MAIL-2-TRACY USER GUIDE. This document replaces revision D of this document.
|
|
|
- Julius Daniels
- 10 years ago
- Views:
Transcription
1 DESCRIPTION 1 (5) MAIL-2-TRACY USER GUIDE This document replaces revision D of this document. Abstract This document describes the use of MAIL-2-TRACY to transfer tracability data from Contract Manufacturers ( CM ) to the Ericsson central tracability database TRACY. This document does not cover the interface between the local system Bartrack and TRACY. Please ask the supplier for Bartrack (Prevas AB) for information about Bartrack. The interface between the CM and Ericsson is built on . The sent from the CM will be processed automatically by the MAIL-2-TRACY server. A message will be returned from the MAIL-2-TRACY server to acknowledge that the tracability data has been received by Ericsson. This message will always be sent back to the original sender. Results from request and subscriptions will also be sent to the CM using the Mail-2-TRACY server.
2 DESCRIPTION 2 (5) 1 FORMAT OF THE TRACABILITY (TRACY) FILE The file sent to MAIL-2-TRACY shall follow the format defined for tracability files as described in the Ericsson Corporate Standard document Transmission of Information on Individual Marking to the central Data Base TRACY (Ericsson document no CRL Uen). All records types may be mixed in the same transfer, if needed. The files with the TRACY information should have unique names as they are saved as a backup in MAIL-2-TRACY. Max length of file name = 30! 2 MAIL FORMAT Depending on the platform used at the client side, a number of differentmethods and tools may be used to transfer the TRACY file to Ericsson. The table below gives an overview of this for three different client types : Client typ Direction File compression tool Mail encoding PC / Windows To Ericsson PKZIP / WinZip MIME attachment PC / Windows From Ericsson PKZIP / WinZip MIME attachment UNIX To Ericsson Compress or ZIP uuencode UNIX From Ericsson Compress or ZIP uuencode OpenVMS To Ericsson ZIP MFTU OpenVMS From Ericsson ZIP MFTU 2.1 NOTES ABOUT THE PC CLIENT TYPE Before being sent, the file should be compressed by PKZIP or WinZip. Note that gzip will not work and should be avoided. When sent, the ZIP file shall be attached to the mail as a MIME compliant BASE64 encoded attachment (standard attachment format in most mail client tools, such as Microsoft Outlook). Each ZIP file should contain just one (1) TRACY file. Each mail should contain just one (1) ZIP file.
3 DESCRIPTION 3 (5) 2.2 NOTES ABOUT THE UNIX CLIENT TYPE The Compress/Uncompress and UUencode/UUdecode tools are standard tools included in most or all different UNIX implementations. ZIP can also be used instead of Compress. Since there may be minor differences between UNIX es, some testing may be needed to verify that all is working as expected. Each compressed file should contain just one (1) TRACY file. Each mail should contain just one (1) compressed file. 2.3 NOTES ABOUT THE OPENVMS CLIENT TYP ZIP and UNZIP is the version of ZIP/UNZIP that is ported to OpenVMS. (Note that this is not the same tool as the gzip. gzip should not be used.) MFTU (Mail File Transfer Utility) is a tool for OpenVMS that codes binary files in a way so they can be sent by . Each ZIP file should contain just one (1) TRACY file. Each mail should contain just one (1) ZIP file.
4 DESCRIPTION 4 (5) 3 THE SUBJECT OF THE MAIL The Subject of the mail should include a string consisting of the site code and the text -FILE. E.g. if the site code is A01, the Subject must include A01-FILE. It could include other text, but the string as described above must also be included in the subject. N.B. Do not replace the text -FILE with the actual filename in the mail! 4 MAIL ADDRESS The mail shall be sent to: [email protected] 5 RESULT MAIL When the mail have been processed by the MAIL-2-TRACY server, a result mail with a log is returned to the sender of the mail. An example of one of this messages follows: :21 Processing of MAIL-2-TRACY started :21 Mail received from : [mail address] :21 Subject of mail : [file name} :21 Site code : [site code] :21 (Using new TRACY format) :21 Unique ID : :21 Bartrack ID : :21 Processing of file TRCY SAV started :21 Number of E-records in file : :21 Transferred to TRACY OK :21 File TRCY SAV sent :21 Processing of MAIL-2-TRACY ended Any questions about Mail-2-TRACY can be forwardedto: [email protected] Regards Mail-2-TRACY operations The actual content of this message may vary depending on the content of the file sent to Ericsson. The texts [mail address], [site code], [file name] are replaced with values from the actual transfer. There may be one or more lines with Number of?-records in file : nnn depending on the record types sent in the TRACY file. The text Transferred to TRACY OK shows that all has been processed successfully.
5 DESCRIPTION 5 (5) The Unique ID : is used to identify each transfer and may be used in communications with the Mail-2-TRACY support at Ericsson to make fault tracing easier. 6 REQUEST ANSWER When sending Y-records, a mail will be sent back to the sender with the basic individual information that corresponds to the actual Y-records. The subject of the mail will be TRACY-file <site> <Unique-ID>, where <site> is the actual site code and <Unique-ID> is the same unique ID as in the Result mail described in chapter 4. The TRACY file will be coded according to the table in chapter MAIL FORMAT depending on the client type of the actual site. 7 SUBSCRIPTIONS External sites that have subscriptions set up in TRACY to receive tracability information from other sites, will get this as s coded according to the table in chapter MAIL FORMAT depending on the client type of the actual site. 8 GETTING HELP 8.1 SUPPORT. Problems and other questions regarding the use of MAIL-2-TRACY, may be sent the MAIL-2-TRACY support mail address. See mail address below. Problems or questions regarding tracability in general or other matters regarding the business relation between the Contract Manufacturer and Ericsson, must be directed through proper channels, not through the support mail address mentioned below. Matters about MAIL-2-TRACY may be sent (by the local contact person) to : [email protected] Specify the following in the mail : The Unique ID :, if available. Your site code. A description of the actual problem or question. The name of the file transmitted and when the original mail was sent.
