On Covert Data Communication Channels Employing DNA Steganography with Application in Massive Data Storage
|
|
|
- Monica Mitchell
- 9 years ago
- Views:
Transcription
1 ARAB ACADEMY FOR SCIENCE, TECHNOLOGY AND MARITIME TRANSPORT COLLEGE OF ENGINEERING AND TECHNOLOGY COMPUTER ENGINEERING DEPARTMENT On Covert Data Communication Channels Employing DNA Steganography with Application in Massive Data Storage Thesis submitted in partial fulfillment of the Requirements for the Degree of Master of Science in Computer Engineering. Submitted by: Mohamed El-Sayed El-Zanaty Supervised by: Prof. Dr. Magdy Saeb. Dr. Eman El-Abd.
2 Abstract DNA is the carrier of the life code, the form which was identified by Watson and Crick as a double helix of deoxyribonucleic acid (DNA). The DNA molecule consists of two-phosphate side chains linked by the nucleotide bases Adenine(A), Guanine(G), Cytosine(C) and Thymine(T). The DNA within each cell carries the fifty thousands genes that control cellular activities. Most of the modern steganographic techniques are based on digital media and these have some limitations or drawbacks where specialized filters can be applied to internet firewalls to detect packets that carry hidden information. The major drawback of the above techniques is the unsecured concealing of secret message. In the recent few years researchers have inclined to use DNA as one of the data hiding media. In this work we propose two new methods of embedding messages into DNA strands and employing restriction enzymes that cut the DNA in specific positions. The first method uses Recombinant DNA Technology,the second method uses the DNA Mutagenesis to insert the message into DNA. The receiver will be able to retrieve the hidden message using the key. In addition, we discuss the message space issues and the vulnerability of the two methods and the proposed modifications. Moreover we proposed the usefulness of the DNA in massive data storage and in solving NP complete problems Finally we construct a C# program that simulate the two previous methods that can hide a message into DNA file and send this file to the receiver. At the receiver side the program will extract the message from the received DNA file.
3 ACKNOWLEDGMENT I wish to express my grateful and indebtedness to professor Magdy Saeb and Dr Eman El-Abd, for their distinct supervision, support, permanent unlimited help, and encouragement during the making of this thesis. I would like to express my gratitude to the faculty and staff of the Computer Engineering department, at Arab Academy for Sciences, Technology and Maritime Transport, for their valuable advices. I send my success in this thesis to my family, work colleagues and friends.
4 Acronyms DNA : Deoxyribonucleic Acid. PCR : Polymerase Chain Reaction. YAC : Yeast Artificial Chromosome. Indels : DNA Insertion / Deletion Mutations. Kpb : Kilo base pair. Mbp : Mega base pair.
5 List of Figures Figure 1: DNA shape... 9 Figure 2: Process of steganography..11 Figure 3: Least significant bit process..12 Figure 4: Embed a message with a stego-key...13 Figure 5: DNA Steganography using PCR...14 Figure 6: The Hamiltonian path.19 Figure 7: The solution of the Hamiltonian path..21 Figure 8: The plasmid vector 29 Figure 9: The Lambda phage vector.30 Figure 10: (a) The Cosmid vector and COS site. (b) The Cosmid vector after being cleaved with restriction enzyme.. 31 Figure 11: The YAC vector 32 Figure 12: Procedure of hiding message into DNA using Recombinant technique.33 Figure 13: Procedure of hiding message into Plasmid vector...34 Figure 14: Procedure of hiding message into DNA using Mutagenesis Figure 15: The enzymes and its target substrings. 50 Figure 16: The word and its DNA mapping.51 Figure 17:The Enzyme and its occurrence number in the DNA...52 Figure 18:The message, header and the selected two enzymes...53 Figure 19: Get the message back..54 Figure 20: The program overall process..56 Figure 21: DNA Mutagenesis Step 1.59 Figure 22: DNA Mutagenesis Step 2.60 Figure 23: DNA Mutagenesis Step 3.60 Figure 24: DNA Mutagenesis Step 4.60 Figure 25: DNA Mutagenesis Step 5.61 Figure 26: The biological overall process.62 Figure 27: The original DNA message with restriction enzymes.68 Figure 28: The restriction map of vector ptz57r/t.70
6 List of Tables Table 1: Cities and paths encoded with DNA 20 Table 2: Some of the restriction enzymes and their target substrings 26 Table 3: The most 1024 commonly used words and the DNA representation 27 Table 4: Possible vectors and its maximum length that can carry Table 5: Troubleshooting in Recombinant DNA... 71
7 PUBLICATIONS Paper: MAGDY SAEB, EMAN EL-ABD, MOHAMED E. EL-ZANATY, On Covert Data Communication Channels Employing DNA Recombinant and Mutagenesis-based Steganographic Techniques, WSEAS World Scientific And Engineering Academy And Society Proceedings Computer Engineering and Applications (CEA 07), Gold Cost, Australia, January Journal: MAGDY SAEB, EMAN EL-ABD, MOHAMED E. EL-ZANATY, DNA Steganography Using DNA Recombinant and DNA Mutagenesis Techniques, WSEAS World Scientific And Engineering Academy And Society Transactions Computer Research, Issue 1,Voulume 2, January 2007, ISSN
8 Table of Contents List of Figures.5 List of Tables..6 Acronyms Introduction Basics of DNA Applicability of Bioinformatics and Data security using DNA Classical Methods of Steganography Fingerprinting and Watermarking Least Significant Bit Insertion Public Key Steganography Frequency Domain encoding DNA steganography using Polymerase Chain Reaction Summary DNA Applications Introduction Using DNA as Massive Data Storage Encoding Data Indexing Data Retrieving Data Using DNA in Solving NP-Complete Problems Hamiltonian Path Problem Solving the Hamiltonian Path Problem using DNA Generation-&-Test Algorithm The DNA Experiment Summary Methodology Introduction Restriction Enzymes Assumptions Recombinant DNA Vectors Plasmids Lambda Phage Cosmid YAC Sender Point of View Prepare the Message Cut the DNA Vector with Restriction Enzymes Embed the Message using Recombinant DNA 35
