FPGA Based Secure System Design-an Overview
|
|
|
- Karin Beasley
- 10 years ago
- Views:
Transcription
1 FPGA Based Secure System Design-an Overview Gurjit Singh Walia, Gajraj Kuldeep, Rajiv Kapoor, A K Sharma, Navneet Gaba Abstract- The implementation of cryptographic algorithm on FPGA is highly addressed in different forums due to its paramount advantages over the other platforms. Most of the secure systems are designed using SRAM based FPGAs with additional security features provided by the manufactures. In this paper, firstly, attempts are made to address different security problems of FPGA based secure systems. The difficulty levels that an attacker may face while implementing an attack are also tabulated. Finally, some constructive recommendation for tackling these security issues are proposed for designing secure systems. Keywords- Cryptography, FPGA, Secure system, Security, ASIC, SRAM I INTRODUCTION Field Programmable Gate Array (FPGA) is used to implement user defined function using interconnected reprogrammable functional blocks (embedded processors, giga-bit serial transceivers, clock mangers, digital signal processing blocks, ethernet controller etc). The selection of the implementation platform for cryptographic application is dependent upon many critical factors such as complexity of algorithm and its application area, cost, speed, power consumption and desired security aspects (physical security, side channel leakage etc.) [1]&[19]. FPGAs are generally preferred over Application Specific Integrated Circuits (ASIC) when reprogrammability, power and price are considered as metric for decision [2], [10]&[16]. The inherent properties of FPGA, such as parallel operations and execution of customized functions make them performance competitive over the sequential microprocessor and microcontrollers. According to Wollinger et al. [4] and Wollinger and Paar [1], the potential advantages of FPGAs in cryptographic applications are algorithm agility, algorithm upload, architecture efficiency, resource efficiency, algorithm modification and throughput. The rapid acceptance of FPGA solutions and subsequentially increase in these solutions in the market has created a host of new security concerns for system-level designers and system evaluators. Manuscript received Dec 05, Gurjit Singh Walia, Scientist D, Scientific Analysis Group, DRDO, Delhi, ,( [email protected]). Gajraj Kuldeep, Scientist C, Scientific Analysis Group, DRDO, Delhi, ,( [email protected]) Rajiv Kapoor, Professor and Head, Delhi Technological Univeristy (DCE), Delhi,, ,( [email protected]). A K Sharma, Scientist F, Scientific Analysis Group, DRDO, Delhi, ,( [email protected]) Navneet Gaba, Scientist F, Scientific Analysis Group, DRDO, Delhi, ,( [email protected]) From the attacker point of view, not only the FPGA design but also the embedded information in the data being sent to or from a system is important. So taking this into consideration, classification of this topic was done in [7] and [6]: a) Intellectual property (IP) security: Security concerns about the protection of vendor own design (IP) from being cloned" or reverse engineered. b) Data security: Security concerns about the protection of user design from being copied, corrupted, or otherwise interfered with. When considering from cryptographic point of view, data security is the main area to be addressed. So the main work in this paper is based upon taking the data security issues as foremost important. In literature, much work has been done on development of cryptographic application on FPGA [3]&[18], but, still, some nooks are still left untouched when secure systems are considered as whole. Taking these observations into due consideration, it is hoped that this manuscript will definitely give a seminal learning to academia, industry and defense establishments. In this paper, in Section 2, the security problems for secure systems are elaborated. In section 3, difficulty levels an attacker will face while implementing an attack is tabulated. Finally, in Section 4, some of design considerations that should be incorporated in secure system design have been suggested. II SECURITY PROBLEMS FOR FPGA BASED SECURE SYSTEM The motivation behind any attacker who is considered to be an adversary is to disturb the system functionality. The attackers power is faithfully elaborated by IBM [8], Class I (clever outsiders) attackers do not have sufficient knowledge of the system but are often very intelligent; Class II (knowledgeable insiders) attackers have experience and specialized technical education and have expertise with sophisticated tools to analyze parts of a systems; Class III (funded organizations) attackers are able to develop teams of specialists and use the most sophisticated and expensive analysis tools as they have no limitation of money and they are consider to do in-depth analysis of system. The aim of hardware attacker is to get secret information and to make the system non functional. The various attacks are reported in[1], [4], [13], [12], [9], [11], [14], [15]&[23] and these are further elaborated in present work taking into account of present technology and tools available and intensive research work carried out at our laboratory. These attacks are categorized as follow with necessary hardware and software tools required for their implementation and also way out for prevention of these attacks. 134
2 FPGA Based Secure System Design-an overview A. Black Box Attack In this attack, the attacker inputs all possible combinations, while saving the corresponding outputs. After the log of different combination, the algorithm could be deduced with arduous efforts. For implementation of this attack a lot of processor power is required. However, this attack will be less feasible as the number of logic elements and complexity of the FPGA increases. The cost of the attack rises with the usage of state machines, LFSRs, and if pins can be used for input and output. However, advance mathematical techniques such as SAT Solvers could aid the attacker for launching black box attack. B. Read-back Attack The idea of this attack is to read the configuration of the FPGA through the JTAG or programming interface in order to obtain secret information (e.g. keys, algorithm). As reported [20], scan chain in FPGA can be exploited to decipher the cryptogram and this can be avoided by tree based pattern with self checking compactor. Advance tools for easy debugging such as Xilinx JBits are required for read back attack implementation. However, this attack will be less feasible if the programming port is disabled and after detection of interference the whole configuration is deleted or the FPGA is destroyed. C. Cloning of FPGAs In this attack, the attacker targets the configuration file of the system. As shown in fig:1, the bit stream is stored in the flash memory for SRAM based FPGA and this need to be transferred during power on from flash to SRAM FPGA. E. Side channel attacks (Power analysis, timing behavior, electromagnetic radiation) Any physical implementation of a cryptographic system may provide a side channel that leaks information which can be exploited by the attacker to launch this attack. By simple power analysis, differential power analysis, simple electro-magnetic analysis (SEMA), differential electro-magnetic analysis (DEMA) side channel