Business and IT Trends
|
|
|
- Randall Bruce
- 8 years ago
- Views:
Transcription
1 Business and IT Trends Ronald E. Giachetti, Ph.D. Associate Professor Industrial and Systems Engineering Florida International University Duane P. Truex, Ph.D. Associate Professor Robinson College of Business Department of Computer Information Systems Georgia State University January ERP 21, 2010 Methodology and Project Management 1
2 Agenda A high level discussion of business and IT trends impac8ng industry and the enterprise system market Business need for integra8on ERP & EAI Security Supply chains and outsourcing Data warehouses Model and abstrac8on of sodware ar8facts Web services RFID January 21, 2010 Day 1 Module 4 Slide 2
3 Organiza8on Structure Requires Integra8on Organization theory prescribes decomposing the complex organization into smaller units that are easier to manage. Give rise to two problems: INFORMATION PROBLEM Units naturally erect barriers to flow of information. COORDINATION PROBLEM The unit s work must be coordinated with other units in order to meet overall organization goals. Marketing The functional differentiation must be accompanied by appropriate integration. President Design Manufacturing Production IE January 21, 2010 Day 1 Module 4 Slide 3
4 Enterprise Chaos January 21, 2010 Day 1 Module 4 Slide 4
5 Why We Have Heterogeneity Systems are designed for local needs. Outside needs are extraneous. Locally op8mal hardware, sodware applica8ons, and networks. Each dis8nct domain has its own ontology. a set of well- defined terms,which delimit the domain of discourse rela8onships among those terms, chosen from a limited set The ontology may be formal (KIF, KQML) or not (XML) PHYSICAL HETEROGENITY APPLICATION HETEROGENITY SEMANTIC HETEROGENITY January 21, 2010 Day 1 Module 4 Slide 5
6 Economic Drivers NIST (1999) es8mates the US automo8ve industry spends $1 billion per year due to poor interoperability Commercial ERP and related systems are sought ader to integrate the enterprise and annual sales of these ERP systems are expected to exceed $20 billion by 2002 (Gartner Group 1999). Even with ERP most companies must s8ll integrate the ERP system with legacy and other systems (Thermistocleus 2001). Organizations change due to mergers and acquisitions January 21, 2010 Day 1 Module 4 Slide 6
7 Needed: The Horizontal View Optimize the Enterprise Drives the need to suboptimize some business units for the success of the business portfolio Business Value Business Process Information? Business Process Information? Business Process App System Interfaces? App System Interfaces? App System Infrastructure Relationships Relationships Users? Users? Users January 21, 2010 Day 1 Module 4 Slide 7
8 Just connec8ng not sufficient Product Catalog Common Semantic Model Carrier Selection Prices and Freight Charges Exchanging XML messages is the easy part. Ordering Common semantics is the hard part. January 21, 2010 Day 1 Module 4 Slide 8
9 Benefits of Integra8on Integra8on leads to improved enterprise performance Decreasing delivery 8me (30-60%) Product design 8me (20-50%) Product design cost (15-30%) Space (25-40%) Inventory cost of raw materials (30-60%) Direct manpower costs (20-35%) Indirect manpower costs (30-35%) * National Research Council, Impact of integration efforts at McDonnell Aircraft Co., Deere and Co, Westinghouse Defense and Electronic Center, General Motors, and Ingersoll Milling Machine Co, Special Report to NASA, Washington, DC 1986 January 21, 2010 Day 1 Module 4 Slide 9
10 Many varied approaches to Integra8on Database Approaches STEP Federated Process Approaches BPR Workflow Organization Approaches Concurrent Engineering Mechanisms Middleware Approaches Computer Science CORBA, DCOM, JavaRMI Approaches Agents Ontologies January 21, 2010 Day 1 Module 4 Slide 10
11 ERP to the rescue! Integrates the en8re business process. Integrates Process (standard processes) Integrates Applica8on (a single applica8on, i.e., the ERP package) Integrates Data (standard common data) A single- vendor solu8on (thus avoid interoperability issues). SAP, PeopleSoD, SSA (Baan), JD Edwards, Manuguis8cs, others. January 21, 2010 Day 1 Module 4 Slide 11
12 ERP & the Reality of elimina8ng need for integra8on ERP lacks 100% coverage ERP versioning problems due to size and complexity Legacy applica8ons are s8ll around Mergers and acquisi8ons change organiza8on and come with new systems. S8ll have integra8on problem with suppliers, partners, and customers. Altman & Altman IP1, Feb 2004 January 21, 2010 Day 1 Module 4 Slide 12
13 EAI Enterprise Applica.on Integra.on is the unrestricted sharing of data and business processes among any connected applica8ons and data sources in the enterprise. To do this you should not have to make changes to the data structures or applica8ons. Note, ERP has these proper8es within the ERP package but not necessarily with applica8ons external to ERP (e.g. legacy systems). January 21, 2010 Day 1 Module 4 Slide 13
14 EAI Market EAI in industry refers largely to the middleware market. This market is the sodware infrastructure to connect various applica8ons. Some es8mates put up to 70% of all code consis8ng of interfaces, protocols, and other procedures to establish linkages between systems. January 21, 2010 Day 1 Module 4 Slide 14
15 EAI Vendors Year 2000 data for a total market of $1.15 Billion. January 21, 2010 Day 1 Module 4 Slide 15
16 Security has become an over-riding concern Viruses, spam, worms, terrorism, identify theft, fraud, undiscovered threats One reason we are more vulnerable today is the increased integration of our world!
17 ERP Security Authorized Users with Username and Password Access based on authoriza8on level and user roles E.g., an accounts payable clerk should not have access to human resource modules data encryp+on which limits someone's ability to export the database Audit logs within an ERP system track individual transac8ons or changes system administrators can configure customized audit reports that employ simple logic to iden8fy "outliers" - system transac8ons that fall outside of normal parameters, such as date and 8me, loca8on of the user logging into the system and checks larger than a predefined selng con8nuous transac8on and incident monitoring is a best prac8ce to avoid security breaches January 21, 2010 Day 1 Module 4 Slide 17
18 Security and People ODen people are the weakest link in security. Not checking creden8als adequately. Two examples: When obtaining my new Florida Driver s License the clerk in the Dept. of Motor Vehicles never opened my passport to verify that it was indeed my passport. In a recent consul8ng job at a hospital the security guard who issues ID cards could not find the reques8ng an ID for myself and then issued the card without ever checking any iden8fica8on! Need to train people in security policies and procedures. Audit security. Don t rely on minimum wage workers for security. social engineering where users are tricked into freely divulging their creden8als January 21, 2010 Day 1 Module 4 Slide 18
19 Security during Maintenance As employees change posi8ons, new employees, new partners, mergers, and other business events change the roles and authoriza8on of users then the profiles must be updated. Need to establish new policies and procedures to handle these changes to maintain internal ERP controls. January 21, 2010 Day 1 Module 4 Slide 19
20 Supply Chain Mul8na8onal organiza8ons inherently involve supply chains Link suppliers, customers A great deal of value in open systems A major ERP trend since 1999 January 21, 2010 Day 1 Module 4 Slide 20
21 What is a Supply- Chain? Manage Lifecycle Commit Date Buy Build Store Ship ERP-1 ERP-2 ERP-3 January 21, 2010 Day 1 Module 4 Slide 21
22 Process Map Example created in ARIS EasySCOR Suppliers Supplier Suppliers Assemble/ Package Distribution Centers Geo Ports of Entry Americas---> Europe---> Asia---> January 21, 2010 Day 1 Module 4 Slide 22