9 Receiver Point of View DNA Mutagenesis Mutation Process Kinds of Mutations Point Mutation Frame-Shift Mutation Deletion Insertion Inversion Mutation using PCR DNA Insertion/Deletion Mutations ("indels") Sender Point of View Prepare the Message Scan Specific DNA Sequence for Specific Two Restriction Sites Use DNA Mutagenesis Technique to Modify Bases Receiver Point of View Probability of Finding the Target Substring of Restriction Enzyme Maximum Message Space Recombinant DNA DNA Mutagenesis Summary Vulnerability and Modifications Introduction Vulnerability Attacks Steganalysis Brute Force Attack Modifications Summary Implementation Introduction Initializations Restriction Enzymes Table Mapping Table Procedure of Hiding Message into DNA File Get all the enzymes and its number of occurrences Construct the new DNA file with hidden message Procedure of Retrieving the Message From DNA File Algorithm of Hiding and Retrieving a Message From DNA Summary...56
10 6 - Lab Experiments Introduction Recombinant DNA DNA Mutagenesis Summary Summary, Conclusion and Future Work Summary and Conclusion Future Work..65 References Appendix A: Recombinant DNA Procedure...68 Appendix B: Source Code of The Program...72
On Covert Data Communication Channels Employing DNA Recombinant and Mutagenesis-based Steganographic Techniques
 On Covert Data Communication Channels Employing DNA Recombinant and Mutagenesis-based Steganographic Techniques MAGDY SAEB 1, EMAN EL-ABD 2, MOHAMED E. EL-ZANATY 1 1. School of Engineering, Computer Department,
On Covert Data Communication Channels Employing DNA Recombinant and Mutagenesis-based Steganographic Techniques MAGDY SAEB 1, EMAN EL-ABD 2, MOHAMED E. EL-ZANATY 1 1. School of Engineering, Computer Department,
CCR Biology - Chapter 9 Practice Test - Summer 2012
 Name: Class: Date: CCR Biology - Chapter 9 Practice Test - Summer 2012 Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Genetic engineering is possible
Name: Class: Date: CCR Biology - Chapter 9 Practice Test - Summer 2012 Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Genetic engineering is possible
CHAPTER 6: RECOMBINANT DNA TECHNOLOGY YEAR III PHARM.D DR. V. CHITRA
 CHAPTER 6: RECOMBINANT DNA TECHNOLOGY YEAR III PHARM.D DR. V. CHITRA INTRODUCTION DNA : DNA is deoxyribose nucleic acid. It is made up of a base consisting of sugar, phosphate and one nitrogen base.the
CHAPTER 6: RECOMBINANT DNA TECHNOLOGY YEAR III PHARM.D DR. V. CHITRA INTRODUCTION DNA : DNA is deoxyribose nucleic acid. It is made up of a base consisting of sugar, phosphate and one nitrogen base.the
Alaa Alhamami, Avan Sabah Hamdi Amman Arab University Amman, Jordan
 World of Computer Science and Information Technology Journal (WCSIT) ISSN: 2221-0741 Vol. 5, No. 5, 87-91, 2015 Mobile Secure Transmission Method Based on Audio Steganography Alaa Alhamami, Avan Sabah
World of Computer Science and Information Technology Journal (WCSIT) ISSN: 2221-0741 Vol. 5, No. 5, 87-91, 2015 Mobile Secure Transmission Method Based on Audio Steganography Alaa Alhamami, Avan Sabah
restriction enzymes 350 Home R. Ward: Spring 2001
 restriction enzymes 350 Home Restriction Enzymes (endonucleases): molecular scissors that cut DNA Properties of widely used Type II restriction enzymes: recognize a single sequence of bases in dsdna, usually
restriction enzymes 350 Home Restriction Enzymes (endonucleases): molecular scissors that cut DNA Properties of widely used Type II restriction enzymes: recognize a single sequence of bases in dsdna, usually
Replication Study Guide
 Replication Study Guide This study guide is a written version of the material you have seen presented in the replication unit. Self-reproduction is a function of life that human-engineered systems have
Replication Study Guide This study guide is a written version of the material you have seen presented in the replication unit. Self-reproduction is a function of life that human-engineered systems have
Lecture 13: DNA Technology. DNA Sequencing. DNA Sequencing Genetic Markers - RFLPs polymerase chain reaction (PCR) products of biotechnology
 Lecture 13: DNA Technology DNA Sequencing Genetic Markers - RFLPs polymerase chain reaction (PCR) products of biotechnology DNA Sequencing determine order of nucleotides in a strand of DNA > bases = A,
Lecture 13: DNA Technology DNA Sequencing Genetic Markers - RFLPs polymerase chain reaction (PCR) products of biotechnology DNA Sequencing determine order of nucleotides in a strand of DNA > bases = A,
Expression and Purification of Recombinant Protein in bacteria and Yeast. Presented By: Puspa pandey, Mohit sachdeva & Ming yu
 Expression and Purification of Recombinant Protein in bacteria and Yeast Presented By: Puspa pandey, Mohit sachdeva & Ming yu DNA Vectors Molecular carriers which carry fragments of DNA into host cell.
Expression and Purification of Recombinant Protein in bacteria and Yeast Presented By: Puspa pandey, Mohit sachdeva & Ming yu DNA Vectors Molecular carriers which carry fragments of DNA into host cell.
Safer data transmission using Steganography
 Safer data transmission using Steganography Arul Bharathi, B.K.Akshay, M.Priy a, K.Latha Department of Computer Science and Engineering Sri Sairam Engineering College Chennai, India Email: [email protected],
Safer data transmission using Steganography Arul Bharathi, B.K.Akshay, M.Priy a, K.Latha Department of Computer Science and Engineering Sri Sairam Engineering College Chennai, India Email: [email protected],
DNA Replication & Protein Synthesis. This isn t a baaaaaaaddd chapter!!!
