How do I share a file with a friend or trusted associate?
|
|
|
- Maximillian Melton
- 10 years ago
- Views:
Transcription
1 Sharing Information How do I share a file with a friend or trusted associate? Sharing a file in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information with loved ones and other trusted friends or service providers. Before you want to share a file, make sure that your computer is connected to internet. Once the computer is connected to internet, simply follow the steps given below to share a file with a friend or trusted associate. 1. To share a file, click the Share button in the tool bar. 2. The Share Documents by dialog will be displayed. You can encrypted copy of whatever IformationSAFE data you wish them to access. To a single page copy of one of your records, click the check box, Send This File. NOTE: If your recipient is not expecting this , it might be prudent to let him know you ve sent it. Occasionally from an unknown third party such as InformationSAFE can be accidentally caught in a recipient s spam filter. Informing the recipient of the will allow them to check for the message in the event it does not show up in their Inbox automatically. 3. Select the file that you want to share from the drop down list. 4. Then click the Continue button at the end. 5. The Send Document dialog will be displayed. 1
2 6. Enter the Name of the recipient to whom you wish to send the file. 7. Enter the right id of the recipient to send the file. 8. If you wish, you can send any instruction or Message along with the file. Simply delete default message and then add your message or edit default message. If you don t change anything, the default message is sent to the recipient along with the file. 9. Then for security reasons, provide at least 1 question along with the answer that must be provided by the recipient in order to access the file that you have shared. You can provide up to 3 security questions with answers for highly secured sharing. 10. To preview what you are sending, click the Preview button. 11. Finally click the Send button at the end to send the file for sharing. 12. The success message will be displayed. You are also asked whether you would like to send file to another recipient or not. If you wish to continue sending the file to more recipients, click the Yes button else click the No button to end the sharing process. How do I share a category of files with a friend or trusted associate? Sharing a category of files in InformationSAFE is easy. The share utility in InformationSAFE allows you to securely share your information with loved ones and other trusted friends or service providers. 1. Before you want to share a category of files, make sure that your computer is connected to internet. 2. Once the computer is connected to internet, simply follow the steps given below to share a category of files with a friend or trusted associate. 3. To share a category of files, click the Share button in the tool bar. 4. The Share Documents by dialog will be displayed. You can 2
3 encrypted copy of whatever InformationSAFE data you wish them to access. To a category of files, click the check box, Send This Category. 5. Select the category of files that you want to share from the drop down list. 6. Then click the Continue button at the end. 7. The Send Document dialog will be displayed. 8. Enter the Name of the recipient to whom you wish to send the category of files. 9. Enter the right id of the recipient to send the category of files. 10. If you wish, you can send any instruction or Message along with the category of files. Simply delete default message and then add your message or edit default message. If you don t change anything, the default message is sent to the recipient along with the category of files. 11. Then for security reasons, provide at least 1 question along with the answer that must be provided by the recipient in order to access the category of files that you have shared. You can provide up to 3 security questions with answers for highly secured sharing. 12. To preview what you are sending, click the Preview button. 13. Finally click the Send button at the end to send the category of files for sharing. 14. The success message will be displayed. You are also asked whether you would like to send the category of files to another recipient or not. If you wish to continue sending files to more recipients, click the Yes button else click the No button to end the sharing process. How do I share an entire InformationSAFE Reference Book via with a friend or trusted associate? Sharing an entire InformationSAFE reference book is easy. The share utility in InformationSAFE allows you to securely share your information with loved ones and other trusted friends or service providers. 3
4 Before you want to share an entire InformationSAFE reference book, make sure that your computer is connected to internet. Once the computer is connected to internet, simply follow the steps given below to share an entire InformationSAFE reference book with a friend or trusted associate. 1. To share an entire InformationSAFE reference book, click the Share button in the tool bar. 2. The Share Documents by dialog will be displayed. You can encrypted copy of whatever InformationSAFE data you wish them to access. To an entire InformationSAFE reference book, click the check box, Send This Reference Book. 3. Then click the Continue button at the end. 4. The Send Document dialog will be displayed. 5. Enter the Name of the recipient to whom you wish to send an entire InformationSAFE reference book. 6. Enter the right id of the recipient to send an entire InformationSAFE reference book. 7. If you wish, you can send any instruction or Message along with the entire InformationSAFE reference book. Simply delete default message and then add your message or edit default message. If you don t change anything, the default message is sent to the recipient along with the entire InformationSAFE reference book. 8. Then for security reasons, provide at least 1 question along with the answer that must be provided by the recipient in order to access the entire InformationSAFE reference book that you have shared. You can provide up to 3 security questions with answers for highly secured sharing. 9. To preview what you are sending, click the Preview button. 10. Finally click the Send button at the end to send the entire InformationSAFE reference book for sharing. 4
5 11. The success message will be displayed. You are also asked whether you would like to send the entire InformationSAFE reference book to another recipient or not. If you wish to continue sending the entire InformationSAFE reference book to more recipients, click the Yes button else click the No button to end the sharing process. How do I share my login username and password with a friend or trusted associate? The share utility in InformationSAFE allows you to securely share your login username and password information with loved ones and other trusted friends or service providers. Before you want to share your login username and password information, make sure that your computer is connected to internet. Once the computer is connected to internet, simply follow the steps given below to share your login username and password information with a friend or trusted associate. 1. To share your login username and password information, click the Share button in the tool bar. 2. The Share Documents by dialog will be displayed. You can encrypted copy of whatever InformationSAFE data you wish them to access. To your login username and password information, click the check box, Send My Login Username and Password. 3. Then click the Continue button at the end. 4. The Send Document dialog will be displayed. 5. Enter the Name of the recipient to whom you wish to send your login username and password information. 6. Enter the right id of the recipient to send your login username and password information. 5