File Transfer Protocol. What is Anonymous FTP? What is FTP?
 File Transfer Protocol (FTP) File Transfer Protocol Sometimes browsing for information is not sufficient you may want to obtain copies of software programs or data files for your own use and manipulation.
File Transfer Protocol (FTP) File Transfer Protocol Sometimes browsing for information is not sufficient you may want to obtain copies of software programs or data files for your own use and manipulation.
tips A quick and easy guide to securing your private information www.pkware.com
 tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
tips A quick and easy guide to securing your private information tips A quick and easy guide to securing your private information Basic Information 1. How to install SecureZIP for Windows Desktop for individual
Secure Data Transfer
 Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
EDI Support Services
 EDI Support Services User Documentation: Bulletin Board System (BBS) Dialing and Logging into the BBS To submit electronic files to EDISS, Trading Partners log into the BBS with a unique ID issued by EDISS.
EDI Support Services User Documentation: Bulletin Board System (BBS) Dialing and Logging into the BBS To submit electronic files to EDISS, Trading Partners log into the BBS with a unique ID issued by EDISS.
Setting up secure e-mail communication with Ericsson. Guideline for Ericsson partners
 Setting up secure e-mail communication with Ericsson Guideline for Ericsson partners In this presentation Introduction Technical prerequisites Getting started Exchanging Public Keys Sending a signed e-mail
Setting up secure e-mail communication with Ericsson Guideline for Ericsson partners In this presentation Introduction Technical prerequisites Getting started Exchanging Public Keys Sending a signed e-mail
1. Navigate to Control Panel and click on User Accounts and Family Safety. 2. Click on User Accounts
 This document will guide you through setting up your outgoing server (SMTP) Microsoft Outlook and Windows Live Mail. There is also a section below that guides you through the manual configuration of your
This document will guide you through setting up your outgoing server (SMTP) Microsoft Outlook and Windows Live Mail. There is also a section below that guides you through the manual configuration of your
Module 16: Some Other Tools in UNIX
 Module 16: Some Other Tools in UNIX We have emphasized throughout that the philosophy of Unix is to provide - (a) a large number of simple tools and (b) methods to combine these tools in flexible ways.
Module 16: Some Other Tools in UNIX We have emphasized throughout that the philosophy of Unix is to provide - (a) a large number of simple tools and (b) methods to combine these tools in flexible ways.
Centers for Medicare and Medicaid Services. Connect: Enterprise Secure Client (SFTP) Gentran. Internet Option Manual 2006-2007
 Centers for Medicare and Medicaid Services Connect: Enterprise Secure Client (SFTP) Gentran Internet Option Manual 2006-2007 Version 8 The Connect: Enterprise Secure Client (SFTP) Manual is not intended
Centers for Medicare and Medicaid Services Connect: Enterprise Secure Client (SFTP) Gentran Internet Option Manual 2006-2007 Version 8 The Connect: Enterprise Secure Client (SFTP) Manual is not intended
www.faxmyway.com USER MANUAL www.faxmyway.com Online Faxing Anywhere, Anytime [email protected] Paperless Secure Faxing Anytime, Anywhere
 www.faxmyway.com www.faxmyway.com Paperless Secure Faxing Anytime, Anywhere Online Faxing Anywhere, Anytime USER MANUAL [email protected] [email protected] GETTING STARTED Faxmyway is an email and web-based
www.faxmyway.com www.faxmyway.com Paperless Secure Faxing Anytime, Anywhere Online Faxing Anywhere, Anytime USER MANUAL [email protected] [email protected] GETTING STARTED Faxmyway is an email and web-based
PrivateWire Gateway Load Balancing and High Availability using Microsoft SQL Server Replication
 PrivateWire Gateway Load Balancing and High Availability using Microsoft SQL Server Replication Introduction The following document describes how to install PrivateWire in high availability mode using
PrivateWire Gateway Load Balancing and High Availability using Microsoft SQL Server Replication Introduction The following document describes how to install PrivateWire in high availability mode using
How to Backup and FTP your SQL database using E2.
 How to Backup and FTP your SQL database using E2. To follow these instructions steps 1 14 must be completed either on the SQL Server or on a workstation that has the SQL Client Tools installed. You may
How to Backup and FTP your SQL database using E2. To follow these instructions steps 1 14 must be completed either on the SQL Server or on a workstation that has the SQL Client Tools installed. You may
InformationNOW SQL 2008 Database Backup and Restoration
 InformationNOW SQL 2008 Database Backup and Restoration Backing up a SQL 2008 Database Users are advised to create frequent multiple offsite backups. Occasionally, it may be necessary to manually initiate
InformationNOW SQL 2008 Database Backup and Restoration Backing up a SQL 2008 Database Users are advised to create frequent multiple offsite backups. Occasionally, it may be necessary to manually initiate
What is SOAP MTOM? How it works?
 What is SOAP MTOM? SOAP Message Transmission Optimization Mechanism (MTOM) is the use of MIME to optimize the bitstream transmission of SOAP messages that contain significantly large base64binary elements.