 DNA Replication & Protein Synthesis This isn t a baaaaaaaddd chapter!!! The Discovery of DNA s Structure Watson and Crick s discovery of DNA s structure was based on almost fifty years of research by other
DNA Replication & Protein Synthesis This isn t a baaaaaaaddd chapter!!! The Discovery of DNA s Structure Watson and Crick s discovery of DNA s structure was based on almost fifty years of research by other
Chapter 6 DNA Replication
 Chapter 6 DNA Replication Each strand of the DNA double helix contains a sequence of nucleotides that is exactly complementary to the nucleotide sequence of its partner strand. Each strand can therefore
Chapter 6 DNA Replication Each strand of the DNA double helix contains a sequence of nucleotides that is exactly complementary to the nucleotide sequence of its partner strand. Each strand can therefore
DNA, RNA, Protein synthesis, and Mutations. Chapters 12-13.3
 DNA, RNA, Protein synthesis, and Mutations Chapters 12-13.3 1A)Identify the components of DNA and explain its role in heredity. DNA s Role in heredity: Contains the genetic information of a cell that can
DNA, RNA, Protein synthesis, and Mutations Chapters 12-13.3 1A)Identify the components of DNA and explain its role in heredity. DNA s Role in heredity: Contains the genetic information of a cell that can
Academic Nucleic Acids and Protein Synthesis Test
 Academic Nucleic Acids and Protein Synthesis Test Multiple Choice Identify the letter of the choice that best completes the statement or answers the question. 1. Each organism has a unique combination
Academic Nucleic Acids and Protein Synthesis Test Multiple Choice Identify the letter of the choice that best completes the statement or answers the question. 1. Each organism has a unique combination
INTERNATIONAL CONFERENCE ON HARMONISATION OF TECHNICAL REQUIREMENTS FOR REGISTRATION OF PHARMACEUTICALS FOR HUMAN USE Q5B
 INTERNATIONAL CONFERENCE ON HARMONISATION OF TECHNICAL REQUIREMENTS FOR REGISTRATION OF PHARMACEUTICALS FOR HUMAN USE ICH HARMONISED TRIPARTITE GUIDELINE QUALITY OF BIOTECHNOLOGICAL PRODUCTS: ANALYSIS
INTERNATIONAL CONFERENCE ON HARMONISATION OF TECHNICAL REQUIREMENTS FOR REGISTRATION OF PHARMACEUTICALS FOR HUMAN USE ICH HARMONISED TRIPARTITE GUIDELINE QUALITY OF BIOTECHNOLOGICAL PRODUCTS: ANALYSIS
Bob Jesberg. Boston, MA April 3, 2014
 DNA, Replication and Transcription Bob Jesberg NSTA Conference Boston, MA April 3, 2014 1 Workshop Agenda Looking at DNA and Forensics The DNA, Replication i and Transcription i Set DNA Ladder The Double
DNA, Replication and Transcription Bob Jesberg NSTA Conference Boston, MA April 3, 2014 1 Workshop Agenda Looking at DNA and Forensics The DNA, Replication i and Transcription i Set DNA Ladder The Double
Structure and Function of DNA
 Structure and Function of DNA DNA and RNA Structure DNA and RNA are nucleic acids. They consist of chemical units called nucleotides. The nucleotides are joined by a sugar-phosphate backbone. The four
Structure and Function of DNA DNA and RNA Structure DNA and RNA are nucleic acids. They consist of chemical units called nucleotides. The nucleotides are joined by a sugar-phosphate backbone. The four
Arabidopsis. A Practical Approach. Edited by ZOE A. WILSON Plant Science Division, School of Biological Sciences, University of Nottingham
 Arabidopsis A Practical Approach Edited by ZOE A. WILSON Plant Science Division, School of Biological Sciences, University of Nottingham OXPORD UNIVERSITY PRESS List of Contributors Abbreviations xv xvu
Arabidopsis A Practical Approach Edited by ZOE A. WILSON Plant Science Division, School of Biological Sciences, University of Nottingham OXPORD UNIVERSITY PRESS List of Contributors Abbreviations xv xvu
2. The number of different kinds of nucleotides present in any DNA molecule is A) four B) six C) two D) three
 Chem 121 Chapter 22. Nucleic Acids 1. Any given nucleotide in a nucleic acid contains A) two bases and a sugar. B) one sugar, two bases and one phosphate. C) two sugars and one phosphate. D) one sugar,
Chem 121 Chapter 22. Nucleic Acids 1. Any given nucleotide in a nucleic acid contains A) two bases and a sugar. B) one sugar, two bases and one phosphate. C) two sugars and one phosphate. D) one sugar,
European Medicines Agency
 European Medicines Agency July 1996 CPMP/ICH/139/95 ICH Topic Q 5 B Quality of Biotechnological Products: Analysis of the Expression Construct in Cell Lines Used for Production of r-dna Derived Protein
European Medicines Agency July 1996 CPMP/ICH/139/95 ICH Topic Q 5 B Quality of Biotechnological Products: Analysis of the Expression Construct in Cell Lines Used for Production of r-dna Derived Protein
From DNA to Protein. Proteins. Chapter 13. Prokaryotes and Eukaryotes. The Path From Genes to Proteins. All proteins consist of polypeptide chains
 Proteins From DNA to Protein Chapter 13 All proteins consist of polypeptide chains A linear sequence of amino acids Each chain corresponds to the nucleotide base sequence of a gene The Path From Genes
Proteins From DNA to Protein Chapter 13 All proteins consist of polypeptide chains A linear sequence of amino acids Each chain corresponds to the nucleotide base sequence of a gene The Path From Genes
CHAPTER 1 INTRODUCTION
 CHAPTER 1 INTRODUCTION 1.1 Overview Steganography is the process of hiding secret data inside other, normally transmitted data. In other words, as defined by [40] steganography means hiding of a secret
CHAPTER 1 INTRODUCTION 1.1 Overview Steganography is the process of hiding secret data inside other, normally transmitted data. In other words, as defined by [40] steganography means hiding of a secret
Genetic information (DNA) determines structure of proteins DNA RNA proteins cell structure 3.11 3.15 enzymes control cell chemistry ( metabolism )
 Biology 1406 Exam 3 Notes Structure of DNA Ch. 10 Genetic information (DNA) determines structure of proteins DNA RNA proteins cell structure 3.11 3.15 enzymes control cell chemistry ( metabolism ) Proteins
Biology 1406 Exam 3 Notes Structure of DNA Ch. 10 Genetic information (DNA) determines structure of proteins DNA RNA proteins cell structure 3.11 3.15 enzymes control cell chemistry ( metabolism ) Proteins
Basic Concepts Recombinant DNA Use with Chapter 13, Section 13.2
 Name Date lass Master 19 Basic oncepts Recombinant DN Use with hapter, Section.2 Formation of Recombinant DN ut leavage Splicing opyright lencoe/mcraw-hill, a division of he Mcraw-Hill ompanies, Inc. Bacterial
Name Date lass Master 19 Basic oncepts Recombinant DN Use with hapter, Section.2 Formation of Recombinant DN ut leavage Splicing opyright lencoe/mcraw-hill, a division of he Mcraw-Hill ompanies, Inc. Bacterial
a. Ribosomal RNA rrna a type ofrna that combines with proteins to form Ribosomes on which polypeptide chains of proteins are assembled
 Biology 101 Chapter 14 Name: Fill-in-the-Blanks Which base follows the next in a strand of DNA is referred to. as the base (1) Sequence. The region of DNA that calls for the assembly of specific amino
Biology 101 Chapter 14 Name: Fill-in-the-Blanks Which base follows the next in a strand of DNA is referred to. as the base (1) Sequence. The region of DNA that calls for the assembly of specific amino
Appendix 2 Molecular Biology Core Curriculum. Websites and Other Resources
 Appendix 2 Molecular Biology Core Curriculum Websites and Other Resources Chapter 1 - The Molecular Basis of Cancer 1. Inside Cancer http://www.insidecancer.org/ From the Dolan DNA Learning Center Cold
Appendix 2 Molecular Biology Core Curriculum Websites and Other Resources Chapter 1 - The Molecular Basis of Cancer 1. Inside Cancer http://www.insidecancer.org/ From the Dolan DNA Learning Center Cold
Recombinant DNA Technology
 Recombinant DNA Technology Dates in the Development of Gene Cloning: 1965 - plasmids 1967 - ligase 1970 - restriction endonucleases 1972 - first experiments in gene splicing 1974 - worldwide moratorium
Recombinant DNA Technology Dates in the Development of Gene Cloning: 1965 - plasmids 1967 - ligase 1970 - restriction endonucleases 1972 - first experiments in gene splicing 1974 - worldwide moratorium
Basic Concepts of DNA, Proteins, Genes and Genomes
 Basic Concepts of DNA, Proteins, Genes and Genomes Kun-Mao Chao 1,2,3 1 Graduate Institute of Biomedical Electronics and Bioinformatics 2 Department of Computer Science and Information Engineering 3 Graduate
Basic Concepts of DNA, Proteins, Genes and Genomes Kun-Mao Chao 1,2,3 1 Graduate Institute of Biomedical Electronics and Bioinformatics 2 Department of Computer Science and Information Engineering 3 Graduate
Recombinant DNA & Genetic Engineering. Tools for Genetic Manipulation
 Recombinant DNA & Genetic Engineering g Genetic Manipulation: Tools Kathleen Hill Associate Professor Department of Biology The University of Western Ontario Tools for Genetic Manipulation DNA, RNA, cdna
Recombinant DNA & Genetic Engineering g Genetic Manipulation: Tools Kathleen Hill Associate Professor Department of Biology The University of Western Ontario Tools for Genetic Manipulation DNA, RNA, cdna
DNA Fingerprinting. Unless they are identical twins, individuals have unique DNA
 DNA Fingerprinting Unless they are identical twins, individuals have unique DNA DNA fingerprinting The name used for the unambiguous identifying technique that takes advantage of differences in DNA sequence
DNA Fingerprinting Unless they are identical twins, individuals have unique DNA DNA fingerprinting The name used for the unambiguous identifying technique that takes advantage of differences in DNA sequence
Translation Study Guide
 Translation Study Guide This study guide is a written version of the material you have seen presented in the replication unit. In translation, the cell uses the genetic information contained in mrna to
Translation Study Guide This study guide is a written version of the material you have seen presented in the replication unit. In translation, the cell uses the genetic information contained in mrna to
Genetic Technology. Name: Class: Date: Multiple Choice Identify the choice that best completes the statement or answers the question.
