|
|
|
- Aubrie Moody
- 9 years ago
- Views:
Transcription
1 ASocialMechanismofReputationManagement inelectroniccommunities 446EGRC,1010MainCampusDrive BinYuandMunindarP.Singh? DepartmentofComputerScience NorthCarolinaStateUniversity Raleigh,NC ,USA Abstract.Trustisimportantwhereveragentsmustinteract.Weconsidertheimportantcaseofinteractionsinelectroniccommunities,whernesses.Weproposeasocialmechanismofreputationmanagement,which theagentsassistandrepresentprincipalentities,suchaspeopleandbusinismscomplementhardsecuritytechniques(suchaspasswordsanddigitalcerticates),whichonlyguaranteethatapartyisauthenticatedand aimsatavoidinginteractionwithundesirableparticipants.socialmecha- whentrustedthirdpartiesarenotavailable.ourspecicapproachto thatisdesirabletoothers.socialmechanismsareevenmoreimportant authorized,butdonotensurethatitexercisesitsauthorizationinaway 1Introduction helpeachotherweedoutundesirableplayers. reputationmanagementleadstoadecentralizedsocietyinwhichagents communityprovideservicesaswellasreferralsforservicestoeachother.our Theworldwideexpansionofnetworkaccessisdrivinganincreaseininteractions munityasasetofinteractingparties(peopleorbusinesses).themembersofa notionofservicesisgeneralinthattheyneednotbebusinessservicesprovided amongpeopleandbetweenpeopleandbusinesses.wedeneanelectroniccom- sense,e.g.,justcompanionshiporlivelydiscussion. forafee,butmaybevolunteerservices,ornoteven\services"inthetraditional participants'reputationsbothforexpertise(providinggoodservice)andhelpfulness(providinggoodreferrals).thesocialnetworkismaintainedbypersonal decidingwhetherorhowtorespondtoarequest.theagentsassisttheirusers agentsassistingdierentusers.agentsandtheirusershavefullautonomyin Wemodelanelectroniccommunityasasocialnetwork,whichsupportsthe inevaluatingtheservicesandreferralsprovidedbyothers,maintainingcontact lists,anddecidingwhomtocontact.inthismanner,theagentsassisttheirusers?thisresearchwassupportedbythenationalsciencefoundationundergrantiis (CareerAward).Weareindebtedtotheanonymousreviewersforhelpful comments.
2 inndingthemosthelpfulandreliablepartiestodealwith.therecommendationsbythepersonalagentsarebasedonarepresentationofhowmuchtheother partiescanbetrusted.theagentsbuildandmanagetheserepresentationsof Hardsecurityapproacheshelpestablishthatthepartyyouaredealingwithis trust.todoso,theagentsnotonlytakeintoaccountthepreviousexperiencesof authenticatedandauthorizedtotakevariousactions.theydon'tensurethat theirusers,butalsocommunicatewithotheragents(belongingtootherusers). thatpartyisdoingwhatyouexpectanddeliveringgoodservice.inotherwords, thehardsecurityapproachessimplyplacealowhurdleoflegalitythatsomeone Thenotionoftrustcomplementshardsecurity,e.g.,throughcryptography. accountableevenforthelegalactionsthattheyperform. reputationmanagement.section3presentssomenecessarybackgroundonhow mustcrossinordertoparticipate,whereastrustmanagementmakespeople toestablishanelectroniccommunity.section4introducesourapproach,giving thekeydenitionsanddiscussingsomeinformalpropertiesoftrust.section5 presentsourexperimentalmodelandsomebasicresultsthatwehaveobtained. Thispaperisorganizedasfollows.Section2presentssomerelatedworkin forfutureresearch. Section6concludesourpaperwithadiscussionofthemainresultsanddirections 2RelatedWork OnSaleExchangeandeBayareimportantpracticalexamplesofreputationmanagement.OnSaleallowsitsuserstorateandsubmittextualcommentsabout sellers.theoverallreputationofaselleristheaverageoftheratingsobtained someoneratesthem,whileonebaytheystartwithzerofeedbackpoints.both approachesrequireuserstoexplicitlymakeandrevealtheirratingsofothers.as fromhiscustomers.inebay,sellersreceivefeedback(+1,0,?1)fortheirreliabilityineachauctionandtheirreputationiscalculatedasthesumofthoseratings overthelastsixmonths.inonsale,thenewcomershavenoreputationuntil aresult,theuserslosecontroltothecentralauthority. andkasbah[2,12]requirethatusersgivearatingforthemselvesandeitherhave usestheseratingstocomputeaperson'soverallreputationorreputationwith Acentralsystemkeepstrackoftheusers'explicitratingsofeachother,and acentralagency(directratings)orothertrustedusers(collaborativeratings). Someprototypeapproachesarerelevant.Yenta[3],weavingaweboftrust[4], suchrelationshipsandhowtheratingspropagatethroughthiscommunity. inelectronicmarketplaces.however,ttpismostappropriateforclosedmarketplaces.inlooselyfederated,opensystemsattpmayeithernotbeavailable TrustedThirdParties(TTP)[7]actasabridgebetweenbuyersandsellers amongtheusersoftheirelectroniccommunity.itisnotclearhowtoestablish respecttoaspecicuser.thesesystemsrequirepreexistingsocialrelationships orhavelimitedpowertoenforcegoodbehavior. controlthroughreputation[6].insoftsecurity,theagentspolicethemselves Rasmusson&Jansonproposedthenotionofsoftsecuritybasedonsocial
3 withoutreadyrecoursetoacentralauthority.softsecurityisespeciallyattractive inopensettings,andmotivatesourapproach. Work(SIF)[8].InSIF,anagentevaluatesthereputationofanotheragentbased considersonlyanagent'sownexperiencesanddoesn'tinvolveanysocialmechanisms.hence,agroupofagentscannotcollectivelybuildupareputationfor others.amorerelevantcomputationalmethodisfromsocialinteractionframe- Marshpresentsaformalizationoftheconceptoftrust[5].Hisformalization describehowtondsuchwitnesses,whereasintheelectroniccommunities,deals arebrokeredamongpeoplewhoprobablyhavenevermeteachother. ondirectobservationsaswellthroughotherwitnesses.however,sifdoesnot approachforreputationmanagement:howto(1)givefullcontroltotheusersin termsofwhentorevealtheirratings;(2)helpanagentndtrustworthyagents (veritablestrangers)evenwithoutpriorrelationships;and,(3)speedupthe propagationofinformationthroughthesocialnetwork.oursocialmechanism Challenges.Thefollowingaresomeimportantchallengesforanyagent-based amongagents,evenacrosssub-communities.therefore,undesirableagentscan seekstoaddresstheabovechallenges.inparticular,ratingsareconveyedquickly quicklyberuledout. 