Shibboleth On-line Authentication System
|
|
|
- Rolf Marshall
- 10 years ago
- Views:
Transcription
1 Shibboleth On-line Authentication System Jon Browne Senior Consultant Drew Heald BSc (Hons), MPhil, MCP Systems Developer IBIS Business Consultants Ltd
2 Accessing a Web Resource Request Client W W W Server Response Client user accesses a free resource Client user is authenticated via a username and password to access a protected resource Client user is responsible for setting up that account
3 Web Resources for Education Educational establishments subscribe to resources on behalf of many users Parts of a given resource may only be accessible by some of the users in a given educational establishment The resources to which a given user has access change periodically
4 Authentication School Resource Students Directory/Database Student data Authentication Authorisation Directory/Database Student data Available to all Available to year 3 and above Available to year 6 and above
5 Authentication Common Issues Exposure of personal information High administrative burden Lack of traceability Password leakage Many passwords problem Resource accessibility is restricted Complicated to use
6 Shibboleth Aims to: Ensure no personal information is exposed unless necessary Minimise the number of passwords a user needs to remember Minimise the administrative burden Enable user traceability Be transparent to the user Enable access from any location
7 Shibboleth User Authentication Request LEA/RBC (Origin) Handle Service Resource (Target) SHIRE User Authentication User Attributes (LDAP/SQL) WAYF Bash Street St Trinians Hogwarts LGfL Oxford Resource(s) Attribute Authority SHAR
8 Shibboleth User Authentication 1.Request URL LEA/RBC (Origin) Resource (Target) Handle Service 5. Request URL + Handle + AA URL SHIRE 4. Username + password User Authentication User Attributes (LDAP/SQL) 9. User Attributes Attribute Authority 8. Handle returns User ID 3. Request URL + SHIRE URL WAYF Bash Street St Trinians Hogwarts LGfL Oxford 7. Request URL + Handle 10. Request URL + User Attributes 2. Request URL + SHIRE URL 6. Request URL + Handle + AA URL Resource(s) 11. User Attributes SHAR
9 Shibboleth User Authentication 1.Subsequent Request URL (Same Domain) LEA/RBC (Origin) Resource (Target) Handle Service User Authentication User Attributes (LDAP/SQL) WAYF Bash Street St Trinians Hogwarts LGfL Oxford SHIRE SHIRE has Cached Session & Handle = OK Resource(s) Attribute Authority SHAR SHAR has Cached Attributes = OK
10 Shibboleth User Authentication 1.Subsequent Request URL (Different Domain) LEA/RBC (Origin) Handle Service Resource (Target) SHIRE User Authentication User Attributes (LDAP/SQL) Handle returns User ID WAYF Bash Street St Trinians Hogwarts LGfL Oxford SHIRE has Cached Session & Handle = OK Resource(s) Attribute Authority Request New Domain Attributes Return New Domain Attributes SHAR SHAR has no Cached Attributes for the new Domain so ask AA
11 Shibboleth User Authentication LEA/RBC (Origin) Resource (Target) Handle Service SHIRE P o r t a l User Authentication User Attributes (LDAP/SQL) Resource(s) Attribute Authority SHAR
12 Shibboleth User Authentication Pros Low administrative burden Exposure of personal information under user s control Same identity for all resources User traceability Resources can be accessed from any location Cons (Possible) multi-stage authentication
13 Shibboleth Demonstration 1 7 Shibboleth Target Windows 2003 Server IIS 6.0 Browser WAYF Service Windows 2003 Server IIS 6.0 Shibboleth Origin Windows XP Pro Apache Server LDAP Directory (Active Directory) Windows 2003 Server
14 Shibboleth Demonstration Browser 1 7 Shibboleth Target Windows 2003 Server IIS 6.0 WAYF Service Shibboleth Origin Windows 2003 Server Apache Server LDAP Directory (Active Directory)
15 Shibboleth Then said they unto him, Say now Shibboleth: and he said Sibboleth: for he could not frame to pronounce it right. Then they took him, and slew him at the passages of Jordan: and there fell at that time of the Ephraimites forty and two thousand. Judges 12:6
Authentication Methods
 Authentication Methods Overview In addition to the OU Campus-managed authentication system, OU Campus supports LDAP, CAS, and Shibboleth authentication methods. LDAP users can be configured through the
Authentication Methods Overview In addition to the OU Campus-managed authentication system, OU Campus supports LDAP, CAS, and Shibboleth authentication methods. LDAP users can be configured through the
Web based single sign on. Caleb Racey Web development officer Webteam, customer services, ISS
 Web based single sign on Caleb Racey Web development officer Webteam, customer services, ISS Overview The need for single sign on (SSO) User and admin perspectives Current state off SSO provision pubcookie
Web based single sign on Caleb Racey Web development officer Webteam, customer services, ISS Overview The need for single sign on (SSO) User and admin perspectives Current state off SSO provision pubcookie
Configuring User Identification via Active Directory
 Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] User Identification Overview User Identification allows you to create security policies based
Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] User Identification Overview User Identification allows you to create security policies based
Windows XP Exchange Client Installation Instructions
 WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
WINDOWS XP with Outlook 2003 or Outlook 2007 1. Click the Start button and select Control Panel: 2. If your control panel looks like this: Click Switch to Classic View. 3. Double click Mail. 4. Click show
Web Meetings through VPN. Note: Conductor means person leading the meeting. Table of Contents. Instant Web Meetings with VPN (Conductor)...
