Partnership with Benetech, a non-profit organization that develops and supports Martus, secure information management software for human rights
|
|
|
- Elmer Martin
- 8 years ago
- Views:
Transcription
1 Partnership with Benetech, a non-profit organization that develops and supports Martus, secure information management software for human rights monitoring. 1
2 Benetech creates and develops new technology solutions that serve humanity, empower people, and address social justice questions. Benetech as several initiatives. The Global Literacy Program centers on Bookshare, a program for people with vision and reading disabilities. As part of this project, Benetech has formed the world's largest accessible digital library of scanned material. The Environmental Program has created a project management tool called Miradi especially for environmental conservation projects. The Human Rights Program at Benetech produces Martus, a free and open source secure documentation software that allows users to encrypt, search, analyze, and back up their data to a secure network of servers. Providing the capacity to securely document stories of human rights abuses, Martus protects the identities of witnesses and the promotes safety of human rights defenders. Currently available in 12 languages, Martus has been downloaded in over 100 countries, and Benetech has trained Martus users in over 40 of those. The demand for Martus technology and training is rapidly growing. Our Mobile Martus app for Android was released in September 2013, which is exciting and provides capacity for unobtrusive, secure mobile data collection. Martus is the Greek word for witness. And Benetech s most recent initiative is Benetech Labs, an incubator project to identify big ideas and possible solutions to today s major challenges. It s where we begin to develop new technology or enhancements to our existing technology so that, ultimately, we can launch successful, useful, relevant tech tools for social good. 2
3 Benetech is based in Palo Alto, California and is a non-profit organization. Benetech is funded through the support of foundation and government grants as well as donations from individuals. The Human Rights Program is composed of six full time staff as well as associated engineers and trainers that develop Martus, provide support to Martus users, and conduct outreach and training on Martus to those who would like to learn to use the program. The Benetech Human Rights Program released the first version of Martus in 2003 and has trained and supported Martus users all over the world since then. You can contact the Benetech Human Rights Program with questions or for assistance with troubleshooting Martus at any time by ing help@martus.org or info@martus.org. 3
4 Information is a human rights advocates greatest asset, but it must be protected and properly utilized. To better understand why Benetech developed Martus, let s start in Guatemala. This is a picture of the National Police Archives in Guatemala containing millions of pages of police records that detail many of the happenings during Guatemala s long internal conflict in the 1980s and 1990s, including about torture, killings, detentions, and other illegal practices committed by state authorities, largely against the Mayan peoples of Guatemala. You may have heard in the news that one of Guatemala s former leaders was sentenced for his role in carrying out genocide during this time. The National Police Archive, and the information accidentally discovered within it nearly 10 years ago, was instrumental in providing the evidence necessary for the verdict. But, as one can see, this pile of evidence is vulnerable to theft, loss, and easy destruction. In paper form, it is also not easily searchable or possible to analyze. The National Police Archives painstakingly preserved and digitized this warehouse full of information and safely stored samples of the data in Martus in order to be able to preserve it, secure it, make it searchable, analyze it, and transform it into powerful evidence. That evidence helped provide the proof that led to a verdict of a prison sentence of 80 years for genocide and crimes against humanity for Guatemala s former leader. One of the keys was securing the data, and that s where Martus came in. 4
5 Benetech designed Martus to serve organizations and situations like the National Police Archives, in which human rights advocates and defenders need to preserve, backup, and secure their information keeping unauthorized viewers out while at the same time being able to get their information back in the event of a theft or attack. When Benetech asked its human rights partners what they would need from an information management program designed specifically for human rights, they gave Benetech this wish list. They said that the program would need to be: Easy to use Affordable Easy to customize Offer flexibility with data sharing Include backup servers for safeguarding information Provide the ability to search and report on information Provide a way to publicize public data on the Internet 5
6 So, Benetech created Martus to meet all these needs: In its efforts to make Martus as widely accessible as possible, Martus is absolutely free and can be downloaded on the website. Martus is also open-source, which means that the program s source code is published and freely available for anyone to use, review, or build upon, as well as verify that the software does exactly what it says it does. Open source software means you don t have trust the developers you can verify that you both have the *real* software and that it actually does what it says it does. You can contrast this with Skype for example. Skype uses encryption and it s free, but it is owned by Microsoft, we can t see the code behind the software, and therefore we can t verify that it does what it says it does. Contributing to and drawing on the open source community is an important part of who Benetech is. Martus prioritizes security and uses standard encryption, like that which is often used by banks or sites like Google.com. Encryption is a way to obscure data so that it is only r eadable by authorized people. Finally, Martus offers a way to store, standardize, organize, search, and share digital information, making it a useful tool to transform information into useful evidence. 6
7 These are some of the logos of the many organizations that have worked with the Benetech Human Rights Program over the last ten years. We look forward to working with you! 7
8 The following screenshots offer a quick visual overview of the functionality of Martus, but an in-person training can provide more examples of how Martus can be used successfully for your project. 8
9 Martus data entry format templates are customizable, so you can shape your form to match the data you are collecting and any interview/intake forms you are already using. Martus allows various field types, including text fields, drop down menus, checkboxes, grids (tables), date and date range fields, among others. 9
10 For each Martus bulletin, you can attach as many files you would like, of any size, and of any file type. This includes video files, but remember, when backing up to the server, sending a video over the internet will be expensive and will take a long time (imagine uploading a 1gb video file to Dropbox or Google Drive same thing when ending a Martus bulletin with a 1gb file attached). 10
11 On your computer, all of the data in your Martus account is stored encrypted, so that only you or someone you designate can read it. You can choose to publish some of this information to the Martus public search engine if you like, or ensure that all of your data NEVER shows up on the search engine. In Martus, a red border around a bulletin section means that information is PRIVATE, which means it will never show up on the Martus search engine. If the border around a section is grey, then once sealed and saved on the server, the information in that section will be available on the open internet. This includes attachments within the bordered areas any attachments inside a grey/public section will appear on the Martus search engine once the bulletin has been saved to a Martus server. On every bulletin, there is a section that can be Public or Private, and a section that is ALWAYS Private. Most Martus users do not ever make any data public, but some do. 11
12 The same encryption methods that major banks and commercial websites use to protect their data are employed by Martus. PGP is an open source standard that has been around for many years, and Martus uses the same methods. 12
13 Martus encrypts private bulletin data in multiple ways. It encrypts the DATA on your machine, before it s ever sent to a server. And, it encrypts the CONNECTION itself, so that snooping attackers cannot see what information is being sent or received by either end. Even if they were able to decrypt the connection (very very hard), all they would see is encrypted data being sent to or received from the server. And the data also stays encrypted on the servers so that nobody, including Benetech or server operators, can read the data. 13
14 This is a VERY basic example of encryption, illustrating the IDEA of encryption. THIS IS NOT THE TYPE OF ENCRYPTION MARTUS USES. If it did, the encryption could be cracked instantly. Instead, Martus uses very, very advanced encryption methods that change the original data into something unreadable and indecipherable without the decryption key. 14
15 This is what your data encrypted inside Martus looks like. Data encrypted in Martus can only be decrypted and viewed inside Martus and only by the Martus account in which it was created, or anyone that you have authorized to decrypt and read it. If you try to open the encrypted files on your computer that contain the data in your Martus bulletins outside of Martus, this is what you will see. You can see that there is data, but you can t read it. In the event that an attacker or authority were to gain access to the Martus server, this is also what they would see: there is data, but it s unreadable. 15
16 Benetech makes two servers available for free to all Martus users. There is no limit to the amount of data you are allowed to back up on the server, and the servers mirror each other several times a day, so there is always a backup of your backup. 16
