Hardware security Part 1: Smartcards and other tamper-resistant modules
|
|
|
- Vivian Ramsey
- 9 years ago
- Views:
Transcription
1 Hardware security Part 1: Smartcards and other tamper-resistant modules Markus Kuhn Computer Laboratory mgk25/ Tamper-resistant modules 1) Single chip systems Consist of a microcontroller that contains the entire CPU, system bus, communication interface, firmware and non-volatile memory on a single chip. Examples: smartcards, SIMs, proximity cards, dongles. Advantages: small low cost easy to handle with standard production technologies Disadvantages: limited capacity no continuous power source for alarm mechanisms access feasible with skillful use of semiconductor test equipment 3 Applications of Tamper Resistant Modules Some Pay TV Pirate Devices Security of cryptographic applications is based on secure storage of secret keys and unobservability of computation Distributed and mobile applications allow attacker full physical access to hardware over extended period of time pay TV access control electronic purses financial transaction terminals anti theft protection authentic telemetry protection of algorithms "Battery powered smartcard", Megasat Bochum Conductive silver ink attack on BSkyB P10 card (top), with card CPU replaced by external DS5002FP (right) software copy protection cellular phones prepayment meters... 2 BSkyB P9 deactivation blocker ISO 7816 to RS 232 adapter (Season7) 4
2 Classes of Attacks on Security Modules Preparation II: Bonding into a Test Package Microprobing Open the package, access the chip surface with semiconductor test equipment, and observe and manipulate the internal data paths Software Attacks Use the normal communication interface and abuse security vulnerabilities found in the protocols, cryptographic algorithms, or their implementation Eavesdropping Without opening the package, try to get access to protected information by analyzing compromising signals in emanated electromagnetic radiation, supply current fluctuations, leakage currents on signal lines, and protocol timings Fault Generation Provoke malfunctions by operating the device under environmental stress conditions such as high/low temperature, supply voltage variations and spikes, clock phase jumps, ionising radiation, protocol violations, partial resets, etc. 5 A manual bonding station establishes reliable contacts to the supply, communication, and test pads of the microprocessor using ultrasonic welding of a fine aluminium wire. 7 Preparation I: Depackaging the Processor Optical Reverse Engineering of VLSI Circuits VCC A B A B B B A B polysilicon metal n well dopant areas GND A A 1) 2) Heat up card plastic, bend it, and remove chip module Dissolve package in 60 C fuming nitric acid, then wash in acetone, deionized water, and finally isopropanol. The etching should be carried out under very dry conditions. 6 VCC B B A GND A A B A B Confocal microscopes represent the different chip layers in different colors. In the right image, the metal interconnects have been removed with hydrofluoric acid. Both images together can be read almost as easily as a circuit diagram. 8
3 Optical Access to Diffusion Layer ROM Content UV Read out of Standard Microcontrollers UV light EEPROM Security Fuse After all covering layers including the surrounding field oxide have been removed with hydrofluoric acid, the shape of the now visible diffusion areas will reveal the ROM content (here 16x10 bits). polysilicon row access line metal column access line ground connection 9 Many microcontrollers have an EEPROM security fuse located outside the EEPROM program memory. Open chip package Cover program memory with opaque material Reset security fuse in UV EPROM eraser Access memory with program/verify commands 11 Optical Reconstruction of Ion Implantation ROM Content Access to CPU Bus via Laser Depassivation and Microprobing View of ROM with polysilicon intact Diffusion layer after crystallographic etch This type of ROM does not reveal the bit pattern in the shape of the diffusion areas, but a crystallographic staining technique (Dash etchand) that etches doped regions faster than undoped regions will still show the ROM bits. 10 Top: A complete microprobing station consisting of a micro scope (Mitutoyo FS 60), laser cutter (New Wave QuikLaze), four micropositioners (Karl Suss), CCD camera, PC with DSP card for card protocol interface handling and data acquisition, oscilloscope, pattern generator, power supply, logic analyzer, etc. Right: Eight depassivated data bus lines. Photos: ADSR 12
4 Laser cutter as a powerful reverse engineering tool Microprobing Access to All Memory Locations Passively monitoring and recording all memory bus accesses might not be sufficient to attack all applications. Carefully designed smartcard software makes it difficult to trigger memory accesses to all secrets in a laboratory. Card software that calculates a full memory checksum after each reset simplifies attacks considerably! Solution for Attacker: Abuse existing processor hardware as an address generator that accesses Local removal of passivation layer with <1 µm precision (355 nm UV light) all memory locations predictably. A single probing needle can now capture all memory values, probing one bus line at a time. Removal of oxide (532 nm green light) Options: Exposure of lower metal layers for probing Disable instruction decoder, such that no JMP/CALL/RET/HALT instructions Cuts in metal and polysilicon lines (532 nm) Order of magnitude less expensive than FIB Photos: New Wave Research are executed (preferably only NOP like instructions should be allowed). Disable program counter load gate In many smartcard processors, this can be accomplished with just a single probe! Focused Ion Beam Workstations for IC Modification Restricted Program Counter A standard program counter mechanism is too easily abused as an address sequence generator. Tamper resistant design of the instruction decoder is difficult. Watchdog circuitry requires many transistors and simple forms are also easily disabled. Solution: Replace the normal program counter (e.g., 16 bit) by a combination of a full size segment register S and a short (e.g., 7 bit) offset register O. Instructions are fetched from address S+O. Only O is automatically incremented after every instruction. An overflow Focused ion beam machines make high resolution of O will halt the processor. images of chip structures and allow us to both remove and deposit materials (metal and insulators) with 0.01 µm resolution. Gallium ions are accelerated with 30 kv and process gases like iodine or an organo A jump to address X is performed by loading X into S and setting O to zero. Unconditional jump commands must be less than 128 bytes apart, which an assembler preprocessor used by the developer can ensure automatically. metallic compound are injected near the target location. Left Photo: Dept. of Material Sciences, University of Cambridge 14 Now, no simple FIB edit can cause the program counter to cover all addresses. 16
5 Example of a Top Layer Sensor Mesh SENSE VCC Power Supply Current Forms a Significant Covert Channel Record current in VCC/GND connection with 12 bit, 30 MHz ADC, in order to reconstruct executed instruction sequence and observe cryptographic computations. Instruction 1: CLR C Instruction 2: XOR B Instruction 3: ST16SF48A GND SENSE The sensor line is checked during operation for interruptions or short circuits, which trigger alarms (e.g., processor halt or flash erase). The power lines are at some places used to supply the circuits below. 17 Characteristic current spikes can identify executed instruction Data values appear in power profiles either as differential Hamming weights (~0.5 1 ma/bit) or as individual bits, e.g. with multiplication or shift instructions Current signature depends on accessed memory type (SRAM write short circuit, EEPROM read out amplifier, etc.) Activation of EEPROM programming voltage charge pump observable, which allows to abort before state changes (e.g., with bad retry counters) 19 Sensor Meshes: Vulnerabilities and Attacks Change single instructions by signal glitches VCC CLK RST a) b) a) b) c) FIB workstation can be used to place a new via between mesh lines with an access cross on top for easy microprobing. Design flaw: redundant bus lines extend beyond the sensor mesh, allowing easy microprobing access ("Freedom for imprisoned crypto bits!"). Not all power supply lines are used, so they can be removed with a laser cutter to allow access to signals below the mesh. c) 18 Fault model: R Links between transistors form RC delay elements R and C vary between links and individual chips Maximum RC of any link determines maximum CLK frequency RST signal sometimes not latched, which allows partial resets Transistors compare VCC and V C, which allows VCC glitches C 20
