Chung-Ho Chen Department of Electrical Engineering, National Cheng Kung University, Tainan, Taiwan
|
|
|
- Arnold Hensley
- 8 years ago
- Views:
Transcription
1 A Hybrid Software-Based Self-Testing methodology for Embedded Processor Tai-Hua Lu Department of Electrical Engineering, National Cheng Kung University, Tainan, Taiwan Chung-Ho Chen Department of Electrical Engineering, National Cheng Kung University, Tainan, Taiwan Kuen-Jong Lee Department of Electrical Engineering, National Cheng Kung University, Tainan, Taiwan ABSTRACT Software-based self-test (SBST) is emerging as a promising technology for enabling at-speed testing of high-speed embedded s testing in an SoC system. For SBST, test routine development or generation can base on deterministic and random methodology. The deterministic test methodology develops the test program for a pipeline using the information abstracted from its architecture model, RTL descriptions, and gate-level net-list for different types of circuits. The random test methodology tries to make the pseudo-exhaustive testing possible using random instructions or patterns. The proposed methodology improves coverage for structural faults using both deterministic and random development of the test code. Not only can the deterministic test program test lots of faults using very small code size, but also the random test program can help detect some of the faults that the deterministic test program is difficult to test. We demonstrated the feasibility of the proposed methodology by the achieved fault coverage, test program size, and testing cycle count on a complex pipeline core. Comparisons with previous work are also made. Experimental results show its potential as an effective method for practical use. Categories and Subject Descriptors C.1.3 [Processor Architectures]: Other Architecture - Embedded testing General Terms Measurement, Design, and Experimentation. Keywords Embedded testing, fault coverage, functional testing, software-based self-test. 1. INTRODUCTION With rapidly advanced semiconductor manufacturing technology, more and more embedded s are integrated in an SOC. However, the poor controllability and observability of s make the testing of an SOC system more and more difficult. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, or republish, to post on servers or to redistribute to lists, requires prior specific permission and/or a fee. SAC 08, March 16-20, 2008, Fortaleza, Ceará, Brazil. Copyright 2008 ACM /08/0003 $ Traditional scan-based test architectures are applied to embedded s to achieve high fault coverage, in which scan are inserted to the designed circuits to improve the controllability and observability. However, these test methods usually cause area overhead, and performance degradation [1]. Therefore, softwarebased self-test (SBST) becomes increasingly popular for embedded testing [2]. In general, test generation of the software-based methods can be classified into two categories: deterministic development and random generations. Since early 1980 s, several graph-theory based test generation algorithms for micros have been proposed which have established the framework of functional testing using deterministic patterns [3-6]. Much work related to deterministic test generation has been presented thereafter. A deterministic methodology to test the data path modules of a is developed in [7]. It can use the same test program and operands to test any architecture of adders and multipliers. In [8] Shen and Abraham describe a language that represents every instruction in an instruction set to simplify the test generation procedure. In [9][10], criterions to classify instructions according to the functionalities of components in the are provided. In [11], a genetic algorithm-based system is used to generate test programs for micro cores. Recently, several new methodologies were developed to extract functional constraints for modules of a from HDL description. Commercial ATPG tools can then be used to generate test patterns of the modules with the extracted constraints. The patterns are then translated into instructions [12] [15]. For the random pattern generation, several methodologies have been developed [16][17][18]. In [16], a LFSR is used to generate random numbers as random instructions, and a filter is designed to replace each illegal instruction with a legal one. A randomizer in [17] fills a randomized instruction in memory after the micro fetches the instruction previously stored at the same address. Therefore, the micro will get a different instruction at the next time from the identical memory address. In [18], a test generation tool, FRITS, for Intel Pentium 4 and Itanium family was introduced. In this paper we present a software-based self-testing methodology using deterministic and random development of the test code for embedded s. The deterministic test methodology explores the different types of circuit based on the design information from the architecture, registertransfer-level, and gate-level for SBST development and uses the information to improve coverage for structural faults. Our deterministic test methodology uses an ATPG tool to generate the constrained test patterns for testing the simple combinational fundamental IPs used in the. The deterministic
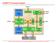
2 approach refers to the RTL code for the rest of the control and steering logic in the for test routine development. The pseudo-random test methodology is carefully developed and tries to make the pseudo-exhaustive testing possible. The concept of basic block is used to form the random test programs. Basic blocks provide reasonable instruction sequences like the normal user programs that perform: load to register file from memory, arithmetic or logical operations, result store of the operations, and control transfers. We use pseudo-random test program to detect the faults that the deterministic test programs are unable to test. Finally, we combine deterministic test program with pseudorandom test program to test embedded s. The SBST methodology is demonstrated by the achieved fault coverage, test program size, and testing cycle count on a Linuxverified pipeline core that incorporates pipeline hazard control and operand forwarding. Comparisons with previous work are also presented. The rest of this paper is organized as follows. Section 2 discusses related researches. Section 3 presents the proposed methodology. Section 4 shows the experimental results and comparisons with other SBST-based schemes. Finally, Section 5 gives the conclusions of this paper. 2. PREVIOUS WORK Software-based testing was proposed by S. M. Thatte and J. A. Abraham first [3]. They proposed the graph-theory based test generation algorithm for micros in The test method is functional testing without any knowledge of the structure. However, low fault coverage is the main issue of using software-based testing [2-11][16-22]. In [2], the authors analyze the RTL descriptions of a, and then choose instructions and operands to form the test routines according to their test library. This approach is carried out at a high abstraction level and gate-level information is not required during test development. There are three phases in their methodology. First, they extract information of the. In the second phase, they classify the components into three classes, functional components, control components, and hidden components. In the final phase, the most appropriate instructions and operands are selected for the considered components. The authors use two cores implementing the MIPS instruction set to evaluate their proposed methodology. Their work report fault coverage of 95.3% for a 3-stage pipelined implementation in a synthesis case resulting in a gate-count of For a more complicated implementation of the same instruction set that has a 5-stage pipeline, a fault coverage of 92.6% is achieved in a synthesis case resulting in a gate-count of Deterministic SBST has also been used in testing the specific functional units of a such as the ALU, multiplier-accumulator, and shifter [7]. The approach in [21] uses pseudo-random patterns to test a component by component. There are two steps in their self-test scheme, the test preparation step and the self-testing step. In the test preparation step, test patterns for a component are developed using random number generator under constraints imposed by instructions. The consideration of constraints is to make sure that the generated patterns are realizable by instructions. Alternatively, the patterns can be generated by ATPG under constraints. In the case of random patterns, these patterns are encapsulated into signatures. In the self-testing step, the generated patterns are applied to the considered components by a software tester. First, the on-chip test generation program (a software LFSR) emulates a pseudo-random pattern generator and expands the signatures into test patterns. Then the test application program applies these patterns to the considered components. Finally, the responses are collected and analyzed by the response analysis program. The authors use an 8-bit Parwan core which consists of 888 equivalent NAND gates and 53 flip-flops as the target. The experimental result shows that fault coverage of 91.42% can be achieved. Apart from SBST for cores, full scan approach has been used in testing a fully synthesizable core [1]. The downside of scan-based approach comes from the area overheads and possible performance degradation. 3. THE SBST METHODOLOGY In this section, we first present the overview of the proposed SBST methodology. Then, we introduce the deterministic approach followed by random test code development. An early version of the deterministic method has appeared in [23]. Figure 1 shows the SBST methodology for cores consisting of four stages of work as follows. Stage 1: Deterministic test program development. The first stage is to classify the above mentioned parts based on the abstraction model that includes ISA, pipeline architecture, and synthesized gate-level core. Then, construct the deterministic test program by each individual part, which can be conducted in parallel. Stage 2: Random test program development. The second stage is to generate a random program using constrained basic block. Stage 3: Fault simulation. The third stage is to combine deterministic test program with random test program for fault simulation. If the fault coverage is not accepted, repeat stage 1 or 2. We explain the detail of our SBST strategy in the following subsections. 3.1 Stage 1: Deterministic test routine development Before deterministic test code development, we classify the components into the four functional groups as illustrated in Section 3. The concepts of the deterministic test routine development methodology are as follows. Synthesized codes i. Tests for programmer-visible 1. Consider synthesized state elements. 2. Consider fault propagation. ii. Tests for Fundamental IPs 1. IP extraction 2. Constraint setting 3. Perform ATPG and develop test sequences. RTL codes i. Tests for control and steering logic and pipeline 1. Cover each statement, branch, and condition. 2. Consider fault model and fault propagation. System architecture 1529
