Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9)
|
|
|
- Barbara Dalton
- 10 years ago
- Views:
Transcription
1 Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9)
2 Table of Contents Introduction... 3 Nessus Perimeter Service... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning Interface... 5 Scan Policies... 5 Creating and Launching a Scan... 7 Scheduling a Scan... 7 Managing Scans... 8 Viewing Scan Results... 9 Reviewing Scan Results... 9 PCI ASV Validation Submitting Scan Results for PCI Customer Review Customer Review Interface Reviewing Scan Results Disputing Scan Results Submitting Attachments as Evidence for a Dispute Submitting a Scan Report for Tenable Review PCI ASV Report Formats Support Changing Your Password For More Information About Tenable Network Security
3 Introduction This document describes Tenable Network Security s Nessus Perimeter Service. Please any comments and suggestions to [email protected]. This document covers the Nessus Perimeter Service as used for vulnerability scanning, assessment, and reporting. The contents of this document include the processes of Perimeter Service subscription and activation, customer scan initiation, vulnerability and compliance reporting, PCI ASV validation, and Perimeter Service support. The Nessus Perimeter Service is available in both Flash and HTML5 interfaces. This document describes the HTML5 interface. If you are using the Flash interface, which is the default only for the Microsoft Internet Explorer browser, please refer to the Nessus Perimeter Service User Guide (Flash Interface) document available through the Tenable Support Portal. A basic understanding of Tenable s Nessus vulnerability scanner, network protocols, vulnerability analysis and remediation, and cloud-based services is assumed. Important notes and considerations are highlighted with this symbol and grey text boxes. Tips, examples, and best practices are highlighted with this symbol and white on blue text. Nessus Perimeter Service The Nessus Perimeter Service is an enterprise-class remote vulnerability scanning service that may be used to audit Internet-facing IP addresses for both network and web application vulnerabilities from the cloud. Subscribers, who log in to Nessus scanners hosted in Tenable's secure data center, may employ the Nessus Perimeter Service to scan any number of Internet-facing sites covering a wide variety of devices enterprise servers, desktop computers, mobile laptops, iphones wherever is convenient and as often as needed, all for one flat fee. The Nessus Perimeter Service portal provides secure access to detailed vulnerability audits and remediation information hosted on Tenable s infrastructure. The Nessus Perimeter Service can be accessed from any computer with Internet access and a standard web browser, as well as from mobile devices including Android and iphone/ipad, providing fixed or mobile scanner command and control, plus access to vulnerability and compliance reports from anywhere, anytime. The Nessus Perimeter Service is supported by a world renowned research team and has the industry s largest vulnerability knowledge base, making it suitable for even the most complex audits. Subscription and Activation Tenable s Nessus Perimeter Service is available as an annual subscription. Subscriptions are available through the Tenable Store. For pricing, please visit the Tenable Store or inquire at [email protected] for more information. A Nessus Perimeter Service subscription package includes: Unlimited scanning of your perimeter systems Web application audits Ability to prepare for security assessments against current PCI standards Up to 2 quarterly report submissions for PCI ASV validation through Tenable Network Security, Inc. 24/7 access to the Tenable Support Portal for access to Nessus knowledgebase and support ticket creation One user account per subscription 3
4 Upon purchase of a Nessus Perimeter Service subscription, Tenable Product Delivery will notify the customer of product availability via . The notification will also include the customer s order number, product expiration date, and a product activation link. An activation help document is available online at: If you experience any problems with the activation process, please contact [email protected]. You must include your Customer ID with any inquiry. If you do not have a Customer ID, please include your order number to receive the proper assistance. Multi Scanner Support The Multi Scanner functionality gives your Nessus scanner the ability to delegate vulnerability scanning to multiple secondary servers, or be delegated to perform scans for another. You can use your own Nessus server to act as the primary, or you can configure your Nessus Perimeter Service scanner in the cloud to be the primary. This allows for consolidated reporting in a single Nessus user interface with scheduled scanning and ing results. The use of this functionality positions companies to create an extended network of Nessus scanners that give added value. Through strategic positioning of the scanners, you are able to not only test for vulnerabilities and misconfigurations, but also examine the system from different viewpoints on the network. This can greatly assist you in ensuring that network screening devices (e.g., firewalls, routers) are properly restricting access to a given system. It is important to note that primary scanners do not reach out to the secondary scanners. Instead, secondary scanners periodically poll the primary scanner they are registered with to receive new instructions. When deploying a network of Nessus scanners using this functionality, this must be kept in mind to ensure that nothing will hinder the secondary scanner in connecting to its primary. 4
5 Customer Scanning Interface Customers who subscribe to the Nessus Perimeter Service interact with a secure web-based portal. To access the service, all customers require credentials to the portal that are provided by Tenable Network Security upon purchase of the service. The following screen capture displays the portal login page, which offers Nessus HTML5 user interface by default: Initial Nessus Perimeter Service Login Screen For more information on using the Nessus Perimeter Service with the older Flash interface, refer to the Nessus Perimeter Service User Guide (Flash Interface) document, which is available through the Tenable Support Portal. Scan Policies Once logged into the service, Nessus Perimeter Service customers have the option to select one of seven preset scan policies: Perimeter Scan (exhaustive) This policy will use more bandwidth but will find all external TCP-based services hosted in an externally facing network. This policy contains the default settings that will perform an exhaustive perimeter scan: - A fast port scan of 65,536 TCP ports - CGI checks are enabled - Web Application checks are disabled - Low false positives Perimeter Scan (fast) This is an ideal policy to perform as an initial scan. This policy contains the default settings that will perform a quick perimeter scan: - A fast port scan checking the most common 8,000 TCP ports - CGI checks are enabled - Web Application checks are disabled 5
6 - Low false positives Web App Tests (exhaustive) This policy will perform a web application test on the remote host. The application(s) will be tested for custom vulnerabilities, use the all pairs method for argument testing, check all parameters of each page, and run for a maximum of 24 hours. Web App Tests (fast) This policy will perform a web application test on the remote host. The application will be tested for custom vulnerabilities, use the all pairs method for argument testing, check all parameters of each page, and run for a maximum of 2 hours. PCI-DSS ASV Scan This policy may be used by Perimeter Service customers who wish to perform external vulnerability scans that may be used in a PCI DSS compliance validation effort. More information about performing scans using the PCI DSS ASV Scan policy and scan validation through Tenable s PCI ASV service can be found later in this document. PCI-DSS ASV Scan (low bandwidth) This policy is identical to the PCI DSS ASV Scan policy with the exception of the max_hosts setting, which is set to 2 in order to limit the amount of bandwidth used by Nessus Perimeter Service scans. PCI-DSS ASV Scan (unresponsive hosts) This policy is identical to the PCI DSS ASV Scan policy with the exception of the Ping Host setting, which is disabled to allow Nessus Perimeter Service scans to roll over into different scanning options instead of ceasing to scan a host due to the host being unresponsive to a remote ping. These policies are regularly reviewed and updated by Tenable staff to ensure that they include updates to plugin families and other enhancements to settings. Customers do not have the ability to view or alter any of the preset parameters of the PCI DSS policy. Instead of directly editing preset scan policies, it is highly recommended to make a copy of a preset scan policy and edit the copy. If a preset scan policy has been directly edited, ownership of the policy will change from admin to the Nessus Perimeter Service user and the original settings cannot be automatically restored. The Upload button will allow you to upload previously created policies to the Perimeter Service scanner. Using the Browse dialog box, select the policy from your local system, and click Submit. 6
