Securing Computer Hardware Using 3D Integrated Circuit (IC) Technology and Split Manufacturing for Obfuscation
|
|
|
- Linette Atkinson
- 7 years ago
- Views:
Transcription
1 Securing Computer Hardware Using D Integrated Circuit (IC) Technology and Split Manufacturing for Obfuscation Frank Imeson ECE, University of Waterloo USENIX Security Collaborators: Ariq Emtenan, Siddharth Garg, and Mahesh V. Tripunitara (Waterloo). Frank Imeson, Waterloo ECE D Hardware Security /6
2 Computer Hardware Computer Hardware = Digital IC Physical realization of digital logic Complex and ubiquitous Credit: Frank Imeson, Waterloo ECE D Hardware Security /6
3 Introduction Attack Model k-security Layout Randomization Summary Manufacturing Process HDL Netlist IC case(display_state) UPDATE : begin seg00_reg <= seg00; seg0_reg <= seg0; // update leds if (count00[0]) begin state <= UPDATE; end default : begin ons00 <= 0; count00 <= 0; display_state <= UPDATE; end endcase Credit: Frank Imeson, Waterloo ECE D Hardware Security /6
4 Threat Model Netlist External Foundry ICs News story, May 0: Security backdoor found in US military chip made in [foreign country]. Frank Imeson, Waterloo ECE D Hardware Security /6
5 Attack Types Examples: Privilege escalation [King et al., LEET 08] Leaking private information [Skorobogatov et al., CHES 0] Credit: King et al., LEET 08 Frank Imeson, Waterloo ECE D Hardware Security /6
6 Premise Successful Attack Uniquely identify at least one gate Credit: Cynthia Sturton, Matthew Hicks, David Wagner, and Samuel T. King. Defeating UCI: Building stealthy and malicious hardware. In Security and Privacy (SP), 0 IEEE Symposium on, pp IEEE, 0. Frank Imeson, Waterloo ECE D Hardware Security 6/6
7 Premise Successful Attack Uniquely identify at least one gate Credit: Cynthia Sturton, Matthew Hicks, David Wagner, and Samuel T. King. Defeating UCI: Building stealthy and malicious hardware. In Security and Privacy (SP), 0 IEEE Symposium on, pp IEEE, 0. Frank Imeson, Waterloo ECE D Hardware Security 6/6
8 Example Full Adder Netlist C IN S A B M C OUT T Malicious Gate Frank Imeson, Waterloo ECE D Hardware Security 7/6
9 Example Full Adder Netlist C IN S A B 0 0 M C OUT T Frank Imeson, Waterloo ECE D Hardware Security 7/6
10 Example Full Adder Netlist C IN S A B 0 M 0 C OUT T Frank Imeson, Waterloo ECE D Hardware Security 7/6
11 Our Solution Circuit Obfuscation Full Adder Netlist C IN A B S C OUT Obfuscated Netlist U X V W Y Frank Imeson, Waterloo ECE D Hardware Security 8/6
12 Our Solution Circuit Obfuscation Full Adder Netlist C IN A B S C OUT Obfuscated Netlist U X V W Y Frank Imeson, Waterloo ECE D Hardware Security 8/6
13 D IC Technology Top Tier (Hidden) Two or more tiers Tiers are connected via bond points Wire only tiers are relatively inexpensive Hidden Wires IO Pins Substrate Bond Points Unhidden Wires Transistors/Gates Bottom Tier (Obfuscated) Frank Imeson, Waterloo ECE D Hardware Security 9/6
14 D Xilinx FPGA 6.8 billion transistors,9,60 logic cells. Mbits of SRAM 6, Kbits of RAM 00 user I/O.D Credit: Frank Imeson, Waterloo ECE D Hardware Security 0/6
15 Circuit Obfuscation with D Technology A B CIN S C OUT Hide Wires X Place and Route U V W Y Hidden Circuit Fabrication In House Stacking Obfuscated Circuit Fabrication Outsourced Frank Imeson, Waterloo ECE D Hardware Security /6
16 Circuit Obfuscation with D Technology A B CIN S C OUT Hide Wires X Place and Route U V W Y Hidden Circuit Fabrication In House Stacking Obfuscated Circuit Fabrication Outsourced Frank Imeson, Waterloo ECE D Hardware Security /6
17 Circuit Obfuscation with D Technology A B CIN S C OUT Hide Wires X Place and Route U V W Y Hidden Circuit Fabrication In House Stacking Obfuscated Circuit Fabrication Outsourced Frank Imeson, Waterloo ECE D Hardware Security /6
18 Attack Model Summary Original Netlist C IN S G A B C OUT Obfuscated Circuit V X U W Y H W X Y V U Frank Imeson, Waterloo ECE D Hardware Security /6
19 Attack Model Summary Original Netlist C IN S G A B C OUT Obfuscated Circuit V X U W Y H W X Y V U Frank Imeson, Waterloo ECE D Hardware Security /6
20 What an Attacker Needs to Do Input graphs G and H G H Y W V X U Frank Imeson, Waterloo ECE D Hardware Security /6
21 What an Attacker Needs to Do Input graphs G and H Find subgraph isomorphisms G H W X Y V U Frank Imeson, Waterloo ECE D Hardware Security /6
22 What an Attacker Needs to Do Input graphs G and H Find subgraph isomorphisms G H W X Y V U M M M M Frank Imeson, Waterloo ECE D Hardware Security /6
23 k-security S(w) = G H Y W V X U A vertex v H is k-secure if there exist at least k subgraph isomorphisms each of which maps v to a distinct vertex in G. An obfuscated graph (circuit) H is k-secure if every vertex (gate) in H is k-secure. Frank Imeson, Waterloo ECE D Hardware Security /6
24 k-security S(w) = S(v),S(u),S(x) = G H W Y V X U A vertex v H is k-secure if there exist at least k subgraph isomorphisms each of which maps v to a distinct vertex in G. An obfuscated graph (circuit) H is k-secure if every vertex (gate) in H is k-secure. Frank Imeson, Waterloo ECE D Hardware Security /6
25 k-security S(w) = S(v),S(u),S(x) = S(y) = G H W X Y V U A vertex v H is k-secure if there exist at least k subgraph isomorphisms each of which maps v to a distinct vertex in G. An obfuscated graph (circuit) H is k-secure if every vertex (gate) in H is k-secure. Frank Imeson, Waterloo ECE D Hardware Security /6
26 k-security S(w) = S(v),S(u),S(x) = S(y) = S(H) = G H W X Y V U A vertex v H is k-secure if there exist at least k subgraph isomorphisms each of which maps v to a distinct vertex in G. An obfuscated graph (circuit) H is k-secure if every vertex (gate) in H is k-secure. Frank Imeson, Waterloo ECE D Hardware Security /6
27 Computational Complexity G, H is k-secure NP-complete. We investigated two approaches: Reduction to Subgraph Isomorphism and use of VF solver Reduction to SAT and use of MiniSAT solver 00 Avg Time vf 0.0 sat e Number of Vertices Frank Imeson, Waterloo ECE D Hardware Security /6
28 Cost vs. Security Cost = Number of hidden edges G 6 Goal: Explore Cost vs. Security trade-off Greedy approach Start with no edges in H. H 6 Frank Imeson, Waterloo ECE D Hardware Security 6/6
