Overview of edx Analytics
|
|
|
- Edmund Barnett
- 9 years ago
- Views:
Transcription
1 Overview of edx Analytics I. Data Available from edx EdX provides researchers with data about your institution's classes running on edx.org and edge.edx.org. This includes: Course data Student information Event tracking Courseware data Discussion forum data Wiki data Student state For more details, see Research Data Package Details. Complete data formats are described in edx Data Documentation. In addition, course staff can access some real-time course data from the Instructor Dashboard in the edx Learning Management System II. Description of edx Research Packages EdX provides two types of research data to partners who are running classes on edx.org and edge.edx.org: Log (event tracking) data Database data, including student information To access log and database data packages, you download files from edx, then extract the information from those files for analysis, as described in How Do I Get my Research Data Package? Event tracking data The edx platform gathers tracking information on almost every interaction of every student. Details about collected information are available in the Tracking Log documentation.
2 Event tracking data for your institution is collected in a file named: Date- Institution-tracking.tar. For example: UniversityA-tracking.tar When you extract the contents of this TAR file, sub-directories are created for each edx server that the course is running on. For example, you may see the following sub-directories: prod-edxapp-003 prod-edxapp-004 prod-edxapp-005 Each of these sub-directories contains a file of tracking data for each day. The TAR file is cumulative; that is, it contains files for all previous days your course was running on that server. The filename format for event tracking data files is: Date_Institution.log.gpg. For example: _UniversityA.log.gpg. You must decrypt these files. Note: Because a course runs on multiple servers, during analysis you must combine events from each server to get a complete picture of course activity. Database data Database data files are collected in a ZIP file named: Institution-Date.zip For example: UniversityA zip When you extract the contents of this ZIP file, files are placed in the same directory as the ZIP file. The filename format of extracted files is: institution-course-date-data_type-serveranalytics.sql.gpg For example: UniversityA-Physics _user_id_map-prod-analytics.sql.gpg You must decrypt these files. Data file types The data files are views on database tables used by the edx Learning Management System. The following table describes the types of data files that edx delivers.
3 Type Filename Format Description edx Data Formats Documentation Authorized Users Institution-Course-Dateauth_user-Serveranalytics.sql.gpg about users authorized to access the course. auth_user table Authorized User Profiles Institution-Course-Dateauth_userprofile-Serveranalytics.sql.gpg about student demographics. auth_userprofile table Generated Certificates certificates_generatedcertificate- Server-analytics.sql.gpg Certificate status for graded students after course completion. certificates_generatedcertificates table Courseware courseware_studentmodule- Server-analytics.sql.gpg about courseware state for each student. There is a separate row for each (UNIT?) the course. For courses that do not have any records in this table no file is produced. courseware_studentmodule table Forums Server.mongo.gpg Course discussion forum data. Discussion forum data Course Enrollment student_courseenrollment- Server-analytics.sql.gpg about students enrolled in the course, enrollment status, and type of enrollment. student_courseenrollment table User IDs Institution-Course-Dateuser_id_map-Serveranalytics.sql.gpg A mapping of user IDs and obfuscated user_id_map table
4 Type Filename Format Description edx Data Formats Documentation IDs used in surveys. Wiki articles Institution-Course-Datewiki_article-Serveranalytics.sql.gpg Course wiki data. Wiki data III. Frequently Asked Questions 1. What kind of data does edx store? EdX collects course data of two different types: stateful and event data. The stateful data includes course XML, the self-reported demographic data that students supply when they register and the posts they make to course discussions and wikis, and student answers to assessments. The event data is a timestamped record of page requests and explicit events made in a course over a period of time. 2. Who has access to edx data? Partner institutions can arrange to download raw stateful and event data for their edx courses, even while they are still in progress Course staff have access to some of the data for a course from the Instructor Dashboard, including some aggregate statistics, as soon as they create the course. 3. How is data delivered? What is a data package? To package course data and deliver it to researchers, edx uses Amazon Web Services (AWS) Simple Storage Service (Amazon S3). EdX creates an account for each partner institution on Amazon S3 that a single designated "data czar" can access. Only an institution's data czar can access S3 to download the data package, which is the collection of files that contain raw, unprocessed stateful and event data. 4. How often are data packages delivered? Data packages are available for download from Amazon S3 weekly. They are usually available on Saturdays or Sundays. 5. What do the data packages contain? Do data packages include custom reports about each of my courses? The data package contains a ZIP file with the database state, that is, the
