MacScan. MacScan User Guide. Detect, Isolate and Remove Spyware
|
|
|
- Allen Barker
- 8 years ago
- Views:
Transcription
1 MacScan MacScan User Guide Detect, Isolate and Remove Spyware
2
3 Part Introduction MacScan is a spyware detection utility for Macintosh OS X that finds and removes spyware and other Internet files that may compromise your privacy from your computer. MacScan uses advanced detection methods to detect, isolate, and remove Spyware, keystroke loggers, and Trojan horses from your system. It alerts you to remote administration programs that may have been maliciously installed on your Macintosh. When MacScan detects spyware, it generates a report which allows the user to isolate the components. MacScan will move all selected spyware programs, extensions, preferences, and log files to a single and secured location. Page 3 of 16
4 Part Preferences This section highlights the options that are found on the Preferences screen in MacScan. To change the preferences, select Preferences under the MacScan menu, or click the Prefs icon in the MacScan toolbar Detect Remote Administration Programs This option enables additional auditing of files for remote administration programs during a spyware scan. Remote administration programs can be found in shareware, freeware, and commercial applications and allow complete remote control of a computer. In the hands of a malicious user, these programs could be used to access personal information, passwords, and private files Automatically check for updated Spyware Definition* This option will enable MacScan to automatically check for updated Spyware Definitions. If an update is available, MacScan will notify you of the update and allow you to download it. * This feature requires an active Internet connection. Page 4 of 16
5 Part Getting Started To get started with MacScan, double-click on the MacScan icon. The MacScan Mode Selection screen will appear. No Click the No button if you do not want to run MacScan in authenticated mode. Yes Click the Yes button if you want to run MacScan in authenticated mode MacScan Mode Selection Running MacScan in normal mode does not require a username or password. In order to run MacScan in authenticated mode, you will need to provide your OS X username and password. You may be required to authenticate as administrator by entering your username and password before running the scan to complete a full level or custom scan. This will grant MacScan full scanning privileges to your computer. Page 5 of 16
6 Name Enter the username of the Administrator account in the Name field. By default, the account created after installing OS X is an administrator account. Password Enter the password for the account in the password field. OK Click the OK button to proceed after entering the username and password of an Administrator account. Cancel Click the Cancel button to close the Authenticate screen if you choose not to run MacScan in authenticated mode. After successfully authenticating, or if running MacScan in Normal Mode, MacScan will display the main window: Page 6 of 16
7 MacScan's intuitive interface makes it easy to start scanning your computer for spyware. When MacScan starts up, the status screen displays statistics about spyware scans performed by MacScan as well as information about the version of MacScan currently running. The spyware statistics are automatically updated after each spyware scan and include the date and time of the last spyware scan, the number of spyware components detected on the last scan, the total number spyware scans that have been run, and the number of spyware components detected overall. Below the scan statistics are internal details about the current version of MacScan, which includes the scan engine version, the Spyware Definitions version, and the creation date of the current definitions. The status screen also includes information on the Cookie Blacklist, a list of known cookies that can track your internet surfing habits. The Cookie Blacklist Version and creation date are also displayed. Page 7 of 16
8 Part Scanning for Spyware To view the different types of scans, click on the scan icon located in the MacScan toolbar, or click on the scan button located on the status screen. The scan screen contains information on each type of scan. To choose a scan type, select the appropriate tab. MacScan offers three different types of spyware scans: quick scan, full scan, and custom scan Quick Scan The Quick Scan checks the files in your home folder for known spyware applications. MacScan will also scan your running processes for the presence of spyware. If spyware is detected in the current processes but does not appear for isolation after Quick Scan is finished, it may be running from a folder not accessible with your current permissions. If this is the case, try running a Full Scan. If a full scan fails to isolate the spyware file, restart MacScan in Authenticated Mode. Page 8 of 16
9 Running a Quick Scan To perform a Quick Scan, click the Quick Scan tab on the Scan Screen, and then click on the Scan button in the lower right corner. You can then view the scan status as MacScan scans your hard drive. Quick Scans should be performed frequently (daily or weekly). The scans are short but ensure protection of your computer and your privacy. However, running a Full Scan upon installation of MacScan is strongly recommended. Page 9 of 16
10 4.1.2 Full Scan MacScan's Full Scan function will scan your startup disk for spyware and check for actively running spyware applications. It will search thoroughly for spyware by scanning all accessible files on your start up disk. If you would like to scan a specific folder on your computer such as an external hard drive or removable media such as CDs or DVDs, use Custom Scan instead Running a Full Scan Click on the Scan button to run a Full Scan on your hard drive. Note: Running MacScan in authenticated mode allows Full Scan to run at full capability. Page 10 of 16
11 4.1.3 Custom Scan Custom Scan allows you to scan a specific folder or drive for spyware. You can specify a folder, data CD, DVD, or other hard drives by selecting those locations for a Custom Scan. Custom Scan will scan for spyware in all accessible files in the specified location. Note: Spyware detected on a locked volume such as a data CD or DVD cannot be isolated Running a Custom Scan To configure and perform a Custom Scan, click on the Scan button and choose Custom Scan from the tabbed items. Select the folder or drive to be scanned from the window that appears, and click Select. MacScan will start scanning the specified folder or drive for spyware. Page 11 of 16