29 Cost vs. Security Cost = Number of hidden edges G 6 Goal: Explore Cost vs. Security trade-off Greedy approach Start with no edges in H. Greedily pick an edge to add to H that maximizes security. H 6 Frank Imeson, Waterloo ECE D Hardware Security 6/6
30 Cost vs. Security Cost = Number of hidden edges G 6 Goal: Explore Cost vs. Security trade-off Greedy approach Start with no edges in H. Greedily pick an edge to add to H that maximizes security. Repeat. H 6 Frank Imeson, Waterloo ECE D Hardware Security 6/6
31 Security vs. Number of Removed Edges Security greedy 0 rand % Hidden Wires (Cost) Figure: Experiments on the c circuit, which contains 0 edges. The c circuit is a 7-channel interrupt controller. Frank Imeson, Waterloo ECE D Hardware Security 7/6
32 Security vs. Number of Removed Edges Security 0 0 Lower Cost 0 greedy 0 rand % Hidden Wires (Cost) Figure: Experiments on the c circuit, which contains 0 edges. The c circuit is a 7-channel interrupt controller. Frank Imeson, Waterloo ECE D Hardware Security 7/6
33 Layout Randomization Netlist A B CIN S C OUT Layout Placement of Gates Routing Placement of Wires Frank Imeson, Waterloo ECE D Hardware Security 8/6
34 Layout Randomization Obfuscated Netlist Hidden Netlist Layout Routing Unhidden Wires Hidden Wires Frank Imeson, Waterloo ECE D Hardware Security 8/6
35 Layout and Routing Results (a) Unsecure Circuit (b) Obfuscated Tier (c) Hidden Tier Figure: Layout of c without any security (left), and the obfuscated (middle) and hidden tiers of an 8-secure version of c circuit. Green and red lines correspond to metal wires. Frank Imeson, Waterloo ECE D Hardware Security 9/6
36 Wire Length Distribution Ratio Unsecure Obfuscated Hidden Distance (um) Figure: Comparison of the wire length distribution for the unsecured, obfuscated and hidden circuits. Also the hidden wire length distribution passes the χ test when compared to a random distribution Frank Imeson, Waterloo ECE D Hardware Security 0/6
37 Power and Delay Costs. Ratio Delay Power Security Figure: Power and delay ratio calculated from base/unsecured circuit. Frank Imeson, Waterloo ECE D Hardware Security /6
38 Case Study: DES Circuit Plaintext IP Symmetric key-based encryption/ decryption algorithm.,000 gate implementation from OpenCores library. A fault in LSB of th round reveals secret key []. Round 0 Round Round Round 6 FB Ciphertext Frank Imeson, Waterloo ECE D Hardware Security /6
39 Case Study: DES Circuit Plaintext IP Symmetric key-based encryption/ decryption algorithm.,000 gate implementation from OpenCores library. A fault in LSB of th round reveals secret key []. 6-secure circuit is obtained by removing only % of wires. Further lifting can increase security. Round 0 Round Round Round 6 FB Ciphertext Frank Imeson, Waterloo ECE D Hardware Security /6
40 Impact on Attack Footprint Implemented a 6-secure DES circuit. th round LSB is actually -secure. 0x area overhead to attack a -secure gate. Trigger Target Attacking a non-secure circuit Attacking a k-secure circuit Trigger t target t target FSM 8:6 t t Modified Target t Attacking all k possible targets t target Frank Imeson, Waterloo ECE D Hardware Security /6
41 Raising the Bar on the Attacker Attack out of k gates or Attack all k gates MIPS MIPS Frank Imeson, Waterloo ECE D Hardware Security /6
42 Related Work and References Alina Campan and Traian Truta. Data and structural k-anonymity in social networks. Privacy, Security, and Trust in KDD, pages, 009. Alex Baumgarten, Michael Steffen, Matthew Clausman, and Joseph Zambreno. A case study in hardware trojan design and implementation. International Journal of Information Security, 0():, 0. Dan Boneh, Richard DeMillo, and Richard Lipton. On the importance of checking cryptographic protocols for faults. In Advances in CryptologyEUROCRYPT97, pages 7. Springer, 997. F. Brglez. Neutral netlist of ten combinational benchmark circuits and a target translator in fortran. In Special session on ATPG and fault simulation, Proc. IEEE Int. Symp. Circuits and Systems, June 98, pages , 98. Y. Jin, N. Kupp, and Y. Makris. Experiences in hardware trojan design and implementation. In Hardware-Oriented Security and Trust, 009. HOST 09. IEEE International Workshop on, pages 0 7. IEEE, 009. S. h and C. Woods. Breakthrough silicon scanning discovers backdoor in military chip. Cryptographic Hardware and Embedded Systems CHES 0, pages 0, 0. Frank Imeson, Waterloo ECE D Hardware Security /6
43 Frank Imeson, Waterloo ECE D Hardware Security 6/6
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl chris@flylogic.net nohl@srlabs.de Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl chris@flylogic.net nohl@srlabs.de Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Understanding Integrated Circuit Security Threats. Asif Iqbal Senior Program Manager, Apple Inc. SDM 11
 Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Understanding Integrated Circuit Security Threats Asif Iqbal Senior Program Manager, Apple Inc. SDM 11 Outline Vulnerability at different layers and relative impact Some Cases and Proof of Concepts Integrated
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Improving Hardware Security by Using Hidden Information of Computer
 Improving Hardware Security by Using Hidden Information of Computer System Ilya Levin, 2 Osnat Keren, 2 Vladimir Sinelnikov * Tel Aviv University, ilia@post.tau.ac.il 2 Bar Ilan University, kereno@eng.biu.ac.il
Improving Hardware Security by Using Hidden Information of Computer System Ilya Levin, 2 Osnat Keren, 2 Vladimir Sinelnikov * Tel Aviv University, ilia@post.tau.ac.il 2 Bar Ilan University, kereno@eng.biu.ac.il
Strengthen RFID Tags Security Using New Data Structure
 International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
Cryptographic Rights Management of FPGA Intellectual Property Cores
 Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom tom@algotronix.com ABSTRACT As the capacity of FPGA s increases
Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom tom@algotronix.com ABSTRACT As the capacity of FPGA s increases
Implementation Details
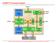 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Implementation of Full -Parallelism AES Encryption and Decryption
 Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