17 Martus 4.3 and above allows for the option of communicating with Martus servers over Tor. Tor is a free and open-source tool that provides internet users with greater anonymity online and a better ability to circumvent censorship. In most cases, when you send or receive information over the internet, you establish a fairly direct connection to the sites or servers you are contacting. For example, if you send an through Gmail, it is easy for those along the way to see that you are connecting to Gmail.com and for Google, who administers the servers, to see information about your computer and where it is located. Instead, Tor protects you by bouncing your communications around a distributed network of relays run by volunteers all around the world and obscuring the trail using encryption. Thus, it prevents somebody watching your Internet connection from learning what sites you visit, and it prevents the sites you visit from learning your physical location. If you need or want to obscure your connection to the Martus server, or to circumvent censorship in order to connect to the backup Martus servers, using Martus over Tor can help you do this. Using Tor will also make sending and receiving bulletins from the Martus servers slower. 17
18 You may choose to share data with other Martus users. When sending data in Martus, the sender is the Field Desk and the receiver is the Headquarters. A Field Desk may also be a Headquarters, and a Field Desk may configure as many Headquarters accounts as she likes. 18
19 Data is shared with other Martus users through the servers. Data is encrypted on your computer, the encrypted data is sent to the server, someone you trust and have authorized downloads that encrypted data, and it is decrypted on that person s computer. Never was the plain, unencrypted message available throughout the interchange. 19
20 End to end encryption means that your data is encrypted locally on your computer and only the encrypted data is sent over the internet. The encrypted data is then downloaded by the recipient and decrypted on their computer back to plain text they can read. At no point during the transit of that data from one computer to the server to another computer is the data ever unencrypted. Martus makes this easy and automatic. End-to-end encryption requires that the keys to decrypt the data are not stored on the server facilitating the exchange. This means that if an unauthorized person, whether a server admin under bribe or threat, or another user or hacker were to gain access to the data on the server, they cannot decrypt the data. It also means that you cannot access your Martus account and view your data through an online web portal, which would require that your keys be stored on the server where your data is stored. This would significantly reduce the security of your data. It s also why some companies have been able to give away their users s or data to inquiring authorities. In those cases, even if the data is encrypted on their servers, they also hold the keys, rendering the encryption little protection from legal subpoenas. But Benetech can t give away your unencrypted data because Benetech doesn t have the keys to decrypt it, and they don t want them! This slide shows that WITHOUT end to end encryption, people in the middle could read what is being sent (or the data could be read if your computer is stolen/confiscated, since the data isn t encrypted there either). 20
21 And WITH end to end encryption, people in the middle cannot read anything (and also can t read what s on the computers at either end because the files are encrypted there as well) 21
22 You can choose if and how you share information with other accounts. There is no preestablished organization of a Martus system. Individuals, organizations, and groups must think through their information flow or desired information flow, and trainers support users to configure their Martus accounts to match the flow of information required. These are some of the ways that Martus accounts can be configured to send and/or receive data from others. Martus uses the language of HQ: Headquarters to describe accounts that receive data, and FD: Field Desks to describe accounts that send data. 22
23 One account can be both a Field Desk and a Headquarters account. 23
24 This may seem complicated, but it is a rather typical information flow. Several field desks report to a regional manager, who shares with the Executive Director, or something similar. Martus is flexible with regard to data sharing and can be set up to match your organization s current information flow. 24
25 You can see various field types here, including drop downs, checkboxes, grids (tables) and date range fields. 25
26 There are benefits to customization, including minimizing typing errors (which impact searching and reporting), and standardizing data across accounts. 26
27 Martus offers a robust search function, including using multiple search criteria, saving searches, specifying a field (or multiple fields) or searching all fields for text. 27
28 Martus also offers reporting, which allows users to gather certain parts of their data to be presented together. There are two reporting formats (page report and tabular report). 28
29 Table reports have one row per bulletin; Page reports display fields in the order they appear in the bulletins (you can print all fields or only a subset) 29
30 Bar and Pie charts summarize any bulletin field you select, and only those that match the search criteria you define. 30
31 Mobile Martus for Android allows for more unobtrusive use of Martus e.g. you can take a photo with your phone (or other mobile device) and very quickly back it up securely to be retrieved at a later point; especially useful if you are in a place where you are worried about your phone being confiscated etc. Write-only means that you can send bulletins to the server, to be retrieved and viewed by you or another user in the Martus client on your computer, but you cannot see the bulletins you created on the phone. Technically speaking, this is because only the part of the key used to encrypt the data (called the public key) is stored on the phone, but the part of the key used to decrypt (or read) that data (called the private key) remains only on the desktop HQ account connected to your Mobile account. You can send to Martus using the standard share functionality with other apps that create files (e.g. Gallery for photos/video) Data is encrypted on the phone and during transmission to server, after which the bulletin data is removed from the phone (the original attachment, e.g. photo in your Gallery, is not removed automatically by Martus but you can delete it after sending to Martus) 31
32 Tor can help you if you are working in a place where certain internet activity is blocked, and makes it harder for folks doing surveillance to recognize your activity. As with the Martus client on a computer, Mobile Martus will accept, encrypt, and send any kid of attachment images, videos, voice notes, text, etc 32
33 This photo was sent securely to the Martus servers using the Share or Send to feature inside the Gallery. 33
34 Tails (The Amnesic Incognito Live System) is a portable operating system that can be installed to a USB stick, DVD or SD card and booted from virtually any computer. It provides extra security by ensuring the underlying file system can t be altered, running all internet traffic through the Tor network, only ever writing to RAM (and wiping RAM at shutdown), and providing state-of-the-art encryption software out of the box. It s entirely free and open source, and when using Tails on a USB or SD card, users can install and run Martus. Tails is not necessary for all Martus users, but can provide the highest level of accessible, usable security to those who need it. 34
35 Martus is available in 12 languages (English, Spanish, Russian, Arabic, Burmese, Farsi, Vietnamese, Thai, French, Khmer, Nepali, Armenian), with others being planned (e.g. Chinese). The map above shows just some of the locations where Martus users live and work 35
36 One of Benetech s long time partners and Martus Users is the Network for Human Rights Documentation Burma, a network of a dozen organizations that collaborate using Martus to produce information about human rights violations inside Burma. 36
37 Another example of a long-time partner is the Guatemalan National Police Archive, discussed above, which has been a Martus user since
38 Some other tools that Martus users might be interested in using to protect their data and communications: PGP for encryption Pidgin (Windows/Linux) or Adium (Mac) for encrypted chat Jitsi for encrypted voice and video calls Tor for anonymity and privacy online. Benetech has integrated Tor in Martus (both on mobile and on the desktop versions). For whole disk encryption, please see "Disk Encryption" recommendations on 38
39 39
Introduction to Encryption What it s all about
 Introduction to Encryption What it s all about At MOA Project, we believe privacy and the ability to communicate without government or corporate eavesdropping is a basic right of all people. Some groups,
Introduction to Encryption What it s all about At MOA Project, we believe privacy and the ability to communicate without government or corporate eavesdropping is a basic right of all people. Some groups,
A Guide to Mobile Security For Citizen Journalists
 A Guide to Mobile Security For Citizen Journalists Your Citizen journalism, and with it the rise of alternative media voices, is one of the most exciting possibilities for mobile phones in activism. Mobile
A Guide to Mobile Security For Citizen Journalists Your Citizen journalism, and with it the rise of alternative media voices, is one of the most exciting possibilities for mobile phones in activism. Mobile
Reducing Email Threats
 Reducing Email Threats MyMail Solves Common Privacy and Security Email Threats MyMail Technology, LLC 2009 West Beauregard Avenue San Angelo, TX 76901 (866) 949-8572 www.mymail.com March 2008 REDUCING
Reducing Email Threats MyMail Solves Common Privacy and Security Email Threats MyMail Technology, LLC 2009 West Beauregard Avenue San Angelo, TX 76901 (866) 949-8572 www.mymail.com March 2008 REDUCING
How did Wiki Leaks happen?