12 If no spyware is found, the following window will be displayed: Done Click the Done button when the scan is over. Cancel Click the Cancel button at any time during a scan to end the current scan. Any spyware detected by that point will be displayed. Threat Each piece of spyware detected by MacScan is assigned a threat level to indicate the impact on your operating system. Trojan horses and keystroke loggers are the biggest threats to your system security and are visually represented by a red triangle. Tracking cookies are medium level threats and are represented by a yellow triangle. Remote administration programs that are not necessarily spyware but can be used to compromise your system security are represented by a green triangle. Spyware Name The spyware applications that have been detected will be displayed in the column labeled Spyware Name. Page 12 of 16
13 Spyware Type The classification of spyware applications that have been detected (Trojan horse, Keylogger, or Remote Administration Program) will be displayed in the column labeled Spyware Type. As with all of the scan types, Custom Scan will only be able to scan folders and files that you can access with your user account. If you are unable to scan a specific location with Custom Scan, run MacScan in Authenticated Mode. If you do not have administrator access to run in Authenticated Mode, contact the administrator and ask for assistance. If spyware is found, the following screen will be displayed: Select which spyware to isolate, and click the "Isolate" button. Spyware such as Trojan horses and Keyloggers will be isolated to the folder MacScan Isolated Spyware on the Desktop. Tracking cookies will be removed immediately. Page 13 of 16
14 Part Cleaning Internet/Web Files Cookies are messages given to a web browser by a web server. The browser stores messages in text files. The message is sent back to the server whenever the browser requests a page from that particular server. MacScan can remove these cookies from your system. After clicking on the Web Files icon, the following screen will appear: You can select specific web browsers and specific files you want to clean. To clean Internet/Web files, you must select at least one browser and at least one file type to clean. Web Browsers to clean: Indicate the web browsers to be cleaned by clicking on the Select box next to the name of the desired browser. Web browsers not installed on the computer will be grayed out and not selectable. You can select more than one web browser to clean at a time. Files to clean: Indicate the files to be cleaned by clicking on the Select box next to the name of the file you want to clean. Page 14 of 16
15 You can select more than one file to clean at a time. Cookies History Select this box to clear cookies from your computer. Select this box to clear History files. Downloaded Files List Temporary Cache Files Select this box to clear the Downloaded Files list. Select this box to clear Temporary Cache files. Page 15 of 16
16 Part Spyware Information Database MacScan comes bundled with spyware information. This section provides you with information about spyware, Keyloggers, Trojan Horses and Remote Administration Programs Display Spyware Information Select a Spyware Information entry in the popup menu to display detailed information about that particular topic Keyloggers Select Keyloggers to get information about Keyloggers Trojan Horses Select Trojan Horses to get information about Trojan Horses Spyware Select Spyware to get information about Spyware Remote Administration Programs Select Remote Administration Programs to get information about Remote Administration programs. Page 16 of 16
Software. Webroot. Spy Sweeper. User Guide. for. Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com. Version 6.
 Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
Webroot Software User Guide for Spy Sweeper Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 6.1 Webroot Software User Guide Version 6.1 2003 2009 Webroot Software, Inc. All
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.7.0 1996-2006 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.7.0 1996-2006 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
MiraCosta College now offers two ways to access your student virtual desktop.
 MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
MiraCosta College now offers two ways to access your student virtual desktop. We now feature the new VMware Horizon View HTML access option available from https://view.miracosta.edu. MiraCosta recommends
CONNECT-TO-CHOP USER GUIDE
 CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
CONNECT-TO-CHOP USER GUIDE VERSION V8 Table of Contents 1 Overview... 3 2 Requirements... 3 2.1 Security... 3 2.2 Computer... 3 2.3 Application... 3 2.3.1 Web Browser... 3 2.3.2 Prerequisites... 3 3 Logon...
Instructions for Connecting to PACS outside of a Regional Facility
 Instructions for Connecting to PACS outside of a Regional Facility For support, please contact the ehealth Saskatchewan Helpdesk at 1-888-316-7446 Recommended options provide optimal performance 1 The
Instructions for Connecting to PACS outside of a Regional Facility For support, please contact the ehealth Saskatchewan Helpdesk at 1-888-316-7446 Recommended options provide optimal performance 1 The
Installing Novell Client Software (Windows 95/98)
 Installing Novell Client Software (Windows 95/98) Platform: Windows 95/98 Level of Difficulty: Intermediate The following procedure describes how to install the Novell Client software. This software allows
Installing Novell Client Software (Windows 95/98) Platform: Windows 95/98 Level of Difficulty: Intermediate The following procedure describes how to install the Novell Client software. This software allows
Remote Access - Mac OS X
 Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Remote Access - Mac OS X Overview Sections: Page: Security Precautions to Consider When Connecting Remotely 2 1. Check for Operating System updates 2 2. Install Sophos antivirus 2 3. Check for updates
Sophos Anti-Virus standalone startup guide. For Windows and Mac OS X
 Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Sophos Anti-Virus standalone startup guide For Windows and Mac OS X Document date: June 2007 Contents 1 What you need for installation...4 2 Installing Sophos Anti-Virus for Windows...5 3 Installing Sophos
Contents. McAfee Internet Security 3
 User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
User Guide i Contents McAfee Internet Security 3 McAfee SecurityCenter... 5 SecurityCenter features... 6 Using SecurityCenter... 7 Fixing or ignoring protection problems... 16 Working with alerts... 21
Virtual Office Remote Installation Guide
 Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Virtual Office Remote Installation Guide Table of Contents VIRTUAL OFFICE REMOTE INSTALLATION GUIDE... 3 UNIVERSAL PRINTER CONFIGURATION INSTRUCTIONS... 12 CHANGING DEFAULT PRINTERS ON LOCAL SYSTEM...
