Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure
|
|
|
- Lambert Jefferson
- 9 years ago
- Views:
Transcription
1 Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system hardening, and continuous monitoring so you can regain visibility, reduce attack surface, and detect malware across your Microsoft Azure deployments. This document describes how to deploy the following Tenable solutions to help ensure a secure and compliant Microsoft Azure cloud environment: Auditing Microsoft Azure Cloud Environment Nessus BYOL (Bring Your Own License) Scanner Nessus Agent Scans of Microsoft Azure Cloud Instances With more than one million users, Nessus is the world s most widely-deployed vulnerability, configuration, and compliance assessment product. Nessus prevents attacks by identifying the vulnerabilities, configuration issues, and malware that hackers could use to penetrate your network. It is as important to run these assessments in Microsoft Azure as it is in any other IT environment. Please any comments and suggestions to [email protected]. Auditing the Microsoft Azure Cloud Environment Tenable offers the ability to audit the Microsoft Azure Cloud environment to detect misconfigurations within the cloud environment and with account settings. Audits can be performed using Nessus Cloud, Nessus Manager, or a standalone Nessus scanner. No pre-authorization is needed from Microsoft to perform the audit, but a Microsoft Azure account is required. In order to perform an audit of the Microsoft Azure cloud environment, Nessus will need a Microsoft Azure Client ID. To obtain a Client ID, navigate to Microsoft Azure ( and log in. Copyright Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security, Inc.
2 Once logged in, click the browse > button on the left-hand menu and select Active Directory. Click on Applications and then click on Add located at the bottom center of the window. 2
3 Click Add an application my organization is developing. Enter a name for the application, select Native Client Application, and click the right arrow to proceed. Enter a Redirect URI and click the checkmark to complete the setup. 3
4 Click Configure to display the Client ID. Copy the Client ID. This information will be used to complete the audit configuration with Nessus. On the bottom of that same window click Add application. 4
5 Click the + next to Windows Azure Service Management API to add the necessary permissions. When the permissions have been granted, the + will turn into a green checkmark. Click the green checkmark on the bottom right-hand side of the screen to complete the process. You will be returned to the previous configuration screen. Click Save located near the bottom of the window to finalize the setup. Log into Nessus and click New Scan. 5
6 Select the Audit Cloud Infrastructure template. Enter a descriptive name for the scan and then click on Credentials. 6
7 Click the + next to Microsoft Azure to open the Credentials options. Enter your Microsoft Azure Username and Password, Client ID, and Subscription IDs into the appropriate boxes. Leave the Subscription IDs box blank if you want to audit all of your Azure subscriptions. 7
8 Click Compliance and expand the Microsoft Azure option. Tenable offers three pre-configured compliance checks and also provides the ability to upload a custom Azure audit file. Click the + next to each compliance check you want to add to the scan. If you choose to add a custom audit file, click Add File and select the file to upload. Once the compliance checks are added, click Save or click the drop-down arrow next to Save and select Launch to initiate the scan. Microsoft Azure Best Practices Infrastructure: This audit file implements a set of general best practices for Microsoft Azure infrastructure items including Principals, Virtual Networks, Certificates, and Virtual Machines. Microsoft Azure Best Practices Websites: This audit file implements a set of general best practices for Microsoft Azure Website items including Website Status, SSL Status, and recent Site modifications. Microsoft Azure Best Practices Databases: This audit file implements a set of general best practices for Microsoft Azure items including Database Configuration, Audit Events, and Recoverable Databases. For additional information on configuring Nessus scans, please refer to the Nessus documentation on the Tenable website. Provisioning Nessus BYOL from the Microsoft Azure Marketplace The Nessus BYOL is an instance of Nessus installed within Microsoft Azure that allows scanning of the Azure cloud environments and instances. Nessus BYOL capabilities include web application scanning and detection of vulnerabilities, compliance violations, misconfigurations, and malware. Customers interested in leveraging Nessus BYOL to secure their environments and instances must first purchase a Nessus license either directly from Tenable's e-commerce store or from an authorized reseller. The license will provide an Activation Code to apply when provisioning Nessus from your Microsoft Azure account. 8
9 To provision a Nessus BYOL instance, go to Microsoft Azure ( and log in. Click on Marketplace and search for Nessus. Click Tenable Nessus (BYOL) to review the product page. 9
10 Choose an option under Select a deployment model and click Create to begin deployment of the Nessus BYOL virtual machine. On the Basics screen, enter the following information and click OK. Table 1 Nessus BYOL Scanner Basics Option Name Description Descriptive name for the Nessus BYOL scanner User name User account name used to access the Nessus BYOL scanner Authentication Type Select SSH public key SSH public key Once generated, enter the SSH public key Subscription Select the subscription to which the virtual machine will be added Resource group Enter the name of a new Resource group or select an existing Resource group Location Select the geographical location for the virtual machine 10
11 Microsoft s recommended sizes are displayed. To view all available sizes, click on View all. Choose a desired virtual machine size by clicking on one of the displayed options and clicking Select. 11
12 On the Settings screen, enter the following information and click OK. Table 2 Nessus BYOL Scanner Settings Option Disk type Description Select Standard or Premium disk type Storage account Create or select a storage account type Virtual network Create or select a virtual network the Nessus BYOL will reside in Subnet Assign Nessus BYOL to a subnet in the virtual network Public IP address Network security group Option to create a public IP address so that the Nessus BYOL virtual machine is accessible outside the virtual network Enables firewall rules to control traffic to and from the Nessus BYOL virtual machine Diagnostics Availability set Enabling this option provides minute-by-minute metrics on the Nessus BYOL virtual machine Provides redundancy by grouping two or more virtual machines in an availability set 12
