Creation of Load Balanced Mail Server Management System Using Cloud Computing
|
|
|
- Melina Clark
- 8 years ago
- Views:
Transcription
1 Creation of Load Balanced Mail Server Management System Using Cloud Computing D.Sharanya 1 Dr.N. Chandra Sekhar Reddy 2 Chaitanya3 M.Tech CSE Dept., Institute of Aeronautical Engineering, HYD , AP, India. Professor, CSE Dept., Institute of Aeronautical Engineering, HYD , AP, India Professor, CSE Dept., Institute of Aeronautical Engineering,HYD , AP, India. ABSTRACT: This system facilitates mailing among the users of an internet, having an efficient and easy to communicate with telecommunications. The mails are transmitted and receiving by individual users registered in a mail management server. To prevent unauthorized to access the mail, message arrive in mail atleast one of them is deleted to store efficient I.INTRODUCTION: Electronic mail service is the rapid growth of the Intranet/Internet its explains how to read and use Management Information Base(MIB),[5] Simple Network Management Protocol(SNMP) these devices are managed ones that can be controlled, monitored and are capable of reporting events.osi(open System Interconnection) (ISO 7498,1984), because protocols and architecture other than OSI[6][2]. They are widely used for Open Systems networking, SNMP can be used to manage objects by configuration, performance framework called the structure of management information. TCP/IP is an open system networking largely inability of the OSI standards developers to deliver. The term TCP/IP is commonly used to refer Specifically Transmission Control Protocol(TCP) and Internet Protocol(IP)[. In Internet community, QoS control for Internet Protocol Network's and it has become a hot issue. Internet Engineering Task Force(IETF)[1] the Quality Of Service controls the Internet.CGI is a Common Gateway Interface for interfacing the external programs with information servers on the Internet.CGI is distinguished from plain HTML; "HTML"[11] is static, while executes in real-time the output in dynamic information that implements while [CGI Executables. The Scripts can be written in any languages like (c, c++, Fortran, Visual Basic and unix shells).[17]cgi script is to debug eaiser and modify and maintains the typical executed programs. mail using less storage space. There exits various applications Intranet/Internet services such as , Flip, news, telnet, archive the web-based internet/intranet service management to evaluate the performance. Keywords: mail server management system, load balancing, cloud computing, telnet, intranet and internet. II.RELATED WORK: Mail Server is also known as mail transfer agent or MTA. An application that receives incoming from local users and remote sends and forwards outgoing for delivery. The mail server works in conjunction to make sometimes refer to as messaging systems. While sending an , message,[17] your program like outlook, which passes the message to your mail server. The rule that works "SMTP" or "ESMTP" or "POP3" or "IMAP".[17] Web based intranet/internet service management to present design and implementation system with quality of service(qos). [10]Management information bases requires the various internet service management. Internet services have been applied to improve many organizations, internet services such as web hosting, being developed an enterprise network that controls different domains. The standard SNMP to achieve a proxy forward on the 6LOWPAN[2] gateway.[2][5] Proxy forwarder is converted from SNMP messages from one version to another. Its transfers current messages to SNMP versions. The messages gets conversion and its forwards the details in some multiple requests coming messages regularly. Electronic mail sending and receiving files, images, text files between different computers using fax modems,[3] networks must have mail software. More than 3.1 billion people send 244 billion messages monthly. Software ISSN: Page114
2 applications allowing people to communicate with each other (exchange data) using fax they are sending like hardcopy of text or photographs between computers it receives internet telephone software Standards developed by cooperating among forms and government. A set of rules that govern all the aspects of data between computer networks. These includes the following characteristics of network : access method, allowed physical topologies, speed of data transfer. A simple network management system(snmp)[1],[4] it allows simple maintenance remote monitoring of any device on network SNMP admin indentifies the issues such as with intranet card in a server program, or a device such as hub or router. The system management system and the management information base QOS[9] provides a traffic management intranet particularly during the times of congestion or failure. Resources management enable you to collect, display, store and analyze data about system performance it s a realtime monitoring, analyze and report using records of system activity[3]. RM may rake a minute to generate alerts abnormally terminates the server. However the servers have been shutdown/remote/have MAS service stopped in the normally it stores information about server performance, these can sends alerts via " ", "SMS", "SNMP".[9][18] Security is a process which manages the security environment of network, it includes during the security violations to maintain security audits and performs the network management tasks. The real-time tracking mechanisms of IP-based enterprise networks and[4] ISP network. There are security violations and issues such as fault-tolerant and suitable intrusion information transport with reasonable remote controlling network resources.the UNIX operating system was born late 1960s. Its originally began a one man project led by Ken Thompson of Bell Labs. Since grown to become most widely used Operating System Multi-user, Multi-Tasking of UNIX capable of allowing multiple users to log on to system. Large number of applications are available for UNIX[ Operating System such as[15] CAD, word perfect and many other available free applications. Internet development of the backbone of the internet is run by UNIX servers and more general web servers run UNIX with the apache web server.[6][4] The OSI model is a concept that includes a set of protocols to define and standardization of the data communication process. Its defined by the International Standard Organization(ISO)[6]. In the beginning of 1983 Operating System model developed by representatives of major computer and telecommunication companies. According to OSI document(sio 7498) the purpose of Operating System is International Standard reference model of open systems interconnection to provide common basis for the coordination of Standard developments. Network group is made up of [8] physical layer, data-link layer, network layer. Transport group consists of "Single-layer" and the "Transport layer"[16]. Application to group consists of session layer, presentation layer and application layer. The basic functions of physical layer are handles voltage electrical pulses, switches so that the data can be transmitted from one to another drive. The data link layer is often divided into 2 parts : logical link control(llc) and medium access control(mac).[10] The main function of data link layer are handles the physical transfer, farming, flow-control and error-control functions over a single transmission link. Network layer is the third layer of OSI model. Network layer establishes the rate between the sending and receiving stations. In this layer we use the Internet Protocol(IP)[17]. The forth transport layer of OSI model is responsible for constructing stream of data packets and checking for correct delivery if the data is sent incorrectly, this layer has the responsibility to ask for retransmission of the data. The session layer uses of POP, TCP/IP protocols.[17],[10] Presentation layer provides files and services, in this layer POP, SMTP, FTP protocols are used. Application layer is the common functions for opening, closing, reading and writing files. It provides functions to users networks, including , web application and files transfer access and management(ftam),[14] directory services, network management common gateway interface interfacing external programs with information servers of the internet. ISSN: Page115
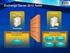