3 Abstraction i. Tests for pipeline features 1. Control hazards. 2. Forwarding. Synthesized codes Deterministic test program development for programmervisible Instruction Set Random test program development Fault simulation No Single Load to Register Single Store to Memory Randomly generate in-order blocks Other component(s)/ip(s) exist? Yes for fundamental IPs Multiple Load to Registers Randomly choose basic block type Randomly generate out-of-order blocks No RTL codes Enough block? Yes Combine deterministic test program with random test program Assemble test program Logic simulation and capture input signals Transfer data stream of input signals into test pattern No Multiple Store to Memory Fault simulation Acceptable fault coverage? SBST test program for control, steering logic, and pipeline Yes Branch System architecture ALU for pipeline features Randomly generate return blocks Status Register Access Figure 1. Overview of the proposed software-based self-test methodology Test routine development for programmervisible We derive the test sequences for programmer-visible according to the information in the gate-level and the pipeline architecture. When using the information from these two levels, the deterministic test routines development can be easier without the tedious manual efforts. The programmer visible are typically mapped into D flip-flops after synthesis. Some of the faults on the D flip-flops, such as the faults on the write enable pins, are invisible in this level and thus are probably ignored and untested by the test program based on the high RTlevel. In addition, information of architectural level such as the pipeline forwarding depth between the EXE stage and the WB stage must also be used in order to develop useful test sequences for the general purpose. In a synthesized core, the programmer-visible in RTL descriptions are synthesized into clocked D flip-flops. Hence, it is simple and effective to develop the test routine which focuses on the structural faults of the D flip-flops input/output interface with the consideration of the pipeline architecture, i.e., the pipeline forwarding structure Test routine development for Fundamental IPs Among these combinational logics, some of them are the fundamental intellectual properties (IPs) introduced by the synthesis tool. The fundamental IP refers to small components such as adders, multipliers introduced by related RTL statements. For example, if we write an addition statement in the hardware description of a, the synthesis tool will insert an adder into the design to realize the addition function. In a core, the fundamental IPs mainly come from two components, the ALU and the memory access unit. For these simple fundamental IPs, the effective strategy for test routine development is to rely on the ATPG tool for the generation of efficient test patterns with only simple constraints. The test routine for a fundamental IP can be easily designed without struggling in the complex constraint setting process. After the fundamental IPs are extracted from the core, the next step is to perform constrained ATPG and generate the dedicated test patterns for each fundamental IP. We use ATPG just for fundamental IPs that are much smaller and less complicated than components or modules. A component or module may include control logics, multiplexers, or and has heterogeneous inputs. These features will make constraint setting and pattern application more complicated. On the other hand, a fundamental IP is simply a small computational component, such as an adder or subtractor, without any control logic or memory elements. So the constraint setting is relatively easy or even not required at all Test routine development for control, steering logic, and pipeline Apart from the programmer-visible and fundamental IPs, the control and steering logic, including the distributed logic gates, multiplexers, and pipeline, are considered. For the distributed logic gates and multiplexers, they are difficult to be identified with the structural information from the gate-level netlist. Pipeline are not programmer accessible. To test these units, we explore the instruction sequences similar to the programs for verification, which attains very high code coverage of the RTL descriptions with the consideration of fault observations. We refer to the RTL descriptions of the core to develop test routines for control, steering logic, and pipeline. For example, when we pursue code coverage for a multiplexer, we just need to write an instruction sequence that will select every input of the multiplexer. But, in the case of testing, besides selecting every input, we must differentiate every input value to prevent masking of faults on the select signals by identical input values. And we must use store or other instructions to propagate the test responses to primary outputs. 1530
4 The methodology for testing the pipeline is similar, but the difficulty of testing them well becomes higher. This is because there is no instruction that can explicitly access them as well as there is no way to definitely freeze their values. To test a specific pipeline register, we refer to the ISA specification and RTL descriptions to select the proper instructions. In general, the faults related to D, Q, and CK of all pipeline are easy to be detected while R s s-a-0 and EN s s-a-1 are the faults that appear to be functionally undetectable Test routine development for pipeline-related control logic Pipeline architecture is widely used in designs to enhance the performance. Information of pipeline architecture can be explored to test additional stuck-at faults related to pipeline control. When the encounters a branch instruction, exception, or external interrupt, its execution flow will be altered. In a pipelined, the mechanism to handle these operations is known as the branch hazard detection or control hazard detection. Another commonly found pipeline control logic is the forwarding logic which bypasses the result to the execution unit before the destination register is updated. To test the pipeline control logic, the methodology relies on the exploration of the pipeline architecture of the target. Specifically, the test routine examines the single stuck-at faults from the pipeline control hazard logic and the forwarding logic. In a classic five-stage pipelined with always not-taken for branch prediction, when a branch occurs, the IF and ID pipeline stage must be flushed for correct program execution. It means that the decoding of the instruction following the branch must be disabled, and the fetching of the next instruction must be disabled, too. We can insert another control-transfer instruction following the branch to functionally test these mechanisms. As for the forwarding mechanism, the idea is simply to test if the forwarding does occur from behind the pipeline stages. 3.2 Stage 2: Random test program development We develop a random test program generation methodology for fault coverage improvement of the test program. In this section, we will illustrate the structure and hardware support for the random test program Random test program Deterministic test program written by hands can test lots of faults using very small size of memory space. It is, however, impossible to test some faults no matter how good the deterministic program is. For example, the 12 bits close to MSB of the 32-bit program counter will never be touched if the memory size of manual program is allocated in 0 to 1 mega-byte. Additionally, deterministic test program is unable to enumerate all the combinations of instructions. Random instructions can test micros as random patterns do. They contribute the fault coverage that a deterministic test program cannot achieve and take much less test generation time than a deterministic methodology. Random test program can contain pseudoexhaustive combinations of operation codes, addressing modes, and branch targets. Instead of fully random instruction sequence, we use the concept of basic block formed by instructions to generate the random test program. The advantage of using basic blocks to form the test program is that we can define several constraints in the basic blocks. In our method, we define what kind of instructions can be present in a basic block, and how the instruction sequences are ordered. Table 1. Categories of ARMv4 instruction set. Classification Description Single Load to Register Load a value from memory, and write it into only one register. Single Store to Memory Store a value from only one register to memory. Multiple Load to Load a block of data from memory, and write Registers them into several. Multiple Store to Store a group of register contents to memory. Memory Branch Change the program counter. ALU Status Register Access Arithmetic and logical operations (Some have the effect of branch). Read or write the status The structure of basic block To build the basic blocks, we classify the instruction set into several categories first. For example, for the ARMv4 instruction set, it has seven categories as Table 1 shows. Each basic block contains every classification of instructions. In our method, there are eleven instructions in a basic block. Two types of basic block are used for the switching of mode. The first one is a general block, and the second is return block. For lots of simple micro, using general block is enough because they do not have different modes. A return block is used for the purpose of returning from privilege mode to user mode. Figure 2 and Figure 3 show the instruction sequence of basic blocks. We make some true data dependencies as shown by those curved arrows to test forwarding mechanism. There are also two types of general block. The difference between them is the order of the instruction sequence. The first one is the in-order basic block as Figure 2 shows, and the other is the out-of-order basic block. The sequences of instructions in an out-of-order basic block are changed randomly, but the basic blocks still contain every type of instructions. This is just like we shuffle the in-order basic blocks to form the out-of-order ones. The out-of-order basic blocks give random instruction sequence that is almost impossibly given in normal programs. But they will test some corner cases and detect the difficult-to-test faults Test Shell While the random test program runs, the address of the instruction and data access are unpredicted. If we do not use any mechanism to handle this, the will fetch unknown instructions and access unknown data because it sends the addresses to places where no test program exists. So, we develop a hardware device to solve this problem. Figure 4 shows the block diagram of the test system. The block on the left side is the core. The test program is placed in the memory on the right side. The test shell is placed between the core and system bus, just like a bus interface. If the core needs a bus interface 1531
