Secure configuration document
|
|
|
- Lee Jennings
- 10 years ago
- Views:
Transcription
1 Secure configuration document MS Exchange 2003 Draft 0.1 DEPARTMENT OF ELECTRONICS AND INFORMATION TECHNOLOGY Ministry of Communication and Information Technology, Government of India. Submitted by Wipro Consulting Services 9/12/2013
2 Secure Configuration Document - MS Exchange 2003 Server Document Control S. No. Type of Information Document Data 1. Document Title Secure Configuration Document Wi-Fi 2. Document Code PR_SCD_Wi-Fi 3. Date of Release 4. Next Review Date 12 th September Document Owner DietY 6. Document Author(s) Wipro Consulting Services 7. Document Reviewer Negd 8. Document Reference 6th Sep 2013 PR_Harden Draft Version Document Approval S. No. Document Approver Approver Designation Approver ID 1. Archana Dureja Director, DietY [email protected] Document Change History Version No. Revision Date Nature of Change th Sep 2013 Draft Version Date of Approval Document Classification: Internal Page 1 of 46
3 Secure Configuration Document - MS Exchange 2003 Server Purpose This document is intended to guide MS Exchange system administrators to secure Microsoft Exchange 2003 Server. This document should be used to harden MS Exchange 2003 server/s deployed in e-gov service delivery environment. Security compliance on Exchange 2003 devices can be measured and reported considering the below mentioned control points as benchmark or criteria How to use this Document The document covers the mandatory security configurations for MS Exchange Server Please test the prescribed settings in the staging setup before deploying it to production environment. The document also mentions the How to check section, the output of these can be utilized to capture in hardening reports. These reports can serve as audit artifacts in meeting Hardening compliance on a specific server. The sections in control point/s below provide solutions and configurations as per industry best practices. The configurations also provide recommended values in a production environment, determined with practical experience in a production environment. The recommended values and parameters can be redefined specific to the environment if found not suitable or as desired. The SCD document may also provide suggestive steps to harden the target systems hosting other supporting technologies/tools and utilities prevalent in the industry. In case the target environment is not hosting such tools and technologies the control point can be marked Not Applicable while determining the compliance. Document Classification: Internal Page 2 of 46
4 Secure Configuration Document - MS Exchange 2003 Server General Exchange Security Guidance: The following recommendations are provided to facilitate a more secure platform. Review all recommendations to ensure they comply with local policy. Do not install Exchange Server 2003 on a domain controller. Load the operating system and secure it before loading Exchange onto the platform. It is important to realize that the system cannot be considered to be secured until the operating system has first been secured. If the operating system is not secured, Exchange functionality might be secure but the platform as a whole will be vulnerable. Ensure the following services have been started before attempting to install Exchange: o NNTP o HTTP o SMTP o World Wide Web o.net Framework Ensure that all relevant operating system security patches have been applied. Ensure that all relevant Exchange security patches have been applied. Exchange Administrator should require a User s network/domain username to be different than their alias. The possible threat in not following this recommendation: once a malicious user has access to your address, they now have a valid network/domain username to conduct malicious activity. The recommended settings only increase security. It is essential to continually monitor the latest in best security practices. Exchange Server 2003 can operate in two modes: Native mode and Mixed mode. In Native mode we can Rename and consolidate administrative groups, Define routing groups and administrative groups, Move mailboxes between servers in different administrative groups, Create an administrative group that spans multiple routing groups and Use query-based distribution groups. Does not allow Exchange 2003 to interoperate with Exchange 5.5 systems. Mixed mode does not provide the above mentioned functionality. It was designed for Exchange 2003 to interoperate with Exchange 5.5 systems, and is the default mode. If your environment contains Exchange 5.5 systems, mixed mode should be used. To switch from mixed mode to native mode, all of the Exchange servers in your organization must be Document Classification: Internal Page 3 of 46
5 Secure Configuration Document - MS Exchange 2003 Server running Exchange 2003 or Exchange Once the Exchange servers have been updated, the switch to Native mode can take place. Once the switch occurs, the change cannot be reversed, and the organization is no longer able to interoperate with Exchange 5.5 systems. Exchange 2003 servers can be configured to function as role based servers. That is as an HTTP server, IMAP server, POP 3 server, NNTP server or SMTP server. SMTP service must be running on every Exchange 2003 server. Without SMTP service, Exchange will not function. With OWA 2003, your organization s users can access their mailboxes using a Web browser. OWA 2003 has come a long way By default, the authentication method for accessing OWA is basic and/or Integrated Windows authentication, but actually there are five different authentication methods that can be used to validate your OWA users: Anonymous access: Enabling anonymous connections allows HTTP clients to access resources without specifying a Microsoft Windows 200x user account. Passwords for anonymous accounts are not verified; the password is only logged in the Windows 200x Event Log. By default, anonymous access is not enabled. The server creates and uses the account IUSR_computername. Integrated Windows authentication: The Integrated Windows authentication method is enabled by default (except on front-end servers). This authentication method also requires HTTP users to have a valid Windows 200x user account and password to access information. Users are not prompted for their account names and passwords; instead, the server negotiates with the Windows 2000 security packages installed on the client computer. This method allows the server to authenticate users without prompting them for information and without transmitting unencrypted information across the network. Digest authentication: Digest authentication works only with Active Directory accounts. It s quite secure because it sends a hash value over the network rather than a plaintext password, as is the case with basic authentication. Digest authentication works across proxy servers and other firewalls and is available on Web Distributed Authoring and Versioning (WebDAV) directories. To use this form of authentication, your clients must use Internet Explorer 5.0 or later. Basic authentication: Basic authentication transmits user passwords across the network as unencrypted information. Although this method allows users to access all Exchange resources, it is not very secure. To enhance security, it is strongly advised that you use SSL with basic authentication to encrypt all information. We will show you how to enable Secure Socket Layer (SSL) on your OWA virtual directories in the next section..net Passport authentication:.net Passport authentication allows your site s users to create a single sign-in name and password for easy, secure access to all.net Passport-enabled Web sites and services..net Passport-enabled sites rely on the.net Passport central server to authenticate users rather than hosting and Document Classification: Internal Page 4 of 46
6 Secure Configuration Document - MS Exchange 2003 Server maintaining their own proprietary authentication systems. However, the.net Passport central server does not authorize or deny a specific user s access to individual.net Passport-enabled sites. It is Web site s responsibility to control user permissions. Using.NET Passport authentication requires that a default domain be defined. You probably know the.net Passport authentication method from services such as Microsoft s MSN Hotmail and Messenger. Note that this authentication method can be set only through the IIS Manager, not the Exchange System Manager. As you can see in the Figures 5.7 and 5.8, you can set all types of authentication methods on either the HTTP Virtual folders in the exchange System Manager and/or on the OWA virtual directories under the Default Web Site in the IIS Manager. As a general rule, you should set the authentication methods through the Exchange System Manager whenever possible, and through the IIS Manager only as a last resort. Figure 1: Setting Authentication Methods Through Exchange System Manager Document Classification: Internal Page 5 of 46
7 Secure Configuration Document - MS Exchange 2003 Server Figure 2: Setting Authentication Methods Through IIS Document Classification: Internal Page 6 of 46
8 Secure Configuration Document - MS Exchange 2003 Server Table of Contents 1. SPECIFY BLOCK LIST SERVICE PROVIDER BLOCK LIST EXCEPTIONS SIZE OF SENDING/RECEIVING MESSAGES RECIPIENT LIMITS FILTER RECIPIENTS WHO ARE NOT IN DIRECTORY BLOCKING SPECIFIC RECIPIENT AND SENDER IDS.( OPTIONAL) ARCHIVE FILTERED MESSAGES FILTER MESSAGES WITH BLANK SENDER DROP CONNECTION IF ADDRESS MATCHES FILTER ACCEPT MESSAGES WITHOUT NOTIFYING SENDER OF FILTERING( OPTIONAL) AUTHENTICATING AND USING OUTLOOK MOBILE ACCESS OVER SECURED CONNECTION AUTHENTICATING AND USING USER INITIATED SYNCHRONIZATION OVER SECURED CONNECTION CERTIFICATE WIZARD ENABLE ANONYMOUS ACCESS AUTHENTICATION METHOD USING FORM BASED AUTHENTICATION METHOD TO ACCESS EXCHANGE VIRTUAL DIRECTORY OVER SECURED CONNECTION AUTHENTICATION METHOD TO ACCESS EXADMIN VIRTUAL DIRECTORY OVER SECURED CONNECTION AUTHENTICATION METHOD TO ACCESS PUBLIC VIRTUAL DIRECTORY OVER SECURED CONNECTION TCP PORT/SSL PORT LOG FILES TO MONITOR THE ACTIVITY ON THE SERVER AUTHENTICATION METHOD TO BE USED FOR ACCESS IMAP VIRTUAL DIRECTORY OVER SECURED CONNECTION CONNECTION TIME-OUT (MINUTES) EXCLUDE OR LIMIT CONNECTIONS BACKUP/RESTORE RETENTION DURATION FOR DELETED ITEMS RETENTION DURATION FOR DELETED MAILBOX ARCHIVE ALL MESSAGES SENT OR RECEIVED BY MAILBOXES STORAGE LIMITS OF MAILBOX STORES MOUNTING OF MAILBOX STORE WHEN EXCHANGE STARTS Document Classification: Internal Page 7 of 46
9 Secure Configuration Document - MS Exchange 2003 Server 30. ALLOW CONTROL MESSAGES Document Classification: Internal Page 8 of 46