information could be exploited. As shown in Fig: 2, Only Squaring Squaring and Multiplication Fig 2: Power analysis of RSA The RSA algorithm is implemented with main usage of squaring and multiplication functions. As reported in the literature, CMOS gates while switching draw current spikes which are exploited using the highly sensitive E & H probes and high end oscilloscope for launching this power analysis attack. However, preventive measures for side channel power analysis of RSA system for key generation could be taken either at designer or manufacture level. F. Reverse Engineering of the Bit Streams SRAM based FPGA Transfer of Bit Stream Interception Flash The aim behind this attack is to get the design of proprietary crypto algorithm or the secret keys by reverse engineering of Bit streams. As shown in Fig 3, a typical design flow of FPGA consist of various stages which are shown below. Fig 1 : Configuration of SRAM FPGA This file could be intercepted during transfer by the third party to make a clone of the same. Advanced memory programmer, logic analyzer, data loggers etc. are required for launching this attack.the use of flash based FPGA could avoid this attack. But using flash based FPGA has inherent limitation for usage in secure system. The encryption of the configuration file is the most effective and practical counter measure against the cloning of SRAM FPGA. D. Physical Attack The aim of attack is to investigate the chip design in order to get information by probing inside the chip. This attack can be achieved through visual inspections and by tools such as optical microscopes, mechanical probes, Focused Ion Beams, Electron beam tester. However, the manufacture could take precautionary measure in order to avoid this attack. HDL Netlist Placelist Synthesis Place & Route Fig 3: Software flow for FPGA implementation Attacker may deduce HDL code from bitstream file. Advance tools are available for reverse engineering of Bit stream such as Debit which gives information about look up tables (LUT). Hiding keys in the look up table and RAMs can partially avoid this attack. G. Tampering in Tools Encoding Bitstream In this attack, an adversary could add additional functionality to expose sensitive information, or provide unauthorized access. Layout-versus-schematic (LVS) tools could be used for detecting tampering in tools which is shown in the fig 4 below: 135
3 Design Include IP libraries Synthesis, place and route Get Netlist Layout vs Schematic comparison (LVS) tool The physical characteristics such as design of system can be exploited for inserting hardware Trojan in secure system. Activation can be subdivided into externally activated and internally activated Trojan. When doing the statistical analysis, activation of Trojan is considered to be a very rare event. Further, the action characteristic is subdivided into three different divisions: changing of functionality, alteration in specification and transmitting information through any medium which may be wired or wireless. However, ATPG based Trojan detection technique and side channel analysis of RF emitted could be used for detection of Trojan. Also, Trojan could be avoided if Code walk through by independent authority. III ATTACKER DIFFICULTY LEVELS Fig 4: Design validation However, Tampering could be avoided by comparing the implemented design and the original design. H. Fault Attacks Fault attacks exit where some hardware fault (an unexpected condition or defect) leads to a processing mistake that could be beneficial to the attacker. Advance timing comparison tools, logic analyzer etc. are imperative for implementation of this attack. However, this attack will be less feasible by avoiding supply of noisy power, incorrect voltage, excessive temperature, radiation or high energy beams such as UV, laser, etc. I. Tempering in Hardware Attackers make use of system hardware to get the secure information from the secure system. Attacker could exploit ports such as JTAG and redundant hardware present in the secure system. Tools such as Quartas, ISE, Visual DSP++, emulator, memory readers etc. are essential for this attack. However, Designer could prevent this attack by taking care of temper resistance, detection, response and evidence while designing the secure hardware. J. Trojan Trojan is intentional malicious code written into the system design or it may be the malicious modification in the hardware circuitry, usually to the attacker benefit. Access to secure system and knowledge of software used is needed for implementation of Trojan. Xiaoxiao Wang et al. [22], classified Trojan into the different category which are shown below in fig 5. Trojan As per IBM systems Journal, Abraham et al. [8] has marked security levels for secure systems. While considering different technological development in the field of FPGA since 1980 and taking IBM security levels as reference for classification, we have marked different level of difficulties that an attacker may face while launching the attack in table 1 below. The few of listed difficulty levels are measured by actual performing the experiments but for some of attacks efforts are made to implement them, but either lack of time, prohibitively high difficulty of implementation or potentially destructive nature put impediments for actual measurements. Further, the listed difficulty level classification may vary with the attacker who is going to perform attack. Table 1 : Attacks in Secure Hardware Sr No. Security Shortcomings of FPGA *Attacker Difficulty Level 1. Black Box Attack 5 2. Readback Attack 2 3. Cloning of FPGAs a. Indigenous 5 Flash/Antifuse FPGA b. Flash FPGA 4 c. Antifuse FPGA 4 d. SRAM FPGA with 3 bitstream encryption. e. SRAM FPGA 1 4. Reverse Engineering of the Bit 4 streams 5. Physical Attack 5 6. Side channel attacks 4 7. Tampering in tools 3 8. Fault attack 4 9. Tempering in hardware Trojan 1 Physical Activation Action *Note: Level represented in scale of 1-5 with 5 as the maximum level of difficulty to launch the attack. Fig 5: Classification of Trojan 136
4 FPGA Based Secure System Design-an overview IV RECOMMENDATIONS FOR FPGA BASED SECURE SYSTEMS Although, there is no upper limit on the level of security that can be achieved, here some of key features which should be incorporated during design of FPGA based secure systems have been suggested. A. In order to avoid reverse engineering and cloning of FPGA design, PROM should store only the encrypted bitstream file and also there should be feature of on-chip bit stream decryption. Now days, vendors are providing these features with 3- DES implementation for bit stream encryption [17]. B. Cryptographic operations in secure system are extensively used which causes long term retention effects in SRAM memory cell. Designer should include dummy cycles while doing cryptographic operation. C. In order to avoid the tampering in original design by the design tools, the final implemented design and original design should be checked for their equivalence. It may be part and parcel of validation stage of software development cycle. D. For secure system, FPGAs which have security level 3 or above as shown in table 1 above should be used to avoid reverse engineering of bitstream. Also, Designer should include the feature such as deletion of bitstream when tempering is detected. E. The designers should be cleaver enough