3ElectronicCommunities adeal.thepayosinthegamearesuchthatbothagentswouldbenetifboth withtwoagents.theagentshavetodecidewhethertocooperateordefectfrom cooperate.however,ifoneagentweretotrytocooperatewhentheotherdefects, Tobetterunderstandthenotionoftrustincommunities,let'sdiscussthefamous prisoners'dilemma[1].theprisoner'sdilemmaarisesinanon-cooperativegame foreachagenttodefect,therebyleadingtoaworsepayoforbothagentsthan theonehand,iftheplayerstrusteachother,theycanbothcooperateandavert ifbothweretocooperate. thecooperatorwouldsuerconsiderably.thismakesthelocallyrationalchoice buildupinasettingwheretheplayershavetorepeatlyinteractwitheachother. amutualdefectionwherebothsuer.ontheotherhand,suchtrustcanonly Ourobservationisthatareputationmechanismsustainsrationalcooperation, Theprisoner'sdilemmaisintimatelyrelatedtotheevolutionoftrust.On becausethegoodplayersarerewardedbysocietywhereasthebadplayersare penalized.boththerewardsandpenaltiesfromasocietyaregreaterthanfrom socialnetworkforinformationgathering[10,11].inourarchitecture,eachuseris anindividual. associatedwithapersonalagent.usersposequeriestotheiragents.thequeries whomtosendthequery.afterconsultationwiththeuser,theagentsendsthe bytheuserarerstseenbyhisagentwhodecidesthepotentialcontactsto Theproposedapproachbuildson(andappliesin)ourworkonconstructinga querytotheagentsforotherlikelypeople.theagentwhoreceivesaquerycan decideifitsuitsitsuserandlettheuserseethatquery.inadditiontoorinstead
4 ofjustforwardingthequerytoitsuser,theagentmayrespondwithreferralsto otherusers. alimitonthenumberofreferralsrequested.aresponsemayincludeananswer incomingquery.areferraldependsonthequeryandonthereferringagent's orareferral,orboth,orneither(inwhichcasenoresponseisneeded).an agentanswersonlyifitisreasonablycondentthatitsexpertisematchesthe Aqueryincludesthequestionaswellastherequester'sIDandaddressand modelofotheragents;areferralisgivenonlyifthereferringagentplacessome itsmodeloftheexpertiseoftheansweringagent,anditsmodelsofanyagent evaluatingtheexpertiseoftheagentwhogavetheanswer.thisevaluationaects itup.whentheagentreceivesananswer,itusestheanswerasabasisfor trustintheagentbeingreferred. whomayhavegivenareferraltothisansweringagent.ingeneral,theoriginating Whentheoriginatingagentreceivesareferral,itdecideswhethertofollow agentmaykeeptrackofmorepeersthanhisneighbors.periodicallyhedecide 4ReputationRatingandPropagation whichpeerstokeepasneighbors,i.e.,whichareworthremembering. Inourapproach,agentAassignsaratingtoagentBbasedon(1)itsdirect A'sratingofthoseneighbors.Thesecondaspectmakesourapproachasocialone observationsofbaswellas(2)theratingsofbasgivenbyb'sneighbors,and andenablesinformationaboutreputationstopropagatethroughthenetwork. sources.however,suchapproachesdonotconsiderthereputationsofthewitnessesthemselves.clearly,theweightassignedtoaratingshoulddependon thereputationoftherater.moreover,reputationratingscannotbeallowedto asimplisticapproachthatdirectlycombinestheratingsassignedbydierent Traditionalapproacheseitherignorethesocialaspectsaltogetheroremploy Denition1.Ti(j)tisthetrustratingassignedbyagentitoagentjattime increaseadinnitum.toachievetheabove,werstdeneanagent'sratingof t.werequirethat?1<ti(j)t<1andti(j)0=0. anotheragent.initially,theratingiszero. Cooperationbytheotheragentgeneratesapositiveevidenceanddefection anegativeevidence.thus0and0.toprotectthosewhointeract reputations,meaningthatreputationsshouldbehardtobuildup,buteasyto withanagentwhocheatssomeofthetime,wetakeaconservativestancetoward Eachagentwilladaptitsratingofanotheragentbasedonitsobservation. teardown.thiscontrastswithmarsh[5],whereanagentmaycheatasizable fraction(20%)ofthetimebutstillmaintainamonotonicallyincreasingreputation.wecanachievethedesiredeectbyrequiringthatjj<jj.weusea simpleapproachtocombineinevidencefromrecentinteractions. bythefollowingtableanddependsontheprevioustrustrating. Denition2.Afteraninteraction,theupdatedtrustratingTi(j)t+1isgiven
5 Ti(j)tCooperationbyj >0Ti(j)t+(1?Ti(j)t) <0(Ti(j)t+)=(1?minfjTi(j)tj;jjg)Ti(j)t+(1+Ti(j)t) Defectionbyj =0 (Ti(j)t+)=(1?minfjTi(j)tj;jj)g fortrust. Denition3.Foragenti:?1!i1and?1i1,where!ii. Ti(j)!iindicatesthatitrustsjandwillcooperatewithj;Ti(j)iindicates FollowingMarsh[5],wedeneforeachagentanupperandalowerthreshold thatimistrustsjandwilldefectagainstj;i<ti(j)<!imeansthatimust decideonsomeothergrounds. 4.1PropagationofReputationRating Eachagenthasasetofpotentiallychangingneighborswithwhomitmaydirectly interact.howanagentevaluatesthereputationsofotherswilldependinpart onthetestimoniesofitsneighbors.thisnaturallyleadstotheideaofareferral chain. Denition4.=hA0;:::;Aniisa(possible)referralchainfromagentA0to agentan,whereai+1isaneighborofai. Denition5.xy=if(x0^y0)thenxyelse?jxyj A0willuseareferralchaintoAntocomputeitsratingT0(n)towardsAn. chainisnegative.below,let=ha0;:::;anibeareferralchainfromagenta0 Wedeneatrustpropagationoperator,. toagentanattimet.wenowdenetrustpropagationoverareferralchain. Denition6.Foranyk,0kn,T0(k)t=T0(1)t:::Tk?1(k)t Inotherwords,theleveloftrustpropagatedoveranegativelinkinareferral agentsonthechain.forthisreason,wetermthepenultimateagentthewitness. denedase0(k)t=t0(k)ttk(k+1)t.herekisthewitnessofthistestimony. Denition7.Atestimonyforagent0fromagentkrelativetoachainis Thepenultimateagentonareferralchainhasdirectevidenceofthelast onlyifagentkistrusted,i.e.,t siderwitnessesreliableaslongastheyhaveapositivetrustrating. reliable.soastoallowtestimonyfromweakagentstobecombinedin,wecon- Denition8.Foragentiattimet,atestimonyfromagentkisreliableifand Testimonyfromawitnessisusedwhenthewitnessisconsideredsuciently case,wechooseareferralchainthatyieldsthehighesttrustratingfork. Denition9.Foragenti,atestimonyfromagentkwithrespecttoreferral Tworeferralchains1and2maypassthroughthesameagentk.Inthis i(k)t>0. chain1ismorereliablethanwithrespecttoreferralchain2ifandonlyif1 yieldsahighertrustratingforagentk,i.e.,t1 i(k)t2 i(k).