13 You are now presented with a summary of your selections. Click OK to continue; you will be given the option to Purchase the Nessus BYOL virtual machine you have configured. 13
14 If you are deploying the instance into an Azure Virtual Network, you must ensure you can reach TCP port 8834 on an IP address associated with the instance. This will be needed to complete the configuration process, as well as for the use of the product. Configure the instance and/or the Azure Virtual Network so that Nessus can communicate with Tenable servers; this is required for registration and plugin updates. If for some reason this is not possible, please refer to the Nessus documentation regarding off-line updates. Generally, you will connect to the public IP address (or external hostname) associated with an instance. If you are connecting to Nessus over a VPN to an Azure Virtual Network, it may be the private IP address. The IP addresses associated with the instance can be found under the virtual machine Settings. After the instance has initialized, open a browser and connect to the instance to complete the configuration. For example: address or hostname>:
15 The following welcome screen will be displayed: To complete the configuration, please refer to the Nessus documentation on the Tenable website. Prior to scanning, you must request permission to conduct vulnerability and penetration testing on instances in the Microsoft Azure cloud environment. Please visit the following page to review the approval process and to submit a testing request: Nessus Agent Scans of Microsoft Azure Cloud Instances Tenable s Nessus Agents provide the ability to perform local scans on instances within the Microsoft Azure cloud environment. Nessus agent scans, which are configured, managed, and updated through Nessus Cloud or Nessus Manager, help identify vulnerabilities, compliance violations, misconfigurations, and malware. Nessus Agents are downloaded from the Tenable Support Portal, installed on an instance running in the Microsoft Azure cloud environment, and then linked to Nessus Cloud or Nessus Manager. Agents can be installed on your target(s) manually, via Group Policy, SCCM, or other third-party software deployment applications. Nessus Agents are linked to a Nessus Cloud or Nessus Manager in the same manner as linking to a secondary scanner. Prior to installing Nessus Agents, you must acquire the Agent Key from within Nessus Cloud or Nessus Manager. To acquire the Agent Key, log into Nessus Cloud or Nessus Manager and go to Settings. Select Agents under the Scanners section, and then select Linked. A key will be generated that is used as a shared secret for the Nessus Agents to link to the scanner. 15
16 For more information on installing and configuring Nessus Agents refer to the Nessus documentation on the Tenable website. About Tenable Network Security Tenable Network Security provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. Our family of products includes SecurityCenter Continuous View, which provides the most comprehensive and integrated view of network health, and Nessus, the global standard in detecting and assessing network data. Tenable is relied upon by many of the world s largest corporations, not-for-profit organizations and public sector agencies, including the entire U.S. Department of Defense. For more information, visit tenable.com. 16
Nessus Cloud User Registration
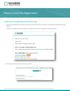 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Tenable for CyberArk
 HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
Nessus Agents. October 2015
 Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide. July 16, 2014 (Revision 2)
 Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9)
 Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Perimeter Service... 3 Subscription and Activation... 3 Multi Scanner Support...
Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Perimeter Service... 3 Subscription and Activation... 3 Multi Scanner Support...
Nessus Enterprise Cloud User Guide. October 2, 2014 (Revision 9)
 Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
SecurityCenter 5.1 with Nessus Agent Support. October 22, 2015
 SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
Tenable Network Security Support Portal. January 12, 2015 (Revision 14)
 Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
Configuring Virtual Switches for Use with PVS. February 7, 2014 (Revision 1)
 Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
Web Application Firewall
 Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
Nessus and Mobile Device Scanning. November 7, 2014 (Revision 12)
 Nessus and Mobile Device Scanning November 7, 2014 (Revision 12) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 Scanning for Mobile Devices with Nessus... 4 Creating a
Nessus and Mobile Device Scanning November 7, 2014 (Revision 12) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 Scanning for Mobile Devices with Nessus... 4 Creating a
Patch Management Integration
 Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
DreamFactory on Microsoft SQL Azure
 DreamFactory on Microsoft SQL Azure Account Setup and Installation Guide For general information about the Azure platform, go to http://www.microsoft.com/windowsazure/. For general information about the
DreamFactory on Microsoft SQL Azure Account Setup and Installation Guide For general information about the Azure platform, go to http://www.microsoft.com/windowsazure/. For general information about the
SecurityCenter 4.8 Administration Guide. October 2, 2015 (Revision 13)
 SecurityCenter 4.8 Administration Guide October 2, 2015 (Revision 13) Table of Contents Introduction... 5 Standards and Conventions... 5 Abbreviations... 6 SecurityCenter Administrator Functions... 6 Starting/Halting
SecurityCenter 4.8 Administration Guide October 2, 2015 (Revision 13) Table of Contents Introduction... 5 Standards and Conventions... 5 Abbreviations... 6 SecurityCenter Administrator Functions... 6 Starting/Halting
USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29. Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB
 USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29 Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB Table of Contents UNIT 1: Lab description... 3 Pre-requisites:... 3 UNIT 2: Launching an instance on EC2...