5 stateful data, and a compressed TAR file with daily event data. The data packages contain only raw, unprocessed data, without aggregation or customizations. 6. Our university does not yet have live courses. Can we get a sample of all the data formats, so that we can begin setting up research projects now? Sample data is available only on request; however, the data formats are described in the edx Data Documentation guide. 7. What is the typical size of the data for a 7-10 week course? Data packages contain the data for all courses offered by a partner institution. They include data for courses that are in progress, not yet started, and complete, and that have different course assets and numbers of enrolled students. All of these factors have an effect on the amount of data collected for a each course. That said, in general the stateful data for a course can be approximately 100 MB or larger, and the event data can be approximately 1 GB or larger in size. 8. Is there a sample data package? An obfuscated data sample is available from edx on request. 9. What resources does a university need to have in order to start doing research with the data? Different skills and areas of expertise participate in educational research, so you are likely to need a team of contributors. The team is likely to include database administrators who can work with raw, no-sql data to set up a SQL database and queries, engineers who can interpret files in JSON and XML format, statisticians and data analysts to mine the data, and educational researchers to pose questions and interpret results. 10. What is a Data Czar? How do we get one? A data czar is the single representative of a partner institution who is given credentials to securely download and decrypt edx data packages, and who is the primary contact for data within the organization. The data czar is also responsible for transferring the data securely after it is received by your organization. After partners select an individual to be their data czar, they work with their edx Program Manager to get the required credentials set up. 11. What technical qualifications should a Data Czar have? Data czars have experience working with sensitive student data, are familiar with encryption/decryption and file transfer protocols, and can sanity check, copy, move, and store large files. Some data czars are also
6 database administrators who can work with SQL and NoSQL databases and write queries on the data after it is downloaded. 12. I am a Data Czar. How do I get data for my university? You work with your edx Program Manager to set up a public/private key pair for GNU Privacy Guard. EdX creates an account on Amazon S3, and provides your Program Manager with the credentials for account access. (See How Do I Get my Data Research Package?) You download your data packages from Amazon S3 and decrypt them using the private key. 13. I am a course author, and would like some statistics about my course. Whom should I contact? The Instructor Dashboard provides access to certain demographics, and provides options to download CSV files of student data and course grades. For complete course data and help working with it, contact your data czar and the team that is working with your institution's data to conduct research. 14. Is there documentation? The edx Data Documentation guide provides information about the data and its structure. EdX also hosts a wiki with information and a discussion forum. Getting the first Data Package 1. I am a Data Czar for an xconsortium partner University or Organization. How do I get my data packages? You download data packages from an Amazon S3 account. To access the account, you use the credentials provided by edx. Review and contact your edx Program Manager if you have not received your Amazon S3 username and credentials. 2. How many files should I be downloading for one data package? To deliver the data each week, the edx team uploads two archives of encrypted files to Amazon S3. 3. What format are the files in the data package in? What do I do to "open" the data package? The data package contains a TAR file of event data and a ZIP file of stateful data. To open the package, you uncompress each archive. Each archive contains a folder with with subfolders and encrypted GPG files.you then use your private GPG key to unencrypt the GPG files.
7 4. What encryption mechanism does edx use? You define a GNU Privacy Guard (GPG) key pair, which consists of a public key and a private key. You share only your public key with edx. EdX uses the public key to encrypt your data files before compressing them. 5. How do I decrypt the files in my data package? You use your private GPG key to decrypt the data package. Different utilities for the decryption process are available for the Windows and Mac operating systems. 6. What do all the acronyms mean what is S3, PGP/GPG, and AWS? AWS is the Amazon Web Service, an online file service for storing files. S3 is the Simple Storage Service from AWS that edx uses for transferring data packages. PGP, or pretty good privacy, is a data encryption and decryption program. GPG, or GNU Privacy Guard, is an OpenPGP replacement for PGP. Sources:
GETTING STARTED SECURE FILE TRANSFER PROCEDURES A. Secure File Transfer Protocol (SFTP) Procedures
 A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
A. Secure File Transfer Protocol (SFTP) Procedures Overview IEHP utilizes our Secure File Transfer Protocol (SFTP) server to conduct all electronic data file transactions. Some of the benefits to using
PDG Software. Encryption Guide
 Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2006 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2006 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Molina Medicaid Solutions EDI Unit sftp Companion Guide 9/5/2012
 Molina Medicaid Solutions EDI Unit sftp Companion Guide 9/5/2012 Contents Introduction... 2 Enrollment... 2 System Regions... 3 Files Sent to Molina... 3 Files Sent From Molina... 4 First Time Logging
Molina Medicaid Solutions EDI Unit sftp Companion Guide 9/5/2012 Contents Introduction... 2 Enrollment... 2 System Regions... 3 Files Sent to Molina... 3 Files Sent From Molina... 4 First Time Logging
EdX Research Guide. Release
 EdX Research Guide Release May 10, 2016 Contents 1 For Your Information 3 1.1 Read Me................................................. 3 1.2 Other edx Resources...........................................
EdX Research Guide Release May 10, 2016 Contents 1 For Your Information 3 1.1 Read Me................................................. 3 1.2 Other edx Resources...........................................
Published. Technical Bulletin: Use and Configuration of Quanterix Database Backup Scripts 1. PURPOSE 2. REFERENCES 3.
 Technical Bulletin: Use and Configuration of Quanterix Database Document No: Page 1 of 11 1. PURPOSE Quanterix can provide a set of scripts that can be used to perform full database backups, partial database
Technical Bulletin: Use and Configuration of Quanterix Database Document No: Page 1 of 11 1. PURPOSE Quanterix can provide a set of scripts that can be used to perform full database backups, partial database
File Share Service User guide
 File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
File Share Service User guide Version: 2.0 Written by: Sriram Rao Last Modified: 03/16/2012 1 Index Index... 2 Overview... 3 Change Log... 4 Login Instructions... 5 Searching files by name or content...
