DOD INTERIM CREDENTIAL IMPLEMENTATION INSTRUCTIONS BlackBerry Devices
|
|
|
- Rosalind Virginia Flowers
- 9 years ago
- Views:
Transcription
1
2 DOD INTERIM CREDENTIAL IMPLEMENTATION INSTRUCTIONS BlackBerry Devices A. INTRODUCTION 1. The objective of this document is to provide an outline of the technical and administrative process necessary to establish and use derived PKI credentials on a BlackBerry smartphone. 2. The process outlined in the following steps will generate a key pair and an associated signing certificate and recover the user's private encryption certificate and associated private key (used to decrypt s). Additionally, these steps will provide instructions for loading the certificates and private keys onto a BlackBerry. 3. These instructions are written and intended to be used only by DoD information technology (IT) personnel in direct support of the DoD service/agency they are supporting. 4. These instructions are only applicable to the BlackBerry smartphone operating system versions 7.X.X and newer and 10.2.X and newer. B. TECHNICAL APPROACH 1. A DoD IT Professional will perform these steps with the user present. 2. The DoD IT professional will use a properly configured workstation with two CAC readers in the support area to perform this operation. Encryption credential 1. To recover the encryption credential, use Microsoft Internet Explorer 10 or newer and navigate to one of the following sites: a. Or b Authenticate to the site using the user s identity certificate (certificate without in the display name). The user will enter their PIN. Make sure you chose the user s certificate and not your own or you may lock out the CAC. 3. Identify the user s current encryption certificate and choose Recover. The site will display a link to download the certificate and display the password to be used when importing the certificate. Create a folder on the local drive to temporarily store the certificate (e.g. c:\pki). Click the download link and save the certificate in the 1
3 designated location for certificates on the local hard drive. The location shall not be a network or shared drive. 4. Document the password displayed in the above step. Do not save the password electronically on the same system as the certificates. Signature Certificate 5. To generate the derived signature certificate, use Mozilla Firefox version 32.0 configured in accordance with the Security Technical Implementation Guide (STIG). Note: newer versions do not work at this time. 6. Firefox has to be configured with a software security device to perform this operation. Follow the steps under, Using Common Access Card (CAC) certificates in Firefox at this site: 7. Once you verify Firefox is configured appropriately, navigate to the following site: or 27.csd.disa.mil/ca/ auth.html. 8. Set the certificate key length to 2048 and choose: Signature Certificate only from the dropdown. 9. Type the user s address that matches their address on their CAC (enter twice). (NOTE: Verify their address on their CAC before proceeding. If the address is incorrect, it must be fixed prior to proceeding. For more details: uction.htm). When you select Get Certificate, you will be prompted to choose a token. If Firefox is configured correctly, the dialog box will show FIPS Module. Choose OK. When prompted for a PIN, make sure the user enters their PIN. Be careful to choose the correct authentication certificate or you may lock one of both CACs. 10. The next dialog will ask you to choose the certificate to present to verify identification. Choose the identity certificate of the user and make sure you uncheck Remember this decision. You may receive two alerts and then a screen stating the certificate has been stored in your browser with instructions on how to recover the certificate; do not follow those instructions. NOTE: If you receive an Authentication Error message, you may not have deleted a previous certificate. To do this, navigate to options, advanced, certificates, and choose view certificates. Delete the certificate labeled software security device located in the tab labeled your certificates and try again. 11. Once this is successful and you receive the instruction page from step 10 above, navigate back to Your Certificates at the location in the NOTE from step 10, select the certificate, and choose backup. 2
4 12. You will be prompted for a location to save the certificate. Navigate to the same location you stored the certificate, type a file name and choose save. 13. You will be prompted for a password. You MUST use a 16 character complex (i.e. uppercase, lowercase, numbers, and special characters) to protect this certificate. 14. For more information on protecting certificates, review the document at the following link: Installing certificates on the BlackBerry 15. Loading certificates shall be done at the same workstation on which the certificates were stored per paragraph B.3., above. 16. For legacy BlackBerry devices, only operating system 7.x.x and newer shall be used. a. The device should already have the key store password set and synchronized with the device password. Additionally, ensure the key store is configured in accordance with the latest STIG. b. Ensure the devices key store settings on the BlackBerry Enterprise Server (BES) match the STIG required settings. The goal is to give the user the same experience as they have at their desktop with respect to the timeout period for entering their CAC PIN. c. Connect the user s device using a USB cable, and use desktop manager certificate sync to transfer the certificates to the device. NOTE: If you do not see "Certificates" as an option, go to tools, and look under the "General" tab and check the box "Use certificate synchronization. d. Certificates are not exportable once imported to the BlackBerry. 17. For BlackBerry 10 devices, operating system (OS) x and newer shall be used. a. Connect the BlackBerry to the desktop. The BlackBerry should appear as an external drive on the computer. Drag both certificates to a folder on the device (not the micro SD card). This will place the certificates on the Personal side of the device. b. On the device, navigate to Certificates located in Settings under Security and Privacy. Select the "Import" button, then "Device-Personal, and navigate to the certificates file, select it, enter the password, then select import to work perimeter. Then repeat the import for the 2 nd certificate. Be sure to enter the right password for each certificate. Once the import is completed, delete the certificate files in the file system on the personal side of the device. 3
