Development and Implementation of Compression and Split Techniques for Multimedia Messaging Service Applications
|
|
|
- Austin Roberts
- 7 years ago
- Views:
Transcription
1 Development and Implementation of Compression and Split Techniques for Multimedia Messaging Service Applications Andik Setyono, 2 Md. Jahangir Alam and 3 C. Eswaran, 2, 3 Faculty of Information Technology Multimedia University Cyberjaya, Malaysia Faculty of Computer Science Dian Nuswantoro University Semarang, Indonesia setyono_andik@yahoo.com, 2 md.jahangir.alam@mmu.edu.my and 3 eswaran@mmu.edu.my Abstract MMS is a mobile messaging system that can be used for sending multimedia messages such as text, image, audio, video and a combination of them. This message can be sent to one or many mobile phones or external servers such as and fax servers. In this paper, we present compression and splitting techniques for enhancing the capability of MMS technology. With the enhanced technology, one can send large files of multimedia messages without any degradation in the quality of the data which is not possible with the existing MMS technology. The developed techniques are tested using images with JPEG format. The experimental results demonstrate that the proposed system outperforms the conventional MMS in handling large data files. The modified MMS presented in this paper serves as a basis for developing practical internet applications. Keywords MMS; Multimedia message; Compression; Split message; JPEG I. INTRODUCTION Multimedia Messaging Service (MMS) is a rich content message sending system that not only sends text but also sends image, voice, animation, video and combination of them [], [2]. MMS can be sent to mobile phone number or to external servers such as servers. Several types of multimedia files such as text, images, audio and video can be sent using MMS. Open Mobile Alliance (OMA) organization has proposed the standards for MMS versions.,.2 and.3 in the years 2002, 2005 and 2008 respectively [3]-[5]. Currently, it is possible to send multimedia messages up to 600 KB in a single delivery using MMS version.3 [5]. In this paper, we focus on image files with JPEG format. We choose the JPEG file format because it is relatively easy to implement the compression and split techniques with this format. JPEG is a standardized image compression mechanism. JPEG stands for Joint Photographic Experts Group, the original name of the committee that wrote the standard. JPEG is "lossy," meaning that the decompressed image is not exactly the same as the original image [6]. There are lossless image compression algorithms, but JPEG achieves much greater compression than is possible with lossless methods. A useful property of JPEG is that the degree of loss (or the degree of degradation) can be varied by adjusting the compression parameters. This means that one can trade off file size against the output image quality. We use the split technique to facilitate the delivery of multimedia messages if the compressed file is still too large to be sent directly using MMS. Though usage of split technique requires a fairly high cost as it involves payment for each individual split file, this technique is essential if one wants to send large multimedia files without any degradation in the quality of data. In this paper, we present a systematic procedure for implementing the MMS technology for sending images with JPEG format by using compression and split techniques. The proposed method is suitable for the development of internet applications for transmitting and displaying large size images without affecting the quality of the image. The rest of the paper is organized as follows: section 2 discusses data compression and split message techniques. The proposed framework of the MMS system and its description are presented in section 3. Implementation and evaluation details are presented in section 4 and finally conclusion and future work are given in section 5. II. COMPRESSION AND SPLIT TECHNIQUES Data compression is a branch of computer science that comes from information theory. Information theory itself is a branch of mathematics that has been developed in the late decades of the 940s. The aim of data compression is to reduce the redundancy (useless information) in the message [7]. A. The Baseline JPEG Image Algorithm JPEG compression technique involves several stages starting from DCT, quantization, zigzag run-length encoding and lossless compression using Huffman coding for building the compressed file. The steps in implementing the JPEG image compression are shown in Figure /0/$ IEEE V2-2
2 The most common DCT definition of a -D sequence of length N is formulated by [] 2 cos 2 2 for u = 0,, 2 N, where Figure. JPEG compression process [8]. The various steps are explained below [9], [0]:. The image is separated into intensity and color channels. They are subdivided into 8x8-pixel blocks. They are subsequently processed left to right and top to bottom. 2. Each 8x8-pixel block is processed using discrete cosine transform (DCT) and applied to each block. 3. Each block is compressed through quantization. The 64 coefficients for each block are quantized to a lower precision by dividing a fixed table of values that gives the least precision for high-frequency term. 4. The first of the 64 coefficients for each block is the average brightness or DC term and remaining 63 coefficients for each block are scanned in zig-zag diagonal order that starts with the lowest frequencies and progressed to the highest. 5. Entropy coding is the process of using entropy algorithm, such as Huffman or Arithmetic for encoding. The DCT and quantization processes will eliminate the pixels with zero values. 6. The image is reconstructed through decompression, a process that uses the Inverse Discrete Cosine Transform (IDCT). B. Discrete Cosine Transform (DCT) The DCT is a converting process of unit data values into a sum of cosine functions []. As described in the previous section, the process of JPEG compression uses DCT process. Figure 2 illustrates the concept DCT. Figure 2. Concept of DCT for JPEG. The function f(x) represents the value of the x th sample of the input signal. F(u) represents a DCT coefficient for u= 0,,..., N- []. The two-dimensional DCT (2-D DCT) of a block of M x N samples of a two-dimensional signal F(x,y) is formulated as follows []:, 2 2 2, cos cos 2 2 for u = 0,, 2 N and v= 0,, 2 M, where. The three-dimensional variant of the DCT (3D-DCT) is a composition of three of -D DCT along each dimension [2]. The formal definition is as given below.,,,,... For u, v, w = 0,, 2..., N-, where Cux, Cvy, Cwz are as follow:.. cos 2.cos 2.cos 2 6 C. Huffman Coding In general, a data compression technique consists of two major activities, namely modeling and coding. The fundamental process of a data compression technique is to determine a set of parts of the data (a stream of symbols) to turn it into code (a stream of codes). If the compression process is effective, then the stream of codes will be smaller than the size in terms of streams of symbols. The decision to make certain symbols with certain codes is the core of the modeling process. Generally means that a model is a collection of data and rules that determine the symbol elements as input and output of the code for the compression process. In Huffman coding, symbols that often appear will be transformed into code with a small number of bits, while the less frequent will be the code with a large number of bits [3]. The block diagram of the static Huffman model is shown in Figure V2-3
3 Figure 3. Static compression of Huffman coding. Procedure to build this tree is simple and easy to understand. Each symbol is sorted according to frequency, this frequency is considered as the weight of each symbol, and then followed by steps as follows:. Two free nodes with the lowest weights are paired. 2. Parent node for the second node created in the previous step. Summing up the the frequencies and use them as weights. 3. Now parent node serves as a node free. 4. Give code node 0 to for the left and right nodes. 