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Sophos Endpoint Security and Control standalone startup guide
 Sophos Endpoint Security and Control standalone startup guide Sophos Endpoint Security and Control version 9 Sophos Anti-Virus for Mac OS X, version 7 Document date: October 2009 Contents 1 Before you
Sophos Endpoint Security and Control standalone startup guide Sophos Endpoint Security and Control version 9 Sophos Anti-Virus for Mac OS X, version 7 Document date: October 2009 Contents 1 Before you
FTP Over SSL (FTPS) Core FTP LE. Installing Core FTP LE"
 FTP Over SSL (FTPS) Gordon State College has setup FTP Over SSL (also known as FTPS ) to allow students, faculty, and staff to access resources from our Servers from off-campus using an encrypted connection.
FTP Over SSL (FTPS) Gordon State College has setup FTP Over SSL (also known as FTPS ) to allow students, faculty, and staff to access resources from our Servers from off-campus using an encrypted connection.
How to install and use the File Sharing Outlook Plugin
 How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
How to install and use the File Sharing Outlook Plugin Thank you for purchasing Green House Data File Sharing. This guide will show you how to install and configure the Outlook Plugin on your desktop.
User's Manual. Intego Remote Management Console User's Manual Page 1
 User's Manual Intego Remote Management Console User's Manual Page 1 Intego Remote Management Console for Macintosh 2007 Intego, Inc. All Rights Reserved Intego, Inc. www.intego.com This manual was written
User's Manual Intego Remote Management Console User's Manual Page 1 Intego Remote Management Console for Macintosh 2007 Intego, Inc. All Rights Reserved Intego, Inc. www.intego.com This manual was written
Immotec Systems, Inc. SQL Server 2005 Installation Document
 SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
SQL Server Installation Guide 1. From the Visor 360 installation CD\USB Key, open the Access folder and install the Access Database Engine. 2. Open Visor 360 V2.0 folder and double click on Setup. Visor
Installing Microsoft Outlook on a Macintosh. This document explains how to download, install and configure Microsoft Outlook on a Macintosh.
 Reference : USER184 Issue date : December 2002 Revision date : September 2007 Classification : Software Originator : Hugh Burt REVISED DOCUMENT Installing Microsoft Outlook on a Macintosh This document
Reference : USER184 Issue date : December 2002 Revision date : September 2007 Classification : Software Originator : Hugh Burt REVISED DOCUMENT Installing Microsoft Outlook on a Macintosh This document
How To Use Secureanything On A Mac Or Ipad (For A Mac)
 User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
User Guide for Mac OS X Copyright Webroot SecureAnywhere User Guide for Mac OS X March, 2013 2012-2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere is
Using Remote Web Workplace Version 1.01
 Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Using Remote Web Workplace Version 1.01 Remote web workplace allows you to access your Windows XP desktop through Small Business Server 2003 from a web browser. 1. Connect to the Internet in your remote
Bloomfield Hills Schools VPN and Viewconnect Instructions
 Connect to Bloomfield Hills Schools VPN - Open Internet Explorer. - Type https://vpn.bloomfield.org into the address bar. - Click Continue to this website (not recommended). if prompted. - If this is your
Connect to Bloomfield Hills Schools VPN - Open Internet Explorer. - Type https://vpn.bloomfield.org into the address bar. - Click Continue to this website (not recommended). if prompted. - If this is your
Protecting Your Computer from Viruses and Spyware
 Protecting Your Computer from Viruses and Spyware PROTECTING YOUR COMPUTER FROM VIRUSES AND SPYWARE A virus is a program that runs on your computer without asking permission and makes copies of itself.
Protecting Your Computer from Viruses and Spyware PROTECTING YOUR COMPUTER FROM VIRUSES AND SPYWARE A virus is a program that runs on your computer without asking permission and makes copies of itself.
INSTALLING MÜSE UPDATES FOR ISTAN
 INSTALLING MÜSE UPDATES FOR ISTAN System updates are available periodically and can be downloaded using any computer with an Internet connection. CAE Healthcare Instructor Workstations should NOT be connected
INSTALLING MÜSE UPDATES FOR ISTAN System updates are available periodically and can be downloaded using any computer with an Internet connection. CAE Healthcare Instructor Workstations should NOT be connected
Quick Start. Installing the software. for Webroot Internet Security Complete, Version 7.0
 Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
Quick Start for Webroot Internet Security Complete, Version 7.0 This Quick Start describes how to install and begin using the Webroot Internet Security Complete 2011 software. This integrated suite delivers
ESET NOD32 Antivirus 4 for Linux Desktop. Quick Start Guide
 ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
ESET NOD32 Antivirus 4 for Linux Desktop Quick Start Guide ESET NOD32 Antivirus 4 provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning engine
User's Manual. Intego VirusBarrier Server 2 / VirusBarrier Mail Gateway 2 User's Manual Page 1
 User's Manual Intego VirusBarrier Server 2 / VirusBarrier Mail Gateway 2 User's Manual Page 1 VirusBarrier Server 2 and VirusBarrier Mail Gateway 2 for Macintosh 2008 Intego. All Rights Reserved Intego
User's Manual Intego VirusBarrier Server 2 / VirusBarrier Mail Gateway 2 User's Manual Page 1 VirusBarrier Server 2 and VirusBarrier Mail Gateway 2 for Macintosh 2008 Intego. All Rights Reserved Intego
QUANTIFY INSTALLATION GUIDE
 QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
QUANTIFY INSTALLATION GUIDE Thank you for putting your trust in Avontus! This guide reviews the process of installing Quantify software. For Quantify system requirement information, please refer to the
