Wireless Robust Security Networks: Keeping the Bad Guys Out with i (WPA2)
|
|
|
- Reynold Freeman
- 8 years ago
- Views:
Transcription
1 Wireless Robust Security Networks: Keeping the Bad Guys Out with i (WPA2) SUNY Technology Conference June 21, 2011 Bill Kramp FLCC Network Administrator Copyright 2011 William D. Kramp All Rights Reserved
2 What is a robust security network (RSN)? What is involved in deploying WPA2? What are the support issues with WPA2? Wireless Security Questions
3 Enforce authorized access to network Protect against downgrade attacks Data protection Confidentiality Data integrity Data origin authentication Replay protection Hardjono & Dondeti (2005) RSN (802.11i) Security Goals
4 Basic Wireless Terms Description of EAP and EAP-Methods 802.1x Phases Deploying WPA2 Support issues Best practices for deployment Agenda
5 WEP - Wired Encryption Protocol WPA - WiFi Protected Access WPA2 - WiFi Protected Access 2 TKIP - Temporal Key Integrity Protocol AES - Advanced Encryption Standard CCMP - Counter Mode with Cipher Block Chaining MAC Protocol EAP EAPOL EAP-Methods Terms
6 Remote Authentication Dial In User Service Developed for MODEM pools back in the day. RADIUS
7 Extensible Authentication Protocol (EAP) A Point to Point Protocol (PPP) RFC 2284 added authentication to PPP EAP
8 Must be supported by Radius server 40+ methods available TLS MS-CHAPv2 PEAP LEAP FAST SIM i requires mutual authentication EAP-Methods
9 Developed by IEEE EAP over LAN (EAPOL) Allowed EAP and Radius to be used Point-to-Point communication only Encapsulates EAP packets for x protocol
10 Blocks all inbound and outbound traffic until after authentication is passed Exceptions to rule: Outbound to wireless device: Wake-on-LAN magic packets Inbound from wireless device: EAPOL packet type 4 SNMP notification (Encapsulated ASF Alert) Uses IEEE 802.1D to accomplish this Network aspects of 802.1x
11 RSN Phases
12 Robust Security Network (802.11i) Phases: 1. Discovery 2. Authentication 3. Key Generation and Distribution 4. Protected Data Transfer 5. Connection Termination Authentication and Association
13 AP Beacons AP Probe Responses Beacon and Probe Responses provide: Cipher suites: WEP TKIP CCMP (AES) Authentication mechanisms: 802.1x Phase 1 - Discovery
14 STA (laptop) and AS (Authentication Server) prove identities using EAP. AP blocks network traffic (802.1x) AP forwards traffic between STA and AS Master Session Key (MSK) established MSK key used to generate subsequent keys Phase 2: Authentication
15 Cryptographic keys generated Keys placed on STA and AP Frames exchanged only between AP and STA Phase 3: Key Generation and Distribution
16 Frames with encapsulated traffic between STA and AP Only frame traffic encrypted Traffic forwarded between AP and wired network Wired traffic not encrypted Phase 4: Protected Data Transfer
17 Secure connection torn down 802.1x port blocking enabled Phase 5: Connection Termination
18 RSN Phases of Operation
19 Easiest: itouch, ipad, iphone Moderate effort: Microsoft, especially Vista A lot of people don t update OS Most difficult: Apple Laptops Impossible: Windows 95 laptops Difficulty Deploying WPA2 Enterprise by Platform/OS
20 Deploying WPA2 With Machine Authentication
21 Wireless device must have been joined to the Windows domain over physical network first. Keys for Radius certificates installed on wireless devices. Configuring WPA2 Step 1
22 SSID has been added. Select Connect automatically when network is in range. Click the Security tab Configuring WPA2 Step 2
23 Set security type to WPA2-Enterprise Set encryption type to AES Select network authentication based on your authentication server Click Settings button Remember my credentials is dependent on policies. Configuring WPA2 Step 3
24 Select Validate server certificate Connect to these servers should be checked, and the radius servers listed. Select only the Trusted Root Cert Authorities needed. Select Do not prompt user to authorize new servers. Select inner Auth Method Click Configure button Configuring WPA2 Step 4
25 Select to use the Windows domain credentials. Click OK Then click OK for the Protected EAP Properties window. Configuring WPA2 Step 5
26 Click the Advanced settings button Configuring WPA2 Step 6
27 Select Specify authentication mode Select proper mode Click OK buttons Configuring WPA2 Step 7
28 Device should first join to the domain with Machine credentials, then use the Windows domain credentials to authenticate. WPA2 Machine Authentication
29 Possible causes: No DHCP address: Out of leases DHCP forwarding failure User exceeded failed logins attempts Radius Failure: Server spacing out Bad radius shared key AD problem Machine Auth password expired Curse of Domain Not Found With WPA2 Machine Authentication
30 Update Operating System Latest wireless drivers: Windows, Linux, OS X Use Windows to manage wireless adapter Place wireless network at top of stack Use good passwords Notify users about change in advance Make people available to help convert Best Practices Deploying WPA2 Enterprise
31 Vulnerability found on the last line of page 196 for the IEEE (2007) Standard AES not compromised Wireless device has to be authenticated Uses shared Group Temporal Key (GTK) GTK intended for use by AP only ARP spoofing for MITM could occur WPA2 Hole 196 Vulnerability
32 Removing IT Staff cred s from user laptops 1. Click Start, and then click Run. 2. In the Open box, type regedit, and then click OK. 3. Locate and then click the following registry key: HKEY_CURRENT_USER\Software\Mi crosoft\eapol\usereapinfo 4. On the Edit menu, click Delete. Clearing Cached Credentials
33 Beaver, K., Davis, P.T., (2005). Hacking Wireless Networks for Dummies. Wiley Publishing, Inc.: Hoboken, NJ. Hardjono, T., Dondeti, L.R. (2005). Security in Wireless LANs and MANs. Artech House, Inc: Norwood, MA. Resources
How to connect to the diamonds wireless network with Vista.
