To Improve Register File Integrity against Soft Errors By using self - Immunity Technique
|
|
|
- Jasmine Ford
- 10 years ago
- Views:
Transcription
1 To Improve Register File Integrity against Soft Errors By using self - Immunity Technique A. Praveen Post Graduate Scholar, Indur Institute of Engineering & Technology, Siddipet N.Sai Kumar Assistant Professor, Indur Institute of Engineering & Technology, Siddipet Abstract - Continuous shrinking in feature size, increasing power density etc, increase the vulnerability of microprocessors against soft errors even in terrestrial applications. The register file is one of the essential architectural components where soft errors can be very mischievous because errors may rapidly spread from there throughout the whole system. Thus, register files are recognized as one of the major concerns when it comes to reliability. The paper introduces Self-Immunity, a technique that improves the integrity of the register file with respect to soft errors. Based on the observation that a certain number of register bits are not always used to represent a value stored in a register. The paper deals with the difficulty to exploit this obvious observation to enhance the register file integrity against soft errors. We show that our technique can reduce the vulnerability of the register file considerably while exhibiting smaller overhead in terms of area and power consumption compared to state-of-the-art in register file protection. For embedded systems under stringent cost constraints, where area, performance, power and reliability cannot be simply compromised, we propose a soft error mitigation technique for register files. Key words: self immunity Technique, Register, ECC, MTBF I.INTRODUCTION In the early days of computers, glitches were an accepted way of life. Since then, as computers have become more reliable (and more relied upon), glitches are no longer acceptable yet they still occur. One of the most intractable sources of glitches has been the transient bit-flip, or soft memory error: a random event that corrupts the value stored in a memory cell without damaging the cell itself. Soft errors* in electronic memory were first traced to alpha particle* emissions from chip packaging materials. Since then, memory manufacturers have eliminated most alpha particle sources from their materials, changed their designs to make them less susceptible. Tests and standards have been developed to measure and improve the resistance of memory chips to alpha particles but soft errors have not disappeared. Further testing, mostly performed by avionics and space organizations, pinpointed a more pernicious source of soft errors: cosmic rays*. At ground level, cosmic radiation is about 95% neutrons and 5% protons. These particles can cause soft errors directly; they can also interact with atomic nuclei to produce troublesome short-range heavy ions. Cosmic rays cannot be eliminated at their source, and effective shielding would require meters of concrete or rock. To eliminate the soft memory errors that are induced by cosmic rays, memory manufacturers must either produce designs that can resist cosmic ray effects or else invent mechanisms to detect and correct the errors. Over the last decade, and in spite of the increasingly complex architectures, and the rapid growth of new technologies, the technology scaling has raised soft errors to become one of the major sources for processor crashing in many systems in the nano scale era. Soft errors caused by charged particles are dangerous primarily in high atmospheric, where heavy alpha particles are available. However, trends in today s nanometer technologies such as aggressive shrinking have made low-energy particles, which are more superabundant than high-energy particles, cause appropriate charge to provoke a soft error. Due to their large number of components, supercomputers are particularly susceptible to soft errors. I.I Register file soft errors Register file (RF) is extremely vulnerable to soft errors, and traditional redundancy based schemes to protect the Vol. 2 Issue 3 May ISSN: X
2 RF are prohibitive not only because RF is often in the timing critical path of the processor, but also since it is one of the hottest blocks on the chip, and therefore adding any extra circuitry to it is not desirable. Device scaling trends dramatically increase the susceptibility of microprocessors to soft errors. Further, mounting demand for embedded microprocessors in a wide array of safety critical applications, ranging from automobiles to pacemakers, compounds the importance of addressing the soft error problem. The paper addresses this challenge by introducing a novel technique, called Self-Immunity to improve the resiliency of register files to soft errors, especially desirable for processors that demand high register file integrity under stringent constraints. Our contributions within this paper are as follows: (1) We present a technique for improving the immunity of register files against soft errors by storing the ECC in the unused bits of a register. (2) We solve the problem of the area and power overhead that typically comes as a negative side effect in register file protection by achieving high area and power saving With a slight degrading in the register file vulnerability reduction (7%) compared to a full protection scheme. II. SOFT ERROR BACKGROUND AND TERMINOLOGY II.I.IMTBF and FIT Vendors express an error budget at a reference altitude in terms of Mean Time between Failures (MTBF). Errors are often further classified as undetected or detected. The former are typically referred to as silent data corruption (SDC); we call the latter detected unrecoverable errors (DUE).For example, for its Power4 processor-based systems, IBM targets 1000 years system MTBF for SDC errors, 25 years system MTBF for DUE errors that result in a system crash, and 10 years system MTBF for DUE errors that result in an application crash. One FIT specifies one failure in a billion hours. Thus, 1000 years MTBF equals 114 FIT (109 / ( )). A zero error rate corresponds to zero FIT and infinite MTBF. Designers usually work with FIT because FIT is additive, unlike MTBF.The effective FIT rate for a structure is the product of its raw circuit FIT rate and the structure s vulnerability factor, i.e., an estimate of the probability that a circuit fault will result in an observable error. The overall FIT rate of the chip is calculated by summing the effective FIT rates of all the structures on the chip.current predictions show that typical raw FIT rate numbers for latches and SRAM cells vary between FIT/bit at sea level II.II Vulnerability Factors The effective FIT rate per bit is influenced by several vulnerability factors (also known as derating factors or soft error sensitivity factors). In general, a vulnerability factor indicates the probability that an internal fault in a device s operation will result in an externally visible error. If the latch is accepting data 50% of the time, this effect results in atiming vulnerability factor for the latch of 50%.The earliest schemes of register file protection such as Triple Modular Redundancy (TMR) and ECC can achieve a high level of fault tolerance but they may not be suitable solutions in embedded systems due to their power and area overhead The proposed approach in utilizes the Cross-parity check as a method for correcting multiple errors in the register files. Spica et al.showed that there is a very little gain (just 2%) in fault tolerance for caches if they increase the protection to Double Error Correction while the overhead for that gain is considerable. Building on the concept of Architectural Vulnerability Factor (AVF), introduced by Mukherjee, Yan et al. proposed the Register Vulnerability Factor (RVF) to describe the likelihood that a soft error in registers can be spread to other system parts. In general, a value is written into a register, then it is read frequently, and later a new value is written again. Thus, any soft error occurring during write-write or read-write intervals will have no effect on the system, because it will be corrected automatically by the next write operation. On the other hand, write-read and read-read intervals are considered vulnerable intervals as is depicted in Figure-2.1. The RVF of a register is defined as the sum of the lengths of all its vulnerable intervals divided by the sum of the lengths of all its lifetimes. Vol. 2 Issue 3 May ISSN: X