3 CGI executes in real-time output dynamic information. HTML document is "static", document exists as constant text file that does not change. In 1993,the world wide web was small, but software developers and website developers kept in touch with the www-talk mailing list.[17] CGI script can be written in any language (e.g.: C/C++,visual Basic, Unix shells), A CGI script is easier to debug, modify and maintain than the typical executed program. POP3 (Post Office Protocol) used to retrieve from a mail server. The applications uses the POP protocol, some can use the Internet Message Access Protocol(IMAP).[17][8]The first version called POP2,it became a standard in mid-80's and requires SMTP to send messages. The newer version POP3, can be used SMTP POP3 uses TCP/IP port 110. Hence you need to have delivered atleast one message to the user, to create their own mailbox, before they can login and look for logging messages.[11] to achieve instant communication between employees. The "Intranet/Internet"[1] namespaces and also it occurs in authentication for clients, session affinity doesn't requires at load balancer, because there is no problem in forwarding the one session to another client access server's Existing model exchanges the deployments are overly complicated, while doing a load balancing [17]exchanges the "right" hard and its requires the expensive solutions, there are many hard wares to load balancing impacts scalability significantly organizations needs in a consistent and transparent efficiency. IV.PROPOSED SYSTEM Mail Transfer Agent (MTA) is done through messages tranfer agent (MTAs). to send mail, a system should have client MTA and to receive mail, a system must have server MTA.[13] If you are using SMTP in MTA mode or HTTP in active bridge mode: ->select the mode blocking. ->select the SMTP HELO name. ->set the Next HOP if required(eg:company mails mainly). III.PROBLEM STATEMENT: Mail Server Exchange 2013 brings a new set of technologies, services and features to the exchange the server product line. Social integration and making it easier to find people important to users. Microsoft outlook 2013 and Microsoft outlook web app had a fresh new look.[17] E2013 builds upon the exchange server 2010 architecture have been redesigned or failure isolation. An Organization grows in size in terms of departments and functionalities; it requires a efficient Figure(1):E E2013 Server Architecture There are like many namespaces are used(mainly in site resilent designs) the customers, mainly deploy and its based on dedicated server rules. ISSN: Page116
4 Figure(2):Exchange The Evolution Figure(3):Exchange The Evolution Of Simplify for Scale, Balanced, Utilization, and Isolation. 2. Integrate HA for all roles. 3. Simplify Network Architecture. The screen appears two major items [18][10] Xmail and roundcube. The Xmail is act as mail server to manager all of mails send/receive for all users. The roundcube is a tool that user can access own mails through interface; it normally called web mail. To better understand this definition, we must first break down IoE s individual components. People: In IoE, people will be able to connect to the Internet in innumerable ways. Today, most people connect to the Internet through their use of devices (such as PCs, tablets, TVs, and smart phones) and social networks (such as Face book, Twitter, LinkedIn, and Interest). [6]As the Internet evolves toward IoE, we will be connected in more relevant and valuable ways. For example, in the future, people will be able to swallow a pill that senses and reports the health of their digestive tract to a doctor over a secure Internet connection.[8] In addition, sensors placed on the skin or sewn into clothing will provide information about a person s vital signs. According to Gartner, people themselves will become nodes on the Internet with both static information and a constantly emitting activity system. Figure (4): functional layering The Exchange Server 2013 has been announced in technical preview, communication and messaging platforms its occurring in new level. In 2007 splitting the functionality into[11],[3] HUB, CAS, UM, Edge and mailbox. The architecture remained same in exchange 2010.[18]Exchange server, the architecture has been changed to consolidate all the role to the following three components like "Client protocol"(http, IMAP,POP), "SMTP" "UM call router". using RPC eliminating the need its support RPC protocol outside using single box and making communications in mailbox and CAS servers over HTTPs or SMTP. Its provides a unified[13],16]. Load balancing is used to require managing the yours servers and receive traffics. Its provides failover redundancy to ensure a client access servers. Its help to distributing incoming client connections over a variety of endpoints for example: To ensure your users to continue receive services to failure in case of computer by using load balancing its also enables to handle more than one servers traffic. High availability uses database availability groups (DAGS) in E2013[10] multiple copies to keep your mailboxes with different servers. In that way, database fails on from one server, the users connected to synchronized database to another server. In online mailbox move, those users can access accounts while during the move. Here, users accounts while during the move. The users locked out their accounts for ISSN: Page117
5 only a particular time at the end of the process. it can perform online across forests or else in the same forest. 3.Collection of Servers that form a HA unit Data Base copies/server.[11][14] Mail Delivery from a client application to the server and server is handled to the destination server, is the Simple Mail Transfer Protocol. There are two primary Protocols used by client application to retrieve the from mail servers: Post Office Protocols(POP) and the Internet Message Access Protocol(IMAP).[1][18] Figures(5):Exchange in load Balance server The New Store Process is effectively made up of three processes : Replication service, Store service process/ store service controller, store worker process. Store service process/controller manages the store worker processes, Each database have its own store worker process and the Replication service initiates failovers and responsible for issuing mount/dismount operations. V.ALGORITHM Pseudo Code Carton: DRL-UpdateCapacities() Once every units of time do Figure(6):Mail Box Server Role Mail Box Server Role reduced in micro soft exchange 2013 to just two " increase simplicity of scale, Hardware utilization and failure isolation"[lb][18] which includes all the Client access protocol and Hub Transport Service and mailbox databases also handles all activity. Clients do not directly to MBX2013 servers, and Connectivity through CAS2013. [18]Server hosts all the components that process, renders and store the data evolution of E2010 DAG: 1.DataBase are replicated between servers in a given DAG. 2.Maximum of 16 Mail Box servers. for i=1:n µ i µ i +Ƞ (i,j) ϵe (q i- q j ) endfor enddo InitializeCapacities() for i=1:n µ i µ/n endfor UpdateDemands() g(k)=subgradient of V in x(k) ISSN: Page118
6 DESCRIPTION: x(k+1)=x(k)- 1/ k g(k) Step1: Control cloud based services for load balancing and distributed rate limiting. Step2: The matrix demand allocation X and capacities which performance is approximately equal and minimizes the aggregate cost. V(x)= M j=1 N i=1c ij x j (i) + N i=1d i (y i ) Figure(8) Expectation Graph(1). Step3: The capacities of dynamic resource allocation is required update() for every delta units of time. Step4: Integer value 1isto N no. of servers its passes to the mean value. Step5: Its "end for" must be a demand allocations. Step6: The initializations start and become load balancing and distributed rate limiting. Step7: one is to N no. of servers to the mean value must be sub gradient of vertices in x(k) to minimizes the cost in DRL(Dynamic Resource Allocation). VI.EXPERIMENTAL EVOLUTION Figure(8) Expectation Graph(2) VII.FUTURE WORK ES2013 ES2007 Figure (7) :Graph: ES2007 ES2010 ES2013 A user can empowering educators are developed their own Intranet pages and therefore they are encouraging module pages for which they are responsible,[9]with the need for material to be posted via Intranet development team, like integration of animations and video clips to increase student/staff interaction[12].the choice to encrypt them it as to be assured that the data will not be altered or read during transmission. The furthermore, issues regarding the legality of a formal document sent electronically.(eg: via )need to be explored. [13].and we plan to develop applications based on micro soft exchange server to enable the user with services like messaging to physicians, and hospital departments and staff, the customer services, send text, charts, graphs and other documents[14] it includes links to world wide web sites in network wide address book. The internet management ISSN: Page119