10 1. Specify Block List Service Provider Description Block list services are the one that collect IP address of known spammers and other hostile parties. One can subscribe to these block list services and configure Exchange to use it to filter out/block messages from these IP addresses If IP filtering on an exchange server is not working the server is exposed to various threats and vulnerabilities caused by spammers. Block List service provider can configure by clicking the Add button under the Block list configuration list. Exchange System Manager Global Settings Message Delivery Properties Connection Filtering Tab Block List Service Configuration Add Button Use the DNS Suffix of subscribed Provider in the field to specify the block list provider. Block list Service provider will provide a value for this field. Please note that block list provider settings will not be in effect; unless the Apply connection filter checkbox is selected on SMTP Virtual Server. How to check Please ensure correct IP Blocking service provider DNS Suffix and other details in the following path. Exchange System Manager Global Settings Message Delivery Properties Connection Filtering Tab Block List Service Configuration Add Buton Applicable to Document Classification: Internal Page 4 of 46
11 2. Block List Exceptions Description Known Servers in internet found spamming, sending virus or executing other malicious activities can be marked in exception list of SMTP servers. Any s from these IPs ( SMTP Servers) can be blocked. Unblocked State of Blacklisted SMTP server/s on our Exchange server exposes the server to the threat of all kinds of malicious intend that can lead to security breaches. Add SMTP addresses that should not be blocked despite being in blacklist. Exchange System Manager Global Settings Message Delivery Properties Connection Filtering Tab Block List Service Configuration Exception Button How to check Exchange System Manager Global Settings Message Delivery Properties Connection Filtering Tab Block List Service Configuration Exception Button Applicable to Document Classification: Internal Page 5 of 46
12 3. Size of Sending/Receiving Messages Description These fields control the maximum size of acceptable outbound and inbound messages, respectively i.e. size of Sending/receiving message. This will reduce the network congestion and minimize the chance of internal users sending large messages to external parties. Absence of a limit on messages can cause congestion on mail and network traffic. The precise limits can vary depending on the need, message size at most should be set to <=10 MB. ( best practice) The appropriate value 10 MB or greater can be configured as per appropriate and applicable policy Selecting the no limit radio button on either field can be done if only specific users have legitimate need to send large messages. How to check Exchange System Manager Global Settings Message Deliver Properties Defaults Tab Sending message size and Receiving message size Applicable to Document Classification: Internal Page 6 of 46
13 4. Recipient Limits Description This field is used to control the maximum number of recipients that can be specified in a single message sent from the server Absence of any limit on number of senders in an can lead to the risk of mail traffic and congestion caused due to bulk mails. While the precise value of this control may vary between organizations, the maximum number of recipients per message should be <=100 How to check Ensure recipient limits are configured in the server as per applicable policy Exchange System Manager Global Settings Message Delivery Properties Defaults Tab Recipient limits Applicable To Document Classification: Internal Page 7 of 46
14 5. Filter Recipients who are not in Directory Description By blocking of recipients who are not listed in domain's Active Directory we are potentially telling whether such user exists in the domain. In absence of filters on recipients not listed in domain's Active Directory, sender can get a clue of user accounts in the system and can perform malicious activities. Clear the checkbox as this filter should not be applied because it would seem reasonable to want to immediately filter messages to recipients who are not in Active Directory since mail accounts are, in fact, stored in Active Directory. However, this feature can be used by external entities to determine whether a particular user exists in the Active Directory domain. By monitoring whether or not messages are filtered, an external entity could build a list of known accounts on the system. But if this feature is enabled then we have to make sure that addresses are different from Windows account usernames. How to check Exchange System Manager Global Settings Message Delivery Properties Recipient Filtering Tab Filter recipients who are not in the Directory Applicable to Document Classification: Internal Page 8 of 46
15 6. Blocking Specific Recipient and Sender ids.( Optional) Description administrator may need to block messages that are sent or received from specific ids/mailboxes Absence of such a feature can open a threat caused from specific internal or external ids. Specify and Block Recipients at following path: Exchange System Manager Global Settings Message Delivery Properties Recipient Filtering Specify and Block Senders at following path: Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Senders How to check Check and ensure sender and recipient ids are configured at following path if/as desired. Exchange System Manager Global Settings Message Delivery Properties Recipient Filtering Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Senders Applicable to Document Classification: Internal Page 9 of 46
16 7. Archive Filtered Messages Description Archiving of the messages that were blocked by the sender filter helps to recover messages that might have been inappropriately filtered. In absence of a backup of filtered messages, may result in delivering an important to expected mailbox (once traced.). Also it can lead to issues and inefficient incident tracking in the event of a security breach. This feature has to be enabled as it provides a backup copy of filtered messages. Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Archive filtered messages How to check Check if the feature is enabled at following path. Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Archive filtered messages Also check if filtered messages are being actually archived. Applicable to Document Classification: Internal Page 10 of 46
17 8. Filter Messages with Blank Sender Description All the messages with blank sender have to be blocked An unauthorized and malicious activity can go undetected and unnoticed. This feature has to be enabled by clicking at following option: Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Filter messages with blank sender How to check Check if following feature is enabled. Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Filter messages with blank sender Applicable to Document Classification: Internal Page 11 of 46
18 9. Drop Connection if Address Matches Filter Description This control allows specifying that any inbound connections from an address that has been filtered should be immediately dropped In absence of a feature to drop connections from suspected IPs can cause security beaches and malicious activities on the server. Enable this feature because by dropping the connection it will be the most effective way to handle the message as it minimizes the server s resources. Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Drop connection if address matches filter If enabled a malicious user who has successfully been able to relay a mail through the server will be thrown out of the connection immediately. Also the mail will be filtered out. How to check Check if the filtered IP addresses are dropped at following path. Exchange System Manager Global Settings Message Delivery Properties Sender Applicable to Filtering Tab Drop connection if address matches filter Document Classification: Internal Page 12 of 46
19 10. Accept Messages without Notifying Sender of Filtering( Optional) Description This feature allows filtering silently to avoid giving indications that messages were filtered to the sender. Giving indications to sender about filtering can suggest the malicious sender about the Server security and internal environment that can help the sender in performing further malicious activities. This feature can be enabled only when then Drop connection if address matches filter is disabled. (Note that Drop connection if address matches filter is even more efficient and secure configuration.) Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Accept messages without notifying sender of filtering How to check Exchange System Manager Global Settings Message Delivery Properties Sender Filtering Tab Accept messages without notifying sender of filtering Applicable to Document Classification: Internal Page 13 of 46
20 11. Authenticating and Using Outlook Mobile Access over secured connection Description OMA is used to provide an Outlook-like interface for mobile devices that offers many of the features of using Outlook itself. If Outlook Mobile access is enabled then Enable unsupported devices option will also be available potentially causing Exchange to provide OMA pages to any requesting devices. Opening OAM over an insecure connection exposes the server for malicious activities and security breaches. Disable this feature and delete the OMA virtual directory from IIS. If OMA is enabled it should Use default value of Basic authentication as Enabling Integrated Windows Authentication or Digest authentication is unlikely to have much of an effect since OMA cannot use these protocols. Enabled with Read permission Execute permission control can also be enabled to allows to specify whether scripts and/or executable may be run on this virtual server. Used over a secure connection with a policy regarding secure practices with mobile devices. But if a particular client application does not support secure communication this feature will need to be disabled or such client applications need to be upgraded with 128 bit encryption. How to check Configure OMA as per following steps: Exchange System Manager Global Settings Mobile Services Properties General Tab Outlook Mobile Access Enable Outlook Mobile Access and Enable unsupported devices Authentication IIS Manager [server] Web Sites Default Web Site OMA Properties Directory Security Tab Authentication and access control Edit Button Authenticated access (Multiple Items) With Read enabled IIS Manager [server] Web Sites Default Web Site Document Classification: Internal Page 14 of 46
21 OMA Properties Virtual Directory Tab Access Control (Multiple Items) With Execute Permission IIS Manager [server] Web Sites Default Web Site OMA Properties Virtual Directory Tab Execute permissions (Multiple Items) Over Secured Connection IIS Manager [server] Web Sites Default Web Site OMA Properties Directory Security Tab Secure communications Edit Button Require secure channel (SSL) (Multiple Items) Applicable to Document Classification: Internal Page 15 of 46