3 Finally, the total vulnerability of the register file is assumed as the sum of vulnerability of all registers. Figure-2.1:Different Register Access Intervals The pure software approach at compile level introduced by Yan et al.i re-schedules the instructions in order to decrease the RVF of a register file but the proposed technique is not always very effective because it may increase the execution cycles and even the RVF in some benchmark II.III Register Vulnerability factor Toward the goal to measure register file susceptibility to soft errors accurately and quantitatively, we define the register vulnerability factor (RVF) to be the probability that a soft error in registers can be propagated to other system components (i.e., functional units, memory). As depicted in figure-2.1,in this below Equation, RVi represents any register value, the Susceptible Time (RVi) represents the time intervals that RVi is exposed to the susceptible intervals (i.e., W-R and R-R intervals for RVi), and the Lifetime (RVi) represents the lifetime of RVi, which is time interval between the time that a register is allocated for RVi and the time it is overlapped by another value. Since both the Susceptible Time (RVi) and Lifetime (RVi) can be easily obtained from a performance simulator, it would be straightforward to compute the RVF. The RVF indicates the probability that register soft errors can spread to other hardware elements and thus impact the system output. The higher the RVF, the lower the register file reliability, and hence more expensive techniques are needed to fight soft errors.in contrast, traditional software optimizations mainly focus on performance. Therefore, the RVF allows compilers to consider both performance and reliability to optimize the register access patterns. Such a software based approach has no hardware overhead, which is fundamentally different from traditional space redundancy or information redundancy techniques. Techniques to reduce register vulnerability factor are: (a) Reschedule Instructions to Reduce RVF. (b) Reliability oriented Register Assignment with Partial ECC Protection.. Vol. 2 Issue 3 May ISSN: X
4 III.SELF IMMUNITY TECHNIQUE III.I.Proposed Self-Immunity Technique We propose to exploit the register values that do not require all of the bits of a register to represent a certain value. Then, the upper unused bits of a register can beexploited to increase the register s immunity by storing the corresponding SEC Hamming Code without the need for extra bits. The Hamming Code is defined by k, the number of bits in the original word and p, the required number of parity bits (approximately log2k). Thus, the code word will be (k + log2k + 1). In our proposed technique, the optimal value of k is the value which guarantees that w, the bit-width of the register file, can cover both k, the required number of bits to represent the value, and the corresponding ECC bits of that value. In other words, the value and its ECC should be stored together within the bit-width of a register. Consequently, the following condition should be valid (k + log2k + 1 w). Thus, the optimal value of k is 26 in 32-bit architectures and 57 in 64-bit architectures.for instance, when studying 32-bit architectures, where each register can represent a 32-bit value, we may exploit the register values, which require less than or equal to 26 bits by storing the corresponding ECC bits in the upper unused six bits of that register to enhance the register file immunity against soft errors1. We call this technique Self- Immunity and we call such values 26-bit values. On the other hand, we call register values which need more than 26 bits to be represented over-26-bit register values. Figure-3.1 shows the percentage of register values usage for different applications of the MiBench Benchmark compiled for MIPS architecture. Figure-3.2: 26-bit register values and over-26-bit register values in different benchmarks As it can be noticed, in all benchmarks most of the register values are 26-bit values. In other words, the upper six bits of 88% of the stored data in the register file are actually unused. In addition to the previous key observation, the contribution of 26-bit register values in the total vulnerable intervals is much more than the contribution of over-26-bit register values. In Figure3.1, the fraction of vulnerable intervals of each benchmark is reported. As is demonstrated, the fraction of vulnerable intervals of 26-bit values is 93% on average. Vol. 2 Issue 3 May ISSN: X
5 Figure-3.2: The fraction of vulnerable intervals of 26-bit register values and over-26-bit register values in different benchmarks. III.II Implementation details Since the probability of multiple bit-errors is largely lower than the single bit-error, a single bit-error model has been considered. In our fault injection environment, faults are injected on the fly while the processor executes an application. In each fault injection simulation, one of the 32 registers is selected randomly and a bit in that register is chosen randomly and then flipped. Notice that a write operation clears out the previous injected error into that register. Likewise, by using a uniform distribution, a random cycle is chosen as the time that soft error occurs. This makes sure that the faults will be injected only when the program is executed. Since an injected fault might produce an infinite loop, a watchdog timer was implemented for the required number of execution cycles. We stop the simulation when the cycle count exceeds two times the number of cycles in the fault-free case. Towards evaluating our proposed technique, we use different applications from MiBench Benchmark compiled for MIPS architecture to take into account different possible scenarios for register utilization. Simulations were conducted using the MIPS model simulator. When a simulation terminates, the corresponding output information (final results, content of the register file, execution time and state of the processor) are stored and used to classify the simulation. 1. Wrong Answer: The application terminates normally but the results produced are not correct. 2. Latent: The application terminates normally, the results are correct but at the end of simulation the content of the register file is different from that of fault-free case. 3. Effect-Less: The application terminates normally, the results are correct, and the content of the register file is similar to that of fault-free case. 4. Exception: The processor detected the injected fault and generated an exception (e.g., invalid address exception). 5. Timed-Out: The application failed to terminate and produce results with a predefined time limit. 6. Stalling: The processor computed the expected results in a time greater than the time of fault-free case. 7. Crashing: The processor fails to terminate normally. Each benchmark was simulated 10,000 times. As a result, 10,000 soft errors were injected randomly in the register file. This number complies with those used by other research to keep the total time of simulations reasonable. For a fair comparison, we consider three models of the processor: IV.CONCLUSION For embedded systems under stringent cost constraints, where area, performance, power and reliability cannot be simply compromised, we propose a soft error mitigation technique for register files. Our experiments on different embedded system applications demonstrate that our proposed Self-Immunity technique reduces the register file vulnerability effectively and achieves high system fault coverage. Moreover, our technique is generic as it can be implemented into diverse architectures with minimum impact on the cost. It can be concluded that this technique achieves the best overall result compared to state-of-the-art in register file vulnerability reduction Vol. 2 Issue 3 May ISSN: X
