Hybrid Lossless Compression Method For Binary Images
|
|
|
- Johnathan Booker
- 10 years ago
- Views:
Transcription
1 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), Hybrid Lossless Compression Method For Binary Images M. Fatih TALU, İbrahim TÜRKOĞLU Inonu University, Dept. of Computer Engineering, Engineering Faculty, 44280, Merkez, Malatya, Turkey Tel: , Fax: Abstract: In this paper, we propose a lossless compression scheme for binary images which consists of a novel encoding algorithm which uses a new edge tracking algorithm. The proposed compression scheme has two substages: (i) encoding binary image data using the proposed encoding method (ii) compression the encoded image data using any well-known image compression method such as Huffman, Run-Length or Lempel-Ziv-Welch (LZW). The proposed encoding method contains two subsequent processes: (i) determining the starting points of independent objects (ii) obtaining their edge points and geometrical shapes information. Experimental results show that using the proposed encoding method together with any traditional compressing method improves the compression performance. Computed mathematical results related to compression performance are represented comparatively in a tabular format. 1. Introduction The objective of image compression techniques is to reduce redundancy of the image data in order to be able to store or transmit data in an efficient form. Image compression techniques can be classified into two categories: lossy and lossless. Lossless compression allows the exact original data to be reconstructed from the compressed data. It is especially preferred for artificial images such as technical drawings, icons or comics [3, 4]. 2. Related Works There are many researches and several standards involve in lossless compression of binary images in literature. In [5], a combining method which consists of gray coding and JBIG for lossless image compression was presented. In [6], finite automata based compression of bi-level image which based on graph theory was presented. In [7], a lossless bi-level image compression technique based on using reordering row and column of image data matrix and boolean function was proposed. Tompkins and Kossentini [8] proposed a segmentation algorithm for bi-level image compression using JBIG2 which were proposed by JBIG Committee. Bogdan [9] proposed a lossless binary image compression method using logic functions and spectra. Notice that lots of above mentioned algorithms are not used for artificial images. They are generally Figure 1. The schema of the proposed characteristic vector based approach Received on: Accepted on:
2 1400 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), used for CCITT standard facsimile images [10]. Finally, a lossless compression method which uses chain codes was proposed in [13]. As seen above, most previous works in literature directly compress binary image data without taking care of the characteristic vector information of objects in them. However, analysis of the characteristic vectors of objects can provide efficiency for the compression algorithms. These vectors have very important information about geometrical features of objects. When determining characteristic vector information of binary image data having especially high size, the original image data can be presented in a very smaller size. Therefore, compressing only characteristic vectors instead of whole image data can provide a very high performance aspect of execution time and compression rate for especially artificial images such as technical drawings, icons or comics. In this article, we propose a novel lossless binary image compression scheme. The proposed scheme consists of two major steps: (i) firstly, encoding image data to only characteristic vector information of objects in image by using a new edge tracing method which aims to obtain simultaneously faultless edge points and geometrical shape information of objects by scanning image matrix only once. Therefore, both characteristic vector information of image is obtained and image data which have especially high size and artificial can be encoded to a very small size. (ii) compressing the encoded data using well-known other image compression algorithms such as Huffman, Run- Length or Lempel-Ziv-Welch (LZW). In additional, the proposed scheme can reconstruct lossless copy of original image data from compressed data. that more time can be given for other processes such as classification, compression or transmission that can be used after the recognition process. It consists of a main procedure and a subfunction. The main procedure determines the starting points of inner and outer edge lines of each independent object in image. The sub-function takes a starting point from the main procedure and it starts to investigate other edge points on edge line. While strolling on any edge line, the sub-function also obtains its geometrical information. In section (2.1.1) and (2.1.2) contains sequentially sufficient information about the modified starting point detection and edge tracing algorithms The detection algorithm of starting points The starting point detection algorithm determines only starting points of inner and outer edge lines of each independent object in binary image. According to the starting point detection algorithm, any independent object has an outer starting point. This point is the starting point of outer edge line of object. In addition, any independent object has inner starting points as its hole number as. These points are starting points of inner edge lines of objects. The flow diagram of the starting point detection algorithm is represented in Figure 2. The algorithm provides to reach all objects and holes in image. The vector variable used in the algorithm is 3. Proposed Method The proposed characteristic vector based approach is showed in Figure 1. All stages related to encoding, compressing, decompressing and reconstructing of binary image data are mentioned widely at following Encoding image data A modified version of the binary object recognition method in [11, 12] is used for encoding of whole image data to characteristic vectors. It can obtain rapidly all of the inner and outer contour lines of all objects in a binary image. The method consists of a new detection algorithm of starting point and an edge detection algorithm. It aims to obtain simultaneously faultless edge points and geometrical shape information of objects by scanning image matrix only once. Therefore, the object recognition process in binary images can be carried out very quickly. It means Figure 2. Flow diagram of the starting point detection algorithm
3 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), necessary for the edge tracing algorithm Edge tracing algorithm The edge tracing algorithm takes a point from the starting point detection algorithm. This point is the starting point of any inner or outer edge line. Starting from this point, the edge tracing algorithm determines other edge points on the edge line. During this tracing process, edge direction changes are saved and encoded by using the direction vectors in Figure 3. Hence, it is hindered to control all points of objects to obtain their edge points and geometrical information. Controlling less point means that the comparison number of the algorithm is decreases. Therefore, the algorithm operates in desired speed and performance. In Figure 4 is showed the flow diagram of the edge tracing algorithm. As is seen in the flow diagram, the edge tracing algorithm takes starting points and the starting vector value from the starting point detection algorithm. Figure 4. Flow diagram the edge tracing algorithm are taken into consideration in the controlling process. After the controlling process, the angle between the found point and the current point is expressed in Equation (1). Using this angle in Equation (2), new coordinate values of the found point are computed. Figure 3. Direction vectors used by edge tracing algorithm. Vector number takes 3, 2, 1, 0 in a, b, c, d. Direction vectors are used to hold edge points of objects that have four main directions (left, right, top and bottom). Direction vectors give information about which direction we control to move to the subsequent edge point from the current edge point. Numbers on these vectors express the priority of the directions we should move. There is an angle of 900 among each vector. The edge tracing algorithm needs new direction number and vector number using former direction number and vector number to move to subsequent edge point from the current edge point. The new direction number is determined by controlling points at 8-neighboor of the current edge point. Direction numbers on the current vector sa su 45* Direction 2* Vector 180 sx round sin sy round cos 2 * (1) (2) When coming a new point in the edge tracing algorithm, it is also necessary to compute the new vector number for the following controlling process. The new vector number depends on the new direction number found. The new direction vector number is calculated by using the expression in Equation (3). The edge tracing algorithm can go ahead on edge lines on objects by renewing direction and vector values as mentioned above. The algorithm ends when it encounter to the starting point. Therefore, all inner and outer edge lines of objects can be determined by controlling only edge points of objects. (3)