 How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
How to Access Coast Wi-Fi
 How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
How to Access Coast Wi-Fi Below is a summary of the information required to configure your device to connect to the coast-wifi network. For further assistance in configuring your specific device, continue
Eduroam wireless network Windows Vista
 Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Eduroam wireless network Windows Vista university for the creative arts How to configure laptop computers to connect to the eduroam wireless network Contents Contents Introduction Prerequisites Instructions
Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530
 SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
SJSU Premier Wi-Fi Service Network Services One Washington Square, San Jose, CA 95192-0209 408-924-1530 The SJSU Premier Wi-Fi service transmits your data across a secure, encrypted connection. This ensures
User Guide for eduroam
 User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
User Guide for eduroam 獲 以 下 認 證 : Certificado pela: Certified by: 澳 門 望 廈 山 Colina de Mong-Há, Macau 電 話 : (853) 8598 3120 Tel: (853) 8598 3120 傳 真 : (853) 8598 3151 Fax: (853) 8598 3151 www.ift.edu.mo
Wireless Network Configuration Guide
 CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
WIRELESS SETUP FOR WINDOWS 7
 Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
Computing & Communications WIRELESS SETUP FOR WINDOWS 7 For assistance during the configuration process please call the Computing and Communications Help Desk at 639-2049, avdesk@swgc.mun.ca Who should
Table of Contents. Cisco Wi Fi Protected Access 2 (WPA 2) Configuration Example
 Table of Contents Wi Fi Protected Access 2 (WPA 2) Configuration Example...1 Document ID: 67134...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...2 Conventions...2 Background Information...2
Table of Contents Wi Fi Protected Access 2 (WPA 2) Configuration Example...1 Document ID: 67134...1 Introduction...1 Prerequisites...1 Requirements...1 Components Used...2 Conventions...2 Background Information...2
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall:
 How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
How to connect to NAU s WPA2 Enterprise implementation in a Residence Hall: General Settings To connect to the ResNet-Secure SSID, a device is needed that supports 802.1X authentication and WPA2 Enterprise.
Connecting to the Rovernet WPA2 Secured Wireless Network with Windows 7
 Connecting to the Rovernet WPA2 Secured Wireless Network with Windows 7 Configuring your wireless device to use WPA2 takes a few minutes. You will, however, need to meet the following system requirements
Connecting to the Rovernet WPA2 Secured Wireless Network with Windows 7 Configuring your wireless device to use WPA2 takes a few minutes. You will, however, need to meet the following system requirements
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College
 Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
Windows Vista: Connecting to the fastnsecure@hood wireless network at Hood College Please ensure your computer meets the following criteria in order to successfully make a connection to this network: 802.11n
Configuring Eduroam in Windows Vista
 Configuring Eduroam in Windows Vista How to configure Windows Vista wireless settings for use with Eduroam Opening the "Network and Sharing Center" Left Click the network connections icon in the taskbar.
Configuring Eduroam in Windows Vista How to configure Windows Vista wireless settings for use with Eduroam Opening the "Network and Sharing Center" Left Click the network connections icon in the taskbar.
How To Set Up Hopkins Wireless On Windows 7 On A Pc Or Mac Or Ipad (For A Laptop) On A Network Card (For Windows 7) On Your Computer Or Ipa (For Mac Or Mac) On An Ipa Or
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 8, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops
 Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops A wireless network for Faculty and Staff to use with their personal laptops, is available throughout campus with
Windows Vista and Windows 7 Wireless Configuration For NCC Faculty and Staff Owned Laptops A wireless network for Faculty and Staff to use with their personal laptops, is available throughout campus with
CS 356 Lecture 29 Wireless Security. Spring 2013
 CS 356 Lecture 29 Wireless Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter
CS 356 Lecture 29 Wireless Security Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
RSC-Secure-Wireless provides...
 RSC-Secure-Wireless provides... Security: RSC-Secure-Wireless provides a layer of encryption for added security. Convenience: You don't have to type in your username and password each time you connect.
RSC-Secure-Wireless provides... Security: RSC-Secure-Wireless provides a layer of encryption for added security. Convenience: You don't have to type in your username and password each time you connect.