5 to connect to the system bus, the test shell will be placed between the core and the bus interface. The functionality of the test shell is to correct the illegal instruction and data addresses sent from the to legal ones. This functionality is only enabled when the executes the random test program. When executing normal user programs, generating the legal address is the responsibility of the programmers. We also use the test shell to control exception signals and control test modes for test procedure in our test method. We use undefined instructions to control our test shell to trigger the exception signals. has 110 input pins, so after transformation the input stimulus for a time frame (a half cycle) will has 110 characters representing the 110-bit input signals. Finally, we perform fault simulation using the previously transformed stimuli and the gate-level net-list of the as inputs and get the fault coverage. 1. Load to R0. 2. Multiple Load use R0 as base register. 3. ALU operation. 4. ALU operation. 5. Store the result of instruction Store the result of instruction Move CPSR or SPSR to one of R0 to R Multiple Store contents of R0 to R Multiple Store (randomly select to store). 10. No operation 11. Branch or Branch and link Figure 2. Instruction sequence of a general block. 1. Load to R0. 2. Multiple Load use R0 as base register. 3. ALU operation. 4. Store the result of instruction Move some values to CPSR or SPSR 6. Move CPSR or SPSR to one of R0 to R Multiple Store contents of R0 to R Multiple Store (randomly select to store). 9. Move an immediate value 16 to R Move R0 to SPSR[7:0]. 11. Return to User Mode. Figure 3. Instruction sequence of a return block. 3.3 Stage 3: Fault simulation We here describe fault simulation which is depicted in Figure 1. We first prepare the memory image file that contains instructions and data required for test program execution. Our test program has two parts, deterministic test program and random test program. After the preparation of the memory image file, we perform logic simulation using ModelSim to acquire stimuli for fault simulation. During the logic simulation, the instructions and data in the memory image file will be fetched into the core according to the execution of the test program. We write codes in the test bench of the logic simulation to capture all input signals during the logic simulation, and these captured signals will become the stimuli fed to the fault simulation tool. The recorded data do not conform to the TurboScan s input format, so some simple character transformation is required. Our core Figure 4. Block diagram of test system. 4. EXPERIMENTAL RESULTS We have realized a core that implements the ARMv4 instruction set to demonstrate the proposed methodology [24][25]. The ARMv4 instruction set is a RISC one, but it has several CISC features, such as the multiple load or store instructions that manipulate more than one memory address and by just one instruction. In addition to the complex instruction set, the includes five-stage pipeline that supports the mechanisms for resolving branch hazard, load-use hazards, and pipeline forwarding [26]. This also supports the caches, TLBs, and MMU system. Besides, the core was verified in an FPGA board that successfully runs the Linux operating system. Different from many previous works that use a much simpler [2][9][17-21], the we use in this paper incorporates the complete functionality for operating system support. We have synthesized the target using the TSMC 0.35 um library. The synthesized has a gate count of (2-input NAND-gate equivalence) and operation speed of 30 MHz. The deterministic test program has a 1747-instruction test sequence (6988 bytes). And the size of the test data is 2356 bytes (2120 bytes of them are patterns generated by the ATPG tool, and the other 236 bytes are hand-made patterns, page tables, and so on). Thus, a deterministic test program (instructions + data) of 9108 bytes must be loaded into the memory by the external tester before self-testing. And it takes only (with cache) or (without cache) cycles to execute this test program. We also generate different random test programs in the forms of basic blocks and combine these random test programs with deterministic test program. Table 3 lists the resultant fault coverage of each part as well as the. The pure deterministic test program and a pure random test program of 1000 basic blocks (1100 instructions) can attain fault coverage 93.84% and 90.43% respectively, but this still is not enough for practical use. Unfortunately, it seems that there is a bottleneck to further raise fault coverage only using deterministic and random methods. However, when we combine the deterministic test program and the random test program which has 5000 basic blocks, the fault coverage achieves 97.30%. 1532
6 Because pseudo-random instruction blocks can detect hard-to-test faults of the deterministic program, the test program which combines the deterministic part and pseudo-random instruction block achieves 97.30% fault coverage. The total fault coverage improvement is 3.46%. For the status and access control category, the improvement is much greater, a fault coverage gain of 12.39%. Table 3. Breakdown of fault coverage Component # faults Det.. Ran 1000 Det.+ Ran 1000 Det.+ Ran 5000 Register file & access control ALU Shifter Memory access unit Instruction fetch unit Decoder Status & access control Co access unit Exception handling unit Other Whole Table 4 summarizes the comparisons of the SBST methodology with other works. Only our target core possesses the full functionality of pipeline hazard control, forwarding mechanism, and modern operating system supports. The table is clearly shown from the statistics of gate count used and the number of faults present. The achieved fault coverage of full scan chain is 97.88%. But the full-scan test method is of high area overhead and has a longer test application time. The SBST methodology has achieved 97.30% in coverage. The SBST test method not only is of very low area overhead but also has at-speed test application time. The difference of the fault coverage between applying the full scan chain and the SBST methodology is 0.58%. These results indicate that the proposed SBST methodology can be an option sufficient for practical use. 5. CONCLUSIONS We have presented a software-based self-test methodology and demonstrated on a complex pipeline. The proposed methodology produces a test program using both deterministic and random development of test codes. The deterministic test program which refers to the design information of architecture, RT-level, and gate-level for different types of the components. The deterministic test routine development methodology applies the most useful information of a certain level to the different parts of the core. The pseudorandom test program tries to make the pseudo-exhaustive testing possible. They also can detect the faults that the deterministic test programs are unable to detect. The concept of basic block is used to form the random test programs. Experimental results show that this concept can help the deterministic test program to get higher fault coverage. We have demonstrated that the proposed SBST methodology has attained 97.30% (Deterministic Random basic blocks) in fault coverage, 0.58% less than the expensive full scan approach. The result indicates that the proposed SBST methodology is an option for practical use. The experiments were performed on a pipeline which has full functionality of pipeline hazard control, forwarding mechanism, and complete ISA supports for modern operating systems. Table 4. Comparisons of various SBST work. CPU [2] 32-bit MIPS [9] 8-bit PARWAN Methodol ogy style [17] 16-bit DLX Random + DFT hardware Gate count/fault number Program size F.C. % Det. 37,402 /N.A. 1,728 (words) Det. 1,300/N.A. 885 bytes ,860/43, inst. seeds [19] 8-bit 8051 Random 6,000 /N.A. 624 inst [20] 8-bit 8051 Random 12,000/ 28,792 N.A [21] 8-bit PARWAN Random 888 gates + 53 FFs/N.A. 1,129 (bytes) Det. 45,046/128, inst./ 530 data (words) Random 1000 Det.+ Random 5000 Full scan chain ,046/128, inst ,046/128, inst./ 530 data (words ,961/137,258 N.A ACKNOWLEDGMENTS This work was supported in part by the Nation Science Council, Taiwan, R.O.C., under Grant NSC E MY3 and by the Program for Promoting Academic Excellence of Universities in Taiwan. 7. REFERENCES [1] A. Burdass, G. Campbell, R. Grisenthwaite et. al., Embedded Test and Debug of Full Custom and Synthesisable Micro Cores, Proceedings of the IEEE European Test Workshop, 2000, pp [2] N. Kranitis, A. Paschalis, D. Gizopoulos, and G. Xenoulis, Software-Based Self-Testing of Embedded Processor, 1533