An Efficiency Keyword Search Scheme to improve user experience for Encrypted Data in Cloud
 , pp.246-252 http://dx.doi.org/10.14257/astl.2014.49.45 An Efficiency Keyword Search Scheme to improve user experience for Encrypted Data in Cloud Jiangang Shu ab Xingming Sun ab Lu Zhou ab Jin Wang ab
, pp.246-252 http://dx.doi.org/10.14257/astl.2014.49.45 An Efficiency Keyword Search Scheme to improve user experience for Encrypted Data in Cloud Jiangang Shu ab Xingming Sun ab Lu Zhou ab Jin Wang ab
Security in the Age of Nanocomputing. Hacking Devices
 Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
Security in the Age of Nanocomputing Matthew Tan Creti Hacking Devices The ESA estimates its total worldwide losses due to piracy at $3 billion annually [2] One million unlocked iphones could cost Apple
PFP Technology White Paper
 PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
3D innovations: From design to reliable systems
 3D innovations: From design to reliable systems Uwe Knöchel, Andy Heinig Fraunhofer IIS, Design Automation Division Zeunerstraße 38, 01069 Dresden uwe.knoechel@eas.iis.fraunhofer.de Phone: +49 351 4640
3D innovations: From design to reliable systems Uwe Knöchel, Andy Heinig Fraunhofer IIS, Design Automation Division Zeunerstraße 38, 01069 Dresden uwe.knoechel@eas.iis.fraunhofer.de Phone: +49 351 4640
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Best Practises for LabVIEW FPGA Design Flow. uk.ni.com ireland.ni.com
 Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Tutorial 3. June 8, 2015
 Tutorial 3 June 8, 2015 I. Basic Notions 1. Multiple-choice (Review Questions Chapter 6, 8 and 11) 2. Answers by a small paragraph (Chapter 2: viruses: MBR, rootkits, ) Multiple choice X. Which is the
Tutorial 3 June 8, 2015 I. Basic Notions 1. Multiple-choice (Review Questions Chapter 6, 8 and 11) 2. Answers by a small paragraph (Chapter 2: viruses: MBR, rootkits, ) Multiple choice X. Which is the
A Cost-efficient Building Automation Security Testbed for Educational Purposes
 A Cost-efficient Building Automation Security Testbed for Educational Purposes Jaspreet Kaur, Michael Meier, Sebastian Szlósarczyk and Steffen Wendzel Cyber Security Department Fraunhofer Institute for
A Cost-efficient Building Automation Security Testbed for Educational Purposes Jaspreet Kaur, Michael Meier, Sebastian Szlósarczyk and Steffen Wendzel Cyber Security Department Fraunhofer Institute for
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Performance Oriented Management System for Reconfigurable Network Appliances
 Performance Oriented Management System for Reconfigurable Network Appliances Hiroki Matsutani, Ryuji Wakikawa, Koshiro Mitsuya and Jun Murai Faculty of Environmental Information, Keio University Graduate
Performance Oriented Management System for Reconfigurable Network Appliances Hiroki Matsutani, Ryuji Wakikawa, Koshiro Mitsuya and Jun Murai Faculty of Environmental Information, Keio University Graduate
Security Aspects of. Database Outsourcing. Vahid Khodabakhshi Hadi Halvachi. Dec, 2012
 Security Aspects of Database Outsourcing Dec, 2012 Vahid Khodabakhshi Hadi Halvachi Security Aspects of Database Outsourcing Security Aspects of Database Outsourcing 2 Outline Introduction to Database
Security Aspects of Database Outsourcing Dec, 2012 Vahid Khodabakhshi Hadi Halvachi Security Aspects of Database Outsourcing Security Aspects of Database Outsourcing 2 Outline Introduction to Database
Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits)
 Page 1 of 6 Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits) TNCC Cybersecurity Program web page: http://tncc.edu/programs/cyber-security Course Description: Encompasses
Page 1 of 6 Course Content Summary ITN 261 Network Attacks, Computer Crime and Hacking (4 Credits) TNCC Cybersecurity Program web page: http://tncc.edu/programs/cyber-security Course Description: Encompasses
Network Algorithms for Homeland Security
 Network Algorithms for Homeland Security Mark Goldberg and Malik Magdon-Ismail Rensselaer Polytechnic Institute September 27, 2004. Collaborators J. Baumes, M. Krishmamoorthy, N. Preston, W. Wallace. Partially
Network Algorithms for Homeland Security Mark Goldberg and Malik Magdon-Ismail Rensselaer Polytechnic Institute September 27, 2004. Collaborators J. Baumes, M. Krishmamoorthy, N. Preston, W. Wallace. Partially
The Reduced Address Space (RAS) for Application Memory Authentication
 The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
Layout and Cross-section of an inverter. Lecture 5. Layout Design. Electric Handles Objects. Layout & Fabrication. A V i
 Layout and Cross-section of an inverter Lecture 5 A Layout Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London V DD Q p A V i V o URL: www.ee.ic.ac.uk/pcheung/
Layout and Cross-section of an inverter Lecture 5 A Layout Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London V DD Q p A V i V o URL: www.ee.ic.ac.uk/pcheung/
Contents. System Development Models and Methods. Design Abstraction and Views. Synthesis. Control/Data-Flow Models. System Synthesis Models
 System Development Models and Methods Dipl.-Inf. Mirko Caspar Version: 10.02.L.r-1.0-100929 Contents HW/SW Codesign Process Design Abstraction and Views Synthesis Control/Data-Flow Models System Synthesis
System Development Models and Methods Dipl.-Inf. Mirko Caspar Version: 10.02.L.r-1.0-100929 Contents HW/SW Codesign Process Design Abstraction and Views Synthesis Control/Data-Flow Models System Synthesis
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
FIDES: Enhancing Trust in Reconfigurable Based Hardware Systems
 FIDES: Enhancing Trust in Reconfigurable Based Hardware Systems Devu Manikantan Shila, Vivek Venugopalan United Technologies Research Center 411 Silver Lane, E Hartford, CT USA Email:{manikad, venugov}@utrc.utc.com
FIDES: Enhancing Trust in Reconfigurable Based Hardware Systems Devu Manikantan Shila, Vivek Venugopalan United Technologies Research Center 411 Silver Lane, E Hartford, CT USA Email:{manikad, venugov}@utrc.utc.com
KEEP IT SYNPLE STUPID
 Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain firstname.lastname@tut.fi Department of Computer
System-on. on-chip Design Flow. Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems. jouni.tomberg@tut.