6 Glitch attack on an output loop Typical data output routine in security software: 1 b = answer_address 2 a = answer_length 3 if (a == 0) goto 8 4 transmit(*b) 5 b = b a = a 1 7 goto Cause CLK or VCC glitch when instruction 3 or 6 is being fetched, in order to extend loop length to send additional memory content to port. 21 Tamper-resistant modules 2) Secure packages A security shield encloses an entire printed circuit board. The only non-volatile memory is battery-backed static RAM (SRAM). The alarm mechanism, when triggered, shortcuts the SRAM power supply, thereby erasing the confidential data. Advantages: fairly high security Disadvantages: more complex to manufacture no ventilation power limits only macroscopic mechanic security 23 Destruction of Test Circuitry ibuttons An Alternative Tamper Resistant Module Form Attackers and test engineers share similar interests. Both need easy access to the on chip bus lines with as few probes as possible. Commonly used test circuitry: Parallel/serial converters for full bus Full bus available on large probing pads Pads usually disabled by blowing a poly fuse, but can easily be reconnected via FIB. Solution: Test circuitry must not only be disabled by blowing fuses. It must be structurally destroyed. Test circuitry can be located on the µm wide area between the dies that is removed during wafer cutting. Blown polysilicon fuse near test pad (Motorola) stainless steel can battery for >10 years processor multi layer circuit board clock crystal battery buffered on chip SRAM sealed steel can provides mechanical stability and EMI shielding, which allows very sensitive alarm mechanisms multiple layers of sensor wires on chip and in circuit board chip layout facing circuit board difficult to open can without interrupting battery voltage pressurized with nitrogen 22 24
7 Tamper-resistant modules 3) Bus encryption The CPU chip incorporates a unit that encrypts both the data and address bus. The secret key used is stored on the CPU chip in a batterybacked SRAM register. External memory contains only encrypted data that is decrypted when fetched into the CPU cache. Advantages: no capacity limit SRAM registers are difficult to access for attackers simple to manufacture (no off-chip alarm envelope) can easily be combined with a secure package Disadvantages: design tradeoff between good cryptography and low bus latency traces of external memory accesses lead to information leaks 25 Details: M.G. Kuhn: Cipher instruction search attack on the bus-encryption security microcontroller DS5002FP. IEEE Trans. on Computers 47(10), October 1998, pp Classification of Attackers Class I: Class II: Class III: Clever Outsiders. Often very intelligent, have insufficient knowledge of the system, have access to moderately sophisticated equipment, use existing weaknesses in the system. Knowledgeable Insiders. Substantial specialized technical education and experience, varying degrees of understanding of the system but potential access to most relevant information, often highly sophisticated tools. Funded Organizations. Teams of specialists with complementary skills, great funding resources, capable of in depth analysis and design of sophisticated attacks, most advanced tools, access to knowledgeable insiders. [according to Abraham, Dolan, Double, Stevens: Transaction Security System, IBM Systems Journal, Vol. 30, No. 2, 1991.] 26 28
8 Tamper Resistance versus Tamper Evidence Invasive attacks Microprobing FIB editing Layout reconstruction violate tamper resistance requirement (FIPS 1 1 Level 4) Require between hours and weeks in a specialized laboratory, therefore the owner of the card is likely to notice the attack and can revoke certificates for keys that might be lost. Non invasive attacks Glitch attacks Power analysis Software vulnerabilities violate in addition tamper evidence requirement (FIPS 1 1 Level 2) Can be performed within a few seconds inside a Trojan terminal in a Mafia owned shop, therefore card owner will not notice that card secrets have been stolen and will not revoke keys. 29 Summary and conclusions With sufficient effort, invasive techniques may extract all data from microcontrollers and smartcard CPUs. Obfuscated chip design remains standard security technique for single-chip systems without active alarms. Non-invasive attacks (glitching, power analysis) are the main concern in tamper-evidence applications (access control, banking, signatures), where compromised keys affect only individual users or accounts and can be revoked easily. The smartcard form factor may be unsuitable for applications with strong tamper-resistance requirements (e.g., pay-tv conditional access, digital restrictions management) batterybacked SRAM with active alarms Extremely careful engineering needed to design tamper-evident single-chip systems without active alarms. 30
9 Hardware security Part 2: Electromagnetic eavesdropping on computers Markus Kuhn Computer Laboratory Military History of Side-Channel Attacks 1915: WW1 ground-return current tapping of field telephones. 1960: MI5/GCHQ find high-frequency plaintext crosstalk on encrypted telex cable of French embassy in London. Since 1960s: Secret US government TEMPEST programme investigates electromagnetic eavesdropping on computer and communications equipment and defines Compromising Emanations Laboratory Test Standards (NACSIM 5100A, AMSG 720B, etc. still classified today). Military and diplomatic computer and communication facilities in NATO countries are today protected by red/black separation shielding of devices, rooms, or entire buildings. US market for TEMPEST certified equipment in 1990: over one billion dollars annually. 3 Early use of compromising emanations R1250 Wideband Tempest Receiver The German army started in 1914 to use valve amplifiers for listening into ground return signals of distant British, French and Russian field telephones across front lines [Bauer, 1999]. 2 4
10 Wideband Tempest Measurement Receivers Can be tuned continuously from 100 Hz to 1 GHz. Offers 21 bandwidths from 50 Hz to 200 MHz (1-2-5 steps). For comparison: AM radio: 2 10 khz FM radio: 200 khz TV set: 6 MHz Especially robust antenna input (for listening on power lines). Gain adjustable by a factor of Automatic gain control circuit can be deactivated. Demodulators: AM linear, AM logarithmic, FM, BFO. Export controlled products, k. Second hand offers on Internet for < 1 k 5 pulse 20 MHz 10 MHz 5 MHz 2 MHz 1 MHz Receiving impulse signals IF impulse response µs µs impulse width = 1 bandwidth AM impulse responses 7 Intermediate frequency bandwidth R MHz IF filter characteristic 20 MHz 10 MHz 5 MHz 2 MHz 1 MHz mv MHz 6 8
11 Video Timing The electron beam position on a raster-scan CRT is predictable: Real-world VGA card pixel shapes Video graphics adapter pixel shapes Pixel frequency: f p Deflection frequencies: x t Matrox Millennium II (157.5 MHz) ATI 3D Rage Pro (157.5 MHz) Toshiba 4CDX (49.5 MHz) f h = f p x t, f v = f p x t y t Pixel refresh time: y d display area x d y t mv t = x f p + y f h + n f v The 43 VESA standard modes specify f p with a tolerance of ±0.5% ModeLine "1280x1024@85" Image mostly stable if relative error of f h below ns 9 11 AM audio broadcast from CRT displays Real-world VGA card frequency spectrum s(t) = A cos(2πf c t) [1 + m cos(2πf t t)] 300 and 1200 Hz tones at f c = 1.0 MHz: 10 1 Video graphics adapter signal spectra (100 khz bandwidth) Matrox Millennium II (157.5 MHz) ATI 3D Rage Pro (157.5 MHz) Toshiba 4CDX (49.5 MHz) 10 0 mv 10 1 Play your MP3 music at home via CRT emanations in your AM radio: MHz 12
12 Eavesdropping of CRT Displays CRT Monitor amplifies with 100 MHz bandwidth the video signal to 100 V and applies it to the screen grid in front of the cathode to modulate the e-beam current. All this acts together with the video cable as a (bad) transmission antenna. Test text used in the following experiments: Magnified example of eavesdropped text Test text on targeted CRT: Rasterized output of AM demodulator at 480 MHz center frequency: Characteristics: Vertical lines doubled Horizontal lines disappear (reduced to end points) Glyph shapes modified, but still easily readable unaided 13 Pixel frequency: 50 MHz, IF bandwidth: 50 MHz, AM baseband sampling frequency: 500 MHz, measured peak e-field at 3 m: 46 db/m, corresponds to 12 nw EIRP. [Kuhn, 2003] MHz center frequency, 50 MHz bandwidth, 256 (16) frames averaged, 3 m distance 55 Steganographic transmission of images The user sees on her screen: MHz center frequency, 50 MHz bandwidth, magnified image section AM receiver bandwidth equal to eavesdropped pixel rate distinguishes individual pixels
13 The radio frequency eavesdropper receives instead: 445 MHz center frequency, 10 MHz bandwidth, 1024 frames averaged, 3 m distance Filtered fonts as a protection measure (1) (2) (3) (4) (5) (6) (7) (8) The above lines show (1) bi-level text, (2) anti-aliased text, (3) anti-aliased text without hinting, (4 7) anti-aliased text lowpass filtered to remove to 20, 30,, and 50 % of the spectrum [0, f p /2], respectively. Font: Microsoft s Arial (TTF), rendered at 12 pixels-per-em. [Kuhn, 2003] 19 Amplitude modulation of dither patterns Filtered fonts on the CRT screen Hidden analog transmission of text and images via the compromising emanations of a video display system can be achieved by am plitude modulation of a dither pattern in the displayed cover image. Cover image C x,y,c, embedded image E x,y, all normalized to [0,1]. Then screen display is (1) (2) (3) (4) (5) (6) (7) (8) S x,y,c = ( C γ x,y,c + min{αe x,y, C γ x,y,c, 1 C γ x,y,c} d x,y ) 1/ γ with dither function d x,y = 2[(x + y) mod 2] 1 { 1, 1} and 0 < α
14 bi level antialiased unhinted 20 % 30 % % 50 % Received radio signal 7 MHz center freq., 200 MHz bandwidth, 256 frames averaged, 3 m distance Eavesdropping on flat panel displays 350 MHz center frequency, 50 MHz bandwidth, 16 (1) frames averaged, 3 m distance background Filtered fonts peak-amplitude comparison magnified image section Peak voltages (antenna rms voltage equiv. at DC free AM output) 120 bi level antialiased unhinted 20 % 30 % % % background Removing the top 30 % of the spectrum reduces peak emissions by 12 db, without significantly affecting user comfort. This means the eavesdropper has to come 3 closer, into a 10 smaller area. 22 Horizontal lines intact ( no analog video signal) Horizontal resolution reduced 100 signal amplitude at receiver input (rms equiv.) 57 db/m (50 MHz BW) field strength at 3 m distance equivalent isotropic radiated power around 150 nw Target display: Toshiba 4CDX laptop, @75Hz, f p = 50 MHz 24