 Name: Class: Date: Genetic Technology Multiple Choice Identify the choice that best completes the statement or answers the question. 1. An application of using DNA technology to help environmental scientists
Name: Class: Date: Genetic Technology Multiple Choice Identify the choice that best completes the statement or answers the question. 1. An application of using DNA technology to help environmental scientists
Biotechnology and Recombinant DNA (Chapter 9) Lecture Materials for Amy Warenda Czura, Ph.D. Suffolk County Community College
 Biotechnology and Recombinant DNA (Chapter 9) Lecture Materials for Amy Warenda Czura, Ph.D. Suffolk County Community College Primary Source for figures and content: Eastern Campus Tortora, G.J. Microbiology
Biotechnology and Recombinant DNA (Chapter 9) Lecture Materials for Amy Warenda Czura, Ph.D. Suffolk County Community College Primary Source for figures and content: Eastern Campus Tortora, G.J. Microbiology
Forensic DNA Testing Terminology
 Forensic DNA Testing Terminology ABI 310 Genetic Analyzer a capillary electrophoresis instrument used by forensic DNA laboratories to separate short tandem repeat (STR) loci on the basis of their size.
Forensic DNA Testing Terminology ABI 310 Genetic Analyzer a capillary electrophoresis instrument used by forensic DNA laboratories to separate short tandem repeat (STR) loci on the basis of their size.
A Concept of Digital Picture Envelope for Internet Communication
 A Concept of Digital Picture Envelope for Internet Communication Eiji Kawaguchi, Koichi Nozaki, Michiharu Niimi, Hideki Noda and Richard O. Eason Kyushu Institute of Technology 1-1 Sensui-cho, Tobata,
A Concept of Digital Picture Envelope for Internet Communication Eiji Kawaguchi, Koichi Nozaki, Michiharu Niimi, Hideki Noda and Richard O. Eason Kyushu Institute of Technology 1-1 Sensui-cho, Tobata,
Recombinant DNA and Biotechnology
 Recombinant DNA and Biotechnology Chapter 18 Lecture Objectives What Is Recombinant DNA? How Are New Genes Inserted into Cells? What Sources of DNA Are Used in Cloning? What Other Tools Are Used to Study
Recombinant DNA and Biotechnology Chapter 18 Lecture Objectives What Is Recombinant DNA? How Are New Genes Inserted into Cells? What Sources of DNA Are Used in Cloning? What Other Tools Are Used to Study
2. True or False? The sequence of nucleotides in the human genome is 90.9% identical from one person to the next. False (it s 99.
 1. True or False? A typical chromosome can contain several hundred to several thousand genes, arranged in linear order along the DNA molecule present in the chromosome. True 2. True or False? The sequence
1. True or False? A typical chromosome can contain several hundred to several thousand genes, arranged in linear order along the DNA molecule present in the chromosome. True 2. True or False? The sequence
somatic cell egg genotype gamete polar body phenotype homologous chromosome trait dominant autosome genetics recessive
 CHAPTER 6 MEIOSIS AND MENDEL Vocabulary Practice somatic cell egg genotype gamete polar body phenotype homologous chromosome trait dominant autosome genetics recessive CHAPTER 6 Meiosis and Mendel sex
CHAPTER 6 MEIOSIS AND MENDEL Vocabulary Practice somatic cell egg genotype gamete polar body phenotype homologous chromosome trait dominant autosome genetics recessive CHAPTER 6 Meiosis and Mendel sex
Just the Facts: A Basic Introduction to the Science Underlying NCBI Resources
 1 of 8 11/7/2004 11:00 AM National Center for Biotechnology Information About NCBI NCBI at a Glance A Science Primer Human Genome Resources Model Organisms Guide Outreach and Education Databases and Tools
1 of 8 11/7/2004 11:00 AM National Center for Biotechnology Information About NCBI NCBI at a Glance A Science Primer Human Genome Resources Model Organisms Guide Outreach and Education Databases and Tools
Genetics Test Biology I
 Genetics Test Biology I Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Avery s experiments showed that bacteria are transformed by a. RNA. c. proteins.
Genetics Test Biology I Multiple Choice Identify the choice that best completes the statement or answers the question. 1. Avery s experiments showed that bacteria are transformed by a. RNA. c. proteins.