7 IEEE Transactions on Computers, vol. 54, no.4, April 2005, pp [3] S. M. Thatte and Jacob A. Abraham, Test Generation of Micros, IEEE Trans. Computers, vol.33, no.6, June, 1980, pp [4] D. Brahme and J. A. Abraham, Functional Testing of Micros, IEEE Transactions on Computers, Vol.C-33, No.6, June 1984, pp [5] C.-S. Lin and H.-F. Ho, Automatic Functional Test Program Generation for Micros, Design Automation Conference, June, 1988, pp [6] A. J. van de Goor and Th. J. W. Verhallen, Functional Testing of Current Micros (applied to the Intel i860), International Test Conference, September, 1992, pp [7] A. Paschalis, D. Gizopoulos, N. Kranitis, M. Psarakis, and Y. Zorian, Deterministic Software-Based Self-Testing of Embedded Processor Cores, Design Automation and Test in Europe, [8] J. Shen and J. A. Abraham, Native Mode Functional Test Generation for Processors with Applications to Self Test and Design Validation, International Test Conference, October, 1998, pp [9] N. Kranitis, A. Paschalis, D. Gizopoulos, and Y. Zorian, Effective Software Self-Test Methodology for Processor Cores, Design Automation and Test in Europe, [10] N. Kranitis, D. Gizopoulos, A. Paschalis, and Y. Zorian, Instruction-Based Self-Testing of Processor Cores, In Proc. VLSI Test Symposium, 2002, pp [11] F. Cormo, M. S. Reorda, G. Squillero and M. Violante, A Genetic Algorithm-based System for Generating Test Programs for Micro IP Cores, International Conference on Tools with Artificial Intelligence, 2000, pp [12] R. S. Tupuri and J. A. Abraham, A Novel Hierarchical Test Generation Method for Processors, In Proc. International Conference on VLSI Design, January, 1997, pp [13] R. S. Tupuri and J. A. Abraham, A Novel Functional Test Generation Method for Processors using Commercial ATPG, International Test Conference, November, 1997, pp [14] R. S. Tupuri, A. Krishnamachary and J. A. Abraham, Test Generation for Gigahertz Processors Using an Automatic Functional Constraint Extractor, Design Automation Conference, 1999, pp [15] V. M. Vedula and J. A. Abraham, A Novel Methodology for Hierarchical Test Generation using Functional Constraint Composition, High-Level Design Validation and Test Workshop, 2000, pp [16] H.-P. Klug, Micro Testing by Instruction Sequences Derived from Random Patterns, International Test Conference (September 1988), pp [17] K. Batcher and C. Papachristou, Instruction th Randomization Self Test for Processor Cores, the 17 IEEE VLSI Test Symposium, 1999, pp [18] P. Parvathala, K. Maneparambil, and W. Lindsay, FRITS- A Micro Functional BIST Method, Proceeding of International Test Conference, 2002, pp [19] F. Corno, M. Reorda, G. Squillero, and M. Violante, On the Test of Micro IP Cores, Design Automation and Test in Europe, [20] F. Corno, G. Cumani, M. Reorda, and G. Squillero, Fully Automatic Test Program Generation for Micro Cores, Design Automation and Test in Europe, [21] L. Chen and S. Dey, Software-Based Self-Testing Methodology for Processor Cores, IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, vol. 20, no. 3, March, 2001, pp [22] A. Paschalis and D. Gizopoulos, Effective Software- Based Self-Test Strategies for On-Line Periodic Testing of Embedded Processors, IEEE Transactions on Computer- Aided Design of Integrated Circuits and Systems, vol. 24, no. 1,January, [23] C.-H. Chen, C.-K. Wei, T.-H. Lu, and H.-W. Gao, Software-Based Self-Testing With Multiple-Level Abstractions for Soft Processor Cores, IEEE Transactions on Very Large Scale Integration (VLSI) Systems, vol.15, no.5, May, 2007, pp [24] ARM Corporation, ARM Architecture Reference Manual, ARM DDI 0100E, [25] ARM Corporation, ARM922T Technique Reference Manual, ARM DDI 0184A, [26] David A. Patterson and John L. Hennessy, Computer Organization & Design, San Francisco, CA: Morgan Kaufmann, 3rd,
An Effective Deterministic BIST Scheme for Shifter/Accumulator Pairs in Datapaths
 An Effective Deterministic BIST Scheme for Shifter/Accumulator Pairs in Datapaths N. KRANITIS M. PSARAKIS D. GIZOPOULOS 2 A. PASCHALIS 3 Y. ZORIAN 4 Institute of Informatics & Telecommunications, NCSR
An Effective Deterministic BIST Scheme for Shifter/Accumulator Pairs in Datapaths N. KRANITIS M. PSARAKIS D. GIZOPOULOS 2 A. PASCHALIS 3 Y. ZORIAN 4 Institute of Informatics & Telecommunications, NCSR
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM
 ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM 1 The ARM architecture processors popular in Mobile phone systems 2 ARM Features ARM has 32-bit architecture but supports 16 bit
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM 1 The ARM architecture processors popular in Mobile phone systems 2 ARM Features ARM has 32-bit architecture but supports 16 bit
Contribution to the Methods and Algorithms of Automatic Generation of Functional Tests for Processors
 Contribution to the Methods and Algorithms of Automatic Generation of Functional Tests for Processors Ján Hudec Institute of Computer Systems and Networks Faculty of Informatics and Information Technologies
Contribution to the Methods and Algorithms of Automatic Generation of Functional Tests for Processors Ján Hudec Institute of Computer Systems and Networks Faculty of Informatics and Information Technologies
ARM Microprocessor and ARM-Based Microcontrollers
 ARM Microprocessor and ARM-Based Microcontrollers Nguatem William 24th May 2006 A Microcontroller-Based Embedded System Roadmap 1 Introduction ARM ARM Basics 2 ARM Extensions Thumb Jazelle NEON & DSP Enhancement
ARM Microprocessor and ARM-Based Microcontrollers Nguatem William 24th May 2006 A Microcontroller-Based Embedded System Roadmap 1 Introduction ARM ARM Basics 2 ARM Extensions Thumb Jazelle NEON & DSP Enhancement
Chapter 2 Logic Gates and Introduction to Computer Architecture
 Chapter 2 Logic Gates and Introduction to Computer Architecture 2.1 Introduction The basic components of an Integrated Circuit (IC) is logic gates which made of transistors, in digital system there are
Chapter 2 Logic Gates and Introduction to Computer Architecture 2.1 Introduction The basic components of an Integrated Circuit (IC) is logic gates which made of transistors, in digital system there are
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de jens_onno.krah@fh-koeln.de NIOS II 1 1 What is Nios II? Altera s Second Generation
Introduction to VLSI Testing
 Introduction to VLSI Testing 李 昆 忠 Kuen-Jong Lee Dept. of Electrical Engineering National Cheng-Kung University Tainan, Taiwan, R.O.C. Introduction to VLSI Testing.1 Problems to Think A 32 bit adder A
Introduction to VLSI Testing 李 昆 忠 Kuen-Jong Lee Dept. of Electrical Engineering National Cheng-Kung University Tainan, Taiwan, R.O.C. Introduction to VLSI Testing.1 Problems to Think A 32 bit adder A
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING
 FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
Implementation Details
 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Architectures and Platforms
 Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Hardware/Software Codesign Arch&Platf. - 1 Architectures and Platforms 1. Architecture Selection: The Basic Trade-Offs 2. General Purpose vs. Application-Specific Processors 3. Processor Specialisation
Let s put together a Manual Processor
 Lecture 14 Let s put together a Manual Processor Hardware Lecture 14 Slide 1 The processor Inside every computer there is at least one processor which can take an instruction, some operands and produce
Lecture 14 Let s put together a Manual Processor Hardware Lecture 14 Slide 1 The processor Inside every computer there is at least one processor which can take an instruction, some operands and produce
Advanced Computer Architecture-CS501. Computer Systems Design and Architecture 2.1, 2.2, 3.2
 Lecture Handout Computer Architecture Lecture No. 2 Reading Material Vincent P. Heuring&Harry F. Jordan Chapter 2,Chapter3 Computer Systems Design and Architecture 2.1, 2.2, 3.2 Summary 1) A taxonomy of
Lecture Handout Computer Architecture Lecture No. 2 Reading Material Vincent P. Heuring&Harry F. Jordan Chapter 2,Chapter3 Computer Systems Design and Architecture 2.1, 2.2, 3.2 Summary 1) A taxonomy of
Fault Modeling. Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults. Transistor faults Summary
 Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Fault Modeling Why model faults? Some real defects in VLSI and PCB Common fault models Stuck-at faults Single stuck-at faults Fault equivalence Fault dominance and checkpoint theorem Classes of stuck-at
Computer Architecture Lecture 2: Instruction Set Principles (Appendix A) Chih Wei Liu 劉 志 尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.
 Computer Architecture Lecture 2: Instruction Set Principles (Appendix A) Chih Wei Liu 劉 志 尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Review Computers in mid 50 s Hardware was expensive
Computer Architecture Lecture 2: Instruction Set Principles (Appendix A) Chih Wei Liu 劉 志 尉 National Chiao Tung University cwliu@twins.ee.nctu.edu.tw Review Computers in mid 50 s Hardware was expensive
Von der Hardware zur Software in FPGAs mit Embedded Prozessoren. Alexander Hahn Senior Field Application Engineer Lattice Semiconductor
 Von der Hardware zur Software in FPGAs mit Embedded Prozessoren Alexander Hahn Senior Field Application Engineer Lattice Semiconductor AGENDA Overview Mico32 Embedded Processor Development Tool Chain HW/SW
Von der Hardware zur Software in FPGAs mit Embedded Prozessoren Alexander Hahn Senior Field Application Engineer Lattice Semiconductor AGENDA Overview Mico32 Embedded Processor Development Tool Chain HW/SW
VLSI Design Verification and Testing
 VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: cpatel2@cs.umbc.edu). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: cpatel2@cs.umbc.edu). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
VHDL DESIGN OF EDUCATIONAL, MODERN AND OPEN- ARCHITECTURE CPU
 VHDL DESIGN OF EDUCATIONAL, MODERN AND OPEN- ARCHITECTURE CPU Martin Straka Doctoral Degree Programme (1), FIT BUT E-mail: strakam@fit.vutbr.cz Supervised by: Zdeněk Kotásek E-mail: kotasek@fit.vutbr.cz
VHDL DESIGN OF EDUCATIONAL, MODERN AND OPEN- ARCHITECTURE CPU Martin Straka Doctoral Degree Programme (1), FIT BUT E-mail: strakam@fit.vutbr.cz Supervised by: Zdeněk Kotásek E-mail: kotasek@fit.vutbr.cz
İSTANBUL AYDIN UNIVERSITY
 İSTANBUL AYDIN UNIVERSITY FACULTY OF ENGİNEERİNG SOFTWARE ENGINEERING THE PROJECT OF THE INSTRUCTION SET COMPUTER ORGANIZATION GÖZDE ARAS B1205.090015 Instructor: Prof. Dr. HASAN HÜSEYİN BALIK DECEMBER
İSTANBUL AYDIN UNIVERSITY FACULTY OF ENGİNEERİNG SOFTWARE ENGINEERING THE PROJECT OF THE INSTRUCTION SET COMPUTER ORGANIZATION GÖZDE ARAS B1205.090015 Instructor: Prof. Dr. HASAN HÜSEYİN BALIK DECEMBER
Power Reduction Techniques in the SoC Clock Network. Clock Power
 Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Power Reduction Techniques in the SoC Network Low Power Design for SoCs ASIC Tutorial SoC.1 Power Why clock power is important/large» Generally the signal with the highest frequency» Typically drives a
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course. Module-VII Lecture-I Introduction to Digital VLSI Testing
 Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
Design Verification and Test of Digital VLSI Circuits NPTEL Video Course Module-VII Lecture-I Introduction to Digital VLSI Testing VLSI Design, Verification and Test Flow Customer's Requirements Specifications
Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX
 White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
White Paper Testing Low Power Designs with Power-Aware Test Manage Manufacturing Test Power Issues with DFTMAX and TetraMAX April 2010 Cy Hay Product Manager, Synopsys Introduction The most important trend
ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT
 216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
The WIMP51: A Simple Processor and Visualization Tool to Introduce Undergraduates to Computer Organization
 The WIMP51: A Simple Processor and Visualization Tool to Introduce Undergraduates to Computer Organization David Sullins, Dr. Hardy Pottinger, Dr. Daryl Beetner University of Missouri Rolla Session I.