15 Eavesdropping across two office rooms 350 MHz, 50 MHz BW, 12 frames (160 ms) averaged Minimal/maximal reception contrast 350 MHz center frequency, 50 MHz bandwidth, 16 frames averaged, 3 m distance Target and antenna in a modern office building 10 m apart, with two other offices and three plasterboard walls ( 2.7 db each) in between. Single-shot recording of 8 megasamples with storage oscilloscope at 50 Msamples/s, then offline correlation and averaging of 12 frames : black on white text, 2: maximum-contrast bit patterns fg= and bg= in all channels, 3: same but out of phase across channels, 4 6: different attempts to find minimumcontrast colour combination by shifting edges between channels, 7 9: make the least significant bits random in each channel. 27 FPD-Link a digital video interface Only random bit jamming effective LCD module and video controller are connected in Toshiba 4CDX laptop by eight twisted pairs (each 30 cm long), which feed the 18- bit RGB parallel signal through the hinges via low-voltage differential signaling (LVDS, EIA-644). 25 MHz cycle 285 MHz center frequency, 50 MHz bandwidth, 16 frames averaged, 3 m distance channel 1 r2 g2 r7 r6 r5 r4 r3 r2 g2 r channel 2 g3 b3 b2 g7 g6 g5 g4 g3 b3 b2 30 channel 3 b4 cx cy cz b7 b6 b5 b4 cx cy clock FPD-Link chipset: NEC DS90CF
16 Random LSB jamming Random bits can be added to a text image to generate a phase-locked jamming signal that cannot be averaged away by an attacker. Considerations: Foreground/background colors with equal number of bit transitions. Randomize less significant bits of each color channel. These random bits must only be changed when the text changes: Changing the random bits continuously (like TV noise) would help the attacker to average away the jamming signal. Not changing the random bits when the text changes would help the attacker to average away the text and obtain this way a copy of the random signal that can then be subtracted from the received signal. Independent noise bits must be used for each occurrence of a character. Beware of glyph caches from which the same bitmap might be used several times. Open research question: How to jam without leaking update rate of displayed text? 29 Time-domain observation of CRT light Overall light emitted by CRT is proportional to (gamma corrected) video signal v γ (t) convolved with phosphor impulse response P(t): I(t) = 0 v γ (t t ) P(t ) dt What does the impulse response curve of commonly used CRT phosphors look like? Does it have very fast decay components that preserve the high-frequency areas of the video signal spectrum? Are practically usable light sensors available to detect these? What limits are there and is this a practical risk? What countermeasures are there? 31 Structure of compromising video signals Mathematical tools: Fourier transform: time domain frequency domain Convolution theorem: multiplication in time domain is convolution in frequency domain, and vice versa. Sampling theorem: Sampled time-domain signal is periodic in the frequency domain, and vice versa. Result: Symmetric spectrum of digital 2-color video signal repeats itself at frequency intervals f p Amplitudes of the individual repetitions of the spectrum are predicted by the difference between the DFTs of the two color code words used. Eavesdropping colors can be optimized to place signal energy into quiet part of UHF radio spectrum. Details: M. Kuhn, Technical Report UCAM-CL-TR-577, Requirements: Light sensors very sensitive (to reduce preamp noise) very fast (bandwidth comparable to f p /2, ideally >100 MHz or <5 ns rise and fall time) Options: PIN photodiode (typical sensitivity A/W, µs ns) Avalanche photodiode (internal gain, typical sensitivity 10 2 A/W, < 1 ns raise/fall time) Photomultiplier tube (significant internal gain, typical sensitivity A/W, < 1 ns raise/fall time) 32
17 The photomultiplier tube (PMT) Choice: Hamamatsu H Photomultiplier tube module with integrated high-voltage circuit allows easy operation from 12 V lab power supply. Control voltage 0.25 < U c < 0.9 V adjusts radiant sensitivity to ( ) Uc A/W 1 V Thanks to high internal gain no need for video pre-amplifier, allowing direct connection to 50 Ω DC input of digital storage oscilloscope. Modeling phosphor impulse responses Exponential decay curve of a typical phosphorescent substance: Note that this is for τ = 1 2πf = RC I e (t) = I 0 e t τ the impulse response of a firstorder Butterworth low-pass filter. R C Uout Power-law decay curve of zinc-sulfide based phosphors: I p (t) = U in I 0 (t + α) β. (Results in asymptotically straight line on loglog scale.) Measured phosphor decay curves (a) Emission decay of a single pixel (f p = 36 MHz) Double-log plot of reconstructed P22 impulse response µw/sr µw/sr WV 1 s 1 sr µs µs The sensor output voltage is shown here as the equivalent radiant intensity (power per solid angle) of the light source white blue green red s 36
18 Test image shown on target monitor High-pass filtering result First-order Butterworth high-pass filter applied, 3 db cutoff at 4 MHz Rasterized raw signal from PMT Deconvolution result VESA mode 6 480@85 Hz, 8-bit sampled at 250 MHz, 256 frames (3.0 s, 753 MB) averaged, scaled to 0.1% saturation 38
19 Deconvolution We can model highly accurately the sensor signal blurred by the phosphor afterglow as the convolution of the beam current v γ and the impulse-response function P P22 I(t) = 0 v γ (t t ) P P22 (t ) dt which a Fourier transform turns into a multiplication of frequencydomain signals: F{I} = F{ṽ γ } F{P P22 }. Deconvolution can be accomplished simply by division in the frequency domain, followed by an inverse FFT, leading to the shown estimate of the original beam current: ṽ γ = F 1 { F{I} F{P P22 } } 41 Conclusions (optical) It is feasible to reconstruct the image displayed on a raster screen CRT from the emitted light, even after diffuse reflection. A sufficiently dark environment (i.e., after sunset) is needed to avoid shot noise dominating the signal. Etched/frosted/milky window glass does not necessarily prevent readability of CRT displays at a distance. Off-the-shelf equipment sufficient for a lab demonstration. Real-world attacks will require specially designed receivers and patience. The threat level seems roughly comparable to that of compromising radio-frequency emanations. 43 Other compromising emanations New forms of compromising emanations are still being discovered: Acoustic eavesdropping on keyboards Like a drum changes its sound, depending on where it is hit, the main board of a keyboard is excitied into different modes of vibration, depending on the location of the key being hit. Asonov and Agrawal have demonstrated that it is practical to train a neural network to distinguish keystrokes based on this effect. D. Asonov, R. Agrawal: Keyboard acoustic emanations. Proceedings 2004 IEEE Symposium on Security and Privacy, IEEE Computer Society, pp Ultrasonic CPU emanations from PC motherboards Shamir and Tromer have presented preliminary results that show that the run-time of certain cryptographic loops appears in the spectrum of microphone signals recorded near a PC motherboard. It appears as if the CPU current fluctuations are emitted by blocking capacitors or other power-supply componenets as acoustic and ultrasonic waves. A. Shamir, E. Tromer: Acoustic cryptanalysis On nosy people and noisy machines Conclusions (RF) Digital video interfaces used with flat panel displays can emit significantly stronger and better signal than CRTs. CRT emissions dependent significantly on graphics card. Human-readable text and radio character recognition is possible with contemporary video modes and equipment in nearby rooms even without directional antennas. Various low-cost software countermeasures possible (filtered fonts, random bit jamming). Emission security remains a valid concern in applications with high confidentiality requirements, predictable device usage and easy longterm access to neighbour rooms. 44
Design Principles for Tamper-Resistant Smartcard Processors
 Design Principles for Tamper-Resistant Smartcard Processors Oliver Kömmerling ADSR Markus G. Kuhn Computer Laboratory λ http://www.cl.cam.ac.uk/~mgk25/sc99-tamper[-slides].pdf Microprobing Classes of Attacks
Design Principles for Tamper-Resistant Smartcard Processors Oliver Kömmerling ADSR Markus G. Kuhn Computer Laboratory λ http://www.cl.cam.ac.uk/~mgk25/sc99-tamper[-slides].pdf Microprobing Classes of Attacks
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Note monitors controlled by analog signals CRT monitors are controlled by analog voltage. i. e. the level of analog signal delivered through the
 DVI Interface The outline: The reasons for digital interface of a monitor the transfer from VGA to DVI. DVI v. analog interface. The principles of LCD control through DVI interface. The link between DVI
DVI Interface The outline: The reasons for digital interface of a monitor the transfer from VGA to DVI. DVI v. analog interface. The principles of LCD control through DVI interface. The link between DVI
Video eavesdropping- RF
 Security : Forensic Signal Analysis: MPHIL ACS 2009 Security : Forensic Signal Analysis Video eavesdropping- RF Y.K. Roland Tai 1. Introduction 2. History of TEMPEST 3. Type of RF leakages 4. Counter-measures.