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Linko Software Express Edition Typical Installation Guide
 Linko Software Express Edition Typical Installation Guide Install Database Service Components and Database...1 Install Workstation Components...4 Install DB Administration Tool...6 Office 2003 Security
Linko Software Express Edition Typical Installation Guide Install Database Service Components and Database...1 Install Workstation Components...4 Install DB Administration Tool...6 Office 2003 Security
educ Office 365 email: Remove & create new Outlook profile
 Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
Published: 29/01/2015 If you have previously used Outlook the with the SCC/SWO service then once you have been moved into Office 365 your Outlook will need to contact the SCC/SWO servers one last time
TxEIS on Internet Explorer 7
 TxEIS on Internet Explorer 7 General Set Up Recommendations: Several modifications will need to be made to the computer settings in Internet Explorer to ensure TxEIS runs smoothly, reports pop up as desired,
TxEIS on Internet Explorer 7 General Set Up Recommendations: Several modifications will need to be made to the computer settings in Internet Explorer to ensure TxEIS runs smoothly, reports pop up as desired,
Using SSH Secure Shell Client for FTP
 Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Using SSH Secure Shell Client for FTP The SSH Secure Shell for Workstations Windows client application features this secure file transfer protocol that s easy to use. Access the SSH Secure FTP by double-clicking
Sophos Anti-Virus for Mac OS X: Home Edition Help
 Sophos Anti-Virus for Mac OS X: Home Edition Help For standalone Macs running Mac OS X Product version: 9C Document date: June 2013 Sophos TOC 3 Contents About Sophos Anti-Virus...5 About the Scans window...5
Sophos Anti-Virus for Mac OS X: Home Edition Help For standalone Macs running Mac OS X Product version: 9C Document date: June 2013 Sophos TOC 3 Contents About Sophos Anti-Virus...5 About the Scans window...5
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website
 Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Mapping ITS s File Server Folder to Mosaic Windows to Publish a Website April 16 2012 The following instructions are to show you how to map your Home drive using ITS s Network in order to publish a website
Instructions for Connecting to PACS outside of a Regional Facility
 Instructions for Connecting to PACS outside of a Regional Facility For support, please contact the ehealth Saskatchewan Helpdesk at 1-888-316-7446 Recommended options provide optimal performance The following
Instructions for Connecting to PACS outside of a Regional Facility For support, please contact the ehealth Saskatchewan Helpdesk at 1-888-316-7446 Recommended options provide optimal performance The following
Installation Guide for Kurzweil 3000 Web License (Visual Walkthrough) Macintosh Version 14
 Installation Guide for Kurzweil 3000 Web License (Visual Walkthrough) Macintosh Version 14 Follow the instructions in this guide to download, install, and get started with Kurzweil 3000 Web License (K3000).
Installation Guide for Kurzweil 3000 Web License (Visual Walkthrough) Macintosh Version 14 Follow the instructions in this guide to download, install, and get started with Kurzweil 3000 Web License (K3000).
Using Spy Sweeper for Windows Author: Jocelyn Kasamoto
 WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
WIN1048 February 2009 Using Spy Sweeper for Windows Author: Jocelyn Kasamoto Introduction 1 System Requirements 2 Installation Instructions 2 Post Installation Tasks 3 Running Spy Sweeper 3 Subscription
Learning Management System (LMS) Quick Tips. Contents LMS REFERENCE GUIDE
 Learning Management System (LMS) Quick Tips Contents Process Overview... 2 Sign into the LMS... 3 Troubleshooting... 5 Required Software... 5 Mobile devices are not supported... 5 Using the Check System
Learning Management System (LMS) Quick Tips Contents Process Overview... 2 Sign into the LMS... 3 Troubleshooting... 5 Required Software... 5 Mobile devices are not supported... 5 Using the Check System
Windows 7 Hula POS Server Installation Guide
 Windows 7 Hula POS Server Installation Guide Step-by-step instructions for installing the Hula POS Server on a PC running Microsoft Windows 7 1 Table of Contents Introduction... 3 Getting Started... 3
Windows 7 Hula POS Server Installation Guide Step-by-step instructions for installing the Hula POS Server on a PC running Microsoft Windows 7 1 Table of Contents Introduction... 3 Getting Started... 3
How to easily clean an infected computer (Malware Removal Guide)
 How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
How to easily clean an infected computer (Malware Removal Guide) Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather
extranet.airproducts.com Windows XP Client Configuration
 extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
extranet.airproducts.com Windows XP Client Configuration To successfully connect to the Air Products extranet.airproducts.com website and have full functionality, the client computer needs to have the
Installing the Microsoft Network Driver Interface
 Installing the Microsoft Network Driver Interface Overview This guide explains how to install the PictureTel Live200 Microsoft Network Driver Interface (NDIS) software you have downloaded from PictureTel's
Installing the Microsoft Network Driver Interface Overview This guide explains how to install the PictureTel Live200 Microsoft Network Driver Interface (NDIS) software you have downloaded from PictureTel's
Welcome to EMP Monitor (Employee monitoring system):
 Welcome to EMP Monitor (Employee monitoring system): Overview: Admin End. User End. 1.0 Admin End: Introduction to Admin panel. Admin panel log in. Introduction to UI. Adding an Employee. Getting and editing
Welcome to EMP Monitor (Employee monitoring system): Overview: Admin End. User End. 1.0 Admin End: Introduction to Admin panel. Admin panel log in. Introduction to UI. Adding an Employee. Getting and editing