6 REFERENCES [1] Greg Bronevetsky and Bronis R. de Supinski, Soft Error Vulnerability of Iterative Linear Algebra Methods, in the 22 nd annual international conference on Supercomputing, pp , [2] J.L. Autran, P. Roche, S. Sauze, G. Gasiot, D. Munteanu, P. Loaiza, M. Zampaolo and J. Borel, Real-time neutron and alpha softerror rate testing of CMOS 130nm SRAM: Altitude versus underground measurements, in ICICDT 08, pp , [3] S.S. Mukherjee, C. Weaver, J. Emer, S.K. Reinhardt and T. Austin, A Systematic Methodology to Compute the Architectural Vulnerability Factors for a High-Performance Microprocessor, in International Symposium on Microarchitecture (MICRO-36), pp.29-40, 2003 [4] T.J. Dell, A whitepaper on the benefits of Chippkill-Correct ECC for PC server main memory, in IBM Microelectonics division Nov [5] S. Kim and A.K. Somani, An adaptive write error detection technique in on-chip caches of multi-level cache systems, in Journal of microprocessors and microsystems, pp , March [6] G. Memik, M.T. Kandemir and O. Ozturk, Increasing register file immunity to transient errors, in Design, Automation and Test in Europe, pp , [7] Jongeun Lee and Aviral Shrivastava, A Compiler Optimization to Reduce Soft Errors in Register Files, in LCTES [8] Jason A. Blome, Shantanu Gupta, Shuguang Feng, and Scott Mahlke, Cost-efficient soft error protection for embedded microprocessors, in CASES 06, pp , [9] P. Montesinos, W. Liu, and J.Torrellas, Using register lifetime predictions to protect register files against soft errors, in Dependable Systems and Networks, pp , [10] M. Rebaudengo, M. S. Reorda, and M.Violante, An Accurate Analysis of theeffects of Soft Errors in the Instruction and Data Caches of a Pipelined Microprocessor, in DATE 03, pp , 2003 Vol. 2 Issue 3 May ISSN: X
CLASS: Combined Logic Architecture Soft Error Sensitivity Analysis
 CLASS: Combined Logic Architecture Soft Error Sensitivity Analysis Mojtaba Ebrahimi, Liang Chen, Hossein Asadi, and Mehdi B. Tahoori INSTITUTE OF COMPUTER ENGINEERING (ITEC) CHAIR FOR DEPENDABLE NANO COMPUTING
CLASS: Combined Logic Architecture Soft Error Sensitivity Analysis Mojtaba Ebrahimi, Liang Chen, Hossein Asadi, and Mehdi B. Tahoori INSTITUTE OF COMPUTER ENGINEERING (ITEC) CHAIR FOR DEPENDABLE NANO COMPUTING
Static-Noise-Margin Analysis of Conventional 6T SRAM Cell at 45nm Technology
 Static-Noise-Margin Analysis of Conventional 6T SRAM Cell at 45nm Technology Nahid Rahman Department of electronics and communication FET-MITS (Deemed university), Lakshmangarh, India B. P. Singh Department
Static-Noise-Margin Analysis of Conventional 6T SRAM Cell at 45nm Technology Nahid Rahman Department of electronics and communication FET-MITS (Deemed university), Lakshmangarh, India B. P. Singh Department
A Dynamic Resource Management with Energy Saving Mechanism for Supporting Cloud Computing
 A Dynamic Resource Management with Energy Saving Mechanism for Supporting Cloud Computing Liang-Teh Lee, Kang-Yuan Liu, Hui-Yang Huang and Chia-Ying Tseng Department of Computer Science and Engineering,
A Dynamic Resource Management with Energy Saving Mechanism for Supporting Cloud Computing Liang-Teh Lee, Kang-Yuan Liu, Hui-Yang Huang and Chia-Ying Tseng Department of Computer Science and Engineering,
DESIGN CHALLENGES OF TECHNOLOGY SCALING
 DESIGN CHALLENGES OF TECHNOLOGY SCALING IS PROCESS TECHNOLOGY MEETING THE GOALS PREDICTED BY SCALING THEORY? AN ANALYSIS OF MICROPROCESSOR PERFORMANCE, TRANSISTOR DENSITY, AND POWER TRENDS THROUGH SUCCESSIVE
DESIGN CHALLENGES OF TECHNOLOGY SCALING IS PROCESS TECHNOLOGY MEETING THE GOALS PREDICTED BY SCALING THEORY? AN ANALYSIS OF MICROPROCESSOR PERFORMANCE, TRANSISTOR DENSITY, AND POWER TRENDS THROUGH SUCCESSIVE
End to End Data Path Protection
 End to End Data Path Protection Application Note AN004 February 2012 Corporate Headquarters: 39870 Eureka Dr., Newark, CA 94560, USA Tel:(510) 623 1231 Fax:(510) 623 1434 E mail: [email protected]
End to End Data Path Protection Application Note AN004 February 2012 Corporate Headquarters: 39870 Eureka Dr., Newark, CA 94560, USA Tel:(510) 623 1231 Fax:(510) 623 1434 E mail: [email protected]
How To Improve Performance On A Single Chip Computer
 : Redundant Arrays of Inexpensive Disks this discussion is based on the paper:» A Case for Redundant Arrays of Inexpensive Disks (),» David A Patterson, Garth Gibson, and Randy H Katz,» In Proceedings
: Redundant Arrays of Inexpensive Disks this discussion is based on the paper:» A Case for Redundant Arrays of Inexpensive Disks (),» David A Patterson, Garth Gibson, and Randy H Katz,» In Proceedings
Dependable Systems. 9. Redundant arrays of. Prof. Dr. Miroslaw Malek. Wintersemester 2004/05 www.informatik.hu-berlin.de/rok/zs
 Dependable Systems 9. Redundant arrays of inexpensive disks (RAID) Prof. Dr. Miroslaw Malek Wintersemester 2004/05 www.informatik.hu-berlin.de/rok/zs Redundant Arrays of Inexpensive Disks (RAID) RAID is
Dependable Systems 9. Redundant arrays of inexpensive disks (RAID) Prof. Dr. Miroslaw Malek Wintersemester 2004/05 www.informatik.hu-berlin.de/rok/zs Redundant Arrays of Inexpensive Disks (RAID) RAID is
Radiation effects on space electronics. Jan Kenneth Bekkeng, University of Oslo - Department of Physics
 Radiation effects on space electronics Jan Kenneth Bekkeng, University of Oslo - Department of Physics Background The presence of radiation in space causes effects in electronic devices. The effects range
Radiation effects on space electronics Jan Kenneth Bekkeng, University of Oslo - Department of Physics Background The presence of radiation in space causes effects in electronic devices. The effects range
SRAM Scaling Limit: Its Circuit & Architecture Solutions
 SRAM Scaling Limit: Its Circuit & Architecture Solutions Nam Sung Kim, Ph.D. Assistant Professor Department of Electrical and Computer Engineering University of Wisconsin - Madison SRAM VCC min Challenges
SRAM Scaling Limit: Its Circuit & Architecture Solutions Nam Sung Kim, Ph.D. Assistant Professor Department of Electrical and Computer Engineering University of Wisconsin - Madison SRAM VCC min Challenges
RAID Overview: Identifying What RAID Levels Best Meet Customer Needs. Diamond Series RAID Storage Array
 ATTO Technology, Inc. Corporate Headquarters 155 Crosspoint Parkway Amherst, NY 14068 Phone: 716-691-1999 Fax: 716-691-9353 www.attotech.com [email protected] RAID Overview: Identifying What RAID Levels
ATTO Technology, Inc. Corporate Headquarters 155 Crosspoint Parkway Amherst, NY 14068 Phone: 716-691-1999 Fax: 716-691-9353 www.attotech.com [email protected] RAID Overview: Identifying What RAID Levels
Solving Data Loss in Massive Storage Systems Jason Resch Cleversafe
 Solving Data Loss in Massive Storage Systems Jason Resch Cleversafe 2010 Storage Developer Conference. Insert Your Company Name. All Rights Reserved. 1 In the beginning There was replication Long before
Solving Data Loss in Massive Storage Systems Jason Resch Cleversafe 2010 Storage Developer Conference. Insert Your Company Name. All Rights Reserved. 1 In the beginning There was replication Long before
Dell Reliable Memory Technology
 Dell Reliable Memory Technology Detecting and isolating memory errors THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES. THE CONTENT IS
Dell Reliable Memory Technology Detecting and isolating memory errors THIS WHITE PAPER IS FOR INFORMATIONAL PURPOSES ONLY, AND MAY CONTAIN TYPOGRAPHICAL ERRORS AND TECHNICAL INACCURACIES. THE CONTENT IS
Embedded Real-Time Systems (TI-IRTS) Safety and Reliability Patterns B.D. Chapter 9. 405-456
 Embedded Real-Time Systems (TI-IRTS) Safety and Reliability Patterns B.D. Chapter 9. 405-456 Version: 10-5-2010 Agenda Introduction to safety Patterns: 1. Protected Single Channel Pattern 2. Homogeneous
Embedded Real-Time Systems (TI-IRTS) Safety and Reliability Patterns B.D. Chapter 9. 405-456 Version: 10-5-2010 Agenda Introduction to safety Patterns: 1. Protected Single Channel Pattern 2. Homogeneous
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING
 FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
FAULT TOLERANCE FOR MULTIPROCESSOR SYSTEMS VIA TIME REDUNDANT TASK SCHEDULING Hussain Al-Asaad and Alireza Sarvi Department of Electrical & Computer Engineering University of California Davis, CA, U.S.A.
