Two factor authentication: Ever thought of this?
|
|
|
- Alexander Maxwell
- 10 years ago
- Views:
Transcription
1 Two factor authentication: Ever thought of this? Abhibandu Kafle Entrust Solutions Nepal
2 Abstract: Two Factor Authentication commonly known as 2FA in technical field is a measure to identify the user by the application with what they have and what they know, so that it can authenticate any specific person logging into the system as the real owner of that account. Majority of reputed websites implement 2FA process to enhance the user security. Comprehending the benefits the 2FA scheme offers, more are on the process of implementing the feature. A comprehensive list of sites implementing/planning to implement 'Two Factor Authentication' can be seen on Any new portals bringing forth 2FA security feature should consider possibility of Denial of Service (Dos) before implementing it to production. Premature implementation of this scheme without considering verification module working may lead to Denial of Service (DoS) to a legitimate user which sadly is prevalent at present.
3 The problem: If every kind of information that uniquely identifies a user -something that can t be attribute of multiple users- are not being verified before allowing an account to have access to 2FA management portal, it could lead to DOS, because the account could be impersonating someone with their details. As an instance, I could use of a guy, say Derp, which is [email protected], a unique identifier, and make account on his behalf. I don t have access of [email protected] but I will be able to use that account to impersonate him. Now I add 2FA to that account and attach my cell number to his account. Someday, Derp wants to join the portal with his . When he sees that the has been already used in other account, he will try to reset the password. He can reset the password, but even if he knows the password, there s a dead-end because the account has 2factor enabled with my mobile phone attached to the account. All of 2FA service providers mask the mobile number for privacy reasons and give out message that the text has been sent to your mobile ending with *******123, which is not going to help. In some other portals, it was also possible to search users by unverified , thus allowing an attacker have an added benefit in impersonating a real person. Since 2FA is the ultimate power that could be granted to end user, authenticity of user should be considered prior to handing him over the ultimate power. What apparently seems to instill the sense of security in users, can also lead to authentication problem like this.
4 The authentication flow: How it actually works in vulnerable portals? User registration process User account management portal 2 Factor authentication management. How should it have been? User registration process User account management portal User verification process 2 Factor authentication management
5 Some popular sites that still use this scheme: I spent few hours looking sites that used this type of authentication scheme and it seemed more than 70 percent of those are still vulnerable. Some popular portals like Facebook, Twitter, and Stripe now only allow adding 2 FA after verifying account.
6 The impact (a scenario) : Let us take an example of github. Github doesn t ask you to verify your (as your identity) while you sign up. Now, you can sign up on anyone s behalf using their . Since there is no verification process, you can add 2FA to that account so that it will be inaccessible to legitimate user. It can really come handy at times like when you have a edu mail and if someone else makes an account for you before you even register. If they add 2 FA to your account, it apparently becomes inaccessible to you [unless you mail the service provider and show them your identity]. Thus one won t be able sign up to github using his edu mail and is deprived from using student pack services offered by github. It is not very hard to enumerate addresses of a specific target company since most educational institute or users use [email protected] or [email protected]. Likewise, in portals where from specific domain are only allowed to sign up or join a team, this kind of attack can prove insidious, as long as users aren t verified. Because when a team from a company is to be signed up, probably the whole company will be dispossessed from having an account in that vulnerable portal.
7 Conclusion: Every application that allows user to activate 2FA on their portal should ask for verification of identity separately. For e.g. A user can not only be verified by sending a text to mobile number mentioned during registration, it is equally important to verify the address and similar pertinent information that are unique and can possibly lead to denial of service for legitimate user thus preventing a legit user from accessing the portal.
Client Server Registration Protocol
 Client Server Registration Protocol The Client-Server protocol involves these following steps: 1. Login 2. Discovery phase User (Alice or Bob) has K s Server (S) has hash[pw A ].The passwords hashes are
Client Server Registration Protocol The Client-Server protocol involves these following steps: 1. Login 2. Discovery phase User (Alice or Bob) has K s Server (S) has hash[pw A ].The passwords hashes are
Creating an e mail list in YahooGroups
 Creating an e mail list in YahooGroups Creating an e mail list in Yahoo Groups is easy to do. Just follow the steps below and your group will be created in a matter of minutes. Why use Yahoo Groups? First,
Creating an e mail list in YahooGroups Creating an e mail list in Yahoo Groups is easy to do. Just follow the steps below and your group will be created in a matter of minutes. Why use Yahoo Groups? First,
Two-Factor Authentication: Guide to FEXCO CFX SMS/APP Verification
 Guaranteeing you the Highest Levels of Security Online At FEXCO CFX, we are dedicated to ensuring that our clients enjoy the highest standards of security. In order to combat the risk of online fraud and
Guaranteeing you the Highest Levels of Security Online At FEXCO CFX, we are dedicated to ensuring that our clients enjoy the highest standards of security. In order to combat the risk of online fraud and
CS 356 Lecture 28 Internet Authentication. Spring 2013
 CS 356 Lecture 28 Internet Authentication Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
CS 356 Lecture 28 Internet Authentication Spring 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists
How to Request Access to the Commerce Contract Management System
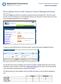 How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
How to Request Access to the Commerce Contract Management System (one-time only) Once you ve logged into SAW, you can add your selected services by clicking on the Click here to add services link. This
Protect Yourself. Who is asking? What information are they asking for? Why do they need it?
