SECURING YOUR LAPTOP
|
|
|
- Rosaline Johnston
- 7 years ago
- Views:
Transcription
1 SECURING YOUR LAPTOP
2 What do you want to secure your laptop from? A) Theft B) Data Loss C) Viruses, Spyware, Malware
3 Physical Security
4 PHYSICAL SECURITY IN THE OFFICE TRAVELING BY CAR AT A HOTEL AT THE AIRPORT
5 Assume no place is safe. GENERAL TIPS Don t use the most common laptop carrying case. When you are not using your laptop p it should be kept away Don t leave you laptop alone for a minute. Laptop should be tagged with an asset tag or tag with company, name and address if possible. Don t use the laptop in overcrowded places. Make sure you have your laptops model number and serial number written down in a safe place and is registered with the manufacturer
6 PROTECTING LAPTOP AT THE OFFICE Use cable locks to secure the laptop down to a strong immovable object.
7 PROTECTING LAPTOP AT THE OFFICE You can use those locks if you laptop have the Universal Security Slot (USS) Most laptops have this Use a docking station. When you leave e your office for any reason lock the door behind you even if it is for a minute. If you are leaving your laptop in your office overnight, lock it in a desk drawer
8 Protecting you laptop in your car Don t keep you laptop stored in the front or back seat of your car. Always store it in the a trunk of the car. Always put the laptop in the trunk before you leave for your destination and not after. Don t know who is watching. Always take the laptop in after reaching your final destination. Laptops in general can get damaged if stored in the car for long periods of time due to extreme heat or cold conditions. Cable locks also can be used as an extra precaution.
9 Protecting the laptop at a Hotel Bring a cable lock with you to secure it down in your room. Lock the laptop in the hotel room safe if possible Don t leave the laptop in the room. Take it wherever you go
10 Protecting your Laptop at the Airport Should always bring your laptop as a carryon item. Do not check in. Be aware of any distractions. Keep an eye on your laptop p case or bag. There will be a few times along the way in the airport you will have to set the bag down below you (ex checking in, security line, waiting area).
11 DATA LOSS PREVENTION
12 Data Loss Prevention Preventing data theft off your laptop is all about building layers of security. When getting a laptop you must choose an operating system that allows a secure logon. If you have a windows based laptop you will have Windows XP, Vista or soon with have Windows 7 which comes out next month. If you have a Mac you will probably have the Mac OS 10.5 operating system. Both allow for an authenticated logon.
13 PASSWORDS AND ACCOUNTS ON LAPTOPS Create a BIOS password Use a strong password for your user accounts on the laptop. Do not use words you can find in the dictionary or use your pets name or any other name. Should rename the administrator account and disable it. Create two additional accounts one with limited privileges and another with administrative privileges. Some laptops have fingerprint readers. This can be setup to use your fingerprint to login to the laptop p
14 MORE DATA LOSS PROTECTION Encrypting your hard drive adds another layer of security to you laptop. It adds on another layer on top of your existing files system, so only anyone who knows the password will be able to access the computer. It also prevents someone from taking out the hard drive and putting it in another computer to access the data.
15 BEST PRACTICES TO PREVENT DATA LOSS Protect your Password. DO NOT WRITE IT ON A POST IT AND PASTE IT ON THE LAPTOP!!!! Change your passwords frequently. Do not store critical or vital data on the laptop. Store it on a external hard drive or usb drive. Do not store this hard drive or usb drive in the same location as the laptop.
16 DATA PROTECTION AND WIRELESS CONNECTIONS When looking for wireless connections, you don t want to just connect to any wireless you find. You want to make sure you have the following settings set in you pc
17
18 To change these settings you must click start->setting->network connection->and right click on wireless connections Then click on wireless connections-> advanced button on bottom right
19 VPN When you are traveling away and connecting to the internet it is a good idea to login to the Virtual Private Network(vpn) for gw. Advantages: 1)able to access gw resources 2) gives secure connection on data being passed
20 To login to the vpn: Two ways: 1) 2) use vpn client on most gwu imaged laptops p called GWBUSSnet Use your gwu net id usernname and password to login
21 PROTECT YOUR LAPTOP FROM VIRUSES, SPYWARE AND MALWARE
22 SOFTWARE PROTECTION Should have antivirus software on the laptop with updated definitions. Should have a firewall program on the laptop p
23 BEST PRACTICES AND PROCEDURES Login to your laptop with account that doesn t have administrator privileges. Use this as your main account. You only need administrator writes when you need to install software most of the time. Don t open s from people you don t know. St f k ti l Stay away from unknown or nonconventional websites.
24 OTHER PREVENTION TIPS Keep your computer software up to date. For windows pcs, the second Tuesday of every month is known as patch Tuesday. This is the day Microsoft releases any critical updates for its windows. These updates must be installed to protect your computer from any vulnerabilities in windows software. You can go to the website to manually run the updates. Have your antivirus software automatically check for updates daily. You should periodically check for updated software for quicktime, adobe products. For Macintosh computers you can click on the apple and click on software updates to check for updates on the computer. It will find any updates for the apple software as well as other apples supported software.