Setting up SJUMobile (Wireless Internet Access for personal devices)
 Setting up SJUMobile (Wireless Internet Access for personal devices) St. John s University provides wireless internet access to personal devices for all current registered students. To setup a connection,
Setting up SJUMobile (Wireless Internet Access for personal devices) St. John s University provides wireless internet access to personal devices for all current registered students. To setup a connection,
vwlan External RADIUS 802.1x Authentication
 6ABSCG0002-29B July 2013 Configuration Guide vwlan External RADIUS 802.1x Authentication This configuration guide provides an in-depth look at external Remote Authentication Dial-In User Service (RADIUS)
6ABSCG0002-29B July 2013 Configuration Guide vwlan External RADIUS 802.1x Authentication This configuration guide provides an in-depth look at external Remote Authentication Dial-In User Service (RADIUS)
6. After connecting reopen the wireless connections window. Right click on RamNet and select properties. Page 2 of 7
 Networking & Telecommunications 001 Allegheny Hall 610-436-3535 West Chester University fax: 610-436-3110 West Chester, Pennsylvania 1938 http://www.wcupa.edu/infoservices/commservices/ RamNet Wireless
Networking & Telecommunications 001 Allegheny Hall 610-436-3535 West Chester University fax: 610-436-3110 West Chester, Pennsylvania 1938 http://www.wcupa.edu/infoservices/commservices/ RamNet Wireless
Eduroam wireless network - Windows 7
 Eduroam wireless network - Windows 7 How to configure laptop computers and tablets to connect to the eduroam wireless network. Contents Introduction 1 Instructions for Windows 7 Devices 2 Technical Information
Eduroam wireless network - Windows 7 How to configure laptop computers and tablets to connect to the eduroam wireless network. Contents Introduction 1 Instructions for Windows 7 Devices 2 Technical Information
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR
 INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows Vista operating systems ΥΠΣ ΕΔ/56 Last review
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows Vista operating systems ΥΠΣ ΕΔ/56 Last review
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
WiFi troubleshooting. How s your WiFi signal? Android WiFi settings. ios WiFi settings
 1 WiFi troubleshooting How s your WiFi signal? If your connection appears to keep dropping off: check in your WiFi settings that you added @kent.ac.uk to your username, and entered your password correctly.
1 WiFi troubleshooting How s your WiFi signal? If your connection appears to keep dropping off: check in your WiFi settings that you added @kent.ac.uk to your username, and entered your password correctly.
White paper. Testing for Wi-Fi Protected Access (WPA) in WLAN Access Points. http://www.veryxtech.com
 White paper Testing for Wi-Fi Protected Access (WPA) in WLAN Access Points http://www.veryxtech.com White Paper Abstract Background The vulnerabilities spotted in the Wired Equivalent Privacy (WEP) algorithm
White paper Testing for Wi-Fi Protected Access (WPA) in WLAN Access Points http://www.veryxtech.com White Paper Abstract Background The vulnerabilities spotted in the Wired Equivalent Privacy (WEP) algorithm
Connec ng to Northwest s WIFI with Windows 7
 Connecting to Northwest s Secure wireless network with your personal computer should be fast and easy if you follow these instructions. To connect your personally-owned computer (with Windows 7 OS) to
Connecting to Northwest s Secure wireless network with your personal computer should be fast and easy if you follow these instructions. To connect your personally-owned computer (with Windows 7 OS) to
Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students.
 Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
Airnet-Student Airnet-Student is a new and improved wireless network that is being made available to all Staffordshire University students. Airnet-Student has two key advantages over the current Airnet
How to Connect to UAB s Wireless Networks
 How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
How to Connect to UAB s Wireless Networks Sections: Page: Checking Windows XP for Service Pack 3 3 Configuring Windows XP SP3 to Connect to uabwifi-nac: Part I 5 Configuring Windows Vista to Connect to
Wireless @ Johns Hopkins
 Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 7 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, Mac OS X, and Linux can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Mac OS X Secure Wireless Setup Guide
 Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
Mac OS X Secure Wireless Setup Guide Requirements: Apple computer with built-in AirPort card capable of WPA2-Enterprise encryption Mac OS X Snow Leopard version 10.6.0 or greater or Mac OS X Lion version
Connecting to the University Wireless Network
 Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Securing Wireless LANs with LDAP
 A P P L I C A T I O N N O T E Securing Wireless LANs with LDAP Many organizations have standardized on LDAP (Lightweight Directory Access Protocol) servers as a repository for their users and related security
A P P L I C A T I O N N O T E Securing Wireless LANs with LDAP Many organizations have standardized on LDAP (Lightweight Directory Access Protocol) servers as a repository for their users and related security
Last Updated: January 23, 2013 1. FLCCsecure
 Last Updated: January 23, 2013 1 FLCCsecure How to Set Up a Secure Wireless Device for Students and Employees Please Note: This packet is a general overview of how to setup the most commonly used personal
Last Updated: January 23, 2013 1 FLCCsecure How to Set Up a Secure Wireless Device for Students and Employees Please Note: This packet is a general overview of how to setup the most commonly used personal
Canterbury College Eduroam Wi-Fi Guide
 Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Canterbury College Eduroam Wi-Fi Guide Version 2.2 (Sept 2014) DG11 Phone: 01227 811144 Email: ITservicedesk@canterburycollege.ac.uk Web: ITservicedesk.cant-col.ac.uk Table of Contents I. Overview... 2
Extension Wireless Access (EWA) v2.0
 Extension Wireless Access (EWA) v2.0 The Extension Wireless Network (EWA) is broken into two parts: the public network (vce pub) and the private network (vce wlan). The public network (vce pub) is secured
Extension Wireless Access (EWA) v2.0 The Extension Wireless Network (EWA) is broken into two parts: the public network (vce pub) and the private network (vce wlan). The public network (vce pub) is secured
Symm ym e m t e r t ic i c cr c yptogr ypt aphy a Ex: RC4, AES 2
