Auditcon 2 Series Software REFERENCE MANUAL
|
|
|
- Britton Horton
- 10 years ago
- Views:
Transcription
1 Auditcon 2 Series Software REFERENCE MANUAL
2 Trademarks The following items are trademarks or registered trademarks of Kaba Mas in the United States and/or other countries. Auditcon PowerStar Technology Smart Key Windows, Windows XP, Windows Vista, and Windows 7 are registered trademarks of Microsoft Corporation. Intel and Pentium are registered trademarks of Intel Corporation. Adobe, Acrobat, and Reader are registered trademarks of Adobe Systems Incorporated. Notice: The information in this manual is subject to change without notice and does not represent a commitment on the part of the Kaba Mas. Kaba Mas shall not be liable for technical or editorial errors or omissions contained herein; nor for incidental or consequential damages resulting from the furnishing, performance or use of this material Kaba Mas All rights reserved Document Number Rev. E - 08/10
3 Table of Contents CHAPTER 1 INTRODUCING THE AUDITCON 2 SERIES SOFTWARE...1 Kaba Mas Welcome...1 The Auditcon 2 Series Software Program Package...1 System Overview...1 System Components...2 PC Based Computer System...2 High Security Locks...2 Smart Keys...3 Key Types...3 Lock Modes Personnel Classifications...4 Master User...4 Access User...4 Supervisor...4 Subordinate User...4 Time Delay Override User...4 User ID...5 Combination...5 Activity Chart...5 System Processes...6 Program Lock...6 Add/Delete Users to/from Lock...6 Upload TIme Windows to Lock...7 Retrieve & Report on Audit Download from Lock...7 Retrieve & Report on User Table Download from Lock...7 CHAPTER 2 AUDITCON 2 SERIES SOFTWARE...9 Software Conventions...9 Start the Auditcon 2 Series Software Program...9 Main Menu...9 Menu Bar Toolbar...11 Status Bar File Menu...12 Print Setup...12 Exit...12
4 Locks Menu...13 Program Lock Add/Delete Users Upload Time Windows...25 SA Keys Menu...29 Initialize Audit Download Key Initialize User Table Download Key Delete SA Key Reports Menu...33 Report on Audit Download Key Report on User Table Download Key Settings Menu...38 Change Adapter and Port Settings System Settings Help Menu...44 Help Topics About Auditcon 2 Series Software GLOSSARY...47
5 CHAPTER 1 INTRODUCING THE AUDITCON 2 SERIES SOFTWARE SYSTEM Kaba Mas Welcome Kaba Mas, part of the world-wide Kaba group, is the world s leading manufacturer and supplier of high security, electronic safe locks. Our complete line of self powered, battery, and mechanical locks meets virtually every safe lock requirement. Kaba Mas is dedicated to satisfying end-user needs for security, safety, and convenience. We welcome you to the world of Kaba Mas security and the Auditcon 2 Series Software system. The Auditcon 2 Series Software Program Package The Auditcon 2 Series Software implementation package includes: The Auditcon 2 Series Software Install CD, Version USB Adapter Serial Key Reader 1 Supervisor Audit Key (Red SA Key) Auditcon 2 Series Software Getting Started Guide Auditcon 2 Series Software Reference Manual (Included on Install CD in electronic format) Note: If you purchased the Software Only package, you will only receive the Install CD (with Reference Manual included) and the Getting Started Guide. If you are missing any of the above items, contact Kaba Mas Customer Service at 1(800) Note: If you will be working with Model 552 locks and wish to update the lock date and time using the software, the teal colored B key (P/N ) is required. This item is ordered separately. Document Number Rev. E - 08/10 Introducing the Auditcon 2 Series Software 1
6 System Overview The Auditcon 2 Series Software allows PC based programming of lock data instead of manual entry at the lock. Additionally, it allows the retrieval and reporting of data stored in the lock. Upload Data to Lock As an alternative to defining setup data and user data manually at the lock, certain types of data can be defined at the PC using the Auditcon 2 Series Software and the information can then be uploaded (transferred) to the lock via a Smart Key. Download Data from Lock There are two types of data that can be downloaded (retrieved) from the Auditcon 2 Series locks using the Auditcon 2 Series Software. Lock audit data and user table data can be retrieved from the lock using a Smart Key and can then be reported on at the PC. It is important that you understand how the entire system operates, even though many of the operations will be carried out by other personnel. Before you start using the program, be sure to read the next few pages. They tell you what this package includes, the equipment you need to use the software, and identify the components of the system and the people who will be working with them. The Auditcon 2 Series Software system consists of three basic components: 1) PC Based Computer Program The PC Based Computer System is actually comprised of hardware and software components, including a Smart Key Reader, consisting of two Smart Key ports. The software component is the PC based Auditcon 2 Series Software. 2) High Security Locks The Auditcon locks are highly secured, advanced design locks. The original design was first developed for use on United States Government safes containing classified material. There are currently 4 different models of the Auditcon lock family that will operate in conjunction with the Auditcon 2 Series Software. They are as follows: Auditcon 2 Series Model 252 Auditcon 2 Series Model 552 Auditcon Series Model 500 Auditcon 2100 Some functions of the software will be limited depending on which type of lock you are working with at the time. 2 Introducing the Auditcon 2 Series Software Document Number Rev. E - 08/10
7 3) Smart Keys Smart Keys are used by everyone who works with the Cencon System 2000, whether it be at the PC using the software program or at the lock. A Smart Key is actually a Dallas Semiconductor electronic device imbedded in a plastic or metal fob. The keys are designed to be carried on a key ring like a traditional key. The keys are placed in the key reader attached to the PC and are initialized with unique data. These sophisticated electronic keys can hold large amounts of both temporary and permanent information. Key Types There are two types of Smart Keys that are used with the Auditcon 2 Series Software. They are designated and used as follows: Supervisor Audit (SA) Key - The red Supervisor Audit key is initialized at the PC key reader with the information needed to take it into the field and program a lock. This key can also be used to retrieve audit records or user tables from a lock. Date & Time (B) Key - The teal Date & Time key is only required if you are setting the date and time in a Model 552 lock. It is initialized at the PC key reader with the information needed to take it into the field and program a lock. The memory in the key is used to transfer data from the computer to the lock and from the lock to the computer. The data read from the key by the lock is used to define lock setup values, users, and time windows. Data can also stored in the key by the lock, such as the data from an audit download. The key can then be read by the computer to provide a record of lock activity. Lock Modes A lock is shipped from the factory with default lock setup values and a pre-set PIN for unlocking the lock. This is referred to as Factory Mode. The lock has two modes of operation: Independent Mode and Supervisory/Subordinate Mode. Within each operation mode, two access modes are available: Single User access and Dual User access. In Single User access, only one combination is required to open the lock. In Dual User access, two combinations must be correctly and consecutively entered to open the lock. Independent Mode - To operate in Independent Mode, the Master User must first add Access Users. One (Single User access) or two (Dual User access) combinations are required to open the lock. Supervisory/Subordinate Mode (Super/Sub Mode) - To operate in Super/Sub Mode, the Master User must first add a Supervisor. Subordinate Users must then be added by and assigned to a Supervisor. A Supervisor must enable lock access for Subordinate User(s). Document Number Rev. E - 08/10 Introducing the Auditcon 2 Series Software 3
8 In Single User access, an enabled Subordinate User combination is required to open the lock. In Dual User access, two enabled Subordinate User combinations are required to open the lock. Once a Supervisor combination and the Supervisor ID are re-entered to disable lock access for the Subordinate User(s) assigned to that Supervisor ID, the Subordinate User combinations for that will no longer open the lock. To remove a lock from an operational mode, one can shelve the lock which places it in Shelved Mode. Most lock values are returned to the factory default. Personnel Classifications There are five different classifications of lock personnel: Master User - The Master User performs the initial lock setup activities and can also shelve the lock. There is a maximum of one Master User per lock. The Master User combination will not open the lock. Access User - In Independent mode, a user added by the Master User. An Access User can open the lock. Supervisor - In Super/Sub mode, a user added by the Master User who has the ability to add/delete Subordinate Users. The maximum number of Supervisors per lock varies according to lock model. A Supervisor cannot open the lock. Subordinate User - In Super/Sub mode, a user who is added by and assigned to a Supervisor. Subordinates can open the lock when enabled by a Supervisor. Time Delay Override User - When Time Delay is set in a lock, designated Users (Access or Subordinate) become Time Delay Override Users. User ID A User ID is a two-digit number that represents a user. In all models, User ID 00 is reserved for the Master User. For a Model 252 lock, the User IDs available for assignment are 01 through 20. For a Model 552, User IDs 01 through 99 are available for assignment. All operations performed by users require the entry of the User s ID as the first two digits of the combination. User IDs are assigned by the Master User or by a Supervisor. In Super/Sub mode certain User IDs are reserved for Supervisors. For a Model 252 in Super/Sub mode, User IDs 01 through 03 are reserved for a Supervisor. For a Model 552 User IDs 01 through 05 are reserved for Supervisors. 4 Introducing the Auditcon 2 Series Software Document Number Rev. E - 08/10
9 Certain User IDs are reserved for the ability to perform a Time Delay Override when Time Delay has been set in the lock. For a Model 252 lock, User ID 20 can perform this action. For a Model 552, Users have this ability. Combination (User ID + PIN) A combination is eight digits long and consists of a User ID + a User PIN. A User Personal Identifier Number (PIN) is six digits. A User PIN can be defined to any combination of numbers. It can also be changed at a later time. The following chart shows the activities that can be performed by each type of user. Activity Keypad Command Master User Access User Supervisor Subordinate User Time Delay Override User Set Master User PIN (p. 5) #1 Set Operating Mode (p. 6) #2 Set Time Delay (p. 6) #5 Toggle Sound On/Off (p. 7) #9 Change Reporting Capabilities (p. 8) ##1 Add Supervisors or Access Users (p. 9) #3 Add Subordinate Users (p. 9) #3 Delete Supervisors or Access Users (p.9) #4 Delete Subordinate Users (p.9) #4 Enable/Disable Lock Access For N/A Subordinates (p.10) Change PIN (p.10) #1 Unlock - Independent Mode (p.10) N/A N/A Unlock - Super/Sub Mode (p.10) N/A Initiate Silent Duress Alarm (p.12) Time Delay Override (p. Shelve Lock (p.12) ##2 Set Lock Date* (p. 13) #6 Set Lock Time* (p. 13) #7 Toggle Daylight Savings Time* (p.14) ##5 User 20 Start Timed Lockout* (p. 14) ##4 User 20 Set Time Windows* (p.14) ##3 Start Time Window Lockout* (p. 16) ##7 User 20 Upload Data to Lock** (p.17) #8 Download Data from Lock** (p.18) #8 * Available on Model 552 only ** Software Based Operations Document Number Rev. E - 08/10 Introducing the Auditcon 2 Series Software 5
10 System Processes Program Lock There are several system processes that involve integrating activity at the PC software level with activity at the lock. It is important that these processes be completed in their entirety. These processes are defined as follows in the form of flow charts and accompanying text. PREPARE SA OR B KEY AT PC TAKE KEY TO LOCK PROGRAM LOCK WITH SA KEY OR B KEY As an alternative to defining setup data and user data manually at the lock, certain types of data can be defined at the PC using the Auditcon 2 Series Software and the information can then be uploaded (transferred) to the lock via a Smart Key. You can prepare an SA Key (or a B Key for Model 552) at the PC that can program the lcok with setup data, users and time windows (if applicable.) The key is then taken to the lock. The lock is powered and the upload data command is entered. The key is held to the key reader on the lock while the key's data is written into the lock's memory. Add/Delete Users to/from Lock PREPARE SA KEY AT PC TAKE KEY TO LOCK ADD/DELETE USERS WITH KEY As an alternative to defining user data manually at the lock, the data can be defined at the PC using the Auditcon 2 Series Software and the information can then be uploaded (transferred) to the lock via a Smart Key. You can prepare an SA Key at the PC that can program the lock with user data. The key is then taken to the lock. The lock is powered and the upload data command is entered. The key is held to the key reader on the lock while the key's data is written into the lock's memory. 6 Introducing the Auditcon 2 Series Software Document Number Rev. E - 08/10