25 FILE MANAGEMENT What is file management? It is about organization of information stored on your computer. You organized your information using Drives Folders Files
26 Why we need file management It improves the way you organize and store your information Three ways to good file management 1) Good Folder Structure 2) Name Files and Folders 3) Backup files
27 Most common places to store your files and folders 1) Desktop 2) My Documents 3) Network drives
28 GWU RESOURCES
29 ANY QUESTIONS?
Quick Start Guide to Logging in to Online Banking
 Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
Quick Start Guide to Logging in to Online Banking Log In to Internet Banking: Note: The first time you log in you are required to use your Customer ID. Your Customer ID is the primary account holder s
The ECU Wireless system uses a captive portal authentication system. There are three steps to configure your computer for wireless access:
 ECU WIRELESS SETUP The ECU Wireless system uses a captive portal authentication system. There are three steps to configure your computer for wireless access: 1. Install a wireless network card into your
ECU WIRELESS SETUP The ECU Wireless system uses a captive portal authentication system. There are three steps to configure your computer for wireless access: 1. Install a wireless network card into your
WakeMyPC technical user guide
 USER GUIDE WakeMyPC technical user guide WakeMyPC is the name for the new Wake-on-LAN (WoL) service that allows you to boot your office PC or Apple Mac from home. With this new service you no longer need
USER GUIDE WakeMyPC technical user guide WakeMyPC is the name for the new Wake-on-LAN (WoL) service that allows you to boot your office PC or Apple Mac from home. With this new service you no longer need
CYBER-SAFETY. A computer security tutorial for UC Davis students, faculty and staff
 CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff I N T R O D U C T I O N This tutorial provides some basic information and practical suggestions for protecting
CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff I N T R O D U C T I O N This tutorial provides some basic information and practical suggestions for protecting
Maxtor OneTouch User's Guide
 EXTERNAL HARD DRIVE Maxtor OneTouch User's Guide TM II P/N:20259600 i Contents 1 Introduction................................................. 1 Maxtor OneTouch II Drive Components............................
EXTERNAL HARD DRIVE Maxtor OneTouch User's Guide TM II P/N:20259600 i Contents 1 Introduction................................................. 1 Maxtor OneTouch II Drive Components............................
Remote Access for LAPD Users Using Aventail SSL VPN
 Remote Access for LAPD Users Using Aventail SSL VPN About Aventail SSL VPN This document describes how to access the LAPD network remotely, using a technology called SSL (Secure Socket Layer) VPN (Virtual
Remote Access for LAPD Users Using Aventail SSL VPN About Aventail SSL VPN This document describes how to access the LAPD network remotely, using a technology called SSL (Secure Socket Layer) VPN (Virtual
Internet basics 2.3 Protecting your computer
 Basics Use this document with the glossary Beginner s guide to Internet basics 2.3 Protecting your computer How can I protect my computer? This activity will show you how to protect your computer from
Basics Use this document with the glossary Beginner s guide to Internet basics 2.3 Protecting your computer How can I protect my computer? This activity will show you how to protect your computer from
Instructions for connecting to the LSC-O Secure Wireless Network
 Instructions for connecting to the LSC-O Secure Wireless Network Wireless computer hot spots are available at various locations around the LSC-O campus. The Academic Center first floor, AHB first and second
Instructions for connecting to the LSC-O Secure Wireless Network Wireless computer hot spots are available at various locations around the LSC-O campus. The Academic Center first floor, AHB first and second
Brazosport College VPN Connection Installation and Setup Instructions. Draft 2 March 24, 2005
 Brazosport College VPN Connection Installation and Setup Instructions Draft 2 March 24, 2005 Introduction This is an initial draft of these instructions. These instructions have been tested by the IT department
Brazosport College VPN Connection Installation and Setup Instructions Draft 2 March 24, 2005 Introduction This is an initial draft of these instructions. These instructions have been tested by the IT department
Desktop and Laptop Security Policy
 Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
Desktop and Laptop Security Policy Appendix A Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Student Desktop@ Home
 Student Desktop@ Home Full Off Campus Access to your Programs and Files Full Access to the University from Home You can access the University from any computer with an internet connection. This system
Student Desktop@ Home Full Off Campus Access to your Programs and Files Full Access to the University from Home You can access the University from any computer with an internet connection. This system
How To Use A Citrix Netscaler Thin Client V1.09.10.1 (Windows) With A Citirix Vpn Desktop (Windows 10) With An Ipad Or Ipad (Windows 8) With Vpn
 Our Mission Statement To ensure that we are providing quality and efficient services and solutions that are consistent with the strategic goals of the Area, and that are closely aligned with the State's
Our Mission Statement To ensure that we are providing quality and efficient services and solutions that are consistent with the strategic goals of the Area, and that are closely aligned with the State's
CYBER-SAFETY BASICS. A computer security tutorial for UC Davis students, faculty and staff
 CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff INTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
CYBER-SAFETY BASICS A computer security tutorial for UC Davis students, faculty and staff INTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
Internet and Email Help. Table of Contents:
 Internet and Email Help The following tips are provided to assist you in troubleshooting and managing your Plex Internet and email services. For additional issues or concerns, you may also call our Product
Internet and Email Help The following tips are provided to assist you in troubleshooting and managing your Plex Internet and email services. For additional issues or concerns, you may also call our Product
Accessing the SUNYIT wireless network for the first time
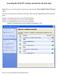 Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Accessing the SUNYIT wireless network for the first time Right click on your wireless network connection icon and select the View Available Wireless Networks option You may see several networks within
Frequently Asked Questions
 Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
Frequently Asked Questions 1) What does SkyBest Internet Guardian do? Prevents e-mail and image spam from reaching your inbox Halts access to dangerous Web pages Stops Web sites from installing dangerous
SSL VPN Service. Once you have installed the AnyConnect Secure Mobility Client, this document is available by clicking on the Help icon on the client.