An Introduction to Secure Email. Presented by: Addam Schroll IT Security & Privacy Analyst
 An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
An Introduction to Secure Email Presented by: Addam Schroll IT Security & Privacy Analyst Topics Secure Email Basics Types of Secure Email Walkthroughs 2 Secure Email Services Confidentiality Message Integrity
PDG Software. PDG Key Manager User Guide
 PDG Key Manager User Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2000 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all
PDG Key Manager User Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2000 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all
PDG Software. Keyman Encryption Guide
 Keyman Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2004 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Keyman Encryption Guide , Inc. 1751 Montreal Circle, Suite B Tucker, Georgia 30084-6802 Copyright 1998-2004 PDG Software, Inc.; All rights reserved. PDG Software, Inc. ("PDG Software") retains all ownership
Secure File Transfer Protocol Updated Procedures. June 20, 2011
 Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
Secure File Transfer Protocol Updated Procedures June 20, 2011 Table Of Contents Section Subject 1 Overview 2 Installation and Environment Considerations 3 Preparing the Files for Transfer 4 Connecting
HMRC Secure Electronic Transfer (SET)
 HMRC Secure Electronic Transfer (SET) How to use HMRC SET using PGP Desktop Version 2.0 Contents Welcome to HMRC SET 1 HMRC SET overview 2 Encrypt a file to send to HMRC 3 Upload files to the Government
HMRC Secure Electronic Transfer (SET) How to use HMRC SET using PGP Desktop Version 2.0 Contents Welcome to HMRC SET 1 HMRC SET overview 2 Encrypt a file to send to HMRC 3 Upload files to the Government
Signing and Encryption with GnuPG
 Signing and Encryption with GnuPG Steve Revilak http://www.srevilak.net/wiki/talks Cryptoparty @ Somerville Public Library January 10, 2015 1 / 20 What is GnuPG? GnuPG is a free software implementation
Signing and Encryption with GnuPG Steve Revilak http://www.srevilak.net/wiki/talks Cryptoparty @ Somerville Public Library January 10, 2015 1 / 20 What is GnuPG? GnuPG is a free software implementation
Global TAC Secure FTP Site Customer User Guide
 Global TAC Secure FTP Site Customer User Guide Introduction This guide is provided to assist you in using the GTAC Secure FTP site. This site resides in the Houston Remote Services Center (RSC), and is
Global TAC Secure FTP Site Customer User Guide Introduction This guide is provided to assist you in using the GTAC Secure FTP site. This site resides in the Houston Remote Services Center (RSC), and is
Ashgate FTP Web Login
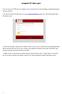 Ashgate FTP Web Login You can access our FTP site very simply via our web portal or by downloading a dedicated program (see pg. 6 below). 1. In your favourite web browser go to www.ashgatepublishing.co.uk.
Ashgate FTP Web Login You can access our FTP site very simply via our web portal or by downloading a dedicated program (see pg. 6 below). 1. In your favourite web browser go to www.ashgatepublishing.co.uk.
1. Product Information
 ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
ORIXCLOUD BACKUP CLIENT USER MANUAL LINUX 1. Product Information Product: Orixcloud Backup Client for Linux Version: 4.1.7 1.1 System Requirements Linux (RedHat, SuSE, Debian and Debian based systems such
Online Backup Client User Manual Linux
 Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
Online Backup Client User Manual Linux 1. Product Information Product: Online Backup Client for Linux Version: 4.1.7 1.1 System Requirements Operating System Linux (RedHat, SuSE, Debian and Debian based
MIS Export via the FEM transfer software
 Content 1 Introduction How does the FEM transfer actually work and how do I transfer files to Fronter for a nightly import? How does the FEM transfer tool work? What does the XML/CSV files do and can I
Content 1 Introduction How does the FEM transfer actually work and how do I transfer files to Fronter for a nightly import? How does the FEM transfer tool work? What does the XML/CSV files do and can I
Background on Elastic Compute Cloud (EC2) AMI s to choose from including servers hosted on different Linux distros
 David Moses January 2014 Paper on Cloud Computing I Background on Tools and Technologies in Amazon Web Services (AWS) In this paper I will highlight the technologies from the AWS cloud which enable you
David Moses January 2014 Paper on Cloud Computing I Background on Tools and Technologies in Amazon Web Services (AWS) In this paper I will highlight the technologies from the AWS cloud which enable you
Networks & Security Course. Web of Trust and Network Forensics
 Networks & Security Course Web of Trust and Network Forensics Virtual Machine Virtual Machine Internet connection You need to connect the VM to the Internet for some of the Web of Trust exercises. Make
Networks & Security Course Web of Trust and Network Forensics Virtual Machine Virtual Machine Internet connection You need to connect the VM to the Internet for some of the Web of Trust exercises. Make
PayFlex FTP - Wired Commute
 PayFlex FTP - Wired Commute What is FTP? FTP stands for File Transfer Protocol. PayFlex uses FTP to send and receive files from our clients. We do so through a secure website that uses PGP encryption to
PayFlex FTP - Wired Commute What is FTP? FTP stands for File Transfer Protocol. PayFlex uses FTP to send and receive files from our clients. We do so through a secure website that uses PGP encryption to
RecoveryVault Express Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Sophos for Microsoft SharePoint Help
 Sophos for Microsoft SharePoint Help Product version: 2.0 Document date: March 2011 Contents 1 About Sophos for Microsoft SharePoint...3 2 Dashboard...4 3 Configuration...5 4 Reports...27 5 Search...28
Sophos for Microsoft SharePoint Help Product version: 2.0 Document date: March 2011 Contents 1 About Sophos for Microsoft SharePoint...3 2 Dashboard...4 3 Configuration...5 4 Reports...27 5 Search...28
Capture Pro Software FTP Server System Output
 Capture Pro Software FTP Server System Output Overview The Capture Pro Software FTP server will transfer batches and index data (that have been scanned and output to the local PC) to an FTP location accessible
Capture Pro Software FTP Server System Output Overview The Capture Pro Software FTP server will transfer batches and index data (that have been scanned and output to the local PC) to an FTP location accessible
Online Backup Linux Client User Manual
 Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Online Backup Linux Client User Manual Software version 4.0.x For Linux distributions August 2011 Version 1.0 Disclaimer This document is compiled with the greatest possible care. However, errors might
Student Project 1 - Explorative Data Analysis with Hadoop and Spark