6 4.2IncorporatingTestimoniesfromDierentWitnesses theratingbyagivenagent.first,toeliminatedoublecountingofwitnesses,we Wenowshowhowtestimoniesfromdierentagentscanbeincorporatedinto distinctifandonlyifthewitnessesofalltestimoniesinearedistinct,i.e., jfe1w;:::;elwgj=l. denedistinctsetsoftestimonies.(ewreferstothewitnessoftestimonye). Denition10.AsetoftestimoniesE=fE1;:::;ELgtowardsagentnis fromthatwitness.noticethattheindividualwitnessesdonothavetobetrusted allthetrustabletestimonies,andforanywitness,itcontainsthebesttestimony greaterthan!ifortheirtestimonytobeused. Themaximallyreliabledistinct(MRD)subsetofasetoftestimoniescontains distinct,ve,and(8e:(e2e^te Denition11.VisaMRDsubsetofasetoftestimoniesEifandonlyifVis wecomputetheaverageoftestimoniesfromv:e=1=lpjvj Ew^TV GivenasetoftestimoniesEaboutAn,werstnditsMRDsubsetV.Next i(vw)te i(ew))). i(ew)>0))(9v:v2v^vw= agenta0willupdateitstrustratingofagentanasfollows(allratingsareat timetexceptwherespecied). when thent0(n)t+1= i=1vi.therefore, T0(n)andEarepositive oneoft0(n)andeisnegativet0(n)+e=(1?minfjt0(n)j;jejg) T0(n)andEarenegative T0(n)+E(1?T0(n)) 4.3Gossip T0(n)+E(1+T0(n)) IfanagentAencountersabadpartnerBduringsomeexchange,Awillpenalize BbydecreasingitsratingofBbyandinformingitsneighbors.Anagentwho receivesthisinformationcancombineitintoitstrustmodelofb. Denition12.SupposeagentireceivesamessageTk(n)(fromagentkabout isprocessedincrementally. propagatearumorwithouthavingbeenexplicitlyqueried.forthisreason,gossip Gossipisdierentfromtheusualreferralprocess,becauseanagentcan agentn).ifti(k)isnegative,theniignoresthemessage.ifti(k)ispositive, thenagentiupdatesitstrustratingofagentnasfollows. whenti(n)andtk(n)thenti(n)t+1= arebothpositive arebothnegative haveoppositesigns Ti(n)=Ti(n)+Ti(k)Tk(n)(1?Ti(n)) Ti(n)+Ti(k)Tk(n)(1+Ti(n)) (Ti(n)+Ti(k)Tk(n))=(1?minfjTi(n)j;jTi(k)Tk(n)jg)
7 Wenowdescribeandformalizesomeimportantpropertiesoftrust. 4.4PropertiesofTrust 1.Symmetry Ingeneral,symmetrywillnothold,becauseanagentmaytrustanothermore thanitistrustedback.however,whentheagentsaretrustworthy,through 2.Transitivity haveforanytwoagentsaxanday,tx(y)tty(x)twhent!1. ifoneoftheagentsdoesn'tactinatrustworthymanner,theotheragent willbeforcedtopenalizeit,leadingtolowmutualtrust.forthisreason,we repeatedinteractions,theywillconvergetohighmutualtrust.conversely, 3.Self-reinforcement Trustisnottransitive,butthefollowingwillholdifxisarationalagent: Trustisself-reinforcing,becauseagentsactpositivelywiththosewhomthey (Tx(y)t>Tx(z)t)^(Tx(z)t>Tx(w)t))(Tx(y)t>Tx(w)t) trust.theconverseistrue,asbelowacertaintrust,individualstendto conrmtheirsuspicionsofothers[9].therstpartofthefollowingruleis basedontheideathatiftrustbetweentwoagentsisinitiallyabove!,then Between!and,anythingcanhappen[5]. willtendnottocooperatewitheachotherwhateverthesituation,thus thetrustbetweenthosetwoagentswillnotdecreasebelowthatthreshold. reinforcingtheother'sopinionaboutthemasnon-cooperativeandunhelpful. Theconverseistrue,sinceifbothagentstrusteachotherbelow,they {If(Tx(y)t>!x)^(Ty(x)t>!y)then 4.Propagation {If(Tx(y)t<x)^(Ty(x)t<y)then (Tx(y)t+1Tx(y)t)^(Ty(x)t+1Ty(x)t) notknowz.howmuchxtrustszshoulddependonhowmuchxtrustsy, Considerthreeagentsx,y,andz.Ifxknowsyandyknowsz,butxdoes (Tx(y)t+1Tx(y)t)^(Ty(x)t+1Ty(x)t) andhowmuchytrustsz.thefollowingrulewillholdifxisrational. Asimpleformulafordeterminingtrustthatsatisestheaboveconstraint,is (Tx(z)t+1Tx(y)t)^(Tx(z)t+1Ty(z)t) 5ExperimentsandResults Tx(z)t+1=Tx(y)tTy(z)t manyagentsknowthegivenagent,howmanyagentsitknows,whichcommunity Inoursimulatedsetup,eachagenthasaninterestvector,anexpertisevector, itbelongsto,andsoon.inourcase,theneighbormodelskeptbyanagentare andmodelsofseveralneighbors.ingeneral,theneighbormodelsdependonhow thegivenagent'srepresentationoftheotheragents'expertiseandreputation.
8 generatedasvectorsbyperturbingtheinterestvectorofthegivenagent.the dependingonitsinterests. motivationforthisistocapturetheintuitionthatanagentwillproducequeries Anagent'squeriesaregeneratedbasedonitsinterestvector.Thequeriesare vector,orrefertootheragentsitknows.theoriginatingagentcollectsallpossible referrals,andcontinuestheprocessbycontactingsomeofthesuggestedreferrals. Atthesametime,itchangesitsmodelsforotheragents. Whenanagentreceivesaquery,itwilltrytoansweritbasedonitsexpertise vectorsofdimension5.theagentssendqueries,referrals,andresponsestoone another,allthewhilelearningabouteachothers'interestandexpertisevectors. Theagentsarelimitedinthenumberofneighborstheymayhave inourcase thelimitis4. Ourexperimentsinvolvebetween20and60agentswithinterestandexpertise 5.1Metrics Wenowdenesomeusefulmetricsinwhichtointuitivelycapturetheresultsof ourexperiments. wherenisthenumberofagentswhoknowagentai.wesaythatagentak agentsisgivenbyr(ai):r(ai)=1=npnj=1tj(ai) Denition13.TheaveragereputationofanagentAifromthepointofother wherenisthetotalnumberofagents. Denition14.Theaveragereputationofallagentsis:R=1=NPNi=1r(Ai), knowsagentaiifandonlyifaiisaneighborofak. 5.2SelectionofRewardsandPenalties Figure1illustratesthechangeoftrustratingsdependingondierentvaluesof Thisaverageisametricfordeterminingthestabilizationofacommunity. and.partaappliestoanewagentwhoinitiallyhasatrustof0,butbuildsup whoisalreadywell-trusted;partcappliestoanuntrustedagentwhothrough theratingthroughpositiveinteractions;partbappliestoacooperativeagent repeatedpositiveinteractionsbecomestrusted;partdappliestoanewagent whoseratingfallsbecauseofnegativeinteractions;partedescribesatrusted untrustedagentwhobecomesfurtheruntrustedbecauseofdefections. agentwhobecomesuntrustedbecauseofdefections;and,partfappliestoan betheratiobetweenthenumberofcooperationsanddefections.byappropriatelyselectingtheratingsofand,wecanlet!1.assumetheinitial trustratingofagentaiis0:6.let=5;10;20.figure2displaysthechangeof trustrating.noticethattrustbuiltupthroughseveralpositiveinteractionsis Consideranagentwhocooperatesanddefectsondierentinteractions.Let lostthroughevenasingledefection.