6 7. If you wish, you can send any instruction or Message along with your login username and password information. Simply delete default message and then add your message or edit default message. If you don t change anything, the default message is sent to the recipient along with your login username and password information. 8. Then for security reasons, provide at least 1 question along with the answer that must be provided by the recipient in order to access your login username and password information that you have shared. You can provide up to 3 security questions with answers for highly secured sharing. 9. To preview what you are sending, click the Preview button. 10. Finally click the Send button at the end to send your login username and password information for sharing. 11. The success message will be displayed. You are also asked whether you would like to send your login username and password information to another recipient or not. If you wish to continue sending your login username and password information to more recipients, click the Yes button else click the No button to end the sharing process. How do I see if a recipient has accessed shared logon information? 1. Click the Contacts button in the tool bar. 2. Select the recipient from your contacts list and then click the History button in the right side column. 3. If the recipient has made login attempts, the list of login attempts will be displayed along with the details such as the Login Date, IP Address of the system he logged in and also whether the login attempt was successful or not. 6
7 How do I cancel a recipient s ability to retrieve a shared document? 1. Click the Contacts button in the tool bar. 2. Select the recipient name in the contacts list and then click the Access button in the right side column. 3. Under Permissions section, click the None link above the View column. By not giving permission to view your information, you are canceling the recipient s ability to retrieve a shared document. How do I cancel a recipient s ability to access shared logon information? 1. Click the Contacts button in the tool bar. 2. Select the recipient name in the contacts list and then click the Access button in the right side column. 3. Under Permissions section, click the None link above the Change column. By not giving permission to change your information, you are canceling the recipient s ability to access shared logon information. 7
Email - Spam Spam Email Firewall How Does the Spam Firewall Work? Getting Started username Create New Password
 Email - Spam Spam Email Firewall ODU s Information Services has implemented a Spam Firewall to help you manage spam e-mail from Internet senders. Generally defined, spam e-mail is an unsolicited mailing,
Email - Spam Spam Email Firewall ODU s Information Services has implemented a Spam Firewall to help you manage spam e-mail from Internet senders. Generally defined, spam e-mail is an unsolicited mailing,
ClicktoFax Service Usage Manual
 ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
ClicktoFax Service Usage Manual 1. Log in to Fax Service 2. Configure your account 3. Send a fax 4. Receive a fax/search for Faxes/View Faxes 5. Logout 6. Additional Support 1. Log into fax service: a.
How to access your email via Outlook Web Access
 How to access your email via Outlook Web Access 1) Open your internet browser and type in the following address: www.law.miami.edu * Aol users must minimize their browser and use Internet Explorer 6.0+
How to access your email via Outlook Web Access 1) Open your internet browser and type in the following address: www.law.miami.edu * Aol users must minimize their browser and use Internet Explorer 6.0+
Managed File Transfer Utility
 The Managed File Transfer Utility (MFT) is a file transfer solution that enables DOT users and external parties to transfer files securely through an intuitive interface without some of the email pitfalls.
The Managed File Transfer Utility (MFT) is a file transfer solution that enables DOT users and external parties to transfer files securely through an intuitive interface without some of the email pitfalls.
Barracuda Spam Firewall Users Guide. Greeting Message Obtaining a new password Summary report Quarantine Inbox Preferences
 Barracuda Spam Firewall Users Guide Greeting Message Obtaining a new password Summary report Quarantine Inbox Preferences Greeting Message The first time the Barracuda Spam Firewall quarantines an email
Barracuda Spam Firewall Users Guide Greeting Message Obtaining a new password Summary report Quarantine Inbox Preferences Greeting Message The first time the Barracuda Spam Firewall quarantines an email
Barracuda Spam Control System
 Barracuda Spam Control System 1. General Information The Barracuda anti-spam server inspects all email coming into campus from the Internet for spam and either delivers the message to your email inbox,
Barracuda Spam Control System 1. General Information The Barracuda anti-spam server inspects all email coming into campus from the Internet for spam and either delivers the message to your email inbox,
How to access your email from WORK & HOME
 How to access your email from WORK & HOME 1. Open your browser and go to the district website by typing in the following address: http://www.islandtrees.org 2. Click on Staff Resources 3. Click on the
How to access your email from WORK & HOME 1. Open your browser and go to the district website by typing in the following address: http://www.islandtrees.org 2. Click on Staff Resources 3. Click on the
Email Filtering Admin Guide. Guide to Administrative Functions of Spam and Virus Filtering Service
 Email Filtering Admin Guide Guide to Administrative Functions of Spam and Virus Filtering Service Table of Contents Welcome Page 3 Logon Page 3 Home Page 4 Spam Page 5 Message Searching Releasing Held
Email Filtering Admin Guide Guide to Administrative Functions of Spam and Virus Filtering Service Table of Contents Welcome Page 3 Logon Page 3 Home Page 4 Spam Page 5 Message Searching Releasing Held
Using the City of Stamford / Stamford Public Schools. Web Email System
 Using the City of Stamford / Stamford Public Schools Web Email System Open the Login Screen: Go to the following site: www.stamfordct.gov/mail and choose the login link. The login screen will look like
Using the City of Stamford / Stamford Public Schools Web Email System Open the Login Screen: Go to the following site: www.stamfordct.gov/mail and choose the login link. The login screen will look like
How To Read A Quarantine Email On Hb.Com
 HB Spam Filtering Account Revised 10/22/08 Each faculty and staff member has a spam account while at HB. You should log in on a daily basis to review any messages. 1. Logging in Go to the following website
HB Spam Filtering Account Revised 10/22/08 Each faculty and staff member has a spam account while at HB. You should log in on a daily basis to review any messages. 1. Logging in Go to the following website
SPAM QUARANTINE. Quarantine
 SPAM QUARANTINE Whenever an email is thought to be spam by EOP it will be delivered to a holding area known as quarantine. This area sits outside of your inbox meaning potentially dangerous or annoying
SPAM QUARANTINE Whenever an email is thought to be spam by EOP it will be delivered to a holding area known as quarantine. This area sits outside of your inbox meaning potentially dangerous or annoying
Adjust Webmail Spam Settings
 Adjust Webmail Spam Settings An unsolicited bulk email message is known as "spam." Spam, which usually contains some sort of commercial advertising or proposition, is sent to a large number of recipients
Adjust Webmail Spam Settings An unsolicited bulk email message is known as "spam." Spam, which usually contains some sort of commercial advertising or proposition, is sent to a large number of recipients
YSU Spam Solution Guide to Using Proofpoint
 Proofpoint Web Interface Introduction In 2006, YSU deployed the Proofpoint appliance in response to a growing number of spam messages infiltrating their way past current detection technologies into user
Proofpoint Web Interface Introduction In 2006, YSU deployed the Proofpoint appliance in response to a growing number of spam messages infiltrating their way past current detection technologies into user
91.527 - Human Computer Interaction Final Project Tutorial. Hardware Inventory Management System (HIMS) By M. Michael Nourai
 91.527 - Human Computer Interaction Final Project Tutorial Hardware Inventory Management System (HIMS) By Table of Contents Introduction... 3 Running HIMS... 3 Successful Login to HIMS... 4 HIMS Main Screen...