4 1402 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), (a) Field Field Description Size Width of the original image 2 Bytes Height of the original image 2 Bytes Characteristic vector information of edge points ( equals the number of edge point ) Variable*3 Bits Starting points of edge lines ( equals the total number of independent object and hole, it includes and coordinate Variable*3 Bytes points of each point) Filling Points ( equals the number of filled object, it includes and coordinate points of each point) Variable*2 Bytes After completing the edge tracing algorithm, the encoded data format of original binary image shown in Figure 5 is obtained. The encoded data format consists of the dimensions of the original image (Size_Height and Size_Weight), characteristic vector information ( C ), starting points of edge lines ( D ), and filling points ( E ). The field C includes direction changes of edge points. Direction values in the field C are determined by using the direction vector in Figure 3. The field D includes starting points of inner and outer edge lines of each independent object in image. Each record in the field D includes information about one edge line. The field E includes first point of each filled object. Figure 6 presents an example binary image and result of the edge tracing algorithm for the image. Values x, y in the fields D and E are coordinate values of each point determined. The value pn in the field D shows the length of each edge line Compressing The field C obtained after the encoding process has a dataset with large size and its each (b) Field details Figure 5. (a)encoded data format (b) Detail information of (a) value is between 0 and 7 as is shown in Figure 8. Therefore, the array is very suitable to compress by using other compression techniques. In this article, we use Huffman and Lempel-Ziv-Welch (LZW) compression techniques which are known as lossless binary image compressing algorithms. The encoded array compressed by using these techniques will have been a quite small size Decompressing The decompressing process provides again obtaining of the encoded data. For this stage, one of the well known decompressing algorithms of Huffman or LZW can be used Decoding of The Encoded Data For the decoding process, first of all, a white image by using the dimensions of the original image which are Size_Height and Size_Weight is first drawn. Each record which consists of x, y and pn in the array D is sequentially read. Edge lines of objects are started to draw at x, y coordinate points of each record read. Length of each independent edge equals pn value of record read. Direction information of each (a) Figure 6. (a) Original binary image (b) Data of the original image and the encoded image. (b)
5 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), edge line is available in the field C. Edge lines are reconstructed by using this information together with the direction vectors in Figure 3. After obtaining edge points of original image, interior parts of some objects determined prior are filled using the points of the field E. Therefore, obtaining image is exact copy of original image. 4. Experiments and Discussitions We compare the comparison result produced by Run-Length which is one of lossless binary image algorithms with our method. Run-Length algorithm was especially selected among traditional algorithms. Particularly for images of technical drawings, icons or comics, it is a very efficient algorithm. However, for CCITT standard facsimile images, it is not better than other algorithms such as Huffman and LZW. Comparisons are made aspects of compression ratio and execution time. Figure 8 shows twenty binary images which have different dimensions and objects with concave or convex geometrical shape. Table 1 shows the comparison of compression ratios for the selected images. Images between image1 and image9 have smaller size than images between image10 and image19. Analyzing carefully the obtained results from images between image1 and image9, it is shown clearly that Run-Length obtains better results than proposed methods for images such as image1, image3 and image4 which have flat objects. For other images between image1 and image9, its values of compression ratios approximate to values of proposed methods, but can not reach. Compression ratios of the proposed method used together with Huffman or LZW for images between image10 and image19 which have high dimensions are very good. Table 2 shows execution times of the proposed method for processes of encoding and comparison processes and Run-Length obtained on a Pentium III 1300 MHz personal computer with 768 MB RAM. It is shown clearly that the proposed method operates very fast because of compressing only edge lines. 5. Conclusions A novel lossless binary image compression scheme based on compressing only characteristic vector information of objects in images is presented. Unlike the existing approaches, our method encodes information of edge lines obtained using the modified edge tracing method in [11] instead of directly encoding whole image data. The encoded data is then compressed by using well-known other lossless image compression algorithms such as Huffman and LZW. We believe that the proposed method will able to provide a different point of view for traditional lossless binary image compression algorithms. Finally, we have shown in the experiments that the proposed method was able to compress at least %10 better than other traditional techniques. In addition to this advantage, execution times of the proposed method are less. Focusing on gray level images without noise, we will investigate to applicable of the proposed Figure 8. Binary test images having objects with concave and convex geometrical shape.
6 1404 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), method. Table 1. Comparison of compression ratios for binary images. Image Name Black Point Num. Size Run-Length Proposed Method with LZW Proposed Method with Huffman Image x100 76,733 56,300 61,800 Image x100 31,700 30,700 63,633 Image x100 42,600 24,800 39,300 Image x100 43,867 10,167 29,167 Image x100 34,667 8,600 38,367 Image x100 23,033 13,133 51,333 Image x256 70,744 74,609 84,238 Image x256 5,390 2,227 16,133 Image x256 14,053 5,010 20,410 Image x512 74,473 88,266 88,931 Image x512 80,748 92,413 92,565 Image x512 69,716 87,300 85,500 Image x512 70,439 86,483 85,944 Image x512 76,504 89,072 86,969 Image x512 82,146 92,026 88,013 Image x512 70,928 87,012 87,774 Image x512 81,349 89,488 87,883 Image x512 63,223 77,339 78,905 Image x512 74,569 89,137 87,979 Table 2. Execution timings for compression of binary images in seconds. Proposed Method Image Run-Length Encoding Comparison time with Comparison time Image1 Name 0,120 0,080 time Huffman 0,050 with 0,120 LZW Image2 0,231 0,050 0,030 0,140 Image3 0,120 0,060 0,050 0,180 Image4 0,121 0,050 0,050 0,220 Image5 0,180 0,070 0,050 0,231 Image6 0,250 0,060 0,040 0,180 Image7 2,234 0,070 0,091 0,580 Image8 1,011 0,320 0,300 5,448 Image9 1,142 0,340 0,231 4,476 Image10 5,518 0,841 0,191 2,914 Image11 5,377 0,800 0,140 1,593 Image12 5,368 0,874 0,301 3,825 Image13 3,715 0,781 0,270 4,617 Image14 3,685 0,792 0,281 3,385 Image15 4,075 0,781 0,240 2,965 Image16 5,268 0,801 0,210 3,425 Image17 3,104 0,781 0,230 2,564 Image18 5,328 0,830 0,350 7,992 Image19 4,987 0,791 0,240 3,245
7 M.F. TALU AND İ. TÜRKOĞLU/ IU-JEEE Vol. 11(2), (2011), References [1] Russ, J.C.: The Image Processing Handbook, North Carolina State University, pp.35-41, [2] Pitas, I.: Digital Image Processing Algorithms and Applications, United States of America, pp , [3] Nelson M, Gailly JL. Data Compression Book, Second edition. New York: M&T Books, [4] Shi, Yun Q., and Sun, H., Image and video compression for multimedia engineering, ISBN , Chapter 6, pp.20-23, [5] Abdat, M., and Bellanger, M.G., Combining Gray coding and JBIG for lossless image compression, Proc. ICIP-94, vol.3 pp , [6] Culik, K. and Valenta, V., Finite automata based compression of bi-level images, Proc. Data Compression, pp , [7] Phimoltares, S., Chamnongthai, K., and Lursinsap, C., Hybrid Binary Image Compression, Fifth International Symposium on Signal Processing and its Applications, ISSPA 99, Brisbane, Australia, [8] Tompkins, D., and Kossentini, F., A Fast Segmentation Algorithm for Bi-Level Image Compression using JBIG2, /99, IEEE, [9] Bogdan J. F., Lossless binary image compression using logic functions and spectra, Computers and Electrical Engineering 30, pp.17 43, [10] CCITT Standard Fax Images at [11] Turkoglu, I. and Arslan, A., An Edge Tracing Method Developed For Object Recognition, The 7-th International Conference in Central Europe on Computer Graphics, pp. 9-12, Plzen, Slovakia (1999) [12] Talu, M.F., Tatar, Y., A new edge tracing method developed for object recognition, TAINN 2003, Çanakkale, Haziran [13] Akimov, A., Kolesnikov, A. and Franti, P., "Lossless compression of map contours by context tree modeling of chain codes", Pattern Recognition, 40 (3), , March M. Fatih TALU received the B.Sc. degrees in Computer Engineering and M.Sc. and Ph.D. degrees in Electrical- Electronics Engineering of the Firat University, Elazig, Turkey, in 2003, 2005, and He is currently an Assistant Professor in Computer Engineering Department of Inonu University. His research interests include object tracking, machine learning and feature extraction methods. Ibrahim TURKOGLU was born in Elazig, Turkey, He received the B.S., M.S. and Ph.D.degrees in Electrical- Electronics Engineering from Firat University, Turkey in 1994, 1996 and 2002 respectively. He is working as an assistant professor in Electronics and Computer Science at Firat University. His research interests include artificial intelligent, pattern recognition, intelligent modeling, radar systems and biomedical signal processing.