 Contents Introduction... 2 Prepare Work PC for Remote Desktop... 4 Add VPN url as a Trusted Site in Internet Explorer... 5 VPN Client Installation... 5 Starting the VPN Application... 6 Connect to Work
Contents Introduction... 2 Prepare Work PC for Remote Desktop... 4 Add VPN url as a Trusted Site in Internet Explorer... 5 VPN Client Installation... 5 Starting the VPN Application... 6 Connect to Work
Yale Software Library http://www.yale.edu/software/
 e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, helpdesk@yale.edu Remote Desktop General overview With Remote Desktop, you get full access
e/ Yale Software Library http://www.yale.edu/software/ For assistance contact the ITS Help Desk 785-3200, 432-9000, helpdesk@yale.edu Remote Desktop General overview With Remote Desktop, you get full access
IT@DUSON. IT Service Desk
 IT@DUSON Technology plays a key role in the learning process for nursing students at Duke. This is your guide to the technology used at the Duke School of Nursing and how to request assistance for all
IT@DUSON Technology plays a key role in the learning process for nursing students at Duke. This is your guide to the technology used at the Duke School of Nursing and how to request assistance for all
Yale Software Library
 Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Remote Desktop for Macintosh connection to Windows MS Remote Desktop Client
Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, helpdesk@yale.edu Remote Desktop for Macintosh connection to Windows MS Remote Desktop Client
E-mail Encryption Guide version 1.2, by Thomas Reed
 E-mail Encryption Guide version 1.2, by Thomas Reed In order for two people to send and receive encrypted e-mails to/from each other, both parties need: An e-mail reader that supports encryption (such
E-mail Encryption Guide version 1.2, by Thomas Reed In order for two people to send and receive encrypted e-mails to/from each other, both parties need: An e-mail reader that supports encryption (such
E-Mail: SupportCenter@uhcl.edu Phone: 281-283-2828 Fax: 281-283-2969 Box: 230 http://www.uhcl.edu/uct
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
Connecting to the King s College VPN with Windows 7
 Connecting to the King s College VPN with Windows 7 This guide will walk you through the steps of connecting to the King s College VPN from a Windows 7 computer. A VPN connection is a tool that allows
Connecting to the King s College VPN with Windows 7 This guide will walk you through the steps of connecting to the King s College VPN from a Windows 7 computer. A VPN connection is a tool that allows
Connecting to the Staff Desktop Service
 Connecting to the Staff Desktop Service Access your programs and files just like you were in the office Get Setup The first step to use our Remote Connection service is to check that you have the free
Connecting to the Staff Desktop Service Access your programs and files just like you were in the office Get Setup The first step to use our Remote Connection service is to check that you have the free
Digital Persona Fingerprint Reader Installation
 Digital Persona Fingerprint Reader Installation The link to download the Fingerprint Reader Software for AXIS-ACH is http://corpcu.com/fingerprint-reader-software This will begin the download for the drivers.
Digital Persona Fingerprint Reader Installation The link to download the Fingerprint Reader Software for AXIS-ACH is http://corpcu.com/fingerprint-reader-software This will begin the download for the drivers.
Sharing files on Windows XP with Mac OS X clients
 apple 1 Getting started Sharing files on Windows XP with Mac OS X clients Do you need to exchange files between Macs and Windows PCs? With built-in support for Windows SMB/CIFS protocol, Mac OS X lets
apple 1 Getting started Sharing files on Windows XP with Mac OS X clients Do you need to exchange files between Macs and Windows PCs? With built-in support for Windows SMB/CIFS protocol, Mac OS X lets
Introduction to Computing @ WSU
 Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
Introduction to Computing @ WSU Table of Contents 1 - Information Technology (IT) Security... 2 Information to Remember... 2 2 - Malware... 2 Information to Remember... 3 3 - Firewalls... 3 Information
LSGMI REMOTE DESKTOP SERVICES.
 LSGMI REMOTE DESKTOP SERVICES. This Document is to describe the steps that you should follow in order to have a secured Remote Access to this Service. Requirements: Access to Remote Services is only supported
LSGMI REMOTE DESKTOP SERVICES. This Document is to describe the steps that you should follow in order to have a secured Remote Access to this Service. Requirements: Access to Remote Services is only supported
Canterbury College Eduroam Wi-Fi Guide
 Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Wireless Printing Setup Guide
 Temple University Beasley School of Law Wireless Printing Setup Guide Updated August, 2012 Temple Law Computer Services 8/27/2012 Table of Contents Computer Operating System Page Windows 7 2 Windows Vista
Temple University Beasley School of Law Wireless Printing Setup Guide Updated August, 2012 Temple Law Computer Services 8/27/2012 Table of Contents Computer Operating System Page Windows 7 2 Windows Vista
Internet Guide. Prepared for 55 John Street
 Internet Guide Prepared for 55 John Street I. Internet Service How do I connect to the Internet? WiFi (Wireless Connectivity) is available throughout the building. In order to connect, you will need a
Internet Guide Prepared for 55 John Street I. Internet Service How do I connect to the Internet? WiFi (Wireless Connectivity) is available throughout the building. In order to connect, you will need a
Online Banking Fraud Prevention Recommendations and Best Practices
 Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Online Banking Fraud Prevention Recommendations and Best Practices This document provides you with fraud prevention best practices that every employee at Continental National Bank of Miami needs to know
Downloading, Installing, and Updating Sophos Anti-Virus
 Downloading, Installing, and Updating Sophos Anti-Virus Part 1: Downloading Sophos Anti-Virus 1) Open your Internet browser and go to www.bol.ucla.edu. *Only use Chrome or Firefox to download this installation.