7 framework was conceived mainly for [1],[5]LAN/MAN management. It follows a "lowest common denominator" approach to management standardization its fixes some of the problems of VIII.CONCLUSION SNMP provides valuable insight to any network administrator which requires the complete visibility into network.tcp/ip[3],[5] makes so much assertion in the web-based Intranet/Internet mail server management system. It's a real-time multicast systems.osi asserts that distributed applications operate over a strict hierarchy of layers. we have defined SNMP and MIB[1] monitoring mail server process. such as CGI and java enables human users to learn and maintain easily and cost effectively. Configuration management evolution is a software product. The operation level for[6],[11]configuration management systems an area in software engineering environment when progress has been made. IX.REFERENCES [1] Robert Cailliau,Jean-Francois Groff, Bernd Pollermann, "World-Wide Web: The Information Universe", CERN,1211 Geneva 23,Switzerland. [2] Haksoo Choi, Nakyoung Kim, Hojung Cha "6LoWPAN- SNMP:Simple Network Management Protocol for 6LoWPAN" Yonsei University, 2009,11th, Seoul, Korea. [3]By Ken Arnold, James Gosling, David Holmes, "THE Java TM Programming Language,Fourth Edition"August 17,2005 Pages:928 [4]Jong-Tae Park and Jong-Wook Beak,"Web-based Internet/Intranet Service Management with QoS Support"Taegu,Korea version(eg: object/creation/deletion)[15] the OSI management framework was conceived by mainly for WAN management and telecommunications. [8]Michael Fauscette "The Future of Is Social"Sponsored by:ibm,february [9]HathaiTanta-ngai, TonyAbou-Assaleh, SittichaiJiampojamarn, and NickCercone,Fellow,"Secure Mail Transfer Protocol(SecMTP)"IEEE10. [10]Taesang Choi,Yoonhee Jung,Sungwon Sohn,"An Architecture of a Qos Management System for Next Generation Internet"161 Kajong-Doung Yusung-Gu,Taejon City,KOREA. [11]Kanji Hayashi, Takafumi Chujo, Kazuyoshi Kumatani, Akira Hakata, "Fujitsu's Activities for Next-Generation Network" July 21,2006. [12]Michael H Sosabowski,Katie Herson and Andrew W Llyod,"Implementation and student Assessment of Intranet-Based learning Resources "UnitedKingdom. [13]BourasChristos,Destounis Panagiotis,Garofalakis John,Triantafillou Bill,Tzimas john,zorafidis Panagiotis,"An Intranet and Internet based information system for Administration and Information purposes"patras,greece. [14]S.Pavlopoulos,T.Tagaris,A.Berler,D.Koutsouries"Design and Implementation of an Internet Hospital Information System"15773 Zografou Greece. [15]George pavlon:"osi System Management Internet SNMP and ODP/OMG CORBA as Technologies for telecommunications Network Management"London WC1E 6BT,UK. [16]"List of network protocols layers" october 31st [17]"Simple Network Protocol" "common Gateway Interface", "Network Protocols" [18]"Load Balancing", "Future enhancement of E: " [5]By David T.Perkins, "Understanding SNMP MIBs,September,1993.Revision [6]George Paylou,"OSI Systems Management,Internet SNMP and ODP/OMG CORBA as Technologies for Telecommunications Network Management"London WCIE 6BT,UK. [7]Bouras Christos,Destounis Panagiotis,Garofalakis John,Triantafillou Bill,Tzimas John,Zarafidis Panagiotis, "An Intranet/Internet based Information System for Administration and Information purposes"gr-26221,patras,greece. ISSN: Page120
MOC 5047B: Intro to Installing & Managing Microsoft Exchange Server 2007 SP1
 MOC 5047B: Intro to Installing & Managing Microsoft Exchange Server 2007 SP1 Course Number: 5047B Course Length: 3 Days Certification Exam This course will help you prepare for the following Microsoft
MOC 5047B: Intro to Installing & Managing Microsoft Exchange Server 2007 SP1 Course Number: 5047B Course Length: 3 Days Certification Exam This course will help you prepare for the following Microsoft
A host-based firewall can be used in addition to a network-based firewall to provide multiple layers of protection.
 A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
A firewall is a software- or hardware-based network security system that allows or denies network traffic according to a set of rules. Firewalls can be categorized by their location on the network: A network-based
Oct 15, 2004 www.dcs.bbk.ac.uk/~gmagoulas/teaching.html 3. Internet : the vast collection of interconnected networks that all use the TCP/IP protocols
 E-Commerce Infrastructure II: the World Wide Web The Internet and the World Wide Web are two separate but related things Oct 15, 2004 www.dcs.bbk.ac.uk/~gmagoulas/teaching.html 1 Outline The Internet and
E-Commerce Infrastructure II: the World Wide Web The Internet and the World Wide Web are two separate but related things Oct 15, 2004 www.dcs.bbk.ac.uk/~gmagoulas/teaching.html 1 Outline The Internet and
Guide to Deploying Microsoft Exchange 2013 with Citrix NetScaler
 Deployment Guide Guide to Deploying Microsoft Exchange 2013 with Citrix NetScaler Extensive guide covering details of NetScaler ADC deployment with Microsoft Exchange 2013. Table of Contents Introduction
Deployment Guide Guide to Deploying Microsoft Exchange 2013 with Citrix NetScaler Extensive guide covering details of NetScaler ADC deployment with Microsoft Exchange 2013. Table of Contents Introduction
5/20/2013. The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team
 Additions and Subtractions The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team Exchange Version Exchange Server 2003 and earlier versions
Additions and Subtractions The primary design goal was for simplicity of scale, hardware utilization, and failure isolation. Microsoft Exchange Team Exchange Version Exchange Server 2003 and earlier versions
Basic Network Configuration
 Basic Network Configuration 2 Table of Contents Basic Network Configuration... 25 LAN (local area network) vs WAN (wide area network)... 25 Local Area Network... 25 Wide Area Network... 26 Accessing the
Basic Network Configuration 2 Table of Contents Basic Network Configuration... 25 LAN (local area network) vs WAN (wide area network)... 25 Local Area Network... 25 Wide Area Network... 26 Accessing the
Network Configuration Settings
 Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Network Configuration Settings Many small businesses already have an existing firewall device for their local network when they purchase Microsoft Windows Small Business Server 2003. Often, these devices
Configuration Guide. BlackBerry Enterprise Service 12. Version 12.0
 Configuration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2014-12-19 SWD-20141219132902639 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12...
Configuration Guide BlackBerry Enterprise Service 12 Version 12.0 Published: 2014-12-19 SWD-20141219132902639 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12...
Discuss the new server architecture in Exchange 2013. Discuss the Client Access server role. Discuss the Mailbox server role
 Discuss the new server architecture in Exchange 2013 Discuss the Client Access server role Discuss the Mailbox server role 5 major roles Tightly coupled Forefront Online Protection for Exchange Edge Transport
Discuss the new server architecture in Exchange 2013 Discuss the Client Access server role Discuss the Mailbox server role 5 major roles Tightly coupled Forefront Online Protection for Exchange Edge Transport
524 Computer Networks
 524 Computer Networks Section 1: Introduction to Course Dr. E.C. Kulasekere Sri Lanka Institute of Information Technology - 2005 Course Outline The Aim The course is design to establish the terminology
524 Computer Networks Section 1: Introduction to Course Dr. E.C. Kulasekere Sri Lanka Institute of Information Technology - 2005 Course Outline The Aim The course is design to establish the terminology
This course is intended for IT professionals who are responsible for the Exchange Server messaging environment in an enterprise.