 Student Project 1 - Explorative Data Analysis with Hadoop and Spark 42matters is a rapidly growing start up, leading the development of next generation mobile user modeling technology. Our solutions are
Student Project 1 - Explorative Data Analysis with Hadoop and Spark 42matters is a rapidly growing start up, leading the development of next generation mobile user modeling technology. Our solutions are
Online Backup Client User Manual
 For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
For Linux distributions Software version 4.1.7 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by
Receiving Secure Email from Citi For External Customers and Business Partners
 Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Citi Secure Email Program Receiving Secure Email from Citi For External Customers and Business Partners Protecting the privacy and security of client information is a top priority at Citi. Citi s Secure
Experian Secure Transport Service
 Experian Secure Transport Service Secure Transport Overview In an effort to provide higher levels of data protection and standardize our file transfer processes, Experian will be utilizing the Secure Transport
Experian Secure Transport Service Secure Transport Overview In an effort to provide higher levels of data protection and standardize our file transfer processes, Experian will be utilizing the Secure Transport
Online Backup Client User Manual
 Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
Online Backup Client User Manual Software version 3.21 For Linux distributions January 2011 Version 2.0 Disclaimer This document is compiled with the greatest possible care. However, errors might have
HW/Lab 1: Email Security with PGP, and Crypto CS 336/536: Computer Network Security DUE 09/28/2015 (11am)
 HW/Lab 1: Email Security with PGP, and Crypto CS 336/536: Computer Network Security DUE 09/28/2015 (11am) This HW/Lab assignment covers Lectures 2 to 4. Please review these thoroughly before starting to
HW/Lab 1: Email Security with PGP, and Crypto CS 336/536: Computer Network Security DUE 09/28/2015 (11am) This HW/Lab assignment covers Lectures 2 to 4. Please review these thoroughly before starting to
Please note that a username and password will be made available upon request. These are necessary to transfer files.
 Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
Transferring Data Using Secure File Transfer Process ASU Center for Health Information and Research (CHiR) data partners can now securely electronically send their data submissions by means of Secure File
Amazon WorkDocs. Administration Guide Version 1.0
 Amazon WorkDocs Administration Guide Amazon WorkDocs: Administration Guide Copyright 2015 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not
Amazon WorkDocs Administration Guide Amazon WorkDocs: Administration Guide Copyright 2015 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not
MTRS 2.0 Transaction Reporting Gateway Guide
 MTRS 2.0 Transaction Reporting Gateway Guide Version 1.1 October 19, 2015 Document History Version Description of Change Date V1.0 Initial version Sept 23, 2014 V1.1 Added Certification and Enrollment
MTRS 2.0 Transaction Reporting Gateway Guide Version 1.1 October 19, 2015 Document History Version Description of Change Date V1.0 Initial version Sept 23, 2014 V1.1 Added Certification and Enrollment
TRUD Service Download Guide
 TRUD Service Download Guide TRUD Service Download Guide Contents 1 Overview... 2 2 FTP Directory Structure Overview... 3 2.1 Release Files... 5 3 Download Methods... 6 3.1 A Dedicated FTP Client (Recommended
TRUD Service Download Guide TRUD Service Download Guide Contents 1 Overview... 2 2 FTP Directory Structure Overview... 3 2.1 Release Files... 5 3 Download Methods... 6 3.1 A Dedicated FTP Client (Recommended
File Space / Web Space / Database Space - Self-Service Allocation August 2009
 File Space / Web Space / Database Space - Self-Service Allocation August 2009 All Purchase students can use this self-service application to obtain file space, web publishing space, and database space.
File Space / Web Space / Database Space - Self-Service Allocation August 2009 All Purchase students can use this self-service application to obtain file space, web publishing space, and database space.
GPG installation and configuration
 Contents Introduction... 3 Windows... 5 Install GPG4WIN... 5 Configure the certificate manager... 7 Configure GPG... 7 Create your own set of keys... 9 Upload your public key to the keyserver... 11 Importing
Contents Introduction... 3 Windows... 5 Install GPG4WIN... 5 Configure the certificate manager... 7 Configure GPG... 7 Create your own set of keys... 9 Upload your public key to the keyserver... 11 Importing
Pretty Good Privacy with GnuPG
 Pretty Good Privacy with GnuPG Steve Revilak Cabot House Sep. 24, 2013 1 / 16 Encryption and Signing Encryption The purpose is to ensure that a message is readable only by someone possessing a specific
Pretty Good Privacy with GnuPG Steve Revilak Cabot House Sep. 24, 2013 1 / 16 Encryption and Signing Encryption The purpose is to ensure that a message is readable only by someone possessing a specific
Using the Filex File Distribution System
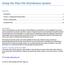 Using the Filex File Distribution System Contents Introduction... 1 Section 1: Creating and Sharing Folders... 1 Section 2: Sharing Files... 6 Important notes... 10 Introduction Filex is a file distribution
Using the Filex File Distribution System Contents Introduction... 1 Section 1: Creating and Sharing Folders... 1 Section 2: Sharing Files... 6 Important notes... 10 Introduction Filex is a file distribution
Sophos for Microsoft SharePoint Help. Product version: 2.0
 Sophos for Microsoft SharePoint Help Product version: 2.0 Document date: September 2015 Contents 1 About Sophos for Microsoft SharePoint...3 2 Dashboard...4 3 Configuration...5 3.1 On-access scan...5 3.2
Sophos for Microsoft SharePoint Help Product version: 2.0 Document date: September 2015 Contents 1 About Sophos for Microsoft SharePoint...3 2 Dashboard...4 3 Configuration...5 3.1 On-access scan...5 3.2
Security Correlation Server Backup and Recovery Guide
 orrelog Security Correlation Server Backup and Recovery Guide This guide provides information to assist administrators and operators with backing up the configuration and archive data of the CorreLog server,
orrelog Security Correlation Server Backup and Recovery Guide This guide provides information to assist administrators and operators with backing up the configuration and archive data of the CorreLog server,
Online Backup Client User Manual
 For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
For Mac OS X Software version 4.1.7 Version 2.2 Disclaimer This document is compiled with the greatest possible care. However, errors might have been introduced caused by human mistakes or by other means.