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems
 Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC [email protected] 2. NASA/GSFC [email protected]
Verification of Triple Modular Redundancy (TMR) Insertion for Reliable and Trusted Systems Melanie Berg 1, Kenneth LaBel 2 1.AS&D in support of NASA/GSFC [email protected] 2. NASA/GSFC [email protected]
Price/performance Modern Memory Hierarchy
 Lecture 21: Storage Administration Take QUIZ 15 over P&H 6.1-4, 6.8-9 before 11:59pm today Project: Cache Simulator, Due April 29, 2010 NEW OFFICE HOUR TIME: Tuesday 1-2, McKinley Last Time Exam discussion
Lecture 21: Storage Administration Take QUIZ 15 over P&H 6.1-4, 6.8-9 before 11:59pm today Project: Cache Simulator, Due April 29, 2010 NEW OFFICE HOUR TIME: Tuesday 1-2, McKinley Last Time Exam discussion
Yaffs NAND Flash Failure Mitigation
 Yaffs NAND Flash Failure Mitigation Charles Manning 2012-03-07 NAND flash is one of very few types of electronic device which are knowingly shipped with errors and are expected to generate further errors
Yaffs NAND Flash Failure Mitigation Charles Manning 2012-03-07 NAND flash is one of very few types of electronic device which are knowingly shipped with errors and are expected to generate further errors
CS 61C: Great Ideas in Computer Architecture. Dependability: Parity, RAID, ECC
 CS 61C: Great Ideas in Computer Architecture Dependability: Parity, RAID, ECC Instructor: Justin Hsia 8/08/2013 Summer 2013 Lecture #27 1 Review of Last Lecture MapReduce Data Level Parallelism Framework
CS 61C: Great Ideas in Computer Architecture Dependability: Parity, RAID, ECC Instructor: Justin Hsia 8/08/2013 Summer 2013 Lecture #27 1 Review of Last Lecture MapReduce Data Level Parallelism Framework
Silent data corruption in SATA arrays: A solution
 Silent data corruption in SATA arrays: A solution Josh Eddy August 2008 Abstract Recent large academic studies have identified the surprising frequency of silent read failures that are not identified or
Silent data corruption in SATA arrays: A solution Josh Eddy August 2008 Abstract Recent large academic studies have identified the surprising frequency of silent read failures that are not identified or
CHASE Survey on 6 Most Important Topics in Hardware Security
 University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
University of Connecticut CHASE Survey on 6 Most Important Topics in Hardware Security Prepared By Prof. M. Tehranipoor Charles H. Knapp Associate Professor in Engineering Innovation Topics! Counterfeit
Hardware-Aware Analysis and. Presentation Date: Sep 15 th 2009 Chrissie C. Cui
 Hardware-Aware Analysis and Optimization of Stable Fluids Presentation Date: Sep 15 th 2009 Chrissie C. Cui Outline Introduction Highlights Flop and Bandwidth Analysis Mehrstellen Schemes Advection Caching
Hardware-Aware Analysis and Optimization of Stable Fluids Presentation Date: Sep 15 th 2009 Chrissie C. Cui Outline Introduction Highlights Flop and Bandwidth Analysis Mehrstellen Schemes Advection Caching
Improving Grid Processing Efficiency through Compute-Data Confluence
 Solution Brief GemFire* Symphony* Intel Xeon processor Improving Grid Processing Efficiency through Compute-Data Confluence A benchmark report featuring GemStone Systems, Intel Corporation and Platform
Solution Brief GemFire* Symphony* Intel Xeon processor Improving Grid Processing Efficiency through Compute-Data Confluence A benchmark report featuring GemStone Systems, Intel Corporation and Platform
Spacecraft Computer Systems. Colonel John E. Keesee
 Spacecraft Computer Systems Colonel John E. Keesee Overview Spacecraft data processing requires microcomputers and interfaces that are functionally similar to desktop systems However, space systems require:
Spacecraft Computer Systems Colonel John E. Keesee Overview Spacecraft data processing requires microcomputers and interfaces that are functionally similar to desktop systems However, space systems require:
Embedded Systems Lecture 9: Reliability & Fault Tolerance. Björn Franke University of Edinburgh
 Embedded Systems Lecture 9: Reliability & Fault Tolerance Björn Franke University of Edinburgh Overview Definitions System Reliability Fault Tolerance Sources and Detection of Errors Stage Error Sources
Embedded Systems Lecture 9: Reliability & Fault Tolerance Björn Franke University of Edinburgh Overview Definitions System Reliability Fault Tolerance Sources and Detection of Errors Stage Error Sources
Enhancing IBM Netfinity Server Reliability
 IBM Chipkill Memory Advanced ECC Memory for the IBM Netfinity 7000 M10 IBM Chipkill Memory (Chipkill), part of the IBM Netfinity X-architecture initiative, will be available during the first quarter of
IBM Chipkill Memory Advanced ECC Memory for the IBM Netfinity 7000 M10 IBM Chipkill Memory (Chipkill), part of the IBM Netfinity X-architecture initiative, will be available during the first quarter of
GameTime: A Toolkit for Timing Analysis of Software
 GameTime: A Toolkit for Timing Analysis of Software Sanjit A. Seshia and Jonathan Kotker EECS Department, UC Berkeley {sseshia,jamhoot}@eecs.berkeley.edu Abstract. Timing analysis is a key step in the
GameTime: A Toolkit for Timing Analysis of Software Sanjit A. Seshia and Jonathan Kotker EECS Department, UC Berkeley {sseshia,jamhoot}@eecs.berkeley.edu Abstract. Timing analysis is a key step in the
CS 6290 I/O and Storage. Milos Prvulovic
 CS 6290 I/O and Storage Milos Prvulovic Storage Systems I/O performance (bandwidth, latency) Bandwidth improving, but not as fast as CPU Latency improving very slowly Consequently, by Amdahl s Law: fraction
CS 6290 I/O and Storage Milos Prvulovic Storage Systems I/O performance (bandwidth, latency) Bandwidth improving, but not as fast as CPU Latency improving very slowly Consequently, by Amdahl s Law: fraction
General Parallel File System (GPFS) Native RAID For 100,000-Disk Petascale Systems
 General Parallel File System (GPFS) Native RAID For 100,000-Disk Petascale Systems Veera Deenadhayalan IBM Almaden Research Center 2011 IBM Corporation Hard Disk Rates Are Lagging There have been recent
General Parallel File System (GPFS) Native RAID For 100,000-Disk Petascale Systems Veera Deenadhayalan IBM Almaden Research Center 2011 IBM Corporation Hard Disk Rates Are Lagging There have been recent