7 Creating and Launching a Scan To create a scan, a Nessus Perimeter Service customer enters the Scans section of the service and selects New Scan. The customer then enters a unique name for the scan, the type of scan, selects the policy, and enters the IP address(es), IP range(s), or hostnames of their externally-facing servers that will be the target of the scan. Click Launch to initiate the new scan immediately. Note that the Scanner option will only appear if secondary scanners have been configured. To set up secondary scanners that can be used to conduct scans on behalf of the perimeter scanner, please consult the Nessus 5.2 HTML5 User Guide. More information on the use of additional scanners and the network flow can be found below in the section titled Multi Scanner Support. Scheduling a Scan To initiate a scan as a template, start by creating a new scan via the Scans menu or the Schedules menu. After filling out the basic settings, select Schedule Settings and select the frequency: 7
8 Once saved, the scheduled scans can be accessed through the Schedules menu at the top: Managing Scans Once started, scans can be paused or stopped during the scan process by using the pause or stop icon to the right of the scan: 8
9 Viewing Scan Results Results obtained from a scan that is currently in progress can be viewed by selecting the Scans menu and clicking on the scan that is running or completed: Reviewing Scan Results Once a scan has completed, the status will appear under the Scans section along with the date and time that the scan was either last updated or completed. The customer has the option to browse the scan or download the report in a variety of formats, including the.nessus, CSV, PDF, HTML, and Nessus DB file formats. 9
10 Completed Scan in Vulnerabilities View 10
11 Export Option to Download Current Scan The HTML report download format allows for the selection of chapter types within the report. Select HTML as the export format, and then click on the chapters to include in the report output: 11
12 HTML Report Output for Hosts Summary (Executive) Customers are not limited in the number of scans they can perform and reports they can generate during an active subscription to the Nessus Perimeter Service. Detailed information on Nessus policies, scanning, and reporting can be found in the Nessus User Guide available here: PCI ASV Validation Tenable Network Security, Inc. is a PCI Approved Scanning Vendor (ASV), and is certified to validate vulnerability scans of Internet-facing systems for adherence to certain aspects of the PCI Data Security Standards (PCI DSS). The Nessus Perimeter Service includes a pre-built static PCI DSS policy that adheres to the quarterly scanning requirements of the PCI DSS v2.0. This policy may be used by merchants and providers to initially assess their environments based on PCI DSS requirements, and also to perform external vulnerability scans and generate reports that can be validated by qualified Tenable Network Security staff members for the PCI DSS ASV validation requirement. It is important to note that, while customers can use the PCI DSS scan policy to test their externally-facing systems as often as they wish, a scan must be submitted to Tenable for validation before it can be considered to qualify as a valid PCI ASV scan. Customers are allowed up to two quarterly report submissions for PCI ASV validation through Tenable Network Security, Inc. Once logged into the service, customers have the option to select a policy titled PCI DSS that adheres to the requirements of the PCI ASV Program Guide v2.0 section titled ASV Scan Solution Required Components. Customers do not have the ability to alter any of the preset parameters of this policy. To qualify as a PCI DSS ASV scan for validation through the Nessus Perimeter Service, one of the three PCI- DSS policies must be selected. 12
13 Submitting Scan Results for PCI Customer Review Customers have the option to submit their scan results to Tenable Network Security for PCI ASV validation. By clicking Submit for PCI, the scan results will be uploaded to an administrative section of the Nessus Perimeter Service (the PCI Scanning Service) for customer review, and the customer will be prompted to log in to the user section of the service to review the findings of the scan results from a PCI DSS perspective. Link to Submit for PCI (highlighted in red) Report Upload and PCI Scanning Service Link Dialog Box 13
14 Customers are strongly urged to thoroughly review their PCI scan results before submitting their report(s) to Tenable Network Security through the PCI Scanning Service. Reports with failed results are required to undergo a full PCI Scanning Service review cycle, of which Nessus Perimeter Service customers are limited to two (2) per quarterly period. Customer Review Interface PCI Scanning Service Customer Login Screen Once a customer logs into the PCI Validation user section, they are presented with a list of reports that have been submitted by their unique Nessus Perimeter Service login. The Report Filter allows reports to be filtered by Owner, Name, and Status. 14
15 Reviewing Scan Results To pass a PCI DSS ASV assessment, all items (except for denial of service (DoS) vulnerabilities) listed as Critical, High, or Medium (or with a CVSS score of 4.0 or higher) must either be remediated or disputed by the customer, and all disputed items must either be resolved, accepted as exceptions, accepted as false positives, or mitigated through the use of compensating controls. All items listed as Critical, High, or Medium in the Nessus Perimeter Service can be viewed in detail, and all items carry an option to dispute the item in question. Clicking the name of the scan in the List of Reports allows the user to view a list of hosts and the number of vulnerabilities found on each host, sorted by severity. Clicking the number of Failed Items in the List of Reports will display a list of items that will need to be addressed in order to qualify for a compliant ASV report through Tenable s PCI Scanning Service. Nessus Perimeter Service/PCI Scanning Service customers are responsible for reviewing all of their Failed Items before submitting a scan report to Tenable Network Security. Selecting the Failed Items in the List of Reports allows you to jump directly to the items that may affect your PCI ASV Validation compliance status. 15
16 Use the green + button under the far left column to expand an individual entry for additional vulnerability details. Scan Report Item Description with Dispute Functionality As shown above, a Dispute button is displayed for each individual item, which allows the customer to enter additional details about vulnerability remediation, or dispute what they believe may be a false positive generated by the initial scan. 16
17 Disputing Scan Results When an item is disputed, a ticket is created that allows for the selection of an amendment type, the addition of text to the amendment, and any other notes that the customer may want to add prior to submission for review by Tenable Network Security. Once a ticket for a particular item has been created, the customer can view it by selecting the item in question and then selecting View Ticket. 17
18 Scan Report Item Description with View Ticket Functionality 18
19 Additional comments can be added by clicking the Edit button, then Add Note, and saving the note into the ticket by clicking Update. 19
20 Plugin 33929, PCI DSS Compliance, is an administrative plugin that links to the results of other plugins. If a report shows that a host is not PCI DSS compliant, resolving all failed items will then allow plugin to resolve and be replaced with plugin 33930, PCI DSS Compliance: Passed. In cases of disputes or exceptions, if all failed report items are successfully disputed or given exceptions, an exception can then be given for plugin based on the remediation of all other report issues. Submitting Attachments as Evidence for a Dispute Once a ticket is created, it is possible to submit supporting evidence as an attachment. After creating a ticket, click the number listed under Open Tickets to display all open tickets: 20