Security : Forensic Signal Analysis: MPHIL ACS 2009 Security : Forensic Signal Analysis Video eavesdropping- RF Y.K. Roland Tai 1. Introduction 2. History of TEMPEST 3. Type of RF leakages 4. Counter-measures.
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
Secure Hardware PV018 Masaryk University Faculty of Informatics
 Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
DDX 7000 & 8003. Digital Partial Discharge Detectors FEATURES APPLICATIONS
 DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
A PC-BASED TIME INTERVAL COUNTER WITH 200 PS RESOLUTION
 35'th Annual Precise Time and Time Interval (PTTI) Systems and Applications Meeting San Diego, December 2-4, 2003 A PC-BASED TIME INTERVAL COUNTER WITH 200 PS RESOLUTION Józef Kalisz and Ryszard Szplet
35'th Annual Precise Time and Time Interval (PTTI) Systems and Applications Meeting San Diego, December 2-4, 2003 A PC-BASED TIME INTERVAL COUNTER WITH 200 PS RESOLUTION Józef Kalisz and Ryszard Szplet
Graphical displays are generally of two types: vector displays and raster displays. Vector displays
 Display technology Graphical displays are generally of two types: vector displays and raster displays. Vector displays Vector displays generally display lines, specified by their endpoints. Vector display
Display technology Graphical displays are generally of two types: vector displays and raster displays. Vector displays Vector displays generally display lines, specified by their endpoints. Vector display
Logical Operations. Control Unit. Contents. Arithmetic Operations. Objectives. The Central Processing Unit: Arithmetic / Logic Unit.
 Objectives The Central Processing Unit: What Goes on Inside the Computer Chapter 4 Identify the components of the central processing unit and how they work together and interact with memory Describe how
Objectives The Central Processing Unit: What Goes on Inside the Computer Chapter 4 Identify the components of the central processing unit and how they work together and interact with memory Describe how
On Security Evaluation Testing
 On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
Spike-Based Sensing and Processing: What are spikes good for? John G. Harris Electrical and Computer Engineering Dept
 Spike-Based Sensing and Processing: What are spikes good for? John G. Harris Electrical and Computer Engineering Dept ONR NEURO-SILICON WORKSHOP, AUG 1-2, 2006 Take Home Messages Introduce integrate-and-fire
Spike-Based Sensing and Processing: What are spikes good for? John G. Harris Electrical and Computer Engineering Dept ONR NEURO-SILICON WORKSHOP, AUG 1-2, 2006 Take Home Messages Introduce integrate-and-fire
DDX 7000 & 8003. Digital Partial Discharge Detectors FEATURES APPLICATIONS
 DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
DDX 7000 & 8003 Digital Partial Discharge Detectors The HAEFELY HIPOTRONICS DDX Digital Partial Discharge Detector offers the high accuracy and flexibility of digital technology, plus the real-time display
Smart Card Security How Can We Be So Sure?
 Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Comp 410/510. Computer Graphics Spring 2016. Introduction to Graphics Systems
 Comp 410/510 Computer Graphics Spring 2016 Introduction to Graphics Systems Computer Graphics Computer graphics deals with all aspects of creating images with a computer Hardware (PC with graphics card)
Comp 410/510 Computer Graphics Spring 2016 Introduction to Graphics Systems Computer Graphics Computer graphics deals with all aspects of creating images with a computer Hardware (PC with graphics card)
Harmonics and Noise in Photovoltaic (PV) Inverter and the Mitigation Strategies
 Soonwook Hong, Ph. D. Michael Zuercher Martinson Harmonics and Noise in Photovoltaic (PV) Inverter and the Mitigation Strategies 1. Introduction PV inverters use semiconductor devices to transform the
Soonwook Hong, Ph. D. Michael Zuercher Martinson Harmonics and Noise in Photovoltaic (PV) Inverter and the Mitigation Strategies 1. Introduction PV inverters use semiconductor devices to transform the
Impedance 50 (75 connectors via adapters)
 VECTOR NETWORK ANALYZER PLANAR TR1300/1 DATA SHEET Frequency range: 300 khz to 1.3 GHz Measured parameters: S11, S21 Dynamic range of transmission measurement magnitude: 130 db Measurement time per point:
VECTOR NETWORK ANALYZER PLANAR TR1300/1 DATA SHEET Frequency range: 300 khz to 1.3 GHz Measured parameters: S11, S21 Dynamic range of transmission measurement magnitude: 130 db Measurement time per point:
Fundamentals of Signature Analysis
 Fundamentals of Signature Analysis An In-depth Overview of Power-off Testing Using Analog Signature Analysis www.huntron.com 1 www.huntron.com 2 Table of Contents SECTION 1. INTRODUCTION... 7 PURPOSE...
Fundamentals of Signature Analysis An In-depth Overview of Power-off Testing Using Analog Signature Analysis www.huntron.com 1 www.huntron.com 2 Table of Contents SECTION 1. INTRODUCTION... 7 PURPOSE...
Open Architecture Design for GPS Applications Yves Théroux, BAE Systems Canada
 Open Architecture Design for GPS Applications Yves Théroux, BAE Systems Canada BIOGRAPHY Yves Théroux, a Project Engineer with BAE Systems Canada (BSC) has eight years of experience in the design, qualification,
Open Architecture Design for GPS Applications Yves Théroux, BAE Systems Canada BIOGRAPHY Yves Théroux, a Project Engineer with BAE Systems Canada (BSC) has eight years of experience in the design, qualification,
Displays. Cathode Ray Tube. Semiconductor Elements. Basic applications. Oscilloscope TV Old monitors. 2009, Associate Professor PhD. T.
 Displays Semiconductor Elements 1 Cathode Ray Tube Basic applications Oscilloscope TV Old monitors 2 1 Idea of Electrostatic Deflection 3 Inside an Electrostatic Deflection Cathode Ray Tube Gun creates
Displays Semiconductor Elements 1 Cathode Ray Tube Basic applications Oscilloscope TV Old monitors 2 1 Idea of Electrostatic Deflection 3 Inside an Electrostatic Deflection Cathode Ray Tube Gun creates
Module 2. Embedded Processors and Memory. Version 2 EE IIT, Kharagpur 1
 Module 2 Embedded Processors and Memory Version 2 EE IIT, Kharagpur 1 Lesson 5 Memory-I Version 2 EE IIT, Kharagpur 2 Instructional Objectives After going through this lesson the student would Pre-Requisite
Module 2 Embedded Processors and Memory Version 2 EE IIT, Kharagpur 1 Lesson 5 Memory-I Version 2 EE IIT, Kharagpur 2 Instructional Objectives After going through this lesson the student would Pre-Requisite
Computer Performance. Topic 3. Contents. Prerequisite knowledge Before studying this topic you should be able to:
 55 Topic 3 Computer Performance Contents 3.1 Introduction...................................... 56 3.2 Measuring performance............................... 56 3.2.1 Clock Speed.................................
55 Topic 3 Computer Performance Contents 3.1 Introduction...................................... 56 3.2 Measuring performance............................... 56 3.2.1 Clock Speed.................................