NAND Flash FAQ. Eureka Technology. apn5_87. NAND Flash FAQ
 What is NAND Flash? What is the major difference between NAND Flash and other Memory? Structural differences between NAND Flash and NOR Flash What does NAND Flash controller do? How to send command to
What is NAND Flash? What is the major difference between NAND Flash and other Memory? Structural differences between NAND Flash and NOR Flash What does NAND Flash controller do? How to send command to
Enterprise-class versus Desktopclass
 Enterprise-class versus Desktopclass Hard Drives April, 2008 Enterprise Platforms and Services Division - Marketing Revision History Date Revision Number April, 2008 1.0 Initial Release Modifications Disclaimers
Enterprise-class versus Desktopclass Hard Drives April, 2008 Enterprise Platforms and Services Division - Marketing Revision History Date Revision Number April, 2008 1.0 Initial Release Modifications Disclaimers
Value Paper Author: Edgar C. Ramirez. Diverse redundancy used in SIS technology to achieve higher safety integrity
 Value Paper Author: Edgar C. Ramirez Diverse redundancy used in SIS technology to achieve higher safety integrity Diverse redundancy used in SIS technology to achieve higher safety integrity Abstract SIS
Value Paper Author: Edgar C. Ramirez Diverse redundancy used in SIS technology to achieve higher safety integrity Diverse redundancy used in SIS technology to achieve higher safety integrity Abstract SIS
Fault Tolerance & Reliability CDA 5140. Chapter 3 RAID & Sample Commercial FT Systems
 Fault Tolerance & Reliability CDA 5140 Chapter 3 RAID & Sample Commercial FT Systems - basic concept in these, as with codes, is redundancy to allow system to continue operation even if some components
Fault Tolerance & Reliability CDA 5140 Chapter 3 RAID & Sample Commercial FT Systems - basic concept in these, as with codes, is redundancy to allow system to continue operation even if some components
In-Block Level Redundancy Management for Flash Storage System
 , pp.309-318 http://dx.doi.org/10.14257/ijmue.2015.10.9.32 In-Block Level Redundancy Management for Flash Storage System Seung-Ho Lim Division of Computer and Electronic Systems Engineering Hankuk University
, pp.309-318 http://dx.doi.org/10.14257/ijmue.2015.10.9.32 In-Block Level Redundancy Management for Flash Storage System Seung-Ho Lim Division of Computer and Electronic Systems Engineering Hankuk University
Why disk arrays? CPUs speeds increase faster than disks. - Time won t really help workloads where disk in bottleneck
 1/19 Why disk arrays? CPUs speeds increase faster than disks - Time won t really help workloads where disk in bottleneck Some applications (audio/video) require big files Disk arrays - make one logical
1/19 Why disk arrays? CPUs speeds increase faster than disks - Time won t really help workloads where disk in bottleneck Some applications (audio/video) require big files Disk arrays - make one logical
High availability for parallel computers
 High availability for parallel computers Dolores Rexachs and Emilio Luque Computer Architecture an Operating System Department, Universidad Autónoma de Barcelona, Barcelona 8193, Spain ABSTRACT Fault tolerance
High availability for parallel computers Dolores Rexachs and Emilio Luque Computer Architecture an Operating System Department, Universidad Autónoma de Barcelona, Barcelona 8193, Spain ABSTRACT Fault tolerance
Computer Systems Structure Main Memory Organization
 Computer Systems Structure Main Memory Organization Peripherals Computer Central Processing Unit Main Memory Computer Systems Interconnection Communication lines Input Output Ward 1 Ward 2 Storage/Memory
Computer Systems Structure Main Memory Organization Peripherals Computer Central Processing Unit Main Memory Computer Systems Interconnection Communication lines Input Output Ward 1 Ward 2 Storage/Memory
Flash Memory. For Automotive Applications. White Paper F-WP001
 Flash Memory For Automotive Applications White Paper F-WP001 Corporate Headquarters: 39870 Eureka Dr., Newark, CA 94560, USA Tel: (510) 623-1231 Fax: (510) 623-1434 E-mail: [email protected] Customer Service:
Flash Memory For Automotive Applications White Paper F-WP001 Corporate Headquarters: 39870 Eureka Dr., Newark, CA 94560, USA Tel: (510) 623-1231 Fax: (510) 623-1434 E-mail: [email protected] Customer Service:
Dynamic resource management for energy saving in the cloud computing environment
 Dynamic resource management for energy saving in the cloud computing environment Liang-Teh Lee, Kang-Yuan Liu, and Hui-Yang Huang Department of Computer Science and Engineering, Tatung University, Taiwan
Dynamic resource management for energy saving in the cloud computing environment Liang-Teh Lee, Kang-Yuan Liu, and Hui-Yang Huang Department of Computer Science and Engineering, Tatung University, Taiwan
Improved NAND Flash Memories Storage Reliablity Using Nonlinear Multi Error Correction Codes
 Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 9 (2013), pp. 1121-1134 Research India Publications http://www.ripublication.com/aeee.htm Improved NAND Flash Memories Storage
Advance in Electronic and Electric Engineering. ISSN 2231-1297, Volume 3, Number 9 (2013), pp. 1121-1134 Research India Publications http://www.ripublication.com/aeee.htm Improved NAND Flash Memories Storage
MultiPARTES. Virtualization on Heterogeneous Multicore Platforms. 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM
 MultiPARTES Virtualization on Heterogeneous Multicore Platforms 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM Contents Analysis of scheduling approaches Virtualization of devices Dealing with heterogeneous
MultiPARTES Virtualization on Heterogeneous Multicore Platforms 2012/7/18 Slides by TU Wien, UPV, fentiss, UPM Contents Analysis of scheduling approaches Virtualization of devices Dealing with heterogeneous
Energy aware RAID Configuration for Large Storage Systems
 Energy aware RAID Configuration for Large Storage Systems Norifumi Nishikawa [email protected] Miyuki Nakano [email protected] Masaru Kitsuregawa [email protected] Abstract
Energy aware RAID Configuration for Large Storage Systems Norifumi Nishikawa [email protected] Miyuki Nakano [email protected] Masaru Kitsuregawa [email protected] Abstract
Index Terms Cloud Storage Services, data integrity, dependable distributed storage, data dynamics, Cloud Computing.