11 Upload Time Windows to Lock PREPARE SA KEY AT PC TAKE KEY TO LOCK UPLOAD TIME WINDOWS WITH KEY As an alternative to defining time window data manually at the lock, the data can be defined at the PC using the Auditcon 2 Series Software and the information can then be uploaded (transferred) to the lock via a Smart Key. You can prepare an SA Key at the PC that can program the lock with the time window data. The key is then taken to the lock. The lock is powered and the upload data command is entered. The key is held to the key reader on the lock while the key's data is written into the lock's memory. Retrieve & Report on Audit Download from Lock INITIALIZE SA KEY AT PC TAKE SA KEY TO LOCK RETRIEVE AUDIT DATA WITH SA KEY RETURN SA KEY TO PC TO READ AUDIT INFORMATION The audit records recorded in a lock may be written to an SA key which is then taken to the PC to be printed. The procedure is to use the Auditcon 2 Series Software to initialize an SA key for the retrieval of the audit data. The key is then taken to the lock. The lock is powered up and the retrieve audit command is entered. The key is held to the key reader on the lock while the data is written into its memory. The key with the data now written in it is taken to the PC where the data is read and a report is either printed or displayed. Retrieve & Report on User Table Download from Lock INITIALIZE SA KEY AT PC TAKE SA KEY TO LOCK RETRIEVE USER TABLE WITH SA KEY RETURN SA KEY TO PC TO READ USER INFORMATION The user table defined in a lock may be written to an SA key which is then taken to the PC to be printed. The procedure is to use the Auditcon 2 Series Software to initialize an SA key for the retrieval of the user table. The key is then taken to the lock. The lock is powered up and the retrieve user table command is entered. The key is held to the key reader on the lock while the data is written into its memory. The key with the data now written in it is taken to the PC where the data is read and a report is either printed or displayed. Document Number Rev. E - 08/10 Introducing the Auditcon 2 Series Software 7
12 8 Introducing the Auditcon 2 Series Software Document Number Rev. E - 08/10
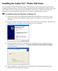
13 CHAPTER 2 AUDITCON 2 SERIES SOFTWARE Software Conventions The Auditcon 2 Series Software program is operated through several windows. It conforms to Windows conventions so Windows users should have no trouble using it. Enough detail is included in this manual to enable a non-experienced user to follow the required procedures. Note: The screens shown in the Auditcon 2 Series Software manuals were captured on a Windows XP system. If your PC is running under a different operating system, your screens may look slightly different. Start the Auditcon 2 Series Program To start the Auditcon 2 Series Software program, you can select the Auditcon 2 Series Software icon from the desktop. If you prefer, you can complete the following steps to start the Auditcon 2 Series Software Program from the Programs Menu: 1. Select the Start icon from the Windows task bar. 2. Select the Programs menu item. 3. Select the Auditcon 2 Series Software menu item. 4. Select the Auditcon 2 Series Software icon. Main Menu The Auditcon 2 Series Software Main Menu will be displayed. Document Number Rev. E - 08/10 Auditcon 2 Series Software 9
14 Menu Bar Toolbar Status Bar Menu Bar The Menu Bar displays the available menu options.some of these options are also available from the toolbar. The menus available from the Auditcon 2 Series Software menu bar are listed below and the corresponding toolbar icon (if applicable) is located to the left of each menu description: File - Exit the Cencon for Windows Software. Locks - Program Lock, Add/Delete Users or Upload Time Windows SA Keys - Initialize or Delete SA Keys Reports - View or Print Reports Settings - Define or Maintain System Settings & Data Help - 1) Display the Auditcon 2 Series Software basic program information, version number and copyright or 2) access the online system help information. 10 Auditcon 2 Series Software Document Number Rev. E - 08/10
15 You can select an option on the menu bar by 1) positioning the mouse pointer on the option name and clicking the left mouse button one time 2) using the shortcut keys underlined on the option s label. For example, for the option label Locks, you can select the option by pressing the Alt and L keys at the same time (Alt + L). Toolbar The Toolbar is located directly below the menu bar and displays the icons for the menu bar options. You can select an icon on the toolbar by positioning the mouse pointer on the icon and clicking the left mouse button one time. The available toolbar icons are pictured and described in the previous Menu Bar section. Status Bar The Status Bar is located at the bottom of the Auditcon 2 Series Software window. This bar displays system information (e.g., a brief description of the Toolbar button on which the mouse pointer is positioned). Document Number Rev. E - 08/10 Auditcon 2 Series Software 11
16 File Menu Perform Print Setup or Exit Auditcon 2 Series Software The first option on the Menu bar is File. The File menu options allow you to define your Print Setup or exit the software. From the Main menu: 1. Select File. Print Setup This menu item is used to display the printer settings dialog, to allow the user to change the various printer settings for Windows. Exit The Exit option is used to end the Auditcon 2 Series program. 12 Auditcon 2 Series Software Document Number Rev. E - 08/10
17 Locks Menu Program Lock, Add/Delete Users or Upload Time Windows The second menu option on the Main Menu is Locks. The Locks Menu options allow you to program the lock, add/delete users, or define time windows for the lock. The Locks menu options can also be accessed by selecting the Locks icon from the Tool Bar. From the Main menu: 1. Select the Locks Menu or the tool bar icon. Document Number Rev. E - 08/10 Auditcon 2 Series Software 13
18 Program Lock The first option on the Locks menu is Program Lock. This menu item is used to initiate the program locks wizard and is only applicable for Model 252 or 552 locks. It should be selected to define the original lock setup data, users, and time windows for a lock. If you choose the Program the Lock menu option from the Auditcon 2 Series PC software, you can define the following data in a lock: Lock ID Access Mode Lock Mode Sound ON/OFF Reporting Capabilities Delay Time and Delayed Opening Window Users Note: The Program Lock operation requires a red SA key that has been properly prepared at the PC using the Auditcon 2 Series Software. If you are programming a Model 552 lock, you can also set the Date & Time in the lock and define Time Windows. Note: If you choose to set the time in the lock using the software, the operation requires a teal colored B key (P/N ), prepared at the PC using the Auditcon 2 Series Software, rather than a red SA key. 1. Select Program Lock. The Select lock model screen is displayed. 14 Auditcon 2 Series Software Document Number Rev. E - 08/10
19 2. Select the Model number for the lock you wish to program. 3. Click on Next. Document Number Rev. E - 08/10 Auditcon 2 Series Software 15
20 The Program Lock Options screen for the selected Model type is displayed. The program lock options for the selected model will be enabled. Any that are not available will be grayed. 4. If you would like to assign a lock ID to the lock, enter a two-digit number (01-99) for the lock ID. Otherwise, you may leave the default of 00 for no lock ID assignment. This ID will identify a lock in an audit report. 5. Select the lock mode. The default is Independent Mode. 6. Select the access type. The default is Single User Access. 7. Select whether you would like to have Sound turned On or Off in the lock. Note: Some beeps will always sound regardless of whether the sound is toggled on or off. They are as follows: beeps to indicate lock is powered, beeps that sound during the open window after a time delay, beep that accompanies the Clear ( ) key, beeps that sound between combination entry for Dual access. 16 Auditcon 2 Series Software Document Number Rev. E - 08/10
21 8. Select the reporting capabilities for the lock. The default is All, but you can also choose to restrict the reporting capabilities to the Master User and other designated User IDs (00-03 for the Model 252 and for the Model 552.) 9. If you would like to set a time delay in the lock, enter a delay time and a delayed opening window value (in minutes). You can specify a time delay of minutes. The time delay begins as soon as a single valid combination is entered. For the delayed opening window, you can specify a period of 1-20 minutes. After the specified time delay has expired, the delayed opening window will begin. During this window, you must re-enter the original combination that initiated the Time Delay. If you do not choose to set the Time Delay, it will default to a value of 0 in the lock. Note: When Time Delay is set in a lock, designated Users (Access or Subordinate) become Time Delay Override Users. Users who have the ability to override Time Delay cannot open the lock. User ID 20 is designated for this purpose in a Model 252 lock while Users are designated in a Model If you are programming a Model 552 lock and would like to set the date and time in the lock, select the Set time in lock button. Other wise select the Do not set time button. Note: The date and time in the lock must be set if you are going to implement time windows or timed lockouts in the lock. The teal colored B key is required to program the lock if this option is selected. 11. Click on Next to continue. Document Number Rev. E - 08/10 Auditcon 2 Series Software 17
22 You will be prompted with the Program Lock - Add/Delete Users screen. Note: In Super/Sub mode certain User IDs are reserved for Supervisors. For a Model 252 in Super/Sub mode, User IDs 01 through 03 are reserved for a Supervisor. For a Model 552 User IDs 01 through 05 are reserved for Supervisors. Certain User IDs are reserved for the ability to perform a Time Delay Override when Time Delay has been set in the lock. For a Model 252 lock, User ID 20 can perform this action. For a Model 552, Users have this ability. 12. Select the User ID(s) for whom you want an add or delete operation performed at the lock. Indication an Add or Delete by moving them to the appropriate list box. You have several options available for selecting groups of users as follows: To select an individual User ID, highlight the user in the appropriate list box and click the or the button or simply double click on the group. To select multiple sequential User IDs, click the first user you want to select, press and hold down the Shift key, click the last group you want to select, and click the or the button. Both users and all users in between are selected. 18 Auditcon 2 Series Software Document Number Rev. E - 08/10
23 To select multiple non-sequential User IDs, press and hold down the Ctrl key, click each user you want to select, and click the or the button. Note: If you are programming the lock to operate in Independent Mode, you have the option to add all of the valid Users (other than the Master User) for a lock model at this time. If, however, you are programming the lock for Supervisor/Subordinate Mode, you will only have the option to add the valid Supervisor User IDs for the lock model. Once the Supervisor IDs have been defined in the lock and the Supervisor PINs have been manually changed at the lock, then the Add/Delete Users option can be selected from the software to add Subordinate Users for individual Supervisors. 13. If you are programming a Model 252 lock, ensure that a Smart Key has been placed in the key reader and click on FInish and go to Step 16. Otherwise, if you are programming a Model 552 lock, click on Next to continue. If you chose a Model 552 lock, you will also be prompted with the Program Lock - Time Window Upload screen. Document Number Rev. E - 08/10 Auditcon 2 Series Software 19
24 Note: If you have set the Time Window Dialog Setting to Use time window settings last entered, the data displayed in the screen will default to the last data entered. See the System Settings option on the Settings Menu for details. 14. To change the window settings for a given day, click on the Change Window Settings box for that day. If the box is not checked, the lock window settings will not be affected for that day and will remain set to whatever values are currently set at the lock. Note: The time window access values will default to no window restriction at the lock unless defined otherwise via manual programming at the lock or via data upload to the lock from the software. Once the Change Window Settings box has been selected for a specific day, the other input fields for that day will become enabled for data entry. 14a.If you want No Window Restriction (24 hour access) for the selected day, select the appropriate box. All other input fields will become unavailable for that day. 14b.If you want no lock access allowed for the selected day, select the No Access box. All other input fields will become unavailable for that day. 20 Auditcon 2 Series Software Document Number Rev. E - 08/10