 Protect Yourself Your home computer serves many purposes: email, shopping, social networking and more. As you surf the Internet, you should be aware of the various ways to protect yourself. Of primary
Protect Yourself Your home computer serves many purposes: email, shopping, social networking and more. As you surf the Internet, you should be aware of the various ways to protect yourself. Of primary
GUIDELINE FOR PME 35 ONLINE BOOKING SYSTEM
 GUIDELINE FOR PME 35 ONLINE BOOKING SYSTEM INDEX VERIFICATION OF REGISTRATION... 2 ACCOMMODATION RESERVATION... 6 TRANSFER RESERVATION... 9 PRE POST TOUR RESERVATIONS... 12 GUIDELINE FOR PAYMENTS... 15
GUIDELINE FOR PME 35 ONLINE BOOKING SYSTEM INDEX VERIFICATION OF REGISTRATION... 2 ACCOMMODATION RESERVATION... 6 TRANSFER RESERVATION... 9 PRE POST TOUR RESERVATIONS... 12 GUIDELINE FOR PAYMENTS... 15
Evaluation of different Open Source Identity management Systems
 Evaluation of different Open Source Identity management Systems Ghasan Bhatti, Syed Yasir Imtiaz Linkoping s universitetet, Sweden [ghabh683, syeim642]@student.liu.se 1. Abstract Identity management systems
Evaluation of different Open Source Identity management Systems Ghasan Bhatti, Syed Yasir Imtiaz Linkoping s universitetet, Sweden [ghabh683, syeim642]@student.liu.se 1. Abstract Identity management systems
7. In the boxed unlabeled field, enter the last 4 digits of your Social Security number.
 CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
CREATE YOUR MYVIEW LOGIN To access myview while ensuring security, you will be given an encrypted access key token. You will use this token the first time you log into myview. Once you have successfully
IMATS - SAMS User Registration Webinar
 Secure Access Management Services (SAMS) Electronic Authentication Process for the Inventory Management and Tracking System (IMATS) IMATS - SAMS User Registration Webinar Objective To provide information
Secure Access Management Services (SAMS) Electronic Authentication Process for the Inventory Management and Tracking System (IMATS) IMATS - SAMS User Registration Webinar Objective To provide information
OAuth Web Authorization Protocol Barry Leiba
 www.computer.org/internet computing OAuth Web Authorization Protocol Barry Leiba Vol. 16, No. 1 January/February, 2012 This material is presented to ensure timely dissemination of scholarly and technical
www.computer.org/internet computing OAuth Web Authorization Protocol Barry Leiba Vol. 16, No. 1 January/February, 2012 This material is presented to ensure timely dissemination of scholarly and technical
How To Secure Cloud Computing
 Next Generation Cloud Computing Issues and Solutions Jeon SeungHwan 1, Yvette E. Gelogo 1 and Byungjoo Park 1 * 1 Department of Multimedia Engineering, Hannam University 133 Ojeong-dong, Daeduk-gu, Daejeon,
Next Generation Cloud Computing Issues and Solutions Jeon SeungHwan 1, Yvette E. Gelogo 1 and Byungjoo Park 1 * 1 Department of Multimedia Engineering, Hannam University 133 Ojeong-dong, Daeduk-gu, Daejeon,
Enhanced Security for Online Banking
 Enhanced Security for Online Banking MidSouth Bank is focused on protecting your personal and account information at all times. As instances of internet fraud increase, it is no longer sufficient to use
Enhanced Security for Online Banking MidSouth Bank is focused on protecting your personal and account information at all times. As instances of internet fraud increase, it is no longer sufficient to use
Some Progressive Marketing Steps. The Mark Garner Real Estate Team. Will Take To Get Your Property Sold!