Composite Video Separation Techniques
 TM Composite Video Separation Techniques Application Note October 1996 AN9644 Author: Stephen G. LaJeunesse Introduction The most fundamental job of a video decoder is to separate the color from the black
TM Composite Video Separation Techniques Application Note October 1996 AN9644 Author: Stephen G. LaJeunesse Introduction The most fundamental job of a video decoder is to separate the color from the black
Security & Chip Card ICs SLE 44R35S / Mifare
 Security & Chip Card ICs SLE 44R35S / Mifare Intelligent 1 Kbyte EEPROM with Interface for Contactless Transmission, Security Logic and Anticollision according to the MIFARE -System Short Product Info
Security & Chip Card ICs SLE 44R35S / Mifare Intelligent 1 Kbyte EEPROM with Interface for Contactless Transmission, Security Logic and Anticollision according to the MIFARE -System Short Product Info
Local Heating Attacks on Flash Memory Devices. Dr Sergei Skorobogatov
 Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Low- Cost Chip Microprobing
 Low- Cost Chip Microprobing Philipp Maier Karsten Nohl SRLabs Template v11 A few smart cards chips cover numerous security domains Security chip applica.ons Payment
Low- Cost Chip Microprobing Philipp Maier Karsten Nohl SRLabs Template v11 A few smart cards chips cover numerous security domains Security chip applica.ons Payment
LVDS Technology Solves Typical EMI Problems Associated with Cell Phone Cameras and Displays
 AN-5059 Fairchild Semiconductor Application Note May 2005 Revised May 2005 LVDS Technology Solves Typical EMI Problems Associated with Cell Phone Cameras and Displays Differential technologies such as
AN-5059 Fairchild Semiconductor Application Note May 2005 Revised May 2005 LVDS Technology Solves Typical EMI Problems Associated with Cell Phone Cameras and Displays Differential technologies such as
Department of Electrical and Computer Engineering Ben-Gurion University of the Negev. LAB 1 - Introduction to USRP
 Department of Electrical and Computer Engineering Ben-Gurion University of the Negev LAB 1 - Introduction to USRP - 1-1 Introduction In this lab you will use software reconfigurable RF hardware from National
Department of Electrical and Computer Engineering Ben-Gurion University of the Negev LAB 1 - Introduction to USRP - 1-1 Introduction In this lab you will use software reconfigurable RF hardware from National
POCKET SCOPE 2. The idea 2. Design criteria 3
 POCKET SCOPE 2 The idea 2 Design criteria 3 Microcontroller requirements 3 The microcontroller must have speed. 3 The microcontroller must have RAM. 3 The microcontroller must have secure Flash. 3 The
POCKET SCOPE 2 The idea 2 Design criteria 3 Microcontroller requirements 3 The microcontroller must have speed. 3 The microcontroller must have RAM. 3 The microcontroller must have secure Flash. 3 The
RX-AM4SF Receiver. Pin-out. Connections
 RX-AM4SF Receiver The super-heterodyne receiver RX-AM4SF can provide a RSSI output indicating the amplitude of the received signal: this output can be used to create a field-strength meter capable to indicate
RX-AM4SF Receiver The super-heterodyne receiver RX-AM4SF can provide a RSSI output indicating the amplitude of the received signal: this output can be used to create a field-strength meter capable to indicate
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices
 An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany [email protected]
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany [email protected]
Supply voltage Supervisor TL77xx Series. Author: Eilhard Haseloff
 Supply voltage Supervisor TL77xx Series Author: Eilhard Haseloff Literature Number: SLVAE04 March 1997 i IMPORTANT NOTICE Texas Instruments (TI) reserves the right to make changes to its products or to
Supply voltage Supervisor TL77xx Series Author: Eilhard Haseloff Literature Number: SLVAE04 March 1997 i IMPORTANT NOTICE Texas Instruments (TI) reserves the right to make changes to its products or to
INTRODUCTION TO COMMUNICATION SYSTEMS AND TRANSMISSION MEDIA
 COMM.ENG INTRODUCTION TO COMMUNICATION SYSTEMS AND TRANSMISSION MEDIA 9/6/2014 LECTURES 1 Objectives To give a background on Communication system components and channels (media) A distinction between analogue
COMM.ENG INTRODUCTION TO COMMUNICATION SYSTEMS AND TRANSMISSION MEDIA 9/6/2014 LECTURES 1 Objectives To give a background on Communication system components and channels (media) A distinction between analogue
Grounding Demystified
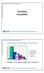 Grounding Demystified 3-1 Importance Of Grounding Techniques 45 40 35 30 25 20 15 10 5 0 Grounding 42% Case 22% Cable 18% Percent Used Filter 12% PCB 6% Grounding 42% Case Shield 22% Cable Shielding 18%
Grounding Demystified 3-1 Importance Of Grounding Techniques 45 40 35 30 25 20 15 10 5 0 Grounding 42% Case 22% Cable 18% Percent Used Filter 12% PCB 6% Grounding 42% Case Shield 22% Cable Shielding 18%
A+ Guide to Managing and Maintaining Your PC, 7e. Chapter 1 Introducing Hardware
 A+ Guide to Managing and Maintaining Your PC, 7e Chapter 1 Introducing Hardware Objectives Learn that a computer requires both hardware and software to work Learn about the many different hardware components
A+ Guide to Managing and Maintaining Your PC, 7e Chapter 1 Introducing Hardware Objectives Learn that a computer requires both hardware and software to work Learn about the many different hardware components
What is a Smart Card?
 An Introduction to Smart Cards and RFIDs Prof. Keith E. Mayes [email protected] Director of the ISG - Smart Card Centre www.scc.rhul.ac.uk Learning Objectives (MSc MSc) Identify the various types
An Introduction to Smart Cards and RFIDs Prof. Keith E. Mayes [email protected] Director of the ISG - Smart Card Centre www.scc.rhul.ac.uk Learning Objectives (MSc MSc) Identify the various types
Extended Resolution TOA Measurement in an IFM Receiver
 Extended Resolution TOA Measurement in an IFM Receiver Time of arrival (TOA) measurements define precisely when an RF signal is received, necessary in the identification of type and mode of RF and radar
Extended Resolution TOA Measurement in an IFM Receiver Time of arrival (TOA) measurements define precisely when an RF signal is received, necessary in the identification of type and mode of RF and radar
ELECTRONIC DOCUMENT IMAGING
 AIIM: Association for Information and Image Management. Trade association and professional society for the micrographics, optical disk and electronic image management markets. Algorithm: Prescribed set
AIIM: Association for Information and Image Management. Trade association and professional society for the micrographics, optical disk and electronic image management markets. Algorithm: Prescribed set
Overview. Raster Graphics and Color. Overview. Display Hardware. Liquid Crystal Display (LCD) Cathode Ray Tube (CRT)
 Raster Graphics and Color Greg Humphreys CS445: Intro Graphics University of Virginia, Fall 2004 Color models Color models Display Hardware Video display devices Cathode Ray Tube (CRT) Liquid Crystal Display
Raster Graphics and Color Greg Humphreys CS445: Intro Graphics University of Virginia, Fall 2004 Color models Color models Display Hardware Video display devices Cathode Ray Tube (CRT) Liquid Crystal Display
PCM Encoding and Decoding:
 PCM Encoding and Decoding: Aim: Introduction to PCM encoding and decoding. Introduction: PCM Encoding: The input to the PCM ENCODER module is an analog message. This must be constrained to a defined bandwidth
PCM Encoding and Decoding: Aim: Introduction to PCM encoding and decoding. Introduction: PCM Encoding: The input to the PCM ENCODER module is an analog message. This must be constrained to a defined bandwidth
On a New Way to Read Data from Memory
 On a New Way to Read Data from Memory David Samyde 1, Sergei Skorobogatov 2, Ross Anderson 2 and Jean-Jacques Quisquater 1 1: Université catholique de Louvain, UCL Crypto Group Place du Levant, 3, B-1348
On a New Way to Read Data from Memory David Samyde 1, Sergei Skorobogatov 2, Ross Anderson 2 and Jean-Jacques Quisquater 1 1: Université catholique de Louvain, UCL Crypto Group Place du Levant, 3, B-1348
MANUAL FOR RX700 LR and NR
 MANUAL FOR RX700 LR and NR 2013, November 11 Revision/ updates Date, updates, and person Revision 1.2 03-12-2013, By Patrick M Affected pages, ETC ALL Content Revision/ updates... 1 Preface... 2 Technical