25 14c.If you want to limit access to a certain time period of the selected day, define an access time window by entering a Start Time and End Time under the Window 1 section of the screen. Specify all times in HH:MM format. Enter times as they would be set at the lock. If the time in the locks is set to GMT, use the same GMT time here. If set to local time at the lock, use the standard 24-hour format (00:00 to 23:59). Caution: If a GMT offset is set, it is NOT used to adjust the values entered in Start Time and End Time. The time values entered should reflect lock times. There can be some drifting in the lock clocks in the Model 500 and 552 locks, up to 15 minutes per year. Because of this possible variance, there should be minor allowances made in both the starting time and the ending time when setting time windows. Note: When data is entered for Window 1, the same Start and End Time will automatically be filled in for Window 2. If you want to define a second access time window for the selected day, update the Start Time and End Time under the Window 2 section of the screen to the values for the second window. 15. Tab to the Start Time in Window 2. If you want to define a second access time window for the selected day, update the Start Time and End Time under the Window 2 section of the screen to the values for the second window. Note: If you do not choose to define a second window, the second window will default to the same time period as the first window. Repeat steps 14 and 15 for each day that you would like to define lock access. 16. Once you are finished with the Time Windows screen, ensure that a Smart Key has been placed in the key reader and click on FInish. 17. The key should now be taken to the lock to program the lock data. Note: Previous to uploading the Program Lock data to a lock, the Master User PIN must be set in the lock. The default PIN assigned to a new User or Supervisor ID is A user must change this default PIN before any lock operations can be performed. Document Number Rev. E - 08/10 Auditcon 2 Series Software 21
26 Add/Delete Users This option is used to add and/or delete users to or from a lock using an SA Key. The option should be selected only to add or delete users to a lock that has already been programmed. Note: If the lock is operating in Supervisor/Subordinate Mode, Supervisors cannot be added or deleted using this option. Time Delay Overide Users can be added using this option even if the Time Delay value has already been programmed at the lock. 1. Select Add/Delete Users. The Add/Delete Users screen is displayed. 22 Auditcon 2 Series Software Document Number Rev. E - 08/10
27 Note: In Super/Sub mode certain User IDs are reserved for Supervisors. For a Model 252 in Super/Sub mode, User IDs 01 through 03 are reserved for a Supervisor. For a Model 552 User IDs 01 through 05 are reserved for Supervisors. Certain User IDs are reserved for the ability to perform a Time Delay Override when Time Delay has been set in the lock. For a Model 252 lock, User ID 20 can perform this action. For a Model 552, Users have this ability. 2. Select the model of the lock to which you want to add/delete users. 3. Select the lock mode that was previously defined in the lock. 4. If the lock is operating in Supervisor/Subordinate mode, you must also enter the Supervisor ID of the Supervisor to whom the Subordinate Users will be assigned or are currently assigned (if deleting.) Note: If adding or deleting Subordinate Users, the Supervisor s combination must be used to perform the download of the data to the lock. 5. Select the User ID(s) for whom you want an add or delete operation performed at the lock. Indication an Add or Delete by moving them to the appropriate list box. You have several options available for selecting groups of users as follows: To select an individual User ID, highlight the user in the appropriate list box and click the or the button or simply double click on the group. To select multiple sequential User IDs, click the first user you want to select, press and hold down the Shift key, click the last group you want to select, and click the or the button. Both users and all users in between are selected. To select multiple non-sequential User IDs, press and hold down the Ctrl key, click each user you want to select, and click the or the button. Document Number Rev. E - 08/10 Auditcon 2 Series Software 23
28 6. If you have existing users in the lock and do not want to change any of the existing user data, select the button for Existing users in lock will not be modified. Otherwise, the button for Existing users in the lock will be modified. Note: If the lock is in Supervisor/Subordinate mode, users that are assigned to another Supervisor will NOT be modified even in Existing users will be modified has been selected. 7. When all settings are complete and all desired users have been moved to the appropriate lists, ensure that a Smart Key has been placed in the key reader and click on the OK button. A window will be displayed indicdating that the SA key was written successfully. 24 Auditcon 2 Series Software Document Number Rev. E - 08/10
29 8. Click on OK to return to the Main Menu. 9. The key should now be taken to the lock to add/delete users to/from the lock. Note: Previous to uploading the user data to a lock, the Master User PIN must be set in the lock. The default PIN assigned to a new User or Supervisor ID is A user must change this default PIN before any lock operations can be performed. Upload Time Windows By default, the lock is set to have No Window Restriction for all seven days. This means that users can open the lock at any time during any day. This option allows time window access to be programmed at the PC and then uploaded to the lock. From the Locks menu: 1. Select Upload Time Windows. The Time Window Upload screen is displayed. Document Number Rev. E - 08/10 Auditcon 2 Series Software 25
30 Note: If you have set the Time Window Dialog Setting to Use time window settings last entered, the data displayed in the screen will default to the last data entered. See the System Settings option on the Settings Menu for details. 2. To change the window settings for a given day, click on the Change Window Settings box for that day. If the box is not checked, the lock window settings will not be affected for that day and will remain set to whatever values are currently set at the lock. Note: The time window access values will default to no window restriction at the lock unless defined otherwise via manual programming at the lock or via data upload to the lock from the software. Once the Change Window Settings box has been selected for a specific day, the other input fields for that day will become enabled for data entry. 26 Auditcon 2 Series Software Document Number Rev. E - 08/10
31 2a.If you want No Window Restriction (24 hour access) for the selected day, select the appropriate box. All other input fields will become unavailable for that day. 2b.If you want no lock access allowed for the selected day, select the No Access box. All other input fields will become unavailable for that day. 2c.If you want to limit access to a certain time period of the selected day, define an access time window by entering a Start Time and End Time under the Window 1 section of the screen. Specify all times in HH:MM format. Enter times as they would be set at the lock. If the time in the locks is set to GMT, use the same GMT time here. If set to local time at the lock, use the standard 24-hour format (00:00 to 23:59). Caution: If a GMT offset is set, it is NOT used to adjust the values entered in Start Time and End Time. The time values entered should reflect lock times. There can be some drifting in the lock clocks in the Model 500 and 552 locks, up to 15 minutes per year. Because of this possible variance, there should be minor allowances made in both the starting time and the ending time when setting time windows. Document Number Rev. E - 08/10 Auditcon 2 Series Software 27
32 Note: When data is entered for Window 1, the same Start and End Time will automatically be filled in for Window Tab to the Start Time in Window 2. If you want to define a second access time window for the selected day, update the Start Time and End Time under the Window 2 section of the screen to the values for the second window. Note: If you do not choose to define a second window, the second window will default to the same time period as the first window. Repeat steps 2 and 3 for each day that you would like to define lock access. 4. Once you are finished with the Time Windows screen, ensure that a Smart Key has been placed in the key reader and click on OK. A window will be displayed indicdating that the SA key was written successfully. 5. Click on OK to return to the Main Menu. 6. The key should now be taken to the lock to upload time windows to the lock. Note: Previous to uploading the Time Window information to a lock, the lock must have been programmed, including the setting of the lock date and time. 28 Auditcon 2 Series Software Document Number Rev. E - 08/10
33 SA Keys Initialize or Delete SA Keys The third menu option on the Main Menu is SA Keys. The SA key is used to transfer data between the Auditcon 2 Series Software program and the locks. The SA key is programmed by the Auditcon 2 Series program for a specific function and can only be used for that function until reprogrammed. The SA Keys menu options can also be accessed by selecting the SA Keys icon from the Tool Bar. From the Main menu: 1. Select the SA Keys Menu or the tool bar icon. Document Number Rev. E - 08/10 Auditcon 2 Series Software 29
34 Initialize Audit Download Key The first option on the SA Keys menu is Initialize Audit Download Key. This function is used to initialize a Supervisor Audit key so that it can be taken to a lock to obtain an audit download from a lock s memory. The key is then returned to this system so that the data can be retrieved from the key. From the SA Keys menu: 1. Select Initialize Audit Download Key. The SA Key reminder message is displayed. 2. Ensure that there is an SA key in the key reader and click on the OK button to proceed. The SA key will be initialized for the lock audit download and the following confirmation message will be displayed. 3. Click on the OK button to close the window. 4. Take the SA key to the lock to retrieve the audit data. Return the SA key to report the audit data. Initialize User Table Download Key This option is used to initialize an SA key so that it can be used to download the user table from a lock. From the SA Keys menu: 1. Select Initialize User Table Download Key. The SA Key reminder message is displayed. 30 Auditcon 2 Series Software Document Number Rev. E - 08/10
35 2. Ensure that there is an SA key in the key reader and click on the OK button to proceed. The SA key will be initialized for the user table download and the following confirmation message will be displayed. 3. Click on the OK button to close the window. Delete SA Key The next option on the SA Keys menu is Delete SA Key. This option is used to delete the contents of a Supervisor Audit key after data has been retrieved from a lock. Once data has been retrieved from a lock and the data has been viewed, printed or saved through a Report option, you may want to delete the data from the key for security purposes. From the SA Keys menu: 1. Select Delete SA Key. The SA Key reminder message is displayed. 2. Ensure that there is an SA key in the key reader and click on the OK button to proceed. The contents of the SA key will be deleted and the following confirmation message will be displayed. Document Number Rev. E - 08/10 Auditcon 2 Series Software 31
36 3. Click on the OK button to close the window. 32 Auditcon 2 Series Software Document Number Rev. E - 08/10
37 Reports View or Print Reports The fourth menu option on the Main Menu is Reports. This menu option allows the operator to generate reports from data retrieved from a lock. The Reports menu options can also be accessed by selecting the Reports icon from the Tool Bar. From the Main menu: 1. Select the Reports Menu or the tool bar icon. Document Number Rev. E - 08/10 Auditcon 2 Series Software 33
38 Report on Audit Download Key This option allows you to display a report on a Supervisor Audit Key. This will only report on a key that was used for an Audit Download from a lock and cannot be used for a user table report. 1. Select Report on Audit Download Key. The SA Key reminder message will be displayed. 2. Make sure that the SA key with audit data is in the key reader. 3. Click on the OK button to close the window and display the audit data. 34 Auditcon 2 Series Software Document Number Rev. E - 08/10