USER CONFERENCE 2011 SAN FRANCISCO APRIL 26 29 Running MarkLogic in the Cloud DEVELOPER LOUNGE LAB Table of Contents UNIT 1: Lab description... 3 Pre-requisites:... 3 UNIT 2: Launching an instance on EC2...
SecurityCenter 4.4 Administration Guide
 SecurityCenter 4.4 Administration Guide September 18, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_admin_guide.pdf
SecurityCenter 4.4 Administration Guide September 18, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_admin_guide.pdf
System Administration Training Guide. S100 Installation and Site Management
 System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
Your Archiving Service
 It s as simple as 1, 2, 3 This email archiving setup guide provides you with easy to follow instructions on how to setup your new archiving service as well as how to create archiving users and assign archiving
It s as simple as 1, 2, 3 This email archiving setup guide provides you with easy to follow instructions on how to setup your new archiving service as well as how to create archiving users and assign archiving
Web Sites, Virtual Machines, Service Management Portal and Service Management API Beta Installation Guide
 Web Sites, Virtual Machines, Service Management Portal and Service Management API Beta Installation Guide Contents Introduction... 2 Environment Topology... 2 Virtual Machines / System Requirements...
Web Sites, Virtual Machines, Service Management Portal and Service Management API Beta Installation Guide Contents Introduction... 2 Environment Topology... 2 Virtual Machines / System Requirements...
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
Crystal Reports Installation Guide
 Crystal Reports Installation Guide Version XI Infor Global Solutions, Inc. Copyright 2006 Infor IP Holdings C.V. and/or its affiliates or licensors. All rights reserved. The Infor word and design marks
Crystal Reports Installation Guide Version XI Infor Global Solutions, Inc. Copyright 2006 Infor IP Holdings C.V. and/or its affiliates or licensors. All rights reserved. The Infor word and design marks
uh6 efolder BDR Guide for Veeam Page 1 of 36
 efolder BDR for Veeam Hyper-V Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder
efolder BDR for Veeam Hyper-V Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder
How to Configure a High Availability Cluster in Azure via Web Portal and ASM
 How to Configure a High Availability Cluster in Azure via Web Portal and ASM To safeguard against hardware and software failures in the Azure cloud, use a high availability (HA) setup. The Barracuda NextGen
How to Configure a High Availability Cluster in Azure via Web Portal and ASM To safeguard against hardware and software failures in the Azure cloud, use a high availability (HA) setup. The Barracuda NextGen
SecurityCenter 4.2 Administration Guide
 SecurityCenter 4.2 Administration Guide January 24, 2012 (Revision 5) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.2_admin_guide.pdf
SecurityCenter 4.2 Administration Guide January 24, 2012 (Revision 5) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.2_admin_guide.pdf
Using Microsoft Expression Web to Upload Your Site
 Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
Using Microsoft Expression Web to Upload Your Site Using Microsoft Expression Web to Upload Your Web Site This article briefly describes how to use Microsoft Expression Web to connect to your Web server
OneLogin Integration User Guide
 OneLogin Integration User Guide Table of Contents OneLogin Account Setup... 2 Create Account with OneLogin... 2 Setup Application with OneLogin... 2 Setup Required in OneLogin: SSO and AD Connector...
OneLogin Integration User Guide Table of Contents OneLogin Account Setup... 2 Create Account with OneLogin... 2 Setup Application with OneLogin... 2 Setup Required in OneLogin: SSO and AD Connector...
IBM Security QRadar SIEM Version 7.1.0 MR1. Vulnerability Assessment Configuration Guide
 IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
MultiSite Manager. Setup Guide
 MultiSite Manager Setup Guide Contents 1. Introduction... 2 How MultiSite Manager works... 2 How MultiSite Manager is implemented... 2 2. MultiSite Manager requirements... 3 Operating System requirements...
MultiSite Manager Setup Guide Contents 1. Introduction... 2 How MultiSite Manager works... 2 How MultiSite Manager is implemented... 2 2. MultiSite Manager requirements... 3 Operating System requirements...