23 Outsourcing Offshore outsourcing is just one small part of a (US)$5 trillion global outsourcing market. This market is growing by more than 15 percent per year, and the offshore component is certainly among the fastest growing," Michael Corber, president and CEO of New York- based Michael F. Corber & Associates January 21, 2010 Day 1 Module 4 Slide 23
24 IT Offshore Outsourcing A McKinsey Global Institute study reveals the extent of the mutual benefits. In this way, offshoring, far from being bad for the United States, creates net value for the economy. It directly recaptures 67 cents of every dollar of spending that goes abroad and indirectly might capture an additional 45 to 47 cents--producing a net gain of 12 cents to 14 cents for every dollar of costs moved offshore. Offshoring and beyond The McKinsey Quarterly, 2003 Number 4 January 21, 2010 Day 1 Module 4 Slide 24
25 Outsourcing ERP When a large organiza8on implements ERP, they oden hire a consultant to operate it Texas Instruments: transferred 250 IT personnel to Andersen Consul8ng Rolls- Royce: transferred IT development to EDS While not called outsourcing, in effect it is Technical difference ownership of plauorm and rental of sodware January 21, 2010 Day 1 Module 4 Slide 25
26 Data Warehouses Collects and stores data from mul8ple, distributed, and heterogeneous databases and related informa8on sources. Users access the data warehouse and do not need to access the original data source. Power of data warehouse is the integra8on of mul8ple sources. Used for analy8cal decision- making. OLAP (On- Line Analy8cal Processing) versus the OLTP (On- Line Transac8on Processing) of tradi8onal databases. January 21, 2010 Day 1 Module 4 Slide 26
27 Crea8ng a Data Warehouse January 21, 2010 Day 1 Module 4 Slide 27
28 Star Schema for Sales January 21, 2010 Day 1 Module 4 Slide 28
29 Informa8on overload Data starva8on More databases public & corporate Faster communica+on digital packe+ng: TCP- IP, ATM World- wide connec+vity Internet & Intranets world- wide web Disintermedia+on ubiquitous publishing
30 Change in Supply vs Demand What information consumes is rather obvious, it consumes the attention of its recipients. Hence a wealth of information creates a poverty of attention, and a need to allocate that attention efficiently among the overabundance of information sources that might consume it. [Herbert Simon] January 21, 2010 Day 1 Module 4 Slide 30
31 IT Trends Moving to higher levels of abstrac8on in order to understand, analyze, design, and build sodware systems Greater usage of off- the- shelf components More tool automa8on Other trends???? January 21, 2010 Day 1 Module 4 Slide 31
32 II. Breve Tour por UML UML Diagrams The diagrams express graphically parts of the model Model Component Diagram January 21, 2010 Day 1 Module 4 Slide 32
33 Model Driven Architecture (MDA) These models belong to diverse independent domains of interest with regard to the universe of discourse that they represent. TWO APPROACHES IN SYSTEM MODELING AND THEIR ILLUSTRATIONS WITH MDA AND RM-ODP Andrey Naumenko, Alain Wegmann Laboratory of Systemic Modeling, Swiss Federal Institute of Technology - Lausanne, EPFL-I&C-LAMS,1015 Lausanne, Switzerland andrey.naumenko@epfl.ch, alain.wegmann@epfl.ch For a given domain of interest, its corresponding metamodel defines relations between different conceptual categories that exist in the domain models, as well as the meaning of each modeling concept. January 21, 2010 Day 1 Module 4 Slide 33
34 RFID What is it? Radio Frequency Iden8fica8on Three parts to an RFID implementa8on: Tag (chip and antenna) Reader Database & sodware Tag holds unique data a serial number and/or other unique arributes of the item January 21, 2010 Day 1 Module 4 Slide 34
35 RFID Uses Retail & Distribu8on Contactless Payment Keyless Entry Livestock Tagging Pharmaceu8cals Logis8cs Assets (containers, trailers) Pet Iden8fica8on January 21, 2010 Day 1 Module 4 Slide 35
36 RFID Benefits More informa8on Individual item data & tracking Fast No contact No line of sight Miliseconds Simultaneous read of mul8ple items January 21, 2010 Day 1 Module 4 Slide 36
37 Tag Power Source RFID Tag Arributes Active RFID Internal to tag Tag Battery Yes No Required signal strength Very Low Passive RFID Energy transferred using RF from reader Very High Range Up to 100m Up to 3-5m, usually less Multi-tag reading 1000 s of tags recognized up to 100mph Few hundred within 3m of reader Data Storage Up to 128 Kb or read/ write & search 128 bytes of read/write January 21, 2010 Day 1 Module 4 Slide 37
38 Status Today Issue #1: RFID Mandate Madness S8ll high risk decisions due to technology, standards, and procedures. January 21, 2010 Day 1 Module 4 Slide 38
39 Status Today Issue #3: Tag costs too high Goal is 5 tag; can t afford $2 tag on 99 item Biggest limit on widespread business use January 21, 2010 Day 1 Module 4 Slide 39
40 RFID adds to Data Glut Issue #4: Lack of SoDware What to do with all that data? Problem: Petabytes Answer: Middleware January 21, 2010 Day 1 Module 4 Slide 40
41 Web Services Web Services are self- contained, self- describing, modular applica8ons that can be published, located, and invoked across the Web. Web Services allow the crea8on of new applica8ons by aggrega8ng the services of many other applica8ons that exist locally or over the Internet. Web Services perform func8ons, which can be anything from simple requests to complicated business processes. Once a Web service is deployed, other applica8ons (and other Web services) can discover and invoke the deployed service. Examples are: currency conversion, language transla8on, shipping, and claims processing. January 21, 2010 Day 1 Module 4 Slide 41
42 Web Services Web services provide a structured way to format data, a way to handle transac8ons, and a standard means to describe what the service does and make the services available to others. Web services are based on the standard protocols of XML, SOAP, and WSDL, which allow them to interoperate across plauorms and programming languages. Web services are discrete units of code; each handles a limited set of tasks. January 21, 2010 Day 1 Module 4 Slide 42
43 Web Services Unlike websites, which are pictures of data designed to be viewed in a browser by a person, a Web service is designed to be accessed directly by another service or software application. January 21, 2010 Day 1 Module 4 Slide 43
44 Web Services Technologies There are a suite of technologies to enable web services: SOAP protocol for exchange WSDL describes services UDDI registry to list available services All are based on XML and are standards defined by OMG. MicrosoD s.net is built around these technologies. January 21, 2010 Day 1 Module 4 Slide 44
45 Con8nuous Learning As we like to tell college students, you must develop a penchant for life- long learning January 21, 2010 Day 1 Module 4 Slide 45
Business Process Management Systems ITEC 4030 Winter 2011 Peter Khaiter Lecture 9 Enabling Business (IT) Integration Feb 7
 Business Process Management Systems ITEC 4030 Winter 2011 Peter Khaiter Lecture 9 Enabling Business (IT) Integration Feb 7 Business Integration: Goals and Approaches - Review: BI is the exchange of business-critical
Business Process Management Systems ITEC 4030 Winter 2011 Peter Khaiter Lecture 9 Enabling Business (IT) Integration Feb 7 Business Integration: Goals and Approaches - Review: BI is the exchange of business-critical
Using FICAM as a model for TSCP Best Prac:ces in Physical Iden:ty and Access Management. TSCP Symposium November 2013
 Using FICAM as a model for TSCP Best Prac:ces in Physical Iden:ty and Access Management TSCP Symposium November 2013 Quantum Secure s Focus on FICAM and Related Standards Complete Suite of Physical Iden:ty
Using FICAM as a model for TSCP Best Prac:ces in Physical Iden:ty and Access Management TSCP Symposium November 2013 Quantum Secure s Focus on FICAM and Related Standards Complete Suite of Physical Iden:ty
B2B Offerings. Helping businesses op2mize. Infolob s amazing b2b offerings helps your company achieve maximum produc2vity