39 Note: Audits from a Model 500, 552, or a System 2100 lock will display date and time stamps. Only an audit from a System 2100 lock will display the close date and time. The System 2100 lock is also the only lock model that has the capability for Holidays in addition to Time Windows. The Lock Status field is represented in Hexadecimal format, but can be decoded as follows. The first two characters of the lock status refer to the Product Code: 5A-9F designates Model 252 AA-FF designates Model 552 The second two characters refer to the hardware level, and is always a 00 or 01, where 01 distinguishes a Model 552. The last two digits refer to the software level and ranges from 00 to FF. The Lock Mode field when represented in binary coded decimal can be decoded for troubleshooting purposes as follows, where bit positions 0 through 7 have the following meanings: if bit 0 is set - indicates daylight savings time is in effect if bit 1 is set - indicates super/subordinate mode is in effect if bit 2 is set - indicates audit buffer has wrapped if bit 3 is set - indicates factory mode is active if bit 4 is set - indicates single user mode is active if bit 5 is set - indicates dual user mode is active if bit 6 is set - indicates the sound (beeper) is on if bit 7 is set - indicates that audit downloades are restructed to allowed id s The User/Key ID field on each audit record indicates the User ID of the person who performed tha action. Note: If the audit data being reviewed is from a Model 500 or 552, lock Time Windows will also be displayed. You may print the report by clicking on the Print button. The following confirmation message will be displayed after the report is printed. You also have the option of saving the report data to a file on your disk drive. Document Number Rev. E - 08/10 Auditcon 2 Series Software 35
40 4. To save the report data in a file, click on the File button. The Open window will be displayed. Enter the name of the file where you want the data filed and click on the OK button to save. The report data will be saved and the following confirmation screen will be displayed. 5. Click on the OK button to close the window and return to the main window. Report on User Table Download Key This option is used to generate a report from an SA key that has been used to download the user table from a lock. 1. Select Report on User Table Download Key. The SA Key reminder message will be displayed. 2. Make sure that the SA key with audit data is in the key reader. 3. Click on the OK button to close the window and display the user table data. 36 Auditcon 2 Series Software Document Number Rev. E - 08/10
41 The ID 2 field on each user table record indicates the User ID of the person who added the User. You may print the report by clicking on the Print button. The following confirmation message will be displayed after the report is printed. You also have the option of saving the report data to a file on your disk drive. 4. To save the report data in a file, click on the File button. The Open window will be displayed. Enter the name of the file where you want the data filed and click on the OK button to save. The report data will be saved and the following confirmation screen will be displayed. 5. Click on the Close button to close the report window. Document Number Rev. E - 08/10 Auditcon 2 Series Software 37
42 Settings Define or Maintain System Settings & Data The last option on the Main Menu is the Settings Menu. These menu options allow you to perform system maintenance functions. System Settings should be addressed at System startup but can also be maintained from this menu. The Settings menu options can also be accessed by selecting the Settings icon from the Tool Bar. From the Main menu: 1. Select the Settings Menu or the tool bar icon. 38 Auditcon 2 Series Software Document Number Rev. E - 08/10
43 Change Adapter and Port Settings This option is used to change the adapter and port settings in case the adaptert type is changed or the adapter has to be moved to a different port. From the Settings menu: 1. Select Change Adapter and Port Settings. The Select Adapter and Port screen is displayed. This window prompts you to specify what type of key reader you have and where it is installed. 2. Select the Adapter Type that you have installed with your system. The default value for the Adapter Type is the DS9490R USB Adapter. If the Adapter Type is different from the default, change it at this time. 3. To ensure that your selection(s) are correct, we recommend that you Test your selection(s) to verify communications. Insert an SA Key into either port of the reader and click on the Test button. Document Number Rev. E - 08/10 Auditcon 2 Series Software 39
44 If the Test is successful, a message window is displayed indicating the key was found and communication was successful. If the key reader was not installed or the proper adapter type/port is not selected, the following error message will be displayed and you will not be able to proceed until the problem is corrected. If the SA key is not in the reader, the following error message will be displayed and you will not be able to proceed until the problem is corrected. 4. Click on OK. If the test was not successful, attempt to correct the problem and test again. If the test was successful, all selection boxes will be grayed out. 40 Auditcon 2 Series Software Document Number Rev. E - 08/10
45 5. If you have succesfully finished Testing and wish to accept the adapter and port settings, click on the OK button to proceed. System Settings This option is used to change your GMT offset setting or to disable GMT offset and use local time in the locks. From the menu: 1. From the Settings menu, select the System Settings option. The System Settings screen will be displayed. Document Number Rev. E - 08/10 Auditcon 2 Series Software 41
46 2. If you wish to use the time window settings last entered when defining time windows for a lock under the Time Window Upload option of the Locks menu, click on the check box to select. When not selected, the time windows dialog is displayed with all fields blank. 3. If you wish to have the European Date format (DD/MM/CCYY) used for reporting options, click on the check box to select this option. The default is to display dates as MM/DD/CCYY. 4. If the locks in your system are set to local time, the GMT Offset should be disabled. Audit Reports will show the actual lock time for each audit record. If the locks in your system are set to Greenwich Mean Time, the GMT Offset should be enabled. When the GMT Offset is enabled, the software adjusts the time of each record in the Audit Download report to the local time using the GMT offset values specified in this screen. Use the following chart to determine the appropriate GMT Offset to use for your time zone. You should ensure that this value, along with the internal date and time on your PC, is correct at installation time. Select West if you are located to the west of Greenwich, England, between Greenwich and the international date line. Select East if you are located to the east. For example: The United States is West, Germany is East. 42 Auditcon 2 Series Software Document Number Rev. E - 08/10
47 United States Time Zone Offsets Time Zone Standard Time Daylight Savings Offset Time Offset Eastern 5 hours 4 hours Central 6 hours 5 hours Mountain 7 hours 6 hours Pacific 8 hours 7 hours Alaska 10 hours 9 hours Hawaii 10 hours 10 hours 5. After all fields have been completed, click on the OK button to process the system settings. Note: When the system detects a change in daylight savings time, a Daylight Savings Time window will be displayed. This screen allows you to change the PC clock and/or the GMT offset or to select to not change either option. Document Number Rev. E - 08/10 Auditcon 2 Series Software 43
48 Help System Help From this menu, you can: 1) Access the online system help information, or 2) Display the Auditcon 2 Series Software version number and copyright information. From the Main Menu: 1. Select Help. Help Topics The Auditcon 2 Series Software has extensive Help screens available which cover all portions of the operation of the Auditcon 2 Series Software. The Help Topics option displays the main Help window. From this window, you may obtain help on the Auditcon 2 Series Softwrae software functions by clicking on the name of the function. The detailed help screen for the selected function is displayed. If the Help data is longer than one screen, use the scroll bars to move through the data. The taskbar commands at the top of the screen may be used to move through the help screen for the different functions. Select the Windows File/Exit command to close the Help functions. 44 Auditcon 2 Series Software Document Number Rev. E - 08/10
49 About Auditcon 2 Series Software The About Auditcon 2 Series Software option displays data about the Auditcon 2 Series Software program. From the Main menu: 1. Select About Auditcon 2 Series Software. The About Auditcon 2 Series window is displayed. Document Number Rev. E - 08/10 Auditcon 2 Series Software 45
50 2. Click on the OK button to close the window. 46 Auditcon 2 Series Software Document Number Rev. E - 08/10
51 GLOSSARY CCW - Counterclockwise rotation to the left. This is used in referring to the direction that the lock dial should be turned at certain times when performing lock operations. CW - Clockwise rotation to the right. This is used in referring to the direction that the lock dial should be turned at certain times when performing lock operations. B Key - The teal Date & Time Key that is used to transfer data to the lock. This type of key is required if setting the date and time in a Model 552 lock. Dual User Access Mode - A setting in the lock activation process that causes the lock to require two users to open the lock. Fob - A plastic or metal molding into which an electronic chip can be imbedded to form a Smart Key. GMT - The acronym for Greenwich Mean Time. This is the zero line for all time zones. Each time zone is offset from the zero line by a specific number of hours. The number of hours to be used for offset correlates to the number of time zones that you are away from the zero line. With the induction of daylight savings time, this offset decreases by one hour. ibutton - The trademarked Dallas Semiconductor name for the electronic Smart Keys used with the Auditcon 2 Series system. PowerStar TM technology - The technology that allows the System 2000 lock to operate using internally generated power. No batteries or external power are required. SA Key - A red Smart Key that is initialized at the PC with information needed to transfer data to and from a lock. Single User Access - A setting in the lock activation process that causes the lock to require only one user to open the lock. Smart Key - This is a Dallas Semiconductor electronic chip imbedded in a fob. Smart Key Reader - This is the key reader that is attached to the PC as a peripheral item. It is used to write and read data to and from, respectively, the Smart Keys. Two Person Integrity ( TPI ) - When two keys are required to perform certain functions. This provides a higher level of security and is called Two Person Integrity (TPI). Two person integrity applies if a lock is set up for Dual Mode. Document Number Rev. E - 08/10 Glossary 47
52 48 Glossary Document Number Rev. E - 08/10
53
54 Document Number Rev. E - 08/10 Kaba Mas LLC 749 W. Short Street, Lexington, KY USA Phone: (859) FAX: (859) Customer Service: (800)
Centran Version 4 Getting Started Guide KABA MAS. Table Of Contents
 Page 1 Centran Version 4 Getting Started Guide KABA MAS Kaba Mas Welcome Kaba Mas, part of the world-wide Kaba group, is the world's leading manufacturer and supplier of high security, electronic safe
Page 1 Centran Version 4 Getting Started Guide KABA MAS Kaba Mas Welcome Kaba Mas, part of the world-wide Kaba group, is the world's leading manufacturer and supplier of high security, electronic safe
S&G Audit Lock. Audit Trail Software Manual
 S&G Audit Lock Audit Trail Software Manual The Sargent & Greenleaf Audit Lock is designed to provide a high level of security. One of the ways they accomplish this is by offering detailed audit trails.
S&G Audit Lock Audit Trail Software Manual The Sargent & Greenleaf Audit Lock is designed to provide a high level of security. One of the ways they accomplish this is by offering detailed audit trails.
ACCESS CONTROL SYSTEMS USER MANUAL
 Ritenergy Pro (Version 3.XX) ACCESS CONTROL SYSTEMS USER MANUAL 1 User Manual Ritenergy International, LLC TABLE OF CONTENTS RITENERGY PRO PROGRAMMING GUIDE 3 System Requirement 3 System Components 3 Basic
Ritenergy Pro (Version 3.XX) ACCESS CONTROL SYSTEMS USER MANUAL 1 User Manual Ritenergy International, LLC TABLE OF CONTENTS RITENERGY PRO PROGRAMMING GUIDE 3 System Requirement 3 System Components 3 Basic
The following items are trademarks or registered trademarks of Kaba Mas in the United States and/or other countries. GITCON
 The Gitcon Access Management Software Installation Guide is a publication of Kaba Mas LLC (hereinafter Kaba Mas). No part of this book may be reproduced or transmitted in any form or by any means, electronic
The Gitcon Access Management Software Installation Guide is a publication of Kaba Mas LLC (hereinafter Kaba Mas). No part of this book may be reproduced or transmitted in any form or by any means, electronic
Table of Contents. 1. Overview... 3. 1.1 Materials Required. 3 1.2 System Requirements. 3 1.3 User Mode 3. 2. Installation Instructions..