 10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course Number: 10233A Course Length: 5 Day Course Overview This instructor-led course provides you with the knowledge
10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course Number: 10233A Course Length: 5 Day Course Overview This instructor-led course provides you with the knowledge
Firewall VPN Router. Quick Installation Guide M73-APO09-380
 Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Firewall VPN Router Quick Installation Guide M73-APO09-380 Firewall VPN Router Overview The Firewall VPN Router provides three 10/100Mbit Ethernet network interface ports which are the Internal/LAN, External/WAN,
Exchange 2013 Server Architecture: Part 1. Jeff Mealiffe Senior Program Manager Exchange Product Group
 Exchange 2013 Server Architecture: Part 1 Jeff Mealiffe Senior Program Manager Exchange Product Group Agenda Part 1 Overview of the new Architecture The Client Access server role Part 2 The Mailbox server
Exchange 2013 Server Architecture: Part 1 Jeff Mealiffe Senior Program Manager Exchange Product Group Agenda Part 1 Overview of the new Architecture The Client Access server role Part 2 The Mailbox server
Designing a Microsoft Exchange Server 2003 Organization
 Course Outline Other Information MS2008 Days 2 Starting Time 9:00 Finish Time 4:30 Lunch & refreshments are included with this course. Designing a Microsoft Exchange Server 2003 Organization Introduction
Course Outline Other Information MS2008 Days 2 Starting Time 9:00 Finish Time 4:30 Lunch & refreshments are included with this course. Designing a Microsoft Exchange Server 2003 Organization Introduction
INTERNET SECURITY: THE ROLE OF FIREWALL SYSTEM
 INTERNET SECURITY: THE ROLE OF FIREWALL SYSTEM Okumoku-Evroro Oniovosa Lecturer, Department of Computer Science Delta State University, Abraka, Nigeria Email: victorkleo@live.com ABSTRACT Internet security
INTERNET SECURITY: THE ROLE OF FIREWALL SYSTEM Okumoku-Evroro Oniovosa Lecturer, Department of Computer Science Delta State University, Abraka, Nigeria Email: victorkleo@live.com ABSTRACT Internet security
RAS Associates, Inc. Systems Development Proposal. Scott Klarman. March 15, 2009
 Systems Development Proposal Scott Klarman March 15, 2009 Systems Development Proposal Page 2 Planning Objective: RAS Associates will be working to acquire a second location in Detroit to add to their
Systems Development Proposal Scott Klarman March 15, 2009 Systems Development Proposal Page 2 Planning Objective: RAS Associates will be working to acquire a second location in Detroit to add to their
Security+ Guide to Network Security Fundamentals, Fourth Edition. Chapter 6 Network Security
 Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 6 Network Security Objectives List the different types of network security devices and explain how they can be used Define network
Security+ Guide to Network Security Fundamentals, Fourth Edition Chapter 6 Network Security Objectives List the different types of network security devices and explain how they can be used Define network
HARTING Ha-VIS Management Software
 HARTING Ha-VIS Management Software People Power Partnership HARTING Management Software Network Management Automation IT - with mcon Switches from HARTING With the Ha-VIS mcon families, HARTING has expanded
HARTING Ha-VIS Management Software People Power Partnership HARTING Management Software Network Management Automation IT - with mcon Switches from HARTING With the Ha-VIS mcon families, HARTING has expanded
Computer networks, data communication and Internet
 **** 1 Computer networks, data communication and Internet Introduction **** Computer networks: summary 2 The following gives an overview of computer networks and data communication:»the basic principles»local
**** 1 Computer networks, data communication and Internet Introduction **** Computer networks: summary 2 The following gives an overview of computer networks and data communication:»the basic principles»local
SiteCelerate white paper
 SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
SiteCelerate white paper Arahe Solutions SITECELERATE OVERVIEW As enterprises increases their investment in Web applications, Portal and websites and as usage of these applications increase, performance
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
EXPLORER. TFT Filter CONFIGURATION
 EXPLORER TFT Filter Configuration Page 1 of 9 EXPLORER TFT Filter CONFIGURATION Thrane & Thrane Author: HenrikMøller Rev. PA4 Page 1 6/15/2006 EXPLORER TFT Filter Configuration Page 2 of 9 1 Table of Content
EXPLORER TFT Filter Configuration Page 1 of 9 EXPLORER TFT Filter CONFIGURATION Thrane & Thrane Author: HenrikMøller Rev. PA4 Page 1 6/15/2006 EXPLORER TFT Filter Configuration Page 2 of 9 1 Table of Content
Designing a Microsoft Exchange Server 2003 Organization
 Designing a Microsoft Exchange Server 2003 Organization Course 2008 - Two days - Instructor-led - Hands-On Introduction This two-day instructor-led course provides students with the knowledge and skills
Designing a Microsoft Exchange Server 2003 Organization Course 2008 - Two days - Instructor-led - Hands-On Introduction This two-day instructor-led course provides students with the knowledge and skills
Basic Networking Concepts. 1. Introduction 2. Protocols 3. Protocol Layers 4. Network Interconnection/Internet
 Basic Networking Concepts 1. Introduction 2. Protocols 3. Protocol Layers 4. Network Interconnection/Internet 1 1. Introduction -A network can be defined as a group of computers and other devices connected
Basic Networking Concepts 1. Introduction 2. Protocols 3. Protocol Layers 4. Network Interconnection/Internet 1 1. Introduction -A network can be defined as a group of computers and other devices connected
The changing face of global data network traffic
 The changing face of global data network traffic Around the turn of the 21st century, MPLS very rapidly became the networking protocol of choice for large national and international institutions. This
The changing face of global data network traffic Around the turn of the 21st century, MPLS very rapidly became the networking protocol of choice for large national and international institutions. This
Lecture 1. Lecture Overview. Intro to Networking. Intro to Networking. Motivation behind Networking. Computer / Data Networks
 Lecture 1 An Introduction to Networking Chapter 1, pages 1-22 Dave Novak BSAD 146, Introduction to Networking School of Business Administration University of Vermont Lecture Overview Brief introduction
Lecture 1 An Introduction to Networking Chapter 1, pages 1-22 Dave Novak BSAD 146, Introduction to Networking School of Business Administration University of Vermont Lecture Overview Brief introduction
Multi-Homing Dual WAN Firewall Router
 Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
Multi-Homing Dual WAN Firewall Router Quick Installation Guide M73-APO09-400 Multi-Homing Dual WAN Firewall Router Overview The Multi-Homing Dual WAN Firewall Router provides three 10/100Mbit Ethernet
A Model Design of Network Security for Private and Public Data Transmission
 2011, TextRoad Publication ISSN 2090-424X Journal of Basic and Applied Scientific Research www.textroad.com A Model Design of Network Security for Private and Public Data Transmission Farhan Pervez, Ali
2011, TextRoad Publication ISSN 2090-424X Journal of Basic and Applied Scientific Research www.textroad.com A Model Design of Network Security for Private and Public Data Transmission Farhan Pervez, Ali
BCIS 4680 -- BUSINESS DATA COMMUNICATIONS and NETWORKING Mr. Cengiz Capan -- Spring 2016
 Office : BLB 290E, Business Leadership Building Office Hours: Tu &Th 9:00 am - 11:00 am, or by appointment/drop-in Telephone: 940-565-4660 Web Page: http://www.coba.unt.edu/bcis/faculty/capan/capan.htm
Office : BLB 290E, Business Leadership Building Office Hours: Tu &Th 9:00 am - 11:00 am, or by appointment/drop-in Telephone: 940-565-4660 Web Page: http://www.coba.unt.edu/bcis/faculty/capan/capan.htm