Signing and Encryption with GnuPG
 Signing and Encryption with GnuPG Steve Revilak Cryptoparty @ Northeastern Law School Feb. 9, 2014 1 / 22 What is GnuPG? GnuPG is a free software implementation of the OpenPGP standard. PGP stands for
Signing and Encryption with GnuPG Steve Revilak Cryptoparty @ Northeastern Law School Feb. 9, 2014 1 / 22 What is GnuPG? GnuPG is a free software implementation of the OpenPGP standard. PGP stands for
1. Please login to the Own Web Now Support Portal (https://support.ownwebnow.com) with your email address and a password.
 Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
Offsite Backups Introduction The purpose of this Startup Guide is to familiarize you with Own Web Now's Offsite Backup offering and show you how to purchase, deploy and manage the service. Offsite Backup
ShadowLink 2. Overview. May 4, 2015. ONLINE SUPPORT emdat.com/ticket/ PHONE SUPPORT (608) 270-6400 ext. 1
 ShadowLink 2 Overview May 4, 2015 ONLINE SUPPORT emdat.com/ticket/ PHONE SUPPORT (608) 270-6400 ext. 1 1 Interfacing with Emdat ShadowLink is an Emdat developed product that securely moves data between
ShadowLink 2 Overview May 4, 2015 ONLINE SUPPORT emdat.com/ticket/ PHONE SUPPORT (608) 270-6400 ext. 1 1 Interfacing with Emdat ShadowLink is an Emdat developed product that securely moves data between
Managing Your Class. Managing Users
 13 Managing Your Class Now that we ve covered all the learning tools in Moodle, we ll look at some of the administrative functions that are necessary to keep your course and students organized. This chapter
13 Managing Your Class Now that we ve covered all the learning tools in Moodle, we ll look at some of the administrative functions that are necessary to keep your course and students organized. This chapter
SonicWALL CDP Local Archiving
 This document describes how to configure, implement, and manage a local archive for your SonicWALL CDP appliance. It contains the following sections: Feature Overview section on page 1 Using Local Archiving
This document describes how to configure, implement, and manage a local archive for your SonicWALL CDP appliance. It contains the following sections: Feature Overview section on page 1 Using Local Archiving
Internet Programming. Security
 Internet Programming Security Introduction Security Issues in Internet Applications A distributed application can run inside a LAN Only a few users have access to the application Network infrastructures
Internet Programming Security Introduction Security Issues in Internet Applications A distributed application can run inside a LAN Only a few users have access to the application Network infrastructures
We begin with a number of definitions, and follow through to the conclusion of the installation.
 Owl-Hosted Server Version 0.9x HOW TO Set up Owl using cpanel Introduction Much of the documentation for the installation of Owl Intranet Knowledgebase assumes a knowledge of servers, and that the installation
Owl-Hosted Server Version 0.9x HOW TO Set up Owl using cpanel Introduction Much of the documentation for the installation of Owl Intranet Knowledgebase assumes a knowledge of servers, and that the installation
Unless otherwise stated, our SaaS Products and our Downloadable Products are treated the same for the purposes of this document.
 Privacy Policy This Privacy Policy explains what information Fundwave Pte Ltd and its related entities ("Fundwave") collect about you and why, what we do with that information, how we share it, and how
Privacy Policy This Privacy Policy explains what information Fundwave Pte Ltd and its related entities ("Fundwave") collect about you and why, what we do with that information, how we share it, and how
LiteCommerce Advanced Security Module. Version 2.8
 LiteCommerce Advanced Security Module Version 2.8 Reference Manual Revision date: Jul/03/2007 LiteCommerce Advanced Security Module Reference Manual I Table of Contents Introduction...1 Administrator...2
LiteCommerce Advanced Security Module Version 2.8 Reference Manual Revision date: Jul/03/2007 LiteCommerce Advanced Security Module Reference Manual I Table of Contents Introduction...1 Administrator...2
Tutorial: Encrypted Email with Thunderbird and Enigmail. Author: Shashank Areguli. Published: Ed (August 9, 2014)
 Tutorial: Encrypted Email with Thunderbird and Enigmail Author: Shashank Areguli Published: Ed (August 9, 2014) There are three issues of security that needs to dealt with on the internet, concerning information.
Tutorial: Encrypted Email with Thunderbird and Enigmail Author: Shashank Areguli Published: Ed (August 9, 2014) There are three issues of security that needs to dealt with on the internet, concerning information.