 Table of Contents 1. Overview..... 3 1.1 Materials Required. 3 1.2 System Requirements. 3 1.3 User Mode 3 2. Installation Instructions.. 4 2.1 Installing the On Call Diabetes Management Software. 4 2.2
Table of Contents 1. Overview..... 3 1.1 Materials Required. 3 1.2 System Requirements. 3 1.3 User Mode 3 2. Installation Instructions.. 4 2.1 Installing the On Call Diabetes Management Software. 4 2.2
Installation and Operating Instructions Audit Trail Software for 6126/6127/6128/6129 Series
 Installation and Operating Instructions Audit Trail Software for 6126/6127/6128/6129 Series General Notes These instructions are for installing S&G Audit Software (and all associated software components)
Installation and Operating Instructions Audit Trail Software for 6126/6127/6128/6129 Series General Notes These instructions are for installing S&G Audit Software (and all associated software components)
Installing the Gerber P2C Plotter USB Driver
 Installing the Gerber P2C Plotter USB Driver 1 You can install a Gerber P2C plotter using a USB connection and communicate with it using compatible design software. The following procedures describe installing
Installing the Gerber P2C Plotter USB Driver 1 You can install a Gerber P2C plotter using a USB connection and communicate with it using compatible design software. The following procedures describe installing
SOFTWARE INSTALLATION INSTRUCTIONS
 AUDITGARD LGA Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS Implementation Package The AuditGard Software implementation package includes: 707013 AuditGard Software Install CD 42145 Programming/Audit
AUDITGARD LGA Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS Implementation Package The AuditGard Software implementation package includes: 707013 AuditGard Software Install CD 42145 Programming/Audit
File Management Utility. T u t o r i a l
 File Management Utility T u t o r i a l Contents System Requirements... 2 Preparing Files for Transfer to GlobalMark... 2 Application Launch... 2 Printer Setup... 2 Communication Status... 4 Communication
File Management Utility T u t o r i a l Contents System Requirements... 2 Preparing Files for Transfer to GlobalMark... 2 Application Launch... 2 Printer Setup... 2 Communication Status... 4 Communication
PC Program User s Guide (01.01.05) 1. Connecting the PC. 2. Installation and Start-up. 3. Programming
 Work Off-Line Set up a new database or modify a previously saved database (without being connected to the telephone system). This helps minimize on-site programming time. Work On-Line (connected directly
Work Off-Line Set up a new database or modify a previously saved database (without being connected to the telephone system). This helps minimize on-site programming time. Work On-Line (connected directly
COMBOGARDPRO. 39E Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS
 COMBOGARDPRO 39E Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS IMPLEMENTATION PACKAGE The ComboGard Pro Software implementation package includes: 707012 ComboGard Pro Software Install
COMBOGARDPRO 39E Electronic Combination Lock SOFTWARE INSTALLATION INSTRUCTIONS IMPLEMENTATION PACKAGE The ComboGard Pro Software implementation package includes: 707012 ComboGard Pro Software Install
HP Point of Sale (POS) Peripherals Configuration Guide 2D Imaging / Linear / Presentation Scanner
 HP Point of Sale (POS) Peripherals Configuration Guide 2D Imaging / Linear / Presentation Scanner Document Version 3.42 December 2011 1 Copyright 2007-2011 Hewlett-Packard Development Company, L.P. The
HP Point of Sale (POS) Peripherals Configuration Guide 2D Imaging / Linear / Presentation Scanner Document Version 3.42 December 2011 1 Copyright 2007-2011 Hewlett-Packard Development Company, L.P. The
VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide
 VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide N109548 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes
VERITAS Backup Exec 9.1 for Windows Servers Quick Installation Guide N109548 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes
Cencon Gen2. Cencon Generation II Lock Cencon/CenTran 4 Software
 Cencon Gen2 x Cencon Generation II Lock Cencon/CenTran 4 Software Introduction Dear Valued Customer: Kaba Mas is committed to continuously improving existing products and driving new product development.
Cencon Gen2 x Cencon Generation II Lock Cencon/CenTran 4 Software Introduction Dear Valued Customer: Kaba Mas is committed to continuously improving existing products and driving new product development.
VERITAS Backup Exec TM 10.0 for Windows Servers
 VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
VERITAS Backup Exec TM 10.0 for Windows Servers Quick Installation Guide N134418 July 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software
DCA. Document Control & Archiving USER S GUIDE
 DCA Document Control & Archiving USER S GUIDE Decision Management International, Inc. 1111 Third Street West Suite 250 Bradenton, FL 34205 Phone 800-530-0803 FAX 941-744-0314 www.dmius.com Copyright 2002,
DCA Document Control & Archiving USER S GUIDE Decision Management International, Inc. 1111 Third Street West Suite 250 Bradenton, FL 34205 Phone 800-530-0803 FAX 941-744-0314 www.dmius.com Copyright 2002,
Profit Developers, Inc. (PDI) 2015 SAXTAX Software Installation Guide
 2015 SAXTAX Software Installation Guide 1. Installation: Installing from a Link: Please click on the link provided in the setup email received. Some email accounts will not allow access to executable links
2015 SAXTAX Software Installation Guide 1. Installation: Installing from a Link: Please click on the link provided in the setup email received. Some email accounts will not allow access to executable links
HP LaserJet MFP Analog Fax Accessory 300 Send Fax Driver Guide
 HP LaserJet MFP Analog Fax Accessory 300 Send Fax Driver Guide Copyright and License 2008 Copyright Hewlett-Packard Development Company, L.P. Reproduction, adaptation, or translation without prior written
HP LaserJet MFP Analog Fax Accessory 300 Send Fax Driver Guide Copyright and License 2008 Copyright Hewlett-Packard Development Company, L.P. Reproduction, adaptation, or translation without prior written
Page 1 S5.5 Monitoring Software Manual Rev 1.2 for Software Ver 1.0
 Trantec S5.5 Monitoring Software Manual Initial Setup Minimum PC Requirements 1.6 GHz CPU, 256 MB Memory, 1 available USB port, Windows XP Recommended PC >2.0 GHz CPU, 512 MB (XP) 1 GB (Vista) memory,
Trantec S5.5 Monitoring Software Manual Initial Setup Minimum PC Requirements 1.6 GHz CPU, 256 MB Memory, 1 available USB port, Windows XP Recommended PC >2.0 GHz CPU, 512 MB (XP) 1 GB (Vista) memory,
Personal Call Manager User Guide. BCM Business Communications Manager
 Personal Call Manager User Guide BCM Business Communications Manager Document Status: Standard Document Version: 04.01 Document Number: NN40010-104 Date: August 2008 Copyright Nortel Networks 2005 2008
Personal Call Manager User Guide BCM Business Communications Manager Document Status: Standard Document Version: 04.01 Document Number: NN40010-104 Date: August 2008 Copyright Nortel Networks 2005 2008
Data Analysis Software
 TRAKPRO Data Analysis Software User s Manual November 1996 P/N 1980200 Rev. D TSI Incorporated TRAKPRO Data Analysis Software User s Manual November 1996 P/N 1980200 Rev. D SHIP TO: TSI Incorporated 500
TRAKPRO Data Analysis Software User s Manual November 1996 P/N 1980200 Rev. D TSI Incorporated TRAKPRO Data Analysis Software User s Manual November 1996 P/N 1980200 Rev. D SHIP TO: TSI Incorporated 500
TimeValue Software Due Date Tracking and Task Management Software
 User s Guide TM TimeValue Software Due Date Tracking and Task Management Software File In Time Software User s Guide Copyright TimeValue Software, Inc. (a California Corporation) 1992-2010. All rights
User s Guide TM TimeValue Software Due Date Tracking and Task Management Software File In Time Software User s Guide Copyright TimeValue Software, Inc. (a California Corporation) 1992-2010. All rights
NCD ThinPATH Load Balancing Startup Guide
 NCD ThinPATH Load Balancing Startup Guide Copyright Copyright 1999 by Network Computing Devices, Inc. (NCD).The information contained in this document is subject to change without notice. Network Computing
NCD ThinPATH Load Balancing Startup Guide Copyright Copyright 1999 by Network Computing Devices, Inc. (NCD).The information contained in this document is subject to change without notice. Network Computing
Exeba -ATS. User Guide. Escan Technologies Corporation
 Escan Technologies Corporation Exeba -ATS User Guide Escan Technologies Corp. 12140 Severn Way Riverside, CA 92503 Phone (909) 270-0043 Fax (909) 270-0920 1 ESCAN TECHNOLOGIES CORPORATION Exeba -ATS User
Escan Technologies Corporation Exeba -ATS User Guide Escan Technologies Corp. 12140 Severn Way Riverside, CA 92503 Phone (909) 270-0043 Fax (909) 270-0920 1 ESCAN TECHNOLOGIES CORPORATION Exeba -ATS User
Keep it Simple Timing
 Keep it Simple Timing Support... 1 Introduction... 2 Turn On and Go... 3 Start Clock for Orienteering... 3 Pre Start Clock for Orienteering... 3 Real Time / Finish Clock... 3 Timer Clock... 4 Configuring
Keep it Simple Timing Support... 1 Introduction... 2 Turn On and Go... 3 Start Clock for Orienteering... 3 Pre Start Clock for Orienteering... 3 Real Time / Finish Clock... 3 Timer Clock... 4 Configuring
Creating a Database in Access
 Creating a Database in Access Microsoft Access is a database application. A database is collection of records and files organized for a particular purpose. For example, you could use a database to store
Creating a Database in Access Microsoft Access is a database application. A database is collection of records and files organized for a particular purpose. For example, you could use a database to store
User Manual. Thermo Scientific Orion
 User Manual Thermo Scientific Orion Orion Star Com Software Program 68X637901 Revision A April 2013 Contents Chapter 1... 4 Introduction... 4 Star Com Functions... 5 Chapter 2... 6 Software Installation
User Manual Thermo Scientific Orion Orion Star Com Software Program 68X637901 Revision A April 2013 Contents Chapter 1... 4 Introduction... 4 Star Com Functions... 5 Chapter 2... 6 Software Installation
2002 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or
 041902 2002 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or mechanical, including photocopying, recording, storage
041902 2002 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or mechanical, including photocopying, recording, storage
Downloading Images and Movies from a Digital Camera to OLYMPUS Master 2
 Overview Downloading Images and Movies from a Digital Camera to OLYMPUS Master 2 This article describes how to download image and movie files from an Olympus digital camera 1 to the OLYMPUS Master 2 application.
Overview Downloading Images and Movies from a Digital Camera to OLYMPUS Master 2 This article describes how to download image and movie files from an Olympus digital camera 1 to the OLYMPUS Master 2 application.
