Nessus and Mobile Device Scanning. November 7, 2014 (Revision 12)
|
|
|
- Felix Harrell
- 10 years ago
- Views:
Transcription
1 Nessus and Mobile Device Scanning November 7, 2014 (Revision 12)
2 Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 Scanning for Mobile Devices with Nessus... 4 Creating a Scan... 4 Plugins and Policy Preferences... 5 Reports For Further Information About Tenable Network Security
3 Introduction This document describes how Tenable Network Security s Nessus vulnerability scanner integrates with Microsoft Active Directory and mobile device management servers to identify mobile devices in use on the network. Please any comments and suggestions to [email protected]. This document specifically covers Nessus integration with mobile device management. Installation, configuration, and management of Nessus is covered by other documents. A basic understanding of Nessus functionality, mobile devices, and system administration is assumed. Standards and Conventions Throughout the documentation, filenames, daemons, and executables are indicated with a courier bold font such as gunzip, httpd, and /etc/passwd. Command line options and keywords are also indicated with the courier bold font. Command line examples may or may not include the command line prompt and output text from the results of the command. Command line examples will display the command being run in courier bold to indicate what the user typed while the sample output generated by the system will be indicated in courier (not bold). Following is an example running of the Unix pwd command: # pwd /opt/sc4/daemons # Important notes and considerations are highlighted with this symbol and grey text boxes. Tips, examples, and best practices are highlighted with this symbol and white on blue text. Overview Mobile device saturation has reached an all-time high, as both individuals and corporations become more reliant on them to conduct their affairs. An entire market has quickly evolved, centered on Bring Your Own Device (BYOD) security and integration. Like it or not, and know it or not, mobile devices are increasingly being connected to corporate networks. In some cases, such connections may seem like a harmless activity such as charging a battery. In reality, simply charging the device is often performed via USB connection, and doing so may bridge the device with the computer. Active scanning cannot always detect mobile devices on the network directly since the devices are not always active on the network. There are several approaches that can be taken to identify mobile devices connecting to the network. One is to leverage a Mobile Device Management (MDM) console, which will contain a lot of useful information about mobile devices on the network. The drawback to this approach is the reason the issue is called Bring Your Own Device ; the device is often a personal device that is not enrolled in the MDM system. A better approach is to leverage information obtained from devices that connect to Microsoft Exchange servers. Basically, any employees who self-enroll with ActiveSync are sending their mobile OS version and more information back to the Exchange server. This provides a non-intrusive method to obtain the device type and OS version. Since Exchange is so widely deployed, the information is already available in many infrastructures. The drawback to this approach is that the information obtained is less granular than what is available on an MDM. 3
4 The Nessus Mobile Devices plugin family provides the ability to obtain information from devices registered in a MDM and from Active Directory servers that contain information from MS Exchange servers. This currently includes Apple iphone, Apple ipad, Windows Phone, and Android devices that supply version information, and have checked in to their respective servers in the last 3 months. The Nessus scanner must be able to reach the mobile device management (MDM) servers to query for information. You must ensure there are no screening devices that block traffic to these systems from the Nessus scanner. In addition, Nessus must be provided administrative credentials (e.g., domain administrator) to the Active Directory servers. Scanning for Mobile Devices with Nessus Nessus 5 currently has the ability to scan Microsoft Active Directory Service Interfaces (ADSI), Apple Profile Manager, MobileIron, and Good, allowing for the inventory and vulnerability scanning of both Apple ios-based and Android devices. Nessus can be configured to authenticate to these servers, query for mobile device information, and report on any issues. To scan for mobile devices, Nessus must be configured with authentication information for the management server and the mobile plugins of interest. Since Nessus authenticates directly to the management servers, a scan policy does not need to be configured to scan specific hosts. Creating a Scan In order to scan a mobile system, create a new policy and select the Mobile Device Scan policy wizard. It will ask the basic information required to perform the scan and auto-create the rest of the policy. The wizard will also let you control report verbosity, scan result sharing, and input credentials to access the mobile manager. 4
5 If any changes need to be made regarding the Mobile scanning, editing the policy will also update the settings for the Mobile template. For ActiveSync scans that access data from Microsoft Exchange servers, Nessus will retrieve information from phones that have been updated in the last 365 days. Plugins and Policy Preferences To complete a scan of mobile devices, you can also create a policy the traditional way. Rather than selecting the default Mobile Device Scan, select Advanced Scan. To scan mobile device management servers, authentication credentials are established in the Credentials tab and the Mobile sub-heading of an Advanced Scan, or Step 2 of the Mobile Scan policy wizard. Your scan policy does not need to be configured to scan any ports or use any port scanners. A majority of mobile device plugins can be found in the plugin family Mobile Devices, visible under an Advanced Scan policy. In addition, there are a few mobile device related plugins in the Service detection (Apple Profile Manager Detection) and Settings families (Apple Profile Manager API Settings and ADSI Settings for ActiveSync). 5
6 Nessus can also use ActiveSync in addition to a mobile manager: ActiveSync (Microsoft Exchange) allows Nessus to query an ActiveSync server to determine if any Android or iosbased devices are connected. Using the credentials and server information, Nessus authenticates to the domain controller (not the Exchange server) to directly query it for device information. This feature does not require any ports be specified in the scan policy. These settings are required for mobile device scanning. Nessus supports obtaining the mobile information from Exchange Server 2010 and 2013 only. Nessus cannot retrieve that information from Exchange Server
7 AirWatch allows Nessus to query the AirWatch API to gather information about all the mobile devices it manages. Using the credentials and the API key, Nessus authenticates to the server to directly query it for device information. This feature does not require any ports be specified in the scan policy. Optionally, communications over SSL can be specified, as well as verifying the SSL certificate. 7