5 c. On BlackBerry 10 OS devices, the work space timeout is what controls access to the certificates. This should be set in accordance with the latest STIG. d. Certificates are not exportable from the BlackBerry once imported. C. ADMINISTRATIVE TASKS 1. The DoD agency using these instructions shall create an addendum to the user agreement with the following language, at a minimum. a. The user understands there is additional risk in using derived PKI credentials on mobile devices. b. The user will treat the BlackBerry smartphone as if it were their Common Access Card (CAC) (e.g. report the card lost or stolen immediately). The user agreement will provide information on how to report a lost or stolen device. c. The user acknowledges they have been trained how to wipe the device in the event the device starts to operate abnormally. d. The user understands that if they lose their CAC, they also have to replace the credentials on their mobile devices. If the user loses their mobile device which contains their PKI credentials, they must also replace their CAC. 2. The DoD agency using these instructions shall keep a list of users and certificate information (e.g. types of certs, s/n s, etc.) which have PKI derived credentials on their BlackBerry smartphone. Tracking shall be done on a spreadsheet or in a ticket tracking system (e.g. Remedy) where reports can be easily created identifying who has derived PKI credentials on their BlackBerry. 3. The DoD IT personnel performing these steps shall ensure both credentials stored on the computer during the transfer process are deleted from the local storage and certificate stores on all browsers. Additionally, empty the trash or deleted files to ensure the files no longer resides on the system in any form. The paper the password(s) were written down on shall be shredded or placed in a burn bag. 4. DISA shall incorporate these procedures in the next revision of the BlackBerry STIG located here: 5. These instructions are to be used as an interim step to provide the derived PKI capability and functionality until an approved scalable enterprise solution is available. 6. The DoD CIO point of contact for the technical instructions is Will Alberts at [email protected] or
6 REFERENCES (a) NIST Special Publication , Electronic Authentication Guideline, February, 2013 (b) NSA Memorandum, Commercial Mobile Device (CMD) Public Key Infrastructure (PKI) for Unclassified National Security Systems (NSS) Way Forward-DECISION MEMORANDUM, July 31, 2014 (c) National Information Assurance Partnership Protection Profile, Protection Profile for Mobile Device Fundamentals, February 12, 2014 (d) DoD Annex for Mobile Device Fundamentals Protection Profile, Version 1, Release 1, January 29, 2014 (e) DoD CIO Memorandum, DoD Interim Guidance on the Use of DoD Personal Identity Verification Derived Public Key Infrastructure Credentials on Unclassified Commercial Mobile Devices, September 24,
Allscripts Mobile Installation Guide for BlackBerry
 CONTENTS Getting Started... 1 Step One - Download and Install Allscripts Mobile... 2 Step Two - Configure Allscripts Mobile... 4 Security... 8 Support... 10 Getting Started SUPPORTED PLATFORMS Allscripts
CONTENTS Getting Started... 1 Step One - Download and Install Allscripts Mobile... 2 Step Two - Configure Allscripts Mobile... 4 Security... 8 Support... 10 Getting Started SUPPORTED PLATFORMS Allscripts
Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file
 Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file You may use your Medium Assurance Certificate(s) on any computer that you wish to by importing them
Importing your personal certificate(s) to Microsoft Internet Explorer from a Back-up (or export) file You may use your Medium Assurance Certificate(s) on any computer that you wish to by importing them
SECURE EMAIL USER GUIDE OUTLOOK 2000
 WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
WELLS FARGO AUTHENTICATION SERVICES DATED: MAY 2003 TABLE OF CONTENTS GENERAL INFORMATION... 1 INSTALLING THE WELLS FARGO ROOT CERTIFICATE CHAIN.. 2 INSTALLING THE CERTIFICATES INTO IE... 3 SETTING UP
Outlook Web Access 2003 Remote User Guide
 UNITED STATES COAST GUARD Outlook Web Access 2003 Remote User Guide Using Common Access Card Access TISCOM TIS-42 07/29/2008 Version 1.0 CAC Enabled Outlook Web Access CAC Enabled OWA is a way to view
UNITED STATES COAST GUARD Outlook Web Access 2003 Remote User Guide Using Common Access Card Access TISCOM TIS-42 07/29/2008 Version 1.0 CAC Enabled Outlook Web Access CAC Enabled OWA is a way to view
How to Publish Your Smart Card Certificates Using Outlook 2010
 How to Publish Your Smart Card Certificates Using Outlook 2010 To send or receive (and read) digitally signed or encrypted email messages with colleagues at NIH, you must first publish your PIV certificate
How to Publish Your Smart Card Certificates Using Outlook 2010 To send or receive (and read) digitally signed or encrypted email messages with colleagues at NIH, you must first publish your PIV certificate
Procedure for How to Enroll for Digital Signature
 Procedure for How to Enroll for Digital Signature In Online Processing System getting to implement Digital Signature and Electronic Token for security and Authentication Purpose. For that bidder must have
Procedure for How to Enroll for Digital Signature In Online Processing System getting to implement Digital Signature and Electronic Token for security and Authentication Purpose. For that bidder must have
GoldKey Software. User s Manual. Revision 7.12. WideBand Corporation www.goldkey.com. Copyright 2007-2014 WideBand Corporation. All Rights Reserved.
 GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
GoldKey Software User s Manual Revision 7.12 WideBand Corporation www.goldkey.com 1 Table of Contents GoldKey Installation and Quick Start... 5 Initial Personalization... 5 Creating a Primary Secure Drive...