9 Part A. T 0 =0,α=0.05,0.1,0.2 1 Part B. T 0 =0.6,α=0.05,0.1,0.2 1 Part C. T 0 = 0.6,α=0.05,0.1, Part D. T 0 =0,β= 0.1, 0.2, Part E. T 0 =0.6,β= 0.1, 0.2, Part F. T 0 = 0.6,β= 0.1, 0.2, Fig.1.Selectionofand,where=0:05(0?0),0:1(0?:0),0:2(0??0)and= 0.4?0:1(0x0),?0:2(0+0),?0:3(00) AvoidingUndesirableAgents Ourmechanismquicklylowersthereputationsofselshagents.Considerthe agentsax,ay,andazknowhim.theirinitialratingstowardsaware0:4,0:5, followingexample.assumeagentawisanon-cooperativeagent,andonlythree and0:6,respectively. agentaxwilldisseminateitsobservationofagentawthroughoutthesocialnetwork.eventuallytheaveragereputationofagentawmaydecreasetoalowlevel. Thisisthepowerofreferrals.Figure3experimentallyconrmsourhypothesis. 1,agentAwdefectsagainstagentAx.Let=0:05and=?0:3.Accordingto theformulaforupdatingtrust,tx(w)=(0:4+(?0:3))=(1?minj0:4j;j?0:3j)= 0:1=0:7=0:1429.Thenewreputationoftheagentisr(Aw)=0:413.Moreover, SotheaveragereputationofagentAwattime0is0:5.However,sayattime continuallyintroduceandremovethemselvesfromthenetwork.toevaluatehow 5.4IntroducingNewAgents ourapproachaccommodateschangesofthisvariety,webeginwithastable Clearly,asocialnetworkwillnotremainstableforlong,becauseagentswill thenewagentwouldhavetokeepcooperatingreliablyorelsebeostracizedearly. networkandintroduceanewagentrandomlyintoit.thenewagentisgiven randomneighbors,andalloftheirtrustratingstowardsthisnewagentarezero. AssumeR=0:637attimet.Inordertobeembeddedintothesocialnetwork,
10 Fig.2.Changeoftrustfor=5(0?0),10(0?:0),20(0?+0)when=0:05and=?0: Times interactions Average reputation Fig.3.AveragereputationofagentAwforN=30,=0:05and=?0: agents,thenewagentcanhaveitsaveragereputationincreasesteadily.figure conrmsthishypothesis. Itsinitialthresholdforcooperatingislow.Byfrequentlycooperatingwithother Numbers of messages 6Discussion Althoughwepresentourresultsinthecontextofelectroniccommunities,our oftheotheragents.theabilitytodealwithselsh,antisocial,orunreliable mentcanhelptheagentsnessetheirinteractionsdependingonthereputations agentsaretrustworthyandreliable.approachesforexplicitreputationmanage- approachappliestomultiagentsystemsingeneral.mostcurrentmultiagentsystemsassumebenevolence,meaningthattheagentsimplicitlyassumethatother agentscanleadtomorerobustmultiagentsystems.
11 Average reputation Fig.4.AveragereputationofnewagentAnewforN=30,=0:05and=?0: bymaliciousagents.itreliesonlyontherebeingalargenumberofagentswho withothers.however,itdoesnotfullyprotectagainstspuriousratingsgenerated Ourpresentapproachadjuststheratingsofagentsbasedontheirinteractions Numbers of messages agents.thisisnotideal,butnotanyworsethandemocraticruleinhuman oerhonestratingstooverridetheeectoftheratingsprovidedbythemalicious societies.democraticsocietiescannotguaranteethatamaliciousrulerwon'tbe ofthepopulationintheratingprocess. elected,buttheyreducethechanceofsuchaneventbyengagingalargefraction aswellasofcommunityformation.wealsowanttostudytheevolutionary situationswheregroupsofagentsconsiderratingschemesforotheragents.the purposeisnotonlytostudyalternativeapproachesforachievingmoreecient communities,butalsototestifourmechanismisrobustagainstinvasionand, Infuturework,weplantostudythespecialproblemsoflyingandrumors hence,morestable. References 3.LennyFoner.Yenta:Amulti-agent,referral-basedmatchmakingsystem.InProceedingsofthe1stInternationalConferenceonAutonomousAgents,pages301{ sellinggoods.inproceedingsofthe1stinternationalconferenceonthepractical 1.RobertAxelrod.TheEvolutionofCooperation.BasicBooks,NewYork, AnthonyChavezandPattieMaes.Kasbah:Anagentmarketplaceforbuyingand ApplicationofIntelligentAgentsandMultiagentTechnology(PAAM'96), RohitKhareandAdamRifkin.Weavingaweboftrust.WorldWideWeb,2(3):77{ 5.P.StevenMarsh.FormalisingTrustasaComputationalConcept.PhDthesis, 307, LarsRasmussonandSverkerJanson.SimulatedsocialcontrolforsecureInternet 112,1997. DepartmentofComputingScienceandMathematics,UniversityofStirling,April commerce.inproceedingsoftheworkshoponnewsecurityparadigms,
12 7.TimReaandPeterSkevington.Engenderingtrustinelectroniccommerce.British 8.MichaelSchilloandPetraFunk.Whocanyoutrust:Dealingwithdeception.In TelecommunicationsEngineering,17(3):150{157, BinYuandMunindarP.Singh.Anmultiagentreferralsystemforexpertiselocation.InWorkingNotesoftheAAAIWorkshoponIntelligentInformationSystems, 9.SusanP.Shapiro.Thesocialcontrolofimpersonaltrust.TheAmericanJournal ProceedingsoftheworkshopDeception,FraudandtrustinAgentSocietiesatthe ofsociology,93(3):623{658,1987. AutonomousAgentsConference,pages95{106, GiorgosZacharia,AlexandrosMoukas,andPattieMaes.Collaborativereputation 11.BinYu,MahadevanVenkatraman,andMunindarP.Singh.Anadaptivesocial pages66{69,1999. ticialintelligence,2000.toappear. mechanismsinelectronicmarketplaces.inproceedingsofthehicss-32minitrack networkforinformationaccess:theoreticalandexperimentalresults.appliedar- onelectroniccommercetechnology,1999.
 α α λ α = = λ λ α ψ = = α α α λ λ ψ α = + β = > θ θ β > β β θ θ θ β θ β γ θ β = γ θ > β > γ θ β γ = θ β = θ β = θ β = β θ = β β θ = = = β β θ = + α α α α α = = λ λ λ λ λ λ λ = λ λ α α α α λ ψ + α =
α α λ α = = λ λ α ψ = = α α α λ λ ψ α = + β = > θ θ β > β β θ θ θ β θ β γ θ β = γ θ > β > γ θ β γ = θ β = θ β = θ β = β θ = β β θ = = = β β θ = + α α α α α = = λ λ λ λ λ λ λ = λ λ α α α α λ ψ + α =
 DistributedSharedMemorySystems? AdaptiveLoadBalancinginSoftware CompilerandRun-TimeSupportfor SotirisIoannidisandSandhyaDwarkadas fsi,[email protected] DepartmentofComputerScience Rochester,NY14627{0226
DistributedSharedMemorySystems? AdaptiveLoadBalancinginSoftware CompilerandRun-TimeSupportfor SotirisIoannidisandSandhyaDwarkadas fsi,[email protected] DepartmentofComputerScience Rochester,NY14627{0226
A Social Mechanism of Reputation Management in Electronic Communities
 A Social Mechanism of Reputation Management in Electronic Communities Bin Yu and Munindar P. Singh? Department of Computer Science North Carolina State University Raleigh, NC 27695-7534, USA fbyu, [email protected]
A Social Mechanism of Reputation Management in Electronic Communities Bin Yu and Munindar P. Singh? Department of Computer Science North Carolina State University Raleigh, NC 27695-7534, USA fbyu, [email protected]
portion,theso-calledserver,providesbasicservicessuchasdatai/o,buermanagementandconcurrency
 DynamO:DynamicObjectswithPersistentStorage JiongYang,SilviaNittel,WeiWang,andRichardMuntz UniversityofCalifornia,LosAngeles DepartmentofComputerScience intensiveapplications,e.g.,datamining,scienticcomputing,imageprocessing,etc.inthispaper,we
DynamO:DynamicObjectswithPersistentStorage JiongYang,SilviaNittel,WeiWang,andRichardMuntz UniversityofCalifornia,LosAngeles DepartmentofComputerScience intensiveapplications,e.g.,datamining,scienticcomputing,imageprocessing,etc.inthispaper,we
M-RPC:ARemoteProcedureCallServiceforMobileClients. DepartmentofComputerScience. Rutgers,TheStateUniversityofNewJersey. Piscataway,NJ08855
 M-RPC:ARemoteProcedureCallServiceforMobileClients AjayBakreandB.R.Badrinath DepartmentofComputerScience Rutgers,TheStateUniversityofNewJersey Piscataway,NJ08855 Email:fbakre,[email protected] Abstract
M-RPC:ARemoteProcedureCallServiceforMobileClients AjayBakreandB.R.Badrinath DepartmentofComputerScience Rutgers,TheStateUniversityofNewJersey Piscataway,NJ08855 Email:fbakre,[email protected] Abstract
Chapter 7 Notes - Inference for Single Samples. You know already for a large sample, you can invoke the CLT so:
 Chapter 7 Notes - Inference for Single Samples You know already for a large sample, you can invoke the CLT so: X N(µ, ). Also for a large sample, you can replace an unknown σ by s. You know how to do a
Chapter 7 Notes - Inference for Single Samples You know already for a large sample, you can invoke the CLT so: X N(µ, ). Also for a large sample, you can replace an unknown σ by s. You know how to do a
MITIGATING!WASTE,!DELAY!AND!RISK!