Image Compression through DCT and Huffman Coding Technique
 International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347 5161 2015 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Research Article Rahul
International Journal of Current Engineering and Technology E-ISSN 2277 4106, P-ISSN 2347 5161 2015 INPRESSCO, All Rights Reserved Available at http://inpressco.com/category/ijcet Research Article Rahul
Lossless Grey-scale Image Compression using Source Symbols Reduction and Huffman Coding
 Lossless Grey-scale Image Compression using Source Symbols Reduction and Huffman Coding C. SARAVANAN [email protected] Assistant Professor, Computer Centre, National Institute of Technology, Durgapur,WestBengal,
Lossless Grey-scale Image Compression using Source Symbols Reduction and Huffman Coding C. SARAVANAN [email protected] Assistant Professor, Computer Centre, National Institute of Technology, Durgapur,WestBengal,
Comparison of different image compression formats. ECE 533 Project Report Paula Aguilera
 Comparison of different image compression formats ECE 533 Project Report Paula Aguilera Introduction: Images are very important documents nowadays; to work with them in some applications they need to be
Comparison of different image compression formats ECE 533 Project Report Paula Aguilera Introduction: Images are very important documents nowadays; to work with them in some applications they need to be
Image Compression and Decompression using Adaptive Interpolation
 Image Compression and Decompression using Adaptive Interpolation SUNILBHOOSHAN 1,SHIPRASHARMA 2 Jaypee University of Information Technology 1 Electronicsand Communication EngineeringDepartment 2 ComputerScience
Image Compression and Decompression using Adaptive Interpolation SUNILBHOOSHAN 1,SHIPRASHARMA 2 Jaypee University of Information Technology 1 Electronicsand Communication EngineeringDepartment 2 ComputerScience
How To Filter Spam Image From A Picture By Color Or Color
 Image Content-Based Email Spam Image Filtering Jianyi Wang and Kazuki Katagishi Abstract With the population of Internet around the world, email has become one of the main methods of communication among
Image Content-Based Email Spam Image Filtering Jianyi Wang and Kazuki Katagishi Abstract With the population of Internet around the world, email has become one of the main methods of communication among
A NEW LOSSLESS METHOD OF IMAGE COMPRESSION AND DECOMPRESSION USING HUFFMAN CODING TECHNIQUES
 A NEW LOSSLESS METHOD OF IMAGE COMPRESSION AND DECOMPRESSION USING HUFFMAN CODING TECHNIQUES 1 JAGADISH H. PUJAR, 2 LOHIT M. KADLASKAR 1 Faculty, Department of EEE, B V B College of Engg. & Tech., Hubli,
A NEW LOSSLESS METHOD OF IMAGE COMPRESSION AND DECOMPRESSION USING HUFFMAN CODING TECHNIQUES 1 JAGADISH H. PUJAR, 2 LOHIT M. KADLASKAR 1 Faculty, Department of EEE, B V B College of Engg. & Tech., Hubli,
An Algorithm for Classification of Five Types of Defects on Bare Printed Circuit Board
 IJCSES International Journal of Computer Sciences and Engineering Systems, Vol. 5, No. 3, July 2011 CSES International 2011 ISSN 0973-4406 An Algorithm for Classification of Five Types of Defects on Bare
IJCSES International Journal of Computer Sciences and Engineering Systems, Vol. 5, No. 3, July 2011 CSES International 2011 ISSN 0973-4406 An Algorithm for Classification of Five Types of Defects on Bare
FCE: A Fast Content Expression for Server-based Computing
 FCE: A Fast Content Expression for Server-based Computing Qiao Li Mentor Graphics Corporation 11 Ridder Park Drive San Jose, CA 95131, U.S.A. Email: qiao [email protected] Fei Li Department of Computer Science
FCE: A Fast Content Expression for Server-based Computing Qiao Li Mentor Graphics Corporation 11 Ridder Park Drive San Jose, CA 95131, U.S.A. Email: qiao [email protected] Fei Li Department of Computer Science
The Role of Size Normalization on the Recognition Rate of Handwritten Numerals
 The Role of Size Normalization on the Recognition Rate of Handwritten Numerals Chun Lei He, Ping Zhang, Jianxiong Dong, Ching Y. Suen, Tien D. Bui Centre for Pattern Recognition and Machine Intelligence,
The Role of Size Normalization on the Recognition Rate of Handwritten Numerals Chun Lei He, Ping Zhang, Jianxiong Dong, Ching Y. Suen, Tien D. Bui Centre for Pattern Recognition and Machine Intelligence,
RESEARCH PAPERS FACULTY OF MATERIALS SCIENCE AND TECHNOLOGY IN TRNAVA SLOVAK UNIVERSITY OF TECHNOLOGY IN BRATISLAVA
 RESEARCH PAPERS FACULTY OF MATERIALS SCIENCE AND TECHNOLOGY IN TRNAVA SLOVAK UNIVERSITY OF TECHNOLOGY IN BRATISLAVA 2010 Number 29 3D MODEL GENERATION FROM THE ENGINEERING DRAWING Jozef VASKÝ, Michal ELIÁŠ,
RESEARCH PAPERS FACULTY OF MATERIALS SCIENCE AND TECHNOLOGY IN TRNAVA SLOVAK UNIVERSITY OF TECHNOLOGY IN BRATISLAVA 2010 Number 29 3D MODEL GENERATION FROM THE ENGINEERING DRAWING Jozef VASKÝ, Michal ELIÁŠ,
HP Smart Document Scan Software compression schemes and file sizes
 Technical white paper HP Smart Document Scan Software compression schemes and file s Table of contents Introduction 2 schemes supported in HP Smart Document Scan Software 2 Scheme Types 2 2 PNG 3 LZW 3
Technical white paper HP Smart Document Scan Software compression schemes and file s Table of contents Introduction 2 schemes supported in HP Smart Document Scan Software 2 Scheme Types 2 2 PNG 3 LZW 3
ENG4BF3 Medical Image Processing. Image Visualization
 ENG4BF3 Medical Image Processing Image Visualization Visualization Methods Visualization of medical images is for the determination of the quantitative information about the properties of anatomic tissues
ENG4BF3 Medical Image Processing Image Visualization Visualization Methods Visualization of medical images is for the determination of the quantitative information about the properties of anatomic tissues
Online Farsi Handwritten Character Recognition Using Hidden Markov Model
 Online Farsi Handwritten Character Recognition Using Hidden Markov Model Vahid Ghods*, Mohammad Karim Sohrabi Department of Electrical and Computer Engineering, Semnan Branch, Islamic Azad University,
Online Farsi Handwritten Character Recognition Using Hidden Markov Model Vahid Ghods*, Mohammad Karim Sohrabi Department of Electrical and Computer Engineering, Semnan Branch, Islamic Azad University,
ANALYSIS OF THE EFFECTIVENESS IN IMAGE COMPRESSION FOR CLOUD STORAGE FOR VARIOUS IMAGE FORMATS
 ANALYSIS OF THE EFFECTIVENESS IN IMAGE COMPRESSION FOR CLOUD STORAGE FOR VARIOUS IMAGE FORMATS Dasaradha Ramaiah K. 1 and T. Venugopal 2 1 IT Department, BVRIT, Hyderabad, India 2 CSE Department, JNTUH,
ANALYSIS OF THE EFFECTIVENESS IN IMAGE COMPRESSION FOR CLOUD STORAGE FOR VARIOUS IMAGE FORMATS Dasaradha Ramaiah K. 1 and T. Venugopal 2 1 IT Department, BVRIT, Hyderabad, India 2 CSE Department, JNTUH,
Colour Image Encryption and Decryption by using Scan Approach
 Colour Image Encryption and Decryption by using Scan Approach, Rinkee Gupta,Master of Engineering Scholar, Email: [email protected] Jaipal Bisht, Asst. Professor Radharaman Institute Of Technology
Colour Image Encryption and Decryption by using Scan Approach, Rinkee Gupta,Master of Engineering Scholar, Email: [email protected] Jaipal Bisht, Asst. Professor Radharaman Institute Of Technology
MANAGING QUEUE STABILITY USING ART2 IN ACTIVE QUEUE MANAGEMENT FOR CONGESTION CONTROL
 MANAGING QUEUE STABILITY USING ART2 IN ACTIVE QUEUE MANAGEMENT FOR CONGESTION CONTROL G. Maria Priscilla 1 and C. P. Sumathi 2 1 S.N.R. Sons College (Autonomous), Coimbatore, India 2 SDNB Vaishnav College
MANAGING QUEUE STABILITY USING ART2 IN ACTIVE QUEUE MANAGEMENT FOR CONGESTION CONTROL G. Maria Priscilla 1 and C. P. Sumathi 2 1 S.N.R. Sons College (Autonomous), Coimbatore, India 2 SDNB Vaishnav College