What is SOAP MTOM? SOAP Message Transmission Optimization Mechanism (MTOM) is the use of MIME to optimize the bitstream transmission of SOAP messages that contain significantly large base64binary elements.
How to configure your email client
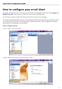 How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
How to configure your email client This guide will teach you how to set up your email client. In this guide we will cover both Outlook and Windows Live mail, which are two of the major email clients used
Internet E-Mail Encryption S/Mime Standard
 Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
Internet E-Mail Encryption S/Mime Standard Disclaimer: Successfully setting up encryption functions in most e-mail clients is usually not a problematic task. However, it should be noted that, when configuring
ACTi NVR Config Converter User s Manual. Version 1.0.0.17 2012/06/07
 ACTi NVR Config Converter User s Manual Version 1.0.0.17 2012/06/07 Legal Notice Disclaimer The information contained in this document is intended for general information purposes. ACTi Corporation shall
ACTi NVR Config Converter User s Manual Version 1.0.0.17 2012/06/07 Legal Notice Disclaimer The information contained in this document is intended for general information purposes. ACTi Corporation shall
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2007
 Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2007 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Prerequisite. Getting Started. Email Signing and Encryption using Microsoft outlook 2010
 Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
Email Signing and Encryption using Microsoft outlook 2010 Prerequisite a. The user s email account has been added and correctly configured into Microsoft outlook. b. The user has an authentication certificate.
InformationNOW SQL 2005 Database Backup and Restoration
 InformationNOW SQL 2005 Database Backup and Restoration Backing up a SQL 2005 Database Users are advised to create an hourly or nightly database backup maintenance plan. Occasionally, it may be necessary
InformationNOW SQL 2005 Database Backup and Restoration Backing up a SQL 2005 Database Users are advised to create an hourly or nightly database backup maintenance plan. Occasionally, it may be necessary
Using etoken for Securing E-mails Using Outlook and Outlook Express
 Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Using etoken for Securing E-mails Using Outlook and Outlook Express Lesson 15 April 2004 etoken Certification Course Securing Email Using Certificates Unprotected emails can be easily read and/or altered
Extracting an S/MIME certificate from a digital signature
 Extracting an S/MIME certificate from a digital signature Instructions for Microsoft Outlook 2007 and 2010 Document User_Instruction_Outlook_Certificate_Handling Status Final Date: 03.06.2012 Version:
Extracting an S/MIME certificate from a digital signature Instructions for Microsoft Outlook 2007 and 2010 Document User_Instruction_Outlook_Certificate_Handling Status Final Date: 03.06.2012 Version:
emedny FTP Batch Dial-Up Number 866 488 3006 emedny SUN UNIX Server ftp 172.27.16.79
 This document contains most of the information needed to submit FTP Batch transactions with emedny. It does not contain the unique FTP User ID/Password required to log in to the emedny SUN UNIX Server.
This document contains most of the information needed to submit FTP Batch transactions with emedny. It does not contain the unique FTP User ID/Password required to log in to the emedny SUN UNIX Server.
Gold Lock Desktop. User Manual. Follow these simple steps to install, configure, and use Gold Lock Desktop.
 User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
User Manual Follow these simple steps to install, configure, and use. Content 1 Installation...02 2 Configuration...03-06 3 Use...07 4 Verification & Security...08 5 Backup & Restore...09 6 File Encryption...10
Chapter 6 Electronic Mail Security
 Cryptography and Network Security Chapter 6 Electronic Mail Security Lectured by Nguyễn Đức Thái Outline Pretty Good Privacy S/MIME 2 Electronic Mail Security In virtually all distributed environments,
Cryptography and Network Security Chapter 6 Electronic Mail Security Lectured by Nguyễn Đức Thái Outline Pretty Good Privacy S/MIME 2 Electronic Mail Security In virtually all distributed environments,
Domainz Mail Client Setup User Guide Version 3.0 06 July 2011
 Domainz Mail Client Setup User Guide Version 3.0 06 July 2011 1 1 Domainz Limited Level 1, 138 The Terrace Private Bag 1810 Wellington New Zealand Phone: +64 4 473 4567 Fax: +64 4 4734569 Email: [email protected]
Domainz Mail Client Setup User Guide Version 3.0 06 July 2011 1 1 Domainz Limited Level 1, 138 The Terrace Private Bag 1810 Wellington New Zealand Phone: +64 4 473 4567 Fax: +64 4 4734569 Email: [email protected]
Email Setup Guide. network support pc repairs web design graphic design Internet services spam filtering hosting sales programming
 Email Setup Guide 1. Entourage 2008 Page 2 2. ios / iphone Page 5 3. Outlook 2013 Page 10 4. Outlook 2007 Page 17 5. Windows Live Mail a. New Account Setup Page 21 b. Change Existing Account Page 25 Entourage
Email Setup Guide 1. Entourage 2008 Page 2 2. ios / iphone Page 5 3. Outlook 2013 Page 10 4. Outlook 2007 Page 17 5. Windows Live Mail a. New Account Setup Page 21 b. Change Existing Account Page 25 Entourage
Configuring Email Notification for Business Glossary
 Configuring Email Notification for Business Glossary 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
Configuring Email Notification for Business Glossary 1993-2016 Informatica LLC. No part of this document may be reproduced or transmitted in any form, by any means (electronic, photocopying, recording
ClearView Connects Help
 ClearView Connects Help Table of Contents General... 1 1. How does this system work?... 1 2. How do I make a report?... 1 3. Can I use my computer at home?... 1 4. Who receives the information in my report?...