1 Mutation and Genetic Change
 CHAPTER 14 1 Mutation and Genetic Change SECTION Genes in Action KEY IDEAS As you read this section, keep these questions in mind: What is the origin of genetic differences among organisms? What kinds
CHAPTER 14 1 Mutation and Genetic Change SECTION Genes in Action KEY IDEAS As you read this section, keep these questions in mind: What is the origin of genetic differences among organisms? What kinds
Genetics Module B, Anchor 3
 Genetics Module B, Anchor 3 Key Concepts: - An individual s characteristics are determines by factors that are passed from one parental generation to the next. - During gamete formation, the alleles for
Genetics Module B, Anchor 3 Key Concepts: - An individual s characteristics are determines by factors that are passed from one parental generation to the next. - During gamete formation, the alleles for
STEGANOGRAPHY: TEXT FILE HIDING IN IMAGE YAW CHOON KIT CA10022
 STEGANOGRAPHY: TEXT FILE HIDING IN IMAGE YAW CHOON KIT CA10022 FACULTY OF COMPUTER SYSTEM AND SOFTWARE ENGINEERING 2012/2013 1 ABSTRACT Steganography is the art or science in hiding. It is origin from
STEGANOGRAPHY: TEXT FILE HIDING IN IMAGE YAW CHOON KIT CA10022 FACULTY OF COMPUTER SYSTEM AND SOFTWARE ENGINEERING 2012/2013 1 ABSTRACT Steganography is the art or science in hiding. It is origin from
Proteins and Nucleic Acids
 Proteins and Nucleic Acids Chapter 5 Macromolecules: Proteins Proteins Most structurally & functionally diverse group of biomolecules. : o Involved in almost everything o Enzymes o Structure (keratin,
Proteins and Nucleic Acids Chapter 5 Macromolecules: Proteins Proteins Most structurally & functionally diverse group of biomolecules. : o Involved in almost everything o Enzymes o Structure (keratin,
HCS604.03 Exercise 1 Dr. Jones Spring 2005. Recombinant DNA (Molecular Cloning) exercise:
 HCS604.03 Exercise 1 Dr. Jones Spring 2005 Recombinant DNA (Molecular Cloning) exercise: The purpose of this exercise is to learn techniques used to create recombinant DNA or clone genes. You will clone
HCS604.03 Exercise 1 Dr. Jones Spring 2005 Recombinant DNA (Molecular Cloning) exercise: The purpose of this exercise is to learn techniques used to create recombinant DNA or clone genes. You will clone
Name: Date: Period: DNA Unit: DNA Webquest
 Name: Date: Period: DNA Unit: DNA Webquest Part 1 History, DNA Structure, DNA Replication DNA History http://www.dnaftb.org/dnaftb/1/concept/index.html Read the text and answer the following questions.
Name: Date: Period: DNA Unit: DNA Webquest Part 1 History, DNA Structure, DNA Replication DNA History http://www.dnaftb.org/dnaftb/1/concept/index.html Read the text and answer the following questions.
Biological Sciences Initiative. Human Genome
 Biological Sciences Initiative HHMI Human Genome Introduction In 2000, researchers from around the world published a draft sequence of the entire genome. 20 labs from 6 countries worked on the sequence.
Biological Sciences Initiative HHMI Human Genome Introduction In 2000, researchers from around the world published a draft sequence of the entire genome. 20 labs from 6 countries worked on the sequence.
Multi-factor Authentication in Banking Sector
 Multi-factor Authentication in Banking Sector Tushar Bhivgade, Mithilesh Bhusari, Ajay Kuthe, Bhavna Jiddewar,Prof. Pooja Dubey Department of Computer Science & Engineering, Rajiv Gandhi College of Engineering
Multi-factor Authentication in Banking Sector Tushar Bhivgade, Mithilesh Bhusari, Ajay Kuthe, Bhavna Jiddewar,Prof. Pooja Dubey Department of Computer Science & Engineering, Rajiv Gandhi College of Engineering
A Model-based Methodology for Developing Secure VoIP Systems
 A Model-based Methodology for Developing Secure VoIP Systems Juan C Pelaez, Ph. D. November 24, 200 VoIP overview What is VoIP? Why use VoIP? Strong effect on global communications VoIP will replace PSTN
A Model-based Methodology for Developing Secure VoIP Systems Juan C Pelaez, Ph. D. November 24, 200 VoIP overview What is VoIP? Why use VoIP? Strong effect on global communications VoIP will replace PSTN
Today you will extract DNA from some of your cells and learn more about DNA. Extracting DNA from Your Cells
 DNA Based on and adapted from the Genetic Science Learning Center s How to Extract DNA from Any Living Thing (http://learn.genetics.utah.edu/units/activities/extraction/) and BioRad s Genes in a bottle
DNA Based on and adapted from the Genetic Science Learning Center s How to Extract DNA from Any Living Thing (http://learn.genetics.utah.edu/units/activities/extraction/) and BioRad s Genes in a bottle
Genetics Lecture Notes 7.03 2005. Lectures 1 2
 Genetics Lecture Notes 7.03 2005 Lectures 1 2 Lecture 1 We will begin this course with the question: What is a gene? This question will take us four lectures to answer because there are actually several
Genetics Lecture Notes 7.03 2005 Lectures 1 2 Lecture 1 We will begin this course with the question: What is a gene? This question will take us four lectures to answer because there are actually several
How To Encrypt With Dna
 , pp.215-222 http://dx.doi.org/10.14257/ijbsbt.2014.6.5.22 Message Transmission Based on DNA Cryptography: Review Tausif Anwar 1, Dr. Sanchita Paul 2 and Shailendra Kumar Singh 3 1 Dept. of Computer Science
, pp.215-222 http://dx.doi.org/10.14257/ijbsbt.2014.6.5.22 Message Transmission Based on DNA Cryptography: Review Tausif Anwar 1, Dr. Sanchita Paul 2 and Shailendra Kumar Singh 3 1 Dept. of Computer Science
RETRIEVING SEQUENCE INFORMATION. Nucleotide sequence databases. Database search. Sequence alignment and comparison
 RETRIEVING SEQUENCE INFORMATION Nucleotide sequence databases Database search Sequence alignment and comparison Biological sequence databases Originally just a storage place for sequences. Currently the
RETRIEVING SEQUENCE INFORMATION Nucleotide sequence databases Database search Sequence alignment and comparison Biological sequence databases Originally just a storage place for sequences. Currently the
GA as a Data Optimization Tool for Predictive Analytics
 GA as a Data Optimization Tool for Predictive Analytics Chandra.J 1, Dr.Nachamai.M 2,Dr.Anitha.S.Pillai 3 1Assistant Professor, Department of computer Science, Christ University, Bangalore,India, [email protected]
GA as a Data Optimization Tool for Predictive Analytics Chandra.J 1, Dr.Nachamai.M 2,Dr.Anitha.S.Pillai 3 1Assistant Professor, Department of computer Science, Christ University, Bangalore,India, [email protected]
RNA & Protein Synthesis
 RNA & Protein Synthesis Genes send messages to cellular machinery RNA Plays a major role in process Process has three phases (Genetic) Transcription (Genetic) Translation Protein Synthesis RNA Synthesis
RNA & Protein Synthesis Genes send messages to cellular machinery RNA Plays a major role in process Process has three phases (Genetic) Transcription (Genetic) Translation Protein Synthesis RNA Synthesis
12.1 The Role of DNA in Heredity
 12.1 The Role of DNA in Heredity Only in the last 50 years have scientists understood the role of DNA in heredity. That understanding began with the discovery of DNA s structure. In 1952, Rosalind Franklin
12.1 The Role of DNA in Heredity Only in the last 50 years have scientists understood the role of DNA in heredity. That understanding began with the discovery of DNA s structure. In 1952, Rosalind Franklin
Becker Muscular Dystrophy
 Muscular Dystrophy A Case Study of Positional Cloning Described by Benjamin Duchenne (1868) X-linked recessive disease causing severe muscular degeneration. 100 % penetrance X d Y affected male Frequency
Muscular Dystrophy A Case Study of Positional Cloning Described by Benjamin Duchenne (1868) X-linked recessive disease causing severe muscular degeneration. 100 % penetrance X d Y affected male Frequency
PRESTWICK ACADEMY NATIONAL 5 BIOLOGY CELL BIOLOGY SUMMARY
 Name PRESTWICK ACADEMY NATIONAL 5 BIOLOGY CELL BIOLOGY SUMMARY Cell Structure Identify animal, plant, fungal and bacterial cell ultrastructure and know the structures functions. Plant cell Animal cell
Name PRESTWICK ACADEMY NATIONAL 5 BIOLOGY CELL BIOLOGY SUMMARY Cell Structure Identify animal, plant, fungal and bacterial cell ultrastructure and know the structures functions. Plant cell Animal cell
Turgut Ozal University. Computer Engineering Department. TR-06010 Ankara, Turkey
 Dr. YILDIRAY YALMAN Associate Professor CONTACT INFORMATION Turgut Ozal University Computer Engineering Department TR-06010 Ankara, Turkey Phone: +90 (0)312-5515437 E-mail: [email protected] RESEARCH
Dr. YILDIRAY YALMAN Associate Professor CONTACT INFORMATION Turgut Ozal University Computer Engineering Department TR-06010 Ankara, Turkey Phone: +90 (0)312-5515437 E-mail: [email protected] RESEARCH
Transfection-Transfer of non-viral genetic material into eukaryotic cells. Infection/ Transduction- Transfer of viral genetic material into cells.