JPEG compression of monochrome 2D-barcode images using DCT coefficient distributions
 Edith Cowan University Research Online ECU Publications Pre. JPEG compression of monochrome D-barcode images using DCT coefficient distributions Keng Teong Tan Hong Kong Baptist University Douglas Chai
Edith Cowan University Research Online ECU Publications Pre. JPEG compression of monochrome D-barcode images using DCT coefficient distributions Keng Teong Tan Hong Kong Baptist University Douglas Chai
Study and Implementation of Video Compression standards (H.264/AVC, Dirac)
 Study and Implementation of Video Compression standards (H.264/AVC, Dirac) EE 5359-Multimedia Processing- Spring 2012 Dr. K.R Rao By: Sumedha Phatak(1000731131) Objective A study, implementation and comparison
Study and Implementation of Video Compression standards (H.264/AVC, Dirac) EE 5359-Multimedia Processing- Spring 2012 Dr. K.R Rao By: Sumedha Phatak(1000731131) Objective A study, implementation and comparison
Low-resolution Character Recognition by Video-based Super-resolution
 2009 10th International Conference on Document Analysis and Recognition Low-resolution Character Recognition by Video-based Super-resolution Ataru Ohkura 1, Daisuke Deguchi 1, Tomokazu Takahashi 2, Ichiro
2009 10th International Conference on Document Analysis and Recognition Low-resolution Character Recognition by Video-based Super-resolution Ataru Ohkura 1, Daisuke Deguchi 1, Tomokazu Takahashi 2, Ichiro
The enhancement of the operating speed of the algorithm of adaptive compression of binary bitmap images
 The enhancement of the operating speed of the algorithm of adaptive compression of binary bitmap images Borusyak A.V. Research Institute of Applied Mathematics and Cybernetics Lobachevsky Nizhni Novgorod
The enhancement of the operating speed of the algorithm of adaptive compression of binary bitmap images Borusyak A.V. Research Institute of Applied Mathematics and Cybernetics Lobachevsky Nizhni Novgorod
Enhanced Boosted Trees Technique for Customer Churn Prediction Model
 IOSR Journal of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vol. 04, Issue 03 (March. 2014), V5 PP 41-45 www.iosrjen.org Enhanced Boosted Trees Technique for Customer Churn Prediction
IOSR Journal of Engineering (IOSRJEN) ISSN (e): 2250-3021, ISSN (p): 2278-8719 Vol. 04, Issue 03 (March. 2014), V5 PP 41-45 www.iosrjen.org Enhanced Boosted Trees Technique for Customer Churn Prediction
Secured Lossless Medical Image Compression Based On Adaptive Binary Optimization
 IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IV (Mar-Apr. 2014), PP 43-47 Secured Lossless Medical Image Compression Based On Adaptive Binary
IOSR Journal of Computer Engineering (IOSR-JCE) e-issn: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IV (Mar-Apr. 2014), PP 43-47 Secured Lossless Medical Image Compression Based On Adaptive Binary
An Implementation of a High Capacity 2D Barcode
 An Implementation of a High Capacity 2D Barcode Puchong Subpratatsavee 1 and Pramote Kuacharoen 2 Department of Computer Science, Graduate School of Applied Statistics National Institute of Development
An Implementation of a High Capacity 2D Barcode Puchong Subpratatsavee 1 and Pramote Kuacharoen 2 Department of Computer Science, Graduate School of Applied Statistics National Institute of Development
Wan Accelerators: Optimizing Network Traffic with Compression. Bartosz Agas, Marvin Germar & Christopher Tran
 Wan Accelerators: Optimizing Network Traffic with Compression Bartosz Agas, Marvin Germar & Christopher Tran Introduction A WAN accelerator is an appliance that can maximize the services of a point-to-point(ptp)
Wan Accelerators: Optimizing Network Traffic with Compression Bartosz Agas, Marvin Germar & Christopher Tran Introduction A WAN accelerator is an appliance that can maximize the services of a point-to-point(ptp)
A comprehensive survey on various ETC techniques for secure Data transmission
 A comprehensive survey on various ETC techniques for secure Data transmission Shaikh Nasreen 1, Prof. Suchita Wankhade 2 1, 2 Department of Computer Engineering 1, 2 Trinity College of Engineering and
A comprehensive survey on various ETC techniques for secure Data transmission Shaikh Nasreen 1, Prof. Suchita Wankhade 2 1, 2 Department of Computer Engineering 1, 2 Trinity College of Engineering and
Novel Automatic PCB Inspection Technique Based on Connectivity
 Novel Automatic PCB Inspection Technique Based on Connectivity MAURO HIROMU TATIBANA ROBERTO DE ALENCAR LOTUFO FEEC/UNICAMP- Faculdade de Engenharia Elétrica e de Computação/ Universidade Estadual de Campinas
Novel Automatic PCB Inspection Technique Based on Connectivity MAURO HIROMU TATIBANA ROBERTO DE ALENCAR LOTUFO FEEC/UNICAMP- Faculdade de Engenharia Elétrica e de Computação/ Universidade Estadual de Campinas
Building an Advanced Invariant Real-Time Human Tracking System
 UDC 004.41 Building an Advanced Invariant Real-Time Human Tracking System Fayez Idris 1, Mazen Abu_Zaher 2, Rashad J. Rasras 3, and Ibrahiem M. M. El Emary 4 1 School of Informatics and Computing, German-Jordanian
UDC 004.41 Building an Advanced Invariant Real-Time Human Tracking System Fayez Idris 1, Mazen Abu_Zaher 2, Rashad J. Rasras 3, and Ibrahiem M. M. El Emary 4 1 School of Informatics and Computing, German-Jordanian
ELECTRONIC DOCUMENT IMAGING
 AIIM: Association for Information and Image Management. Trade association and professional society for the micrographics, optical disk and electronic image management markets. Algorithm: Prescribed set
AIIM: Association for Information and Image Management. Trade association and professional society for the micrographics, optical disk and electronic image management markets. Algorithm: Prescribed set
Analecta Vol. 8, No. 2 ISSN 2064-7964
 EXPERIMENTAL APPLICATIONS OF ARTIFICIAL NEURAL NETWORKS IN ENGINEERING PROCESSING SYSTEM S. Dadvandipour Institute of Information Engineering, University of Miskolc, Egyetemváros, 3515, Miskolc, Hungary,
EXPERIMENTAL APPLICATIONS OF ARTIFICIAL NEURAL NETWORKS IN ENGINEERING PROCESSING SYSTEM S. Dadvandipour Institute of Information Engineering, University of Miskolc, Egyetemváros, 3515, Miskolc, Hungary,
Reading.. IMAGE COMPRESSION- I IMAGE COMPRESSION. Image compression. Data Redundancy. Lossy vs Lossless Compression. Chapter 8.
 Reading.. IMAGE COMPRESSION- I Week VIII Feb 25 Chapter 8 Sections 8.1, 8.2 8.3 (selected topics) 8.4 (Huffman, run-length, loss-less predictive) 8.5 (lossy predictive, transform coding basics) 8.6 Image
Reading.. IMAGE COMPRESSION- I Week VIII Feb 25 Chapter 8 Sections 8.1, 8.2 8.3 (selected topics) 8.4 (Huffman, run-length, loss-less predictive) 8.5 (lossy predictive, transform coding basics) 8.6 Image
Digitisation Disposal Policy Toolkit
 Digitisation Disposal Policy Toolkit Glossary of Digitisation Terms August 2014 Department of Science, Information Technology, Innovation and the Arts Document details Security Classification Date of review
Digitisation Disposal Policy Toolkit Glossary of Digitisation Terms August 2014 Department of Science, Information Technology, Innovation and the Arts Document details Security Classification Date of review
Face detection is a process of localizing and extracting the face region from the
 Chapter 4 FACE NORMALIZATION 4.1 INTRODUCTION Face detection is a process of localizing and extracting the face region from the background. The detected face varies in rotation, brightness, size, etc.
Chapter 4 FACE NORMALIZATION 4.1 INTRODUCTION Face detection is a process of localizing and extracting the face region from the background. The detected face varies in rotation, brightness, size, etc.