5. Repeat the steps above until only one node left [4]. D. Split Message This technique is used to split a large file into a number of small files. These files are sent one by one with a single key press. The files are merged back into a single file on the mobile phone recipient. This technique is similar to the process of splitting an SMS message with large number of characters into multiple SMS each with a maximum number of 60 characters. The MMS packages the compressed message in MIME format and encodes into a binary message. We need to split the compressed message file into several smaller files in order to send a large message. The splitting method is employed if the original file size (OFS) is larger than the maximum capacity (MC) permitted. If M = OFS / MC, the number of split files N is given by Figure 4. Proposed Framework of MMS technology. MMS application already installed on the mobile phone can also be used as input media for building various kinds of internet applications. This is because the multimedia message that has been sent to the mobile phone number and servers can be retrieved and stored into a database server. From that database, we can develop Internet applications such as telemedicine, monitoring and e- commerce system. Figure 5 shows the flowchart of sending MMS using the proposed method. Let the original image be of size (w x h) where w and h denote the width and height of the image respectively. Then the size of each of the N split images will be equal to {w x (h / N)}. III. PROPOSED FRAMEWORK The proposed MMS application is developed using Java 2 Micro Edition. The application has been simulated using the NetBeans emulator. The simulated results show that the developed application can be installed on a mobile phone. In this study, we have developed the MMS application to send image files for JPEG format using compression and the split message techniques. This aims to enhance the existing ability of the MMS within the message delivery. After developing the MMS application, the next step is to install it on a mobile phone to send multimedia messages to other mobile phones or external servers, such as servers. The proposed framework of the MMS is shown in Figure 4. Figure 5. Flowchart of the algorithm for sending MMS. The multimedia message in the form of text, image, audio or video that will be sent using MMS technology is compressed first, if the size of the file exceeds the capacity allowed. Then if the size of the compressed file is still larger than the maximum capacity allowed then the message will be split into a number of small size files so that they can be V2-4
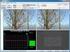
4 sent using the MMS technology. Multimedia messages that have been split are sent one by one until all successfully delivered. IV. IMPLEMENTATION AND EVALUATION In this research work, we have implemented the compression and split message techniques before sending the JPEG file. We have also performed various evaluations and analysis of the implementation process. The following section discusses the details of implementation and evaluation processes. A. Implementation To implement the compression and split techniques for MMS application on a mobile phone, we use mobile phones, Sony Ericsson K630i and J05i. These mobile phones have fairly comprehensive features including MMS and Java. The MMS application is installed on the mobile phones. We have simulated an experiment to determine the outcome of the implementation of the compression and split techniques. For this simulation, we have used test JPEG images with file sizes exceeding the maximum capacity permitted. In this simulation, we have used Java 2 Micro Edition (J2ME). Java library allows only up to 30 KB of data for each delivery. If a file of size exceeding 30 KB is transmitted, the data will be compressed to get a smaller size file. If the compressed file size is still more than 30 KB, it will be split into smaller files. Figure 6 shows the simulation results. The explanation of the simulation results shown in Figure 6 are: (a) user interface for sending MMS, (b) file (image) that will be sent, (c) selecting a file that will be sent, (d) the information in the form of notification that the file is more than 30 KB, (e) compressing files with a selected value of the quality factor, (f) determining the destination number, (g) splitting file to be smaller files, (h) delivery process, where in one time multiple messages are sent sequentially and (i) MMS inbox (sending the multimedia message successfully). In this research, we only focus on developing an MMS application to send JPEG images. The sequence diagram of the MMS application that has been installed on a mobile phone is shown in Figure 7. Figure 7. Sequence diagram for sending MMS. Figure 6. Simulation of the proposed framework. B. Evaluation The compression and split techniques provide benefits, such as (i) the application can send files larger than the one that is possible with the existing application, (ii) the application can maintain the quality of the original file by merging and decompressing the split files on the mobile phone receiver and (iii) the method is suitable for clientserver applications which requires a good quality data, such as telemedicine system. A comparison between the existing and the developed systems are shown in Table I. V2-5
5 TABLE I. The Existing. Max Size 30 KB. 2. Resize Image. 3. Single message. 4. Size and quality reduced 5. The file cannot be reconstructed to become similar to the original one. COMPARISON THE METHODS The Developed. Max size > 30 KB. 2. Compress and Split Image 3. Multiple message single sending. 4. Size and quality are not reduced. It can be merged and decompressed 5. The files can be merged and decompressed to become similar to the original file. compression and split techniques on the mobile phone. The compression technique is used to reduce the file size. The splitting technique is used to break the original file into smaller files according to the limitation of the MMS. The simulation results show that the proposed method can be successfully implemented on a mobile phone to send large amount of data using MMS application. The proposed framework is useful for developing mobile applications using MMS technology such as mobile telemedicine systems. The extension of this method for the audio and video files is under investigation. In comparing the applications, we assume that both the existing and developed applications have been developed using Java technology. From this comparison, we can see that the developed system has many benefits: it can send large size image file, it can send several files at a single sending and it can also merge and decompress several files to become a single file. Moreover, it keeps the quality of the image file intact, same as the original one. To evaluate the performance of applications that are developed, we have conducted experiments using JPEG images of sizes larger than the maximum capacity of 30 KB. The results of the compression and split file techniques are shown in Table II. TABLE II. Data Size 53 KB 5 KB 2 KB 0 KB 00 KB MEASUREMENT PERFORMANCE BASED ON COMPRESSION RESULT (QUANTIZATION 50%). Reduced File Size After Compression 5 KB 33 KB 52 KB 2 KB 69 KB Split files files 2 files 2 files file 3 files Split File Sizes 5 6, 7 25, , 26, 23 V. CONCLUSION AND FUTURE WORK In this paper, we have presented a novel technique to improve the ability of the existing MMS for sending large size JPEG image files. This is achieved by implementing REFERENCES [] Gwenae l Le Bodic, Mobile Messaging Technologies and Services SMS, EMS, MMS, Second Edition, Jhon Wiley & Sons, Chichester, England, 2005, pp [2] Gwenae l Le Bodic, Multimedia Messaging Service: An Engineering Approach to MMS, Jhon Wiley & Sons, Chichester, England, 2003, pp [3] Open Mobile Alliance, Multimedia Messaging Service Architecture Overview, OMA-WAP-MMS-ARCH-v_ C, Approved Version., [4] Open Mobile Alliance, Multimedia Messaging Service Encapsulation Protocol, OMA-MMS-ENC-V_ A, Approved Version.2, [5] Open Mobile Alliance, Multimedia Messaging Service Requirement Candidate Version, OMA-MMS-ENC-V_ C, Approved Version.3, [6] JPEG image compression FAQ [Online], Available: (200). [7] Mark Nelson and Jean Loup Gailly, the Data Compression Book, Second Edition. M&T Books, 996. [8] Tinku Acharya and Ping-Sing Tsai, JPEG2000 Standard for Image Compression: Concepts, Algorithms and VLSI Architectures, A Jhon Wiley & Sons, Canada, [9] Rafael C. Gonzales and Richard E. Woods, Digital Image Processing: Second Edition, Prentice Hall, USA, 200. [0] Jhon C. Russ, Image Processing Handbook Fifth Edition, CRC Taylor and Francis, USA, [] Syed Ali Khayam, the Discrete Cosine Transform (DCT): Theory and Application, Department of Electrical and Computer Engineering, Michigan State University, [2] Jiří Hermany, Compression Methods Using 3D DCT, Doctoral Degree Programme. [3] Forum Nokia, Nokia MMS FAQ Version. [online], available: [4] David Salomon, Data Compression, the Complete Reference, Third Edition, Springer, USA, V2-6
Conceptual Framework Strategies for Image Compression: A Review
 International Journal of Computer Sciences and Engineering Open Access Review Paper Volume-4, Special Issue-1 E-ISSN: 2347-2693 Conceptual Framework Strategies for Image Compression: A Review Sumanta Lal
International Journal of Computer Sciences and Engineering Open Access Review Paper Volume-4, Special Issue-1 E-ISSN: 2347-2693 Conceptual Framework Strategies for Image Compression: A Review Sumanta Lal
Image Compression through DCT and Huffman Coding Technique
 International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347 5161 2015 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Research Article Rahul
International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347 5161 2015 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Research Article Rahul