 Table of Contents Instant Web Meetings with VPN (Conductor)...2 How to Set Up a Scheduled Web Meeting with VPN (Conductor)...6 How to Set Up a Support Web Meeting with GVSU VPN Service (Conductor)...15
Table of Contents Instant Web Meetings with VPN (Conductor)...2 How to Set Up a Scheduled Web Meeting with VPN (Conductor)...6 How to Set Up a Support Web Meeting with GVSU VPN Service (Conductor)...15
Shibboleth : An Open Source, Federated Single Sign-On System David E. Martin [email protected]
 Shibboleth : An Open Source, Federated Single Sign-On System David E. Martin [email protected] International Center for Advanced Internet Research Outline Security Mechanisms Access Control Schemes
Shibboleth : An Open Source, Federated Single Sign-On System David E. Martin [email protected] International Center for Advanced Internet Research Outline Security Mechanisms Access Control Schemes
External Authentication with WebCT. What We ll Discuss
 External Authentication with WebCT WebCT, Inc http://www.webct.com/ What We ll Discuss Introductions Terminology Authentication in WebCT External Authentication Custom Authentication Authorization in WebCT
External Authentication with WebCT WebCT, Inc http://www.webct.com/ What We ll Discuss Introductions Terminology Authentication in WebCT External Authentication Custom Authentication Authorization in WebCT
Agenda. Federation using ADFS and Extensibility options. Office 365 Identity overview. Federation and Synchronization
 Agenda Office 365 Identity overview 1 Federation and Synchronization Federation using ADFS and Extensibility options 2 3 What s New in Azure AD? Cloud Business App - Overview 4 Identity Management is
Agenda Office 365 Identity overview 1 Federation and Synchronization Federation using ADFS and Extensibility options 2 3 What s New in Azure AD? Cloud Business App - Overview 4 Identity Management is
Wireless Network Configuration Guide
 CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
CIT Table of Contents Introduction... 1 General Wireless Settings... 1 1. Windows XP Wireless Configuration... 2 2. Windows XP Intel Pro Wireless Tool... 7 3. Windows Vista Using the Windows Wireless Tools...
InfoRouter LDAP Authentication Web Service documentation for inforouter Versions 7.5.x & 8.x
 InfoRouter LDAP Authentication Web Service documentation for inforouter Versions 7.5.x & 8.x Active Innovations, Inc. Copyright 1998 2015 www.inforouter.com Installing the LDAP Authentication Web Service
InfoRouter LDAP Authentication Web Service documentation for inforouter Versions 7.5.x & 8.x Active Innovations, Inc. Copyright 1998 2015 www.inforouter.com Installing the LDAP Authentication Web Service
Web Applications Access Control Single Sign On
 Web Applications Access Control Single Sign On Anitha Chepuru, Assocaite Professor IT Dept, G.Narayanamma Institute of Technology and Science (for women), Shaikpet, Hyderabad - 500008, Andhra Pradesh,
Web Applications Access Control Single Sign On Anitha Chepuru, Assocaite Professor IT Dept, G.Narayanamma Institute of Technology and Science (for women), Shaikpet, Hyderabad - 500008, Andhra Pradesh,
CREDENTIAL MANAGER IN WINDOWS 7
 CREDENTIAL MANAGER IN WINDOWS 7 What is Credential Manager Whenever we try to access some resource, whether it is local or remote resource, Windows always validates our credentials to make sure we have
CREDENTIAL MANAGER IN WINDOWS 7 What is Credential Manager Whenever we try to access some resource, whether it is local or remote resource, Windows always validates our credentials to make sure we have
Connecting to Delta College Exchange services off-campus
 Connecting to Delta College Exchange services off-campus The following instructions are provided to document the client configuration used to connect to Microsoft Exchange services at Delta College from
Connecting to Delta College Exchange services off-campus The following instructions are provided to document the client configuration used to connect to Microsoft Exchange services at Delta College from
Livezilla How to Install on Shared Hosting http://www.jonathanmanning.com By: Jon Manning
 Livezilla How to Install on Shared Hosting By: Jon Manning This is an easy to follow tutorial on how to install Livezilla 3.2.0.2 live chat program on a linux shared hosting server using cpanel, linux
Livezilla How to Install on Shared Hosting By: Jon Manning This is an easy to follow tutorial on how to install Livezilla 3.2.0.2 live chat program on a linux shared hosting server using cpanel, linux
Chapter Thirteen (b): Using Active Directory Integration
 Chapter Thirteen (b): Using Active Directory Integration Summary of Chapter: How to add a User to your Net/Cache/SecurePilot that will match your Active Directory Security Group. How to set-up your Net/Cache/SecurePilot
Chapter Thirteen (b): Using Active Directory Integration Summary of Chapter: How to add a User to your Net/Cache/SecurePilot that will match your Active Directory Security Group. How to set-up your Net/Cache/SecurePilot
Massey University Wireless Network Client Configuration Mac OS X 10.6 10.9
 Massey University Wireless Network Client Configuration Mac OS X 10.6 10.9 MAC wireless network Requirements Information Technology Services You must have an active Massey username and password (i.e. you
Massey University Wireless Network Client Configuration Mac OS X 10.6 10.9 MAC wireless network Requirements Information Technology Services You must have an active Massey username and password (i.e. you
Remote Desktop Solution, (RDS), replacing CITRIX Home Access
 Remote Desktop Solution, (RDS), replacing CITRIX Home Access RDS Applications on a Computer Overview RDS has replaced citrix for remote access at home for College staff and pupils. This does not replace
Remote Desktop Solution, (RDS), replacing CITRIX Home Access RDS Applications on a Computer Overview RDS has replaced citrix for remote access at home for College staff and pupils. This does not replace
Please return this document to [email protected] when complete.