 Some Progressive Marketing Steps The Mark Garner Real Estate Team Will Take To Get Your Property Sold! We ll create a Sharp Website For Your Property. It will have a unique domain name for your street
Some Progressive Marketing Steps The Mark Garner Real Estate Team Will Take To Get Your Property Sold! We ll create a Sharp Website For Your Property. It will have a unique domain name for your street
Market Intelligence Cell. Fighting Financial Crime
 Market Intelligence Cell Fighting Financial Crime 1 Market Intelligence Cell Our objective To investigate and suppress illegal, dishonorable and improper practices, market abuse and any potential breach
Market Intelligence Cell Fighting Financial Crime 1 Market Intelligence Cell Our objective To investigate and suppress illegal, dishonorable and improper practices, market abuse and any potential breach
Nessus Cloud User Registration
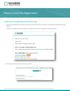 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Emails and anti-spam Page 1
 Emails and anti-spam Page 1 As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send emails from your webcrm system, we use the webcrm servers to send emails
Emails and anti-spam Page 1 As the spammers become increasing aggressive more and more legit emails get banned as spam. When you send emails from your webcrm system, we use the webcrm servers to send emails
Course Title: Penetration Testing: Network Threat Testing, 1st Edition
 Course Title: Penetration Testing: Network Threat Testing, 1st Edition Page 1 of 6 Course Description: The Security Analyst Series from EC-Council Press is comprised of five books covering a broad base
Course Title: Penetration Testing: Network Threat Testing, 1st Edition Page 1 of 6 Course Description: The Security Analyst Series from EC-Council Press is comprised of five books covering a broad base
Using YSU Password Self-Service
 Using YSU Password Self-Service Using YSU Password Self-Service Password Self-Service Web Interface Required Items: YSU (MyYSU) Directory account, Web browser This guide will assist you with using the
Using YSU Password Self-Service Using YSU Password Self-Service Password Self-Service Web Interface Required Items: YSU (MyYSU) Directory account, Web browser This guide will assist you with using the
Provider OnLine. Log-In Guide
 Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
Provider OnLine Log-In Guide Table of Contents 1 LOG-IN ACCESS... 3 1.1 ENTERING THE USER ID AND PASSWORD... 4 1.2 OVERVIEW AND PURPOSE OF TRICIPHER... 5 1.2.1 Log-in for Users Who Are Active, But Not
Set internet safety parental controls with Windows
 How to Microsoft lets parents set up internet safety settings on a Windows computer for their kids, using Family Safety. Family Safety provides a website and a free program that you install on the computers
How to Microsoft lets parents set up internet safety settings on a Windows computer for their kids, using Family Safety. Family Safety provides a website and a free program that you install on the computers
Cloud Portal Guest Invitations 4.0
 Release Notes Cloud Portal Guest Invitations 4.0 January 2014 Cloud Portal Guest Invitations 4.0 Release Notes Copyright sentence ( 2014, CTERA Networks. All rights reserved) 1 Release Contents Copyright
Release Notes Cloud Portal Guest Invitations 4.0 January 2014 Cloud Portal Guest Invitations 4.0 Release Notes Copyright sentence ( 2014, CTERA Networks. All rights reserved) 1 Release Contents Copyright
Virtual Cabinet Document Portal User Guide
 Virtual Cabinet Document Portal User Guide Contents / Introduction Introduction... 2 What to expect when publishing a document... 3 Having difficulty? Troubleshooting guide.... 7 The Virtual Cabinet Document
Virtual Cabinet Document Portal User Guide Contents / Introduction Introduction... 2 What to expect when publishing a document... 3 Having difficulty? Troubleshooting guide.... 7 The Virtual Cabinet Document
Kentico CMS security facts
 Kentico CMS security facts ELSE 1 www.kentico.com Preface The document provides the reader an overview of how security is handled by Kentico CMS. It does not give a full list of all possibilities in the
Kentico CMS security facts ELSE 1 www.kentico.com Preface The document provides the reader an overview of how security is handled by Kentico CMS. It does not give a full list of all possibilities in the
Social Network Security. Frank K. F. Chow Vice-Chairperson Professional Information Security Association (PISA)
 Social Network Security Frank K. F. Chow Vice-Chairperson Professional Information Security Association (PISA) How Do We Communicate Today? I can write you a letter by snail mail. I can write you a letter