 MITIGATINGWASTE,DELAYANDRISK INTODAY SDESIGNREVIEWS: FINDING&ANSWERS&IN&RENEWED&DESIGN&VISUALIZATION& Respondents)in)the)2014)Design) Validation)and)Review)study)stated)they) averaged)20.5)design)reviews)a)month,)
MITIGATINGWASTE,DELAYANDRISK INTODAY SDESIGNREVIEWS: FINDING&ANSWERS&IN&RENEWED&DESIGN&VISUALIZATION& Respondents)in)the)2014)Design) Validation)and)Review)study)stated)they) averaged)20.5)design)reviews)a)month,)
Combined Virtual Mobile Core Network Function Placement and Topology Optimization with Latency bounds
 Combined Virtual Mobile Core Network Function Placement and Topology Optimization with Latency bounds Andreas Baumgartner Varun Reddy Thomas Bauschert Chair of Communication Networks Technische Universita
Combined Virtual Mobile Core Network Function Placement and Topology Optimization with Latency bounds Andreas Baumgartner Varun Reddy Thomas Bauschert Chair of Communication Networks Technische Universita
A DIGITAL SOLUTIONS AGENCY. 2212 Queen Anne Ave N. Ste. 337 Seattle WA, 98109 206.280.3422 [email protected] www.peelinteractive.
 A DIGITAL SOLUTIONS AGENCY We are an Enteractive Agency! We are a full service digital production agency located in Seattle Washington. We specialize in developing digital marketing for the entertainment
A DIGITAL SOLUTIONS AGENCY We are an Enteractive Agency! We are a full service digital production agency located in Seattle Washington. We specialize in developing digital marketing for the entertainment
CPUInheritance Scheduling. http://www.cs.utah.edu/projects/flux/ UniversityofUtah
 CPUInheritance Scheduling DepartmentofComputerScience ComputerSystemsLaboratory BryanFord SaiSusarla http://www.cs.utah.edu/projects/flux/ UniversityofUtah October30,1996 [email protected] 1 KeyConcepts
CPUInheritance Scheduling DepartmentofComputerScience ComputerSystemsLaboratory BryanFord SaiSusarla http://www.cs.utah.edu/projects/flux/ UniversityofUtah October30,1996 [email protected] 1 KeyConcepts
API Q2 Specification for Quality Management System Requirements for Service Supply Organizations for the Petroleum and Natural Gas Industries
 API Q2 Specification for Quality Management System Requirements for Service Supply Organizations for the Petroleum and Natural Gas Industries A Service Providers Perspective How is API Q2 Different ISO
API Q2 Specification for Quality Management System Requirements for Service Supply Organizations for the Petroleum and Natural Gas Industries A Service Providers Perspective How is API Q2 Different ISO
CSSE 372 Software Project Management: Earned Value Analysis (EVA) Exercises
 E 372 oftware Project Management: Earned Value Analysis (EVA) Exercises hawn Bohner Office: Moench Room F212 Phone: (812) 877-8685 Email: [email protected] Learning Outcomes: Plan (verb) reate a
E 372 oftware Project Management: Earned Value Analysis (EVA) Exercises hawn Bohner Office: Moench Room F212 Phone: (812) 877-8685 Email: [email protected] Learning Outcomes: Plan (verb) reate a
Concentrations. Concentration Advising
 UniversityofHartford HillyerCollegeAssociateofArtsinLiberalStudies(AA) Concentrations All Hillyer College students are designated Liberal Studies Majors. To enhance your programofstudy,youmadejoinaconcentrationgivingyouadesignationsuchas:liberal
UniversityofHartford HillyerCollegeAssociateofArtsinLiberalStudies(AA) Concentrations All Hillyer College students are designated Liberal Studies Majors. To enhance your programofstudy,youmadejoinaconcentrationgivingyouadesignationsuchas:liberal
Themethodofmovingcurvesandmovingsurfacesisanew,eectivetoolfor Abstract
 OnaRelationshipbetweentheMovingLineand MovingConicCoecientMatrices DepartmentofComputerScience Houston,Texas77005 [email protected] RiceUniversity MingZhang DepartmentofInformationSystemsandComputerScience
OnaRelationshipbetweentheMovingLineand MovingConicCoecientMatrices DepartmentofComputerScience Houston,Texas77005 [email protected] RiceUniversity MingZhang DepartmentofInformationSystemsandComputerScience
OPTIMIZING THE USE OF VHA s FEE BASIS CLAIMS SYSTEM (FBCS)
 VA-CASE VISN 11 VA Center for Applied Systems Engineering OPTIMIZING THE USE OF VHA s FEE BASIS CLAIMS SYSTEM (FBCS) The Fee Basis Claims System (FBCS) Optimization initiative aims to improve, standardize,
VA-CASE VISN 11 VA Center for Applied Systems Engineering OPTIMIZING THE USE OF VHA s FEE BASIS CLAIMS SYSTEM (FBCS) The Fee Basis Claims System (FBCS) Optimization initiative aims to improve, standardize,
Trust-based Service Management for Social Internet of Things Systems
 Trust-based Service Management for Social Internet of Things Systems Ing-Ray Chen, Fenye Bao, and Jia Guo Abstract A social Internet of Things (IoT) system can be viewed as a mix of traditional peer-to-peer
Trust-based Service Management for Social Internet of Things Systems Ing-Ray Chen, Fenye Bao, and Jia Guo Abstract A social Internet of Things (IoT) system can be viewed as a mix of traditional peer-to-peer
Continuous Integration Optimizing Your Release Management Process
 Continuous Integration Optimizing Your Release Management Process Continuous Integration? Why should I care? What s in it for me? Continuous Integration? Why should I care? What s in it for me? The cost
Continuous Integration Optimizing Your Release Management Process Continuous Integration? Why should I care? What s in it for me? Continuous Integration? Why should I care? What s in it for me? The cost
LINKS Tutorial #4: Forecasting. Katrina A. Zalatan & Randall G. Chapman
 LINKS Tutorial #4: Forecasting Katrina A. Zalatan & Randall G. Chapman Your LINKS is evaluated on financial, operating, and customer-related results. Planning is the process you go through to make decisions
LINKS Tutorial #4: Forecasting Katrina A. Zalatan & Randall G. Chapman Your LINKS is evaluated on financial, operating, and customer-related results. Planning is the process you go through to make decisions
SkillSoft Services. Achieve Success with SkillSoft Services. Overview
 Achieve Success with SkillSoft Services SkillSoft Services Overview Consulting Services Solution Services Custom Development Services SkillSoft s service philosophy is built on supporting customers in
Achieve Success with SkillSoft Services SkillSoft Services Overview Consulting Services Solution Services Custom Development Services SkillSoft s service philosophy is built on supporting customers in
Mathematics. (www.tiwariacademy.com : Focus on free Education) (Chapter 5) (Complex Numbers and Quadratic Equations) (Class XI)
 ( : Focus on free Education) Miscellaneous Exercise on chapter 5 Question 1: Evaluate: Answer 1: 1 ( : Focus on free Education) Question 2: For any two complex numbers z1 and z2, prove that Re (z1z2) =
( : Focus on free Education) Miscellaneous Exercise on chapter 5 Question 1: Evaluate: Answer 1: 1 ( : Focus on free Education) Question 2: For any two complex numbers z1 and z2, prove that Re (z1z2) =
Optimal Mail Sizing for Direct Marketing
 Optimal Mail Sizing for Direct Marketing Ph: 732-972-8969 [email protected] Some Typical Problems in Direct Marketing Test an offer to enroll in credit card registration Test a new creative with a