 Section 1 to be completed prior to quote Please return this document to [email protected] when complete. 1. Institution Name: 2. OCLC has selected an institution domain name for this server. This is
Section 1 to be completed prior to quote Please return this document to [email protected] when complete. 1. Institution Name: 2. OCLC has selected an institution domain name for this server. This is
How to Configure Active Directory based User Authentication
 How to Configure Active Directory based User Authentication You Must Have: Microsoft server with Active Directory configured. Windows 2000 Server is configured as Active Directory server in this example.
How to Configure Active Directory based User Authentication You Must Have: Microsoft server with Active Directory configured. Windows 2000 Server is configured as Active Directory server in this example.
Authentication and Single Sign On
 Contents 1. Introduction 2. Fronter Authentication 2.1 Passwords in Fronter 2.2 Secure Sockets Layer 2.3 Fronter remote authentication 3. External authentication through remote LDAP 3.1 Regular LDAP authentication
Contents 1. Introduction 2. Fronter Authentication 2.1 Passwords in Fronter 2.2 Secure Sockets Layer 2.3 Fronter remote authentication 3. External authentication through remote LDAP 3.1 Regular LDAP authentication
Entrust Managed Services PKI. Configuring secure LDAP with Domain Controller digital certificates
 Entrust Managed Services Entrust Managed Services PKI Configuring secure LDAP with Domain Controller digital certificates Document issue: 1.0 Date of issue: October 2009 Copyright 2009 Entrust. All rights
Entrust Managed Services Entrust Managed Services PKI Configuring secure LDAP with Domain Controller digital certificates Document issue: 1.0 Date of issue: October 2009 Copyright 2009 Entrust. All rights
Getting Started with AD/LDAP SSO
 Getting Started with AD/LDAP SSO Active Directory and LDAP single sign- on (SSO) with Syncplicity Business Edition accounts allows companies of any size to leverage their existing corporate directories
Getting Started with AD/LDAP SSO Active Directory and LDAP single sign- on (SSO) with Syncplicity Business Edition accounts allows companies of any size to leverage their existing corporate directories
Secure Global Desktop (SGD)
 Secure Global Desktop (SGD) Table of Contents Checking your Java Version...3 Preparing Your Desktop Computer...3 Accessing SGD...5 Logging into SGD...6 Using SGD to Access Your Desktop...7 Using SGD to
Secure Global Desktop (SGD) Table of Contents Checking your Java Version...3 Preparing Your Desktop Computer...3 Accessing SGD...5 Logging into SGD...6 Using SGD to Access Your Desktop...7 Using SGD to
How to Configure Outlook 2010 E-mail Client for Exchange
 LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
LAUSD IT Help Desk How to Configure Outlook 2010 E-mail Client for Exchange (03/04/2012) LAUSD IT Help Desk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Table of Contents Configure Outlook 2010 for
Cloud Identity Management Tool Quick Start Guide
 Cloud Identity Management Tool Quick Start Guide Software version 2.0.0 October 2013 General Information: [email protected] Online Support: [email protected] Copyright 2013 CionSystems Inc., All
Cloud Identity Management Tool Quick Start Guide Software version 2.0.0 October 2013 General Information: [email protected] Online Support: [email protected] Copyright 2013 CionSystems Inc., All
External Authentication with Cisco ASA Authenticating Users Using SecurAccess Server by SecurEnvoy
 External Authentication with Cisco ASA Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale Reading
External Authentication with Cisco ASA Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale Reading
www.nexuswebsites.co.uk Professional Mailbox Email Software Setup Guide
 Professional Mailbox Email Software Setup Guide Table of contents Before you start... 2 Setting up Outlook 2010... 2 Using Autodiscover to configure Outlook 2010... 2 The Autodiscover wizard has not worked...
Professional Mailbox Email Software Setup Guide Table of contents Before you start... 2 Setting up Outlook 2010... 2 Using Autodiscover to configure Outlook 2010... 2 The Autodiscover wizard has not worked...
