Low- Cost Chip Microprobing
|
|
|
- Geoffrey Patterson
- 10 years ago
- Views:
Transcription
1 Low- Cost Chip Microprobing Philipp Maier Karsten Nohl SRLabs Template v11
2 A few smart cards chips cover numerous security domains Security chip applica.ons Payment cards, electronic ID cards, access badges Trusted plalorm modules (TPM) Device and accessory idenoficaoon SIM cards, NFC secure elements Content protecoon Chip hacking mo.va.on Recent trend FuncOonality that users tradioonally circumvented or exposed in their devices moves into hardware: Usage restricoons DRM, Dongeling Secret protocols Devices are increasingly controlled by their manufac- turer, not their owner We need more wide- spread hardware analysis knowledge and cheaper tools to combat this trend 2
3 Reverse- engineering hardware funcoons requires specific tools Disassamler, decompiler Oscilloscope, logic analyzer Microscope, microposi-.oner (this talk s focus) 3
4 This talk introduces the methodology and tools of earlier (and hopefully future) works Reverse- engineer chip func.onality Read out memories Introductory Deep Silicon Analysis Starbug, Nohl 25C3, HAR 2009 This Talk Dexter, Nohl 29C3 Reviving Smart Card Analysis Tarnovsky, Nohl Camp 2011, BlackHat 2011 Advanced Mifare, Legic, DECT Reversing Starbug, Plötz, dedected *, Nohl 24C3, 26C3 Hacking the Smart Card Chip et al. Tarnovsky Various BlackHat, ToorCon * dedected team: Karsten Nohl, Andreas Schuler, Erik Tews, Ralf- Philipp Weinmann, Mathias Wenzel 4
5 Microprobing background Probing with simple tools Advanced probing techniques 5
6 Basic CPU principle: Current instrucoon decides which instrucoon gets loaded next Program memory: (EEP)ROM, Flash CPU Core Instruc.on latch For most instrucoons: Program counter ++ Data For flow- altering instrucoons (branches, jumps, returns): Register / memory Program counter Address 6
7 Probing and glitching with only two needles allows full memory read- out Alacker goal: Make the CPU go to all places in memory independent of security checks and other flow characterisocs. This alack is called Linear Code Extrac.on. Instruc.ons, data Instruc.ons latch CPU logic with program counter Memory address Alacker probes one bus bit at a Ome (first needle) Alack vector 2: Overwrite one bit that is set for all flow- altering instrucoon (works on ARM and a few other instrucoon sets) Clock Alack vector 1: Freeze the latch clock so that one instrucoon is executed indefinitely (second needle) 7
8 Microprobing background Probing with simple tools Advanced probing techniques 8
9 Basic probing setup Buffer Needle Chip target MicroposiOoner Moveable stage 9
10 Step 1: Decapsulate chip OpOon A Mechanically pry open package OpOon B Chemically etch into package 10
11 Step 2: Expose wires (1/2) OpOon A Scratching A microposiooner in combinaoon with hard needles can break the silicon oxide (aka glass) above metal tracks Works best for highest ( top ) metal layer on non- planarized chips 11
12 Step 2: Expose wires (2/2) OpOon B Lasering A laser shot through the microscope destroys chip structures to: Expose wires for probing - or- Cut wires to alter chip logic; i.e. permanently reset lock bit OpOmal for planarized chips and for working on top metal Takes pracoce to not destroy chips through shorong wires or inducing overvoltage Higher cost alternaove when compared to scratching but more reliable aser pracoce 12
13 Step 3: Find exploitable wires Most interesong chip structures: Security bits (fuses) Data buses Discover them: Reverse- engineer (HAR 09, Camp 11) Trial and error EPROM Addressing Fuses Fuse output Source: Chris Tarnovsky, Flylogic (fuse image) 13
14 Step 4: Connect to wires with probing needle 14
15 Some level of probing can even be done with simple opocal microscopes and few extra components Old opocal microscope Micro- posiooner Drawback: Probe distance limited to 2mm Compare to 2cm w/ special probing microscope Stage 300 Measurement amplifier parts: 70 (design to be released under CC soon) parts: 50 15
16 Microprobing background Probing with simple tools Advanced probing techniques 16
17 Focused Ion Beams prepare small feature- size chips for probing Focus Ion Beam (FIB) operaoon mode 1: Cut into chip to expose structures FIB operaoon mode 2: Deposit material to allow probing connecovity to hidden/small wires Source: Chris Tarnovsky, Flylogic 17
18 ProtecOon meshes create addioonal complexity for FIB probing Protec.on meshes Tight metal trace on top layer hides criocal structures Mesh breach triggers alarm Source: Chris Tarnovsky, Flylogic 18
19 Meshes slow down alack, but do not prevent them Mesh circumven.on Either remove parts of mesh, then bridge/fix the mesh with FIB edits - or- Circumvent mesh alarm: If defense is bulk- erase of non- volaole memory: Cut off the programming pumps If chip it is logic reset: Exploit in the small Ome window before the reset triggers Source: Chris Tarnovsky, Flylogic 19
20 Arms race around front- side FIB alacks makes back- side alacks more alracove Invasive alacks and defenses have thus far concentrated on touching metal tracks on the chip The same criocal data can also be intercepted or manipulated at transistors, which are reachable from the other side of the chip Source: Oliver Kömmerling 20
21 Take aways Device funcoonality is increasingly hidden in hardware and needs to be freed Sosware can be extracted from chips using fuse overwrites or linear code extracoon Simple controllers can be alacked with cheap tools; smart cards require focused ion beams QuesOons? Philipp Maier Karsten Nohl 21
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Smart Card Security How Can We Be So Sure?
 Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Local Heating Attacks on Flash Memory Devices. Dr Sergei Skorobogatov
 Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
Local Heating Attacks on Flash Memory Devices Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Introduction Semi-invasive attacks were introduced in 2002 ( Optical fault induction
BadUSB On accessories that turn evil
 BadUSB On accessories that turn evil Karsten Nohl Sascha Krißler Jakob Lell SRLabs Template v12 Demo 1 USB s&ck takes over Windows machine 2 Agenda
BadUSB On accessories that turn evil Karsten Nohl Sascha Krißler Jakob Lell SRLabs Template v12 Demo 1 USB s&ck takes over Windows machine 2 Agenda
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
With respect to the way of data access we can classify memories as:
 Memory Classification With respect to the way of data access we can classify memories as: - random access memories (RAM), - sequentially accessible memory (SAM), - direct access memory (DAM), - contents
Memory Classification With respect to the way of data access we can classify memories as: - random access memories (RAM), - sequentially accessible memory (SAM), - direct access memory (DAM), - contents
Data remanence in Flash Memory Devices
 Data remanence in Flash Memory Devices Sergei Skorobogatov 1 Data remanence Residual representation of data after erasure Magnetic media SRAM and DRAM Low-temperature data remanence Long-term retention
Data remanence in Flash Memory Devices Sergei Skorobogatov 1 Data remanence Residual representation of data after erasure Magnetic media SRAM and DRAM Low-temperature data remanence Long-term retention
Chapter 13. PIC Family Microcontroller
 Chapter 13 PIC Family Microcontroller Lesson 01 PIC Characteristics and Examples PIC microcontroller characteristics Power-on reset Brown out reset Simplified instruction set High speed execution Up to
Chapter 13 PIC Family Microcontroller Lesson 01 PIC Characteristics and Examples PIC microcontroller characteristics Power-on reset Brown out reset Simplified instruction set High speed execution Up to
8-Bit Flash Microcontroller for Smart Cards. AT89SCXXXXA Summary. Features. Description. Complete datasheet available under NDA
 Features Compatible with MCS-51 products On-chip Flash Program Memory Endurance: 1,000 Write/Erase Cycles On-chip EEPROM Data Memory Endurance: 100,000 Write/Erase Cycles 512 x 8-bit RAM ISO 7816 I/O Port
Features Compatible with MCS-51 products On-chip Flash Program Memory Endurance: 1,000 Write/Erase Cycles On-chip EEPROM Data Memory Endurance: 100,000 Write/Erase Cycles 512 x 8-bit RAM ISO 7816 I/O Port
Design of a High Speed Communications Link Using Field Programmable Gate Arrays
 Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
Karsten Nohl University of Virginia. Henryk Plötz HU Berlin
 Karsten Nohl University of Virginia Henryk Plötz HU Berlin Radio Frequency IDentification Tiny computer chips Passively Powered Karsten Nohl, Henryk Plötz - RFID Security 2 Constant monitoring is already
Karsten Nohl University of Virginia Henryk Plötz HU Berlin Radio Frequency IDentification Tiny computer chips Passively Powered Karsten Nohl, Henryk Plötz - RFID Security 2 Constant monitoring is already
Advances in Smartcard Security
 Advances in Smartcard Security Marc Witteman Introduction Over the last decade smartcards have entered our global community. Although initially they were only used as simple phone cards they now support
Advances in Smartcard Security Marc Witteman Introduction Over the last decade smartcards have entered our global community. Although initially they were only used as simple phone cards they now support
NAND Flash FAQ. Eureka Technology. apn5_87. NAND Flash FAQ
 What is NAND Flash? What is the major difference between NAND Flash and other Memory? Structural differences between NAND Flash and NOR Flash What does NAND Flash controller do? How to send command to
What is NAND Flash? What is the major difference between NAND Flash and other Memory? Structural differences between NAND Flash and NOR Flash What does NAND Flash controller do? How to send command to
S4000TH HART. HART Communication Manual
 HART Communication Manual The information and technical data disclosed in this document may be used and disseminated only for the purposes and to the extent specifically authorized in writing by General
HART Communication Manual The information and technical data disclosed in this document may be used and disseminated only for the purposes and to the extent specifically authorized in writing by General
Objective. Testing Principle. Types of Testing. Characterization Test. Verification Testing. VLSI Design Verification and Testing.