Optimal Mail Sizing for Direct Marketing Ph: 732-972-8969 [email protected] Some Typical Problems in Direct Marketing Test an offer to enroll in credit card registration Test a new creative with a
WEATHERSTORM FORENSIC ACCOUNTING LONG-SHORT INDEX. External Index Methodology Document
 WEATHERSTORM FORENSIC ACCOUNTING LONG-SHORT INDEX External Index Methodology Document 6/18/2015 CONTENTS 1 Index Overview... 2 2 Index Construction Methodology... 2 2.1 Index Constitution... 2 2.2 Universe
WEATHERSTORM FORENSIC ACCOUNTING LONG-SHORT INDEX External Index Methodology Document 6/18/2015 CONTENTS 1 Index Overview... 2 2 Index Construction Methodology... 2 2.1 Index Constitution... 2 2.2 Universe
A Dual Eigenvector Condition for Strong Lumpability of Markov Chains
 A Dual Eigenvector Condition for Strong Lumpability of Markov Chains Martin Nilsson Jacobi Olof Göernerup SFI WORKING PAPER: 2008-01-002 SFI Working Papers contain accounts of scientific work of the author(s)
A Dual Eigenvector Condition for Strong Lumpability of Markov Chains Martin Nilsson Jacobi Olof Göernerup SFI WORKING PAPER: 2008-01-002 SFI Working Papers contain accounts of scientific work of the author(s)
SAMPLE SIZE CONSIDERATIONS
 SAMPLE SIZE CONSIDERATIONS Learning Objectives Understand the critical role having the right sample size has on an analysis or study. Know how to determine the correct sample size for a specific study.
SAMPLE SIZE CONSIDERATIONS Learning Objectives Understand the critical role having the right sample size has on an analysis or study. Know how to determine the correct sample size for a specific study.
MAT 242 Test 3 SOLUTIONS, FORM A
 MAT Test SOLUTIONS, FORM A. Let v =, v =, and v =. Note that B = { v, v, v } is an orthogonal set. Also, let W be the subspace spanned by { v, v, v }. A = 8 a. [5 points] Find the orthogonal projection
MAT Test SOLUTIONS, FORM A. Let v =, v =, and v =. Note that B = { v, v, v } is an orthogonal set. Also, let W be the subspace spanned by { v, v, v }. A = 8 a. [5 points] Find the orthogonal projection
Sybilproof Reputation Mechanisms
 Sybilproof Reputation Mechanisms Alice Cheng Center for Applied Mathematics Cornell University, Ithaca, NY 14853 [email protected] Eric Friedman School of Operations Research and Industrial Engineering
Sybilproof Reputation Mechanisms Alice Cheng Center for Applied Mathematics Cornell University, Ithaca, NY 14853 [email protected] Eric Friedman School of Operations Research and Industrial Engineering
A linear combination is a sum of scalars times quantities. Such expressions arise quite frequently and have the form
 Section 1.3 Matrix Products A linear combination is a sum of scalars times quantities. Such expressions arise quite frequently and have the form (scalar #1)(quantity #1) + (scalar #2)(quantity #2) +...
Section 1.3 Matrix Products A linear combination is a sum of scalars times quantities. Such expressions arise quite frequently and have the form (scalar #1)(quantity #1) + (scalar #2)(quantity #2) +...
Trend Micro Healthcare Compliance Solutions
 How Trend Micro s innovative security solutions help healthcare organizations address risk and compliance challenges WHITE Worry-Free Business Security Fast, effective, and simple protection against viruses
How Trend Micro s innovative security solutions help healthcare organizations address risk and compliance challenges WHITE Worry-Free Business Security Fast, effective, and simple protection against viruses
Joseph I. Lubin School of Accounting. MS Program
 Joseph I. Lubin School of Accounting MS Program THE WHITMAN DIFFERENCE In today s marketplace, rapid innovation and business without borders require accounting professionals to think critically and conceive
Joseph I. Lubin School of Accounting MS Program THE WHITMAN DIFFERENCE In today s marketplace, rapid innovation and business without borders require accounting professionals to think critically and conceive
QUANTIFYING OPERATIONAL RISK Charles Smithson
 This article originally appeared in the March 2000 issue of RISK QUANTIFYING OPERATIONAL RISK Charles Smithson Financial institutions recognize the importance of quantifying (and managing) operational
This article originally appeared in the March 2000 issue of RISK QUANTIFYING OPERATIONAL RISK Charles Smithson Financial institutions recognize the importance of quantifying (and managing) operational
1.3. DOT PRODUCT 19. 6. If θ is the angle (between 0 and π) between two non-zero vectors u and v,
 1.3. DOT PRODUCT 19 1.3 Dot Product 1.3.1 Definitions and Properties The dot product is the first way to multiply two vectors. The definition we will give below may appear arbitrary. But it is not. It
1.3. DOT PRODUCT 19 1.3 Dot Product 1.3.1 Definitions and Properties The dot product is the first way to multiply two vectors. The definition we will give below may appear arbitrary. But it is not. It
Production Functions and Cost of Production
 1 Returns to Scale 1 14.01 Principles of Microeconomics, Fall 2007 Chia-Hui Chen October, 2007 Lecture 12 Production Functions and Cost of Production Outline 1. Chap 6: Returns to Scale 2. Chap 6: Production
1 Returns to Scale 1 14.01 Principles of Microeconomics, Fall 2007 Chia-Hui Chen October, 2007 Lecture 12 Production Functions and Cost of Production Outline 1. Chap 6: Returns to Scale 2. Chap 6: Production
Resource-Efficiency Testing. Introduction to Resource Efficiency Testing
 Introduction to Resource Efficiency Testing Contents Introduction Metrics Acquisition - Windows Performance Monitor OPC Server test plan model OPC Client test plan model Network Failure Simulation Batch
Introduction to Resource Efficiency Testing Contents Introduction Metrics Acquisition - Windows Performance Monitor OPC Server test plan model OPC Client test plan model Network Failure Simulation Batch
QUALITY MANAGEMENT PLAN
 Last updated: 10/30/09 Revision Number: V3 QUALITY MANAGEMENT PLAN 1 INTRODUCTION 1.1 PURPOSE OF THE PROJECT QUALITY MANAGEMENT PLAN The Project Quality Management Plan documents the necessary information
Last updated: 10/30/09 Revision Number: V3 QUALITY MANAGEMENT PLAN 1 INTRODUCTION 1.1 PURPOSE OF THE PROJECT QUALITY MANAGEMENT PLAN The Project Quality Management Plan documents the necessary information
 AClassofLinearAlgorithmstoProcessSetsofSegments GonzaloNavarroRicardoBaeza-Yates DepartmentofComputerScience fgnavarro,[email protected] BlancoEncalada2120 UniversityofChile Santiago-Chile currentsolutionstooperatesegmentsfocusonsingleoperations(e.g.insertionorsearching),
AClassofLinearAlgorithmstoProcessSetsofSegments GonzaloNavarroRicardoBaeza-Yates DepartmentofComputerScience fgnavarro,[email protected] BlancoEncalada2120 UniversityofChile Santiago-Chile currentsolutionstooperatesegmentsfocusonsingleoperations(e.g.insertionorsearching),
CSCMP Level One : Cornerstones of Supply Chain Management. Learning Blocks
 CSCMP Level One : Cornerstones of Supply Chain Management Learning Blocks Level one training will consist of eight learning blocks: 1. Supply Chain Concepts 2. Demand Planning 3. Procurement and Supply
CSCMP Level One : Cornerstones of Supply Chain Management Learning Blocks Level one training will consist of eight learning blocks: 1. Supply Chain Concepts 2. Demand Planning 3. Procurement and Supply