so that they can design their systems with due consideration of all the attacks based on malicious logic in the base array of FPGA. It is suggested that designer implements all critical parts of the design with minimum three level of modular redundancy (MR). F. In case of physical compromise of the system, the designer should incorporate the feature of self destruction of the system. For example, with the detection of unauthorized interference, system design should be such that it erases the firmware & secret key information from the system. G. The designers should give due consideration to make all unused I/O pins/ports as tri state so that unauthorized access could be avoided. H. The design of FPGA should be such that provision of maintaining keys by the user must be avoided in order to cater for future changes in the design of secure systems. I. The design should have provision of software countermeasure for all the side channel attacks. For example, design should mask secret key with the random values. J. The designer should use TRNG for initialization of algorithm and also strength of crypto algorithm should be high in FPGA based secure systems to avoid Black Box attack. K. The designer should use customized FPGA based board for cryptographic applications so that minimum resources with actual use should be included in the hardware. L. Physical/logical separation should be incorporated for plain and cipher data at design level. V CONCLUSION FPGAs in cryptographic applications are generally preferred over ASIC due to their potential advantages such as algorithm agility, algorithm upload, architecture efficiency, resource efficiency, algorithm modification and throughput. However, when security aspects are taken into consideration there are numerous nooks for improvement which have been described in this paper. The tabulated difficulty levels may vary with the class of attacker and development of technological tools. Efforts are made to address all the possible vulnerabilities but sill this area is open for research due to latest developments of sophisticated tools and hardware. ACKNOWLEDGEMENT We are heartily grateful to Dr. P. K. Saxena, Director, outstanding Scientist H, for his support, benevolent guidance & motivation which inspired us and framed the state of mind that allowed this work to happen. We are indebted to Dr. S. S. Bedi, Associate Director for his invaluable support and informative suggestions. REFERENCES [1] T. Wollinger and C. Paar. How Secure Are FPGAs in Crypto-graphic Applications?(Long Version).Report 2003/119,IACR,2003. [2] A. Elbirt, W. Yip, B. Chetwynd, and C. Paar. An FPGA-based performance Evaluation of the AES block cipher candidate algorithm finalists. IEEE Transactions on VLSI Design, 9(4):545{557, August [3] Jr. Kaliski, B. S. Koc, C. K. and C. Paar, Eds Workshop on Cryptographic Hardware and Embedded Systems CHES Vol. LNCS Springer-Verlag, Berlin, Germany. [4] T. Wollinger, J. Guajardo and C. Paar Security on FPGAs: State of the Art Implementations and Attacks ACM Special Issue Security and Embedded Systems Vol. No. March [5] K. K Parhi, VLSI Digital Signal Processing Systems: Design and Implementation, John Wiley & Sons, Inc [6] T. Kean. Cryptographic rights management of FPGA intellectual property cores. In Field Programmable Gate Arrays Symposium, pages , New York, NY, USA, ACM Press. [7] Actel Corporation Design Security in Nonvolatile Flash and Antifuse FPGAs, Security Backgrounder [8] D.G Abraham, G.M. Dolan, G.P. Double and J.V. Stevens Transaction Security System. IBM Systems Journal vol. 30 no. 2New York: International Machines Business Corporation: [9] P. Vikram. Embedded systems challenge faq. Information Systems And Internet Security Laboratory,Department of Computer Science, NYU- Polytechnic University. [10] D.P. Wilt, R.C. Meitzler, and J.P. DeVale. Metrics for TRUST in Integrated Circuits, 2008 [11] A. Ross. Security Engineering, A Gudie to Building Dependable Distributed Systems. Wiley, New York, second edition edition, [12] FPGA Reverse Engineering Services. [13] E. J. Chikofsky and J. H. Cross, II, Reverse Engineering and Design Recovery, IEEE Software, vol. 7, no. 1, pp , January [14] P. Kocher, Timing attacks on implementations of Diffie-Hellman, RSA, DSS and other systems, in Advances in Cryptology: Proceedings of CRYPTO 96, N. Koblitz, Ed., 1996, vol of LNCS, pp ,Springer- Verlag. [15] P. Kocher, J. Jaffe, and B. Jun, Differential power analysis, in Advances in Cryptology: Proceedings of CRYPTO 99, M. Wiener, Ed.1999, vol of LNCS, pp , Springer-Verlag [16] J. G. Proakis and D. G. Manolakis Digital Signal Processing 137
5 Principles, Algorithms and Applications; Third Edition; Prentice Hall of India, [17] Xilinx Inc., "Using Bitstream Encryption", in Chapter 2 of the Virtex II Platform FPGA. [18] T. Kean, Secure Configuration of Field Programmable Gate Arrays, Proceedings of FPL 2001, Belfast, UK. Published as Springer LNCS. [19] Algotronix Ltd., Method of Protecting Intellectual Property Cores on Field Programmable Gate Array, unpublished pending patent application. [20] D Mukhopadyay et al., Cryptoscan: A Secured Scan Chain Architecture, 2005 Proceedings of the 14 th Asian Test Symposium(ATS 05). [21] A Baumgarten et al A case study of hardware Trojan design and implementation Springer-Verlag 2010 [22] Xiaoxiao Wang; Tehranipoor, M.; Plusquellic, J Detecting malicious inclusions in secure hardware: Challenges and solutions 2008 IEEE international workshop on hardware-oriented security and trust (HOST) 138
Cryptographic Rights Management of FPGA Intellectual Property Cores
 Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom [email protected] ABSTRACT As the capacity of FPGA s increases
Cryptographic Rights Management of FPGA Intellectual Property Cores Tom Kean Algotronix Ltd. PO Box 23116 Edinburgh EH8 8YB United Kingdom [email protected] ABSTRACT As the capacity of FPGA s increases
Side Channel Analysis and Embedded Systems Impact and Countermeasures
 Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Side Channel Analysis and Embedded Systems Impact and Countermeasures Job de Haas Agenda Advances in Embedded Systems Security From USB stick to game console Current attacks Cryptographic devices Side
Horst Görtz Institute for IT-Security
 Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Horst Görtz Institute for IT-Security On the Vulnerability of FPGA Bitstream Encryption against Power Analysis Attacks Extracting Keys from Xilinx Virtex-II FPGAs Amir Moradi, Alessandro Barenghi, Timo
Hardware Trojans Detection Methods Julien FRANCQ
 DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
DEFENDING WORLD SECURITY Hardware Trojans Detection Methods Julien FRANCQ 2013, December the 12th Outline c 2013 CASSIDIAN CYBERSECURITY - All rights reserved TRUDEVICE 2013, December the 12th Page 2 /
Preventing Piracy and Reverse Engineering of SRAM FPGAs Bitstream
 Approche de conception d interface de communication pour les systèmes sur puce Preventing Piracy and Reverse Engineering of SRAM FPGAs Bitstream Lilian Bossuet 1, Guy Gogniat 1, Wayne Burleson 2 1 LESTER
Approche de conception d interface de communication pour les systèmes sur puce Preventing Piracy and Reverse Engineering of SRAM FPGAs Bitstream Lilian Bossuet 1, Guy Gogniat 1, Wayne Burleson 2 1 LESTER
7a. System-on-chip design and prototyping platforms