21 In the List of Tickets screen, click View : When the screen for the open ticket is displayed, options for Upload File and Attach are displayed: Click Browse to navigate to and select the evidence file (screenshot, Word document, PDF, etc.) to be uploaded: Sample Evidence File (no_shiro.png) 21
22 Next, click Attach to attach the file to the ticket. When completed, the screen will display a message that the file was uploaded successfully: Clicking the Download link next to Attachments will show the names of all files attached to the ticket: Submitting a Scan Report for Tenable Review When tickets have been created for all outstanding report items under user review, the report can then be sent to Tenable Network Security for ASV review. Before a report can be submitted for review, the customer must fill in contact information and agree to an attestation that includes mandatory text as described in the ASV Program Guide. 22
23 Report Submission Attestation Text If a customer neglects to address any outstanding item for a particular scan before the report is submitted for ASV review, they will be prompted to make sure that a ticket has been created for each item. Any report with outstanding items that have not been addressed by the customer cannot be submitted to Tenable Network Security for review. 23
24 When a report is finally submitted to Tenable Network Security for review, the status of the report changes from Under User Review to Under Admin Review and the Submit option is removed (greyed out) to prevent the submission of duplicate items or reports. Submitted Report Under Admin Review The Withdraw function within an open ticket is only available once a report has been submitted for review by Tenable s PCI Scanning Service. Be careful when using the Withdraw function; withdrawing a ticket will cause the item in question to be flagged as unresolved due to having inconclusive evidence, and the report as a whole will be deemed as non-compliant. If a Tenable Network Security staff member requests more information or if any other user action is required by the customer for a ticket, an indicator will appear in the customer s List of Reports as shown below: User Action Required Notification 24
25 The ticket can then be amended by the user and resubmitted to Tenable Network Security for further review. PCI ASV Report Formats Once a scan report has earned compliance status by Tenable s PCI Scanning Service, customers have the option of viewing reports in Attestation Report, Executive Report, or Detailed Report formats. An ASV Feedback Form is also provided to the Nessus Perimeter Service customer. These options are available through the Download icon listed next to each report. The Attestation Report, Executive Report, and Details Report are only available to the customer in PDF format and cannot be edited. 25
26 Sample Attestation Report 26
27 Sample Executive Report When a report name and then host name is selected within the web-based interface, a list of items pertaining to the selected report is displayed. List of Items Displayed in the Web Interface 27
28 Support When a Tenable Nessus Perimeter Service subscription is purchased, the name(s) and address(es) of your Technical Contact Person(s) is provided to Tenable. A separate Tenable Support Portal account is automatically created for each Technical Contact Person. Support requests are accepted via the Tenable Support Portal, or an may be sent to [email protected]. Note that requests must be sent from one of the addresses provided to Tenable as a support contact. Changing Your Password If you need to change your Nessus Perimeter Service password, click on your address in the upper right hand side of the scanner screen and chose the User Profile option in the drop-down list. After changing your password, a dialogue will display confirming: For More Information Nessus documentation can be found here: More information about the Tenable Support Portal features can be found here: If you experience any problems with the registration process, please contact [email protected]. The Nessus Perimeter Service is supported by only. Please direct all support related questions to [email protected] and provide your Customer ID with a detailed description of the issue you are having. You may also log in to the Tenable Support Portal to generate a support ticket. 28
29 About Tenable Network Security Tenable Network Security is relied upon by more than 20,000 organizations, including the entire U.S. Department of Defense and many of the world s largest companies and governments, to stay ahead of emerging vulnerabilities, threats and compliance-related risks. Its Nessus and SecurityCenter solutions continue to set the standard to identify vulnerabilities, prevent attacks and comply with a multitude of regulatory requirements. For more information, please visit GLOBAL HEADQUARTERS Tenable Network Security 7021 Columbia Gateway Drive Suite 500 Columbia, MD Copyright Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security, Inc. 29
Nessus Enterprise Cloud User Guide. October 2, 2014 (Revision 9)
 Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure
 Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Nessus Cloud User Registration
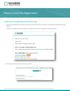 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Configuring Virtual Switches for Use with PVS. February 7, 2014 (Revision 1)
 Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
Tenable Network Security Support Portal. January 12, 2015 (Revision 14)
 Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
PCI Compliance. Network Scanning. Getting Started Guide
 PCI Compliance Getting Started Guide Qualys PCI provides businesses, merchants and online service providers with the easiest, most cost effective and highly automated way to achieve compliance with the
PCI Compliance Getting Started Guide Qualys PCI provides businesses, merchants and online service providers with the easiest, most cost effective and highly automated way to achieve compliance with the
GETTING STARTED WITH THE PCI COMPLIANCE SERVICE VERSION 2.3. May 1, 2008
 GETTING STARTED WITH THE PCI COMPLIANCE SERVICE VERSION 2.3 May 1, 2008 Copyright 2006-2008 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys,
GETTING STARTED WITH THE PCI COMPLIANCE SERVICE VERSION 2.3 May 1, 2008 Copyright 2006-2008 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys,
Patch Management Integration
 Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide. July 16, 2014 (Revision 2)
 Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
TRIPWIRE PURECLOUD. TRIPWIRE PureCloud USER GUIDE
 TRIPWIRE PURECLOUD TRIPWIRE PureCloud USER GUIDE 2001-2015 Tripwire, Inc. All rights reserved. Tripwire and ncircle are registered trademarks of Tripwire, Inc. Other brand or product names may be trademarks
TRIPWIRE PURECLOUD TRIPWIRE PureCloud USER GUIDE 2001-2015 Tripwire, Inc. All rights reserved. Tripwire and ncircle are registered trademarks of Tripwire, Inc. Other brand or product names may be trademarks
SecurityCenter 5.1 with Nessus Agent Support. October 22, 2015
 SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
EMC Smarts Network Configuration Manager
 EMC Smarts Network Configuration Manager Version 9.4.1 Advisors User Guide P/N 302-002-279 REV 01 Copyright 2013-2015 EMC Corporation. All rights reserved. Published in the USA. Published October, 2015
EMC Smarts Network Configuration Manager Version 9.4.1 Advisors User Guide P/N 302-002-279 REV 01 Copyright 2013-2015 EMC Corporation. All rights reserved. Published in the USA. Published October, 2015
Nipper Studio Beginner s Guide
 Nipper Studio Beginner s Guide Multiple Award Winning Security Software Version 2.1 Published March 2015 Titania Limited 2014. All Rights Reserved This document is intended to provide advice and assistance
Nipper Studio Beginner s Guide Multiple Award Winning Security Software Version 2.1 Published March 2015 Titania Limited 2014. All Rights Reserved This document is intended to provide advice and assistance
Tenable for CyberArk
 HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
TRUSTWAVE VULNERABILITY MANAGEMENT USER GUIDE
 .trust TRUSTWAVE VULNERABILITY MANAGEMENT USER GUIDE 2007 Table of Contents Introducing Trustwave Vulnerability Management 3 1 Logging In and Accessing Scans 4 1.1 Portal Navigation and Utility Functions...