QUICK START GUIDE. SG2 Client - Programming Software SG2 Series Programmable Logic Relay
 QUICK START GUIDE SG2 Client - Programming Software SG2 Series Programmable Logic Relay SG2 Client Programming Software T he SG2 Client software is the program editor for the SG2 Series Programmable Logic
QUICK START GUIDE SG2 Client - Programming Software SG2 Series Programmable Logic Relay SG2 Client Programming Software T he SG2 Client software is the program editor for the SG2 Series Programmable Logic
Automation License Manager
 s Contents Product Overview 1 Installation 2 Working with the Automation License Manager 3 Glossary Manual Index 12/2008 A5E02389428-01 Legal information Warning notice system This manual contains notices
s Contents Product Overview 1 Installation 2 Working with the Automation License Manager 3 Glossary Manual Index 12/2008 A5E02389428-01 Legal information Warning notice system This manual contains notices
Installing Remote Desktop Connection
 SETTING UP YOUR REMOTE DESKTOP This section will assist you in setting you Remote Desktop Connection. This will allow you to create an icon for easy access to your virtual desktop. DISCLAIMER: All images
SETTING UP YOUR REMOTE DESKTOP This section will assist you in setting you Remote Desktop Connection. This will allow you to create an icon for easy access to your virtual desktop. DISCLAIMER: All images
AXIS Camera Station Quick Installation Guide
 AXIS Camera Station Quick Installation Guide Copyright Axis Communications AB April 2005 Rev. 3.5 Part Number 23997 1 Table of Contents Regulatory Information.................................. 3 AXIS Camera
AXIS Camera Station Quick Installation Guide Copyright Axis Communications AB April 2005 Rev. 3.5 Part Number 23997 1 Table of Contents Regulatory Information.................................. 3 AXIS Camera
NETWORK PRINT MONITOR User Guide
 NETWORK PRINT MONITOR User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
NETWORK PRINT MONITOR User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable
NDA-30141 ISSUE 1 STOCK # 200893. CallCenterWorX-Enterprise IMX MAT Quick Reference Guide MAY, 2000. NEC America, Inc.
 NDA-30141 ISSUE 1 STOCK # 200893 CallCenterWorX-Enterprise IMX MAT Quick Reference Guide MAY, 2000 NEC America, Inc. LIABILITY DISCLAIMER NEC America, Inc. reserves the right to change the specifications,
NDA-30141 ISSUE 1 STOCK # 200893 CallCenterWorX-Enterprise IMX MAT Quick Reference Guide MAY, 2000 NEC America, Inc. LIABILITY DISCLAIMER NEC America, Inc. reserves the right to change the specifications,
TR-3 Channel Editor. Software Manual
 TR-3 Channel Editor Software Manual Trilithic Company Profile Trilithic is a privately held manufacturer founded in 1986 as an engineering and assembly company that built and designed customer-directed
TR-3 Channel Editor Software Manual Trilithic Company Profile Trilithic is a privately held manufacturer founded in 1986 as an engineering and assembly company that built and designed customer-directed
Printer Driver Installation Guide
 Fujitsu Dot Matrix Printer DL Series Printer Driver Installation Guide - Windows 7 - Windows Server 2008 R2 Rev.01: April 12, 2010 IMPORTANT NOTE TO USERS For Windows 7 / Windows Server 2008 R2, install
Fujitsu Dot Matrix Printer DL Series Printer Driver Installation Guide - Windows 7 - Windows Server 2008 R2 Rev.01: April 12, 2010 IMPORTANT NOTE TO USERS For Windows 7 / Windows Server 2008 R2, install
Model 288B Charge Plate Graphing Software Operators Guide
 Monroe Electronics, Inc. Model 288B Charge Plate Graphing Software Operators Guide P/N 0340175 288BGraph (80207) Software V2.01 100 Housel Ave PO Box 535 Lyndonville NY 14098 1-800-821-6001 585-765-2254
Monroe Electronics, Inc. Model 288B Charge Plate Graphing Software Operators Guide P/N 0340175 288BGraph (80207) Software V2.01 100 Housel Ave PO Box 535 Lyndonville NY 14098 1-800-821-6001 585-765-2254
HDD Password Tool. User s Manual. English
 HDD Password Tool User s Manual English 1 Table of Contents Chapter 1: Introduction... 3 Trademarks... 3 Chapter 2: Required Operating System... 5 - HDD Password Tool for Windows... 5 - HDD Password Tool
HDD Password Tool User s Manual English 1 Table of Contents Chapter 1: Introduction... 3 Trademarks... 3 Chapter 2: Required Operating System... 5 - HDD Password Tool for Windows... 5 - HDD Password Tool
Diamond II v2.3 Service Pack 4 Installation Manual
 Diamond II v2.3 Service Pack 4 Installation Manual P/N 460987001B ISS 26APR11 Copyright Disclaimer Trademarks and patents Intended use Software license agreement FCC compliance Certification and compliance
Diamond II v2.3 Service Pack 4 Installation Manual P/N 460987001B ISS 26APR11 Copyright Disclaimer Trademarks and patents Intended use Software license agreement FCC compliance Certification and compliance
DSG SoftPhone & USB Phone Series User Guide
 DSG SoftPhone & USB Phone Series User Guide Table of Contents Overview Before You Start Installation Step 1. Installing DSG SoftPhone Step 2. Installing USB Phone Step 3. System Check First Time Use Step
DSG SoftPhone & USB Phone Series User Guide Table of Contents Overview Before You Start Installation Step 1. Installing DSG SoftPhone Step 2. Installing USB Phone Step 3. System Check First Time Use Step
Unified Communications Installation & Configuration Guide
 Unified Communications Installation & Configuration Guide Table of contents Page Applications License 1 Mitel 5110 Softphone 5 Click to Dial Application 22 Applications License Obtaining and Configuration
Unified Communications Installation & Configuration Guide Table of contents Page Applications License 1 Mitel 5110 Softphone 5 Click to Dial Application 22 Applications License Obtaining and Configuration
FrontDesk Installation And Configuration
 Chapter 2 FrontDesk Installation And Configuration FrontDesk v4.1.25 FrontDesk Software Install Online Software Activation Installing State Related Databases Setting up a Workstation Internet Transfer
Chapter 2 FrontDesk Installation And Configuration FrontDesk v4.1.25 FrontDesk Software Install Online Software Activation Installing State Related Databases Setting up a Workstation Internet Transfer
Nortel Networks Call Center Reporting Set Up and Operation Guide
 Nortel Networks Call Center Reporting Set Up and Operation Guide www.nortelnetworks.com 2001 Nortel Networks P0919439 Issue 07 (24) Table of contents How to use this guide... 5 Introduction...5 How this
Nortel Networks Call Center Reporting Set Up and Operation Guide www.nortelnetworks.com 2001 Nortel Networks P0919439 Issue 07 (24) Table of contents How to use this guide... 5 Introduction...5 How this
TECHNICAL BULLETIN. Configuring Wireless Settings in an i-stat 1 Wireless Analyzer
 i-stat TECHNICAL BULLETIN Configuring Wireless Settings in an i-stat 1 Wireless Analyzer Before configuring wireless settings, please enable the wireless functionality by referring to the Technical Bulletin
i-stat TECHNICAL BULLETIN Configuring Wireless Settings in an i-stat 1 Wireless Analyzer Before configuring wireless settings, please enable the wireless functionality by referring to the Technical Bulletin
Datacolor TOOLS. Datacolor TOOLS QCX. Datacolor TOOLS WORKSTATION
 Datacolor TOOLS Datacolor TOOLS QCX Datacolor TOOLS WORKSTATION Installation Instructions Datacolor TOOLS Installation Guide (June, 2009) All efforts have been made to ensure the accuracy of the information
Datacolor TOOLS Datacolor TOOLS QCX Datacolor TOOLS WORKSTATION Installation Instructions Datacolor TOOLS Installation Guide (June, 2009) All efforts have been made to ensure the accuracy of the information
e-dpp 4.0.2 May 2013 Quick Installation Guide Microsoft Windows 2003 Server, XP, Vista, 7 Access Database
 e-dpp 4.0.2 May 2013 Microsoft Windows 2003 Server, XP, Vista, 7 Access Database ELTECHS Engineering and Consulting Co., Ltd., Japan www.eltechs.co.jp Tel No. +81 (47) 490-1010 Fax No. +81 (47) 490-1011
e-dpp 4.0.2 May 2013 Microsoft Windows 2003 Server, XP, Vista, 7 Access Database ELTECHS Engineering and Consulting Co., Ltd., Japan www.eltechs.co.jp Tel No. +81 (47) 490-1010 Fax No. +81 (47) 490-1011
Horizon Inventory. User s and Administrator s Guide
 Horizon Inventory User s and Administrator s Guide Windows is a trademark of the Microsoft Corporation. Percon, PT 2000, PT Dock, and TopGun are trademarks or registered trademarks of PSC, Inc. Telxon
Horizon Inventory User s and Administrator s Guide Windows is a trademark of the Microsoft Corporation. Percon, PT 2000, PT Dock, and TopGun are trademarks or registered trademarks of PSC, Inc. Telxon
How To Set Up Total Recall Web On A Microsoft Memorybook 2.5.2.2 (For A Microtron)
 Total Recall Web Web Module Manual and Customer Quick Reference Guides COPYRIGHT NOTICE Copyright 1994-2009 by DHS Associates, Inc. All Rights Reserved. All TOTAL RECALL, TOTAL RECALL SQL, TOTAL RECALL
Total Recall Web Web Module Manual and Customer Quick Reference Guides COPYRIGHT NOTICE Copyright 1994-2009 by DHS Associates, Inc. All Rights Reserved. All TOTAL RECALL, TOTAL RECALL SQL, TOTAL RECALL
Quick Start Guide for SAXTAX 2010 Programs
 Quick Start Guide for SAXTAX 2010 Programs 1. Installation: Installing from a Link: Please click on the link provided in the setup email received. You will automatically be prompted with a download window.
Quick Start Guide for SAXTAX 2010 Programs 1. Installation: Installing from a Link: Please click on the link provided in the setup email received. You will automatically be prompted with a download window.
GX-2009 Data Logger Management Program Operator s Manual
 GX-2009 Data Logger Management Program Operator s Manual Part Number: 71-0163RK Revision: C Released: 3/19/12 www.rkiinstruments.com Warranty RKI Instruments, Inc. warrants gas alarm equipment sold by
GX-2009 Data Logger Management Program Operator s Manual Part Number: 71-0163RK Revision: C Released: 3/19/12 www.rkiinstruments.com Warranty RKI Instruments, Inc. warrants gas alarm equipment sold by
IMATION SECURE SCAN. ck Start Guide. Imation Secure Scan
 IMATION SECURE SCAN Quick ck Start Guide Imation Corp 2012 Imation Secure Scan page 1 of 6 1 Unpacking your Imation Secure Scan The following items are contained inside the case: 1 2 Imation Secure Scan
IMATION SECURE SCAN Quick ck Start Guide Imation Corp 2012 Imation Secure Scan page 1 of 6 1 Unpacking your Imation Secure Scan The following items are contained inside the case: 1 2 Imation Secure Scan
MN POS TM. Hardware & Peripherals. All required hardware may be purchased from Home Office.