 System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems jouni.tomberg@tut.fi 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
System-on on-chip Design Flow Prof. Jouni Tomberg Tampere University of Technology Institute of Digital and Computer Systems jouni.tomberg@tut.fi 26.03.2003 Jouni Tomberg / TUT 1 SoC - How and with whom?
Hardware Trojans: A Threat for CyberSecurity
 Hardware Trojans: A Threat for CyberSecurity Julien Francq julien.francq@cassidian.com Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
Hardware Trojans: A Threat for CyberSecurity Julien Francq julien.francq@cassidian.com Cassidian CyberSecurity 2013, July the 8th Outline 1 Introduction to Hardware Trojans 2 3 4 5 2 1 Introduction to
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 2 Systems Threats and Risks
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 2 Systems Threats and Risks Objectives Describe the different types of software-based attacks List types of hardware attacks Define
ARTIFICIAL NEURAL CRYPTOGRAPHY DATAGRAM HIDING TECHNIQUES FOR COMPUTER SECURITY OBJECTS REGISTER
 International Journal of Computer Engineering & Technology (IJCET) Volume 7, Issue 2, March-April 2016, pp. 36 43, Article ID: IJCET_07_02_005 Available online at http://www.iaeme.com/ijcet/issues.asp?jtype=ijcet&vtype=7&itype=2
International Journal of Computer Engineering & Technology (IJCET) Volume 7, Issue 2, March-April 2016, pp. 36 43, Article ID: IJCET_07_02_005 Available online at http://www.iaeme.com/ijcet/issues.asp?jtype=ijcet&vtype=7&itype=2
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Computer Networks. Network Security and Ethics. Week 14. College of Information Science and Engineering Ritsumeikan University
 Computer Networks Network Security and Ethics Week 14 College of Information Science and Engineering Ritsumeikan University Security Intro for Admins l Network administrators can break security into two
Computer Networks Network Security and Ethics Week 14 College of Information Science and Engineering Ritsumeikan University Security Intro for Admins l Network administrators can break security into two
Agenda. Michele Taliercio, Il circuito Integrato, Novembre 2001
 Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Agenda Introduzione Il mercato Dal circuito integrato al System on a Chip (SoC) La progettazione di un SoC La tecnologia Una fabbrica di circuiti integrati 28 How to handle complexity G The engineering
Intel s Revolutionary 22 nm Transistor Technology
 Intel s Revolutionary 22 nm Transistor Technology Mark Bohr Intel Senior Fellow Kaizad Mistry 22 nm Program Manager May, 2011 1 Key Messages Intel is introducing revolutionary Tri-Gate transistors on its
Intel s Revolutionary 22 nm Transistor Technology Mark Bohr Intel Senior Fellow Kaizad Mistry 22 nm Program Manager May, 2011 1 Key Messages Intel is introducing revolutionary Tri-Gate transistors on its
Pavithra.S, Vaishnavi.M, Vinothini.M, Umadevi.V
 International Journal of Scientific & Engineering Research, Volume 6, Issue 4, April-2015 965 OPTIMIZATION OF AES ALGORITHM USING HARDWARE AND SOFTWARE Pavithra.S, Vaishnavi.M, Vinothini.M, Umadevi.V Abstract-In
International Journal of Scientific & Engineering Research, Volume 6, Issue 4, April-2015 965 OPTIMIZATION OF AES ALGORITHM USING HARDWARE AND SOFTWARE Pavithra.S, Vaishnavi.M, Vinothini.M, Umadevi.V Abstract-In
Designing a Schematic and Layout in PCB Artist
 Designing a Schematic and Layout in PCB Artist Application Note Max Cooper March 28 th, 2014 ECE 480 Abstract PCB Artist is a free software package that allows users to design and layout a printed circuit
Designing a Schematic and Layout in PCB Artist Application Note Max Cooper March 28 th, 2014 ECE 480 Abstract PCB Artist is a free software package that allows users to design and layout a printed circuit
Center of Academic Excellence Cyber Operations Program 2013 Application
 Center of Academic Excellence Cyber Operations Program 2013 Application Name of Institution: Mailing Address of Institution: Date: Institution s President s Name and Official Email Address: Department
Center of Academic Excellence Cyber Operations Program 2013 Application Name of Institution: Mailing Address of Institution: Date: Institution s President s Name and Official Email Address: Department
Secure and Efficient Data Retrieval Process based on Hilbert Space Filling Curve
 Secure and Efficient Data Retrieval Process based on Hilbert Space Filling Curve N.S. Jeya karthikka PG Scholar Sri Ramakrishna Engg Collg S.Bhaggiaraj Assistant Professor Sri Ramakrishna Engg Collg V.Sumathy
Secure and Efficient Data Retrieval Process based on Hilbert Space Filling Curve N.S. Jeya karthikka PG Scholar Sri Ramakrishna Engg Collg S.Bhaggiaraj Assistant Professor Sri Ramakrishna Engg Collg V.Sumathy
Batch Decryption of Encrypted Short Messages and Its Application on Concurrent SSL Handshakes
 Batch Decryption of ncrypted Short Messages and Its Application on Concurrent SSL Handshakes Yongdong Wu and Feng Bao System and Security Department Institute for Infocomm Research 21, Heng Mui Keng Terrace,
Batch Decryption of ncrypted Short Messages and Its Application on Concurrent SSL Handshakes Yongdong Wu and Feng Bao System and Security Department Institute for Infocomm Research 21, Heng Mui Keng Terrace,
Block encryption. CS-4920: Lecture 7 Secret key cryptography. Determining the plaintext ciphertext mapping. CS4920-Lecture 7 4/1/2015
 CS-4920: Lecture 7 Secret key cryptography Reading Chapter 3 (pp. 59-75, 92-93) Today s Outcomes Discuss block and key length issues related to secret key cryptography Define several terms related to secret
CS-4920: Lecture 7 Secret key cryptography Reading Chapter 3 (pp. 59-75, 92-93) Today s Outcomes Discuss block and key length issues related to secret key cryptography Define several terms related to secret
That Point of Sale is a PoS
 SESSION ID: HTA-W02 That Point of Sale is a PoS Charles Henderson Vice President Managed Security Testing Trustwave @angus_tx David Byrne Senior Security Associate Bishop Fox Agenda POS Architecture Breach
SESSION ID: HTA-W02 That Point of Sale is a PoS Charles Henderson Vice President Managed Security Testing Trustwave @angus_tx David Byrne Senior Security Associate Bishop Fox Agenda POS Architecture Breach