Video-Conferencing System
 Video-Conferencing System Evan Broder and C. Christoher Post Introductory Digital Systems Laboratory November 2, 2007 Abstract The goal of this project is to create a video/audio conferencing system. Video
Video-Conferencing System Evan Broder and C. Christoher Post Introductory Digital Systems Laboratory November 2, 2007 Abstract The goal of this project is to create a video/audio conferencing system. Video
Comparison of different image compression formats. ECE 533 Project Report Paula Aguilera
 Comparison of different image compression formats ECE 533 Project Report Paula Aguilera Introduction: Images are very important documents nowadays; to work with them in some applications they need to be
Comparison of different image compression formats ECE 533 Project Report Paula Aguilera Introduction: Images are very important documents nowadays; to work with them in some applications they need to be
Compression techniques
 Compression techniques David Bařina February 22, 2013 David Bařina Compression techniques February 22, 2013 1 / 37 Contents 1 Terminology 2 Simple techniques 3 Entropy coding 4 Dictionary methods 5 Conclusion
Compression techniques David Bařina February 22, 2013 David Bařina Compression techniques February 22, 2013 1 / 37 Contents 1 Terminology 2 Simple techniques 3 Entropy coding 4 Dictionary methods 5 Conclusion
Lossless Grey-scale Image Compression using Source Symbols Reduction and Huffman Coding
 Lossless Grey-scale Image Compression using Source Symbols Reduction and Huffman Coding C. SARAVANAN cs@cc.nitdgp.ac.in Assistant Professor, Computer Centre, National Institute of Technology, Durgapur,WestBengal,
Lossless Grey-scale Image Compression using Source Symbols Reduction and Huffman Coding C. SARAVANAN cs@cc.nitdgp.ac.in Assistant Professor, Computer Centre, National Institute of Technology, Durgapur,WestBengal,
JPEG Image Compression by Using DCT
 International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-4, Issue-4 E-ISSN: 2347-2693 JPEG Image Compression by Using DCT Sarika P. Bagal 1* and Vishal B. Raskar 2 1*
International Journal of Computer Sciences and Engineering Open Access Research Paper Volume-4, Issue-4 E-ISSN: 2347-2693 JPEG Image Compression by Using DCT Sarika P. Bagal 1* and Vishal B. Raskar 2 1*
How to Send Video Images Through Internet
 Transmitting Video Images in XML Web Service Francisco Prieto, Antonio J. Sierra, María Carrión García Departamento de Ingeniería de Sistemas y Automática Área de Ingeniería Telemática Escuela Superior
Transmitting Video Images in XML Web Service Francisco Prieto, Antonio J. Sierra, María Carrión García Departamento de Ingeniería de Sistemas y Automática Área de Ingeniería Telemática Escuela Superior
SECURE AND EFFICIENT TRANSMISSION OF MEDICAL IMAGES OVER WIRELESS NETWORK
 SECURE AND EFFICIENT TRANSMISSION OF MEDICAL IMAGES OVER WIRELESS NETWORK Deepika.K 1, Varshini Karthik 2 1 Post Graduate Student, Department of BME, SRM University, Tamilnadu, India 2 Assistant Professor,
SECURE AND EFFICIENT TRANSMISSION OF MEDICAL IMAGES OVER WIRELESS NETWORK Deepika.K 1, Varshini Karthik 2 1 Post Graduate Student, Department of BME, SRM University, Tamilnadu, India 2 Assistant Professor,
Hybrid Lossless Compression Method For Binary Images
 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), 1399-1405 Hybrid Lossless Compression Method For Binary Images M. Fatih TALU, İbrahim TÜRKOĞLU Inonu University, Dept. of Computer Engineering, Engineering
M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), 1399-1405 Hybrid Lossless Compression Method For Binary Images M. Fatih TALU, İbrahim TÜRKOĞLU Inonu University, Dept. of Computer Engineering, Engineering
Information, Entropy, and Coding
 Chapter 8 Information, Entropy, and Coding 8. The Need for Data Compression To motivate the material in this chapter, we first consider various data sources and some estimates for the amount of data associated
Chapter 8 Information, Entropy, and Coding 8. The Need for Data Compression To motivate the material in this chapter, we first consider various data sources and some estimates for the amount of data associated
Reading.. IMAGE COMPRESSION- I IMAGE COMPRESSION. Image compression. Data Redundancy. Lossy vs Lossless Compression. Chapter 8.
 Reading.. IMAGE COMPRESSION- I Week VIII Feb 25 Chapter 8 Sections 8.1, 8.2 8.3 (selected topics) 8.4 (Huffman, run-length, loss-less predictive) 8.5 (lossy predictive, transform coding basics) 8.6 Image
Reading.. IMAGE COMPRESSION- I Week VIII Feb 25 Chapter 8 Sections 8.1, 8.2 8.3 (selected topics) 8.4 (Huffman, run-length, loss-less predictive) 8.5 (lossy predictive, transform coding basics) 8.6 Image
Study and Implementation of Video Compression Standards (H.264/AVC and Dirac)
 Project Proposal Study and Implementation of Video Compression Standards (H.264/AVC and Dirac) Sumedha Phatak-1000731131- sumedha.phatak@mavs.uta.edu Objective: A study, implementation and comparison of
Project Proposal Study and Implementation of Video Compression Standards (H.264/AVC and Dirac) Sumedha Phatak-1000731131- sumedha.phatak@mavs.uta.edu Objective: A study, implementation and comparison of
A NEW LOSSLESS METHOD OF IMAGE COMPRESSION AND DECOMPRESSION USING HUFFMAN CODING TECHNIQUES
 A NEW LOSSLESS METHOD OF IMAGE COMPRESSION AND DECOMPRESSION USING HUFFMAN CODING TECHNIQUES 1 JAGADISH H. PUJAR, 2 LOHIT M. KADLASKAR 1 Faculty, Department of EEE, B V B College of Engg. & Tech., Hubli,
A NEW LOSSLESS METHOD OF IMAGE COMPRESSION AND DECOMPRESSION USING HUFFMAN CODING TECHNIQUES 1 JAGADISH H. PUJAR, 2 LOHIT M. KADLASKAR 1 Faculty, Department of EEE, B V B College of Engg. & Tech., Hubli,
Statistical Modeling of Huffman Tables Coding
 Statistical Modeling of Huffman Tables Coding S. Battiato 1, C. Bosco 1, A. Bruna 2, G. Di Blasi 1, G.Gallo 1 1 D.M.I. University of Catania - Viale A. Doria 6, 95125, Catania, Italy {battiato, bosco,
Statistical Modeling of Huffman Tables Coding S. Battiato 1, C. Bosco 1, A. Bruna 2, G. Di Blasi 1, G.Gallo 1 1 D.M.I. University of Catania - Viale A. Doria 6, 95125, Catania, Italy {battiato, bosco,
Introduction to Medical Image Compression Using Wavelet Transform
 National Taiwan University Graduate Institute of Communication Engineering Time Frequency Analysis and Wavelet Transform Term Paper Introduction to Medical Image Compression Using Wavelet Transform 李 自
National Taiwan University Graduate Institute of Communication Engineering Time Frequency Analysis and Wavelet Transform Term Paper Introduction to Medical Image Compression Using Wavelet Transform 李 自
A Robust and Lossless Information Embedding in Image Based on DCT and Scrambling Algorithms
 A Robust and Lossless Information Embedding in Image Based on DCT and Scrambling Algorithms Dr. Mohammad V. Malakooti Faculty and Head of Department of Computer Engineering, Islamic Azad University, UAE
A Robust and Lossless Information Embedding in Image Based on DCT and Scrambling Algorithms Dr. Mohammad V. Malakooti Faculty and Head of Department of Computer Engineering, Islamic Azad University, UAE
Introduction to image coding
 Introduction to image coding Image coding aims at reducing amount of data required for image representation, storage or transmission. This is achieved by removing redundant data from an image, i.e. by
Introduction to image coding Image coding aims at reducing amount of data required for image representation, storage or transmission. This is achieved by removing redundant data from an image, i.e. by
DCT-JPEG Image Coding Based on GPU
 , pp. 293-302 http://dx.doi.org/10.14257/ijhit.2015.8.5.32 DCT-JPEG Image Coding Based on GPU Rongyang Shan 1, Chengyou Wang 1*, Wei Huang 2 and Xiao Zhou 1 1 School of Mechanical, Electrical and Information
, pp. 293-302 http://dx.doi.org/10.14257/ijhit.2015.8.5.32 DCT-JPEG Image Coding Based on GPU Rongyang Shan 1, Chengyou Wang 1*, Wei Huang 2 and Xiao Zhou 1 1 School of Mechanical, Electrical and Information
JPEG compression of monochrome 2D-barcode images using DCT coefficient distributions
 Edith Cowan University Research Online ECU Publications Pre. JPEG compression of monochrome D-barcode images using DCT coefficient distributions Keng Teong Tan Hong Kong Baptist University Douglas Chai
Edith Cowan University Research Online ECU Publications Pre. JPEG compression of monochrome D-barcode images using DCT coefficient distributions Keng Teong Tan Hong Kong Baptist University Douglas Chai
ANALYSIS OF THE EFFECTIVENESS IN IMAGE COMPRESSION FOR CLOUD STORAGE FOR VARIOUS IMAGE FORMATS
 ANALYSIS OF THE EFFECTIVENESS IN IMAGE COMPRESSION FOR CLOUD STORAGE FOR VARIOUS IMAGE FORMATS Dasaradha Ramaiah K. 1 and T. Venugopal 2 1 IT Department, BVRIT, Hyderabad, India 2 CSE Department, JNTUH,
ANALYSIS OF THE EFFECTIVENESS IN IMAGE COMPRESSION FOR CLOUD STORAGE FOR VARIOUS IMAGE FORMATS Dasaradha Ramaiah K. 1 and T. Venugopal 2 1 IT Department, BVRIT, Hyderabad, India 2 CSE Department, JNTUH,
Figure 1: Relation between codec, data containers and compression algorithms.