Web Application Report
 Web Application Report This report includes important security information about your Web Application. Security Report This report was created by IBM Rational AppScan 8.5.0.1 11/14/2012 8:52:13 AM 11/14/2012
Web Application Report This report includes important security information about your Web Application. Security Report This report was created by IBM Rational AppScan 8.5.0.1 11/14/2012 8:52:13 AM 11/14/2012
NeoMail Guide. Neotel (Pty) Ltd
 NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
NeoMail Guide Neotel (Pty) Ltd NeoMail Connect Guide... 1 1. POP and IMAP Client access... 3 2. Outlook Web Access... 4 3. Outlook (IMAP and POP)... 6 4. Outlook 2007... 16 5. Outlook Express... 24 1.
Middleware integration in the Sympa mailing list software. Olivier Salaün - CRU
 Middleware integration in the Sympa mailing list software Olivier Salaün - CRU 1. Sympa, its middleware connectors 2. Sympa web authentication 3. CAS authentication 4. Shibboleth authentication 5. Sympa
Middleware integration in the Sympa mailing list software Olivier Salaün - CRU 1. Sympa, its middleware connectors 2. Sympa web authentication 3. CAS authentication 4. Shibboleth authentication 5. Sympa
Customer Tips. Configuring Color Access on the WorkCentre 7328/7335/7345 using Windows Active Directory. for the user. Overview
 Xerox Multifunction Devices Customer Tips February 13, 2008 This document applies to the stated Xerox products. It is assumed that your device is equipped with the appropriate option(s) to support the
Xerox Multifunction Devices Customer Tips February 13, 2008 This document applies to the stated Xerox products. It is assumed that your device is equipped with the appropriate option(s) to support the
5. For Display name, Your Full Name or the name you want to appear in the from box when writing or responding to e-mail click Next
 Setting up Outlook Express. 1. Open Outlook Express 2. From Tools menu a. Choose Accounts. 3. Click Add button a. Choose Mail 5. For Display name, Your Full Name or the name you want to appear in the from
Setting up Outlook Express. 1. Open Outlook Express 2. From Tools menu a. Choose Accounts. 3. Click Add button a. Choose Mail 5. For Display name, Your Full Name or the name you want to appear in the from
Connecting to the University Wireless Network
 Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Connecting to the University Wireless Network Wifi is available to staff and registered students of University in certain areas of the three campuses of the University. This area of coverage will be expanded
Egnyte Single Sign-On (SSO) Configuration for Active Directory Federation Services (ADFS)
 w w w. e g n y t e. c o m Egnyte Single Sign-On (SSO) Configuration for Active Directory Federation Services (ADFS) To set up ADFS so that your employees can access Egnyte using their ADFS credentials,
w w w. e g n y t e. c o m Egnyte Single Sign-On (SSO) Configuration for Active Directory Federation Services (ADFS) To set up ADFS so that your employees can access Egnyte using their ADFS credentials,
Single Sign-On: Reviewing the Field
 Outline Michael Grundmann Erhard Pointl Johannes Kepler University Linz January 16, 2009 Outline 1 Why Single Sign-On? 2 3 Criteria Categorization 4 Overview shibboleth 5 Outline Why Single Sign-On? Why
Outline Michael Grundmann Erhard Pointl Johannes Kepler University Linz January 16, 2009 Outline 1 Why Single Sign-On? 2 3 Criteria Categorization 4 Overview shibboleth 5 Outline Why Single Sign-On? Why
Authentication Integration
 Authentication Integration VoiceThread provides multiple authentication frameworks allowing your organization to choose the optimal method to implement. This document details the various available authentication
Authentication Integration VoiceThread provides multiple authentication frameworks allowing your organization to choose the optimal method to implement. This document details the various available authentication
Using Internet or Windows Explorer to Upload Your Site
 Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
Using Internet or Windows Explorer to Upload Your Site This article briefly describes what an FTP client is and how to use Internet Explorer or Windows Explorer to upload your Web site to your hosting
How to use Certificate in Outlook Express
 How to use Certificate in Outlook Express Macau Post esigntrust Version. 2006-01.01p Agenda Configure Outlook Express for using esigntrust Certificate Use certificate to sign email Use Outlook Express
How to use Certificate in Outlook Express Macau Post esigntrust Version. 2006-01.01p Agenda Configure Outlook Express for using esigntrust Certificate Use certificate to sign email Use Outlook Express
Managing User Accounts
 Managing User Accounts This chapter includes the following sections: Active Directory, page 1 Configuring Local Users, page 3 Viewing User Sessions, page 5 Active Directory Active Directory is a technology
Managing User Accounts This chapter includes the following sections: Active Directory, page 1 Configuring Local Users, page 3 Viewing User Sessions, page 5 Active Directory Active Directory is a technology
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail
 Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Instructions: Configuring Outlook 2003 with Exchange 2010 on the FIUMail Environment Some users have been using Outlook 2003 with their IMAP or POP account, and already have a profile set up. For those
Active Directory Integration
 Active Directory Integration Last updated March 2016 Contents Introduction:... 2 Administration configuration set up:... 2 Configuring for a single OU import... 3 User Importing... 3 Active Directory and
Active Directory Integration Last updated March 2016 Contents Introduction:... 2 Administration configuration set up:... 2 Configuring for a single OU import... 3 User Importing... 3 Active Directory and
FireBLAST Email Marketing Solution v2
 Installation Guide WELCOME to fireblast, one of the Industry s leading Email Marketing Software Solutions for your business. Whether you are creating a small email campaign, or you are looking to upgrade
Installation Guide WELCOME to fireblast, one of the Industry s leading Email Marketing Software Solutions for your business. Whether you are creating a small email campaign, or you are looking to upgrade
Stoneware Inc. Hyland Software OnBase. Stoneware, Inc.