.trust TRUSTWAVE VULNERABILITY MANAGEMENT USER GUIDE 2007 Table of Contents Introducing Trustwave Vulnerability Management 3 1 Logging In and Accessing Scans 4 1.1 Portal Navigation and Utility Functions...
Simplêfy Client Support and Information Services. PCI Compliance Guidebook
 Simplêfy Client Support and Information Services PCI Compliance Guidebook Simplêfy, Inc. 301 Science Drive, Suite 280 Moorpark, CA 93021 Phone 888.341.2999 Fax 877.280.0885 Simplêfy is a Registered Trademark
Simplêfy Client Support and Information Services PCI Compliance Guidebook Simplêfy, Inc. 301 Science Drive, Suite 280 Moorpark, CA 93021 Phone 888.341.2999 Fax 877.280.0885 Simplêfy is a Registered Trademark
Web Application Vulnerability Testing with Nessus
 The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP [email protected] Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP [email protected] Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
FAQ S: TRUSTWAVE TRUSTKEEPER PCI MANAGER
 FAQ S: TRUSTWAVE TRUSTKEEPER PCI MANAGER SAQ FAQ S Q: Should I complete the PCI Wizard or should I go straight to the PCI Forms? A: The PCI Wizard has been designed to simplify the self-assessment requirement
FAQ S: TRUSTWAVE TRUSTKEEPER PCI MANAGER SAQ FAQ S Q: Should I complete the PCI Wizard or should I go straight to the PCI Forms? A: The PCI Wizard has been designed to simplify the self-assessment requirement
SecurityCenter 4.4 Administration Guide
 SecurityCenter 4.4 Administration Guide September 18, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_admin_guide.pdf
SecurityCenter 4.4 Administration Guide September 18, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_admin_guide.pdf
3D Tool 2.0 Quick Start Guide
 www.tenable.com [email protected] 3D Tool 2.0 Quick Start Guide ABOUT THE 3D TOOL Tenable s 3D Tool is a Windows application that is used to query data from a SecurityCenter 4 server and present it in
www.tenable.com [email protected] 3D Tool 2.0 Quick Start Guide ABOUT THE 3D TOOL Tenable s 3D Tool is a Windows application that is used to query data from a SecurityCenter 4 server and present it in
rating of 5 out 5 stars
 SPM User Guide Contents Aegify comprehensive benefits... 2 Security Posture Assessment workflow... 3 Scanner Management... 3 Upload external scan output... 6 Reports - Views... 6 View Individual Security
SPM User Guide Contents Aegify comprehensive benefits... 2 Security Posture Assessment workflow... 3 Scanner Management... 3 Upload external scan output... 6 Reports - Views... 6 View Individual Security
Unified Security Management (USM) 5.2 Vulnerability Assessment Guide
 AlienVault Unified Security Management (USM) 5.2 Vulnerability Assessment Guide USM 5.2 Vulnerability Assessment Guide, rev 1 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
AlienVault Unified Security Management (USM) 5.2 Vulnerability Assessment Guide USM 5.2 Vulnerability Assessment Guide, rev 1 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
System Administration Training Guide. S100 Installation and Site Management
 System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
System Administration Training Guide S100 Installation and Site Management Table of contents System Requirements for Acumatica ERP 4.2... 5 Learning Objects:... 5 Web Browser... 5 Server Software... 5
VULNERABILITY MANAGEMENT
 Vulnerability Management (VM) software differ in the richness of reporting, and the capabilities for application and security configuration assessment. Companies must consider how a VM technology will
Vulnerability Management (VM) software differ in the richness of reporting, and the capabilities for application and security configuration assessment. Companies must consider how a VM technology will
Defender 5.7 - Token Deployment System Quick Start Guide
 Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Qualys Scanning for PCI Devices University of Minnesota
 Qualys is the vulnerability scanner that will be used to map and scan devices that are involved in credit card processing to meet the PCI-DSS quarterly internal scan and map requirement. This document
Qualys is the vulnerability scanner that will be used to map and scan devices that are involved in credit card processing to meet the PCI-DSS quarterly internal scan and map requirement. This document
ReadyNAS Remote. User Manual. June 2013 202-11078-03. 350 East Plumeria Drive San Jose, CA 95134 USA
 User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
User Manual June 2013 202-11078-03 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for selecting this NETGEAR product. After installing your device, locate the serial number on the label
IBM. Vulnerability scanning and best practices
 IBM Vulnerability scanning and best practices ii Vulnerability scanning and best practices Contents Vulnerability scanning strategy and best practices.............. 1 Scan types............... 2 Scan duration
IBM Vulnerability scanning and best practices ii Vulnerability scanning and best practices Contents Vulnerability scanning strategy and best practices.............. 1 Scan types............... 2 Scan duration
Citrix Virtual Classroom. Deliver file sharing and synchronization services using Citrix ShareFile. Self-paced exercise guide
 Deliver file sharing and synchronization services using Citrix ShareFile Self-paced exercise guide Table of Contents Table of Contents... 2 Overview... 3 Exercise 1: Setting up a ShareFile Account... 6
Deliver file sharing and synchronization services using Citrix ShareFile Self-paced exercise guide Table of Contents Table of Contents... 2 Overview... 3 Exercise 1: Setting up a ShareFile Account... 6
How To Use Senior Systems Cloud Services
 Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Senior Systems Cloud Services In this guide... Senior Systems Cloud Services 1 Cloud Services User Guide 2 Working In Your Cloud Environment 3 Cloud Profile Management Tool 6 How To Save Files 8 How To
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Security Scanning Procedures Version 1.1 Release: September 2006 Table of Contents Purpose...1 Introduction...1 Scope of PCI Security Scanning...1 Scanning
Payment Card Industry (PCI) Data Security Standard Security Scanning Procedures Version 1.1 Release: September 2006 Table of Contents Purpose...1 Introduction...1 Scope of PCI Security Scanning...1 Scanning
Web Application Firewall
 Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