Guidance for IA DMM: Connecting Your Computer to FSU Video File Server
 1 Guidance for IA DMM: Connecting Your Computer to FSU Video File Server This guide will walk you through the process of connecting your computer to the FSU Video File Server and then uploading video files
1 Guidance for IA DMM: Connecting Your Computer to FSU Video File Server This guide will walk you through the process of connecting your computer to the FSU Video File Server and then uploading video files
This survey addresses individual projects, partnerships, data sources and tools. Please submit it multiple times - once for each project.
 Introduction This survey has been developed jointly by the United Nations Statistics Division (UNSD) and the United Nations Economic Commission for Europe (UNECE). Our goal is to provide an overview of
Introduction This survey has been developed jointly by the United Nations Statistics Division (UNSD) and the United Nations Economic Commission for Europe (UNECE). Our goal is to provide an overview of
GPG - GNU Privacy Guard
 GPG - GNU Privacy Guard How to use Károly Erdei October 15, 2014 Károly Erdei GPG - GNU Privacy Guard 1/60 1 Why 2 Cryptography 3 PGP 4 KGPG-Assistant 5 -Key-Manager 6 -Editor 7 GPG4Win 8 Enigmail Károly
GPG - GNU Privacy Guard How to use Károly Erdei October 15, 2014 Károly Erdei GPG - GNU Privacy Guard 1/60 1 Why 2 Cryptography 3 PGP 4 KGPG-Assistant 5 -Key-Manager 6 -Editor 7 GPG4Win 8 Enigmail Károly
XCloner Official User Manual
 XCloner Official User Manual Copyright 2010 XCloner.com www.xcloner.com All rights reserved. xcloner.com is not affiliated with or endorsed by Open Source Matters or the Joomla! Project. What is XCloner?
XCloner Official User Manual Copyright 2010 XCloner.com www.xcloner.com All rights reserved. xcloner.com is not affiliated with or endorsed by Open Source Matters or the Joomla! Project. What is XCloner?
DSI File Server Client Documentation
 Updated 11/23/2009 Page 1 of 10 Table Of Contents 1.0 OVERVIEW... 3 1.0.1 CONNECTING USING AN FTP CLIENT... 3 1.0.2 CONNECTING USING THE WEB INTERFACE... 3 1.0.3 GETTING AN ACCOUNT... 3 2.0 TRANSFERRING
Updated 11/23/2009 Page 1 of 10 Table Of Contents 1.0 OVERVIEW... 3 1.0.1 CONNECTING USING AN FTP CLIENT... 3 1.0.2 CONNECTING USING THE WEB INTERFACE... 3 1.0.3 GETTING AN ACCOUNT... 3 2.0 TRANSFERRING
Privacy Policy. Introduction. Scope of Privacy Policy. 1. Definitions
 Privacy Policy Introduction This Privacy Policy explains what information TORO Limited and its related entities ("TORO") collect about you and why, what we do with that information, how we share it, and
Privacy Policy Introduction This Privacy Policy explains what information TORO Limited and its related entities ("TORO") collect about you and why, what we do with that information, how we share it, and
How To Encrypt A Traveltrax Report On Gpg On A Pc Or Mac Or Mac (For A Free Download) On A Thumbdrive Or Ipad Or Ipa (For Free) On Pc Or Ipo (For An Ipo)
 EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
EMAIL ENCRYPTION Guide June 3, 2013 TABLE OF CONTENTS Steps to Create Encryption Public Key... 3 Installing GPG... 3 Key Generation Process... 4 Update User Settings... 6 Decrypting an encrypted file...
How to Create and Maintain an Anonymous Identity Online
 How to Create and Maintain an Anonymous Identity Online By Anonymous33 Email: [email protected] Revision 1 Date: 23/03/2011 WARNING: The information contained in this guide is for educational and protection
How to Create and Maintain an Anonymous Identity Online By Anonymous33 Email: [email protected] Revision 1 Date: 23/03/2011 WARNING: The information contained in this guide is for educational and protection
Report and Dashboard Template 9.5.1 User Guide
 Report and Dashboard Template 9.5.1 User Guide Introduction The Informatica Data Quality Reporting and Dashboard Template for Informatica Data Quality 9.5.1, is designed to provide you a framework to capture
Report and Dashboard Template 9.5.1 User Guide Introduction The Informatica Data Quality Reporting and Dashboard Template for Informatica Data Quality 9.5.1, is designed to provide you a framework to capture
Secure Data Transfer
 Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
Secure Data Transfer INSTRUCTIONS 3 Options to SECURELY TRANSMIT DATA 1. FTP 2. WinZip 3. Password Protection Version 2.0 Page 1 Table of Contents Acronyms & Abbreviations...1 Option 1: File Transfer Protocol
A SHORT INTRODUCTION TO CYBERDUCK WITH CLOUD OBJECT STORAGE. Version 1.12 2014-07-01
 A SHORT INTRODUCTION TO CYBERDUCK WITH CLOUD OBJECT STORAGE Version 1.12 2014-07-01 PAGE _ 2 TABLE OF CONTENTS 1. Introduction....Page 03 2. Access Cloud Object Storage using Cyberduck...Page 04 3. Create
A SHORT INTRODUCTION TO CYBERDUCK WITH CLOUD OBJECT STORAGE Version 1.12 2014-07-01 PAGE _ 2 TABLE OF CONTENTS 1. Introduction....Page 03 2. Access Cloud Object Storage using Cyberduck...Page 04 3. Create
Kickstart Your Profits With. Prosper 202. Your Quickstart Guide to Profitable Tracking. By Sheldon Gray
 Kickstart Your Profits With Prosper 202 Your Quickstart Guide to Profitable Tracking By Sheldon Gray Hi, and thanks for checking out this report on setting up the free campaign tracker, Prosper202. In
Kickstart Your Profits With Prosper 202 Your Quickstart Guide to Profitable Tracking By Sheldon Gray Hi, and thanks for checking out this report on setting up the free campaign tracker, Prosper202. In
USER GUIDE for Salesforce
 for Salesforce USER GUIDE Contents 3 Introduction to Backupify 5 Quick-start guide 6 Administration 6 Logging in 6 Administrative dashboard 7 General settings 8 Account settings 9 Add services 9 Contact
for Salesforce USER GUIDE Contents 3 Introduction to Backupify 5 Quick-start guide 6 Administration 6 Logging in 6 Administrative dashboard 7 General settings 8 Account settings 9 Add services 9 Contact