The WIMP51: A Simple Processor and Visualization Tool to Introduce Undergraduates to Computer Organization David Sullins, Dr. Hardy Pottinger, Dr. Daryl Beetner University of Missouri Rolla Session I.
Computer System: User s View. Computer System Components: High Level View. Input. Output. Computer. Computer System: Motherboard Level
 System: User s View System Components: High Level View Input Output 1 System: Motherboard Level 2 Components: Interconnection I/O MEMORY 3 4 Organization Registers ALU CU 5 6 1 Input/Output I/O MEMORY
System: User s View System Components: High Level View Input Output 1 System: Motherboard Level 2 Components: Interconnection I/O MEMORY 3 4 Organization Registers ALU CU 5 6 1 Input/Output I/O MEMORY
EE361: Digital Computer Organization Course Syllabus
 EE361: Digital Computer Organization Course Syllabus Dr. Mohammad H. Awedh Spring 2014 Course Objectives Simply, a computer is a set of components (Processor, Memory and Storage, Input/Output Devices)
EE361: Digital Computer Organization Course Syllabus Dr. Mohammad H. Awedh Spring 2014 Course Objectives Simply, a computer is a set of components (Processor, Memory and Storage, Input/Output Devices)
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Design Cycle for Microprocessors
 Cycle for Microprocessors Raúl Martínez Intel Barcelona Research Center Cursos de Verano 2010 UCLM Intel Corporation, 2010 Agenda Introduction plan Architecture Microarchitecture Logic Silicon ramp Types
Cycle for Microprocessors Raúl Martínez Intel Barcelona Research Center Cursos de Verano 2010 UCLM Intel Corporation, 2010 Agenda Introduction plan Architecture Microarchitecture Logic Silicon ramp Types
SDLC Controller. Documentation. Design File Formats. Verification
 January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: info@cast-inc.com URL: www.cast-inc.com Features AllianceCORE
January 15, 2004 Product Specification 11 Stonewall Court Woodcliff Lake, NJ 07677 USA Phone: +1-201-391-8300 Fax: +1-201-391-8694 E-mail: info@cast-inc.com URL: www.cast-inc.com Features AllianceCORE
MICROPROCESSOR. Exclusive for IACE Students www.iace.co.in iacehyd.blogspot.in Ph: 9700077455/422 Page 1
 MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
MICROPROCESSOR A microprocessor incorporates the functions of a computer s central processing unit (CPU) on a single Integrated (IC), or at most a few integrated circuit. It is a multipurpose, programmable
Logical Operations. Control Unit. Contents. Arithmetic Operations. Objectives. The Central Processing Unit: Arithmetic / Logic Unit.
 Objectives The Central Processing Unit: What Goes on Inside the Computer Chapter 4 Identify the components of the central processing unit and how they work together and interact with memory Describe how
Objectives The Central Processing Unit: What Goes on Inside the Computer Chapter 4 Identify the components of the central processing unit and how they work together and interact with memory Describe how
Exception and Interrupt Handling in ARM
 Exception and Interrupt Handling in ARM Architectures and Design Methods for Embedded Systems Summer Semester 2006 Author: Ahmed Fathy Mohammed Abdelrazek Advisor: Dominik Lücke Abstract We discuss exceptions
Exception and Interrupt Handling in ARM Architectures and Design Methods for Embedded Systems Summer Semester 2006 Author: Ahmed Fathy Mohammed Abdelrazek Advisor: Dominik Lücke Abstract We discuss exceptions
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Delay Time Analysis of Reconfigurable Firewall Unit
 Delay Time Analysis of Reconfigurable Unit Tomoaki SATO C&C Systems Center, Hirosaki University Hirosaki 036-8561 Japan Phichet MOUNGNOUL Faculty of Engineering, King Mongkut's Institute of Technology
Delay Time Analysis of Reconfigurable Unit Tomoaki SATO C&C Systems Center, Hirosaki University Hirosaki 036-8561 Japan Phichet MOUNGNOUL Faculty of Engineering, King Mongkut's Institute of Technology
Multi-Objective Genetic Test Generation for Systems-on-Chip Hardware Verification
 Multi-Objective Genetic Test Generation for Systems-on-Chip Hardware Verification Adriel Cheng Cheng-Chew Lim The University of Adelaide, Australia 5005 Abstract We propose a test generation method employing
Multi-Objective Genetic Test Generation for Systems-on-Chip Hardware Verification Adriel Cheng Cheng-Chew Lim The University of Adelaide, Australia 5005 Abstract We propose a test generation method employing
Digital Systems Design! Lecture 1 - Introduction!!
 ECE 3401! Digital Systems Design! Lecture 1 - Introduction!! Course Basics Classes: Tu/Th 11-12:15, ITE 127 Instructor Mohammad Tehranipoor Office hours: T 1-2pm, or upon appointments @ ITE 441 Email:
ECE 3401! Digital Systems Design! Lecture 1 - Introduction!! Course Basics Classes: Tu/Th 11-12:15, ITE 127 Instructor Mohammad Tehranipoor Office hours: T 1-2pm, or upon appointments @ ITE 441 Email:
Efficient Teaching of Digital Design with Automated Assessment and Feedback
 Efficient Teaching of Digital Design with Automated Assessment and Feedback 1 Paul W. Nutter, Member, IEEE, 2 Vasilis F. Pavlidis, Member, IEEE, and 2 Jeffrey Pepper 1 Nano Engineering and Storage Technology
Efficient Teaching of Digital Design with Automated Assessment and Feedback 1 Paul W. Nutter, Member, IEEE, 2 Vasilis F. Pavlidis, Member, IEEE, and 2 Jeffrey Pepper 1 Nano Engineering and Storage Technology
Arbitrary Density Pattern (ADP) Based Reduction of Testing Time in Scan-BIST VLSI Circuits
 Arbitrary Density Pattern (ADP) Based Reduction of Testing Time in Scan-BIST VLSI Circuits G. Naveen Balaji S. Vinoth Vijay Abstract Test power reduction done by Arbitrary Density Patterns (ADP) in which
Arbitrary Density Pattern (ADP) Based Reduction of Testing Time in Scan-BIST VLSI Circuits G. Naveen Balaji S. Vinoth Vijay Abstract Test power reduction done by Arbitrary Density Patterns (ADP) in which
Asynchronous IC Interconnect Network Design and Implementation Using a Standard ASIC Flow
 Asynchronous IC Interconnect Network Design and Implementation Using a Standard ASIC Flow Bradley R. Quinton Dept. of Electrical and Computer Engineering University of British Columbia bradq@ece.ubc.ca
Asynchronous IC Interconnect Network Design and Implementation Using a Standard ASIC Flow Bradley R. Quinton Dept. of Electrical and Computer Engineering University of British Columbia bradq@ece.ubc.ca
Introducción. Diseño de sistemas digitales.1
 Introducción Adapted from: Mary Jane Irwin ( www.cse.psu.edu/~mji ) www.cse.psu.edu/~cg431 [Original from Computer Organization and Design, Patterson & Hennessy, 2005, UCB] Diseño de sistemas digitales.1
Introducción Adapted from: Mary Jane Irwin ( www.cse.psu.edu/~mji ) www.cse.psu.edu/~cg431 [Original from Computer Organization and Design, Patterson & Hennessy, 2005, UCB] Diseño de sistemas digitales.1
Design Verification & Testing Design for Testability and Scan
 Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Overview esign for testability (FT) makes it possible to: Assure the detection of all faults in a circuit Reduce the cost and time associated with test development Reduce the execution time of performing
Automatic Logging of Operating System Effects to Guide Application-Level Architecture Simulation
 Automatic Logging of Operating System Effects to Guide Application-Level Architecture Simulation Satish Narayanasamy, Cristiano Pereira, Harish Patil, Robert Cohn, and Brad Calder Computer Science and
Automatic Logging of Operating System Effects to Guide Application-Level Architecture Simulation Satish Narayanasamy, Cristiano Pereira, Harish Patil, Robert Cohn, and Brad Calder Computer Science and
Lesson 7: SYSTEM-ON. SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY. Chapter-1L07: "Embedded Systems - ", Raj Kamal, Publs.: McGraw-Hill Education
 Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
Chapter 4 Register Transfer and Microoperations. Section 4.1 Register Transfer Language