MaaS360 Cloud Extender
 MaaS360 Cloud Extender Installation Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software described
MaaS360 Cloud Extender Installation Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software described
Using LifeSize systems with Microsoft Office Communications Server 2007. Server Setup
 Using LifeSize systems with Microsoft Office Communications Server 2007 This technical note describes the steps to integrate a LifeSize video communications device with Microsoft Office Communication Server
Using LifeSize systems with Microsoft Office Communications Server 2007 This technical note describes the steps to integrate a LifeSize video communications device with Microsoft Office Communication Server
MaaS360 On-Premises Cloud Extender
 MaaS360 On-Premises Cloud Extender Installation Guide Copyright 2014 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
MaaS360 On-Premises Cloud Extender Installation Guide Copyright 2014 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
Accessing the Media General SSL VPN
 Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Launching Applications and Mapping Drives Remote Desktop Outlook Launching Web Applications Full Access VPN Note: To access the Media General VPN, anti-virus software must be installed and running on your
Using and Contributing Virtual Machines to VM Depot
 Using and Contributing Virtual Machines to VM Depot Introduction VM Depot is a library of open source virtual machine images that members of the online community have contributed. You can browse the library
Using and Contributing Virtual Machines to VM Depot Introduction VM Depot is a library of open source virtual machine images that members of the online community have contributed. You can browse the library
An Oracle White Paper September 2013. Oracle WebLogic Server 12c on Microsoft Windows Azure
 An Oracle White Paper September 2013 Oracle WebLogic Server 12c on Microsoft Windows Azure Table of Contents Introduction... 1 Getting Started: Creating a Single Virtual Machine... 2 Before You Begin...
An Oracle White Paper September 2013 Oracle WebLogic Server 12c on Microsoft Windows Azure Table of Contents Introduction... 1 Getting Started: Creating a Single Virtual Machine... 2 Before You Begin...
TRIPWIRE PURECLOUD. TRIPWIRE PureCloud USER GUIDE
 TRIPWIRE PURECLOUD TRIPWIRE PureCloud USER GUIDE 2001-2015 Tripwire, Inc. All rights reserved. Tripwire and ncircle are registered trademarks of Tripwire, Inc. Other brand or product names may be trademarks
TRIPWIRE PURECLOUD TRIPWIRE PureCloud USER GUIDE 2001-2015 Tripwire, Inc. All rights reserved. Tripwire and ncircle are registered trademarks of Tripwire, Inc. Other brand or product names may be trademarks
Setting Up Scan to SMB on TaskALFA series MFP s.
 Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
Setting Up Scan to SMB on TaskALFA series MFP s. There are three steps necessary to set up a new Scan to SMB function button on the TaskALFA series color MFP. 1. A folder must be created on the PC and
Sophos Mobile Control SaaS startup guide. Product version: 6
 Sophos Mobile Control SaaS startup guide Product version: 6 Document date: January 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8
Sophos Mobile Control SaaS startup guide Product version: 6 Document date: January 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8
MultiSite Manager. Setup Guide
 MultiSite Manager Setup Guide Contents 1. Introduction... 2 How MultiSite Manager works... 2 How MultiSite Manager is implemented... 2 2. MultiSite Manager requirements... 3 Operating System requirements...
MultiSite Manager Setup Guide Contents 1. Introduction... 2 How MultiSite Manager works... 2 How MultiSite Manager is implemented... 2 2. MultiSite Manager requirements... 3 Operating System requirements...
SHAREPOINT 2013 IN INFRASTRUCTURE AS A SERVICE
 SHAREPOINT 2013 IN INFRASTRUCTURE AS A SERVICE Contents Introduction... 3 Step 1 Create Azure Components... 5 Step 1.1 Virtual Network... 5 Step 1.1.1 Virtual Network Details... 6 Step 1.1.2 DNS Servers
SHAREPOINT 2013 IN INFRASTRUCTURE AS A SERVICE Contents Introduction... 3 Step 1 Create Azure Components... 5 Step 1.1 Virtual Network... 5 Step 1.1.1 Virtual Network Details... 6 Step 1.1.2 DNS Servers
DIGIPASS Authentication for Cisco ASA 5500 Series
 DIGIPASS Authentication for Cisco ASA 5500 Series With IDENTIKEY Server 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 20 Disclaimer Disclaimer of Warranties and Limitations
DIGIPASS Authentication for Cisco ASA 5500 Series With IDENTIKEY Server 2010 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 20 Disclaimer Disclaimer of Warranties and Limitations
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.7.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Deploying Virtual Cyberoam Appliance in the Amazon Cloud Version 10
 Deploying Virtual Cyberoam Appliance in the Amazon Cloud Version 10 Document version 1.0 10.6.2.378-13/03/2015 Important Notice Cyberoam Technologies Pvt. Ltd. has supplied this Information believing it
Deploying Virtual Cyberoam Appliance in the Amazon Cloud Version 10 Document version 1.0 10.6.2.378-13/03/2015 Important Notice Cyberoam Technologies Pvt. Ltd. has supplied this Information believing it
Getting Started With Halo for Windows
 Getting Started With Halo for Windows For CloudPassage Halo Protecting your Windows servers in a public or private cloud is much easier and more secure with CloudPassage Halo for Windows. Halo for Windows
Getting Started With Halo for Windows For CloudPassage Halo Protecting your Windows servers in a public or private cloud is much easier and more secure with CloudPassage Halo for Windows. Halo for Windows
Windows Azure Pack Installation and Initial Configuration
 Windows Azure Pack Installation and Initial Configuration Windows Server 2012 R2 Hands-on lab In this lab, you will learn how to install and configure the components of the Windows Azure Pack. To complete
Windows Azure Pack Installation and Initial Configuration Windows Server 2012 R2 Hands-on lab In this lab, you will learn how to install and configure the components of the Windows Azure Pack. To complete
360 Online authentication
 360 Online authentication Version October 2015 This document will help you set up a trust for authentication of 360 Online users between Azure Access Control Service and either Office 365 or Active Directory
360 Online authentication Version October 2015 This document will help you set up a trust for authentication of 360 Online users between Azure Access Control Service and either Office 365 or Active Directory
Installation Guide ARGUS Symphony 1.6 and Business App Toolkit. 6/13/2014 2014 ARGUS Software, Inc.