 Stoneware Inc. Hyland Software OnBase Stoneware, Inc. Configuration Sheet Date: March 2005 Introduction This document provides the information necessary to secure and provide single sign-on for Hyland
Stoneware Inc. Hyland Software OnBase Stoneware, Inc. Configuration Sheet Date: March 2005 Introduction This document provides the information necessary to secure and provide single sign-on for Hyland
Configuring Color Access on the WorkCentre 7120 Using Microsoft Active Directory Customer Tip
 Configuring Color Access on the WorkCentre 7120 Using Microsoft Active Directory Customer Tip October 21, 2010 Overview This document describes how to limit access to color copying and printing on the
Configuring Color Access on the WorkCentre 7120 Using Microsoft Active Directory Customer Tip October 21, 2010 Overview This document describes how to limit access to color copying and printing on the
Installing TestNav Mac with Apple Remote Desktop
 Installing TestNav Mac with Apple Remote Desktop 1 2 3 Getting TestNav Installation from Servicedesk 1.1 Connect to Servicedesk 4 1.2 Download Package to Desktop 7 Installing TestNav 2.1 Add Computers
Installing TestNav Mac with Apple Remote Desktop 1 2 3 Getting TestNav Installation from Servicedesk 1.1 Connect to Servicedesk 4 1.2 Download Package to Desktop 7 Installing TestNav 2.1 Add Computers
Adobe Connect LMS Integration for Blackboard Learn 9
 Adobe Connect LMS Integration for Blackboard Learn 9 Install Guide Introduction The Adobe Connect LMS Integration for Blackboard Learn 9 gives Instructors, Teaching Assistants and Course Builders the ability
Adobe Connect LMS Integration for Blackboard Learn 9 Install Guide Introduction The Adobe Connect LMS Integration for Blackboard Learn 9 gives Instructors, Teaching Assistants and Course Builders the ability
Configuring Microsoft Active Directory for Integration with NextPage NXT 3 Access Control
 Configuring Microsoft Active Directory for Integration with NextPage NXT 3 Access Control This document explains how to configure Microsoft Active Directory for integration with NXT 3 access control. Step
Configuring Microsoft Active Directory for Integration with NextPage NXT 3 Access Control This document explains how to configure Microsoft Active Directory for integration with NXT 3 access control. Step
Configuring Thunderbird with UEA Exchange 2007:
 Configuring Thunderbird with UEA Exchange 2007: This document covers Thunderbird v10.0.2 please contact [email protected] if you require an upgrade. Mail Account Setup. Step 1: Open Thunderbird, you should
Configuring Thunderbird with UEA Exchange 2007: This document covers Thunderbird v10.0.2 please contact [email protected] if you require an upgrade. Mail Account Setup. Step 1: Open Thunderbird, you should
IP Phone Service Administration and Subscription
 CHAPTER 6 IP Phone Service Administration and Subscription Cisco CallManager administrators maintain the list of services to which users can subscribe. These sections provide details about administering
CHAPTER 6 IP Phone Service Administration and Subscription Cisco CallManager administrators maintain the list of services to which users can subscribe. These sections provide details about administering
How To Integrate Watchguard Xtm With Secur Access With Watchguard And Safepower 2Factor Authentication On A Watchguard 2T (V2) On A 2Tv 2Tm (V1.2) With A 2F
 External Authentication with Watchguard XTM Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington Business Park
External Authentication with Watchguard XTM Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington Business Park
OpenLDAP Oracle Enterprise Gateway Integration Guide
 An Oracle White Paper June 2011 OpenLDAP Oracle Enterprise Gateway Integration Guide 1 / 29 Disclaimer The following is intended to outline our general product direction. It is intended for information
An Oracle White Paper June 2011 OpenLDAP Oracle Enterprise Gateway Integration Guide 1 / 29 Disclaimer The following is intended to outline our general product direction. It is intended for information
Case Study - Configuration between NXC2500 and LDAP Server
 Case Study - Configuration between NXC2500 and LDAP Server 1 1. Scenario:... 3 2. Topology:... 4 3. Step-by-step Configurations:...4 a. Configure NXC2500:...4 b. Configure LDAP setting on NXC2500:...10
Case Study - Configuration between NXC2500 and LDAP Server 1 1. Scenario:... 3 2. Topology:... 4 3. Step-by-step Configurations:...4 a. Configure NXC2500:...4 b. Configure LDAP setting on NXC2500:...10
External Authentication with Cisco VPN 3000 Concentrator Authenticating Users Using SecurAccess Server by SecurEnvoy
 External Authentication with Cisco VPN 3000 Concentrator Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
External Authentication with Cisco VPN 3000 Concentrator Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
External Authentication with Windows 2003 Server with Routing and Remote Access service Authenticating Users Using SecurAccess Server by SecurEnvoy
 External Authentication with Windows 2003 Server with Routing and Remote Access service Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845
External Authentication with Windows 2003 Server with Routing and Remote Access service Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845
SCADA Security. Enabling Integrated Windows Authentication For CitectSCADA Web Client. Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.