 Transfection Key words: Transient transfection, Stable transfection, transfection methods, vector, plasmid, origin of replication, reporter gene/ protein, cloning site, promoter and enhancer, signal peptide,
Transfection Key words: Transient transfection, Stable transfection, transfection methods, vector, plasmid, origin of replication, reporter gene/ protein, cloning site, promoter and enhancer, signal peptide,
1. Molecular computation uses molecules to represent information and molecular processes to implement information processing.
 Chapter IV Molecular Computation These lecture notes are exclusively for the use of students in Prof. MacLennan s Unconventional Computation course. c 2013, B. J. MacLennan, EECS, University of Tennessee,
Chapter IV Molecular Computation These lecture notes are exclusively for the use of students in Prof. MacLennan s Unconventional Computation course. c 2013, B. J. MacLennan, EECS, University of Tennessee,
Crime Scenes and Genes
 Glossary Agarose Biotechnology Cell Chromosome DNA (deoxyribonucleic acid) Electrophoresis Gene Micro-pipette Mutation Nucleotide Nucleus PCR (Polymerase chain reaction) Primer STR (short tandem repeats)
Glossary Agarose Biotechnology Cell Chromosome DNA (deoxyribonucleic acid) Electrophoresis Gene Micro-pipette Mutation Nucleotide Nucleus PCR (Polymerase chain reaction) Primer STR (short tandem repeats)
Name Class Date. Figure 13 1. 2. Which nucleotide in Figure 13 1 indicates the nucleic acid above is RNA? a. uracil c. cytosine b. guanine d.
 13 Multiple Choice RNA and Protein Synthesis Chapter Test A Write the letter that best answers the question or completes the statement on the line provided. 1. Which of the following are found in both
13 Multiple Choice RNA and Protein Synthesis Chapter Test A Write the letter that best answers the question or completes the statement on the line provided. 1. Which of the following are found in both
Transcription and Translation of DNA
 Transcription and Translation of DNA Genotype our genetic constitution ( makeup) is determined (controlled) by the sequence of bases in its genes Phenotype determined by the proteins synthesised when genes
Transcription and Translation of DNA Genotype our genetic constitution ( makeup) is determined (controlled) by the sequence of bases in its genes Phenotype determined by the proteins synthesised when genes
Subject Area(s) Biology. Associated Unit Engineering Nature: DNA Visualization and Manipulation. Associated Lesson Imaging the DNA Structure
 Subject Area(s) Biology Associated Unit Engineering Nature: DNA Visualization and Manipulation Associated Lesson Imaging the DNA Structure Activity Title Inside the DNA Header Image 1 ADA Description:
Subject Area(s) Biology Associated Unit Engineering Nature: DNA Visualization and Manipulation Associated Lesson Imaging the DNA Structure Activity Title Inside the DNA Header Image 1 ADA Description:
PRACTICE TEST QUESTIONS
 PART A: MULTIPLE CHOICE QUESTIONS PRACTICE TEST QUESTIONS DNA & PROTEIN SYNTHESIS B 1. One of the functions of DNA is to A. secrete vacuoles. B. make copies of itself. C. join amino acids to each other.
PART A: MULTIPLE CHOICE QUESTIONS PRACTICE TEST QUESTIONS DNA & PROTEIN SYNTHESIS B 1. One of the functions of DNA is to A. secrete vacuoles. B. make copies of itself. C. join amino acids to each other.
