Registration for My Profile & Administration
|
|
|
- Juniper Hill
- 9 years ago
- Views:
Transcription
1 Registration for My Profile & Administration
2
3 Table Of Contents User Registration... 1 Registering as a New User... 1 About the IDcipherTM Card... 7 How Do I Get An IDcipher TM Card?... 8 Two-Factor Authentication... 9 New Division Registration Registering as a New Division New Top-Level Organization Registering as a New Top Level Organization iii
4 User Registration Registering as a New User Complete the following steps to register for a user ID and Password, when you have received an invitation to do so. 1. Click on the link in the invitation you received to launch the registration wizard. The Enter User Information screen is displayed. 2. Key in all fields as required. Be sure that: o o the mobile number you listed is enabled to receive SMS text messages if your organization allows text messages as second-factor authorization for log in, if your organization requires this type. you are able to access the address you listed. All password resets, confirmations, etc are sent directly to this Click Continue Registration. The User Sign On Information screen is displayed. 1
5 Printed_Documentation_Registration click Show Password Rules and review before attempting to create a password. the challenge question you select will be used later to confirm your identity should you need to reset your password, retrieve your user ID, call the Help Desk, etc. when you provide the answer in the challenge answer field, note that this is a case-sensitive field. Later, when you are prompted with the challenge question, you must be able to give the challenge answer exactly as you have provided it in this field (case and space sensitive). 4. Key in all fields as required, then click Continue Registration. 5. If the Select Service Package screen is displayed, enable the checkbox of each application you wish request then click continue. If it is not displayed, proceed to the next step. 6. If the Configure Two Factor Authorization screen is displayed, continue to step 7. If it is not, proceed to step 8. 2
6 User Registration 7. Select one of the following (not all options are available to all customers): If You Wish To: receive an SMS (text message) as the second factor required during log in Then... a. Enable the SMS radio button b. Select the country in which your cell phone is registered. c. Enable the radio button next to Mobile Phone Number field. d. Key in your mobile number to which you will receive SMS text messages required for log in. e. Click Verify. The passcode is sent via text to your mobile phone number provided, and the Enter Passcode field is displayed. f. Key in the passcode in the Enter Passcode field (retrieved from your mobile phone). g. Click Validate and Continue. The Review Request and Submit screen is displayed. receive a voice recording as the second factor required during log in h. Proceed to step 8. a. Enable the Phone radio button b. Select the country in which your cell phone is registered. c. Enable the radio button next to Phone Number field. d. Key in your number to which you will receive voice recording. e. Click Verify. Your phone will ring, and a voice recording will state your passcode, and the Enter Passcode field is displayed. f. Key in the passcode in the Enter Passcode field (retrieved from voice recording on your phone). g. Click Validate and Continue. The Review Request and Submit screen is displayed. 3
7 Printed_Documentation_Registration If You Wish To: Then... receive a mobile push (AKA Smartphone Push)A mobile push (aka Smartphone push) is the push notification services offered by modern mobile platforms, such as iphone's APNS and Android's C2DM, and can be used to provide a real-time challenge/respons e mechanism on a mobile device. Upon performing a sensitive transaction or login, the user will instantly receive a challenge pushed to their mobile phone, be prompted with the full details of that transaction, and be able to respond to approve or deny that transaction by simply pressing a h. Proceed to step 8. a. Enable the Mobile Push radio button b. Select the country in which your cell phone is registered. c. Key in your number to which you will receive the mobile push. d. Select the phone type from the drop down list. e. Select one of the following, if you selected: o "landline" in step d, click Call Me button. o "mobile" in step d, click Text Me button, or Call Me button, whichever you prefer. The passcode is sent via your selected method, and the Verify Code field is displayed. f. Key in the code in the Verify Code field (retrieved from your phone). g. Click Verify. h. Click continue. i. Optionally, continue with installation, or click skip this step. j. Proceed to step 8. 4
8 User Registration If You Wish To: button on their mobile phone. Smartphone push two-factor has the capability to not only be more user-friendly, but also more secure as a mutually connection can be established to the phone over the data network. as the second factor required during log in Then... receive an as the second factor required during log in a. Enable the radio button b. Key in the address to which you will receive the passcode. c. Click Resend Passcode. The passcode is sent via text to your address, and the Enter Passcode field is displayed. d. Key in the passcode in the Enter Passcode field (retrieved from your ). e. Click Validate and Continue. The Review Request and Submit screen is displayed. f. Proceed to step 8. use the IDCipher card as your second factor during log in a. Enable the IDCipher radio button. b. Click Continue Registration. The Review Request and Submit screen is displayed. 5
9 Printed_Documentation_Registration If You Wish To: Then... c. Proceed to step Key in the reason for your User ID request in the request reason field. 9. Click Submit Registration. Your request has been submitted. If your organization uses IDCipher as the second-factor authorization, your IDCipher Card will sent to the address you provided during registration. RESULTS: You have successfully submitted a registration request as a new user. 6
10 User Registration About the IDcipherTM Card The IDcipher TM Card is a premium service, available for purchase by your organization. The IDcipher TM card provides two-factor (something the user knows and something the user has) which is one form of that may be used when two-factor is required. The card provides a low-cost, easy-to-use, easy-to-deploy mechanism that provides an extra level of assurance when a user is authenticated. Covisint has trademarked the IDcipher Card. (IDcipher TM card is a premium service available for purchase by portal customers. Please contact your Covisint sales representative for details) 7
11 Printed_Documentation_Registration How Do I Get An IDcipher TM Card? The IDcipher TM card is used as a method for that may optionally be used within Portals that require two-factor. The process for obtaining an IDCipher TM Card is dependent upon your user status. Click on the link that best describes you: I am an existing user, I can already log in to the portal, but I need a new IDcipher TM Card >>> I am new to the portal, and not yet a registered user? (You have not yet registered for the portal) >>> When you register for portal access, an IDcipher TM card will automatically be generated and ed to you upon approval of your registration request if the portal you are requesting access to requires the IDcipher TM card for up-level. After submitting a registration request, users need not perform additional action to obtain an IDCipher TM card. (IDcipher TM card is a premium service available for purchase by portal customers. Please contact your Covisint sales representative for details.) 8
12 User Registration Two-Factor Authentication Two-factor is an process that prompts the user for an additional, stronger form of than a user name and password, when a user attempts to gain access to a system resource that requires an additional level of protection. Additionally, the user may be prompted for uplevel based on specified criteria which can be derived from user provided information (e.g. a specific user name), system collected information (e.g. an unknown PC IP Address), as well as transaction patterns (e.g. time of day or how frequently the user signs on). Covisint provides two-factor (something the user knows and something the user has) for your organization by any of the following methods: o IDCipher Card - User is prompted to key in the code on his/her IDCipher Card Grid at time of login. o SMS Text Messages - User is prompted to key in the code that the system sends to his/her mobile phone at time of login. (IDcipher TM card is a premium service available for purchase by portal customers. Please contact your Covisint sales representative for details) 9