 VLSI Design Verification and Testing Objective VLSI Testing Mohammad Tehranipoor Electrical and Computer Engineering University of Connecticut Need to understand Types of tests performed at different stages
VLSI Design Verification and Testing Objective VLSI Testing Mohammad Tehranipoor Electrical and Computer Engineering University of Connecticut Need to understand Types of tests performed at different stages
Main Memory & Backing Store. Main memory backing storage devices
 Main Memory & Backing Store Main memory backing storage devices 1 Introduction computers store programs & data in two different ways: nmain memory ntemporarily stores programs & data that are being processed
Main Memory & Backing Store Main memory backing storage devices 1 Introduction computers store programs & data in two different ways: nmain memory ntemporarily stores programs & data that are being processed
National CR16C Family On-Chip Emulation. Contents. Technical Notes V9.11.75
 _ V9.11.75 Technical Notes National CR16C Family On-Chip Emulation Contents Contents... 1 1 Introduction... 2 2 Emulation options... 3 2.1 Hardware Options... 3 2.2 Initialization Sequence... 4 2.3 JTAG
_ V9.11.75 Technical Notes National CR16C Family On-Chip Emulation Contents Contents... 1 1 Introduction... 2 2 Emulation options... 3 2.1 Hardware Options... 3 2.2 Initialization Sequence... 4 2.3 JTAG
Fairchild Solutions for 133MHz Buffered Memory Modules
 AN-5009 Fairchild Semiconductor Application Note April 1999 Revised December 2000 Fairchild Solutions for 133MHz Buffered Memory Modules Fairchild Semiconductor provides several products that are compatible
AN-5009 Fairchild Semiconductor Application Note April 1999 Revised December 2000 Fairchild Solutions for 133MHz Buffered Memory Modules Fairchild Semiconductor provides several products that are compatible
On Security Evaluation Testing
 On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
Security & Chip Card ICs SLE 44R35S / Mifare
 Security & Chip Card ICs SLE 44R35S / Mifare Intelligent 1 Kbyte EEPROM with Interface for Contactless Transmission, Security Logic and Anticollision according to the MIFARE -System Short Product Info
Security & Chip Card ICs SLE 44R35S / Mifare Intelligent 1 Kbyte EEPROM with Interface for Contactless Transmission, Security Logic and Anticollision according to the MIFARE -System Short Product Info
On a New Way to Read Data from Memory
 On a New Way to Read Data from Memory David Samyde 1, Sergei Skorobogatov 2, Ross Anderson 2 and Jean-Jacques Quisquater 1 1: Université catholique de Louvain, UCL Crypto Group Place du Levant, 3, B-1348
On a New Way to Read Data from Memory David Samyde 1, Sergei Skorobogatov 2, Ross Anderson 2 and Jean-Jacques Quisquater 1 1: Université catholique de Louvain, UCL Crypto Group Place du Levant, 3, B-1348
Design Principles for Tamper-Resistant Smartcard Processors
 Design Principles for Tamper-Resistant Smartcard Processors Oliver Kömmerling ADSR Markus G. Kuhn Computer Laboratory λ http://www.cl.cam.ac.uk/~mgk25/sc99-tamper[-slides].pdf Microprobing Classes of Attacks
Design Principles for Tamper-Resistant Smartcard Processors Oliver Kömmerling ADSR Markus G. Kuhn Computer Laboratory λ http://www.cl.cam.ac.uk/~mgk25/sc99-tamper[-slides].pdf Microprobing Classes of Attacks
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion
 Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Sequential Logic: Clocks, Registers, etc.
 ENEE 245: igital Circuits & Systems Lab Lab 2 : Clocks, Registers, etc. ENEE 245: igital Circuits and Systems Laboratory Lab 2 Objectives The objectives of this laboratory are the following: To design
ENEE 245: igital Circuits & Systems Lab Lab 2 : Clocks, Registers, etc. ENEE 245: igital Circuits and Systems Laboratory Lab 2 Objectives The objectives of this laboratory are the following: To design
BadUSB On accessories that turn evil
 BadUSB On accessories that turn evil Karsten Nohl Sascha Krißler Jakob Lell SRLabs Template v12 Demo 1 USB s&ck takes over Windows machine 2 Agenda
BadUSB On accessories that turn evil Karsten Nohl Sascha Krißler Jakob Lell SRLabs Template v12 Demo 1 USB s&ck takes over Windows machine 2 Agenda
Security testing of hardware product
 Alain MERLE CESTI LETI CEA Grenoble [email protected] Security testing of hardware product DCIS/SASTI/CESTI 1 Abstract «What are you doing in ITSEFs?» Testing, Security testing, Attacks, Evaluations,
Alain MERLE CESTI LETI CEA Grenoble [email protected] Security testing of hardware product DCIS/SASTI/CESTI 1 Abstract «What are you doing in ITSEFs?» Testing, Security testing, Attacks, Evaluations,
Reverse engineering hardware for software reversers: studying an encrypted external HDD
 Reverse engineering hardware for software reversers: studying an encrypted external HDD Joffrey Czarny & Raphaël Rigo / AGI / TX5IT 2015-10-02 / Hardwear.io 2015-10-02 / Hardwear.io 2 Introduction Why
Reverse engineering hardware for software reversers: studying an encrypted external HDD Joffrey Czarny & Raphaël Rigo / AGI / TX5IT 2015-10-02 / Hardwear.io 2015-10-02 / Hardwear.io 2 Introduction Why
Automation System TROVIS 6400 TROVIS 6493 Compact Controller
 Automation System TROVIS 6400 TROVIS 6493 Compact Controller For panel mounting (front frame 48 x 96 mm/1.89 x 3.78 inch) Application Digital controller to automate industrial and process plants for general
Automation System TROVIS 6400 TROVIS 6493 Compact Controller For panel mounting (front frame 48 x 96 mm/1.89 x 3.78 inch) Application Digital controller to automate industrial and process plants for general
CHANCES AND RISKS FOR SECURITY IN MULTICORE PROCESSORS
 CHANCES AND RISKS FOR SECURITY IN MULTICORE PROCESSORS Prof. Dr.-Ing. Georg Sigl Institute for Security in Information Technology Technical University Munich [email protected] Fraunhofer Research Institution
CHANCES AND RISKS FOR SECURITY IN MULTICORE PROCESSORS Prof. Dr.-Ing. Georg Sigl Institute for Security in Information Technology Technical University Munich [email protected] Fraunhofer Research Institution
Design of an Insulin Pump. Purpose of an Insulin Pump:
 Design of an Insulin Pump Purpose of an Insulin Pump: Insulin is a hormone central to regulating carbohydrate and fat metabolism in the body. It is secreted regularly within the body and aids in converting
Design of an Insulin Pump Purpose of an Insulin Pump: Insulin is a hormone central to regulating carbohydrate and fat metabolism in the body. It is secreted regularly within the body and aids in converting
Outline. Institute of Computer and Communication Network Engineering. Institute of Computer and Communication Network Engineering
 Institute of Computer and Communication Network Engineering Institute of Computer and Communication Network Engineering Communication Networks Software Defined Networking (SDN) Prof. Dr. Admela Jukan Dr.