Web Application Firewall Getting Started Guide August 3, 2015 Copyright 2014-2015 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other trademarks
IBM Security QRadar SIEM Version 7.1.0 MR1. Vulnerability Assessment Configuration Guide
 IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
WildFire Reporting. WildFire Administrator s Guide 55. Copyright 2007-2015 Palo Alto Networks
 WildFire Reporting When malware is discovered on your network, it is important to take quick action to prevent spread of the malware to other systems. To ensure immediate alerts to malware discovered on
WildFire Reporting When malware is discovered on your network, it is important to take quick action to prevent spread of the malware to other systems. To ensure immediate alerts to malware discovered on
Copyright 2012 Trend Micro Incorporated. All rights reserved.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
SecurityCenter 4.2 Administration Guide
 SecurityCenter 4.2 Administration Guide January 24, 2012 (Revision 5) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.2_admin_guide.pdf
SecurityCenter 4.2 Administration Guide January 24, 2012 (Revision 5) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.2_admin_guide.pdf
MultiSite Manager. User Guide
 MultiSite Manager User Guide Contents 1. Getting Started... 2 Opening the MultiSite Manager... 2 Navigating MultiSite Manager... 2 2. The All Sites tabs... 3 All Sites... 3 Reports... 4 Licenses... 5 3.
MultiSite Manager User Guide Contents 1. Getting Started... 2 Opening the MultiSite Manager... 2 Navigating MultiSite Manager... 2 2. The All Sites tabs... 3 All Sites... 3 Reports... 4 Licenses... 5 3.
Payment Card Industry Data Security Standard
 Symantec Managed Security Services support for IT compliance Solution Overview: Symantec Managed Services Overviewview The (PCI DSS) was developed to facilitate the broad adoption of consistent data security
Symantec Managed Security Services support for IT compliance Solution Overview: Symantec Managed Services Overviewview The (PCI DSS) was developed to facilitate the broad adoption of consistent data security
Qualys PC/SCAP Auditor
 Qualys PC/SCAP Auditor Getting Started Guide August 3, 2015 COPYRIGHT 2011-2015 BY QUALYS, INC. ALL RIGHTS RESERVED. QUALYS AND THE QUALYS LOGO ARE REGISTERED TRADEMARKS OF QUALYS, INC. ALL OTHER TRADEMARKS
Qualys PC/SCAP Auditor Getting Started Guide August 3, 2015 COPYRIGHT 2011-2015 BY QUALYS, INC. ALL RIGHTS RESERVED. QUALYS AND THE QUALYS LOGO ARE REGISTERED TRADEMARKS OF QUALYS, INC. ALL OTHER TRADEMARKS
Nessus Agents. October 2015
 Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NMS300 Network Management System
 NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
NMS300 Network Management System User Manual June 2013 202-11289-01 350 East Plumeria Drive San Jose, CA 95134 USA Support Thank you for purchasing this NETGEAR product. After installing your device, locate
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
Getting Started With Halo for Windows
 Getting Started With Halo for Windows For CloudPassage Halo Protecting your Windows servers in a public or private cloud is much easier and more secure with CloudPassage Halo for Windows. Halo for Windows
Getting Started With Halo for Windows For CloudPassage Halo Protecting your Windows servers in a public or private cloud is much easier and more secure with CloudPassage Halo for Windows. Halo for Windows
SOA Software API Gateway Appliance 7.1.x Administration Guide
 SOA Software API Gateway Appliance 7.1.x Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names,
SOA Software API Gateway Appliance 7.1.x Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names,
AUTOMATING AUDITS AND ENSURING CONTINUOUS COMPLIANCE WITH ALGOSEC
 AUTOMATING AUDITS AND ENSURING CONTINUOUS COMPLIANCE WITH ALGOSEC MANAGE SECURITY AT THE SPEED OF BUSINESS AlgoSec Whitepaper Simplifying PCI-DSS Audits and Ensuring Continuous Compliance with AlgoSec
AUTOMATING AUDITS AND ENSURING CONTINUOUS COMPLIANCE WITH ALGOSEC MANAGE SECURITY AT THE SPEED OF BUSINESS AlgoSec Whitepaper Simplifying PCI-DSS Audits and Ensuring Continuous Compliance with AlgoSec
Plesk 11 Manual. Fasthosts Customer Support
 Fasthosts Customer Support Plesk 11 Manual This guide covers everything you need to know in order to get started with the Parallels Plesk 11 control panel. Contents Introduction... 3 Before you begin...
Fasthosts Customer Support Plesk 11 Manual This guide covers everything you need to know in order to get started with the Parallels Plesk 11 control panel. Contents Introduction... 3 Before you begin...
How To Import Credit Card Charges Into Concur
 Importing Credit Card Expenses into Concur For faster expense reporting and less manual data entry, try importing your credit card charges into Concur. Step 1: Download Credit Card Data Log onto your credit
Importing Credit Card Expenses into Concur For faster expense reporting and less manual data entry, try importing your credit card charges into Concur. Step 1: Download Credit Card Data Log onto your credit
REMOTE ACCESS DDNS CONFIGURATION MANUAL
 REMOTE ACCESS DDNS CONFIGURATION MANUAL Analog DVR Series 1 www.mezory.com INTRODUCTION TO REMOTE ACCESS As the World sinks into one global village, reliable connectivity is one of the most demanding facilities
REMOTE ACCESS DDNS CONFIGURATION MANUAL Analog DVR Series 1 www.mezory.com INTRODUCTION TO REMOTE ACCESS As the World sinks into one global village, reliable connectivity is one of the most demanding facilities
Backups User Guide. for Webroot SecureAnywhere Essentials Webroot SecureAnywhere Complete
 Backups User Guide for Webroot SecureAnywhere Essentials Webroot SecureAnywhere Complete Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Version 8.0.1 Webroot
Backups User Guide for Webroot SecureAnywhere Essentials Webroot SecureAnywhere Complete Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Version 8.0.1 Webroot
User Manual. 3CX VOIP client / Soft phone Version 6.0
 User Manual 3CX VOIP client / Soft phone Version 6.0 Copyright 2006-2008, 3CX ltd. http:// E-mail: [email protected] Information in this document is subject to change without notice. Companies names and data
User Manual 3CX VOIP client / Soft phone Version 6.0 Copyright 2006-2008, 3CX ltd. http:// E-mail: [email protected] Information in this document is subject to change without notice. Companies names and data
Note: With v3.2, the DocuSign Fetch application was renamed DocuSign Retrieve.