91.527 - Human Computer Interaction Final Project Tutorial Hardware Inventory Management System (HIMS) By Table of Contents Introduction... 3 Running HIMS... 3 Successful Login to HIMS... 4 HIMS Main Screen...
Broker Portal Tutorial Broker Portal Basics
 Broker Portal Tutorial Broker Portal Basics Create Agent Connect Link Forgotten Password Change Your Broker Portal Password Delegate View Application Status Create Agent Connect Link Log in to your Producer
Broker Portal Tutorial Broker Portal Basics Create Agent Connect Link Forgotten Password Change Your Broker Portal Password Delegate View Application Status Create Agent Connect Link Log in to your Producer
User Guide. Voice Services Self Care Portal. Logging In. Welcome to the Self Care Portal
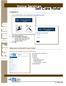 Logging In 1. From your Internet browser, enter the following URL: http://selfcare.ucc.ny.gov 2. Choose End User Self Care. 3. Enter your username and password: a. Username: Enter your LDAP user ID. (same
Logging In 1. From your Internet browser, enter the following URL: http://selfcare.ucc.ny.gov 2. Choose End User Self Care. 3. Enter your username and password: a. Username: Enter your LDAP user ID. (same
How to Use Red Condor Spam Filtering
 What is Spam Filtering? Spam filtering is used to detect unsolicited and unwanted email. By looking for certain words in an email's subject line, or through suspicious word patterns or word frequencies
What is Spam Filtering? Spam filtering is used to detect unsolicited and unwanted email. By looking for certain words in an email's subject line, or through suspicious word patterns or word frequencies
Secure File Transfer Guest User Guide Updated: 5/8/14
 Secure File Transfer Guest User Guide Updated: 5/8/14 TABLE OF CONTENTS INTRODUCTION... 3 ACCESS SECURE FILE TRANSFER TOOL... 3 REGISTRATION... 4 SELF REGISTERING... 4 REGISTER VIA AN INVITATION SENT BY
Secure File Transfer Guest User Guide Updated: 5/8/14 TABLE OF CONTENTS INTRODUCTION... 3 ACCESS SECURE FILE TRANSFER TOOL... 3 REGISTRATION... 4 SELF REGISTERING... 4 REGISTER VIA AN INVITATION SENT BY
Baylor Secure Messaging. For Non-Baylor Users
 Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
Baylor Secure Messaging For Non-Baylor Users TABLE OF CONTENTS SECTION ONE: GETTING STARTED...4 Receiving a Secure Message for the First Time...4 Password Configuration...5 Logging into Baylor Secure Messaging...7
TriCore Secure Web Email Gateway User Guide 1
 TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
TriCore Secure Web Email Gateway User Guide This document provides information about TriCore Secure Web Email Gateway. This document is for users who are authorized to send and receive encrypted email
Forefront Online Protection for Exchange (FOPE) User documentation
 Forefront Online Protection for Exchange (FOPE) User documentation About Your FOPE Quarantine Mailbox Applies To: Forefront Online Protection for Exchange This document will help you get started with the
Forefront Online Protection for Exchange (FOPE) User documentation About Your FOPE Quarantine Mailbox Applies To: Forefront Online Protection for Exchange This document will help you get started with the
Login Instructions. 1. Type web URL https://www.getrave.com/login/wmichmed into your browser s address bar.
 Rave Alert System WMed has partnered with Rave Mobile Safety to provide an emergency alert system to inform you of emergency situations, closures, and other important notifications. The system allows for
Rave Alert System WMed has partnered with Rave Mobile Safety to provide an emergency alert system to inform you of emergency situations, closures, and other important notifications. The system allows for
BOTTOM UP THINKING EMAIL SETUP INSTRUCTIONS. Unique businesses require unique solutions CLIENT GUIDE
 BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
How To Register For A Course Online
 How to Register and Pay for BEST Center Classes Online Welcome to our new online registration system for The BEST Center at Genesee Community College! All of our scheduled noncredit classes are listed
How to Register and Pay for BEST Center Classes Online Welcome to our new online registration system for The BEST Center at Genesee Community College! All of our scheduled noncredit classes are listed
GUIDEWIRE. Introduction to Using WebMail. macrobatix. Learn how to: august 2008
 macrobatix GUIDEWIRE august 2008 Introduction to Using WebMail Learn how to: Manage Your Inbox Compose a Message Activate Spam Filter Modify Spam Settings Check Held Messages *To download the complete
macrobatix GUIDEWIRE august 2008 Introduction to Using WebMail Learn how to: Manage Your Inbox Compose a Message Activate Spam Filter Modify Spam Settings Check Held Messages *To download the complete
Selection Manager: Quick Start Guide
 VERSION 1103 01.24.12 SELECTION MANAGER GUIDE Selection Manager: Quick Start Guide PART 1: GENERAL INFORMATION Selection Manager is the hiring official s interface for USA Staffing. In Selection Manager,
VERSION 1103 01.24.12 SELECTION MANAGER GUIDE Selection Manager: Quick Start Guide PART 1: GENERAL INFORMATION Selection Manager is the hiring official s interface for USA Staffing. In Selection Manager,
WatchGuard QMS End User Guide
 WatchGuard QMS End User Guide WatchGuard QMS Overview The WatchGuard QMS device enables spam messages from the WatchGuard XCS to be directed to a local quarantine area that provides spam storage for each