7 Network Security. 7.1 Introduction 7.2 Improving the Security 7.3 Internet Security Framework. 7.5 Absolute Security?
 7 Network Security 7.1 Introduction 7.2 Improving the Security 7.3 Internet Security Framework 7.4 Firewalls 7.5 Absolute Security? 7.1 Introduction Security of Communications data transport e.g. risk
7 Network Security 7.1 Introduction 7.2 Improving the Security 7.3 Internet Security Framework 7.4 Firewalls 7.5 Absolute Security? 7.1 Introduction Security of Communications data transport e.g. risk
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge
 Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
Internet Anonymity and the Design Process - A Practical Approach
 anon.next: A Framework for Privacy in the Next Generation Internet Matthew Wright Department of Computer Science and Engineering, The University of Texas at Arlington, Arlington, TX, USA, mwright@uta.edu,
anon.next: A Framework for Privacy in the Next Generation Internet Matthew Wright Department of Computer Science and Engineering, The University of Texas at Arlington, Arlington, TX, USA, mwright@uta.edu,
Towards a Hardware Trojan Detection Cycle
 Towards a Hardware Trojan Detection Cycle Adrian Dabrowski, Heidelinde Hobel, Johanna Ullrich, Katharina Krombholz, Edgar Weippl SBA Research, Vienna, Austria E-Mail: (firstletterfirstname)(lastname)@sba-research.org
Towards a Hardware Trojan Detection Cycle Adrian Dabrowski, Heidelinde Hobel, Johanna Ullrich, Katharina Krombholz, Edgar Weippl SBA Research, Vienna, Austria E-Mail: (firstletterfirstname)(lastname)@sba-research.org
Testing & Verification of Digital Circuits ECE/CS 5745/6745. Hardware Verification using Symbolic Computation
 Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla (kalla@ece.utah.edu) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
Testing & Verification of Digital Circuits ECE/CS 5745/6745 Hardware Verification using Symbolic Computation Instructor: Priyank Kalla (kalla@ece.utah.edu) 3 Credits Mon, Wed, 1:25-2:45pm, WEB L105 Office
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler
 ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
ARM Cortex-A9 MPCore Multicore Processor Hierarchical Implementation with IC Compiler DAC 2008 Philip Watson Philip Watson Implementation Environment Program Manager ARM Ltd Background - Who Are We? Processor
Architectural Level Power Consumption of Network on Chip. Presenter: YUAN Zheng
 Architectural Level Power Consumption of Network Presenter: YUAN Zheng Why Architectural Low Power Design? High-speed and large volume communication among different parts on a chip Problem: Power consumption
Architectural Level Power Consumption of Network Presenter: YUAN Zheng Why Architectural Low Power Design? High-speed and large volume communication among different parts on a chip Problem: Power consumption
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems
 Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC Melanie.D.Berg@NASA.gov 2. NASA/GSFC Kenneth.A.LaBel@NASA.gov
Programmable Logic IP Cores in SoC Design: Opportunities and Challenges
 Programmable Logic IP Cores in SoC Design: Opportunities and Challenges Steven J.E. Wilton and Resve Saleh Department of Electrical and Computer Engineering University of British Columbia Vancouver, B.C.,
Programmable Logic IP Cores in SoC Design: Opportunities and Challenges Steven J.E. Wilton and Resve Saleh Department of Electrical and Computer Engineering University of British Columbia Vancouver, B.C.,
Managing Security in FPGA-Based Embedded Systems
 Managing Security in FPGA-Based Embedded Systems Ted Huffmire Naval Postgraduate School Timothy Sherwood University of California, Santa Barbara Brett Brotherton Special Technologies Laboratory Ryan Kastner
Managing Security in FPGA-Based Embedded Systems Ted Huffmire Naval Postgraduate School Timothy Sherwood University of California, Santa Barbara Brett Brotherton Special Technologies Laboratory Ryan Kastner
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 1 January 9, 2012 CPSC 467b, Lecture 1 1/22 Course Overview Symmetric Cryptography CPSC 467b, Lecture 1 2/22 Course Overview CPSC
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 1 January 9, 2012 CPSC 467b, Lecture 1 1/22 Course Overview Symmetric Cryptography CPSC 467b, Lecture 1 2/22 Course Overview CPSC
Cryptography & Network-Security: Implementations in Hardware
 Kris Gaj joined ECE GMU in Fall 1998 Cryptography & Network-Security: Implementations in Hardware http://ece.gmu.edu/crypto-text.htm 6 Ph.D. Students Pawel Chodowiec Charikleia Zouridaki Chang Shu Sashisu
Kris Gaj joined ECE GMU in Fall 1998 Cryptography & Network-Security: Implementations in Hardware http://ece.gmu.edu/crypto-text.htm 6 Ph.D. Students Pawel Chodowiec Charikleia Zouridaki Chang Shu Sashisu
End-to-End Security in Wireless Sensor Networks (WSNs) Talk by Claudio Anliker Supervised by Dr. Corinna Schmitt CSG@IFI, University of Zurich
 End-to-End Security in Wireless Sensor (WSNs) Talk by Supervised by Dr. Corinna Schmitt CSG@IFI, University of Zurich Content 1. Motivation 2. Security Issues and Principles 3. Internet-of-Things and Wireless
End-to-End Security in Wireless Sensor (WSNs) Talk by Supervised by Dr. Corinna Schmitt CSG@IFI, University of Zurich Content 1. Motivation 2. Security Issues and Principles 3. Internet-of-Things and Wireless
Safer data transmission using Steganography
 Safer data transmission using Steganography Arul Bharathi, B.K.Akshay, M.Priy a, K.Latha Department of Computer Science and Engineering Sri Sairam Engineering College Chennai, India Email: arul.bharathi@yahoo.com,