Downloading, Installing, and Updating Sophos Anti-Virus Part 1: Downloading Sophos Anti-Virus 1) Open your Internet browser and go to www.bol.ucla.edu. *Only use Chrome or Firefox to download this installation.
Frequently Asked Questions
 FAQs Frequently Asked Questions Connecting your Linksys router to the Internet 1 What computer operating systems does my Linksys router support? 1 Why can t I connect my computer or device to my router?
FAQs Frequently Asked Questions Connecting your Linksys router to the Internet 1 What computer operating systems does my Linksys router support? 1 Why can t I connect my computer or device to my router?
SURPASS HOSTING SERVICE GETTING STARTED AND OPERATIONS GUIDE
 SURPASS HOSTING SERVICE GETTING STARTED AND OPERATIONS GUIDE Welcome To Surpass Hosting Service. This document contains instructions to help you get up and running with your new service. The instructions
SURPASS HOSTING SERVICE GETTING STARTED AND OPERATIONS GUIDE Welcome To Surpass Hosting Service. This document contains instructions to help you get up and running with your new service. The instructions
Getting Started with a Mac For businesses with a Windows Server
 Getting Started with a Mac For businesses with a Windows Server This document, a quick guide designed to help you integrate a Mac into your environment, is geared toward businesses with a Microsoft server
Getting Started with a Mac For businesses with a Windows Server This document, a quick guide designed to help you integrate a Mac into your environment, is geared toward businesses with a Microsoft server
HomeNet. Gateway User Guide
 HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
This software will update your Samsung Galaxy S II to Android 4.1.2 software version GB28.
 Samsung Galaxy S II Android Jelly Bean Update Instructions This software update provided by Samsung will update your Samsung Galaxy S II from Android Gingerbread to Android Jelly Bean. This software will
Samsung Galaxy S II Android Jelly Bean Update Instructions This software update provided by Samsung will update your Samsung Galaxy S II from Android Gingerbread to Android Jelly Bean. This software will
Mac - Juniper Remote Desktop Instructions
 Mac - Juniper Remote Desktop Instructions How to Set up & Remotely Connect to your Hospital Windows Workstation from your Remote Macintosh Computer Using the JSAM Feature of Juniper. Note: These instructions
Mac - Juniper Remote Desktop Instructions How to Set up & Remotely Connect to your Hospital Windows Workstation from your Remote Macintosh Computer Using the JSAM Feature of Juniper. Note: These instructions
Using Access.Centegra.Com (Physician Access) Secure Remote Access from the Internet
 System Requirements These are the minimum requirements necessary to ensure the proper operation of Centegra Health System s Access.Centegra.Com. Administrative level access to the PC or other device used
System Requirements These are the minimum requirements necessary to ensure the proper operation of Centegra Health System s Access.Centegra.Com. Administrative level access to the PC or other device used
EZblue BusinessServer The All - In - One Server For Your Home And Business
 EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.11 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS. ftrsecure.com
 AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS ftrsecure.com Can You Separate Myths From Facts? Many Internet myths still persist that could leave you vulnerable to internet crimes. Check out
AVOIDING ONLINE THREATS CYBER SECURITY MYTHS, FACTS, TIPS ftrsecure.com Can You Separate Myths From Facts? Many Internet myths still persist that could leave you vulnerable to internet crimes. Check out
Before you begin 2 Initial laptop setup 2 Configure Microsoft update 3 Install University of Kent programs 3
 Advanced IT user guide Staff laptop setup For staff laptops owned by the University Contents Before you begin 2 Initial laptop setup 2 Configure Microsoft update 3 Install University of Kent programs 3
Advanced IT user guide Staff laptop setup For staff laptops owned by the University Contents Before you begin 2 Initial laptop setup 2 Configure Microsoft update 3 Install University of Kent programs 3
Access to applications and the network depends on whether or not you are using personal equipment or a Firm-issued laptop or desktop.
 Overview of Help & Tips The new System allows authorized users to log in and access the Firm s network through either Citrix or VPN (also known as Stonegate IPSec VPN). This system incorporates additional
Overview of Help & Tips The new System allows authorized users to log in and access the Firm s network through either Citrix or VPN (also known as Stonegate IPSec VPN). This system incorporates additional
Secure Mail Message Retrieval Instructions
 2015 Secure Mail Message Retrieval Instructions IT Security University Medical Center 1/26/2015 Table of Contents INTRODUCTION... 3 REGISTRATION MESSAGES... 3 RETRIEVING THE SECURE EMAIL... 4 SECURE MESSAGE...