Quantum and Non-deterministic computers facing NP-completeness
 Quantum and Non-deterministic computers facing NP-completeness Thibaut University of Vienna Dept. of Business Administration Austria Vienna January 29th, 2013 Some pictures come from Wikipedia Introduction
Quantum and Non-deterministic computers facing NP-completeness Thibaut University of Vienna Dept. of Business Administration Austria Vienna January 29th, 2013 Some pictures come from Wikipedia Introduction
DNA. Discovery of the DNA double helix
 DNA Replication DNA Discovery of the DNA double helix A. 1950 s B. Rosalind Franklin - X-ray photo of DNA. C. Watson and Crick - described the DNA molecule from Franklin s X-ray. What is DNA? Question:
DNA Replication DNA Discovery of the DNA double helix A. 1950 s B. Rosalind Franklin - X-ray photo of DNA. C. Watson and Crick - described the DNA molecule from Franklin s X-ray. What is DNA? Question:
The E. coli Insulin Factory
 The E. coli Insulin Factory BACKGROUND Bacteria have not only their normal DNA, they also have pieces of circular DNA called plasmids. Plasmids are a wonderfully ally for biologists who desire to get bacteria
The E. coli Insulin Factory BACKGROUND Bacteria have not only their normal DNA, they also have pieces of circular DNA called plasmids. Plasmids are a wonderfully ally for biologists who desire to get bacteria
Guidelines for Establishment of Contract Areas Computer Science Department
 Guidelines for Establishment of Contract Areas Computer Science Department Current 07/01/07 Statement: The Contract Area is designed to allow a student, in cooperation with a member of the Computer Science
Guidelines for Establishment of Contract Areas Computer Science Department Current 07/01/07 Statement: The Contract Area is designed to allow a student, in cooperation with a member of the Computer Science
A NOVEL STRATEGY TO PROVIDE SECURE CHANNEL OVER WIRELESS TO WIRE COMMUNICATION
 A NOVEL STRATEGY TO PROVIDE SECURE CHANNEL OVER WIRELESS TO WIRE COMMUNICATION Prof. Dr. Alaa Hussain Al- Hamami, Amman Arab University for Graduate Studies [email protected] Dr. Mohammad Alaa Al-
A NOVEL STRATEGY TO PROVIDE SECURE CHANNEL OVER WIRELESS TO WIRE COMMUNICATION Prof. Dr. Alaa Hussain Al- Hamami, Amman Arab University for Graduate Studies [email protected] Dr. Mohammad Alaa Al-
Mitochondrial DNA Analysis
 Mitochondrial DNA Analysis Lineage Markers Lineage markers are passed down from generation to generation without changing Except for rare mutation events They can help determine the lineage (family tree)
Mitochondrial DNA Analysis Lineage Markers Lineage markers are passed down from generation to generation without changing Except for rare mutation events They can help determine the lineage (family tree)
Difficult DNA Templates Sequencing. Primer Walking Service
 Difficult DNA Templates Sequencing Primer Walking Service Result 16/18s (ITS 5.8s) rrna Sequencing Phylogenetic tree 16s rrna Region ITS rrna Region ITS and 26s rrna Region Order and Result Cloning Service
Difficult DNA Templates Sequencing Primer Walking Service Result 16/18s (ITS 5.8s) rrna Sequencing Phylogenetic tree 16s rrna Region ITS rrna Region ITS and 26s rrna Region Order and Result Cloning Service
Compiled and/or written by Amy B. Vento and David R. Gillum
 Fact Sheet Describing Recombinant DNA and Elements Utilizing Recombinant DNA Such as Plasmids and Viral Vectors, and the Application of Recombinant DNA Techniques in Molecular Biology Compiled and/or written
Fact Sheet Describing Recombinant DNA and Elements Utilizing Recombinant DNA Such as Plasmids and Viral Vectors, and the Application of Recombinant DNA Techniques in Molecular Biology Compiled and/or written
Data Analysis for Ion Torrent Sequencing
 IFU022 v140202 Research Use Only Instructions For Use Part III Data Analysis for Ion Torrent Sequencing MANUFACTURER: Multiplicom N.V. Galileilaan 18 2845 Niel Belgium Revision date: August 21, 2014 Page
IFU022 v140202 Research Use Only Instructions For Use Part III Data Analysis for Ion Torrent Sequencing MANUFACTURER: Multiplicom N.V. Galileilaan 18 2845 Niel Belgium Revision date: August 21, 2014 Page
MUTATION, DNA REPAIR AND CANCER
 MUTATION, DNA REPAIR AND CANCER 1 Mutation A heritable change in the genetic material Essential to the continuity of life Source of variation for natural selection New mutations are more likely to be harmful
MUTATION, DNA REPAIR AND CANCER 1 Mutation A heritable change in the genetic material Essential to the continuity of life Source of variation for natural selection New mutations are more likely to be harmful
Chapter 11: Molecular Structure of DNA and RNA
 Chapter 11: Molecular Structure of DNA and RNA Student Learning Objectives Upon completion of this chapter you should be able to: 1. Understand the major experiments that led to the discovery of DNA as
Chapter 11: Molecular Structure of DNA and RNA Student Learning Objectives Upon completion of this chapter you should be able to: 1. Understand the major experiments that led to the discovery of DNA as
Algorithms in Computational Biology (236522) spring 2007 Lecture #1
 Algorithms in Computational Biology (236522) spring 2007 Lecture #1 Lecturer: Shlomo Moran, Taub 639, tel 4363 Office hours: Tuesday 11:00-12:00/by appointment TA: Ilan Gronau, Taub 700, tel 4894 Office
Algorithms in Computational Biology (236522) spring 2007 Lecture #1 Lecturer: Shlomo Moran, Taub 639, tel 4363 Office hours: Tuesday 11:00-12:00/by appointment TA: Ilan Gronau, Taub 700, tel 4894 Office
Provincial Exam Questions. 9. Give one role of each of the following nucleic acids in the production of an enzyme.
 Provincial Exam Questions Unit: Cell Biology: Protein Synthesis (B7 & B8) 2010 Jan 3. Describe the process of translation. (4 marks) 2009 Sample 8. What is the role of ribosomes in protein synthesis? A.
Provincial Exam Questions Unit: Cell Biology: Protein Synthesis (B7 & B8) 2010 Jan 3. Describe the process of translation. (4 marks) 2009 Sample 8. What is the role of ribosomes in protein synthesis? A.
To be able to describe polypeptide synthesis including transcription and splicing
 Thursday 8th March COPY LO: To be able to describe polypeptide synthesis including transcription and splicing Starter Explain the difference between transcription and translation BATS Describe and explain
Thursday 8th March COPY LO: To be able to describe polypeptide synthesis including transcription and splicing Starter Explain the difference between transcription and translation BATS Describe and explain
FINDING RELATION BETWEEN AGING AND
 FINDING RELATION BETWEEN AGING AND TELOMERE BY APRIORI AND DECISION TREE Jieun Sung 1, Youngshin Joo, and Taeseon Yoon 1 Department of National Science, Hankuk Academy of Foreign Studies, Yong-In, Republic
FINDING RELATION BETWEEN AGING AND TELOMERE BY APRIORI AND DECISION TREE Jieun Sung 1, Youngshin Joo, and Taeseon Yoon 1 Department of National Science, Hankuk Academy of Foreign Studies, Yong-In, Republic
The Techniques of Molecular Biology: Forensic DNA Fingerprinting
 Revised Fall 2011 The Techniques of Molecular Biology: Forensic DNA Fingerprinting The techniques of molecular biology are used to manipulate the structure and function of molecules such as DNA and proteins
Revised Fall 2011 The Techniques of Molecular Biology: Forensic DNA Fingerprinting The techniques of molecular biology are used to manipulate the structure and function of molecules such as DNA and proteins
Recombinant DNA Unit Exam
 Recombinant DNA Unit Exam Question 1 Restriction enzymes are extensively used in molecular biology. Below are the recognition sites of two of these enzymes, BamHI and BclI. a) BamHI, cleaves after the
Recombinant DNA Unit Exam Question 1 Restriction enzymes are extensively used in molecular biology. Below are the recognition sites of two of these enzymes, BamHI and BclI. a) BamHI, cleaves after the
The sequence of bases on the mrna is a code that determines the sequence of amino acids in the polypeptide being synthesized:
 Module 3F Protein Synthesis So far in this unit, we have examined: How genes are transmitted from one generation to the next Where genes are located What genes are made of How genes are replicated How
Module 3F Protein Synthesis So far in this unit, we have examined: How genes are transmitted from one generation to the next Where genes are located What genes are made of How genes are replicated How
CURRICULUM GUIDE. When this Forensics course has been completed successfully, students should be able to:
 CURRICULUM GUIDE NAME OF COURSE: FORENSICS COURSE NUMBER: SCI 40 WRITTEN / REVISED: SEPTEMBER, 2011 LEVEL OF COURSE: REPLACMENT NUMBER OF CREDITS: SIX (6) PREREQUISITES: BIOLOGY GRADE LEVELS OFFERED TO:
CURRICULUM GUIDE NAME OF COURSE: FORENSICS COURSE NUMBER: SCI 40 WRITTEN / REVISED: SEPTEMBER, 2011 LEVEL OF COURSE: REPLACMENT NUMBER OF CREDITS: SIX (6) PREREQUISITES: BIOLOGY GRADE LEVELS OFFERED TO:
How is genome sequencing done?