 B2B Offerings Helping businesses op2mize Infolob s amazing b2b offerings helps your company achieve maximum produc2vity What is B2B? B2B is shorthand for the sales prac4ce called business- to- business
B2B Offerings Helping businesses op2mize Infolob s amazing b2b offerings helps your company achieve maximum produc2vity What is B2B? B2B is shorthand for the sales prac4ce called business- to- business
From Big Data to Value
 From Big Data to Value The Power of Master Data Management 2.0 Sergio Juarez SVP Elemica EMEA & LATAM Reveal Oct 2014 Agenda Master Data Management Why Now? What To Do? How To Do It? What s Next? Today
From Big Data to Value The Power of Master Data Management 2.0 Sergio Juarez SVP Elemica EMEA & LATAM Reveal Oct 2014 Agenda Master Data Management Why Now? What To Do? How To Do It? What s Next? Today
Phone Systems Buyer s Guide
 Phone Systems Buyer s Guide Contents How Cri(cal is Communica(on to Your Business? 3 Fundamental Issues 4 Phone Systems Basic Features 6 Features for Users with Advanced Needs 10 Key Ques(ons for All Buyers
Phone Systems Buyer s Guide Contents How Cri(cal is Communica(on to Your Business? 3 Fundamental Issues 4 Phone Systems Basic Features 6 Features for Users with Advanced Needs 10 Key Ques(ons for All Buyers
RFID BASED VEHICLE TRACKING SYSTEM
 RFID BASED VEHICLE TRACKING SYSTEM Operating a managed, busy parking lot can pose significant challenges, especially to a government organization that also owns some of the vehicles in the lot. The parking
RFID BASED VEHICLE TRACKING SYSTEM Operating a managed, busy parking lot can pose significant challenges, especially to a government organization that also owns some of the vehicles in the lot. The parking
Data Warehousing. Yeow Wei Choong Anne Laurent
 Data Warehousing Yeow Wei Choong Anne Laurent Databases Databases are developed on the IDEA that DATA is one of the cri>cal materials of the Informa>on Age Informa>on, which is created by data, becomes
Data Warehousing Yeow Wei Choong Anne Laurent Databases Databases are developed on the IDEA that DATA is one of the cri>cal materials of the Informa>on Age Informa>on, which is created by data, becomes
Big Data. The Big Picture. Our flexible and efficient Big Data solu9ons open the door to new opportuni9es and new business areas
 Big Data The Big Picture Our flexible and efficient Big Data solu9ons open the door to new opportuni9es and new business areas What is Big Data? Big Data gets its name because that s what it is data that
Big Data The Big Picture Our flexible and efficient Big Data solu9ons open the door to new opportuni9es and new business areas What is Big Data? Big Data gets its name because that s what it is data that
!"#$%&'()*#"+,&-(.#,"*'/'.%-*
 !"#$%&'()*#"+,&-(.#,"*'/'.%-*!01234567* #0894:6;90* '!#'?* 15* =@3* 03A* B30346;90* 98* 10=3B46=3C* 59DA643* 894* %0=34E4153* &359F4G3* -606B3:30=* >%&-?* =@6=* E4921C35* =@3* 836=F435* 60C* 8F0G;90671;35*
!"#$%&'()*#"+,&-(.#,"*'/'.%-*!01234567* #0894:6;90* '!#'?* 15* =@3* 03A* B30346;90* 98* 10=3B46=3C* 59DA643* 894* %0=34E4153* &359F4G3* -606B3:30=* >%&-?* =@6=* E4921C35* =@3* 836=F435* 60C* 8F0G;90671;35*
BPO. Accerela*ng Revenue Enhancements Through Sales Support Services
 BPO Accerela*ng Revenue Enhancements Through Sales Support Services What is BPO? Business Process Outsorcing (BPO) is the process of outsourcing specific business func6ons to a third- party service provider
BPO Accerela*ng Revenue Enhancements Through Sales Support Services What is BPO? Business Process Outsorcing (BPO) is the process of outsourcing specific business func6ons to a third- party service provider
Everything You Need to Know about Cloud BI. Freek Kamst
 Everything You Need to Know about Cloud BI Freek Kamst Business Analy2cs Insight, Bussum June 10th, 2014 What s it all about? Has anything changed in the world of BI? Is Cloud Compu2ng a Hype or here to
Everything You Need to Know about Cloud BI Freek Kamst Business Analy2cs Insight, Bussum June 10th, 2014 What s it all about? Has anything changed in the world of BI? Is Cloud Compu2ng a Hype or here to
Strategy and Architecture to Establish 'Smart Plants'
 Strategy and Architecture to Establish 'Smart Plants' About Intrigo We are a solu*on provider of Business Applica:ons focused on orchestra*ng Customer Value Networks in the changing SAP Enterprise technology
Strategy and Architecture to Establish 'Smart Plants' About Intrigo We are a solu*on provider of Business Applica:ons focused on orchestra*ng Customer Value Networks in the changing SAP Enterprise technology
A R o a d t o y o u r C l o u d. Professional Service. C R M a n d C l o u d C o n s u l t i n g
 RM-C A R o a d t o y o u r C l o u d Professional Service C R M a n d C l o u d C o n s u l t i n g CRM-C Highlights! A Unique Cloud CRM Consulting service firm! Specializing in cloud CRM and Office Collaboration
RM-C A R o a d t o y o u r C l o u d Professional Service C R M a n d C l o u d C o n s u l t i n g CRM-C Highlights! A Unique Cloud CRM Consulting service firm! Specializing in cloud CRM and Office Collaboration
Splunk for Networking and SDN
 Copyright 2013 Splunk Inc. Splunk for Networking and SDN Stela Udovicic Senior Product Marke?ng Manager, Splunk #splunkconf Legal No?ces During the course of this presenta?on, we may make forward- looking
Copyright 2013 Splunk Inc. Splunk for Networking and SDN Stela Udovicic Senior Product Marke?ng Manager, Splunk #splunkconf Legal No?ces During the course of this presenta?on, we may make forward- looking
Modernizing EDI: How to Cut Your Migra6on Costs by Over 50%
 Modernizing EDI: How to Cut Your Migra6on Costs by Over 50% EDI Moderniza6on: Before and ABer External Loca;ons, Partners, and Services Customers Suppliers / Service Providers Cloud/SaaS Applica;ons &
Modernizing EDI: How to Cut Your Migra6on Costs by Over 50% EDI Moderniza6on: Before and ABer External Loca;ons, Partners, and Services Customers Suppliers / Service Providers Cloud/SaaS Applica;ons &
The Real Score of Cloud
 The Real Score of Cloud Mayur Sahni Sr. Research Manger IDC Asia/Pacific msahni@idc.com @mayursahni Digital Transformation Changing Role of IT Innova&on Informa&on Business agility Changing role of the
The Real Score of Cloud Mayur Sahni Sr. Research Manger IDC Asia/Pacific msahni@idc.com @mayursahni Digital Transformation Changing Role of IT Innova&on Informa&on Business agility Changing role of the
Cost Effec/ve Approaches to Best Prac/ces in Data Analy/cs for Internal Audit
 Cost Effec/ve Approaches to Best Prac/ces in Data Analy/cs for Internal Audit Presented to: ISACA and IIA Joint Mee/ng October 10, 2014 By Outline Introduc.on The Evolving Role of Internal Audit The importance
Cost Effec/ve Approaches to Best Prac/ces in Data Analy/cs for Internal Audit Presented to: ISACA and IIA Joint Mee/ng October 10, 2014 By Outline Introduc.on The Evolving Role of Internal Audit The importance
EAI. Op'mizing your integra'on cost. Sunil Kumar Pandey Persistent Systems Ltd. Session: 20188
 EAI Op'mizing your integra'on cost Sunil Kumar Pandey Persistent Systems Ltd. Session: 20188 EAI need and challenges Mergers and acquisi'ons have become more common than ever before. Current economic situa'on
EAI Op'mizing your integra'on cost Sunil Kumar Pandey Persistent Systems Ltd. Session: 20188 EAI need and challenges Mergers and acquisi'ons have become more common than ever before. Current economic situa'on
Project Por)olio Management
 Project Por)olio Management Important markers for IT intensive businesses Rest assured with Infolob s project management methodologies What is Project Por)olio Management? Project Por)olio Management (PPM)
Project Por)olio Management Important markers for IT intensive businesses Rest assured with Infolob s project management methodologies What is Project Por)olio Management? Project Por)olio Management (PPM)
How To Grow A Data Center System
 Zettaset Big Data Ecosystem Discussion Guide Jim Vogt, President & CEO, Zettaset June 20, 2014 The informa,on provided in this document cons,tutes confiden,al and proprietary informa,on of Ze8aset, Inc.