 Wi-Fi Security FEUP>MIEIC>Mobile Communications Jaime Dias Symmetric cryptography Ex: RC4, AES 2 Digest (hash) Cryptography Input: variable length message Output: a fixed-length bit
Wi-Fi Security FEUP>MIEIC>Mobile Communications Jaime Dias Symmetric cryptography Ex: RC4, AES 2 Digest (hash) Cryptography Input: variable length message Output: a fixed-length bit
Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops
 Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops A wireless network for Students to use with their personal laptops, is available throughout campus with the SSID NCC-STUDENT. This network
Windows 8 & RT Wireless Configuration For NCC Student Owned Laptops A wireless network for Students to use with their personal laptops, is available throughout campus with the SSID NCC-STUDENT. This network
Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18
 Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Contents Automatic Setup... 1 Manual Setup... 2 Installing the Wireless Certificates... 18 Automatic Setup 1. Click on the Wireless icon in your system tray that looks like. 2. You will see a list of available
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP with Service Pack 2 Your wireless card must support 802.1x, AES, and WPA2. Windows XP with service pack 2, it is recommended
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP with Service Pack 2 Your wireless card must support 802.1x, AES, and WPA2. Windows XP with service pack 2, it is recommended
Setting up Windows XP for WPA Wireless Access (ISU-OIT-WPA)
 Preface: The ISU-OIT-WPA implementation supports either WPA with TKIP or WPA2 with AES. Both support the enterprise DOT1X & CCKM Authentication Key Management features as well. This document is designed
Preface: The ISU-OIT-WPA implementation supports either WPA with TKIP or WPA2 with AES. Both support the enterprise DOT1X & CCKM Authentication Key Management features as well. This document is designed
Configure WorkGroup Bridge on the WAP131 Access Point
 Article ID: 5036 Configure WorkGroup Bridge on the WAP131 Access Point Objective The Workgroup Bridge feature enables the Wireless Access Point (WAP) to bridge traffic between a remote client and the wireless
Article ID: 5036 Configure WorkGroup Bridge on the WAP131 Access Point Objective The Workgroup Bridge feature enables the Wireless Access Point (WAP) to bridge traffic between a remote client and the wireless
Connecting to Secure Wireless (iitk-sec) on Fedora
 Connecting to Secure Wireless (iitk-sec) on Fedora Go to System Preferences Network Connections. Click on Wireless tab and then Add button. Check Connect automatically and Available to all users. Set SSID
Connecting to Secure Wireless (iitk-sec) on Fedora Go to System Preferences Network Connections. Click on Wireless tab and then Add button. Check Connect automatically and Available to all users. Set SSID
Wireless LAN Client Configuration Guide for Windows 7 2015. Configuring 802.1X Authentication Client for Windows 7
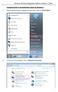 Configuring 802.1X Authentication Client for Windows 7 1. Click on Windows button to display the main menu. Click on Control Panel. 1.1 In the Control Panel window, click on Network and Internet. 1 1.2
Configuring 802.1X Authentication Client for Windows 7 1. Click on Windows button to display the main menu. Click on Control Panel. 1.1 In the Control Panel window, click on Network and Internet. 1 1.2
Internet access system through the Wireless Network of the University of Bologna (last update 6.3.2012)
 Internet access system through the Wireless Network of the University of Bologna (last update 6.3.2012) Printable service summary document: the updated version is available online at the following address
Internet access system through the Wireless Network of the University of Bologna (last update 6.3.2012) Printable service summary document: the updated version is available online at the following address
Wireless security. Any station within range of the RF receives data Two security mechanism
 802.11 Security Wireless security Any station within range of the RF receives data Two security mechanism A means to decide who or what can use a WLAN authentication A means to provide privacy for the
802.11 Security Wireless security Any station within range of the RF receives data Two security mechanism A means to decide who or what can use a WLAN authentication A means to provide privacy for the
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows 7
 Seamless and Secure Access (SSA) Manual Configuration Guide for Windows 7 Page 1 1 Enable Wi-Fi a) Please refer to your computer s user manual to enable the Wireless (Wi-Fi) connection. b) Please click
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows 7 Page 1 1 Enable Wi-Fi a) Please refer to your computer s user manual to enable the Wireless (Wi-Fi) connection. b) Please click
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 6. Wireless Network Security
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 6 Wireless Network Security Objectives Overview of IEEE 802.11 wireless security Define vulnerabilities of Open System Authentication,
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 6 Wireless Network Security Objectives Overview of IEEE 802.11 wireless security Define vulnerabilities of Open System Authentication,
CruzNet Secure Set-Up Instructions for Windows Vista
 CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
CruzNet Secure Set-Up Instructions for Windows Vista 1. In order to start using CruzNet Secure, you'll first need to create a password at https://vpn.soe.ucsc.edu/. Click on the reset your password link.
Huawei WLAN Authentication and Encryption
 Huawei WLAN Authentication and Encryption The Huawei integrated Wireless Local Area Network (WLAN) solution can provide all-round services for municipalities at various levels and enterprises and institutions
Huawei WLAN Authentication and Encryption The Huawei integrated Wireless Local Area Network (WLAN) solution can provide all-round services for municipalities at various levels and enterprises and institutions
GPC JagTalk Secure Wireless Network. Connection Instructions
 GPC JagTalk Secure Wireless Network Connection Instructions Contents Windows 10... 2 Windows 7... 4 Windows 8 / Surface... 6 Android... 7 BlackBerry... 9 Mac OS X... 10 Apple ios Devices... 12 1 Connecting
GPC JagTalk Secure Wireless Network Connection Instructions Contents Windows 10... 2 Windows 7... 4 Windows 8 / Surface... 6 Android... 7 BlackBerry... 9 Mac OS X... 10 Apple ios Devices... 12 1 Connecting
Wireless Security. New Standards for 802.11 Encryption and Authentication. Ann Geyer 209-754-9130 ageyer@tunitas.com www.tunitas.