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access
 Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
Installation and Troubleshooting Guide for SSL-VPN CONNECTIONS Access Version 1 Revised 11/29/2007 Table of Contents Java Installation:...4 Browser Configuration:...4 Citrix Client Installation:...8 Attempting
NAS 253 Introduction to Backup Plan
 NAS 253 Introduction to Backup Plan Create backup jobs using Backup Plan in Windows A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Create backup
NAS 253 Introduction to Backup Plan Create backup jobs using Backup Plan in Windows A S U S T O R C O L L E G E COURSE OBJECTIVES Upon completion of this course you should be able to: 1. Create backup
User Guide for the Identity Shield
 User Guide for the Identity Shield Copyright Webroot SecureAnywhere User Guide for the Identity Shield January, 2013 2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and
User Guide for the Identity Shield Copyright Webroot SecureAnywhere User Guide for the Identity Shield January, 2013 2013 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and
Windows Server 2003 x64 with Symantec AntiVirus 10 Corporate Edition
 NC State University 1 of 5 Windows Server 2003 x64 with Symantec AntiVirus 10 Corporate Edition home download free antivirus now windows server 2003 x64 with symantec antivirus 10 corporate edition CAUTION:
NC State University 1 of 5 Windows Server 2003 x64 with Symantec AntiVirus 10 Corporate Edition home download free antivirus now windows server 2003 x64 with symantec antivirus 10 corporate edition CAUTION:
How to Install Windows 7 software
 Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
Connecting Windows 7 to the network This document outlines the procedure for setting up Windows 7 to use the College and University network. It assumes that the computer is set up and working correctly
McAfee Internet Security Suite Quick-Start Guide
 Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Enjoy a Worry Free Online Experience McAfee Internet Security Suite protects your PC, identity and online experience. It also includes PC and network tools, plus McAfee SiteAdvisor for safe surfing. Internet
Verizon Anti-Spyware 1 Introduction
 Verizon Anti-Spyware 1 Introduction Verizon Anti-Spyware provides real-time protection that runs transparently in the background to protect personal information and eliminate tracking software. When enabled,
Verizon Anti-Spyware 1 Introduction Verizon Anti-Spyware provides real-time protection that runs transparently in the background to protect personal information and eliminate tracking software. When enabled,
Student ANGEL FAQs. General Issues: System Requirements:
 Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
Student ANGEL FAQs General Issues: What is ANGEL? How do I log in? What is my username and password? How do I activate my account? I forgot my C number/password, what do I do? I registered after the first
ViRobot Desktop 5.5. User s Guide
 ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
ViRobot Desktop 5.5 User s Guide ViRobot Desktop 5.5 User s Guide Copyright Notice Copyright 2007 by HAURI Inc. All rights reserved worldwide. No part of this publication or software may be reproduced,
Sophos Enterprise Console Help. Product version: 5.1 Document date: June 2012
 Sophos Enterprise Console Help Product version: 5.1 Document date: June 2012 Contents 1 About Enterprise Console...3 2 Guide to the Enterprise Console interface...4 3 Getting started with Sophos Enterprise
Sophos Enterprise Console Help Product version: 5.1 Document date: June 2012 Contents 1 About Enterprise Console...3 2 Guide to the Enterprise Console interface...4 3 Getting started with Sophos Enterprise
The Peer Reviewer s Guide to Editorial Manager
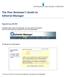 The Peer Reviewer s Guide to Editorial Manager Registering with EM The Register option is found in the main toolbar. New users simply click on REGISTER. [Note: You may have been proxy registered as a review
The Peer Reviewer s Guide to Editorial Manager Registering with EM The Register option is found in the main toolbar. New users simply click on REGISTER. [Note: You may have been proxy registered as a review
Hallpass Instructions for Connecting to Mac with a Mac
 Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Hallpass Instructions for Connecting to Mac with a Mac The following instructions explain how to enable screen sharing with your Macintosh computer using another Macintosh computer. Note: You must leave
Sophos Anti-Virus for Mac OS X Help
 Sophos Anti-Virus for Mac OS X Help For networked and standalone Macs running Mac OS X Product version: 9 Document date: June 2013 Sophos TOC 3 Contents About Sophos Anti-Virus...5 About the Scans window...5
Sophos Anti-Virus for Mac OS X Help For networked and standalone Macs running Mac OS X Product version: 9 Document date: June 2013 Sophos TOC 3 Contents About Sophos Anti-Virus...5 About the Scans window...5
Steps for using MagicConnect
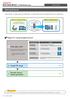 Getting Started Getting Started MagicConnect is a remote access service that allows you safe remote access to a target device from your remote device. What is a remote device? It is a Windows device, iphone/ipad,
Getting Started Getting Started MagicConnect is a remote access service that allows you safe remote access to a target device from your remote device. What is a remote device? It is a Windows device, iphone/ipad,
Portal Instructions for Mac
 Portal Instructions for Mac Table of Contents Introduction... 1 Preparing Safari... 2 Advanced Access Instructions... 3 Installing Java... 3 Setting the Default Browser... 3 Installing the Browser Plug-in...
Portal Instructions for Mac Table of Contents Introduction... 1 Preparing Safari... 2 Advanced Access Instructions... 3 Installing Java... 3 Setting the Default Browser... 3 Installing the Browser Plug-in...