2015 Secure Mail Message Retrieval Instructions IT Security University Medical Center 1/26/2015 Table of Contents INTRODUCTION... 3 REGISTRATION MESSAGES... 3 RETRIEVING THE SECURE EMAIL... 4 SECURE MESSAGE...
Paul Nguyen. 2014 CSG Interna0onal
 Paul Nguyen 2014 CSG Interna0onal Security is Top- of- Mind Everywhere High- profile breaches: 2K+ breaches expose nearly 1B records in 2013 Increased regulatory pressure State- sponsored hacking around
Paul Nguyen 2014 CSG Interna0onal Security is Top- of- Mind Everywhere High- profile breaches: 2K+ breaches expose nearly 1B records in 2013 Increased regulatory pressure State- sponsored hacking around
Using a VPN Connection
 Bullis School Using a VPN Connection Access Files and Resources While Off Campus Mark Smith Table of Contents What is a VPN?... 2 Can I set up my home computer to use a VPN connection?... 2 So how do I
Bullis School Using a VPN Connection Access Files and Resources While Off Campus Mark Smith Table of Contents What is a VPN?... 2 Can I set up my home computer to use a VPN connection?... 2 So how do I
Best Practices for Information Security
 Best Practices for Information Security Suzanne Dmytrenko, Information Privacy Officer Email: suzanne@sfsu.edu. Ph: 415-338-2823 Mig Hofmann, Information Security Officer Email: mig@sfsu.edu. Ph: 415-338-3018
Best Practices for Information Security Suzanne Dmytrenko, Information Privacy Officer Email: suzanne@sfsu.edu. Ph: 415-338-2823 Mig Hofmann, Information Security Officer Email: mig@sfsu.edu. Ph: 415-338-3018
GETTING STARTED ON THE WINDOWS SERVICE A GUIDE FOR NEW STAFF MEMBERS
 Your Login ID: GETTING STARTED ON THE WINDOWS SERVICE A GUIDE FOR NEW STAFF MEMBERS CONTENTS 1.0 Introduction... 3 1.1 Welcome to Edinburgh Napier University from Information Services!... 3 1.2 About Information
Your Login ID: GETTING STARTED ON THE WINDOWS SERVICE A GUIDE FOR NEW STAFF MEMBERS CONTENTS 1.0 Introduction... 3 1.1 Welcome to Edinburgh Napier University from Information Services!... 3 1.2 About Information
Using TS-ACCESS for Remote Desktop Access
 Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Using TS-ACCESS for Remote Desktop Access Introduction TS-ACCESS is a remote desktop access feature available to CUA faculty and staff who need to access administrative systems or other computing resources
Connecting to the King s College VPN with Windows 8
 Connecting to the King s College VPN with Windows 8 This guide will walk you through the steps of connecting to the King s College VPN (Virtual Private Network) from a Windows 8 device. A VPN connection
Connecting to the King s College VPN with Windows 8 This guide will walk you through the steps of connecting to the King s College VPN (Virtual Private Network) from a Windows 8 device. A VPN connection
Before proceeding with the update process, Back-up/Synch your data to maintian: Calendar Events Contacts E-mail Accounts Messages
 Samsung Repp Bootloader Update Instructions Samsung has released a Bootloader Update for the Samsung Repp (SCH-R680) to correct a network connectivity issue. Please follow the instructions below to download
Samsung Repp Bootloader Update Instructions Samsung has released a Bootloader Update for the Samsung Repp (SCH-R680) to correct a network connectivity issue. Please follow the instructions below to download
Why you need. McAfee. Multi Acess PARTNER SERVICES
 Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
Why you need McAfee Multi Acess PARTNER SERVICES McAfee Multi Access is an online security app that protects all types of devices. All at once. The simple monthly subscription covers up to five devices
Important Note Regarding Your Blu ray Drives
 Important Note Regarding Your Blu ray Drives Use these supplemental instructions to complete the setup of your unit Your Disc Publisher unit uses esata to connect the Blu-ray drive(s) to the computer.
Important Note Regarding Your Blu ray Drives Use these supplemental instructions to complete the setup of your unit Your Disc Publisher unit uses esata to connect the Blu-ray drive(s) to the computer.