Zettaset Big Data Ecosystem Discussion Guide Jim Vogt, President & CEO, Zettaset June 20, 2014 The informa,on provided in this document cons,tutes confiden,al and proprietary informa,on of Ze8aset, Inc.
Interna'onal Standards Ac'vi'es on Cloud Security EVA KUIPER, CISA CISSP EVA.KUIPER@HP.COM HP ENTERPRISE SECURITY SERVICES
 Interna'onal Standards Ac'vi'es on Cloud Security EVA KUIPER, CISA CISSP EVA.KUIPER@HP.COM HP ENTERPRISE SECURITY SERVICES Agenda Importance of Common Cloud Standards Outline current work undertaken Define
Interna'onal Standards Ac'vi'es on Cloud Security EVA KUIPER, CISA CISSP EVA.KUIPER@HP.COM HP ENTERPRISE SECURITY SERVICES Agenda Importance of Common Cloud Standards Outline current work undertaken Define
Service-oriented architecture in e-commerce applications
 Service-oriented architecture in e-commerce applications What is a Service Oriented Architecture? Depends on who you ask Web Services A technical architecture An evolution of distributed computing and
Service-oriented architecture in e-commerce applications What is a Service Oriented Architecture? Depends on who you ask Web Services A technical architecture An evolution of distributed computing and
Day 3: Modeling and ERP Reference Architectures
 Day 3: Modeling and ERP Reference Architectures CIS Department Professor Duane Truex III Air Force Mentor-Protégé Enterprise Reference Architectures Ronald E. Giachetti, Ph.D. Associate Professor Industrial
Day 3: Modeling and ERP Reference Architectures CIS Department Professor Duane Truex III Air Force Mentor-Protégé Enterprise Reference Architectures Ronald E. Giachetti, Ph.D. Associate Professor Industrial
Why Migrate to the Cloud. ABSS Solutions, Inc. 2014
 Why Migrate to the Cloud ABSS Solutions, Inc. 2014 ASI Cloud Services Information Systems Basics Cloud Fundamentals Cloud Options Why Move to the Cloud Our Service Providers Our Process Information System
Why Migrate to the Cloud ABSS Solutions, Inc. 2014 ASI Cloud Services Information Systems Basics Cloud Fundamentals Cloud Options Why Move to the Cloud Our Service Providers Our Process Information System
Applying Business Architecture to the Cloud
 Applying Business Architecture to the Cloud Mike Rosen, Chief Scientist Mike.Rosen@ WiltonConsultingGroup.com Michael Rosen Agenda n What do we mean by the cloud? n Sample architecture and cloud support
Applying Business Architecture to the Cloud Mike Rosen, Chief Scientist Mike.Rosen@ WiltonConsultingGroup.com Michael Rosen Agenda n What do we mean by the cloud? n Sample architecture and cloud support
SOA Myth or Reality??
 IBM TRAINING S04 SOA Myth or Reality Jaqui Lynch IBM Corporation 2007 SOA Myth or Reality?? Jaqui Lynch Mainline Information Systems Email jaqui.lynch@mainline.com Session S04 http://www.circle4.com/papers/s04soa.pdf
IBM TRAINING S04 SOA Myth or Reality Jaqui Lynch IBM Corporation 2007 SOA Myth or Reality?? Jaqui Lynch Mainline Information Systems Email jaqui.lynch@mainline.com Session S04 http://www.circle4.com/papers/s04soa.pdf
ERP Misfit Analysis. Air Force Mentor-Protégé Program. ERP Methodology and Project Management 1. Ronald E. Giachetti, Ph.D. Duane P. Truex, Ph.D.
 Air Force Mentor-Protégé Program ERP Misfit Analysis Ronald E. Giachetti, Ph.D. Associate Professor Industrial and Systems Engineering Florida International University Duane P. Truex, Ph.D. Associate Professor
Air Force Mentor-Protégé Program ERP Misfit Analysis Ronald E. Giachetti, Ph.D. Associate Professor Industrial and Systems Engineering Florida International University Duane P. Truex, Ph.D. Associate Professor
ebusiness Web Hosting Alternatives Considerations Self hosting Internet Service Provider (ISP) hosting
 ebusiness Web Hosting and E-Business Software Web Hosting Alternatives Self hosting Internet Service Provider (ISP) hosting Commerce Service Provider (CSP) hosting Shared hosting Dedicated hosting Considerations
ebusiness Web Hosting and E-Business Software Web Hosting Alternatives Self hosting Internet Service Provider (ISP) hosting Commerce Service Provider (CSP) hosting Shared hosting Dedicated hosting Considerations
Web Services - Consultant s View. From IT Stategy to IT Architecture. Agenda. Introduction
 Web Services - A Consultant s View From IT Stategy to IT Architecture Hans-Peter Hoidn, Timothy Jones, Jürg Baumann, Oliver Vogel February 12, 2003 Copyright IBM Corporation 2002 Agenda Introduction I.
Web Services - A Consultant s View From IT Stategy to IT Architecture Hans-Peter Hoidn, Timothy Jones, Jürg Baumann, Oliver Vogel February 12, 2003 Copyright IBM Corporation 2002 Agenda Introduction I.
Tim Blevins Execu;ve Director Labor and Revenue Solu;ons. FTA Technology Conference August 4th, 2015
 Tim Blevins Execu;ve Director Labor and Revenue Solu;ons FTA Technology Conference August 4th, 2015 Governance and Organiza;onal Strategy PaIerns of Fraud and Abuse in Government What tools can we use
Tim Blevins Execu;ve Director Labor and Revenue Solu;ons FTA Technology Conference August 4th, 2015 Governance and Organiza;onal Strategy PaIerns of Fraud and Abuse in Government What tools can we use
Radio Frequency Identification (RFID) An Overview
 Radio Frequency Identification (RFID) An Overview How RFID Is Changing the Business Environment Today Radio frequency identification (RFID) technology has been in use for several decades to track and identify
Radio Frequency Identification (RFID) An Overview How RFID Is Changing the Business Environment Today Radio frequency identification (RFID) technology has been in use for several decades to track and identify
GAME-CHANGING TRENDS IN SUPPLY CHAIN
 customer teams FIRST focused ANNUAL on serving REPORT override system designations BY THE of SUPPLY available CHAIN MANAGEMENT FACULTY AT THE The research partners at UNIVERSITY Ernst and Young OF TENNESSEE
customer teams FIRST focused ANNUAL on serving REPORT override system designations BY THE of SUPPLY available CHAIN MANAGEMENT FACULTY AT THE The research partners at UNIVERSITY Ernst and Young OF TENNESSEE
Hunk & Elas=c MapReduce: Big Data Analy=cs on AWS
 Copyright 2014 Splunk Inc. Hunk & Elas=c MapReduce: Big Data Analy=cs on AWS Dritan Bi=ncka BD Solu=ons Architecture Disclaimer During the course of this presenta=on, we may make forward looking statements
Copyright 2014 Splunk Inc. Hunk & Elas=c MapReduce: Big Data Analy=cs on AWS Dritan Bi=ncka BD Solu=ons Architecture Disclaimer During the course of this presenta=on, we may make forward looking statements
CHAPTER 1 INTRODUCTION
 1 CHAPTER 1 INTRODUCTION Internet has revolutionized the world. There seems to be no limit to the imagination of how computers can be used to help mankind. Enterprises are typically comprised of hundreds
1 CHAPTER 1 INTRODUCTION Internet has revolutionized the world. There seems to be no limit to the imagination of how computers can be used to help mankind. Enterprises are typically comprised of hundreds
Service Oriented Architecture (SOA) An Introduction
 Oriented Architecture (SOA) An Introduction Application Evolution Time Oriented Applications Monolithic Applications Mainframe Client / Server Distributed Applications DCE/RPC CORBA DCOM EJB s Messages
Oriented Architecture (SOA) An Introduction Application Evolution Time Oriented Applications Monolithic Applications Mainframe Client / Server Distributed Applications DCE/RPC CORBA DCOM EJB s Messages
Research on the Model of Enterprise Application Integration with Web Services
 Research on the Model of Enterprise Integration with Web Services XIN JIN School of Information, Central University of Finance& Economics, Beijing, 100081 China Abstract: - In order to improve business
Research on the Model of Enterprise Integration with Web Services XIN JIN School of Information, Central University of Finance& Economics, Beijing, 100081 China Abstract: - In order to improve business
Service-Oriented Architecture: Analysis, the Keys to Success!