CTS2134 Introduction to Networking. Module 8.4 8.7 Network Security
 CTS2134 Introduction to Networking Module 8.4 8.7 Network Security Switch Security: VLANs A virtual LAN (VLAN) is a logical grouping of computers based on a switch port. VLAN membership is configured by
CTS2134 Introduction to Networking Module 8.4 8.7 Network Security Switch Security: VLANs A virtual LAN (VLAN) is a logical grouping of computers based on a switch port. VLAN membership is configured by
MCN Health Monitor. The finger on the pulse of your critical systems. David Tayler Service Engineer, OSISoft
 MCN Health Monitor The finger on the pulse of your critical systems David Tayler Service Engineer, OSISoft MCN Health Monitor Today s presentation Introduction Description Interfaces Tag Builders Client
MCN Health Monitor The finger on the pulse of your critical systems David Tayler Service Engineer, OSISoft MCN Health Monitor Today s presentation Introduction Description Interfaces Tag Builders Client
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007
 5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
5053A: Designing a Messaging Infrastructure Using Microsoft Exchange Server 2007 Course Number: 5053A Course Length: 3 Days Course Overview This three-day instructor-led course provides students with the
Flexible Identity Federation
 Flexible Identity Federation Quick start guide version 1.0.1 Publication history Date Description Revision 2015.09.23 initial release 1.0.0 2015.12.11 minor updates 1.0.1 Copyright Orange Business Services
Flexible Identity Federation Quick start guide version 1.0.1 Publication history Date Description Revision 2015.09.23 initial release 1.0.0 2015.12.11 minor updates 1.0.1 Copyright Orange Business Services
IP Networking. Overview. Networks Impact Daily Life. IP Networking - Part 1. How Networks Impact Daily Life. How Networks Impact Daily Life
 Overview Dipl.-Ing. Peter Schrotter Institute of Communication Networks and Satellite Communications Graz University of Technology, Austria Fundamentals of Communicating over the Network Application Layer
Overview Dipl.-Ing. Peter Schrotter Institute of Communication Networks and Satellite Communications Graz University of Technology, Austria Fundamentals of Communicating over the Network Application Layer
Resonate Central Dispatch
 Resonate Central Dispatch Microsoft Exchange 2010 Resonate, Inc. Tel. + 1.408.545.5535 Fax + 1.408.545.5502 www.resonate.com Copyright 2013 Resonate, Inc. All rights reserved. Resonate Incorporated and
Resonate Central Dispatch Microsoft Exchange 2010 Resonate, Inc. Tel. + 1.408.545.5535 Fax + 1.408.545.5502 www.resonate.com Copyright 2013 Resonate, Inc. All rights reserved. Resonate Incorporated and
BlackBerry Enterprise Service 10. Version: 10.2. Configuration Guide
 BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
BlackBerry Enterprise Service 10 Version: 10.2 Configuration Guide Published: 2015-02-27 SWD-20150227164548686 Contents 1 Introduction...7 About this guide...8 What is BlackBerry Enterprise Service 10?...9
9236245 Issue 2EN. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
JK0-022 CompTIA Academic/E2C Security+ Certification Exam CompTIA
 JK0-022 CompTIA Academic/E2C Security+ Certification Exam CompTIA To purchase Full version of Practice exam click below; http://www.certshome.com/jk0-022-practice-test.html FOR CompTIA JK0-022 Exam Candidates
JK0-022 CompTIA Academic/E2C Security+ Certification Exam CompTIA To purchase Full version of Practice exam click below; http://www.certshome.com/jk0-022-practice-test.html FOR CompTIA JK0-022 Exam Candidates
Monitoring and Troubleshooting Microsoft Exchange Server 2007 (5051A) Course length: 2 days
 Monitoring and Troubleshooting Microsoft Exchange Server 2007 (5051A) Course length: 2 days Who Should Attend: This workshop is intended for experienced enterprise-level messaging professionals who have
Monitoring and Troubleshooting Microsoft Exchange Server 2007 (5051A) Course length: 2 days Who Should Attend: This workshop is intended for experienced enterprise-level messaging professionals who have
Chapter 2 - The TCP/IP and OSI Networking Models
 Chapter 2 - The TCP/IP and OSI Networking Models TCP/IP : Transmission Control Protocol/Internet Protocol OSI : Open System Interconnection RFC Request for Comments TCP/IP Architecture Layers Application
Chapter 2 - The TCP/IP and OSI Networking Models TCP/IP : Transmission Control Protocol/Internet Protocol OSI : Open System Interconnection RFC Request for Comments TCP/IP Architecture Layers Application
SuSE email Solutions Based on
 SuSE email Solutions Based on SuSE Linux Enterprise Server 8 SuSE Linux AG Whitepaper SuSE email Solutions Based on SuSE Linux Enterprise Server 8 1 Overview... 3 2 Value Propositions... 3 3 System Structure
SuSE email Solutions Based on SuSE Linux Enterprise Server 8 SuSE Linux AG Whitepaper SuSE email Solutions Based on SuSE Linux Enterprise Server 8 1 Overview... 3 2 Value Propositions... 3 3 System Structure
Building a Systems Infrastructure to Support e- Business
 Building a Systems Infrastructure to Support e- Business NO WARRANTIES OF ANY NATURE ARE EXTENDED BY THE DOCUMENT. Any product and related material disclosed herein are only furnished pursuant and subject
Building a Systems Infrastructure to Support e- Business NO WARRANTIES OF ANY NATURE ARE EXTENDED BY THE DOCUMENT. Any product and related material disclosed herein are only furnished pursuant and subject
Configuration Guide BES12. Version 12.1
 Configuration Guide BES12 Version 12.1 Published: 2015-04-22 SWD-20150422113638568 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12... 8 Product documentation...
Configuration Guide BES12 Version 12.1 Published: 2015-04-22 SWD-20150422113638568 Contents Introduction... 7 About this guide...7 What is BES12?...7 Key features of BES12... 8 Product documentation...
Http://www.passcert.com
 Http://www.passcert.com Exam : 70-337 Title : Enterprise Voice & Online Services with Microsoft Lync Server 2013 Version : DEMO 1 / 18 Topic 1, Litware, Inc Case A Overview Litware, Inc., is an international
Http://www.passcert.com Exam : 70-337 Title : Enterprise Voice & Online Services with Microsoft Lync Server 2013 Version : DEMO 1 / 18 Topic 1, Litware, Inc Case A Overview Litware, Inc., is an international
CSE 3461 / 5461: Computer Networking & Internet Technologies
 Autumn Semester 2014 CSE 3461 / 5461: Computer Networking & Internet Technologies Instructor: Prof. Kannan Srinivasan 08/28/2014 Announcement Drop before Friday evening! k. srinivasan Presentation A 2
Autumn Semester 2014 CSE 3461 / 5461: Computer Networking & Internet Technologies Instructor: Prof. Kannan Srinivasan 08/28/2014 Announcement Drop before Friday evening! k. srinivasan Presentation A 2
Basics of Internet Security
 Basics of Internet Security Premraj Jeyaprakash About Technowave, Inc. Technowave is a strategic and technical consulting group focused on bringing processes and technology into line with organizational
Basics of Internet Security Premraj Jeyaprakash About Technowave, Inc. Technowave is a strategic and technical consulting group focused on bringing processes and technology into line with organizational
Addressing Convergence and IP Telephony in Enterprise Communications
 Addressing Convergence and IP Telephony in Enterprise Communications Introduction The convergence of voice and data networks has begun to drive radical changes in the development and delivery of products
Addressing Convergence and IP Telephony in Enterprise Communications Introduction The convergence of voice and data networks has begun to drive radical changes in the development and delivery of products
Astaro Deployment Guide High Availability Options Clustering and Hot Standby
 Connect With Confidence Astaro Deployment Guide Clustering and Hot Standby Table of Contents Introduction... 2 Active/Passive HA (Hot Standby)... 2 Active/Active HA (Cluster)... 2 Astaro s HA Act as One...