Information Security
 Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
Information Security A staff guide to the University's Information Systems Security Policy Issued by the IT Security Group on behalf of the University. Information Systems Security Guidelines for Staff
Chapter 1 Downloading Images to Your Computer (Windows)
 Software User Guide For the safe use of your camera, be sure to read the Safety Precautions thoroughly before use. Types of software installed on your computer varies depending on the method of installation
Software User Guide For the safe use of your camera, be sure to read the Safety Precautions thoroughly before use. Types of software installed on your computer varies depending on the method of installation
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines
 Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Secure and Safe Computing Primer Examples of Desktop and Laptop standards and guidelines 1. Implement anti-virus software An anti-virus program is necessary to protect your computer from malicious programs,
Corporate Account Takeover (CATO) Risk Assessment
 Corporate Account Takeover (CATO) Risk Assessment As a business, you want to be sure you have a strong process in place for monitoring and managing who has access to your ECorp services and how the information
Corporate Account Takeover (CATO) Risk Assessment As a business, you want to be sure you have a strong process in place for monitoring and managing who has access to your ECorp services and how the information
Remote Access Using the USDA LincPass
 If you require an accessible version of this course please follow these directions. Press Shift+Control+Y to activate the Adobe Read Out Loud function. Once you have activated the Read Out Loud function
If you require an accessible version of this course please follow these directions. Press Shift+Control+Y to activate the Adobe Read Out Loud function. Once you have activated the Read Out Loud function
Office of Information Technology Desktop Security and Best Practices
 2013.06 All computer operating systems have vulnerabilities that are targeted by are subject to security risks. In a networked environment, such as a college campus, a compromised computer can affect other
2013.06 All computer operating systems have vulnerabilities that are targeted by are subject to security risks. In a networked environment, such as a college campus, a compromised computer can affect other
Barbara Ann Karmanos Cancer Institute. Instructions for Installing Cisco Systems VPN Client
 Barbara Ann Karmanos Cancer Institute Instructions for Installing Cisco Systems VPN Client DISCLAIMER: IMPORTANT INFORMATION - PLEASE READ THIS AGREEMENT CAREFULLY BEFORE OPENING THE PACKAGE AND/OR USING
Barbara Ann Karmanos Cancer Institute Instructions for Installing Cisco Systems VPN Client DISCLAIMER: IMPORTANT INFORMATION - PLEASE READ THIS AGREEMENT CAREFULLY BEFORE OPENING THE PACKAGE AND/OR USING
PREMIUM BUSINESS GATEWAY - DEVG2020 DIGITAL BUSINESS USER GUIDE
 PREMIUM BUSINESS GATEWAY - DEVG2020 DIGITAL BUSINESS USER GUIDE NEED MORE SUPPORT? If you have questions beyond this guide, we want to help. To learn more about your Business Broadband or Digital Business
PREMIUM BUSINESS GATEWAY - DEVG2020 DIGITAL BUSINESS USER GUIDE NEED MORE SUPPORT? If you have questions beyond this guide, we want to help. To learn more about your Business Broadband or Digital Business
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall:
 How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
How to Install a Network-Licensed Version of IBM SPSS Statistics 19
 How to Install a Network-Licensed Version of IBM SPSS Statistics 19 Important: IBM SPSS Statistics 19 requires either Windows XP Professional or later. IBM SPSS Statistics 19 installs from a DVD and your
How to Install a Network-Licensed Version of IBM SPSS Statistics 19 Important: IBM SPSS Statistics 19 requires either Windows XP Professional or later. IBM SPSS Statistics 19 installs from a DVD and your
Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro)
 Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
Contents Connect to the Sheridan College / Gillette College - STUDENT Secure Wireless Network with the PEAP Client (Windows XP Pro) 1. Introduction 2. Configuring the Sheridan College / Gillette College
Remote Desktop Gateway. Accessing a Campus Managed Device (Windows Only) from home.
 Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
Remote Desktop Gateway Accessing a Campus Managed Device (Windows Only) from home. Contents Introduction... 2 Quick Reference... 2 Gateway Setup - Windows Desktop... 3 Gateway Setup Windows App... 4 Gateway
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network.
 This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
This manual will help you connect your Microsoft Windows XP, Vista, or 7, or Apple OS X computer to the University of Maryland campus data network. Prerequisites for Network Registration: 1. In order to
File Management and File Storage
 File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
File Management and File Storage http://training.usask.ca Information Technology Services Division Table of Contents File Management at the University of Saskatchewan...3 Introduction...3 Creating Files
Using UWyo Wireless vs. WyoLync
 Winter 2013 In this issue: Lync - Making Conference Calls Simple IT - Helping You Stretch Your Dollar Windows OS Update Avoiding Phishing Top 4 Reasons to Use UWyo Wireless vs UW Guest Microsoft Updates
Winter 2013 In this issue: Lync - Making Conference Calls Simple IT - Helping You Stretch Your Dollar Windows OS Update Avoiding Phishing Top 4 Reasons to Use UWyo Wireless vs UW Guest Microsoft Updates
Wireless Networking. Mac/PC Compatibility: QuickStart Guide for Business
 Wireless Networking Mac/PC Compatibility: QuickStart Guide for Business 2 Wireless Networking QuickStart Guide for Business The Basics Wireless networking is an alternative to running cable around your
Wireless Networking Mac/PC Compatibility: QuickStart Guide for Business 2 Wireless Networking QuickStart Guide for Business The Basics Wireless networking is an alternative to running cable around your
Mac OS X Secure Wireless Setup Guide
 Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
Wireless @ Johns Hopkins
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Access Your Cisco Smart Storage Remotely Via WebDAV
 Application Note Access Your Cisco Smart Storage Remotely Via WebDAV WebDAV (Web-based Distributed Authoring and Versioning), is a set of extensions to the HTTP(S) protocol that allows a web server to
Application Note Access Your Cisco Smart Storage Remotely Via WebDAV WebDAV (Web-based Distributed Authoring and Versioning), is a set of extensions to the HTTP(S) protocol that allows a web server to
EZblue BusinessServer The All - In - One Server For Your Home And Business
 EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.8 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
EZblue BusinessServer The All - In - One Server For Your Home And Business Quick Start Guide Version 3.8 1 2 3 EZblue Server Overview EZblue Server Installation EZblue Server Configuration 4 EZblue Magellan
Keeping Agency Data Secure
 Keeping Agency Data Secure By Kate Gluck & Paul Fuller, Strategic Insurance Software An Introduction from Jeff Yates, Executive Director, ACT About this article: The authors provide nine great tips for
Keeping Agency Data Secure By Kate Gluck & Paul Fuller, Strategic Insurance Software An Introduction from Jeff Yates, Executive Director, ACT About this article: The authors provide nine great tips for
INFORMATION SECURITY GUIDE. Employee Teleworking. Information Security Unit. Information Technology Services (ITS) July 2013
 INFORMATION SECURITY GUIDE Employee Teleworking Information Security Unit Information Technology Services (ITS) July 2013 CONTENTS 1. Introduction... 2 2. Teleworking Risks... 3 3. Safeguards for College
INFORMATION SECURITY GUIDE Employee Teleworking Information Security Unit Information Technology Services (ITS) July 2013 CONTENTS 1. Introduction... 2 2. Teleworking Risks... 3 3. Safeguards for College
Using the UMD Wireless Network with OSX 10.5.x Leopard, 10.6 Snow Leopard, and 10.7 Lion Updated 10/2011
 Using the UMD Wireless Network with OSX 10.5.x Leopard, 10.6 Snow Leopard, and 10.7 Lion Updated 10/2011 Using the Wireless network at UMass Dartmouth is easy, but takes some initial effort to set up.