ClearView Connects Help Table of Contents General... 1 1. How does this system work?... 1 2. How do I make a report?... 1 3. Can I use my computer at home?... 1 4. Who receives the information in my report?...
Recalling A Sent Message in Outlook 2010
 Recall or replace an email message that you sent The recall feature in Microsoft Outlook tries to stop delivery and, optionally, replace an email message that you have already sent to another Microsoft
Recall or replace an email message that you sent The recall feature in Microsoft Outlook tries to stop delivery and, optionally, replace an email message that you have already sent to another Microsoft
Protocolo FTP. FTP: Active Mode. FTP: Active Mode. FTP: Active Mode. FTP: the file transfer protocol. Separate control, data connections
 : the file transfer protocol Protocolo at host interface local file system file transfer remote file system utilizes two ports: - a 'data' port (usually port 20...) - a 'command' port (port 21) SISTEMAS
: the file transfer protocol Protocolo at host interface local file system file transfer remote file system utilizes two ports: - a 'data' port (usually port 20...) - a 'command' port (port 21) SISTEMAS
CompleteView Admin Console Users Guide. Version 3.0.0 Revised: 02/15/2008
 CompleteView Admin Console Users Guide Version 3.0.0 Revised: 02/15/2008 Table Of Contents Configuration... 3 Starting the Admin Console... 3 Adding a Server... 4 Monitoring Server Status... 6 Menus...
CompleteView Admin Console Users Guide Version 3.0.0 Revised: 02/15/2008 Table Of Contents Configuration... 3 Starting the Admin Console... 3 Adding a Server... 4 Monitoring Server Status... 6 Menus...
Encryption. Introduction to using 7-Zip
 IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
IT Services Training Guide Encryption Introduction to using 7-Zip It Services Training Team The University of Manchester email: [email protected] www.itservices.manchester.ac.uk/trainingcourses/coursesforstaff
The FTP Monitor application performs the following main functions:
 FTP Monitor Application The FTP Monitor application performs the following main functions: 1. Periodically monitors the files to be uploaded. 2. Automatically compresses and encrypts the files to be uploaded.
FTP Monitor Application The FTP Monitor application performs the following main functions: 1. Periodically monitors the files to be uploaded. 2. Automatically compresses and encrypts the files to be uploaded.
mailtunnel Quick Guide ENCRYPTED TUNNEL COMENDO DATA CENTER SECURITY CENTER SPAM+VIRUS LOGS
 COMENDO CUSTOMER ENCRYPTED TUNNEL INBOUND E-MAIL COMENDO DATA CENTER RECEIVED E-MAIL SECURITY CENTER SPAM+VIRUS LOGS Comendo offers encryption of your e-mail connection. It ensures that all e-mail communication
COMENDO CUSTOMER ENCRYPTED TUNNEL INBOUND E-MAIL COMENDO DATA CENTER RECEIVED E-MAIL SECURITY CENTER SPAM+VIRUS LOGS Comendo offers encryption of your e-mail connection. It ensures that all e-mail communication
Emailing from The E2 Shop System EMail address Server Name Server Port, Encryption Protocol, Encryption Type, SMTP User ID SMTP Password
 Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Emailing from The E2 Shop System With recent releases of E2SS (at least 7.2.7.23), we will be allowing two protocols for EMail delivery. A new protocol for EMail delivery Simple Mail Transfer Protocol
Event Center (rev b) EVENT CENTER. VPI 160 Camino Ruiz, Camarillo, CA 93012-6700 (Voice) 800-200-5430 805-389-5200 (Fax) 805-389-5202 www.vpi-corp.
 EVENT CENTER 1 VPI 160 Camino Ruiz, Camarillo, CA 93012-6700 (Voice) 800-200-5430 805-389-5200 (Fax) 805-389-5202 www.vpi-corp.com All information in this manual is Copyright protected material by Voice
EVENT CENTER 1 VPI 160 Camino Ruiz, Camarillo, CA 93012-6700 (Voice) 800-200-5430 805-389-5200 (Fax) 805-389-5202 www.vpi-corp.com All information in this manual is Copyright protected material by Voice
Instructions Microsoft Outlook Express Page 1
 Instructions Microsoft Outlook Express Page 1 Instructions Microsoft Outlook Express This manual is written for users who already have an e-mail account configured in Outlook Express and will therefore
Instructions Microsoft Outlook Express Page 1 Instructions Microsoft Outlook Express This manual is written for users who already have an e-mail account configured in Outlook Express and will therefore
Online Banking for Business Secure FTP with SSL (Secure Socket Layer) USER GUIDE
 Online Banking for Business Secure FTP with SSL (Secure Socket Layer) USER GUIDE Contents Secure FTP Setup... 1 Introduction...1 Secure FTP Setup Diagram...1 Before You Set Up S/FTP...2 Setting Up S/FTP...2
Online Banking for Business Secure FTP with SSL (Secure Socket Layer) USER GUIDE Contents Secure FTP Setup... 1 Introduction...1 Secure FTP Setup Diagram...1 Before You Set Up S/FTP...2 Setting Up S/FTP...2
Set Up E-mail Setup with Microsoft Outlook 2007 using POP3
 Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
Page 1 of 14 Help Center Set Up E-mail Setup with Microsoft Outlook 2007 using POP3 Learn how to configure Outlook 2007 for use with your 1&1 e-mail account using POP3. Before you begin, you will need
EDGAR. EDGAR Public Dissemination Service New Subscriber Document
 EDGAR ELECTRONIC DATA GATHERING, ANALYSIS, AND RETRIEVAL EDGAR Public Dissemination Service New Subscriber Document Updated Jul-01-14 Table of Contents 1.0 PDS System Overview...2 1.1 PDS Points of Contact...