 How did Wiki Leaks happen? A disgruntled employee with an agenda goes to work with USB flash drives and copies restricted files off of the server. There is no adequate secure network access and identity
How did Wiki Leaks happen? A disgruntled employee with an agenda goes to work with USB flash drives and copies restricted files off of the server. There is no adequate secure network access and identity
Storing and securing your data
 Storing and securing your data Research Data Management Support Services UK Data Service University of Essex April 2014 Overview Looking after research data for the longer-term and protecting them from
Storing and securing your data Research Data Management Support Services UK Data Service University of Essex April 2014 Overview Looking after research data for the longer-term and protecting them from
Backing Up Your Files. External Hard Drives
 Backing Up Your Files As we become more and more dependent on technology to help accomplish our everyday tasks, we tend to forget how easily the information stored on our computers can be lost. Imagine
Backing Up Your Files As we become more and more dependent on technology to help accomplish our everyday tasks, we tend to forget how easily the information stored on our computers can be lost. Imagine
Is your data secure?
 You re not as safe as you think Think for a moment: Where do you keep information about your congregants or donors? In an Excel file on someone s desktop computer? An Access database housed on your laptop?
You re not as safe as you think Think for a moment: Where do you keep information about your congregants or donors? In an Excel file on someone s desktop computer? An Access database housed on your laptop?
Google Drive @ Holy Family University
 Google Drive @ Holy Family University A Hard Drive in the Cloud. Access & share anything everywhere Google Docs has been retired and replaced by Drive. And if you are familiar with Google Docs, Google
Google Drive @ Holy Family University A Hard Drive in the Cloud. Access & share anything everywhere Google Docs has been retired and replaced by Drive. And if you are familiar with Google Docs, Google
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216
 Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
Last modified: November 22, 2013 This manual was updated for the TeamDrive Android client version 3.0.216 2013 TeamDrive Systems GmbH Page 1 Table of Contents 1 Starting TeamDrive for Android for the First
Avoiding Malware in Your Dental Practice. 10 Best Practices to Defend Your Data
 Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
Stable and Secure Network Infrastructure Benchmarks
 Last updated: March 4, 2014 Stable and Secure Network Infrastructure Benchmarks 501 Commons has developed a list of key benchmarks for maintaining a stable and secure IT Infrastructure for conducting day-to-day
Last updated: March 4, 2014 Stable and Secure Network Infrastructure Benchmarks 501 Commons has developed a list of key benchmarks for maintaining a stable and secure IT Infrastructure for conducting day-to-day
WDL RemoteBunker Online Backup For Client Name
 WDL RemoteBunker Online Backup For Client Name November, 2011 Contact Phone: +234 802 698 7025 Email: commercials@webdatalinks.com remotebunker@webdatalinks.com http://remotebunker.webdatalinks.com INTRODUCTION
WDL RemoteBunker Online Backup For Client Name November, 2011 Contact Phone: +234 802 698 7025 Email: commercials@webdatalinks.com remotebunker@webdatalinks.com http://remotebunker.webdatalinks.com INTRODUCTION
Storage, backup, transfer, encryption of data
 Storage, backup, transfer, encryption of data Veerle Van den Eynden UK Data Archive Looking after your research data: practical data management for research projects 5 May 2015 Overview Looking after research
Storage, backup, transfer, encryption of data Veerle Van den Eynden UK Data Archive Looking after your research data: practical data management for research projects 5 May 2015 Overview Looking after research
NCS 330. Information Assurance Policies, Ethics and Disaster Recovery. NYC University Polices and Standards 4/15/15.