Safer data transmission using Steganography Arul Bharathi, B.K.Akshay, M.Priy a, K.Latha Department of Computer Science and Engineering Sri Sairam Engineering College Chennai, India Email: arul.bharathi@yahoo.com,
Introduction to Computer Security
 Introduction to Computer Security (ECE 458) Vijay Ganesh Spring 2014 Online Resources, Books, Notes,... Books Introduction to Computer Security by Matt Bishop Computer Security: Art and Science by Matt
Introduction to Computer Security (ECE 458) Vijay Ganesh Spring 2014 Online Resources, Books, Notes,... Books Introduction to Computer Security by Matt Bishop Computer Security: Art and Science by Matt
Securing Logic Circuits Using Run-Time Programmable Interconnection Network
 Middle-East Journal of Scientific Research 22 (8): 1165-1175, 2014 ISSN 1990-9233 IDOSI Publications, 2014 DOI: 10.5829/idosi.mejsr.2014.22.08.21987 Securing Logic Circuits Using Run-Time Programmable
Middle-East Journal of Scientific Research 22 (8): 1165-1175, 2014 ISSN 1990-9233 IDOSI Publications, 2014 DOI: 10.5829/idosi.mejsr.2014.22.08.21987 Securing Logic Circuits Using Run-Time Programmable
VLSI Design Verification and Testing
 VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: cpatel2@cs.umbc.edu). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
VLSI Design Verification and Testing Instructor Chintan Patel (Contact using email: cpatel2@cs.umbc.edu). Text Michael L. Bushnell and Vishwani D. Agrawal, Essentials of Electronic Testing, for Digital,
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy
 Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Reductions & NP-completeness as part of Foundations of Computer Science undergraduate course
 Reductions & NP-completeness as part of Foundations of Computer Science undergraduate course Alex Angelopoulos, NTUA January 22, 2015 Outline Alex Angelopoulos (NTUA) FoCS: Reductions & NP-completeness-
Reductions & NP-completeness as part of Foundations of Computer Science undergraduate course Alex Angelopoulos, NTUA January 22, 2015 Outline Alex Angelopoulos (NTUA) FoCS: Reductions & NP-completeness-
Design and Verification of Nine port Network Router
 Design and Verification of Nine port Network Router G. Sri Lakshmi 1, A Ganga Mani 2 1 Assistant Professor, Department of Electronics and Communication Engineering, Pragathi Engineering College, Andhra
Design and Verification of Nine port Network Router G. Sri Lakshmi 1, A Ganga Mani 2 1 Assistant Professor, Department of Electronics and Communication Engineering, Pragathi Engineering College, Andhra
FPGA Implementation of an Advanced Traffic Light Controller using Verilog HDL
 FPGA Implementation of an Advanced Traffic Light Controller using Verilog HDL B. Dilip, Y. Alekhya, P. Divya Bharathi Abstract Traffic lights are the signaling devices used to manage traffic on multi-way
FPGA Implementation of an Advanced Traffic Light Controller using Verilog HDL B. Dilip, Y. Alekhya, P. Divya Bharathi Abstract Traffic lights are the signaling devices used to manage traffic on multi-way
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic
 Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
Example-driven Interconnect Synthesis for Heterogeneous Coarse-Grain Reconfigurable Logic Clifford Wolf, Johann Glaser, Florian Schupfer, Jan Haase, Christoph Grimm Computer Technology /99 Overview Ultra-Low-Power
AES1. Ultra-Compact Advanced Encryption Standard Core. General Description. Base Core Features. Symbol. Applications
 General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (start at 800 Actel tiles). Enhanced versions
General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (start at 800 Actel tiles). Enhanced versions
Privacy and Security in library RFID Issues, Practices and Architecture
 Privacy and Security in library RFID Issues, Practices and Architecture David Molnar and David Wagner University of California, Berkeley CCS '04 October 2004 Overview Motivation RFID Background Library
Privacy and Security in library RFID Issues, Practices and Architecture David Molnar and David Wagner University of California, Berkeley CCS '04 October 2004 Overview Motivation RFID Background Library
A NOVEL STRATEGY TO PROVIDE SECURE CHANNEL OVER WIRELESS TO WIRE COMMUNICATION
 A NOVEL STRATEGY TO PROVIDE SECURE CHANNEL OVER WIRELESS TO WIRE COMMUNICATION Prof. Dr. Alaa Hussain Al- Hamami, Amman Arab University for Graduate Studies Alaa_hamami@yahoo.com Dr. Mohammad Alaa Al-
A NOVEL STRATEGY TO PROVIDE SECURE CHANNEL OVER WIRELESS TO WIRE COMMUNICATION Prof. Dr. Alaa Hussain Al- Hamami, Amman Arab University for Graduate Studies Alaa_hamami@yahoo.com Dr. Mohammad Alaa Al-
A NOVEL APPROACH FOR MULTI-KEYWORD SEARCH WITH ANONYMOUS ID ASSIGNMENT OVER ENCRYPTED CLOUD DATA
 A NOVEL APPROACH FOR MULTI-KEYWORD SEARCH WITH ANONYMOUS ID ASSIGNMENT OVER ENCRYPTED CLOUD DATA U.Pandi Priya 1, R.Padma Priya 2 1 Research Scholar, Department of Computer Science and Information Technology,
A NOVEL APPROACH FOR MULTI-KEYWORD SEARCH WITH ANONYMOUS ID ASSIGNMENT OVER ENCRYPTED CLOUD DATA U.Pandi Priya 1, R.Padma Priya 2 1 Research Scholar, Department of Computer Science and Information Technology,
Lab 1: Full Adder 0.0
 Lab 1: Full Adder 0.0 Introduction In this lab you will design a simple digital circuit called a full adder. You will then use logic gates to draw a schematic for the circuit. Finally, you will verify
Lab 1: Full Adder 0.0 Introduction In this lab you will design a simple digital circuit called a full adder. You will then use logic gates to draw a schematic for the circuit. Finally, you will verify
Tor Anonymity Network & Traffic Analysis. Presented by Peter Likarish