Institute of Computer and Communication Network Engineering Institute of Computer and Communication Network Engineering Communication Networks Software Defined Networking (SDN) Prof. Dr. Admela Jukan Dr.
DDR3 DIMM Slot Interposer
 DDR3 DIMM Slot Interposer DDR3-1867 Digital Validation High Speed DDR3 Digital Validation Passive 240-pin DIMM Slot Interposer Custom Designed for Agilent Logic Analyzers Compatible with Agilent Software
DDR3 DIMM Slot Interposer DDR3-1867 Digital Validation High Speed DDR3 Digital Validation Passive 240-pin DIMM Slot Interposer Custom Designed for Agilent Logic Analyzers Compatible with Agilent Software
Penetration Testing Windows Vista TM BitLocker TM
 Penetration Testing BitLocker TM Drive Encryption Douglas MacIver Penetration Engineer System Integrity Group, Corporation Hack In The Box 2006/09/21 2006 Corporation. All rights reserved. Trustworthy
Penetration Testing BitLocker TM Drive Encryption Douglas MacIver Penetration Engineer System Integrity Group, Corporation Hack In The Box 2006/09/21 2006 Corporation. All rights reserved. Trustworthy
Digital Image Formation. Storage Technology
 Digital Image Formation Storage Technology Storage Technology Quiz Name one type of data storage?! Storage Technology Data Storage Device is a device for recording (storing) information (data).!! Recording
Digital Image Formation Storage Technology Storage Technology Quiz Name one type of data storage?! Storage Technology Data Storage Device is a device for recording (storing) information (data).!! Recording
ZigBee Technology Overview
 ZigBee Technology Overview Presented by Silicon Laboratories Shaoxian Luo 1 EM351 & EM357 introduction EM358x Family introduction 2 EM351 & EM357 3 Ember ZigBee Platform Complete, ready for certification
ZigBee Technology Overview Presented by Silicon Laboratories Shaoxian Luo 1 EM351 & EM357 introduction EM358x Family introduction 2 EM351 & EM357 3 Ember ZigBee Platform Complete, ready for certification
Lecture-3 MEMORY: Development of Memory:
 Lecture-3 MEMORY: It is a storage device. It stores program data and the results. There are two kind of memories; semiconductor memories & magnetic memories. Semiconductor memories are faster, smaller,
Lecture-3 MEMORY: It is a storage device. It stores program data and the results. There are two kind of memories; semiconductor memories & magnetic memories. Semiconductor memories are faster, smaller,
Secure Hardware PV018 Masaryk University Faculty of Informatics
 Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
Technical Note. Micron NAND Flash Controller via Xilinx Spartan -3 FPGA. Overview. TN-29-06: NAND Flash Controller on Spartan-3 Overview
 Technical Note TN-29-06: NAND Flash Controller on Spartan-3 Overview Micron NAND Flash Controller via Xilinx Spartan -3 FPGA Overview As mobile product capabilities continue to expand, so does the demand
Technical Note TN-29-06: NAND Flash Controller on Spartan-3 Overview Micron NAND Flash Controller via Xilinx Spartan -3 FPGA Overview As mobile product capabilities continue to expand, so does the demand
Joint Interpretation Library
 for smart cards and similar devices Document purpose: provide requirements to developers and guidance to evaluators to fulfill the Security Architecture requirements of CC V3 ADV_ARC family. Version 2.0
for smart cards and similar devices Document purpose: provide requirements to developers and guidance to evaluators to fulfill the Security Architecture requirements of CC V3 ADV_ARC family. Version 2.0
R&D Access Touch 3.1 User Manual Version 1.00 Public 1 (13) User Manual. Access Touch 3.1
 Public 1 (13) User Manual Access Touch 3.1 Version Date Author Description 1.00 30.09.2011 Pah First version Public 2 (13) 1. Purpose of this user manual... 3 2. Description of Access Touch 3.1... 3 3.
Public 1 (13) User Manual Access Touch 3.1 Version Date Author Description 1.00 30.09.2011 Pah First version Public 2 (13) 1. Purpose of this user manual... 3 2. Description of Access Touch 3.1... 3 3.
Today. Important From Last Time. Old Joke. Computer Security. Embedded Security. Trusted Computing Base
 Important From Last Time A system is safety critical when its failure may result in injuries or deaths Verification and validation can dominate overall development effort Today Embedded system security
Important From Last Time A system is safety critical when its failure may result in injuries or deaths Verification and validation can dominate overall development effort Today Embedded system security
Chapter 02: Computer Organization. Lesson 04: Functional units and components in a computer organization Part 3 Bus Structures
 Chapter 02: Computer Organization Lesson 04: Functional units and components in a computer organization Part 3 Bus Structures Objective: Understand the IO Subsystem and Understand Bus Structures Understand
Chapter 02: Computer Organization Lesson 04: Functional units and components in a computer organization Part 3 Bus Structures Objective: Understand the IO Subsystem and Understand Bus Structures Understand
AN1837. Non-Volatile Memory Technology Overview By Stephen Ledford Non-Volatile Memory Technology Center Austin, Texas.