Social Network Security Frank K. F. Chow Vice-Chairperson Professional Information Security Association (PISA) How Do We Communicate Today? I can write you a letter by snail mail. I can write you a letter
How to Recognize Phishing Emails Targeting the University of Mary
 How to Recognize Phishing Emails Targeting the University of Mary For the past several years, University of Mary has been targeted by phishing emails. It is important that you recognize these scams so
How to Recognize Phishing Emails Targeting the University of Mary For the past several years, University of Mary has been targeted by phishing emails. It is important that you recognize these scams so
Identity & Access Frequently Asked Questions (FAQs)
 Contents Contents... 1 General... 2 Registration... 7 My Profile... 9 Employer Information... 11 My Connections... 15 My Staff... 22 Appendix A Acronyms, Key Terms, and Definitions... 25 6/27/2015 1 General
Contents Contents... 1 General... 2 Registration... 7 My Profile... 9 Employer Information... 11 My Connections... 15 My Staff... 22 Appendix A Acronyms, Key Terms, and Definitions... 25 6/27/2015 1 General
User Manual. For. Digitally Signing of your application
 User Manual For Digitally Signing of your application How to Digital Signature In your Application Digital Signature: A digital signature is an electronic form of a signature that can be used to authenticate
User Manual For Digitally Signing of your application How to Digital Signature In your Application Digital Signature: A digital signature is an electronic form of a signature that can be used to authenticate
Multi-Factor Authentication
 Making the Most of Multi-Factor Authentication Introduction The news stories are commonplace: Hackers steal or break passwords and gain access to a company s data, often causing huge financial losses to
Making the Most of Multi-Factor Authentication Introduction The news stories are commonplace: Hackers steal or break passwords and gain access to a company s data, often causing huge financial losses to
Why is a strong password important?
 Internet Security Why is a strong password important? Identity theft motives: To gain access to resources For the challenge/fun Personal reasons Theft methods Brute forcing and other script hacking methods
Internet Security Why is a strong password important? Identity theft motives: To gain access to resources For the challenge/fun Personal reasons Theft methods Brute forcing and other script hacking methods
Using Voice Biometrics in the Call Center. Best Practices for Authentication and Anti-Fraud Technology Deployment
 Using Voice Biometrics in the Call Center Best Practices for Authentication and Anti-Fraud Technology Deployment This whitepaper is designed for executives and managers considering voice biometrics to
Using Voice Biometrics in the Call Center Best Practices for Authentication and Anti-Fraud Technology Deployment This whitepaper is designed for executives and managers considering voice biometrics to
Entrust IdentityGuard Comprehensive
 Entrust IdentityGuard Comprehensive Entrust IdentityGuard Comprehensive is a five-day, hands-on overview of Entrust Course participants will gain experience planning, installing and configuring Entrust
Entrust IdentityGuard Comprehensive Entrust IdentityGuard Comprehensive is a five-day, hands-on overview of Entrust Course participants will gain experience planning, installing and configuring Entrust
THE UNIVERSITY OF TRINIDAD & TOBAGO
 THE UNIVERSITY OF TRINIDAD & TOBAGO FINAL ASSESSMENT/EXAMINATIONS DECEMBER 2013 ALTERNATE Course Code and Title: TCOM3003 Communication Security and Privacy Programme: Bachelor of Applied Science in Computer
THE UNIVERSITY OF TRINIDAD & TOBAGO FINAL ASSESSMENT/EXAMINATIONS DECEMBER 2013 ALTERNATE Course Code and Title: TCOM3003 Communication Security and Privacy Programme: Bachelor of Applied Science in Computer
Offline Payment Methods
 Offline Payment Methods STRONGVON Tournament Management System 1 Overview The STRONGVON Tournament Management System allows you to collect online registration, while arranging for offline payment methods
Offline Payment Methods STRONGVON Tournament Management System 1 Overview The STRONGVON Tournament Management System allows you to collect online registration, while arranging for offline payment methods
User Guide for CDC s SAMS Partner Portal. Document Version 1.0
 User Guide for CDC s SAMS Partner Portal Document Version 1.0 Introduction If you are reading this guide, it probably means that you have been (or will be) invited to register with the SAMS Partner Portal.
User Guide for CDC s SAMS Partner Portal Document Version 1.0 Introduction If you are reading this guide, it probably means that you have been (or will be) invited to register with the SAMS Partner Portal.