SIS Data Importer Guide for Administrators 1.0 (Beta) Contents
 SIS Data Importer Guide for Administrators 1.0 (Beta) Contents Overview Data Elements Data Refresh SIS Data Flow Calculating the preparedness indicator Displaying a set of SIS data elements in the student
SIS Data Importer Guide for Administrators 1.0 (Beta) Contents Overview Data Elements Data Refresh SIS Data Flow Calculating the preparedness indicator Displaying a set of SIS data elements in the student
Archive Document Management for Dynamics CRM
 Archive Document Management for Dynamics CRM Archive document management powered by Microsoft Dynamics CRM2011/2013 Seamless integration to Microsoft Office Outlook, Excel and Word Archive Dynamics Collaboration
Archive Document Management for Dynamics CRM Archive document management powered by Microsoft Dynamics CRM2011/2013 Seamless integration to Microsoft Office Outlook, Excel and Word Archive Dynamics Collaboration
PGP from: Cryptography and Network Security
 PGP from: Cryptography and Network Security Fifth Edition by William Stallings Lecture slides by Lawrie Brown (*) (*) adjusted by Fabrizio d'amore Electronic Mail Security Despite the refusal of VADM Poindexter
PGP from: Cryptography and Network Security Fifth Edition by William Stallings Lecture slides by Lawrie Brown (*) (*) adjusted by Fabrizio d'amore Electronic Mail Security Despite the refusal of VADM Poindexter
Introduction to Directory Services
 Introduction to Directory Services Overview This document explains how AirWatch integrates with your organization's existing directory service such as Active Directory, Lotus Domino and Novell e-directory
Introduction to Directory Services Overview This document explains how AirWatch integrates with your organization's existing directory service such as Active Directory, Lotus Domino and Novell e-directory
Simple Solution. Brighter Futures. TSDS Technical Course Module 3: Loading Data Using the DTU
 Simple Solution. Brighter Futures. TSDS Technical Course Module 3: Loading Data Using the DTU Click Course to Menu edit Master title style 2 Process Map Overview File Preparation DTU Overview DTU On Demand
Simple Solution. Brighter Futures. TSDS Technical Course Module 3: Loading Data Using the DTU Click Course to Menu edit Master title style 2 Process Map Overview File Preparation DTU Overview DTU On Demand
vcenter Operations Management Pack for SAP HANA Installation and Configuration Guide
 vcenter Operations Management Pack for SAP HANA Installation and Configuration Guide This document supports the version of each product listed and supports all subsequent versions until a new edition replaces
vcenter Operations Management Pack for SAP HANA Installation and Configuration Guide This document supports the version of each product listed and supports all subsequent versions until a new edition replaces
Webmail Using the Hush Encryption Engine
 Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
Webmail Using the Hush Encryption Engine Introduction...2 Terms in this Document...2 Requirements...3 Architecture...3 Authentication...4 The Role of the Session...4 Steps...5 Private Key Retrieval...5
How to Use the File Transfer (FTP) Service
 How to Use the File Transfer (FTP) Service How to Use the File Transfer (FTP) Service...1 What is a File Transfer Service?...2 First Steps...2 How to Upload Files to the File Transfer Service...2 How to
How to Use the File Transfer (FTP) Service How to Use the File Transfer (FTP) Service...1 What is a File Transfer Service?...2 First Steps...2 How to Upload Files to the File Transfer Service...2 How to
SAP HANA Cloud Platform Frequently Asked Questions - Business
 SAP HANA Cloud Platform Frequently Asked Questions - Business SAP HANA Cloud Platform 1. What is SAP HANA Cloud Platform? SAP HANA Cloud Platform, the in-memory Platform-as-a-Service offering from SAP,
SAP HANA Cloud Platform Frequently Asked Questions - Business SAP HANA Cloud Platform 1. What is SAP HANA Cloud Platform? SAP HANA Cloud Platform, the in-memory Platform-as-a-Service offering from SAP,
SIX Trade Repository AG
 May 2016 Please note: The SIX Trade Repository (SIX TR) has not yet been registered with FINMA. It is therefore not yet an authorized Swiss trade repository. The content of this documentation is without
May 2016 Please note: The SIX Trade Repository (SIX TR) has not yet been registered with FINMA. It is therefore not yet an authorized Swiss trade repository. The content of this documentation is without
HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA. Installation
 HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
HOW TO CONNECT TO FTP.TARGETANALYSIS.COM USING FILEZILLA Note: These instructions direct you to download a free secure FTP client called FileZilla. If you already use a secure client such as WS-FTP Pro
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3 April 8, 2016. Integration Guide IBM
 IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3 April 8, 2016 Integration Guide IBM Note Before using this information and the product it supports, read the information
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3 April 8, 2016 Integration Guide IBM Note Before using this information and the product it supports, read the information
Optimization of LMS for Improving User Response Time
 Optimization of LMS for Improving User Response Time 24 June 2014 B.RAJU (123050091) Under the guidance of Prof. Deepak B. Phatak Dept. of Computer Science and Engineering IIT Bombay Outline LMS Moodle
Optimization of LMS for Improving User Response Time 24 June 2014 B.RAJU (123050091) Under the guidance of Prof. Deepak B. Phatak Dept. of Computer Science and Engineering IIT Bombay Outline LMS Moodle
Quick Reference Guide. Online Courier: FTP. Signing On. Using FTP Pickup. To Access Online Courier. https://onlinecourier.suntrust.