8 Apple Profile Manager allows Nessus to query an Apple Profile Manager server to enumerate Apple ios-based devices (e.g., iphone, ipad) on the network. Using the credentials and server information, Nessus authenticates to the Profile Manager to directly query it for device information. Optionally, communications over SSL can be specified, as well as directing the server to force a device information update (i.e., each device will update its information with the Profile Manager server). 8
9 Good for Enterprise allows Nessus to query a Good server to enumerate mobile devices on the network. Using the credentials and server information, Nessus authenticates to the Good server to directly query it for device information. Optionally, communications over SSL can be specified as well as strict SSL certificate verification. 9
10 MobileIron allows Nessus to query a MobileIron server to enumerate any attached mobile devices (e.g., iphone, ipad, HTC, BlackBerry, Android). Using the credentials and server information, Nessus uses authenticated API calls to query the server for device information. Optionally, communications over SSL can be specified, as well as directing the server to verify the SSL certificate for enhanced security. Reports Once your scan has completed, the results will be available under the Reports tab. Click on the report to begin navigating through the information. More information on reporting can be found in the Nessus User Guide. 10
11 Each finding will display a list of devices presenting the issue at the bottom of the report: For Further Information Tenable has produced a variety of other documents detailing Nessus installation, deployment, configuration, user operation, and overall testing: Nessus 6.0 Installation and Configuration Guide step by step walk through of installation and configuration Nessus 6.0 User Guide how to configure and operate the Nessus User Interface Nessus Enterprise 6.0 User Guide how to configure and operate the Nessus User Interface for Nessus Enterprise Nessus Enterprise Cloud User Guide describes use of Nessus Enterprise Cloud and includes subscription and activation, vulnerability scanning, compliance reporting, and Nessus Enterprise Cloud support Nessus Credential Checks for Unix and Windows information on how to perform authenticated network scans with the Nessus vulnerability scanner Nessus Compliance Checks high-level guide to understanding and running compliance checks using Nessus and SecurityCenter Nessus Compliance Checks Reference comprehensive guide to Nessus Compliance Check syntax 11
12 Nessus v2 File Format describes the structure for the.nessus file format, which was introduced with Nessus 3.2 and NessusClient 3.2 Nessus 5.0 REST Protocol Specification describes the REST protocol and interface in Nessus Nessus and Antivirus outlines how several popular security software packages interact with Nessus, and provides tips or workarounds to allow the software to better co-exist without compromising your security or hindering your vulnerability scanning efforts Nessus and Scanning Virtual Machines describes how Tenable Network Security's Nessus vulnerability scanner can be used to audit the configuration of virtual platforms as well as the software that is running on them Strategic Anti-malware Monitoring with Nessus, PVS, and LCE describes how Tenable's USM platform can detect a variety of malicious software and identify and determine the extent of malware infections Patch Management Integration document describes how Nessus and SecurityCenter can leverage credentials on the Red Hat Network Satellite, IBM TEM, Dell KACE 1000, and Microsoft WSUS and SCCM patch management systems to perform patch auditing on systems for which credentials may not be available to the Nessus scanner Real-Time Compliance Monitoring outlines how Tenable s solutions can be used to assist in meeting many different types of government and financial regulations Tenable Products Plugin Families provides a description and summary of the plugin families for Nessus, Log Correlation Engine, and the Passive Vulnerability Scanner SecurityCenter Administration Guide Other online resources are listed below: Nessus Discussions Forum: Tenable Blog: Tenable Podcast: Example Use Videos: Tenable Twitter Feed: Please feel free to contact Tenable at [email protected], [email protected], or visit our web site at About Tenable Network Security Tenable Network Security provides continuous network monitoring to identify vulnerabilities, reduce risk, and ensure compliance. Our family of products includes SecurityCenter Continuous View, which provides the most comprehensive and integrated view of network health, and Nessus, the global standard in detecting and assessing network data. Tenable is relied upon by more than 24,000 organizations, including the entire U.S. Department of Defense and many of the world s largest companies and governments. We offer customers peace of mind thanks to the largest install base, the best expertise, and the ability to identify their biggest threats and enable them to respond quickly. For more information, please visit tenable.com. 12
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide. July 16, 2014 (Revision 2)
 Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
Nessus Enterprise for Amazon Web Services (AWS) Installation and Configuration Guide July 16, 2014 (Revision 2) Table of Contents Introduction... 3 Requirements... 3 Standards and Conventions... 3 Nessus
How To Run The Nessus 6 Vulnerability Scanner On A Pc Or Mac Or Linux (For A Non-Procedure) On A Microsoft Mac Or Pc Or Linux On A Mac Or Mac (For An Unprocedured Pc Or
 Nessus v6 Command Line Reference November 26, 2014 (Revision 2) Table of Contents Introduction... 3 Standards and Conventions... 3 Nessus Command Line... 3 Overview and Basic Usage... 3 Nessus Command
Nessus v6 Command Line Reference November 26, 2014 (Revision 2) Table of Contents Introduction... 3 Standards and Conventions... 3 Nessus Command Line... 3 Overview and Basic Usage... 3 Nessus Command
Tenable Network Security Support Portal. January 12, 2015 (Revision 14)
 Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
Tenable Network Security Support Portal January 12, 2015 (Revision 14) Table of Contents Introduction... 3 Activate Tenable Support Portal... 3 Locate Your Customer ID... 6 Manage Your Activation Codes...
Nessus and Antivirus. January 31, 2014 (Revision 4)
 Nessus and Antivirus January 31, 2014 (Revision 4) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 A Note on SCAP Audits... 4 Microsoft Windows Defender... 4 Kaspersky
Nessus and Antivirus January 31, 2014 (Revision 4) Table of Contents Introduction... 3 Standards and Conventions... 3 Overview... 3 A Note on SCAP Audits... 4 Microsoft Windows Defender... 4 Kaspersky
Log Correlation Engine Backup Strategy
 Log Correlation Engine Backup Strategy August 10, 2012 (Revision 1) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of
Log Correlation Engine Backup Strategy August 10, 2012 (Revision 1) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of
Patch Management Integration
 Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Patch Management Integration January 10, 2012 (Revision 5) Copyright 2002-2012 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks of Tenable
Log Correlation Engine 4.6 Quick Start Guide. January 25, 2016 (Revision 2)
 Log Correlation Engine 4.6 Quick Start Guide January 25, 2016 (Revision 2) Table of Contents Introduction... 4 Standards and Conventions... 4 Product Overview... 4 Prerequisites... 4 LCE Quick Start...