BlackBerry Link for Windows. Version: 1.2.3. User Guide
 BlackBerry Link for Windows Version: 1.2.3 User Guide Published: 2014-01-20 SWD-20140120093847797 Contents Related resources...5 Getting started...6 About BlackBerry Link... 6 Getting to know BlackBerry
BlackBerry Link for Windows Version: 1.2.3 User Guide Published: 2014-01-20 SWD-20140120093847797 Contents Related resources...5 Getting started...6 About BlackBerry Link... 6 Getting to know BlackBerry
Transitioning from TurningPoint 5 to TurningPoint Cloud - LMS 1
 Transitioning from TurningPoint 5 to TurningPoint Cloud - LMS 1 A Turning Account is a unique identifier that is used to tie together all software accounts and response devices. A Turning Account is required
Transitioning from TurningPoint 5 to TurningPoint Cloud - LMS 1 A Turning Account is a unique identifier that is used to tie together all software accounts and response devices. A Turning Account is required
MICROSOFT OUTLOOK 2011 SYNC ACCOUNTS AND BACKUP
 MICROSOFT OUTLOOK 2011 SYNC ACCOUNTS AND BACKUP Last Edited: 2012-07-10 1 Sync Exchange and IMAP accounts... 3 Sync basics... 3 Sync Outlook with ical and Apple Mail on Mac... 3 Set schedule to synchronize
MICROSOFT OUTLOOK 2011 SYNC ACCOUNTS AND BACKUP Last Edited: 2012-07-10 1 Sync Exchange and IMAP accounts... 3 Sync basics... 3 Sync Outlook with ical and Apple Mail on Mac... 3 Set schedule to synchronize
Get Smart Card Ready. How to Recover Your Old (Expired) Certificates
 How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
How to Recover Your Old (Expired) Certificates If you want to read signed or encrypted email messages that you sent or received using a nowexpired certificate, you first need to recover that certificate
Virtual Code Authentication User s Guide. June 25, 2015
 Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
Virtual Code Authentication User s Guide June 25, 2015 Virtual Code Authentication User s Guide Overview of New Security Modern technologies call for higher security standards as practiced among many other
GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry GO!Enterprise MDM Version 4.11.x GO!Enterprise MDM for BlackBerry 1 Table of Contents GO!Enterprise MDM for
GO!Enterprise MDM Device Application User Guide Installation and Configuration for BlackBerry GO!Enterprise MDM Version 4.11.x GO!Enterprise MDM for BlackBerry 1 Table of Contents GO!Enterprise MDM for
Digital Signatures on iqmis User Access Request Form
 Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Digital Signatures on iqmis User Access Request Form When a user clicks in the User Signature block on the iqmis Access Form, the following window appears: Click Save a Copy and rename it with your name,
Adding Outlook to a Blackberry, Downloading, Installing and Configuring Blackberry Desktop Manager
 Adding Outlook to a Blackberry, Downloading, Installing and Configuring Blackberry Desktop Manager The following instructions work for the District provided Blackberrys from Sprint, but I think it should
Adding Outlook to a Blackberry, Downloading, Installing and Configuring Blackberry Desktop Manager The following instructions work for the District provided Blackberrys from Sprint, but I think it should
Administration Guide ActivClient for Windows 6.2
 Administration Guide ActivClient for Windows 6.2 ActivClient for Windows Administration Guide P 2 Table of Contents Chapter 1: Introduction....................................................................12
Administration Guide ActivClient for Windows 6.2 ActivClient for Windows Administration Guide P 2 Table of Contents Chapter 1: Introduction....................................................................12
GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual
 GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual Overview GadgetTrak Mobile Security is an advanced software application designed to assist in the recovery of your mobile
GadgetTrak Mobile Security Android & BlackBerry Installation & Operation Manual Overview GadgetTrak Mobile Security is an advanced software application designed to assist in the recovery of your mobile
Installation Guide. (You can get these files from http://www.clariostechnology.com/intelligentreports/install)
 Clarios Technology Pty. Ltd. Intelligent Reporter Installation Guide Installing Intelligent Reports JIRA plugin The Intelligent Reports plugin for JIRA is available through the Atlassian Marketplace. Follow
Clarios Technology Pty. Ltd. Intelligent Reporter Installation Guide Installing Intelligent Reports JIRA plugin The Intelligent Reports plugin for JIRA is available through the Atlassian Marketplace. Follow
Smart Card Authentication Client. Administrator's Guide
 Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
Smart Card Authentication Client Administrator's Guide April 2013 www.lexmark.com Contents 2 Contents Overview...3 Configuring Smart Card Authentication Client...4 Configuring printer settings for use
BlackBerry Business Cloud Services. Administration Guide
 BlackBerry Business Cloud Services Administration Guide Published: 2012-07-25 SWD-20120725193410416 Contents 1 About BlackBerry Business Cloud Services... 8 BlackBerry Business Cloud Services feature overview...
BlackBerry Business Cloud Services Administration Guide Published: 2012-07-25 SWD-20120725193410416 Contents 1 About BlackBerry Business Cloud Services... 8 BlackBerry Business Cloud Services feature overview...
Yale Software Library
 Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
Yale Software Library http://www.yale.edu/its/software/ For assistance contact the ITS Help Desk 203-432-9000, [email protected] Two-factor authentication: Installation and configuration instructions for
PKI Contacts PKI for Fraunhofer Contacts
 Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 15.10.2013
USER MANUAL. v. 1.0.0.95 Windows Client ------------------------ January 2014 ------------------------
 USER MANUAL v. 1.0.0.95 Windows Client ------------------------ January 2014 ------------------------ 1 Contents At a Glance Troubleshoot 3 About SkyCrypt 23 FAQ 4 About this manual 23 Contact support
USER MANUAL v. 1.0.0.95 Windows Client ------------------------ January 2014 ------------------------ 1 Contents At a Glance Troubleshoot 3 About SkyCrypt 23 FAQ 4 About this manual 23 Contact support
Using an Edline Gradebook. EGP Teacher Guide
 Using an Edline Gradebook EGP Teacher Guide Table of Contents Introduction...3 Setup...3 Get the Gradebook Web Plugin... 3 Using Your Web Gradebook... 4 Using the Web Gradebook on a Shared Computer...
Using an Edline Gradebook EGP Teacher Guide Table of Contents Introduction...3 Setup...3 Get the Gradebook Web Plugin... 3 Using Your Web Gradebook... 4 Using the Web Gradebook on a Shared Computer...
Entrust Managed Services PKI
 Entrust Managed Services PKI Entrust Managed Services PKI Windows Smart Card Logon Configuration Guide Using Web-based applications Document issue: 1.0 Date of Issue: June 2009 Copyright 2009 Entrust.