 Wireless Security New Standards for 802.11 Encryption and Authentication Ann Geyer 209-754-9130 ageyer@tunitas.com www.tunitas.com National Conference on m-health and EOE Minneapolis, MN Sept 9, 2003 Key
Wireless Security New Standards for 802.11 Encryption and Authentication Ann Geyer 209-754-9130 ageyer@tunitas.com www.tunitas.com National Conference on m-health and EOE Minneapolis, MN Sept 9, 2003 Key
Setting up a WiFi Network (WLAN)
 Setting up a WiFi Network (WLAN) How to set up Wi-Fi on your Huawei E960 InZone Step 1: In the address field on your internet browser, type http://192.168.1.1/ Step 2: Type admin into the Password box
Setting up a WiFi Network (WLAN) How to set up Wi-Fi on your Huawei E960 InZone Step 1: In the address field on your internet browser, type http://192.168.1.1/ Step 2: Type admin into the Password box
State of Kansas. Interim Wireless Local Area Networks Security and Technical Architecture
 State of Kansas Interim Wireless Local Area Networks Security and Technical Architecture October 6, 2005 Prepared for Wireless Policy Committee Prepared by Revision Log DATE Version Change Description
State of Kansas Interim Wireless Local Area Networks Security and Technical Architecture October 6, 2005 Prepared for Wireless Policy Committee Prepared by Revision Log DATE Version Change Description
KU Information Technology provides wireless access for both the KU campus community and for guest users at many points across campus.
 Wireless at KU KU Information Technology provides wireless access for both the KU campus community and for guest users at many points across campus. The Campus IT map provides building locations where
Wireless at KU KU Information Technology provides wireless access for both the KU campus community and for guest users at many points across campus. The Campus IT map provides building locations where
Certified Wireless Security Professional (CWSP) Course Overview
 Certified Wireless Security Professional (CWSP) Course Overview This course will teach students about Legacy Security, encryption ciphers and methods, 802.11 authentication methods, dynamic encryption
Certified Wireless Security Professional (CWSP) Course Overview This course will teach students about Legacy Security, encryption ciphers and methods, 802.11 authentication methods, dynamic encryption
Configuring Windows 7 for eduroam at DkIT
 Configuring Windows 7 for eduroam at DkIT Author: Paul Scollon, Computer Services Date: 18 th July, 2011 Version: 1.0 Note: see http://www.eduroam.ie/userdocs.php for details of other operating systems.
Configuring Windows 7 for eduroam at DkIT Author: Paul Scollon, Computer Services Date: 18 th July, 2011 Version: 1.0 Note: see http://www.eduroam.ie/userdocs.php for details of other operating systems.
Connecting to UNOSECURE using Windows 7
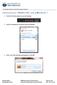 Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
Connecting to UNOSECURE using Windows 7 1. Click the Wireless status icon on the task bar. 2. Select the unosecure connection and click connect. 3. Enter your UNO username and password. Click OK. UCC Help
How To Set Up Isu-Oit-Wpa On Windows 7 For Wireless Access (Isu- Oit- Wpa) On A Pc Or Mac Or Ipa (Windows 7) On An Ipa Or Ipac (Windows
 Preface: The ISU-OIT-WPA implementation supports either WPA with TKIP or WPA2 with AES. Both support the enterprise DOT1X & CCKM Authentication Key Management features as well. This document is designed
Preface: The ISU-OIT-WPA implementation supports either WPA with TKIP or WPA2 with AES. Both support the enterprise DOT1X & CCKM Authentication Key Management features as well. This document is designed
Massey University Wireless Network Client Configuration Windows 7
 Massey University Wireless Network Client Configuration Windows 7 Windows 7 wireless network Requirements You must have an active Massey network account, i.e. you should already be able to log onto the
Massey University Wireless Network Client Configuration Windows 7 Windows 7 wireless network Requirements You must have an active Massey network account, i.e. you should already be able to log onto the
Belnet Networking Conference 2013
 Belnet Networking Conference 2013 Thursday 12 December 2013 @ http://events.belnet.be Workshop roaming services: eduroam / govroam Belnet Aris Adamantiadis, Nicolas Loriau Bruxelles 05 December 2013 Agenda
Belnet Networking Conference 2013 Thursday 12 December 2013 @ http://events.belnet.be Workshop roaming services: eduroam / govroam Belnet Aris Adamantiadis, Nicolas Loriau Bruxelles 05 December 2013 Agenda
How To Secure Wireless Networks
 Lecture 24 Wireless Network Security modified from slides of Lawrie Brown Wireless Security Overview concerns for wireless security are similar to those found in a wired environment security requirements
Lecture 24 Wireless Network Security modified from slides of Lawrie Brown Wireless Security Overview concerns for wireless security are similar to those found in a wired environment security requirements
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device
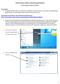 Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Case Study - Configuration between NXC2500 and LDAP Server
 Case Study - Configuration between NXC2500 and LDAP Server 1 1. Scenario:... 3 2. Topology:... 4 3. Step-by-step Configurations:...4 a. Configure NXC2500:...4 b. Configure LDAP setting on NXC2500:...10
Case Study - Configuration between NXC2500 and LDAP Server 1 1. Scenario:... 3 2. Topology:... 4 3. Step-by-step Configurations:...4 a. Configure NXC2500:...4 b. Configure LDAP setting on NXC2500:...10
Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet)
 Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet) What is WPA (Wi-Fi Protected Access)? WPA is a powerful, standards-based, interoperable security technology
Using WPA Enterprise on Windows XP to Access Cleveland State University s Wireless Network (WoWnet) What is WPA (Wi-Fi Protected Access)? WPA is a powerful, standards-based, interoperable security technology
ICT DEPARTMENT. Windows 7. Wireless Authentication Procedures for Windows 7 & 8 Users For Linux and windows XP users visit ICT office
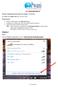 ICT DEPARTMENT Wireless Authentication Procedures for Windows 7 & 8 Users For Linux and windows XP users visit ICT office Requirements: 1. Wireless enable laptop with Valid Anti-Virus 2. Configure your
ICT DEPARTMENT Wireless Authentication Procedures for Windows 7 & 8 Users For Linux and windows XP users visit ICT office Requirements: 1. Wireless enable laptop with Valid Anti-Virus 2. Configure your
The following chart provides the breakdown of exam as to the weight of each section of the exam.
 Introduction The CWSP-205 exam, covering the 2015 objectives, will certify that the successful candidate understands the security weaknesses inherent in WLANs, the solutions available to address those
Introduction The CWSP-205 exam, covering the 2015 objectives, will certify that the successful candidate understands the security weaknesses inherent in WLANs, the solutions available to address those
Developing Network Security Strategies
 NETE-4635 Computer Network Analysis and Design Developing Network Security Strategies NETE4635 - Computer Network Analysis and Design Slide 1 Network Security Design The 12 Step Program 1. Identify network
NETE-4635 Computer Network Analysis and Design Developing Network Security Strategies NETE4635 - Computer Network Analysis and Design Slide 1 Network Security Design The 12 Step Program 1. Identify network
Configuring WPA-Enterprise/WPA2 with Microsoft RADIUS Authentication
 Configuring WPA-Enterprise/WPA2 with Microsoft RADIUS Authentication This document describes how to configure WPA-Enterprise and WPA2 security protocols with RADIUS authentication for Check Point Embedded
Configuring WPA-Enterprise/WPA2 with Microsoft RADIUS Authentication This document describes how to configure WPA-Enterprise and WPA2 security protocols with RADIUS authentication for Check Point Embedded
Instructions for connecting to winthropsecure. Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Apple Quick Connect Apple Settings Check Windows 7 Windows 8 Quick Connect 1. Select the Wi-Fi
chap18.wireless Network Security
 SeoulTech UCS Lab 2015-1 st chap18.wireless Network Security JeongKyu Lee Email: jungkyu21@seoultech.ac.kr Table of Contents 18.1 Wireless Security 18.2 Mobile Device Security 18.3 IEEE 802.11 Wireless
SeoulTech UCS Lab 2015-1 st chap18.wireless Network Security JeongKyu Lee Email: jungkyu21@seoultech.ac.kr Table of Contents 18.1 Wireless Security 18.2 Mobile Device Security 18.3 IEEE 802.11 Wireless
Lecture 3. WPA and 802.11i
 Lecture 3 WPA and 802.11i Lecture 3 WPA and 802.11i 1. Basic principles of 802.11i and WPA 2. IEEE 802.1X 3. Extensible Authentication Protocol 4. RADIUS 5. Efficient Handover Authentication 1 Lecture
Lecture 3 WPA and 802.11i Lecture 3 WPA and 802.11i 1. Basic principles of 802.11i and WPA 2. IEEE 802.1X 3. Extensible Authentication Protocol 4. RADIUS 5. Efficient Handover Authentication 1 Lecture
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7
 WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
WORKING WITH WINDOWS FIREWALL IN WINDOWS 7 Firewall in Windows 7 Windows 7 comes with two firewalls that work together. One is the Windows Firewall, and the other is Windows Firewall with Advanced Security
Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services a...
 1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
1 di 9 31/05/2011 14.48 Search This Site All UCSD Sites Blink Home > Technology > Network Services > Connections > Wireless > Windows 7 Configuring Windows 7 to Use Encrypted (WPA-E) Wireless Services
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Eduroam wireless network Apple Mac OSX 10.5
 Eduroam wireless network Apple Mac OSX 0. How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
Eduroam wireless network Apple Mac OSX 0. How to configure laptop computers to connect to the eduroam wireless network Contents university for the creative arts Contents Introduction Prerequisites Instructions
The Importance of Wireless Security
 The Importance of Wireless Security Because of the increasing popularity of wireless networks, there is an increasing need for security. This is because unlike wired networks, wireless networks can be
The Importance of Wireless Security Because of the increasing popularity of wireless networks, there is an increasing need for security. This is because unlike wired networks, wireless networks can be
How To Secure Your Network With 802.1X (Ipo) On A Pc Or Mac Or Macbook Or Ipo On A Microsoft Mac Or Ipow On A Network With A Password Protected By A Keyed Key (Ipow)
 Wireless LAN Security with 802.1x, EAP-TLS, and PEAP Steve Riley Senior Consultant MCS Trustworthy Computing Services So what s the problem? WEP is a euphemism Wired Equivalent Privacy Actually, it s a
Wireless LAN Security with 802.1x, EAP-TLS, and PEAP Steve Riley Senior Consultant MCS Trustworthy Computing Services So what s the problem? WEP is a euphemism Wired Equivalent Privacy Actually, it s a
ALL1682511. 500Mbits Powerline WLAN N Access Point. User s Manual
 ALL1682511 500Mbits Powerline WLAN N Access Point User s Manual Contents 1. Introduction...1 2. System Requirements...1 3. Configuration...1 4. WPS...9 5. Wireless AP Settings...9 6. FAQ... 15 7. Glossary...
ALL1682511 500Mbits Powerline WLAN N Access Point User s Manual Contents 1. Introduction...1 2. System Requirements...1 3. Configuration...1 4. WPS...9 5. Wireless AP Settings...9 6. FAQ... 15 7. Glossary...
12/3/08. Security in Wireless LANs and Mobile Networks. Wireless Magnifies Exposure Vulnerability. Mobility Makes it Difficult to Establish Trust
 Security in Wireless LANs and Mobile Networks Wireless Magnifies Exposure Vulnerability Information going across the wireless link is exposed to anyone within radio range RF may extend beyond a room or
Security in Wireless LANs and Mobile Networks Wireless Magnifies Exposure Vulnerability Information going across the wireless link is exposed to anyone within radio range RF may extend beyond a room or
CS549: Cryptography and Network Security
 CS549: Cryptography and Network Security by Xiang-Yang Li Department of Computer Science, IIT Cryptography and Network Security 1 Notice This lecture note (Cryptography and Network Security) is prepared
CS549: Cryptography and Network Security by Xiang-Yang Li Department of Computer Science, IIT Cryptography and Network Security 1 Notice This lecture note (Cryptography and Network Security) is prepared
Understanding Wireless Security on Your Polycom SpectraLink 8400 Series Wireless Phones
 Understanding Wireless Security on Your Polycom SpectraLink 8400 Series Wireless Phones Polycom s SpectraLink 8400 Series wireless phones meet the highest security requirements. By the time you deploy
Understanding Wireless Security on Your Polycom SpectraLink 8400 Series Wireless Phones Polycom s SpectraLink 8400 Series wireless phones meet the highest security requirements. By the time you deploy
Wireless computer access at K-State
 Wireless computer access at K-State Information Technology Services provides wireless access across campus for both the K-State community and for campus visitors. Instructions for connecting to KSU Wireless
Wireless computer access at K-State Information Technology Services provides wireless access across campus for both the K-State community and for campus visitors. Instructions for connecting to KSU Wireless
Defiance College Networking Handbook
 Defiance College Networking Handbook Installation Instructions and Reference Manual for Campus Network Connections including Residence Halls and Wireless Access Points Revision 20141203 Preface All residence
Defiance College Networking Handbook Installation Instructions and Reference Manual for Campus Network Connections including Residence Halls and Wireless Access Points Revision 20141203 Preface All residence
WIRELESS SECURITY. Information Security in Systems & Networks Public Development Program. Sanjay Goel University at Albany, SUNY Fall 2006
 WIRELESS SECURITY Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Wireless LAN Security Learning Objectives Students should be able
WIRELESS SECURITY Information Security in Systems & Networks Public Development Program Sanjay Goel University at Albany, SUNY Fall 2006 1 Wireless LAN Security Learning Objectives Students should be able
WiFi Internet Access. Windows XP Setup Instructions. Please Return After Use. Produced Oct 2010
 WiFi Internet Access Windows XP Setup Instructions Produced Oct 2010 Please Return After Use About the Janet Roaming Service The University of Plymouth provides an infrastructure for guest users to use
WiFi Internet Access Windows XP Setup Instructions Produced Oct 2010 Please Return After Use About the Janet Roaming Service The University of Plymouth provides an infrastructure for guest users to use
RWL Tech Note Wireless 802.1x Authentication with Windows NPS
 Wireless 802.1x Authentication with Windows NPS Prepared by Richard Litchfield HP Networking Solution Architect Hewlett-Packard Australia Limited 410 Concord Road Rhodes NSW 2138 AUSTRALIA Date Prepared:
Wireless 802.1x Authentication with Windows NPS Prepared by Richard Litchfield HP Networking Solution Architect Hewlett-Packard Australia Limited 410 Concord Road Rhodes NSW 2138 AUSTRALIA Date Prepared:
Security Technical. Overview. BlackBerry Enterprise Service 10. BlackBerry Device Service Solution Version: 10.2
 BlackBerry Enterprise Service 10 BlackBerry Device Service Solution Version: 10.2 Security Technical Overview Published: 2014-09-10 SWD-20140908123239883 Contents 1 About BlackBerry Device Service solution
BlackBerry Enterprise Service 10 BlackBerry Device Service Solution Version: 10.2 Security Technical Overview Published: 2014-09-10 SWD-20140908123239883 Contents 1 About BlackBerry Device Service solution
How To Set Up Wireless Network Security Part 1: WEP Part 2: WPA-PSK Part 3-1: RADIUS Server Installation Part 3-2: 802.1x-TLS Part 3-3: WPA
 How To Set Up Wireless Network Security Part 1: WEP Part 2: WPA-PSK Part 3-1: RADIUS Server Installation Part 3-2: 802.1x-TLS Part 3-3: WPA You can secure your wireless connection using one of the methods
How To Set Up Wireless Network Security Part 1: WEP Part 2: WPA-PSK Part 3-1: RADIUS Server Installation Part 3-2: 802.1x-TLS Part 3-3: WPA You can secure your wireless connection using one of the methods
A Division of Cisco Systems, Inc. GHz 2.4 802.11g. Wireless-G. USB Network Adapter with RangeBooster. User Guide WIRELESS WUSB54GR. Model No.