WatchGuard QMS End User Guide WatchGuard QMS Overview The WatchGuard QMS device enables spam messages from the WatchGuard XCS to be directed to a local quarantine area that provides spam storage for each
KUMC Spam Firewall: Barracuda Instructions
 KUMC Spam Firewall: Barracuda Instructions Receiving Messages from the KUMC Spam Firewall Greeting Message The first time the KUMC Spam Firewall quarantines an email intended for you, the system sends
KUMC Spam Firewall: Barracuda Instructions Receiving Messages from the KUMC Spam Firewall Greeting Message The first time the KUMC Spam Firewall quarantines an email intended for you, the system sends
DocuSign for Microsoft Dynamics CRM 2011 2.0.2
 Quick Start Guide DocuSign for Microsoft Dynamics CRM 2011 2.0.2 Published April 2014 Overview This guide provides information on installing and sending documents for signature with DocuSign for Microsoft
Quick Start Guide DocuSign for Microsoft Dynamics CRM 2011 2.0.2 Published April 2014 Overview This guide provides information on installing and sending documents for signature with DocuSign for Microsoft
DATA PROTECTION. OneWorld Encrypted Messages USER GUIDE
 DATA PROTECTION OneWorld Encrypted Messages USER GUIDE Table of Contents 1 Why use Encrypted emails?... 3 2 Activation and Login... 4 2.1 Activating Your New OneWorld Encrypted Messages Account... 4 2.2
DATA PROTECTION OneWorld Encrypted Messages USER GUIDE Table of Contents 1 Why use Encrypted emails?... 3 2 Activation and Login... 4 2.1 Activating Your New OneWorld Encrypted Messages Account... 4 2.2
HOW TO USE OIT EMAIL VIA THE WEB
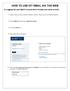 HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
HOW TO USE OIT EMAIL VIA THE WEB A) Logging into your MyOIT account which includes your email account 1) Open a browser such as Firefox, Chrome or Safari. Please do not use Internet Explorer. 2) In the
E-MAIL - Spam Filtering
 E-MAIL - Spam Filtering SPAM FILTERING OVERVIEW... USER S GUIDE...... Common Login Errors......... Lists Tab... 5 Profile Tab... 7 Quarantine Tab... 0 LOGGING IN MAIN SCREEN SPAMBLOCKER TABS (LISTS, PROFILE
E-MAIL - Spam Filtering SPAM FILTERING OVERVIEW... USER S GUIDE...... Common Login Errors......... Lists Tab... 5 Profile Tab... 7 Quarantine Tab... 0 LOGGING IN MAIN SCREEN SPAMBLOCKER TABS (LISTS, PROFILE
Email Migration Manual (For Outlook Express 6)
 Email Migration Manual (For Outlook Express 6) By SYSCOM (USA) May 13, 2013 Version 1.0 1 Contents 1. How to Change POP3/SMTP Setup for Outlook Express... 3 2. How to Login to Webmail... 7 3. How to Change
Email Migration Manual (For Outlook Express 6) By SYSCOM (USA) May 13, 2013 Version 1.0 1 Contents 1. How to Change POP3/SMTP Setup for Outlook Express... 3 2. How to Login to Webmail... 7 3. How to Change
User Guide for Kelani Mail
 User Guide for Kelani Mail Table of Contents Log in to Kelani Mail 1 Using Kelani Mail 1 Changing Password 2 Using Mail Application 3 Using email system folders 3 Managing Your Mail 4 Using your Junk folder
User Guide for Kelani Mail Table of Contents Log in to Kelani Mail 1 Using Kelani Mail 1 Changing Password 2 Using Mail Application 3 Using email system folders 3 Managing Your Mail 4 Using your Junk folder
NCAA Single-Source Sign-On System User Guide
 NCAA Single-Source Sign-On System Table of Contents General Description... 1 Glossary of Terms... 1 Common Features Log In... 2 Password... 3 Log Out... 4 Tabs... 4 Buttons and Links... 4 Management and
NCAA Single-Source Sign-On System Table of Contents General Description... 1 Glossary of Terms... 1 Common Features Log In... 2 Password... 3 Log Out... 4 Tabs... 4 Buttons and Links... 4 Management and
Personal Spam Solution Overview
 Personal Spam Solution Overview Please logon to https://mailstop.dickinson.edu using your network logon and password. This is an overview of what you can do with this system. Common Terms used in this
Personal Spam Solution Overview Please logon to https://mailstop.dickinson.edu using your network logon and password. This is an overview of what you can do with this system. Common Terms used in this
THE UNIVERSITY OF EAST ANGLIA S NEW SPAM TRAP SYSTEM
 THE UNIVERSITY OF EAST ANGLIA S NEW SPAM TRAP SYSTEM Information Services University of East Anglia Norwich NR4 7TJ [email protected] 01603 592345 Page 1 UEA has a new anti-spam appliance CanIt, which
THE UNIVERSITY OF EAST ANGLIA S NEW SPAM TRAP SYSTEM Information Services University of East Anglia Norwich NR4 7TJ [email protected] 01603 592345 Page 1 UEA has a new anti-spam appliance CanIt, which
https://mail.wheelock.edu
 The Wheelock College Guide to Understanding Microsoft Outlook Web Access Maintained by: Wheelock College Department of Information Technology Version 1.1 June 2006 https://mail.wheelock.edu This document
The Wheelock College Guide to Understanding Microsoft Outlook Web Access Maintained by: Wheelock College Department of Information Technology Version 1.1 June 2006 https://mail.wheelock.edu This document
Strategic Information Reporting Initiative (SIRI) User Guide for Student Dashboard
 Strategic Information Reporting Initiative (SIRI) User Guide for Student Dashboard Table of Contents I. Signing into SIRI... 3 A. Logging on... 3 B. Accessing SIRI off campus... 4 C. Questions... 4 II.
Strategic Information Reporting Initiative (SIRI) User Guide for Student Dashboard Table of Contents I. Signing into SIRI... 3 A. Logging on... 3 B. Accessing SIRI off campus... 4 C. Questions... 4 II.
Outlook Web Access Tipsheets
 You can use a Web browser to access your Outlook mailbox from any computer with an Internet connection. You can use Outlook Web Access with Microsoft Internet Explorer, Mozilla Firefox and many other browsers.
You can use a Web browser to access your Outlook mailbox from any computer with an Internet connection. You can use Outlook Web Access with Microsoft Internet Explorer, Mozilla Firefox and many other browsers.
ACCESSING YOUR CHAFFEY COLLEGE E-MAIL VIA THE WEB
 ACCESSING YOUR CHAFFEY COLLEGE E-MAIL VIA THE WEB If a District PC has not been permanently assigned to you for work purposes, access your Chaffey College e-mail account via the Web (Internet). You can
ACCESSING YOUR CHAFFEY COLLEGE E-MAIL VIA THE WEB If a District PC has not been permanently assigned to you for work purposes, access your Chaffey College e-mail account via the Web (Internet). You can
How do I use ProofPoint anti-spam software at the GC
 This FAQ contains: ProofPoint Login instructions Introduction to ProofPoint web interface component Views available in Proofpoint ProofPoint Web Interface Actions Introduction to ProofPoint Digest ProofPoint
This FAQ contains: ProofPoint Login instructions Introduction to ProofPoint web interface component Views available in Proofpoint ProofPoint Web Interface Actions Introduction to ProofPoint Digest ProofPoint
This exhibit describes how to upload project information from Estimator (PC) to Trns.port PES (server). Figure 1 summarizes this process.
 Facilities Development Manual Chapter 19 Plans, Specifications and Estimates Section 5 Estimates Wisconsin Department of Transportation Exhibit 10.5 Uploading project from Estimator to Trns port PES September
Facilities Development Manual Chapter 19 Plans, Specifications and Estimates Section 5 Estimates Wisconsin Department of Transportation Exhibit 10.5 Uploading project from Estimator to Trns port PES September
SchoolMessenger for iphone
 The SchoolMessenger app lets you quickly and easily send messages from anywhere using your iphone. Setting up and using the application is simple. This guide will show you how! [Important: Before you can
The SchoolMessenger app lets you quickly and easily send messages from anywhere using your iphone. Setting up and using the application is simple. This guide will show you how! [Important: Before you can
How To Access A Secure Email From The State Of Iceland
 STATE OF IOWA External User's Guide to State of Iowa Secure Email System This guide contains step by step instructions for setting up and using the State of Iowa Secure Email system. Contents Secure Email...
STATE OF IOWA External User's Guide to State of Iowa Secure Email System This guide contains step by step instructions for setting up and using the State of Iowa Secure Email system. Contents Secure Email...
Cyber Pay ONLINE Product Manual Payroll Administrator User Guide
 -1- Cyber Pay ONLINE Product Manual Payroll Administrator User Guide -2- Table of Contents 1. Overview 3 2. Logging In 4 a. The Log In Screen 4 b. Forgotten Password 5 3. Basic Interface 5 4. Payroll Entry
-1- Cyber Pay ONLINE Product Manual Payroll Administrator User Guide -2- Table of Contents 1. Overview 3 2. Logging In 4 a. The Log In Screen 4 b. Forgotten Password 5 3. Basic Interface 5 4. Payroll Entry
SPC Connect Configuration Manual V1.0
 SPC Connect Configuration Manual V1.0 I-200090-1 28.11.2014 Copyright Copyright Technical specifications and availability subject to change without notice. Copyright Siemens AB We reserve all rights in
SPC Connect Configuration Manual V1.0 I-200090-1 28.11.2014 Copyright Copyright Technical specifications and availability subject to change without notice. Copyright Siemens AB We reserve all rights in
IT Email Services page 1 of 10 Spam Filtering. Overview
 IT Email Services page 1 of 10 Overview Comcast Spectacor has implemented a system to control unwanted Internet email (spam) from the Internet. Virus emails and some known spam will be filtered automatically.
IT Email Services page 1 of 10 Overview Comcast Spectacor has implemented a system to control unwanted Internet email (spam) from the Internet. Virus emails and some known spam will be filtered automatically.
Using the Portal and Direct Messaging HOW TO SETUP AND USE PORTAL AND DIRECT MESSAGING FUNCTIONALITY STARTING IN VERSION 7
 Using the Portal and Direct Messaging HOW TO SETUP AND USE PORTAL AND DIRECT MESSAGING FUNCTIONALITY STARTING IN VERSION 7 Set up your practice and user accounts Are you an existing Updox user? No Did
Using the Portal and Direct Messaging HOW TO SETUP AND USE PORTAL AND DIRECT MESSAGING FUNCTIONALITY STARTING IN VERSION 7 Set up your practice and user accounts Are you an existing Updox user? No Did
Using MailStore to Archive MDaemon Email
 Using MailStore to Archive MDaemon Email This guide details how to archive all inbound and outbound email using MailStore, as well as archiving any emails currently found in the users accounts in MDaemon.
Using MailStore to Archive MDaemon Email This guide details how to archive all inbound and outbound email using MailStore, as well as archiving any emails currently found in the users accounts in MDaemon.