Entrust Managed Services PKI Entrust Managed Services PKI Windows Smart Card Logon Configuration Guide Using Web-based applications Document issue: 1.0 Date of Issue: June 2009 Copyright 2009 Entrust.
Using Microsoft Visual Studio 2010. API Reference
 2010 API Reference Published: 2014-02-19 SWD-20140219103929387 Contents 1... 4 Key features of the Visual Studio plug-in... 4 Get started...5 Request a vendor account... 5 Get code signing and debug token
2010 API Reference Published: 2014-02-19 SWD-20140219103929387 Contents 1... 4 Key features of the Visual Studio plug-in... 4 Get started...5 Request a vendor account... 5 Get code signing and debug token
Help. F-Secure Online Backup
 Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
Help F-Secure Online Backup F-Secure Online Backup Help... 3 Introduction... 3 What is F-Secure Online Backup?... 3 How does the program work?... 3 Using the service for the first time... 3 Activating
Using your Encrypted BlackBerry
 Using your Encrypted BlackBerry How do I change the Language on my BlackBerry? 1. On the Home screen or in a folder, click the Options icon. 2. Click Typing and Input > Language. 3. To change the display
Using your Encrypted BlackBerry How do I change the Language on my BlackBerry? 1. On the Home screen or in a folder, click the Options icon. 2. Click Typing and Input > Language. 3. To change the display
CONNECTING TO THE DTS WIRELESS NETWORK USING WINDOWS VISTA
 CONNECTING TO THE DTS WIRELESS NETWORK USING WINDOWS VISTA There are three steps to accessing the web through the DTS wireless network. 1. Obtain the wireless network Username and Password. This is something
CONNECTING TO THE DTS WIRELESS NETWORK USING WINDOWS VISTA There are three steps to accessing the web through the DTS wireless network. 1. Obtain the wireless network Username and Password. This is something
IMPORTING AND EXPORTING CERTIFICATES IN IE AND FIREFOX FOR BPIA AND PRACS
 IMPORTING AND EXPORTING CERTIFICATES IN IE AND FIREFOX FOR BPIA AND PRACS Exporting a certificate is useful for keeping a backup copy of your certificate or for importing it to another browser (either
IMPORTING AND EXPORTING CERTIFICATES IN IE AND FIREFOX FOR BPIA AND PRACS Exporting a certificate is useful for keeping a backup copy of your certificate or for importing it to another browser (either
User Guide Remote Access to VDI/Workplace Using PIV
 User Guide Remote Access to VDI/Workplace Using PIV Innovation & Engineering Office (IM-64) May 2015 Table of Contents 1 Overview... 3 1.1 Web Browsers... 3 1.2 Operating Systems... 3 2 Types of Smart
User Guide Remote Access to VDI/Workplace Using PIV Innovation & Engineering Office (IM-64) May 2015 Table of Contents 1 Overview... 3 1.1 Web Browsers... 3 1.2 Operating Systems... 3 2 Types of Smart
BlackBerry Link for Windows. Version: 1.1.1. User Guide
 BlackBerry Link for Windows Version: 1.1.1 User Guide Published: 2013-07-22 SWD-20130722144723525 Contents Getting started...5 About BlackBerry Link... 5 Getting to know BlackBerry Link...5 Connecting
BlackBerry Link for Windows Version: 1.1.1 User Guide Published: 2013-07-22 SWD-20130722144723525 Contents Getting started...5 About BlackBerry Link... 5 Getting to know BlackBerry Link...5 Connecting
Contents. Getting Started...1. Managing Your Drives...14. Backing Up & Restoring Folders...28. Synchronizing Folders...48. Managing Security...
 Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Contents Getting Started.....................................................1 Using the Formatting Tool........................................1 Preparing the Software Manually..................................4
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7.
 Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Use the below instructions to configure your wireless settings to connect to the secure wireless network using Microsoft Windows Vista/7. 1. Click the Windows Start button, then Control Panel How-To-WCC-Secure-Windows-7-11/4/2010-4:09
Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate on Aladdin etoken (Personal eid)
 The World Internet Security Company Solutions for Security Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate on Aladdin etoken (Personal eid) Wherever Security relies on Identity,
The World Internet Security Company Solutions for Security Guide to Obtaining Your Free WISeKey CertifyID Personal Digital Certificate on Aladdin etoken (Personal eid) Wherever Security relies on Identity,
Windows Mail POP Instructions - Bloomsburg University Students
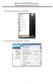 1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
1. Open Windows Mail from your Start Menu. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add to add your account. 4. Click on Email Account and then click Next. 2 5. Enter your full name
1. To ensure the appropriate level of security, you will need Microsoft Windows XP or above.
 System Requirements This section describes the resources you will need on your computer and how to configure your system to use @venture. Because individual systems widely vary, these guidelines are general
System Requirements This section describes the resources you will need on your computer and how to configure your system to use @venture. Because individual systems widely vary, these guidelines are general
Smart Card Authentication. Administrator's Guide
 Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
Smart Card Authentication Administrator's Guide October 2012 www.lexmark.com Contents 2 Contents Overview...4 Configuring the applications...5 Configuring printer settings for use with the applications...5
Pendragon Forms Industrial
 Pendragon Forms Industrial Version 7 Installation & Reference Guide for Android Devices Contents What Is Pendragon Forms Industrial?... 2 Installing Pendragon Forms Industrial... 2 Installing Pendragon
Pendragon Forms Industrial Version 7 Installation & Reference Guide for Android Devices Contents What Is Pendragon Forms Industrial?... 2 Installing Pendragon Forms Industrial... 2 Installing Pendragon
Installing the Citrix Online Plug-In
 Installing the Citrix Online Plug-In If you are a first-time user accessing NeoSystems Citrix environment, you are required to install a small program on your computer. This program will enable you to
Installing the Citrix Online Plug-In If you are a first-time user accessing NeoSystems Citrix environment, you are required to install a small program on your computer. This program will enable you to
Shakambaree Technologies Pvt. Ltd.