Connect With Confidence Astaro Deployment Guide Clustering and Hot Standby Table of Contents Introduction... 2 Active/Passive HA (Hot Standby)... 2 Active/Active HA (Cluster)... 2 Astaro s HA Act as One...
Firewall Environments. Name
 Complliiance Componentt DEEFFI INITION Description Rationale Firewall Environments Firewall Environment is a term used to describe the set of systems and components that are involved in providing or supporting
Complliiance Componentt DEEFFI INITION Description Rationale Firewall Environments Firewall Environment is a term used to describe the set of systems and components that are involved in providing or supporting
IMPLEMENTATION OF INTELLIGENT FIREWALL TO CHECK INTERNET HACKERS THREAT
 IMPLEMENTATION OF INTELLIGENT FIREWALL TO CHECK INTERNET HACKERS THREAT Roopa K. Panduranga Rao MV Dept of CS and Engg., Dept of IS and Engg., J.N.N College of Engineering, J.N.N College of Engineering,
IMPLEMENTATION OF INTELLIGENT FIREWALL TO CHECK INTERNET HACKERS THREAT Roopa K. Panduranga Rao MV Dept of CS and Engg., Dept of IS and Engg., J.N.N College of Engineering, J.N.N College of Engineering,
Middleware- Driven Mobile Applications
 Middleware- Driven Mobile Applications A motwin White Paper When Launching New Mobile Services, Middleware Offers the Fastest, Most Flexible Development Path for Sophisticated Apps 1 Executive Summary
Middleware- Driven Mobile Applications A motwin White Paper When Launching New Mobile Services, Middleware Offers the Fastest, Most Flexible Development Path for Sophisticated Apps 1 Executive Summary
Solution Brief FortiMail for Service Providers. Nathalie Rivat
 Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Solution Brief FortiMail for Service Providers Nathalie Rivat Agenda FortiMail for Internet Service Providers Outbound antispam to prevent blacklisting MMS routing for Mobile Operators Inbound antispam
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0
 Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
Internetworking Microsoft TCP/IP on Microsoft Windows NT 4.0 Course length: 5 Days Course No. 688 - Five days - Instructor-led Introduction This course provides students with the knowledge and skills required
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010
 10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
10135A: Configuring, Managing, and Troubleshooting Microsoft Exchange Server 2010 Course Number: 10135A Course Length: 5 Day Course Overview This instructor-led course will provide you with the knowledge
Web Application Hosting Cloud Architecture
 Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
Web Application Hosting Cloud Architecture Executive Overview This paper describes vendor neutral best practices for hosting web applications using cloud computing. The architectural elements described
TFS ApplicationControl White Paper
 White Paper Transparent, Encrypted Access to Networked Applications TFS Technology www.tfstech.com Table of Contents Overview 3 User Friendliness Saves Time 3 Enhanced Security Saves Worry 3 Software Componenets
White Paper Transparent, Encrypted Access to Networked Applications TFS Technology www.tfstech.com Table of Contents Overview 3 User Friendliness Saves Time 3 Enhanced Security Saves Worry 3 Software Componenets
Microsoft Exchange 2013 Ultimate Bootcamp Your pathway to becoming a GREAT Exchange Administrator
 Microsoft Exchange 2013 Ultimate Bootcamp Your pathway to becoming a GREAT Exchange Administrator Introduction Microsoft Exchange with its inherent high level of security features, improved assistant,
Microsoft Exchange 2013 Ultimate Bootcamp Your pathway to becoming a GREAT Exchange Administrator Introduction Microsoft Exchange with its inherent high level of security features, improved assistant,
Exchange Server. Microsoft UNLEASHED SAM. Guy Yardeni. Technical Edit by Ed Crowley. Rand Morimo io Michael Noel. Chris Amaris.
 Rand Morimo io Michael Noel Guy Yardeni Chris Amaris Andrew Abbate Technical Edit by Ed Crowley Microsoft Exchange Server 201 UNLEASHED SAM 800 East 96th Street, Indianapolis, Indiana 46240 USA Table of
Rand Morimo io Michael Noel Guy Yardeni Chris Amaris Andrew Abbate Technical Edit by Ed Crowley Microsoft Exchange Server 201 UNLEASHED SAM 800 East 96th Street, Indianapolis, Indiana 46240 USA Table of
Terminology. Internet Addressing System
 Terminology A local area network (LAN) is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. The defining characteristics
Terminology A local area network (LAN) is a computer network covering a small physical area, like a home, office, or small group of buildings, such as a school, or an airport. The defining characteristics
Effective disaster recovery using Software defined networking
 Effective disaster recovery using Software defined networking Thyagaraju, Mrs. Jyothi. K.S, Girish.L PG Student, Associate professor, Assistant Professor Dept of CSE, Cit, Gubbi, Tumkur Abstract In this
Effective disaster recovery using Software defined networking Thyagaraju, Mrs. Jyothi. K.S, Girish.L PG Student, Associate professor, Assistant Professor Dept of CSE, Cit, Gubbi, Tumkur Abstract In this
Introduction to Network Management
 Introduction to Network Management Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network Management Requirement SNMP family OSI management function
Introduction to Network Management Chu-Sing Yang Department of Electrical Engineering National Cheng Kung University Outline Introduction Network Management Requirement SNMP family OSI management function
Transport server data paths
 1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
Exchange 2013 Uusi sähköposti. Jussi Lehtoalho Principal Consultant, Microsoft Oy Sakari Kouti Järjestelmäpäällikkö, FC Sovelto Oyj
 Exchange 2013 Uusi sähköposti Jussi Lehtoalho Principal Consultant, Microsoft Oy Sakari Kouti Järjestelmäpäällikkö, FC Sovelto Oyj Agenda Uusi Exchange 2013 arkkitehtuuri Exchange 2013 versiot Exchange
Exchange 2013 Uusi sähköposti Jussi Lehtoalho Principal Consultant, Microsoft Oy Sakari Kouti Järjestelmäpäällikkö, FC Sovelto Oyj Agenda Uusi Exchange 2013 arkkitehtuuri Exchange 2013 versiot Exchange
MANAGING NETWORK COMPONENTS USING SNMP
 MANAGING NETWORK COMPONENTS USING SNMP Abubucker Samsudeen Shaffi 1 Mohanned Al-Obaidy 2 Gulf College 1, 2 Sultanate of Oman. Email: abobacker.shaffi@gulfcollegeoman.com mohaned@gulfcollegeoman.com Abstract:
MANAGING NETWORK COMPONENTS USING SNMP Abubucker Samsudeen Shaffi 1 Mohanned Al-Obaidy 2 Gulf College 1, 2 Sultanate of Oman. Email: abobacker.shaffi@gulfcollegeoman.com mohaned@gulfcollegeoman.com Abstract:
CITS1231 Web Technologies. Client, Server, the Internet, and the Web
 CITS1231 Web Technologies Client, Server, the Internet, and the Web Topic Outline How does the Internet work Client Server Architecture Connections Communications Protocols Addressing Routing One of the
CITS1231 Web Technologies Client, Server, the Internet, and the Web Topic Outline How does the Internet work Client Server Architecture Connections Communications Protocols Addressing Routing One of the
Microsoft. Exchange 2013. Referent: Daniel Glomb System Architect