 Order this document by /D Non-Volatile Memory Technology Overview By Stephen Ledford Non-Volatile Memory Technology Center Austin, Texas Introduction Today s microcontroller applications are more sophisticated
Order this document by /D Non-Volatile Memory Technology Overview By Stephen Ledford Non-Volatile Memory Technology Center Austin, Texas Introduction Today s microcontroller applications are more sophisticated
GSM-DL2 GSM auto dialer
 Introduction GSM-DL2 GSM auto dialer GSM-DL2 is a GSM auto dialer; designed for car alarm, boat alarm, home alarm and other applications. When it is triggered, it dials pre-programmed telephone numbers
Introduction GSM-DL2 GSM auto dialer GSM-DL2 is a GSM auto dialer; designed for car alarm, boat alarm, home alarm and other applications. When it is triggered, it dials pre-programmed telephone numbers
Development of a Simple Sound Activated Burglar Alarm System
 [ Leonardo Journal of Sciences ISSN 1583-0233 Issue 9, July-December 2006 p. 97-102 Development of a Simple Sound Activated Burglar Alarm System Department of Electrical and Computer Engineering, Federal
[ Leonardo Journal of Sciences ISSN 1583-0233 Issue 9, July-December 2006 p. 97-102 Development of a Simple Sound Activated Burglar Alarm System Department of Electrical and Computer Engineering, Federal
Software Hardware Binding with Quiddikey
 Software Hardware Binding with Quiddikey Mass scale solution against software piracy Secure your digital life Software-Hardware Binding solutions are typically required for Flash-based systems in which
Software Hardware Binding with Quiddikey Mass scale solution against software piracy Secure your digital life Software-Hardware Binding solutions are typically required for Flash-based systems in which
How to design an insulin pump
 How to design an insulin pump Learn about the purpose of an insulin pump, its overall workings, and the requirements needed for its design as well as implementation. By Asha Ganesan Applications Engineer
How to design an insulin pump Learn about the purpose of an insulin pump, its overall workings, and the requirements needed for its design as well as implementation. By Asha Ganesan Applications Engineer
Production Flash Programming Best Practices for Kinetis K- and L-series MCUs
 Freescale Semiconductor Document Number:AN4835 Application Note Rev 1, 05/2014 Production Flash Programming Best Practices for Kinetis K- and L-series MCUs by: Melissa Hunter 1 Introduction This application
Freescale Semiconductor Document Number:AN4835 Application Note Rev 1, 05/2014 Production Flash Programming Best Practices for Kinetis K- and L-series MCUs by: Melissa Hunter 1 Introduction This application
Defending mobile phones. Karsten Nohl, [email protected] Luca Melette, [email protected]
 Defending mobile phones Karsten Nohl, [email protected] Luca Melette, [email protected] GSM networks provide the base for various attacks SS7 Phone Base station GSM backend network User database (HLR) Vulnerability
Defending mobile phones Karsten Nohl, [email protected] Luca Melette, [email protected] GSM networks provide the base for various attacks SS7 Phone Base station GSM backend network User database (HLR) Vulnerability
CHAPTER 7: The CPU and Memory
 CHAPTER 7: The CPU and Memory The Architecture of Computer Hardware, Systems Software & Networking: An Information Technology Approach 4th Edition, Irv Englander John Wiley and Sons 2010 PowerPoint slides
CHAPTER 7: The CPU and Memory The Architecture of Computer Hardware, Systems Software & Networking: An Information Technology Approach 4th Edition, Irv Englander John Wiley and Sons 2010 PowerPoint slides
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
The modular concept of the MPA-3 system is designed to enable easy accommodation to a huge variety of experimental requirements.
 HARDWARE DESCRIPTION The modular concept of the MPA-3 system is designed to enable easy accommodation to a huge variety of experimental requirements. BASE MODULE GO LINE Digital I/O 8 Analog Out AUX 1
HARDWARE DESCRIPTION The modular concept of the MPA-3 system is designed to enable easy accommodation to a huge variety of experimental requirements. BASE MODULE GO LINE Digital I/O 8 Analog Out AUX 1
Silicon Lab Bonn. Physikalisches Institut Universität Bonn. DEPFET Test System Test Beam @ DESY
 Silicon Lab Bonn Physikalisches Institut Universität Bonn DEPFET Test System Test Beam @ DESY H. Krüger, EUDET Brainstorming, 3/4.11.2005 1 SI LAB DEPFET Prototype System DEPFET sensors 64 x 128 pixels,
Silicon Lab Bonn Physikalisches Institut Universität Bonn DEPFET Test System Test Beam @ DESY H. Krüger, EUDET Brainstorming, 3/4.11.2005 1 SI LAB DEPFET Prototype System DEPFET sensors 64 x 128 pixels,
GSM HOME SECURITY SYSTEM
 Cell /Mobile phone home security system GSM HOME SECURITY SYSTEM Model : GSM-120 TABLE OF CONTENTS 1. FEATURES... 1 2. APPLICATION... 2 3. SPECIFICATIONS... 3 4. FRONT PANEL & LAYOUT DESCRIPTION...6 5.
Cell /Mobile phone home security system GSM HOME SECURITY SYSTEM Model : GSM-120 TABLE OF CONTENTS 1. FEATURES... 1 2. APPLICATION... 2 3. SPECIFICATIONS... 3 4. FRONT PANEL & LAYOUT DESCRIPTION...6 5.
Documentation. M-Bus 130-mbx
 Documentation M-Bus 130-mbx Introduction The mx M-Bus module is part of the mx Smart Slot communications family. With the integrated SmartSlot technology, mx systems ag offers automatic consumer data read-out
Documentation M-Bus 130-mbx Introduction The mx M-Bus module is part of the mx Smart Slot communications family. With the integrated SmartSlot technology, mx systems ag offers automatic consumer data read-out
PAC1 Door Access Controller
 PAC1 Door Access Controller Series 2 IMPORTANT DIFFERENCES FROM SERIES 1 1. A PACDL data logger revision 4.0 or higher attached to the DLOG terminal is able to program all features (i.e. times, relay type,
PAC1 Door Access Controller Series 2 IMPORTANT DIFFERENCES FROM SERIES 1 1. A PACDL data logger revision 4.0 or higher attached to the DLOG terminal is able to program all features (i.e. times, relay type,
DESIGN OF SMS ENABLED CAR SECURITY SYSTEM
 DESIGN OF SMS ENABLED CAR SECURITY SYSTEM K. A. Amusa Federal University of Agriculture, Abeokuta, O. O. Nuga Federal University of Agriculture, Abeokuta, A. A. Adetomi Federal University of Agriculture,
DESIGN OF SMS ENABLED CAR SECURITY SYSTEM K. A. Amusa Federal University of Agriculture, Abeokuta, O. O. Nuga Federal University of Agriculture, Abeokuta, A. A. Adetomi Federal University of Agriculture,
DRV8312-C2-KIT How to Run Guide
 DRV8312-C2-KIT How to Run Guide Version 1.1 October 2011 C2000 Systems and Applications Team This Guide explains the steps needed to run the DRV8312-C2-KIT with the software supplied through controlsuite.