 Service-Oriented Architecture: Analysis, the Keys to Success! Presented by: William F. Nazzaro CTO, Inc. bill@iconatg.com www.iconatg.com Introduction Service-Oriented Architecture is hot, but we seem
Service-Oriented Architecture: Analysis, the Keys to Success! Presented by: William F. Nazzaro CTO, Inc. bill@iconatg.com www.iconatg.com Introduction Service-Oriented Architecture is hot, but we seem
Solving today's integra@on challenges with Oracle SOA Suite, and Oracle Coherence
 Solving today's integra@on challenges with Oracle SOA Suite, and Oracle Coherence Asaf Lev Sales Consul@ng asaf.lev@oracle.com Agenda Industry Trends Oracle SOA Suite Oracle Coherence Oracle Service Bus
Solving today's integra@on challenges with Oracle SOA Suite, and Oracle Coherence Asaf Lev Sales Consul@ng asaf.lev@oracle.com Agenda Industry Trends Oracle SOA Suite Oracle Coherence Oracle Service Bus
How To Perform a SaaS Applica7on Inventory in. 5Simple Steps. A Guide for Informa7on Security Professionals. Share this ebook
 How To Perform a SaaS Applica7on Inventory in 5Simple Steps A Guide for Informa7on Security Professionals WHY SHOULD I READ THIS? This book will help you, the person in the organiza=on who cares deeply
How To Perform a SaaS Applica7on Inventory in 5Simple Steps A Guide for Informa7on Security Professionals WHY SHOULD I READ THIS? This book will help you, the person in the organiza=on who cares deeply
Privileged Administra0on Best Prac0ces :: September 1, 2015
 Privileged Administra0on Best Prac0ces :: September 1, 2015 Discussion Contents Privileged Access and Administra1on Best Prac1ces 1) Overview of Capabili0es Defini0on of Need 2) Preparing your PxM Program
Privileged Administra0on Best Prac0ces :: September 1, 2015 Discussion Contents Privileged Access and Administra1on Best Prac1ces 1) Overview of Capabili0es Defini0on of Need 2) Preparing your PxM Program
Emerging Technologies Shaping the Future of Data Warehouses & Business Intelligence
 Emerging Technologies Shaping the Future of Data Warehouses & Business Intelligence Service Oriented Architecture SOA and Web Services John O Brien President and Executive Architect Zukeran Technologies
Emerging Technologies Shaping the Future of Data Warehouses & Business Intelligence Service Oriented Architecture SOA and Web Services John O Brien President and Executive Architect Zukeran Technologies
1 Actuate Corpora-on 2013. Big Data Business Analy/cs
 1 Big Data Business Analy/cs Introducing BIRT Analy3cs Provides analysts and business users with advanced visual data discovery and predictive analytics to make better, more timely decisions in the age
1 Big Data Business Analy/cs Introducing BIRT Analy3cs Provides analysts and business users with advanced visual data discovery and predictive analytics to make better, more timely decisions in the age
Effec%ve AX 2012 Upgrade Project Planning and Microso< Sure Step. Arbela Technologies
 Effec%ve AX 2012 Upgrade Project Planning and Microso< Sure Step Arbela Technologies Why Upgrade? What to do? How to do it? Tools and templates Agenda Sure Step 2012 Ax2012 Upgrade specific steps Checklist
Effec%ve AX 2012 Upgrade Project Planning and Microso< Sure Step Arbela Technologies Why Upgrade? What to do? How to do it? Tools and templates Agenda Sure Step 2012 Ax2012 Upgrade specific steps Checklist
Chapter 3. Database Architectures and the Web Transparencies
 Week 2: Chapter 3 Chapter 3 Database Architectures and the Web Transparencies Database Environment - Objec
Week 2: Chapter 3 Chapter 3 Database Architectures and the Web Transparencies Database Environment - Objec
So#ware Defined Radio (SDR) Architecture and Systems Issues
 So#ware Defined Radio (SDR) Architecture and Systems Issues Workshop on Spacecra# Flight So#ware (FSW 09) 2009 11 6 Kenneth J. Peters Jet Propulsion Laboratory, California Ins9tute of Technology Speaker
So#ware Defined Radio (SDR) Architecture and Systems Issues Workshop on Spacecra# Flight So#ware (FSW 09) 2009 11 6 Kenneth J. Peters Jet Propulsion Laboratory, California Ins9tute of Technology Speaker
TECHNOLOGY BRIEF. Business Benefits from Radio Frequency Identification (RFID)
 TECHNOLOGY BRIEF Business Benefits from Radio Frequency Identification (RFID) Executive summary Today the largest government and business enterprises in the world are developing plans to deploy electronic
TECHNOLOGY BRIEF Business Benefits from Radio Frequency Identification (RFID) Executive summary Today the largest government and business enterprises in the world are developing plans to deploy electronic
1) A complete SCM solution includes customers, service providers and partners. Answer: TRUE Diff: 2 Page Ref: 304
 Enterprise Systems for Management, 2e (Motiwalla/Thompson) Chapter 11 Supply Chain Management 1) A complete SCM solution includes customers, service providers and partners. Diff: 2 Page Ref: 304 2) SCM
Enterprise Systems for Management, 2e (Motiwalla/Thompson) Chapter 11 Supply Chain Management 1) A complete SCM solution includes customers, service providers and partners. Diff: 2 Page Ref: 304 2) SCM
Five Factors Driving Businesses to Rethink EDI on IBM i
 Simplify and Accelerate e- Business Integra6on Five Factors Driving Businesses to Rethink EDI on IBM i EDI Change Drivers External Loca6ons, Partners, and Services Customers Suppliers / Service Providers
Simplify and Accelerate e- Business Integra6on Five Factors Driving Businesses to Rethink EDI on IBM i EDI Change Drivers External Loca6ons, Partners, and Services Customers Suppliers / Service Providers
Distributed systems. Distributed Systems Architectures
 Distributed systems Distributed Systems Architectures Virtually all large computer-based systems are now distributed systems. Information processing is distributed over several computers rather than confined
Distributed systems Distributed Systems Architectures Virtually all large computer-based systems are now distributed systems. Information processing is distributed over several computers rather than confined
Proposal for a Vehicle Tracking System (VTS)
 Proposal for a Vehicle Tracking System (VTS) 2 Executive Summary Intelligent Instructions is an IT product development and consulting company. At Intelligent Instructions, we focus on the needs of the
Proposal for a Vehicle Tracking System (VTS) 2 Executive Summary Intelligent Instructions is an IT product development and consulting company. At Intelligent Instructions, we focus on the needs of the
Getting Real with Policies for Software Defined Infrastructure. Manish Dave Principal Engineer, Intel IT
 Getting Real with Policies for Software Defined Infrastructure Manish Dave Principal Engineer, Intel IT Manish Dave, Principal Engineer, Intel IT Network Security Architect @ Intel IT 15+ years of experience
Getting Real with Policies for Software Defined Infrastructure Manish Dave Principal Engineer, Intel IT Manish Dave, Principal Engineer, Intel IT Network Security Architect @ Intel IT 15+ years of experience
Qubera Solu+ons Access Governance a next genera0on approach to Iden0ty Management
 Qubera Solu+ons Access Governance a next genera0on approach to Iden0ty Management Presented by: Toby Emden Prac0ce Director Iden0ty Management and Access Governance Agenda Typical Business Drivers for
Qubera Solu+ons Access Governance a next genera0on approach to Iden0ty Management Presented by: Toby Emden Prac0ce Director Iden0ty Management and Access Governance Agenda Typical Business Drivers for
The Evolu*on of Service Management
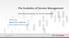 The Evolu*on of Extending Disciplines Across the Enterprise Michael Jones Regional CTO - Architecture Michael.Jones@servicenow.com 2015 Now All Rights Reserved 1 How work gets done today! Emails Spreadsheets
The Evolu*on of Extending Disciplines Across the Enterprise Michael Jones Regional CTO - Architecture Michael.Jones@servicenow.com 2015 Now All Rights Reserved 1 How work gets done today! Emails Spreadsheets
CONDIS. IT Service Management and CMDB
 CONDIS IT Service and CMDB 2/17 Table of contents 1. Executive Summary... 3 2. ITIL Overview... 4 2.1 How CONDIS supports ITIL processes... 5 2.1.1 Incident... 5 2.1.2 Problem... 5 2.1.3 Configuration...