 Chapter 4 Register Transfer and Microoperations Section 4.1 Register Transfer Language Digital systems are composed of modules that are constructed from digital components, such as registers, decoders,
Chapter 4 Register Transfer and Microoperations Section 4.1 Register Transfer Language Digital systems are composed of modules that are constructed from digital components, such as registers, decoders,
Processor Architectures
 ECPE 170 Jeff Shafer University of the Pacific Processor Architectures 2 Schedule Exam 3 Tuesday, December 6 th Caches Virtual Memory Input / Output OperaKng Systems Compilers & Assemblers Processor Architecture
ECPE 170 Jeff Shafer University of the Pacific Processor Architectures 2 Schedule Exam 3 Tuesday, December 6 th Caches Virtual Memory Input / Output OperaKng Systems Compilers & Assemblers Processor Architecture
LSN 2 Computer Processors
 LSN 2 Computer Processors Department of Engineering Technology LSN 2 Computer Processors Microprocessors Design Instruction set Processor organization Processor performance Bandwidth Clock speed LSN 2
LSN 2 Computer Processors Department of Engineering Technology LSN 2 Computer Processors Microprocessors Design Instruction set Processor organization Processor performance Bandwidth Clock speed LSN 2
CHAPTER 3 Boolean Algebra and Digital Logic
 CHAPTER 3 Boolean Algebra and Digital Logic 3.1 Introduction 121 3.2 Boolean Algebra 122 3.2.1 Boolean Expressions 123 3.2.2 Boolean Identities 124 3.2.3 Simplification of Boolean Expressions 126 3.2.4
CHAPTER 3 Boolean Algebra and Digital Logic 3.1 Introduction 121 3.2 Boolean Algebra 122 3.2.1 Boolean Expressions 123 3.2.2 Boolean Identities 124 3.2.3 Simplification of Boolean Expressions 126 3.2.4
SIM-PL: Software for teaching computer hardware at secondary schools in the Netherlands
 SIM-PL: Software for teaching computer hardware at secondary schools in the Netherlands Ben Bruidegom, benb@science.uva.nl AMSTEL Instituut Universiteit van Amsterdam Kruislaan 404 NL-1098 SM Amsterdam
SIM-PL: Software for teaching computer hardware at secondary schools in the Netherlands Ben Bruidegom, benb@science.uva.nl AMSTEL Instituut Universiteit van Amsterdam Kruislaan 404 NL-1098 SM Amsterdam
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines
 Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada ken@unb.ca Micaela Serra
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada ken@unb.ca Micaela Serra
Hardware Implementation of Improved Adaptive NoC Router with Flit Flow History based Load Balancing Selection Strategy
 Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
Hardware Implementation of Improved Adaptive NoC Rer with Flit Flow History based Load Balancing Selection Strategy Parag Parandkar 1, Sumant Katiyal 2, Geetesh Kwatra 3 1,3 Research Scholar, School of
A Lab Course on Computer Architecture
 A Lab Course on Computer Architecture Pedro López José Duato Depto. de Informática de Sistemas y Computadores Facultad de Informática Universidad Politécnica de Valencia Camino de Vera s/n, 46071 - Valencia,
A Lab Course on Computer Architecture Pedro López José Duato Depto. de Informática de Sistemas y Computadores Facultad de Informática Universidad Politécnica de Valencia Camino de Vera s/n, 46071 - Valencia,
CS352H: Computer Systems Architecture
 CS352H: Computer Systems Architecture Topic 9: MIPS Pipeline - Hazards October 1, 2009 University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell Data Hazards in ALU Instructions
CS352H: Computer Systems Architecture Topic 9: MIPS Pipeline - Hazards October 1, 2009 University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell Data Hazards in ALU Instructions
TEACHING COMPUTER ARCHITECTURE THROUGH SIMULATION (A BRIEF EVALUATION OF CPU SIMULATORS) *
 TEACHING COMPUTER ARCHITECTURE THROUGH SIMULATION (A BRIEF EVALUATION OF CPU SIMULATORS) * Timothy Stanley, PhD Computer and Network Sciences, Utah Valley University, Orem, Utah 84058, 801 863-8978, TStanley@uvu.edu
TEACHING COMPUTER ARCHITECTURE THROUGH SIMULATION (A BRIEF EVALUATION OF CPU SIMULATORS) * Timothy Stanley, PhD Computer and Network Sciences, Utah Valley University, Orem, Utah 84058, 801 863-8978, TStanley@uvu.edu
BEAGLEBONE BLACK ARCHITECTURE MADELEINE DAIGNEAU MICHELLE ADVENA
 BEAGLEBONE BLACK ARCHITECTURE MADELEINE DAIGNEAU MICHELLE ADVENA AGENDA INTRO TO BEAGLEBONE BLACK HARDWARE & SPECS CORTEX-A8 ARMV7 PROCESSOR PROS & CONS VS RASPBERRY PI WHEN TO USE BEAGLEBONE BLACK Single
BEAGLEBONE BLACK ARCHITECTURE MADELEINE DAIGNEAU MICHELLE ADVENA AGENDA INTRO TO BEAGLEBONE BLACK HARDWARE & SPECS CORTEX-A8 ARMV7 PROCESSOR PROS & CONS VS RASPBERRY PI WHEN TO USE BEAGLEBONE BLACK Single
VLSI IMPLEMENTATION OF INTERNET CHECKSUM CALCULATION FOR 10 GIGABIT ETHERNET
 VLSI IMPLEMENTATION OF INTERNET CHECKSUM CALCULATION FOR 10 GIGABIT ETHERNET Tomas Henriksson, Niklas Persson and Dake Liu Department of Electrical Engineering, Linköpings universitet SE-581 83 Linköping
VLSI IMPLEMENTATION OF INTERNET CHECKSUM CALCULATION FOR 10 GIGABIT ETHERNET Tomas Henriksson, Niklas Persson and Dake Liu Department of Electrical Engineering, Linköpings universitet SE-581 83 Linköping
Best Practises for LabVIEW FPGA Design Flow. uk.ni.com ireland.ni.com
 Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
INSTRUCTION LEVEL PARALLELISM PART VII: REORDER BUFFER
 Course on: Advanced Computer Architectures INSTRUCTION LEVEL PARALLELISM PART VII: REORDER BUFFER Prof. Cristina Silvano Politecnico di Milano cristina.silvano@polimi.it Prof. Silvano, Politecnico di Milano
Course on: Advanced Computer Architectures INSTRUCTION LEVEL PARALLELISM PART VII: REORDER BUFFER Prof. Cristina Silvano Politecnico di Milano cristina.silvano@polimi.it Prof. Silvano, Politecnico di Milano
On Demand Loading of Code in MMUless Embedded System
 On Demand Loading of Code in MMUless Embedded System Sunil R Gandhi *. Chetan D Pachange, Jr.** Mandar R Vaidya***, Swapnilkumar S Khorate**** *Pune Institute of Computer Technology, Pune INDIA (Mob- 8600867094;
On Demand Loading of Code in MMUless Embedded System Sunil R Gandhi *. Chetan D Pachange, Jr.** Mandar R Vaidya***, Swapnilkumar S Khorate**** *Pune Institute of Computer Technology, Pune INDIA (Mob- 8600867094;
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
EE482: Advanced Computer Organization Lecture #11 Processor Architecture Stanford University Wednesday, 31 May 2000. ILP Execution
 EE482: Advanced Computer Organization Lecture #11 Processor Architecture Stanford University Wednesday, 31 May 2000 Lecture #11: Wednesday, 3 May 2000 Lecturer: Ben Serebrin Scribe: Dean Liu ILP Execution
EE482: Advanced Computer Organization Lecture #11 Processor Architecture Stanford University Wednesday, 31 May 2000 Lecture #11: Wednesday, 3 May 2000 Lecturer: Ben Serebrin Scribe: Dean Liu ILP Execution
Instruction Set Architecture (ISA)
 Instruction Set Architecture (ISA) * Instruction set architecture of a machine fills the semantic gap between the user and the machine. * ISA serves as the starting point for the design of a new machine
Instruction Set Architecture (ISA) * Instruction set architecture of a machine fills the semantic gap between the user and the machine. * ISA serves as the starting point for the design of a new machine
A Processor Generation Method from Instruction Behavior Description Based on Specification of Pipeline Stages and Functional Units
 A Processor Generation Method from Instruction Behavior Description Based on Specification of Pipeline Stages and Functional Units Takeshi SHIRO, Masaaki ABE, Keishi SAKANUSHI, Yoshinori TAKEUCHI, and
A Processor Generation Method from Instruction Behavior Description Based on Specification of Pipeline Stages and Functional Units Takeshi SHIRO, Masaaki ABE, Keishi SAKANUSHI, Yoshinori TAKEUCHI, and
Using a Failure Modes, Effects and Diagnostic Analysis (FMEDA) to Measure Diagnostic Coverage in Programmable Electronic Systems.