 7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
7a. System-on-chip design and prototyping platforms Labros Bisdounis, Ph.D. Department of Computer and Communication Engineering 1 What is System-on-Chip (SoC)? System-on-chip is an integrated circuit
CryptoFirewall Technology Introduction
 CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
CryptoFirewall Technology Introduction Cryptography Research, Inc. www.cryptography.com 575 Market St., 21 st Floor, San Francisco, CA 94105 1998-2007 Cryptography Research, Inc. Protected under issued
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge
 Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
Secure Embedded Systems eine Voraussetzung für Cyber Physical Systems und das Internet der Dinge Mitgliederversammlung EIKON e.v. 26. Februar 2014 Prof. Dr.-Ing. Georg Sigl Lehrstuhl für Sicherheit in
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion
 Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Securing Host Operations with a Dedicated Cryptographic IC - CryptoCompanion By Kerry Maletsky, Business Unit Director Crypto Products Summary There is a growing need for strong hardware security devices
Secure Hardware PV018 Masaryk University Faculty of Informatics
 Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
Secure Hardware PV018 Masaryk University Faculty of Informatics Jan Krhovják Vašek Matyáš Roadmap Introduction The need of secure HW Basic terminology Architecture Cryptographic coprocessors/accelerators
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
PUF Physical Unclonable Functions
 Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Physical Unclonable Functions Protecting next-generation Smart Card ICs with SRAM-based s The use of Smart Card ICs has become more widespread, having expanded from historical banking and telecommunication
Lesson 7: SYSTEM-ON. SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY. Chapter-1L07: "Embedded Systems - ", Raj Kamal, Publs.: McGraw-Hill Education
 Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
Lesson 7: SYSTEM-ON ON-CHIP (SoC( SoC) AND USE OF VLSI CIRCUIT DESIGN TECHNOLOGY 1 VLSI chip Integration of high-level components Possess gate-level sophistication in circuits above that of the counter,
How To Fix A 3 Bit Error In Data From A Data Point To A Bit Code (Data Point) With A Power Source (Data Source) And A Power Cell (Power Source)
 FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
FPGA IMPLEMENTATION OF 4D-PARITY BASED DATA CODING TECHNIQUE Vijay Tawar 1, Rajani Gupta 2 1 Student, KNPCST, Hoshangabad Road, Misrod, Bhopal, Pin no.462047 2 Head of Department (EC), KNPCST, Hoshangabad
Introduction to Digital System Design
 Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
Introduction to Digital System Design Chapter 1 1 Outline 1. Why Digital? 2. Device Technologies 3. System Representation 4. Abstraction 5. Development Tasks 6. Development Flow Chapter 1 2 1. Why Digital
ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT
 216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
9/14/2011 14.9.2011 8:38
 Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain [email protected] Department of Computer
Algorithms and Implementation Platforms for Wireless Communications TLT-9706/ TKT-9636 (Seminar Course) BASICS OF FIELD PROGRAMMABLE GATE ARRAYS Waqar Hussain [email protected] Department of Computer
Implementation of Full -Parallelism AES Encryption and Decryption
 Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
Implementation of Full -Parallelism AES Encryption and Decryption M.Anto Merline M.E-Commuication Systems, ECE Department K.Ramakrishnan College of Engineering-Samayapuram, Trichy. Abstract-Advanced Encryption
On Security Evaluation Testing
 On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
On Security Evaluation Testing Kerstin Lemke-Rust Hochschule Bonn-Rhein-Sieg Workshop: Provable Security against Physical Attacks Lorentz Center, 19 Feb 2010 Kerstin Lemke-Rust (H BRS) On Security Evaluation
IJESRT. [Padama, 2(5): May, 2013] ISSN: 2277-9655
![IJESRT. [Padama, 2(5): May, 2013] ISSN: 2277-9655 IJESRT. [Padama, 2(5): May, 2013] ISSN: 2277-9655](/thumbs/30/14171228.jpg) IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Design and Verification of VLSI Based AES Crypto Core Processor Using Verilog HDL Dr.K.Padama Priya *1, N. Deepthi Priya 2 *1,2
IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY Design and Verification of VLSI Based AES Crypto Core Processor Using Verilog HDL Dr.K.Padama Priya *1, N. Deepthi Priya 2 *1,2
Open Flow Controller and Switch Datasheet
 Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
Open Flow Controller and Switch Datasheet California State University Chico Alan Braithwaite Spring 2013 Block Diagram Figure 1. High Level Block Diagram The project will consist of a network development
Cryptography & Network-Security: Implementations in Hardware
 Kris Gaj joined ECE GMU in Fall 1998 Cryptography & Network-Security: Implementations in Hardware http://ece.gmu.edu/crypto-text.htm 6 Ph.D. Students Pawel Chodowiec Charikleia Zouridaki Chang Shu Sashisu
Kris Gaj joined ECE GMU in Fall 1998 Cryptography & Network-Security: Implementations in Hardware http://ece.gmu.edu/crypto-text.htm 6 Ph.D. Students Pawel Chodowiec Charikleia Zouridaki Chang Shu Sashisu
AES1. Ultra-Compact Advanced Encryption Standard Core. General Description. Base Core Features. Symbol. Applications
 General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (start at 800 Actel tiles). Enhanced versions
General Description The AES core implements Rijndael encoding and decoding in compliance with the NIST Advanced Encryption Standard. Basic core is very small (start at 800 Actel tiles). Enhanced versions
Implementation and Design of AES S-Box on FPGA
 International Journal of Research in Engineering and Science (IJRES) ISSN (Online): 232-9364, ISSN (Print): 232-9356 Volume 3 Issue ǁ Jan. 25 ǁ PP.9-4 Implementation and Design of AES S-Box on FPGA Chandrasekhar
International Journal of Research in Engineering and Science (IJRES) ISSN (Online): 232-9364, ISSN (Print): 232-9356 Volume 3 Issue ǁ Jan. 25 ǁ PP.9-4 Implementation and Design of AES S-Box on FPGA Chandrasekhar
A PERFORMANCE EVALUATION OF COMMON ENCRYPTION TECHNIQUES WITH SECURE WATERMARK SYSTEM (SWS)
 A PERFORMANCE EVALUATION OF COMMON ENCRYPTION TECHNIQUES WITH SECURE WATERMARK SYSTEM (SWS) Ashraf Odeh 1, Shadi R.Masadeh 2, Ahmad Azzazi 3 1 Computer Information Systems Department, Isra University,
A PERFORMANCE EVALUATION OF COMMON ENCRYPTION TECHNIQUES WITH SECURE WATERMARK SYSTEM (SWS) Ashraf Odeh 1, Shadi R.Masadeh 2, Ahmad Azzazi 3 1 Computer Information Systems Department, Isra University,
What is a System on a Chip?
 What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
What is a System on a Chip? Integration of a complete system, that until recently consisted of multiple ICs, onto a single IC. CPU PCI DSP SRAM ROM MPEG SoC DRAM System Chips Why? Characteristics: Complex
Strengthen RFID Tags Security Using New Data Structure
 International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
International Journal of Control and Automation 51 Strengthen RFID Tags Security Using New Data Structure Yan Liang and Chunming Rong Department of Electrical Engineering and Computer Science, University
Smart Card Security How Can We Be So Sure?
 Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Smart Card Security How Can We Be So Sure? Ernst Bovelander TNO Centre for Evaluation of Instrumentation and Security Techniques PO Box 5013 2600 GA Delft, The Netherlands [email protected] 1. Introduction
Reviving smart card analysis
 Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
Reviving smart card analysis Christopher Tarnovsky Karsten Nohl [email protected] [email protected] Executive summary Modern smart cards should be analyzed 1. Smart card chips provide the trust base for
INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET)
 INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET) International Journal of Electronics and Communication Engineering & Technology (IJECET), ISSN 0976 ISSN 0976 6464(Print)
INTERNATIONAL JOURNAL OF ELECTRONICS AND COMMUNICATION ENGINEERING & TECHNOLOGY (IJECET) International Journal of Electronics and Communication Engineering & Technology (IJECET), ISSN 0976 ISSN 0976 6464(Print)
Rapid System Prototyping with FPGAs
 Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Rapid System Prototyping with FPGAs By R.C. Coferand Benjamin F. Harding AMSTERDAM BOSTON HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO SINGAPORE SYDNEY TOKYO Newnes is an imprint of
Introduction to Programmable Logic Devices. John Coughlan RAL Technology Department Detector & Electronics Division
 Introduction to Programmable Logic Devices John Coughlan RAL Technology Department Detector & Electronics Division PPD Lectures Programmable Logic is Key Underlying Technology. First-Level and High-Level
Introduction to Programmable Logic Devices John Coughlan RAL Technology Department Detector & Electronics Division PPD Lectures Programmable Logic is Key Underlying Technology. First-Level and High-Level
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy
 Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Secure Network Communications FIPS 140 2 Non Proprietary Security Policy 21 June 2010 Table of Contents Introduction Module Specification Ports and Interfaces Approved Algorithms Test Environment Roles
Implementation Details
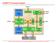 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
Pre-tested System-on-Chip Design. Accelerates PLD Development
 Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Pre-tested System-on-Chip Design Accelerates PLD Development March 2010 Lattice Semiconductor 5555 Northeast Moore Ct. Hillsboro, Oregon 97124 USA Telephone: (503) 268-8000 www.latticesemi.com 1 Pre-tested
Aims and Objectives. E 3.05 Digital System Design. Course Syllabus. Course Syllabus (1) Programmable Logic
 Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: [email protected] How to go
Aims and Objectives E 3.05 Digital System Design Peter Cheung Department of Electrical & Electronic Engineering Imperial College London URL: www.ee.ic.ac.uk/pcheung/ E-mail: [email protected] How to go
Best Practises for LabVIEW FPGA Design Flow. uk.ni.com ireland.ni.com
 Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Best Practises for LabVIEW FPGA Design Flow 1 Agenda Overall Application Design Flow Host, Real-Time and FPGA LabVIEW FPGA Architecture Development FPGA Design Flow Common FPGA Architectures Testing and
Security Policy for Oracle Advanced Security Option Cryptographic Module
 Security Policy for Oracle Advanced Security Option Cryptographic Module Version 1.0 September 1999 Prepared by Oracle Corporation A. Scope of Document This document describes the security policy for the
Security Policy for Oracle Advanced Security Option Cryptographic Module Version 1.0 September 1999 Prepared by Oracle Corporation A. Scope of Document This document describes the security policy for the
Digitale Signalverarbeitung mit FPGA (DSF) Soft Core Prozessor NIOS II Stand Mai 2007. Jens Onno Krah
 (DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
(DSF) Soft Core Prozessor NIOS II Stand Mai 2007 Jens Onno Krah Cologne University of Applied Sciences www.fh-koeln.de [email protected] NIOS II 1 1 What is Nios II? Altera s Second Generation
Software Defined Radio Architecture for NASA s Space Communications
 From July 2007 High Frequency Electronics Copyright 2007 Summit Technical Media Software Defined Radio Architecture for NASA s Space Communications By Maximilian C. Scardelletti, Richard C. Reinhart, Monty
From July 2007 High Frequency Electronics Copyright 2007 Summit Technical Media Software Defined Radio Architecture for NASA s Space Communications By Maximilian C. Scardelletti, Richard C. Reinhart, Monty
AStudyofEncryptionAlgorithmsAESDESandRSAforSecurity
 Global Journal of Computer Science and Technology Network, Web & Security Volume 13 Issue 15 Version 1.0 Year 2013 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
Global Journal of Computer Science and Technology Network, Web & Security Volume 13 Issue 15 Version 1.0 Year 2013 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals
On a New Way to Read Data from Memory
 On a New Way to Read Data from Memory David Samyde 1, Sergei Skorobogatov 2, Ross Anderson 2 and Jean-Jacques Quisquater 1 1: Université catholique de Louvain, UCL Crypto Group Place du Levant, 3, B-1348
On a New Way to Read Data from Memory David Samyde 1, Sergei Skorobogatov 2, Ross Anderson 2 and Jean-Jacques Quisquater 1 1: Université catholique de Louvain, UCL Crypto Group Place du Levant, 3, B-1348
KEEP IT SYNPLE STUPID
 Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Utilizing Programmable Logic for Analyzing Hardware Targets Dmitry Nedospasov SHORT DESCRIPTION Hardware security analysis differs from software security analysis primarily in the tools
Wireless Sensor Network: Challenges, Issues and Research
 ISBN 978-93-84468-20-0 Proceedings of 2015 International Conference on Future Computational Technologies (ICFCT'2015) Singapore, March 29-30, 2015, pp. 224-228 Wireless Sensor Network: Challenges, Issues
ISBN 978-93-84468-20-0 Proceedings of 2015 International Conference on Future Computational Technologies (ICFCT'2015) Singapore, March 29-30, 2015, pp. 224-228 Wireless Sensor Network: Challenges, Issues
Hardware Implementation of AES Encryption and Decryption System Based on FPGA
 Send Orders for Reprints to [email protected] The Open Cybernetics & Systemics Journal, 2015, 9, 1373-1377 1373 Open Access Hardware Implementation of AES Encryption and Decryption System Based
Send Orders for Reprints to [email protected] The Open Cybernetics & Systemics Journal, 2015, 9, 1373-1377 1373 Open Access Hardware Implementation of AES Encryption and Decryption System Based
THREAT MODELLING FOR SECURITY TOKENS IN WEB APPLICATIONS
 THREAT MODELLING FOR SECURITY TOKENS IN WEB APPLICATIONS Danny De Cock, Karel Wouters, Dries Schellekens, Dave Singelee and Bart Preneel COSIC Research Group, Dept. Electrical Engineering-ESAT, Katholieke
THREAT MODELLING FOR SECURITY TOKENS IN WEB APPLICATIONS Danny De Cock, Karel Wouters, Dries Schellekens, Dave Singelee and Bart Preneel COSIC Research Group, Dept. Electrical Engineering-ESAT, Katholieke
Design and Analysis of Parallel AES Encryption and Decryption Algorithm for Multi Processor Arrays
 IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 5, Issue, Ver. III (Jan - Feb. 205), PP 0- e-issn: 239 4200, p-issn No. : 239 497 www.iosrjournals.org Design and Analysis of Parallel AES
IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 5, Issue, Ver. III (Jan - Feb. 205), PP 0- e-issn: 239 4200, p-issn No. : 239 497 www.iosrjournals.org Design and Analysis of Parallel AES
NVM memory: A Critical Design Consideration for IoT Applications
 NVM memory: A Critical Design Consideration for IoT Applications Jim Lipman Sidense Corp. Introduction The Internet of Things (IoT), sometimes called the Internet of Everything (IoE), refers to an evolving
NVM memory: A Critical Design Consideration for IoT Applications Jim Lipman Sidense Corp. Introduction The Internet of Things (IoT), sometimes called the Internet of Everything (IoE), refers to an evolving
NIOS II Based Embedded Web Server Development for Networking Applications
 NIOS II Based Embedded Web Server Development for Networking Applications 1 Sheetal Bhoyar, 2 Dr. D. V. Padole 1 Research Scholar, G. H. Raisoni College of Engineering, Nagpur, India 2 Professor, G. H.