 NCS 330 Information Assurance Policies, Ethics and Disaster Recovery NYC University Polices and Standards 4/15/15 Jess Yanarella Table of Contents: Introduction: Part One: Risk Analysis Threats Vulnerabilities
NCS 330 Information Assurance Policies, Ethics and Disaster Recovery NYC University Polices and Standards 4/15/15 Jess Yanarella Table of Contents: Introduction: Part One: Risk Analysis Threats Vulnerabilities
Skype for Business for Android
 Skype for Business for Android November 2015 Customization note: This document contains guidance and/or step-by-step installation instructions that can be reused, customized, or deleted entirely if they
Skype for Business for Android November 2015 Customization note: This document contains guidance and/or step-by-step installation instructions that can be reused, customized, or deleted entirely if they
Email Compliance in 5 Steps
 Email Compliance in 5 Steps Introduction For most businesses, email is a vital communication resource. Used to perform essential business functions, many organizations rely on email to send sensitive confidential
Email Compliance in 5 Steps Introduction For most businesses, email is a vital communication resource. Used to perform essential business functions, many organizations rely on email to send sensitive confidential
The Complete Guide to Email Encryption for Google Apps Administrators
 The Complete Guide to Email Encryption for Google Apps Administrators virtru.com The Complete Guide to Email Encryption for Google Apps Administrators Alarming increases in security breaches and data leaks,
The Complete Guide to Email Encryption for Google Apps Administrators virtru.com The Complete Guide to Email Encryption for Google Apps Administrators Alarming increases in security breaches and data leaks,
How to configure Mac OS X Server
 How to configure Mac OS X Server By Rob Buckley In the previous article in this series, we showed you how to secure a Mac using the functions built into its operating system, OS X. See photo story here
How to configure Mac OS X Server By Rob Buckley In the previous article in this series, we showed you how to secure a Mac using the functions built into its operating system, OS X. See photo story here
10 steps to better secure your Mac laptop from physical data theft
 10 steps to better secure your Mac laptop from physical data theft Executive summary: This paper describes changes Mac users can make to improve the physical security of their laptops, discussing the context
10 steps to better secure your Mac laptop from physical data theft Executive summary: This paper describes changes Mac users can make to improve the physical security of their laptops, discussing the context
Hiding Tracks on the Net
 Hiding Tracks on the Net Ways one might hide their tracks Private Browsing Anonymizers & Proxy Servers SSL / TLS Passwords False Information Public Networks Email Services Encryption Firewalls Private
Hiding Tracks on the Net Ways one might hide their tracks Private Browsing Anonymizers & Proxy Servers SSL / TLS Passwords False Information Public Networks Email Services Encryption Firewalls Private
Management and Storage of Sensitive Information UH Information Security Team (InfoSec)
 Management and Storage of Sensitive Information UH Information Security Team (InfoSec) Who Are We? UH Information Security Team Jodi Ito - Information Security Officer Deanna Pasternak & Taylor Summers
Management and Storage of Sensitive Information UH Information Security Team (InfoSec) Who Are We? UH Information Security Team Jodi Ito - Information Security Officer Deanna Pasternak & Taylor Summers
Chapter 8: Security Measures Test your knowledge
 Security Equipment Chapter 8: Security Measures Test your knowledge 1. How does biometric security differ from using password security? Biometric security is the use of human physical characteristics (such
Security Equipment Chapter 8: Security Measures Test your knowledge 1. How does biometric security differ from using password security? Biometric security is the use of human physical characteristics (such
HIPAA SECURITY AWARENESS
 April, 2005 HIPAA SECURITY AWARENESS Department of Mental Health, Mental Retardation, and Substance Abuse Services What is HIPAA? HIPAA means Health Insurance Portability and Accountability Act It is a
April, 2005 HIPAA SECURITY AWARENESS Department of Mental Health, Mental Retardation, and Substance Abuse Services What is HIPAA? HIPAA means Health Insurance Portability and Accountability Act It is a
Secure Email Frequently Asked Questions
 Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secure Email Frequently Asked Questions Frequently Asked Questions Contents General Secure Email Questions and Answers Forced TLS Questions and Answers SecureMail Questions and Answers Glossary Support
Secured email Global Communication version 4.6
 Secured email Global Communication version 4.6 A new and improved way to receive Secured email Authors: Daniel Nilsson and Jeff Sherwood May 11, 2010 Content Introduction...3 Secured email...4 Sending
Secured email Global Communication version 4.6 A new and improved way to receive Secured email Authors: Daniel Nilsson and Jeff Sherwood May 11, 2010 Content Introduction...3 Secured email...4 Sending
Document OwnCloud Collaboration Server (DOCS) User Manual. How to Access Document Storage
 Document OwnCloud Collaboration Server (DOCS) User Manual How to Access Document Storage You can connect to your Document OwnCloud Collaboration Server (DOCS) using any web browser. Server can be accessed
Document OwnCloud Collaboration Server (DOCS) User Manual How to Access Document Storage You can connect to your Document OwnCloud Collaboration Server (DOCS) using any web browser. Server can be accessed
www.thedatalocker.com Customer Service: 1-877-264-3715 Email Us: marketing@thedatalocker.com
 TheDataLocker online backup allows you to store, backup and retrieve any computer data over the internet to a secured remote system. Its main function is to generate a duplicate of your important files
TheDataLocker online backup allows you to store, backup and retrieve any computer data over the internet to a secured remote system. Its main function is to generate a duplicate of your important files
Why Email Encryption is Essential to the Safety of Your Business
 Why Email Encryption is Essential to the Safety of Your Business What We ll Cover Email is Like a Postcard o The Cost of Unsecured Email 5 Steps to Implement Email Encryption o Know Your Compliance Regulations
Why Email Encryption is Essential to the Safety of Your Business What We ll Cover Email is Like a Postcard o The Cost of Unsecured Email 5 Steps to Implement Email Encryption o Know Your Compliance Regulations
Avoiding Malware in Your Dental Practice. 10 Best Practices to Defend Your Data
 Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
Avoiding Malware in Your Dental Practice 10 Best Practices to Defend Your Data Avoiding Malware in Your Dental Practice Like most small business owners, you must protect your dental practice s computer
Defense Media Activity Guide To Keeping Your Social Media Accounts Secure
 Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
Guide To Keeping Your Social Media Accounts Secure Social media is an integral part of the strategic communications and public affairs missions of the Department of Defense. Like any asset, it is something
imail Frequently Asked Questions (FAQs) 27 July 2015 Version 2.2
 imail Frequently Asked Questions (FAQs) 27 July 2015 Version 2.2 Owner: Cynthia Tan IT Services Table of Contents GENERAL FAQS... 4 1. How to access to Sunway imail account?... 4 2. I can t login to my
imail Frequently Asked Questions (FAQs) 27 July 2015 Version 2.2 Owner: Cynthia Tan IT Services Table of Contents GENERAL FAQS... 4 1. How to access to Sunway imail account?... 4 2. I can t login to my
Chapter 15: Computer Security and Privacy
 Understanding Computers Today and Tomorrow 12 th Edition Chapter 15: Computer Security and Privacy Learning Objectives Explain why all computer users should be concerned about computer security. List some
Understanding Computers Today and Tomorrow 12 th Edition Chapter 15: Computer Security and Privacy Learning Objectives Explain why all computer users should be concerned about computer security. List some
Why the Fuss over Encrypting Email? Empowering People and Business through Technology SMALL AND MEDIUM BUSINESS TECHNOLOGY STRATEGIES
 Empowering People and Business through Technology SMALL AND MEDIUM BUSINESS TECHNOLOGY STRATEGIES Why the Fuss over Encrypting Email? Presented By: TS Technology Revised May 2014 Statement of Confidentiality
Empowering People and Business through Technology SMALL AND MEDIUM BUSINESS TECHNOLOGY STRATEGIES Why the Fuss over Encrypting Email? Presented By: TS Technology Revised May 2014 Statement of Confidentiality
GPG installation and configuration
 Contents Introduction... 3 Windows... 5 Install GPG4WIN... 5 Configure the certificate manager... 7 Configure GPG... 7 Create your own set of keys... 9 Upload your public key to the keyserver... 11 Importing
Contents Introduction... 3 Windows... 5 Install GPG4WIN... 5 Configure the certificate manager... 7 Configure GPG... 7 Create your own set of keys... 9 Upload your public key to the keyserver... 11 Importing
InstaFile. Complete Document management System
 InstaFile Complete Document management System Index : About InstaFile 1.1 What is InstaFile 1.2 How does it work 1.3 Where you can use InstaFile 1.4 Why only InstaFile InstaFile features and benefits Start
InstaFile Complete Document management System Index : About InstaFile 1.1 What is InstaFile 1.2 How does it work 1.3 Where you can use InstaFile 1.4 Why only InstaFile InstaFile features and benefits Start
Did you know your security solution can help with PCI compliance too?
 Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
Did you know your security solution can help with PCI compliance too? High-profile data losses have led to increasingly complex and evolving regulations. Any organization or retailer that accepts payment
Protect your personal data while engaging in IT related activities
 Protect your personal data while engaging in IT related activities Personal Data (Privacy) Ordinance Six Data Protection Principles Principle 1 purpose and manner of collection of personal data Collection
Protect your personal data while engaging in IT related activities Personal Data (Privacy) Ordinance Six Data Protection Principles Principle 1 purpose and manner of collection of personal data Collection
Gladinet Cloud Backup V3.0 User Guide
 Gladinet Cloud Backup V3.0 User Guide Foreword The Gladinet User Guide gives step-by-step instructions for end users. Revision History Gladinet User Guide Date Description Version 8/20/2010 Draft Gladinet
Gladinet Cloud Backup V3.0 User Guide Foreword The Gladinet User Guide gives step-by-step instructions for end users. Revision History Gladinet User Guide Date Description Version 8/20/2010 Draft Gladinet
Storage Guardian Remote Backup Restore and Archive Services
 Storage Guardian Remote Backup Restore and Archive Services Storage Guardian is the unique alternative to traditional backup methods, replacing conventional tapebased backup systems with a fully automated,
Storage Guardian Remote Backup Restore and Archive Services Storage Guardian is the unique alternative to traditional backup methods, replacing conventional tapebased backup systems with a fully automated,
National Cyber Security Month 2015: Daily Security Awareness Tips
 National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
National Cyber Security Month 2015: Daily Security Awareness Tips October 1 New Threats Are Constantly Being Developed. Protect Your Home Computer and Personal Devices by Automatically Installing OS Updates.
Information Security It s Everyone s Responsibility
 Information Security It s Everyone s Responsibility Developed By The University of Texas at Dallas (ISO) Purpose of Training As an employee, you are often the first line of defense protecting valuable
Information Security It s Everyone s Responsibility Developed By The University of Texas at Dallas (ISO) Purpose of Training As an employee, you are often the first line of defense protecting valuable
RingCentral Office@Hand from AT&T Desktop App for Windows & Mac. User Guide
 RingCentral Office@Hand from AT&T Desktop App for Windows & Mac User Guide RingCentral Office@Hand from AT&T User Guide Table of Contents 2 Table of Contents 3 Welcome 4 Download and install the app 5
RingCentral Office@Hand from AT&T Desktop App for Windows & Mac User Guide RingCentral Office@Hand from AT&T User Guide Table of Contents 2 Table of Contents 3 Welcome 4 Download and install the app 5
Data Security Considerations for Research
 Data Security Considerations for Research Institutional Review Board Annual Education May 8, 2012 1 PRIVACY vs. SECURITY What s the Difference?: PRIVACY Refers to WHAT is protected Health information about
Data Security Considerations for Research Institutional Review Board Annual Education May 8, 2012 1 PRIVACY vs. SECURITY What s the Difference?: PRIVACY Refers to WHAT is protected Health information about
Camtasia Relay. Release Notes. Release 2.0. April 2010. 2010 TechSmith Corporation. All rights reserved.
 Camtasia Relay Release Notes Release 2.0 April 2010 2010 TechSmith Corporation. All rights reserved. Contents Contents Introduction...3 What s New...4 System...4 Server...4 Recorder...4 Changes for Current
Camtasia Relay Release Notes Release 2.0 April 2010 2010 TechSmith Corporation. All rights reserved. Contents Contents Introduction...3 What s New...4 System...4 Server...4 Recorder...4 Changes for Current
Backups User Guide. for Webroot SecureAnywhere Essentials Webroot SecureAnywhere Complete
 Backups User Guide for Webroot SecureAnywhere Essentials Webroot SecureAnywhere Complete Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Version 8.0.1 Webroot
Backups User Guide for Webroot SecureAnywhere Essentials Webroot SecureAnywhere Complete Webroot Software, Inc. 385 Interlocken Crescent Suite 800 Broomfield, CO 80021 www.webroot.com Version 8.0.1 Webroot
1. Our staff would like to exchange files with outside parties (clients, attorneys) using a web service (such as Dropbox ). Is this safe?
 1. Our staff would like to exchange files with outside parties (clients, attorneys) using a web service (such as Dropbox ). Is this safe? The key is to do your "due diligence. Make sure that you fully
1. Our staff would like to exchange files with outside parties (clients, attorneys) using a web service (such as Dropbox ). Is this safe? The key is to do your "due diligence. Make sure that you fully
ONE Mail Direct for Mobile Devices
 ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
ONE Mail Direct for Mobile Devices User Guide Version: 2.0 Document ID: 3292 Document Owner: ONE Mail Product Team Copyright Notice Copyright 2014, ehealth Ontario All rights reserved No part of this document
Advanced Training Reliance Communications, Inc.
 Reliance Communications, Inc. 603 Mission Street Santa Cruz, CA 95060 888-527-5225 www.schoolmessenger.com Contents Contents... 2 Before you Begin... 4 Advanced Lists... 4 List Builder... 4 Create a List...
Reliance Communications, Inc. 603 Mission Street Santa Cruz, CA 95060 888-527-5225 www.schoolmessenger.com Contents Contents... 2 Before you Begin... 4 Advanced Lists... 4 List Builder... 4 Create a List...
Facebook Smart Card FB 121211_1800
 Facebook Smart Card FB 121211_1800 Social Networks - Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any
Facebook Smart Card FB 121211_1800 Social Networks - Do s and Don ts Only establish and maintain connections with people you know and trust. Review your connections often. Assume that ANYONE can see any
Concepts in Crypto. Parker Higgins parker@eff.org @xor. Micah Lee micah@eff.org @micahflee PGP: 4FF3 AA1B D29E 1638 32DE C765 9433 5F88 9A36 7709
 Concepts in Crypto Parker Higgins parker@eff.org @xor PGP: 4FF3 AA1B D29E 1638 32DE C765 9433 5F88 9A36 7709 Micah Lee micah@eff.org @micahflee PGP: 5C17 6163 61BD 9F92 422A C08B B4D2 5A1E 9999 9697 Who
Concepts in Crypto Parker Higgins parker@eff.org @xor PGP: 4FF3 AA1B D29E 1638 32DE C765 9433 5F88 9A36 7709 Micah Lee micah@eff.org @micahflee PGP: 5C17 6163 61BD 9F92 422A C08B B4D2 5A1E 9999 9697 Who
Unless otherwise stated, our SaaS Products and our Downloadable Products are treated the same for the purposes of this document.