 Welcome to Support Express by Shakambaree Technologies Pvt. Ltd. Introduction: This document is our sincere effort to put in some regular issues faced by a Digital Signature and USB Token user doing on
Welcome to Support Express by Shakambaree Technologies Pvt. Ltd. Introduction: This document is our sincere effort to put in some regular issues faced by a Digital Signature and USB Token user doing on
BlackBerry Internet Service. Version: 4.5.1. Administration Guide
 BlackBerry Internet Service Version: 4.5.1 Administration Guide Published: 2014-01-22 SWD-20140122155744258 Contents 1 Getting started...6 Administrative feature availability... 6 Availability of features
BlackBerry Internet Service Version: 4.5.1 Administration Guide Published: 2014-01-22 SWD-20140122155744258 Contents 1 Getting started...6 Administrative feature availability... 6 Availability of features
BOTTOM UP THINKING EMAIL SETUP INSTRUCTIONS. Unique businesses require unique solutions CLIENT GUIDE
 BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
MCBDirect Corporate Logging on using a Soft Token
 MCBDirect Corporate Logging on using a Soft Token Document issue: 2.1 Date of issue: September 2014 Contents About Soft Token authentication... 3 Logging onto MCBDirect Corporate online banking... 4 Soft
MCBDirect Corporate Logging on using a Soft Token Document issue: 2.1 Date of issue: September 2014 Contents About Soft Token authentication... 3 Logging onto MCBDirect Corporate online banking... 4 Soft
PROXKey Tool User Manual
 PROXKey Tool User Manual 1 Table of Contents 1 Introduction...4 2 PROXKey Product... 5 2.1 PROXKey Tool... 5 2.2 PROXKey function modules...6 2.3 PROXKey using environment...6 3 PROXKey Tool Installation...7
PROXKey Tool User Manual 1 Table of Contents 1 Introduction...4 2 PROXKey Product... 5 2.1 PROXKey Tool... 5 2.2 PROXKey function modules...6 2.3 PROXKey using environment...6 3 PROXKey Tool Installation...7
Hyperoo 2.0 A (Very) Quick Start
 Hyperoo 2.0 A (Very) Quick Start Download and install the Hyperoo 2.0 beta Hyperoo 2.0 is a client/server based application and as such requires that you install both the Hyperoo Client and Hyperoo Server
Hyperoo 2.0 A (Very) Quick Start Download and install the Hyperoo 2.0 beta Hyperoo 2.0 is a client/server based application and as such requires that you install both the Hyperoo Client and Hyperoo Server
NetSupport DNA Configuration of Microsoft SQL Server Express
 NetSupport DNA Configuration of Microsoft SQL Server Express Configuration of Microsoft SQL Server Express and NetSupport DNA Installation Requirements If installing Microsoft SQL Server Express on Windows
NetSupport DNA Configuration of Microsoft SQL Server Express Configuration of Microsoft SQL Server Express and NetSupport DNA Installation Requirements If installing Microsoft SQL Server Express on Windows
Yubico Authenticator User's Guide
 Yubico Authenticator User's Guide YubiKeys with desktop computers and NFCenabled Android smartphones Yubico Authenticator User's Guide 2016 Yubico. All rights reserved. Page 1 of 23 Copyright 2016 Yubico
Yubico Authenticator User's Guide YubiKeys with desktop computers and NFCenabled Android smartphones Yubico Authenticator User's Guide 2016 Yubico. All rights reserved. Page 1 of 23 Copyright 2016 Yubico
Outlook Express POP Instructions - Bloomsburg University Students
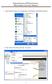 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
Secure Email Client Guide
 PRESIDIO BANK 33 Secure Email Client Guide THE BUSINESS BANK THAT WORKS 8/2013 Table of Contents Introduction.....3 Our Responsibility to Protect Confidential Information....4 Registering and Accessing
PRESIDIO BANK 33 Secure Email Client Guide THE BUSINESS BANK THAT WORKS 8/2013 Table of Contents Introduction.....3 Our Responsibility to Protect Confidential Information....4 Registering and Accessing
NHSmail mobile configuration guide Android mobile devices
 NHSmail mobile configuration guide Android mobile devices Version: V.6 Date: September 2011 THIS INFORMATION IS FOR NHS STAFF AND IS NOT TO BE DISTRIBUTED OR COPIED OUTSIDE OF THE NHS Version 6.0 Crown
NHSmail mobile configuration guide Android mobile devices Version: V.6 Date: September 2011 THIS INFORMATION IS FOR NHS STAFF AND IS NOT TO BE DISTRIBUTED OR COPIED OUTSIDE OF THE NHS Version 6.0 Crown
TrustKey Tool User Manual
 TrustKey Tool User Manual 1 Table of Contents 1 Introduction... 5 2 TrustKey Product...6 2.1 TrustKey Tool... 6 2.2 TrustKey function modules...7 2.3 TrustKey using environment...7 3 TrustKey Tool Installation...
TrustKey Tool User Manual 1 Table of Contents 1 Introduction... 5 2 TrustKey Product...6 2.1 TrustKey Tool... 6 2.2 TrustKey function modules...7 2.3 TrustKey using environment...7 3 TrustKey Tool Installation...
