University 1 Today's Lecture Medium Access Control Schemes: FDMA TDMA
EPL 657 Wireless Networks
 EPL 657 Wireless Networks Some fundamentals: Multiplexing / Multiple Access / Duplex Infrastructure vs Infrastructureless Panayiotis Kolios Recall: The big picture... Modulations: some basics 2 Multiplexing
EPL 657 Wireless Networks Some fundamentals: Multiplexing / Multiple Access / Duplex Infrastructure vs Infrastructureless Panayiotis Kolios Recall: The big picture... Modulations: some basics 2 Multiplexing
EDGE: The Introduction of High Speed Data in GSM / GPRS Networks
 10 September 2003 EDGE: The Introduction of High Speed Data in GSM / GPRS Networks Wendy Florence Ericsson South Africa Rev A 10 September 2003 1 Agenda What is EDGE? Implementing EDGE Network and transmission
10 September 2003 EDGE: The Introduction of High Speed Data in GSM / GPRS Networks Wendy Florence Ericsson South Africa Rev A 10 September 2003 1 Agenda What is EDGE? Implementing EDGE Network and transmission
GSM Network and Services
 GSM Network and Services Cellular networks GSM Network and Services 2G1723 Johan Montelius 1 The name of the game The number one priority for mobile/cellular networks is to implement full-duplex voice
GSM Network and Services Cellular networks GSM Network and Services 2G1723 Johan Montelius 1 The name of the game The number one priority for mobile/cellular networks is to implement full-duplex voice
EE 4105 Communication Engg-II Dr. Mostafa Zaman Chowdhury Slide # 1
 EE 4105 Communication Engg-II Dr. Mostafa Zaman Chowdhury Slide # 1 1 Circuit-Switched Systems In a circuit-switched system, each traffic channel is dedicated to a user until its cell is terminated. Circuit
EE 4105 Communication Engg-II Dr. Mostafa Zaman Chowdhury Slide # 1 1 Circuit-Switched Systems In a circuit-switched system, each traffic channel is dedicated to a user until its cell is terminated. Circuit
Mobile Phone Security. Hoang Vo Billy Ngo
 Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
Mobile Phone Security Hoang Vo Billy Ngo Table of Content 1. Introduction Page 2 1.1 Analog Network Page 2 1.2 Digital Network Page 2 2. Security Protocols Page 4 2.1 Analog Page 4 2.2 Digital Page 5 3.
GSM Research. Chair in Communication Systems Department of Applied Sciences University of Freiburg 2010
 Chair in Communication Systems Department of Applied Sciences University of Freiburg 2010 Dennis Wehrle, Konrad Meier, Dirk von Suchodoletz, Klaus Rechert, Gerhard Schneider Overview 1. GSM Infrastructure
Chair in Communication Systems Department of Applied Sciences University of Freiburg 2010 Dennis Wehrle, Konrad Meier, Dirk von Suchodoletz, Klaus Rechert, Gerhard Schneider Overview 1. GSM Infrastructure