 ARGUS Symphony 1.6 and Business App Toolkit 6/13/2014 2014 ARGUS Software, Inc. Installation Guide for ARGUS Symphony 1.600.0 6/13/2014 Published by: ARGUS Software, Inc. 3050 Post Oak Boulevard Suite
ARGUS Symphony 1.6 and Business App Toolkit 6/13/2014 2014 ARGUS Software, Inc. Installation Guide for ARGUS Symphony 1.600.0 6/13/2014 Published by: ARGUS Software, Inc. 3050 Post Oak Boulevard Suite
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus. February 3, 2015 (Revision 4)
 Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
SOLGARI CLOUD BUSINESS COMMUNICATION SERVICES CLOUD CONTACT CENTRE MICROSOFT DYNAMICS INTEGRATION
 SOLGARI CLOUD BUSINESS COMMUNICATION SERVICES CLOUD CONTACT CENTRE MICROSOFT DYNAMICS INTEGRATION APRIL 2015 Microsoft Dynamics CRM Integration The Solgari CRM Integration module provides out of the box
SOLGARI CLOUD BUSINESS COMMUNICATION SERVICES CLOUD CONTACT CENTRE MICROSOFT DYNAMICS INTEGRATION APRIL 2015 Microsoft Dynamics CRM Integration The Solgari CRM Integration module provides out of the box
ThinPoint Quick Start Guide
 ThinPoint Quick Start Guide 2 ThinPoint Quick Start Guide Table of Contents Part 1 Introduction 3 Part 2 ThinPoint Windows Host Installation 3 1 Compatibility... list 3 2 Pre-requisites... 3 3 Installation...
ThinPoint Quick Start Guide 2 ThinPoint Quick Start Guide Table of Contents Part 1 Introduction 3 Part 2 ThinPoint Windows Host Installation 3 1 Compatibility... list 3 2 Pre-requisites... 3 3 Installation...
Setting up Sharp MX-Color Imagers for Inbound Fax Routing to Email or Network Folder
 Setting up Sharp MX-Color Imagers for Inbound Fax Routing to Email or Network Folder MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, *MX-M850, *MX-M950,
Setting up Sharp MX-Color Imagers for Inbound Fax Routing to Email or Network Folder MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, *MX-M850, *MX-M950,
IIS, FTP Server and Windows
 IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
IIS, FTP Server and Windows The Objective: To setup, configure and test FTP server. Requirement: Any version of the Windows 2000 Server. FTP Windows s component. Internet Information Services, IIS. Steps:
Virtual Data Centre. User Guide
 Virtual Data Centre User Guide 2 P age Table of Contents Getting Started with vcloud Director... 8 1. Understanding vcloud Director... 8 2. Log In to the Web Console... 9 3. Using vcloud Director... 10
Virtual Data Centre User Guide 2 P age Table of Contents Getting Started with vcloud Director... 8 1. Understanding vcloud Director... 8 2. Log In to the Web Console... 9 3. Using vcloud Director... 10
IBM Security QRadar Version 7.2.5. Vulnerability Assessment Configuration Guide IBM
 IBM Security QRadar Version 7.2.5 Vulnerability Assessment Configuration Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 93. Product
IBM Security QRadar Version 7.2.5 Vulnerability Assessment Configuration Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 93. Product
Lab 1: Windows Azure Virtual Machines
 Lab 1: Windows Azure Virtual Machines Overview In this hands-on Lab, you will learn how to deploy a simple web page to a Web server hosted in Windows Azure and configure load balancing. Objectives In this
Lab 1: Windows Azure Virtual Machines Overview In this hands-on Lab, you will learn how to deploy a simple web page to a Web server hosted in Windows Azure and configure load balancing. Objectives In this
Tenable for Google Cloud Platform
 HOW-TO GUIDE Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
HOW-TO GUIDE Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
Comodo Endpoint Security Manager SME Software Version 2.1
 Comodo Endpoint Security Manager SME Software Version 2.1 Quick Start Guide Guide Version 2.1.111114 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Endpoint Security Manager - SME Quick
Comodo Endpoint Security Manager SME Software Version 2.1 Quick Start Guide Guide Version 2.1.111114 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Endpoint Security Manager - SME Quick
NovaBACKUP xsp Version 15.0 Upgrade Guide
 NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
NovaBACKUP xsp Version 15.0 Upgrade Guide NovaStor / November 2013 2013 NovaStor, all rights reserved. All trademarks are the property of their respective owners. Features and specifications are subject
SOLARWINDS ORION. Patch Manager Evaluation Guide for ConfigMgr 2012
 SOLARWINDS ORION Patch Manager Evaluation Guide for ConfigMgr 2012 About SolarWinds SolarWinds, Inc. develops and markets an array of network management, monitoring, and discovery tools to meet the diverse
SOLARWINDS ORION Patch Manager Evaluation Guide for ConfigMgr 2012 About SolarWinds SolarWinds, Inc. develops and markets an array of network management, monitoring, and discovery tools to meet the diverse