Log Correlation Engine 4.6 Quick Start Guide January 25, 2016 (Revision 2) Table of Contents Introduction... 4 Standards and Conventions... 4 Product Overview... 4 Prerequisites... 4 LCE Quick Start...
Nessus Enterprise Cloud User Guide. October 2, 2014 (Revision 9)
 Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Nessus Enterprise Cloud User Guide October 2, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Enterprise Cloud... 3 Subscription and Activation... 3 Multi Scanner Support... 4 Customer Scanning
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure
 Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Quick Start Guide: Utilizing Nessus to Secure Microsoft Azure Introduction Tenable Network Security is the first and only solution to offer security visibility, Azure cloud environment auditing, system
Nessus Agents. October 2015
 Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
Nessus Agents October 2015 Table of Contents Introduction... 3 What Are Nessus Agents?... 3 Scanning... 4 Results... 6 Conclusion... 6 About Tenable Network Security... 6 2 Introduction Today s changing
How to Add, Deactivate, or Edit a Contact
 How to Add, Deactivate, or Edit a Contact Add Contact (Add account option only available to the Primary Contact for the account) 1. Log in to the Tenable Support Portal with authorized credentials: https://support.tenable.com/
How to Add, Deactivate, or Edit a Contact Add Contact (Add account option only available to the Primary Contact for the account) 1. Log in to the Tenable Support Portal with authorized credentials: https://support.tenable.com/
Tenable for CyberArk
 HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
HOW-TO GUIDE Tenable for CyberArk Introduction This document describes how to deploy Tenable SecurityCenter and Nessus for integration with CyberArk Enterprise Password Vault. Please email any comments
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus. February 3, 2015 (Revision 4)
 Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
Comprehensive Malware Detection with SecurityCenter Continuous View and Nessus February 3, 2015 (Revision 4) Table of Contents Overview... 3 Malware, Botnet Detection, and Anti-Virus Auditing... 3 Malware
SecurityCenter 4.4 Administration Guide
 SecurityCenter 4.4 Administration Guide September 18, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_admin_guide.pdf
SecurityCenter 4.4 Administration Guide September 18, 2012 (Revision 3) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_admin_guide.pdf
Configuring Virtual Switches for Use with PVS. February 7, 2014 (Revision 1)
 Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
Configuring Virtual Switches for Use with PVS February 7, 2014 (Revision 1) Table of Contents Introduction... 3 Basic PVS VM Configuration... 3 Platforms... 3 VMware ESXi 5.5... 3 Configure the ESX Management
SecurityCenter 4.2 Administration Guide
 SecurityCenter 4.2 Administration Guide January 24, 2012 (Revision 5) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.2_admin_guide.pdf
SecurityCenter 4.2 Administration Guide January 24, 2012 (Revision 5) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.2_admin_guide.pdf
Nessus Credentialed Checks. November 24, 2014 (Revision 38)
 Nessus Credentialed Checks November 24, 2014 (Revision 38) Table of Contents Introduction... 4 Standards and Conventions... 4 Overview of Nessus Credentialed Checks... 4 Purpose... 4 Access Level... 5
Nessus Credentialed Checks November 24, 2014 (Revision 38) Table of Contents Introduction... 4 Standards and Conventions... 4 Overview of Nessus Credentialed Checks... 4 Purpose... 4 Access Level... 5
Passive Vulnerability Scanner 4.0 User Guide. September 18, 2014 (Revision 12)
 Passive Vulnerability Scanner 4.0 User Guide September 18, 2014 (Revision 12) Table of Contents Introduction... 5 Standards and Conventions... 5 Passive Vulnerability Scanner Background and Theory... 5
Passive Vulnerability Scanner 4.0 User Guide September 18, 2014 (Revision 12) Table of Contents Introduction... 5 Standards and Conventions... 5 Passive Vulnerability Scanner Background and Theory... 5
SecurityCenter 4.8 Administration Guide. October 2, 2015 (Revision 13)
 SecurityCenter 4.8 Administration Guide October 2, 2015 (Revision 13) Table of Contents Introduction... 5 Standards and Conventions... 5 Abbreviations... 6 SecurityCenter Administrator Functions... 6 Starting/Halting
SecurityCenter 4.8 Administration Guide October 2, 2015 (Revision 13) Table of Contents Introduction... 5 Standards and Conventions... 5 Abbreviations... 6 SecurityCenter Administrator Functions... 6 Starting/Halting
Nessus 5.2 Enterprise User Guide. September 5, 2014 (Revision 9)
 Nessus 5.2 Enterprise User Guide September 5, 2014 (Revision 9) Table of Contents Introduction... 5 Standards and Conventions... 5 New in Nessus 5.2... 5 Nessus Enterprise Overview... 6 UI Description...
Nessus 5.2 Enterprise User Guide September 5, 2014 (Revision 9) Table of Contents Introduction... 5 Standards and Conventions... 5 New in Nessus 5.2... 5 Nessus Enterprise Overview... 6 UI Description...