MANUAL FOR RX700 LR and NR 2013, November 11 Revision/ updates Date, updates, and person Revision 1.2 03-12-2013, By Patrick M Affected pages, ETC ALL Content Revision/ updates... 1 Preface... 2 Technical
Product Information S N O. Portable VIP protection CCTV & Alarm System 2
 Product Information S N O Portable VIP protection CCTV & Alarm System 2 G O V E R N M E N T A L S E C U R I T Y S O L U T I VIP KIT Rapid Deployment VIP Protection Kit The VIP KIT has been designed to
Product Information S N O Portable VIP protection CCTV & Alarm System 2 G O V E R N M E N T A L S E C U R I T Y S O L U T I VIP KIT Rapid Deployment VIP Protection Kit The VIP KIT has been designed to
8-Bit Flash Microcontroller for Smart Cards. AT89SCXXXXA Summary. Features. Description. Complete datasheet available under NDA
 Features Compatible with MCS-51 products On-chip Flash Program Memory Endurance: 1,000 Write/Erase Cycles On-chip EEPROM Data Memory Endurance: 100,000 Write/Erase Cycles 512 x 8-bit RAM ISO 7816 I/O Port
Features Compatible with MCS-51 products On-chip Flash Program Memory Endurance: 1,000 Write/Erase Cycles On-chip EEPROM Data Memory Endurance: 100,000 Write/Erase Cycles 512 x 8-bit RAM ISO 7816 I/O Port
Frequency Response of Filters
 School of Engineering Department of Electrical and Computer Engineering 332:224 Principles of Electrical Engineering II Laboratory Experiment 2 Frequency Response of Filters 1 Introduction Objectives To
School of Engineering Department of Electrical and Computer Engineering 332:224 Principles of Electrical Engineering II Laboratory Experiment 2 Frequency Response of Filters 1 Introduction Objectives To
Monitoring of Intravenous Drip Rate
 Monitoring of Intravenous Drip Rate Vidyadhar V. Kamble, Prem C. Pandey, Chandrashekar P. Gadgil, and Dinesh S. Choudhary Abstract A drip rate meter, for monitoring intravenous infusion, is developed using
Monitoring of Intravenous Drip Rate Vidyadhar V. Kamble, Prem C. Pandey, Chandrashekar P. Gadgil, and Dinesh S. Choudhary Abstract A drip rate meter, for monitoring intravenous infusion, is developed using
Security in Near Field Communication (NFC)
 Security in Near Field Communication (NFC) Strengths and Weaknesses Ernst Haselsteiner and Klemens Breitfuß Philips Semiconductors Mikronweg 1, 8101 Gratkorn, Austria [email protected] [email protected]
Security in Near Field Communication (NFC) Strengths and Weaknesses Ernst Haselsteiner and Klemens Breitfuß Philips Semiconductors Mikronweg 1, 8101 Gratkorn, Austria [email protected] [email protected]
AN1200.04. Application Note: FCC Regulations for ISM Band Devices: 902-928 MHz. FCC Regulations for ISM Band Devices: 902-928 MHz
 AN1200.04 Application Note: FCC Regulations for ISM Band Devices: Copyright Semtech 2006 1 of 15 www.semtech.com 1 Table of Contents 1 Table of Contents...2 1.1 Index of Figures...2 1.2 Index of Tables...2
AN1200.04 Application Note: FCC Regulations for ISM Band Devices: Copyright Semtech 2006 1 of 15 www.semtech.com 1 Table of Contents 1 Table of Contents...2 1.1 Index of Figures...2 1.2 Index of Tables...2
Data remanence in Flash Memory Devices
 Data remanence in Flash Memory Devices Sergei Skorobogatov 1 Data remanence Residual representation of data after erasure Magnetic media SRAM and DRAM Low-temperature data remanence Long-term retention
Data remanence in Flash Memory Devices Sergei Skorobogatov 1 Data remanence Residual representation of data after erasure Magnetic media SRAM and DRAM Low-temperature data remanence Long-term retention
Network Design. Yiannos Mylonas
 Network Design Yiannos Mylonas Physical Topologies There are two parts to the topology definition: the physical topology, which is the actual layout of the wire (media), and the logical topology, which
Network Design Yiannos Mylonas Physical Topologies There are two parts to the topology definition: the physical topology, which is the actual layout of the wire (media), and the logical topology, which
RF Measurements Using a Modular Digitizer
 RF Measurements Using a Modular Digitizer Modern modular digitizers, like the Spectrum M4i series PCIe digitizers, offer greater bandwidth and higher resolution at any given bandwidth than ever before.
RF Measurements Using a Modular Digitizer Modern modular digitizers, like the Spectrum M4i series PCIe digitizers, offer greater bandwidth and higher resolution at any given bandwidth than ever before.
PS 29M DUAL CHANNEL BELTPACK IN METAL CASE
 PS 29M DUAL CHANNEL BELTPACK IN METAL CASE USER MANUAL October 2013 This product is designed and manufactured by: ASL Intercom BV Zonnebaan 42 3542 EG Utrecht The Netherlands Phone: +31 (0)30 2411901 Fax:
PS 29M DUAL CHANNEL BELTPACK IN METAL CASE USER MANUAL October 2013 This product is designed and manufactured by: ASL Intercom BV Zonnebaan 42 3542 EG Utrecht The Netherlands Phone: +31 (0)30 2411901 Fax:
Alpha CPU and Clock Design Evolution
 Alpha CPU and Clock Design Evolution This lecture uses two papers that discuss the evolution of the Alpha CPU and clocking strategy over three CPU generations Gronowski, Paul E., et.al., High Performance
Alpha CPU and Clock Design Evolution This lecture uses two papers that discuss the evolution of the Alpha CPU and clocking strategy over three CPU generations Gronowski, Paul E., et.al., High Performance
Timing Errors and Jitter
 Timing Errors and Jitter Background Mike Story In a sampled (digital) system, samples have to be accurate in level and time. The digital system uses the two bits of information the signal was this big
Timing Errors and Jitter Background Mike Story In a sampled (digital) system, samples have to be accurate in level and time. The digital system uses the two bits of information the signal was this big
COMPUTER HARDWARE. Input- Output and Communication Memory Systems
 COMPUTER HARDWARE Input- Output and Communication Memory Systems Computer I/O I/O devices commonly found in Computer systems Keyboards Displays Printers Magnetic Drives Compact disk read only memory (CD-ROM)
COMPUTER HARDWARE Input- Output and Communication Memory Systems Computer I/O I/O devices commonly found in Computer systems Keyboards Displays Printers Magnetic Drives Compact disk read only memory (CD-ROM)
Problems of Security in Ad Hoc Sensor Network
 Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
DEVELOPMENT OF DEVICES AND METHODS FOR PHASE AND AC LINEARITY MEASUREMENTS IN DIGITIZERS
 DEVELOPMENT OF DEVICES AND METHODS FOR PHASE AND AC LINEARITY MEASUREMENTS IN DIGITIZERS U. Pogliano, B. Trinchera, G.C. Bosco and D. Serazio INRIM Istituto Nazionale di Ricerca Metrologica Torino (Italia)
DEVELOPMENT OF DEVICES AND METHODS FOR PHASE AND AC LINEARITY MEASUREMENTS IN DIGITIZERS U. Pogliano, B. Trinchera, G.C. Bosco and D. Serazio INRIM Istituto Nazionale di Ricerca Metrologica Torino (Italia)
How To Understand The Power Of An Freddi Tag (Rfid) System
 Radio Frequency Identification Done by: Haitham Habli. Table of contents Definition of RFID. Do they need license? RFID vs other identification systems. Classification of RFID systems. Emerge of passive
Radio Frequency Identification Done by: Haitham Habli. Table of contents Definition of RFID. Do they need license? RFID vs other identification systems. Classification of RFID systems. Emerge of passive
Data Transmission. Data Communications Model. CSE 3461 / 5461: Computer Networking & Internet Technologies. Presentation B
 CSE 3461 / 5461: Computer Networking & Internet Technologies Data Transmission Presentation B Kannan Srinivasan 08/30/2012 Data Communications Model Figure 1.2 Studying Assignment: 3.1-3.4, 4.1 Presentation
CSE 3461 / 5461: Computer Networking & Internet Technologies Data Transmission Presentation B Kannan Srinivasan 08/30/2012 Data Communications Model Figure 1.2 Studying Assignment: 3.1-3.4, 4.1 Presentation
RFSPACE CLOUD-IQ #CONNECTED SOFTWARE DEFINED RADIO
 CLOUD-IQ #CONNECTED SOFTWARE DEFINED RADIO 1 - SPECIFICATIONS Cloud-IQ INTRODUCTION The Cloud-IQ is a high performance, direct sampling software radio with an ethernet interface. It offers outstanding
CLOUD-IQ #CONNECTED SOFTWARE DEFINED RADIO 1 - SPECIFICATIONS Cloud-IQ INTRODUCTION The Cloud-IQ is a high performance, direct sampling software radio with an ethernet interface. It offers outstanding
Today. Important From Last Time. Old Joke. Computer Security. Embedded Security. Trusted Computing Base