Citrix Receiver 11.8 for Macintosh OS X
 1. Document Control Record Document title Document Owner Citrix Receiver 11.8 for Macintosh OS X Rayna McKinley 2. Issue and Amendment Record Issue Date Revised by Comments 1 8/15/2013 Rayna McKinley Original
1. Document Control Record Document title Document Owner Citrix Receiver 11.8 for Macintosh OS X Rayna McKinley 2. Issue and Amendment Record Issue Date Revised by Comments 1 8/15/2013 Rayna McKinley Original
Microsoft Security Essentials Installation and Configuration Guide
 Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
Microsoft Security Essentials Installation and Configuration Guide This installation guide is for users who are intending to download the software from Microsoft s web site. If you are not intending on
Introduction and Overview
 Inmagic Content Server Workgroup 10.00 Microsoft SQL Server 2005 Express Edition Installation Notes Introduction and Overview These installation notes are intended for the following scenarios: 1) New installations
Inmagic Content Server Workgroup 10.00 Microsoft SQL Server 2005 Express Edition Installation Notes Introduction and Overview These installation notes are intended for the following scenarios: 1) New installations
Adding Outlook to a Blackberry, Downloading, Installing and Configuring Blackberry Desktop Manager
 Adding Outlook to a Blackberry, Downloading, Installing and Configuring Blackberry Desktop Manager The following instructions work for the District provided Blackberrys from Sprint, but I think it should
Adding Outlook to a Blackberry, Downloading, Installing and Configuring Blackberry Desktop Manager The following instructions work for the District provided Blackberrys from Sprint, but I think it should
Sophos Anti-Virus for Windows, version 7 user manual. For Windows 2000 and later
 Sophos Anti-Virus for Windows, version 7 user manual For Windows 2000 and later Document date: August 2008 Contents 1 About Sophos Anti-Virus...3 2 Introduction to Sophos Anti-Virus...5 3 Checking the
Sophos Anti-Virus for Windows, version 7 user manual For Windows 2000 and later Document date: August 2008 Contents 1 About Sophos Anti-Virus...3 2 Introduction to Sophos Anti-Virus...5 3 Checking the
Cox Business Premium Security Service FAQs
 FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
FAQ s Content Cox Business Premium Security Service FAQs Questions before installing the software Q: Does Cox Business Premium Security Service work with other antivirus or firewall software installed
ONLINE BANKING - INTERNET BROWSER SETTINGS: COOKIES
 One of the biggest challenges in today s online banking landscape is the process to prevent unauthorized parties from accessing your personal online banking information. Because mal-ware, spy-ware, and
One of the biggest challenges in today s online banking landscape is the process to prevent unauthorized parties from accessing your personal online banking information. Because mal-ware, spy-ware, and
VIVIDESK Desktops can be accessed with a Macintosh Computer by one of two methods:
 VIVIDESK Desktops can be accessed with a Macintosh Computer by one of two methods: 1. If you have Macintosh OS version IX, then VIVIDESK is best viewed using Windows emulation software. 2. If you have
VIVIDESK Desktops can be accessed with a Macintosh Computer by one of two methods: 1. If you have Macintosh OS version IX, then VIVIDESK is best viewed using Windows emulation software. 2. If you have
Citrix Client Install Instructions
 Citrix Client Install Instructions If you are using Citrix remotely, Information Technology Services recommends updating Citrix client to the newest version available online. You must be an administrator
Citrix Client Install Instructions If you are using Citrix remotely, Information Technology Services recommends updating Citrix client to the newest version available online. You must be an administrator
Configuring VPN Using Windows XP
 Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
Configuring VPN Using Windows XP How to Create a VPN Connection What is VPN? Connecting to VPN Create a VPN Connection Connect to Your Work Computer Copying Files What is VPN? Virtual Private Networks
Chapter7 Setting the Receiving PC for Direct Upload. Setting the Receiving PC for Direct Upload... 148 For Windows... 148 For Macintosh...
 Chapter7 Setting the Receiving PC for Direct Upload Setting the Receiving PC for Direct Upload... 148 For Windows... 148 For Macintosh... 153 Setting the Receiving PC for Direct Upload This section explains
Chapter7 Setting the Receiving PC for Direct Upload Setting the Receiving PC for Direct Upload... 148 For Windows... 148 For Macintosh... 153 Setting the Receiving PC for Direct Upload This section explains
System Administrator Guide
 System Administrator Guide Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 3.5 Webroot AntiSpyware Corporate Edition System Administrator Guide Version 3.5 2007 Webroot Software,
System Administrator Guide Webroot Software, Inc. PO Box 19816 Boulder, CO 80308 www.webroot.com Version 3.5 Webroot AntiSpyware Corporate Edition System Administrator Guide Version 3.5 2007 Webroot Software,
Windows XP with Symantec AntiVirus 10 Corporate Edition
 NC State University 1 of 7 Windows XP with Symantec AntiVirus 10 Corporate Edition home download free antivirus now windows xp with symantec antivirus 10 corporate edition Install SAV10 on Windows XP only
NC State University 1 of 7 Windows XP with Symantec AntiVirus 10 Corporate Edition home download free antivirus now windows xp with symantec antivirus 10 corporate edition Install SAV10 on Windows XP only
IIS, FTP Server and Windows
 IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
Contents. VPN Instructions. VPN Instructions... 1
 VPN Instructions Contents VPN Instructions... 1 Download & Install Check Point VPN Software... 2 Connect to FPUA by VPN... 6 Connect to Your Computer... 8 Determine Your Machine Type... 10 Identify 32-bit
VPN Instructions Contents VPN Instructions... 1 Download & Install Check Point VPN Software... 2 Connect to FPUA by VPN... 6 Connect to Your Computer... 8 Determine Your Machine Type... 10 Identify 32-bit
How to remotely access your Virtual Desktop from outside the college using VMware View Client. How to guide
 How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
How to remotely access your Virtual Desktop from outside the college using VMware View Client How to guide Author: ICT Services Version: 1.0 Date: November 2015 Contents What is the VMware View Client?...