Course Supply Chain Management: Inventory Management. Inventories cost money: Reasons for inventory. Types of inventory
 Inventories cost money: Inventories are to be avoided at all cost? Course Supply Chain Management: Or Inventory Management Inventories can be useful? Chapter 10 Marjan van den Akker What are reasons for
Inventories cost money: Inventories are to be avoided at all cost? Course Supply Chain Management: Or Inventory Management Inventories can be useful? Chapter 10 Marjan van den Akker What are reasons for
HYPOTHESIS TESTING: POWER OF THE TEST
 HYPOTHESIS TESTING: POWER OF THE TEST The first 6 steps of the 9-step test of hypothesis are called "the test". These steps are not dependent on the observed data values. When planning a research project,
HYPOTHESIS TESTING: POWER OF THE TEST The first 6 steps of the 9-step test of hypothesis are called "the test". These steps are not dependent on the observed data values. When planning a research project,
Parabolic Equations. Chapter 5. Contents. 5.1.2 Well-Posed Initial-Boundary Value Problem. 5.1.3 Time Irreversibility of the Heat Equation
 7 5.1 Definitions Properties Chapter 5 Parabolic Equations Note that we require the solution u(, t bounded in R n for all t. In particular we assume that the boundedness of the smooth function u at infinity
7 5.1 Definitions Properties Chapter 5 Parabolic Equations Note that we require the solution u(, t bounded in R n for all t. In particular we assume that the boundedness of the smooth function u at infinity
Supply Chain Analysis Tools
 Supply Chain Analysis Tools MS&E 262 Supply Chain Management April 14, 2004 Inventory/Service Trade-off Curve Motivation High Inventory Low Poor Service Good Analytical tools help lower the curve! 1 Outline
Supply Chain Analysis Tools MS&E 262 Supply Chain Management April 14, 2004 Inventory/Service Trade-off Curve Motivation High Inventory Low Poor Service Good Analytical tools help lower the curve! 1 Outline
How to Book a Clichefter With or Without Windows XP
 Instructionsfor reservingand viewingcurryspaces usingoutlook Calendar 6/25/2015 Contents Overview...2 MacOSXandOffice2011...3 SchedulingAssistant...3 AddingCalendars...6 Windows7or8andOffice2010...9 SchedulingAssistant...9
Instructionsfor reservingand viewingcurryspaces usingoutlook Calendar 6/25/2015 Contents Overview...2 MacOSXandOffice2011...3 SchedulingAssistant...3 AddingCalendars...6 Windows7or8andOffice2010...9 SchedulingAssistant...9
Value Chain Analysis
 FAO High-Level Policy Learning Programme for decision makers and policy analysts Value Chain Analysis FAO VCA Software Tool 3.1 By Lorenzo Giovanni Bellù, Policy Officer and Piera Tortora, Consultant Policy
FAO High-Level Policy Learning Programme for decision makers and policy analysts Value Chain Analysis FAO VCA Software Tool 3.1 By Lorenzo Giovanni Bellù, Policy Officer and Piera Tortora, Consultant Policy
Achieving Competitive Advantage Through Supply Chain Excellence. Jim Webb, Senior Vice President of Operations, Provista
 Achieving Competitive Advantage Through Supply Chain Excellence Jim Webb, Senior Vice President of Operations, Provista Presentation objectives Competitive Forces Sources of Competitive Advantage Focus
Achieving Competitive Advantage Through Supply Chain Excellence Jim Webb, Senior Vice President of Operations, Provista Presentation objectives Competitive Forces Sources of Competitive Advantage Focus
Application-LayerAnycasting
 Application-LayerAnycasting fbobby,ammar,ewz,viren,[email protected] SamratBhattacharjee MostafaH.Ammar GIT{CC{96/25 EllenW.Zegura ZongmingFei VirenShah nicatewiththe\best"server,accordingtosomeperformanceorpolicycriteria,inagroup
Application-LayerAnycasting fbobby,ammar,ewz,viren,[email protected] SamratBhattacharjee MostafaH.Ammar GIT{CC{96/25 EllenW.Zegura ZongmingFei VirenShah nicatewiththe\best"server,accordingtosomeperformanceorpolicycriteria,inagroup
Performance Analysis of a Telephone System with both Patient and Impatient Customers
 Performance Analysis of a Telephone System with both Patient and Impatient Customers Yiqiang Quennel Zhao Department of Mathematics and Statistics University of Winnipeg Winnipeg, Manitoba Canada R3B 2E9
Performance Analysis of a Telephone System with both Patient and Impatient Customers Yiqiang Quennel Zhao Department of Mathematics and Statistics University of Winnipeg Winnipeg, Manitoba Canada R3B 2E9
Chapter 7: Dummy variable regression
 Chapter 7: Dummy variable regression Why include a qualitative independent variable?........................................ 2 Simplest model 3 Simplest case.............................................................
Chapter 7: Dummy variable regression Why include a qualitative independent variable?........................................ 2 Simplest model 3 Simplest case.............................................................
Metric Spaces. Chapter 7. 7.1. Metrics
 Chapter 7 Metric Spaces A metric space is a set X that has a notion of the distance d(x, y) between every pair of points x, y X. The purpose of this chapter is to introduce metric spaces and give some
Chapter 7 Metric Spaces A metric space is a set X that has a notion of the distance d(x, y) between every pair of points x, y X. The purpose of this chapter is to introduce metric spaces and give some
Thepurposeofahospitalinformationsystem(HIS)istomanagetheinformationthathealth
 FederatedDatabaseSystemsforReplicatingInformationin UniversityofDortmund,DepartmentofComputerScience,Informatik10 ExtendingtheSchemaArchitectureof E-mail:[email protected] HospitalInformationSystems
FederatedDatabaseSystemsforReplicatingInformationin UniversityofDortmund,DepartmentofComputerScience,Informatik10 ExtendingtheSchemaArchitectureof E-mail:[email protected] HospitalInformationSystems
Risk Management Policy
 Risk Management Policy June 2015 1 2 Contents 1. Policy Objectives and Background... 4 1.1. Policy Background... 4 1.2. Policy Objective... 4 1.3. Policy Sponsor and Maintenance... 4 2. Risk Types and
Risk Management Policy June 2015 1 2 Contents 1. Policy Objectives and Background... 4 1.1. Policy Background... 4 1.2. Policy Objective... 4 1.3. Policy Sponsor and Maintenance... 4 2. Risk Types and
Software Quality Assurance Plan
 Applying Broadcasting/Multicasting/Secured Communication to agentmom in Multi-Agent Systems Software Quality Assurance Plan Version 1.1 This document conforms to IEEE Std 730.1-1995 Software Quality Assurance
Applying Broadcasting/Multicasting/Secured Communication to agentmom in Multi-Agent Systems Software Quality Assurance Plan Version 1.1 This document conforms to IEEE Std 730.1-1995 Software Quality Assurance
Estimating the random coefficients logit model of demand using aggregate data
 Estimating the random coefficients logit model of demand using aggregate data David Vincent Deloitte Economic Consulting London, UK [email protected] September 14, 2012 Introduction Estimation
Estimating the random coefficients logit model of demand using aggregate data David Vincent Deloitte Economic Consulting London, UK [email protected] September 14, 2012 Introduction Estimation
Internet!of!Services! Project!IntroducMon!