Web Application Vulnerability Testing with Nessus
 The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP [email protected] Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP [email protected] Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
Microsoft Azure Configuration
 Microsoft Azure Configuration Azure Setup for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Create Azure Private VLAN 10 Launch VNS3 Image from Azure Marketplace 15 VNS3 Configuration Document
Microsoft Azure Configuration Azure Setup for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Create Azure Private VLAN 10 Launch VNS3 Image from Azure Marketplace 15 VNS3 Configuration Document
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
5nine Cloud Security Azure Pack Extension. Version 5.2
 5nine Cloud Security Azure Pack Extension Version 5.2 June 2015 2015 5nine Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be
5nine Cloud Security Azure Pack Extension Version 5.2 June 2015 2015 5nine Software. All rights reserved. All trademarks are the property of their respective owners. No part of this publication may be
PaperClip. em4 Cloud Client. Manual Setup Guide
 PaperClip em4 Cloud Client Manual Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand
PaperClip em4 Cloud Client Manual Setup Guide Copyright Information Copyright 2014, PaperClip Inc. - The PaperClip32 product name and PaperClip Logo are registered trademarks of PaperClip Inc. All brand
WhatsUp Gold v16.3 Installation and Configuration Guide
 WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
Protected Trust Setup Guide for Brother MFC Devices
 Protected Trust Setup Guide for Brother MFC Devices Summary Protected Trust Email Encryption is a versatile secure email service. This guide details three use cases between Protected Trust and your Brother
Protected Trust Setup Guide for Brother MFC Devices Summary Protected Trust Email Encryption is a versatile secure email service. This guide details three use cases between Protected Trust and your Brother
VPN Overview. The path for wireless VPN users
 VPN Overview The path for wireless VPN users First, the user's computer (the blue computer) connects to an access point in the uiuc-wireless-net network and is assigned an IP address in that range (172.21.0.0
VPN Overview The path for wireless VPN users First, the user's computer (the blue computer) connects to an access point in the uiuc-wireless-net network and is assigned an IP address in that range (172.21.0.0
Sophos UTM. Remote Access via SSL Configuring Remote Client
 Sophos UTM Remote Access via SSL Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
Sophos UTM Remote Access via SSL Configuring Remote Client Product version: 9.300 Document date: Tuesday, October 14, 2014 The specifications and information in this document are subject to change without
5nine Security for Hyper-V Datacenter Edition. Version 3.0 Plugin for Microsoft System Center 2012 Virtual Machine Manager
 5nine Security for Hyper-V Datacenter Edition Version 3.0 Plugin for Microsoft System Center 2012 Virtual Machine Manager November 2013 11 Table of Contents Summary... 5 System requirements... 5 Permissions...
5nine Security for Hyper-V Datacenter Edition Version 3.0 Plugin for Microsoft System Center 2012 Virtual Machine Manager November 2013 11 Table of Contents Summary... 5 System requirements... 5 Permissions...
Defender 5.7 - Token Deployment System Quick Start Guide
 Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Managing Qualys Scanners
 Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Q1 Labs Help Build 7.0 Maintenance Release 3 [email protected] Managing Qualys Scanners Managing Qualys Scanners A QualysGuard vulnerability scanner runs on a remote web server. QRadar must access
Juniper Networks Management Pack Documentation
 Juniper Networks Management Pack Documentation Juniper Networks Data Center Switching Management Pack for VMware vrealize Operations (vrops) Release 2.5 Modified: 2015-10-12 Juniper Networks, Inc. 1133
Juniper Networks Management Pack Documentation Juniper Networks Data Center Switching Management Pack for VMware vrealize Operations (vrops) Release 2.5 Modified: 2015-10-12 Juniper Networks, Inc. 1133
Plesk 11 Manual. Fasthosts Customer Support
 Fasthosts Customer Support Plesk 11 Manual This guide covers everything you need to know in order to get started with the Parallels Plesk 11 control panel. Contents Introduction... 3 Before you begin...
Fasthosts Customer Support Plesk 11 Manual This guide covers everything you need to know in order to get started with the Parallels Plesk 11 control panel. Contents Introduction... 3 Before you begin...