 Quick Start Guide DocuSign Retrieve 3.2.2 Published April 2015 Overview DocuSign Retrieve is a windows-based tool that "retrieves" envelopes, documents, and data from DocuSign for use in external systems.
Quick Start Guide DocuSign Retrieve 3.2.2 Published April 2015 Overview DocuSign Retrieve is a windows-based tool that "retrieves" envelopes, documents, and data from DocuSign for use in external systems.
CaseWare Time. CaseWare Cloud Integration Guide. For Time 2015 and CaseWare Cloud
 CaseWare Time CaseWare Cloud Integration Guide For Time 2015 and CaseWare Cloud Copyright and Trademark Notice Copyright. 2015 CaseWare International Inc. ( CWI ). All Rights Reserved. Use, duplication,
CaseWare Time CaseWare Cloud Integration Guide For Time 2015 and CaseWare Cloud Copyright and Trademark Notice Copyright. 2015 CaseWare International Inc. ( CWI ). All Rights Reserved. Use, duplication,
User Management Guide
 AlienVault Unified Security Management (USM) 4.x-5.x User Management Guide USM v4.x-5.x User Management Guide, rev 1 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
AlienVault Unified Security Management (USM) 4.x-5.x User Management Guide USM v4.x-5.x User Management Guide, rev 1 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
Payment Card Industry (PCI) Data Security Standard
 Payment Card Industry (PCI) Data Security Standard Technical and Operational Requirements for Approved Scanning Vendors (ASVs) Version 1.1 Release: September 2006 Table of Contents Introduction...1-1 Naming
Payment Card Industry (PCI) Data Security Standard Technical and Operational Requirements for Approved Scanning Vendors (ASVs) Version 1.1 Release: September 2006 Table of Contents Introduction...1-1 Naming
Anchor End-User Guide
 Table of Contents How to Access Your Account How to Upload Files How to Download the Desktop Sync Folder Sync Folder How to Share a File 3 rd Party Share from Web UI 3 rd Party Share from Sync Folder Team-Share
Table of Contents How to Access Your Account How to Upload Files How to Download the Desktop Sync Folder Sync Folder How to Share a File 3 rd Party Share from Web UI 3 rd Party Share from Sync Folder Team-Share
How to Add, Deactivate, or Edit a Contact
 How to Add, Deactivate, or Edit a Contact Add Contact (Add account option only available to the Primary Contact for the account) 1. Log in to the Tenable Support Portal with authorized credentials: https://support.tenable.com/
How to Add, Deactivate, or Edit a Contact Add Contact (Add account option only available to the Primary Contact for the account) 1. Log in to the Tenable Support Portal with authorized credentials: https://support.tenable.com/
Cypress Connexion HELP Guide www.cypressconnexion.com
 Welcome to Cypress Connexion your one-stop-shop for accessing and managing your Cypress Communications account online, at your convenience. The following guide will provide you with helpful information
Welcome to Cypress Connexion your one-stop-shop for accessing and managing your Cypress Communications account online, at your convenience. The following guide will provide you with helpful information
User Guide. A guide to online services available through Sircon for Education Providers. DOC CX 08/13/10 02/02 v5
 User Guide A guide to online services available through Sircon for Education Providers DOC CX 08/13/10 02/02 v5 Contents Contents Contents... 2 Introduction... 4 About this Guide... 4 Getting Started...
User Guide A guide to online services available through Sircon for Education Providers DOC CX 08/13/10 02/02 v5 Contents Contents Contents... 2 Introduction... 4 About this Guide... 4 Getting Started...
Council of Ontario Universities. COFO Online Reporting System. User Manual
 Council of Ontario Universities COFO Online Reporting System User Manual Updated September 2014 Page 1 Updated September 2014 Page 2 Table of Contents 1. Security... 5 Security Roles Defined in the Application...
Council of Ontario Universities COFO Online Reporting System User Manual Updated September 2014 Page 1 Updated September 2014 Page 2 Table of Contents 1. Security... 5 Security Roles Defined in the Application...
Host Excellence. Client Helpdesk. Version 1.0
 Host Excellence Client Helpdesk Version 1.0 1 Table of Contents 1 Accessing the Helpdesk... 3 2 What Is A Helpdesk Ticket?... 3 3 Ticket Overview... 3 3.1 Ticket Status... 4 3.2 Ticket Category... 4 3.3
Host Excellence Client Helpdesk Version 1.0 1 Table of Contents 1 Accessing the Helpdesk... 3 2 What Is A Helpdesk Ticket?... 3 3 Ticket Overview... 3 3.1 Ticket Status... 4 3.2 Ticket Category... 4 3.3
Nessus and Mobile Device Scanning. November 7, 2014 (Revision 12)
 Nessus and Mobile Device Scanning November 7, 2014 (Revision 12) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 Scanning for Mobile Devices with Nessus... 4 Creating a
Nessus and Mobile Device Scanning November 7, 2014 (Revision 12) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 Scanning for Mobile Devices with Nessus... 4 Creating a
Symantec Database Security and Audit 3100 Series Appliance. Getting Started Guide
 Symantec Database Security and Audit 3100 Series Appliance Getting Started Guide Symantec Database Security and Audit 3100 Series Getting Started Guide The software described in this book is furnished
Symantec Database Security and Audit 3100 Series Appliance Getting Started Guide Symantec Database Security and Audit 3100 Series Getting Started Guide The software described in this book is furnished
WHITEPAPER. Nessus Exploit Integration
 Nessus Exploit Integration v2 Tenable Network Security has committed to providing context around vulnerabilities, and correlating them to other sources, such as available exploits. We currently pull information
Nessus Exploit Integration v2 Tenable Network Security has committed to providing context around vulnerabilities, and correlating them to other sources, such as available exploits. We currently pull information
WatchDox Administrator's Guide. Application Version 3.7.5
 Application Version 3.7.5 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Application Version 3.7.5 Confidentiality This document contains confidential material that is proprietary WatchDox. The information and ideas herein may not be disclosed to any unauthorized individuals
Novell ZENworks Asset Management 7.5
 Novell ZENworks Asset Management 7.5 w w w. n o v e l l. c o m October 2006 USING THE WEB CONSOLE Table Of Contents Getting Started with ZENworks Asset Management Web Console... 1 How to Get Started...