 Video Compression Djordje Mitrovic University of Edinburgh This document deals with the issues of video compression. The algorithm, which is used by the MPEG standards, will be elucidated upon in order
Video Compression Djordje Mitrovic University of Edinburgh This document deals with the issues of video compression. The algorithm, which is used by the MPEG standards, will be elucidated upon in order
encoding compression encryption
 encoding compression encryption ASCII utf-8 utf-16 zip mpeg jpeg AES RSA diffie-hellman Expressing characters... ASCII and Unicode, conventions of how characters are expressed in bits. ASCII (7 bits) -
encoding compression encryption ASCII utf-8 utf-16 zip mpeg jpeg AES RSA diffie-hellman Expressing characters... ASCII and Unicode, conventions of how characters are expressed in bits. ASCII (7 bits) -
MMGD0203 Multimedia Design MMGD0203 MULTIMEDIA DESIGN. Chapter 3 Graphics and Animations
 MMGD0203 MULTIMEDIA DESIGN Chapter 3 Graphics and Animations 1 Topics: Definition of Graphics Why use Graphics? Graphics Categories Graphics Qualities File Formats Types of Graphics Graphic File Size Introduction
MMGD0203 MULTIMEDIA DESIGN Chapter 3 Graphics and Animations 1 Topics: Definition of Graphics Why use Graphics? Graphics Categories Graphics Qualities File Formats Types of Graphics Graphic File Size Introduction
A comprehensive survey on various ETC techniques for secure Data transmission
 A comprehensive survey on various ETC techniques for secure Data transmission Shaikh Nasreen 1, Prof. Suchita Wankhade 2 1, 2 Department of Computer Engineering 1, 2 Trinity College of Engineering and
A comprehensive survey on various ETC techniques for secure Data transmission Shaikh Nasreen 1, Prof. Suchita Wankhade 2 1, 2 Department of Computer Engineering 1, 2 Trinity College of Engineering and
http://www.springer.com/0-387-23402-0
 http://www.springer.com/0-387-23402-0 Chapter 2 VISUAL DATA FORMATS 1. Image and Video Data Digital visual data is usually organised in rectangular arrays denoted as frames, the elements of these arrays
http://www.springer.com/0-387-23402-0 Chapter 2 VISUAL DATA FORMATS 1. Image and Video Data Digital visual data is usually organised in rectangular arrays denoted as frames, the elements of these arrays
CM0340 SOLNS. Do not turn this page over until instructed to do so by the Senior Invigilator.
 CARDIFF UNIVERSITY EXAMINATION PAPER Academic Year: 2008/2009 Examination Period: Examination Paper Number: Examination Paper Title: SOLUTIONS Duration: Autumn CM0340 SOLNS Multimedia 2 hours Do not turn
CARDIFF UNIVERSITY EXAMINATION PAPER Academic Year: 2008/2009 Examination Period: Examination Paper Number: Examination Paper Title: SOLUTIONS Duration: Autumn CM0340 SOLNS Multimedia 2 hours Do not turn
Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals. Introduction
 Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals Modified from the lecture slides of Lami Kaya (LKaya@ieee.org) for use CECS 474, Fall 2008. 2009 Pearson Education Inc., Upper
Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals Modified from the lecture slides of Lami Kaya (LKaya@ieee.org) for use CECS 474, Fall 2008. 2009 Pearson Education Inc., Upper
INTERNATIONAL TELECOMMUNICATION UNION TERMINAL EQUIPMENT AND PROTOCOLS FOR TELEMATIC SERVICES
 INTERNATIONAL TELECOMMUNICATION UNION CCITT T.81 THE INTERNATIONAL (09/92) TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE TERMINAL EQUIPMENT AND PROTOCOLS FOR TELEMATIC SERVICES INFORMATION TECHNOLOGY
INTERNATIONAL TELECOMMUNICATION UNION CCITT T.81 THE INTERNATIONAL (09/92) TELEGRAPH AND TELEPHONE CONSULTATIVE COMMITTEE TERMINAL EQUIPMENT AND PROTOCOLS FOR TELEMATIC SERVICES INFORMATION TECHNOLOGY
CHAPTER 2 LITERATURE REVIEW
 11 CHAPTER 2 LITERATURE REVIEW 2.1 INTRODUCTION Image compression is mainly used to reduce storage space, transmission time and bandwidth requirements. In the subsequent sections of this chapter, general
11 CHAPTER 2 LITERATURE REVIEW 2.1 INTRODUCTION Image compression is mainly used to reduce storage space, transmission time and bandwidth requirements. In the subsequent sections of this chapter, general
Development and Evaluation of Point Cloud Compression for the Point Cloud Library
 Development and Evaluation of Point Cloud Compression for the Institute for Media Technology, TUM, Germany May 12, 2011 Motivation Point Cloud Stream Compression Network Point Cloud Stream Decompression
Development and Evaluation of Point Cloud Compression for the Institute for Media Technology, TUM, Germany May 12, 2011 Motivation Point Cloud Stream Compression Network Point Cloud Stream Decompression
How To Recognize Voice Over Ip On Pc Or Mac Or Ip On A Pc Or Ip (Ip) On A Microsoft Computer Or Ip Computer On A Mac Or Mac (Ip Or Ip) On An Ip Computer Or Mac Computer On An Mp3
 Recognizing Voice Over IP: A Robust Front-End for Speech Recognition on the World Wide Web. By C.Moreno, A. Antolin and F.Diaz-de-Maria. Summary By Maheshwar Jayaraman 1 1. Introduction Voice Over IP is
Recognizing Voice Over IP: A Robust Front-End for Speech Recognition on the World Wide Web. By C.Moreno, A. Antolin and F.Diaz-de-Maria. Summary By Maheshwar Jayaraman 1 1. Introduction Voice Over IP is
Sachin Dhawan Deptt. of ECE, UIET, Kurukshetra University, Kurukshetra, Haryana, India
 Abstract Image compression is now essential for applications such as transmission and storage in data bases. In this paper we review and discuss about the image compression, need of compression, its principles,
Abstract Image compression is now essential for applications such as transmission and storage in data bases. In this paper we review and discuss about the image compression, need of compression, its principles,
Video Coding Basics. Yao Wang Polytechnic University, Brooklyn, NY11201 yao@vision.poly.edu
 Video Coding Basics Yao Wang Polytechnic University, Brooklyn, NY11201 yao@vision.poly.edu Outline Motivation for video coding Basic ideas in video coding Block diagram of a typical video codec Different
Video Coding Basics Yao Wang Polytechnic University, Brooklyn, NY11201 yao@vision.poly.edu Outline Motivation for video coding Basic ideas in video coding Block diagram of a typical video codec Different
MP3 Player CSEE 4840 SPRING 2010 PROJECT DESIGN. zl2211@columbia.edu. ml3088@columbia.edu
 MP3 Player CSEE 4840 SPRING 2010 PROJECT DESIGN Zheng Lai Zhao Liu Meng Li Quan Yuan zl2215@columbia.edu zl2211@columbia.edu ml3088@columbia.edu qy2123@columbia.edu I. Overview Architecture The purpose