24/7 Visibility into Advanced Malware on Networks and Endpoints
 WHITEPAPER DATA SHEET 24/7 Visibility into Advanced Malware on Networks and Endpoints Leveraging threat intelligence to detect malware and exploitable vulnerabilities Oct. 24, 2014 Table of Contents Introduction
WHITEPAPER DATA SHEET 24/7 Visibility into Advanced Malware on Networks and Endpoints Leveraging threat intelligence to detect malware and exploitable vulnerabilities Oct. 24, 2014 Table of Contents Introduction
VULNERABILITY MANAGEMENT
 Vulnerability Management (VM) software differ in the richness of reporting, and the capabilities for application and security configuration assessment. Companies must consider how a VM technology will
Vulnerability Management (VM) software differ in the richness of reporting, and the capabilities for application and security configuration assessment. Companies must consider how a VM technology will
SecurityCenter 5.1 with Nessus Agent Support. October 22, 2015
 SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
SecurityCenter 5.1 with Nessus Agent Support October 22, 2015 Table of Contents Introduction... 3 Adding an Agent Repository... 6 Add Agent Scans and Import Agent Scan Results... 7 Tips and Tricks... 8
Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9)
 Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Perimeter Service... 3 Subscription and Activation... 3 Multi Scanner Support...
Nessus Perimeter Service User Guide (HTML5 Interface) March 18, 2014 (Revision 9) Table of Contents Introduction... 3 Nessus Perimeter Service... 3 Subscription and Activation... 3 Multi Scanner Support...
3D Tool 2.0 Quick Start Guide
 www.tenable.com [email protected] 3D Tool 2.0 Quick Start Guide ABOUT THE 3D TOOL Tenable s 3D Tool is a Windows application that is used to query data from a SecurityCenter 4 server and present it in
www.tenable.com [email protected] 3D Tool 2.0 Quick Start Guide ABOUT THE 3D TOOL Tenable s 3D Tool is a Windows application that is used to query data from a SecurityCenter 4 server and present it in
Secret Server Qualys Integration Guide
 Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
Secret Server Qualys Integration Guide Table of Contents Secret Server and Qualys Cloud Platform... 2 Authenticated vs. Unauthenticated Scanning... 2 What are the Advantages?... 2 Integrating Secret Server
WHITEPAPER. Nessus Exploit Integration
 Nessus Exploit Integration v2 Tenable Network Security has committed to providing context around vulnerabilities, and correlating them to other sources, such as available exploits. We currently pull information
Nessus Exploit Integration v2 Tenable Network Security has committed to providing context around vulnerabilities, and correlating them to other sources, such as available exploits. We currently pull information
Nessus 5.2 HTML5 User Guide. September 5, 2014 (Revision 48)
 Nessus 5.2 HTML5 User Guide September 5, 2014 (Revision 48) Table of Contents Introduction... 5 Standards and Conventions... 5 New in Nessus 5.2... 5 Nessus UI Overview... 6 Description... 6 Supported
Nessus 5.2 HTML5 User Guide September 5, 2014 (Revision 48) Table of Contents Introduction... 5 Standards and Conventions... 5 New in Nessus 5.2... 5 Nessus UI Overview... 6 Description... 6 Supported
Nessus Cloud User Registration
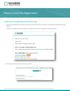 Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Nessus Cloud User Registration Create Your Tenable Nessus Cloud Account 1. Click on the provided URL to create your account. If the link does not work, please cut and paste the entire URL into your browser.
Best Practices. Understanding BeyondTrust Patch Management
 Best Practices Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and Approve Patches...
Best Practices Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and Approve Patches...
Passive Vulnerability Scanner 4.2 User Guide. June 8, 2015 (Revision 12)
 Passive Vulnerability Scanner 4.2 User Guide June 8, 2015 (Revision 12) Table of Contents Introduction... 7 Standards and Conventions... 7 Passive Vulnerability Scanner Background and Theory... 7 System
Passive Vulnerability Scanner 4.2 User Guide June 8, 2015 (Revision 12) Table of Contents Introduction... 7 Standards and Conventions... 7 Passive Vulnerability Scanner Background and Theory... 7 System
April 11, 2011. (Revision 2)
 Passive Vulnerability Scanning Overview April 11, 2011 (Revision 2) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Passive Vulnerability Scanning Overview April 11, 2011 (Revision 2) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Kaspersky Lab Mobile Device Management Deployment Guide
 Kaspersky Lab Mobile Device Management Deployment Guide Introduction With the release of Kaspersky Security Center 10.0 a new functionality has been implemented which allows centralized management of mobile
Kaspersky Lab Mobile Device Management Deployment Guide Introduction With the release of Kaspersky Security Center 10.0 a new functionality has been implemented which allows centralized management of mobile
Understanding BeyondTrust Patch Management
 Best Practices WHITE PAPER Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and
Best Practices WHITE PAPER Understanding BeyondTrust Patch Management February 2014 Contents Overview... 3 1 - Configure Retina CS... 4 2 - Enable Patch Management for Smart Groups... 6 3 Identify and
SecurityCenter 4.4 Architecture
 SecurityCenter 4.4 Architecture September 21, 2012 (Revision 2) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_architecture.pdf
SecurityCenter 4.4 Architecture September 21, 2012 (Revision 2) The newest version of this document is available at the following URL: http://static.tenable.com/prod_docs/securitycenter_4.4_architecture.pdf
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
IBM Security QRadar Version 7.2.5. Vulnerability Assessment Configuration Guide IBM
 IBM Security QRadar Version 7.2.5 Vulnerability Assessment Configuration Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 93. Product
IBM Security QRadar Version 7.2.5 Vulnerability Assessment Configuration Guide IBM Note Before using this information and the product that it supports, read the information in Notices on page 93. Product