 Volume 3, Issue 5, May 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Privacy - Preserving
Volume 3, Issue 5, May 2013 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Privacy - Preserving
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines
 Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada [email protected] Micaela Serra
Reconfigurable Architecture Requirements for Co-Designed Virtual Machines Kenneth B. Kent University of New Brunswick Faculty of Computer Science Fredericton, New Brunswick, Canada [email protected] Micaela Serra
EE552. Advanced Logic Design and Switching Theory. Metastability. Ashirwad Bahukhandi. (Ashirwad Bahukhandi) [email protected]
 EE552 Advanced Logic Design and Switching Theory Metastability by Ashirwad Bahukhandi (Ashirwad Bahukhandi) [email protected] This is an overview of what metastability is, ways of interpreting it, the issues
EE552 Advanced Logic Design and Switching Theory Metastability by Ashirwad Bahukhandi (Ashirwad Bahukhandi) [email protected] This is an overview of what metastability is, ways of interpreting it, the issues
TRUE SINGLE PHASE CLOCKING BASED FLIP-FLOP DESIGN
 TRUE SINGLE PHASE CLOCKING BASED FLIP-FLOP DESIGN USING DIFFERENT FOUNDRIES Priyanka Sharma 1 and Rajesh Mehra 2 1 ME student, Department of E.C.E, NITTTR, Chandigarh, India 2 Associate Professor, Department
TRUE SINGLE PHASE CLOCKING BASED FLIP-FLOP DESIGN USING DIFFERENT FOUNDRIES Priyanka Sharma 1 and Rajesh Mehra 2 1 ME student, Department of E.C.E, NITTTR, Chandigarh, India 2 Associate Professor, Department
RAID Technology Overview
 RAID Technology Overview HP Smart Array RAID Controllers HP Part Number: J6369-90050 Published: September 2007 Edition: 1 Copyright 2007 Hewlett-Packard Development Company L.P. Legal Notices Copyright
RAID Technology Overview HP Smart Array RAID Controllers HP Part Number: J6369-90050 Published: September 2007 Edition: 1 Copyright 2007 Hewlett-Packard Development Company L.P. Legal Notices Copyright
RAID Technology. RAID Overview
 Technology In the 1980s, hard-disk drive capacities were limited and large drives commanded a premium price. As an alternative to costly, high-capacity individual drives, storage system developers began
Technology In the 1980s, hard-disk drive capacities were limited and large drives commanded a premium price. As an alternative to costly, high-capacity individual drives, storage system developers began
IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits
 IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits SUMMARY CONTENTS 1. CONTEXT 2. TECHNOLOGY TRENDS 3. MOTIVATION 4. WHAT IS IC-EMC 5. SUPPORTED STANDARD 6. EXAMPLES CONTEXT - WHY
IC-EMC Simulation of Electromagnetic Compatibility of Integrated Circuits SUMMARY CONTENTS 1. CONTEXT 2. TECHNOLOGY TRENDS 3. MOTIVATION 4. WHAT IS IC-EMC 5. SUPPORTED STANDARD 6. EXAMPLES CONTEXT - WHY
Enery Efficient Dynamic Memory Bank and NV Swap Device Management
 Enery Efficient Dynamic Memory Bank and NV Swap Device Management Kwangyoon Lee and Bumyong Choi Department of Computer Science and Engineering University of California, San Diego {kwl002,buchoi}@cs.ucsd.edu
Enery Efficient Dynamic Memory Bank and NV Swap Device Management Kwangyoon Lee and Bumyong Choi Department of Computer Science and Engineering University of California, San Diego {kwl002,buchoi}@cs.ucsd.edu
The Reduced Address Space (RAS) for Application Memory Authentication
 The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
The Reduced Address Space (RAS) for Application Memory Authentication David Champagne, Reouven Elbaz and Ruby B. Lee Princeton University, USA Introduction Background: TPM, XOM, AEGIS, SP, SecureBlue want
SOFTWARE PERFORMANCE EVALUATION ALGORITHM EXPERIMENT FOR IN-HOUSE SOFTWARE USING INTER-FAILURE DATA
 I.J.E.M.S., VOL.3(2) 2012: 99-104 ISSN 2229-6425 SOFTWARE PERFORMANCE EVALUATION ALGORITHM EXPERIMENT FOR IN-HOUSE SOFTWARE USING INTER-FAILURE DATA *Jimoh, R. G. & Abikoye, O. C. Computer Science Department,
I.J.E.M.S., VOL.3(2) 2012: 99-104 ISSN 2229-6425 SOFTWARE PERFORMANCE EVALUATION ALGORITHM EXPERIMENT FOR IN-HOUSE SOFTWARE USING INTER-FAILURE DATA *Jimoh, R. G. & Abikoye, O. C. Computer Science Department,
2-1-5 Space Radiation Effect on Satellites
 2-1-5 Space Radiation Effect on Satellites Solar activity and space environment is considered as fundamental and important factors for space system design and operation. Space and solar radiation is widely
2-1-5 Space Radiation Effect on Satellites Solar activity and space environment is considered as fundamental and important factors for space system design and operation. Space and solar radiation is widely
ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT
 216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
216 ON SUITABILITY OF FPGA BASED EVOLVABLE HARDWARE SYSTEMS TO INTEGRATE RECONFIGURABLE CIRCUITS WITH HOST PROCESSING UNIT *P.Nirmalkumar, **J.Raja Paul Perinbam, @S.Ravi and #B.Rajan *Research Scholar,
PIONEER RESEARCH & DEVELOPMENT GROUP
 SURVEY ON RAID Aishwarya Airen 1, Aarsh Pandit 2, Anshul Sogani 3 1,2,3 A.I.T.R, Indore. Abstract RAID stands for Redundant Array of Independent Disk that is a concept which provides an efficient way for
SURVEY ON RAID Aishwarya Airen 1, Aarsh Pandit 2, Anshul Sogani 3 1,2,3 A.I.T.R, Indore. Abstract RAID stands for Redundant Array of Independent Disk that is a concept which provides an efficient way for
A Hierarchical Approach for Dependability Analysis of a Commercial Cache-Based RAID Storage Architecture
 28 th IEEE International Symposium on Fault-Tolerant Computing (FTCS-28), Munich (Allemagne), IEEE Computer Society, Juin 1998, pp.6-15 A Hierarchical Approach for Dependability Analysis of a Commercial
28 th IEEE International Symposium on Fault-Tolerant Computing (FTCS-28), Munich (Allemagne), IEEE Computer Society, Juin 1998, pp.6-15 A Hierarchical Approach for Dependability Analysis of a Commercial
Proactive, Resource-Aware, Tunable Real-time Fault-tolerant Middleware
 Proactive, Resource-Aware, Tunable Real-time Fault-tolerant Middleware Priya Narasimhan T. Dumitraş, A. Paulos, S. Pertet, C. Reverte, J. Slember, D. Srivastava Carnegie Mellon University Problem Description
Proactive, Resource-Aware, Tunable Real-time Fault-tolerant Middleware Priya Narasimhan T. Dumitraş, A. Paulos, S. Pertet, C. Reverte, J. Slember, D. Srivastava Carnegie Mellon University Problem Description
Don t Let RAID Raid the Lifetime of Your SSD Array
 Don t Let RAID Raid the Lifetime of Your SSD Array Sangwhan Moon Texas A&M University A. L. Narasimha Reddy Texas A&M University Abstract Parity protection at system level is typically employed to compose
Don t Let RAID Raid the Lifetime of Your SSD Array Sangwhan Moon Texas A&M University A. L. Narasimha Reddy Texas A&M University Abstract Parity protection at system level is typically employed to compose
Chapter 2 Features of Embedded System
 Chapter 2 Features of Embedded System Abstract This chapter will introduce the basic elements of embedded systems (or dedicated systems). The integrated control systems represent one of the areas of modern
Chapter 2 Features of Embedded System Abstract This chapter will introduce the basic elements of embedded systems (or dedicated systems). The integrated control systems represent one of the areas of modern