MP3 Player CSEE 4840 SPRING 2010 PROJECT DESIGN Zheng Lai Zhao Liu Meng Li Quan Yuan zl2215@columbia.edu zl2211@columbia.edu ml3088@columbia.edu qy2123@columbia.edu I. Overview Architecture The purpose
The enhancement of the operating speed of the algorithm of adaptive compression of binary bitmap images
 The enhancement of the operating speed of the algorithm of adaptive compression of binary bitmap images Borusyak A.V. Research Institute of Applied Mathematics and Cybernetics Lobachevsky Nizhni Novgorod
The enhancement of the operating speed of the algorithm of adaptive compression of binary bitmap images Borusyak A.V. Research Institute of Applied Mathematics and Cybernetics Lobachevsky Nizhni Novgorod
For Articulation Purpose Only
 E305 Digital Audio and Video (4 Modular Credits) This document addresses the content related abilities, with reference to the module. Abilities of thinking, learning, problem solving, team work, communication,
E305 Digital Audio and Video (4 Modular Credits) This document addresses the content related abilities, with reference to the module. Abilities of thinking, learning, problem solving, team work, communication,
ANALYSIS OF THE COMPRESSION RATIO AND QUALITY IN MEDICAL IMAGES
 ISSN 392 24X INFORMATION TECHNOLOGY AND CONTROL, 2006, Vol.35, No.4 ANALYSIS OF THE COMPRESSION RATIO AND QUALITY IN MEDICAL IMAGES Darius Mateika, Romanas Martavičius Department of Electronic Systems,
ISSN 392 24X INFORMATION TECHNOLOGY AND CONTROL, 2006, Vol.35, No.4 ANALYSIS OF THE COMPRESSION RATIO AND QUALITY IN MEDICAL IMAGES Darius Mateika, Romanas Martavičius Department of Electronic Systems,
H.264/MPEG-4 AVC Video Compression Tutorial
 Introduction The upcoming H.264/MPEG-4 AVC video compression standard promises a significant improvement over all previous video compression standards. In terms of coding efficiency, the new standard is
Introduction The upcoming H.264/MPEG-4 AVC video compression standard promises a significant improvement over all previous video compression standards. In terms of coding efficiency, the new standard is
 SteganographyinaVideoConferencingSystem? AndreasWestfeld1andGrittaWolf2 2InstituteforOperatingSystems,DatabasesandComputerNetworks 1InstituteforTheoreticalComputerScience DresdenUniversityofTechnology
SteganographyinaVideoConferencingSystem? AndreasWestfeld1andGrittaWolf2 2InstituteforOperatingSystems,DatabasesandComputerNetworks 1InstituteforTheoreticalComputerScience DresdenUniversityofTechnology
Chapter 10: Multimedia and the Web
 Understanding Computers Today and Tomorrow 12 th Edition Chapter 10: Multimedia and the Web Learning Objectives Define Web-based multimedia and list some advantages and disadvantages of using multimedia.
Understanding Computers Today and Tomorrow 12 th Edition Chapter 10: Multimedia and the Web Learning Objectives Define Web-based multimedia and list some advantages and disadvantages of using multimedia.
Secured Lossless Medical Image Compression Based On Adaptive Binary Optimization
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IV (Mar-Apr. 2014), PP 43-47 Secured Lossless Medical Image Compression Based On Adaptive Binary
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IV (Mar-Apr. 2014), PP 43-47 Secured Lossless Medical Image Compression Based On Adaptive Binary
HIGH DENSITY DATA STORAGE IN DNA USING AN EFFICIENT MESSAGE ENCODING SCHEME Rahul Vishwakarma 1 and Newsha Amiri 2
 HIGH DENSITY DATA STORAGE IN DNA USING AN EFFICIENT MESSAGE ENCODING SCHEME Rahul Vishwakarma 1 and Newsha Amiri 2 1 Tata Consultancy Services, India derahul@ieee.org 2 Bangalore University, India ABSTRACT
HIGH DENSITY DATA STORAGE IN DNA USING AN EFFICIENT MESSAGE ENCODING SCHEME Rahul Vishwakarma 1 and Newsha Amiri 2 1 Tata Consultancy Services, India derahul@ieee.org 2 Bangalore University, India ABSTRACT
Video Authentication for H.264/AVC using Digital Signature Standard and Secure Hash Algorithm
 Video Authentication for H.264/AVC using Digital Signature Standard and Secure Hash Algorithm Nandakishore Ramaswamy Qualcomm Inc 5775 Morehouse Dr, Sam Diego, CA 92122. USA nandakishore@qualcomm.com K.
Video Authentication for H.264/AVC using Digital Signature Standard and Secure Hash Algorithm Nandakishore Ramaswamy Qualcomm Inc 5775 Morehouse Dr, Sam Diego, CA 92122. USA nandakishore@qualcomm.com K.
Indexing and Compression of Text
 Compressing the Digital Library Timothy C. Bell 1, Alistair Moffat 2, and Ian H. Witten 3 1 Department of Computer Science, University of Canterbury, New Zealand, tim@cosc.canterbury.ac.nz 2 Department
Compressing the Digital Library Timothy C. Bell 1, Alistair Moffat 2, and Ian H. Witten 3 1 Department of Computer Science, University of Canterbury, New Zealand, tim@cosc.canterbury.ac.nz 2 Department
Structures for Data Compression Responsible persons: Claudia Dolci, Dante Salvini, Michael Schrattner, Robert Weibel
 Geographic Information Technology Training Alliance (GITTA) presents: Responsible persons: Claudia Dolci, Dante Salvini, Michael Schrattner, Robert Weibel Content 1.... 2 1.1. General Compression Concepts...3
Geographic Information Technology Training Alliance (GITTA) presents: Responsible persons: Claudia Dolci, Dante Salvini, Michael Schrattner, Robert Weibel Content 1.... 2 1.1. General Compression Concepts...3
Implementation of ASIC For High Resolution Image Compression In Jpeg Format
 IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 5, Issue 4, Ver. I (Jul - Aug. 2015), PP 01-10 e-issn: 2319 4200, p-issn No. : 2319 4197 www.iosrjournals.org Implementation of ASIC For High
IOSR Journal of VLSI and Signal Processing (IOSR-JVSP) Volume 5, Issue 4, Ver. I (Jul - Aug. 2015), PP 01-10 e-issn: 2319 4200, p-issn No. : 2319 4197 www.iosrjournals.org Implementation of ASIC For High
Fast Arithmetic Coding (FastAC) Implementations
 Fast Arithmetic Coding (FastAC) Implementations Amir Said 1 Introduction This document describes our fast implementations of arithmetic coding, which achieve optimal compression and higher throughput by
Fast Arithmetic Coding (FastAC) Implementations Amir Said 1 Introduction This document describes our fast implementations of arithmetic coding, which achieve optimal compression and higher throughput by
ANALYSIS AND EFFICIENCY OF ERROR FREE COMPRESSION ALGORITHM FOR MEDICAL IMAGE
 ANALYSIS AND EFFICIENCY OF ERROR FREE COMPRESSION ALGORITHM FOR MEDICAL IMAGE 1 J HEMAMALINI, 2 D KAAVYA 1 Asstt Prof., Department of Information Technology, Sathyabama University, Chennai, Tamil Nadu