Novell ZENworks Asset Management 7.5 w w w. n o v e l l. c o m October 2006 USING THE WEB CONSOLE Table Of Contents Getting Started with ZENworks Asset Management Web Console... 1 How to Get Started...
SecureAnywhereTM Web Security Service
 SecureAnywhereTM Web Security Service This document provides a general overview of the Webroot SecureAnywhere Web Security Service Partner Management Portal. Webroot Partners such as Managed Service Providers
SecureAnywhereTM Web Security Service This document provides a general overview of the Webroot SecureAnywhere Web Security Service Partner Management Portal. Webroot Partners such as Managed Service Providers
Getting Started Guide: Getting the most out of your Windows Intune cloud
 Getting Started Guide: Getting the most out of your Windows Intune cloud service Contents Overview... 3 Which Configuration is Right for You?... 3 To Sign up or Sign in?... 4 Getting Started with the Windows
Getting Started Guide: Getting the most out of your Windows Intune cloud service Contents Overview... 3 Which Configuration is Right for You?... 3 To Sign up or Sign in?... 4 Getting Started with the Windows
Configuration Information
 Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
IBM Security QRadar Vulnerability Manager Version 7.2.1. User Guide
 IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
QualysGuard WAS. Getting Started Guide Version 4.1. April 24, 2015
 QualysGuard WAS Getting Started Guide Version 4.1 April 24, 2015 Copyright 2011-2015 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
QualysGuard WAS Getting Started Guide Version 4.1 April 24, 2015 Copyright 2011-2015 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
Apollo ACC PCI Registry Export Basics
 Training Apollo ACC PCI Registry Export Basics Barbara O Brien Product Education Trainer Registry Export Assistance Clinical Content Contact the Registry Software Questions LUMEDX Support 1.800.966.0669
Training Apollo ACC PCI Registry Export Basics Barbara O Brien Product Education Trainer Registry Export Assistance Clinical Content Contact the Registry Software Questions LUMEDX Support 1.800.966.0669
Drake Hosted User Guide
 Drake Hosted User Guide Last Revision Date: 11/23/2015 Support.DrakeSoftware.com (828) 524-8020 Drake Hosted User Guide Copyright The Drake Hosted User Guide, Drake Tax Software, and any other related
Drake Hosted User Guide Last Revision Date: 11/23/2015 Support.DrakeSoftware.com (828) 524-8020 Drake Hosted User Guide Copyright The Drake Hosted User Guide, Drake Tax Software, and any other related
Sophos Mobile Control SaaS startup guide. Product version: 6
 Sophos Mobile Control SaaS startup guide Product version: 6 Document date: January 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8
Sophos Mobile Control SaaS startup guide Product version: 6 Document date: January 2016 Contents 1 About this guide...4 2 About Sophos Mobile Control...5 3 What are the key steps?...7 4 Change your password...8
.Trustwave.com Updated October 9, 2007. Secure Web Gateway Version 11.0 Amazon EC2 Platform Set-up Guide
 .Trustwave.com Updated October 9, 2007 Secure Web Gateway Version 11.0 Amazon EC2 Platform Set-up Guide Legal Notice Copyright 2012 Trustwave Holdings, Inc. All rights reserved. This document is protected
.Trustwave.com Updated October 9, 2007 Secure Web Gateway Version 11.0 Amazon EC2 Platform Set-up Guide Legal Notice Copyright 2012 Trustwave Holdings, Inc. All rights reserved. This document is protected
WhatsUp Gold v16.3 Installation and Configuration Guide
 WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
CONTENTS. PCI DSS Compliance Guide
 CONTENTS PCI DSS COMPLIANCE FOR YOUR WEBSITE BUILD AND MAINTAIN A SECURE NETWORK AND SYSTEMS Requirement 1: Install and maintain a firewall configuration to protect cardholder data Requirement 2: Do not
CONTENTS PCI DSS COMPLIANCE FOR YOUR WEBSITE BUILD AND MAINTAIN A SECURE NETWORK AND SYSTEMS Requirement 1: Install and maintain a firewall configuration to protect cardholder data Requirement 2: Do not
Comparison of TaxWise Online & TaxWise Desktop. 2010 IRS Training
 Comparison of TaxWise Online & TaxWise Desktop 2010 IRS Training 2010 CCH Small Firm Services. All rights reserved. 225 Chastain Meadows Court NW Suite 200 Kennesaw, GA 30144 Information in this manuscript
Comparison of TaxWise Online & TaxWise Desktop 2010 IRS Training 2010 CCH Small Firm Services. All rights reserved. 225 Chastain Meadows Court NW Suite 200 Kennesaw, GA 30144 Information in this manuscript
Administrator's Guide
 Administrator's Guide Copyright SecureAnywhere Mobile Protection Administrator's Guide November, 2012 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere
Administrator's Guide Copyright SecureAnywhere Mobile Protection Administrator's Guide November, 2012 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere
How To Convert A Lead In Sugarcrm
 Attract. Convert. Retain. Lead Management in SugarCRM Written by: Josh Sweeney and Matthew Poer www.atcoresystems.com Atcore Systems, LLC 2010 All rights reserved. No part of this publication may be reproduced
Attract. Convert. Retain. Lead Management in SugarCRM Written by: Josh Sweeney and Matthew Poer www.atcoresystems.com Atcore Systems, LLC 2010 All rights reserved. No part of this publication may be reproduced
IBM Security QRadar Version 7.2.5. Vulnerability Assessment Configuration Guide IBM
 IBM Security QRadar Version 7.2.5 Vulnerability Assessment Configuration Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 93. Product
IBM Security QRadar Version 7.2.5 Vulnerability Assessment Configuration Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 93. Product
Adobe Marketing Cloud Bloodhound for Mac 3.0
 Adobe Marketing Cloud Bloodhound for Mac 3.0 Contents Adobe Bloodhound for Mac 3.x for OSX...3 Getting Started...4 Processing Rules Mapping...6 Enable SSL...7 View Hits...8 Save Hits into a Test...9 Compare
Adobe Marketing Cloud Bloodhound for Mac 3.0 Contents Adobe Bloodhound for Mac 3.x for OSX...3 Getting Started...4 Processing Rules Mapping...6 Enable SSL...7 View Hits...8 Save Hits into a Test...9 Compare
enicq 5 System Administrator s Guide
 Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Vermont Oxford Network enicq 5 Documentation enicq 5 System Administrator s Guide Release 2.0 Published November 2014 2014 Vermont Oxford Network. All Rights Reserved. enicq 5 System Administrator s Guide
Understanding BeyondTrust Patch Management
 Best Practices WHITE PAPER Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and
Best Practices WHITE PAPER Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and
Secure Web Service - Hybrid. Policy Server Setup. Release 9.2.5 Manual Version 1.01
 Secure Web Service - Hybrid Policy Server Setup Release 9.2.5 Manual Version 1.01 M86 SECURITY WEB SERVICE HYBRID QUICK START USER GUIDE 2010 M86 Security All rights reserved. 828 W. Taft Ave., Orange,
Secure Web Service - Hybrid Policy Server Setup Release 9.2.5 Manual Version 1.01 M86 SECURITY WEB SERVICE HYBRID QUICK START USER GUIDE 2010 M86 Security All rights reserved. 828 W. Taft Ave., Orange,
LEA Monitoring User Guide
 LEA Monitoring User Guide v. 3.0 September 2012 Contents Contents... 2 Introduction... 4 Acknowledgements... 4 Questions... 4 What is DMI Tracker?... 5 Monitoring... 5 End User System Guidelines... 5 Accessing
LEA Monitoring User Guide v. 3.0 September 2012 Contents Contents... 2 Introduction... 4 Acknowledgements... 4 Questions... 4 What is DMI Tracker?... 5 Monitoring... 5 End User System Guidelines... 5 Accessing
E-SPIN PCI Compliancy Solution
 E-SPIN PCI Compliancy Solution PCI Requirements For compliancy - Any company that accepts, processes, or stores credit card information needs to comply with the requirements set by the Payment Card Industry
E-SPIN PCI Compliancy Solution PCI Requirements For compliancy - Any company that accepts, processes, or stores credit card information needs to comply with the requirements set by the Payment Card Industry
USER GUIDE: MaaS360 Services
 USER GUIDE: MaaS360 Services 05.2010 Copyright 2010 Fiberlink Corporation. All rights reserved. Information in this document is subject to change without notice. The software described in this document
USER GUIDE: MaaS360 Services 05.2010 Copyright 2010 Fiberlink Corporation. All rights reserved. Information in this document is subject to change without notice. The software described in this document
Advanced Event Viewer Manual
 Advanced Event Viewer Manual Document version: 2.2944.01 Download Advanced Event Viewer at: http://www.advancedeventviewer.com Page 1 Introduction Advanced Event Viewer is an award winning application
Advanced Event Viewer Manual Document version: 2.2944.01 Download Advanced Event Viewer at: http://www.advancedeventviewer.com Page 1 Introduction Advanced Event Viewer is an award winning application
FINRA DR Portal. User Guide for Arbitration and Mediation Case Participants
 FINRA DR Portal for Arbitration and Mediation Case Participants December 2015 Disclaimer These materials are for training and instructional purposes only. No part of this publication may be reproduced,
FINRA DR Portal for Arbitration and Mediation Case Participants December 2015 Disclaimer These materials are for training and instructional purposes only. No part of this publication may be reproduced,
uh6 efolder BDR Guide for Veeam Page 1 of 36
 efolder BDR for Veeam Hyper-V Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder
efolder BDR for Veeam Hyper-V Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION Thank you for choosing the efolder
ASV Scan Report Attestation of Scan Compliance
 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Company: David S. Marcus, Ph. D Approved Scanning Vendor Information Company: ComplyGuard Networks Contact: Contact: Support Tel:
ASV Scan Report Attestation of Scan Compliance Scan Customer Information Company: David S. Marcus, Ph. D Approved Scanning Vendor Information Company: ComplyGuard Networks Contact: Contact: Support Tel:
Managed Service Solutions Catalogue. MANAGED SERVICES SOLUTIONS CATALOGUE MS Offering Overview June 2014
 Managed Service Solutions Catalogue MANAGED SERVICES SOLUTIONS CATALOGUE MS Offering Overview June 2014 1 MANAGED SERVICES SOLUTIONS CATALOGUE Managed Services Solutions Catalogue Managed Service Solutions
Managed Service Solutions Catalogue MANAGED SERVICES SOLUTIONS CATALOGUE MS Offering Overview June 2014 1 MANAGED SERVICES SOLUTIONS CATALOGUE Managed Services Solutions Catalogue Managed Service Solutions
Payment Card Industry (PCI) Executive Report 08/04/2014
 Payment Card Industry (PCI) Executive Report 08/04/2014 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: A.B. Yazamut Company: Qualys
Payment Card Industry (PCI) Executive Report 08/04/2014 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: A.B. Yazamut Company: Qualys
Best Practices. Understanding BeyondTrust Patch Management
 Best Practices Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and Approve Patches...
Best Practices Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and Approve Patches...
NETWRIX USER ACTIVITY VIDEO REPORTER
 NETWRIX USER ACTIVITY VIDEO REPORTER ADMINISTRATOR S GUIDE Product Version: 1.0 January 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
NETWRIX USER ACTIVITY VIDEO REPORTER ADMINISTRATOR S GUIDE Product Version: 1.0 January 2013. Legal Notice The information in this publication is furnished for information use only, and does not constitute
360Pro Providers Quick Reference Guide. Introduction
 360Pro Providers Quick Reference Guide This guide will step you through the basics, from logging on, to answering ATM questions and then submitting a Response. This Guide is available at: https://langeconsulting.zendesk.com/entries/24921676-360pro-providers-quick-reference-guide
360Pro Providers Quick Reference Guide This guide will step you through the basics, from logging on, to answering ATM questions and then submitting a Response. This Guide is available at: https://langeconsulting.zendesk.com/entries/24921676-360pro-providers-quick-reference-guide
QualysGuard WAS. Getting Started Guide Version 3.3. March 21, 2014
 QualysGuard WAS Getting Started Guide Version 3.3 March 21, 2014 Copyright 2011-2014 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
QualysGuard WAS Getting Started Guide Version 3.3 March 21, 2014 Copyright 2011-2014 by Qualys, Inc. All Rights Reserved. Qualys, the Qualys logo and QualysGuard are registered trademarks of Qualys, Inc.