 Privacy Policy This Privacy Policy explains what information Fundwave Pte Ltd and its related entities ("Fundwave") collect about you and why, what we do with that information, how we share it, and how
Privacy Policy This Privacy Policy explains what information Fundwave Pte Ltd and its related entities ("Fundwave") collect about you and why, what we do with that information, how we share it, and how
Technology Requirements for Using Video Conferencing with Victims
 Videoconferencing can offer survivors an alternative way to meet with a provider or counselor. For survivors who lack transportation or live too far from a program or counselor, videoconferencing may be
Videoconferencing can offer survivors an alternative way to meet with a provider or counselor. For survivors who lack transportation or live too far from a program or counselor, videoconferencing may be
Undercover. User Guide
 Undercover User Guide Contents 1. Installing and Registering Undercover 1 Undercover requirements Setting up Undercover 2. Setting up your Mac 2 Creating a dummy account Privacy Settings Setting up the
Undercover User Guide Contents 1. Installing and Registering Undercover 1 Undercover requirements Setting up Undercover 2. Setting up your Mac 2 Creating a dummy account Privacy Settings Setting up the
Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information.
 Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information. Mobile Devices: Risks to to Health Mobile Information Devices: Risks to Health Information Risks vary based on the
Mobile Devices: Know the RISKS. Take the STEPS. PROTECT AND SECURE Health Information. Mobile Devices: Risks to to Health Mobile Information Devices: Risks to Health Information Risks vary based on the
Swiftcoin is electronic money that resides on the user s computer, much like Word documents do, enabling it to be sent to anybody just as quickly and
 Overview According to Dr. Gloria Mark at the University of California, Irvine, workers are having to struggle through overflowing inboxes more than ever during their work day now. They are also checking
Overview According to Dr. Gloria Mark at the University of California, Irvine, workers are having to struggle through overflowing inboxes more than ever during their work day now. They are also checking
Presented by Todd McElmurry, Network Administrator
 Presented by Todd McElmurry, Network Administrator Why do we invest in technology? Keep business moving forward To Make Money IT should grow your business, not cost your business Be competitive Stay Connected
Presented by Todd McElmurry, Network Administrator Why do we invest in technology? Keep business moving forward To Make Money IT should grow your business, not cost your business Be competitive Stay Connected
Cloud storage buyer s guide
 Cloud storage buyer s guide for small business sponsored by 1 Table of contents Why should you read this guide? 3 Step 1: Decide how much security you need 4 Step 2: Consider what you need cloud storage
Cloud storage buyer s guide for small business sponsored by 1 Table of contents Why should you read this guide? 3 Step 1: Decide how much security you need 4 Step 2: Consider what you need cloud storage
Computer Network and Internet Security Awareness and Responsible Use. Indian River County School District 2014-2015
 Computer Network and Internet Security Awareness and Responsible Use Indian River County School District 2014-2015 1 Through the availability of electronic resources provided by the School District of
Computer Network and Internet Security Awareness and Responsible Use Indian River County School District 2014-2015 1 Through the availability of electronic resources provided by the School District of
Samsung KNOX User Guide KNOX for Consumers Edition
 Samsung KNOX User Guide KNOX for Consumers Edition Version 1.3 Jan 07, 2015 Copyright Notice Copyright 2013 Samsung Electronics Co. Ltd. All rights reserved. Samsung is a registered trademark of Samsung
Samsung KNOX User Guide KNOX for Consumers Edition Version 1.3 Jan 07, 2015 Copyright Notice Copyright 2013 Samsung Electronics Co. Ltd. All rights reserved. Samsung is a registered trademark of Samsung
Hosted Email Managed by Email Specialists
 Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Hosted Email Managed by Email Specialists The Mailtrust email system is the premium hosted email platform that provides your business with powerful, secure, and reliable email with absolutely no maintenance
Saint Martin s Catholic Academy
 Saint Martin s Catholic Academy E-Safety Policy - Acceptable Use - Students January 2015 Why have an Acceptable Use Policy? An Acceptable Use Policy is about ensuring that you, as a student at Saint Martin
Saint Martin s Catholic Academy E-Safety Policy - Acceptable Use - Students January 2015 Why have an Acceptable Use Policy? An Acceptable Use Policy is about ensuring that you, as a student at Saint Martin
Employee Active Directory Self-Service Quick Setup Guide
 Employee Active Directory Self-Service Quick Setup Guide (V2.0) Last update: 11/5/2014 Copyright 2014 InfraDog Inc. All rights reserved Corporate Phone: +1 (416) 473-4096, Fax: +1 (888) 863-3936, Email:
Employee Active Directory Self-Service Quick Setup Guide (V2.0) Last update: 11/5/2014 Copyright 2014 InfraDog Inc. All rights reserved Corporate Phone: +1 (416) 473-4096, Fax: +1 (888) 863-3936, Email:
The Security Rule of The Health Insurance Portability and Accountability Act (HIPAA) Security Training
 The Security Rule of The Health Insurance Portability and Accountability Act (HIPAA) Security Training Introduction The HIPAA Security Rule specifically requires training of all members of the workforce.
The Security Rule of The Health Insurance Portability and Accountability Act (HIPAA) Security Training Introduction The HIPAA Security Rule specifically requires training of all members of the workforce.
Responsible Access and Use of Information Technology Resources and Services Policy
 Responsible Access and Use of Information Technology Resources and Services Policy Functional Area: Information Technology Services (IT Services) Applies To: All users and service providers of Armstrong
Responsible Access and Use of Information Technology Resources and Services Policy Functional Area: Information Technology Services (IT Services) Applies To: All users and service providers of Armstrong
In the Cloud. Scoville Memorial Library February, 2013 ccayne@biblio.org
 In the Cloud Scoville Memorial Library February, 2013 ccayne@biblio.org What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the
In the Cloud Scoville Memorial Library February, 2013 ccayne@biblio.org What is the Cloud? You may have heard people using terms like the cloud, cloud computing, or cloud storage. But what exactly is the
Life after Microsoft Outlook Google Apps
 Welcome Welcome to Gmail! Now that you ve switched from Microsoft Outlook to, here are some tips on beginning to use Gmail. Google Apps What s Different? Here are some of the differences you ll notice
Welcome Welcome to Gmail! Now that you ve switched from Microsoft Outlook to, here are some tips on beginning to use Gmail. Google Apps What s Different? Here are some of the differences you ll notice
SecureAge SecureDs Data Breach Prevention Solution
 SecureAge SecureDs Data Breach Prevention Solution In recent years, major cases of data loss and data leaks are reported almost every week. These include high profile cases like US government losing personal
SecureAge SecureDs Data Breach Prevention Solution In recent years, major cases of data loss and data leaks are reported almost every week. These include high profile cases like US government losing personal
Solving the Online File-Sharing Problem Replacing Rogue Tools with the Right Tools
 White Paper Solving the Online File-Sharing Problem Replacing Rogue Tools with the Right Tools Introduction The modern workforce is on the hunt for tools that help them get stuff done. When the technology
White Paper Solving the Online File-Sharing Problem Replacing Rogue Tools with the Right Tools Introduction The modern workforce is on the hunt for tools that help them get stuff done. When the technology
Introduction to Cloud Storage GOOGLE DRIVE
 Introduction to Cloud Storage What is Cloud Storage? Cloud computing is one method to store and access data over the internet instead of using a physical hard drive (e.g. computer s hard drive, flash drive,
Introduction to Cloud Storage What is Cloud Storage? Cloud computing is one method to store and access data over the internet instead of using a physical hard drive (e.g. computer s hard drive, flash drive,
Read this guide and you ll discover:
 BUSINESS ADVISOR REPORT Provided as an educational service by: Rick Reynolds, General Manager Read this guide and you ll discover: What remote, offsite, or managed backups are, and why EVERY business should
BUSINESS ADVISOR REPORT Provided as an educational service by: Rick Reynolds, General Manager Read this guide and you ll discover: What remote, offsite, or managed backups are, and why EVERY business should
How to enable Disk Encryption on a laptop
 How to enable Disk Encryption on a laptop Skills and pre-requisites Intermediate IT skills required. You need to: have access to, and know how to change settings in the BIOS be confident that your data
How to enable Disk Encryption on a laptop Skills and pre-requisites Intermediate IT skills required. You need to: have access to, and know how to change settings in the BIOS be confident that your data
Best Practices Top 10: Keep your e-marketing safe from threats
 Best Practices Top 10: Keep your e-marketing safe from threats Months of work on a marketing campaign can go down the drain in a matter of minutes thanks to an unforeseen vulnerability on your campaign
Best Practices Top 10: Keep your e-marketing safe from threats Months of work on a marketing campaign can go down the drain in a matter of minutes thanks to an unforeseen vulnerability on your campaign
Secure Email Inside the Corporate Network: INDEX 1 INTRODUCTION 2. Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR DESKTOP ENCRYPTION 3
 A Tumbleweed Whitepaper Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop INDEX INDEX 1 INTRODUCTION 2 Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR
A Tumbleweed Whitepaper Secure Email Inside the Corporate Network: Providing Encryption at the Internal Desktop INDEX INDEX 1 INTRODUCTION 2 Encryption at the Internal Desktop 2 CURRENT TECHNIQUES FOR
Kerio Connect. Kerio Connect Client. Kerio Technologies
 Kerio Connect Kerio Connect Client Kerio Technologies 2015 Kerio Technologies s.r.o. Contents Kerio Connect Client.......................................................... 10 Kerio Connect Client.....................................................
Kerio Connect Kerio Connect Client Kerio Technologies 2015 Kerio Technologies s.r.o. Contents Kerio Connect Client.......................................................... 10 Kerio Connect Client.....................................................
Here is a guide on how to encrypt a part of your USB flash drive and access it on any computer:
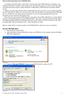 How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
How to password protect your USB flash drive. According to the XXX agency reports 80% of all lost and stolen USB flash drives contained a very important information: business or government data. The following
Outlook.com Preview. www.outlook.com. Product guide
 Outlook.com Preview Product guide 2012 Microsoft Corporation. All Rights Reserved 2 3 Contents Welcome to modern email 6 Modern 8 A fresh, clean design 10 Designed for modern devices 11 Intuitive 12 Smart
Outlook.com Preview Product guide 2012 Microsoft Corporation. All Rights Reserved 2 3 Contents Welcome to modern email 6 Modern 8 A fresh, clean design 10 Designed for modern devices 11 Intuitive 12 Smart
Using End User Device Encryption to Protect Sensitive Information
 Using End User Device Encryption to Protect Sensitive Information April 29, 2015 Mel Jackob, CISSP, GSEC, eplace Solutions, Inc. William Ewy, CIPP/US, eplace Solutions, Inc. William Ewy, BSEE, CIPP/US
Using End User Device Encryption to Protect Sensitive Information April 29, 2015 Mel Jackob, CISSP, GSEC, eplace Solutions, Inc. William Ewy, CIPP/US, eplace Solutions, Inc. William Ewy, BSEE, CIPP/US
HIPAA Email Compliance & Privacy. What You Need to Know Now
 HIPAA Email Compliance & Privacy What You Need to Know Now Introduction The Health Insurance Portability and Accountability Act of 1996 (HIPAA) places a number of requirements on the healthcare industry
HIPAA Email Compliance & Privacy What You Need to Know Now Introduction The Health Insurance Portability and Accountability Act of 1996 (HIPAA) places a number of requirements on the healthcare industry
Making Endpoint Encryption Work in the Real World
 Endpoint Data Encryption That Actually Works The Essentials Series Making Endpoint Encryption Work in the Real World sponsored by Ma king Endpoint Encryption Work in the Real World... 1 Th e Key: Policy
Endpoint Data Encryption That Actually Works The Essentials Series Making Endpoint Encryption Work in the Real World sponsored by Ma king Endpoint Encryption Work in the Real World... 1 Th e Key: Policy
School of Nursing Research Seminar. Data Security in The Academic Health Center. Presented By Jon Harper AHC Information Systems
 School of Nursing Research Seminar Data Security in The Academic Health Center Presented By Jon Harper AHC Information Systems 1 Overview of AHC-IS and Supported Services Provide desktop support to ~8500+
School of Nursing Research Seminar Data Security in The Academic Health Center Presented By Jon Harper AHC Information Systems 1 Overview of AHC-IS and Supported Services Provide desktop support to ~8500+
HIPAA Security Rule Changes and Impacts
 HIPAA Security Rule Changes and Impacts Susan A. Miller, JD Tony Brooks, CISA, CRISC HIPAA in a HITECH WORLD American Health Lawyers Association March 22, 2013 Baltimore, MD Agenda I. Introduction II.
HIPAA Security Rule Changes and Impacts Susan A. Miller, JD Tony Brooks, CISA, CRISC HIPAA in a HITECH WORLD American Health Lawyers Association March 22, 2013 Baltimore, MD Agenda I. Introduction II.
DSHS CA Security For Providers
 DSHS CA Security For Providers Pablo F Matute DSHS Children's Information Security Officer 7/21/2015 1 Data Categories: An Overview All DSHS-owned data falls into one of four categories: Category 1 - Public
DSHS CA Security For Providers Pablo F Matute DSHS Children's Information Security Officer 7/21/2015 1 Data Categories: An Overview All DSHS-owned data falls into one of four categories: Category 1 - Public
RFP Questions & Answers Housing Authority of the City of Austin - Website Design and Development
 RFP Questions & Answers Housing Authority of the City of Austin - Website Design and Development 1. Who is the primary audience for the website? Who are secondary audiences? The primary audience for the
RFP Questions & Answers Housing Authority of the City of Austin - Website Design and Development 1. Who is the primary audience for the website? Who are secondary audiences? The primary audience for the
Secure Data Exchange Solution
 Secure Data Exchange Solution I. CONTENTS I. CONTENTS... 1 II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE DOCUMENT EXCHANGE SOLUTIONS... 3 INTRODUCTION... 3 Certificates
Secure Data Exchange Solution I. CONTENTS I. CONTENTS... 1 II. INTRODUCTION... 2 OVERVIEW... 2 COPYRIGHTS AND TRADEMARKS... 2 III. SECURE DOCUMENT EXCHANGE SOLUTIONS... 3 INTRODUCTION... 3 Certificates
Security for the Road Warrior
 Security for the Road Warrior Mark K. Mellis Associate Information Security Officer Stanford University Information Security Office Version 1.1 We are all mobile We all travel from home to campus or from
Security for the Road Warrior Mark K. Mellis Associate Information Security Officer Stanford University Information Security Office Version 1.1 We are all mobile We all travel from home to campus or from
OET Cloud Services Getting Started Guide
 OET Cloud Services Getting Started Guide Introduction OET Cloud Services uses Google Drive to let you store and access OET files anywhere -- on the web, and access them on your PC, or on any device connected
OET Cloud Services Getting Started Guide Introduction OET Cloud Services uses Google Drive to let you store and access OET files anywhere -- on the web, and access them on your PC, or on any device connected
ScoMIS Encryption Service
 Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Introduction This guide explains how to implement the ScoMIS Encryption Service for a secondary school. We recommend that the software should be installed onto the laptop by ICT staff; they will then spend
Keep Yourself Safe from the Prying Eyes of Hackers and Snoopers!
 Protect Your Privacy Online P 7/1 Keep Yourself Safe from the Prying Eyes of Hackers and Snoopers! With the information in this article you can: Find out what secret information your PC is sharing with
Protect Your Privacy Online P 7/1 Keep Yourself Safe from the Prying Eyes of Hackers and Snoopers! With the information in this article you can: Find out what secret information your PC is sharing with
Qsync Install Qsync utility Login the NAS The address is 192.168.1.210:8080 bfsteelinc.info:8080
 Qsync Qsync is a cloud based file synchronization service empowered by QNAP Turbo NAS. Simply add files to your local Qsync folder, and they will be available on your Turbo NAS and all its connected devices.
Qsync Qsync is a cloud based file synchronization service empowered by QNAP Turbo NAS. Simply add files to your local Qsync folder, and they will be available on your Turbo NAS and all its connected devices.
How Endpoint Encryption Works
 WHITE PAPER: HOW ENDPOINT ENCRYPTION WORKS........................................ How Endpoint Encryption Works Who should read this paper Security and IT administrators Content Introduction to Endpoint
WHITE PAPER: HOW ENDPOINT ENCRYPTION WORKS........................................ How Endpoint Encryption Works Who should read this paper Security and IT administrators Content Introduction to Endpoint
This session was presented by Jim Stickley of TraceSecurity on Wednesday, October 23 rd at the Cyber Security Summit.
 The hidden risks of mobile applications This session was presented by Jim Stickley of TraceSecurity on Wednesday, October 23 rd at the Cyber Security Summit. To learn more about TraceSecurity visit www.tracesecurity.com
The hidden risks of mobile applications This session was presented by Jim Stickley of TraceSecurity on Wednesday, October 23 rd at the Cyber Security Summit. To learn more about TraceSecurity visit www.tracesecurity.com
Welcome to Sookasa. Getting Started Guide for SafeMonk users
 Welcome to Sookasa Getting Started Guide for SafeMonk users Welcome to Sookasa! About Us Like Safemonk, Sookasa provides Dropbox encryption to protect your information at the file level, so it s safe both
Welcome to Sookasa Getting Started Guide for SafeMonk users Welcome to Sookasa! About Us Like Safemonk, Sookasa provides Dropbox encryption to protect your information at the file level, so it s safe both
Aircloak Analytics: Anonymized User Data without Data Loss
 Aircloak Analytics: Anonymized User Data without Data Loss An Aircloak White Paper Companies need to protect the user data they store for business analytics. Traditional data protection, however, is costly
Aircloak Analytics: Anonymized User Data without Data Loss An Aircloak White Paper Companies need to protect the user data they store for business analytics. Traditional data protection, however, is costly
Qlik Sense Enabling the New Enterprise
 Technical Brief Qlik Sense Enabling the New Enterprise Generations of Business Intelligence The evolution of the BI market can be described as a series of disruptions. Each change occurred when a technology
Technical Brief Qlik Sense Enabling the New Enterprise Generations of Business Intelligence The evolution of the BI market can be described as a series of disruptions. Each change occurred when a technology
cbox YOUR FILES GO MOBILE! FOR ANDROID SMARTPHONES AND TABLETS USER MANUAL
 cbox YOUR FILES GO MOBILE! FOR ANDROID SMARTPHONES AND TABLETS USER MANUAL Introduction cbox is a software that you can easily install on your computer. Once done, an online storage drive cbox appears
cbox YOUR FILES GO MOBILE! FOR ANDROID SMARTPHONES AND TABLETS USER MANUAL Introduction cbox is a software that you can easily install on your computer. Once done, an online storage drive cbox appears
The data which you put into our systems is yours, and we believe it should stay that way. We think that means three key things.
 Privacy and Security FAQ Privacy 1. Who owns the data that organizations put into Google Apps? 2. When can Google employees access my account? 3. Who can gain access to my Google Apps administrative account?
Privacy and Security FAQ Privacy 1. Who owns the data that organizations put into Google Apps? 2. When can Google employees access my account? 3. Who can gain access to my Google Apps administrative account?
Seagate Dashboard User Guide
 Seagate Dashboard User Guide Seagate Dashboard User Guide 2013 Seagate Technology LLC. All rights reserved. Seagate, Seagate Technology, the Wave logo, and FreeAgent are trademarks or registered trademarks
Seagate Dashboard User Guide Seagate Dashboard User Guide 2013 Seagate Technology LLC. All rights reserved. Seagate, Seagate Technology, the Wave logo, and FreeAgent are trademarks or registered trademarks
Mobile Device Management (MDM) Policies
 Mobile Device Management (MDM) Policies Best Practices Guide Copyright 2012 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice.
Mobile Device Management (MDM) Policies Best Practices Guide Copyright 2012 Fiberlink Communications Corporation. All rights reserved. Information in this document is subject to change without notice.
starting your website project
 starting your website project Here are three comprehensive posts from our blog, refined and updated through feedback from our clients. Together, they cover the essentials of building a successful website.
starting your website project Here are three comprehensive posts from our blog, refined and updated through feedback from our clients. Together, they cover the essentials of building a successful website.
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