ANALYSIS AND EFFICIENCY OF ERROR FREE COMPRESSION ALGORITHM FOR MEDICAL IMAGE 1 J HEMAMALINI, 2 D KAAVYA 1 Asstt Prof., Department of Information Technology, Sathyabama University, Chennai, Tamil Nadu
Storage Optimization in Cloud Environment using Compression Algorithm
 Storage Optimization in Cloud Environment using Compression Algorithm K.Govinda 1, Yuvaraj Kumar 2 1 School of Computing Science and Engineering, VIT University, Vellore, India kgovinda@vit.ac.in 2 School
Storage Optimization in Cloud Environment using Compression Algorithm K.Govinda 1, Yuvaraj Kumar 2 1 School of Computing Science and Engineering, VIT University, Vellore, India kgovinda@vit.ac.in 2 School
Narrow Bandwidth Streaming Video Codec
 Software Requirements Specification for Narrow Bandwidth Streaming Video Codec Version 1.0 approved Internal Supervisors Dr. Shantha Frenando Dr. Chathura de Silva External Supervisors Mr. Harsha Samarawicrama
Software Requirements Specification for Narrow Bandwidth Streaming Video Codec Version 1.0 approved Internal Supervisors Dr. Shantha Frenando Dr. Chathura de Silva External Supervisors Mr. Harsha Samarawicrama
A JPEG Decoder Implementation in C Chris Tralie ELE 201 Fall 2007
 A JPEG Decoder Implementation in C Chris Tralie ELE 201 Fall 2007 Due 1/11/2008 Professor Sanjeev Kulkarni 1. Introduction The purpose of this project is to create a decoder program in C that can interpret
A JPEG Decoder Implementation in C Chris Tralie ELE 201 Fall 2007 Due 1/11/2008 Professor Sanjeev Kulkarni 1. Introduction The purpose of this project is to create a decoder program in C that can interpret
Analysis of Compression Algorithms for Program Data
 Analysis of Compression Algorithms for Program Data Matthew Simpson, Clemson University with Dr. Rajeev Barua and Surupa Biswas, University of Maryland 12 August 3 Abstract Insufficient available memory
Analysis of Compression Algorithms for Program Data Matthew Simpson, Clemson University with Dr. Rajeev Barua and Surupa Biswas, University of Maryland 12 August 3 Abstract Insufficient available memory
Dynamic Adaptation in an Image Transcoding Proxy For Mobile Web Browsing
 Dynamic Adaptation in an Image Transcoding Proxy For Mobile Web Browsing Pravin Bhagwat, Richard Han, Richard LaMaire, Todd Mummert, Veronique Perret, Jim Rubas Mobile Networking Group Chung-Sheng Li,
Dynamic Adaptation in an Image Transcoding Proxy For Mobile Web Browsing Pravin Bhagwat, Richard Han, Richard LaMaire, Todd Mummert, Veronique Perret, Jim Rubas Mobile Networking Group Chung-Sheng Li,
Transform-domain Wyner-Ziv Codec for Video
 Transform-domain Wyner-Ziv Codec for Video Anne Aaron, Shantanu Rane, Eric Setton, and Bernd Girod Information Systems Laboratory, Department of Electrical Engineering Stanford University 350 Serra Mall,
Transform-domain Wyner-Ziv Codec for Video Anne Aaron, Shantanu Rane, Eric Setton, and Bernd Girod Information Systems Laboratory, Department of Electrical Engineering Stanford University 350 Serra Mall,
ADVANCED APPLICATIONS OF ELECTRICAL ENGINEERING
 Development of a Software Tool for Performance Evaluation of MIMO OFDM Alamouti using a didactical Approach as a Educational and Research support in Wireless Communications JOSE CORDOVA, REBECA ESTRADA
Development of a Software Tool for Performance Evaluation of MIMO OFDM Alamouti using a didactical Approach as a Educational and Research support in Wireless Communications JOSE CORDOVA, REBECA ESTRADA
Multi-factor Authentication in Banking Sector
 Multi-factor Authentication in Banking Sector Tushar Bhivgade, Mithilesh Bhusari, Ajay Kuthe, Bhavna Jiddewar,Prof. Pooja Dubey Department of Computer Science & Engineering, Rajiv Gandhi College of Engineering
Multi-factor Authentication in Banking Sector Tushar Bhivgade, Mithilesh Bhusari, Ajay Kuthe, Bhavna Jiddewar,Prof. Pooja Dubey Department of Computer Science & Engineering, Rajiv Gandhi College of Engineering
Study and Implementation of Video Compression standards (H.264/AVC, Dirac)
 Study and Implementation of Video Compression standards (H.264/AVC, Dirac) EE 5359-Multimedia Processing- Spring 2012 Dr. K.R Rao By: Sumedha Phatak(1000731131) Objective A study, implementation and comparison
Study and Implementation of Video Compression standards (H.264/AVC, Dirac) EE 5359-Multimedia Processing- Spring 2012 Dr. K.R Rao By: Sumedha Phatak(1000731131) Objective A study, implementation and comparison
Quality Estimation for Scalable Video Codec. Presented by Ann Ukhanova (DTU Fotonik, Denmark) Kashaf Mazhar (KTH, Sweden)
 Quality Estimation for Scalable Video Codec Presented by Ann Ukhanova (DTU Fotonik, Denmark) Kashaf Mazhar (KTH, Sweden) Purpose of scalable video coding Multiple video streams are needed for heterogeneous
Quality Estimation for Scalable Video Codec Presented by Ann Ukhanova (DTU Fotonik, Denmark) Kashaf Mazhar (KTH, Sweden) Purpose of scalable video coding Multiple video streams are needed for heterogeneous
International Archives of the Photogrammetry, Remote Sensing and Spatial Information Sciences, Vol. XXXIV-5/W10
 Accurate 3D information extraction from large-scale data compressed image and the study of the optimum stereo imaging method Riichi NAGURA *, * Kanagawa Institute of Technology nagura@ele.kanagawa-it.ac.jp
Accurate 3D information extraction from large-scale data compressed image and the study of the optimum stereo imaging method Riichi NAGURA *, * Kanagawa Institute of Technology nagura@ele.kanagawa-it.ac.jp
Lossless Medical Image Compression using Predictive Coding and Integer Wavelet Transform based on Minimum Entropy Criteria
 Lossless Medical Image Compression using Predictive Coding and Integer Wavelet Transform based on Minimum Entropy Criteria 1 Komal Gupta, Ram Lautan Verma, 3 Md. Sanawer Alam 1 M.Tech Scholar, Deptt. Of
Lossless Medical Image Compression using Predictive Coding and Integer Wavelet Transform based on Minimum Entropy Criteria 1 Komal Gupta, Ram Lautan Verma, 3 Md. Sanawer Alam 1 M.Tech Scholar, Deptt. Of
Data Storage. Chapter 3. Objectives. 3-1 Data Types. Data Inside the Computer. After studying this chapter, students should be able to:
 Chapter 3 Data Storage Objectives After studying this chapter, students should be able to: List five different data types used in a computer. Describe how integers are stored in a computer. Describe how
Chapter 3 Data Storage Objectives After studying this chapter, students should be able to: List five different data types used in a computer. Describe how integers are stored in a computer. Describe how
JOURNAL OF TELECOMMUNICATIONS, VOLUME 2, ISSUE 2, MAY 2010 126. Simulink based VoIP Analysis. Hardeep Singh Dalhio, Jasvir Singh, M.