Euler Vector: A Combinatorial Signature for Gray-Tone Images
 Euler Vector: A Combinatorial Signature for Gray-Tone Images Arijit Bishnu, Bhargab B. Bhattacharya y, Malay K. Kundu, C. A. Murthy fbishnu t, bhargab, malay, [email protected] Indian Statistical Institute,
Euler Vector: A Combinatorial Signature for Gray-Tone Images Arijit Bishnu, Bhargab B. Bhattacharya y, Malay K. Kundu, C. A. Murthy fbishnu t, bhargab, malay, [email protected] Indian Statistical Institute,
Study and Implementation of Video Compression Standards (H.264/AVC and Dirac)
 Project Proposal Study and Implementation of Video Compression Standards (H.264/AVC and Dirac) Sumedha Phatak-1000731131- [email protected] Objective: A study, implementation and comparison of
Project Proposal Study and Implementation of Video Compression Standards (H.264/AVC and Dirac) Sumedha Phatak-1000731131- [email protected] Objective: A study, implementation and comparison of
Research on Chinese financial invoice recognition technology
 Pattern Recognition Letters 24 (2003) 489 497 www.elsevier.com/locate/patrec Research on Chinese financial invoice recognition technology Delie Ming a,b, *, Jian Liu b, Jinwen Tian b a State Key Laboratory
Pattern Recognition Letters 24 (2003) 489 497 www.elsevier.com/locate/patrec Research on Chinese financial invoice recognition technology Delie Ming a,b, *, Jian Liu b, Jinwen Tian b a State Key Laboratory
Automatic Calibration of an In-vehicle Gaze Tracking System Using Driver s Typical Gaze Behavior
 Automatic Calibration of an In-vehicle Gaze Tracking System Using Driver s Typical Gaze Behavior Kenji Yamashiro, Daisuke Deguchi, Tomokazu Takahashi,2, Ichiro Ide, Hiroshi Murase, Kazunori Higuchi 3,
Automatic Calibration of an In-vehicle Gaze Tracking System Using Driver s Typical Gaze Behavior Kenji Yamashiro, Daisuke Deguchi, Tomokazu Takahashi,2, Ichiro Ide, Hiroshi Murase, Kazunori Higuchi 3,
Document Image Retrieval using Signatures as Queries
 Document Image Retrieval using Signatures as Queries Sargur N. Srihari, Shravya Shetty, Siyuan Chen, Harish Srinivasan, Chen Huang CEDAR, University at Buffalo(SUNY) Amherst, New York 14228 Gady Agam and
Document Image Retrieval using Signatures as Queries Sargur N. Srihari, Shravya Shetty, Siyuan Chen, Harish Srinivasan, Chen Huang CEDAR, University at Buffalo(SUNY) Amherst, New York 14228 Gady Agam and
A Direct Numerical Method for Observability Analysis
 IEEE TRANSACTIONS ON POWER SYSTEMS, VOL 15, NO 2, MAY 2000 625 A Direct Numerical Method for Observability Analysis Bei Gou and Ali Abur, Senior Member, IEEE Abstract This paper presents an algebraic method
IEEE TRANSACTIONS ON POWER SYSTEMS, VOL 15, NO 2, MAY 2000 625 A Direct Numerical Method for Observability Analysis Bei Gou and Ali Abur, Senior Member, IEEE Abstract This paper presents an algebraic method
Video compression: Performance of available codec software
 Video compression: Performance of available codec software Introduction. Digital Video A digital video is a collection of images presented sequentially to produce the effect of continuous motion. It takes
Video compression: Performance of available codec software Introduction. Digital Video A digital video is a collection of images presented sequentially to produce the effect of continuous motion. It takes
Structures for Data Compression Responsible persons: Claudia Dolci, Dante Salvini, Michael Schrattner, Robert Weibel
 Geographic Information Technology Training Alliance (GITTA) presents: Responsible persons: Claudia Dolci, Dante Salvini, Michael Schrattner, Robert Weibel Content 1.... 2 1.1. General Compression Concepts...3
Geographic Information Technology Training Alliance (GITTA) presents: Responsible persons: Claudia Dolci, Dante Salvini, Michael Schrattner, Robert Weibel Content 1.... 2 1.1. General Compression Concepts...3
Galaxy Morphological Classification
 Galaxy Morphological Classification Jordan Duprey and James Kolano Abstract To solve the issue of galaxy morphological classification according to a classification scheme modelled off of the Hubble Sequence,
Galaxy Morphological Classification Jordan Duprey and James Kolano Abstract To solve the issue of galaxy morphological classification according to a classification scheme modelled off of the Hubble Sequence,
CHAPTER 2 LITERATURE REVIEW
 11 CHAPTER 2 LITERATURE REVIEW 2.1 INTRODUCTION Image compression is mainly used to reduce storage space, transmission time and bandwidth requirements. In the subsequent sections of this chapter, general
11 CHAPTER 2 LITERATURE REVIEW 2.1 INTRODUCTION Image compression is mainly used to reduce storage space, transmission time and bandwidth requirements. In the subsequent sections of this chapter, general
Bachelor of Games and Virtual Worlds (Programming) Subject and Course Summaries
 First Semester Development 1A On completion of this subject students will be able to apply basic programming and problem solving skills in a 3 rd generation object-oriented programming language (such as
First Semester Development 1A On completion of this subject students will be able to apply basic programming and problem solving skills in a 3 rd generation object-oriented programming language (such as
Locating and Decoding EAN-13 Barcodes from Images Captured by Digital Cameras
 Locating and Decoding EAN-13 Barcodes from Images Captured by Digital Cameras W3A.5 Douglas Chai and Florian Hock Visual Information Processing Research Group School of Engineering and Mathematics Edith
Locating and Decoding EAN-13 Barcodes from Images Captured by Digital Cameras W3A.5 Douglas Chai and Florian Hock Visual Information Processing Research Group School of Engineering and Mathematics Edith
How to Send Video Images Through Internet
 Transmitting Video Images in XML Web Service Francisco Prieto, Antonio J. Sierra, María Carrión García Departamento de Ingeniería de Sistemas y Automática Área de Ingeniería Telemática Escuela Superior
Transmitting Video Images in XML Web Service Francisco Prieto, Antonio J. Sierra, María Carrión García Departamento de Ingeniería de Sistemas y Automática Área de Ingeniería Telemática Escuela Superior
DCT-JPEG Image Coding Based on GPU
 , pp. 293-302 http://dx.doi.org/10.14257/ijhit.2015.8.5.32 DCT-JPEG Image Coding Based on GPU Rongyang Shan 1, Chengyou Wang 1*, Wei Huang 2 and Xiao Zhou 1 1 School of Mechanical, Electrical and Information
, pp. 293-302 http://dx.doi.org/10.14257/ijhit.2015.8.5.32 DCT-JPEG Image Coding Based on GPU Rongyang Shan 1, Chengyou Wang 1*, Wei Huang 2 and Xiao Zhou 1 1 School of Mechanical, Electrical and Information
Keywords image processing, signature verification, false acceptance rate, false rejection rate, forgeries, feature vectors, support vector machines.