 Microsoft Exchange 2013 Referent: Daniel Glomb System Architect Agenda What s new Architecture Client Access Server Mailbox Server Migration Outlook 2013 / OWA What s new in Exchange 2013 Exchange Administration
Microsoft Exchange 2013 Referent: Daniel Glomb System Architect Agenda What s new Architecture Client Access Server Mailbox Server Migration Outlook 2013 / OWA What s new in Exchange 2013 Exchange Administration
Score your ACE in Business and IT Efficiency
 Score your ACE in Business and IT Efficiency Optimize your Data Center capabilities with Cisco s Application Control Engine (ACE) Agenda In this webinar, you will be given an insight into the following:
Score your ACE in Business and IT Efficiency Optimize your Data Center capabilities with Cisco s Application Control Engine (ACE) Agenda In this webinar, you will be given an insight into the following:
Lesson Plans Configuring Exchange Server 2007
 Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Lesson Plans Configuring Exchange Server 2007 (Exam 70-236) Version 2.1 Table of Contents Course Overview... 2 Section 1.1: Server-based Messaging... 4 Section 1.2: Exchange Versions... 5 Section 1.3:
Configuration Guide BES12. Version 12.2
 Configuration Guide BES12 Version 12.2 Published: 2015-07-07 SWD-20150630131852557 Contents About this guide... 8 Getting started... 9 Administrator permissions you need to configure BES12... 9 Obtaining
Configuration Guide BES12 Version 12.2 Published: 2015-07-07 SWD-20150630131852557 Contents About this guide... 8 Getting started... 9 Administrator permissions you need to configure BES12... 9 Obtaining
Des Moines Area Community College
 Des Moines Area Community College Course Information EFFECTIVE Aug. 2006 Acronym/Number NET 653 Historical Ref. MCSE 340 Title Microsoft Exchange Server Credit breakout 4 3 2 0 0 (credit lecture lab practicum
Des Moines Area Community College Course Information EFFECTIVE Aug. 2006 Acronym/Number NET 653 Historical Ref. MCSE 340 Title Microsoft Exchange Server Credit breakout 4 3 2 0 0 (credit lecture lab practicum
Secure Networks for Process Control
 Secure Networks for Process Control Leveraging a Simple Yet Effective Policy Framework to Secure the Modern Process Control Network An Enterasys Networks White Paper There is nothing more important than
Secure Networks for Process Control Leveraging a Simple Yet Effective Policy Framework to Secure the Modern Process Control Network An Enterasys Networks White Paper There is nothing more important than
Configuration Guide BES12. Version 12.3
 Configuration Guide BES12 Version 12.3 Published: 2016-01-19 SWD-20160119132230232 Contents About this guide... 7 Getting started... 8 Configuring BES12 for the first time...8 Configuration tasks for managing
Configuration Guide BES12 Version 12.3 Published: 2016-01-19 SWD-20160119132230232 Contents About this guide... 7 Getting started... 8 Configuring BES12 for the first time...8 Configuration tasks for managing
Netsweeper Whitepaper
 Netsweeper Inc. Corporate Headquarters 104 Dawson Road Suite 100 Guelph, ON, Canada N1H 1A7 CANADA T: +1 (519) 826 5222 F: +1 (519) 826 5228 Netsweeper Whitepaper Deploying Netsweeper Internet Content
Netsweeper Inc. Corporate Headquarters 104 Dawson Road Suite 100 Guelph, ON, Canada N1H 1A7 CANADA T: +1 (519) 826 5222 F: +1 (519) 826 5228 Netsweeper Whitepaper Deploying Netsweeper Internet Content
CNS-207 Implementing Citrix NetScaler 10.5 for App and Desktop Solutions
 CNS-207 Implementing Citrix NetScaler 10.5 for App and Desktop Solutions The objective of Implementing Citrix NetScaler 10.5 for App and Desktop Solutions is to provide the foundational concepts and skills
CNS-207 Implementing Citrix NetScaler 10.5 for App and Desktop Solutions The objective of Implementing Citrix NetScaler 10.5 for App and Desktop Solutions is to provide the foundational concepts and skills
Sage ERP Accpac Online
 Sage ERP Accpac Online Mac Resource Guide Thank you for choosing Sage ERP Accpac Online. This Resource Guide will provide important information and instructions on how you can get started using your Mac
Sage ERP Accpac Online Mac Resource Guide Thank you for choosing Sage ERP Accpac Online. This Resource Guide will provide important information and instructions on how you can get started using your Mac
Connecting with Computer Science, 2e. Chapter 5 The Internet
 Connecting with Computer Science, 2e Chapter 5 The Internet Objectives In this chapter you will: Learn what the Internet really is Become familiar with the architecture of the Internet Become familiar
Connecting with Computer Science, 2e Chapter 5 The Internet Objectives In this chapter you will: Learn what the Internet really is Become familiar with the architecture of the Internet Become familiar
SECTION 1: INTRODUCTION
 3117 NETWORK ARCHITECTURE STANDARD OWNER: Security Management Branch ISSUE DATE: 10/25/2011 DISTRIBUTION: All Employees REVISED DATE: 7/1/2013 SECTION 1: INTRODUCTION The California Department of Technology
3117 NETWORK ARCHITECTURE STANDARD OWNER: Security Management Branch ISSUE DATE: 10/25/2011 DISTRIBUTION: All Employees REVISED DATE: 7/1/2013 SECTION 1: INTRODUCTION The California Department of Technology
Sage 300 ERP Online. Mac Resource Guide. (Formerly Sage ERP Accpac Online) Updated June 1, 2012. Page 1
 Sage 300 ERP Online (Formerly Sage ERP Accpac Online) Mac Resource Guide Updated June 1, 2012 Page 1 Table of Contents 1.0 Introduction... 3 2.0 Getting Started with Sage 300 ERP Online using a Mac....
Sage 300 ERP Online (Formerly Sage ERP Accpac Online) Mac Resource Guide Updated June 1, 2012 Page 1 Table of Contents 1.0 Introduction... 3 2.0 Getting Started with Sage 300 ERP Online using a Mac....
1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet
 Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
Review questions 1 Data information is sent onto the network cable using which of the following? A Communication protocol B Data packet C Media access method D Packages 2 To which TCP/IP architecture layer
EE4367 Telecom. Switching & Transmission. Prof. Murat Torlak
 Packet Switching and Computer Networks Switching As computer networks became more pervasive, more and more data and also less voice was transmitted over telephone lines. Circuit Switching The telephone
Packet Switching and Computer Networks Switching As computer networks became more pervasive, more and more data and also less voice was transmitted over telephone lines. Circuit Switching The telephone
The Internet, Intranets, and Extranets. What is the Internet. What is the Internet cont d.
 C H A P T E R 7 The Internet, Intranets, and Extranets What is the Internet Millions of computers, all linked together on a computer network. A home computer usually links to the Internet using a phone
C H A P T E R 7 The Internet, Intranets, and Extranets What is the Internet Millions of computers, all linked together on a computer network. A home computer usually links to the Internet using a phone
Management Software. Web Browser User s Guide AT-S106. For the AT-GS950/48 Gigabit Ethernet Smart Switch. Version 1.0.0. 613-001339 Rev.