Using the UMD Wireless Network with OSX 10.5.x Leopard, 10.6 Snow Leopard, and 10.7 Lion Updated 10/2011 Using the Wireless network at UMass Dartmouth is easy, but takes some initial effort to set up.
Microsoft Exchange ActiveSync Administrator s Guide
 Microsoft Exchange ActiveSync Administrator s Guide Copyright 2005 palmone, Inc. All rights reserved. palmone, HotSync, Treo, VersaMail, and Palm OS are among the trademarks or registered trademarks owned
Microsoft Exchange ActiveSync Administrator s Guide Copyright 2005 palmone, Inc. All rights reserved. palmone, HotSync, Treo, VersaMail, and Palm OS are among the trademarks or registered trademarks owned
SAO Remote Access POLICY
 SAO Remote Access POLICY Contents PURPOSE... 4 SCOPE... 4 POLICY... 4 AUTHORIZATION... 4 PERMITTED FORMS OF REMOTE ACCESS... 5 REMOTE ACCESS USER DEVICES... 5 OPTION ONE: SAO-OWNED PC... 5 OPTION TWO:
SAO Remote Access POLICY Contents PURPOSE... 4 SCOPE... 4 POLICY... 4 AUTHORIZATION... 4 PERMITTED FORMS OF REMOTE ACCESS... 5 REMOTE ACCESS USER DEVICES... 5 OPTION ONE: SAO-OWNED PC... 5 OPTION TWO:
VPN Network Access. Principles and Restrictions
 BBG VPN WINDOWS CLIENT INSTALLATION PROCEDURES Page 1 of 11 Principles and Restrictions VPN Network Access High Speed access via broadband Internet connections is available for the Agency network resources
BBG VPN WINDOWS CLIENT INSTALLATION PROCEDURES Page 1 of 11 Principles and Restrictions VPN Network Access High Speed access via broadband Internet connections is available for the Agency network resources
Bosco Internet Setup Guide For Zest Apartments. Windows XP, Vista and Mac OS X
 Bosco Internet Setup Guide For Zest Apartments Windows XP, Vista and Mac OS X Contents Page Windows XP... 3 Windows Vista... 19 Mac OS X... 25 Bosco Internet Setup Guide - Page 2 How to get connected at
Bosco Internet Setup Guide For Zest Apartments Windows XP, Vista and Mac OS X Contents Page Windows XP... 3 Windows Vista... 19 Mac OS X... 25 Bosco Internet Setup Guide - Page 2 How to get connected at
Refer to the Troubleshooting section first if you experience a problem with the product.
 D3 Station Your product comes with a quick start guide and a user s manual. Following the instructions and precautions of this manual will ensure easier and more enjoyable use of your D3 Station External
D3 Station Your product comes with a quick start guide and a user s manual. Following the instructions and precautions of this manual will ensure easier and more enjoyable use of your D3 Station External
Imaging License Server User Guide
 IMAGING LICENSE SERVER USER GUIDE Imaging License Server User Guide PerkinElmer Viscount Centre II, University of Warwick Science Park, Millburn Hill Road, Coventry, CV4 7HS T +44 (0) 24 7669 2229 F +44
IMAGING LICENSE SERVER USER GUIDE Imaging License Server User Guide PerkinElmer Viscount Centre II, University of Warwick Science Park, Millburn Hill Road, Coventry, CV4 7HS T +44 (0) 24 7669 2229 F +44
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
User Guide HUAWEI UML397. Welcome to HUAWEI
 User Guide HUAWEI UML397 Welcome to HUAWEI 1 Huawei UML397 4G LTE Wireless Modem User Manual CHAPTER 1 BEFORE USING YOUR UML397 WIRELESS MODEM ABOUT THIS USER MANUAL...4 WHAT S INSIDE THE PRODUCT PACKAGE...4
User Guide HUAWEI UML397 Welcome to HUAWEI 1 Huawei UML397 4G LTE Wireless Modem User Manual CHAPTER 1 BEFORE USING YOUR UML397 WIRELESS MODEM ABOUT THIS USER MANUAL...4 WHAT S INSIDE THE PRODUCT PACKAGE...4
HDD Password Tool. User s Manual. English
 HDD Password Tool User s Manual English 1 Table of Contents Chapter 1: Introduction... 3 Trademarks... 3 Chapter 2: Required Operating System... 5 - HDD Password Tool for Windows... 5 - HDD Password Tool
HDD Password Tool User s Manual English 1 Table of Contents Chapter 1: Introduction... 3 Trademarks... 3 Chapter 2: Required Operating System... 5 - HDD Password Tool for Windows... 5 - HDD Password Tool
Charter Business Desktop Security Administrator's Guide
 Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
Charter Business Desktop Security Administrator's Guide Table of Contents Chapter 1: Introduction... 4 Chapter 2: Getting Started... 5 Creating a new user... 6 Recovering and changing your password...