NIOS II Based Embedded Web Server Development for Networking Applications 1 Sheetal Bhoyar, 2 Dr. D. V. Padole 1 Research Scholar, G. H. Raisoni College of Engineering, Nagpur, India 2 Professor, G. H.
Design of a High Speed Communications Link Using Field Programmable Gate Arrays
 Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
Customer-Authored Application Note AC103 Design of a High Speed Communications Link Using Field Programmable Gate Arrays Amy Lovelace, Technical Staff Engineer Alcatel Network Systems Introduction A communication
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES
 SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
SECURE IMPLEMENTATIONS OF CONTENT PROTECTION (DRM) SCHEMES ON CONSUMER ELECTRONIC DEVICES Contents Introduction... 3 DRM Threat Model... 3 DRM Flow... 4 DRM Assets... 5 Threat Model... 5 Protection of
CycurHSM An Automotive-qualified Software Stack for Hardware Security Modules
 CycurHSM An Automotive-qualified Software Stack for Hardware Security Modules Dr. Frederic Stumpf, ESCRYPT GmbH Embedded Security, Stuttgart, Germany 1 Introduction Electronic Control Units (ECU) are embedded
CycurHSM An Automotive-qualified Software Stack for Hardware Security Modules Dr. Frederic Stumpf, ESCRYPT GmbH Embedded Security, Stuttgart, Germany 1 Introduction Electronic Control Units (ECU) are embedded
Networking Virtualization Using FPGAs
 Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
Networking Virtualization Using FPGAs Russell Tessier, Deepak Unnikrishnan, Dong Yin, and Lixin Gao Reconfigurable Computing Group Department of Electrical and Computer Engineering University of Massachusetts,
SECURITY IMPROVMENTS TO THE DIFFIE-HELLMAN SCHEMES
 www.arpapress.com/volumes/vol8issue1/ijrras_8_1_10.pdf SECURITY IMPROVMENTS TO THE DIFFIE-HELLMAN SCHEMES Malek Jakob Kakish Amman Arab University, Department of Computer Information Systems, P.O.Box 2234,
www.arpapress.com/volumes/vol8issue1/ijrras_8_1_10.pdf SECURITY IMPROVMENTS TO THE DIFFIE-HELLMAN SCHEMES Malek Jakob Kakish Amman Arab University, Department of Computer Information Systems, P.O.Box 2234,
Offline HW/SW Authentication for Reconfigurable Platforms
 Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech [email protected] Patrick Schaumont Virginia Tech [email protected] Abstract Many Field-Programmable Gate Array (FPGA) based
Offline HW/SW Authentication for Reconfigurable Platforms Eric Simpson Virginia Tech [email protected] Patrick Schaumont Virginia Tech [email protected] Abstract Many Field-Programmable Gate Array (FPGA) based
PFP Technology White Paper
 PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
PFP Technology White Paper Summary PFP Cybersecurity solution is an intrusion detection solution based on observing tiny patterns on the processor power consumption. PFP is capable of detecting intrusions
Hardware and Software
 Hardware and Software 1 Hardware and Software: A complete design Hardware and software support each other Sometimes it is necessary to shift functions from software to hardware or the other way around
Hardware and Software 1 Hardware and Software: A complete design Hardware and software support each other Sometimes it is necessary to shift functions from software to hardware or the other way around
IMPLEMENTATION OF FPGA CARD IN CONTENT FILTERING SOLUTIONS FOR SECURING COMPUTER NETWORKS. Received May 2010; accepted July 2010
 ICIC Express Letters Part B: Applications ICIC International c 2010 ISSN 2185-2766 Volume 1, Number 1, September 2010 pp. 71 76 IMPLEMENTATION OF FPGA CARD IN CONTENT FILTERING SOLUTIONS FOR SECURING COMPUTER
ICIC Express Letters Part B: Applications ICIC International c 2010 ISSN 2185-2766 Volume 1, Number 1, September 2010 pp. 71 76 IMPLEMENTATION OF FPGA CARD IN CONTENT FILTERING SOLUTIONS FOR SECURING COMPUTER
Getting Started with Embedded System Development using MicroBlaze processor & Spartan-3A FPGAs. MicroBlaze
 Getting Started with Embedded System Development using MicroBlaze processor & Spartan-3A FPGAs This tutorial is an introduction to Embedded System development with the MicroBlaze soft processor and low
Getting Started with Embedded System Development using MicroBlaze processor & Spartan-3A FPGAs This tutorial is an introduction to Embedded System development with the MicroBlaze soft processor and low
Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012)
 Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012) Sergei Skorobogatov University of Cambridge Cambridge, UK [email protected] Christopher Woods Quo Vadis Labs London,
Breakthrough silicon scanning discovers backdoor in military chip (DRAFT of 05 March 2012) Sergei Skorobogatov University of Cambridge Cambridge, UK [email protected] Christopher Woods Quo Vadis Labs London,
A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks
 A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks HoonJae Lee 1, ManKi Ahn 2, SeonGan Lim 3, and SangJae Moon 4 1 Dongseo University, Busan, 617-716, Korea [email protected]
A Study on Smart Card Security Evaluation Criteria for Side Channel Attacks HoonJae Lee 1, ManKi Ahn 2, SeonGan Lim 3, and SangJae Moon 4 1 Dongseo University, Busan, 617-716, Korea [email protected]
A Compact FPGA Implementation of Triple-DES Encryption System with IP Core Generation and On-Chip Verification
 Proceedings of the 2010 International Conference on Industrial Engineering and Operations Management Dhaka, Bangladesh, January 9 10, 2010 A Compact FPGA Implementation of Triple-DES Encryption System
Proceedings of the 2010 International Conference on Industrial Engineering and Operations Management Dhaka, Bangladesh, January 9 10, 2010 A Compact FPGA Implementation of Triple-DES Encryption System
A Comparative Study Of Two Symmetric Encryption Algorithms Across Different Platforms.