Email Migration Manual (For Outlook 2010)
 Email Migration Manual (For Outlook 2010) By SYSCOM (USA) May 13, 2013 Version 2.2 1 Contents 1. How to Change POP3/SMTP Setting for Outlook 2010... 3 2. How to Login to Webmail... 10 3. How to Change
Email Migration Manual (For Outlook 2010) By SYSCOM (USA) May 13, 2013 Version 2.2 1 Contents 1. How to Change POP3/SMTP Setting for Outlook 2010... 3 2. How to Login to Webmail... 10 3. How to Change
Table of Contents. Changing Your Password in Windows NT p. 1. Changing Your Password in Alpha Connection.. pp. 1-3
 Table of Contents Changing Your Password in Windows NT p. 1 Changing Your Password in Alpha Connection.. pp. 1-3 Not Able to Get Outlook Express Mail Because Alpha Connection Password Expires... pp. 3-4
Table of Contents Changing Your Password in Windows NT p. 1 Changing Your Password in Alpha Connection.. pp. 1-3 Not Able to Get Outlook Express Mail Because Alpha Connection Password Expires... pp. 3-4
Using the Barracuda Spam Firewall to Filter Your Emails
 Using the Barracuda Spam Firewall to Filter Your Emails This chapter describes how end users interact with the Barracuda Spam Firewall to check their quarantined messages, classify messages as spam and
Using the Barracuda Spam Firewall to Filter Your Emails This chapter describes how end users interact with the Barracuda Spam Firewall to check their quarantined messages, classify messages as spam and
Centralized Internship Support System for Greek Higher Education Students
 Centralized Internship Support System for Greek Higher Education Students Host Company s Application User Guide Once the account that you created as Internship Host in the program Atlas has been certified,
Centralized Internship Support System for Greek Higher Education Students Host Company s Application User Guide Once the account that you created as Internship Host in the program Atlas has been certified,
Email Instructions. Outlook (Windows) Mail (Mac) Webmail Windows Live Mail iphone 4, 4S, 5, 5c, 5s Samsung Galaxy S4 BlackBerry
 Email Instructions Outlook (Windows) Mail (Mac) Webmail Windows Live Mail iphone 4, 4S, 5, 5c, 5s Samsung Galaxy S4 BlackBerry ii Table of Contents Table of Contents 1 Mail Account Settings 1 Account Set
Email Instructions Outlook (Windows) Mail (Mac) Webmail Windows Live Mail iphone 4, 4S, 5, 5c, 5s Samsung Galaxy S4 BlackBerry ii Table of Contents Table of Contents 1 Mail Account Settings 1 Account Set
DataDirector Getting Started
 DataDirector Getting Started LOGIN Log into the DataDirector website: https://www.achievedata.com/yourdistrictname User Name: New Password: Enter your User Name and Password o After login, you may need
DataDirector Getting Started LOGIN Log into the DataDirector website: https://www.achievedata.com/yourdistrictname User Name: New Password: Enter your User Name and Password o After login, you may need
Netmail Search for Outlook 2010
 Netmail Search for Outlook 2010 Quick Reference Guide Netmail Search is an easy-to-use web-based electronic discovery tool that allows you to easily search, sort, retrieve, view, and manage your archived
Netmail Search for Outlook 2010 Quick Reference Guide Netmail Search is an easy-to-use web-based electronic discovery tool that allows you to easily search, sort, retrieve, view, and manage your archived
Discoverer Training Guide
 Discoverer Training Guide Learning objectives Understand what Discoverer is Login and Log out procedures Run a report Select parameters for reports Change report formats Export a report and choose different
Discoverer Training Guide Learning objectives Understand what Discoverer is Login and Log out procedures Run a report Select parameters for reports Change report formats Export a report and choose different
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Remote Access: Citrix Client Setup
 Introduction: The following documentation is intended to assist first time or active users with installation of the Citrix ICA connection software required to access the MSVU Remote Access system desktop
Introduction: The following documentation is intended to assist first time or active users with installation of the Citrix ICA connection software required to access the MSVU Remote Access system desktop
Fax User Guide 07/31/2014 USER GUIDE
 Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
Fax User Guide 07/31/2014 USER GUIDE Contents: Access Fusion Fax Service 3 Search Tab 3 View Tab 5 To E-mail From View Page 5 Send Tab 7 Recipient Info Section 7 Attachments Section 7 Preview Fax Section
Barracuda SPAM Firewall
 Barracuda SPAM Firewall SPAM and other types of unwanted email is a steadily growing problem for all businesses and schools. Because of the growing nature of the problem, we have a SPAM filter and Quarantine
Barracuda SPAM Firewall SPAM and other types of unwanted email is a steadily growing problem for all businesses and schools. Because of the growing nature of the problem, we have a SPAM filter and Quarantine
The Institute of Education Spam filter service allows you to take control of your spam filtering.
 CUSTOMISING THE IOE SPAM FILTER The Institute of Education Spam filter service allows you to take control of your spam filtering. The interface is very simple to access and use. Through a secure web page
CUSTOMISING THE IOE SPAM FILTER The Institute of Education Spam filter service allows you to take control of your spam filtering. The interface is very simple to access and use. Through a secure web page
How To Use Webmail. Guiding you through the Universities online email
 How To Use Webmail Guiding you through the Universities online email Table of Contents LOGGING ON...2 VIEWING MESSAGES...2 SENDING A MESSAGE...3 Using the University s Address Book...3 To send a message
How To Use Webmail Guiding you through the Universities online email Table of Contents LOGGING ON...2 VIEWING MESSAGES...2 SENDING A MESSAGE...3 Using the University s Address Book...3 To send a message
Resource Scheduler (Meeting Room Manager) User s Manual
 Resource Scheduler (Meeting Room Manager) User s Manual Resource Scheduler (or Meeting Room Manager) is a web based software package for reserving facilities and equipment. The NS&M web client can be run
Resource Scheduler (Meeting Room Manager) User s Manual Resource Scheduler (or Meeting Room Manager) is a web based software package for reserving facilities and equipment. The NS&M web client can be run
Background Information
 User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
User Guide 1 Background Information ********************************Disclaimer******************************************** This is a government system intended for official use only. Using this system
Barracuda Spam Firewall User s Guide
 Barracuda Spam Firewall User s Guide 1 Managing your Quarantine Inbox This chapter describes how you can check your quarantine messages, classify messages as spam and not spam, and modify your user preferences
Barracuda Spam Firewall User s Guide 1 Managing your Quarantine Inbox This chapter describes how you can check your quarantine messages, classify messages as spam and not spam, and modify your user preferences
Tufts Technology Services (TTS) Proofpoint Frequently Asked Questions (FAQ)
 Tufts Technology Services (TTS) Proofpoint Frequently Asked Questions (FAQ) What is Proofpoint?... 2 What is an End User Digest?... 2 In my End User Digest I see an email that is not spam. What are my
Tufts Technology Services (TTS) Proofpoint Frequently Asked Questions (FAQ) What is Proofpoint?... 2 What is an End User Digest?... 2 In my End User Digest I see an email that is not spam. What are my
Table of Contents. I. Approver Setup Process... 3. II. Client Login and Password Functions... 4. III. Setup Email Notification and Alternates...