Technical notes for HIGHSEC eid App Middleware
 Technical notes for HIGHSEC eid App Middleware Version 2.1 February 2014. 1 Contents 1 Technical Notes... 3 1.1 All Operating Systems... 3 1.1.1 Slowing down of the cards while pairing... 3 1.1.2 Load
Technical notes for HIGHSEC eid App Middleware Version 2.1 February 2014. 1 Contents 1 Technical Notes... 3 1.1 All Operating Systems... 3 1.1.1 Slowing down of the cards while pairing... 3 1.1.2 Load
IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1. User Guide IBM SC23-9950-05
 IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05 IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05
IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05 IBM Security Access Manager for Enterprise Single Sign-On Version 8.2.1 User Guide IBM SC23-9950-05
User Guide Remote PIV to VDI Using a PIV Card
 User Guide Remote PIV to VDI Using a PIV Card Energy IT Services (IM-64) March 2015 Authors Prepared By Matthew Cummings Senior Systems Engineer IM-64 Version Control Date Version Document Revision Description
User Guide Remote PIV to VDI Using a PIV Card Energy IT Services (IM-64) March 2015 Authors Prepared By Matthew Cummings Senior Systems Engineer IM-64 Version Control Date Version Document Revision Description
BlackBerry Web Desktop Manager. Version: 5.0 Service Pack: 4. User Guide
 BlackBerry Web Desktop Manager Version: 5.0 Service Pack: 4 User Guide Published: 2012-10-03 SWD-20121003174218242 Contents 1 Basics... 5 Log in to the BlackBerry Web Desktop Manager... 5 Connect your
BlackBerry Web Desktop Manager Version: 5.0 Service Pack: 4 User Guide Published: 2012-10-03 SWD-20121003174218242 Contents 1 Basics... 5 Log in to the BlackBerry Web Desktop Manager... 5 Connect your
Quest Soft Token for Windows Phone User Guide
 Quest Soft Token for Windows Phone User Guide What is the Quest Soft Token for Windows Phone? The Quest Soft Token for Windows Phone is a two-factor authentication token that can be used with any OATH-compliant
Quest Soft Token for Windows Phone User Guide What is the Quest Soft Token for Windows Phone? The Quest Soft Token for Windows Phone is a two-factor authentication token that can be used with any OATH-compliant
BlackBerry Desktop Software User Guide
 BlackBerry Desktop Software User Guide Version: 2.4 SWD-1905381-0426093716-001 Contents Basics... 3 About the BlackBerry Desktop Software... 3 Set up your smartphone with the BlackBerry Desktop Software...
BlackBerry Desktop Software User Guide Version: 2.4 SWD-1905381-0426093716-001 Contents Basics... 3 About the BlackBerry Desktop Software... 3 Set up your smartphone with the BlackBerry Desktop Software...
PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents
 1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
1 PORTLANDDIOCESE.ORG Email - How to Connect Table of Contents Email Access via a Web Browser... 2 Email Client Setup... 3 Outlook 2007, 2010 & 2013 for Windows... 3 Outlook for Mac 2011... 5 Mac OS X
Export the address book from the Blackberry handheld to MS Outlook 2003, using the synchronize utility in Blackberry Desktop Manager.
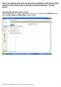 Export the address book from the Blackberry handheld to MS Outlook 2003, using the synchronize utility in Blackberry Desktop Manager. Revised 2/25/07 Creating a New Contacts Folder in Outlook Open Outlook
Export the address book from the Blackberry handheld to MS Outlook 2003, using the synchronize utility in Blackberry Desktop Manager. Revised 2/25/07 Creating a New Contacts Folder in Outlook Open Outlook
Transitioning from TurningPoint 5 to TurningPoint Cloud - NO LMS 1
 Transitioning from TurningPoint 5 to TurningPoint Cloud - NO LMS 1 A Turning Account is a unique identifier that is used to tie together all software accounts and response devices. A Turning Account is
Transitioning from TurningPoint 5 to TurningPoint Cloud - NO LMS 1 A Turning Account is a unique identifier that is used to tie together all software accounts and response devices. A Turning Account is
EMMA Application v. 4.9 User Manual
 EMMA Application v. 4.9 User Manual Prepared by: HP/DMDC 1600 N. Beauregard Street Alexandria, VA 22311 Abstract This guide describes how to use the EMMA system, which allows users to provision for required
EMMA Application v. 4.9 User Manual Prepared by: HP/DMDC 1600 N. Beauregard Street Alexandria, VA 22311 Abstract This guide describes how to use the EMMA system, which allows users to provision for required
How to Configure Entourage 2008 for Email Client
 How to Configure Entourage 2008 for Email Client Introduction (Revised 04/28/11) LAUSD IT Helpdesk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Before you configure Microsoft Entourage 2008 E-mail
How to Configure Entourage 2008 for Email Client Introduction (Revised 04/28/11) LAUSD IT Helpdesk 333 S. Beaudry Ave. 9 th Floor Phone 213.241.5200 Before you configure Microsoft Entourage 2008 E-mail
Entrust Certificate Services for Adobe CDS
 Entrust Certificate Services Entrust Certificate Services for Adobe CDS Getting Started Guide Entrust SafeNet Authentication Client: 8.3 Date of issue: July 2015 Document issue: 3.0 Revisions Issue and
Entrust Certificate Services Entrust Certificate Services for Adobe CDS Getting Started Guide Entrust SafeNet Authentication Client: 8.3 Date of issue: July 2015 Document issue: 3.0 Revisions Issue and
Exchange ActiveSync (EAS)
 Exchange ActiveSync (EAS) EAS allows for the synchronization of email, contacts, calendar, tasks and notes from an Exchange email server to a mobile device. Configuring and Connecting ios devices (iphone,
Exchange ActiveSync (EAS) EAS allows for the synchronization of email, contacts, calendar, tasks and notes from an Exchange email server to a mobile device. Configuring and Connecting ios devices (iphone,
Objectives. At the end of this chapter students should be able to:
 NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
NTFS PERMISSIONS AND SECURITY SETTING.1 Introduction to NTFS Permissions.1.1 File Permissions and Folder Permission.2 Assigning NTFS Permissions and Special Permission.2.1 Planning NTFS Permissions.2.2
To check the version of your firmware, press the menu button on your BlackBerry then, select Options:
 Wireless network instructions Note: This guide is for use with a BlackBerry 9000 mobile device and BlackBerry Desktop Software version 6.1.0.35. Other BlackBerry devices and software may function in a
Wireless network instructions Note: This guide is for use with a BlackBerry 9000 mobile device and BlackBerry Desktop Software version 6.1.0.35. Other BlackBerry devices and software may function in a
User Guide. Time Warner Cable Business Class Cloud Solutions Control Panel. Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007
 Chapter Title Time Warner Cable Business Class Cloud Solutions Control Panel User Guide Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007 Version 1.1 Table of Contents Table of Contents...