 126 Simulink based VoIP Analysis Hardeep Singh Dalhio, Jasvir Singh, M. Mian Abstract Voice communication over internet not be possible without a reliable data network, this was first available when distributed
126 Simulink based VoIP Analysis Hardeep Singh Dalhio, Jasvir Singh, M. Mian Abstract Voice communication over internet not be possible without a reliable data network, this was first available when distributed
Technical Specifications for KD5HIO Software
 Technical Specifications for KD5HIO Software Version 0.2 12/12/2000 by Glen Hansen, KD5HIO HamScope Forward Error Correction Algorithms HamScope is a terminal program designed to support multi-mode digital
Technical Specifications for KD5HIO Software Version 0.2 12/12/2000 by Glen Hansen, KD5HIO HamScope Forward Error Correction Algorithms HamScope is a terminal program designed to support multi-mode digital
WATERMARKING FOR IMAGE AUTHENTICATION
 WATERMARKING FOR IMAGE AUTHENTICATION Min Wu Bede Liu Department of Electrical Engineering Princeton University, Princeton, NJ 08544, USA Fax: +1-609-258-3745 {minwu, liu}@ee.princeton.edu ABSTRACT A data
WATERMARKING FOR IMAGE AUTHENTICATION Min Wu Bede Liu Department of Electrical Engineering Princeton University, Princeton, NJ 08544, USA Fax: +1-609-258-3745 {minwu, liu}@ee.princeton.edu ABSTRACT A data
Khalid Sayood and Martin C. Rost Department of Electrical Engineering University of Nebraska
 PROBLEM STATEMENT A ROBUST COMPRESSION SYSTEM FOR LOW BIT RATE TELEMETRY - TEST RESULTS WITH LUNAR DATA Khalid Sayood and Martin C. Rost Department of Electrical Engineering University of Nebraska The
PROBLEM STATEMENT A ROBUST COMPRESSION SYSTEM FOR LOW BIT RATE TELEMETRY - TEST RESULTS WITH LUNAR DATA Khalid Sayood and Martin C. Rost Department of Electrical Engineering University of Nebraska The
Multimedia Technology Bachelor of Science
 Multimedia Technology Bachelor of Science 1. Program s Name Thai Name : ว ทยาศาสตรบ ณฑ ต สาขาว ชาเทคโนโลย ม ลต ม เด ย English Name : Bachelor of Science Program in Multimedia Technology 2. Degree Full
Multimedia Technology Bachelor of Science 1. Program s Name Thai Name : ว ทยาศาสตรบ ณฑ ต สาขาว ชาเทคโนโลย ม ลต ม เด ย English Name : Bachelor of Science Program in Multimedia Technology 2. Degree Full
Video compression: Performance of available codec software
 Video compression: Performance of available codec software Introduction. Digital Video A digital video is a collection of images presented sequentially to produce the effect of continuous motion. It takes
Video compression: Performance of available codec software Introduction. Digital Video A digital video is a collection of images presented sequentially to produce the effect of continuous motion. It takes
Today s topics. Digital Computers. More on binary. Binary Digits (Bits)
 Today s topics! Binary Numbers! Brookshear.-.! Slides from Prof. Marti Hearst of UC Berkeley SIMS! Upcoming! Networks Interactive Introduction to Graph Theory http://www.utm.edu/cgi-bin/caldwell/tutor/departments/math/graph/intro
Today s topics! Binary Numbers! Brookshear.-.! Slides from Prof. Marti Hearst of UC Berkeley SIMS! Upcoming! Networks Interactive Introduction to Graph Theory http://www.utm.edu/cgi-bin/caldwell/tutor/departments/math/graph/intro
Hybrid Compression of Medical Images Based on Huffman and LPC For Telemedicine Application
 IJIRST International Journal for Innovative Research in Science & Technology Volume 1 Issue 6 November 2014 ISSN (online): 2349-6010 Hybrid Compression of Medical Images Based on Huffman and LPC For Telemedicine
IJIRST International Journal for Innovative Research in Science & Technology Volume 1 Issue 6 November 2014 ISSN (online): 2349-6010 Hybrid Compression of Medical Images Based on Huffman and LPC For Telemedicine
Data Storage 3.1. Foundations of Computer Science Cengage Learning
 3 Data Storage 3.1 Foundations of Computer Science Cengage Learning Objectives After studying this chapter, the student should be able to: List five different data types used in a computer. Describe how
3 Data Storage 3.1 Foundations of Computer Science Cengage Learning Objectives After studying this chapter, the student should be able to: List five different data types used in a computer. Describe how
ENG4BF3 Medical Image Processing. Image Visualization
 ENG4BF3 Medical Image Processing Image Visualization Visualization Methods Visualization of medical images is for the determination of the quantitative information about the properties of anatomic tissues
ENG4BF3 Medical Image Processing Image Visualization Visualization Methods Visualization of medical images is for the determination of the quantitative information about the properties of anatomic tissues
2695 P a g e. IV Semester M.Tech (DCN) SJCIT Chickballapur Karnataka India
 Integrity Preservation and Privacy Protection for Digital Medical Images M.Krishna Rani Dr.S.Bhargavi IV Semester M.Tech (DCN) SJCIT Chickballapur Karnataka India Abstract- In medical treatments, the integrity
Integrity Preservation and Privacy Protection for Digital Medical Images M.Krishna Rani Dr.S.Bhargavi IV Semester M.Tech (DCN) SJCIT Chickballapur Karnataka India Abstract- In medical treatments, the integrity
Fast Sequential Summation Algorithms Using Augmented Data Structures
 Fast Sequential Summation Algorithms Using Augmented Data Structures Vadim Stadnik vadim.stadnik@gmail.com Abstract This paper provides an introduction to the design of augmented data structures that offer
Fast Sequential Summation Algorithms Using Augmented Data Structures Vadim Stadnik vadim.stadnik@gmail.com Abstract This paper provides an introduction to the design of augmented data structures that offer
Introduction and Comparison of Common Videoconferencing Audio Protocols I. Digital Audio Principles
 Introduction and Comparison of Common Videoconferencing Audio Protocols I. Digital Audio Principles Sound is an energy wave with frequency and amplitude. Frequency maps the axis of time, and amplitude
Introduction and Comparison of Common Videoconferencing Audio Protocols I. Digital Audio Principles Sound is an energy wave with frequency and amplitude. Frequency maps the axis of time, and amplitude
Steganography Based Seaport Security Communication System
 , pp.302-306 http://dx.doi.org/10.14257/astl.2014.46.63 Steganography Based Seaport Security Communication System Yair Wiseman 1, 1 Computer Science Department Ramat-Gan 52900, Israel wiseman@cs.biu.ac.il
, pp.302-306 http://dx.doi.org/10.14257/astl.2014.46.63 Steganography Based Seaport Security Communication System Yair Wiseman 1, 1 Computer Science Department Ramat-Gan 52900, Israel wiseman@cs.biu.ac.il
From Concept to Production in Secure Voice Communications
 From Concept to Production in Secure Voice Communications Earl E. Swartzlander, Jr. Electrical and Computer Engineering Department University of Texas at Austin Austin, TX 78712 Abstract In the 1970s secure
From Concept to Production in Secure Voice Communications Earl E. Swartzlander, Jr. Electrical and Computer Engineering Department University of Texas at Austin Austin, TX 78712 Abstract In the 1970s secure
Identification of TV Programs Based on Provider s Logo Analysis
 AUTOMATYKA 2010 Tom 14 Zeszyt 3/1 Marta Chodyka*, W³odzimierz Mosorow** Identification of TV Programs Based on Provider s Logo Analysis 1. Introduction The problem of an easy access of underage persons
AUTOMATYKA 2010 Tom 14 Zeszyt 3/1 Marta Chodyka*, W³odzimierz Mosorow** Identification of TV Programs Based on Provider s Logo Analysis 1. Introduction The problem of an easy access of underage persons
Module 8 VIDEO CODING STANDARDS. Version 2 ECE IIT, Kharagpur
 Module 8 VIDEO CODING STANDARDS Version ECE IIT, Kharagpur Lesson H. andh.3 Standards Version ECE IIT, Kharagpur Lesson Objectives At the end of this lesson the students should be able to :. State the
Module 8 VIDEO CODING STANDARDS Version ECE IIT, Kharagpur Lesson H. andh.3 Standards Version ECE IIT, Kharagpur Lesson Objectives At the end of this lesson the students should be able to :. State the
HYPER MEDIA MESSAGING
 Email based document interchange known as messaging service and contribute to corporate productivity in following ways 1. it strengthens the automation of documentation life cycle 2. It allows document
Email based document interchange known as messaging service and contribute to corporate productivity in following ways 1. it strengthens the automation of documentation life cycle 2. It allows document
An Implementation of a High Capacity 2D Barcode
 An Implementation of a High Capacity 2D Barcode Puchong Subpratatsavee 1 and Pramote Kuacharoen 2 Department of Computer Science, Graduate School of Applied Statistics National Institute of Development
An Implementation of a High Capacity 2D Barcode Puchong Subpratatsavee 1 and Pramote Kuacharoen 2 Department of Computer Science, Graduate School of Applied Statistics National Institute of Development
Data Mining Project Report. Document Clustering. Meryem Uzun-Per
 Data Mining Project Report Document Clustering Meryem Uzun-Per 504112506 Table of Content Table of Content... 2 1. Project Definition... 3 2. Literature Survey... 3 3. Methods... 4 3.1. K-means algorithm...