 A Comparative Study Of Two Symmetric Algorithms Across Different Platforms. Dr. S.A.M Rizvi 1,Dr. Syed Zeeshan Hussain 2 and Neeta Wadhwa 3 Deptt. of Computer Science, Jamia Millia Islamia, New Delhi,
A Comparative Study Of Two Symmetric Algorithms Across Different Platforms. Dr. S.A.M Rizvi 1,Dr. Syed Zeeshan Hussain 2 and Neeta Wadhwa 3 Deptt. of Computer Science, Jamia Millia Islamia, New Delhi,
Design and Verification of Area-Optimized AES Based on FPGA Using Verilog HDL
 Design and Verification of Area-Optimized AES Based on FPGA Using Verilog HDL 1 N. Radhika, 2 Obili Ramesh, 3 Priyadarshini, 3 Asst.Profosser, 1,2 M.Tech ( Digital Systems & Computer Electronics), 1,2,3,
Design and Verification of Area-Optimized AES Based on FPGA Using Verilog HDL 1 N. Radhika, 2 Obili Ramesh, 3 Priyadarshini, 3 Asst.Profosser, 1,2 M.Tech ( Digital Systems & Computer Electronics), 1,2,3,
Enabling Security in ProASIC 3 FPGAs with Hardware and Software Features
 Enabling Security in ProASIC 3 FPGAs with Hardware and Software Features Hans Schmitz Area Technical Manager / Field Applications Engineer September 2, 2009 Abstract Two types of security features available
Enabling Security in ProASIC 3 FPGAs with Hardware and Software Features Hans Schmitz Area Technical Manager / Field Applications Engineer September 2, 2009 Abstract Two types of security features available
CONNECT PROTECT SECURE. Communication, Networking and Security Solutions for Defense
 CONNECT PROTECT Communication, Networking and Security Solutions for Defense Engage Communication provides Defense, Homeland Security and Intelligence Communities with innovative and cost effective solutions
CONNECT PROTECT Communication, Networking and Security Solutions for Defense Engage Communication provides Defense, Homeland Security and Intelligence Communities with innovative and cost effective solutions
SENSE Security overview 2014
 SENSE Security overview 2014 Abstract... 3 Overview... 4 Installation... 6 Device Control... 7 Enrolment Process... 8 Authentication... 9 Network Protection... 12 Local Storage... 13 Conclusion... 15 2
SENSE Security overview 2014 Abstract... 3 Overview... 4 Installation... 6 Device Control... 7 Enrolment Process... 8 Authentication... 9 Network Protection... 12 Local Storage... 13 Conclusion... 15 2
A PPENDIX H RITERIA FOR AES E VALUATION C RITERIA FOR
 A PPENDIX H RITERIA FOR AES E VALUATION C RITERIA FOR William Stallings Copyright 20010 H.1 THE ORIGINS OF AES...2 H.2 AES EVALUATION...3 Supplement to Cryptography and Network Security, Fifth Edition
A PPENDIX H RITERIA FOR AES E VALUATION C RITERIA FOR William Stallings Copyright 20010 H.1 THE ORIGINS OF AES...2 H.2 AES EVALUATION...3 Supplement to Cryptography and Network Security, Fifth Edition
Testing of Digital System-on- Chip (SoC)
 Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Testing of Digital System-on- Chip (SoC) 1 Outline of the Talk Introduction to system-on-chip (SoC) design Approaches to SoC design SoC test requirements and challenges Core test wrapper P1500 core test
Network Security 網 路 安 全. Lecture 1 February 20, 2012 洪 國 寶
 Network Security 網 路 安 全 Lecture 1 February 20, 2012 洪 國 寶 1 Outline Course information Motivation Introduction to security Basic network concepts Network security models Outline of the course 2 Course
Network Security 網 路 安 全 Lecture 1 February 20, 2012 洪 國 寶 1 Outline Course information Motivation Introduction to security Basic network concepts Network security models Outline of the course 2 Course
Chapter 2 Features of Embedded System
 Chapter 2 Features of Embedded System Abstract This chapter will introduce the basic elements of embedded systems (or dedicated systems). The integrated control systems represent one of the areas of modern
Chapter 2 Features of Embedded System Abstract This chapter will introduce the basic elements of embedded systems (or dedicated systems). The integrated control systems represent one of the areas of modern
Problems of Security in Ad Hoc Sensor Network
 Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
Problems of Security in Ad Hoc Sensor Network Petr Hanáček * [email protected] Abstract: The paper deals with a problem of secure communication between autonomous agents that form an ad hoc sensor wireless
How To Perform Differential Frequency Analysis (Dfa) On A Powerline (Aes) On An Iphone Or Ipad (Ase) On Microsoft Powerline 2 (Aces) On Pc Or Ipa (Aas)
 A New Frequency-Based Side Channel Attack for Embedded Systems by Chin Chi Tiu A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree of Master of Applied
A New Frequency-Based Side Channel Attack for Embedded Systems by Chin Chi Tiu A thesis presented to the University of Waterloo in fulfillment of the thesis requirement for the degree of Master of Applied
Split Based Encryption in Secure File Transfer
 Split Based Encryption in Secure File Transfer Parul Rathor, Rohit Sehgal Assistant Professor, Dept. of CSE, IET, Nagpur University, India Assistant Professor, Dept. of CSE, IET, Alwar, Rajasthan Technical
Split Based Encryption in Secure File Transfer Parul Rathor, Rohit Sehgal Assistant Professor, Dept. of CSE, IET, Nagpur University, India Assistant Professor, Dept. of CSE, IET, Alwar, Rajasthan Technical
Design of a High-speed and large-capacity NAND Flash storage system based on Fiber Acquisition
 Design of a High-speed and large-capacity NAND Flash storage system based on Fiber Acquisition Qing Li, Shanqing Hu * School of Information and Electronic Beijing Institute of Technology Beijing, China
Design of a High-speed and large-capacity NAND Flash storage system based on Fiber Acquisition Qing Li, Shanqing Hu * School of Information and Electronic Beijing Institute of Technology Beijing, China
International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research)
 International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0020 ISSN (Online): 2279-0039 International
International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) ISSN (Print): 2279-0020 ISSN (Online): 2279-0039 International
Anti-Counterfeiting with Hardware Intrinsic Security
 Anti-Counterfeiting with Hardware Intrinsic Security Vincent van der Leest and Pim Tuyls Intrinsic-ID, Eindhoven, The Netherlands http://www.intrinsic-id.com Abstract Counterfeiting of goods and electronic
Anti-Counterfeiting with Hardware Intrinsic Security Vincent van der Leest and Pim Tuyls Intrinsic-ID, Eindhoven, The Netherlands http://www.intrinsic-id.com Abstract Counterfeiting of goods and electronic
Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified
 Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