 Tor Anonymity Network & Traffic Analysis Presented by Peter Likarish This is NOT the presenter s original work. This talk reviews: Tor: The Second Generation Onion Router Dingledine, Mathewson, Syverson
Tor Anonymity Network & Traffic Analysis Presented by Peter Likarish This is NOT the presenter s original work. This talk reviews: Tor: The Second Generation Onion Router Dingledine, Mathewson, Syverson
INSTITUTE OF AERONAUTICAL ENGINEERING Dundigal, Hyderabad - 500 043
 INSTITUTE OF AERONAUTICAL ENGINEERING Dundigal, Hyderabad - 500 043 ELECTRONICS AND COMMUNICATION ENGINEERING Course Title VLSI DESIGN Course Code 57035 Regulation R09 COURSE DESCRIPTION Course Structure
INSTITUTE OF AERONAUTICAL ENGINEERING Dundigal, Hyderabad - 500 043 ELECTRONICS AND COMMUNICATION ENGINEERING Course Title VLSI DESIGN Course Code 57035 Regulation R09 COURSE DESCRIPTION Course Structure
Computer Security DD2395
 Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger buc@kth.se Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
Computer Security DD2395 http://www.csc.kth.se/utbildning/kth/kurser/dd2395/dasakh11/ Fall 2011 Sonja Buchegger buc@kth.se Lecture 7 Malicious Software DD2395 Sonja Buchegger 1 Course Admin Lab 2: - prepare
Lecture 5: Gate Logic Logic Optimization
 Lecture 5: Gate Logic Logic Optimization MAH, AEN EE271 Lecture 5 1 Overview Reading McCluskey, Logic Design Principles- or any text in boolean algebra Introduction We could design at the level of irsim
Lecture 5: Gate Logic Logic Optimization MAH, AEN EE271 Lecture 5 1 Overview Reading McCluskey, Logic Design Principles- or any text in boolean algebra Introduction We could design at the level of irsim
Microsemi Security Center of Excellence
 Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Lecture 10: Latch and Flip-Flop Design. Outline
 Lecture 1: Latch and Flip-Flop esign Slides orginally from: Vladimir Stojanovic Computer Systems Laboratory Stanford University horowitz@stanford.edu 1 Outline Recent interest in latches and flip-flops
Lecture 1: Latch and Flip-Flop esign Slides orginally from: Vladimir Stojanovic Computer Systems Laboratory Stanford University horowitz@stanford.edu 1 Outline Recent interest in latches and flip-flops
Structural Cloud Audits that Protect Private Information
 Structural Cloud Audits that Protect Private Information Hongda Xiao, Bryan Ford, Joan Feigenbaum Department of Computer Science Yale University Cloud Computing Security Workshop November 8, 2013 Motivation
Structural Cloud Audits that Protect Private Information Hongda Xiao, Bryan Ford, Joan Feigenbaum Department of Computer Science Yale University Cloud Computing Security Workshop November 8, 2013 Motivation
LES: Layered Encryption Security
 LES: Layered Encryption Security Manish Karir John S. Baras Center for Satellite and Hybrid Communication Networks Department of Electrical and Computer Engineering & Institute for Systems Engineering
LES: Layered Encryption Security Manish Karir John S. Baras Center for Satellite and Hybrid Communication Networks Department of Electrical and Computer Engineering & Institute for Systems Engineering
Why VPN Alone Will not Secure your Wireless Network
 Why VPN Alone Will not Secure your Wireless Network Christian H. Mosveen Department of Computer Science University of Auckland E-mail: cmos024@ec.auckland.ac.nz Abstract Any wireless device will, because
Why VPN Alone Will not Secure your Wireless Network Christian H. Mosveen Department of Computer Science University of Auckland E-mail: cmos024@ec.auckland.ac.nz Abstract Any wireless device will, because
Verifiable Outsourced Computations Outsourcing Computations to Untrusted Servers
 Outsourcing Computations to Untrusted Servers Security of Symmetric Ciphers in Network Protocols ICMS, May 26, 2015, Edinburgh Problem Motivation Problem Motivation Problem Motivation Problem Motivation
Outsourcing Computations to Untrusted Servers Security of Symmetric Ciphers in Network Protocols ICMS, May 26, 2015, Edinburgh Problem Motivation Problem Motivation Problem Motivation Problem Motivation
Problems of Security in Ad Hoc Sensor Network
 Problems of Security in Ad Hoc Sensor Network Petr Hanáček * hanacek@fit.vutbr.cz Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Problems of Security in Ad Hoc Sensor Network Petr Hanáček * hanacek@fit.vutbr.cz Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Microsoft Cloud Computing Research Centre
 Microsoft Cloud Computing Research Centre 1 st Annual Symposium, Cambridge 2014 Regional clouds: technical considerations Jon Crowcroft jon.crowcroft@cl.cam.ac.uk Jat Singh jatinder.singh@cl.cam.ac.uk
Microsoft Cloud Computing Research Centre 1 st Annual Symposium, Cambridge 2014 Regional clouds: technical considerations Jon Crowcroft jon.crowcroft@cl.cam.ac.uk Jat Singh jatinder.singh@cl.cam.ac.uk
DEVELOPING TRENDS OF SYSTEM ON A CHIP AND EMBEDDED SYSTEM
 DEVELOPING TRENDS OF SYSTEM ON A CHIP AND EMBEDDED SYSTEM * Monire Norouzi Young Researchers and Elite Club, Shabestar Branch, Islamic Azad University, Shabestar, Iran *Author for Correspondence ABSTRACT
DEVELOPING TRENDS OF SYSTEM ON A CHIP AND EMBEDDED SYSTEM * Monire Norouzi Young Researchers and Elite Club, Shabestar Branch, Islamic Azad University, Shabestar, Iran *Author for Correspondence ABSTRACT
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD. Olivier THOMAS Blackhat USA 2015
 ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
ADVANCED IC REVERSE ENGINEERING TECHNIQUES: IN DEPTH ANALYSIS OF A MODERN SMART CARD Olivier THOMAS Blackhat USA 2015 About Texplained Texplained [Technology Explained] refers
Chapter 23. Database Security. Security Issues. Database Security