 International Journal of Computer Application and Engineering Technology Volume 3-Issue2, Apr 2014.Pp. 188-192 www.ijcaet.net OFFLINE SIGNATURE VERIFICATION SYSTEM -A REVIEW Pooja Department of Computer
International Journal of Computer Application and Engineering Technology Volume 3-Issue2, Apr 2014.Pp. 188-192 www.ijcaet.net OFFLINE SIGNATURE VERIFICATION SYSTEM -A REVIEW Pooja Department of Computer
Colour by Numbers Image Representation
 Activity 2 Colour by Numbers Image Representation Summary Computers store drawings, photographs and other pictures using only numbers. The following activity demonstrates how they can do this. Curriculum
Activity 2 Colour by Numbers Image Representation Summary Computers store drawings, photographs and other pictures using only numbers. The following activity demonstrates how they can do this. Curriculum
Lossless Medical Image Compression using Redundancy Analysis
 5 Lossless Medical Image Compression using Redundancy Analysis Se-Kee Kil, Jong-Shill Lee, Dong-Fan Shen, Je-Goon Ryu, Eung-Hyuk Lee, Hong-Ki Min, Seung-Hong Hong Dept. of Electronic Eng., Inha University,
5 Lossless Medical Image Compression using Redundancy Analysis Se-Kee Kil, Jong-Shill Lee, Dong-Fan Shen, Je-Goon Ryu, Eung-Hyuk Lee, Hong-Ki Min, Seung-Hong Hong Dept. of Electronic Eng., Inha University,
PageX: An Integrated Document Processing and Management Software for Digital Libraries
 PageX: An Integrated Document Processing and Management Software for Digital Libraries Hanchuan Peng, Zheru Chi, Wanchi Siu, and David Dagan Feng Department of Electronic & Information Engineering The
PageX: An Integrated Document Processing and Management Software for Digital Libraries Hanchuan Peng, Zheru Chi, Wanchi Siu, and David Dagan Feng Department of Electronic & Information Engineering The
An Overview of Knowledge Discovery Database and Data mining Techniques
 An Overview of Knowledge Discovery Database and Data mining Techniques Priyadharsini.C 1, Dr. Antony Selvadoss Thanamani 2 M.Phil, Department of Computer Science, NGM College, Pollachi, Coimbatore, Tamilnadu,
An Overview of Knowledge Discovery Database and Data mining Techniques Priyadharsini.C 1, Dr. Antony Selvadoss Thanamani 2 M.Phil, Department of Computer Science, NGM College, Pollachi, Coimbatore, Tamilnadu,
SCAN-CA Based Image Security System
 SCAN-CA Based Image Security System Bhagyashree.S.Anantwar 1, S.P.Sonavane 2 Student, Department of Computer Science and Engg, Walchand College of Engg, Sanli, India 1 Asso. Professor, Department of Information
SCAN-CA Based Image Security System Bhagyashree.S.Anantwar 1, S.P.Sonavane 2 Student, Department of Computer Science and Engg, Walchand College of Engg, Sanli, India 1 Asso. Professor, Department of Information
ANALYSIS OF THE COMPRESSION RATIO AND QUALITY IN MEDICAL IMAGES
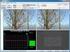 ISSN 392 24X INFORMATION TECHNOLOGY AND CONTROL, 2006, Vol.35, No.4 ANALYSIS OF THE COMPRESSION RATIO AND QUALITY IN MEDICAL IMAGES Darius Mateika, Romanas Martavičius Department of Electronic Systems,
ISSN 392 24X INFORMATION TECHNOLOGY AND CONTROL, 2006, Vol.35, No.4 ANALYSIS OF THE COMPRESSION RATIO AND QUALITY IN MEDICAL IMAGES Darius Mateika, Romanas Martavičius Department of Electronic Systems,
A New Digital Encryption Scheme: Binary Matrix Rotations Encryption Algorithm
 International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 2, February 2015, PP 18-27 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org A
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 2, February 2015, PP 18-27 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org A
Compression algorithm for Bayesian network modeling of binary systems
 Compression algorithm for Bayesian network modeling of binary systems I. Tien & A. Der Kiureghian University of California, Berkeley ABSTRACT: A Bayesian network (BN) is a useful tool for analyzing the
Compression algorithm for Bayesian network modeling of binary systems I. Tien & A. Der Kiureghian University of California, Berkeley ABSTRACT: A Bayesian network (BN) is a useful tool for analyzing the
A New Digital Communications Course Enhanced by PC-Based Design Projects*
 Int. J. Engng Ed. Vol. 16, No. 6, pp. 553±559, 2000 0949-149X/91 $3.00+0.00 Printed in Great Britain. # 2000 TEMPUS Publications. A New Digital Communications Course Enhanced by PC-Based Design Projects*
Int. J. Engng Ed. Vol. 16, No. 6, pp. 553±559, 2000 0949-149X/91 $3.00+0.00 Printed in Great Britain. # 2000 TEMPUS Publications. A New Digital Communications Course Enhanced by PC-Based Design Projects*
Markovian Process and Novel Secure Algorithm for Big Data in Two-Hop Wireless Networks
 Markovian Process and Novel Secure Algorithm for Big Data in Two-Hop Wireless Networks K. Thiagarajan, Department of Mathematics, PSNA College of Engineering and Technology, Dindigul, India. A. Veeraiah,
Markovian Process and Novel Secure Algorithm for Big Data in Two-Hop Wireless Networks K. Thiagarajan, Department of Mathematics, PSNA College of Engineering and Technology, Dindigul, India. A. Veeraiah,
Morphological segmentation of histology cell images
 Morphological segmentation of histology cell images A.Nedzved, S.Ablameyko, I.Pitas Institute of Engineering Cybernetics of the National Academy of Sciences Surganova, 6, 00 Minsk, Belarus E-mail [email protected]
Morphological segmentation of histology cell images A.Nedzved, S.Ablameyko, I.Pitas Institute of Engineering Cybernetics of the National Academy of Sciences Surganova, 6, 00 Minsk, Belarus E-mail [email protected]
COMPARISON OF OBJECT BASED AND PIXEL BASED CLASSIFICATION OF HIGH RESOLUTION SATELLITE IMAGES USING ARTIFICIAL NEURAL NETWORKS
 COMPARISON OF OBJECT BASED AND PIXEL BASED CLASSIFICATION OF HIGH RESOLUTION SATELLITE IMAGES USING ARTIFICIAL NEURAL NETWORKS B.K. Mohan and S. N. Ladha Centre for Studies in Resources Engineering IIT
COMPARISON OF OBJECT BASED AND PIXEL BASED CLASSIFICATION OF HIGH RESOLUTION SATELLITE IMAGES USING ARTIFICIAL NEURAL NETWORKS B.K. Mohan and S. N. Ladha Centre for Studies in Resources Engineering IIT
A Parallel Processor for Distributed Genetic Algorithm with Redundant Binary Number
 A Parallel Processor for Distributed Genetic Algorithm with Redundant Binary Number 1 Tomohiro KAMIMURA, 2 Akinori KANASUGI 1 Department of Electronics, Tokyo Denki University, [email protected]
A Parallel Processor for Distributed Genetic Algorithm with Redundant Binary Number 1 Tomohiro KAMIMURA, 2 Akinori KANASUGI 1 Department of Electronics, Tokyo Denki University, [email protected]
Multimodal Biometric Recognition Security System
 Multimodal Biometric Recognition Security System Anju.M.I, G.Sheeba, G.Sivakami, Monica.J, Savithri.M Department of ECE, New Prince Shri Bhavani College of Engg. & Tech., Chennai, India ABSTRACT: Security
Multimodal Biometric Recognition Security System Anju.M.I, G.Sheeba, G.Sivakami, Monica.J, Savithri.M Department of ECE, New Prince Shri Bhavani College of Engg. & Tech., Chennai, India ABSTRACT: Security
Performance Analysis of medical Image Using Fractal Image Compression
 Performance Analysis of medical Image Using Fractal Image Compression Akhil Singal 1, Rajni 2 1 M.Tech Scholar, ECE, D.C.R.U.S.T, Murthal, Sonepat, Haryana, India 2 Assistant Professor, ECE, D.C.R.U.S.T,
Performance Analysis of medical Image Using Fractal Image Compression Akhil Singal 1, Rajni 2 1 M.Tech Scholar, ECE, D.C.R.U.S.T, Murthal, Sonepat, Haryana, India 2 Assistant Professor, ECE, D.C.R.U.S.T,
MMGD0203 Multimedia Design MMGD0203 MULTIMEDIA DESIGN. Chapter 3 Graphics and Animations
 MMGD0203 MULTIMEDIA DESIGN Chapter 3 Graphics and Animations 1 Topics: Definition of Graphics Why use Graphics? Graphics Categories Graphics Qualities File Formats Types of Graphics Graphic File Size Introduction
MMGD0203 MULTIMEDIA DESIGN Chapter 3 Graphics and Animations 1 Topics: Definition of Graphics Why use Graphics? Graphics Categories Graphics Qualities File Formats Types of Graphics Graphic File Size Introduction