Standard: Data Security Standard (DSS) Requirement: 6.6 Date: February 2008 Information Supplement: Requirement 6.6 Code Reviews and Application Firewalls Clarified Release date: 2008-04-15 General PCI
Microsemi Security Center of Excellence
 Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Microsemi Security Center of Excellence Sales and FAE Training August 24, 2015 1 Outline What is the Security Center of Excellence (SCoE)? Overview of Microsemi s Security capabilities and expertise Threat
Evaluating The Performance of Symmetric Encryption Algorithms
 International Journal of Network Security, Vol.10, No.3, PP.213 219, May 2010 213 Evaluating The Performance of Symmetric Encryption Algorithms Diaa Salama Abd Elminaam 1, Hatem Mohamed Abdual Kader 2,
International Journal of Network Security, Vol.10, No.3, PP.213 219, May 2010 213 Evaluating The Performance of Symmetric Encryption Algorithms Diaa Salama Abd Elminaam 1, Hatem Mohamed Abdual Kader 2,
Thwarting Selective Insider Jamming Attacks in Wireless Network by Delaying Real Time Packet Classification
 Thwarting Selective Insider Jamming Attacks in Wireless Network by Delaying Real Time Packet Classification LEKSHMI.M.R Department of Computer Science and Engineering, KCG College of Technology Chennai,
Thwarting Selective Insider Jamming Attacks in Wireless Network by Delaying Real Time Packet Classification LEKSHMI.M.R Department of Computer Science and Engineering, KCG College of Technology Chennai,
How To Protect A Web Application From Attack From A Trusted Environment
 Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
Standard: Version: Date: Requirement: Author: PCI Data Security Standard (PCI DSS) 1.2 October 2008 6.6 PCI Security Standards Council Information Supplement: Application Reviews and Web Application Firewalls
Handout 17. by Dr Sheikh Sharif Iqbal. Memory Unit and Read Only Memories
 Handout 17 by Dr Sheikh Sharif Iqbal Memory Unit and Read Only Memories Objective: - To discuss different types of memories used in 80x86 systems for storing digital information. - To learn the electronic
Handout 17 by Dr Sheikh Sharif Iqbal Memory Unit and Read Only Memories Objective: - To discuss different types of memories used in 80x86 systems for storing digital information. - To learn the electronic
Hardware Security Modules for Protecting Embedded Systems
 Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
Hardware Security Modules for Protecting Embedded Systems Marko Wolf, ESCRYPT GmbH Embedded Security, Munich, Germany André Weimerskirch, ESCRYPT Inc. Embedded Security, Ann Arbor, USA 1 Introduction &
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices
 An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany [email protected]
An On-chip Security Monitoring Solution For System Clock For Low Cost Devices Frank Vater Innovations for High Performance Microelectronics Im Technologiepark 25 15236 Frankfurt (Oder), Germany [email protected]
Physical Security: Status and Outlook
 Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
Chapter 1: Introduction
 Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
Chapter 1 Introduction 1 Chapter 1: Introduction 1.1 Inspiration Cloud Computing Inspired by the cloud computing characteristics like pay per use, rapid elasticity, scalable, on demand self service, secure
MovieLabs Specification for Enhanced Content Protection Version 1.0
 MovieLabs Specification for Enhanced Content Protection Version 1.0 Introduction Digital content distribution technologies are evolving and advancing at a rapid pace. Content creators are using these technologies
MovieLabs Specification for Enhanced Content Protection Version 1.0 Introduction Digital content distribution technologies are evolving and advancing at a rapid pace. Content creators are using these technologies
International Journal of Engineering Research & Management Technology
 International Journal of Engineering Research & Management Technology March- 2015 Volume 2, Issue-2 Radio Frequency Identification Security System Mr. Shailendra Kumar Assistant Professor Department of
International Journal of Engineering Research & Management Technology March- 2015 Volume 2, Issue-2 Radio Frequency Identification Security System Mr. Shailendra Kumar Assistant Professor Department of
Pervasive Computing und. Informationssicherheit
 Pervasive Computing und 11. Symposium on Privacy and Security Rüschlikon, 13. September 2006 Prof. Christof Paar European Competence Center for IT Security www.crypto.rub.de Contents 1. Pervasive Computing
Pervasive Computing und 11. Symposium on Privacy and Security Rüschlikon, 13. September 2006 Prof. Christof Paar European Competence Center for IT Security www.crypto.rub.de Contents 1. Pervasive Computing
2. TEACHING ENVIRONMENT AND MOTIVATION
 A WEB-BASED ENVIRONMENT PROVIDING REMOTE ACCESS TO FPGA PLATFORMS FOR TEACHING DIGITAL HARDWARE DESIGN Angel Fernández Herrero Ignacio Elguezábal Marisa López Vallejo Departamento de Ingeniería Electrónica,
A WEB-BASED ENVIRONMENT PROVIDING REMOTE ACCESS TO FPGA PLATFORMS FOR TEACHING DIGITAL HARDWARE DESIGN Angel Fernández Herrero Ignacio Elguezábal Marisa López Vallejo Departamento de Ingeniería Electrónica,
Unknown Plaintext Template Attacks
 Unknown Plaintext Template Attacks Neil Hanley, Michael Tunstall 2, and William P. Marnane Department of Electrical and Electronic Engineering, University College Cork, Ireland. [email protected], [email protected]
Unknown Plaintext Template Attacks Neil Hanley, Michael Tunstall 2, and William P. Marnane Department of Electrical and Electronic Engineering, University College Cork, Ireland. [email protected], [email protected]
LatticeXP2 Configuration Encryption and Security Usage Guide
 April 2013 Introduction Technical Note TN1142 Unlike a volatile FPGA, which requires an external boot-prom to store configuration data, the LatticeXP2 devices are non-volatile and have on-chip configuration
April 2013 Introduction Technical Note TN1142 Unlike a volatile FPGA, which requires an external boot-prom to store configuration data, the LatticeXP2 devices are non-volatile and have on-chip configuration
Design Security in Nonvolatile Flash and Antifuse FPGAs. Security Backgrounder
 Design Security in Nonvolatile Flash and Antifuse FPGAs Security Backgrounder 2002 Actel Corporation All Rights Reserved. Actel and the Actel logo are trademarks of Actel Corporation. All other brand or
Design Security in Nonvolatile Flash and Antifuse FPGAs Security Backgrounder 2002 Actel Corporation All Rights Reserved. Actel and the Actel logo are trademarks of Actel Corporation. All other brand or