 Internet!of!Services! Project!IntroducMon! Prof.!Dr.!Küpper,!S.!Göndör,!S.!Zickau,!M.!Slawik,!et!al.! ServiceIcentric!Networking! Telekom!InnovaMon!Laboratories!and!TU!Berlin! Introduc)on* Project!OrganizaMon!!
Internet!of!Services! Project!IntroducMon! Prof.!Dr.!Küpper,!S.!Göndör,!S.!Zickau,!M.!Slawik,!et!al.! ServiceIcentric!Networking! Telekom!InnovaMon!Laboratories!and!TU!Berlin! Introduc)on* Project!OrganizaMon!!
Max M. Fisher College of Business The Ohio State University. MHR 802 Managerial Negotiations Winter, 1997
 1997 MHR 802 Outline Day 1 Max M. Fisher College of Business The Ohio State University MHR 802 Managerial Negotiations Winter, 1997 Instructor: Professor Roy Lewicki Office: 304C Hall, 292-0258 E-mail:
1997 MHR 802 Outline Day 1 Max M. Fisher College of Business The Ohio State University MHR 802 Managerial Negotiations Winter, 1997 Instructor: Professor Roy Lewicki Office: 304C Hall, 292-0258 E-mail:
 NP-completeproblemstractable Copyingquantumcomputermakes MikaHirvensalo February1998 ISBN952-12-0158-4 TurkuCentreforComputerScience ISSN1239-1891 TUCSTechnicalReportNo161 superpositions,weshowthatnp-completeproblemscanbesolvedprobabilisticallyinpolynomialtime.wealsoproposetwomethodsthatcould
NP-completeproblemstractable Copyingquantumcomputermakes MikaHirvensalo February1998 ISBN952-12-0158-4 TurkuCentreforComputerScience ISSN1239-1891 TUCSTechnicalReportNo161 superpositions,weshowthatnp-completeproblemscanbesolvedprobabilisticallyinpolynomialtime.wealsoproposetwomethodsthatcould
About the Whitman School of Management
 About the Whitman School of Management Do you want to start your career at a multinational corporation or an emerging business? Or perhaps you dream of becoming an entrepreneur. Whatever your aspirations,
About the Whitman School of Management Do you want to start your career at a multinational corporation or an emerging business? Or perhaps you dream of becoming an entrepreneur. Whatever your aspirations,
Logic in general. Inference rules and theorem proving
 Logical Agents Knowledge-based agents Logic in general Propositional logic Inference rules and theorem proving First order logic Knowledge-based agents Inference engine Knowledge base Domain-independent
Logical Agents Knowledge-based agents Logic in general Propositional logic Inference rules and theorem proving First order logic Knowledge-based agents Inference engine Knowledge base Domain-independent
Commercialization Life Cycle
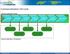 Commercialization Life Cycle Commercialization Phases Commercialization Checkpoints Definition Phase 1. Product Alignment with Company Strategy and Roadmap 2. Competitive Analysis Lessons/feedback from
Commercialization Life Cycle Commercialization Phases Commercialization Checkpoints Definition Phase 1. Product Alignment with Company Strategy and Roadmap 2. Competitive Analysis Lessons/feedback from
Calculus with Parametric Curves
 Calculus with Parametric Curves Suppose f and g are differentiable functions and we want to find the tangent line at a point on the parametric curve x f(t), y g(t) where y is also a differentiable function
Calculus with Parametric Curves Suppose f and g are differentiable functions and we want to find the tangent line at a point on the parametric curve x f(t), y g(t) where y is also a differentiable function
Software Testing Interview Questions
 Software Testing Interview Questions 1. What s the Software Testing? A set of activities conducted with the intent of finding errors in software. 2.What is Acceptance Testing? Testing conducted to enable
Software Testing Interview Questions 1. What s the Software Testing? A set of activities conducted with the intent of finding errors in software. 2.What is Acceptance Testing? Testing conducted to enable
Chapter 7 Risk, Return, and the Capital Asset Pricing Model
 Chapter 7 Risk, Return, and the Capital Asset Pricing Model MULTIPLE CHOICE 1. Suppose Sarah can borrow and lend at the risk free-rate of 3%. Which of the following four risky portfolios should she hold
Chapter 7 Risk, Return, and the Capital Asset Pricing Model MULTIPLE CHOICE 1. Suppose Sarah can borrow and lend at the risk free-rate of 3%. Which of the following four risky portfolios should she hold
6.2 Permutations continued
 6.2 Permutations continued Theorem A permutation on a finite set A is either a cycle or can be expressed as a product (composition of disjoint cycles. Proof is by (strong induction on the number, r, of
6.2 Permutations continued Theorem A permutation on a finite set A is either a cycle or can be expressed as a product (composition of disjoint cycles. Proof is by (strong induction on the number, r, of
How Far is too Far? Statistical Outlier Detection
 How Far is too Far? Statistical Outlier Detection Steven Walfish President, Statistical Outsourcing Services [email protected] 30-325-329 Outline What is an Outlier, and Why are
How Far is too Far? Statistical Outlier Detection Steven Walfish President, Statistical Outsourcing Services [email protected] 30-325-329 Outline What is an Outlier, and Why are
1 Solution of Homework
 Math 3181 Dr. Franz Rothe February 4, 2011 Name: 1 Solution of Homework 10 Problem 1.1 (Common tangents of two circles). How many common tangents do two circles have. Informally draw all different cases,
Math 3181 Dr. Franz Rothe February 4, 2011 Name: 1 Solution of Homework 10 Problem 1.1 (Common tangents of two circles). How many common tangents do two circles have. Informally draw all different cases,
Electron-Muon Ranger (EMR)
 Electron-Muon Ranger (EMR) Ruslan Asfandiyarov MICE Video Conference April 11, 2013 Construction Construction quarter of the detector completed (12 planes) every plane tested (LED / Camera / image analysis)
Electron-Muon Ranger (EMR) Ruslan Asfandiyarov MICE Video Conference April 11, 2013 Construction Construction quarter of the detector completed (12 planes) every plane tested (LED / Camera / image analysis)
Asymmetric Threat Assessment Tool (ATAT)
 Asymmetric Threat Assessment Tool (ATAT) Gary W. King, Matthew Schmill, Andrew Hannon. Paul Cohen 140 Governors Drive University of Massachusetts, Amherst Amherst, MA 01003 413 577-0176 [email protected]
Asymmetric Threat Assessment Tool (ATAT) Gary W. King, Matthew Schmill, Andrew Hannon. Paul Cohen 140 Governors Drive University of Massachusetts, Amherst Amherst, MA 01003 413 577-0176 [email protected]
Subtitles on everything for everyone Enabling community subtitling and translation for every video on the net.
 Subtitles on everything for everyone Enabling community subtitling and translation for every video on the net. 1. Overview: The potential: community-driven subtitling could make video global Inside a community
Subtitles on everything for everyone Enabling community subtitling and translation for every video on the net. 1. Overview: The potential: community-driven subtitling could make video global Inside a community
HP Cyber Security Control Cyber Insight & Defence
 HP Cyber Security Control Cyber Insight & Defence Security awareness at board level Security leadership is under immense pressure Cyber threat Extended supply chain Financial loss Reputation damage Cost
HP Cyber Security Control Cyber Insight & Defence Security awareness at board level Security leadership is under immense pressure Cyber threat Extended supply chain Financial loss Reputation damage Cost