Those who wish to remotely log on to a Pepperdine Windows desktop computer will also need to have these instructions with them when they connect.
 Using Microsoft s Remote Desktop Connection (RDC) program, Pepperdine faculty and staff who use Macintosh and Windows computers can log on to Pepperdine s Remote Access Server (remoteaccess.pepperdine.edu)
Using Microsoft s Remote Desktop Connection (RDC) program, Pepperdine faculty and staff who use Macintosh and Windows computers can log on to Pepperdine s Remote Access Server (remoteaccess.pepperdine.edu)
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Configuring Thunderbird for Flinders Mail at home.
 Configuring Thunderbird for Flinders Mail at home. Downloading Thunderbird can be downloaded from the Mozilla web site located at http://www.mozilla.org/download.html This web site also contains links
Configuring Thunderbird for Flinders Mail at home. Downloading Thunderbird can be downloaded from the Mozilla web site located at http://www.mozilla.org/download.html This web site also contains links
Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18
 Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Mercy s Remote Access Instructions
 Mercy s Remote Access Instructions ~~~~~~~~~~~~~~ Section A Windows 2000 / XP ~~~~~~~~~~~~~~ I. Install Meditech............................... A1 II. Install VPN Client............................. A3
Mercy s Remote Access Instructions ~~~~~~~~~~~~~~ Section A Windows 2000 / XP ~~~~~~~~~~~~~~ I. Install Meditech............................... A1 II. Install VPN Client............................. A3
iprint For Apple Computers
 iprint For Apple Computers Note: If you experience difficulties or are not comfortable installing the iprint drivers, please visit the TAC located in Randall Library for assistance IMPORTANT: If you have
iprint For Apple Computers Note: If you experience difficulties or are not comfortable installing the iprint drivers, please visit the TAC located in Randall Library for assistance IMPORTANT: If you have
16.4.3 Lab: Data Backup and Recovery in Windows XP
 16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
16.4.3 Lab: Data Backup and Recovery in Windows XP Introduction Print and complete this lab. In this lab, you will back up data. You will also perform a recovery of the data. Recommended Equipment The
Installing TestNav Mac with Apple Remote Desktop
 Installing TestNav Mac with Apple Remote Desktop 1 2 3 Getting TestNav Installation from Servicedesk 1.1 Connect to Servicedesk 4 1.2 Download Package to Desktop 7 Installing TestNav 2.1 Add Computers
Installing TestNav Mac with Apple Remote Desktop 1 2 3 Getting TestNav Installation from Servicedesk 1.1 Connect to Servicedesk 4 1.2 Download Package to Desktop 7 Installing TestNav 2.1 Add Computers
NS Financials. Client Platform Guide for Mac Using Safari Incl Citrix Setup As A Local Client
 NS Financials Client Platform Guide for Mac Using Safari Incl Citrix Setup As A Local Client This document describes how to access the NS Financials system through Safari on an Apple Mac and outlines the
NS Financials Client Platform Guide for Mac Using Safari Incl Citrix Setup As A Local Client This document describes how to access the NS Financials system through Safari on an Apple Mac and outlines the
ACCOUNT SERVICES HELP
 ACCOUNT SERVICES HELP 1. How do I create an on line account? Before you can view your on line account information you first need to register a username profile. You do this by clicking on the Register
ACCOUNT SERVICES HELP 1. How do I create an on line account? Before you can view your on line account information you first need to register a username profile. You do this by clicking on the Register
Sophos Anti-Virus for Mac OS X Help
 Sophos Anti-Virus for Mac OS X Help For networked and standalone Macs running Mac OS X version 10.4 or later Product version: 8 Document date: April 2012 Contents 1 About Sophos Anti-Virus...3 2 Scanning
Sophos Anti-Virus for Mac OS X Help For networked and standalone Macs running Mac OS X version 10.4 or later Product version: 8 Document date: April 2012 Contents 1 About Sophos Anti-Virus...3 2 Scanning
Introduction to Computer Security Table of Contents
 Introduction to Computer Security Table of Contents Introduction... 2 1 - Viruses... 3 Virus Scanners... 3 2 - Spyware... 7 Spyware Scanners... 8 3 - Firewalls... 10 Windows Firewall... 10 4 - References...
Introduction to Computer Security Table of Contents Introduction... 2 1 - Viruses... 3 Virus Scanners... 3 2 - Spyware... 7 Spyware Scanners... 8 3 - Firewalls... 10 Windows Firewall... 10 4 - References...