Deploying Bitnami Stacks on Windows Azure
 Deploying Bitnami Stacks on Windows Azure In this whitepaper we walk you through the process of setting up a Bitnami cloud image stack on Windows Azure and look at the advantages over other deployment
Deploying Bitnami Stacks on Windows Azure In this whitepaper we walk you through the process of setting up a Bitnami cloud image stack on Windows Azure and look at the advantages over other deployment
Virtual Appliance Setup Guide
 The Barracuda SSL VPN Vx Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda SSL VPN hardware appliance. It is designed for easy deployment
The Barracuda SSL VPN Vx Virtual Appliance includes the same powerful technology and simple Web based user interface found on the Barracuda SSL VPN hardware appliance. It is designed for easy deployment
Installing and Configuring vcenter Support Assistant
 Installing and Configuring vcenter Support Assistant vcenter Support Assistant 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Installing and Configuring vcenter Support Assistant vcenter Support Assistant 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Device LinkUP + Desktop LP Guide RDP
 Device LinkUP + Desktop LP Guide RDP Version 2.1 January 2016 Copyright 2015 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Device LinkUP + Desktop LP Guide RDP Version 2.1 January 2016 Copyright 2015 iwebgate. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
MadCap Software. Upgrading Guide. Pulse
 MadCap Software Upgrading Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
MadCap Software Upgrading Guide Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
Configuring Global Protect SSL VPN with a user-defined port
 Configuring Global Protect SSL VPN with a user-defined port Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] Global Protect SSL VPN Overview This document gives you an overview on how to configure
Configuring Global Protect SSL VPN with a user-defined port Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] Global Protect SSL VPN Overview This document gives you an overview on how to configure
CWOPA Broadband Users. Windows Operating System
 CWOPA Broadband Users Windows Operating System October 2012 Background These instructions are to be used for VPN users who have been assigned a CWOPA username and password. If your machine has Internet
CWOPA Broadband Users Windows Operating System October 2012 Background These instructions are to be used for VPN users who have been assigned a CWOPA username and password. If your machine has Internet
Configuring User Identification via Active Directory
 Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] User Identification Overview User Identification allows you to create security policies based
Configuring User Identification via Active Directory Version 1.0 PAN-OS 5.0.1 Johan Loos [email protected] User Identification Overview User Identification allows you to create security policies based
Juniper SSL VPN Authentication QUICKStart Guide
 Juniper SSL VPN Authentication QUICKStart Guide Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights
Juniper SSL VPN Authentication QUICKStart Guide Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights
BlackShield ID Agent for Remote Web Workplace
 Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
Agent for Remote Web Workplace 2010 CRYPTOCard Corp. All rights reserved. http:// www.cryptocard.com Copyright Copyright 2010, CRYPTOCard All Rights Reserved. No part of this publication may be reproduced,
http://docs.trendmicro.com
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the product, please review the readme files,
TechNote. Configuring SonicOS for MS Windows Azure
 Network Security SonicOS Contents Overview...1 Deployment Considerations...2 Supported Platforms...2 Configuring a Policy-Based VPN...2 Configuring a Route-Based VPN...17 Overview This TechNote details
Network Security SonicOS Contents Overview...1 Deployment Considerations...2 Supported Platforms...2 Configuring a Policy-Based VPN...2 Configuring a Route-Based VPN...17 Overview This TechNote details
AWS Plug-in Guide. Qlik Sense 1.1 Copyright 1993-2015 QlikTech International AB. All rights reserved.
 AWS Plug-in Guide Qlik Sense 1.1 Copyright 1993-2015 QlikTech International AB. All rights reserved. Copyright 1993-2015 QlikTech International AB. All rights reserved. Qlik, QlikTech, Qlik Sense, QlikView,
AWS Plug-in Guide Qlik Sense 1.1 Copyright 1993-2015 QlikTech International AB. All rights reserved. Copyright 1993-2015 QlikTech International AB. All rights reserved. Qlik, QlikTech, Qlik Sense, QlikView,
Configuration Guide. BES12 Cloud
 Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
Configuration Guide BES12 Cloud Published: 2016-04-08 SWD-20160408113328879 Contents About this guide... 6 Getting started... 7 Configuring BES12 for the first time...7 Administrator permissions you need
How to integrate RSA ACE Server SecurID Authentication with Juniper Networks Secure Access SSL VPN (SA) with Single Node or Cluster (A/A or A/P)
 How to integrate RSA ACE Server SecurID Authentication with Juniper Networks Secure Access SSL VPN (SA) with Single Node or Cluster (A/A or A/P) Scenario # 1: Single Node or Standalone SA... 2 Scenario
How to integrate RSA ACE Server SecurID Authentication with Juniper Networks Secure Access SSL VPN (SA) with Single Node or Cluster (A/A or A/P) Scenario # 1: Single Node or Standalone SA... 2 Scenario
Multi-Factor Authentication Job Aide
 To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
To start your account configuration and begin using Multi-Factor Authentication, log in to the CCHMC Multi-Factor Authentication User Portal at https://mfa.cchmc.org/multifactorauth. For assistance, please
Software Version 1.0 ConnectKey TM Share to Cloud April 2013. Xerox ConnectKey Share to Cloud User / Administrator s Guide
 Software Version 1.0 ConnectKey TM Share to Cloud April 2013 Xerox ConnectKey Share to Cloud User / Administrator s Guide 2013 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, and Xerox
Software Version 1.0 ConnectKey TM Share to Cloud April 2013 Xerox ConnectKey Share to Cloud User / Administrator s Guide 2013 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, and Xerox
Log Correlation Engine 4.6 Quick Start Guide. January 25, 2016 (Revision 2)
 Log Correlation Engine 4.6 Quick Start Guide January 25, 2016 (Revision 2) Table of Contents Introduction... 4 Standards and Conventions... 4 Product Overview... 4 Prerequisites... 4 LCE Quick Start...