22 12. Authenticating and Using User Initiated Synchronization over secured connection Description Using ActiveSync one can synchronize , calendaring, and contact information between the Exchange server and Windows supporting mobile devices. Connection to ActiveSync Virtual directory should be carried with proper authentication. Unauthenticated and insecure synchronization between mobile user and Exchange server can lead to security breaches. Disable ActiveSync and delete Microsoft-Server-ActiveSync Virtual Directory from IIS. If ActiveSync is enabled it should Use default value of Basic authentication as Enabling Integrated Windows Authentication or Digest authentication is unlikely to have much of an effect since OMA cannot use these protocols. Enabled with Read permission Execute permission control can also be enabled to allows to specify whether scripts and/or executable may be run on this virtual server. Used over a secure connection with a policy regarding secure practices with mobile devices. But if a particular client application does not support secure communication this feature will need to be disabled or such client applications need to be upgraded with 128 bit encryption. To enable ActiveSync, Enable user initiated synchronization must be selected. This enables Enable up-to-date notifications checkbox to send out alerts to the user's mobile device when new mail has arrived. This in-turn gives the option of Enable notifications to user specified SMTP addresses checkbox which allows individual users to select their own wireless service provider for up-to-date notifications. Document Classification: Internal Page 16 of 46
23 Refer detailed steps in How to check section. How to check Exchange System Manager Global Settings Mobile Services Properties General Tab Exchange ActiveSync Enable user initiated synchronization/enable upto-date notifications/enable notifications to user specified SMTP addresses Authenticating IIS Manager [server] Web Sites Default Web Site Microsoft Server-ActiveSync Properties Directory Security Tab Authentication and access control Edit Button Authenticated access (Multiple Items) With Read enabled IIS Manager [server] Web Sites Default Web Site Microsoft-Server-ActiveSync Properties Virtual Directory Tab Access Control (Multiple Items) With Execute Permission IIS Manager [server] Web Sites Default Web Site Microsoft-Server-ActiveSync Properties Virtual Directory Tab Execute permissions (Multiple Items) Over Secured Connection IIS Manager [server] Web Sites Default Web Site Microsoft Server ActiveSync Properties Directory Security Tab Secure communications Edit Button Require secure channel (SSL) (Multiple Items). Applicable to.. Document Classification: Internal Page 17 of 46
24 13. Certificate Wizard Description Server certificates are required for many security features in Exchange, and without them the server cannot engage in many forms of secure communication. Certificate Wizard guides through the process of requesting a new certificate or of importing an existing certificate. Certificates must be manually installed on each virtual server. Use of any virtual server that has not been given a certificate should be considered a highly insecure. Execute Wizard to Install Certificate. Once a certificate is installed on one virtual server, any other virtual server (regardless of protocol used) may easily be configured to use this certificate by selecting Assign an existing certificate in the first page of the Wizard How to check For HTTP IIS Manager [server] Web Sites Default Web Site Properties Directory Security Tab Server Certificate Button Wizard Button For IMAP Exchange System Manager Administrative Groups [administrative group] Servers [server] Protocols IMAP4 [Specific IMAP4 Virtual Server] Properties Access Tab Certificate Button Wizard Button Applicable to HTTP Server, POP3 Server, IMAP4 Server, NNTP Server, and SMTP Server Document Classification: Internal Page 18 of 46
25 14. Enable Anonymous Access Description Exchange 2003 supports 3 types of authentication methods Anonymous access Basic Authentication Integrated Windows Authentication. Typically, you select anonymous access for servers that are directly connected to the Internet. If you select this check box, other servers on the Internet will not authenticate to this server prior to sending mail. For increased security, disable anonymous access on your internal SMTP virtual servers that do not accept incoming Internet mail. For similar security purposes, you can also disable anonymous access on dedicated SMTP virtual servers that are used for remote IMAP and POP users. If the Anonymous access check box is not selected on your Internet gateway servers, you may not receive incoming mail from the Internet. Hence anonymous access for a server accepting HTTP requests facing internet should be enabled. How to check In absence of anonymous access being enabled the server may not receive incoming mail from internet. Use the IUSR_<computer-name> account. This account is created for the processes that are created by anonymous Internet users and thus have a reduced access to the computer as a whole. Different user identities can be specified in this field, but they should not have greater access to the computer than the IUSR_<computer-name> account. IIS Manager [server] Web Sites Default Web Site Properties Directory Security Tab Authentication and access control Edit Button Enable anonymous access User name and Password. Document Classification: Internal Page 19 of 46
26 Applicable to Document Classification: Internal Page 20 of 46
27 15. Authentication Method Description This feature controls the authentication method used to connect to the virtual server and its virtual directories( Refer General Exchange Security Guidance section of this doc). The Integrated Windows authentication method is enabled by default. This authentication method also requires HTTP users to have a valid Windows 200x user account and password to access information. Users are not prompted for their account names and passwords; instead, the server negotiates with the Windows 2000 security packages installed on the client computer. This method allows the server to authenticate users without prompting them for information and without transmitting unencrypted information across the network In absence of appropriate authentication method and encryption, can cause security breaches. Out of the options available select integrated windows authentication checkbox. For any changes that are made to this panel, the IIS manager will give the administrator the option of having these changes applied to all the virtual directories residing on this virtual server. In general this option should not be exercised. Note that Integrated Windows Authentication cannot be used through frontend servers. How to check IIS Manager [server] Web Sites Default Web Site Properties Directory Security Tab Authentication and access control Edit Button Authenticated access (Multiple Items) Applicable to Document Classification: Internal Page 21 of 46
28 16. Using Form based Authentication Method to Access Exchange Virtual Directory over secured connection. Description The Exchange Virtual Directory called Outlook Web Access (OWA) is used to allow web access to user mail accounts using an Outlook client, through a web browser. Form based authentication stores user name and password information in the browser cookies. These cookies persist throughout the OWA session after which they are destroyed. If forms based authentication is not used, credentials remain for a much longer period of time, giving an unauthorized user a greater window of opportunity. Disable and delete the Exchange Virtual Directory from IIS. But if OWA is to be used Enable forms based authentication. Use the default authentication methods of Integrated Windows Authentication and Basic authentication over a secure connection with a policy regarding secure practices with mobile devices. Enabled with Read permission Execute permission control can also be enabled to allows to specify whether scripts and/or executables may be run on this virtual server. How check to For Exchange Virtual Directory Exchange System Manager Administrative Groups [administrative group] Servers [server] Protocols HTTP Exchange Virtual Server Exchange Properties Access Tab Authentication Settings Authentication Button Form Based Authentication [server] Protocols HTTP Exchange Virtual Server Properties Settings Tab Outlook Web Access Enable Forms Based Authentication Document Classification: Internal Page 22 of 46
29 With Read enabled [server] Protocols HTTP Exchange Virtual Server Exchange Properties Access Tab Access Control With Execute Permission [server] Protocols HTTP Exchange Virtual Server Exchange Properties Access Tab Execute permissions Over Secured Connection IIS Manager [server] Web Sites Default Web Site Exchange Properties Directory Security Tab Secure communications Edit Button Require secure channel (SSL) (Multiple Items) Over Secured Connection (IMAP4) [server] Protocols IMAP4 [Specific IMAP4 Virtual Server] Properties Calendaring Tab Use SSL connections Applicable to Document Classification: Internal Page 23 of 46
30 17. Authentication Method to Access Exadmin Virtual Directory over secured connection.. Description The Exadmin Virtual Directory, a required part of the Exchange application is used by the Exchange System Manager to access mailboxes and public folders. This feature controls the authentication method used to connect to this virtual directory. Integrated Windows Authentication is to be used to access Exadmin Virtual Directory. Clients can use secured connection to communicate with the virtual directory. ( Refer How to check section for exact details) Enabled with Read permission Execute permission control can also be enabled to allows to specify whether scripts and/or executables may be run on this virtual server. How to check Exchange System Manager Administrative Groups [administrative group] Servers [server] Protocols HTTP Exchange Virtual Server Exadmin Properties Access Tab Authentication Settings Authentication Button With Read enabled [server] Protocols HTTP Exchange Virtual Server Exadmin Properties Access Tab Access Control (Multiple Items) With Execute Permission [server] Protocols HTTP Exchange Virtual Server Exadmin Properties Access Tab Execute Permissions (Multiple Items) Over Secured Connection Document Classification: Internal Page 24 of 46
31 IIS Manager [server] Web Sites Default Web Site Exadmin Properties Directory Security Tab Secure communications Edit Button Require secure channel (SSL) (Multiple Items) Applicable to Document Classification: Internal Page 25 of 46
32 18. Authentication Method to Access Public Virtual Directory over secured connection.. Description The Public Virtual Directory is used to provide access to public folders. In absence of appropriate authentication method and encryption, can cause security breaches If Public folders are not used on the current exchange then delete and How to check remove by using IIS manager. If public folders are to be used, leave this feature at the default value of Integrated Windows Authentication and Basic authentication and use over a secure connection with a policy regarding secure practices with mobile devices. Enabled with Read permission Execute permission control can also be enabled to allows to specify whether scripts and/or executable may be run on this virtual server. For Public Virtual Directory Exchange System Manager Administrative Groups [Administrative group] Servers [server] Protocols HTTP Exchange Virtual Server Public Properties Access Tab Authentication Settings Authentication Button With Read enabled [server] Protocols HTTP Exchange Virtual Server Public Properties Access Tab Access Control With Execute Permission [server] Protocols HTTP Exchange Virtual Server Public Properties Access Tab Execute Permissions Over Secured Connection IIS Manager [server] Web Sites Default Web Site Public Properties Directory Document Classification: Internal Page 26 of 46