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM
 ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM 1 The ARM architecture processors popular in Mobile phone systems 2 ARM Features ARM has 32-bit architecture but supports 16 bit
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-12: ARM 1 The ARM architecture processors popular in Mobile phone systems 2 ARM Features ARM has 32-bit architecture but supports 16 bit
HP Smart Array Controllers and basic RAID performance factors
 Technical white paper HP Smart Array Controllers and basic RAID performance factors Technology brief Table of contents Abstract 2 Benefits of drive arrays 2 Factors that affect performance 2 HP Smart Array
Technical white paper HP Smart Array Controllers and basic RAID performance factors Technology brief Table of contents Abstract 2 Benefits of drive arrays 2 Factors that affect performance 2 HP Smart Array
Implementation Details
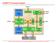 LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
LEON3-FT Processor System Scan-I/F FT FT Add-on Add-on 2 2 kbyte kbyte I- I- Cache Cache Scan Scan Test Test UART UART 0 0 UART UART 1 1 Serial 0 Serial 1 EJTAG LEON_3FT LEON_3FT Core Core 8 Reg. Windows
SOLUTION BRIEF. Advanced ODBC and JDBC Access to Salesforce Data. www.datadirect.com
 SOLUTION BRIEF Advanced ODBC and JDBC Access to Salesforce Data 2 CLOUD DATA ACCESS In the terrestrial world of enterprise computing, organizations depend on advanced JDBC and ODBC technologies to provide
SOLUTION BRIEF Advanced ODBC and JDBC Access to Salesforce Data 2 CLOUD DATA ACCESS In the terrestrial world of enterprise computing, organizations depend on advanced JDBC and ODBC technologies to provide
Why disk arrays? CPUs improving faster than disks
 Why disk arrays? CPUs improving faster than disks - disks will increasingly be bottleneck New applications (audio/video) require big files (motivation for XFS) Disk arrays - make one logical disk out of
Why disk arrays? CPUs improving faster than disks - disks will increasingly be bottleneck New applications (audio/video) require big files (motivation for XFS) Disk arrays - make one logical disk out of
Nanocomputer & Architecture
 Nanocomputer & Architecture Yingjie Wei Western Michigan University Department of Computer Science CS 603 - Dr. Elise dedonckor Febrary 4 th, 2004 Nanocomputer Architecture Contents Overview of Nanotechnology
Nanocomputer & Architecture Yingjie Wei Western Michigan University Department of Computer Science CS 603 - Dr. Elise dedonckor Febrary 4 th, 2004 Nanocomputer Architecture Contents Overview of Nanotechnology
An Open Architecture through Nanocomputing
 2009 International Symposium on Computing, Communication, and Control (ISCCC 2009) Proc.of CSIT vol.1 (2011) (2011) IACSIT Press, Singapore An Open Architecture through Nanocomputing Joby Joseph1and A.
2009 International Symposium on Computing, Communication, and Control (ISCCC 2009) Proc.of CSIT vol.1 (2011) (2011) IACSIT Press, Singapore An Open Architecture through Nanocomputing Joby Joseph1and A.
Physical Security: Status and Outlook
 Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
Physical Security: Status and Outlook ECRYPT II: Crypto for 2020 January 22-24, Tenerife, Spain Stefan Tillich Ideal World P C 2 Real World P C, C,errC 3 Implementation Attacks First publication ~ 16 years
1 Storage Devices Summary
 Chapter 1 Storage Devices Summary Dependability is vital Suitable measures Latency how long to the first bit arrives Bandwidth/throughput how fast does stuff come through after the latency period Obvious
Chapter 1 Storage Devices Summary Dependability is vital Suitable measures Latency how long to the first bit arrives Bandwidth/throughput how fast does stuff come through after the latency period Obvious
Certification Authorities Software Team (CAST) Position Paper CAST-13
 Certification Authorities Software Team (CAST) Position Paper CAST-13 Automatic Code Generation Tools Development Assurance Completed June 2002 NOTE: This position paper has been coordinated among the
Certification Authorities Software Team (CAST) Position Paper CAST-13 Automatic Code Generation Tools Development Assurance Completed June 2002 NOTE: This position paper has been coordinated among the
Programming NAND devices
 Technical Guide Programming NAND devices Kelly Hirsch, Director of Advanced Technology, Data I/O Corporation Recent Design Trends In the past, embedded system designs have used NAND devices for storing
Technical Guide Programming NAND devices Kelly Hirsch, Director of Advanced Technology, Data I/O Corporation Recent Design Trends In the past, embedded system designs have used NAND devices for storing
Security Considerations for the Spiral Development Model
 Security Considerations for the Spiral Development Model Loye Lynn Ray University of Maryland University College 3501 University Blvd East Adelphi, MD 20783 [email protected] 717-718-5727 Abstract
Security Considerations for the Spiral Development Model Loye Lynn Ray University of Maryland University College 3501 University Blvd East Adelphi, MD 20783 [email protected] 717-718-5727 Abstract
On Demand Loading of Code in MMUless Embedded System
 On Demand Loading of Code in MMUless Embedded System Sunil R Gandhi *. Chetan D Pachange, Jr.** Mandar R Vaidya***, Swapnilkumar S Khorate**** *Pune Institute of Computer Technology, Pune INDIA (Mob- 8600867094;
On Demand Loading of Code in MMUless Embedded System Sunil R Gandhi *. Chetan D Pachange, Jr.** Mandar R Vaidya***, Swapnilkumar S Khorate**** *Pune Institute of Computer Technology, Pune INDIA (Mob- 8600867094;
3D On-chip Data Center Networks Using Circuit Switches and Packet Switches
 3D On-chip Data Center Networks Using Circuit Switches and Packet Switches Takahide Ikeda Yuichi Ohsita, and Masayuki Murata Graduate School of Information Science and Technology, Osaka University Osaka,
3D On-chip Data Center Networks Using Circuit Switches and Packet Switches Takahide Ikeda Yuichi Ohsita, and Masayuki Murata Graduate School of Information Science and Technology, Osaka University Osaka,
Energy Monitoring and Management Technology based on IEEE 802.15. 4g Smart Utility Networks and Mobile Devices
 Monitoring and Management Technology based on IEEE 802.15. 4g Smart Utility Networks and Mobile Devices Hyunjeong Lee, Wan-Ki Park, Il-Woo Lee IT Research Section IT Convergence Technology Research Laboratory,
Monitoring and Management Technology based on IEEE 802.15. 4g Smart Utility Networks and Mobile Devices Hyunjeong Lee, Wan-Ki Park, Il-Woo Lee IT Research Section IT Convergence Technology Research Laboratory,
PowerPC Microprocessor Clock Modes
 nc. Freescale Semiconductor AN1269 (Freescale Order Number) 1/96 Application Note PowerPC Microprocessor Clock Modes The PowerPC microprocessors offer customers numerous clocking options. An internal phase-lock
nc. Freescale Semiconductor AN1269 (Freescale Order Number) 1/96 Application Note PowerPC Microprocessor Clock Modes The PowerPC microprocessors offer customers numerous clocking options. An internal phase-lock
what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored?