 Enabling Integrated Windows Authentication For CitectSCADA Web Client Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.xx Summary: What is the difference between Basic Authentication and Windows
Enabling Integrated Windows Authentication For CitectSCADA Web Client Applies To: CitectSCADA 6.xx and 7.xx VijeoCitect 6.xx and 7.xx Summary: What is the difference between Basic Authentication and Windows
Integrating Web Applications with Shibboleth
 Integrating Web Applications with Shibboleth Application Authentication Done Right July 11, 2016 Eric Goodman, UCOP IAM Architect Jeffrey Crawford, UCSC Application Admin What is Shibboleth? Shibboleth
Integrating Web Applications with Shibboleth Application Authentication Done Right July 11, 2016 Eric Goodman, UCOP IAM Architect Jeffrey Crawford, UCSC Application Admin What is Shibboleth? Shibboleth
SPC Connect Configuration Manual V1.0
 SPC Connect Configuration Manual V1.0 I-200090-1 28.11.2014 Copyright Copyright Technical specifications and availability subject to change without notice. Copyright Siemens AB We reserve all rights in
SPC Connect Configuration Manual V1.0 I-200090-1 28.11.2014 Copyright Copyright Technical specifications and availability subject to change without notice. Copyright Siemens AB We reserve all rights in
Only LDAP-synchronized users can access SAML SSO-enabled web applications. Local end users and applications users cannot access them.
 This chapter provides information about the Security Assertion Markup Language (SAML) Single Sign-On feature, which allows administrative users to access certain Cisco Unified Communications Manager and
This chapter provides information about the Security Assertion Markup Language (SAML) Single Sign-On feature, which allows administrative users to access certain Cisco Unified Communications Manager and
Email Client configuration and migration Guide Setting up Thunderbird 3.1
 Email Client configuration and migration Guide Setting up Thunderbird 3.1 1. Open Mozilla Thunderbird. : 1. On the Edit menu, click Account Settings. 2. On the Account Settings page, under Account Actions,
Email Client configuration and migration Guide Setting up Thunderbird 3.1 1. Open Mozilla Thunderbird. : 1. On the Edit menu, click Account Settings. 2. On the Account Settings page, under Account Actions,
Computer Networking LAB 2 HTTP
 Computer Networking LAB 2 HTTP 1 OBJECTIVES The basic GET/response interaction HTTP message formats Retrieving large HTML files Retrieving HTML files with embedded objects HTTP authentication and security
Computer Networking LAB 2 HTTP 1 OBJECTIVES The basic GET/response interaction HTTP message formats Retrieving large HTML files Retrieving HTML files with embedded objects HTTP authentication and security
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Remote Terminal Service (RTS) User Guide (Version 2.1)
 Remote Terminal Service (RTS) User Guide (Version 2.1) Page 1 Table of Content Content Page 1 Introduction 3 2 Prerequisite 3 3 Logon Corporate Network via Internet 4 4 Download and Install RTS Client
Remote Terminal Service (RTS) User Guide (Version 2.1) Page 1 Table of Content Content Page 1 Introduction 3 2 Prerequisite 3 3 Logon Corporate Network via Internet 4 4 Download and Install RTS Client
Use Enterprise SSO as the Credential Server for Protected Sites
 Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Webthority HOW TO Use Enterprise SSO as the Credential Server for Protected Sites This document describes how to integrate Webthority with Enterprise SSO version 8.0.2 or 8.0.3. Webthority can be configured
Follow these easy instructions to list your business on the BEC Australia National Business Directory.