 Table of Contents I. Approver Setup Process... 3 II. Client Login and Password Functions... 4 III. Setup Email Notification and Alternates... 6 IV. Email Notification for Approval... 9 V. Viewing/Approving
Table of Contents I. Approver Setup Process... 3 II. Client Login and Password Functions... 4 III. Setup Email Notification and Alternates... 6 IV. Email Notification for Approval... 9 V. Viewing/Approving
Barracuda User Guide. Managing your Spam Quarantine
 Managing your Spam Quarantine Barracuda User Guide Step1: Open your internet browser and go to http://myspam.datatechhosting.com this will automatically redirect you to Barracuda s email security service
Managing your Spam Quarantine Barracuda User Guide Step1: Open your internet browser and go to http://myspam.datatechhosting.com this will automatically redirect you to Barracuda s email security service
Stationery & POS Online Ordering Step-By-Step Guide
 Stationery & POS Online Ordering Step-By-Step Guide Log on to Choice Online www.choiceonline.carpetchoice.com.au 1. Enter Store Username & Password (please check with Central Office if you require your
Stationery & POS Online Ordering Step-By-Step Guide Log on to Choice Online www.choiceonline.carpetchoice.com.au 1. Enter Store Username & Password (please check with Central Office if you require your
BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8
 BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8 User Guide SWDT653811-793266-0827104650-001 Contents Getting started... 3 About messaging service plans for BlackBerry
BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8 User Guide SWDT653811-793266-0827104650-001 Contents Getting started... 3 About messaging service plans for BlackBerry
Log-in to the patient booking website
 Log-in to the patient booking website From the HealthSpace home page you can select Choose and Book from the menu or by clicking on the Choose and Book image both shown on the left side of the screen.
Log-in to the patient booking website From the HealthSpace home page you can select Choose and Book from the menu or by clicking on the Choose and Book image both shown on the left side of the screen.
Faculty Introduction to Self-Service
 Faculty Introduction to Self-Service This user guide focuses on how faculty members can use Self-Service to access and update their information. Using a Web browser, faculty members can enter student grades,
Faculty Introduction to Self-Service This user guide focuses on how faculty members can use Self-Service to access and update their information. Using a Web browser, faculty members can enter student grades,
How To Open An Encrypted Email
 Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
Due to HIPAA requirements, HCDDS must implement a secure method for sending emails that contain information about individuals we serve to people outside the agency s secure network. To accomplish this,
Note: With v3.2, the DocuSign Fetch application was renamed DocuSign Retrieve.
 Quick Start Guide DocuSign Retrieve 3.2.2 Published April 2015 Overview DocuSign Retrieve is a windows-based tool that "retrieves" envelopes, documents, and data from DocuSign for use in external systems.
Quick Start Guide DocuSign Retrieve 3.2.2 Published April 2015 Overview DocuSign Retrieve is a windows-based tool that "retrieves" envelopes, documents, and data from DocuSign for use in external systems.
Creating Your PALS Online Account for New Teachers Navigate to the PALS Online homepage
 Creating Your PALS Online Account for New Teachers Navigate to the PALS Online homepage Type www.wi.palsk8.com into the address bar of your internet browser. New or Returning? To create a new teacher account,
Creating Your PALS Online Account for New Teachers Navigate to the PALS Online homepage Type www.wi.palsk8.com into the address bar of your internet browser. New or Returning? To create a new teacher account,
[MP2 TRAINING MANUAL]
![[MP2 TRAINING MANUAL] [MP2 TRAINING MANUAL]](/thumbs/31/15009339.jpg) 2015 Technical Services James Titford [MP2 TRAINING MANUAL] Process for Work Order and Purchase Requisition entry on MP2. Table of Contents Introduction... 2 Logging on to MP2... 2 Navigating MP2:... 3
2015 Technical Services James Titford [MP2 TRAINING MANUAL] Process for Work Order and Purchase Requisition entry on MP2. Table of Contents Introduction... 2 Logging on to MP2... 2 Navigating MP2:... 3
Citrus Valley Health Partners. Web Outlook User Guide. Table of Contents
 Citrus Valley Health Partners Web Outlook User Guide Table of Contents Getting Started Page Access to Web Outlook... 1 Log in Instructions... 1 Basic Navigation... 1 The Menu Bar... 1 The Reading Pane...
Citrus Valley Health Partners Web Outlook User Guide Table of Contents Getting Started Page Access to Web Outlook... 1 Log in Instructions... 1 Basic Navigation... 1 The Menu Bar... 1 The Reading Pane...
Contents 1 Overview 2 Steps to run an Excel Add-In Setup: 3 Add-Ins 4 LOGIN 5 SEND SMS 5.1 Send Text or Flash Sms 5.2 Select Range 5.
 Contents 1 Overview 2 Steps to run an Excel Add-In Setup: 3 Add-Ins 4 LOGIN 5 SEND SMS 5.1 Send Text or Flash Sms 5.2 Select Range 5.3 Selected Range Preview List 5.4 Scheduling of Messages 5.5 Scheduled
Contents 1 Overview 2 Steps to run an Excel Add-In Setup: 3 Add-Ins 4 LOGIN 5 SEND SMS 5.1 Send Text or Flash Sms 5.2 Select Range 5.3 Selected Range Preview List 5.4 Scheduling of Messages 5.5 Scheduled
MyFaxCentral User Administration Guide
 faxing simplified. anytime. anywhere. MyFaxCentral User Administration Guide www.myfax.com MyFaxCentral Common Controls...1 Navigation Controls...1 Customize View...1 MyFaxCentral User Administration...2
faxing simplified. anytime. anywhere. MyFaxCentral User Administration Guide www.myfax.com MyFaxCentral Common Controls...1 Navigation Controls...1 Customize View...1 MyFaxCentral User Administration...2
Using Server-Side Filters to Manage/Organize Your E-Mail (Including Accept and Block Lists) Table of Contents Why Use Server-Side Mail Filters INBOX
 Using Server-Side Filters to Manage/Organize Your E-Mail (Including Accept and Block Lists) 1 of 9 U-M Information Technology Central Services S4325 May 2005 You can create server-side mail filters to
Using Server-Side Filters to Manage/Organize Your E-Mail (Including Accept and Block Lists) 1 of 9 U-M Information Technology Central Services S4325 May 2005 You can create server-side mail filters to
How does the Excalibur Technology SPAM & Virus Protection System work?