DRV8312-C2-KIT How to Run Guide Version 1.1 October 2011 C2000 Systems and Applications Team This Guide explains the steps needed to run the DRV8312-C2-KIT with the software supplied through controlsuite.
Programming Logic controllers
 Programming Logic controllers Programmable Logic Controller (PLC) is a microprocessor based system that uses programmable memory to store instructions and implement functions such as logic, sequencing,
Programming Logic controllers Programmable Logic Controller (PLC) is a microprocessor based system that uses programmable memory to store instructions and implement functions such as logic, sequencing,
Chapter 2: Computer-System Structures. Computer System Operation Storage Structure Storage Hierarchy Hardware Protection General System Architecture
 Chapter 2: Computer-System Structures Computer System Operation Storage Structure Storage Hierarchy Hardware Protection General System Architecture Operating System Concepts 2.1 Computer-System Architecture
Chapter 2: Computer-System Structures Computer System Operation Storage Structure Storage Hierarchy Hardware Protection General System Architecture Operating System Concepts 2.1 Computer-System Architecture
Nanotechnologies for the Integrated Circuits
 Nanotechnologies for the Integrated Circuits September 23, 2015 Dr. Bertrand Cambou Professor of Practice NAU, Cybersecurity School of Informatics, Computing, and Cyber-Systems Agenda The Market Silicon
Nanotechnologies for the Integrated Circuits September 23, 2015 Dr. Bertrand Cambou Professor of Practice NAU, Cybersecurity School of Informatics, Computing, and Cyber-Systems Agenda The Market Silicon
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 2 Systems Threats and Risks
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
Tamper resistant devices
 Foundations of Secure e-commerce (bmevihim219) Dr. Levente Buttyán Associate Professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) [email protected],
Foundations of Secure e-commerce (bmevihim219) Dr. Levente Buttyán Associate Professor BME Hálózati Rendszerek és Szolgáltatások Tanszék Lab of Cryptography and System Security (CrySyS) [email protected],
1 / 25. CS 137: File Systems. Persistent Solid-State Storage
 1 / 25 CS 137: File Systems Persistent Solid-State Storage Technology Change is Coming Introduction Disks are cheaper than any solid-state memory Likely to be true for many years But SSDs are now cheap
1 / 25 CS 137: File Systems Persistent Solid-State Storage Technology Change is Coming Introduction Disks are cheaper than any solid-state memory Likely to be true for many years But SSDs are now cheap
ES_LPC4357/53/37/33. Errata sheet LPC4357/53/37/33. Document information
 Rev. 1.1 8 August 2012 Errata sheet Document information Info Keywords Abstract Content LPC4357FET256; LPC4357FET180; LPC4357FBD208; LPC4353FET256; LPC4353FET180; LPC4353FBD208; LPC4337FET256; LPC4337FET180;
Rev. 1.1 8 August 2012 Errata sheet Document information Info Keywords Abstract Content LPC4357FET256; LPC4357FET180; LPC4357FBD208; LPC4353FET256; LPC4353FET180; LPC4353FBD208; LPC4337FET256; LPC4337FET180;
Chapter 1 Lesson 3 Hardware Elements in the Embedded Systems. 2008 Chapter-1L03: "Embedded Systems - ", Raj Kamal, Publs.: McGraw-Hill Education
 Chapter 1 Lesson 3 Hardware Elements in the Embedded Systems 1 Typical Embedded System Hardware units 2 Basic Circuit Elements at the System 3 (i) Power Source 1. System own supply with separate supply
Chapter 1 Lesson 3 Hardware Elements in the Embedded Systems 1 Typical Embedded System Hardware units 2 Basic Circuit Elements at the System 3 (i) Power Source 1. System own supply with separate supply
Bluetooth in Automotive Applications Lars-Berno Fredriksson, KVASER AB
 Bluetooth in Automotive Applications Lars-Berno Fredriksson, KVASER AB ABSTRACT There is a potential for 50-400 million per year Bluetooth nodes within the car market if Bluetooth can be integrated into
Bluetooth in Automotive Applications Lars-Berno Fredriksson, KVASER AB ABSTRACT There is a potential for 50-400 million per year Bluetooth nodes within the car market if Bluetooth can be integrated into
Memory unit. 2 k words. n bits per word
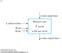 9- k address lines Read n data input lines Memory unit 2 k words n bits per word n data output lines 24 Pearson Education, Inc M Morris Mano & Charles R Kime 9-2 Memory address Binary Decimal Memory contents
9- k address lines Read n data input lines Memory unit 2 k words n bits per word n data output lines 24 Pearson Education, Inc M Morris Mano & Charles R Kime 9-2 Memory address Binary Decimal Memory contents
Computer Architecture
 Computer Architecture Slide Sets WS 2013/2014 Prof. Dr. Uwe Brinkschulte M.Sc. Benjamin Betting Part 11 Memory Management Computer Architecture Part 11 page 1 of 44 Prof. Dr. Uwe Brinkschulte, M.Sc. Benjamin