 Chapter 23 Database Security Security Issues Legal and ethical issues Policy issues System-related issues The need to identify multiple security levels 2 Database Security A DBMS typically includes a database
Chapter 23 Database Security Security Issues Legal and ethical issues Policy issues System-related issues The need to identify multiple security levels 2 Database Security A DBMS typically includes a database
Certifying Program Execution with Secure Processors
 Certifying Program Execution with Secure Processors Benjie Chen Robert Morris MIT Laboratory for Computer Science {benjie,rtm}@lcs.mit.edu Abstract Cerium is a trusted computing architecture that protects
Certifying Program Execution with Secure Processors Benjie Chen Robert Morris MIT Laboratory for Computer Science {benjie,rtm}@lcs.mit.edu Abstract Cerium is a trusted computing architecture that protects
State-of-Art (SoA) System-on-Chip (SoC) Design HPC SoC Workshop
 Photos placed in horizontal position with even amount of white space between photos and header State-of-Art (SoA) System-on-Chip (SoC) Design HPC SoC Workshop Michael Holmes Manager, Mixed Signal ASIC/SoC
Photos placed in horizontal position with even amount of white space between photos and header State-of-Art (SoA) System-on-Chip (SoC) Design HPC SoC Workshop Michael Holmes Manager, Mixed Signal ASIC/SoC
1. Memory technology & Hierarchy
 1. Memory technology & Hierarchy RAM types Advances in Computer Architecture Andy D. Pimentel Memory wall Memory wall = divergence between CPU and RAM speed We can increase bandwidth by introducing concurrency
1. Memory technology & Hierarchy RAM types Advances in Computer Architecture Andy D. Pimentel Memory wall Memory wall = divergence between CPU and RAM speed We can increase bandwidth by introducing concurrency
Patterns for Secure Boot and Secure Storage in Computer Systems
 Patterns for Secure Boot and Secure Storage in Computer Systems Hans Löhr, Ahmad-Reza Sadeghi, Marcel Winandy Horst Görtz Institute for IT Security, Ruhr-University Bochum, Germany {hans.loehr,ahmad.sadeghi,marcel.winandy}@trust.rub.de
Patterns for Secure Boot and Secure Storage in Computer Systems Hans Löhr, Ahmad-Reza Sadeghi, Marcel Winandy Horst Görtz Institute for IT Security, Ruhr-University Bochum, Germany {hans.loehr,ahmad.sadeghi,marcel.winandy}@trust.rub.de
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
12/3/08. Security in Wireless LANs and Mobile Networks. Wireless Magnifies Exposure Vulnerability. Mobility Makes it Difficult to Establish Trust
 Security in Wireless LANs and Mobile Networks Wireless Magnifies Exposure Vulnerability Information going across the wireless link is exposed to anyone within radio range RF may extend beyond a room or
Security in Wireless LANs and Mobile Networks Wireless Magnifies Exposure Vulnerability Information going across the wireless link is exposed to anyone within radio range RF may extend beyond a room or
FPGA Based Secure System Design-an Overview
 FPGA Based Secure System Design-an Overview Gurjit Singh Walia, Gajraj Kuldeep, Rajiv Kapoor, A K Sharma, Navneet Gaba Abstract- The implementation of cryptographic algorithm on FPGA is highly addressed
FPGA Based Secure System Design-an Overview Gurjit Singh Walia, Gajraj Kuldeep, Rajiv Kapoor, A K Sharma, Navneet Gaba Abstract- The implementation of cryptographic algorithm on FPGA is highly addressed
Decryption. Palo Alto Networks. PAN-OS Administrator s Guide Version 6.0. Copyright 2007-2015 Palo Alto Networks
 Decryption Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
Decryption Palo Alto Networks PAN-OS Administrator s Guide Version 6.0 Contact Information Corporate Headquarters: Palo Alto Networks 4401 Great America Parkway Santa Clara, CA 95054 www.paloaltonetworks.com/company/contact-us
159.334 Computer Networks. Network Security 1. Professor Richard Harris School of Engineering and Advanced Technology
 Network Security 1 Professor Richard Harris School of Engineering and Advanced Technology Presentation Outline Overview of Identification and Authentication The importance of identification and Authentication
Network Security 1 Professor Richard Harris School of Engineering and Advanced Technology Presentation Outline Overview of Identification and Authentication The importance of identification and Authentication
Disk encryption... (not only) in Linux. Milan Brož mbroz@redhat.com
 Disk encryption... (not only) in Linux Milan Brož mbroz@redhat.com FDE - Full Disk Encryption FDE (Full Disk Encryption) whole disk FVE (Full Volume Encryption) just some volumes (dis)advantages? + for
Disk encryption... (not only) in Linux Milan Brož mbroz@redhat.com FDE - Full Disk Encryption FDE (Full Disk Encryption) whole disk FVE (Full Volume Encryption) just some volumes (dis)advantages? + for
VICTORIA UNIVERSITY OF WELLINGTON Te Whare Wānanga o te Ūpoko o te Ika a Māui
 VICTORIA UNIVERSITY OF WELLINGTON Te Whare Wānanga o te Ūpoko o te Ika a Māui School of Engineering and Computer Science Te Kura Mātai Pūkaha, Pūrorohiko PO Box 600 Wellington New Zealand Tel: +64 4 463
VICTORIA UNIVERSITY OF WELLINGTON Te Whare Wānanga o te Ūpoko o te Ika a Māui School of Engineering and Computer Science Te Kura Mātai Pūkaha, Pūrorohiko PO Box 600 Wellington New Zealand Tel: +64 4 463
SECURE DATA TRANSMISSION USING INDISCRIMINATE DATA PATHS FOR STAGNANT DESTINATION IN MANET
 SECURE DATA TRANSMISSION USING INDISCRIMINATE DATA PATHS FOR STAGNANT DESTINATION IN MANET MR. ARVIND P. PANDE 1, PROF. UTTAM A. PATIL 2, PROF. B.S PATIL 3 Dept. Of Electronics Textile and Engineering
SECURE DATA TRANSMISSION USING INDISCRIMINATE DATA PATHS FOR STAGNANT DESTINATION IN MANET MR. ARVIND P. PANDE 1, PROF. UTTAM A. PATIL 2, PROF. B.S PATIL 3 Dept. Of Electronics Textile and Engineering