33 Security Tab Secure communications Edit Button Require secure channel (SSL) (Multiple Items) Applicable to Document Classification: Internal Page 27 of 46
34 19. TCP Port/SSL Port Description This controls the ports to which the standard and secured servers bind. If different ports are used, clients will need to be explicitly configured to use the non-standard ports. Changing the ports introduces a large amount of complexity for a relatively small gain. The standard ports should be used. 80 for HTTP and 443 for HTTPS 143 for regular IMAP And 993 for secured IMAP How to check For HTTP IIS Manager [server] Web Sites Default Web Site Properties Web Site Tab Web site identification TCP port and SSL port For IMAP [server] Protocols IMAP4 [Specific IMAP4 Virtual Server] Properties General Tab Advanced Button Edit Button TCP port and SSL port Applicable to Document Classification: Internal Page 28 of 46
35 20. Log files to monitor the activity on the server Description Log files keep the record of the attempts made to connect to the virtual server. Changing the ports introduces a large amount of complexity for a relatively small gain. The standard ports should be used. Enable logging. In the case of an attack on the HTTP server, these logs could contain useful details regarding the time and nature of the attack. Due to the size of log files, the files should be regularly copied to external storage and deleted from the server to conserve memory. How to check IIS Manager [server] Web Sites Default Web Site Properties Web Site Tab Enable Logging Applicable to Document Classification: Internal Page 29 of 46
36 21. Authentication Method to be used for Access IMAP Virtual Directory over secured connection Description This controls the form of authentication used by clients attempting to connect to this virtual server In absence of appropriate authentication method and encryption, can cause security breaches Select Basic authentication and Require SSL/TLS. The use of SSL/TLS not only protects the username and password during authentication, but encrypts the mail messages as they are being transmitted, preventing eavesdroppers from reading messages. NTLM (Simple Authentication and Security Layer checkbox), while it can protect the username and password during authentication, it does not provide encryption of message bodies How to check Exchange System Manager Administrative Groups [administrative group] Servers [server] Protocols IMAP4 [Specific IMAP4 Virtual Server] Properties Access Tab Access control Authentication Button Over Secured Connection Exchange System Manager Administrative Groups [administrative group] Servers [server] Protocols IMAP4 [Specific IMAP4 Virtual Server] Properties Access Tab Secure communication Communication Button Require Secure Channel and Require 128-bit encryption Applicable to Document Classification: Internal Page 30 of 46
37 22. Connection Time-out (Minutes) Description This controls the number of minutes that an idle connection to the IMAP server will be maintained before being dropped by the server. Dropping out of connections this ways helps in limiting the number of idle connections that the server maintains. In absence of appropriate authentication method and encryption, can cause security breaches The default value, minimum value and recommended value for this control is 30 minutes. However the value can be increased to desired value (if required) as per the steps in How to Check section. How to check [server] Protocols IMAP4 [Specific IMAP4 Virtual Server] Properties General Tab Connection time-out (minutes) Applicable to Document Classification: Internal Page 31 of 46
38 23. Exclude or Limit Connections Description This controls which IP addresses are allowed to connect to this virtual server to send or download messages. The control can be set to either allow all computers to connect except for a specified few, or to deny all computers except for a specified few. In absence of appropriate authentication method and encryption, can cause security breaches The recommended approach is to configure Only the list below however if required All except the list below can be selected with appropriate monitoring. Refer How to Check section to find detailed path to configure this option. Select Only the list below so that the administrator must explicitly specify which clients can connect to the IMAP Virtual Server. This significantly reduces the chance of unauthorized connections to the server If All except the list below must be selected, administrators should monitor connectivity to the IMAP server to ensure that no suspicious connections are being made. How to check Exchange System Manager Administrative Groups [administrative group] Servers [server] Protocols IMAP4 [Specific IMAP4 Virtual Server] Properties Access Tab Connection control Connection Button (Multiple Items) Applicable to HTTP Server, POP3 Server, IMAP4 Server, NNTP Server, and SMTP Server Document Classification: Internal Page 32 of 46
39 24. Backup/Restore Description Mailbox store backups should take place with or in addition to backups of the full server. In absence of appropriate authentication method and encryption, can cause security breaches Configure following options to ensure mailbox backups are managed appropriately. Refer How to Check section for complete path. Full backups of the mailbox store should occur at least on a weekly basis. Incremental backups of the mailbox store should occur at least on a daily basis. Maintenance should be taken daily for at least 4 hours manually and should be scheduled for periods when the load on the server is less. Ideally, the maintenance interval should take place after backups run. Mailboxes should not be deleted permanently until backup is taken. How to check Time of Last Full Backup [server] [storage group] Mailbox Store [server] Properties Database Tab Time of last fullbackup. Time of Last Incremental Backup [server] [storage group] Mailbox Store [server] Properties Database Tab Time of last incremental backup. Do Not Permanently Delete Mailboxes Until Backed Up [server] [storage group] Mailbox Store [server] Properties Limits Tab Deletion settings Do not permanently delete mailboxes and items until the store has been backed up Document Classification: Internal Page 33 of 46
40 Maintenance Interval [server] [storage group] Mailbox Store [server] Properties Database Tab Maintenance interval Database can be Overwritten by a Restore [server] [storage group] Mailbox Store [server] Properties Database Tab This database can be overwritten by a restore Applicable to Document Classification: Internal Page 34 of 46
41 25. Retention Duration for deleted Items Description How to check This controls the minimum number of days that a deleted item (such as an message) will be retained before it is purged from the system In absence of further retention of deleted items before completely purging the system can lead to accidental data loss. It is recommended that deleted messages be retained for 7 days before being purged. This strikes a balance between the desire to be able to recover deleted messages within a reasonable amount of time without resorting to backups, while at the same time reducing the amount of storage being consumed by deleted messages [server] [storage group] Mailbox Store [server] Properties Limits Tab Deletion settings Keep deleted items for (days) Applicable to Document Classification: Internal Page 35 of 46
42 26. Retention Duration for deleted Mailbox Description How to check This controls the minimum number of days that a deleted mailbox will be retained before it is purged from the system. It is recommended that deleted mailboxes be retained for 30 days before being purged. This gives a large amount of flexibility to easily restore a user s mailbox. [server] [storage group] Mailbox Store [server] Properties Limits Tab Deletion settings Keep deleted mailboxes for (days) Applicable to Document Classification: Internal Page 36 of 46
43 27. Archive All Messages Sent or Received by Mailboxes Description This controls whether messages that are received by or sent from a mailbox store should be archived. This feature is also called Journaling and is used to provide a paper trail of all correspondence that passes through the server. When the checkbox is selected, select a user, distribution list, contact, or public folder to whom all messages will be copied. [server] [storage group] Mailbox Store [server] Properties General Tab Archive all messages sent or received by mailboxes on this store How to check Ensure destination configuration for archiving Journaling in mailbox store [server] [storage group] Mailbox Store [server] Properties General Tab Archive all messages sent or received by mailboxes on this store Applicable to Document Classification: Internal Page 37 of 46
44 28. Storage limits of Mailbox Stores Description It controls the maximum size of a user s mailbox and the system s response if these limits are exceeded. If no limits are applied to a user s mailbox, the mailbox size is effectively unlimited. Ensure destination configuration for in mailbox store limits are defined at the path [server] [storage group] Mailbox Store [server] Properties Limits Tab Storage limits (Multiple Items) Provide storage limits for mailboxes to 2 MB(max) ( recommended best practice) Select all the 3 controls in Storage limits section of Limits tab which are Sending an warning message to the user alerting them that they have exceeded their mailbox quota. Preventing the user from sending , although they will still be able to receive messages. A warning message sent saying no further messages may be sent or received by the user. How to check Ensure destination configuration for in mailbox store limits are defined [server] [storage group] Mailbox Store [server] Properties Limits Tab Storage limits (Multiple Items) Applicable to Document Classification: Internal Page 38 of 46
45 29. Mounting of Mailbox Store when exchange starts Description This controls whether a Mailbox Store should be mounted when Exchange starts. Stores are usually only unmounted when manual maintenance is being performed on them. When a store is unmounted, its contents are inaccessible to other users. Unmounted storage on reboots can lead to issues in mail services due to inaccessibility o storage being mounted. Explore to following path [server] [storage group] Mailbox Store [server] Properties Database Tab Do not mount this store at start-up. Uncheck/Clear it. Doing this ensures that the store is mounted when Exchange starts and thus is accessible to users. If, however, conditions require that the store be unmounted (for example, maintenance), then this checkbox should be selected so that, Exchange should restart before maintenance is completed, it will not be inadvertently mounted in a bad state. Once the store is ready to mount again, the checkbox should be cleared so that the store will be remounted on boot as well How to check [server] [storage group] Mailbox Store [server] Properties Database Tab Do not mount this store at start-up. Applicable to Document Classification: Internal Page 39 of 46