 Important From Last Time A system is safety critical when its failure may result in injuries or deaths Verification and validation can dominate overall development effort Today Embedded system security
Important From Last Time A system is safety critical when its failure may result in injuries or deaths Verification and validation can dominate overall development effort Today Embedded system security
Attacks on Pay-TV Access Control Systems. Markus G. Kuhn Computer Laboratory
 Attacks on Pay-TV Access Control Systems Markus G. Kuhn Computer Laboratory Generations of Pay-TV Access Control Systems Analog Systems remove sync information, try to confuse gain-control in receiver,
Attacks on Pay-TV Access Control Systems Markus G. Kuhn Computer Laboratory Generations of Pay-TV Access Control Systems Analog Systems remove sync information, try to confuse gain-control in receiver,
Broadcasting encryption or systematic #FAIL? Phil
 WE 201 EK 2 42 Broadcasting encryption or systematic #FAIL? SUMMARY Intro : Broadcasting something... 1984 : Discret 11 1995 : Syster 1996 2002 : Seca 1 2002 2008 : Seca 2 Conclusion 2/49 Broadcasting
WE 201 EK 2 42 Broadcasting encryption or systematic #FAIL? SUMMARY Intro : Broadcasting something... 1984 : Discret 11 1995 : Syster 1996 2002 : Seca 1 2002 2008 : Seca 2 Conclusion 2/49 Broadcasting
E190Q Lecture 5 Autonomous Robot Navigation
 E190Q Lecture 5 Autonomous Robot Navigation Instructor: Chris Clark Semester: Spring 2014 1 Figures courtesy of Siegwart & Nourbakhsh Control Structures Planning Based Control Prior Knowledge Operator
E190Q Lecture 5 Autonomous Robot Navigation Instructor: Chris Clark Semester: Spring 2014 1 Figures courtesy of Siegwart & Nourbakhsh Control Structures Planning Based Control Prior Knowledge Operator
1 PERSONAL COMPUTERS
 PERSONAL COMPUTERS 1 2 Personal computer a desktop computer a laptop a tablet PC or a handheld PC Software applications for personal computers include word processing spreadsheets databases web browsers
PERSONAL COMPUTERS 1 2 Personal computer a desktop computer a laptop a tablet PC or a handheld PC Software applications for personal computers include word processing spreadsheets databases web browsers
With respect to the way of data access we can classify memories as:
 Memory Classification With respect to the way of data access we can classify memories as: - random access memories (RAM), - sequentially accessible memory (SAM), - direct access memory (DAM), - contents
Memory Classification With respect to the way of data access we can classify memories as: - random access memories (RAM), - sequentially accessible memory (SAM), - direct access memory (DAM), - contents
KBA Oktatási Kft OKÉV nyilvántartási szám: 01-0469-04
 KBA Oktatási Kft OKÉV nyilvántartási szám: 01-0469-04 2004 Built-in spy in your CRT-monitor or the glamour of the radio reception László M Biró Allianz Hungária Biztosító Rt. [email protected] Data
KBA Oktatási Kft OKÉV nyilvántartási szám: 01-0469-04 2004 Built-in spy in your CRT-monitor or the glamour of the radio reception László M Biró Allianz Hungária Biztosító Rt. [email protected] Data
How To Sell A Talan
 The TALAN represents state-of-the-art capability to rapidly and reliably detect and locate illicit tampering and security vulnerabilities on both digital and analog telephone systems. Marketing Characteristics
The TALAN represents state-of-the-art capability to rapidly and reliably detect and locate illicit tampering and security vulnerabilities on both digital and analog telephone systems. Marketing Characteristics
Instruction Manual Service Program ULTRA-PROG-IR
 Instruction Manual Service Program ULTRA-PROG-IR Parameterizing Software for Ultrasonic Sensors with Infrared Interface Contents 1 Installation of the Software ULTRA-PROG-IR... 4 1.1 System Requirements...
Instruction Manual Service Program ULTRA-PROG-IR Parameterizing Software for Ultrasonic Sensors with Infrared Interface Contents 1 Installation of the Software ULTRA-PROG-IR... 4 1.1 System Requirements...
Hello and welcome to this training module for the STM32L4 Liquid Crystal Display (LCD) controller. This controller can be used in a wide range of
 Hello and welcome to this training module for the STM32L4 Liquid Crystal Display (LCD) controller. This controller can be used in a wide range of applications such as home appliances, medical, automotive,
Hello and welcome to this training module for the STM32L4 Liquid Crystal Display (LCD) controller. This controller can be used in a wide range of applications such as home appliances, medical, automotive,
Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals. Introduction
 Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals Modified from the lecture slides of Lami Kaya ([email protected]) for use CECS 474, Fall 2008. 2009 Pearson Education Inc., Upper
Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals Modified from the lecture slides of Lami Kaya ([email protected]) for use CECS 474, Fall 2008. 2009 Pearson Education Inc., Upper
Step Response of RC Circuits
 Step Response of RC Circuits 1. OBJECTIVES...2 2. REFERENCE...2 3. CIRCUITS...2 4. COMPONENTS AND SPECIFICATIONS...3 QUANTITY...3 DESCRIPTION...3 COMMENTS...3 5. DISCUSSION...3 5.1 SOURCE RESISTANCE...3
Step Response of RC Circuits 1. OBJECTIVES...2 2. REFERENCE...2 3. CIRCUITS...2 4. COMPONENTS AND SPECIFICATIONS...3 QUANTITY...3 DESCRIPTION...3 COMMENTS...3 5. DISCUSSION...3 5.1 SOURCE RESISTANCE...3
PHYS 222 Spring 2012 Final Exam. Closed books, notes, etc. No electronic device except a calculator.
 PHYS 222 Spring 2012 Final Exam Closed books, notes, etc. No electronic device except a calculator. NAME: (all questions with equal weight) 1. If the distance between two point charges is tripled, the
PHYS 222 Spring 2012 Final Exam Closed books, notes, etc. No electronic device except a calculator. NAME: (all questions with equal weight) 1. If the distance between two point charges is tripled, the
Introduction To Computers: Hardware and Software
 What Is Hardware? Introduction To Computers: Hardware and Software A computer is made up of hardware. Hardware is the physical components of a computer system e.g., a monitor, keyboard, mouse and the computer
What Is Hardware? Introduction To Computers: Hardware and Software A computer is made up of hardware. Hardware is the physical components of a computer system e.g., a monitor, keyboard, mouse and the computer
Spectrum Analyzer Two models available: OGR-24 (24 GHz) and OGR-8 (8 GHz)
 TM Spectrum Analyzer Two models available: OGR-24 (24 GHz) and OGR-8 (8 GHz) U.S. PATENTS: 6,397,154; 7,058,530 Additional Patents Pending Whip antenna extension connector Auto Switching Antenna Panel
TM Spectrum Analyzer Two models available: OGR-24 (24 GHz) and OGR-8 (8 GHz) U.S. PATENTS: 6,397,154; 7,058,530 Additional Patents Pending Whip antenna extension connector Auto Switching Antenna Panel
MAINTENANCE & ADJUSTMENT
 MAINTENANCE & ADJUSTMENT Circuit Theory The concept of PLL system frequency synthesization is not of recent development, however, it has not been a long age since the digital theory has been couplet with
MAINTENANCE & ADJUSTMENT Circuit Theory The concept of PLL system frequency synthesization is not of recent development, however, it has not been a long age since the digital theory has been couplet with
Computer Systems Structure Main Memory Organization
 Computer Systems Structure Main Memory Organization Peripherals Computer Central Processing Unit Main Memory Computer Systems Interconnection Communication lines Input Output Ward 1 Ward 2 Storage/Memory
Computer Systems Structure Main Memory Organization Peripherals Computer Central Processing Unit Main Memory Computer Systems Interconnection Communication lines Input Output Ward 1 Ward 2 Storage/Memory
MPC 4. Machinery Protection Card Type MPC 4 FEATURES. Continuous on-line Machinery Protection Card
 Machinery Protection Card Type FEATURES Continuous on-line Machinery Protection Card Real-time measurement and monitoring using state-of-the-art DSP techniques Fully VME-compatible slave interface Fully
Machinery Protection Card Type FEATURES Continuous on-line Machinery Protection Card Real-time measurement and monitoring using state-of-the-art DSP techniques Fully VME-compatible slave interface Fully
MICROPROCESSOR AND MICROCOMPUTER BASICS