EDGAR ELECTRONIC DATA GATHERING, ANALYSIS, AND RETRIEVAL EDGAR Public Dissemination Service New Subscriber Document Updated Jul-01-14 Table of Contents 1.0 PDS System Overview...2 1.1 PDS Points of Contact...
Key Components of WAN Optimization Controller Functionality
 Key Components of WAN Optimization Controller Functionality Introduction and Goals One of the key challenges facing IT organizations relative to application and service delivery is ensuring that the applications
Key Components of WAN Optimization Controller Functionality Introduction and Goals One of the key challenges facing IT organizations relative to application and service delivery is ensuring that the applications
Using AppMetrics to Handle Hung Components and Applications
 Using AppMetrics to Handle Hung Components and Applications AppMetrics has the ability to detect hung COM+ components and applications, providing a means of alerting staff to situations where critical
Using AppMetrics to Handle Hung Components and Applications AppMetrics has the ability to detect hung COM+ components and applications, providing a means of alerting staff to situations where critical
94x MeF e-file Application Guidelines
 Step 1: Registration for the e-file Application Transmitters, Software Developers and Reporting Agents who have not submitted an online e-file Application must do so through e-services. Publication 3112
Step 1: Registration for the e-file Application Transmitters, Software Developers and Reporting Agents who have not submitted an online e-file Application must do so through e-services. Publication 3112
PC Instructions for Miller LiveArc Software
 PC Instructions for Miller LiveArc Software Contents Instructions for Installing LiveArc Software on a PC... 2 Instructions for Loading Data from the LiveArc System onto a PC... 10 Instructions for Transferring
PC Instructions for Miller LiveArc Software Contents Instructions for Installing LiveArc Software on a PC... 2 Instructions for Loading Data from the LiveArc System onto a PC... 10 Instructions for Transferring
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Attachment 6 - Email Interface For External Systems Wersja: 4.0
 MINISTRY OF FINANCE SYSTEM INTEGRATION PLAN ATTACHMENT 6 SEAP SPECIFICATION EMAIL INTERFACE FOR EXTERNAL SYSTEMS PROJECT ECIP/SEAP VERSION 1 z 15 Table of Contents 1. Email Interface for External
MINISTRY OF FINANCE SYSTEM INTEGRATION PLAN ATTACHMENT 6 SEAP SPECIFICATION EMAIL INTERFACE FOR EXTERNAL SYSTEMS PROJECT ECIP/SEAP VERSION 1 z 15 Table of Contents 1. Email Interface for External
CONTRACT MODEL IPONZ DESIGN SERVICE VERSION 2. Author: Foster Moore Date: 20 September 2011 Document Version: 1.7
 CONTRACT MODEL IPONZ DESIGN SERVICE VERSION 2 Author: Foster Moore Date: 20 September 2011 Document Version: 1.7 Level 6, Durham House, 22 Durham Street West PO Box 106857, Auckland City Post Shop, Auckland
CONTRACT MODEL IPONZ DESIGN SERVICE VERSION 2 Author: Foster Moore Date: 20 September 2011 Document Version: 1.7 Level 6, Durham House, 22 Durham Street West PO Box 106857, Auckland City Post Shop, Auckland
StreamServe Persuasion SP4 Encryption and Authentication
 StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United
StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP4 Encryption and Authentication User Guide Rev A 2001-2009 STREAMSERVE, INC. ALL RIGHTS RESERVED United
Microsoft Outlook Web Access Handbook
 Microsoft Outlook Web Access Handbook Introduction Outlook Web access allows you to use a web browser (Internet Explorer or Firefox) to read your email, send email, and check your online calendar. This
Microsoft Outlook Web Access Handbook Introduction Outlook Web access allows you to use a web browser (Internet Explorer or Firefox) to read your email, send email, and check your online calendar. This
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling
 Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
Erado Archiving & Setup Instruction Microsoft Exchange 2007 Push Journaling This document covers the following Microsoft Exchange Server Editions Microsoft Exchange Enterprise Edition 2007 Microsoft Exchange
SmartWatch Eco/Eco Compact
 SmartWatch Eco/Eco Compact Digital Video Recorders SmartWatch Eco SmartWatch Eco Compact Mobile Application Installation & Operation Manual Table of Contents Introduction...3 Installation and Operation
SmartWatch Eco/Eco Compact Digital Video Recorders SmartWatch Eco SmartWatch Eco Compact Mobile Application Installation & Operation Manual Table of Contents Introduction...3 Installation and Operation
CS43: Computer Networks Email. Kevin Webb Swarthmore College September 24, 2015
 CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
CS43: Computer Networks Email Kevin Webb Swarthmore College September 24, 2015 Three major components: mail (MUA) mail transfer (MTA) simple mail transfer protocol: SMTP User Agent a.k.a. mail reader composing,
StreamServe Persuasion SP5 Encryption and Authentication
 StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United
StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A StreamServe Persuasion SP5 Encryption and Authentication User Guide Rev A 2001-2010 STREAMSERVE, INC. ALL RIGHTS RESERVED United
FILE TRANSFER PROTOCOL (FTP) SITE
 FILE TRANSFER PROTOCOL (FTP) SITE Section 1 - SPIN System Overview As part of the digital plan submission process that Registries is currently implementing a File Transfer Protocol (FTP) site has been