Office 365 Windows Intune Administration Guide
 Chapter 7 Office 365 Windows Intune Administration Guide Office 365 is a suite of technologies delivered as a Software as a Service (SaaS) offering. Office 365 reduces the IT costs for businesses of any
Chapter 7 Office 365 Windows Intune Administration Guide Office 365 is a suite of technologies delivered as a Software as a Service (SaaS) offering. Office 365 reduces the IT costs for businesses of any
How to Register for Training
 How to Register for Training We have created a Training Console to help you manage your Tenable training from the Tenable Support Portal. You will be able to enroll in On Demand Training Course(s) or Certification
How to Register for Training We have created a Training Console to help you manage your Tenable training from the Tenable Support Portal. You will be able to enroll in On Demand Training Course(s) or Certification
BlackBerry Enterprise Service 10. Universal Device Service Version: 10.2. Administration Guide
 BlackBerry Enterprise Service 10 Universal Service Version: 10.2 Administration Guide Published: 2015-02-24 SWD-20150223125016631 Contents 1 Introduction...9 About this guide...10 What is BlackBerry
BlackBerry Enterprise Service 10 Universal Service Version: 10.2 Administration Guide Published: 2015-02-24 SWD-20150223125016631 Contents 1 Introduction...9 About this guide...10 What is BlackBerry
Description of Actual State Sensor Types for the Software Asset Management (SWAM) Capability. 7 Jul 2014
 Description of Actual State Sensor Types for the Software Asset Management (SWAM) Capability 7 Jul 2014 1 Purpose This document is intended to provide insight on the types of tools and technologies that
Description of Actual State Sensor Types for the Software Asset Management (SWAM) Capability 7 Jul 2014 1 Purpose This document is intended to provide insight on the types of tools and technologies that
Security Guide. BlackBerry Enterprise Service 12. for ios, Android, and Windows Phone. Version 12.0
 Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Security Guide BlackBerry Enterprise Service 12 for ios, Android, and Windows Phone Version 12.0 Published: 2015-02-06 SWD-20150206130210406 Contents About this guide... 6 What is BES12?... 7 Key features
Nessus 6.4 User Guide
 Nessus 6.4 User Guide April 5, 2016 (Revision 3) Copyright 2015. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security,
Nessus 6.4 User Guide April 5, 2016 (Revision 3) Copyright 2015. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of Tenable Network Security,
Continuous Network Monitoring for the New IT Landscape. March 16, 2015 (Revision 4)
 Continuous Network Monitoring for the New IT Landscape March 16, 2015 (Revision 4) Table of Contents Introduction... 3 The New IT Landscape... 3 Gaps in the Modern IT Landscape... 5 Tenable s Five Critical
Continuous Network Monitoring for the New IT Landscape March 16, 2015 (Revision 4) Table of Contents Introduction... 3 The New IT Landscape... 3 Gaps in the Modern IT Landscape... 5 Tenable s Five Critical
4. Getting started: Performing an audit
 4. Getting started: Performing an audit Introduction Security scans enable systems administrators to identify and assess possible risks within a network. Through GFI LANguard N.S.S. this is performed automatically,
4. Getting started: Performing an audit Introduction Security scans enable systems administrators to identify and assess possible risks within a network. Through GFI LANguard N.S.S. this is performed automatically,
IBM Endpoint Manager Version 9.1. Patch Management for Red Hat Enterprise Linux User's Guide
 IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide Note Before using
IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide IBM Endpoint Manager Version 9.1 Patch Management for Red Hat Enterprise Linux User's Guide Note Before using
AlienVault. Unified Security Management (USM) 5.1 Running the Getting Started Wizard
 AlienVault Unified Security Management (USM) 5.1 Running the Getting Started Wizard USM v5.1 Running the Getting Started Wizard, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault
AlienVault Unified Security Management (USM) 5.1 Running the Getting Started Wizard USM v5.1 Running the Getting Started Wizard, rev. 2 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault
Tenable for Google Cloud Platform
 HOW-TO GUIDE Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
HOW-TO GUIDE Tenable for Google Cloud Platform Introduction This document describes how to deploy Tenable SecurityCenter Continuous View (Security Center CV ) for integration with Google Cloud Platform.
PULSE APPCONNECT. A Micro VPN That Allows Specific Applications on Mobile Devices to Independently Leverage the Connect Secure Gateway.
 PULSE APPCONNECT A Micro VPN That Allows Specific Applications on Mobile Devices to Independently Leverage the Connect Secure Gateway Published Date July 2015 Contents Executive Summary 3 Introduction
PULSE APPCONNECT A Micro VPN That Allows Specific Applications on Mobile Devices to Independently Leverage the Connect Secure Gateway Published Date July 2015 Contents Executive Summary 3 Introduction
Defender 5.7 - Token Deployment System Quick Start Guide
 Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
Defender 5.7 - Token Deployment System Quick Start Guide This guide describes how to install, configure and use the Defender Token Deployment System, based on default settings and how to self register
IBM Security QRadar SIEM Version 7.1.0 MR1. Vulnerability Assessment Configuration Guide
 IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
IBM Security QRadar SIEM Version 7.1.0 MR1 Vulnerability Assessment Configuration Guide Note: Before using this information and the product that it supports, read the information in Notices and Trademarks
Concierge SIEM Reporting Overview
 Concierge SIEM Reporting Overview Table of Contents Introduction... 2 Inventory View... 3 Internal Traffic View (IP Flow Data)... 4 External Traffic View (HTTP, SSL and DNS)... 5 Risk View (IPS Alerts
Concierge SIEM Reporting Overview Table of Contents Introduction... 2 Inventory View... 3 Internal Traffic View (IP Flow Data)... 4 External Traffic View (HTTP, SSL and DNS)... 5 Risk View (IPS Alerts