National Cyber Security Month 2015: Daily Security Awareness Tips
 National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
MAPPING THE WEBDRIVE REFERENCE GUIDE
 MAPPING THE WEBDRIVE REFERENCE GUIDE INTRODUCTION The university WebDrive is a dedicated drive to host all university web content. For help with mapping the WebDrive, please read the instructions below
MAPPING THE WEBDRIVE REFERENCE GUIDE INTRODUCTION The university WebDrive is a dedicated drive to host all university web content. For help with mapping the WebDrive, please read the instructions below
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems
 Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
Security Tool Kit System Checklist Departmental Servers and Enterprise Systems INSTRUCTIONS System documentation specifically related to security controls of departmental servers and enterprise systems
Cyber Security: Software Security and Hard Drive Encryption
 Links in this document have been set for a desktop computer with the resolution set to 1920 x 1080 pixels. Cyber Security: Software Security and Hard Drive Encryption 301-1497, Rev A September 2012 Copyright
Links in this document have been set for a desktop computer with the resolution set to 1920 x 1080 pixels. Cyber Security: Software Security and Hard Drive Encryption 301-1497, Rev A September 2012 Copyright
SUBJECT: Effective Date Policy Number Security of Mobile Computing, Data Storage, and Communication Devices
 SUBJECT: Effective Date Policy Number Security of Mobile Computing, Data Storage, and Communication Devices 8-27-2015 4-007.1 Supersedes 4-007 Page Of 1 5 Responsible Authority Vice Provost for Information
SUBJECT: Effective Date Policy Number Security of Mobile Computing, Data Storage, and Communication Devices 8-27-2015 4-007.1 Supersedes 4-007 Page Of 1 5 Responsible Authority Vice Provost for Information
E-Mail: SupportCenter@uhcl.edu Phone: 281-283-2828 Fax: 281-283-2969 Box: 230 http://www.uhcl.edu/uct
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
INFORMATION SECURITY BASICS. A computer security tutorial for Holyoke Community College
 INFORMATION SECURITY BASICS A computer security tutorial for Holyoke Community College I NTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
INFORMATION SECURITY BASICS A computer security tutorial for Holyoke Community College I NTRODUCTION This tutorial provides some basic information and practical suggestions for protecting your personal
Each ievo reader needs its own network cable, as each reader has its own IP address. Ensure this has been taken into consideration
 WELCOME ievo would like to thank you for purchasing our product. ievo advise the use of a. Ensure you have calculated the correct power supply amp rating if you are connecting the ievo board and other
WELCOME ievo would like to thank you for purchasing our product. ievo advise the use of a. Ensure you have calculated the correct power supply amp rating if you are connecting the ievo board and other
Adobe Reader 7.0 Frequently Asked Questions for Digital Edition Users
 FAQ Adobe Reader 7.0 TOPICS 1 General 4 Adobe DRM 4 digital edition support 4 Activation 5 Mac OS support 6 PDA support General Q: What is a digital edition (formerly known as an ebook)? A: A digital edition
FAQ Adobe Reader 7.0 TOPICS 1 General 4 Adobe DRM 4 digital edition support 4 Activation 5 Mac OS support 6 PDA support General Q: What is a digital edition (formerly known as an ebook)? A: A digital edition
ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS
 $ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
$ ONLINE BANKING SECURITY TIPS FOR OUR BUSINESS CLIENTS Boston Private Bank & Trust Company takes great care to safeguard the security of your Online Banking transactions. In addition to our robust security
How To Install A Cisco Vpn Client V4.9.9 On A Mac Or Ipad (For A University)
 Cisco VPN Client v4.9.x for Mac OS X 10.4-10.5.x: Installation and Usage Guide Revised July 2009 by UTHSCSA IMS Departments of Client Support Services and Systems & Network Operations INTRODUCTION If you
Cisco VPN Client v4.9.x for Mac OS X 10.4-10.5.x: Installation and Usage Guide Revised July 2009 by UTHSCSA IMS Departments of Client Support Services and Systems & Network Operations INTRODUCTION If you
CLEO Remote Access Services CLEO Remote Desktop Access User Guide v1.3
 CLEO ~Remote Access Services Remote Desktop Access User guide CLEO Remote Access Services CLEO Remote Desktop Access User Guide v1.3 August 2007 page 1 of 16 CLEO 2007 CLEO Remote Access Services 3SGD
CLEO ~Remote Access Services Remote Desktop Access User guide CLEO Remote Access Services CLEO Remote Desktop Access User Guide v1.3 August 2007 page 1 of 16 CLEO 2007 CLEO Remote Access Services 3SGD