CONDIS IT Service and CMDB 2/17 Table of contents 1. Executive Summary... 3 2. ITIL Overview... 4 2.1 How CONDIS supports ITIL processes... 5 2.1.1 Incident... 5 2.1.2 Problem... 5 2.1.3 Configuration...
The Drug Quality & Security Act
 The Drug Quality & Security Act Drug Traceability & Interoperable Exchange of Transaction Information, History & Statement Mujadala Abdul-Majid 3E Company February 20, 2014 About 3E Company About 3E Supply
The Drug Quality & Security Act Drug Traceability & Interoperable Exchange of Transaction Information, History & Statement Mujadala Abdul-Majid 3E Company February 20, 2014 About 3E Company About 3E Supply
Cloudian The Storage Evolution to the Cloud.. Cloudian Inc. Pre Sales Engineering
 Cloudian The Storage Evolution to the Cloud.. Cloudian Inc. Pre Sales Engineering Agenda Industry Trends Cloud Storage Evolu4on of Storage Architectures Storage Connec4vity redefined S3 Cloud Storage Use
Cloudian The Storage Evolution to the Cloud.. Cloudian Inc. Pre Sales Engineering Agenda Industry Trends Cloud Storage Evolu4on of Storage Architectures Storage Connec4vity redefined S3 Cloud Storage Use
Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions. July, 2006. Developed by: Smart Card Alliance Identity Council
 Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions July, 2006 Developed by: Smart Card Alliance Identity Council Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked
Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked Questions July, 2006 Developed by: Smart Card Alliance Identity Council Contactless Smart Cards vs. EPC Gen 2 RFID Tags: Frequently Asked
Kaseya Fundamentals Workshop DAY THREE. Developed by Kaseya University. Powered by IT Scholars
 Kaseya Fundamentals Workshop DAY THREE Developed by Kaseya University Powered by IT Scholars Kaseya Version 6.5 Last updated March, 2014 Day Two Overview Day Two Lab Review Patch Management Configura;on
Kaseya Fundamentals Workshop DAY THREE Developed by Kaseya University Powered by IT Scholars Kaseya Version 6.5 Last updated March, 2014 Day Two Overview Day Two Lab Review Patch Management Configura;on
AVOIDING SILOED DATA AND SILOED DATA MANAGEMENT
 AVOIDING SILOED DATA AND SILOED DATA MANAGEMENT Dalton Cervo Author, Consultant, Management Expert September 2015 This presenta?on contains extracts from books that are: Copyright 2011 John Wiley & Sons,
AVOIDING SILOED DATA AND SILOED DATA MANAGEMENT Dalton Cervo Author, Consultant, Management Expert September 2015 This presenta?on contains extracts from books that are: Copyright 2011 John Wiley & Sons,
Financial Fraud Threats & Preven3on. Mark Frank EVP, Senior Opera3ons Officer Colorado Business Bank
 Financial Fraud Threats & Preven3on Mark Frank EVP, Senior Opera3ons Officer Colorado Business Bank Why Pay ACen3on to Fraud Risks? Fraud occurs everywhere, and NO organiza3on is immune Changing business
Financial Fraud Threats & Preven3on Mark Frank EVP, Senior Opera3ons Officer Colorado Business Bank Why Pay ACen3on to Fraud Risks? Fraud occurs everywhere, and NO organiza3on is immune Changing business
Unlocking the Power of SOA with Business Process Modeling
 White Paper Unlocking the Power of SOA with Business Process Modeling Business solutions through information technology TM Entire contents 2006 by CGI Group Inc. All rights reserved. Reproduction of this
White Paper Unlocking the Power of SOA with Business Process Modeling Business solutions through information technology TM Entire contents 2006 by CGI Group Inc. All rights reserved. Reproduction of this
Help Framework. Ticket Management Ticket Resolu/on Communica/ons. Ticket Assignment Follow up Customer - communica/on System updates Delay management
 Help for JD Edwards Our Help Framework Ticket qualifica/on Ticket crea/on Ticket Rou/ng Closures L1 issues Resolu/on KG SOPs Co- ordinate Ticket Assignment Follow up Customer - communica/on System updates
Help for JD Edwards Our Help Framework Ticket qualifica/on Ticket crea/on Ticket Rou/ng Closures L1 issues Resolu/on KG SOPs Co- ordinate Ticket Assignment Follow up Customer - communica/on System updates
IT Asset Management Best Practices Using RFID. Stephen Schwartz
 IT Asset Management Best Practices Using RFID Stephen Schwartz 1 Agenda IAITAM Functional Areas ITAM Best Practice Areas for RFID Asset Life Cycle Process Understanding Your Policies & Processes Suggested
IT Asset Management Best Practices Using RFID Stephen Schwartz 1 Agenda IAITAM Functional Areas ITAM Best Practice Areas for RFID Asset Life Cycle Process Understanding Your Policies & Processes Suggested
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means
 EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
EMV and Chip Cards Key Information On What This Is, How It Works and What It Means Document Purpose This document is intended to provide information about the concepts behind and the processes involved
Infinite Integration: Unlocking the Value of Enterprise Asset Management through Technology Integration May 2010
 Infinite Integration: Unlocking the Value of Enterprise Asset Management through Technology Integration May 2010 RFID, GPS, sensor, and other auto-id technologies promise to revolutionize enterprise asset
Infinite Integration: Unlocking the Value of Enterprise Asset Management through Technology Integration May 2010 RFID, GPS, sensor, and other auto-id technologies promise to revolutionize enterprise asset
YOUR PROCESS MANAGEMENT AND CONTROLLING SUITE FOR MULTI-CHANNEL ONLINE MARKETING.!