 Management Software AT-S106 Web Browser User s Guide For the AT-GS950/48 Gigabit Ethernet Smart Switch Version 1.0.0 613-001339 Rev. A Copyright 2010 Allied Telesis, Inc. All rights reserved. No part of
Management Software AT-S106 Web Browser User s Guide For the AT-GS950/48 Gigabit Ethernet Smart Switch Version 1.0.0 613-001339 Rev. A Copyright 2010 Allied Telesis, Inc. All rights reserved. No part of
Top-Down Network Design
 Top-Down Network Design Chapter Five Designing a Network Topology Copyright 2010 Cisco Press & Priscilla Oppenheimer Topology A map of an internetwork that indicates network segments, interconnection points,
Top-Down Network Design Chapter Five Designing a Network Topology Copyright 2010 Cisco Press & Priscilla Oppenheimer Topology A map of an internetwork that indicates network segments, interconnection points,
Chapter 5. Data Communication And Internet Technology
 Chapter 5 Data Communication And Internet Technology Purpose Understand the fundamental networking concepts Agenda Network Concepts Communication Protocol TCP/IP-OSI Architecture Network Types LAN WAN
Chapter 5 Data Communication And Internet Technology Purpose Understand the fundamental networking concepts Agenda Network Concepts Communication Protocol TCP/IP-OSI Architecture Network Types LAN WAN
Network Simulation Traffic, Paths and Impairment
 Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
Network Simulation Traffic, Paths and Impairment Summary Network simulation software and hardware appliances can emulate networks and network hardware. Wide Area Network (WAN) emulation, by simulating
8. Firewall Design & Implementation
 DMZ Networks The most common firewall environment implementation is known as a DMZ, or DeMilitarized Zone network. A DMZ network is created out of a network connecting two firewalls; i.e., when two or
DMZ Networks The most common firewall environment implementation is known as a DMZ, or DeMilitarized Zone network. A DMZ network is created out of a network connecting two firewalls; i.e., when two or
CompTIA Network+ (Exam N10-005)
 CompTIA Network+ (Exam N10-005) Length: Location: Language(s): Audience(s): Level: Vendor: Type: Delivery Method: 5 Days 182, Broadway, Newmarket, Auckland English, Entry Level IT Professionals Intermediate
CompTIA Network+ (Exam N10-005) Length: Location: Language(s): Audience(s): Level: Vendor: Type: Delivery Method: 5 Days 182, Broadway, Newmarket, Auckland English, Entry Level IT Professionals Intermediate
250-310. Administration of Symantec Enterprise Vault 10.0 for Exchange. Version: Demo. Page <<1/12>>
 250-310 Administration of Symantec Enterprise Vault 10.0 for Exchange Version: Demo Page 1.Enterprise Vault converts mail message attachments to text or HTML. What is a benefit of changing the
250-310 Administration of Symantec Enterprise Vault 10.0 for Exchange Version: Demo Page 1.Enterprise Vault converts mail message attachments to text or HTML. What is a benefit of changing the
The OSI Model and the TCP/IP Protocol Suite PROTOCOL LAYERS. Hierarchy. Services THE OSI MODEL
 The OSI Model and the TCP/IP Protocol Suite - the OSI model was never fully implemented. - The TCP/IP protocol suite became the dominant commercial architecture because it was used and tested extensively
The OSI Model and the TCP/IP Protocol Suite - the OSI model was never fully implemented. - The TCP/IP protocol suite became the dominant commercial architecture because it was used and tested extensively
Course Description and Outline. IT Essential II: Network Operating Systems V2.0
 Course Description and Outline IT Essential II: Network Operating Systems V2.0 Course Outline 1. Operating System Fundamentals 1.1 Operating System Basics 1.1.1 Overview of PC operating systems 1.1.2 PCs
Course Description and Outline IT Essential II: Network Operating Systems V2.0 Course Outline 1. Operating System Fundamentals 1.1 Operating System Basics 1.1.1 Overview of PC operating systems 1.1.2 PCs
Features of AnyShare
 of AnyShare of AnyShare CONTENT Brief Introduction of AnyShare... 3 Chapter 1 Centralized Management... 5 1.1 Operation Management... 5 1.2 User Management... 5 1.3 User Authentication... 6 1.4 Roles...
of AnyShare of AnyShare CONTENT Brief Introduction of AnyShare... 3 Chapter 1 Centralized Management... 5 1.1 Operation Management... 5 1.2 User Management... 5 1.3 User Authentication... 6 1.4 Roles...
70-662: Deploying Microsoft Exchange Server 2010
 70-662: Deploying Microsoft Exchange Server 2010 Course Introduction Course Introduction Chapter 01 - Active Directory and Supporting Infrastructure Active Directory and Supporting Infrastructure Network
70-662: Deploying Microsoft Exchange Server 2010 Course Introduction Course Introduction Chapter 01 - Active Directory and Supporting Infrastructure Active Directory and Supporting Infrastructure Network
FAQs for Oracle iplanet Proxy Server 4.0
 FAQs for Oracle iplanet Proxy Server 4.0 Get answers to the questions most frequently asked about Oracle iplanet Proxy Server Q: What is Oracle iplanet Proxy Server (Java System Web Proxy Server)? A: Oracle
FAQs for Oracle iplanet Proxy Server 4.0 Get answers to the questions most frequently asked about Oracle iplanet Proxy Server Q: What is Oracle iplanet Proxy Server (Java System Web Proxy Server)? A: Oracle
Communication Networks. MAP-TELE 2011/12 José Ruela
 Communication Networks MAP-TELE 2011/12 José Ruela Network basic mechanisms Introduction to Communications Networks Communications networks Communications networks are used to transport information (data)
Communication Networks MAP-TELE 2011/12 José Ruela Network basic mechanisms Introduction to Communications Networks Communications networks Communications networks are used to transport information (data)
Protocols and Architecture. Protocol Architecture.
 Protocols and Architecture Protocol Architecture. Layered structure of hardware and software to support exchange of data between systems/distributed applications Set of rules for transmission of data between
Protocols and Architecture Protocol Architecture. Layered structure of hardware and software to support exchange of data between systems/distributed applications Set of rules for transmission of data between
Application Discovery Manager User s Guide vcenter Application Discovery Manager 6.2.1
 Application Discovery Manager User s Guide vcenter Application Discovery Manager 6.2.1 This document supports the version of each product listed and supports all subsequent versions until the document
Application Discovery Manager User s Guide vcenter Application Discovery Manager 6.2.1 This document supports the version of each product listed and supports all subsequent versions until the document
MS-10135 - Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010
 MS-10135 - Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Introduction This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange
MS-10135 - Configuring, Managing and Troubleshooting Microsoft Exchange Server 2010 Introduction This course will provide you with the knowledge and skills to configure and manage a Microsoft Exchange
Introduction Chapter 1. Uses of Computer Networks
 Introduction Chapter 1 Uses of Computer Networks Network Hardware Network Software Reference Models Example Networks Network Standardization Metric Units Revised: August 2011 Uses of Computer Networks
Introduction Chapter 1 Uses of Computer Networks Network Hardware Network Software Reference Models Example Networks Network Standardization Metric Units Revised: August 2011 Uses of Computer Networks
Exchange Server 2013 Architecture. Ross Smith IV Principal Program Manager, Exchange Server
 Exchange Server 2013 Architecture Ross Smith IV Principal Program Manager, Exchange Server Disclaimer 2012 Microsoft Corporation. All rights reserved. Microsoft, Office 365, and other product and service
Exchange Server 2013 Architecture Ross Smith IV Principal Program Manager, Exchange Server Disclaimer 2012 Microsoft Corporation. All rights reserved. Microsoft, Office 365, and other product and service
BUILT FOR YOU. Contents. Cloudmore Exchange
 BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