Microsoft STRIDE (six) threat categories
 Risk-based Security Testing: Prioritizing Security Testing with Threat Modeling This lecture provides reference material for the book entitled The Art of Software Security Testing by Wysopal et al. 2007
Risk-based Security Testing: Prioritizing Security Testing with Threat Modeling This lecture provides reference material for the book entitled The Art of Software Security Testing by Wysopal et al. 2007
Secure Messaging Service
 Human Resources Secure Messaging Service Receiving Secure Emails from West Berkshire Council Table of Contents What are Secure Messaging notifications?... 3 How do I set up my Secure Messaging account?...
Human Resources Secure Messaging Service Receiving Secure Emails from West Berkshire Council Table of Contents What are Secure Messaging notifications?... 3 How do I set up my Secure Messaging account?...
Secure Mail Registration and Viewing Procedures
 Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
Secure Mail Registration and Viewing Procedures May 2011 For External Secure Mail Recipients Contents This document provides a brief, end user oriented overview of the Associated Banc Corp s Secure Email
XGENPLUS SECURITY FEATURES...
 Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
How To Protect Your Computer From Attack
 FREQUENTLY ASKED QUESTIONS on C Y B E R S E C U R I T Y By IEEE USA s Committee on Communications Policy December 2011 This Frequently Asked Questions (FAQs) was prepared by IEEE-USA s Committee on Communications
FREQUENTLY ASKED QUESTIONS on C Y B E R S E C U R I T Y By IEEE USA s Committee on Communications Policy December 2011 This Frequently Asked Questions (FAQs) was prepared by IEEE-USA s Committee on Communications
Personal Secure Email Certificate
 Entrust Certificate Services Personal Secure Email Certificate Enrollment Guide Date of Issue: October 2010 Copyright 2010 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Certificate Services Personal Secure Email Certificate Enrollment Guide Date of Issue: October 2010 Copyright 2010 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Borough of Poole Staff (Adult Social Care) Encryption: Sending secure, encrypted e- mails & attachments
 Borough of Poole Staff (Adult Social Care) Encryption: Sending secure, encrypted e- mails & attachments V8 Contents What is Encryption?...3 Why do I need to know about it?...3 How do I use it?...3 What
Borough of Poole Staff (Adult Social Care) Encryption: Sending secure, encrypted e- mails & attachments V8 Contents What is Encryption?...3 Why do I need to know about it?...3 How do I use it?...3 What
1. How to Register... 2. 2. Forgot Password... 4. 3. Login to MailTrack Webmail... 5. 4. Accessing MailTrack message Centre... 6
 MailTrack How To Document 27 March 2014 Table of Contents 1. How to Register... 2 2. Forgot Password... 4 3. Login to MailTrack Webmail... 5 4. Accessing MailTrack message Centre... 6 5. Creating a MailTrack
MailTrack How To Document 27 March 2014 Table of Contents 1. How to Register... 2 2. Forgot Password... 4 3. Login to MailTrack Webmail... 5 4. Accessing MailTrack message Centre... 6 5. Creating a MailTrack
Class Outline. Part 1 - Introduction Explaining email Parts of an email address Types of email services Acquiring an email account
 EMAIL Basics Class Outline Part 1 - Introduction Explaining email Parts of an email address Types of email services Acquiring an email account Part 3 Managing Your Messages Deleting messages The Trash
EMAIL Basics Class Outline Part 1 - Introduction Explaining email Parts of an email address Types of email services Acquiring an email account Part 3 Managing Your Messages Deleting messages The Trash
Digital Citizenship Lesson Plan
 Digital Citizenship Lesson Plan This course is to help people to understand how to use the Internet in a safe, productive way. Additional resources and links are available on the TechTECS website. http://techtecs.com/digital-citizenship
Digital Citizenship Lesson Plan This course is to help people to understand how to use the Internet in a safe, productive way. Additional resources and links are available on the TechTECS website. http://techtecs.com/digital-citizenship
McKesson Practice Choice TM Electronic Prescribing of Controlled Substances (EPCS) Frequently Asked Questions
 Overview McKesson Practice Choice TM Electronic Prescribing of Controlled Substances (EPCS) Frequently Asked Questions What is EPCS? EPCS stands for Electronic Prescribing of Controlled Substances. Our
Overview McKesson Practice Choice TM Electronic Prescribing of Controlled Substances (EPCS) Frequently Asked Questions What is EPCS? EPCS stands for Electronic Prescribing of Controlled Substances. Our
Frequently Asked Questions
 Frequently Asked Questions What is an electronic health record? Borgess has transitioned from paper-based medical records to electronic health records (EHRs). An EHR is an electronic version of your medical
Frequently Asked Questions What is an electronic health record? Borgess has transitioned from paper-based medical records to electronic health records (EHRs). An EHR is an electronic version of your medical
How users bypass your security!
