ParlaMI, Enterprise Instant Messaging
|
|
|
- Nathan Hamilton
- 10 years ago
- Views:
Transcription
1 ParlaMI, Enterprise Instant Messaging A step forward for the optimization and protection of corporate communications Why should you use instant messaging in your business environment? Optimize business communications Connect people anywhere in real time Create individual and group conversations Share reports and documents during the instant chat session ParlaMI, a secure enterprise instant messaging service? Conversations are encrypted and protected by authentication Cost-effective Enables to organize calls and virtual meetings from any device Conversations are filtered against viruses and data breaches Conversations are archive for compliance requirements Why should your company use Parla users have an integrated instant messaging service in their , called ParlaMI, which enables real-time conversations with secure point to point communications between Parla individual users, or groups. Now available fully embedded in Outlook. This new ParlaMI Outlook plug-in, enables end users to enjoy and instant messaging within the same window, avoiding application's overlapping and screen switch over. ParlaMI is also available from the Webmail and the Spamina App. This Instant Messaging App comes with encrypted end-to-end technology, DLP, antimalware and archiving, to ensure that the company communications are protected.
2 ParlaMI optimizes the use of the within organizations, and facilitates interdepartmental communications, with the peace of mind that conversations are encrypted from point to point. When a Parla user starts a session, a tab automatically pops up on his screen advising him to access the chat service without needing to close the application . Now, secure and confidence chat conversations from any device with the NEW application ParlaMI for ios and Android devices
3 ParlaMI Key Features Designed by and for business use End-to-end encryption Integrated in Outlook (2013,2010,2007), Parla web and mobile applications for ios and Android User State Management. (Online, Offline, Away or Busy) Ability to add and delete contacts Display of contact requests sent and received. Integration with the company GAL to add contacts easily Viewing the contact list and public halls groups Search for contacts in the agenda Display the list of conversations on mobile applications User avatar display and ability to include and change the avatar (image associated with a user) Create multi-user chat rooms Possibility to join rooms available Direct invitation to your contacts to join a meeting History of the last sent and received 500 messages Possibility of sending emoticons The rooms can be permanent or deleted when all the participants leave, may be public or private and may be password protected Possibility to register for free to use mobile applications and to communicate with customers paying ParlaMI
4 Available options: IM Archiving: Archiving all conversations with the possibility for the manager of the company to monitor them. Audit log administrator access to any kind of domain users search. Firewall & DLP: Data Lost Prevention (manageable by the administrator of the company from its panel management policies) and protection from malware and malicious url. About Spamina SPAMINA, is a European-based security company that develops and provides corporations with flexible and Secure Digital Communications. Managing and mitigating cyber-crime related risk is critical. Widely known electronic communications means such as , as well as the increasingly used instant messaging, are channels where the corporate digital assets can be jeopardized. Simile Fingerprint Filter proprietary technology protects corporate networks from advanced and zero-day threats. Spamina provides with a safe communication environment where business continuity, service scalability and cost-effectiveness are ensured. Our cloud services range from enterprise secure platform, enterprise mobile management, & IM gateway protection to archiving and encryption & DLP solutions for legal compliance. A cloud environment involves storage and transfer of digital information. Spamina is subject to the most demanding EU regulations in terms of data protection and is committed to ensuring the highest security standards for digital safeguard. More information: Phone:
5
anomaly, thus reported to our central servers.
 Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
European developer & provider ensuring data protection User console: Simile Fingerprint Filter Policies and content filtering rules
 Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Cloud Email Firewall Maximum email availability and protection against phishing and advanced threats. If the company email is not protected then the information is not safe Cloud Email Firewall is a solution
Parla, Secure Cloud Email
 Parla, Secure Cloud Email Secure Email, Instant Messaging, Calendar, Contacts, Tasks, File sharing and Notes across all devices The 1 st Secure Email and Instant Messaging from and European Security Vendor
Parla, Secure Cloud Email Secure Email, Instant Messaging, Calendar, Contacts, Tasks, File sharing and Notes across all devices The 1 st Secure Email and Instant Messaging from and European Security Vendor
Nuove Features MDM ParlaMI ITALIAN SFFv2
 NUOVO RILASCIO Spamina Parla Mailbox is a cloud-based email platform with up to 30GB of mailbox space, providing enterprise-class email, calendar, collaboration and integrated security. Designed to maintain
NUOVO RILASCIO Spamina Parla Mailbox is a cloud-based email platform with up to 30GB of mailbox space, providing enterprise-class email, calendar, collaboration and integrated security. Designed to maintain
Secure Email, Calendar, Contacts, Tasks, File sharing and Notes across devices
 - Secure Email, Calendar, Contacts, Tasks, File sharing and Notes across devices Parla Spamina Parla is a cloud-based Email platform with up to 30Gb of mailbox space providing enterprise-class email, calendar,
- Secure Email, Calendar, Contacts, Tasks, File sharing and Notes across devices Parla Spamina Parla is a cloud-based Email platform with up to 30Gb of mailbox space providing enterprise-class email, calendar,
UNCLASSIFIED. UK Email Archiving powered by Mimecast Service Description
 UNCLASSIFIED 11/12/2015 v2.2 UK Email Archiving powered by Mimecast Service Description Cobweb s UK Email Archiving, powered by Mimecast, provides businesses with a secure, scalable cloud-based message
UNCLASSIFIED 11/12/2015 v2.2 UK Email Archiving powered by Mimecast Service Description Cobweb s UK Email Archiving, powered by Mimecast, provides businesses with a secure, scalable cloud-based message
EMAIL MANAGEMENT SOLUTIONS SAFEGUARD BUSINESS CONTINUITY AND PRODUCTIVITY WITH MIMECAST
 EMAIL MANAGEMENT SOLUTIONS SAFEGUARD BUSINESS CONTINUITY AND PRODUCTIVITY WITH MIMECAST Enabling user efficiency with a cloud-based email platform With productivity, revenues and reputation at stake, an
EMAIL MANAGEMENT SOLUTIONS SAFEGUARD BUSINESS CONTINUITY AND PRODUCTIVITY WITH MIMECAST Enabling user efficiency with a cloud-based email platform With productivity, revenues and reputation at stake, an
HomeNet. Gateway User Guide
 HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
HomeNet Gateway User Guide Gateway User Guide Table of Contents HomeNet Gateway User Guide Gateway User Guide Table of Contents... 2 Introduction... 3 What is the HomeNet Gateway (Gateway)?... 3 How do
SafeMail April 2015. SafeMail Helping your business reach further with email hosted at UK based, ISO 27001, Tier 4 data centres.
 SafeMail April 2015 Secure cloud solutions with guaranteed UK data sovereignty. SafeMail Helping your business reach further with email hosted at UK based, ISO 27001, Tier 4 data centres. Detailing the
SafeMail April 2015 Secure cloud solutions with guaranteed UK data sovereignty. SafeMail Helping your business reach further with email hosted at UK based, ISO 27001, Tier 4 data centres. Detailing the
Email Migration Manual (For Outlook 2010)
 Email Migration Manual (For Outlook 2010) By SYSCOM (USA) May 13, 2013 Version 2.2 1 Contents 1. How to Change POP3/SMTP Setting for Outlook 2010... 3 2. How to Login to Webmail... 10 3. How to Change
Email Migration Manual (For Outlook 2010) By SYSCOM (USA) May 13, 2013 Version 2.2 1 Contents 1. How to Change POP3/SMTP Setting for Outlook 2010... 3 2. How to Login to Webmail... 10 3. How to Change
Why Email Encryption is Essential to the Safety of Your Business
 Why Email Encryption is Essential to the Safety of Your Business What We ll Cover Email is Like a Postcard o The Cost of Unsecured Email 5 Steps to Implement Email Encryption o Know Your Compliance Regulations
Why Email Encryption is Essential to the Safety of Your Business What We ll Cover Email is Like a Postcard o The Cost of Unsecured Email 5 Steps to Implement Email Encryption o Know Your Compliance Regulations
Email Migration Manual (For Outlook Express 6)
 Email Migration Manual (For Outlook Express 6) By SYSCOM (USA) May 13, 2013 Version 1.0 1 Contents 1. How to Change POP3/SMTP Setup for Outlook Express... 3 2. How to Login to Webmail... 7 3. How to Change
Email Migration Manual (For Outlook Express 6) By SYSCOM (USA) May 13, 2013 Version 1.0 1 Contents 1. How to Change POP3/SMTP Setup for Outlook Express... 3 2. How to Login to Webmail... 7 3. How to Change
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Business and enterprise cloud sync, backup and sharing solutions
 Business and enterprise cloud sync, backup and sharing solutions Private Cloud Synchronization Collaboration Backup / Versioning Web Access Mobile Access LDAP / Active Directory Federated RADIUS Single
Business and enterprise cloud sync, backup and sharing solutions Private Cloud Synchronization Collaboration Backup / Versioning Web Access Mobile Access LDAP / Active Directory Federated RADIUS Single
Ibrahim Yusuf Presales Engineer at Sophos [email protected]. Smartphones and BYOD: what are the risks and how do you manage them?
 Ibrahim Yusuf Presales Engineer at Sophos [email protected] Smartphones and BYOD: what are the risks and how do you manage them? Tablets on the rise 2 Diverse 3 The Changing Mobile World Powerful devices
Ibrahim Yusuf Presales Engineer at Sophos [email protected] Smartphones and BYOD: what are the risks and how do you manage them? Tablets on the rise 2 Diverse 3 The Changing Mobile World Powerful devices
Mimecast Unified Email Management
 DATA SHEET Mimecast Unified Email Management An always-on, cloud-based email security solution that reduces the complexity of protecting your organization from malware, spam and data leakage. Mimecast
DATA SHEET Mimecast Unified Email Management An always-on, cloud-based email security solution that reduces the complexity of protecting your organization from malware, spam and data leakage. Mimecast
Ben Hall Technical Pre-Sales Manager
 Ben Hall Technical Pre-Sales Manager LANDESK MDM Solutions Mobility Manager (MDM in the Cloud) Secure User Management Suite with CSA LetMobile (Secure Mobile Email) Core MDM Functionality MDM Functionality
Ben Hall Technical Pre-Sales Manager LANDESK MDM Solutions Mobility Manager (MDM in the Cloud) Secure User Management Suite with CSA LetMobile (Secure Mobile Email) Core MDM Functionality MDM Functionality
Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information.
 Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information. Mobile Devices: Risks to Health Information Risks vary based on the mobile device and its use. Some risks include:
Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information. Mobile Devices: Risks to Health Information Risks vary based on the mobile device and its use. Some risks include:
Email Compliance in 5 Steps
 Email Compliance in 5 Steps Introduction For most businesses, email is a vital communication resource. Used to perform essential business functions, many organizations rely on email to send sensitive confidential
Email Compliance in 5 Steps Introduction For most businesses, email is a vital communication resource. Used to perform essential business functions, many organizations rely on email to send sensitive confidential
V1.4. Spambrella Email Continuity SaaS. August 2
 V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
V1.4 August 2 Spambrella Email Continuity SaaS Easy to implement, manage and use, Message Continuity is a scalable, reliable and secure service with no set-up fees. Built on a highly reliable and scalable
Cyber Security. John Leek Chief Strategist
 Cyber Security John Leek Chief Strategist AGENDA The Changing Business Landscape Acknowledge cybersecurity as an enterprise-wide risk management issue not just an IT issue How to develop a cybersecurity
Cyber Security John Leek Chief Strategist AGENDA The Changing Business Landscape Acknowledge cybersecurity as an enterprise-wide risk management issue not just an IT issue How to develop a cybersecurity
Mailbox control panel. User guide
 Mailbox control panel User guide Close this window Mailbox control panel user guide Mailbox control panels enable you to configure your settings for a specific mailbox with ease, with features ranging
Mailbox control panel User guide Close this window Mailbox control panel user guide Mailbox control panels enable you to configure your settings for a specific mailbox with ease, with features ranging
Intermedia: A Worry-Free Transition to the Cloud
 Hosted Exchange 1 Intermedia: A Worry-Free Transition to the Cloud Identity Management File Sync & Share Email Services Collaboration & File Management Archiving & Backup Mobility Voice Services Security
Hosted Exchange 1 Intermedia: A Worry-Free Transition to the Cloud Identity Management File Sync & Share Email Services Collaboration & File Management Archiving & Backup Mobility Voice Services Security
2013 USER GROUP CONFERENCE
 2013 USER GROUP CONFERENCE The Cloud This session will touch anything and everything cloud based that is important to districts today. We will compare and contrast Google Apps and Office 365, Cloud storage
2013 USER GROUP CONFERENCE The Cloud This session will touch anything and everything cloud based that is important to districts today. We will compare and contrast Google Apps and Office 365, Cloud storage
EndUser Protection. Peter Skondro. Sophos
 EndUser Protection Peter Skondro Sophos Agenda Sophos EndUser Solutions Endpoint Usecases Sophos Mobile Solutions Mobile Usecases Endpoint Sophos EndUser Solutions EndUser Protection AV Firewall Application
EndUser Protection Peter Skondro Sophos Agenda Sophos EndUser Solutions Endpoint Usecases Sophos Mobile Solutions Mobile Usecases Endpoint Sophos EndUser Solutions EndUser Protection AV Firewall Application
Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information.
 Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information. Mobile Devices: Risks to to Health Mobile Information Devices: Risks to Health Information Risks vary based on the
Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information. Mobile Devices: Risks to to Health Mobile Information Devices: Risks to Health Information Risks vary based on the
Endpoint protection for physical and virtual desktops
 datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
datasheet Trend Micro officescan Endpoint protection for physical and virtual desktops In the bring-your-own-device (BYOD) environment, protecting your endpoints against ever-evolving threats has become
Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion
 Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion Many organizations are embracing cloud technology and moving from complex, rigid on-premise infrastructure and software to the simplicity
Strengthen Microsoft Office 365 with Sophos Cloud and Reflexion Many organizations are embracing cloud technology and moving from complex, rigid on-premise infrastructure and software to the simplicity
Web Conferencing Guide for Session Hosts using Microsoft Lync
 Web Conferencing Guide for Session Hosts using Microsoft Lync With MS Lync, faculty and staff can plan and schedule online meetings for collaborative activities with the ability to share audio, video,
Web Conferencing Guide for Session Hosts using Microsoft Lync With MS Lync, faculty and staff can plan and schedule online meetings for collaborative activities with the ability to share audio, video,
Compliance Guide ISO 27002. Compliance Guide. September 2015. Contents. Introduction 1. Detailed Controls Mapping 2.
 ISO 27002 Compliance Guide September 2015 Contents Compliance Guide 01 02 03 Introduction 1 Detailed Controls Mapping 2 About Rapid7 7 01 INTRODUCTION If you re looking for a comprehensive, global framework
ISO 27002 Compliance Guide September 2015 Contents Compliance Guide 01 02 03 Introduction 1 Detailed Controls Mapping 2 About Rapid7 7 01 INTRODUCTION If you re looking for a comprehensive, global framework
How To Get The Most Out Of Your Email From Your Mail Server (For A Small Business)
 Hosted Exchange +SharePoint: Communication and Collaboration This is the next generation of affordable, reliable messaging and portal solutions with Microsoft Exchange 2010 and Microsoft SharePoint 2010.
Hosted Exchange +SharePoint: Communication and Collaboration This is the next generation of affordable, reliable messaging and portal solutions with Microsoft Exchange 2010 and Microsoft SharePoint 2010.
AVG AntiVirus. How does this benefit you?
 AVG AntiVirus Award-winning antivirus protection detects, blocks, and removes viruses and malware from your company s PCs and servers. And like all of our cloud services, there are no license numbers to
AVG AntiVirus Award-winning antivirus protection detects, blocks, and removes viruses and malware from your company s PCs and servers. And like all of our cloud services, there are no license numbers to
Injazat s Managed Services Portfolio
 Injazat s Managed Services Portfolio Overview Premium Managed Services to Transform Your IT Environment Injazat s Premier Tier IV Data Center is built to offer the highest level of security and reliability.
Injazat s Managed Services Portfolio Overview Premium Managed Services to Transform Your IT Environment Injazat s Premier Tier IV Data Center is built to offer the highest level of security and reliability.
2015 USER GROUP CONFERENCE
 2015 USER GROUP CONFERENCE The Cloud This session will touch anything and everything cloud based that is important to districts today. We will compare and contrast Google Apps and Office 365, Cloud storage
2015 USER GROUP CONFERENCE The Cloud This session will touch anything and everything cloud based that is important to districts today. We will compare and contrast Google Apps and Office 365, Cloud storage
SPC Connect Configuration Manual V1.0
 SPC Connect Configuration Manual V1.0 I-200090-1 28.11.2014 Copyright Copyright Technical specifications and availability subject to change without notice. Copyright Siemens AB We reserve all rights in
SPC Connect Configuration Manual V1.0 I-200090-1 28.11.2014 Copyright Copyright Technical specifications and availability subject to change without notice. Copyright Siemens AB We reserve all rights in
Electronic Communication In Your Practice. How To Use Email & Mobile Devices While Maintaining Compliance & Security
 Electronic Communication In Your Practice How To Use Email & Mobile Devices While Maintaining Compliance & Security Agenda 1 HIPAA and Electronic Communication 2 3 4 Using Email In Your Practice Mobile
Electronic Communication In Your Practice How To Use Email & Mobile Devices While Maintaining Compliance & Security Agenda 1 HIPAA and Electronic Communication 2 3 4 Using Email In Your Practice Mobile
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY?
 WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
WHAT ARE THE BENEFITS OF OUTSOURCING NETWORK SECURITY? Contents Introduction.... 3 What Types of Network Security Services are Available?... 4 Penetration Testing and Vulnerability Assessment... 4 Cyber
Better protection for customers, and recurring revenue for you!
 AVG AntiVirus Better protection for customers, and recurring revenue for you! Offer your customers the latest protection without draining your resources. A single, central management platform alerts when
AVG AntiVirus Better protection for customers, and recurring revenue for you! Offer your customers the latest protection without draining your resources. A single, central management platform alerts when
Microsoft Office 365 from Vodafone. Administrator s Guide for Midsize Businesses and Enterprises
 Microsoft Office 365 from Vodafone Administrator s Guide for Midsize Businesses and Enterprises Contents Footer bar Return to contents page Go to next of section Return to start of section Previous page
Microsoft Office 365 from Vodafone Administrator s Guide for Midsize Businesses and Enterprises Contents Footer bar Return to contents page Go to next of section Return to start of section Previous page
A Bring-Your-Own-Device (BYOD) Solution Brief
 Empower employees with device freedom without compromising IT Network A Bring-Your-Own-Device (BYOD) Solution Brief Introduction Bring Your Own Device (BYOD) has become one of the most influential trends
Empower employees with device freedom without compromising IT Network A Bring-Your-Own-Device (BYOD) Solution Brief Introduction Bring Your Own Device (BYOD) has become one of the most influential trends
Secure Your Email with Encryption as a Service
 Secure Your Email with Encryption as a Service Janene Casella Symantec Jamie Northey Echoworx Disclaimer Any information regarding pre-release Symantec offerings, future updates or other planned modifications
Secure Your Email with Encryption as a Service Janene Casella Symantec Jamie Northey Echoworx Disclaimer Any information regarding pre-release Symantec offerings, future updates or other planned modifications
Thexyz Premium Webmail
 Webmail Access all the benefits of a desktop program without being tied to the desktop. Log into Thexyz Email from your desktop, laptop, or mobile phone, and get instant access to email, calendars, contacts,
Webmail Access all the benefits of a desktop program without being tied to the desktop. Log into Thexyz Email from your desktop, laptop, or mobile phone, and get instant access to email, calendars, contacts,
Web Meetings through VPN. Note: Conductor means person leading the meeting. Table of Contents. Instant Web Meetings with VPN (Conductor)...
 Table of Contents Instant Web Meetings with VPN (Conductor)...2 How to Set Up a Scheduled Web Meeting with VPN (Conductor)...6 How to Set Up a Support Web Meeting with GVSU VPN Service (Conductor)...15
Table of Contents Instant Web Meetings with VPN (Conductor)...2 How to Set Up a Scheduled Web Meeting with VPN (Conductor)...6 How to Set Up a Support Web Meeting with GVSU VPN Service (Conductor)...15
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training
 McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
McAfee Web Gateway Administration Intel Security Education Services Administration Course Training The McAfee Web Gateway Administration course from Education Services provides an in-depth introduction
TTAsia Secure Email Over the Cloud
 TTAsia Secure Email Over the Cloud Telecommunications & Technology Asia Ltd A leading managed services and cloud computing solutions provider in HK and China We filter millions of emails every month and
TTAsia Secure Email Over the Cloud Telecommunications & Technology Asia Ltd A leading managed services and cloud computing solutions provider in HK and China We filter millions of emails every month and
WEBSENSE EMAIL SECURITY SOLUTIONS OVERVIEW
 WEBSENSE EMAIL SECURITY SOLUTIONS OVERVIEW Challenge The nature of email threats has changed over the past few years. Gone are the days when email security, better known as anti-spam, was primarily tasked
WEBSENSE EMAIL SECURITY SOLUTIONS OVERVIEW Challenge The nature of email threats has changed over the past few years. Gone are the days when email security, better known as anti-spam, was primarily tasked
easy-to-use platform. Our solution offers the best video, audio and screen-sharing quality across Window, Mac, ios, Android
 Getting Started On PC And Mac What is Zoom? Zoom, the cloud meeting company, unifies cloud video conferencing, simple online meetings and mobile collaboration into one easy-to-use platform. Our solution
Getting Started On PC And Mac What is Zoom? Zoom, the cloud meeting company, unifies cloud video conferencing, simple online meetings and mobile collaboration into one easy-to-use platform. Our solution
Business Case for Voltage SecureMail Mobile Edition
 WHITE PAPER Business Case for Voltage SecureMail Mobile Edition Introduction Mobile devices such as smartphones and tablets have become mainstream business productivity tools with email playing a central
WHITE PAPER Business Case for Voltage SecureMail Mobile Edition Introduction Mobile devices such as smartphones and tablets have become mainstream business productivity tools with email playing a central
Home Internet Filter User Guide
 Home Internet Filter User Guide TABLE OF CONTENTS About Home Internet Filter... 2 How Home Internet Filter help you?... 2 Setting up the Residential Gateway and accessing to SingTel Home Internet Filter
Home Internet Filter User Guide TABLE OF CONTENTS About Home Internet Filter... 2 How Home Internet Filter help you?... 2 Setting up the Residential Gateway and accessing to SingTel Home Internet Filter
BE SAFE ONLINE: Lesson Plan
 BE SAFE ONLINE: Lesson Plan Overview Danger lurks online. Web access, social media, computers, tablets and smart phones expose users to the possibility of fraud and identity theft. Learn the steps to take
BE SAFE ONLINE: Lesson Plan Overview Danger lurks online. Web access, social media, computers, tablets and smart phones expose users to the possibility of fraud and identity theft. Learn the steps to take
Introduction to the Mobile Access Gateway
 Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Introduction to the Mobile Access Gateway This document provides an overview of the AirWatch Mobile Access Gateway (MAG) architecture and security and explains how to enable MAG functionality in the AirWatch
Web Manual: Email September 2014
 Table of Contents Getting Started... 3 How to change your password... 3 How to Access Division Email... 4 Outlook Web App (Webmail)... 4 iphone... 4 Android... 4 Blackberry... 4 Outlook Anywhere (MS Outlook)
Table of Contents Getting Started... 3 How to change your password... 3 How to Access Division Email... 4 Outlook Web App (Webmail)... 4 iphone... 4 Android... 4 Blackberry... 4 Outlook Anywhere (MS Outlook)
Outlook Express POP Instructions - Bloomsburg University Students
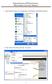 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
RingCentral Meetings QuickStart Guide
 RingCentral Meetings QuickStart Guide RingCentral Meetings empowers your workforce to collaborate from any location with face-to-face online meetings in high definition. Share your screen, websites, documents,
RingCentral Meetings QuickStart Guide RingCentral Meetings empowers your workforce to collaborate from any location with face-to-face online meetings in high definition. Share your screen, websites, documents,
PCI Compliance for Cloud Applications
 What Is It? The Payment Card Industry Data Security Standard (PCIDSS), in particular v3.0, aims to reduce credit card fraud by minimizing the risks associated with the transmission, processing, and storage
What Is It? The Payment Card Industry Data Security Standard (PCIDSS), in particular v3.0, aims to reduce credit card fraud by minimizing the risks associated with the transmission, processing, and storage
Symantec Consulting Services
 GET MORE FROM YOUR SECURITY SOLUTIONS Symantec Consulting 2015 Symantec Corporation. All rights reserved. Access outstanding talent and expertise with Symantec Consulting Symantec s Security Consultants
GET MORE FROM YOUR SECURITY SOLUTIONS Symantec Consulting 2015 Symantec Corporation. All rights reserved. Access outstanding talent and expertise with Symantec Consulting Symantec s Security Consultants
Secure Your Mobile Workplace
 Secure Your Mobile Workplace Sunny Leung Senior System Engineer Symantec 3th Dec, 2013 1 Agenda 1. The Threats 2. The Protection 3. Q&A 2 The Mobile Workplaces The Threats 4 Targeted Attacks up 42% in
Secure Your Mobile Workplace Sunny Leung Senior System Engineer Symantec 3th Dec, 2013 1 Agenda 1. The Threats 2. The Protection 3. Q&A 2 The Mobile Workplaces The Threats 4 Targeted Attacks up 42% in
Managing Web Security in an Increasingly Challenging Threat Landscape
 Managing Web Security in an Increasingly Challenging Threat Landscape Cybercriminals have increasingly turned their attention to the web, which has become by far the predominant area of attack. Small wonder.
Managing Web Security in an Increasingly Challenging Threat Landscape Cybercriminals have increasingly turned their attention to the web, which has become by far the predominant area of attack. Small wonder.
Email Security in Law Firms. What you need to know and how you can use secure email to win more clients
 Email Security in Law Firms What you need to know and how you can use secure email to win more clients Introduction As clients are demanding greater protection of their information, law firms must incorporate
Email Security in Law Firms What you need to know and how you can use secure email to win more clients Introduction As clients are demanding greater protection of their information, law firms must incorporate
SECURE YOUR DATA EXCHANGE WITH SAFE-T BOX
 SECURE YOUR DATA EXCHANGE SAFE-T BOX WHITE PAPER Safe-T. Smart Security Made Simple. 1 The Costs of Uncontrolled Data Exchange 2 Safe-T Box Secure Data Exchange Platform 2.1 Business Applications and Data
SECURE YOUR DATA EXCHANGE SAFE-T BOX WHITE PAPER Safe-T. Smart Security Made Simple. 1 The Costs of Uncontrolled Data Exchange 2 Safe-T Box Secure Data Exchange Platform 2.1 Business Applications and Data
Top Five Ways Any Business Can Benefit from Box
 Top Five Ways Any Business Can Benefit from Box Every business, no matter what size, has documents and information that are the foundation of the company. Team members need to access and collaborate on
Top Five Ways Any Business Can Benefit from Box Every business, no matter what size, has documents and information that are the foundation of the company. Team members need to access and collaborate on
ipecs UCS Unified Communications Solution Easy to access and activate Highlights Single server solution
 ipecs UCS Unified Communications Solution In today s world of remote and dispersed workers, the ipecs UCS application provides tools to enhance productivity and mobility while improving employee collaboration
ipecs UCS Unified Communications Solution In today s world of remote and dispersed workers, the ipecs UCS application provides tools to enhance productivity and mobility while improving employee collaboration
Conquering PCI DSS Compliance
 Any organization that stores, processes or transmits information related to credit and debit card payments has a responsibility to protect each cardholder s personal data. To help accomplish this goal,
Any organization that stores, processes or transmits information related to credit and debit card payments has a responsibility to protect each cardholder s personal data. To help accomplish this goal,
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
Product Overview. Mimecast Training. Student Workbook V 2.3
 Product Overview Mimecast Training Student Workbook V 2.3 2014 by Mimecast Services Ltd. The information posted in this guide is for use by Mimecast customers only. Use of the guide is governed by the
Product Overview Mimecast Training Student Workbook V 2.3 2014 by Mimecast Services Ltd. The information posted in this guide is for use by Mimecast customers only. Use of the guide is governed by the
ensure prompt restart of critical applications and business activities in a timely manner following an emergency or disaster
 Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Selecting Your Essential Cloud Services for Office 365
 DATASHEET Selecting Your Essential Cloud Services for Office 365 Mimecast provides a rich set of cloud services designed to meet the specific needs of Microsoft Office 365 customers. We effectively remove
DATASHEET Selecting Your Essential Cloud Services for Office 365 Mimecast provides a rich set of cloud services designed to meet the specific needs of Microsoft Office 365 customers. We effectively remove
FTP-Stream Data Sheet
 FTP-Stream Data Sheet Problem FTP-Stream solves four demanding business challenges: Global distribution of files any size. File transfer to / from China which is notoriously challenging. Document control
FTP-Stream Data Sheet Problem FTP-Stream solves four demanding business challenges: Global distribution of files any size. File transfer to / from China which is notoriously challenging. Document control
Axway SecureTransport Ad-hoc File Transfer Service
 Axway SecureTransport Ad-hoc File Transfer Service Secure, efficient and reliable Enterprise File Sharing (EFS) In today s fluid, fast-paced, and highly collaborative business environment, people need
Axway SecureTransport Ad-hoc File Transfer Service Secure, efficient and reliable Enterprise File Sharing (EFS) In today s fluid, fast-paced, and highly collaborative business environment, people need
RESCO MOBILE CRM QUICK GUIDE. for MS Dynamics CRM. ios (ipad & iphone) Android phones & tablets
 RESCO MOBILE CRM for MS Dynamics CRM QUICK GUIDE ios (ipad & iphone) Android phones & tablets Windows Phone 7 & 8, Windows XP/Vista/7/8.1 and RT/Surface, Windows Mobile Synchronize Synchronize your mobile
RESCO MOBILE CRM for MS Dynamics CRM QUICK GUIDE ios (ipad & iphone) Android phones & tablets Windows Phone 7 & 8, Windows XP/Vista/7/8.1 and RT/Surface, Windows Mobile Synchronize Synchronize your mobile
Google Apps Overview
 Google Apps Overview Agenda Messaging & collaboration challenges Why existing solutions are costly & limited Google s innovative approach The time is now to switch to the cloud Google Apps Premier Edition
Google Apps Overview Agenda Messaging & collaboration challenges Why existing solutions are costly & limited Google s innovative approach The time is now to switch to the cloud Google Apps Premier Edition
Data Security on the Move. Mark Bloemsma, Sr. Sales Engineer Websense
 Data Security on the Move Mark Bloemsma, Sr. Sales Engineer Websense Consumerization of IT Fast & disruptive Enables business Increases productivity It s Mine! THE MOBILE ENTERPRISE. TYPES OF DEVICES METHODS
Data Security on the Move Mark Bloemsma, Sr. Sales Engineer Websense Consumerization of IT Fast & disruptive Enables business Increases productivity It s Mine! THE MOBILE ENTERPRISE. TYPES OF DEVICES METHODS
Get Started Guide - PC Tools Internet Security
 Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Get Started Guide - PC Tools Internet Security Table of Contents PC Tools Internet Security... 1 Getting Started with PC Tools Internet Security... 1 Installing... 1 Getting Started... 2 iii PC Tools
Web Manual: Email October 2015
 Table of Contents Getting Started... 3 How to change your password... 3 How to Access Division Email... 4 Outlook Web App (Webmail)... 4 iphone... 4 Android... 4 Blackberry... 4 Outlook Anywhere (MS Outlook)
Table of Contents Getting Started... 3 How to change your password... 3 How to Access Division Email... 4 Outlook Web App (Webmail)... 4 iphone... 4 Android... 4 Blackberry... 4 Outlook Anywhere (MS Outlook)
Document control for sensitive company information and large complex projects.
 Data sheet Problem FTP-Stream solves four demanding business challenges: Global distribution of files any size. File transfer to / from China which is notoriously challenging. Document control for sensitive
Data sheet Problem FTP-Stream solves four demanding business challenges: Global distribution of files any size. File transfer to / from China which is notoriously challenging. Document control for sensitive
WatchDox SharePoint Beta Guide. Application Version 1.0.0
 Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Application Version 1.0.0 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
BYOD File Sharing Go Private Cloud to Mitigate Data Risks
 AN ACCELLION WHITE PAPER BYOD File Sharing Go Private Cloud to Mitigate Data Risks Accellion, Inc. Tel +1 650 485-4300 1804 Embarcadero Road Fax +1 650 485-4308 Suite 200 www.accellion.com Palo Alto, CA
AN ACCELLION WHITE PAPER BYOD File Sharing Go Private Cloud to Mitigate Data Risks Accellion, Inc. Tel +1 650 485-4300 1804 Embarcadero Road Fax +1 650 485-4308 Suite 200 www.accellion.com Palo Alto, CA
Voice. Internet. Apps. Data Center. Wide Area Networks. Business is better in the cloud
 Voice Internet Apps Data Center Wide Area Networks Business is better in the cloud Google Apps helps businesses work smarter. Increase Productivity While Reducing Costs Google Apps offers simple, powerful
Voice Internet Apps Data Center Wide Area Networks Business is better in the cloud Google Apps helps businesses work smarter. Increase Productivity While Reducing Costs Google Apps offers simple, powerful
Threat Containment for Facebook
 Threat Containment for Facebook Based on statistics for more than 62M users in 2009, the Blue Coat WebPulse cloud service ranked social networking as the number one most requested web category, surpassing
Threat Containment for Facebook Based on statistics for more than 62M users in 2009, the Blue Coat WebPulse cloud service ranked social networking as the number one most requested web category, surpassing
Payment Card Industry Data Security Standard
 Symantec Managed Security Services support for IT compliance Solution Overview: Symantec Managed Services Overviewview The (PCI DSS) was developed to facilitate the broad adoption of consistent data security
Symantec Managed Security Services support for IT compliance Solution Overview: Symantec Managed Services Overviewview The (PCI DSS) was developed to facilitate the broad adoption of consistent data security
SecuriSync The Goldilocks Solution For File Sharing CALL US EMAIL US ON THE WEB. 1.800.379.7729 [email protected] intermedia.
 SecuriSync The Goldilocks Solution For File Sharing CALL US EMAIL US ON THE WEB 1.800.379.779 [email protected] intermedia.net The full list of features that make SecuriSync just right Humans tend to
SecuriSync The Goldilocks Solution For File Sharing CALL US EMAIL US ON THE WEB 1.800.379.779 [email protected] intermedia.net The full list of features that make SecuriSync just right Humans tend to
Woodcock-Johnson and Woodcock-Muñoz Language Survey Revised Normative Update Technical and Data Security Overview
 Houghton Mifflin Harcourt - Riverside (HMH - Riverside) is pleased to offer online scoring and reporting for Woodcock-Johnson IV (WJ IV) and Woodcock-Muñoz Language Survey Revised Normative Update (WMLS-R
Houghton Mifflin Harcourt - Riverside (HMH - Riverside) is pleased to offer online scoring and reporting for Woodcock-Johnson IV (WJ IV) and Woodcock-Muñoz Language Survey Revised Normative Update (WMLS-R
Agenda. 3 2012, Palo Alto Networks. Confidential and Proprietary.
 Agenda Evolution of the cyber threat How the cyber threat develops Why traditional systems are failing Need move to application controls Need for automation 3 2012, Palo Alto Networks. Confidential and
Agenda Evolution of the cyber threat How the cyber threat develops Why traditional systems are failing Need move to application controls Need for automation 3 2012, Palo Alto Networks. Confidential and
Personal Cloud. Support Guide for Mac Computers. Storing and sharing your content 2
 Personal Cloud Support Guide for Mac Computers Storing and sharing your content 2 Getting started 2 How to use the application 2 Managing your content 2 Adding content manually 3 Renaming files 3 Moving
Personal Cloud Support Guide for Mac Computers Storing and sharing your content 2 Getting started 2 How to use the application 2 Managing your content 2 Adding content manually 3 Renaming files 3 Moving
Mini User Guide. Updating your contact details..2. Setting your Security Questions..4. Changing your password..5. Forgotten password...
 Mini User Guide Contents: Updating your contact details..2 Setting your Security Questions..4 Changing your password..5 Forgotten password......6 Accessing Virgin Care Webmail..9 Sending an Encrypted Email.....12
Mini User Guide Contents: Updating your contact details..2 Setting your Security Questions..4 Changing your password..5 Forgotten password......6 Accessing Virgin Care Webmail..9 Sending an Encrypted Email.....12
With Great Power comes Great Responsibility: Managing Privileged Users
 With Great Power comes Great Responsibility: Managing Privileged Users Darren Harmer Senior Systems Engineer Agenda What is a Privileged User Privileged User Why is it important? Security Intelligence
With Great Power comes Great Responsibility: Managing Privileged Users Darren Harmer Senior Systems Engineer Agenda What is a Privileged User Privileged User Why is it important? Security Intelligence
Visendo Email Suite a reliable solution for SMBs
 Visendo Email Suite a reliable solution for SMBs Visendo offers a range of Email solutions to assist companies in meeting complex e-mail requirements Visendo Security for Email Servers Multi-engine spam
Visendo Email Suite a reliable solution for SMBs Visendo offers a range of Email solutions to assist companies in meeting complex e-mail requirements Visendo Security for Email Servers Multi-engine spam