FILE TRANSFER PROTOCOL (FTP) SITE Section 1 - SPIN System Overview As part of the digital plan submission process that Registries is currently implementing a File Transfer Protocol (FTP) site has been
Guidance for IA DMM: Connecting Your Computer to FSU Video File Server
 1 Guidance for IA DMM: Connecting Your Computer to FSU Video File Server This guide will walk you through the process of connecting your computer to the FSU Video File Server and then uploading video files
1 Guidance for IA DMM: Connecting Your Computer to FSU Video File Server This guide will walk you through the process of connecting your computer to the FSU Video File Server and then uploading video files
Client/Server Messaging System v3.28 Client User's Guide
 Client/Server Messaging System v3.28 Client User's Guide Client/Server Messaging System v3.28 Client User's Guide Page 1 Contents 1 Introduction...3 2 Glossary...3 3 What is the Messaging System?...4 4
Client/Server Messaging System v3.28 Client User's Guide Client/Server Messaging System v3.28 Client User's Guide Page 1 Contents 1 Introduction...3 2 Glossary...3 3 What is the Messaging System?...4 4
Microsoft Office 365 with MailDefender
 (PC) for Microsoft Office 365 with MailDefender V1.0 Contents 1 Logging in to the Office 365 Portal... 3 1.1 Outlook Web Access Exchange & Lync... 3 1.2 Team Site SharePoint Online... 3 2 Configuring your
(PC) for Microsoft Office 365 with MailDefender V1.0 Contents 1 Logging in to the Office 365 Portal... 3 1.1 Outlook Web Access Exchange & Lync... 3 1.2 Team Site SharePoint Online... 3 2 Configuring your
Configuring the CyberData VoIP 4-Port Zone Controller with Audio Out
 NetVanta Unified Communications Technical Note Configuring the CyberData VoIP 4-Port Zone Controller with Audio Out Introduction The CyberData Voice over Internet Protocol (VoIP) zone controller enables
NetVanta Unified Communications Technical Note Configuring the CyberData VoIP 4-Port Zone Controller with Audio Out Introduction The CyberData Voice over Internet Protocol (VoIP) zone controller enables
How To Use Gfi Mailarchiver On A Pc Or Macbook With Gfi Email From A Windows 7.5 (Windows 7) On A Microsoft Mail Server On A Gfi Server On An Ipod Or Gfi.Org (
 GFI MailArchiver for Exchange 4 Manual By GFI Software http://www.gfi.com Email: [email protected] Information in this document is subject to change without notice. Companies, names, and data used in examples
GFI MailArchiver for Exchange 4 Manual By GFI Software http://www.gfi.com Email: [email protected] Information in this document is subject to change without notice. Companies, names, and data used in examples
Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows
 Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows SecureZIP for Windows interoperates with leading PKI vendors including Entrust, VeriSign, and RSA to enable the
Configure SecureZIP for Windows for Entrust Entelligence Security Provider 7.x for Windows SecureZIP for Windows interoperates with leading PKI vendors including Entrust, VeriSign, and RSA to enable the
Docufide Client Installation Guide for Windows
 Docufide Client Installation Guide for Windows This document describes the installation and operation of the Docufide Client application at the sending school installation site. The intended audience is
Docufide Client Installation Guide for Windows This document describes the installation and operation of the Docufide Client application at the sending school installation site. The intended audience is
Connectivity & File Backup
 Connectivity & File Backup Connectivity & File Backup............................. -2 Infrared............................................ -3 Port Alignment......................................... -3
Connectivity & File Backup Connectivity & File Backup............................. -2 Infrared............................................ -3 Port Alignment......................................... -3
Communications and Connectivity
 Chapter V Communications and Connectivity Trading partners are responsible for the purchase of communication protocol packages and access support for the dial-up process to the Enterprise EDI Gateway/Clearinghouse.
Chapter V Communications and Connectivity Trading partners are responsible for the purchase of communication protocol packages and access support for the dial-up process to the Enterprise EDI Gateway/Clearinghouse.
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
WaveWare Technologies, Inc. We Deliver Information at the Speed of Light
 WaveWare Technologies, Inc. We Deliver Information at the Speed of Light Enterprise Messaging Software WaveWare Enterprise SMTP Email Server How-to Send an Email to a Pager Please Note This How to Guide
WaveWare Technologies, Inc. We Deliver Information at the Speed of Light Enterprise Messaging Software WaveWare Enterprise SMTP Email Server How-to Send an Email to a Pager Please Note This How to Guide
NERSP: Saving File Space and Reducing File Storage Charges
 NERSP: Saving File Space and Reducing UFIT EI&O Document ID: D0100 Last Updated: 07/03/2002 This document describes methods of managing and conserving file storage space on CNS's NERSP UNIX system. These