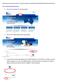 Follow these easy instructions to list your business on the BEC Australia National Business Directory. Go to www.becaustralia.org.au 1. Click on the Directory tab (see below) 2. Click on the Add listing
Follow these easy instructions to list your business on the BEC Australia National Business Directory. Go to www.becaustralia.org.au 1. Click on the Directory tab (see below) 2. Click on the Add listing
Exchange 2010. Outlook Profile/POP/IMAP/SMTP Setup Guide
 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide September, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Exchange 2010 Outlook Profile Configuration... 1 Outlook Profile
Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide September, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Exchange 2010 Outlook Profile Configuration... 1 Outlook Profile
Microsoft Active Directory Oracle Enterprise Gateway Integration Guide
 An Oracle White Paper May 2011 Microsoft Active Directory Oracle Enterprise Gateway Integration Guide 1/33 Disclaimer The following is intended to outline our general product direction. It is intended
An Oracle White Paper May 2011 Microsoft Active Directory Oracle Enterprise Gateway Integration Guide 1/33 Disclaimer The following is intended to outline our general product direction. It is intended
About Me. #ccceu. @shapeblue. Software Architect with ShapeBlue Specialise in. 3 rd party integrations and features in CloudStack
 Software Architect with ShapeBlue Specialise in. 3 rd party integrations and features in CloudStack About Me KVM, API, DB, Upgrades, SystemVM, Build system, various subsystems Contributor and Committer
Software Architect with ShapeBlue Specialise in. 3 rd party integrations and features in CloudStack About Me KVM, API, DB, Upgrades, SystemVM, Build system, various subsystems Contributor and Committer
PAHO Self-Service Password Management Quick Reference Guide December 2014
 PAHO Self-Service Password Management Quick Reference Guide December 2014 Information Technology Services (ITS) PAHO Network Password Management and Recovery Using ADSelfService Quick Reference Guide NOTE:
PAHO Self-Service Password Management Quick Reference Guide December 2014 Information Technology Services (ITS) PAHO Network Password Management and Recovery Using ADSelfService Quick Reference Guide NOTE:
Application Note. ShoreTel 9: Active Directory Integration. Integration checklist. AN-10233 June 2009
 Application Note AN-10233 June 2009 ShoreTel 9: Active Directory Integration This application note outlines the configuration required to prepare a customer s Microsoft Active Directory environment for
Application Note AN-10233 June 2009 ShoreTel 9: Active Directory Integration This application note outlines the configuration required to prepare a customer s Microsoft Active Directory environment for
Transferring Files to the CU2 Global Secure FTP Site. Login & Access Application Preparation Guide.
 CU2 Global Pty Ltd The Global Data Conversion Experts ConvertU2 Technologies The Data and Software Conversion Experts Transferring Files to the CU2 Global Secure FTP Site. Login & Access Application Preparation
CU2 Global Pty Ltd The Global Data Conversion Experts ConvertU2 Technologies The Data and Software Conversion Experts Transferring Files to the CU2 Global Secure FTP Site. Login & Access Application Preparation
Active Directory Requirements and Setup
 Active Directory Requirements and Setup The information contained in this document has been written for use by Soutron staff, clients, and prospective clients. Soutron reserves the right to change the
Active Directory Requirements and Setup The information contained in this document has been written for use by Soutron staff, clients, and prospective clients. Soutron reserves the right to change the
Integrating EJBCA and OpenSSO
 Integrating EJBCA and OpenSSO EJBCA is an Enterprise PKI Certificate Authority issuing certificates to users, servers and devices. In an organization certificate can be used for strong authentication.
Integrating EJBCA and OpenSSO EJBCA is an Enterprise PKI Certificate Authority issuing certificates to users, servers and devices. In an organization certificate can be used for strong authentication.
User Management and Sharing in sciebo, the Academic Cloud Storage Service in NRW Holger Angenent. University of Münster
 User Management and Sharing in sciebo, the Academic Cloud Storage Service in NRW Holger Angenent University of Münster 2 > sciebo sciebo is the brand name, short for science box Sync and share service
User Management and Sharing in sciebo, the Academic Cloud Storage Service in NRW Holger Angenent University of Münster 2 > sciebo sciebo is the brand name, short for science box Sync and share service
How to connect to the diamonds wireless network with Vista.
 How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
How to connect to the diamonds wireless network with Vista. This configuration guide requires the use of Windows to configure the wireless settings. 1. Click on the START menu and click the Control Panel.
Integrating Webalo with LDAP or Active Directory
 Integrating Webalo with LDAP or Active Directory Webalo can be integrated with an external directory to identify valid Webalo users and then authenticate them to the Webalo appliance. Integration with
Integrating Webalo with LDAP or Active Directory Webalo can be integrated with an external directory to identify valid Webalo users and then authenticate them to the Webalo appliance. Integration with
This document is to explain how to setup Outlook to use our Cloud Based Exchange service.
 Introduction This document is to explain how to setup Outlook to use our Cloud Based Exchange service. Prerequisites Before we begin you will need; Your Cloud Exchange Email Address, The Password for your
Introduction This document is to explain how to setup Outlook to use our Cloud Based Exchange service. Prerequisites Before we begin you will need; Your Cloud Exchange Email Address, The Password for your
netld External Authentication Setup Guide
 netld External Authentication Setup Guide Overview netld is able to integrate with authentication servers such as Active Directory and FreeRADIUS. When using this integration, you do not need to create
netld External Authentication Setup Guide Overview netld is able to integrate with authentication servers such as Active Directory and FreeRADIUS. When using this integration, you do not need to create
UNIL Administration. > Many databases and applications:
 Directories at UNIL UNIL Administration > Many databases and applications: > ResHus: contracts with Etat de Vaud > SAP: other contracts > Immat: students > Physical persons in a single table > Moral persons
Directories at UNIL UNIL Administration > Many databases and applications: > ResHus: contracts with Etat de Vaud > SAP: other contracts > Immat: students > Physical persons in a single table > Moral persons
Summary. How-To: Active Directory Integration. April, 2006
 How-To How-To Integrate CanIt-PRO with Active Directory: April, 2006 Summary Several organizations use Active Directory to manage their user accounts. This paper describes how to integrate CanIt-PRO with
How-To How-To Integrate CanIt-PRO with Active Directory: April, 2006 Summary Several organizations use Active Directory to manage their user accounts. This paper describes how to integrate CanIt-PRO with
Managing User Accounts
 Managing User Accounts This chapter includes the following sections: Configuring Local Users, page 1 Active Directory, page 2 Viewing User Sessions, page 6 Configuring Local Users Before You Begin You
Managing User Accounts This chapter includes the following sections: Configuring Local Users, page 1 Active Directory, page 2 Viewing User Sessions, page 6 Configuring Local Users Before You Begin You
Microsoft Outlook Web Access 2013 Authenticating Users Using SecurAccess Server by SecurEnvoy
 Microsoft Outlook Web Access 2013 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale Reading RG7
Microsoft Outlook Web Access 2013 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale Reading RG7
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2013 for Windows... 3 Outlook for Mac 2011... 4 Mac OS X 10.6+... 4 iphone
Remote Working Service Remote Access - VDI User Instructions
 Remote Working Service Remote Access - VDI User Instructions Created By: Devilliers Swart Created Date: 12/02/14 Document Version 1.5a Page 1 Prerequisites Check List Please note these instructions are
Remote Working Service Remote Access - VDI User Instructions Created By: Devilliers Swart Created Date: 12/02/14 Document Version 1.5a Page 1 Prerequisites Check List Please note these instructions are
Installation Guide v3.0
 Installation Guide v3.0 Shepherd TimeClock 4465 W. Gandy Blvd. Suite 800 Tampa, FL 33611 Phone: 813-882-8292 Fax: 813-839-7829 http://www.shepherdtimeclock.com The information contained in this document
Installation Guide v3.0 Shepherd TimeClock 4465 W. Gandy Blvd. Suite 800 Tampa, FL 33611 Phone: 813-882-8292 Fax: 813-839-7829 http://www.shepherdtimeclock.com The information contained in this document
Enroll a Windows Phone 8 Device
 Enroll a Windows Phone 8 Device Download Process Enrolling your Windows 8 device is a quick and easy process that takes around 2 minutes to complete. Your IT administrator will send you a MaaS360 enrollment
Enroll a Windows Phone 8 Device Download Process Enrolling your Windows 8 device is a quick and easy process that takes around 2 minutes to complete. Your IT administrator will send you a MaaS360 enrollment
Data Collection Agent for Active Directory
 Data Collection Agent for Active Directory Installation Guide Version 7.5 - September 2015 This guide provides quick instructions for the installation of Data Collection Agent Active Directory, from an
Data Collection Agent for Active Directory Installation Guide Version 7.5 - September 2015 This guide provides quick instructions for the installation of Data Collection Agent Active Directory, from an
Installation Guide. (You can get these files from http://www.clariostechnology.com/intelligentreports/install)
 Clarios Technology Pty. Ltd. Intelligent Reporter Installation Guide Installing Intelligent Reports JIRA plugin The Intelligent Reports plugin for JIRA is available through the Atlassian Marketplace. Follow
Clarios Technology Pty. Ltd. Intelligent Reporter Installation Guide Installing Intelligent Reports JIRA plugin The Intelligent Reports plugin for JIRA is available through the Atlassian Marketplace. Follow
External authentication with Fortinet Fortigate UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy
 External authentication with Fortinet Fortigate UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
External authentication with Fortinet Fortigate UTM appliances Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 1210 Parkview Arlington
Contents. 1. Infrastructure
 1. Infrastructure 2. Configuration Contents a. Join the Web Server to the Domain Controller b. Install PHP, mysql, apache c. Install and configure wordpress and virtual host d. Install and configure moodle
1. Infrastructure 2. Configuration Contents a. Join the Web Server to the Domain Controller b. Install PHP, mysql, apache c. Install and configure wordpress and virtual host d. Install and configure moodle
Access to Webmail services via a Non Trust Computer
 Access to Webmail services via a Non Trust Computer Aintree Outlook Web Access has been provided via the AppGate SSL Portal, this service can be accessed from any computer on the Internet. Two factor SMS
Access to Webmail services via a Non Trust Computer Aintree Outlook Web Access has been provided via the AppGate SSL Portal, this service can be accessed from any computer on the Internet. Two factor SMS
SchoolBooking SSO Integration Guide
 SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
SchoolBooking SSO Integration Guide Before you start This guide has been written to help you configure SchoolBooking to operate with SSO (Single Sign on) Please treat this document as a reference guide,
HGC SUPERHUB HOSTED EXCHANGE EMAIL
 HGC SUPERHUB HOSTED EXCHANGE EMAIL OUTLOOK 2010 MAPI MANUALLY SETUP GUIDE MICROSOFT HOSTED EXCHANGE V2013.5 Table of Contents 1. Get Started... 1 1.1 Start from Setting up an Email account... 1 1.2 Start
HGC SUPERHUB HOSTED EXCHANGE EMAIL OUTLOOK 2010 MAPI MANUALLY SETUP GUIDE MICROSOFT HOSTED EXCHANGE V2013.5 Table of Contents 1. Get Started... 1 1.1 Start from Setting up an Email account... 1 1.2 Start