 YOUR PROCESS MANAGEMENT AND CONTROLLING SUITE FOR MULTI-CHANNEL ONLINE MARKETING.! AGENDA! 1. Challenges of Online Marke3ng 2. Applicata helps 3. Benefit and Pricing 4. About us! DIFFERENT STAKEHOLDER
YOUR PROCESS MANAGEMENT AND CONTROLLING SUITE FOR MULTI-CHANNEL ONLINE MARKETING.! AGENDA! 1. Challenges of Online Marke3ng 2. Applicata helps 3. Benefit and Pricing 4. About us! DIFFERENT STAKEHOLDER
configurability compares with typical SIEM & Log Management systems Able to install collectors on remote sites rather than pull all data
 Software Comparison Sheet SIEM & Log OpViewTM from Software leverages a completely new database architecture to deliver the most flexible monitoring system available on the market today. This award-winning
Software Comparison Sheet SIEM & Log OpViewTM from Software leverages a completely new database architecture to deliver the most flexible monitoring system available on the market today. This award-winning
CFCFA Logistics Management Training Supply Chain Management Technology
 Your Logo Here CFCFA Logistics Management Training Supply Chain Management Technology Supply Chain Management Technology Supply Chain Management Location Tracking Technologies Satellite-based Positioning
Your Logo Here CFCFA Logistics Management Training Supply Chain Management Technology Supply Chain Management Technology Supply Chain Management Location Tracking Technologies Satellite-based Positioning
configurability compares with typical Asset Monitoring systems Able to install collectors on remote sites rather than pull all data
 Software Comparison Sheet OpViewTM from Software leverages a completely new database architecture to deliver the most flexible monitoring system available on the market today. This award-winning solution
Software Comparison Sheet OpViewTM from Software leverages a completely new database architecture to deliver the most flexible monitoring system available on the market today. This award-winning solution
SharePoint Capacity Planning Balancing Organiza,onal Requirements with Performance and Cost
 SharePoint Capacity Planning Balancing Organiza,onal Requirements with Performance and Cost Kirk Devore / J.D. Wade SharePoint Consultants Horizons Consul;ng Agenda Expecta;ons Defining SharePoint Capacity
SharePoint Capacity Planning Balancing Organiza,onal Requirements with Performance and Cost Kirk Devore / J.D. Wade SharePoint Consultants Horizons Consul;ng Agenda Expecta;ons Defining SharePoint Capacity
Discovering Computers Fundamentals, 2010 Edition. Living in a Digital World
 Discovering Computers Fundamentals, 2010 Edition Living in a Digital World Objec&ves Overview Discuss the importance of project management, feasibility assessment, documenta8on, and data and informa8on
Discovering Computers Fundamentals, 2010 Edition Living in a Digital World Objec&ves Overview Discuss the importance of project management, feasibility assessment, documenta8on, and data and informa8on
ORION Retail Systems. Orion Digital Integration Inc. Point of Sale Reinvented for a Mobile World
 ORION Retail Systems Orion Digital Integration Inc Point of Sale Reinvented for a Mobile World O Orion Retail Systems ORION Digital Integraon Inc. - Corporate Profile Established in 2003, Orion Digital
ORION Retail Systems Orion Digital Integration Inc Point of Sale Reinvented for a Mobile World O Orion Retail Systems ORION Digital Integraon Inc. - Corporate Profile Established in 2003, Orion Digital
Fixed Scope Offering (FSO) for Oracle SRM
 Fixed Scope Offering (FSO) for Oracle SRM Agenda iapps Introduc.on Execu.ve Summary Business Objec.ves Solu.on Proposal Scope - Business Process Scope Applica.on Implementa.on Methodology Time Frames Team,
Fixed Scope Offering (FSO) for Oracle SRM Agenda iapps Introduc.on Execu.ve Summary Business Objec.ves Solu.on Proposal Scope - Business Process Scope Applica.on Implementa.on Methodology Time Frames Team,
San Francisco Chapter. Presented by Mike O. Villegas, CISA, CISSP
 Presented by Mike O. Villegas, CISA, CISSP Agenda Information Security (IS) Vision at Newegg.com Typical Issues at Most Organizations Information Security Governance Four Inter-related CoBIT Domains ISO
Presented by Mike O. Villegas, CISA, CISSP Agenda Information Security (IS) Vision at Newegg.com Typical Issues at Most Organizations Information Security Governance Four Inter-related CoBIT Domains ISO
8/25/2008. Chapter Objectives PART 3. Concepts in Enterprise Resource Planning 2 nd Edition
 Concepts in Enterprise Resource Planning 2 nd Edition Chapter 2 The Development of Enterprise Resource Planning Systems Chapter Objectives Identify the factors that led to the development of Enterprise
Concepts in Enterprise Resource Planning 2 nd Edition Chapter 2 The Development of Enterprise Resource Planning Systems Chapter Objectives Identify the factors that led to the development of Enterprise
RF-Enabled Applications and Technology: Comparing and Contrasting RFID and RF-Enabled Smart Cards
 RF-Enabled Applications and Technology: Comparing and Contrasting RFID and RF-Enabled Smart Cards January 2007 Developed by: Smart Card Alliance Identity Council RF-Enabled Applications and Technology:
RF-Enabled Applications and Technology: Comparing and Contrasting RFID and RF-Enabled Smart Cards January 2007 Developed by: Smart Card Alliance Identity Council RF-Enabled Applications and Technology:
EAI OVERVIEW OF ENTERPRISE APPLICATION INTEGRATION CONCEPTS AND ARCHITECTURES. Enterprise Application Integration. Peter R. Egli INDIGOO.
 EAI OVERVIEW OF ENTERPRISE APPLICATION INTEGRATION CONCEPTS AND ARCHITECTURES Peter R. Egli INDIGOO.COM 1/16 Contents 1. EAI versus SOA versus ESB 2. EAI 3. SOA 4. ESB 5. N-tier enterprise architecture
EAI OVERVIEW OF ENTERPRISE APPLICATION INTEGRATION CONCEPTS AND ARCHITECTURES Peter R. Egli INDIGOO.COM 1/16 Contents 1. EAI versus SOA versus ESB 2. EAI 3. SOA 4. ESB 5. N-tier enterprise architecture
MIFARE CONTACTLESS CARD TECHNOLOLGY AN HID WHITE PAPER
 MIFARE CONTACTLESS CARD TECHNOLOLGY AN HID WHITE PAPER GENERAL The MIFARE contactless smart card and MIFARE card reader/writer were developed to handle payment transactions for public transportation systems.
MIFARE CONTACTLESS CARD TECHNOLOLGY AN HID WHITE PAPER GENERAL The MIFARE contactless smart card and MIFARE card reader/writer were developed to handle payment transactions for public transportation systems.