Technical Note. ForeScout CounterACT Endpoint Detection & Inspection Methods
 ForeScout CounterACT Endpoint Contents Introduction.... 3 Overview of ForeScout CounterACT... 3 Overview of Discovery and Inspection... 4 Host & Network Device Discovery... 4 Endpoint Detection & Inspection
ForeScout CounterACT Endpoint Contents Introduction.... 3 Overview of ForeScout CounterACT... 3 Overview of Discovery and Inspection... 4 Host & Network Device Discovery... 4 Endpoint Detection & Inspection
GlobalSign Integration Guide
 GlobalSign Integration Guide GlobalSign Enterprise PKI (EPKI) and AirWatch Enterprise MDM 1 v.1.1 Table of Contents Table of Contents... 2 Introduction... 3 GlobalSign Enterprise PKI (EPKI)... 3 Partner
GlobalSign Integration Guide GlobalSign Enterprise PKI (EPKI) and AirWatch Enterprise MDM 1 v.1.1 Table of Contents Table of Contents... 2 Introduction... 3 GlobalSign Enterprise PKI (EPKI)... 3 Partner
Vulnerability Management for. Mobility. Issue 2. Identify Mobility Risk through Mobile Device Visibility and Vulnerability Assessment
 Issue 2 1 5 9 Vulnerability Management for Mobility From the Gartner Files: Four Ways to Close the Gap Between Enterprise Mobility and Vulnerability Management About Tenable Network Security Vulnerability
Issue 2 1 5 9 Vulnerability Management for Mobility From the Gartner Files: Four Ways to Close the Gap Between Enterprise Mobility and Vulnerability Management About Tenable Network Security Vulnerability
Extreme Networks Security Vulnerability Assessment Configuration Guide
 Extreme Networks Security Vulnerability Assessment Configuration Guide 9034869 Published July 2015 Copyright 2007 2015 All rights reserved. Legal Notice Extreme Networks, Inc. reserves the right to make
Extreme Networks Security Vulnerability Assessment Configuration Guide 9034869 Published July 2015 Copyright 2007 2015 All rights reserved. Legal Notice Extreme Networks, Inc. reserves the right to make
May 11, 2011. (Revision 10)
 Blended Security Assessments Combining Active, Passive and Host Assessment Techniques May 11, 2011 (Revision 10) Renaud Deraison Director of Research Ron Gula Chief Technology Officer Copyright 2011. Tenable
Blended Security Assessments Combining Active, Passive and Host Assessment Techniques May 11, 2011 (Revision 10) Renaud Deraison Director of Research Ron Gula Chief Technology Officer Copyright 2011. Tenable
The SIEM Evaluator s Guide
 Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
Using SIEM for Compliance, Threat Management, & Incident Response Security information and event management (SIEM) tools are designed to collect, store, analyze, and report on log data for threat detection,
June 8, 2011. (Revision 1)
 Unified Security Monitoring Best Practices June 8, 2011 (Revision 1) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Unified Security Monitoring Best Practices June 8, 2011 (Revision 1) Copyright 2011. Tenable Network Security, Inc. All rights reserved. Tenable Network Security and Nessus are registered trademarks of
Protecting Critical Infrastructure
 Protecting Critical Infrastructure SCADA Network Security Monitoring March 20, 2015 Table of Contents Introduction... 4 SCADA Systems... 4 In This Paper... 4 SCADA Security... 4 Assessing the Security
Protecting Critical Infrastructure SCADA Network Security Monitoring March 20, 2015 Table of Contents Introduction... 4 SCADA Systems... 4 In This Paper... 4 SCADA Security... 4 Assessing the Security
Learn More MaaS360 Cloud Extender Checklist (MDM for Blackberry)
 Learn More MaaS360 Cloud Extender Checklist (MDM for Blackberry) June 2011 Copyright 2011 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without
Learn More MaaS360 Cloud Extender Checklist (MDM for Blackberry) June 2011 Copyright 2011 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without
MaaS360 Cloud Extender
 MaaS360 Cloud Extender Installation Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software described
MaaS360 Cloud Extender Installation Guide Copyright 2013 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software described
Nessus 5.0 Flash User Guide. April 22, 2013 (Revision 23)
 Nessus 5.0 Flash User Guide April 22, 2013 (Revision 23) Table of Contents Introduction... 3 Standards and Conventions... 3 Nessus UI Overview... 3 Description... 3 Supported Platforms... 4 Installation...
Nessus 5.0 Flash User Guide April 22, 2013 (Revision 23) Table of Contents Introduction... 3 Standards and Conventions... 3 Nessus UI Overview... 3 Description... 3 Supported Platforms... 4 Installation...
MaaS360 On-Premises Cloud Extender
 MaaS360 On-Premises Cloud Extender Installation Guide Copyright 2014 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
MaaS360 On-Premises Cloud Extender Installation Guide Copyright 2014 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice. The software
Advanced Configuration Steps
 Advanced Configuration Steps After you have downloaded a trial, you can perform the following from the Setup menu in the MaaS360 portal: Configure additional services Configure device enrollment settings
Advanced Configuration Steps After you have downloaded a trial, you can perform the following from the Setup menu in the MaaS360 portal: Configure additional services Configure device enrollment settings
Getting Started with the iscan Online Data Breach Risk Intelligence Platform
 Getting Started with the iscan Online Data Breach Risk Intelligence Platform 2 Table of Contents Overview... 3 Data Breach Risk Intelligence... 3 Data Breach Prevention Lifecycle Defined... 3 Choosing
Getting Started with the iscan Online Data Breach Risk Intelligence Platform 2 Table of Contents Overview... 3 Data Breach Risk Intelligence... 3 Data Breach Prevention Lifecycle Defined... 3 Choosing
ManageEngine Desktop Central. Mobile Device Management User Guide
 ManageEngine Desktop Central Mobile Device Management User Guide Contents 1 Mobile Device Management... 2 1.1 Supported Devices... 2 1.2 What Management Operations you can Perform?... 2 2 Setting Up MDM...
ManageEngine Desktop Central Mobile Device Management User Guide Contents 1 Mobile Device Management... 2 1.1 Supported Devices... 2 1.2 What Management Operations you can Perform?... 2 2 Setting Up MDM...