 How does the Excalibur Technology SPAM & Virus Protection System work? All e-mail messages sent to your e-mail address are analyzed by the Excalibur Technology SPAM & Virus Protection System before being
How does the Excalibur Technology SPAM & Virus Protection System work? All e-mail messages sent to your e-mail address are analyzed by the Excalibur Technology SPAM & Virus Protection System before being
Managing the Database and Student Records Online (at the District Level)
 ReadyResults.net 2014 Managing the Database and Student Records Online (at the District Level) For Administrators Only For help, send email to: [email protected] or call: 877-456-1547 Table of Contents
ReadyResults.net 2014 Managing the Database and Student Records Online (at the District Level) For Administrators Only For help, send email to: [email protected] or call: 877-456-1547 Table of Contents
Welcome to HomeTown Bank s Secure E-mail! User Guide
 Welcome to HomeTown Bank s Secure E-mail! User Guide To access the secure email message center, click the Secure Email link on the www.htbmn.com main web page. Select whether you are a new user of the
Welcome to HomeTown Bank s Secure E-mail! User Guide To access the secure email message center, click the Secure Email link on the www.htbmn.com main web page. Select whether you are a new user of the
For paid computer support call 604-518-6695 http://www.netdigix.com [email protected]
 Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Setting up your vpn connection on windows 2000 or XP in continuation from installing x.509 certificate on windows (please do not continue if you have not installed your x.509 certificate): Instructions
Outlook Express. Make Changes in Red: Open up Outlook Express. From the Menu Bar. Tools to Accounts - Click on Mail Tab.
 Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Outlook Express Open up Outlook Express From the Menu Bar Tools to Accounts - Click on Mail Tab Click on mail.nefcom.net (default) Click on Properties button Click on the General tab User Information E-mail
Criminal Justice Social Work Community of Practice Subscription, registration and login manual
 Criminal Justice Social Work Community of Practice Subscription, registration and login manual Version: concept 08102014 Introduction Before you can access the Criminal Justice Social Work - Community
Criminal Justice Social Work Community of Practice Subscription, registration and login manual Version: concept 08102014 Introduction Before you can access the Criminal Justice Social Work - Community
New Agent Registration
 Welcome to the Uplink Employer Self Service tutorial for new agent registration. If you are an agent and need to register with the Department of Workforce Development this tutorial has helpful information
Welcome to the Uplink Employer Self Service tutorial for new agent registration. If you are an agent and need to register with the Department of Workforce Development this tutorial has helpful information
YOUR INDIANA COMMUNICATIONS COMPANY. Conference Calling. User Guide
 YO CO CO YOUR INDIANA COMMUNICATIONS COMPANY Conference Calling User Guide For assistance, please call (812) 876-2211. Setting Up Your Conference Call Setting up a Smithville Conference Call is easy. First,
YO CO CO YOUR INDIANA COMMUNICATIONS COMPANY Conference Calling User Guide For assistance, please call (812) 876-2211. Setting Up Your Conference Call Setting up a Smithville Conference Call is easy. First,
Using the Barracuda to Filter Your Emails
 Using the Barracuda to Filter Your Emails The following describes how end users interact with the Barracuda to check their quarantined messages, classify messages as spam and not spam, and modify their
Using the Barracuda to Filter Your Emails The following describes how end users interact with the Barracuda to check their quarantined messages, classify messages as spam and not spam, and modify their
Trouble Ticket Express
 Trouble Ticket Express Operator Manual rev. 1.0. 2006 by United Web Coders www.unitedwebcoders.com 1. System Overview 1.1. Concepts The Trouble Ticket Express is a web based help desk system. The program
Trouble Ticket Express Operator Manual rev. 1.0. 2006 by United Web Coders www.unitedwebcoders.com 1. System Overview 1.1. Concepts The Trouble Ticket Express is a web based help desk system. The program
Vodafone multitxt Outlook Mobile Services (OMS)
 Vodafone multitxt Outlook Mobile Services (OMS) Microsoft Outlook 2007+ Mobile Service (OMS) Sending messages Replies FAQs 2 3 5 6 1 Microsoft Outlook 2007+ Mobile Service (OMS) Outlook Mobile Service
Vodafone multitxt Outlook Mobile Services (OMS) Microsoft Outlook 2007+ Mobile Service (OMS) Sending messages Replies FAQs 2 3 5 6 1 Microsoft Outlook 2007+ Mobile Service (OMS) Outlook Mobile Service
New Help Desk Ticketing System
 New Help Desk Ticketing System Starting Monday, November 30, 2009 at 6 am the University will be going live with their new help desk ticketing system. The website to access the new ticketing system is
New Help Desk Ticketing System Starting Monday, November 30, 2009 at 6 am the University will be going live with their new help desk ticketing system. The website to access the new ticketing system is
Online Timesheets Guide for Contractors
 Online Timesheets Guide for Contractors Table Of Contents 1. Welcome To Online Timesheets Page 2 2. Email Activation Page 2 3. Logging Onto The Online Timesheet Portal Page 2 4. Online Timesheet Portal
Online Timesheets Guide for Contractors Table Of Contents 1. Welcome To Online Timesheets Page 2 2. Email Activation Page 2 3. Logging Onto The Online Timesheet Portal Page 2 4. Online Timesheet Portal
Initial Setup of Microsoft Outlook with Google Apps Sync for Windows 7. Initial Setup of Microsoft Outlook with Google Apps Sync for Windows 7
 Microsoft Outlook with Initial Setup of Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access
Microsoft Outlook with Initial Setup of Concept This document describes the procedures for setting up the Microsoft Outlook email client to download messages from Google Mail using Internet Message Access