NERSP: Saving File Space and Reducing UFIT EI&O Document ID: D0100 Last Updated: 07/03/2002 This document describes methods of managing and conserving file storage space on CNS's NERSP UNIX system. These
Auto Archiving Folders in Outlook XP
 Auto Archiving Folders in Outlook XP Your Outlook email account on the Exchange server is allotted 50 megabytes of storage space on the server. Items in the Inbox, Calendar, Sent Items, Deleted Items,
Auto Archiving Folders in Outlook XP Your Outlook email account on the Exchange server is allotted 50 megabytes of storage space on the server. Items in the Inbox, Calendar, Sent Items, Deleted Items,
Setting up Outgoing Mail (SMTP) Server of CS LoxInfo
 Setting up Outgoing Mail (SMTP) Server of CS LoxInfo Acknowledgement Blocking a direct connection from e mail client or server to mail server which located in foreign countries will cause you unable to
Setting up Outgoing Mail (SMTP) Server of CS LoxInfo Acknowledgement Blocking a direct connection from e mail client or server to mail server which located in foreign countries will cause you unable to
U.S. Department of Education 1998 Electronic Access Conferences
 U.S. Department of Education 1998 Electronic Access Conferences 11/9/98 Session 43-1 Session 43 Mainframe Connectivity to Title IV Wide Area Network Session 43-2 Session 43 Mike Cline - NCS Development
U.S. Department of Education 1998 Electronic Access Conferences 11/9/98 Session 43-1 Session 43 Mainframe Connectivity to Title IV Wide Area Network Session 43-2 Session 43 Mike Cline - NCS Development
Instructions on TLS/SSL Certificates on Yealink Phones
 Instructions on TLS/SSL Certificates on Yealink Phones 1. Summary... 1 2. Encryption, decryption and the keys... 1 3. SSL connection flow... 1 4. The instructions to a certificate... 2 4.1 Phone acts as
Instructions on TLS/SSL Certificates on Yealink Phones 1. Summary... 1 2. Encryption, decryption and the keys... 1 3. SSL connection flow... 1 4. The instructions to a certificate... 2 4.1 Phone acts as
Centricity Electronic Medical Record v9.5
 GE Healthcare Centricity Electronic Medical Record v9.5 Service Pack 3 Release Notes Contents What's new in EMR 9.5.3?...1 Important Product Notifications...2 Known issues...3 Pre-installation activities...3
GE Healthcare Centricity Electronic Medical Record v9.5 Service Pack 3 Release Notes Contents What's new in EMR 9.5.3?...1 Important Product Notifications...2 Known issues...3 Pre-installation activities...3
6. Is it mandatory to have the digital certificate issued from NICCA?...3. 7. Is it mandatory for the sender and receiver to have a NIC email id?...
 FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
FAQ FOR S/MIME 1. What is S/MIME?...2 2. What is digital certificate?...2 3. What is an encrypted email?...2 4. Is it mandatory to use this service?...2 5. What I need to do to start using S/MIME service?...2
NETWRIX EVENT LOG MANAGER
 NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
NETWRIX EVENT LOG MANAGER ADMINISTRATOR S GUIDE Product Version: 4.0 July/2012. Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment
How to backup important data
 How to backup important data How to backup important data Page 1 of 27 Contents Page: A. Backing up your emails into a Personal Folder (.pst file) 1 B. Backing up from My Documents folder. 6 C. Searching
How to backup important data How to backup important data Page 1 of 27 Contents Page: A. Backing up your emails into a Personal Folder (.pst file) 1 B. Backing up from My Documents folder. 6 C. Searching
FTP and email. Computer Networks. FTP: the file transfer protocol
 Computer Networks and email Based on Computer Networking, 4 th Edition by Kurose and Ross : the file transfer protocol transfer file to/from remote host client/ model client: side that initiates transfer
Computer Networks and email Based on Computer Networking, 4 th Edition by Kurose and Ross : the file transfer protocol transfer file to/from remote host client/ model client: side that initiates transfer
Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions
 HOSTING Administrator Control Panel / Quick Reference Guide Page 1 of 9 Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions Exchange 2010 Outlook Profile Setup Page 2 of 9 Exchange
HOSTING Administrator Control Panel / Quick Reference Guide Page 1 of 9 Outlook Profile Setup Guide Exchange 2010 Quick Start and Detailed Instructions Exchange 2010 Outlook Profile Setup Page 2 of 9 Exchange
How to Back Up and Restore an ACT! Database Answer ID 19211
 How to Back Up and Restore an ACT! Database Answer ID 19211 Please note: Answer ID documents referenced in this article can be located at: http://www.act.com/support/index.cfm (Knowledge base link). The
How to Back Up and Restore an ACT! Database Answer ID 19211 Please note: Answer ID documents referenced in this article can be located at: http://www.act.com/support/index.cfm (Knowledge base link). The
CAIL Security Facility NSK Host to Host FTP Encryption
 CAIL Security Facility NSK Host to Host FTP Encryption Aug 12, 2004 1-905-940-9000 [email protected] CAIL Security Update NSK Host to Host FTP Encryption Overview CAIL Security capabilities have been extended
CAIL Security Facility NSK Host to Host FTP Encryption Aug 12, 2004 1-905-940-9000 [email protected] CAIL Security Update NSK Host to Host FTP Encryption Overview CAIL Security capabilities have been extended