 Quick Reference Guide Online Courier: FTP https://onlinecourier.suntrust.com With SunTrust Online Courier, you can have reports and files delivered to you using an FTP connection. There are two delivery
Quick Reference Guide Online Courier: FTP https://onlinecourier.suntrust.com With SunTrust Online Courier, you can have reports and files delivered to you using an FTP connection. There are two delivery
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS
 Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
Online Backup Client User Manual Mac OS 1. Product Information Product: Online Backup Client for Mac OS X Version: 4.1.7 1.1 System Requirements Operating System Mac OS X Leopard (10.5.0 and higher) (PPC
AJ Matrix V5. Installation Manual
 AJ Matrix V5 Installation Manual AJ Square Consultancy Services (p) Ltd., The Lord's Garden, #1-12, Vilacheri Main Road, Vilacheri, Madurai-625 006.TN.INDIA, Ph:+91-452-3917717, 3917790. Fax : 2484600
AJ Matrix V5 Installation Manual AJ Square Consultancy Services (p) Ltd., The Lord's Garden, #1-12, Vilacheri Main Road, Vilacheri, Madurai-625 006.TN.INDIA, Ph:+91-452-3917717, 3917790. Fax : 2484600
EdX Learner s Guide. Release
 EdX Learner s Guide Release June 28, 2016 Contents 1 Welcome! 1 1.1 Learning in a MOOC........................................... 1 1.2 A Note about Time Zones........................................
EdX Learner s Guide Release June 28, 2016 Contents 1 Welcome! 1 1.1 Learning in a MOOC........................................... 1 1.2 A Note about Time Zones........................................
ClockWork Enterprise 5
 ClockWork Enterprise 5 Technical Overview rev 5.1 Table of Contents Overview... 3 Database Requirements... 4 Database Storage Requirements... 4 Sql Server Authentication and Permissions... 5 ClockWork
ClockWork Enterprise 5 Technical Overview rev 5.1 Table of Contents Overview... 3 Database Requirements... 4 Database Storage Requirements... 4 Sql Server Authentication and Permissions... 5 ClockWork
FAQ. Hosted Data Disaster Protection
 Hosted Data Disaster Protection Flexiion is based in the UK and delivers Infrastructure as a Service (IaaS) solutions, making the advantages of the Cloud and IaaS more accessible to mid-size, professional
Hosted Data Disaster Protection Flexiion is based in the UK and delivers Infrastructure as a Service (IaaS) solutions, making the advantages of the Cloud and IaaS more accessible to mid-size, professional
1. Navigate to Control Panel and click on User Accounts and Family Safety. 2. Click on User Accounts
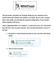 This document will guide you through setting up your outgoing server (SMTP) Microsoft Outlook and Windows Live Mail. There is also a section below that guides you through the manual configuration of your
This document will guide you through setting up your outgoing server (SMTP) Microsoft Outlook and Windows Live Mail. There is also a section below that guides you through the manual configuration of your
SOLUTION GUIDE AND BEST PRACTICES
 SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
SOLUTION GUIDE AND BEST PRACTICES Last Updated December 2012 Solution Overview Combine the best in bare-metal backup with the best in remote backup to offer your customers a complete disaster recovery
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE
 VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
VIPERVAULT STORAGECRAFT SHADOWPROTECT SETUP GUIDE Solution Overview Thank you for choosing the ViperVault cloud replication, backup and disaster recovery service. Using this service you can replicate your
Amazon Web Services EC2 & S3
 2010 Amazon Web Services EC2 & S3 John Jonas FireAlt 3/2/2010 Table of Contents Introduction Part 1: Amazon EC2 What is an Amazon EC2? Services Highlights Other Information Part 2: Amazon Instances What
2010 Amazon Web Services EC2 & S3 John Jonas FireAlt 3/2/2010 Table of Contents Introduction Part 1: Amazon EC2 What is an Amazon EC2? Services Highlights Other Information Part 2: Amazon Instances What
Submitting UITests at the Command Line
 Submitting UITests at the Command Line Overview This guide discusses how to submit your UITests tests to Xamarin Test Cloud using the command line. This scenario is appropriate for continuous integration
Submitting UITests at the Command Line Overview This guide discusses how to submit your UITests tests to Xamarin Test Cloud using the command line. This scenario is appropriate for continuous integration
IBM Campaign and IBM Silverpop Engage Version 1 Release 2 August 31, 2015. Integration Guide IBM
 IBM Campaign and IBM Silverpop Engage Version 1 Release 2 August 31, 2015 Integration Guide IBM Note Before using this information and the product it supports, read the information in Notices on page 93.
IBM Campaign and IBM Silverpop Engage Version 1 Release 2 August 31, 2015 Integration Guide IBM Note Before using this information and the product it supports, read the information in Notices on page 93.