GFI Product Manual. Administration and Configuration Manual
 GFI Product Manual Administration and Configuration Manual http://www.gfi.com [email protected] The information and content in this document is provided for informational purposes only and is provided "as is"
GFI Product Manual Administration and Configuration Manual http://www.gfi.com [email protected] The information and content in this document is provided for informational purposes only and is provided "as is"
Enterprise Mobility Management Migration Migrating from Legacy EMM to an epo Managed EMM Environment. Paul Luetje Enterprise Solutions Architect
 Enterprise Mobility Management Migration Migrating from Legacy EMM to an epo Managed EMM Environment Paul Luetje Enterprise Solutions Architect Table of Contents Welcome... 3 Purpose of this document...
Enterprise Mobility Management Migration Migrating from Legacy EMM to an epo Managed EMM Environment Paul Luetje Enterprise Solutions Architect Table of Contents Welcome... 3 Purpose of this document...
Continuous Compliance for Energy and Nuclear Facility Cyber Security Regulations
 Continuous Compliance for Energy and Nuclear Facility Cyber Security Regulations Leveraging Configuration and Vulnerability Analysis for Critical Assets and Infrastructure May 2015 (Revision 2) Table of
Continuous Compliance for Energy and Nuclear Facility Cyber Security Regulations Leveraging Configuration and Vulnerability Analysis for Critical Assets and Infrastructure May 2015 (Revision 2) Table of
Using Nessus to Detect Wireless Access Points. March 6, 2015 (Revision 4)
 Using Nessus to Detect Wireless Access Points March 6, 2015 (Revision 4) Table of Contents Introduction... 3 Why Detect Wireless Access Points?... 3 Wireless Scanning for WAPs... 4 Detecting WAPs using
Using Nessus to Detect Wireless Access Points March 6, 2015 (Revision 4) Table of Contents Introduction... 3 Why Detect Wireless Access Points?... 3 Wireless Scanning for WAPs... 4 Detecting WAPs using
How To Deploy Software Updates Using SCCM 2012 R2
 prajwaldesai.com http://prajwaldesai.com/deploy-software-updates-using-sccm-2012-r2/ How To Deploy Software Updates Using SCCM 2012 R2 Prajwal Desai In this post we will look at the steps on how to deploy
prajwaldesai.com http://prajwaldesai.com/deploy-software-updates-using-sccm-2012-r2/ How To Deploy Software Updates Using SCCM 2012 R2 Prajwal Desai In this post we will look at the steps on how to deploy
User Management Guide
 AlienVault Unified Security Management (USM) 4.x-5.x User Management Guide USM v4.x-5.x User Management Guide, rev 1 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
AlienVault Unified Security Management (USM) 4.x-5.x User Management Guide USM v4.x-5.x User Management Guide, rev 1 Copyright 2015 AlienVault, Inc. All rights reserved. The AlienVault Logo, AlienVault,
Continuous Monitoring for the New IT Landscape. July 14, 2014 (Revision 1)
 Continuous Monitoring for the New IT Landscape July 14, 2014 (Revision 1) Table of Contents Introduction... 3 The New IT Landscape... 3 Gaps in the New IT Landscape... 5 Tenable s Continuous Monitoring
Continuous Monitoring for the New IT Landscape July 14, 2014 (Revision 1) Table of Contents Introduction... 3 The New IT Landscape... 3 Gaps in the New IT Landscape... 5 Tenable s Continuous Monitoring
Administrator's Guide
 Administrator's Guide Copyright SecureAnywhere Mobile Protection Administrator's Guide November, 2012 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere
Administrator's Guide Copyright SecureAnywhere Mobile Protection Administrator's Guide November, 2012 2012 Webroot Software, Inc. All rights reserved. Webroot is a registered trademark and SecureAnywhere
Introduction to the EIS Guide
 Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
Introduction to the EIS Guide The AirWatch Enterprise Integration Service (EIS) provides organizations the ability to securely integrate with back-end enterprise systems from either the AirWatch SaaS environment
AV Management Dashboard
 LabTech AV Management Dashboard AV MANAGEMENT DASHBOARD... 1 Overview... 1 Requirements... 1 Dashboard Overview... 2 Clients/Groups... 2 Offline AV Agents... 3 Threats... 3 AV Product... 4 Sync Agent Data
LabTech AV Management Dashboard AV MANAGEMENT DASHBOARD... 1 Overview... 1 Requirements... 1 Dashboard Overview... 2 Clients/Groups... 2 Offline AV Agents... 3 Threats... 3 AV Product... 4 Sync Agent Data
5nine Security for Hyper-V Datacenter Edition. Version 3.0 Plugin for Microsoft System Center 2012 Virtual Machine Manager
 5nine Security for Hyper-V Datacenter Edition Version 3.0 Plugin for Microsoft System Center 2012 Virtual Machine Manager November 2013 11 Table of Contents Summary... 5 System requirements... 5 Permissions...
5nine Security for Hyper-V Datacenter Edition Version 3.0 Plugin for Microsoft System Center 2012 Virtual Machine Manager November 2013 11 Table of Contents Summary... 5 System requirements... 5 Permissions...