46 30. Allow Control Messages Description Determine whether control messages can be used to perform simple administrative functions without direct oversight IN absence of administrative control on privileged activities, there can be impacts on services and data in production. [server] Protocols NNTP [specific NNTP Virtual Server] Properties Settings Tab Allow control messages Disable this feature at above path. This way, the ability to create and delete newsgroups remains the exclusive ability of administrators, instead of granted to anyone who can post to the special control newsgroups. However, if this feature (per-user control of NNTP directories) has to be enabled for specific users and computers, security must be applied to the NTFS security tab for the virtual directory folder within the Windows file structure. How to check [server] Protocols NNTP [specific NNTP Virtual Server] Properties Settings Tab Allow control messages Applicable to Document Classification: Internal Page 40 of 46
Configuring, Customizing, and Troubleshooting Outlook Express
 3 Configuring, Customizing, and Troubleshooting Outlook Express............................................... Terms you ll need to understand: Outlook Express Newsgroups Address book Email Preview pane
3 Configuring, Customizing, and Troubleshooting Outlook Express............................................... Terms you ll need to understand: Outlook Express Newsgroups Address book Email Preview pane
PineApp Archive-Secure Quick Installation Guide:
 PineApp Archive-Secure Quick Installation Guide: The following guide provides setup instructions for Archive-SeCure s quick implementation for your network environment. For further detailing and other
PineApp Archive-Secure Quick Installation Guide: The following guide provides setup instructions for Archive-SeCure s quick implementation for your network environment. For further detailing and other
Using Avaya Aura Messaging
 Using Avaya Aura Messaging Release 6.3.2 Issue 1 December 2014 Contents Chapter 1: Getting Started... 4 Messaging overview... 4 Prerequisites... 4 Accessing your mailbox from any phone... 4 Accessing the
Using Avaya Aura Messaging Release 6.3.2 Issue 1 December 2014 Contents Chapter 1: Getting Started... 4 Messaging overview... 4 Prerequisites... 4 Accessing your mailbox from any phone... 4 Accessing the
SonicWALL PCI 1.1 Implementation Guide
 Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
Compliance SonicWALL PCI 1.1 Implementation Guide A PCI Implementation Guide for SonicWALL SonicOS Standard In conjunction with ControlCase, LLC (PCI Council Approved Auditor) SonicWall SonicOS Standard
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling
 Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
F-Secure Messaging Security Gateway. Deployment Guide
 F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
F-Secure Messaging Security Gateway Deployment Guide TOC F-Secure Messaging Security Gateway Contents Chapter 1: Deploying F-Secure Messaging Security Gateway...3 1.1 The typical product deployment model...4
FileCloud Security FAQ
 is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
is currently used by many large organizations including banks, health care organizations, educational institutions and government agencies. Thousands of organizations rely on File- Cloud for their file
BlackBerry Enterprise Service 10. Secure Work Space for ios and Android Version: 10.1.1. Security Note
 BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
BlackBerry Enterprise Service 10 Secure Work Space for ios and Android Version: 10.1.1 Security Note Published: 2013-06-21 SWD-20130621110651069 Contents 1 About this guide...4 2 What is BlackBerry Enterprise
Neoteris IVE Integration Guide
 Neoteris IVE Integration Guide NESD-00090-00 CAY051402 The Secure Email Client upgrade option enables Neoteris IVE users to use standardsbased email clients to access corporate email from remote locations.
Neoteris IVE Integration Guide NESD-00090-00 CAY051402 The Secure Email Client upgrade option enables Neoteris IVE users to use standardsbased email clients to access corporate email from remote locations.
Sophos for Microsoft SharePoint startup guide
 Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Sophos for Microsoft SharePoint startup guide Product version: 2.0 Document date: March 2011 Contents 1 About this guide...3 2 About Sophos for Microsoft SharePoint...3 3 System requirements...3 4 Planning
Business mail 1 MS OUTLOOK CONFIGURATION... 2
 Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK CONFIGURATION... 2 1.1 Outlook 2007, 2010 and 2013 adding new exchange account, automatic
Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK CONFIGURATION... 2 1.1 Outlook 2007, 2010 and 2013 adding new exchange account, automatic
XGENPLUS SECURITY FEATURES...
 Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Security Features Table of Contents TABLE OF CONTENTS... 2 1. INTRODUCTION... 3 2. XGENPLUS SECURITY FEATURES... 3 3. SERVER LEVEL FEATURES... 5 4. DOMAIN LEVEL FEATURES... 8 5. USER LEVEL FEATURES...
Configuration Information
 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard. Other topics covered include Email Security interface navigation,
Click Studios. Passwordstate. Installation Instructions
 Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
74% 96 Action Items. Compliance
 Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Compliance Report PCI DSS 2.0 Generated by Check Point Compliance Blade, on July 02, 2013 11:12 AM 1 74% Compliance 96 Action Items Upcoming 0 items About PCI DSS 2.0 PCI-DSS is a legal obligation mandated
Neoteris IVE Integration Guide
 Neoteris IVE Integration Guide Published Date July 2015 The Secure Email Client upgrade option enables Neoteris IVE users to use standards based email clients to access corporate email from remote locations.
Neoteris IVE Integration Guide Published Date July 2015 The Secure Email Client upgrade option enables Neoteris IVE users to use standards based email clients to access corporate email from remote locations.
Exchange 2010. Outlook Profile/POP/IMAP/SMTP Setup Guide
 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide September, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Exchange 2010 Outlook Profile Configuration... 1 Outlook Profile
Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide September, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Exchange 2010 Outlook Profile Configuration... 1 Outlook Profile
Configuration Information
 Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Configuration Information Email Security Gateway Version 7.7 This chapter describes some basic Email Security Gateway configuration settings, some of which can be set in the first-time Configuration Wizard.
Kaseya Server Instal ation User Guide June 6, 2008
 Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
Kaseya Server Installation User Guide June 6, 2008 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector IT organizations. Kaseya's
HP A-IMC Firewall Manager
 HP A-IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW101-20110805 Legal and notice information Copyright 2011 Hewlett-Packard Development Company, L.P. No part of this
HP A-IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW101-20110805 Legal and notice information Copyright 2011 Hewlett-Packard Development Company, L.P. No part of this
If you encounter difficulty or need further assistance the Archdiocesan help desk can be reached at (410) 547-5305, option 1. Email Access Methods:
 ArchMail (www.archbalt.org/archmail) is a centrally hosted email system for the employees of the Archdiocese. To simplify employee access multiple methods for accessing email have been established. This
ArchMail (www.archbalt.org/archmail) is a centrally hosted email system for the employees of the Archdiocese. To simplify employee access multiple methods for accessing email have been established. This
Service Overview & Installation Guide
 Service Overview & Installation Guide Contents Contents... 2 1.0 Overview... 3 2.0 Simple Setup... 4 3.0 OWA Setup... 5 3.1 Receive Test... 5 3.2 Send Test... 6 4.0 Advanced Setup... 7 4.1 Receive Test
Service Overview & Installation Guide Contents Contents... 2 1.0 Overview... 3 2.0 Simple Setup... 4 3.0 OWA Setup... 5 3.1 Receive Test... 5 3.2 Send Test... 6 4.0 Advanced Setup... 7 4.1 Receive Test
Sonian Getting Started Guide October 2008
 Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
Sonian Getting Started Guide October 2008 Sonian, Inc. For Authorized Use Only 1 Create your new archiving account 3 Configure your firewall for IMAP collections 4 (Skip this step if you will be using
GREEN HOUSE DATA. E-Mail Services Guide. Built right. Just for you. greenhousedata.com. Green House Data 340 Progress Circle Cheyenne, WY 82007
 GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
GREEN HOUSE DATA Built right. Just for you. E-Mail Services Guide greenhousedata.com 1 Green House Data 340 Progress Circle Cheyenne, WY 82007 Table of Contents Getting Started on Business Class Email
MailEnable Connector for Microsoft Outlook
 MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
MailEnable Connector for Microsoft Outlook Version 2.23 This guide describes the installation and functionality of the MailEnable Connector for Microsoft Outlook. Features The MailEnable Connector for
Technical Note. Configuring Outlook Web Access with Secure WebMail Proxy for eprism
 Technical Note Configuring Outlook Web Access with Secure WebMail Proxy for eprism Information in this document is subject to change without notice. This document may be distributed freely only in whole,
Technical Note Configuring Outlook Web Access with Secure WebMail Proxy for eprism Information in this document is subject to change without notice. This document may be distributed freely only in whole,
Email: [email protected] Toll Free: 1-866-716-2040 International: 1-646-506-9354
 1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
1. Check your Welcome e-mail for login credentials for the control panel. 2. Using the login details in the welcome e-mail; login at https://cp.hostallapps.com Adding Domain: 1. On the Home Page of the
Preparing for GO!Enterprise MDM On-Demand Service
 Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
Preparing for GO!Enterprise MDM On-Demand Service This guide provides information on...... An overview of GO!Enterprise MDM... Preparing your environment for GO!Enterprise MDM On-Demand... Firewall rules
RoomWizard Synchronization Software Manual Installation Instructions
 2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
2 RoomWizard Synchronization Software Manual Installation Instructions Table of Contents Exchange Server Configuration... 4 RoomWizard Synchronization Software Installation and Configuration... 5 System
Click Studios. Passwordstate. Installation Instructions
 Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
Passwordstate Installation Instructions This document and the information controlled therein is the property of Click Studios. It must not be reproduced in whole/part, or otherwise disclosed, without prior
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows Mobile Phone ActiveSync setup & configuration Section 3 - Apple iphone
1 Accessing E-mail accounts on the Axxess Mail Server
 1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