 Using a Failure Modes, Effects and Diagnostic Analysis (FMEDA) to Measure Diagnostic Coverage in Programmable Electronic Systems. Dr. William M. Goble exida.com, 42 Short Rd., Perkasie, PA 18944 Eindhoven
Using a Failure Modes, Effects and Diagnostic Analysis (FMEDA) to Measure Diagnostic Coverage in Programmable Electronic Systems. Dr. William M. Goble exida.com, 42 Short Rd., Perkasie, PA 18944 Eindhoven
WAR: Write After Read
 WAR: Write After Read write-after-read (WAR) = artificial (name) dependence add R1, R2, R3 sub R2, R4, R1 or R1, R6, R3 problem: add could use wrong value for R2 can t happen in vanilla pipeline (reads
WAR: Write After Read write-after-read (WAR) = artificial (name) dependence add R1, R2, R3 sub R2, R4, R1 or R1, R6, R3 problem: add could use wrong value for R2 can t happen in vanilla pipeline (reads
CS101 Lecture 26: Low Level Programming. John Magee 30 July 2013 Some material copyright Jones and Bartlett. Overview/Questions
 CS101 Lecture 26: Low Level Programming John Magee 30 July 2013 Some material copyright Jones and Bartlett 1 Overview/Questions What did we do last time? How can we control the computer s circuits? How
CS101 Lecture 26: Low Level Programming John Magee 30 July 2013 Some material copyright Jones and Bartlett 1 Overview/Questions What did we do last time? How can we control the computer s circuits? How
ELEC 5260/6260/6266 Embedded Computing Systems
 ELEC 5260/6260/6266 Embedded Computing Systems Spring 2016 Victor P. Nelson Text: Computers as Components, 3 rd Edition Prof. Marilyn Wolf (Georgia Tech) Course Topics Embedded system design & modeling
ELEC 5260/6260/6266 Embedded Computing Systems Spring 2016 Victor P. Nelson Text: Computers as Components, 3 rd Edition Prof. Marilyn Wolf (Georgia Tech) Course Topics Embedded system design & modeling
Chapter 6. Inside the System Unit. What You Will Learn... Computers Are Your Future. What You Will Learn... Describing Hardware Performance
 What You Will Learn... Computers Are Your Future Chapter 6 Understand how computers represent data Understand the measurements used to describe data transfer rates and data storage capacity List the components
What You Will Learn... Computers Are Your Future Chapter 6 Understand how computers represent data Understand the measurements used to describe data transfer rates and data storage capacity List the components
Chapter 2 Basic Structure of Computers. Jin-Fu Li Department of Electrical Engineering National Central University Jungli, Taiwan
 Chapter 2 Basic Structure of Computers Jin-Fu Li Department of Electrical Engineering National Central University Jungli, Taiwan Outline Functional Units Basic Operational Concepts Bus Structures Software
Chapter 2 Basic Structure of Computers Jin-Fu Li Department of Electrical Engineering National Central University Jungli, Taiwan Outline Functional Units Basic Operational Concepts Bus Structures Software
How To Fix A 3 Bit Error In Data From A Data Point To A Bit Code (Data Point) With A Power Source (Data Source) And A Power Cell (Power Source)
 FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
Introduction to RISC Processor. ni logic Pvt. Ltd., Pune
 Introduction to RISC Processor ni logic Pvt. Ltd., Pune AGENDA What is RISC & its History What is meant by RISC Architecture of MIPS-R4000 Processor Difference Between RISC and CISC Pros and Cons of RISC
Introduction to RISC Processor ni logic Pvt. Ltd., Pune AGENDA What is RISC & its History What is meant by RISC Architecture of MIPS-R4000 Processor Difference Between RISC and CISC Pros and Cons of RISC
Encounter DFT Architect
 Full-chip, synthesis-based, power-aware test architecture development Cadence Encounter DFT Architect addresses and optimizes multiple design and manufacturing objectives such as timing, area, wiring,
Full-chip, synthesis-based, power-aware test architecture development Cadence Encounter DFT Architect addresses and optimizes multiple design and manufacturing objectives such as timing, area, wiring,
Computer organization
 Computer organization Computer design an application of digital logic design procedures Computer = processing unit + memory system Processing unit = control + datapath Control = finite state machine inputs
Computer organization Computer design an application of digital logic design procedures Computer = processing unit + memory system Processing unit = control + datapath Control = finite state machine inputs
Instruction Set Design
 Instruction Set Design Instruction Set Architecture: to what purpose? ISA provides the level of abstraction between the software and the hardware One of the most important abstraction in CS It s narrow,
Instruction Set Design Instruction Set Architecture: to what purpose? ISA provides the level of abstraction between the software and the hardware One of the most important abstraction in CS It s narrow,
ARM Architecture. ARM history. Why ARM? ARM Ltd. 1983 developed by Acorn computers. Computer Organization and Assembly Languages Yung-Yu Chuang
 ARM history ARM Architecture Computer Organization and Assembly Languages g Yung-Yu Chuang 1983 developed by Acorn computers To replace 6502 in BBC computers 4-man VLSI design team Its simplicity it comes
ARM history ARM Architecture Computer Organization and Assembly Languages g Yung-Yu Chuang 1983 developed by Acorn computers To replace 6502 in BBC computers 4-man VLSI design team Its simplicity it comes
Computer Architecture TDTS10
 why parallelism? Performance gain from increasing clock frequency is no longer an option. Outline Computer Architecture TDTS10 Superscalar Processors Very Long Instruction Word Processors Parallel computers
why parallelism? Performance gain from increasing clock frequency is no longer an option. Outline Computer Architecture TDTS10 Superscalar Processors Very Long Instruction Word Processors Parallel computers
Central Processing Unit (CPU)
 Central Processing Unit (CPU) CPU is the heart and brain It interprets and executes machine level instructions Controls data transfer from/to Main Memory (MM) and CPU Detects any errors In the following
Central Processing Unit (CPU) CPU is the heart and brain It interprets and executes machine level instructions Controls data transfer from/to Main Memory (MM) and CPU Detects any errors In the following
Central Processing Unit
 Chapter 4 Central Processing Unit 1. CPU organization and operation flowchart 1.1. General concepts The primary function of the Central Processing Unit is to execute sequences of instructions representing
Chapter 4 Central Processing Unit 1. CPU organization and operation flowchart 1.1. General concepts The primary function of the Central Processing Unit is to execute sequences of instructions representing
The ARM Architecture. With a focus on v7a and Cortex-A8
 The ARM Architecture With a focus on v7a and Cortex-A8 1 Agenda Introduction to ARM Ltd ARM Processors Overview ARM v7a Architecture/Programmers Model Cortex-A8 Memory Management Cortex-A8 Pipeline 2 ARM
The ARM Architecture With a focus on v7a and Cortex-A8 1 Agenda Introduction to ARM Ltd ARM Processors Overview ARM v7a Architecture/Programmers Model Cortex-A8 Memory Management Cortex-A8 Pipeline 2 ARM
RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition
 RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition A Tutorial Approach James O. Hamblen Georgia Institute of Technology Michael D. Furman Georgia Institute of Technology KLUWER ACADEMIC PUBLISHERS Boston
RAPID PROTOTYPING OF DIGITAL SYSTEMS Second Edition A Tutorial Approach James O. Hamblen Georgia Institute of Technology Michael D. Furman Georgia Institute of Technology KLUWER ACADEMIC PUBLISHERS Boston
NIOS II Based Embedded Web Server Development for Networking Applications
 NIOS II Based Embedded Web Server Development for Networking Applications 1 Sheetal Bhoyar, 2 Dr. D. V. Padole 1 Research Scholar, G. H. Raisoni College of Engineering, Nagpur, India 2 Professor, G. H.
NIOS II Based Embedded Web Server Development for Networking Applications 1 Sheetal Bhoyar, 2 Dr. D. V. Padole 1 Research Scholar, G. H. Raisoni College of Engineering, Nagpur, India 2 Professor, G. H.