Chapter Title Time Warner Cable Business Class Cloud Solutions Control Panel User Guide Hosted Microsoft Exchange 2007 Hosted Microsoft SharePoint 2007 Version 1.1 Table of Contents Table of Contents...
Booth Gmail Configuration
 Student email is accessed via a Booth branded Gmail service. Student mailboxes will be accessed via Gmail. Configure Gmail Settings Before you connect Gmail to send and receive Booth Gmail on your mobile
Student email is accessed via a Booth branded Gmail service. Student mailboxes will be accessed via Gmail. Configure Gmail Settings Before you connect Gmail to send and receive Booth Gmail on your mobile
Yale Software Library. PGP 9.6 for Windows
 PGP 9.6 for Windows How to Add keys to the All Keys key ring: 1. Run the PGP application from Start->All Programs->PGP. 2. In the PGP main application window, click on Search for keys. 3. In the Search
PGP 9.6 for Windows How to Add keys to the All Keys key ring: 1. Run the PGP application from Start->All Programs->PGP. 2. In the PGP main application window, click on Search for keys. 3. In the Search
User Guide Supplement. S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series
 User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
User Guide Supplement S/MIME Support Package for BlackBerry Smartphones BlackBerry Pearl 8100 Series SWD-292878-0324093908-001 Contents Certificates...3 Certificate basics...3 Certificate status...5 Certificate
University Computing & Telecommunications Virtual Private Networking: How To/Self- Help Guide Windows 8.1 Operating System.
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
Generating an Apple Push Notification Service Certificate for use with GO!Enterprise MDM. This guide provides information on...
 Generating an Apple Push Notification Service Certificate for use with GO!Enterprise MDM This guide provides information on...... APNs Requirements Tips on Enrolling in the ios Developer Enterprise Program...
Generating an Apple Push Notification Service Certificate for use with GO!Enterprise MDM This guide provides information on...... APNs Requirements Tips on Enrolling in the ios Developer Enterprise Program...
How to Connect to Berkeley College Virtual Lab Using Windows
 How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
How to Connect to Berkeley College Virtual Lab Using Windows Minimum Requirements Create and Save a Remote Desktop Services Connection Connecting to a Remote Desktop Services session Copy Files between
Internet Explorer Settings for use with Privia
 Internet Explorer Settings for use with Privia The following document is intended for users who are running Privia and Internet Explorer who either cannot install the Privia client or the client is not
Internet Explorer Settings for use with Privia The following document is intended for users who are running Privia and Internet Explorer who either cannot install the Privia client or the client is not
SENDING AND RECEIVING PROTECTED INFORMATION VIA ELECTRONIC MAIL. Naval Medical Center Portsmouth IMD Training Division
 SENDING AND RECEIVING PROTECTED INFORMATION VIA ELECTRONIC MAIL Naval Medical Center Portsmouth IMD Training Division INTRODUCTION The following slides will help you set up your computer and Microsoft
SENDING AND RECEIVING PROTECTED INFORMATION VIA ELECTRONIC MAIL Naval Medical Center Portsmouth IMD Training Division INTRODUCTION The following slides will help you set up your computer and Microsoft
TERAcloud w w w. t e r a c l o u d. u k
 Accessing your account Once you have received the confirmation email, there will be a link to your personal area where you can download the backup application. In the example here we are using the support
Accessing your account Once you have received the confirmation email, there will be a link to your personal area where you can download the backup application. In the example here we are using the support
Adding Digital Signature and Encryption in Outlook
 Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
Adding Digital Signature and Encryption in Outlook Using Outlook, the email messages can be signed and encrypted by a digital certificate. To digitally sign a message in Outlook some conditions must be
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
BlackBerry Universal Device Service. Demo Access. AUTHOR: System4u
 Demo Access AUTHOR: System4u BlackBerry Universal Device Service Revisions Date Version Description Author June 26 th 2012 1.0 Roman Přikryl September 25 th 2012 1.5 Revision Roman Přikryl October 5 th
Demo Access AUTHOR: System4u BlackBerry Universal Device Service Revisions Date Version Description Author June 26 th 2012 1.0 Roman Přikryl September 25 th 2012 1.5 Revision Roman Přikryl October 5 th
Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows
 Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows SecureZIP for Windows interoperates with leading PKI vendors including Entrust, VeriSign, and RSA to enable the
Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows SecureZIP for Windows interoperates with leading PKI vendors including Entrust, VeriSign, and RSA to enable the
NotifyMDM Device Application User Guide Installation and Configuration for Windows Mobile 6 Devices
 NotifyMDM Device Application User Guide Installation and Configuration for Windows Mobile 6 Devices End-of-Life Notice Please note that GO!Enterprise MDM server version 3.6.3 is the last to officially
NotifyMDM Device Application User Guide Installation and Configuration for Windows Mobile 6 Devices End-of-Life Notice Please note that GO!Enterprise MDM server version 3.6.3 is the last to officially
FuseMail- Exchange ControlPanel Admin Guide Feb.27-14 V1.0. Exchange ControlPanel Administration Guide
 Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
Exchange ControlPanel Administration Guide Table of Contents Top Level Portal Administration... 4 Signing In to Control Panel... 4 Restoring Account Password... 5 Change Account Details... 7 Viewing Account
McAfee Endpoint Encryption 7.0 Users Guide and FAQ
 McAfee Endpoint Encryption 7.0 Users Guide and FAQ Table of Contents Introduction... 1 Installation... 1 Boot-Up/Login... 1 Encryption Status... 3 Notes for Encryption... 4 Changing Your Password... 4
McAfee Endpoint Encryption 7.0 Users Guide and FAQ Table of Contents Introduction... 1 Installation... 1 Boot-Up/Login... 1 Encryption Status... 3 Notes for Encryption... 4 Changing Your Password... 4
GO!Enterprise MDM Device Application User Guide Installation and Configuration for Android with TouchDown
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for Android with TouchDown GO!Enterprise MDM for Android, Version 3.x GO!Enterprise MDM for Android with TouchDown 1 Table
GO!Enterprise MDM Device Application User Guide Installation and Configuration for Android with TouchDown GO!Enterprise MDM for Android, Version 3.x GO!Enterprise MDM for Android with TouchDown 1 Table
Getting Started with Microsoft Outlook with Exchange Online Software from Time Warner Cable Business Class
 Getting Started with Microsoft Outlook with Exchange Online Software from Time Warner Cable Business Class A Guide for Administrators Table of Contents Requirements... 3 1. Activate & Setup Online Software
Getting Started with Microsoft Outlook with Exchange Online Software from Time Warner Cable Business Class A Guide for Administrators Table of Contents Requirements... 3 1. Activate & Setup Online Software
The Welcome screen displays each time you log on to PaymentNet; it serves as your starting point or home screen.