 How users bypass your security! IT Days Security issues 20 th November 2014 Tom Leclerc, Security Consultant SAGS - Security Audits and Governance Services, a Telindus Security department Classification:
How users bypass your security! IT Days Security issues 20 th November 2014 Tom Leclerc, Security Consultant SAGS - Security Audits and Governance Services, a Telindus Security department Classification:
Using Entrust certificates with VPN
 Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
Entrust Managed Services PKI Using Entrust certificates with VPN Document issue: 1.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered trademark
SchoolBooking SSO Integration Guide
 SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
A Secure Authenticate Framework for Cloud Computing Environment
 A Secure Authenticate Framework for Cloud Computing Environment Nitin Nagar 1, Pradeep k. Jatav 2 Abstract Cloud computing has an important aspect for the companies to build and deploy their infrastructure
A Secure Authenticate Framework for Cloud Computing Environment Nitin Nagar 1, Pradeep k. Jatav 2 Abstract Cloud computing has an important aspect for the companies to build and deploy their infrastructure
Guidelines for Web applications protection with dedicated Web Application Firewall
 Guidelines for Web applications protection with dedicated Web Application Firewall Prepared by: dr inŝ. Mariusz Stawowski, CISSP Bartosz Kryński, Imperva Certified Security Engineer INTRODUCTION Security
Guidelines for Web applications protection with dedicated Web Application Firewall Prepared by: dr inŝ. Mariusz Stawowski, CISSP Bartosz Kryński, Imperva Certified Security Engineer INTRODUCTION Security
Network Security - ISA 656 Email Security
 Network Security - ISA 656 Angelos Stavrou November 13, 2007 The Usual Questions The Usual Questions Assets What are we trying to protect? Against whom? 2 / 33 Assets The Usual Questions Assets Confidentiality
Network Security - ISA 656 Angelos Stavrou November 13, 2007 The Usual Questions The Usual Questions Assets What are we trying to protect? Against whom? 2 / 33 Assets The Usual Questions Assets Confidentiality
Wireless Email Installation Checklist for Novell GroupWise Environments
 Overview Wireless Email Installation Checklist for Novell GroupWise Environments This chapter includes a checklist to be completed before you install Wireless Email for Novell GroupWise. By completing
Overview Wireless Email Installation Checklist for Novell GroupWise Environments This chapter includes a checklist to be completed before you install Wireless Email for Novell GroupWise. By completing
The Feasibility and Application of using a Zero-knowledge Protocol Authentication Systems
 The Feasibility and Application of using a Zero-knowledge Protocol Authentication Systems Becky Cutler [email protected] Mentor: Professor Chris Gregg Abstract Modern day authentication systems
The Feasibility and Application of using a Zero-knowledge Protocol Authentication Systems Becky Cutler [email protected] Mentor: Professor Chris Gregg Abstract Modern day authentication systems
Cloud Storage Security
 Cloud Storage Security Sven Vowé Fraunhofer Institute for Secure Information Technology (SIT) Darmstadt, Germany SIT is a member of CASED (Center for Advanced Security Research Darmstadt) Cloud Storage
Cloud Storage Security Sven Vowé Fraunhofer Institute for Secure Information Technology (SIT) Darmstadt, Germany SIT is a member of CASED (Center for Advanced Security Research Darmstadt) Cloud Storage
SIP and VoIP 1 / 44. SIP and VoIP
 What is SIP? What s a Control Channel? History of Signaling Channels Signaling and VoIP Complexity Basic SIP Architecture Simple SIP Calling Alice Calls Bob Firewalls and NATs SIP URIs Multiple Proxies
What is SIP? What s a Control Channel? History of Signaling Channels Signaling and VoIP Complexity Basic SIP Architecture Simple SIP Calling Alice Calls Bob Firewalls and NATs SIP URIs Multiple Proxies
SELF-SERVICE PASSWORD RESET PORTAL:
 SELF-SERVICE PASSWORD RESET PORTAL: A NEW STUDENT TOOL In its continuous efforts to provide the highest quality student experience, Bryant & Stratton College is giving students access to a new tool which
SELF-SERVICE PASSWORD RESET PORTAL: A NEW STUDENT TOOL In its continuous efforts to provide the highest quality student experience, Bryant & Stratton College is giving students access to a new tool which
Instruction Guide. People First Dependent Certification Process
 People First Dependent Certification Process Each time an employee logs into People First to make an enrollment selection during open enrollment or because of a qualified status change (QSC), he/she must
People First Dependent Certification Process Each time an employee logs into People First to make an enrollment selection during open enrollment or because of a qualified status change (QSC), he/she must
Teacher Activities Page Directions
 Teacher Activities Page Directions The Teacher Activities Page provides teachers with access to student data that is protected by the federal Family Educational Rights and Privacy Act (FERPA). Teachers
Teacher Activities Page Directions The Teacher Activities Page provides teachers with access to student data that is protected by the federal Family Educational Rights and Privacy Act (FERPA). Teachers
Website Privacy Policy Statement. 1519 York Rd Lutherville, MD 21093. We may be reached via email at [email protected].