 Introduction MICROPROCESSOR AND MICROCOMPUTER BASICS At present there are many types and sizes of computers available. These computers are designed and constructed based on digital and Integrated Circuit
Introduction MICROPROCESSOR AND MICROCOMPUTER BASICS At present there are many types and sizes of computers available. These computers are designed and constructed based on digital and Integrated Circuit
The accurate calibration of all detectors is crucial for the subsequent data
 Chapter 4 Calibration The accurate calibration of all detectors is crucial for the subsequent data analysis. The stability of the gain and offset for energy and time calibration of all detectors involved
Chapter 4 Calibration The accurate calibration of all detectors is crucial for the subsequent data analysis. The stability of the gain and offset for energy and time calibration of all detectors involved
14.5GHZ 2.2KW CW GENERATOR. GKP 22KP 14.5GHz WR62 3x400V
 14.5GHZ 2.2KW CW GENERATOR GKP 22KP 14.5GHz WR62 3x400V UTILIZATION OF GKP 22KP GENERATOR With its characteristics of power stability whatever the load, very fast response time at a pulse, low ripple,
14.5GHZ 2.2KW CW GENERATOR GKP 22KP 14.5GHz WR62 3x400V UTILIZATION OF GKP 22KP GENERATOR With its characteristics of power stability whatever the load, very fast response time at a pulse, low ripple,
Hardware Security Modules for Protecting Embedded Systems
 Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
Computer Architecture
 Computer Architecture Random Access Memory Technologies 2015. április 2. Budapest Gábor Horváth associate professor BUTE Dept. Of Networked Systems and Services [email protected] 2 Storing data Possible
Computer Architecture Random Access Memory Technologies 2015. április 2. Budapest Gábor Horváth associate professor BUTE Dept. Of Networked Systems and Services [email protected] 2 Storing data Possible
Location-Aware and Safer Cards: Enhancing RFID Security and Privacy
 Location-Aware and Safer Cards: Enhancing RFID Security and Privacy 1 K.Anudeep, 2 Mrs. T.V.Anantha Lakshmi 1 Student, 2 Assistant Professor ECE Department, SRM University, Kattankulathur-603203 1 [email protected],
Location-Aware and Safer Cards: Enhancing RFID Security and Privacy 1 K.Anudeep, 2 Mrs. T.V.Anantha Lakshmi 1 Student, 2 Assistant Professor ECE Department, SRM University, Kattankulathur-603203 1 [email protected],
APPLICATION NOTE GaGe CompuScope 14200-based Lightning Monitoring System
 APPLICATION NOTE GaGe CompuScope 14200-based Lightning Monitoring System Challenge A customer needed to upgrade an older data acquisition unit for a real-time lightning monitoring system. Unlike many lightning
APPLICATION NOTE GaGe CompuScope 14200-based Lightning Monitoring System Challenge A customer needed to upgrade an older data acquisition unit for a real-time lightning monitoring system. Unlike many lightning
FM Radio Transmitter & Receiver Modules
 FM Radio Transmitter & Receiver Modules T5 / R5 Features MINIATURE SIL PACKAGE FULLY SHIELDED DATA RATES UP TO 128KBITS/S RANGE UPTO 300 METRES SINGLE SUPPLY VOLTAGE INDUSTRY PIN COMPATIBLE QFMT5-434 TEMP
FM Radio Transmitter & Receiver Modules T5 / R5 Features MINIATURE SIL PACKAGE FULLY SHIELDED DATA RATES UP TO 128KBITS/S RANGE UPTO 300 METRES SINGLE SUPPLY VOLTAGE INDUSTRY PIN COMPATIBLE QFMT5-434 TEMP
How To Use A High Definition Oscilloscope
 PRELIMINARY High Definition Oscilloscopes HDO4000 and HDO6000 Key Features 12-bit ADC resolution, up to 15-bit with enhanced resolution 200 MHz, 350 MHz, 500 MHz, 1 GHz bandwidths Long Memory up to 250
PRELIMINARY High Definition Oscilloscopes HDO4000 and HDO6000 Key Features 12-bit ADC resolution, up to 15-bit with enhanced resolution 200 MHz, 350 MHz, 500 MHz, 1 GHz bandwidths Long Memory up to 250
1. Oscilloscope is basically a graph-displaying device-it draws a graph of an electrical signal.
 CHAPTER 3: OSCILLOSCOPE AND SIGNAL GENERATOR 3.1 Introduction to oscilloscope 1. Oscilloscope is basically a graph-displaying device-it draws a graph of an electrical signal. 2. The graph show signal change
CHAPTER 3: OSCILLOSCOPE AND SIGNAL GENERATOR 3.1 Introduction to oscilloscope 1. Oscilloscope is basically a graph-displaying device-it draws a graph of an electrical signal. 2. The graph show signal change
TOTALLY SOLID STATE NON-DIRECTIONAL RADIO BEACONS 190-535 khz
 TOTALLY SOLID STATE NON-DIRECTIONAL RADIO S 190-535 khz This family of radio transmitters has been developed as extremely efficient, highly reliable Non Directional Beacons. ND2000A/4000A» MODULAR CONSTRUCTION»
TOTALLY SOLID STATE NON-DIRECTIONAL RADIO S 190-535 khz This family of radio transmitters has been developed as extremely efficient, highly reliable Non Directional Beacons. ND2000A/4000A» MODULAR CONSTRUCTION»
TOSHIBA CCD Image Sensor CCD (charge coupled device) TCD2955D
 Preliminary TOSHIBA CCD Image Sensor CCD (charge coupled device) TCD2955D The TCD2955D is a high sensitive and low dark current 4240 elements 6 line CCD color image sensor which includes CCD drive circuit
Preliminary TOSHIBA CCD Image Sensor CCD (charge coupled device) TCD2955D The TCD2955D is a high sensitive and low dark current 4240 elements 6 line CCD color image sensor which includes CCD drive circuit
Chapter I Model801, Model802 Functions and Features
 Chapter I Model801, Model802 Functions and Features 1. Completely Compatible with the Seventh Generation Control System The eighth generation is developed based on the seventh. Compared with the seventh,
Chapter I Model801, Model802 Functions and Features 1. Completely Compatible with the Seventh Generation Control System The eighth generation is developed based on the seventh. Compared with the seventh,
Preliminary Draft May 19th 1992. Video Subsystem
 Video Subsystem 2 Preliminary Draft May 19th 1992 Video Subsystem Section 1. Introduction....................... 1-1 Video Subsystem.......................... 1-2 Section 2. VGA Function......................
Video Subsystem 2 Preliminary Draft May 19th 1992 Video Subsystem Section 1. Introduction....................... 1-1 Video Subsystem.......................... 1-2 Section 2. VGA Function......................
RF Network Analyzer Basics
 RF Network Analyzer Basics A tutorial, information and overview about the basics of the RF Network Analyzer. What is a Network Analyzer and how to use them, to include the Scalar Network Analyzer (SNA),
RF Network Analyzer Basics A tutorial, information and overview about the basics of the RF Network Analyzer. What is a Network Analyzer and how to use them, to include the Scalar Network Analyzer (SNA),
Computer Peripherals
 Computer Peripherals Reading: Chapter 10 (except 10.6) Peripherals Devices that are separate from the basic computer Not the CPU, memory, or power supply Classified as input, output, and storage Connect
Computer Peripherals Reading: Chapter 10 (except 10.6) Peripherals Devices that are separate from the basic computer Not the CPU, memory, or power supply Classified as input, output, and storage Connect
Chip Card & Security ICs Mifare NRG SLE 66R35
 Chip Card & Security ICs Mifare NRG Intelligent 1 Kbyte Memory Chip with Interface for Contactless Transmission according to the Mifare -System Short Product Information April 2007 Short Product Information
Chip Card & Security ICs Mifare NRG Intelligent 1 Kbyte Memory Chip with Interface for Contactless Transmission according to the Mifare -System Short Product Information April 2007 Short Product Information
RF data receiver super-reactive ASK modulation, low cost and low consumption ideal for Microchip HCS KEELOQ decoder/encoder family. 0.
 Receiver AC-RX2/CS RF data receiver super-reactive ASK modulation, low cost and low consumption ideal for Microchip HCS KEELOQ decoder/encoder family. Pin-out 38.1 3 Component Side 1 2 3 7 11 13 14 15
Receiver AC-RX2/CS RF data receiver super-reactive ASK modulation, low cost and low consumption ideal for Microchip HCS KEELOQ decoder/encoder family. Pin-out 38.1 3 Component Side 1 2 3 7 11 13 14 15
GETTING STARTED WITH LABVIEW POINT-BY-POINT VIS
 USER GUIDE GETTING STARTED WITH LABVIEW POINT-BY-POINT VIS Contents Using the LabVIEW Point-By-Point VI Libraries... 2 Initializing Point-By-Point VIs... 3 Frequently Asked Questions... 5 What Are the
USER GUIDE GETTING STARTED WITH LABVIEW POINT-BY-POINT VIS Contents Using the LabVIEW Point-By-Point VI Libraries... 2 Initializing Point-By-Point VIs... 3 Frequently Asked Questions... 5 What Are the