Introduction to image coding
 Introduction to image coding Image coding aims at reducing amount of data required for image representation, storage or transmission. This is achieved by removing redundant data from an image, i.e. by
Introduction to image coding Image coding aims at reducing amount of data required for image representation, storage or transmission. This is achieved by removing redundant data from an image, i.e. by
 Tracking Moving Objects In Video Sequences Yiwei Wang, Robert E. Van Dyck, and John F. Doherty Department of Electrical Engineering The Pennsylvania State University University Park, PA16802 Abstract{Object
Tracking Moving Objects In Video Sequences Yiwei Wang, Robert E. Van Dyck, and John F. Doherty Department of Electrical Engineering The Pennsylvania State University University Park, PA16802 Abstract{Object
An Algorithm for Automatic Base Station Placement in Cellular Network Deployment
 An Algorithm for Automatic Base Station Placement in Cellular Network Deployment István Törős and Péter Fazekas High Speed Networks Laboratory Dept. of Telecommunications, Budapest University of Technology
An Algorithm for Automatic Base Station Placement in Cellular Network Deployment István Törős and Péter Fazekas High Speed Networks Laboratory Dept. of Telecommunications, Budapest University of Technology
Data Mining Un-Compressed Images from cloud with Clustering Compression technique using Lempel-Ziv-Welch
 Data Mining Un-Compressed Images from cloud with Clustering Compression technique using Lempel-Ziv-Welch 1 C. Parthasarathy 2 K.Srinivasan and 3 R.Saravanan Assistant Professor, 1,2,3 Dept. of I.T, SCSVMV
Data Mining Un-Compressed Images from cloud with Clustering Compression technique using Lempel-Ziv-Welch 1 C. Parthasarathy 2 K.Srinivasan and 3 R.Saravanan Assistant Professor, 1,2,3 Dept. of I.T, SCSVMV
encoding compression encryption
 encoding compression encryption ASCII utf-8 utf-16 zip mpeg jpeg AES RSA diffie-hellman Expressing characters... ASCII and Unicode, conventions of how characters are expressed in bits. ASCII (7 bits) -
encoding compression encryption ASCII utf-8 utf-16 zip mpeg jpeg AES RSA diffie-hellman Expressing characters... ASCII and Unicode, conventions of how characters are expressed in bits. ASCII (7 bits) -
A Study on M2M-based AR Multiple Objects Loading Technology using PPHT
 A Study on M2M-based AR Multiple Objects Loading Technology using PPHT Sungmo Jung, Seoksoo Kim * Department of Multimedia Hannam University 133, Ojeong-dong, Daedeok-gu, Daejeon-city Korea [email protected],
A Study on M2M-based AR Multiple Objects Loading Technology using PPHT Sungmo Jung, Seoksoo Kim * Department of Multimedia Hannam University 133, Ojeong-dong, Daedeok-gu, Daejeon-city Korea [email protected],
A Performance Study of Load Balancing Strategies for Approximate String Matching on an MPI Heterogeneous System Environment
 A Performance Study of Load Balancing Strategies for Approximate String Matching on an MPI Heterogeneous System Environment Panagiotis D. Michailidis and Konstantinos G. Margaritis Parallel and Distributed
A Performance Study of Load Balancing Strategies for Approximate String Matching on an MPI Heterogeneous System Environment Panagiotis D. Michailidis and Konstantinos G. Margaritis Parallel and Distributed
Cardless Cash Access Using Biometric ATM Security System Neenu Preetam. I 1, Harsh Gupta 2
 Cardless Cash Access Using Biometric ATM Security System Neenu Preetam. I 1, Harsh Gupta 2 1, 2 M.Tech. (Microelectronics), Department of ECE, SEEC, Manipal University Jaipur (MUJ), Rajasthan, India Abstract:
Cardless Cash Access Using Biometric ATM Security System Neenu Preetam. I 1, Harsh Gupta 2 1, 2 M.Tech. (Microelectronics), Department of ECE, SEEC, Manipal University Jaipur (MUJ), Rajasthan, India Abstract:
Circle Object Recognition Based on Monocular Vision for Home Security Robot
 Journal of Applied Science and Engineering, Vol. 16, No. 3, pp. 261 268 (2013) DOI: 10.6180/jase.2013.16.3.05 Circle Object Recognition Based on Monocular Vision for Home Security Robot Shih-An Li, Ching-Chang
Journal of Applied Science and Engineering, Vol. 16, No. 3, pp. 261 268 (2013) DOI: 10.6180/jase.2013.16.3.05 Circle Object Recognition Based on Monocular Vision for Home Security Robot Shih-An Li, Ching-Chang
A HIGH PERFORMANCE SOFTWARE IMPLEMENTATION OF MPEG AUDIO ENCODER. Figure 1. Basic structure of an encoder.
 A HIGH PERFORMANCE SOFTWARE IMPLEMENTATION OF MPEG AUDIO ENCODER Manoj Kumar 1 Mohammad Zubair 1 1 IBM T.J. Watson Research Center, Yorktown Hgts, NY, USA ABSTRACT The MPEG/Audio is a standard for both
A HIGH PERFORMANCE SOFTWARE IMPLEMENTATION OF MPEG AUDIO ENCODER Manoj Kumar 1 Mohammad Zubair 1 1 IBM T.J. Watson Research Center, Yorktown Hgts, NY, USA ABSTRACT The MPEG/Audio is a standard for both
Friendly Medical Image Sharing Scheme
 Journal of Information Hiding and Multimedia Signal Processing 2014 ISSN 2073-4212 Ubiquitous International Volume 5, Number 3, July 2014 Frily Medical Image Sharing Scheme Hao-Kuan Tso Department of Computer
Journal of Information Hiding and Multimedia Signal Processing 2014 ISSN 2073-4212 Ubiquitous International Volume 5, Number 3, July 2014 Frily Medical Image Sharing Scheme Hao-Kuan Tso Department of Computer
DYNAMIC DOMAIN CLASSIFICATION FOR FRACTAL IMAGE COMPRESSION
 DYNAMIC DOMAIN CLASSIFICATION FOR FRACTAL IMAGE COMPRESSION K. Revathy 1 & M. Jayamohan 2 Department of Computer Science, University of Kerala, Thiruvananthapuram, Kerala, India 1 [email protected]
DYNAMIC DOMAIN CLASSIFICATION FOR FRACTAL IMAGE COMPRESSION K. Revathy 1 & M. Jayamohan 2 Department of Computer Science, University of Kerala, Thiruvananthapuram, Kerala, India 1 [email protected]
Efficient on-line Signature Verification System
 International Journal of Engineering & Technology IJET-IJENS Vol:10 No:04 42 Efficient on-line Signature Verification System Dr. S.A Daramola 1 and Prof. T.S Ibiyemi 2 1 Department of Electrical and Information
International Journal of Engineering & Technology IJET-IJENS Vol:10 No:04 42 Efficient on-line Signature Verification System Dr. S.A Daramola 1 and Prof. T.S Ibiyemi 2 1 Department of Electrical and Information
MassArt Studio Foundation: Visual Language Digital Media Cookbook, Fall 2013
 INPUT OUTPUT 08 / IMAGE QUALITY & VIEWING In this section we will cover common image file formats you are likely to come across and examine image quality in terms of resolution and bit depth. We will cover
INPUT OUTPUT 08 / IMAGE QUALITY & VIEWING In this section we will cover common image file formats you are likely to come across and examine image quality in terms of resolution and bit depth. We will cover
Performance Evaluation of Online Image Compression Tools
 Performance Evaluation of Online Image Compression Tools Rupali Sharma 1, aresh Kumar 1, Department of Computer Science, PTUGZS Campus, Bathinda (Punjab), India 1 [email protected], [email protected]
Performance Evaluation of Online Image Compression Tools Rupali Sharma 1, aresh Kumar 1, Department of Computer Science, PTUGZS Campus, Bathinda (Punjab), India 1 [email protected], [email protected]
A Fast Algorithm for Multilevel Thresholding
 JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 17, 713-727 (2001) A Fast Algorithm for Multilevel Thresholding PING-SUNG LIAO, TSE-SHENG CHEN * AND PAU-CHOO CHUNG + Department of Electrical Engineering
JOURNAL OF INFORMATION SCIENCE AND ENGINEERING 17, 713-727 (2001) A Fast Algorithm for Multilevel Thresholding PING-SUNG LIAO, TSE-SHENG CHEN * AND PAU-CHOO CHUNG + Department of Electrical Engineering
Efficient Iceberg Query Evaluation for Structured Data using Bitmap Indices
 Proc. of Int. Conf. on Advances in Computer Science, AETACS Efficient Iceberg Query Evaluation for Structured Data using Bitmap Indices Ms.Archana G.Narawade a, Mrs.Vaishali Kolhe b a PG student, D.Y.Patil