Data Mining Project Report Document Clustering Meryem Uzun-Per 504112506 Table of Content Table of Content... 2 1. Project Definition... 3 2. Literature Survey... 3 3. Methods... 4 3.1. K-means algorithm...
Basics of Digital Recording
 Basics of Digital Recording CONVERTING SOUND INTO NUMBERS In a digital recording system, sound is stored and manipulated as a stream of discrete numbers, each number representing the air pressure at a
Basics of Digital Recording CONVERTING SOUND INTO NUMBERS In a digital recording system, sound is stored and manipulated as a stream of discrete numbers, each number representing the air pressure at a
Structure of the Lecture. Assignment from last week
 Grundzüge der Wirtschaftsinformatik Introduction to Business Information Systems Unit 8 Pr. Dr. Martin Hepp http://www.heppnetz.de mhepp@computer.org http://www.heppnetz.de/teaching/gwi/ Structure the
Grundzüge der Wirtschaftsinformatik Introduction to Business Information Systems Unit 8 Pr. Dr. Martin Hepp http://www.heppnetz.de mhepp@computer.org http://www.heppnetz.de/teaching/gwi/ Structure the
MPEG Unified Speech and Audio Coding Enabling Efficient Coding of both Speech and Music
 ISO/IEC MPEG USAC Unified Speech and Audio Coding MPEG Unified Speech and Audio Coding Enabling Efficient Coding of both Speech and Music The standardization of MPEG USAC in ISO/IEC is now in its final
ISO/IEC MPEG USAC Unified Speech and Audio Coding MPEG Unified Speech and Audio Coding Enabling Efficient Coding of both Speech and Music The standardization of MPEG USAC in ISO/IEC is now in its final
EE3414 Multimedia Communication Systems Part I
 EE3414 Multimedia Communication Systems Part I Spring 2003 Lecture 1 Yao Wang Electrical and Computer Engineering Polytechnic University Course Overview A University Sequence Course in Multimedia Communication
EE3414 Multimedia Communication Systems Part I Spring 2003 Lecture 1 Yao Wang Electrical and Computer Engineering Polytechnic University Course Overview A University Sequence Course in Multimedia Communication
The Application of Text Compression to Short Message Service Using Huffman Table
 Vol.6 No.1 (Januari 2011) JURNAL GENERIC 19 The Application of Text Compression to Short Message Service Using Huffman Table Ahmad Affandi, 1 Saparudin, 2 and Erwin 3 Abstract Short Message Service (SMS)
Vol.6 No.1 (Januari 2011) JURNAL GENERIC 19 The Application of Text Compression to Short Message Service Using Huffman Table Ahmad Affandi, 1 Saparudin, 2 and Erwin 3 Abstract Short Message Service (SMS)
*EP001025692B1* EP 1 025 692 B1 (19) (11) EP 1 025 692 B1 (12) EUROPEAN PATENT SPECIFICATION
 (19) Europäisches Patentamt European Patent Office Office européen des brevets *EP002692B1* (11) EP 1 02 692 B1 (12) EUROPEAN PATENT SPECIFICATION (4) Date of publication and mention of the grant of the
(19) Europäisches Patentamt European Patent Office Office européen des brevets *EP002692B1* (11) EP 1 02 692 B1 (12) EUROPEAN PATENT SPECIFICATION (4) Date of publication and mention of the grant of the
Operational Customer Relationship Management (CRM) using Short Message Service (SMS)
 2011 2nd International Conference on Networking and Information Technology IPCSIT vol.17 (2011) (2011) IACSIT Press, Singapore Operational Customer Relationship Management (CRM) using Short Message Service
2011 2nd International Conference on Networking and Information Technology IPCSIT vol.17 (2011) (2011) IACSIT Press, Singapore Operational Customer Relationship Management (CRM) using Short Message Service
Mike Perkins, Ph.D. perk@cardinalpeak.com
 Mike Perkins, Ph.D. perk@cardinalpeak.com Summary More than 28 years of experience in research, algorithm development, system design, engineering management, executive management, and Board of Directors
Mike Perkins, Ph.D. perk@cardinalpeak.com Summary More than 28 years of experience in research, algorithm development, system design, engineering management, executive management, and Board of Directors
2 SYSTEM DESCRIPTION TECHNIQUES
 2 SYSTEM DESCRIPTION TECHNIQUES 2.1 INTRODUCTION Graphical representation of any process is always better and more meaningful than its representation in words. Moreover, it is very difficult to arrange
2 SYSTEM DESCRIPTION TECHNIQUES 2.1 INTRODUCTION Graphical representation of any process is always better and more meaningful than its representation in words. Moreover, it is very difficult to arrange
Solomon Systech Image Processor for Car Entertainment Application
 Company: Author: Piony Yeung Title: Technical Marketing Engineer Introduction Mobile video has taken off recently as a fun, viable, and even necessary addition to in-car entertainment. Several new SUV
Company: Author: Piony Yeung Title: Technical Marketing Engineer Introduction Mobile video has taken off recently as a fun, viable, and even necessary addition to in-car entertainment. Several new SUV
Get the Best Digital Images Possible. What s it all about anyway?
 Get the Best Digital Images Possible What s it all about anyway? Issues to Consider Resolution Image Size File Size Intended Use of the Image File Formats Issues to Consider Image size (width and height
Get the Best Digital Images Possible What s it all about anyway? Issues to Consider Resolution Image Size File Size Intended Use of the Image File Formats Issues to Consider Image size (width and height
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-17: Memory organisation, and types of memory
 ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-17: Memory organisation, and types of memory 1 1. Memory Organisation 2 Random access model A memory-, a data byte, or a word, or a double
ADVANCED PROCESSOR ARCHITECTURES AND MEMORY ORGANISATION Lesson-17: Memory organisation, and types of memory 1 1. Memory Organisation 2 Random access model A memory-, a data byte, or a word, or a double
Arithmetic Coding: Introduction
 Data Compression Arithmetic coding Arithmetic Coding: Introduction Allows using fractional parts of bits!! Used in PPM, JPEG/MPEG (as option), Bzip More time costly than Huffman, but integer implementation
Data Compression Arithmetic coding Arithmetic Coding: Introduction Allows using fractional parts of bits!! Used in PPM, JPEG/MPEG (as option), Bzip More time costly than Huffman, but integer implementation
Design of Efficient Algorithms for Image Compression with Application to Medical Images
 Design of Efficient Algorithms for Image Compression with Application to Medical Images Ph.D. dissertation Alexandre Krivoulets IT University of Copenhagen February 18, 2004 Abstract This thesis covers
Design of Efficient Algorithms for Image Compression with Application to Medical Images Ph.D. dissertation Alexandre Krivoulets IT University of Copenhagen February 18, 2004 Abstract This thesis covers
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay
 Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 17 Shannon-Fano-Elias Coding and Introduction to Arithmetic Coding
Information Theory and Coding Prof. S. N. Merchant Department of Electrical Engineering Indian Institute of Technology, Bombay Lecture - 17 Shannon-Fano-Elias Coding and Introduction to Arithmetic Coding
Video Conferencing Glossary of Terms
 Video Conferencing Glossary of Terms A Algorithm A step-by-step problem-solving procedure. Transmission of compressed video over a communications network requires sophisticated compression algorithms.
Video Conferencing Glossary of Terms A Algorithm A step-by-step problem-solving procedure. Transmission of compressed video over a communications network requires sophisticated compression algorithms.
International Journal of Advanced Research in Computer Science and Software Engineering
 Volume 3, Issue 7, July 23 ISSN: 2277 28X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Greedy Algorithm:
Volume 3, Issue 7, July 23 ISSN: 2277 28X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Greedy Algorithm:
