Software Security. Memory Virtualization. Jan Nordholz. Prof. Jean-Pierre Seifert Security in Telecommunications TU Berlin.
|
|
|
- Dylan Alfred Austin
- 7 years ago
- Views:
Transcription
1 Software Security Memory Virtualization Jan Nordholz Prof. Jean-Pierre Seifert Security in Telecommunications TU Berlin SoSe 2016 jan (sect) Software Security SoSe / 27
2 Virtualization (Recap) assume basic virtualization support (Intel VT-x, AMD SVM, ARM VE) all sensitive instructions either handled internally (i. e. modify virtual state instead of physical state) or cause a trap into HV But what about memory management? There s still only one MMU! Hint: print this document 2-up... jan (sect) Software Security SoSe / 27
3 MMU: native case recall: hardware register denoting the pagetable base address (x86: CR3) CR3 points to pagetable managed by OS pagetable contains virtual-to-physical mappings with ission bits, notation: V P OS maintains one pagetable for each address space scheduling to a different process means loading another value into CR3 jan (sect) Software Security SoSe / 27
4 jan (sect) Software Security SoSe / 27
5 MMU: native case machine with 256 MB RAM, physical address range [P base, P base + 256M] mapping by OS pagetable: V P P [P base, P base + 256M] (obviously) accessing V ends up at physical address P jan (sect) Software Security SoSe / 27
6 jan (sect) Software Security SoSe / 27
7 MMU: virtualized case machine with 1 GB RAM: physical address range [P base, P base + 1G] three virtual machines, each assigned 256 MB RAM remaining memory reserved for HV itself pseudo-physical ( guest-physical ) range for each guest: [GP base, GP base + 256M] (hypervisor mimicks smaller-size native machine) translation between addresses in GP and P: offset! (different for each guest!) jan (sect) Software Security SoSe / 27
8 jan (sect) Software Security SoSe / 27
9 MMU: virtualized case mapping by guest OS pagetable: V GP [GP base, GP base + 256M] GP accessing V ends up at pseudo-physical address GP That s not what we want! Recall Popek&Goldberg: HV must have full control! guest OS in control of paging guests can touch arbitrary locations guests might possibly overwrite HV violation guests would also stomp on each other s memory (each guest thinks it is running alone on native hardware) jan (sect) Software Security SoSe / 27
10 jan (sect) Software Security SoSe / 27
11 MMU: virtualized case HV must control paging to protect itself and guests from each other effective value in CR3 must point to HV shadow pagetable HV has to: look up intended V GP tuples in guest pagetable apply bounds check on GP, apply guest offset to get P create corresponding V P entries in shadow pagetable jan (sect) Software Security SoSe / 27
12 jan (sect) Software Security SoSe / 27
13 Lazy Mapping, native When are mappings created? Linux (and similar OS) are lazy: load file contents, reserve memory etc. only when actually necessary ex.: when loading /bin/bash, only the page containing the entry point is actually loaded when execution continues to a (yet unmapped) location V trap into OS: Page Fault OS loads desired additional page of executable into free physical page P, creates V RX P OS resumes process same for handling stack growth: if stack exceeds amount of mapped pages, a new physical page is allocated and mapped jan (sect) Software Security SoSe / 27
14 jan (sect) Software Security SoSe / 27
15 Lazy Mapping, virtualized process tries to execute (yet unmapped) location V Page Fault must be handled by HV! HV searches guest pagetable for V Case 1: no entry GP HV cannot know what to do with the fault forward ( inject ) fault into guest OS handles fault (just like the native scenario), but... OS resumes process: faults again! Why? After handling by OS, V RX GP in guest pagetable, but no V RX P in shadow pagetable yet! jan (sect) Software Security SoSe / 27
16 jan (sect) Software Security SoSe / 27
17 Lazy Mapping, virtualized process tries to execute (yet unmapped) location V Page Fault must be handled by HV! HV searches guest pagetable for V Case 2: now there is an entry! GP HV checks that GP [GP base, GP base + 256M] HV calculates P = GP + offset HV inserts V P into shadow pagetable HV resumes guest jan (sect) Software Security SoSe / 27
18 jan (sect) Software Security SoSe / 27
19 MMU: first conclusions HV has to copy and translate guest pagetable entries cost of lazily adding a mapping (native case): 1x Page Fault = 2x transitions between user and system mode cost of lazily adding a mapping (virtualized case): 2x Page Fault = 4x transitions between guest and hypervisor + 1x Injected Page Fault = 2x additional transitions between user and system mode Much more expensive with virtualization! Especially process creation is bad each new process = new pagetable = lots of new entries! jan (sect) Software Security SoSe / 27
20 MMU: unanswered details How does HV know which guest pagetable to consult? Easy: HV has to intercept guest access to CR3 anyway When guest wants to write value to CR3: HV checks for an existing shadow pagetable for this value if exists: use it if not: allocate new spt, tag it with guest CR3 program real CR3 with address of recovered/allocated spt jan (sect) Software Security SoSe / 27
21 MMU: unanswered details Ok, lazy addition of mappings is slow, but can be emulated faithfully i. e. guest does not notice it is running virtualized What does HV do when guest wants to change/delete a mapping? recall: processor contains Translation Lookaside Buffer (TLB) TLB caches V P tuples only positive caching lookup failures are not cacheable changing or deleting mapping requires flush of TLB for change to become effective, even in the native case HV can use that by intercepting TLB flushes and applying to spt as well! You can think of an spt simply as a (large) software TLB. jan (sect) Software Security SoSe / 27
22 Hardware updates to page tables Some architectures support a dirty bit in pagetable: extra bit in pagetable, set to 0 by OS when creating mapping set to 1 by CPU when write to page happens dirty bit checked by OS to determine pages with changed content if memory contents correspond to file loaded from disk, OS can optimize disk write-back by writing only changed ( dirty ) pages HV has to emulate dirty bit behaviour of CPU as well! jan (sect) Software Security SoSe / 27
23 Lazy mapping w/ dirty bit, virtualized changes to established process: when HV translates V guest pagetable GP to V P, HV has to set dirty bit in What if we have to handle a read fault, but the mapping we find is V RW GP? a) we translate to V RW P, but then we have to immediately set dirty bit b) we translate to V R P and don t set dirty in b), we will get a write fault later if the page is really written to in a), we won t, so we have to assume a write might happen jan (sect) Software Security SoSe / 27
24 Dirty bit vs. Flush to Disk if the OS flushes data to disk, it may clear the dirty bit again no TLB flush necessary dirty bit is not TLB-relevant but HV needs to know it has to emulate dirty bit behaviour! imagine spt contains V RW P. HV will never again get a fault for V, so no chance to set dirty bit for V again Clearing of dirty bit must be communicated to HV A) paravirtualize guest, i. e. make aware of HV and insert explicit hypercalls B) observe: guest clearing dirty bit is a memory write operation HV can intercept those! jan (sect) Software Security SoSe / 27
25 Guest Pagetable Tracking New idea: track all changes to guest pagetables When HV intercepts guest write to CR3, in addition to creating/reactivating shadow pagetable: walk guest pagetable at new CR3 value enumerate all pieces in memory that comprise the pagetable (pagetables are not necessarily a contiguous structure) revoke write ission to those memory pages in spt HV now notified of all modifications to pagetable! This changes sequence diagram of page faults! jan (sect) Software Security SoSe / 27
26 Lazy Mapping, virtualized: take II process tries to execute (yet unmapped) location V Page Fault must be handled by HV! HV searches guest pagetable for V Case 1: no entry GP HV cannot know what to do with the fault forward ( inject ) fault into guest OS handles fault, tries to create V GP (nested) Page Fault HV notices change to pagetable HV validates and translates to V P nested fault resolved, HV resumes OS OS resumes process Still 2x Page Fault, now nested, not sequential jan (sect) Software Security SoSe / 27
27 Hardware Solution new hardware extension: Nested Paging ARM VE: already part of the Virtualization Extensions Intel: EPT (Extended Page Tables), 2008 AMD: NPT (Nested Page Tables), 2008 key feature: two CR3 registers, one controlled by guest, one by HV CPU uses guest CR3 to translate V to GP and HV CR3 to translate GP to P faults can now be attributed properly: no entry in guest table? let guest OS handle it no entry in HV table? probably illegal result of guest table, terminate guest (but see next week) jan (sect) Software Security SoSe / 27
Virtual Machines. COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361
 s COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361 1 Virtualization! Create illusion of multiple machines on the same physical hardware! Single computer hosts multiple virtual machines
s COMP 3361: Operating Systems I Winter 2015 http://www.cs.du.edu/3361 1 Virtualization! Create illusion of multiple machines on the same physical hardware! Single computer hosts multiple virtual machines
Full and Para Virtualization
 Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Full and Para Virtualization Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF x86 Hardware Virtualization The x86 architecture offers four levels
Virtual machines and operating systems
 V i r t u a l m a c h i n e s a n d o p e r a t i n g s y s t e m s Virtual machines and operating systems Krzysztof Lichota lichota@mimuw.edu.pl A g e n d a Virtual machines and operating systems interactions
V i r t u a l m a c h i n e s a n d o p e r a t i n g s y s t e m s Virtual machines and operating systems Krzysztof Lichota lichota@mimuw.edu.pl A g e n d a Virtual machines and operating systems interactions
Virtualization in Linux KVM + QEMU
 CS695 Topics in Virtualization and Cloud Computing KVM + QEMU Senthil, Puru, Prateek and Shashank 1 Topics covered KVM and QEMU Architecture VTx support CPU virtualization in KMV Memory virtualization
CS695 Topics in Virtualization and Cloud Computing KVM + QEMU Senthil, Puru, Prateek and Shashank 1 Topics covered KVM and QEMU Architecture VTx support CPU virtualization in KMV Memory virtualization
Virtualization Technology. Zhiming Shen
 Virtualization Technology Zhiming Shen Virtualization: rejuvenation 1960 s: first track of virtualization Time and resource sharing on expensive mainframes IBM VM/370 Late 1970 s and early 1980 s: became
Virtualization Technology Zhiming Shen Virtualization: rejuvenation 1960 s: first track of virtualization Time and resource sharing on expensive mainframes IBM VM/370 Late 1970 s and early 1980 s: became
Uses for Virtual Machines. Virtual Machines. There are several uses for virtual machines:
 Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
Virtual Machines Uses for Virtual Machines Virtual machine technology, often just called virtualization, makes one computer behave as several computers by sharing the resources of a single computer between
CS 695 Topics in Virtualization and Cloud Computing. More Introduction + Processor Virtualization
 CS 695 Topics in Virtualization and Cloud Computing More Introduction + Processor Virtualization (source for all images: Virtual Machines: Versatile Platforms for Systems and Processes Morgan Kaufmann;
CS 695 Topics in Virtualization and Cloud Computing More Introduction + Processor Virtualization (source for all images: Virtual Machines: Versatile Platforms for Systems and Processes Morgan Kaufmann;
AMD 64 Virtualization
 AMD 64 Virtualization AMD India Developer s Conference Bangalore, David O BrienO Senior Systems Software Engineer Advanced Micro Devices, Inc. Virtual Machine Approaches Carve a System into Many Virtual
AMD 64 Virtualization AMD India Developer s Conference Bangalore, David O BrienO Senior Systems Software Engineer Advanced Micro Devices, Inc. Virtual Machine Approaches Carve a System into Many Virtual
WHITE PAPER. AMD-V Nested Paging. AMD-V Nested Paging. Issue Date: July, 2008 Revision: 1.0. Advanced Micro Devices, Inc.
 Issue Date: July, 2008 Revision: 1.0 2008 All rights reserved. The contents of this document are provided in connection with ( AMD ) products. AMD makes no representations or warranties with respect to
Issue Date: July, 2008 Revision: 1.0 2008 All rights reserved. The contents of this document are provided in connection with ( AMD ) products. AMD makes no representations or warranties with respect to
Virtual vs Physical Addresses
 Virtual vs Physical Addresses Physical addresses refer to hardware addresses of physical memory. Virtual addresses refer to the virtual store viewed by the process. virtual addresses might be the same
Virtual vs Physical Addresses Physical addresses refer to hardware addresses of physical memory. Virtual addresses refer to the virtual store viewed by the process. virtual addresses might be the same
Virtualization. Types of Interfaces
 Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
Virtualization Virtualization: extend or replace an existing interface to mimic the behavior of another system. Introduced in 1970s: run legacy software on newer mainframe hardware Handle platform diversity
OSes. Arvind Seshadri Mark Luk Ning Qu Adrian Perrig SOSP2007. CyLab of CMU. SecVisor: A Tiny Hypervisor to Provide
 SecVisor: A Seshadri Mark Luk Ning Qu CyLab of CMU SOSP2007 Outline Introduction Assumption SVM Background Design Problems Implementation Kernel Porting Evaluation Limitation Introducion Why? Only approved
SecVisor: A Seshadri Mark Luk Ning Qu CyLab of CMU SOSP2007 Outline Introduction Assumption SVM Background Design Problems Implementation Kernel Porting Evaluation Limitation Introducion Why? Only approved
Intel s Virtualization Extensions (VT-x) So you want to build a hypervisor?
 Intel s Virtualization Extensions (VT-x) So you want to build a hypervisor? Mr. Jacob Torrey February 26, 2014 Dartmouth College 153 Brooks Road, Rome, NY 315.336.3306 http://ainfosec.com @JacobTorrey
Intel s Virtualization Extensions (VT-x) So you want to build a hypervisor? Mr. Jacob Torrey February 26, 2014 Dartmouth College 153 Brooks Road, Rome, NY 315.336.3306 http://ainfosec.com @JacobTorrey
Xen and the Art of. Virtualization. Ian Pratt
 Xen and the Art of Virtualization Ian Pratt Keir Fraser, Steve Hand, Christian Limpach, Dan Magenheimer (HP), Mike Wray (HP), R Neugebauer (Intel), M Williamson (Intel) Computer Laboratory Outline Virtualization
Xen and the Art of Virtualization Ian Pratt Keir Fraser, Steve Hand, Christian Limpach, Dan Magenheimer (HP), Mike Wray (HP), R Neugebauer (Intel), M Williamson (Intel) Computer Laboratory Outline Virtualization
The Xen of Virtualization
 The Xen of Virtualization Assignment for CLC-MIRI Amin Khan Universitat Politècnica de Catalunya March 4, 2013 Amin Khan (UPC) Xen Hypervisor March 4, 2013 1 / 19 Outline 1 Introduction 2 Architecture
The Xen of Virtualization Assignment for CLC-MIRI Amin Khan Universitat Politècnica de Catalunya March 4, 2013 Amin Khan (UPC) Xen Hypervisor March 4, 2013 1 / 19 Outline 1 Introduction 2 Architecture
Lecture 17: Virtual Memory II. Goals of virtual memory
 Lecture 17: Virtual Memory II Last Lecture: Introduction to virtual memory Today Review and continue virtual memory discussion Lecture 17 1 Goals of virtual memory Make it appear as if each process has:
Lecture 17: Virtual Memory II Last Lecture: Introduction to virtual memory Today Review and continue virtual memory discussion Lecture 17 1 Goals of virtual memory Make it appear as if each process has:
Hypervisor: Requirement Document (Version 3)
 Hypervisor: Requirement Document (Version 3) Jean-Raymond Abrial and Rustan Leino No Institute Given 1 Requirement Document 1.1 A single system memory handling - SM-0: An operating system (OS) makes use
Hypervisor: Requirement Document (Version 3) Jean-Raymond Abrial and Rustan Leino No Institute Given 1 Requirement Document 1.1 A single system memory handling - SM-0: An operating system (OS) makes use
kvm: Kernel-based Virtual Machine for Linux
 kvm: Kernel-based Virtual Machine for Linux 1 Company Overview Founded 2005 A Delaware corporation Locations US Office Santa Clara, CA R&D - Netanya/Poleg Funding Expertise in enterprise infrastructure
kvm: Kernel-based Virtual Machine for Linux 1 Company Overview Founded 2005 A Delaware corporation Locations US Office Santa Clara, CA R&D - Netanya/Poleg Funding Expertise in enterprise infrastructure
Nested Virtualization
 Nested Virtualization Dongxiao Xu, Xiantao Zhang, Yang Zhang May 9, 2013 Agenda Nested Virtualization Overview Dive into Nested Virtualization Details Nested CPU Virtualization Nested MMU Virtualization
Nested Virtualization Dongxiao Xu, Xiantao Zhang, Yang Zhang May 9, 2013 Agenda Nested Virtualization Overview Dive into Nested Virtualization Details Nested CPU Virtualization Nested MMU Virtualization
Board Notes on Virtual Memory
 Board Notes on Virtual Memory Part A: Why Virtual Memory? - Letʼs user program size exceed the size of the physical address space - Supports protection o Donʼt know which program might share memory at
Board Notes on Virtual Memory Part A: Why Virtual Memory? - Letʼs user program size exceed the size of the physical address space - Supports protection o Donʼt know which program might share memory at
Virtualization for Cloud Computing
 Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
Virtualization for Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF CLOUD COMPUTING On demand provision of computational resources
COS 318: Operating Systems. Virtual Memory and Address Translation
 COS 318: Operating Systems Virtual Memory and Address Translation Today s Topics Midterm Results Virtual Memory Virtualization Protection Address Translation Base and bound Segmentation Paging Translation
COS 318: Operating Systems Virtual Memory and Address Translation Today s Topics Midterm Results Virtual Memory Virtualization Protection Address Translation Base and bound Segmentation Paging Translation
ARM Virtualization: CPU & MMU Issues
 ARM Virtualization: CPU & MMU Issues Prashanth Bungale, Sr. Member of Technical Staff 2010 VMware Inc. All rights reserved Overview Virtualizability and Sensitive Instructions ARM CPU State Sensitive Instructions
ARM Virtualization: CPU & MMU Issues Prashanth Bungale, Sr. Member of Technical Staff 2010 VMware Inc. All rights reserved Overview Virtualizability and Sensitive Instructions ARM CPU State Sensitive Instructions
Virtualization. Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/
 Virtualization Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/ What is Virtualization? Virtualization is the simulation of the software and/ or hardware upon which other software runs. This
Virtualization Jia Rao Assistant Professor in CS http://cs.uccs.edu/~jrao/ What is Virtualization? Virtualization is the simulation of the software and/ or hardware upon which other software runs. This
Hardware Based Virtualization Technologies. Elsie Wahlig elsie.wahlig@amd.com Platform Software Architect
 Hardware Based Virtualization Technologies Elsie Wahlig elsie.wahlig@amd.com Platform Software Architect Outline What is Virtualization? Evolution of Virtualization AMD Virtualization AMD s IO Virtualization
Hardware Based Virtualization Technologies Elsie Wahlig elsie.wahlig@amd.com Platform Software Architect Outline What is Virtualization? Evolution of Virtualization AMD Virtualization AMD s IO Virtualization
Chapter 5 Cloud Resource Virtualization
 Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Chapter 5 Cloud Resource Virtualization Contents Virtualization. Layering and virtualization. Virtual machine monitor. Virtual machine. Performance and security isolation. Architectural support for virtualization.
Understanding Full Virtualization, Paravirtualization, and Hardware Assist. Introduction...1 Overview of x86 Virtualization...2 CPU Virtualization...
 Contents Introduction...1 Overview of x86 Virtualization...2 CPU Virtualization...3 The Challenges of x86 Hardware Virtualization...3 Technique 1 - Full Virtualization using Binary Translation...4 Technique
Contents Introduction...1 Overview of x86 Virtualization...2 CPU Virtualization...3 The Challenges of x86 Hardware Virtualization...3 Technique 1 - Full Virtualization using Binary Translation...4 Technique
Virtualization. Explain how today s virtualization movement is actually a reinvention
 Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
Virtualization Learning Objectives Explain how today s virtualization movement is actually a reinvention of the past. Explain how virtualization works. Discuss the technical challenges to virtualization.
Memory Management Outline. Background Swapping Contiguous Memory Allocation Paging Segmentation Segmented Paging
 Memory Management Outline Background Swapping Contiguous Memory Allocation Paging Segmentation Segmented Paging 1 Background Memory is a large array of bytes memory and registers are only storage CPU can
Memory Management Outline Background Swapping Contiguous Memory Allocation Paging Segmentation Segmented Paging 1 Background Memory is a large array of bytes memory and registers are only storage CPU can
Implementation of a Purely Hardware-assisted VMM for x86 Architecture
 Implementation of a Purely Hardware-assisted VMM for x86 Architecture Saidalavi Kalady, Dileep P G, Krishanu Sikdar, Sreejith B S, Vinaya Surya, Ezudheen P Abstract Virtualization is a technique for efficient
Implementation of a Purely Hardware-assisted VMM for x86 Architecture Saidalavi Kalady, Dileep P G, Krishanu Sikdar, Sreejith B S, Vinaya Surya, Ezudheen P Abstract Virtualization is a technique for efficient
Kernel Virtual Machine
 Kernel Virtual Machine Shashank Rachamalla Indian Institute of Technology Dept. of Computer Science November 24, 2011 Abstract KVM(Kernel-based Virtual Machine) is a full virtualization solution for x86
Kernel Virtual Machine Shashank Rachamalla Indian Institute of Technology Dept. of Computer Science November 24, 2011 Abstract KVM(Kernel-based Virtual Machine) is a full virtualization solution for x86
CS5460: Operating Systems. Lecture: Virtualization 2. Anton Burtsev March, 2013
 CS5460: Operating Systems Lecture: Virtualization 2 Anton Burtsev March, 2013 Paravirtualization: Xen Full virtualization Complete illusion of physical hardware Trap _all_ sensitive instructions Virtualized
CS5460: Operating Systems Lecture: Virtualization 2 Anton Burtsev March, 2013 Paravirtualization: Xen Full virtualization Complete illusion of physical hardware Trap _all_ sensitive instructions Virtualized
Hybrid Virtualization The Next Generation of XenLinux
 Hybrid Virtualization The Next Generation of XenLinux Jun Nakajima Principal Engineer Intel Open Source Technology Center Legal Disclaimer INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL
Hybrid Virtualization The Next Generation of XenLinux Jun Nakajima Principal Engineer Intel Open Source Technology Center Legal Disclaimer INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL
Microkernels, virtualization, exokernels. Tutorial 1 CSC469
 Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Microkernels, virtualization, exokernels Tutorial 1 CSC469 Monolithic kernel vs Microkernel Monolithic OS kernel Application VFS System call User mode What was the main idea? What were the problems? IPC,
Outline: Operating Systems
 Outline: Operating Systems What is an OS OS Functions Multitasking Virtual Memory File Systems Window systems PC Operating System Wars: Windows vs. Linux 1 Operating System provides a way to boot (start)
Outline: Operating Systems What is an OS OS Functions Multitasking Virtual Memory File Systems Window systems PC Operating System Wars: Windows vs. Linux 1 Operating System provides a way to boot (start)
Cloud Computing. Dipl.-Wirt.-Inform. Robert Neumann
 Cloud Computing Dipl.-Wirt.-Inform. Robert Neumann Pre-Cloud Provisioning Provisioned IT Capacity Load Forecast IT Capacity Overbuy Underbuy Fixed Cost for Capacity Investment Hurdle Real Load Time 144
Cloud Computing Dipl.-Wirt.-Inform. Robert Neumann Pre-Cloud Provisioning Provisioned IT Capacity Load Forecast IT Capacity Overbuy Underbuy Fixed Cost for Capacity Investment Hurdle Real Load Time 144
VMkit A lightweight hypervisor library for Barrelfish
 Masters Thesis VMkit A lightweight hypervisor library for Barrelfish by Raffaele Sandrini Due date 2 September 2009 Advisors: Simon Peter, Andrew Baumann, and Timothy Roscoe ETH Zurich, Systems Group Department
Masters Thesis VMkit A lightweight hypervisor library for Barrelfish by Raffaele Sandrini Due date 2 September 2009 Advisors: Simon Peter, Andrew Baumann, and Timothy Roscoe ETH Zurich, Systems Group Department
Introduction to Virtual Machines
 Introduction to Virtual Machines Carl Waldspurger (SB SM 89, PhD 95), VMware R&D 2010 VMware Inc. All rights reserved Overview Virtualization and VMs Processor Virtualization Memory Virtualization I/O
Introduction to Virtual Machines Carl Waldspurger (SB SM 89, PhD 95), VMware R&D 2010 VMware Inc. All rights reserved Overview Virtualization and VMs Processor Virtualization Memory Virtualization I/O
Distributed Systems. Virtualization. Paul Krzyzanowski pxk@cs.rutgers.edu
 Distributed Systems Virtualization Paul Krzyzanowski pxk@cs.rutgers.edu Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Distributed Systems Virtualization Paul Krzyzanowski pxk@cs.rutgers.edu Except as otherwise noted, the content of this presentation is licensed under the Creative Commons Attribution 2.5 License. Virtualization
Architecture of the Kernel-based Virtual Machine (KVM)
 Corporate Technology Architecture of the Kernel-based Virtual Machine (KVM) Jan Kiszka, Siemens AG, CT T DE IT 1 Corporate Competence Center Embedded Linux jan.kiszka@siemens.com Copyright Siemens AG 2010.
Corporate Technology Architecture of the Kernel-based Virtual Machine (KVM) Jan Kiszka, Siemens AG, CT T DE IT 1 Corporate Competence Center Embedded Linux jan.kiszka@siemens.com Copyright Siemens AG 2010.
CS 61C: Great Ideas in Computer Architecture Virtual Memory Cont.
 CS 61C: Great Ideas in Computer Architecture Virtual Memory Cont. Instructors: Vladimir Stojanovic & Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/ 1 Bare 5-Stage Pipeline Physical Address PC Inst.
CS 61C: Great Ideas in Computer Architecture Virtual Memory Cont. Instructors: Vladimir Stojanovic & Nicholas Weaver http://inst.eecs.berkeley.edu/~cs61c/ 1 Bare 5-Stage Pipeline Physical Address PC Inst.
Virtualization. ! Physical Hardware. ! Software. ! Isolation. ! Software Abstraction. ! Encapsulation. ! Virtualization Layer. !
 Starting Point: A Physical Machine Virtualization Based on materials from: Introduction to Virtual Machines by Carl Waldspurger Understanding Intel Virtualization Technology (VT) by N. B. Sahgal and D.
Starting Point: A Physical Machine Virtualization Based on materials from: Introduction to Virtual Machines by Carl Waldspurger Understanding Intel Virtualization Technology (VT) by N. B. Sahgal and D.
Performance tuning Xen
 Performance tuning Xen Roger Pau Monné roger.pau@citrix.com Madrid 8th of November, 2013 Xen Architecture Control Domain NetBSD or Linux device model (qemu) Hardware Drivers toolstack netback blkback Paravirtualized
Performance tuning Xen Roger Pau Monné roger.pau@citrix.com Madrid 8th of November, 2013 Xen Architecture Control Domain NetBSD or Linux device model (qemu) Hardware Drivers toolstack netback blkback Paravirtualized
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
COS 318: Operating Systems Virtual Machine Monitors Kai Li and Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall13/cos318/ Introduction u Have
Using Linux as Hypervisor with KVM
 Using Linux as Hypervisor with KVM Qumranet Inc. Andrea Arcangeli andrea@qumranet.com (some slides from Avi Kivity) CERN - Geneve 15 Sep 2008 Agenda Overview/feature list KVM design vs other virtualization
Using Linux as Hypervisor with KVM Qumranet Inc. Andrea Arcangeli andrea@qumranet.com (some slides from Avi Kivity) CERN - Geneve 15 Sep 2008 Agenda Overview/feature list KVM design vs other virtualization
A Hypervisor IPS based on Hardware assisted Virtualization Technology
 A Hypervisor IPS based on Hardware assisted Virtualization Technology 1. Introduction Junichi Murakami (murakami@fourteenforty.jp) Fourteenforty Research Institute, Inc. Recently malware has become more
A Hypervisor IPS based on Hardware assisted Virtualization Technology 1. Introduction Junichi Murakami (murakami@fourteenforty.jp) Fourteenforty Research Institute, Inc. Recently malware has become more
Nested Virtualization
 Nested Virtualization State of the art and future directions Bandan Das Yang Z Zhang Jan Kiszka 2 Outline Introduction Changes and Missing Features for AMD Changes and Missing Features for Intel Working
Nested Virtualization State of the art and future directions Bandan Das Yang Z Zhang Jan Kiszka 2 Outline Introduction Changes and Missing Features for AMD Changes and Missing Features for Intel Working
Memory management basics (1) Requirements (1) Objectives. Operating Systems Part of E1.9 - Principles of Computers and Software Engineering
 Memory management basics (1) Requirements (1) Operating Systems Part of E1.9 - Principles of Computers and Software Engineering Lecture 7: Memory Management I Memory management intends to satisfy the following
Memory management basics (1) Requirements (1) Operating Systems Part of E1.9 - Principles of Computers and Software Engineering Lecture 7: Memory Management I Memory management intends to satisfy the following
Cloud^H^H^H^H^H Virtualization Technology. Andrew Jones (drjones@redhat.com) May 2011
 Cloud^H^H^H^H^H Virtualization Technology Andrew Jones (drjones@redhat.com) May 2011 Outline Promise to not use the word Cloud again...but still give a couple use cases for Virtualization Emulation it's
Cloud^H^H^H^H^H Virtualization Technology Andrew Jones (drjones@redhat.com) May 2011 Outline Promise to not use the word Cloud again...but still give a couple use cases for Virtualization Emulation it's
The Microsoft Windows Hypervisor High Level Architecture
 The Microsoft Windows Hypervisor High Level Architecture September 21, 2007 Abstract The Microsoft Windows hypervisor brings new virtualization capabilities to the Windows Server operating system. Its
The Microsoft Windows Hypervisor High Level Architecture September 21, 2007 Abstract The Microsoft Windows hypervisor brings new virtualization capabilities to the Windows Server operating system. Its
VMware and CPU Virtualization Technology. Jack Lo Sr. Director, R&D
 ware and CPU Virtualization Technology Jack Lo Sr. Director, R&D This presentation may contain ware confidential information. Copyright 2005 ware, Inc. All rights reserved. All other marks and names mentioned
ware and CPU Virtualization Technology Jack Lo Sr. Director, R&D This presentation may contain ware confidential information. Copyright 2005 ware, Inc. All rights reserved. All other marks and names mentioned
kvm: the Linux Virtual Machine Monitor
 Avi Kivity Qumranet avi@qumranet.com kvm: the Linux Virtual Machine Monitor Uri Lublin Qumranet uril@qumranet.com Yaniv Kamay Qumranet yaniv@qumranet.com Dor Laor Qumranet dor.laor@qumranet.com Anthony
Avi Kivity Qumranet avi@qumranet.com kvm: the Linux Virtual Machine Monitor Uri Lublin Qumranet uril@qumranet.com Yaniv Kamay Qumranet yaniv@qumranet.com Dor Laor Qumranet dor.laor@qumranet.com Anthony
Virtualization. Pradipta De pradipta.de@sunykorea.ac.kr
 Virtualization Pradipta De pradipta.de@sunykorea.ac.kr Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
Virtualization Pradipta De pradipta.de@sunykorea.ac.kr Today s Topic Virtualization Basics System Virtualization Techniques CSE506: Ext Filesystem 2 Virtualization? A virtual machine (VM) is an emulation
Chapter 16: Virtual Machines. Operating System Concepts 9 th Edition
 Chapter 16: Virtual Machines Silberschatz, Galvin and Gagne 2013 Chapter 16: Virtual Machines Overview History Benefits and Features Building Blocks Types of Virtual Machines and Their Implementations
Chapter 16: Virtual Machines Silberschatz, Galvin and Gagne 2013 Chapter 16: Virtual Machines Overview History Benefits and Features Building Blocks Types of Virtual Machines and Their Implementations
Hypervisors and Virtual Machines
 Hypervisors and Virtual Machines Implementation Insights on the x86 Architecture DON REVELLE Don is a performance engineer and Linux systems/kernel programmer, specializing in high-volume UNIX, Web, virtualization,
Hypervisors and Virtual Machines Implementation Insights on the x86 Architecture DON REVELLE Don is a performance engineer and Linux systems/kernel programmer, specializing in high-volume UNIX, Web, virtualization,
x86 Virtualization Hardware Support Pla$orm Virtualiza.on
 x86 Virtualization Hardware Support Pla$orm Virtualiza.on Hide the physical characteris.cs of computer resources from the applica.ons Not a new idea: IBM s CP- 40 1967, CP/CMS, VM Full Virtualiza.on Simulate
x86 Virtualization Hardware Support Pla$orm Virtualiza.on Hide the physical characteris.cs of computer resources from the applica.ons Not a new idea: IBM s CP- 40 1967, CP/CMS, VM Full Virtualiza.on Simulate
How To Write A Page Table
 12 Paging: Introduction Remember our goal: to virtualize memory. Segmentation (a generalization of dynamic relocation) helped us do this, but has some problems; in particular, managing free space becomes
12 Paging: Introduction Remember our goal: to virtualize memory. Segmentation (a generalization of dynamic relocation) helped us do this, but has some problems; in particular, managing free space becomes
Virtualization. P. A. Wilsey. The text highlighted in green in these slides contain external hyperlinks. 1 / 16
 Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 1 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the application/operating
Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 1 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the application/operating
Practical Protection of Kernel Integrity for Commodity OS from Untrusted Extensions
 Practical Protection of Kernel Integrity for Commodity OS from Untrusted Extensions Xi Xiong The Pennsylvania State University xixiong@cse.psu.edu Donghai Tian The Pennsylvania State University Beijing
Practical Protection of Kernel Integrity for Commodity OS from Untrusted Extensions Xi Xiong The Pennsylvania State University xixiong@cse.psu.edu Donghai Tian The Pennsylvania State University Beijing
Virtualizing a Virtual Machine
 Virtualizing a Virtual Machine Azeem Jiva Shrinivas Joshi AMD Java Labs TS-5227 Learn best practices for deploying Java EE applications in virtualized environment 2008 JavaOne SM Conference java.com.sun/javaone
Virtualizing a Virtual Machine Azeem Jiva Shrinivas Joshi AMD Java Labs TS-5227 Learn best practices for deploying Java EE applications in virtualized environment 2008 JavaOne SM Conference java.com.sun/javaone
Virtual Machines. Virtualization
 Virtual Machines Marie Roch Tanenbaum 8.3 contains slides from: Tanenbaum 3 rd ed. 2008 1 Virtualization Started with the IBM System/360 in the 1960s Basic concept simulate multiple copies of the underlying
Virtual Machines Marie Roch Tanenbaum 8.3 contains slides from: Tanenbaum 3 rd ed. 2008 1 Virtualization Started with the IBM System/360 in the 1960s Basic concept simulate multiple copies of the underlying
Virtual Machine Monitors. Dr. Marc E. Fiuczynski Research Scholar Princeton University
 Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtual Machine Monitors Dr. Marc E. Fiuczynski Research Scholar Princeton University Introduction Have been around since 1960 s on mainframes used for multitasking Good example VM/370 Have resurfaced
Virtualization. P. A. Wilsey. The text highlighted in green in these slides contain external hyperlinks. 1 / 16
 1 / 16 Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 2 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the
1 / 16 Virtualization P. A. Wilsey The text highlighted in green in these slides contain external hyperlinks. 2 / 16 Conventional System Viewed as Layers This illustration is a common presentation of the
x64 Servers: Do you want 64 or 32 bit apps with that server?
 TMurgent Technologies x64 Servers: Do you want 64 or 32 bit apps with that server? White Paper by Tim Mangan TMurgent Technologies February, 2006 Introduction New servers based on what is generally called
TMurgent Technologies x64 Servers: Do you want 64 or 32 bit apps with that server? White Paper by Tim Mangan TMurgent Technologies February, 2006 Introduction New servers based on what is generally called
How To Understand The Power Of A Virtual Machine Monitor (Vm) In A Linux Computer System (Or A Virtualized Computer)
 KVM - The kernel-based virtual machine Timo Hirt timohirt@gmx.de 13. Februar 2010 Abstract Virtualization has been introduced in the 1960s, when computing systems were large and expensive to operate. It
KVM - The kernel-based virtual machine Timo Hirt timohirt@gmx.de 13. Februar 2010 Abstract Virtualization has been introduced in the 1960s, when computing systems were large and expensive to operate. It
Enabling Technologies for Distributed Computing
 Enabling Technologies for Distributed Computing Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF Multi-core CPUs and Multithreading Technologies
Enabling Technologies for Distributed Computing Dr. Sanjay P. Ahuja, Ph.D. Fidelity National Financial Distinguished Professor of CIS School of Computing, UNF Multi-core CPUs and Multithreading Technologies
Hypervisor-Based, Hardware-Assisted System Monitoring
 Horst Görtz Institute for IT-Security, Chair for System Security VMRay GmbH Hypervisor-Based, Hardware-Assisted System Monitoring VB2013 October 2-4, 2013 Berlin Carsten Willems, Ralf Hund, Thorsten Holz
Horst Görtz Institute for IT-Security, Chair for System Security VMRay GmbH Hypervisor-Based, Hardware-Assisted System Monitoring VB2013 October 2-4, 2013 Berlin Carsten Willems, Ralf Hund, Thorsten Holz
Intel Virtualization Technology Overview Yu Ke
 Intel Virtualization Technology Overview Yu Ke SSG System Software Division Agenda Virtualization Overview Intel Virtualization Technology 2 What is Virtualization VM 0 VM 1 VM n Virtual Machines (VMs)
Intel Virtualization Technology Overview Yu Ke SSG System Software Division Agenda Virtualization Overview Intel Virtualization Technology 2 What is Virtualization VM 0 VM 1 VM n Virtual Machines (VMs)
Virtualization. Clothing the Wolf in Wool. Wednesday, April 17, 13
 Virtualization Clothing the Wolf in Wool Virtual Machines Began in 1960s with IBM and MIT Project MAC Also called open shop operating systems Present user with the view of a bare machine Execute most instructions
Virtualization Clothing the Wolf in Wool Virtual Machines Began in 1960s with IBM and MIT Project MAC Also called open shop operating systems Present user with the view of a bare machine Execute most instructions
COS 318: Operating Systems. Virtual Machine Monitors
 COS 318: Operating Systems Virtual Machine Monitors Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall10/cos318/ Introduction Have been around
COS 318: Operating Systems Virtual Machine Monitors Andy Bavier Computer Science Department Princeton University http://www.cs.princeton.edu/courses/archive/fall10/cos318/ Introduction Have been around
Virtuoso and Database Scalability
 Virtuoso and Database Scalability By Orri Erling Table of Contents Abstract Metrics Results Transaction Throughput Initializing 40 warehouses Serial Read Test Conditions Analysis Working Set Effect of
Virtuoso and Database Scalability By Orri Erling Table of Contents Abstract Metrics Results Transaction Throughput Initializing 40 warehouses Serial Read Test Conditions Analysis Working Set Effect of
IOMMU: A Detailed view
 12/1/14 Security Level: Security Level: IOMMU: A Detailed view Anurup M. Sanil Kumar D. Nov, 2014 HUAWEI TECHNOLOGIES CO., LTD. Contents n IOMMU Introduction n IOMMU for ARM n Use cases n Software Architecture
12/1/14 Security Level: Security Level: IOMMU: A Detailed view Anurup M. Sanil Kumar D. Nov, 2014 HUAWEI TECHNOLOGIES CO., LTD. Contents n IOMMU Introduction n IOMMU for ARM n Use cases n Software Architecture
Cloud Computing CS 15-319
 Cloud Computing CS 15-319 Virtualization Case Studies : Xen and VMware Lecture 20 Majd F. Sakr, Mohammad Hammoud and Suhail Rehman 1 Today Last session Resource Virtualization Today s session Virtualization
Cloud Computing CS 15-319 Virtualization Case Studies : Xen and VMware Lecture 20 Majd F. Sakr, Mohammad Hammoud and Suhail Rehman 1 Today Last session Resource Virtualization Today s session Virtualization
matasano Hardware Virtualization Rootkits Dino A. Dai Zovi
 Hardware Virtualization Rootkits Dino A. Dai Zovi Agenda Introductions Virtualization (Software and Hardware) Intel VT-x (aka Vanderpool ) VM Rootkits Implementing a VT-x based Rootkit Detecting Hardware-VM
Hardware Virtualization Rootkits Dino A. Dai Zovi Agenda Introductions Virtualization (Software and Hardware) Intel VT-x (aka Vanderpool ) VM Rootkits Implementing a VT-x based Rootkit Detecting Hardware-VM
This Unit: Virtual Memory. CIS 501 Computer Architecture. Readings. A Computer System: Hardware
 This Unit: Virtual CIS 501 Computer Architecture Unit 5: Virtual App App App System software Mem CPU I/O The operating system (OS) A super-application Hardware support for an OS Virtual memory Page tables
This Unit: Virtual CIS 501 Computer Architecture Unit 5: Virtual App App App System software Mem CPU I/O The operating system (OS) A super-application Hardware support for an OS Virtual memory Page tables
Knut Omang Ifi/Oracle 19 Oct, 2015
 Software and hardware support for Network Virtualization Knut Omang Ifi/Oracle 19 Oct, 2015 Motivation Goal: Introduction to challenges in providing fast networking to virtual machines Prerequisites: What
Software and hardware support for Network Virtualization Knut Omang Ifi/Oracle 19 Oct, 2015 Motivation Goal: Introduction to challenges in providing fast networking to virtual machines Prerequisites: What
Bridging the Gap between Software and Hardware Techniques for I/O Virtualization
 Bridging the Gap between Software and Hardware Techniques for I/O Virtualization Jose Renato Santos Yoshio Turner G.(John) Janakiraman Ian Pratt Hewlett Packard Laboratories, Palo Alto, CA University of
Bridging the Gap between Software and Hardware Techniques for I/O Virtualization Jose Renato Santos Yoshio Turner G.(John) Janakiraman Ian Pratt Hewlett Packard Laboratories, Palo Alto, CA University of
W4118: segmentation and paging. Instructor: Junfeng Yang
 W4118: segmentation and paging Instructor: Junfeng Yang Outline Memory management goals Segmentation Paging TLB 1 Uni- v.s. multi-programming Simple uniprogramming with a single segment per process Uniprogramming
W4118: segmentation and paging Instructor: Junfeng Yang Outline Memory management goals Segmentation Paging TLB 1 Uni- v.s. multi-programming Simple uniprogramming with a single segment per process Uniprogramming
Virtualization. Dr. Yingwu Zhu
 Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
Virtualization Dr. Yingwu Zhu What is virtualization? Virtualization allows one computer to do the job of multiple computers. Virtual environments let one computer host multiple operating systems at the
System Virtual Machines
 System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
System Virtual Machines Introduction Key concepts Resource virtualization processors memory I/O devices Performance issues Applications 1 Introduction System virtual machine capable of supporting multiple
Virtualization Technologies
 12 January 2010 Virtualization Technologies Alex Landau (lalex@il.ibm.com) IBM Haifa Research Lab What is virtualization? Virtualization is way to run multiple operating systems and user applications on
12 January 2010 Virtualization Technologies Alex Landau (lalex@il.ibm.com) IBM Haifa Research Lab What is virtualization? Virtualization is way to run multiple operating systems and user applications on
How To Make A Minecraft Iommus Work On A Linux Kernel (Virtual) With A Virtual Machine (Virtual Machine) And A Powerpoint (Virtual Powerpoint) (Virtual Memory) (Iommu) (Vm) (
 Operating System and Hypervisor Support for IOMMUs Muli Ben-Yehuda IBM Haifa Research Lab muli@il.ibm.com p. 1/3 Table of Contents The what and why of IOMMUs. How much does it cost? What can we do about
Operating System and Hypervisor Support for IOMMUs Muli Ben-Yehuda IBM Haifa Research Lab muli@il.ibm.com p. 1/3 Table of Contents The what and why of IOMMUs. How much does it cost? What can we do about
9/26/2011. What is Virtualization? What are the different types of virtualization.
 CSE 501 Monday, September 26, 2011 Kevin Cleary kpcleary@buffalo.edu What is Virtualization? What are the different types of virtualization. Practical Uses Popular virtualization products Demo Question,
CSE 501 Monday, September 26, 2011 Kevin Cleary kpcleary@buffalo.edu What is Virtualization? What are the different types of virtualization. Practical Uses Popular virtualization products Demo Question,
Intel Virtualization Technology and Extensions
 Intel Virtualization Technology and Extensions Rochester Institute of Technology Prepared and Presented by: Swapnil S. Jadhav (Computer Engineering) Chaitanya Gadiyam (Computer Engineering) 1 Agenda Virtualization
Intel Virtualization Technology and Extensions Rochester Institute of Technology Prepared and Presented by: Swapnil S. Jadhav (Computer Engineering) Chaitanya Gadiyam (Computer Engineering) 1 Agenda Virtualization
Enabling Technologies for Distributed and Cloud Computing
 Enabling Technologies for Distributed and Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF Multi-core CPUs and Multithreading
Enabling Technologies for Distributed and Cloud Computing Dr. Sanjay P. Ahuja, Ph.D. 2010-14 FIS Distinguished Professor of Computer Science School of Computing, UNF Multi-core CPUs and Multithreading
Windows Server Virtualization & The Windows Hypervisor
 Windows Server Virtualization & The Windows Hypervisor Brandon Baker Lead Security Engineer Windows Kernel Team Microsoft Corporation Agenda - Windows Server Virtualization (WSV) Why a hypervisor? Quick
Windows Server Virtualization & The Windows Hypervisor Brandon Baker Lead Security Engineer Windows Kernel Team Microsoft Corporation Agenda - Windows Server Virtualization (WSV) Why a hypervisor? Quick
Performance Evaluation of Intel EPT Hardware Assist VMware ESX builds 140815 & 136362 (internal builds)
 Performance Evaluation of Intel Hardware Assist VMware ESX builds 140815 & 136362 (internal builds) Introduction For the majority of common workloads, performance in a virtualized environment is close
Performance Evaluation of Intel Hardware Assist VMware ESX builds 140815 & 136362 (internal builds) Introduction For the majority of common workloads, performance in a virtualized environment is close
VMware Horizon FLEX User Guide
 Horizon FLEX 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Outline. Outline. Why virtualization? Why not virtualize? Today s data center. Cloud computing. Virtual resource pool
 Outline CS 6V81-05: System Security and Malicious Code Analysis Overview of System ization: The most powerful platform for program analysis and system security Zhiqiang Lin Department of Computer Science
Outline CS 6V81-05: System Security and Malicious Code Analysis Overview of System ization: The most powerful platform for program analysis and system security Zhiqiang Lin Department of Computer Science
Scaling in a Hypervisor Environment
 Scaling in a Hypervisor Environment Richard McDougall Chief Performance Architect VMware VMware ESX Hypervisor Architecture Guest Monitor Guest TCP/IP Monitor (BT, HW, PV) File System CPU is controlled
Scaling in a Hypervisor Environment Richard McDougall Chief Performance Architect VMware VMware ESX Hypervisor Architecture Guest Monitor Guest TCP/IP Monitor (BT, HW, PV) File System CPU is controlled
BHyVe. BSD Hypervisor. Neel Natu Peter Grehan
 BHyVe BSD Hypervisor Neel Natu Peter Grehan 1 Introduction BHyVe stands for BSD Hypervisor Pronounced like beehive Type 2 Hypervisor (aka hosted hypervisor) FreeBSD is the Host OS Availability NetApp is
BHyVe BSD Hypervisor Neel Natu Peter Grehan 1 Introduction BHyVe stands for BSD Hypervisor Pronounced like beehive Type 2 Hypervisor (aka hosted hypervisor) FreeBSD is the Host OS Availability NetApp is
The MIPS architecture and virtualization
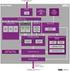 The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
The MIPS architecture and virtualization Simply put, virtualization makes one physical device appear as one or more virtual devices. Virtualization can be implemented at the processor level (e.g. CPU or
Computer Engineering and Systems Group Electrical and Computer Engineering SCMFS: A File System for Storage Class Memory
 SCMFS: A File System for Storage Class Memory Xiaojian Wu, Narasimha Reddy Texas A&M University What is SCM? Storage Class Memory Byte-addressable, like DRAM Non-volatile, persistent storage Example: Phase
SCMFS: A File System for Storage Class Memory Xiaojian Wu, Narasimha Reddy Texas A&M University What is SCM? Storage Class Memory Byte-addressable, like DRAM Non-volatile, persistent storage Example: Phase
The Price of Safety: Evaluating IOMMU Performance Preliminary Results
 The Price of Safety: Evaluating IOMMU Performance Preliminary Results Muli Ben-Yehuda muli@il.ibm.com IBM Haifa Research Lab The Price of Safety: Evaluating IOMMU Performance, 2007 Spring Xen Summit p.1/14
The Price of Safety: Evaluating IOMMU Performance Preliminary Results Muli Ben-Yehuda muli@il.ibm.com IBM Haifa Research Lab The Price of Safety: Evaluating IOMMU Performance, 2007 Spring Xen Summit p.1/14
Using Hypervisor to Provide Data Secrecy for User Applications on a Per-Page Basis
 Using Hypervisor to Provide Data Secrecy for User Applications on a Per-Page Basis Jisoo Yang Kang G. Shin University of Michigan {jisooy,kgshin}@eecs.umich.edu Abstract Hypervisors are increasingly utilized
Using Hypervisor to Provide Data Secrecy for User Applications on a Per-Page Basis Jisoo Yang Kang G. Shin University of Michigan {jisooy,kgshin}@eecs.umich.edu Abstract Hypervisors are increasingly utilized
The Turtles Project: Design and Implementation of Nested Virtualization
 The Turtles Project: Design and Implementation of Nested Virtualization Muli Ben-Yehuda Michael D. Day Zvi Dubitzky Michael Factor Nadav Har El muli@il.ibm.com mdday@us.ibm.com dubi@il.ibm.com factor@il.ibm.com
The Turtles Project: Design and Implementation of Nested Virtualization Muli Ben-Yehuda Michael D. Day Zvi Dubitzky Michael Factor Nadav Har El muli@il.ibm.com mdday@us.ibm.com dubi@il.ibm.com factor@il.ibm.com
ARM Caches: Giving you enough rope... to shoot yourself in the foot. Marc Zyngier <marc.zyngier@arm.com> KVM Forum 15
 ARM Caches: Giving you enough rope... to shoot yourself in the foot Marc Zyngier KVM Forum 15 1 Caches on ARM: A technical issue? Or a cultural one? From: Paolo Bonzini
ARM Caches: Giving you enough rope... to shoot yourself in the foot Marc Zyngier KVM Forum 15 1 Caches on ARM: A technical issue? Or a cultural one? From: Paolo Bonzini
Xen and the Art of Virtualization
 Xen and the Art of Virtualization Paul Barham, Boris Dragovic, Keir Fraser, Steven Hand, Tim Harris, Alex Ho, Rolf Neugebauery, Ian Pratt, Andrew Warfield University of Cambridge Computer Laboratory, SOSP
Xen and the Art of Virtualization Paul Barham, Boris Dragovic, Keir Fraser, Steven Hand, Tim Harris, Alex Ho, Rolf Neugebauery, Ian Pratt, Andrew Warfield University of Cambridge Computer Laboratory, SOSP
VMware Horizon FLEX User Guide
 Horizon FLEX 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
Horizon FLEX 1.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this
CSE 501 Monday, September 09, 2013 Kevin Cleary kpcleary@buffalo.edu
 CSE 501 Monday, September 09, 2013 Kevin Cleary kpcleary@buffalo.edu What is Virtualization? Practical Uses What can be virtualized Popular virtualization products Demo Question, answer, discussion Can
CSE 501 Monday, September 09, 2013 Kevin Cleary kpcleary@buffalo.edu What is Virtualization? Practical Uses What can be virtualized Popular virtualization products Demo Question, answer, discussion Can