Preparing for GO!Enterprise MDM On-Demand Service
 Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
Deployment Guide for Microsoft Lync 2010
 Deployment Guide for Microsoft Lync 2010 Securing and Accelerating Microsoft Lync with Palo Alto Networks Next-Generation Firewall and Citrix NetScaler Joint Solution Table of Contents 1. Overview...3
Deployment Guide for Microsoft Lync 2010 Securing and Accelerating Microsoft Lync with Palo Alto Networks Next-Generation Firewall and Citrix NetScaler Joint Solution Table of Contents 1. Overview...3
Using Nessus In Web Application Vulnerability Assessments
 Using Nessus In Web Application Vulnerability Assessments Paul Asadoorian Product Evangelist Tenable Network Security [email protected] About Tenable Nessus vulnerability scanner, ProfessionalFeed
Using Nessus In Web Application Vulnerability Assessments Paul Asadoorian Product Evangelist Tenable Network Security [email protected] About Tenable Nessus vulnerability scanner, ProfessionalFeed
SOLARWINDS ORION. Patch Manager Evaluation Guide for ConfigMgr 2012
 SOLARWINDS ORION Patch Manager Evaluation Guide for ConfigMgr 2012 About SolarWinds SolarWinds, Inc. develops and markets an array of network management, monitoring, and discovery tools to meet the diverse
SOLARWINDS ORION Patch Manager Evaluation Guide for ConfigMgr 2012 About SolarWinds SolarWinds, Inc. develops and markets an array of network management, monitoring, and discovery tools to meet the diverse
Complete Patch Management
 Complete Management Targeted, Reliable and Cost-efficient In- Depth CSI Corporate Software Inspector Empower your IT-Operations and Security Teams with the most reliable Vulnerability & Management solution
Complete Management Targeted, Reliable and Cost-efficient In- Depth CSI Corporate Software Inspector Empower your IT-Operations and Security Teams with the most reliable Vulnerability & Management solution
Web Application Vulnerability Testing with Nessus
 The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP [email protected] Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
The OWASP Foundation http://www.owasp.org Web Application Vulnerability Testing with Nessus Rïk A. Jones, CISSP [email protected] Rïk A. Jones Web developer since 1995 (16+ years) Involved with information
Nessus Credential Checks for Unix and Windows
 Nessus Credential Checks for Unix and Windows June 15, 2011 (Revision 25) Copyright 2002-2011 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks
Nessus Credential Checks for Unix and Windows June 15, 2011 (Revision 25) Copyright 2002-2011 Tenable Network Security, Inc. Tenable Network Security, Nessus and ProfessionalFeed are registered trademarks
Client Manager for Endpoint Protection (CMEP) User s Guide
 Client Manager for Endpoint Protection (CMEP) July, 2010 All rights reserved. BigFix, Fixlet, Relevance Engine, Powered by BigFix and related BigFix logos are trademarks of BigFix, Inc. All other product
Client Manager for Endpoint Protection (CMEP) July, 2010 All rights reserved. BigFix, Fixlet, Relevance Engine, Powered by BigFix and related BigFix logos are trademarks of BigFix, Inc. All other product
Mobile Labs Plugin for IBM Urban Code Deploy
 Mobile Labs Plugin for IBM Urban Code Deploy Thank you for deciding to use the Mobile Labs plugin to IBM Urban Code Deploy. With the plugin, you will be able to automate the processes of installing or
Mobile Labs Plugin for IBM Urban Code Deploy Thank you for deciding to use the Mobile Labs plugin to IBM Urban Code Deploy. With the plugin, you will be able to automate the processes of installing or
Identity and Access Management Integration with PowerBroker. Providing Complete Visibility and Auditing of Identities
 Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
Identity and Access Management Integration with PowerBroker Providing Complete Visibility and Auditing of Identities Table of Contents Executive Summary... 3 Identity and Access Management... 4 BeyondTrust
Best Practice Configurations for OfficeScan (OSCE) 10.6
 Best Practice Configurations for OfficeScan (OSCE) 10.6 Applying Latest Patch(es) for OSCE 10.6 To find out the latest patches for OfficeScan, click here. Enable Smart Clients 1. Ensure that Officescan
Best Practice Configurations for OfficeScan (OSCE) 10.6 Applying Latest Patch(es) for OSCE 10.6 To find out the latest patches for OfficeScan, click here. Enable Smart Clients 1. Ensure that Officescan
Tenable Enterprise Product Training
 Tenable Enterprise Product Training Tenable Unified Security Monitoring for Analysts (5MD) This hands-on instructor led course provides security analysts with the skills and knowledge necessary to discover
Tenable Enterprise Product Training Tenable Unified Security Monitoring for Analysts (5MD) This hands-on instructor led course provides security analysts with the skills and knowledge necessary to discover
GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios with TouchDown
 GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios with TouchDown GO!Enterprise MDM for ios Devices, Version 3.x GO!Enterprise MDM for ios with TouchDown 1 Table of
GO!Enterprise MDM Device Application User Guide Installation and Configuration for ios with TouchDown GO!Enterprise MDM for ios Devices, Version 3.x GO!Enterprise MDM for ios with TouchDown 1 Table of
IBM Security QRadar Vulnerability Manager Version 7.2.1. User Guide
 IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
IBM Security QRadar Vulnerability Manager Version 7.2.1 User Guide Note Before using this information and the product that it supports, read the information in Notices on page 61. Copyright IBM Corporation
Nessus 6.1 User Guide. December 1, 2014 (Revision 4)
 Nessus 6.1 User Guide December 1, 2014 (Revision 4) Table of Contents Introduction... 4 Standards and Conventions... 4 New in Nessus 6.1... 4 Key Feature Updates... 4 Nessus UI Overview... 5 Description...
Nessus 6.1 User Guide December 1, 2014 (Revision 4) Table of Contents Introduction... 4 Standards and Conventions... 4 New in Nessus 6.1... 4 Key Feature Updates... 4 Nessus UI Overview... 5 Description...
Thexyz Premium Webmail
 Webmail Access all the benefits of a desktop program without being tied to the desktop. Log into Thexyz Email from your desktop, laptop, or mobile phone, and get instant access to email, calendars, contacts,
Webmail Access all the benefits of a desktop program without being tied to the desktop. Log into Thexyz Email from your desktop, laptop, or mobile phone, and get instant access to email, calendars, contacts,
Radia Cloud. User Guide. For the Windows operating systems Software Version: 9.10. Document Release Date: June 2014
 Radia Cloud For the Windows operating systems Software Version: 9.10 User Guide Document Release Date: June 2014 Software Release Date: June 2014 Legal Notices Warranty The only warranties for products
Radia Cloud For the Windows operating systems Software Version: 9.10 User Guide Document Release Date: June 2014 Software Release Date: June 2014 Legal Notices Warranty The only warranties for products