13 New Division Registration Registering as a New Division Complete the following steps to register as a new Division of the organization, when you have received an invitation to do so. Before you begin - Registering as a Division (with a top-level parent) implies that your organization wishes to configure a delegated administration model. This option should only be selected based on instruction from members of your company. The New Organization/Division registration process requires that the registrant accept the Security Administrator role. Check with members of your Organization to ensure that you are the appropriate person to assume this role. 1. Click on the link in the invitation you received to launch the registration wizard. 2. Key in all fields as required regarding your Division information, then click Continue Registration. The Enter User Information screen is displayed. 11
14 Printed_Documentation_Registration 3. Key in all fields as required. Be sure that: o o the mobile number you listed is enabled to receive SMS text messages if your organization allows text messages as second-factor authorization for log in, if your organization requires this type. you are able to access the address you listed. All password resets, confirmations, etc are sent directly to this Click Continue Registration. The User Sign On screen is displayed. o o o click Show Password Rules and review before attempting to create a password. the challenge question you select will be used later to confirm your identity should you need to reset your password, retrieve your user ID, call the Help Desk, etc. when you provide the answer in the challenge answer field, note that this is a case-sensitive field. Later, when you are prompted with the challenge question, you must be able to give the challenge answer exactly as you have provided it in this field (case and space sensitive). 5. Key in all fields as required, then click Continue Registration. 6. If the Select Service Package screen is displayed, enable the checkbox of each application you wish to request then click continue. If it is not displayed, proceed to the next step. 7. If the Configure Two Factor Authorization screen is displayed, continue to step 8. If it is not, proceed to step 9. 12
15 New Division Registration 8. Select one of the following (not all options are available to all customers): If You Wish To: receive an SMS (text message) as the second factor required during log in Then... a. Enable the SMS radio button b. Select the country in which your cell phone is registered. c. Enable the radio button next to Mobile Phone Number field. d. Key in your mobile number to which you will receive SMS text messages required for log in. e. Click Verify. The passcode is sent via text to your mobile phone number provided, and the Enter Passcode field is displayed. f. Key in the passcode in the Enter Passcode field (retrieved from your mobile phone). g. Click Validate and Continue. The Review Request and Submit screen is displayed. h. Proceed to step 9. 13
16 Printed_Documentation_Registration If You Wish To: receive a voice recording as the second factor required during log in Then... a. Enable the Phone radio button b. Select the country in which your cell phone is registered. c. Enable the radio button next to Phone Number field. d. Key in your number to which you will receive voice recording. e. Click Verify. Your phone will ring, and a voice recording will state your passcode, and the Enter Passcode field is displayed. f. Key in the passcode in the Enter Passcode field (retrieved from voice recording on your phone). g. Click Validate and Continue. The Review Request and Submit screen is displayed. receive a mobile push (AKA Smartphone Push)A mobile push (aka Smartphone push) is the push notification services offered by modern mobile platforms, such as iphone's APNS and Android's C2DM, and can be used to provide a real-time challenge/response mechanism on a mobile device. Upon performing a sensitive transaction or login, the user will instantly receive a challenge pushed to their mobile phone, be prompted with the h. Proceed to step 9. a. Enable the Mobile Push radio button b. Select the country in which your cell phone is registered. c. Key in your number to which you will receive the mobile push. d. Select the phone type from the drop down list. e. Select one of the following, if you selected: o "landline" in step d, click Call Me button. o "mobile" in step d, click Text Me button, or Call Me button, whichever you prefer. The passcode is sent via your selected method, and the Verify Code field is displayed. f. Key in the code in the Verify Code field (retrieved from your phone). g. Click Verify. h. Click continue. i. Optionally, continue with installation, or click skip this step. j. Proceed to step 9. 14
17 New Division Registration If You Wish To: full details of that transaction, and be able to respond to approve or deny that transaction by simply pressing a button on their mobile phone. Smartphone push two-factor has the capability to not only be more user-friendly, but also more secure as a mutually connection can be established to the phone over the data network. as the second factor required during log in receive an as the second factor required during log in Then... a. Enable the radio button b. Key in the address to which you will receive the passcode. c. Click Resend Passcode. The passcode is sent via text to your address, and the Enter Passcode field is displayed. d. Key in the passcode in the Enter Passcode field (retrieved from your ). e. Click Validate and Continue. The Review Request and Submit screen is displayed. f. Proceed to step 9. 15
18 Printed_Documentation_Registration If You Wish To: use the IDCipher card as your second factor during log in Then... a. Enable the IDCipher radio button. b. Click Continue Registration. The Review Request and Submit screen is displayed. c. Proceed to step Key in the reason for your User ID request in the request reason field. 10. Click Submit Registration. Your request has been submitted. If you chose IDCipher as your second-factor authorization, your IDCipher Card will sent to the address you provided during registration. RESULTS: You have successfully submitted a registration request as a Security Administrator for a new Division. 16
19 New Top-Level Organization Registering as a New Top Level Organization Complete the following steps to register as a new Top-Level Organization when you have received an invitation to do so. Before you begin - Registering as a Top-Level Organization requires that the registrant accept the Security Administrator role. Check with members of your Organization to ensure that you are the appropriate person to assume this role. 1. Click on the link in the invitation you received to launch the registration wizard. The Enter Organization Information screen is displayed. 2. Key in all fields as required regarding your Organization information, then click Continue Registration. The Enter User Information screen is displayed. 3. Key in all fields as required. Be sure that: o o the mobile number you listed is enabled to receive SMS text messages if your organization allows text messages as second-factor authorization for log in, if your organization requires this type. you are able to access the address you listed. All password resets, confirmations, etc are sent directly to this . 17
20 Printed_Documentation_Registration 4. Click Continue Registration. The User Sign On screen is displayed. click Show Password Rules and review before attempting to create a password. in this step, you will either create a challenge question, or select one from a list, depending on your organization's configuration. The question you create/select will be used later to confirm your identity should you need to reset your password, retrieve your user ID, call the Help Desk, etc. when you provide the answer in the challenge answer field, note that this is a case-sensitive field. Later, when you are prompted with the challenge question, you must be able to give the challenge answer exactly as you have provided it in this field (case and space sensitive). 5. Key in all fields as required, then click Continue Registration. 6. If the Select Service Package screen is displayed, enable the checkbox of each application you wish to request then click continue. If it is not displayed, proceed to the next step. 7. If the Configure Two Factor Authorization screen is displayed, continue to step 8. If it is not, proceed to step 9. 18
21 New Top-Level Organization 8. Select one of the following (not all options are available to all customers): If You Wish To: receive an SMS (text message) as the second factor required during log in Then... a. Enable the SMS radio button b. Select the country in which your cell phone is registered. c. Enable the radio button next to Mobile Phone Number field. d. Key in your mobile number to which you will receive SMS text messages required for log in. e. Click Verify. The passcode is sent via text to your mobile phone number provided, and the Enter Passcode field is displayed. f. Key in the passcode in the Enter Passcode field (retrieved from your mobile phone). g. Click Validate and Continue. The Review Request and Submit screen is displayed. receive a voice recording as the second factor required during log in h. Proceed to step 9. a. Enable the Phone radio button b. Select the country in which your cell phone is registered. c. Enable the radio button next to Phone Number field. d. Key in your number to which you will receive voice recording. e. Click Verify. Your phone will ring, and a voice recording will state your passcode, and the Enter Passcode field is displayed. f. Key in the passcode in the Enter Passcode field (retrieved from voice recording on your phone). g. Click Validate and Continue. The Review Request and Submit screen is displayed. 19
22 Printed_Documentation_Registration If You Wish To: Then... receive a mobile push (AKA Smartphone Push)A mobile push (aka Smartphone push) is the push notification services offered by modern mobile platforms, such as iphone's APNS and Android's C2DM, and can be used to provide a real-time challenge/respons e mechanism on a mobile device. Upon performing a sensitive transaction or login, the user will instantly receive a challenge pushed to their mobile phone, be prompted with the full details of that transaction, and be able to respond to approve or deny that transaction by simply pressing a button on their mobile phone. h. Proceed to step 9. a. Enable the Mobile Push radio button b. Select the country in which your cell phone is registered. c. Key in your number to which you will receive the mobile push. d. Select the phone type from the drop down list. e. Select one of the following, if you selected: o "landline" in step d, click Call Me button. o "mobile" in step d, click Text Me button, or Call Me button, whichever you prefer. The passcode is sent via your selected method, and the Verify Code field is displayed. f. Key in the code in the Verify Code field (retrieved from your phone). g. Click Verify. h. Click continue. i. Optionally, continue with installation, or click skip this step. j. Proceed to step 9. 20
23 New Top-Level Organization If You Wish To: Smartphone push two-factor has the capability to not only be more user-friendly, but also more secure as a mutually connection can be established to the phone over the data network. as the second factor required during log in Then... receive an as the second factor required during log in a. Enable the radio button b. Key in the address to which you will receive the passcode. c. Click Resend Passcode. The passcode is sent via text to your address, and the Enter Passcode field is displayed. d. Key in the passcode in the Enter Passcode field (retrieved from your ). e. Click Validate and Continue. The Review Request and Submit screen is displayed. f. Proceed to step 9. use the IDCipher card as your second factor during log in a. Enable the IDCipher radio button. b. Click Continue Registration. The Review Request and Submit screen is displayed. 21
24 Printed_Documentation_Registration If You Wish To: Then... c. Proceed to step Key in the reason for your User ID request in the request reason field. 10. Click Submit Registration. Your request has been submitted. If you chose IDCipher as your second-factor authorization, your IDCipher Card will sent to the address you provided during registration. RESULTS: You have successfully submitted a registration request as a Security Administrator for a new Top-Level Organization. 22
Multi-Factor Authentication Job Aide
 To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
Setting Up and Accessing VPN
 Setting Up and Accessing VPN Instructions for establishing remote access to the URMC network for PC or Mac Duo Two-Factor Authentication If you have already enrolled and setup Duo Two-Factor Authentication
Setting Up and Accessing VPN Instructions for establishing remote access to the URMC network for PC or Mac Duo Two-Factor Authentication If you have already enrolled and setup Duo Two-Factor Authentication
TARGETPROCESS HELP DESK PORTAL
 TARGETPROCESS HELP DESK PORTAL v.2.17 User Guide This document describes TargetProcess Help Desk Portal functionality and provides information about TargetProcess Help Desk Portal usage. 1 HELP DESK PORTAL...2
TARGETPROCESS HELP DESK PORTAL v.2.17 User Guide This document describes TargetProcess Help Desk Portal functionality and provides information about TargetProcess Help Desk Portal usage. 1 HELP DESK PORTAL...2
Defender 5.7 - Token Deployment System Quick Start Guide
 Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Self Service Portal and 2FA User Guide
 Self Service Portal and 2FA User Guide Accessing Symantec Self Service Portal Self Service Portal (SSP) is a web-based application which you can use to register, test, reset, or remove Symantec VIP credentials.
Self Service Portal and 2FA User Guide Accessing Symantec Self Service Portal Self Service Portal (SSP) is a web-based application which you can use to register, test, reset, or remove Symantec VIP credentials.
Knowledge based authentication (KBA)
 Knowledge based authentication (KBA) Overview Knowledge based authentication (KBA) is an advanced identity validation method to authenticate a signer by asking random questions selected from public and
Knowledge based authentication (KBA) Overview Knowledge based authentication (KBA) is an advanced identity validation method to authenticate a signer by asking random questions selected from public and
Provider Express Obtaining Login Access. Information for Network Providers
 Provider Express Obtaining Login Access Information for Network Providers November 2013 Objectives This presentation will review the following features: How to Log in to Provider Express Retrieve a forgotten
Provider Express Obtaining Login Access Information for Network Providers November 2013 Objectives This presentation will review the following features: How to Log in to Provider Express Retrieve a forgotten
Quick Start Guide. TELUS Business Connect
 Quick Start Guide TELUS Business Connect Let s get started This document outlines steps to help guide Administrators and users through account registration and configuration of the new TELUS Business Connect
Quick Start Guide TELUS Business Connect Let s get started This document outlines steps to help guide Administrators and users through account registration and configuration of the new TELUS Business Connect
Mobile Iron User Guide
 2015 Mobile Iron User Guide Information technology Sparrow Health System 9/1/2015 Contents...0 Introduction...2 Changes to your Mobile Device...2 Self Service Portal...3 Registering your new device...4
2015 Mobile Iron User Guide Information technology Sparrow Health System 9/1/2015 Contents...0 Introduction...2 Changes to your Mobile Device...2 Self Service Portal...3 Registering your new device...4
Enhanced Login Security Frequently Asked Questions
 Enhanced Login Security Frequently Asked Questions Below are Frequently Asked Questions to assist you and you can also contact Customer Service at 903-657-8525 or 800-962-1610. Q: What is Enhanced Login
Enhanced Login Security Frequently Asked Questions Below are Frequently Asked Questions to assist you and you can also contact Customer Service at 903-657-8525 or 800-962-1610. Q: What is Enhanced Login
Getting Started. Getting Started with Time Warner Cable Business Class. Voice Manager. A Guide for Administrators and Users
 Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Getting Started Getting Started with Time Warner Cable Business Class Voice Manager A Guide for Administrators and Users Table of Contents Table of Contents... 2 How to Use This Guide... 3 Administrators...
Electronic Questionnaires for Investigations Processing (e-qip)
 January 2016 Electronic Questionnaires for Investigations Processing (e-qip) Login Instructions for first-time users OR users that have had their accounts reset Step 1 Access the e-qip Login screen at
January 2016 Electronic Questionnaires for Investigations Processing (e-qip) Login Instructions for first-time users OR users that have had their accounts reset Step 1 Access the e-qip Login screen at
Advanced Configuration Steps
 Advanced Configuration Steps After you have downloaded a trial, you can perform the following from the Setup menu in the MaaS360 portal: Configure additional services Configure device enrollment settings
Advanced Configuration Steps After you have downloaded a trial, you can perform the following from the Setup menu in the MaaS360 portal: Configure additional services Configure device enrollment settings
Sophos Mobile Control User guide for Android
 Sophos Mobile Control User guide for Android Product version: 2.5 Document date: July 2012 Contents 1 About Sophos Mobile Control... 3 2 Login to the Self Service Portal... 4 3 Set up Sophos Mobile Control
Sophos Mobile Control User guide for Android Product version: 2.5 Document date: July 2012 Contents 1 About Sophos Mobile Control... 3 2 Login to the Self Service Portal... 4 3 Set up Sophos Mobile Control
Cash Management 5.0 User Guide
 Cash Management 5.0 User Guide Accessing Cash Management Online Banking Access Cash Management using www.busey.com as you always have. 1. Enter your company ID as assigned by your financial institution
Cash Management 5.0 User Guide Accessing Cash Management Online Banking Access Cash Management using www.busey.com as you always have. 1. Enter your company ID as assigned by your financial institution
Department of Defense Travel Card Citibank Electronic Access System. APC Setup Guide
 Department of Defense Travel Card Citibank Electronic Access System APC Setup Guide Version 6.0 18 December 2008 Introduction This guide was developed to allow you to effectively use Citi s EAS. You will
Department of Defense Travel Card Citibank Electronic Access System APC Setup Guide Version 6.0 18 December 2008 Introduction This guide was developed to allow you to effectively use Citi s EAS. You will
Using GhostPorts Two-Factor Authentication
 Using GhostPorts Two-Factor Authentication With CloudPassage Halo GhostPorts is a powerful two-factor authentication feature available with the Halo NetSec and Halo Professional subscription plans. GhostPorts
Using GhostPorts Two-Factor Authentication With CloudPassage Halo GhostPorts is a powerful two-factor authentication feature available with the Halo NetSec and Halo Professional subscription plans. GhostPorts
Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are.
 Two Factor Authentication Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are. For example, one method currently utilized within
Two Factor Authentication Two Factor Authentication (TFA; 2FA) is a security process in which two methods of authentication are used to verify who you are. For example, one method currently utilized within
Sophos Mobile Control User guide for Android. Product version: 4
 Sophos Mobile Control User guide for Android Product version: 4 Document date: May 2014 Contents 1 About Sophos Mobile Control...3 2 About this guide...4 3 Login to the Self Service Portal...5 4 Set up
Sophos Mobile Control User guide for Android Product version: 4 Document date: May 2014 Contents 1 About Sophos Mobile Control...3 2 About this guide...4 3 Login to the Self Service Portal...5 4 Set up
Online Statements. About this guide. Important information
 Online Statements About this guide This guide shows you how to: View online statements, including CommBiz Activity Statements (Billing summaries) and online statements for Transaction Accounts, Credit
Online Statements About this guide This guide shows you how to: View online statements, including CommBiz Activity Statements (Billing summaries) and online statements for Transaction Accounts, Credit
Business Banking Customer Login Experience for Enhanced Login Security
 Business Banking Customer Login Experience for Enhanced Login Security User credentials uniquely identify each person who uses the banking platform. The intent of authentication is unequivocal verification
Business Banking Customer Login Experience for Enhanced Login Security User credentials uniquely identify each person who uses the banking platform. The intent of authentication is unequivocal verification
Cloud Services MDM. Control Panel Provisioning Guide
 Cloud Services MDM Control Panel Provisioning Guide 10/24/2014 CONTENTS Overview... 2 Accessing MDM in the Control Panel... 3 Create the MDM Instance in the Control Panel... 3 Adding a New MDM User...
Cloud Services MDM Control Panel Provisioning Guide 10/24/2014 CONTENTS Overview... 2 Accessing MDM in the Control Panel... 3 Create the MDM Instance in the Control Panel... 3 Adding a New MDM User...
Online Tools. CommPortal. Go to http://myphone.bayring.com. User Name: Your 10-digit telephone number (no dashes) Password: Your voice mail password
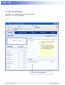 CommPortal Go to http://myphone.bayring.com User Name: Your 10-digit telephone number (no dashes) Password: Your voice mail password Summary Click here to manage forwarding. Messages & Calls You can play
CommPortal Go to http://myphone.bayring.com User Name: Your 10-digit telephone number (no dashes) Password: Your voice mail password Summary Click here to manage forwarding. Messages & Calls You can play
SafeSeaNet Norway User Registration Guide
 SafeSeaNet Norway User Registration Guide Kystverket Vest Flathauggata 12 5525 Haugesund Telephone: +47 07847 Telefax: +47 52 73 32 01 E-post: [email protected] Web: http://www.kystverket.no Table of
SafeSeaNet Norway User Registration Guide Kystverket Vest Flathauggata 12 5525 Haugesund Telephone: +47 07847 Telefax: +47 52 73 32 01 E-post: [email protected] Web: http://www.kystverket.no Table of
Initial DUO 2 Factor Setup, Install, Login and Verification
 Please read this entire document it contains important instructions that will help you with the setup and maintenance of your DUO account. PLEASE NOTE: Use of a smartphone is the fastest and simplest way
Please read this entire document it contains important instructions that will help you with the setup and maintenance of your DUO account. PLEASE NOTE: Use of a smartphone is the fastest and simplest way
AMS Advantage Vendor Self Service. Registration Quick Start Guide Release 3.9
 AMS Advantage Vendor Self Service Registration Quick Start Guide Release 3.9 Copyright 2001, 2011 CGI Technologies and Solutions Inc. All rights reserved. These materials contain the intellectual property
AMS Advantage Vendor Self Service Registration Quick Start Guide Release 3.9 Copyright 2001, 2011 CGI Technologies and Solutions Inc. All rights reserved. These materials contain the intellectual property
Two-Factor Authentication User FAQ s
 Two-Factor Authentication User FAQ s What is Two-Factor Authentication (2FA)? What does Symantec Validation and ID Protection (VIP) do? I don t have a smartphone, what is my alternative? How many devices
Two-Factor Authentication User FAQ s What is Two-Factor Authentication (2FA)? What does Symantec Validation and ID Protection (VIP) do? I don t have a smartphone, what is my alternative? How many devices
DUO SECURITY CISCO VPN USER GUIDE 1/27/2016
 DUO SECURITY CISCO VPN USER GUIDE 1/27/2016 CONTENTS Enrolling Your Devices... 2 Install Cisco AnyConnect VPN Client... 6 Connecting to a PC with Microsoft Remote Desktop... 8 Disconnecting the AnyConnect
DUO SECURITY CISCO VPN USER GUIDE 1/27/2016 CONTENTS Enrolling Your Devices... 2 Install Cisco AnyConnect VPN Client... 6 Connecting to a PC with Microsoft Remote Desktop... 8 Disconnecting the AnyConnect
Allianz Global Investors Remote Access Guide
 Allianz Global Investors Remote Access Guide Web Address: http://remote.allianzgi-us.com/ Page 1 of 34 pages Please contact the Service Desk at Table of Contents 1. Introduction to the Remote Access Page
Allianz Global Investors Remote Access Guide Web Address: http://remote.allianzgi-us.com/ Page 1 of 34 pages Please contact the Service Desk at Table of Contents 1. Introduction to the Remote Access Page
DISCOVER LOCAL TALENT WITH JOBS BANK
 www.jobsbank.gov.sg USER GUIDE FOR EMPLOYERS DISCOVER LOCAL TALENT WITH JOBS BANK The portal that links you to local individuals CONTENTS PREFACE PART I : NAVIGATING THE JOBS BANK MAIN PORTAL A. ACCESS
www.jobsbank.gov.sg USER GUIDE FOR EMPLOYERS DISCOVER LOCAL TALENT WITH JOBS BANK The portal that links you to local individuals CONTENTS PREFACE PART I : NAVIGATING THE JOBS BANK MAIN PORTAL A. ACCESS
TransUnion Direct: Download Digital Certificate Internet Explorer
 TransUnion Direct: Download Digital Certificate Internet Explorer Getting Started What You Need to Know Important: Both the user and the administrator need to be present at the user s PC. The user should
TransUnion Direct: Download Digital Certificate Internet Explorer Getting Started What You Need to Know Important: Both the user and the administrator need to be present at the user s PC. The user should
eaccounts Customer Instruction Manual
 eaccounts Customer Instruction Manual Table of Contents 1.0 eaccounts Homepage... 3 2.0 Login... 4 3.0 Login History... 5 4.0 Download History... 6 5.0 Verify Customer Details... 7 6.0 Verify Operations
eaccounts Customer Instruction Manual Table of Contents 1.0 eaccounts Homepage... 3 2.0 Login... 4 3.0 Login History... 5 4.0 Download History... 6 5.0 Verify Customer Details... 7 6.0 Verify Operations
PaymentNet Federal Card Solutions Cardholder FAQs
 PaymentNet Federal Card Solutions It s easy to find the answers to your questions about PaymentNet! June 2014 Frequently Asked Questions First Time Login How do I obtain my login information?... 2 How
PaymentNet Federal Card Solutions It s easy to find the answers to your questions about PaymentNet! June 2014 Frequently Asked Questions First Time Login How do I obtain my login information?... 2 How
Self-Service Password Manager
 WWW.ROSE-HULMAN.EDU/EIT OFFICE OF ENTERPRISE INFORMATION TECHNOLOGY Self-Service Password Manager Rose-Hulman Institute of Technology has implemented a self-service password manager that provides an easy-to-use
WWW.ROSE-HULMAN.EDU/EIT OFFICE OF ENTERPRISE INFORMATION TECHNOLOGY Self-Service Password Manager Rose-Hulman Institute of Technology has implemented a self-service password manager that provides an easy-to-use
My LMS. Learning Management System Guide for Students
 My LMS Learning Management System Guide for Students Revision Date: October 17, 2014 Table of Contents Learning Management System (LMS) Overview... 2 Accessing My LMS... 2 General Navigation... 5 Your
My LMS Learning Management System Guide for Students Revision Date: October 17, 2014 Table of Contents Learning Management System (LMS) Overview... 2 Accessing My LMS... 2 General Navigation... 5 Your
Single Sign-On Instructions (SSO) Registration for the SSO
 Single Sign-On Instructions (SSO) Registration for the SSO Step 1: Registration to Single Sign-On (SSO) Skip this section if you ve already registered for a SSO account. Open your web browser (Internet
Single Sign-On Instructions (SSO) Registration for the SSO Step 1: Registration to Single Sign-On (SSO) Skip this section if you ve already registered for a SSO account. Open your web browser (Internet
Table of Contents. Lesson 5: Assign Delegate...30 Objectives... 30 Assign A Delegate... 30 Edit Delegate Permissions... 33
 Supervisor Manual Table of Contents Lesson 1: Login... 1 Objectives... 1 Log In to IR University... 1 Retrieve Forgotten Password and/or User ID... 3 Using the IR University Help System... 6 Lesson 2:
Supervisor Manual Table of Contents Lesson 1: Login... 1 Objectives... 1 Log In to IR University... 1 Retrieve Forgotten Password and/or User ID... 3 Using the IR University Help System... 6 Lesson 2:
Signing Documents with Requests for Attachments
 DocuSign Quick Start Signer Guide Signing Documents with Requests for Attachments There may be times when you need to provide supporting documentation to the sender. This guide provides information about
DocuSign Quick Start Signer Guide Signing Documents with Requests for Attachments There may be times when you need to provide supporting documentation to the sender. This guide provides information about
Michigan Care Improvement Registry (MCIR) User Registration Four-Step Process
 Michigan Care Improvement Registry (MCIR) User Registration Four-Step Process Step 1. User Receives PIN Number Email from [email protected] Once a User is added to MCIR, they will receive an email message
Michigan Care Improvement Registry (MCIR) User Registration Four-Step Process Step 1. User Receives PIN Number Email from [email protected] Once a User is added to MCIR, they will receive an email message
Sophos Mobile Control as a Service Startup guide. Product version: 3.5
 Sophos Mobile Control as a Service Startup guide Product version: 3.5 Document date: August 2013 Contents 1 About this guide...3 2 What are the key steps?...4 3 First login...5 4 Change your administrator
Sophos Mobile Control as a Service Startup guide Product version: 3.5 Document date: August 2013 Contents 1 About this guide...3 2 What are the key steps?...4 3 First login...5 4 Change your administrator
Self-Service Portal Registering, downloading & activating a soft token
 Self-Service Portal Registering, downloading & activating a soft token Document issue: 3.2 Date of issue: September 2014 Contents Introduction... 3 About two-factor authentication... 3 About egrid authentication...
Self-Service Portal Registering, downloading & activating a soft token Document issue: 3.2 Date of issue: September 2014 Contents Introduction... 3 About two-factor authentication... 3 About egrid authentication...
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication. Mobile App Activation
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication Mobile App Activation Before you can activate the mobile app you must download it. You can have up to
VoIP Intercom and Elastix Server
 VoIP Intercom and Elastix Server Setup Guide http://www.elastix.org 1.0 Setup Diagram Figure 1-1 is a setup diagram for a single VoIP Intercom configuration. In this configuration, the VoIP Intercom acts
VoIP Intercom and Elastix Server Setup Guide http://www.elastix.org 1.0 Setup Diagram Figure 1-1 is a setup diagram for a single VoIP Intercom configuration. In this configuration, the VoIP Intercom acts
Swisscom Mobile Device Services Quick Start Guide: Set-up Remote Management basic. Mobile Device Services Februar 2014
 Swisscom Mobile Device Services Quick Start Guide: Set-up Remote Management basic Mobile Device Services Februar 2014 Contents 2 Login «Welcome to Swisscom MDS» First steps Step 1: Installing the MDM certificate
Swisscom Mobile Device Services Quick Start Guide: Set-up Remote Management basic Mobile Device Services Februar 2014 Contents 2 Login «Welcome to Swisscom MDS» First steps Step 1: Installing the MDM certificate
RAM ACCESS MANAGEMENT PORTAL USER GUIDE WINSTON-SALEM STATE UNIVERSITY
 RAM ACCESS MANAGEMENT PORTAL USER GUIDE WINSTON-SALEM STATE UNIVERSITY About This Document This document provides the guidelines outlining how to enroll in the Winston-Salem State University RAM Access
RAM ACCESS MANAGEMENT PORTAL USER GUIDE WINSTON-SALEM STATE UNIVERSITY About This Document This document provides the guidelines outlining how to enroll in the Winston-Salem State University RAM Access
Google 2 factor authentication User Guide
 Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
Information Technology Services Centre Google 2 factor authentication User Guide Description: This guide describes how to setup Two factor authentication for your Google account. Version: 1.0 Link: Effective
1. What practices does Raleigh Medical Group, P.A. include? 2. Is my health information secure? Who has access to this information?
 Troubleshooting and Frequently Asked Questions FollowMyHealth Patient Portal 1. What practices does Raleigh Medical Group, P.A. include? 2. Is my health information secure? Who has access to this information?
Troubleshooting and Frequently Asked Questions FollowMyHealth Patient Portal 1. What practices does Raleigh Medical Group, P.A. include? 2. Is my health information secure? Who has access to this information?
EBMS Secure Email. February 11, 2016 Instructions. Version 2
 February 11, 2016 Instructions Version 2 Table of Contents Secure Email Upgrade... 3 Receiving Secure Email... 3 Viewing Past Secure Emails... 3 One-Time Registration... 4 Registration Screen... 5 Viewing
February 11, 2016 Instructions Version 2 Table of Contents Secure Email Upgrade... 3 Receiving Secure Email... 3 Viewing Past Secure Emails... 3 One-Time Registration... 4 Registration Screen... 5 Viewing
1. Registration for users
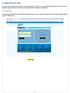 1. Registration for users Every user needs to have login Id and password to use this portal. If you are a new user, you need to register into the system. Once your registration got successful, you will
1. Registration for users Every user needs to have login Id and password to use this portal. If you are a new user, you need to register into the system. Once your registration got successful, you will
Device Enrollment Guide
 TechReady Are you ready to implement IT solutions? Device Enrollment Guide Mobile Device Management with Enterprise Mobility Suite Created for: TechReady 7 iunie 2016 Version 0.3 Created by: Adrian Stoian
TechReady Are you ready to implement IT solutions? Device Enrollment Guide Mobile Device Management with Enterprise Mobility Suite Created for: TechReady 7 iunie 2016 Version 0.3 Created by: Adrian Stoian
Your guide to the HSBC Digital Security Device. HSBC Bank USA, N.A. 2015 All rights reserved.
 Your guide to the HSBC Digital Security Device HSBC Bank USA, N.A. 2015 All rights reserved. 1 Welcome to the next step in the evolution of online security Protecting your money and personal information
Your guide to the HSBC Digital Security Device HSBC Bank USA, N.A. 2015 All rights reserved. 1 Welcome to the next step in the evolution of online security Protecting your money and personal information
Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions
 HOSTING Administrator Control Panel / Quick Reference Guide Page 1 of 9 Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions Exchange 2010 Outlook Profile Setup Page 2 of 9 Exchange
HOSTING Administrator Control Panel / Quick Reference Guide Page 1 of 9 Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions Exchange 2010 Outlook Profile Setup Page 2 of 9 Exchange
SELF-SERVICE PASSWORD RESET PORTAL:
 SELF-SERVICE PASSWORD RESET PORTAL: A NEW STUDENT TOOL In its continuous efforts to provide the highest quality student experience, Bryant & Stratton College is giving students access to a new tool which
SELF-SERVICE PASSWORD RESET PORTAL: A NEW STUDENT TOOL In its continuous efforts to provide the highest quality student experience, Bryant & Stratton College is giving students access to a new tool which
2-FACTOR AUTHENTICATION WITH
 2-FACTOR AUTHENTICATION WITH 2X JUNE 2014 Two-Factor Authentication and Authy What is Two-Factor Authentication? Two-Factor Authentication is a process involving two stages to verify the identity of someone
2-FACTOR AUTHENTICATION WITH 2X JUNE 2014 Two-Factor Authentication and Authy What is Two-Factor Authentication? Two-Factor Authentication is a process involving two stages to verify the identity of someone
Business Online Banking Quick Users Guide
 Business Online Banking Quick Users Guide Business Online Banking Quick Users Guide Table of Contents Overview 2 First Time Login 2 Security 4 Contact Points 4 Registering your Browser / Computer 5 Adding,
Business Online Banking Quick Users Guide Business Online Banking Quick Users Guide Table of Contents Overview 2 First Time Login 2 Security 4 Contact Points 4 Registering your Browser / Computer 5 Adding,
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication
 Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
Guide for Setting Up Your Multi-Factor Authentication Account and Using Multi-Factor Authentication This document serves as a How To reference guide for employees to execute the following MFA tasks: 1.
Configuring an Email Client to Connect to CASS Mail Servers
 Configuring an Email Client to Connect to CASS Mail Servers Table of Contents Introduction... 2 Webmail... 2 Settings... 2 Forwarding... 2 Email Client Configuration... 3 Outlook 2003... 3 Outlook 2007...
Configuring an Email Client to Connect to CASS Mail Servers Table of Contents Introduction... 2 Webmail... 2 Settings... 2 Forwarding... 2 Email Client Configuration... 3 Outlook 2003... 3 Outlook 2007...
Registration Quick Reference Card for Employees/Associates
 Registration Quick Reference Card for Employees/Associates Contents Registration... 2 Activate Your Email Address... 6 Activate Your Mobile Phone... 6 Forgot Your User ID/Password?... 7 ADP and the ADP
Registration Quick Reference Card for Employees/Associates Contents Registration... 2 Activate Your Email Address... 6 Activate Your Mobile Phone... 6 Forgot Your User ID/Password?... 7 ADP and the ADP
ViewPoint Mobile Quick Start Guide
 ViewPoint Mobile Quick Start Guide Step 1 Download the ViewPoint Mobile application. This MUST be done on the ios device, NOT the computer you sync your ios device with. The application will automatically
ViewPoint Mobile Quick Start Guide Step 1 Download the ViewPoint Mobile application. This MUST be done on the ios device, NOT the computer you sync your ios device with. The application will automatically
Secure File Transfer Guest User Guide Updated: 5/8/14
 Secure File Transfer Guest User Guide Updated: 5/8/14 TABLE OF CONTENTS INTRODUCTION... 3 ACCESS SECURE FILE TRANSFER TOOL... 3 REGISTRATION... 4 SELF REGISTERING... 4 REGISTER VIA AN INVITATION SENT BY
Secure File Transfer Guest User Guide Updated: 5/8/14 TABLE OF CONTENTS INTRODUCTION... 3 ACCESS SECURE FILE TRANSFER TOOL... 3 REGISTRATION... 4 SELF REGISTERING... 4 REGISTER VIA AN INVITATION SENT BY
Online Class Registration Quick Guide for Students
 Online Class Registration Quick Guide for Students The purpose of this document is to help students get started with the OCR System. This document will explain about the Login, the general class registration
Online Class Registration Quick Guide for Students The purpose of this document is to help students get started with the OCR System. This document will explain about the Login, the general class registration
Job Aid: Creating Additional Remote Access Logins
 This job aid describes the steps required to add an additional remote access login to the Avaya S8300, S8500, and S8700 Series Media Servers. These logins may be used to establish a Point to Point Protocol
This job aid describes the steps required to add an additional remote access login to the Avaya S8300, S8500, and S8700 Series Media Servers. These logins may be used to establish a Point to Point Protocol
Sophos Mobile Control Startup guide. Product version: 3.5
 Sophos Mobile Control Startup guide Product version: 3.5 Document date: July 2013 Contents 1 About this guide...3 2 What are the key steps?...5 3 Log in as a super administrator...6 4 Activate Sophos Mobile
Sophos Mobile Control Startup guide Product version: 3.5 Document date: July 2013 Contents 1 About this guide...3 2 What are the key steps?...5 3 Log in as a super administrator...6 4 Activate Sophos Mobile
Patient Portal. Accessing the Patient Portal. How to Begin: Enter first and last name, date of birth and create a user name and password.
 Patient Portal How to Begin: If you provided an email address when you registered as a patient, you can expect an email after your discharge that will be sent directly from CPSI, our Electronic Health
Patient Portal How to Begin: If you provided an email address when you registered as a patient, you can expect an email after your discharge that will be sent directly from CPSI, our Electronic Health
Remote Service Manager Installation & Configuration Guide
 Remote Service Manager Installation & Configuration Guide TABLE OF CONTENTS OVERVIEW... 3 SYSTEM REQUIREMENTS... 3 SERVER REQUIREMENTS... 3 CLIENT REQUIREMENTS... 4 NAMED USER LICENSING AND SUPPORT...
Remote Service Manager Installation & Configuration Guide TABLE OF CONTENTS OVERVIEW... 3 SYSTEM REQUIREMENTS... 3 SERVER REQUIREMENTS... 3 CLIENT REQUIREMENTS... 4 NAMED USER LICENSING AND SUPPORT...
Centralized Self-service Password Reset: From the Web and Windows Desktop
 Centralized Self-service Password Reset: From the Web and Windows Desktop Self-service Password Reset Layer v.3.2-007 PistolStar, Inc. dba PortalGuard PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200
Centralized Self-service Password Reset: From the Web and Windows Desktop Self-service Password Reset Layer v.3.2-007 PistolStar, Inc. dba PortalGuard PO Box 1226 Amherst, NH 03031 USA Phone: 603.547.1200
Sophos Mobile Control Startup guide. Product version: 3
 Sophos Mobile Control Startup guide Product version: 3 Document date: January 2013 Contents 1 About this guide...3 2 What are the key steps?...5 3 Log in as a super administrator...6 4 Activate Sophos
Sophos Mobile Control Startup guide Product version: 3 Document date: January 2013 Contents 1 About this guide...3 2 What are the key steps?...5 3 Log in as a super administrator...6 4 Activate Sophos
Dell Mobile Management. Apple Device Enrollment Program
 Dell Mobile Management Contents Dell Mobile Management 3 Setting up the 3 DMM Device Deployment Program Prerequisites 4 Configure Apple VPP Token in DMM 5 Download Apple VPP Token 5 Assign VPP App Licenses
Dell Mobile Management Contents Dell Mobile Management 3 Setting up the 3 DMM Device Deployment Program Prerequisites 4 Configure Apple VPP Token in DMM 5 Download Apple VPP Token 5 Assign VPP App Licenses
Guarantee Trust Life Insurance Company. Agent Portal www.gtlic.com. Agent Portal Guide
 Guarantee Trust Life Insurance Company Agent Portal www.gtlic.com Agent Portal Guide Rev. 3/2014 Table of Contents Log in to Agent Portal... 3 Obtain Quote... 4 Print Quote... 5 Save and Retrieve Quote...
Guarantee Trust Life Insurance Company Agent Portal www.gtlic.com Agent Portal Guide Rev. 3/2014 Table of Contents Log in to Agent Portal... 3 Obtain Quote... 4 Print Quote... 5 Save and Retrieve Quote...
LEVEL 3 SM XPRESSMEET SOLUTIONS
 LEVEL 3 SM XPRESSMEET SOLUTIONS USER GUIDE VERSION 2015 TABLE OF CONTENTS Level 3 XpressMeet Calendar...3 Level 3 SM XpressMeet Outlook Add-In...3 Overview...3 Features...3 Download and Installation Instructions...
LEVEL 3 SM XPRESSMEET SOLUTIONS USER GUIDE VERSION 2015 TABLE OF CONTENTS Level 3 XpressMeet Calendar...3 Level 3 SM XpressMeet Outlook Add-In...3 Overview...3 Features...3 Download and Installation Instructions...
Configuring. SugarCRM. Chapter 121
 Chapter 121 Configuring SugarCRM The following is an overview of the steps required to configure the SugarCRM Web application for single sign-on (SSO) via SAML. SugarCRM offers both IdP-initiated SAML
Chapter 121 Configuring SugarCRM The following is an overview of the steps required to configure the SugarCRM Web application for single sign-on (SSO) via SAML. SugarCRM offers both IdP-initiated SAML
Little League International
 Little League International User Guide for Vendors November 2013 CONFIDENTIAL & PROPRIETARY The recipient of this material (hereinafter "the Material") acknowledges that it contains confidential and proprietary
Little League International User Guide for Vendors November 2013 CONFIDENTIAL & PROPRIETARY The recipient of this material (hereinafter "the Material") acknowledges that it contains confidential and proprietary
How to... Order or transfer a domain
 How to... Order or transfer a domain Table of Contents Section How To... Page Number 1... Register a domain with Tagadab 2 2... Transfer a domain to Tagadab 7 Tagadab Limited www.tagadab.com Registration
How to... Order or transfer a domain Table of Contents Section How To... Page Number 1... Register a domain with Tagadab 2 2... Transfer a domain to Tagadab 7 Tagadab Limited www.tagadab.com Registration
Sophos Mobile Control Installation guide. Product version: 3
 Sophos Mobile Control Installation guide Product version: 3 Document date: January 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...16 4 External
Sophos Mobile Control Installation guide Product version: 3 Document date: January 2013 Contents 1 Introduction...3 2 The Sophos Mobile Control server...4 3 Set up Sophos Mobile Control...16 4 External
TransUnion Direct: Download Digital Certificate Firefox
 TransUnion Direct: Download Digital Certificate Firefox Getting Started What You Need to Know Important: Both the user and the administrator need to be present at the user s PC. The user should log into
TransUnion Direct: Download Digital Certificate Firefox Getting Started What You Need to Know Important: Both the user and the administrator need to be present at the user s PC. The user should log into
Two-Factor Authentication
 Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
Two-Factor Authentication This document describes SonicWALL s implementation of two-factor authentication for SonicWALL SSL-VPN appliances. This document contains the following sections: Feature Overview
Viewing Application Status Online. BlueAccess Individual Application Status
 Viewing Application Status Online BlueAccess Individual Application Status Checking Application Status Online In this session we will discuss: Signing up for BlueAccess. Logging on to the Individual Application
Viewing Application Status Online BlueAccess Individual Application Status Checking Application Status Online In this session we will discuss: Signing up for BlueAccess. Logging on to the Individual Application
TLC 3 Student Mobile Device Configuration Specifications
 All students are REQUIRED to configure and maintain their mobile devices as outlined in this document. Non-compliance is a violation of District policy and may result in disciplinary action and/or revocation
All students are REQUIRED to configure and maintain their mobile devices as outlined in this document. Non-compliance is a violation of District policy and may result in disciplinary action and/or revocation
Mobile Banking. Click To Begin
 Mobile Banking Click To Begin Click On Your Type Of Phone iphone Please select the method you would like to use for accessing your account from the options below: APP (Downloadable Application from itunes)
Mobile Banking Click To Begin Click On Your Type Of Phone iphone Please select the method you would like to use for accessing your account from the options below: APP (Downloadable Application from itunes)
UC Business & UC Team
 UC Business & UC Team Administrator Guide Revision 1.0 GCI Ltd Global House 2 Crofton Close Lincoln Lincolnshire LN3 4NT www.gcicom.net Copyright GCI 2013 UC Business & UC Team Administrator Guide 1 of
UC Business & UC Team Administrator Guide Revision 1.0 GCI Ltd Global House 2 Crofton Close Lincoln Lincolnshire LN3 4NT www.gcicom.net Copyright GCI 2013 UC Business & UC Team Administrator Guide 1 of
Guidelines for new users of the Union Registry ECAS account, registration and enrolment
 Guidelines for new users of the Union Registry ECAS account, registration and enrolment An ECAS account and registration are required for a new user to be added as an account representative Before a new
Guidelines for new users of the Union Registry ECAS account, registration and enrolment An ECAS account and registration are required for a new user to be added as an account representative Before a new
Two-Factor Authentication
 Two-Factor Authentication Two-Factor Authentication is an enhanced security feature for Payentry. It adds an extra layer of protection to ensure only authorized users can gain access to your data. In addition
Two-Factor Authentication Two-Factor Authentication is an enhanced security feature for Payentry. It adds an extra layer of protection to ensure only authorized users can gain access to your data. In addition
ATTENTION: End users should take note that Main Line Health has not verified within a Citrix
 Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
Subject: Citrix Remote Access using PhoneFactor Authentication ATTENTION: End users should take note that Main Line Health has not verified within a Citrix environment the image quality of clinical cal
Online Check Stub Enrollment. from Dominion Payroll Services
 Online Check Stub Enrollment from Dominion Payroll Services How to Create an Account In order to access the Employee Self-Service portal, you will need to go through a one-time process that allows you
Online Check Stub Enrollment from Dominion Payroll Services How to Create an Account In order to access the Employee Self-Service portal, you will need to go through a one-time process that allows you
QuickStart Guide for Mobile Device Management
 QuickStart Guide for Mobile Device Management Version 8.5 Inventory Configuration Security Management Distribution JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made
QuickStart Guide for Mobile Device Management Version 8.5 Inventory Configuration Security Management Distribution JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made
TechNote. Contents. Introduction. System Requirements. SRA Two-factor Authentication with Quest Defender. Secure Remote Access.
 Secure Remote Access SRA Two-factor Authentication with Quest Defender SonicOS Contents Introduction... 1 System Requirements... 1 Defender Configuration... 2 Dell SonicWALL SRA Configuration... 18 Two-factor
Secure Remote Access SRA Two-factor Authentication with Quest Defender SonicOS Contents Introduction... 1 System Requirements... 1 Defender Configuration... 2 Dell SonicWALL SRA Configuration... 18 Two-factor
N750 WiFi DSL Modem Router Premium Edition
 Support Thank you for purchasing this NETGEAR product. After installing your device, locate the serial number on the label of your product and use it to register your product at https://my.netgear.com.
Support Thank you for purchasing this NETGEAR product. After installing your device, locate the serial number on the label of your product and use it to register your product at https://my.netgear.com.
Provider OnLine. Log-In Guide
 Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
Self-service password management user guide
 King s College London IT Services Self-service password management user guide v1.04 26 January 2016 Contents How to register for online services and self-service password management... 2 How to reset your
King s College London IT Services Self-service password management user guide v1.04 26 January 2016 Contents How to register for online services and self-service password management... 2 How to reset your
PECO SMART ENERGY USAGE DATA TOOL (PSEUDT)
 PECO SMART ENERGY USAGE DATA TOOL (PSEUDT) Energy Star Portfolio Manager User Guide V2.5 2 Confidential Table of Contents ENERGY STAR PORTFOLIO MANAGEMENT... 4 1 LOGGING IN TO ENERGY STAR PORTFOLIO MANAGER...
PECO SMART ENERGY USAGE DATA TOOL (PSEUDT) Energy Star Portfolio Manager User Guide V2.5 2 Confidential Table of Contents ENERGY STAR PORTFOLIO MANAGEMENT... 4 1 LOGGING IN TO ENERGY STAR PORTFOLIO MANAGER...
1. Open the preferences screen by opening the Mail menu and selecting Preferences...
 Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Using TLS encryption with OS X Mail This guide assumes that you have already created an account in Mail. If you have not, you can use the new account wizard. The new account wizard is in the Accounts window
Hosted Business Voice END USER PORTAL GUIDE
 Hosted Business Voice END PORTAL 13461 Sunrise Valley Drive Ste. 300 Herndon, VA 20171 800.962.9329 www.apptix.com Table of Contents Hosted Business Voice... 1 END... 1 PORTAL... 1 Table of Contents...
Hosted Business Voice END PORTAL 13461 Sunrise Valley Drive Ste. 300 Herndon, VA 20171 800.962.9329 www.apptix.com Table of Contents Hosted Business Voice... 1 END... 1 PORTAL... 1 Table of Contents...
CoventryOne Agent Portal User Guide
 CoventryOne Agent Portal User Guide CoventryOne is an Individual Product underwritten by PersonalCare Insurance of Illinois, Inc. Welcome to the CoventryOne Agent Portal bringing the convenience of the
CoventryOne Agent Portal User Guide CoventryOne is an Individual Product underwritten by PersonalCare Insurance of Illinois, Inc. Welcome to the CoventryOne Agent Portal bringing the convenience of the
Affirmation of Accurate Information On the next you must affirm that that you are providing complete and accurate information. If you affirm, click
 New Applicants Overview Welcome to the Indiana State Police online handgun license application portal. This brief training document will provide an overview of the application process and show you new
New Applicants Overview Welcome to the Indiana State Police online handgun license application portal. This brief training document will provide an overview of the application process and show you new
Two Factor Authentication - USER GUIDE
 Two Factor Authentication - USER GUIDE Two Factor Authentication (or 2FA) is a two step verification process that provides an extra layer of security for you when accessing your account within Online Services.
Two Factor Authentication - USER GUIDE Two Factor Authentication (or 2FA) is a two step verification process that provides an extra layer of security for you when accessing your account within Online Services.
How do I enroll in the password portal?
 The self-serve portal is designed to allow you to change your password and unlock your locked account even if you have forgotten your password. You must enroll for this service to be able to use it. You
The self-serve portal is designed to allow you to change your password and unlock your locked account even if you have forgotten your password. You must enroll for this service to be able to use it. You
QuickStart Guide for Mobile Device Management. Version 8.6
 QuickStart Guide for Mobile Device Management Version 8.6 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF
QuickStart Guide for Mobile Device Management Version 8.6 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF
WNMS Mobile Application
 WNMS Mobile Application User s Guide Revision 1.0 18 October 2013 Copyright 2013 Deliberant www.deliberant.com Copyright 2013 Deliberant This user s guide and the software described in it are copyrighted
WNMS Mobile Application User s Guide Revision 1.0 18 October 2013 Copyright 2013 Deliberant www.deliberant.com Copyright 2013 Deliberant This user s guide and the software described in it are copyrighted

 January 2015
January 2015