Proc. of Int. Conf. on Advances in Computer Science, AETACS Efficient Iceberg Query Evaluation for Structured Data using Bitmap Indices Ms.Archana G.Narawade a, Mrs.Vaishali Kolhe b a PG student, D.Y.Patil
Mathematical Modelling of Computer Networks: Part II. Module 1: Network Coding
 Mathematical Modelling of Computer Networks: Part II Module 1: Network Coding Lecture 3: Network coding and TCP 12th November 2013 Laila Daniel and Krishnan Narayanan Dept. of Computer Science, University
Mathematical Modelling of Computer Networks: Part II Module 1: Network Coding Lecture 3: Network coding and TCP 12th November 2013 Laila Daniel and Krishnan Narayanan Dept. of Computer Science, University
Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals. Introduction
 Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals Modified from the lecture slides of Lami Kaya ([email protected]) for use CECS 474, Fall 2008. 2009 Pearson Education Inc., Upper
Computer Networks and Internets, 5e Chapter 6 Information Sources and Signals Modified from the lecture slides of Lami Kaya ([email protected]) for use CECS 474, Fall 2008. 2009 Pearson Education Inc., Upper
Algorithms for the resizing of binary and grayscale images using a logical transform
 Algorithms for the resizing of binary and grayscale images using a logical transform Ethan E. Danahy* a, Sos S. Agaian b, Karen A. Panetta a a Dept. of Electrical and Computer Eng., Tufts University, 161
Algorithms for the resizing of binary and grayscale images using a logical transform Ethan E. Danahy* a, Sos S. Agaian b, Karen A. Panetta a a Dept. of Electrical and Computer Eng., Tufts University, 161
Signature Region of Interest using Auto cropping
 ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 1 Signature Region of Interest using Auto cropping Bassam Al-Mahadeen 1, Mokhled S. AlTarawneh 2 and Islam H. AlTarawneh 2 1 Math. And Computer Department,
ISSN (Online): 1694-0784 ISSN (Print): 1694-0814 1 Signature Region of Interest using Auto cropping Bassam Al-Mahadeen 1, Mokhled S. AlTarawneh 2 and Islam H. AlTarawneh 2 1 Math. And Computer Department,
A Robust Method for Solving Transcendental Equations
 www.ijcsi.org 413 A Robust Method for Solving Transcendental Equations Md. Golam Moazzam, Amita Chakraborty and Md. Al-Amin Bhuiyan Department of Computer Science and Engineering, Jahangirnagar University,
www.ijcsi.org 413 A Robust Method for Solving Transcendental Equations Md. Golam Moazzam, Amita Chakraborty and Md. Al-Amin Bhuiyan Department of Computer Science and Engineering, Jahangirnagar University,
Figure 1: Relation between codec, data containers and compression algorithms.
 Video Compression Djordje Mitrovic University of Edinburgh This document deals with the issues of video compression. The algorithm, which is used by the MPEG standards, will be elucidated upon in order
Video Compression Djordje Mitrovic University of Edinburgh This document deals with the issues of video compression. The algorithm, which is used by the MPEG standards, will be elucidated upon in order
http://www.springer.com/0-387-23402-0
 http://www.springer.com/0-387-23402-0 Chapter 2 VISUAL DATA FORMATS 1. Image and Video Data Digital visual data is usually organised in rectangular arrays denoted as frames, the elements of these arrays
http://www.springer.com/0-387-23402-0 Chapter 2 VISUAL DATA FORMATS 1. Image and Video Data Digital visual data is usually organised in rectangular arrays denoted as frames, the elements of these arrays
3. Interpolation. Closing the Gaps of Discretization... Beyond Polynomials
 3. Interpolation Closing the Gaps of Discretization... Beyond Polynomials Closing the Gaps of Discretization... Beyond Polynomials, December 19, 2012 1 3.3. Polynomial Splines Idea of Polynomial Splines
3. Interpolation Closing the Gaps of Discretization... Beyond Polynomials Closing the Gaps of Discretization... Beyond Polynomials, December 19, 2012 1 3.3. Polynomial Splines Idea of Polynomial Splines
INFOCOMMUNICATIONS JOURNAL Mojette Transform Software Hardware Implementations and its Applications
 FEBRUARY 011 VOLUME III NUMBER 1 39 INFOCOMMUNICATIONS JOURNAL 40 FEBRUARY 011 VOLUME III NUMBER 1 FEBRUARY 011 VOLUME III NUMBER 1 41 INFOCOMMUNICATIONS JOURNAL b1 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 a1 10
FEBRUARY 011 VOLUME III NUMBER 1 39 INFOCOMMUNICATIONS JOURNAL 40 FEBRUARY 011 VOLUME III NUMBER 1 FEBRUARY 011 VOLUME III NUMBER 1 41 INFOCOMMUNICATIONS JOURNAL b1 1 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 a1 10
Sachin Dhawan Deptt. of ECE, UIET, Kurukshetra University, Kurukshetra, Haryana, India
 Abstract Image compression is now essential for applications such as transmission and storage in data bases. In this paper we review and discuss about the image compression, need of compression, its principles,
Abstract Image compression is now essential for applications such as transmission and storage in data bases. In this paper we review and discuss about the image compression, need of compression, its principles,
How To Fix Out Of Focus And Blur Images With A Dynamic Template Matching Algorithm
 IJSTE - International Journal of Science Technology & Engineering Volume 1 Issue 10 April 2015 ISSN (online): 2349-784X Image Estimation Algorithm for Out of Focus and Blur Images to Retrieve the Barcode
IJSTE - International Journal of Science Technology & Engineering Volume 1 Issue 10 April 2015 ISSN (online): 2349-784X Image Estimation Algorithm for Out of Focus and Blur Images to Retrieve the Barcode
Statistical Modeling of Huffman Tables Coding
 Statistical Modeling of Huffman Tables Coding S. Battiato 1, C. Bosco 1, A. Bruna 2, G. Di Blasi 1, G.Gallo 1 1 D.M.I. University of Catania - Viale A. Doria 6, 95125, Catania, Italy {battiato, bosco,
Statistical Modeling of Huffman Tables Coding S. Battiato 1, C. Bosco 1, A. Bruna 2, G. Di Blasi 1, G.Gallo 1 1 D.M.I. University of Catania - Viale A. Doria 6, 95125, Catania, Italy {battiato, bosco,
Multimedia Data Transmission over Wired/Wireless Networks
 Multimedia Data Transmission over Wired/Wireless Networks Bharat Bhargava Gang Ding, Xiaoxin Wu, Mohamed Hefeeda, Halima Ghafoor Purdue University Website: http://www.cs.purdue.edu/homes/bb E-mail: [email protected]
Multimedia Data Transmission over Wired/Wireless Networks Bharat Bhargava Gang Ding, Xiaoxin Wu, Mohamed Hefeeda, Halima Ghafoor Purdue University Website: http://www.cs.purdue.edu/homes/bb E-mail: [email protected]
Computer Graphics in Medicine
 Computer Graphics in Medicine Loren Block For my presentation, I will discuss several different papers that are related to graphics and imaging in the medical field. The main areas that the papers cover
Computer Graphics in Medicine Loren Block For my presentation, I will discuss several different papers that are related to graphics and imaging in the medical field. The main areas that the papers cover
On the Use of Compression Algorithms for Network Traffic Classification
 On the Use of for Network Traffic Classification Christian CALLEGARI Department of Information Ingeneering University of Pisa 23 September 2008 COST-TMA Meeting Samos, Greece Outline Outline 1 Introduction
On the Use of for Network Traffic Classification Christian CALLEGARI Department of Information Ingeneering University of Pisa 23 September 2008 COST-TMA Meeting Samos, Greece Outline Outline 1 Introduction
Coding and decoding with convolutional codes. The Viterbi Algor
 Coding and decoding with convolutional codes. The Viterbi Algorithm. 8 Block codes: main ideas Principles st point of view: infinite length block code nd point of view: convolutions Some examples Repetition
Coding and decoding with convolutional codes. The Viterbi Algorithm. 8 Block codes: main ideas Principles st point of view: infinite length block code nd point of view: convolutions Some examples Repetition