Computer Architecture Slide Sets WS 2013/2014 Prof. Dr. Uwe Brinkschulte M.Sc. Benjamin Betting Part 11 Memory Management Computer Architecture Part 11 page 1 of 44 Prof. Dr. Uwe Brinkschulte, M.Sc. Benjamin
GSM Gate Opener GSM Remote Switch RTU5015 User Manual
 GSM Gate, Barrier, Shutter, Garage Door and Door opener Open gate or garage door with a FREE call from your mobile phone! Remote switching machines with a FREE call from your mobile phone! GSM Gate Opener
GSM Gate, Barrier, Shutter, Garage Door and Door opener Open gate or garage door with a FREE call from your mobile phone! Remote switching machines with a FREE call from your mobile phone! GSM Gate Opener
MICROPROCESSOR. Exclusive for IACE Students www.iace.co.in iacehyd.blogspot.in Ph: 9700077455/422 Page 1
 MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
Sharpen your document and data security HP Security solutions for imaging and printing
 Sharpen your document and data security HP Security solutions for imaging and printing Recognize hidden risks You know how valuable data is to your organization. But the more data you acquire and share,
Sharpen your document and data security HP Security solutions for imaging and printing Recognize hidden risks You know how valuable data is to your organization. But the more data you acquire and share,
INSTALLATION GUIDE OWNER S GUIDE
 INSTALLATION GUIDE OWNER S GUIDE TALKING ALARM MODEL 3001 CONTENTS System Features... 1 Technical Assistance... 1 Wiring Instructions... 2 Installation Instructions... 3 Operating Instructions... 4-5 Technical
INSTALLATION GUIDE OWNER S GUIDE TALKING ALARM MODEL 3001 CONTENTS System Features... 1 Technical Assistance... 1 Wiring Instructions... 2 Installation Instructions... 3 Operating Instructions... 4-5 Technical
WINDOWS PROCESSES AND SERVICES
 OBJECTIVES: Services o task manager o services.msc Process o task manager o process monitor Task Scheduler Event viewer Regedit Services: A Windows service is a computer program that operates in the background.
OBJECTIVES: Services o task manager o services.msc Process o task manager o process monitor Task Scheduler Event viewer Regedit Services: A Windows service is a computer program that operates in the background.
INSTALLATION GUIDE. www.security.soundstream.com FCC ID NOTICE
 AL.1 AUTO SECURITY SYSTEM INSTALLATION GUIDE www.security.soundstream.com FCC ID NOTICE This device complies with Part 15 of the FCC rules. Operation is subject to the following conditions: 1. This device
AL.1 AUTO SECURITY SYSTEM INSTALLATION GUIDE www.security.soundstream.com FCC ID NOTICE This device complies with Part 15 of the FCC rules. Operation is subject to the following conditions: 1. This device
USER MANUAL V5.0 ST100
 GPS Vehicle Tracker USER MANUAL V5.0 ST100 Updated on 15 September 2009-1 - Contents 1 Product Overview 3 2 For Your Safety 3 3 ST100 Parameters 3 4 Getting Started 4 4.1 Hardware and Accessories 4 4.2
GPS Vehicle Tracker USER MANUAL V5.0 ST100 Updated on 15 September 2009-1 - Contents 1 Product Overview 3 2 For Your Safety 3 3 ST100 Parameters 3 4 Getting Started 4 4.1 Hardware and Accessories 4 4.2
Logical Operations. Control Unit. Contents. Arithmetic Operations. Objectives. The Central Processing Unit: Arithmetic / Logic Unit.
 Objectives The Central Processing Unit: What Goes on Inside the Computer Chapter 4 Identify the components of the central processing unit and how they work together and interact with memory Describe how
Objectives The Central Processing Unit: What Goes on Inside the Computer Chapter 4 Identify the components of the central processing unit and how they work together and interact with memory Describe how
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Installation Instructions. Wireless Adapter/Repeater. Introduction. 30-3001-887 Rev C
 /Repeater Installation Instructions 30-3001-887 Rev C Workstation Ethernet bcx Controller Repeater Repeater Introduction Schneider Electric has designed a device that allows Andover Continuum controllers
/Repeater Installation Instructions 30-3001-887 Rev C Workstation Ethernet bcx Controller Repeater Repeater Introduction Schneider Electric has designed a device that allows Andover Continuum controllers
Version Date Author Description 1.00 19.07.2010 Jpo First version 1.01 21.12.2010 Jpo FET output descriptions made clearer 1.02 04.02.
 +3 # Version Date Author Description 1.00 19.07.2010 Jpo First version 1.01 21.12.2010 Jpo FET output descriptions made clearer 1.02 04.02.2011 Jpo Reset button added 1. Purpose of this user manual...
+3 # Version Date Author Description 1.00 19.07.2010 Jpo First version 1.01 21.12.2010 Jpo FET output descriptions made clearer 1.02 04.02.2011 Jpo Reset button added 1. Purpose of this user manual...