 Inside the CPU how does the CPU work? what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored? some short, boring programs to illustrate the
Inside the CPU how does the CPU work? what operations can it perform? how does it perform them? on what kind of data? where are instructions and data stored? some short, boring programs to illustrate the
A Study of Network Security Systems
 A Study of Network Security Systems Ramy K. Khalil, Fayez W. Zaki, Mohamed M. Ashour, Mohamed A. Mohamed Department of Communication and Electronics Mansoura University El Gomhorya Street, Mansora,Dakahlya
A Study of Network Security Systems Ramy K. Khalil, Fayez W. Zaki, Mohamed M. Ashour, Mohamed A. Mohamed Department of Communication and Electronics Mansoura University El Gomhorya Street, Mansora,Dakahlya
Efficient Interconnect Design with Novel Repeater Insertion for Low Power Applications
 Efficient Interconnect Design with Novel Repeater Insertion for Low Power Applications TRIPTI SHARMA, K. G. SHARMA, B. P. SINGH, NEHA ARORA Electronics & Communication Department MITS Deemed University,
Efficient Interconnect Design with Novel Repeater Insertion for Low Power Applications TRIPTI SHARMA, K. G. SHARMA, B. P. SINGH, NEHA ARORA Electronics & Communication Department MITS Deemed University,
On the Use of Strong BCH Codes for Improving Multilevel NAND Flash Memory Storage Capacity
 On the Use of Strong BCH Codes for Improving Multilevel NAND Flash Memory Storage Capacity Fei Sun, Ken Rose, and Tong Zhang ECSE Department, Rensselaer Polytechnic Institute, USA Abstract This paper investigates
On the Use of Strong BCH Codes for Improving Multilevel NAND Flash Memory Storage Capacity Fei Sun, Ken Rose, and Tong Zhang ECSE Department, Rensselaer Polytechnic Institute, USA Abstract This paper investigates
Load Balancing in Distributed Data Base and Distributed Computing System
 Load Balancing in Distributed Data Base and Distributed Computing System Lovely Arya Research Scholar Dravidian University KUPPAM, ANDHRA PRADESH Abstract With a distributed system, data can be located
Load Balancing in Distributed Data Base and Distributed Computing System Lovely Arya Research Scholar Dravidian University KUPPAM, ANDHRA PRADESH Abstract With a distributed system, data can be located
Securing the Internet of Things WHITEPAPER
 Securing the Internet of Things WHITEPAPER Table of Contents Introduction...1 Expectations of Security Risk...1 Complexity... 2 What is Secure Enough?... 2 Authenticated Sender & Receiver... 3 Accessible
Securing the Internet of Things WHITEPAPER Table of Contents Introduction...1 Expectations of Security Risk...1 Complexity... 2 What is Secure Enough?... 2 Authenticated Sender & Receiver... 3 Accessible
Pipelining Review and Its Limitations
 Pipelining Review and Its Limitations Yuri Baida [email protected] [email protected] October 16, 2010 Moscow Institute of Physics and Technology Agenda Review Instruction set architecture Basic
Pipelining Review and Its Limitations Yuri Baida [email protected] [email protected] October 16, 2010 Moscow Institute of Physics and Technology Agenda Review Instruction set architecture Basic
RAID-DP: NetApp Implementation of Double- Parity RAID for Data Protection
 Technical Report RAID-DP: NetApp Implementation of Double- Parity RAID for Data Protection Jay White & Chris Lueth, NetApp May 2010 TR-3298 ABSTRACT This document provides an in-depth overview of the NetApp
Technical Report RAID-DP: NetApp Implementation of Double- Parity RAID for Data Protection Jay White & Chris Lueth, NetApp May 2010 TR-3298 ABSTRACT This document provides an in-depth overview of the NetApp
Week 1 out-of-class notes, discussions and sample problems
 Week 1 out-of-class notes, discussions and sample problems Although we will primarily concentrate on RISC processors as found in some desktop/laptop computers, here we take a look at the varying types
Week 1 out-of-class notes, discussions and sample problems Although we will primarily concentrate on RISC processors as found in some desktop/laptop computers, here we take a look at the varying types
Automated Software Testing of Memory Performance in Embedded GPUs. Sudipta Chattopadhyay, Petru Eles and Zebo Peng! Linköping University
 Automated Software Testing of Memory Performance in Embedded GPUs Sudipta Chattopadhyay, Petru Eles and Zebo Peng! Linköping University 1 State-of-the-art in Detecting Performance Loss Input Program profiling
Automated Software Testing of Memory Performance in Embedded GPUs Sudipta Chattopadhyay, Petru Eles and Zebo Peng! Linköping University 1 State-of-the-art in Detecting Performance Loss Input Program profiling
SPARC64 VIIIfx: CPU for the K computer
 SPARC64 VIIIfx: CPU for the K computer Toshio Yoshida Mikio Hondo Ryuji Kan Go Sugizaki SPARC64 VIIIfx, which was developed as a processor for the K computer, uses Fujitsu Semiconductor Ltd. s 45-nm CMOS
SPARC64 VIIIfx: CPU for the K computer Toshio Yoshida Mikio Hondo Ryuji Kan Go Sugizaki SPARC64 VIIIfx, which was developed as a processor for the K computer, uses Fujitsu Semiconductor Ltd. s 45-nm CMOS