 Website Privacy Policy Statement This website juliereisler.com is operated by Empowered Living, LLC and this policy applies to all websites owned, operated, controlled and otherwise made available by Company,
Website Privacy Policy Statement This website juliereisler.com is operated by Empowered Living, LLC and this policy applies to all websites owned, operated, controlled and otherwise made available by Company,
Multi-Factor Authentication Job Aide
 To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
CLAIMS-BASED IDENTITY FOR WINDOWS
 CLAIMS-BASED IDENTITY FOR WINDOWS TECHNOLOGIES AND SCENARIOS DAVID CHAPPELL FEBRUARY 2011 SPONSORED BY MICROSOFT CORPORATION CONTENTS Understanding Claims-Based Identity... 3 The Problem: Working with
CLAIMS-BASED IDENTITY FOR WINDOWS TECHNOLOGIES AND SCENARIOS DAVID CHAPPELL FEBRUARY 2011 SPONSORED BY MICROSOFT CORPORATION CONTENTS Understanding Claims-Based Identity... 3 The Problem: Working with
Email. Daniel Zappala. CS 460 Computer Networking Brigham Young University
 Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
Email Daniel Zappala CS 460 Computer Networking Brigham Young University How Email Works 3/25 Major Components user agents POP, IMAP, or HTTP to exchange mail mail transfer agents (MTAs) mailbox to hold
SECURITY ANALYSIS OF A SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTER NETWORKS
 SECURITY ANALYSIS OF A SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTER NETWORKS Abstract: The Single sign-on (SSO) is a new authentication mechanism that enables a legal user with a single credential
SECURITY ANALYSIS OF A SINGLE SIGN-ON MECHANISM FOR DISTRIBUTED COMPUTER NETWORKS Abstract: The Single sign-on (SSO) is a new authentication mechanism that enables a legal user with a single credential
Introduction to Webmail. Apache County Library District April 2011
 Introduction to Webmail Apache County Library District April 2011 1 Review of terms we will be using in this tutorial: Single-click: This refers to a single click of the left mouse button. If you hold
Introduction to Webmail Apache County Library District April 2011 1 Review of terms we will be using in this tutorial: Single-click: This refers to a single click of the left mouse button. If you hold
Bypassing CAPTCHAs by Impersonating CAPTCHA Providers
 Bypassing CAPTCHAs by Impersonating CAPTCHA Providers Author: Gursev Singh Kalra Principal Consultant Foundstone Professional Services Table of Contents Bypassing CAPTCHAs by Impersonating CAPTCHA Providers...
Bypassing CAPTCHAs by Impersonating CAPTCHA Providers Author: Gursev Singh Kalra Principal Consultant Foundstone Professional Services Table of Contents Bypassing CAPTCHAs by Impersonating CAPTCHA Providers...
Website Privacy Policy Statement
 Website Privacy Policy Statement This website ( CRSF Website ) is operated by Cal Ripken, Sr. Foundation, Inc. ( Company ) and this policy applies to all websites owned, operated, controlled and otherwise
Website Privacy Policy Statement This website ( CRSF Website ) is operated by Cal Ripken, Sr. Foundation, Inc. ( Company ) and this policy applies to all websites owned, operated, controlled and otherwise
STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON
 STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON 1. Registering with Sabarimala Virtual Q Portal A user can register into the site after a few easy steps. A user needs to register with the site to be
STEPS TO REGISTER YOUR PROFILE AND BOOK THE COUPON 1. Registering with Sabarimala Virtual Q Portal A user can register into the site after a few easy steps. A user needs to register with the site to be
Security in an Increasingly Threatened World. SMS: A better way of doing Two Factor Authentication (2FA)
 Security in an Increasingly Threatened World SMS: A better way of doing Two Factor Authentication (2FA) January 2015 The Proliferation of The App World The revolution of the smart phone forever affected
Security in an Increasingly Threatened World SMS: A better way of doing Two Factor Authentication (2FA) January 2015 The Proliferation of The App World The revolution of the smart phone forever affected
1. What practices does Raleigh Medical Group, P.A. include? 2. Is my health information secure? Who has access to this information?