Log Correlation Engine 4.6 Quick Start Guide January 25, 2016 (Revision 2) Table of Contents Introduction... 4 Standards and Conventions... 4 Product Overview... 4 Prerequisites... 4 LCE Quick Start...
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.0.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.0.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
OSF INTEGRATOR for. Integration Guide
 OSF INTEGRATOR for DEMANDWARE and MICROSOFT DYNAMICS CRM 2013 Integration Guide Table of Contents 1 Summary... 3 2 Component Overview... 3 2.1 Functional Overview... 3 2.2 Integration components... 3 2.3
OSF INTEGRATOR for DEMANDWARE and MICROSOFT DYNAMICS CRM 2013 Integration Guide Table of Contents 1 Summary... 3 2 Component Overview... 3 2.1 Functional Overview... 3 2.2 Integration components... 3 2.3
Bentley CONNECT Dynamic Rights Management Service
 v1.0 Implementation Guide Last Updated: March 20, 2013 Table of Contents Notices...5 Chapter 1: Introduction to Management Service...7 Chapter 2: Configuring Bentley Dynamic Rights...9 Adding Role Services
v1.0 Implementation Guide Last Updated: March 20, 2013 Table of Contents Notices...5 Chapter 1: Introduction to Management Service...7 Chapter 2: Configuring Bentley Dynamic Rights...9 Adding Role Services
Flexible Identity. LDAP Synchronization Agent guide. Bronze. version 1.2
 Flexible Identity Bronze LDAP Synchronization Agent guide version 1.2 publication history Date Description Revision 2014.06.27 initial release 1.0 2014.11.24 rebranding 1.1 2015.04.16 LDAP synchronization
Flexible Identity Bronze LDAP Synchronization Agent guide version 1.2 publication history Date Description Revision 2014.06.27 initial release 1.0 2014.11.24 rebranding 1.1 2015.04.16 LDAP synchronization
IDS and Penetration Testing Lab ISA656 (Attacker)
 IDS and Penetration Testing Lab ISA656 (Attacker) Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible
IDS and Penetration Testing Lab ISA656 (Attacker) Ethics Statement Network Security Student Certification and Agreement I,, hereby certify that I read the following: University Policy Number 1301: Responsible
MultiSite Manager. User Guide
 MultiSite Manager User Guide Contents 1. Getting Started... 2 Opening the MultiSite Manager... 2 Navigating MultiSite Manager... 2 2. The All Sites tabs... 3 All Sites... 3 Reports... 4 Licenses... 5 3.
MultiSite Manager User Guide Contents 1. Getting Started... 2 Opening the MultiSite Manager... 2 Navigating MultiSite Manager... 2 2. The All Sites tabs... 3 All Sites... 3 Reports... 4 Licenses... 5 3.
Configuring Single Sign-On from the VMware Identity Manager Service to Office 365
 Configuring Single Sign-On from the VMware Identity Manager Service to Office 365 VMware Identity Manager JULY 2015 V1 Table of Contents Overview... 2 Passive and Active Authentication Profiles... 2 Adding
Configuring Single Sign-On from the VMware Identity Manager Service to Office 365 VMware Identity Manager JULY 2015 V1 Table of Contents Overview... 2 Passive and Active Authentication Profiles... 2 Adding
Cisco ASA Authentication QUICKStart Guide
 Cisco ASA Authentication QUICKStart Guide Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights reserved.
Cisco ASA Authentication QUICKStart Guide Powerful Authentication Management for Service Providers and Enterprises Authentication Service Delivery Made EASY Copyright 2012 SafeNet, Inc. All rights reserved.
SevOne NMS Download Installation and Implementation Guide
 SevOne NMS Download Installation and Implementation Guide 5.3.X 530 V0002 Contents 1. Get Started... 3 2. SevOne Download Installation... 6 3. Appliance Network Configuration... 9 4. Install License and
SevOne NMS Download Installation and Implementation Guide 5.3.X 530 V0002 Contents 1. Get Started... 3 2. SevOne Download Installation... 6 3. Appliance Network Configuration... 9 4. Install License and
Setting Up Sharp MX-Color Imagers To Scan To Email
 Setting Up Sharp MX-Color Imagers To Scan To Email MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, MX-M850, MX-M950, MX-M1100 Step 1. Click Start > Run
Setting Up Sharp MX-Color Imagers To Scan To Email MX-2300, MX-2600, MX-2700, MX-3100, MX-3501, MX-4501, MX-5500, MX-6200, MX-6201, MX-7000, MX-7001, MX-M850, MX-M950, MX-M1100 Step 1. Click Start > Run