Computer Science and Engineering MacOS Cisco VPN Client Installation and Setup Guide
 Computer Science and Engineering MacOS Cisco VPN Client Installation and Setup Guide Contents Installation: For users who have no prior Cisco VPN Client Installed... 2 Profile Import:... 4 Usage:... 4
Computer Science and Engineering MacOS Cisco VPN Client Installation and Setup Guide Contents Installation: For users who have no prior Cisco VPN Client Installed... 2 Profile Import:... 4 Usage:... 4
Dial Up Config & Connecting Instructions with Graphics
 Dial Up Config & Connecting Instructions with Graphics Dial Up Config & Connecting Below are the Basic Manual Configurations Connecting to the Internet for the following operating systems: Windows 2000
Dial Up Config & Connecting Instructions with Graphics Dial Up Config & Connecting Below are the Basic Manual Configurations Connecting to the Internet for the following operating systems: Windows 2000
How to Configure Sophos Anti-Virus for Home Systems
 How to Configure Sophos Anti-Virus for Home Systems When you download and install Sophos on your home computer, on-access scanning is enabled. However, the settings for scheduled scans and scanning for
How to Configure Sophos Anti-Virus for Home Systems When you download and install Sophos on your home computer, on-access scanning is enabled. However, the settings for scheduled scans and scanning for
Computing Guide. How to set up McAfee virus scanning software and become computer virus savvy
 Computing Guide THE LIBRARY www.salford.ac.uk/library How to set up McAfee virus scanning software and become computer virus savvy A virus infection of your workstation can seriously disrupt your learning,
Computing Guide THE LIBRARY www.salford.ac.uk/library How to set up McAfee virus scanning software and become computer virus savvy A virus infection of your workstation can seriously disrupt your learning,
Important Notes for WinConnect Server ES Software Installation:
 Important Notes for WinConnect Server ES Software Installation: 1. Only Windows 8/8.1 Enterprise, Windows 8/8.1 Professional (32-bit & 64-bit) or Windows Server 2012 (64-bit) or Windows Server 2012 Foundation
Important Notes for WinConnect Server ES Software Installation: 1. Only Windows 8/8.1 Enterprise, Windows 8/8.1 Professional (32-bit & 64-bit) or Windows Server 2012 (64-bit) or Windows Server 2012 Foundation
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link:
 TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
TSM for Windows Installation Instructions: Download the latest TSM Client Using the following link: ftp://ftp.software.ibm.com/storage/tivoli-storagemanagement/maintenance/client/v6r2/windows/x32/v623/
Setting up a Virtual Private Network (VPN) connection Windows 8
 Setting up a Virtual Private Network (VPN) connection Windows 8 A Virtual Private Network (VPN) is best described as a tunnel to MAASnet, the university network. After having configured the VPN connection,
Setting up a Virtual Private Network (VPN) connection Windows 8 A Virtual Private Network (VPN) is best described as a tunnel to MAASnet, the university network. After having configured the VPN connection,
MyNetFone Virtual Fax. Virtual Fax Installation
 Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Table of Contents MyNetFone Virtual Fax MyNetFone Virtual Fax Installation... 1 Changing the SIP endpoint details for the fax driver... 11 Uninstalling Virtual Fax... 13 Virtual Fax Installation Follow
Connecting to LRDC Fileserver Remotely Using Windows Vista/7 & SRemote VPN
 Connecting to LRDC Fileserver Remotely Using Windows Vista/7 & SRemote VPN October 2013 In order to access the LRDC file server remotely/off campus, or from Wireless Pittnet, you must first authenticate
Connecting to LRDC Fileserver Remotely Using Windows Vista/7 & SRemote VPN October 2013 In order to access the LRDC file server remotely/off campus, or from Wireless Pittnet, you must first authenticate
IsItUp Quick Start Manual
 IsItUp - When you need to know the status of your network Taro Software Inc. Website: www.tarosoft.com Telephone: 703-405-4697 Postal address: 8829 110th Lane, Seminole Fl, 33772 Electronic mail: Contact1@tarosoft.com
IsItUp - When you need to know the status of your network Taro Software Inc. Website: www.tarosoft.com Telephone: 703-405-4697 Postal address: 8829 110th Lane, Seminole Fl, 33772 Electronic mail: Contact1@tarosoft.com
Florida Atlantic University VPN Client Installation Guide
 Florida Atlantic University VPN Client Installation Guide VPN Client Installation Guide Page 1 Cisco VPN Client Installation Guide Please read the instructions below to assist with the process of downloading,
Florida Atlantic University VPN Client Installation Guide VPN Client Installation Guide Page 1 Cisco VPN Client Installation Guide Please read the instructions below to assist with the process of downloading,
Virtual Owl. Guide for Windows. University Information Technology Services. Training, Outreach, Learning Technologies & Video Production
 Virtual Owl Guide for Windows University Information Technology Services Training, Outreach, Learning Technologies & Video Production Copyright 2015 KSU Division of University Information Technology Services
Virtual Owl Guide for Windows University Information Technology Services Training, Outreach, Learning Technologies & Video Production Copyright 2015 KSU Division of University Information Technology Services
Table of Contents. 1. Overview... 3. 1.1 Materials Required. 3 1.2 System Requirements. 3 1.3 User Mode 3. 2. Installation Instructions..
 Table of Contents 1. Overview..... 3 1.1 Materials Required. 3 1.2 System Requirements. 3 1.3 User Mode 3 2. Installation Instructions.. 4 2.1 Installing the On Call Diabetes Management Software. 4 2.2
Table of Contents 1. Overview..... 3 1.1 Materials Required. 3 1.2 System Requirements. 3 1.3 User Mode 3 2. Installation Instructions.. 4 2.1 Installing the On Call Diabetes Management Software. 4 2.2
Team Foundation Server 2013 Installation Guide
 Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
Team Foundation Server 2013 Installation Guide Page 1 of 164 Team Foundation Server 2013 Installation Guide Benjamin Day benday@benday.com v1.1.0 May 28, 2014 Team Foundation Server 2013 Installation Guide
SOS SO S O n O lin n e lin e Bac Ba kup cku ck p u USER MANUAL
 SOS Online Backup USER MANUAL HOW TO INSTALL THE SOFTWARE 1. Download the software from the website: http://www.sosonlinebackup.com/download_the_software.htm 2. Click Run to install when promoted, or alternatively,
SOS Online Backup USER MANUAL HOW TO INSTALL THE SOFTWARE 1. Download the software from the website: http://www.sosonlinebackup.com/download_the_software.htm 2. Click Run to install when promoted, or alternatively,