Freescale Semiconductor, Inc. Product Brief Integrated Portable System Processor DragonBall ΤΜ
 nc. Order this document by MC68328/D Microprocessor and Memory Technologies Group MC68328 MC68328V Product Brief Integrated Portable System Processor DragonBall ΤΜ As the portable consumer market grows
nc. Order this document by MC68328/D Microprocessor and Memory Technologies Group MC68328 MC68328V Product Brief Integrated Portable System Processor DragonBall ΤΜ As the portable consumer market grows
Car Alarm Tracker Manual-20150814
 CCTR-922 Car Alarm Tracker Manual-20150814 Welcome to use this GSM car alarm with tracker function CCTR-922. this product use 2G GSM network (LBS locate) to locate the car, it has many new and unique functions,
CCTR-922 Car Alarm Tracker Manual-20150814 Welcome to use this GSM car alarm with tracker function CCTR-922. this product use 2G GSM network (LBS locate) to locate the car, it has many new and unique functions,
Penetration Testing Service. By Comsec Information Security Consulting
 Penetration Testing Service By Consulting February, 2007 Background The number of hacking and intrusion incidents is increasing year by year as technology rolls out. Equally, there is no hiding place your
Penetration Testing Service By Consulting February, 2007 Background The number of hacking and intrusion incidents is increasing year by year as technology rolls out. Equally, there is no hiding place your
Smartcards and RFID. IPA Security Course Lejla Batina & Erik Poll. Digital Security University of Nijmegen
 Smartcards and RFID IPA Security Course Lejla Batina & Erik Poll Digital Security University of Nijmegen 1 Overview example uses (security) functionality smartcard technicalities RFID technicalities attacks
Smartcards and RFID IPA Security Course Lejla Batina & Erik Poll Digital Security University of Nijmegen 1 Overview example uses (security) functionality smartcard technicalities RFID technicalities attacks
Firmware security features in HP Compaq business notebooks
 HP ProtectTools Firmware security features in HP Compaq business notebooks Embedded security overview... 2 Basics of protection... 2 Protecting against unauthorized access user authentication... 3 Pre-boot
HP ProtectTools Firmware security features in HP Compaq business notebooks Embedded security overview... 2 Basics of protection... 2 Protecting against unauthorized access user authentication... 3 Pre-boot
Operating Systems. Lecture 03. February 11, 2013
 Operating Systems Lecture 03 February 11, 2013 Goals for Today Interrupts, traps and signals Hardware Protection System Calls Interrupts, Traps, and Signals The occurrence of an event is usually signaled
Operating Systems Lecture 03 February 11, 2013 Goals for Today Interrupts, traps and signals Hardware Protection System Calls Interrupts, Traps, and Signals The occurrence of an event is usually signaled
Security Principles. Related to. Handset Theft
 Security Principles Related to Handset Theft Table of Contents TABLE OF CONTENTS...2 GLOSSARY OF TERMS...3 1. INTRODUCTION...4 1.1 IMPORTANCE OF IMEI INTEGRITY...4 1.2 IMPROVED IMEI INTEGRITY PRINCIPLES...4
Security Principles Related to Handset Theft Table of Contents TABLE OF CONTENTS...2 GLOSSARY OF TERMS...3 1. INTRODUCTION...4 1.1 IMPORTANCE OF IMEI INTEGRITY...4 1.2 IMPROVED IMEI INTEGRITY PRINCIPLES...4
Security Technology for Smartphones
 Security Technology for Smartphones Yasuhiko Abe Hitoshi Ikeda Masafumi Emura Service functions are implemented on smartphones by storing on them personal information, network-operator information, corporate
Security Technology for Smartphones Yasuhiko Abe Hitoshi Ikeda Masafumi Emura Service functions are implemented on smartphones by storing on them personal information, network-operator information, corporate
GSM Gate Opener GSM Remote Switch RTU5015. User Manual. Ver 1.3 Date Issued: 2010-08-18. All rights reserved by King Pigeon Hi-Tech. Co., Ltd.
 GSM Gate, Barrier, Shutter, Garage Door and Door opener Open gate or garage door with a FREE call from your mobile phone! Remote switching machines with a FREE call from your mobile phone! GSM Gate Opener
GSM Gate, Barrier, Shutter, Garage Door and Door opener Open gate or garage door with a FREE call from your mobile phone! Remote switching machines with a FREE call from your mobile phone! GSM Gate Opener
www.sebury.com.cn Digital Keypad Use s Manual
 K3 K4 www.sebury.com.cn Digital Keypad Use s Manual Contents Introduction Introduction Specifications Intramural Interface Circuit 3 Mounting 3 Wiring 5 Power UP 7 Engineer Programming Mode 7 The K3/K4
K3 K4 www.sebury.com.cn Digital Keypad Use s Manual Contents Introduction Introduction Specifications Intramural Interface Circuit 3 Mounting 3 Wiring 5 Power UP 7 Engineer Programming Mode 7 The K3/K4
i ChatterBox! Motorcycle Security
 i Before you Start the Installation * Please read this manual to become familiar with the requirements necessary to complete the installation. * Use a high quality multi-meter to test all wires before
i Before you Start the Installation * Please read this manual to become familiar with the requirements necessary to complete the installation. * Use a high quality multi-meter to test all wires before
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES
 SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
Handout 17. by Dr Sheikh Sharif Iqbal. Memory Unit and Read Only Memories
 Handout 17 by Dr Sheikh Sharif Iqbal Memory Unit and Read Only Memories Objective: - To discuss different types of memories used in 80x86 systems for storing digital information. - To learn the electronic
Handout 17 by Dr Sheikh Sharif Iqbal Memory Unit and Read Only Memories Objective: - To discuss different types of memories used in 80x86 systems for storing digital information. - To learn the electronic
Memory Basics. SRAM/DRAM Basics
 Memory Basics RAM: Random Access Memory historically defined as memory array with individual bit access refers to memory with both Read and Write capabilities ROM: Read Only Memory no capabilities for
Memory Basics RAM: Random Access Memory historically defined as memory array with individual bit access refers to memory with both Read and Write capabilities ROM: Read Only Memory no capabilities for
Physical Attacks on Tamper Resistance: Progress and Lessons
 Physical Attacks on Tamper Resistance: Progress and Lessons Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Why do we need tamper resistance? Theft of service: unauthorised
Physical Attacks on Tamper Resistance: Progress and Lessons Dr Sergei Skorobogatov http://www.cl.cam.ac.uk/~sps32 email: [email protected] Why do we need tamper resistance? Theft of service: unauthorised