ebusiness Web Hosting Alternatives Self hosting Internet Service Provider (ISP) hosting Commerce Service Provider (CSP) hosting
 ebusiness Web Hosting and E-Business Software Web Hosting Alternatives Self hosting Internet Service Provider (ISP) hosting Commerce Service Provider (CSP) hosting Shared hosting Dedicated hosting 1 Considerations
ebusiness Web Hosting and E-Business Software Web Hosting Alternatives Self hosting Internet Service Provider (ISP) hosting Commerce Service Provider (CSP) hosting Shared hosting Dedicated hosting 1 Considerations
An Integrated Approach to Manage IT Network Traffic - An Overview Click to edit Master /tle style
 An Integrated Approach to Manage IT Network Traffic - An Overview Click to edit Master /tle style Agenda A quick look at ManageEngine Tradi/onal Traffic Analysis Techniques & Tools Changing face of Network
An Integrated Approach to Manage IT Network Traffic - An Overview Click to edit Master /tle style Agenda A quick look at ManageEngine Tradi/onal Traffic Analysis Techniques & Tools Changing face of Network
Service-Oriented Architecture and its Implications for Software Life Cycle Activities
 Service-Oriented Architecture and its Implications for Software Life Cycle Activities Grace A. Lewis Software Engineering Institute Integration of Software-Intensive Systems (ISIS) Initiative Agenda SOA:
Service-Oriented Architecture and its Implications for Software Life Cycle Activities Grace A. Lewis Software Engineering Institute Integration of Software-Intensive Systems (ISIS) Initiative Agenda SOA:
Texas Digital Government Summit. Data Analysis Structured vs. Unstructured Data. Presented By: Dave Larson
 Texas Digital Government Summit Data Analysis Structured vs. Unstructured Data Presented By: Dave Larson Speaker Bio Dave Larson Solu6ons Architect with Freeit Data Solu6ons In the IT industry for over
Texas Digital Government Summit Data Analysis Structured vs. Unstructured Data Presented By: Dave Larson Speaker Bio Dave Larson Solu6ons Architect with Freeit Data Solu6ons In the IT industry for over
Unifi Technology Group & Software Toolbox, Inc. Executive Summary. Building the Infrastructure for emanufacturing
 Unifi Technology Group & Software Toolbox, Inc. Executive Summary Building the Infrastructure for emanufacturing Building the Infrastructure for emanufacturing The term emanufacturing has emerged over
Unifi Technology Group & Software Toolbox, Inc. Executive Summary Building the Infrastructure for emanufacturing Building the Infrastructure for emanufacturing The term emanufacturing has emerged over
Cloud Computing & Service Oriented Architecture An Overview
 Cloud Computing & Service Oriented Architecture An Overview Sumantra Sarkar Georgia State University Robinson College of Business November 29 & 30, 2010 MBA 8125 Fall 2010 Agenda Cloud Computing Definition
Cloud Computing & Service Oriented Architecture An Overview Sumantra Sarkar Georgia State University Robinson College of Business November 29 & 30, 2010 MBA 8125 Fall 2010 Agenda Cloud Computing Definition
WebSphere Cast Iron Cloud integration
 Cast Iron Cloud integration Integrate in days Highlights Speeds up time to implementation for Cloud and on premise integration projects with configuration, not coding approach Offers cost savings with
Cast Iron Cloud integration Integrate in days Highlights Speeds up time to implementation for Cloud and on premise integration projects with configuration, not coding approach Offers cost savings with
How To Understand The Power Of An Freddi Tag (Rfid) System
 Radio Frequency Identification Done by: Haitham Habli. Table of contents Definition of RFID. Do they need license? RFID vs other identification systems. Classification of RFID systems. Emerge of passive
Radio Frequency Identification Done by: Haitham Habli. Table of contents Definition of RFID. Do they need license? RFID vs other identification systems. Classification of RFID systems. Emerge of passive
SOA for Healthcare: Promises and Pitfalls
 SOA for Healthcare: Promises and Pitfalls Dennis B. Smith dbs@sei.cmu.edu SOA in Health Care Conference: Value in a Time of Change Chicago, IL USA June 3, 2009 Agenda Healthcare IT Challenges SOA: The
SOA for Healthcare: Promises and Pitfalls Dennis B. Smith dbs@sei.cmu.edu SOA in Health Care Conference: Value in a Time of Change Chicago, IL USA June 3, 2009 Agenda Healthcare IT Challenges SOA: The
Webinar: Having the Best of Both World- Class Customer Experience and Comprehensive Iden=ty Security
 Webinar: Having the Best of Both World- Class Customer Experience and Comprehensive Iden=ty Security With Iden>ty Expert and UnboundID Customer Bill Bonney Today s Speakers Bill Bonney Formerly Director,
Webinar: Having the Best of Both World- Class Customer Experience and Comprehensive Iden=ty Security With Iden>ty Expert and UnboundID Customer Bill Bonney Today s Speakers Bill Bonney Formerly Director,
Getting started with API testing
 Technical white paper Getting started with API testing Test all layers of your composite applications, not just the GUI Table of contents Executive summary... 3 Introduction... 3 Who should read this document?...
Technical white paper Getting started with API testing Test all layers of your composite applications, not just the GUI Table of contents Executive summary... 3 Introduction... 3 Who should read this document?...
GEOG 482/582 : GIS Data Management. Lesson 10: Enterprise GIS Data Management Strategies GEOG 482/582 / My Course / University of Washington
 GEOG 482/582 : GIS Data Management Lesson 10: Enterprise GIS Data Management Strategies Overview Learning Objective Questions: 1. What are challenges for multi-user database environments? 2. What is Enterprise
GEOG 482/582 : GIS Data Management Lesson 10: Enterprise GIS Data Management Strategies Overview Learning Objective Questions: 1. What are challenges for multi-user database environments? 2. What is Enterprise
IT Architecture Review. ISACA Conference Fall 2003
 IT Architecture Review ISACA Conference Fall 2003 Table of Contents Introduction Business Drivers Overview of Tiered Architecture IT Architecture Review Why review IT architecture How to conduct IT architecture
IT Architecture Review ISACA Conference Fall 2003 Table of Contents Introduction Business Drivers Overview of Tiered Architecture IT Architecture Review Why review IT architecture How to conduct IT architecture
Whitepaper. Security Best Practices for Evaluating Google Apps Marketplace Applications. Introduction. At a Glance
 Whitepaper Security Best Practices for Evaluating Google Apps Marketplace Applications At a Glance Intended Audience: Security Officers CIOs of large enterprises evaluating Google Apps Marketplace applications
Whitepaper Security Best Practices for Evaluating Google Apps Marketplace Applications At a Glance Intended Audience: Security Officers CIOs of large enterprises evaluating Google Apps Marketplace applications
Asset Management Services. White Paper
 Asset Management Services White Paper Asset Management Solutions provide a comprehensive and systematic method for managing equipment and intelligence in complex IT infrastructure environments. Through
Asset Management Services White Paper Asset Management Solutions provide a comprehensive and systematic method for managing equipment and intelligence in complex IT infrastructure environments. Through
BIG DATA IN THE SUPPLY CHAIN
 BIG DATA IN THE SUPPLY CHAIN 1 HOW COMPANIES ARE USING DATA TO EXTRACT ACTIONABLE INSIGHT TO OPTIMIZE THEIR SUPPLY CHAINS Prior to investing resources into big data systems, software and people, firms
BIG DATA IN THE SUPPLY CHAIN 1 HOW COMPANIES ARE USING DATA TO EXTRACT ACTIONABLE INSIGHT TO OPTIMIZE THEIR SUPPLY CHAINS Prior to investing resources into big data systems, software and people, firms
Internationalization and Web Services
 Internationalization and Web Services 25 th Internationalization and Unicode Conference Presented by Addison P. Phillips Director, Globalization Architecture webmethods, Inc. 25 th Internationalization
Internationalization and Web Services 25 th Internationalization and Unicode Conference Presented by Addison P. Phillips Director, Globalization Architecture webmethods, Inc. 25 th Internationalization
3rd Party Assurance & Information Governance 2014-2016 outlook IIA Ireland Annual Conference 2014. Straightforward Security and Compliance
 3rd Party Assurance & Information Governance 2014-2016 outlook IIA Ireland Annual Conference 2014 Continuous Education Services (elearning/workshops) Compliance Management Portals Information Security
3rd Party Assurance & Information Governance 2014-2016 outlook IIA Ireland Annual Conference 2014 Continuous Education Services (elearning/workshops) Compliance Management Portals Information Security
1.264 Lecture 24. Service Oriented Architecture Electronic Data Interchange (EDI) Next class: Anderson chapter 1, 2. Exercise due before class
 1.264 Lecture 24 Service Oriented Architecture Electronic Data Interchange (EDI) Next class: Anderson chapter 1, 2. Exercise due before class 1 B-to-B DB svr Web svr Solution- case study Customer anufacturer,
1.264 Lecture 24 Service Oriented Architecture Electronic Data Interchange (EDI) Next class: Anderson chapter 1, 2. Exercise due before class 1 B-to-B DB svr Web svr Solution- case study Customer anufacturer,
Enterprise Application Designs In Relation to ERP and SOA
 Enterprise Application Designs In Relation to ERP and SOA DESIGNING ENTERPRICE APPLICATIONS HASITH D. YAGGAHAVITA 20 th MAY 2009 Table of Content 1 Introduction... 3 2 Patterns for Service Integration...
Enterprise Application Designs In Relation to ERP and SOA DESIGNING ENTERPRICE APPLICATIONS HASITH D. YAGGAHAVITA 20 th MAY 2009 Table of Content 1 Introduction... 3 2 Patterns for Service Integration...
REST (Representa.onal State Transfer) Ingegneria del So-ware e Lab. Università di Modena e Reggio Emilia Do<. Marzio Franzini
 REST (Representa.onal State Transfer) Ingegneria del So-ware e Lab. Università di Modena e Reggio Emilia Do
REST (Representa.onal State Transfer) Ingegneria del So-ware e Lab. Università di Modena e Reggio Emilia Do