 Important Notice Enclosed you will find the MN POS installation DVD for Windows 7 and Windows XP. Please keep all disks in a safe place in the Studio. If you purchased a computer from Home Office, MN POS
Important Notice Enclosed you will find the MN POS installation DVD for Windows 7 and Windows XP. Please keep all disks in a safe place in the Studio. If you purchased a computer from Home Office, MN POS
Korosi Monitoring System (KMS) Software Manual
 PT. KOROSI SPECINDO Corrosion Monitoring System Eng. Doc. No.: KS-MNL-KMS Korosi Monitoring System (KMS) Software Manual Revision Date Prepared Approved Description 0 23/05/2008 ES JH Issued for approval
PT. KOROSI SPECINDO Corrosion Monitoring System Eng. Doc. No.: KS-MNL-KMS Korosi Monitoring System (KMS) Software Manual Revision Date Prepared Approved Description 0 23/05/2008 ES JH Issued for approval
E-PLEX STANDARD SOFTWARE USER GUIDE, VERSION 3.2
 E-PLEX STANDARD SOFTWARE USER GUIDE, VERSION 3.2 Before you start installation 1. Internet Explorer 5.0 or higher must be installed on your computer. All Windows XP Home or Pro (SP2) machines have newer
E-PLEX STANDARD SOFTWARE USER GUIDE, VERSION 3.2 Before you start installation 1. Internet Explorer 5.0 or higher must be installed on your computer. All Windows XP Home or Pro (SP2) machines have newer
Getting Started with Vision 6
 Getting Started with Vision 6 Version 6.9 Notice Copyright 1981-2009 Netop Business Solutions A/S. All Rights Reserved. Portions used under license from third parties. Please send any comments to: Netop
Getting Started with Vision 6 Version 6.9 Notice Copyright 1981-2009 Netop Business Solutions A/S. All Rights Reserved. Portions used under license from third parties. Please send any comments to: Netop
Global Water Instrumentation, Inc.
 Global Water Instrumentation, Inc. 151 Graham Road P.O. Box 9010 College Station, TX 77842-9010 Telephone : 800-876-1172 International : (979) 690-5560, Fax : (979) 690-0440 e-mail : [email protected]
Global Water Instrumentation, Inc. 151 Graham Road P.O. Box 9010 College Station, TX 77842-9010 Telephone : 800-876-1172 International : (979) 690-5560, Fax : (979) 690-0440 e-mail : [email protected]
NortechCommander Software Operating Manual MAN-00004 R6
 NortechCommander Software Operating Manual MAN-00004 R6 If the equipment described herein bears the symbol, the said equipment complies with the applicable European Union Directive and Standards mentioned
NortechCommander Software Operating Manual MAN-00004 R6 If the equipment described herein bears the symbol, the said equipment complies with the applicable European Union Directive and Standards mentioned
STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER
 Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
Notes: STATISTICA VERSION 9 STATISTICA ENTERPRISE INSTALLATION INSTRUCTIONS FOR USE WITH TERMINAL SERVER 1. These instructions focus on installation on Windows Terminal Server (WTS), but are applicable
Dell Statistica 13.0. Statistica Enterprise Installation Instructions
 Dell Statistica 13.0 2015 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license or
Dell Statistica 13.0 2015 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished under a software license or
ADP CollectAll Manager v2.4 User s Guide
 ADP CollectAll Manager v2.4 User s Guide ADP CollectAll Manager Version 2.4 User s Guide 2007 Automatic Data Processing, Inc. ADP provides this publication as is without warranty of any kind, either express
ADP CollectAll Manager v2.4 User s Guide ADP CollectAll Manager Version 2.4 User s Guide 2007 Automatic Data Processing, Inc. ADP provides this publication as is without warranty of any kind, either express
SOFTWARE GUIDE PM1405 DATA PROCESSING SOFTWARE
 SOFTWARE GUIDE PM1405 DATA PROCESSING SOFTWARE Equipment Software Manufacturer Survey meter РМ1405 "РМ1405 Software" Polimaster Copyright Polimaster 2015. All rights reserved. According Copyright protection
SOFTWARE GUIDE PM1405 DATA PROCESSING SOFTWARE Equipment Software Manufacturer Survey meter РМ1405 "РМ1405 Software" Polimaster Copyright Polimaster 2015. All rights reserved. According Copyright protection
Important. Please read this User s Manual carefully to familiarize yourself with safe and effective usage.
 Important Please read this User s Manual carefully to familiarize yourself with safe and effective usage. About ScreenManager Pro for LCD... 3 1. Setting Up... 4 1-1. System Requirements...4 1-2. Installing
Important Please read this User s Manual carefully to familiarize yourself with safe and effective usage. About ScreenManager Pro for LCD... 3 1. Setting Up... 4 1-1. System Requirements...4 1-2. Installing
Setup and Configuration Guide for Pathways Mobile Estimating
 Setup and Configuration Guide for Pathways Mobile Estimating Setup and Configuration Guide for Pathways Mobile Estimating Copyright 2008 by CCC Information Services Inc. All rights reserved. No part of
Setup and Configuration Guide for Pathways Mobile Estimating Setup and Configuration Guide for Pathways Mobile Estimating Copyright 2008 by CCC Information Services Inc. All rights reserved. No part of
Desktop Programmer (DTP)
 INSTALLATION Desktop Programmer (DTP) Keypads & Readers Contents Set up the System...1 RCI DTP Contents...1 Install the System...2 Initialize the Program...2 Initialize the Door Locks...3 Add a User...4
INSTALLATION Desktop Programmer (DTP) Keypads & Readers Contents Set up the System...1 RCI DTP Contents...1 Install the System...2 Initialize the Program...2 Initialize the Door Locks...3 Add a User...4
User Guide for TASKE Desktop
 User Guide for TASKE Desktop For Avaya Aura Communication Manager with Aura Application Enablement Services Version: 8.9 Date: 2013-03 This document is provided to you for informational purposes only.
User Guide for TASKE Desktop For Avaya Aura Communication Manager with Aura Application Enablement Services Version: 8.9 Date: 2013-03 This document is provided to you for informational purposes only.
PORTABLE DATA COLLECTION TERMINAL
 PORTABLE DATA COLLECTION TERMINAL WINDOWS TRANSFER UTILITY HELP FILES BETA EDITION Compsee, Inc. A Subsidiary of McRae Industries, Inc. 2 Welcome Thank you for using the Apex III Windows Transfer Utility
PORTABLE DATA COLLECTION TERMINAL WINDOWS TRANSFER UTILITY HELP FILES BETA EDITION Compsee, Inc. A Subsidiary of McRae Industries, Inc. 2 Welcome Thank you for using the Apex III Windows Transfer Utility
Operating Manual QUESTOR
 QUESTOR AS 273 Management Software Document: KSW3s527.0004 / en 2010.08 Edition: August 2010 QUESTOR TABLE OF CONTENT 1 Product description EN-4 1.1 Purpose... EN-4 1.2 System components... EN-4 1.2.1
QUESTOR AS 273 Management Software Document: KSW3s527.0004 / en 2010.08 Edition: August 2010 QUESTOR TABLE OF CONTENT 1 Product description EN-4 1.1 Purpose... EN-4 1.2 System components... EN-4 1.2.1
Schlage Express Offline Access Control Software - Version 4. Software Manual
 Schlage Express Offline Access Control Software - Version 4 Software Manual Ingersoll Rand Copyright Notice 2013 Ingersoll-Rand Company This documentation and the software/hardware described herein, is
Schlage Express Offline Access Control Software - Version 4 Software Manual Ingersoll Rand Copyright Notice 2013 Ingersoll-Rand Company This documentation and the software/hardware described herein, is
Parallels Desktop for Mac
 Parallels Software International, Inc. Parallels Desktop for Mac Quick Start Guide 3.0 (c) 2005-2007 Copyright 2006-2007 by Parallels Software International, Inc. All rights reserved. Parallels and Parallels
Parallels Software International, Inc. Parallels Desktop for Mac Quick Start Guide 3.0 (c) 2005-2007 Copyright 2006-2007 by Parallels Software International, Inc. All rights reserved. Parallels and Parallels
USB 2.0 VGA ADAPTER USER MANUAL
 USB 2.0 VGA ADAPTER USER MANUAL CONTENTS INTRODUCTION... 3 FEATURES... 3 SYSTEM REQUIREMENTS... 3 PACKAGE CONTENTS... 3 SUPPORTED COMMON DISPLAY RESOLUTION... 4 TECHNICAL SPECIFICATIONS... 4 INSTALLATION
USB 2.0 VGA ADAPTER USER MANUAL CONTENTS INTRODUCTION... 3 FEATURES... 3 SYSTEM REQUIREMENTS... 3 PACKAGE CONTENTS... 3 SUPPORTED COMMON DISPLAY RESOLUTION... 4 TECHNICAL SPECIFICATIONS... 4 INSTALLATION
USB 2.0 Peripheral Switch USER MANUAL US221A / US421A
 USB 2.0 Peripheral Switch USER MANUAL US221A / US421A FCC Information This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules.
USB 2.0 Peripheral Switch USER MANUAL US221A / US421A FCC Information This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to Part 15 of the FCC Rules.
Config software for D2 systems USER S MANUAL
 DT-CONFIG SOFTWARE Config software for D2 systems USER S MANUAL CONTENTS 1. Introductions ------------------------------------------------------------------- 3 2. System Requirement and Connection ----------------------------------------
DT-CONFIG SOFTWARE Config software for D2 systems USER S MANUAL CONTENTS 1. Introductions ------------------------------------------------------------------- 3 2. System Requirement and Connection ----------------------------------------
Table Of Contents. System Monitoring... 14 System Monitoring Display...14 Monitoring Zones...15 About Areas (partitions)...15 Area Status Display...