 A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G USB Network Adapter with RangeBooster User Guide Model No. WUSB54GR Copyright and Trademarks Specifications are subject to change without
A Division of Cisco Systems, Inc. GHz 2.4 802.11g WIRELESS Wireless-G USB Network Adapter with RangeBooster User Guide Model No. WUSB54GR Copyright and Trademarks Specifications are subject to change without
Lab 8.4.5.1 Configuring LEAP/EAP using Local RADIUS Authentication
 Lab 8.4.5.1 Configuring LEAP/EAP using Local RADIUS Authentication Objective Topology Estimated Time: 40 minutes Number of Team Members: Students can work in teams of two. In this lab, the student will
Lab 8.4.5.1 Configuring LEAP/EAP using Local RADIUS Authentication Objective Topology Estimated Time: 40 minutes Number of Team Members: Students can work in teams of two. In this lab, the student will
802.11 Security (WEP, WPA\WPA2) 19/05/2009. Giulio Rossetti Unipi Giulio.Rossetti@gmail.com
 802.11 Security (WEP, WPA\WPA2) 19/05/2009 Giulio Rossetti Unipi Giulio.Rossetti@gmail.com 802.11 Security Standard: WEP Wired Equivalent Privacy The packets are encrypted, before sent, with a Secret Key
802.11 Security (WEP, WPA\WPA2) 19/05/2009 Giulio Rossetti Unipi Giulio.Rossetti@gmail.com 802.11 Security Standard: WEP Wired Equivalent Privacy The packets are encrypted, before sent, with a Secret Key
JK0 015 CompTIA E2C Security+ (2008 Edition) Exam
 JK0 015 CompTIA E2C Security+ (2008 Edition) Exam Version 4.1 QUESTION NO: 1 Which of the following devices would be used to gain access to a secure network without affecting network connectivity? A. Router
JK0 015 CompTIA E2C Security+ (2008 Edition) Exam Version 4.1 QUESTION NO: 1 Which of the following devices would be used to gain access to a secure network without affecting network connectivity? A. Router
Manual Configuration Instructions
 NOTE: The manual configuration instruction below are in the process of being revised to reflect the network name change to eduroam. All configuration settings for the TSCeduroam requires a username in
NOTE: The manual configuration instruction below are in the process of being revised to reflect the network name change to eduroam. All configuration settings for the TSCeduroam requires a username in
WIRELESS NETWORK SECURITY
 WIRELESS NETWORK SECURITY Much attention has been focused recently on the security aspects of existing Wi-Fi (IEEE 802.11) wireless LAN systems. The rapid growth and deployment of these systems into a
WIRELESS NETWORK SECURITY Much attention has been focused recently on the security aspects of existing Wi-Fi (IEEE 802.11) wireless LAN systems. The rapid growth and deployment of these systems into a
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows Vista
 Seamless and Secure Access (SSA) Manual Configuration Guide for Windows Vista Page 1 1 Enable Wi-Fi a) Please refer to your computer s user manual to enable the Wireless (Wi-Fi) connection. b) Please click
Seamless and Secure Access (SSA) Manual Configuration Guide for Windows Vista Page 1 1 Enable Wi-Fi a) Please refer to your computer s user manual to enable the Wireless (Wi-Fi) connection. b) Please click
Chapter 2 Wireless Networking Basics
 Chapter 2 Wireless Networking Basics Wireless Networking Overview Some NETGEAR products conform to the Institute of Electrical and Electronics Engineers (IEEE) 802.11g standard for wireless LANs (WLANs).
Chapter 2 Wireless Networking Basics Wireless Networking Overview Some NETGEAR products conform to the Institute of Electrical and Electronics Engineers (IEEE) 802.11g standard for wireless LANs (WLANs).
Configuring Eduroam on Microsoft Windows Vista and 7 (all editions, 32 and 64 bits)
 Configuring Eduroam on Microsoft Windows Vista and 7 (all editions, 32 and 64 bits) This documents explain to you how to configure the Eduroam Wireless Access (EWA) correctly on Microsoft Windows Vista
Configuring Eduroam on Microsoft Windows Vista and 7 (all editions, 32 and 64 bits) This documents explain to you how to configure the Eduroam Wireless Access (EWA) correctly on Microsoft Windows Vista
MC3WAVES Wireless Connection Wizard
 MC3WAVES Wireless Connection Wizard When viewing available wireless networks on either MCCC campus you will see a network named public. Connection to public is open to all. Upon connecting to the network
MC3WAVES Wireless Connection Wizard When viewing available wireless networks on either MCCC campus you will see a network named public. Connection to public is open to all. Upon connecting to the network
CS 336/536 Computer Network Security. Summer Term 2010. Wi-Fi Protected Access (WPA) compiled by Anthony Barnard
 CS 336/536 Computer Network Security Summer Term 2010 Wi-Fi Protected Access (WPA) compiled by Anthony Barnard 2 Wi-Fi Protected Access (WPA) These notes, intended to follow the previous handout IEEE802.11
CS 336/536 Computer Network Security Summer Term 2010 Wi-Fi Protected Access (WPA) compiled by Anthony Barnard 2 Wi-Fi Protected Access (WPA) These notes, intended to follow the previous handout IEEE802.11
Instructions for connecting to the LSC-O Secure Wireless Network
 Instructions for connecting to the LSC-O Secure Wireless Network Wireless computer hot spots are available at various locations around the LSC-O campus. The Academic Center first floor, AHB first and second
Instructions for connecting to the LSC-O Secure Wireless Network Wireless computer hot spots are available at various locations around the LSC-O campus. The Academic Center first floor, AHB first and second