3. On the E-mail Accounts wizard window, select Add a new e-mail account, and then click Next.
 To Set Up Your E-mail Account in Microsoft Outlook 2003 1. Open Microsoft Outlook 03 3. On the E-mail Accounts wizard window, select Add a new e-mail account, and then click Next. 4. For your server type,
To Set Up Your E-mail Account in Microsoft Outlook 2003 1. Open Microsoft Outlook 03 3. On the E-mail Accounts wizard window, select Add a new e-mail account, and then click Next. 4. For your server type,
Chapter 3 Management. Remote Management
 Chapter 3 Management This chapter describes how to use the management features of your ProSafe 802.11a/g Dual Band Wireless Access Point WAG102. To access these features, connect to the WAG102 as described
Chapter 3 Management This chapter describes how to use the management features of your ProSafe 802.11a/g Dual Band Wireless Access Point WAG102. To access these features, connect to the WAG102 as described
EDGAR ELECTRONIC DATA GATHERING, ANALYSIS, AND RETRIEVAL. Public Dissemination Service New Subscriber Document
 EDGAR ELECTRONIC DATA GATHERING, ANALYSIS, AND RETRIEVAL EDGAR Public Dissemination Service New Subscriber Document Updated February 23, 2015 Table of Contents 1.0 PDS System Overview... 2 1.1 PDS Points
EDGAR ELECTRONIC DATA GATHERING, ANALYSIS, AND RETRIEVAL EDGAR Public Dissemination Service New Subscriber Document Updated February 23, 2015 Table of Contents 1.0 PDS System Overview... 2 1.1 PDS Points
Online Banking for Business Secure FTP with SSH (Secure Shell) USER GUIDE
 Online Banking for Business Secure FTP with SSH (Secure Shell) USER GUIDE Contents Secure FTP Setup... 1 Introduction... 1 Before You Set Up S/FTP... 1 Setting Up FTP with SSH... 2 Sending Files... 3 Address
Online Banking for Business Secure FTP with SSH (Secure Shell) USER GUIDE Contents Secure FTP Setup... 1 Introduction... 1 Before You Set Up S/FTP... 1 Setting Up FTP with SSH... 2 Sending Files... 3 Address
Technical papers How email works
 Technical papers How email works This document has now been archived How email works Contents How email works What is email? What makes up an email? How does email work? The client The server How do email
Technical papers How email works This document has now been archived How email works Contents How email works What is email? What makes up an email? How does email work? The client The server How do email
Chapter 4 Management. Viewing the Activity Log
 Chapter 4 Management This chapter describes how to use the management features of your NETGEAR WG102 ProSafe 802.11g Wireless Access Point. To get to these features, connect to the WG102 as described in
Chapter 4 Management This chapter describes how to use the management features of your NETGEAR WG102 ProSafe 802.11g Wireless Access Point. To get to these features, connect to the WG102 as described in
Instructions for downloading and installing the GPS Map update
 Instructions for downloading and installing the GPS Map update Before starting the process, you will need a USB flash drive with 2 GB or more free space. On your computer: 1. Complete the map update purchase
Instructions for downloading and installing the GPS Map update Before starting the process, you will need a USB flash drive with 2 GB or more free space. On your computer: 1. Complete the map update purchase
Cryptography and Security
 Cunsheng DING Version 3 Lecture 17: Electronic Mail Security Outline of this Lecture 1. Email security issues. 2. Detailed introduction of PGP. Page 1 Version 3 About Electronic Mail 1. In virtually all
Cunsheng DING Version 3 Lecture 17: Electronic Mail Security Outline of this Lecture 1. Email security issues. 2. Detailed introduction of PGP. Page 1 Version 3 About Electronic Mail 1. In virtually all
Electronic Mail Security
 Electronic Mail Security Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-11/
Electronic Mail Security Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 [email protected] Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-11/
Outlook Data File navigate to the PST file that you want to open, select it and choose OK. The file will now appear as a folder in Outlook.
 Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Migrate Archived Outlook Items Outlook includes archiving functionality that is used to free up space on the mail server by moving older items from the mail server to PST files stored on your computer
Frequently Asked Questions About WebDrv Online (Remote) Backup
 Frequently Asked Questions About WebDrv Online (Remote) Backup GENERAL INFORMATION Why backup? What is online backup? What if we already have a tape backup system? How secure are online backups? What tasks
Frequently Asked Questions About WebDrv Online (Remote) Backup GENERAL INFORMATION Why backup? What is online backup? What if we already have a tape backup system? How secure are online backups? What tasks
VRM Monitor. Online Help
 VRM Monitor en Online Help VRM Monitor Table of Contents en 3 Table of Contents 1 Introduction 3 2 System overview 3 3 Getting started 4 3.1 Starting VRM Monitor 4 3.2 Starting Configuration Manager 4
VRM Monitor en Online Help VRM Monitor Table of Contents en 3 Table of Contents 1 Introduction 3 2 System overview 3 3 Getting started 4 3.1 Starting VRM Monitor 4 3.2 Starting Configuration Manager 4
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET)
 2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
2- Electronic Mail (SMTP), File Transfer (FTP), & Remote Logging (TELNET) There are three popular applications for exchanging information. Electronic mail exchanges information between people and file
Email Electronic Mail
 Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
Email Electronic Mail Electronic mail paradigm Most heavily used application on any network Electronic version of paper-based office memo Quick, low-overhead written communication Dates back to time-sharing
IBM Aspera Add-in for Microsoft Outlook 1.3.2
 IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
IBM Aspera Add-in for Microsoft Outlook 1.3.2 Windows: 7, 8 Revision: 1.3.2.100253 Generated: 02/12/2015 10:58 Contents 2 Contents Introduction... 3 System Requirements... 5 Setting Up... 6 Account Credentials...6
Backing up Microsoft Outlook Email For the PC Using MS Outlook 2000 Keith Roberts
 WIN1020 November 2003 Backing up Microsoft Outlook Email For the PC Using MS Outlook 2000 Keith Roberts INTRODUCTION... 1 PREPARATION... 1 BACKING UP EMAIL... 2 RESTORING EMAIL FROM A PERSONAL FILE FOLDER...
WIN1020 November 2003 Backing up Microsoft Outlook Email For the PC Using MS Outlook 2000 Keith Roberts INTRODUCTION... 1 PREPARATION... 1 BACKING UP EMAIL... 2 RESTORING EMAIL FROM A PERSONAL FILE FOLDER...
StreamServe Encryption and Authentication
 StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A StreamServe Encryption and Authentication User Guide 4.1.2 SP2 Rev A 2007 StreamServe, Inc. StreamServe is a trademark of StreamServe,