 Quick Start Table Of Contents Getting Started... 2 NEware Editions...2 Installing NEware...3 Installing Languages...3 Connecting to NEware...3 Changing Your IP100 Password...4 User Codes... 5 Master Feature...5
Quick Start Table Of Contents Getting Started... 2 NEware Editions...2 Installing NEware...3 Installing Languages...3 Connecting to NEware...3 Changing Your IP100 Password...4 User Codes... 5 Master Feature...5
Fleet Maintenance Software
 Fleet Maintenance Software Welcome Thank you for taking time to review FleetWise VB Maintenance Management Made Simple. This guide is intended to provide a quick overview of installing the software and
Fleet Maintenance Software Welcome Thank you for taking time to review FleetWise VB Maintenance Management Made Simple. This guide is intended to provide a quick overview of installing the software and
Topaz Installation Sheet
 Topaz Installation Sheet P/N 460924001E ISS 08FEB12 Content Introduction... 3 Recommended minimum requirements... 3 Setup for Internet Explorer:... 4 Topaz installation... 10 Technical support... 14 Copyright
Topaz Installation Sheet P/N 460924001E ISS 08FEB12 Content Introduction... 3 Recommended minimum requirements... 3 Setup for Internet Explorer:... 4 Topaz installation... 10 Technical support... 14 Copyright
DataSuite Installation and Activation Guide
 DataSuite Installation and Activation Guide This document provides a detailed overview of the installation and activation procedure for the DataSuite v2.4.0.0 software. DataSuite allows you to configure
DataSuite Installation and Activation Guide This document provides a detailed overview of the installation and activation procedure for the DataSuite v2.4.0.0 software. DataSuite allows you to configure
DriveRight. Fleet Management Software. Getting Started Guide. CarChip. DriveRight. Drivers. Vehicles. Product #8186
 DriveRight Fleet Management Software Getting Started Guide CarChip DriveRight Drivers Vehicles Product #8186 DriveRight Fleet Management Software Getting Started Guide; P/N 8186 Davis Instruments Part
DriveRight Fleet Management Software Getting Started Guide CarChip DriveRight Drivers Vehicles Product #8186 DriveRight Fleet Management Software Getting Started Guide; P/N 8186 Davis Instruments Part
EPSON Scan Server & EPSON TWAIN Pro Network
 EPSON Scan Server & EPSON TWAIN Pro Network EPSON Scan Server & EPSON TWAIN Pro Network SCANNER UTILITY PROGRAMS All rights reserved. No part of this publication may be reproduced, stored in a retrieval
EPSON Scan Server & EPSON TWAIN Pro Network EPSON Scan Server & EPSON TWAIN Pro Network SCANNER UTILITY PROGRAMS All rights reserved. No part of this publication may be reproduced, stored in a retrieval
800-02577-TC 3/10 Rev. A
 800-02577-TC 3/10 Rev. A Total Connect Online Help Guide TRADEMARKS Honeywell is a registered trademark of Honeywell International Inc. Windows and Windows Vista are trademarks, or registered trademarks
800-02577-TC 3/10 Rev. A Total Connect Online Help Guide TRADEMARKS Honeywell is a registered trademark of Honeywell International Inc. Windows and Windows Vista are trademarks, or registered trademarks
E-PLEX STANDARD SOFTWARE USER GUIDE, VERSION 3.1
 E-PLEX STANDARD SOFTWARE USER GUIDE, VERSION 3.1 Before you start installation 1. Internet Explorer 5.0 or higher must be installed on your computer. All Windows 2000, XP Home or Pro (SP2) machines have
E-PLEX STANDARD SOFTWARE USER GUIDE, VERSION 3.1 Before you start installation 1. Internet Explorer 5.0 or higher must be installed on your computer. All Windows 2000, XP Home or Pro (SP2) machines have
JEROME COMMUNICATIONS SOFTWARE (JCS) INSTALLATION and OPERATION MANUAL V1.02 for Windows XP
 AZI P/N 700-0042-B Last update May 2009 USER MANUAL JEROME COMMUNICATIONS SOFTWARE (JCS) INSTALLATION and OPERATION MANUAL V1.02 for Windows XP May 2009 ARIZONA INSTRUMENT LLC 3375 N Delaware Street Chandler,
AZI P/N 700-0042-B Last update May 2009 USER MANUAL JEROME COMMUNICATIONS SOFTWARE (JCS) INSTALLATION and OPERATION MANUAL V1.02 for Windows XP May 2009 ARIZONA INSTRUMENT LLC 3375 N Delaware Street Chandler,
The FlexiSchools Online Order Management System Installation Guide
 The FlexiSchools Online Order Management System Installation Guide FlexiSchools May 2012 Page 1 of 18 Installation Pack Welcome to the FlexiSchools system. You will have received a disc containing: Sato
The FlexiSchools Online Order Management System Installation Guide FlexiSchools May 2012 Page 1 of 18 Installation Pack Welcome to the FlexiSchools system. You will have received a disc containing: Sato
Kaspersky Password Manager
 Kaspersky Password Manager User Guide Dear User, Thank you for choosing our product. We hope that you will find this documentation useful and that it will provide answers to most questions that may arise.
Kaspersky Password Manager User Guide Dear User, Thank you for choosing our product. We hope that you will find this documentation useful and that it will provide answers to most questions that may arise.
Corsair Flash Voyager USB 2.0 Flash Drive UFD Utility User s Manual
 Corsair Flash Voyager USB 2.0 Flash Drive UFD Utility User s Manual Contents For AP v2.10.0.0 Release For Windows 98/ME/2000/XP Version 1.1B (08/27/2004) Contents...1 Introduction...1 Features & Specifications...2
Corsair Flash Voyager USB 2.0 Flash Drive UFD Utility User s Manual Contents For AP v2.10.0.0 Release For Windows 98/ME/2000/XP Version 1.1B (08/27/2004) Contents...1 Introduction...1 Features & Specifications...2
Job Scheduler User Guide IGSS Version 11.0
 Job Scheduler User Guide IGSS Version 11.0 The information provided in this documentation contains general descriptions and/or technical characteristics of the performance of the products contained therein.
Job Scheduler User Guide IGSS Version 11.0 The information provided in this documentation contains general descriptions and/or technical characteristics of the performance of the products contained therein.
SHARP Digital Signage Software Pro PN-SS05 OPERATION MANUAL
 SHARP Digital Signage Software Pro PN-SS05 Version 4.1 OPERATION MANUAL Contents Introduction... 2 Precautions on Use...2 Trademarks...2 How to Read this Manual...3 Definitions...3 Installing/Launching...
SHARP Digital Signage Software Pro PN-SS05 Version 4.1 OPERATION MANUAL Contents Introduction... 2 Precautions on Use...2 Trademarks...2 How to Read this Manual...3 Definitions...3 Installing/Launching...
OFFICE KEYBOARD (MT1210 & MT1405) OFFICE FEATURES
 OFFICE KEYBOARD (MT1210 & MT1405) OFFICE FEATURES Thank you for purchasing OFFICE KEYBOARD. This User s manual contains all information that helps you to operate your keyboard. Please keep the software
OFFICE KEYBOARD (MT1210 & MT1405) OFFICE FEATURES Thank you for purchasing OFFICE KEYBOARD. This User s manual contains all information that helps you to operate your keyboard. Please keep the software
Diamante WiFi Wireless Communication User Guide. Linksys E1200
 Diamante WiFi Wireless Communication User Guide Linksys E1200 Release: February 2012; August 2011; February 2011 Patent Pending. Copyright 2012, Stenograph, L.L.C. All Rights Reserved. Printed in U.S.A.
Diamante WiFi Wireless Communication User Guide Linksys E1200 Release: February 2012; August 2011; February 2011 Patent Pending. Copyright 2012, Stenograph, L.L.C. All Rights Reserved. Printed in U.S.A.
PROGRAMMING & OPERATING INSTRUCTIONS CL5000 AUDIT TRAIL
 PROGRAMMING & OPERATING INSTRUCTIONS CL5000 AUDIT TRAIL 1 CODES AND OPERATION CODES The factory set Master Code is #1234. This should be changed immediately after installation (see Program 10). The Master
PROGRAMMING & OPERATING INSTRUCTIONS CL5000 AUDIT TRAIL 1 CODES AND OPERATION CODES The factory set Master Code is #1234. This should be changed immediately after installation (see Program 10). The Master
IBM Sterling Gentran:Director Connection. User Guide
 IBM Sterling Gentran:Director Connection User Guide Version 6.2 4108-540-USER04-0002 Copyright This edition applies to the 6.2 Version of IBM Sterling Gentran:Director Connection and to all subsequent
IBM Sterling Gentran:Director Connection User Guide Version 6.2 4108-540-USER04-0002 Copyright This edition applies to the 6.2 Version of IBM Sterling Gentran:Director Connection and to all subsequent
User Guide Win7Zilla
 User Guide Win7Zilla Table of contents Section 1: Installation... 3 1.1 System Requirements... 3 1.2 Software Installation... 3 1.3 Uninstalling Win7Zilla software... 3 Section 2: Navigation... 4 2.1 Main
User Guide Win7Zilla Table of contents Section 1: Installation... 3 1.1 System Requirements... 3 1.2 Software Installation... 3 1.3 Uninstalling Win7Zilla software... 3 Section 2: Navigation... 4 2.1 Main
Internet Explorer 7. Getting Started The Internet Explorer Window. Tabs NEW! Working with the Tab Row. Microsoft QUICK Source
 Microsoft QUICK Source Internet Explorer 7 Getting Started The Internet Explorer Window u v w x y { Using the Command Bar The Command Bar contains shortcut buttons for Internet Explorer tools. To expand
Microsoft QUICK Source Internet Explorer 7 Getting Started The Internet Explorer Window u v w x y { Using the Command Bar The Command Bar contains shortcut buttons for Internet Explorer tools. To expand
Setting Up Monthly Reporter
 Setting Up Monthly Reporter April 11, 2014 I. HOW IT WORKS A QUICK OVERVIEW A. AuditWare Development Company maintains a powerful, sophisticated server on which a portion of memory is assigned to each
Setting Up Monthly Reporter April 11, 2014 I. HOW IT WORKS A QUICK OVERVIEW A. AuditWare Development Company maintains a powerful, sophisticated server on which a portion of memory is assigned to each
Legal Notes. Regarding Trademarks. Models supported by the KX printer driver. 2011 KYOCERA MITA Corporation
 Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held liable for any problems arising from
Getting Started. rp5800, rp5700 and rp3000 Models
 Getting Started rp5800, rp5700 and rp3000 Models Copyright 2011 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. Microsoft, Windows, and Windows
Getting Started rp5800, rp5700 and rp3000 Models Copyright 2011 Hewlett-Packard Development Company, L.P. The information contained herein is subject to change without notice. Microsoft, Windows, and Windows
Cart Interface Installation & Control Board Manual for M38 XP and RX Carts and Legacy M39 Carts
 Rubbermaid Medical Solutions Cart Interface Installation & Control Board Manual for M38 XP and RX Carts and Legacy M39 Carts REVISED FEBRUARY 25, 2010 Filename: Cart Interface Installation & Control Board
Rubbermaid Medical Solutions Cart Interface Installation & Control Board Manual for M38 XP and RX Carts and Legacy M39 Carts REVISED FEBRUARY 25, 2010 Filename: Cart Interface Installation & Control Board
Web Conference Manager
 Web Conference Manager Reference Guide Table of Contents 1. Introduction to GTB Web Conferencing... 1 2. System Requirements... 2 3. Web Conferencing Host... 3 Accessing the server... 3 Testing your system...
Web Conference Manager Reference Guide Table of Contents 1. Introduction to GTB Web Conferencing... 1 2. System Requirements... 2 3. Web Conferencing Host... 3 Accessing the server... 3 Testing your system...
COMSPHERE 6700 SERIES NETWORK MANAGEMENT SYSTEM
 COMSPHERE 6700 SERIES NETWORK MANAGEMENT SYSTEM SECURITY MANAGER FEATURE SUPPLEMENT Document No. 6700-A2-GB41-30 February 1998 Copyright 1998 Paradyne Corporation. All rights reserved. Printed in U.S.A.
COMSPHERE 6700 SERIES NETWORK MANAGEMENT SYSTEM SECURITY MANAGER FEATURE SUPPLEMENT Document No. 6700-A2-GB41-30 February 1998 Copyright 1998 Paradyne Corporation. All rights reserved. Printed in U.S.A.