1 Accessing E-mail accounts on the Axxess Mail Server The Axxess Mail Server provides users with access to their e-mail folders through POP3, and IMAP protocols, or OpenWebMail browser interface. The server
Installation and configuration guide
 Installation and Configuration Guide Installation and configuration guide Adding X-Username support to Forward and Reverse Proxy TMG Servers Published: December 2010 Applies to: Winfrasoft X-Username for
Installation and Configuration Guide Installation and configuration guide Adding X-Username support to Forward and Reverse Proxy TMG Servers Published: December 2010 Applies to: Winfrasoft X-Username for
GlobalSCAPE DMZ Gateway, v1. User Guide
 GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
GlobalSCAPE DMZ Gateway, v1 User Guide GlobalSCAPE, Inc. (GSB) Address: 4500 Lockhill-Selma Road, Suite 150 San Antonio, TX (USA) 78249 Sales: (210) 308-8267 Sales (Toll Free): (800) 290-5054 Technical
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Installing GFI MailSecurity
 Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
Installing GFI MailSecurity Introduction This chapter explains how to install and configure GFI MailSecurity. You can install GFI MailSecurity directly on your mail server or you can choose to install
Configuring your email client to connect to your Exchange mailbox
 Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
Configuring your email client to connect to your Exchange mailbox Contents Use Outlook Web Access (OWA) to access your Exchange mailbox... 2 Use Outlook 2003 to connect to your Exchange mailbox... 3 Add
ESET Mobile Security Business Edition for Windows Mobile
 ESET Mobile Security Business Edition for Windows Mobile Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security
ESET Mobile Security Business Edition for Windows Mobile Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Mobile Security
How to Install Microsoft Mobile Information Server 2002 Server ActiveSync. Joey Masterson
 How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson Copyright Information
How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson How to Install Microsoft Mobile Information Server 2002 Server ActiveSync Joey Masterson Copyright Information
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Microsoft Forefront TMG How to use SQL Server 2008 Express Reporting Services Abstract In this
Architecture and Data Flow Overview. BlackBerry Enterprise Service 10 721-08877-123 Version: 10.2. Quick Reference
 Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Architecture and Data Flow Overview BlackBerry Enterprise Service 10 721-08877-123 Version: Quick Reference Published: 2013-11-28 SWD-20131128130321045 Contents Key components of BlackBerry Enterprise
Barracuda Spam Firewall User s Guide
 Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2004, Barracuda Networks www.barracudanetworks.com All rights reserved. Use of this product and this manual is subject to license. Information
Barracuda Spam Firewall User s Guide 1 Copyright Copyright 2004, Barracuda Networks www.barracudanetworks.com All rights reserved. Use of this product and this manual is subject to license. Information
WEBROOT EMAIL ARCHIVING SERVICE. Getting Started Guide North America. The best security in an unsecured world. TM
 WEBROOT EMAIL ARCHIVING SERVICE Getting Started Guide North America Webroot Software, Inc. World Headquarters 2560 55th Street Boulder CO 80301 USA www.webroot.com 800.870.8102 Table of Contents Create
WEBROOT EMAIL ARCHIVING SERVICE Getting Started Guide North America Webroot Software, Inc. World Headquarters 2560 55th Street Boulder CO 80301 USA www.webroot.com 800.870.8102 Table of Contents Create
User Guide Online Backup
 User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
User Guide Online Backup Table of contents Table of contents... 1 Introduction... 2 Adding the Online Backup Service to your Account... 2 Getting Started with the Online Backup Software... 4 Downloading
NetBak Replicator 4.0 User Manual Version 1.0
 NetBak Replicator 4.0 User Manual Version 1.0 Copyright 2012. QNAP Systems, Inc. All Rights Reserved. 1 NetBak Replicator 1. Notice... 3 2. Install NetBak Replicator Software... 4 2.1 System Requirements...
NetBak Replicator 4.0 User Manual Version 1.0 Copyright 2012. QNAP Systems, Inc. All Rights Reserved. 1 NetBak Replicator 1. Notice... 3 2. Install NetBak Replicator Software... 4 2.1 System Requirements...
ONE Mail Direct for Desktop Software
 ONE Mail Direct for Desktop Software Version: 1 Document ID: 3931 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2015, ehealth Ontario All rights reserved No part of this document may
ONE Mail Direct for Desktop Software Version: 1 Document ID: 3931 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2015, ehealth Ontario All rights reserved No part of this document may
Configuration Task 3: (Optional) As part of configuration, you can deploy rules. For more information, see "Deploy Inbox Rules" below.
 Configure the E-mail Router After the E-mail Router has been installed, you can configure several aspects of it. Some of these configuration tasks are mandatory. Others are optional in that you use them
Configure the E-mail Router After the E-mail Router has been installed, you can configure several aspects of it. Some of these configuration tasks are mandatory. Others are optional in that you use them
Email Client configuration and migration Guide Setting up Thunderbird 3.1
 Email Client configuration and migration Guide Setting up Thunderbird 3.1 1. Open Mozilla Thunderbird. : 1. On the Edit menu, click Account Settings. 2. On the Account Settings page, under Account Actions,
Email Client configuration and migration Guide Setting up Thunderbird 3.1 1. Open Mozilla Thunderbird. : 1. On the Edit menu, click Account Settings. 2. On the Account Settings page, under Account Actions,
User guide Business Internet e-mail features
 User guide Business Internet e-mail features Page 1 de 1 Table of content Page Introduction 3 1. How do I access my web based e-mail? 3 2. How do I access/alter these enhancements? 3 A. Basic Features
User guide Business Internet e-mail features Page 1 de 1 Table of content Page Introduction 3 1. How do I access my web based e-mail? 3 2. How do I access/alter these enhancements? 3 A. Basic Features
Simplicity Itself. User Guide
 Simplicity Itself User Guide TekEx 2013 Contents WELCOME... 3 TEKEX OVERVIEW... 3 DOWNLOAD OUTLOOK... 4 CONFIGURE OUTLOOK... 5 CONFIGURE MAC EMAIL CLIENT... 10 SMARTPHONE SETUP... 12 IPHONE SETUP... 12
Simplicity Itself User Guide TekEx 2013 Contents WELCOME... 3 TEKEX OVERVIEW... 3 DOWNLOAD OUTLOOK... 4 CONFIGURE OUTLOOK... 5 CONFIGURE MAC EMAIL CLIENT... 10 SMARTPHONE SETUP... 12 IPHONE SETUP... 12
Kaspersky Lab Mobile Device Management Deployment Guide
 Kaspersky Lab Mobile Device Management Deployment Guide Introduction With the release of Kaspersky Security Center 10.0 a new functionality has been implemented which allows centralized management of mobile
Kaspersky Lab Mobile Device Management Deployment Guide Introduction With the release of Kaspersky Security Center 10.0 a new functionality has been implemented which allows centralized management of mobile
www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013
 www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
www.novell.com/documentation Server Installation ZENworks Mobile Management 2.7.x August 2013 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this
PREMIUM MAIL ADMINISTRATOR GUIDE
 PREMIUM MAIL ADMINISTRATOR GUIDE WHO THIS USER GUIDE IS FOR This document is for the: Administrator of the BigPond Premium Mail service. Users who have purchased the Solo Manager or a Solo Manager Plus
PREMIUM MAIL ADMINISTRATOR GUIDE WHO THIS USER GUIDE IS FOR This document is for the: Administrator of the BigPond Premium Mail service. Users who have purchased the Solo Manager or a Solo Manager Plus
HTTP connections can use transport-layer security (SSL or its successor, TLS) to provide data integrity
 Improving File Sharing Security: A Standards Based Approach A Xythos Software White Paper January 2, 2003 Abstract Increasing threats to enterprise networks coupled with an ever-growing dependence upon
Improving File Sharing Security: A Standards Based Approach A Xythos Software White Paper January 2, 2003 Abstract Increasing threats to enterprise networks coupled with an ever-growing dependence upon
Installation and configuration guide
 Installation and Configuration Guide Installation and configuration guide Adding X-Forwarded-For support to Forward and Reverse Proxy TMG Servers Published: May 2010 Applies to: Winfrasoft X-Forwarded-For
Installation and Configuration Guide Installation and configuration guide Adding X-Forwarded-For support to Forward and Reverse Proxy TMG Servers Published: May 2010 Applies to: Winfrasoft X-Forwarded-For
PureMessage for Microsoft Exchange Help. Product version: 4.0
 PureMessage for Microsoft Exchange Help Product version: 4.0 Document date: July 2013 Contents 1 About PureMessage for Microsoft Exchange...3 2 Key concepts...4 3 Administration console...7 4 Monitoring...9
PureMessage for Microsoft Exchange Help Product version: 4.0 Document date: July 2013 Contents 1 About PureMessage for Microsoft Exchange...3 2 Key concepts...4 3 Administration console...7 4 Monitoring...9
Exchange 2013 mailbox setup guide
 Fasthosts Customer Support Exchange 2013 mailbox setup guide This article covers the setup of Exchange 2013 mailboxes in Microsoft Outlook 2013, 2010 and Outlook 2011 for Mac. Contents Exchange 2013 Mailbox
Fasthosts Customer Support Exchange 2013 mailbox setup guide This article covers the setup of Exchange 2013 mailboxes in Microsoft Outlook 2013, 2010 and Outlook 2011 for Mac. Contents Exchange 2013 Mailbox
Installing Policy Patrol on a separate machine
 Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Policy Patrol 3.0 technical documentation July 23, 2004 Installing Policy Patrol on a separate machine If you have Microsoft Exchange Server 2000 or 2003 it is recommended to install Policy Patrol on the
Installation Guide for Pulse on Windows Server 2008R2
 MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
MadCap Software Installation Guide for Pulse on Windows Server 2008R2 Pulse Copyright 2014 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software
Updated: 7/10/2013 Author: Tim Unten
 Office 365 Email Access Updated: 7/10/2013 Author: Tim Unten Contents Outlook 2010 Setup off DOP Network... 1 Outlook 2010 Setup on DOP Network... 2 Outlook 2010 Manual Setup... 2 Android Setup... 3 iphone/ipad
Office 365 Email Access Updated: 7/10/2013 Author: Tim Unten Contents Outlook 2010 Setup off DOP Network... 1 Outlook 2010 Setup on DOP Network... 2 Outlook 2010 Manual Setup... 2 Android Setup... 3 iphone/ipad
Exchange Server Cookbook
 Exchange Server Cookbook Paul Robichaux, Missy Koslosky, and Devin t. Ganger CREILLT Beijing Cambridge Farnham Köln Paris Sebastopol Taipei Tokyo Table of Contents Preface xi 1. Getting Started 1 Cooking
Exchange Server Cookbook Paul Robichaux, Missy Koslosky, and Devin t. Ganger CREILLT Beijing Cambridge Farnham Köln Paris Sebastopol Taipei Tokyo Table of Contents Preface xi 1. Getting Started 1 Cooking
Managing, Monitoring, and Troubleshooting the Exchange Organization...