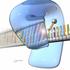 How is genome sequencing done? Using 454 Sequencing on the Genome Sequencer FLX System, DNA from a genome is converted into sequence data through four primary steps: Step One DNA sample preparation; Step
How is genome sequencing done? Using 454 Sequencing on the Genome Sequencer FLX System, DNA from a genome is converted into sequence data through four primary steps: Step One DNA sample preparation; Step
DNA and Forensic Science
 DNA and Forensic Science Micah A. Luftig * Stephen Richey ** I. INTRODUCTION This paper represents a discussion of the fundamental principles of DNA technology as it applies to forensic testing. A brief
DNA and Forensic Science Micah A. Luftig * Stephen Richey ** I. INTRODUCTION This paper represents a discussion of the fundamental principles of DNA technology as it applies to forensic testing. A brief
Lab # 12: DNA and RNA
 115 116 Concepts to be explored: Structure of DNA Nucleotides Amino Acids Proteins Genetic Code Mutation RNA Transcription to RNA Translation to a Protein Figure 12. 1: DNA double helix Introduction Long
115 116 Concepts to be explored: Structure of DNA Nucleotides Amino Acids Proteins Genetic Code Mutation RNA Transcription to RNA Translation to a Protein Figure 12. 1: DNA double helix Introduction Long
Image Authentication Scheme using Digital Signature and Digital Watermarking
 www..org 59 Image Authentication Scheme using Digital Signature and Digital Watermarking Seyed Mohammad Mousavi Industrial Management Institute, Tehran, Iran Abstract Usual digital signature schemes for
www..org 59 Image Authentication Scheme using Digital Signature and Digital Watermarking Seyed Mohammad Mousavi Industrial Management Institute, Tehran, Iran Abstract Usual digital signature schemes for
A greedy algorithm for the DNA sequencing by hybridization with positive and negative errors and information about repetitions
 BULLETIN OF THE POLISH ACADEMY OF SCIENCES TECHNICAL SCIENCES, Vol. 59, No. 1, 2011 DOI: 10.2478/v10175-011-0015-0 Varia A greedy algorithm for the DNA sequencing by hybridization with positive and negative
BULLETIN OF THE POLISH ACADEMY OF SCIENCES TECHNICAL SCIENCES, Vol. 59, No. 1, 2011 DOI: 10.2478/v10175-011-0015-0 Varia A greedy algorithm for the DNA sequencing by hybridization with positive and negative
Bio 102 Practice Problems Chromosomes and DNA Replication
 Bio 102 Practice Problems Chromosomes and DNA Replication Multiple choice: Unless otherwise directed, circle the one best answer: 1. Which one of the following enzymes is NT a key player in the process
Bio 102 Practice Problems Chromosomes and DNA Replication Multiple choice: Unless otherwise directed, circle the one best answer: 1. Which one of the following enzymes is NT a key player in the process
Scottish Qualifications Authority
 National Unit specification: general information Unit code: FH2G 12 Superclass: RH Publication date: March 2011 Source: Scottish Qualifications Authority Version: 01 Summary This Unit is a mandatory Unit
National Unit specification: general information Unit code: FH2G 12 Superclass: RH Publication date: March 2011 Source: Scottish Qualifications Authority Version: 01 Summary This Unit is a mandatory Unit
agucacaaacgcu agugcuaguuua uaugcagucuua
 RNA Secondary Structure Prediction: The Co-transcriptional effect on RNA folding agucacaaacgcu agugcuaguuua uaugcagucuua By Conrad Godfrey Abstract RNA secondary structure prediction is an area of bioinformatics
RNA Secondary Structure Prediction: The Co-transcriptional effect on RNA folding agucacaaacgcu agugcuaguuua uaugcagucuua By Conrad Godfrey Abstract RNA secondary structure prediction is an area of bioinformatics
Course Curriculum for Master Degree in Medical Laboratory Sciences/Clinical Microbiology, Immunology and Serology
 Course Curriculum for Master Degree in Medical Laboratory Sciences/Clinical Microbiology, Immunology and Serology The Master Degree in Medical Laboratory Sciences / Clinical Microbiology, Immunology or
Course Curriculum for Master Degree in Medical Laboratory Sciences/Clinical Microbiology, Immunology and Serology The Master Degree in Medical Laboratory Sciences / Clinical Microbiology, Immunology or
Multimedia Document Authentication using On-line Signatures as Watermarks
 Multimedia Document Authentication using On-line Signatures as Watermarks Anoop M Namboodiri and Anil K Jain Department of Computer Science and Engineering Michigan State University East Lansing, MI 48824
Multimedia Document Authentication using On-line Signatures as Watermarks Anoop M Namboodiri and Anil K Jain Department of Computer Science and Engineering Michigan State University East Lansing, MI 48824
MAKING AN EVOLUTIONARY TREE
 Student manual MAKING AN EVOLUTIONARY TREE THEORY The relationship between different species can be derived from different information sources. The connection between species may turn out by similarities
Student manual MAKING AN EVOLUTIONARY TREE THEORY The relationship between different species can be derived from different information sources. The connection between species may turn out by similarities
Secret Communication through Web Pages Using Special Space Codes in HTML Files
 International Journal of Applied Science and Engineering 2008. 6, 2: 141-149 Secret Communication through Web Pages Using Special Space Codes in HTML Files I-Shi Lee a, c and Wen-Hsiang Tsai a, b, * a
International Journal of Applied Science and Engineering 2008. 6, 2: 141-149 Secret Communication through Web Pages Using Special Space Codes in HTML Files I-Shi Lee a, c and Wen-Hsiang Tsai a, b, * a
A Robust and Lossless Information Embedding in Image Based on DCT and Scrambling Algorithms
 A Robust and Lossless Information Embedding in Image Based on DCT and Scrambling Algorithms Dr. Mohammad V. Malakooti Faculty and Head of Department of Computer Engineering, Islamic Azad University, UAE
A Robust and Lossless Information Embedding in Image Based on DCT and Scrambling Algorithms Dr. Mohammad V. Malakooti Faculty and Head of Department of Computer Engineering, Islamic Azad University, UAE