(Refer Slide Time: 00:01:16 min)
 Digital Computer Organization Prof. P. K. Biswas Department of Electronic & Electrical Communication Engineering Indian Institute of Technology, Kharagpur Lecture No. # 04 CPU Design: Tirning & Control
Digital Computer Organization Prof. P. K. Biswas Department of Electronic & Electrical Communication Engineering Indian Institute of Technology, Kharagpur Lecture No. # 04 CPU Design: Tirning & Control
Security in the Age of Nanocomputing. Hacking Devices
 Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
OpenSPARC T1 Processor
 OpenSPARC T1 Processor The OpenSPARC T1 processor is the first chip multiprocessor that fully implements the Sun Throughput Computing Initiative. Each of the eight SPARC processor cores has full hardware
OpenSPARC T1 Processor The OpenSPARC T1 processor is the first chip multiprocessor that fully implements the Sun Throughput Computing Initiative. Each of the eight SPARC processor cores has full hardware
COMPUTER HARDWARE. Input- Output and Communication Memory Systems
 COMPUTER HARDWARE Input- Output and Communication Memory Systems Computer I/O I/O devices commonly found in Computer systems Keyboards Displays Printers Magnetic Drives Compact disk read only memory (CD-ROM)
COMPUTER HARDWARE Input- Output and Communication Memory Systems Computer I/O I/O devices commonly found in Computer systems Keyboards Displays Printers Magnetic Drives Compact disk read only memory (CD-ROM)
Q. Consider a dynamic instruction execution (an execution trace, in other words) that consists of repeats of code in this pattern:
 Pipelining HW Q. Can a MIPS SW instruction executing in a simple 5-stage pipelined implementation have a data dependency hazard of any type resulting in a nop bubble? If so, show an example; if not, prove
Pipelining HW Q. Can a MIPS SW instruction executing in a simple 5-stage pipelined implementation have a data dependency hazard of any type resulting in a nop bubble? If so, show an example; if not, prove
CHAPTER 4 MARIE: An Introduction to a Simple Computer
 CHAPTER 4 MARIE: An Introduction to a Simple Computer 4.1 Introduction 195 4.2 CPU Basics and Organization 195 4.2.1 The Registers 196 4.2.2 The ALU 197 4.2.3 The Control Unit 197 4.3 The Bus 197 4.4 Clocks
CHAPTER 4 MARIE: An Introduction to a Simple Computer 4.1 Introduction 195 4.2 CPU Basics and Organization 195 4.2.1 The Registers 196 4.2.2 The ALU 197 4.2.3 The Control Unit 197 4.3 The Bus 197 4.4 Clocks
Building Blocks for PRU Development
 Building Blocks for PRU Development Module 1 PRU Hardware Overview This session covers a hardware overview of the PRU-ICSS Subsystem. Author: Texas Instruments, Sitara ARM Processors Oct 2014 2 ARM SoC
Building Blocks for PRU Development Module 1 PRU Hardware Overview This session covers a hardware overview of the PRU-ICSS Subsystem. Author: Texas Instruments, Sitara ARM Processors Oct 2014 2 ARM SoC
find model parameters, to validate models, and to develop inputs for models. c 1994 Raj Jain 7.1
 Monitors Monitor: A tool used to observe the activities on a system. Usage: A system programmer may use a monitor to improve software performance. Find frequently used segments of the software. A systems
Monitors Monitor: A tool used to observe the activities on a system. Usage: A system programmer may use a monitor to improve software performance. Find frequently used segments of the software. A systems
Technical Note. Micron NAND Flash Controller via Xilinx Spartan -3 FPGA. Overview. TN-29-06: NAND Flash Controller on Spartan-3 Overview
 Technical Note TN-29-06: NAND Flash Controller on Spartan-3 Overview Micron NAND Flash Controller via Xilinx Spartan -3 FPGA Overview As mobile product capabilities continue to expand, so does the demand
Technical Note TN-29-06: NAND Flash Controller on Spartan-3 Overview Micron NAND Flash Controller via Xilinx Spartan -3 FPGA Overview As mobile product capabilities continue to expand, so does the demand
Implementation and Design of AES S-Box on FPGA
 International Journal of Research in Engineering and Science (IJRES) ISSN (Online): 232-9364, ISSN (Print): 232-9356 Volume 3 Issue ǁ Jan. 25 ǁ PP.9-4 Implementation and Design of AES S-Box on FPGA Chandrasekhar
International Journal of Research in Engineering and Science (IJRES) ISSN (Online): 232-9364, ISSN (Print): 232-9356 Volume 3 Issue ǁ Jan. 25 ǁ PP.9-4 Implementation and Design of AES S-Box on FPGA Chandrasekhar
A SystemC Transaction Level Model for the MIPS R3000 Processor
 SETIT 2007 4 th International Conference: Sciences of Electronic, Technologies of Information and Telecommunications March 25-29, 2007 TUNISIA A SystemC Transaction Level Model for the MIPS R3000 Processor
SETIT 2007 4 th International Conference: Sciences of Electronic, Technologies of Information and Telecommunications March 25-29, 2007 TUNISIA A SystemC Transaction Level Model for the MIPS R3000 Processor
Techniques for Accurate Performance Evaluation in Architecture Exploration
 IEEE TRANSACTIONS ON VERY LARGE SCALE INTEGRATION (VLSI) SYSTEMS, VOL. 11, NO. 4, AUGUST 2003 601 Techniques for Accurate Performance Evaluation in Architecture Exploration George Hadjiyiannis and Srinivas
IEEE TRANSACTIONS ON VERY LARGE SCALE INTEGRATION (VLSI) SYSTEMS, VOL. 11, NO. 4, AUGUST 2003 601 Techniques for Accurate Performance Evaluation in Architecture Exploration George Hadjiyiannis and Srinivas
Design and Implementation of Concurrent Error Detection and Data Recovery Architecture for Motion Estimation Testing Applications
 Design and Implementation of Concurrent Error Detection and Data Recovery Architecture for Motion Estimation Testing Applications 1 Abhilash B T, 2 Veerabhadrappa S T, 3 Anuradha M G Department of E&C,
Design and Implementation of Concurrent Error Detection and Data Recovery Architecture for Motion Estimation Testing Applications 1 Abhilash B T, 2 Veerabhadrappa S T, 3 Anuradha M G Department of E&C,
Overview. CISC Developments. RISC Designs. CISC Designs. VAX: Addressing Modes. Digital VAX
 Overview CISC Developments Over Twenty Years Classic CISC design: Digital VAX VAXÕs RISC successor: PRISM/Alpha IntelÕs ubiquitous 80x86 architecture Ð 8086 through the Pentium Pro (P6) RJS 2/3/97 Philosophy
Overview CISC Developments Over Twenty Years Classic CISC design: Digital VAX VAXÕs RISC successor: PRISM/Alpha IntelÕs ubiquitous 80x86 architecture Ð 8086 through the Pentium Pro (P6) RJS 2/3/97 Philosophy
The implementation and performance/cost/power analysis of the network security accelerator on SoC applications
 The implementation and performance/cost/power analysis of the network security accelerator on SoC applications Ruei-Ting Gu grating@eslab.cse.nsysu.edu.tw Kuo-Huang Chung khchung@eslab.cse.nsysu.edu.tw
The implementation and performance/cost/power analysis of the network security accelerator on SoC applications Ruei-Ting Gu grating@eslab.cse.nsysu.edu.tw Kuo-Huang Chung khchung@eslab.cse.nsysu.edu.tw
AC 2007-2027: A PROCESSOR DESIGN PROJECT FOR A FIRST COURSE IN COMPUTER ORGANIZATION
 AC 2007-2027: A PROCESSOR DESIGN PROJECT FOR A FIRST COURSE IN COMPUTER ORGANIZATION Michael Black, American University Manoj Franklin, University of Maryland-College Park American Society for Engineering
AC 2007-2027: A PROCESSOR DESIGN PROJECT FOR A FIRST COURSE IN COMPUTER ORGANIZATION Michael Black, American University Manoj Franklin, University of Maryland-College Park American Society for Engineering
Using Graphics and Animation to Visualize Instruction Pipelining and its Hazards
 Using Graphics and Animation to Visualize Instruction Pipelining and its Hazards Per Stenström, Håkan Nilsson, and Jonas Skeppstedt Department of Computer Engineering, Lund University P.O. Box 118, S-221
Using Graphics and Animation to Visualize Instruction Pipelining and its Hazards Per Stenström, Håkan Nilsson, and Jonas Skeppstedt Department of Computer Engineering, Lund University P.O. Box 118, S-221
The Designer's Guide to VHDL
 The Designer's Guide to VHDL Third Edition Peter J. Ashenden EDA CONSULTANT, ASHENDEN DESIGNS PTY. LTD. ADJUNCT ASSOCIATE PROFESSOR, ADELAIDE UNIVERSITY AMSTERDAM BOSTON HEIDELBERG LONDON m^^ yj 1 ' NEW
The Designer's Guide to VHDL Third Edition Peter J. Ashenden EDA CONSULTANT, ASHENDEN DESIGNS PTY. LTD. ADJUNCT ASSOCIATE PROFESSOR, ADELAIDE UNIVERSITY AMSTERDAM BOSTON HEIDELBERG LONDON m^^ yj 1 ' NEW