 6 Managing, Monitoring, and Troubleshooting the Exchange Organization............................................... Terms you ll need to understand: Back-end server Child folder Default public folder
6 Managing, Monitoring, and Troubleshooting the Exchange Organization............................................... Terms you ll need to understand: Back-end server Child folder Default public folder
Grapevine Mail User Guide
 Grapevine Mail User Guide Table of Contents Accessing Grapevine Mail...2 How to access the Mail portal... 2 How to login... 2 Grapevine Mail user guide... 5 Copying your contacts to the new Grapevine Mail
Grapevine Mail User Guide Table of Contents Accessing Grapevine Mail...2 How to access the Mail portal... 2 How to login... 2 Grapevine Mail user guide... 5 Copying your contacts to the new Grapevine Mail
TELSTRA BUSINESS MAIL QUICK REFERENCE GUIDE
 1.1 Introduction 01 1.2 The Checklist 02 1.3 Business Mail Requirements 03 1.4 Downloading & Installing Outlook 2003 04 BEFORE YOU START 1.1 INTRODUCTION 1.1.1 Who this Guide is For 1.1.2 What s in this
1.1 Introduction 01 1.2 The Checklist 02 1.3 Business Mail Requirements 03 1.4 Downloading & Installing Outlook 2003 04 BEFORE YOU START 1.1 INTRODUCTION 1.1.1 Who this Guide is For 1.1.2 What s in this
Deployment Guide. For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php
 Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
Deployment Guide For the latest version of this document please go to: http://www.exchangedefender.com/documentation.php ExchangeDefender Introduction The purpose of this guide is to familiarize you with
Business mail 1 MS OUTLOOK RECONFIGURATION DUE TO SYSTEM MIGRATION... 2
 Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK RECONFIGURATION DUE TO SYSTEM MIGRATION... 2 1.1 Deleting existing Exchange e-mail accounts...
Business mail Instructions for configuration of Outlook, 2007, 2010, 2013 and mobile devices CONTENT 1 MS OUTLOOK RECONFIGURATION DUE TO SYSTEM MIGRATION... 2 1.1 Deleting existing Exchange e-mail accounts...
HP IMC Firewall Manager
 HP IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW102-20120420 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P. No part of this
HP IMC Firewall Manager Configuration Guide Part number: 5998-2267 Document version: 6PW102-20120420 Legal and notice information Copyright 2012 Hewlett-Packard Development Company, L.P. No part of this
Kerio Connect. Step-by-Step. Kerio Technologies
 Kerio Connect Step-by-Step Kerio Technologies 2011 Kerio Technologies s.r.o. All rights reserved. This guide provides detailed description on Kerio Connect, version 7.2. All additional modifications and
Kerio Connect Step-by-Step Kerio Technologies 2011 Kerio Technologies s.r.o. All rights reserved. This guide provides detailed description on Kerio Connect, version 7.2. All additional modifications and
IsItUp Quick Start Manual
 IsItUp - When you need to know the status of your network Taro Software Inc. Website: www.tarosoft.com Telephone: 703-405-4697 Postal address: 8829 110th Lane, Seminole Fl, 33772 Electronic mail: [email protected]
IsItUp - When you need to know the status of your network Taro Software Inc. Website: www.tarosoft.com Telephone: 703-405-4697 Postal address: 8829 110th Lane, Seminole Fl, 33772 Electronic mail: [email protected]
Migrating Exchange Server to Office 365
 Migrating Exchange Server to Office 365 By: Brien M. Posey CONTENTS Domain Verification... 3 IMAP Migration... 4 Cut Over and Staged Migration Prep Work... 5 Cut Over Migrations... 6 Staged Migration...
Migrating Exchange Server to Office 365 By: Brien M. Posey CONTENTS Domain Verification... 3 IMAP Migration... 4 Cut Over and Staged Migration Prep Work... 5 Cut Over Migrations... 6 Staged Migration...
MobileStatus Server Installation and Configuration Guide
 MobileStatus Server Installation and Configuration Guide Guide to installing and configuring the MobileStatus Server for Ventelo Mobilstatus Version 1.2 June 2010 www.blueposition.com All company names,
MobileStatus Server Installation and Configuration Guide Guide to installing and configuring the MobileStatus Server for Ventelo Mobilstatus Version 1.2 June 2010 www.blueposition.com All company names,
Sophos UTM Web Application Firewall for Microsoft Exchange connectivity
 How to configure Sophos UTM Web Application Firewall for Microsoft Exchange connectivity This article explains how to configure your Sophos UTM 9.2 to allow access to the relevant Microsoft Exchange services
How to configure Sophos UTM Web Application Firewall for Microsoft Exchange connectivity This article explains how to configure your Sophos UTM 9.2 to allow access to the relevant Microsoft Exchange services
How to Secure a Groove Manager Web Site
 How to Secure a Groove Manager Web Site Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the companies, organizations,
How to Secure a Groove Manager Web Site Information in this document, including URL and other Internet Web site references, is subject to change without notice. Unless otherwise noted, the companies, organizations,
Exchange 2010. Outlook Profile/POP/IMAP/SMTP Setup Guide
 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide Document Revision Date: Nov. 13, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Introduction... 1 Exchange 2010 Outlook
Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide Document Revision Date: Nov. 13, 2013 Exchange 2010 Outlook Profile/POP/IMAP/SMTP Setup Guide i Contents Introduction... 1 Exchange 2010 Outlook
8.7. NET SatisFAXtion Email Gateway Installation Guide. For NET SatisFAXtion 8.7. Contents
 NET SatisFAXtion Email Gateway Installation Guide For NET SatisFAXtion 8.7 Contents Install Microsoft Virtual SMTP Server 2 XP and 2003 2 2008 and 2008 R2 2 Windows 7 2 Upgrade Path 2 Configure Microsoft
NET SatisFAXtion Email Gateway Installation Guide For NET SatisFAXtion 8.7 Contents Install Microsoft Virtual SMTP Server 2 XP and 2003 2 2008 and 2008 R2 2 Windows 7 2 Upgrade Path 2 Configure Microsoft
Server Software Installation Guide
 Server Software Installation Guide This guide provides information on...... The architecture model for GO!Enterprise MDM system setup... Hardware and supporting software requirements for GO!Enterprise
Server Software Installation Guide This guide provides information on...... The architecture model for GO!Enterprise MDM system setup... Hardware and supporting software requirements for GO!Enterprise
ensure prompt restart of critical applications and business activities in a timely manner following an emergency or disaster
 Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Security Standards Symantec shall maintain administrative, technical, and physical safeguards for the Symantec Network designed to (i) protect the security and integrity of the Symantec Network, and (ii)
Transport server data paths
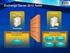 1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
1 of 14 14/11/2011 2:45 PM Applies to: Exchange Server 2010 SP1 Topic Last Modified: 2011-04-22 This topic provides information about ports, authentication, and for all data paths used by Microsoft Exchange
www.novell.com/documentation Administration Guide Novell Filr 1.0.1 May 2014
 www.novell.com/documentation Administration Guide Novell Filr 1.0.1 May 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
www.novell.com/documentation Administration Guide Novell Filr 1.0.1 May 2014 Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation,
CHARTER BUSINESS custom hosting faqs 2010 INTERNET. Q. How do I access my email? Q. How do I change or reset a password for an email account?
 Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
Contents Page Q. How do I access my email? Q. How do I change or reset a password for an email account? Q. How do I forward or redirect my messages to a different email address? Q. How do I set up an auto-reply
BUILT FOR YOU. Contents. Cloudmore Exchange
 BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
BUILT FOR YOU Introduction is designed so it is as cost effective as possible for you to configure, provision and manage to a specification to suit your organisation. With a proven history of delivering
PREMIUM MAIL USER GUIDE
 PREMIUM MAIL USER GUIDE WHO THIS USER GUIDE IS FOR This document is for users of BigPond Premium Mail. It describes the features of BigPond Premium Mail from a user s perspective. It contains: A general
PREMIUM MAIL USER GUIDE WHO THIS USER GUIDE IS FOR This document is for users of BigPond Premium Mail. It describes the features of BigPond Premium Mail from a user s perspective. It contains: A general
9236245 Issue 2EN. Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation
 9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
9236245 Issue 2EN Nokia and Nokia Connecting People are registered trademarks of Nokia Corporation Nokia 9300 Configuring connection settings Legal Notice Copyright Nokia 2005. All rights reserved. Reproduction,
Deploying the Barracuda Load Balancer with Microsoft Exchange Server 2010 Version 2.6. Introduction. Table of Contents
 Deploying the Barracuda Load Balancer with Microsoft Exchange Server 2010 Version 2.6 Introduction Organizations use the Barracuda Load Balancer to distribute the load and increase the availability of
Deploying the Barracuda Load Balancer with Microsoft Exchange Server 2010 Version 2.6 Introduction Organizations use the Barracuda Load Balancer to distribute the load and increase the availability of
User Guide. Version 3.0 April 2006
 User Guide Version 3.0 April 2006 2006 Obvious Solutions Inc. All rights reserved. Dabra and Dabra Network are trademarks of Obvious Solutions Inc. All other trademarks owned by their respective trademark
User Guide Version 3.0 April 2006 2006 Obvious Solutions Inc. All rights reserved. Dabra and Dabra Network are trademarks of Obvious Solutions Inc. All other trademarks owned by their respective trademark
Locking down a Hitachi ID Suite server
 Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Locking down a Hitachi ID Suite server 2016 Hitachi ID Systems, Inc. All rights reserved. Organizations deploying Hitachi ID Identity and Access Management Suite need to understand how to secure its runtime
Apple Mail... 36 Outlook Web Access (OWA)... 38 Logging In... 38 Changing Passwords... 39 Mobile Devices... 40 Blackberry...
 Contents Email Accounts... 3 Adding accounts... 3 Account Modifications... 6 Adding Aliases... 7 Primary E-mail Addresses... 10 Mailbox Quotas... 12 Removing accounts... 13 Mail Forwarding and Distribution
Contents Email Accounts... 3 Adding accounts... 3 Account Modifications... 6 Adding Aliases... 7 Primary E-mail Addresses... 10 Mailbox Quotas... 12 Removing accounts... 13 Mail Forwarding and Distribution
BOTTOM UP THINKING EMAIL SETUP INSTRUCTIONS. Unique businesses require unique solutions CLIENT GUIDE
 BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
BOTTOM UP THINKING Unique businesses require unique solutions EMAIL SETUP INSTRUCTIONS CLIENT GUIDE INDEX How to connect a. Deciding on best method (POP or IMAP) Setting up email on devices Webmail a.
WhatsUp Gold v16.3 Installation and Configuration Guide
 WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
WhatsUp Gold v16.3 Installation and Configuration Guide Contents Installing and Configuring WhatsUp Gold using WhatsUp Setup Installation Overview... 1 Overview... 1 Security considerations... 2 Standard
Web Plus Security Features and Recommendations
 Web Plus Security Features and Recommendations (Based on Web Plus Version 3.x) Centers for Disease Control and Prevention National Center for Chronic Disease Prevention and Health Promotion Division of
Web Plus Security Features and Recommendations (Based on Web Plus Version 3.x) Centers for Disease Control and Prevention National Center for Chronic Disease Prevention and Health Promotion Division of
Zimbra Connector for Microsoft Outlook User Guide 7.1
 Zimbra Connector for Microsoft Outlook User Guide 7.1 March 2011 Legal Notices Copyright 2005-2011 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual
Zimbra Connector for Microsoft Outlook User Guide 7.1 March 2011 Legal Notices Copyright 2005-2011 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual
Copyright http://support.oracle.com/
 Primavera Portfolio Management 9.0 Security Guide July 2012 Copyright Oracle Primavera Primavera Portfolio Management 9.0 Security Guide Copyright 1997, 2012, Oracle and/or its affiliates. All rights reserved.
Primavera Portfolio Management 9.0 Security Guide July 2012 Copyright Oracle Primavera Primavera Portfolio Management 9.0 Security Guide Copyright 1997, 2012, Oracle and/or its affiliates. All rights reserved.
EXAM - 70-662. TS: Microsoft Exchange Server 2010, Configuring. Buy Full Product. http://www.examskey.com/70-662.html
 Microsoft EXAM - 70-662 TS: Microsoft Exchange Server 2010, Configuring Buy Full Product http://www.examskey.com/70-662.html Examskey Microsoft 70-662 exam demo product is here for you to test the quality
Microsoft EXAM - 70-662 TS: Microsoft Exchange Server 2010, Configuring Buy Full Product http://www.examskey.com/70-662.html Examskey Microsoft 70-662 exam demo product is here for you to test the quality
Outlook Synchronisation guide
 Outlook Synchronisation guide Contents Introduction... 2 Installing Outlook Synchronisation Plug-in... 3 Daily Use of Outlook and webcrm... 6 Synchronising Emails... 7 Synchronising Contacts... 8 Contact
Outlook Synchronisation guide Contents Introduction... 2 Installing Outlook Synchronisation Plug-in... 3 Daily Use of Outlook and webcrm... 6 Synchronising Emails... 7 Synchronising Contacts... 8 Contact
What browsers can I use to view my mail?
 How to use webmail. This tutorial is our how-to guide for using Webmail. It does not cover every aspect of Webmail; What browsers can I use to view my mail? Webmail supports the following browsers: Microsoft
How to use webmail. This tutorial is our how-to guide for using Webmail. It does not cover every aspect of Webmail; What browsers can I use to view my mail? Webmail supports the following browsers: Microsoft
Using WinGate 6 Email. Concepts, Features, and Configurations.
 WinGate Feature Guide Using WinGate 6 Email Concepts, Features, and Configurations. Neil Gooden Qbik New Zealand Limited Rev 1.0 December 2004 2 Introduction...3 Basic Email Concepts... 3 Differences in
WinGate Feature Guide Using WinGate 6 Email Concepts, Features, and Configurations. Neil Gooden Qbik New Zealand Limited Rev 1.0 December 2004 2 Introduction...3 Basic Email Concepts... 3 Differences in
8.6. NET SatisFAXtion Email Gateway Installation Guide. For NET SatisFAXtion 8.6. Contents
 NET SatisFAXtion Email Gateway Installation Guide For NET SatisFAXtion 8.6 Contents 1.0 - Install Microsoft Virtual SMTP Server 2 XP and 2003 2 2008 and 2008 R2 2 Windows 7 2 Upgrade Path 2 Configure Microsoft
NET SatisFAXtion Email Gateway Installation Guide For NET SatisFAXtion 8.6 Contents 1.0 - Install Microsoft Virtual SMTP Server 2 XP and 2003 2 2008 and 2008 R2 2 Windows 7 2 Upgrade Path 2 Configure Microsoft
WineWeb Email Account Services
 As part of WineWeb s website services, we can provide email accounts under your domain name. Although this is optional, almost all of our clients use our mail server for their email accounts. We run the
As part of WineWeb s website services, we can provide email accounts under your domain name. Although this is optional, almost all of our clients use our mail server for their email accounts. We run the
Quick Start Guide. Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca!
 Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
Quick Start Guide Cerberus FTP is distributed in Canada through C&C Software. Visit us today at www.ccsoftware.ca! How to Setup a File Server with Cerberus FTP Server FTP and SSH SFTP are application protocols