 Troubleshooting and Frequently Asked Questions FollowMyHealth Patient Portal 1. What practices does Raleigh Medical Group, P.A. include? 2. Is my health information secure? Who has access to this information?
Troubleshooting and Frequently Asked Questions FollowMyHealth Patient Portal 1. What practices does Raleigh Medical Group, P.A. include? 2. Is my health information secure? Who has access to this information?
Password regulations for Karolinska Institutet
 Password regulations for Karolinska Institutet Dnr 1-213/2015 Version 2.0 Applicable from 2015-05-18 Password regulations for Karolinska Institutet - Summary Purpose The main purpose of these regulations
Password regulations for Karolinska Institutet Dnr 1-213/2015 Version 2.0 Applicable from 2015-05-18 Password regulations for Karolinska Institutet - Summary Purpose The main purpose of these regulations
HUMAN RESOURCES POLICIES & PROCEDURES
 HUMAN RESOURCES POLICIES & PROCEDURES Policy title Application IT systems and social networking policy All employees and students CONTENTS PAGE Introduction and scope 2 General points 2 Authorisation to
HUMAN RESOURCES POLICIES & PROCEDURES Policy title Application IT systems and social networking policy All employees and students CONTENTS PAGE Introduction and scope 2 General points 2 Authorisation to
ensuring security the way how we do it
 ensuring security the way how we do it HUSTEF, 2015.11.18 Attila Tóth 1 Nokia Solutions and Networks 2014 Disclaimer The ideas, processes, tools are presented from a practitioner s point of view working
ensuring security the way how we do it HUSTEF, 2015.11.18 Attila Tóth 1 Nokia Solutions and Networks 2014 Disclaimer The ideas, processes, tools are presented from a practitioner s point of view working
Secure Email FAQs for External Stakeholders
 Secure Email FAQs for External Stakeholders Ver: 07 November 2012 What is secure email and why am I getting encrypted emails from the IPCC? Why do I have to register to open a Registered Envelope? What
Secure Email FAQs for External Stakeholders Ver: 07 November 2012 What is secure email and why am I getting encrypted emails from the IPCC? Why do I have to register to open a Registered Envelope? What
 The Truth About Information Security in Schools Region V 23 rd Annual Spring Conference -April 4th, 2013 Evan Francen CISSP, CISM, CCSK President of FRSecure, LLC Thank You for Attending! & Many Thanks
The Truth About Information Security in Schools Region V 23 rd Annual Spring Conference -April 4th, 2013 Evan Francen CISSP, CISM, CCSK President of FRSecure, LLC Thank You for Attending! & Many Thanks
2-Factor Verification Remote Access
 2-Factor Verification: Remote Access User Guide For technical assistance please call the IT Help desk @ 37300 1 How to Login to New Remote Access Portal! is implementing a new Remote Access Portal to enhance
2-Factor Verification: Remote Access User Guide For technical assistance please call the IT Help desk @ 37300 1 How to Login to New Remote Access Portal! is implementing a new Remote Access Portal to enhance
Spam Manager. User Guide
 Spam Manager User Guide Spam Manager User Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark
Spam Manager User Guide Spam Manager User Guide Documentation version: 1.0 Legal Notice Legal Notice Copyright 2013 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark
Network License File. Program CD Workstation
 Setting up Network Licensing for Visual Water Designer These directions will provide a detailed description of how to set up and run the network license version of Visual Water Designer. A network license
Setting up Network Licensing for Visual Water Designer These directions will provide a detailed description of how to set up and run the network license version of Visual Water Designer. A network license
This is the Department s service that creates and manages unique identities, manages usernames and passwords, and provides secure access to edupass.
 These FAQs are specifically tailored to edupass for Students (i.e. Students and those who manage student user names and passwords [i.e. Principals / Delegated Administrators]). General What is identity
These FAQs are specifically tailored to edupass for Students (i.e. Students and those who manage student user names and passwords [i.e. Principals / Delegated Administrators]). General What is identity
Information Security Basic Concepts
 Information Security Basic Concepts 1 What is security in general Security is about protecting assets from damage or harm Focuses on all types of assets Example: your body, possessions, the environment,
Information Security Basic Concepts 1 What is security in general Security is about protecting assets from damage or harm Focuses on all types of assets Example: your body, possessions, the environment,