 PaymentNet Cardholder Quick Reference Card Corporate Card ffwelcome to PaymentNet The Welcome screen displays each time you log on to PaymentNet; it serves as your starting point or home screen. PaymentNet
PaymentNet Cardholder Quick Reference Card Corporate Card ffwelcome to PaymentNet The Welcome screen displays each time you log on to PaymentNet; it serves as your starting point or home screen. PaymentNet
User Guide. Version R91. English
 AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R91 English August 25, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8
 BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8 User Guide SWDT653811-793266-0827104650-001 Contents Getting started... 3 About messaging service plans for BlackBerry
BlackBerry Internet Service Using the Browser on Your BlackBerry Smartphone Version: 2.8 User Guide SWDT653811-793266-0827104650-001 Contents Getting started... 3 About messaging service plans for BlackBerry
INFORMATION TECHNOLOGY CERES DEPARTMENT
 INFORMATION TECHNOLOGY CERES DEPARTMENT LRA APPLICATION MANUAL Name Date Written by: Technical support 18/10/2010 Revised by: Approved by: DOCUMENT TRACEABILITY Version Date Description Author 1.0 18/10/2010
INFORMATION TECHNOLOGY CERES DEPARTMENT LRA APPLICATION MANUAL Name Date Written by: Technical support 18/10/2010 Revised by: Approved by: DOCUMENT TRACEABILITY Version Date Description Author 1.0 18/10/2010
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
E-mail Encryption Guide version 1.2, by Thomas Reed
 E-mail Encryption Guide version 1.2, by Thomas Reed In order for two people to send and receive encrypted e-mails to/from each other, both parties need: An e-mail reader that supports encryption (such
E-mail Encryption Guide version 1.2, by Thomas Reed In order for two people to send and receive encrypted e-mails to/from each other, both parties need: An e-mail reader that supports encryption (such
User Guide. The AMF's File Transfer Service (FTS)
 User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
User Guide The AMF's File Transfer Service (FTS) TABLE OF CONTENTS 1 INTENDED USERS... 3 2 SCOPE OF GUIDE... 3 3 BACKGROUND... 3 4 REQUIRED CONFIGURATION... 3 5 CONTACT INFORMATION FOR SUPPORT... 4 6 SECURITY...
HP ProtectTools User Guide
 HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
HP ProtectTools User Guide Copyright 2007 Hewlett-Packard Development Company, L.P. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. Intel is a trademark or registered trademark
How to Restore a Windows System to Bare Metal
 How to Restore a Windows System to Bare Metal This article applies to Barracuda Backup Server firmware version 5.4 and higher. Bare metal recovery allows you to restore a complete Microsoft Windows system,
How to Restore a Windows System to Bare Metal This article applies to Barracuda Backup Server firmware version 5.4 and higher. Bare metal recovery allows you to restore a complete Microsoft Windows system,
Outlook Express IMAP Instructions - Bloomsburg University Students
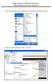 1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
1. Open Outlook Express by clicking Start, All Programs, and Outlook Express. 2. Click on the Tools menu and click Accounts. 1 3. Click on Add Mail 4. Enter your name and click Next. 2 5. Enter your full
This tutorial provides detailed instructions to help you download and configure Internet Explorer 6.0 for use with Web Commerce application.
 IE 6.0 Download and Set-up To use the Web Commerce e-commerce service, you need to: Gain access to the Internet Install Microsoft Internet Explorer 6.0 Configure Temporary Internet files in Internet Explorer.
IE 6.0 Download and Set-up To use the Web Commerce e-commerce service, you need to: Gain access to the Internet Install Microsoft Internet Explorer 6.0 Configure Temporary Internet files in Internet Explorer.
Entrust Managed Services PKI Administrator Guide
 Entrust Managed Services PKI Entrust Managed Services PKI Administrator Guide Document issue: 3.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered
Entrust Managed Services PKI Entrust Managed Services PKI Administrator Guide Document issue: 3.0 Date of issue: May 2009 Copyright 2009 Entrust. All rights reserved. Entrust is a trademark or a registered
Egnyte App for Android Quick Start Guide
 Egnyte App for Android Quick Start Guide Introduction Welcome to the Quick Start Guide for the Egnyte App for Android. This guide will explain how to: Access files. Download content for offline access.
Egnyte App for Android Quick Start Guide Introduction Welcome to the Quick Start Guide for the Egnyte App for Android. This guide will explain how to: Access files. Download content for offline access.
